Unmanned aerial vehicle swarm mission reliability modeling and evaluation method oriented to systematic and networked mission
Lizhi WANG, Xujiao ZHAO, Yuan ZHANG, Xiaohong WANG,c,*,Tilin MA, Xia GAO
a Unmanned System Institute, Beihang University, Beijing 100083, China
b School of Reliability and Systems Engineering, Beihang University, Beijing 100083, China
c Digital Twinning and System Engineering Research Center,Yunnan Innovation Institute,Beihang University,Beijing 650233,China
d Key Laboratory of Advanced Technology of Intelligent Unmanned Flight System of Ministry of Industry and Information Technology, Beijing 100083, China
e School of Astronautics, Beihang University, Beijing 100083, China
KEYWORDS Complex networks;Connectivity;Mission reliability;Unmanned Aerial Vehicles(UAV);Vulnerability
Abstract With the development of Unmanned Aerial Vehicle (UAV) system autonomy, network communication technology and group intelligence theory,mission execution in the form of a UAV swarm will be an important realization of future applications.Traditional single-UAV mission reliability modeling methods have been unable to meet the requirements of UAV swarm mission reliability modeling.Therefore,the UAV swarm mission reliability modeling and evaluation method is proposed. First, aimed at the interdependence among the multiple layers, a multi-layer network model of a UAV swarm is established.At the same time,based on the system having the following characteristics—using a mission chain to complete the mission and applying the connectivity of the mission network—the mission network model of a UAV swarm is established.Second,vulnerability and connectivity are selected as two indicators to reflect the reliability of the mission,and aimed at random attack and deliberate attack, vulnerability and connectivity evaluation methods are proposed.Finally,the validity and accuracy of the constructed model are verified through simulations,
1. Introduction
With the development of aviation technology, the types and mission types of Unmanned Aerial Vehicle (UAV) systems are becoming increasingly more diverse, showing a trend of rapid development and diffusion in various civilian and military fields,such as rescue,exploration,counter-terrorism,warfare, etc. Furthermore, UAV systems have the advantages of low casualty rate,low cost,low use restrictions,good concealment, and the ability to perform missions in harsh environments.1However, single UAV is often limited by factors such as its survivability and mission capability, and it is difficult to meet the needs of complex missions.Through the communication among UAVs, information sharing and collaborating to complete missions are important means of solving the above problems, which can enhance the elasticity and flexibility of the mission.2With the development of UAV system autonomy, network communication technology and group intelligence theory, mission execution in the form of a UAV swarm will be an important realization of future applications.3
The UAV swarm is a technology that can simulate biological bee colony; it adopts the cooperative mode of multiple UAVs, and the information is shared among multiple UAVs through data networking. Thus, it can expand the perception of an environmental situation,and can complete missions such as collaborative mission assignment,4collaborative search,reconnaissance and attack. On the one hand,the UAV swarm performs the mission by distributing the mission’s various submissions and steps to a large number of communicable single UAVs with different loads, and then completing the mission systematically. Therefore, compared with other complex systems, the mission of the UAV swarm has the characteristics of vulnerability. On the other hand, the UAV swarm has certain redundancy and robustness,5,6and when it comes to multi-dimensional threats, complex environments and dynamically changing multiple collaborative missions, the success rate of the mission can be guaranteed even if some of the UAVs are lost. In view of the above characteristics, in order to make the success rate of the UAV swarm mission meet the requirements of complex missions and provide an accurate and effective quantitative basis for its design, mission planning,mission assignment,mission decision,maintenance guarantee,etc.,it is urgent to model the mission process of a UAV swarm and put forward a set of effective mission reliability indicators.
At present, a significant amount of research has been carried out in the fields of multi-UAV cooperative mission7,8and target allocation optimization9,10, swarm flight formation and control,11track planning12and UAV swarm communication.13,14The studies on mission reliability of the UAV swarm are still rarity. Traditional modeling method of single UAV mission reliability can provide certain reference, a single UAV can usually be modeled by the methods such as reliability block diagram, Bayesian network,15,16Markov model, binary decision graph, the Petri-net method,17,18etc. However, the UAV swarm is not a simple combination of single UAVs, in the process of mission implementation, the UAV swarm will emerge some new characteristics, and these characteristics are difficult to be described by traditional mission reliability modeling methods. As a mission system, it has a multidimensional hierarchical structure, such as physical system layer, communication layer and mission layer,19and there are complex logical cross-linking relationships. At the same time,the organizational form is constantly evolving and reconstructing at any time and space, and the transmission form of failure and risk in the system and its impact on missions are also different from those in single-UAV systems.20–23
In the field of UAV swarm reliability research, We19conducted an in-depth study that models the reliability method of UAV swarms by using complex network methods.Although the work is mainly focused on basic reliability and robustness characteristics,it can be used as the basis for UAV swarm reliability research. The UAV swarm system includes multiple UAV systems, payloads and a data communication network composed of multiple UAVs; at the same time, the network layers are not independent of each other, and there are dynamic interactions and related relationships. These characteristics are similar to critical infrastructure networks, so the current work on mission reliability in the field of infrastructure can provide some theoretical support for the research on mission reliability modeling of UAV swarms. Based on the complex network method, certain results about mission reliability have been proved effective in the field of critical infrastructure such as power grid,24traffic network,25and communication network.Thacker et al.26abstracted key urban infrastructures such as natural gas networks, transportation networks, power grids and water supply networks into multi-level complex network models to analyze network fault propagation and then to evaluate network reliability. Chen27applied a scale-free network model to model a power grid and analyzed its vulnerability. Aldrich et al.28and Xu and Sui29used the small world network model to characterize transportation networks.However, the UAV swarm is different from infrastructure such as transportation networks. For example, a UAV swarm is a multi-dimensional space operation and dynamic reconfiguration system, and the way a mission executes in complex networks is different from an infrastructure system, so the existing mission reliability modeling methods cannot be utilized directly.
