Actual TDoA-based augmentation system for enhancing cybersecurity in ADS-B
Ahmed AbdelWahab ELMARADY, Kamel RAHOUMA
Faculty of Engineering, Minia University, Minia 61519, Egypt
KEYWORDS ADS-B;Cybersecurity;Cyber resilience;k-Nearest Neighbors (k-NN)classifier;Machine learning;Multilateration
Abstract Currently, cybersecurity and cyber resilience are emerging and urgent issues in nextgeneration air traffic surveillance systems, which depend primarily on Automatic Dependent Surveillance-Broadcast (ADS-B) owing to its low cost and high accuracy. Unfortunately, ADS-B is prone to cyber-attacks.To verify the ADS-B positioning data of aircraft,multilateration(MLAT)techniques that use Time Differences of Arrivals(TDoAs)have been proposed.MLAT exhibits low accuracy in determining aircraft positions. Recently, a novel technique using a theoretically calculated TDoA fingerprint map has been proposed. This technique is less dependent on the geometry of sensor deployment and achieves better accuracy than MLAT.However,the accuracy of the existing technique is not sufficiently precise for determining aircraft positions and requires a long computation time. In contrast, this paper presents a reliable surveillance framework using an Actual TDoA-Based Augmentation System (ATBAS). It uses historically recorded real-data from the OpenSky network to train our TDoA fingerprint grid network.Our results show that the accuracy of the proposed ATBAS framework in determining the aircraft positions is significantly better than those of the MLAT and expected TDoA techniques by 56.93%and 48.86%,respectively.Additionally, the proposed framework reduced the computation time by 77% compared with the expected TDoA technique.
1. Introduction
Owing to the rapid growth of airspace users worldwide, the management of air traffic has become increasingly important.According to the worldwide forecast of air traffic volume,passenger numbers are expected to reach 7.3 billion by 2034,1accompanied by increasing flight numbers, as reported by the International Air Transport Association. Furthermore,with the new incoming fast-growing unmanned aerial vehicles to airspace users,2additional challenges are posed to the management of airspace. A typical challenge in such tremendous growth is to decrease the minimum separation between aircraft, which requires their precise positioning. Determining the position of aircraft in airspace,known as air traffic surveillance,is crucial in aviation safety based on the management of airspace and separation standard. The Federal Aviation Administration and the European Union launched the Next Generation Air Transportation System (NextGen) project3and the Single European Sky Air traffic management Research(SESAR) project4to cope with the increasing air traffic density.The Automatic Dependent Surveillance-Broadcast(ADSB)5surveillance technique affords high accuracy and low cost compared with traditional surveillance techniques, primary and secondary radar.6,7Therefore, NextGen and SESAR recognize ADS-B5as the main component of next-generation air traffic surveillance systems. ADS-B is used almost in enroute airspace surveillance with a typical coverage of 200 n mile.8ADS-B uses the data fusion of a Global Navigation Satellite System (GNSS) and inertial navigation to determine an aircraft’s position, and periodically broadcasts the position information to be received by ground receivers.Unfortunately,ADS-B is prone to cyber-attacks, such as jamming and spoofing.9–11The likelihood of these cyber-attacks increases12owing to the open nature of ADS-B, the availability of softwaredefined radios13that can be used to send wireless signals such as ADS-B messages, and the lack of a security prospective in ADS-B. Therefore, attackers can capture and modify ADS-B messages, delete messages, and inject misleading messages.Cyber-attacks can negatively affect the economic and political sectors14by providing critical air navigation systems in civil aviation, as well as information and communication technology systems. Additionally, the International Civil Aviation Organization(ICAO),which is a specialized agency of the United Nations with a vision to achieve the sustainable growth of the global civil aviation system, has considered cybersecurity and cyber resilience as emerging issues in the aviation domain worldwide.15Numerous studies have been proposed to address ADS-B security issues.Some techniques use authentication/encryption.16–20Cryptographic techniques require changing the ADS-B protocol,which results in major changes to the related fleet.Meanwhile,location verification techniques such as multilateration (MLAT) techniques21,22have been proposed to verify positioning data in ADS-B. MLAT is a ground sensor-based surveillance technique that determines the aircraft location using the Time Difference of Arrival (TDoA).Unfortunately, MLAT suffers from geometric dilution of precision and is highly dependent on synchronization and the geometry of sensor deployment. Additionally, the localization accuracy of MLAT degrades in a dense multipath environment.In a multipath environment,multiple copies of the same signal are received owing to reflections from objects, such as buildings and aircraft. At typical aircraft cruising altitudes,the multipath effect is small compared with that in large and complex airports, where multipath effects become important.23,13Furthermore, MLAT is prone to cyber-attacks24and exhibits low accuracy in determining the position of aircraft. Recently, a novel grid-based localization technique13has been proposed. Ref. 13 proposed theoretically calculating the expected TDoA fingerprint map and the k-Nearest Neighbors(k-NN)algorithm to estimate the position of aircraft.The proposed technique depends less on the geometry of ADS-B sensor deployment and achieves higher accuracy than MLAT in determining the aircraft position.Furthermore,unlike techniques that use MLAT,22the expected TDoA localization technique13is less dependent on the time synchronization due to using the established TDoA fingerprint map that comprises small squares.Each square has its own theoretically calculated fingerprint that represents the coordinates of the square center, and the fingerprint is constant throughout the square area. For small inaccurate time synchronization, the corresponding TDoA fingerprint still falls in the same square.However, the accuracy of this approach in verifying ADS-B positioning data is insufficient to detect anomalies in ADS-B.Furthermore, a long computation time is required. Unlike the aforementioned technique, the objective of our proposed framework is to use the available recorded historical realdata of ADS-B messages from existing crowdsourced air traffic communication networks, such as OpenSky13and flightradar24,3to enhance the accuracy in determining the aircraft position. Therefore, the probability of detecting spoofing attacks and other anomalies in ADS-B without changing the ADS-B protocol is increased. Furthermore, the computation time to be used in a real-time environment is reduced.
In addition to the parameters used to measure the performance of next-generation air traffic surveillance systems, such as the integrity, accuracy, availability, coverage, and reliability,25we measured a new parameter denoted by the trust of data provided in ADS-B. This trust value indicates the degree to which data provided in ADS-B are trusted, validated and verified against potential spoofing attacks or potential anomalies in ADS-B from inaccurate inputs used to determine aircraft position airborne avionics such as the GNSS, inertial reference system,or flight management systems.The OpenSky network is a crowdsourcing initiative that comprises large numbers of ADS-B receivers and sends the live tracking data to a central server via the Internet.26Some ADS-B ground sensors are equipped with integrated GPS receivers for synchronized timestamps.
Our proposed actual TDoA-based augmentation system localization framework comprises two main components: offline training and online localization phases.In the offline training phase, we divide the surveillance area into small squares,with each square containing a fingerprint.The fingerprint contains feature vectors extracted from the theoretically calculated TDoA augmented with the actual TDoA obtained from historical real-data from the OpenSky network. In the online localization phase, the aircraft location is determined using the k-NN classifier and the velocity/position prediction stage to reduce the search area of interest and hence the computation time. The proposed established TDoA fingerprint map, likewise ETDoA localization technique,13made our proposed framework more robust against time synchronization than MLAT technqiues.22Our results indicated that the accuracy of our proposed ATBAS framework in determining the position of aircraft is superior over those of the MLAT and expected TDoA techniques by 56.93% and 48.86%, respectively.Furthermore,our computation time is 77%shorter than that of the expected TDoA technique. Moreover, our simulation results indicated that the probability of detecting anomalies in ADS-B using our proposed framework is higher than those of ETDoA and MLAT techniques. The remainder of the paper is organized as follows. In Section 2, we present the related studies. In Section 3, we present the system model followed by our proposed offline/online localization framework in Section 4.Subsequently,we evaluate the performance of our proposed framework in Section 5 and conclude the paper in Section 6.