Therefore, based on the existing theoretical methods and research foundations, aimed at the characteristics of UAV swarm mission operation,this paper uses the complex network method to model the UAV swarm mission process and proposes a set of effective mission reliability indicators. In this way, this study provides quantitative reference for UAVswarm-related decision-making work, and supports the development of UAV-swarm-related work.
The rest of this paper is organized as follows: In Section 2,the mission characteristics of UAV swarm are analyzed, and based on the complex network method, the mission network is modeled based on connectivity and the interlayer relationship is modeled based on interlayer dependencies.In Section 3,aimed at random attack and deliberate attack,according to the mission characteristics of a UAV swarm, vulnerability and connectivity are selected to evaluate the mission reliability of a UAV-swarm mission network.In Section 4,the effectiveness of the method is illustrated by a case study.In Section 5,some conclusions and planned future work are given.
2. Modeling UAV swarm system
2.1. Mission characteristics of UAV swarm
The UAV swarm system refers to a complex system in which multiple UAVs cooperate, and UAVs share information through data networking, so it can expand the perception of environmental situation and cooperate to accomplish missions such as mission allocation,cooperative search, reconnaissance and attack30. In general, the basic components of the UAV swarm system include vehicles, payloads and communication datalinks,31and its composition is shown in Fig. 1.
The UAV swarm is usually in motion, and the distance between vehicles in the UAV swarm is constantly changing;however, in order to facilitate the control of the swarm or to complete specific missions, a UAV swarm will be in a certain structure.In general,its structure is related to the control strategy, and we chose three structures of a UAV swarm based on three types of control algorithms, namely a control structure based on the behavior-based method (Structure 1), on leader–follower strategy (Structure 2) and on autonomous control (Structure 3).19
Complex network has the good model description ability,32,33and in order to study the complex interaction and dynamic relationship in the UAV swarm system,the compositions of the UAV swarm system are mapped to the nodes of a multi-layer complex network.First,the UAV swarm system is divided into three layers according to its system composition and function, which are UAV swarm communication layer,structural layer and mission layer. The three layers of the network correspond to the communication datalink, vehicle and payload of the UAV swarm.In the network,both the communication layer and the mission layer nodes are based on the nodes in the UAV structure network.
If H is used to denote edges between the UAV swarm layers,then H = { Hi} (i = 1,2,...,n),where n is used to denote the number of nodes in each layer, and H mainly refers to the connection between the structural layer node and the communication layer node, the structural layer node and the mission layer node. The structure diagram of the established UAV swarming network is shown in Fig. 2. The standardized description of the network is shown in Table 1.
It can be seen that: (A) there is a bidirectional connection between layers,for example,the layer Gadepends on the layer Gbthrough some connections, and the layer Gbalso depends on the layer Gathrough these same connections or other connections. The three layers of networks are interconnected and interdependent, and they form a system. The mission network is affected by the multi-layer network nodes, and each layer has an impact on it;therefore,the mission of the UAV swarm is characterized by its vulnerability.(B)Since the UAV swarm completes the mission in one system, the related payloads are distributed on different single UAVs, and the missions represented by the mission network can be divided into different types of sub-missions according to the order of execution of the missions; different sub-missions correspond to different payloads. As shown in Fig. 3, the connection order of submissions is Sub-mission 1 →Sub-mission 2 →Sub-mission 3 →Sub-mission 4 →Sub-mission 5, if each type of payload exists in the mission network, and they are connected in the specified order,as indicated by the red dotted line(this connection is called the mission chain).As long as the mission chain is connected, the mission network is connected, and the mission network has the ability to complete missions. Therefore, the mission network has the characteristics of connectivity. At the same time, the payload in the mission network is redundant,and the mission network is robust.Therefore,the swarm system can still guarantee the ability to complete the mission even if it is attacked during the mission.19
By considering the above characteristics of the UAV swarm mission process, the algorithm that models the mission network by considering connectivity is introduced in Section 2.2.Based on this, a modeling algorithm that considers inter-level dependencies is introduced in Section 2.3.
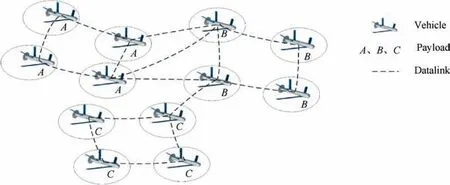
Fig. 1 Schematic diagram of composition of UAV swarm system.
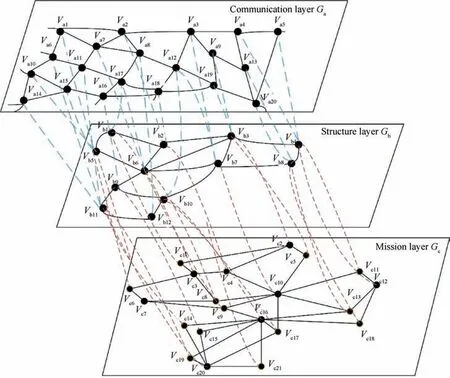
Fig. 2 Schematic diagram of interdependence among three layers of network of UAV swarm.
2.2. Modeling mission network by considering connectivity
According to the connectivity characteristics of the mission network,the model of the UAV swarm mission network is carried out as follows:
(1) Initialization.The mission network consists of payloads.According to the complex network theory, the mission payload is mapped to the nodes of the swarm mission network. Determine the number of nodes and location distribution of the mission network according to the system load configuration and mission order.Suppose that n nodes are generated for the mission network,the number of mission payload types is m, and the number of nodes under each payload is ni(i=1,2,...,m), where n1+n2+···+nm=n.
(2) Connection.
(A) Specify the connection order of different kinds of payloads. If it is assumed that there are four payloads (A, B, C, D) in the mission network, the connection order is specified as A →B →C →D.
(B) Only the two adjacent nodes in the specified connection order can be connected, that is, only the payloads between A, B, C, D are connected to each other.
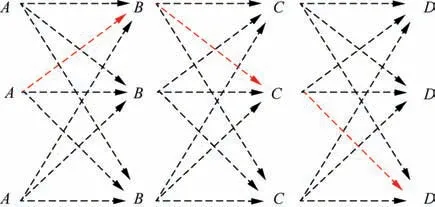
Fig. 4 Schematic diagram of payload topology relationship.
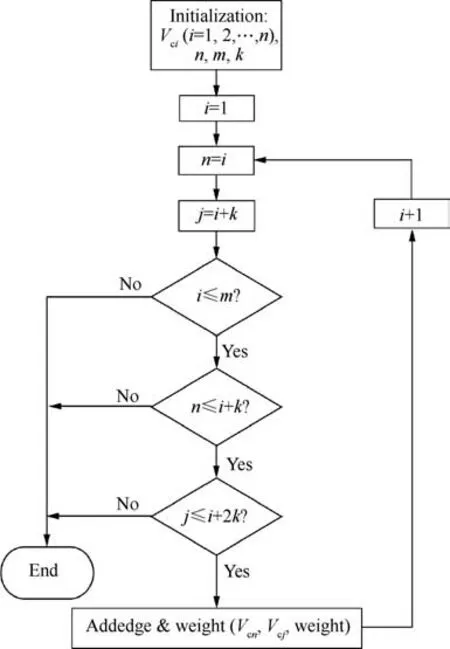
Fig. 5 Modeling algorithm for mission layer.
(C) Different kinds of payloads are connected according to the free combination algorithm, that is, if the number of payloads corresponding to the four payloads are n1, n2, n3, n4,respectively,there are a total of n1n2n3n4connection methods.
(D) When connecting, there can be no repeated edge between the two nodes, and there can be no selfloop.
(E) The topology structure of the payload relationship in the mission network is shown in Fig. 4.
(3) Weight. The edges in the mission layer have no specific weight,and the weights can be randomly assigned within a certain range to simulate the dynamic changes of the network.
(4) Ending. When all nodes, edges, and weights in the network are generated, the constructed network is output.
When different kinds of payloads are connected in a prescribed order to form a mission chain (i.e.,A →B →C →D,as shown in Fig.4 red chain),and any payload on the mission chain is destroyed,indicating that the connectivity of the mission chain is destroyed, then the mission chain cannot complete the specified missions. Regardless of its multiple states (i.e., only good and bad states), when there is no complete mission chain in the mission network, the mission network fails.
The pseudo code for the process is shown in Fig. 5.
2.3. Inter-level modeling considering dependencies
The three-layer network of the UAV swarm is interconnected and interdependent.The mission network is a network affected by the multi-layer network nodes, and each layer has an impact on it. There are two interdependent relationships.One is the communication node and the mission node attached to the structure point.When the structure node is removed,the communication node and the mission node connected to it are also removed correspondingly.The process is shown in Fig.6.The other depends on the mission node of the communication node. When the communication node fails, the mission node will be disabled, and the network mission layer node will be removed accordingly. The process is shown in Fig. 7.
According to the interdependence characteristics of the three-layer network,the modeling of the interlayer relationship is carried out. Specifically, the interlayer relationships can be described as follows:
(1) The node Vaiof the communication network is connected to the node Vbiof the structural network in one-to-one correspondence.
(2) The node Vbiin the structural network arbitrarily chooses a connection to the unselected nodes Vci, Vcj,... in the mission network.
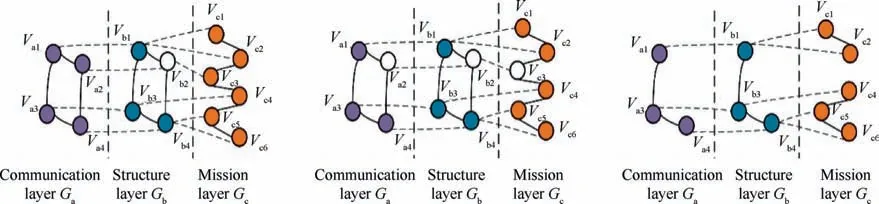
Fig. 6 Schematic diagram of interdependence 1.
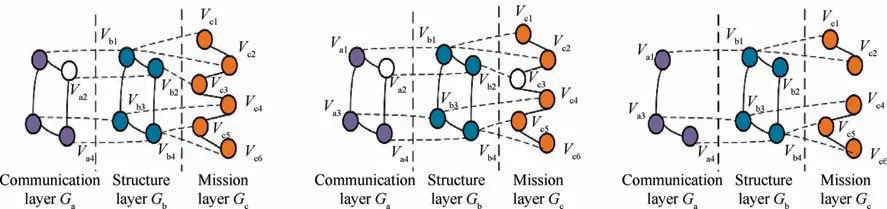
Fig. 7 Schematic diagram of interdependence 2.