2. Related studies
Numerous studies have been proposed to address ADS-B security issues. Some techniques use authentication/encryption(cryptographic solutions), others use the characteristics of the physical layer,while novel techniques involving grid-based localization have been employed more recently.Cryptographic methods use communication encryption in wireless networks between ADS-B receivers on the ground and ADS-B transponders on aircraft.16–20Such techniques require the transmitter and receiver to pre-share a secret key. Cryptographic techniques require changing ADS-B protocols and hence major changes to the related fleet. Researchers have used physical layer characteristics27–31to detect spoofing in ADS-B. Ref.27 proposed a physical layer verification method that uses the Doppler shift to verify not only the aircraft’s position,but also the aircraft’s velocity so that spoofing in ADS-B can be detected without changing the ADS-B standard. This technique relies on the participation of ground ADS-B receivers or other entities.Meanwhile,Ref.30 and Ref.31 proposed spoofing detection techniques involving the Angle of Arrival(AoA).In Ref.30,spoofing was detected by comparing the calculated AoA analyzed from ADS-B position messages and measured AoA obtained from a sector antenna. Sector antennas were assumed in these techniques. Furthermore, the proposed technique can detect spoofing only in terms of the bearing angle rather than the range distance.To use current surveillance systems,such as MLAT with simple antenna designs,Ref.32 used Wide Area Multilateration (WAM) to validate ADS-B position reports without modifying the ADS-B protocol. Hence,anomalies in ADS-B messages that might be caused by spoofing attacks can be detected.The proposed technique considers the expected errors in GPS and WAM. Furthermore, other techniques use the MLAT concept21,22involving the TDoA to detect anomalies in ADS-B. Unfortunately, the proposed MLAT techniques require precise synchronization of the ground sensors and good sensor deployment. Furthermore,Ref. 33 proposed the data fusion of ADS-B, MLAT, dynamic flight model of aircraft, and flight information to enhance the accuracy and security of ADS-B using an interacting multiple model.The proposed approach achieves the precise location of aircraft.Similar to techniques that use MLAT,this data fusion technique requires precise synchronization in ground sensors and good sensor deployment.Ref.34 presented models to analyze the performance of aircraft to be used for air traffic management investigations. Recently, Ref. 13 developed a novel technique that uses a theoretically calculated TDoA fingerprint map to obtain the aircraft position. In their approach, they used a combination of the expected TDoA and the k-NN algorithm to estimate the position of aircraft, which depends less on the geometry of ADS-B sensors. The proposed approach requires a long computation time to search in the available learned positions in the grid. Therefore, our proposed framework is presented herein to mitigate these challenges. A comparison among various ADS-B verification detection techniques is shown in Table 1.
3. System model
In our system model, the aircraft is equipped with an ADS-B transponder that is mandated by many regions, such as Europe, the United States, and Australia. ADS-B periodically broadcasts beacons containing position, velocity, and other aircraft information at a frequency of 1090 MHz. This information is calculated using the GNSS and on-board systems.The ADS-B signal is received by ADS-B ground receivers that are connected to a central server via the Internet or other means of communications. As shown in Fig. 1, messages are broadcasted from the ADS-B transponder on the aircraft and received by ground receivers at different time denoted as t1,t2,...,ts, where s is the number of sensors. The range distance between the ADS-B transponder and ground sensor i is denoted by ri, where i=1,2,...,s. ADS-B is prone to cyber-attacks, where attackers can extract and modify ADSB messages, delete messages, and inject misleading messages.In this study, we focus on the scenario of modifying the contents of position messages,which is considered one of the most complicated attacks and is difficult to detect. Historically recorded real-data available from the OpenSky network are used to train the network and augment the grid with the actual TDoA. The OpenSky network is a crowdsourcing initiative to collect the location information of aircraft through ADS-B receiver sensors deployed worldwide and avail the data to researchers. The data provided by the OpenSky network primarily comprise information regarding the receiving sensors and transmitting airplanes, including the time-of-arrival of the messages and the contents of the messages originating from the aircraft (latitude, longitude, and altitude, aircraft ID).Table 2 shows the main data items used in the study from the real-history data. The training data used were assumed to be verified and trusted.And aircraft typically follows certain airways. Table 3 summarizes the notations used.
4. Proposed actual TDoA-based augmentation system framework
In this section, we introduce the two main components of our proposed ATBAS framework:offline training and online localization phases. Fig. 2 shows the block diagram of proposed ATBAS framework. Next, we explain each of the two components of the framework.
4.1. Offline training phase
Our proposed offline training phase comprises two subcomponents: establishing the expected TDoA fingerprint map followed by augmenting the expected TDoA fingerprint map using available historical real training data.