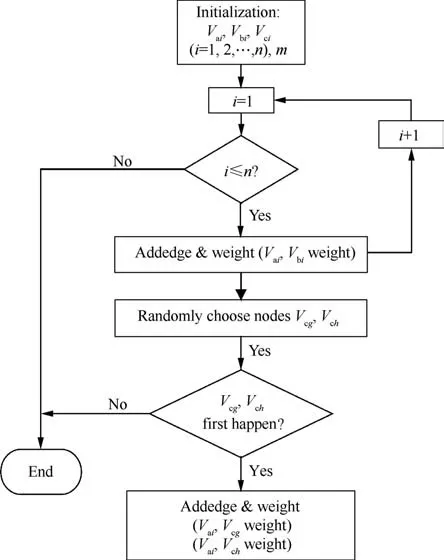
Fig. 8 Modeling algorithm for interlayer relationship.
(3) When connecting, there can be no repeated edge between the two nodes, and there can be no self-loop.Based on the above description, a multi-level, differentiated,and interrelated UAV swarming network model is established. The pseudo code for the process is shown in Fig. 8.
These algorithms are modular and scalable,since the UAV swarm system can change or reconstruct as necessary based on the mission or modeling objectives. Moreover, they can be guidelines for modeling a UAV swarming network with programming or other computer tools.
3. Evaluating mission reliability
The architecture of the UAV swarm has a mission-oriented feature, that is, its strategy and architecture are formed and developed according to missions. To ensure the mission completion rate,and to ensure that the UAV swarm has high mission reliability, reasonable indicators for evaluating mission reliability need to be put forward. This paper focuses on the impact of topology and attack strategies on the reliability of complex networks.
3.1. Topological properties of complex networks
3.2. Mission reliability indicator
For a complex network of the UAV swarm, a single UAV crash has little effect on the entire UAV swarm and can be corrected by mission reconstruction; therefore, from the perspective of mission completion,it is not the focus of attention.The focus is on how many UAVs crash and how that will affect mission completion; that is, we need to pay attention to the reliability of the system mission. The reliability of the mission refers to the possibility of completing the mission as required.Based on the analysis of the mission characteristics of the UAV swarm in Section 2.1,we select vulnerability and connectivity as two indicators to reflect the reliability of the mission.
(1) Vulnerability. Vulnerability refers to whether a system can easily lose its ability to accomplish a specified mission due to external factors.35It has been studied in infrastructure systems such as power systems,36water resources systems,37and grid systems.38For the UAV swarm system, it is very sensitive to external influence,and small fluctuations sometimes can have a marked impact on the system, which makes the whole system lose the ability to complete the specified mission. This is an important feature of the UAV swarm system.Therefore, according to the definition of vulnerability,the vulnerability is chosen as the indicator of the UAV swarm’s mission reliability.
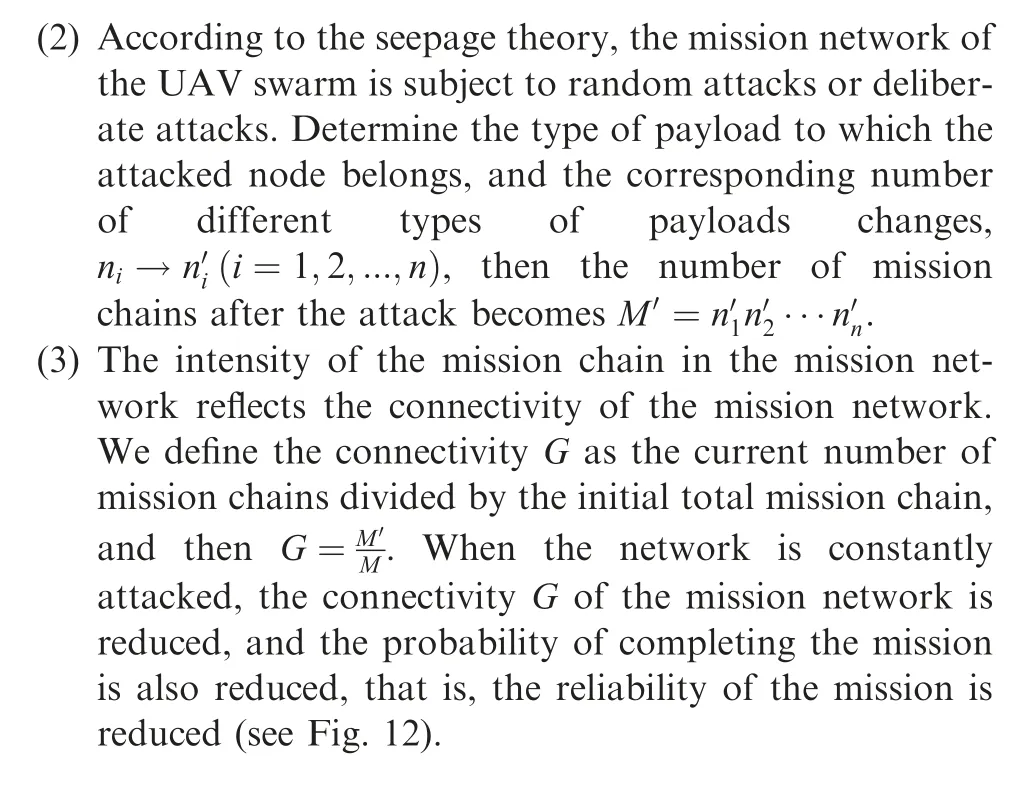
(2) Connectivity. Connectivity is an important indicator of network performance and determines the quality of the entire network. The UAV swarm mission network can complete missions only if each type of payload exists and they are connected in the specified order, different types of payload form a complete mission chain, and missions are accomplished in the form of chains. Due to redundancy, there are multiple mission chains in the network.And the greater the number of connected mission chains, the higher the success rate of the mission.Therefore, the connectivity of the mission network can be characterized by the change in the number of mission chains and the connectivity is chosen as the indicator of the UAV swarm’s mission reliability.