4.1.1. Establishing expected TDoA fingerprint map
In the offline training phase, we established the expected TDoA fingerprint map. First, we divided the surveillance area into a grid of M × N squares, as shown in Fig. 3(a), where N and M are integer numbers representing the number of square cells in latitude and longitude dimensions,respectively.M and N were calculated as follows:

where Latmaxand Latminrepresent the maximum and minimum latitudes of the surveillance area, respectively; ℓ is an integer number representing the square length of each cell in the grid,as shown in Fig. 3(a). Furthermore, M was calculated as follows:

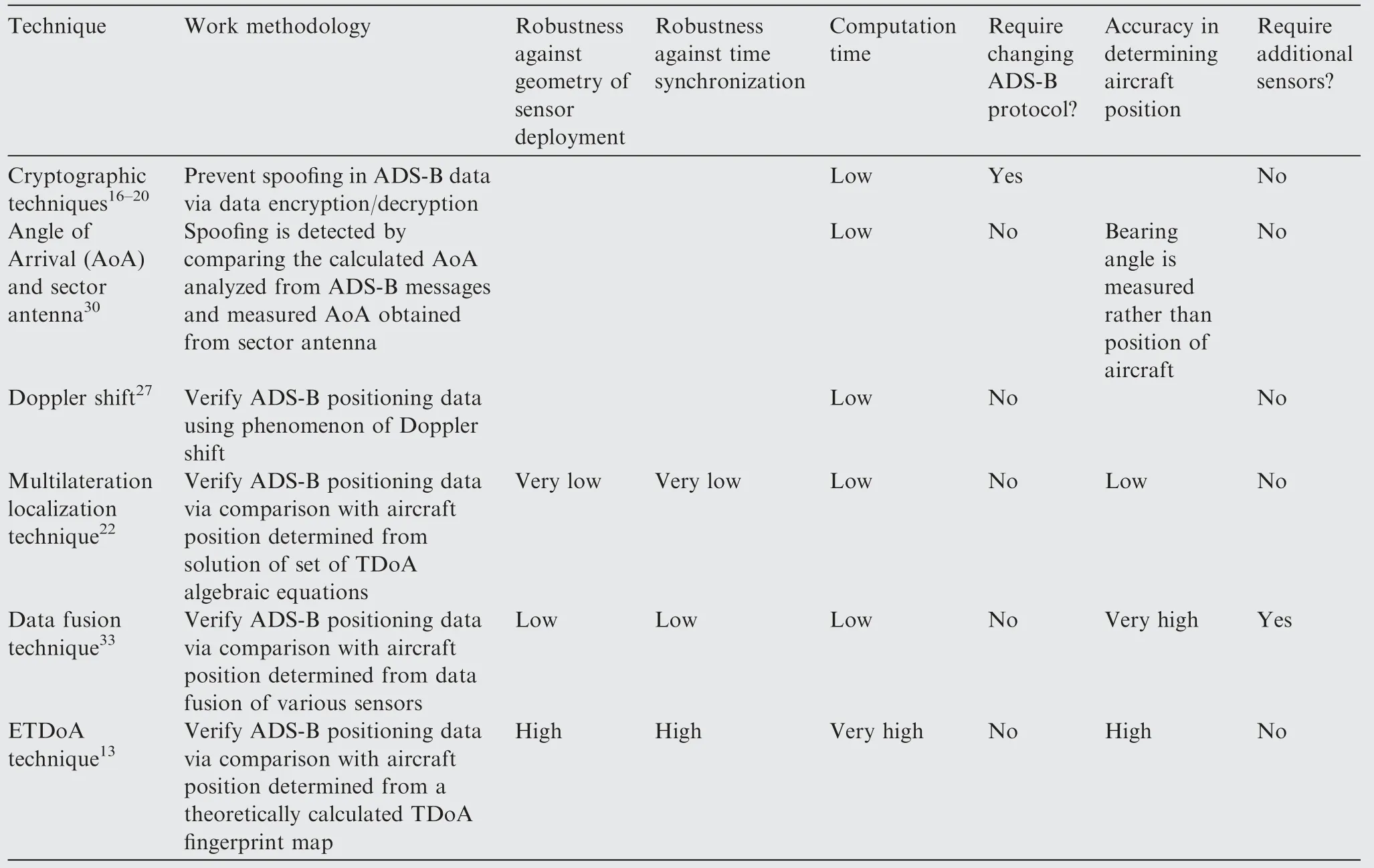
Table 1 Comparison among various ADS-B verification techniques.