3.3. Evaluation methods and evaluation strategies
When evaluating the impact of an attack strategy on the reliability of a complex network, the attack strategy is usually classified into a random attack and a deliberate attack.A random attack is a complete random removal of a certain percentage of nodes from the network; deliberate attacks are the removal of a certain percentage of nodes39,40in a defined order(for example, by the number of connected nodes). The completely random removal method can be mainly related to the random failure of the nodes in the network system in the UAV swarm system. The node removal method according to the importance degree of the node is suitable to reflect the deliberate external attack of the nodes in the UAV swarming network.
3.3.1. Vulnerability
Vulnerability of the mission network is the ability to complete the specified missions when the mission network is attacked.Seepage theory is commonly used to study the situation of complex networks being attacked. Generally, the attack strategy is divided into two methods: node attack and edge attack.The seepage model is a model abstracted from many practical problems41and uses graph theory and phase transition theory to analyze changes in complex network structures.42,43For a network,seepage usually includes both point and side seepage.Point seepage refers to removing a certain proportion of vertices and edges connected to these vertices in a certain way in the network.Side seepage refers to the removal of a portion of the edge in a certain way in the network.Both types can be described by a parameter (occupation probability p): p represents the probability that a vertex or edge still exists.44
As the number of deleted points or edges increases,the network changes from a connected state (functional state) to a non-connected state (non-functional state), and the connectivity of the network changes. For a point seepage or edge seepage of a given network45(see Fig. 9), when the occupancy probability p becomes larger than zero, the largest subgroup of the network will appear at a certain critical probability value Pc. Its proportion in the entire network will continue to grow with the growth of occupation probability. This critical value Pccan be obtained by theoretical calculation of seepage theory or computer simulation.
The size of Pccan be used as an indicator to measure the vulnerability of the original network to an attack or failure.The smaller the value of Pc, the more vertices (or edges) need to be removed to make the largest subgroup disappear, which can resist a large number of node failures without crashing,indicating that the network is not vulnerable.For random networks and scale-free networks,Pchas different performance in the face of random attacks and deliberate attacks.40
(1) For random attacks
The seepage threshold of the network is
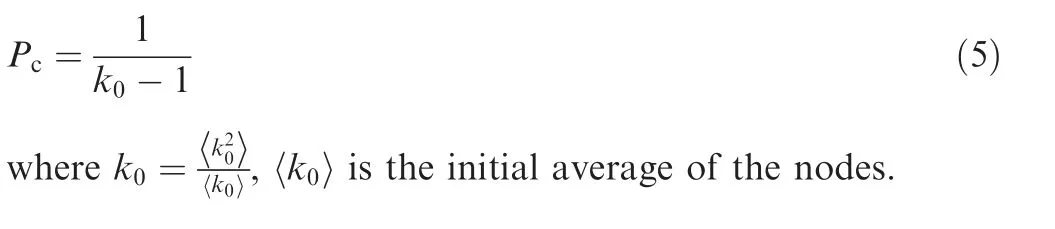
Fig. 9 Schematic diagram of network seepage.
The random ER network degree distribution obeys the Poisson distribution, so we can obtain
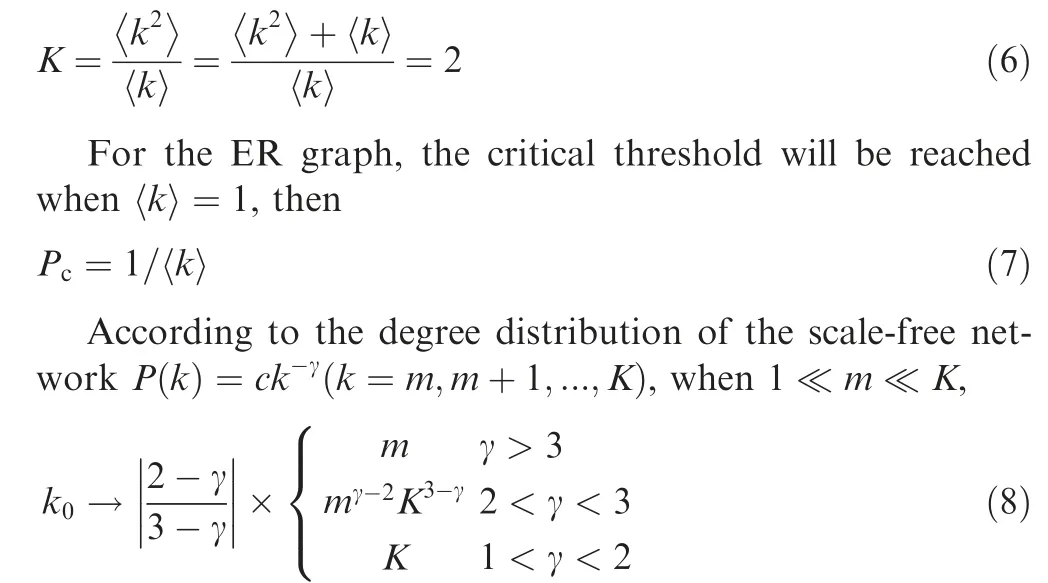
As can be seen from the above formula,
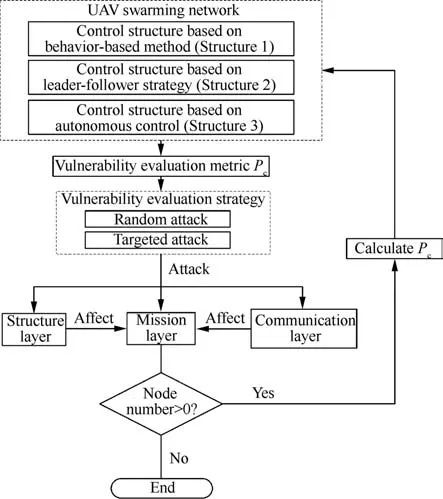
Fig. 10 Vulnerability evaluation flowchart.
(A) When γ>3, the ratio k0is limited,

(B) When γ<3,the ratio k0diverges with K.When K →∞or N →∞, Pc→0; when the network size is limited(N ≪∞), the phase change value k0≈K1/2≈N1/3can always be observed.
(2) For deliberate attacks
In a homogeneous network,such as an ER network,the degree of difference between a node with a higher degree and a node that is randomly selected is not very large.Therefore,although the thresholds are different, there is no significant difference between the deliberate attack process and the random attack process in the random network.
However, in scale-free networks, deliberate attacks cause more severe damage than random attacks, and seepage phase transitions (for limited Pc) occur for all γ>2. As γ increases,Pcdecreases. When γ>2, the decrease of Pccauses only a few nodes to have a large degree,and their removal will affect the entire network. Note that for an infinite system, when γ →2, Pc→0 (see Fig. 10).
3.3.2. Connectivity
According to the network built in Section 2, when the UAV swarm is subjected to random attacks or deliberate attacks,as shown in Fig.11,the corresponding payload fails,the number of payloads in the mission network changes,and the number of mission chains changes. Correspondingly, the connectivity of the mission network is reduced. Therefore,the connectivity of the mission network can be characterized by the change in the number of mission chains and used as an indicator to measure the reliability of the mission network.
The process is as follows:
(1) In the initial state,it is assumed that the number of payloads of each type is ni(i=1,2,...,n),and the number of initial total mission chains is M =n1n2···nnaccording to the principle of free combination.
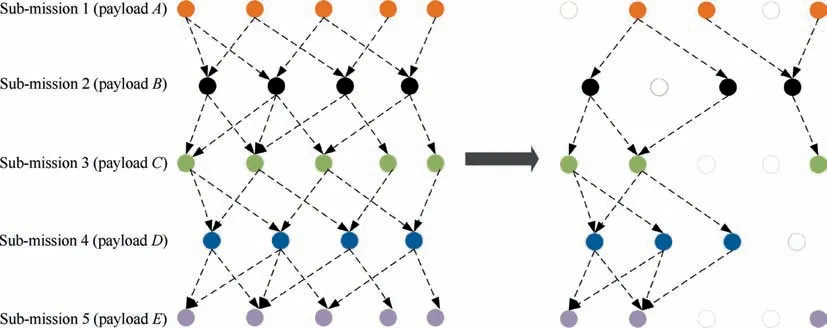
Fig. 11 Mission network connectivity changes.
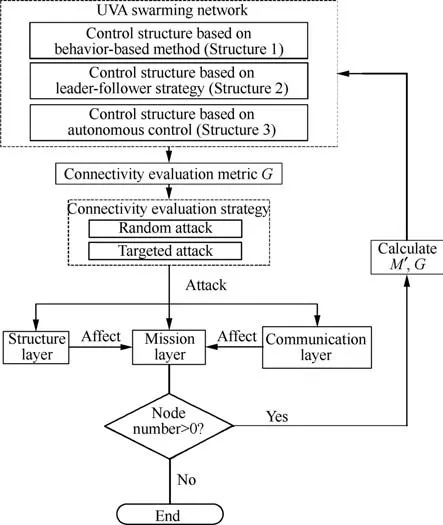
Fig. 12 Connectivity evaluation flowchart.
4. Case study
To illustrate the network modeling process of a UAV swarm system, a case study with the characteristics described in Section 2 is presented. Python NetworkX is used to program the modeling algorithm to present the network structure and conduct further analysis of the statistical feature of the network. Note that the network is built through the properties of the UAV swarm system and three types of control structure,so it can be applied in many mission scenarios. However, the validity of a modeling network using complex-network theory is unknown.Therefore,in Section 4.2,the statistical characteristics of the proposed network are compared with real-world networks to test its validity.
4.1. Model description
Suppose a UAV swarm system consisting of 55 small UAVs in which each UAV carries two payloads to execute a certain mission and there are five types of loads in the mission network.Based on the description in Section 2, three scenarios corresponding to the three structures are considered. The nodes of the communication layer, the structure layer, and the mission layer in these complex networks are expressed as blue, red,and yellow dots, respectively. The black lines in Fig. 13 represent the edges.
The network for the control structure of behavior-based methods is depicted in Fig. 13(a). In this structure, the topology of the UAV swarm system is set to be a classic pigeon flock with one ‘‘leader”.
For Structure 2,suppose there are five leaders and each one has eleven followers in the UAV swarm system.The entire network of Structure 2 is shown in Fig. 13(b).
For Structure 3, let each vehicle connected to four to five adjacent ones consist of a swarm system with random topology. The network of Structure 3 can be seen in Fig. 13(c).
Among them, the complex network model of the mission network is shown in Fig. 13(d).
4.2. Topology analysis
We obtain the indicator values, such as the degree of the network mode, the clustering coefficient, and network efficiency through a topology analysis of the three kinds of UAV mission networks to determine whether the network has any scale characteristics.
To identify the features of scale-free networks, the degree distribution of nodes is estimated to check whether it follows a power-law distribution, i.e.,

where P(k) denotes the proportion of nodes with a node degree of k, c is the coefficient, and λ is the power-law value.
The distribution of degree is calculated with Eq. (10) and then we use a linear fitting method to fit these data and depict their logarithmic relationship. The results are illustrated in Fig. 14. Based on the results and from the perspective of a complex network, the node distributions of all of the three structures generally conform to a power-law decay function with R2greater than 0.8. Thus, the UAV swarming networks have the topological properties of the scale-free network.One can know from the characteristic of the scale-free network that this network may be highly resistant to random attacks and be quite sensitive to a targeted attacky.46
4.3. Mission reliability evaluation
According to the seepage theory, the reliability analysis of the mission network of the UAV swarm is carried out.For the two attack strategies of random attack and deliberate attack, vulnerability indicators and connectivity indicators reflecting mission reliability are analyzed separately.
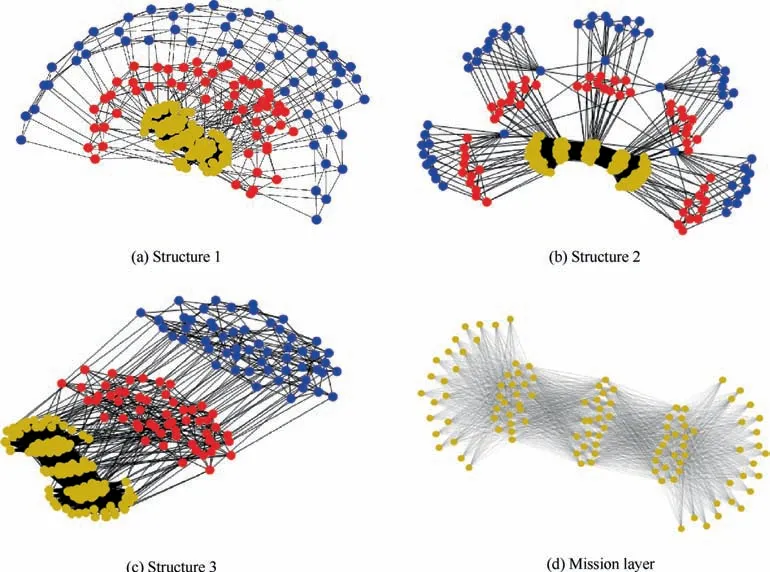
Fig. 13 Network of UAV swarm system.
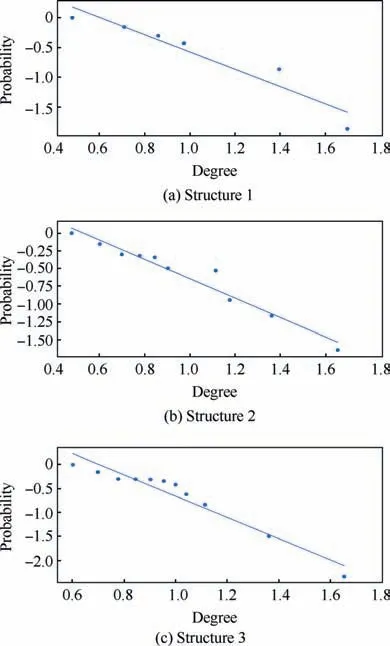
Fig. 14 Cumulative distribution of degree of Structure1, Structure 2 and Structure 3.
4.3.1. Vulnerability
According to the analysis in Section 4.2, the mission network satisfies the scale-free characteristics,and the ER network theory Pcis

where k〈 〉 is the average node degree.
To express more intuitively the changes in the UAV swarm mission network as the node attacks,normalizing the data can still highlight the essential meaning of physical quantities.
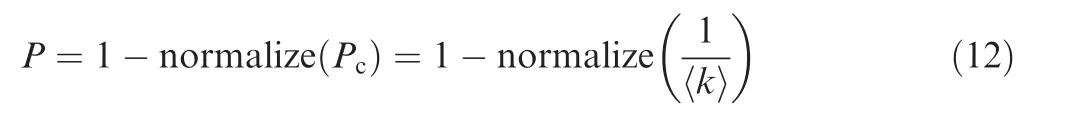
According to the seepage theory, the random attack and deliberate attack of the mission network of the UAV swarm are simulated,and the vulnerability change of the mission network is observed. For random attacks, see Fig. 15(a). For deliberate attacks, see Fig. 15(b).
It can be seen that as the number of nodes being attacked increases, the mission network becomes more and more vulnerable. For random attacks, nodes are randomly removed until all nodes in the mission layer are removed, and the vulnerability after removing the nodes is calculated. When the attacked node is controlled within 100 nodes, the network is relatively stable. Once it exceeds 100 nodes, the vulnerability of mission network increases sharply and the corresponding P value decreases sharply. For deliberate attacks, nodes are removed in order according to the node degree until all nodes in the mission layer are removed, and the vulnerability after removing nodes is calculated. When the attacked node is controlled within 80 nodes,the network is relatively stable.Once it exceeds 80 nodes, the vulnerability of mission network increases sharply and the corresponding P value decreases sharply.It can be seen that the constructed mission network is more resistant to random attacks and less resistant to deliberate attacks. This is also a good proof that the scale-free network is highly resistant to random damage, but it is very vulnerable to deliberate attacks,which verifies the effectiveness of the model.
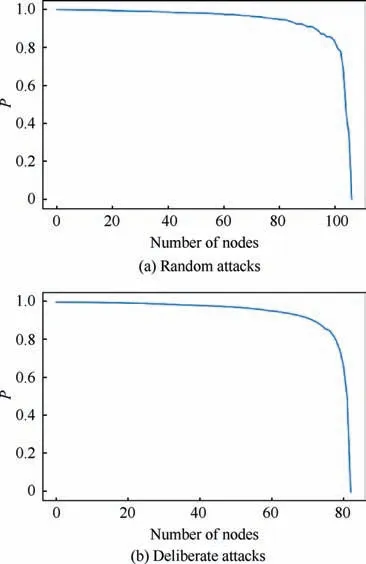
Fig. 15 Vulnerability with random and deliberate attacks.
4.3.2. Connectivity
Taking the autonomous control structure as an example, the mission network is composed of five types of mission payloads,and each of the same types has 22 identical payloads. By analyzing the information in Section 3.3, it can be concluded that

Therefore, the total number of mission chains in the initial state is

By using seepage theory, the random attack and deliberate attack of the mission network of the UAV swarm are simulated, and the connectivity change of the mission network is observed. For random attacks, see Fig. 16(a). For deliberate attacks, see Fig. 16(b).
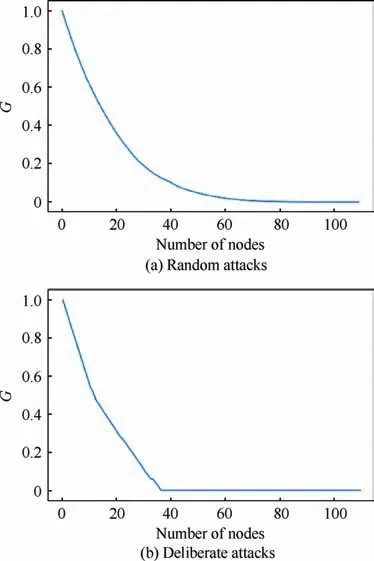
Fig. 16 Connectivity with random and deliberate attacks.
It can be seen that as the number of nodes being attacked increases, the connectivity of the mission network becomes worse and worse. As the number of nodes decreases, the connectivity change of random attacks remains relatively flat with respect to deliberate attacks. For random attacks, the nodes are randomly removed until all nodes in the mission layer are removed, and the connectivity is then calculated. When the attacked node reaches 60, the connectivity of the mission network is reduced to zero;that is,the mission network cannot complete the specified mission. For deliberate attacks, nodes are removed in order according to the node degree until all nodes in the mission layer are removed, and the connectivity is then calculated. When the attack node reaches 40, the connectivity of the mission network is reduced to zero, that is,the mission network cannot complete the specified mission.
5. Conclusions and future work
The UAV swarm performs the mission by distributing the mission’s various sub-missions and steps to a large number of communicable single UAVs with different loads, and then completing the mission systematically. Mission reliability assessment is very important and challenging. Traditional single-UAV mission reliability modeling methods have been unable to meet the requirements of UAV swarm mission reliability modeling. Therefore, the research of mission reliability modeling and evaluation method for UAV swarms is conducted.
(1) We combine complex network theory with a UAV swarm system, aiming at the interdependence among the communication layer, the structure layer and the mission layer of the UAV swarm,and a multi-layer network model of UAV swarm is established. Three structures of a UAV swarm based on three types of control algorithms are presented, namely a control structure based on the behavior-based method (Structure 1), on leader–follower strategy (Structure 2) and on autonomous control (Structure 3). At the same time, based on the system having the following characteristics—using a mission chain to complete the missions and applying the connectivity of the mission network—the mission network model of the UAV swarm is established.
(2) According to the interdependent and interconnected mission characteristics of the UAV swarm,vulnerability and connectivity are selected as two indicators to reflect the reliability of the mission. Based on seepage theory,the mission network of UAV swarm is analyzed, and aimed at random attack and deliberate attack, vulnerability and connectivity evaluation methods are proposed.
(3) The typical control structure of the UAV swarm is analyzed through a case study. The static and dynamic topology analysis of the mission network is carried out.The static analysis shows that the UAV swarm network meets the scale-free characteristics, and the accuracy and effectiveness of the model are verified. At the same time, dynamic analysis shows that the established UAV swarming network can provide a theoretical basis for further analysis of the network(such as vulnerability or connectivity). The UAV swarm system can meet the requirements of complex missions, providing an accurate and effective quantitative basis for their design,mission planning, mission assignment, mission decision,maintenance support, and other aspects, and can support the development of the UAV swarm-related work.
In the future,real data of the UAV swarm will be collected to verify the proposed method, the weight of the mission network will be given,and more indicators to evaluate the mission reliability of UAV swarm will be proposed. Therefore, it will provide guidance for decision-making of UAV swarms.
Acknowledgements
This study was co-supported by the Fundamental Research Funds for the Central Universities, China (No. YWF-19-BJJ-340) and Field Foundation of China (No.JZX7Y20190242012001).
 CHINESE JOURNAL OF AERONAUTICS2021年2期
CHINESE JOURNAL OF AERONAUTICS2021年2期
- CHINESE JOURNAL OF AERONAUTICS的其它文章
- Recent active thermal management technologies for the development of energy-optimized aerospace vehicles in China
- Electrochemical machining of complex components of aero-engines: Developments, trends, and technological advances
- Recent progress of residual stress measurement methods: A review
- Micromanufacturing technologies of compact heat exchangers for hypersonic precooled airbreathing propulsion: A review
- Towards intelligent design optimization: Progress and challenge of design optimization theories and technologies for plastic forming
- A combined technique of Kalman filter, artificial neural network and fuzzy logic for gas turbines and signal fault isolation