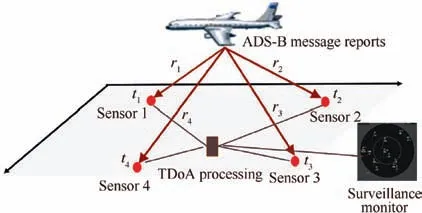
Fig. 1 Illustration of system model.
where Longmaxand Longminrepresent the maximum and minimum longitude, respectively. Subsequently, we calculated the expected TDoA fingerprint vector for each square.The feature used to determine the fingerprint is the Expected Time Difference of Arrival (ETDoA) between ADS-B ground receivers.To calculate the ETDoA,we first calculated the range distance between the aircraft and ADS-B receiver i,ri, as shown in Fig. 1, where rican be calculated as follows:
where x,y,z represent the Cartesian coordinates corresponding to the aircraft position at each square; xi,yi,ziare the Cartesian coordinates corresponding to the position of theADS-B receiver, i=1,2,...,s, where s represents the number of ADS-B receivers.Subsequently,the theoretical propagation time required to receive messages from the aircraft’s transponder at ADS-B ground receiver i is ti,and tican be calculated as
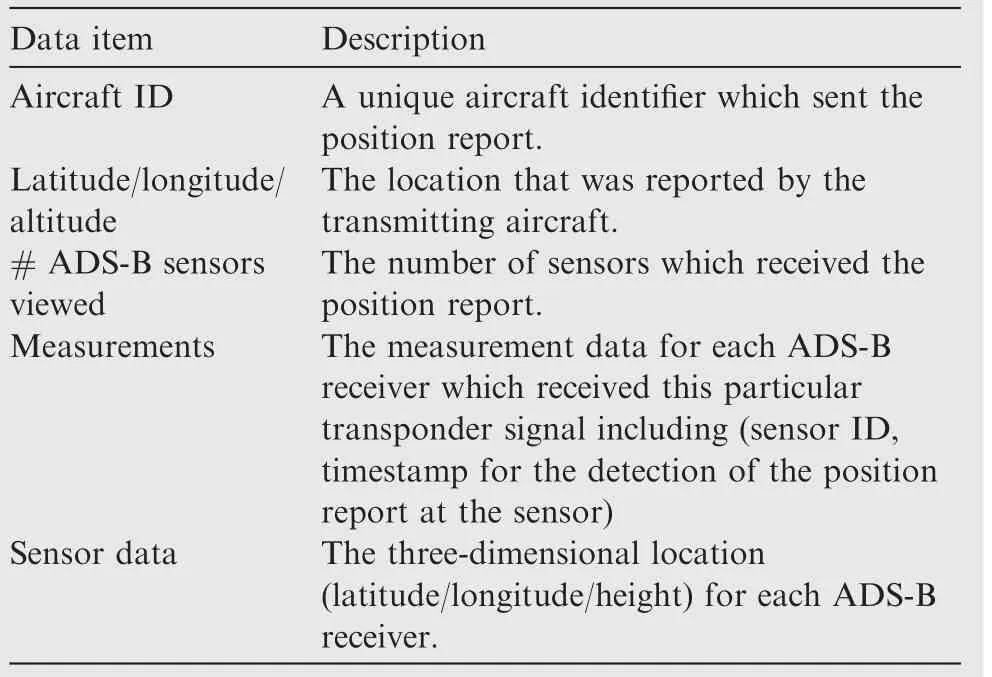
Table 2 Data items used from OpenSky network.


Table 3 Summary of notations used.
By subtracting the shortest calculated propagation time tminfrom the propagation time of other sensors,we can obtain the ETDoAias follows:

Subsequently, the sensors were reordered from the shortest to the longest time tiexcluding the sensor with the minimum time tmin.The feature extraction Fefrom the available expected TDoA was calculated as follows for each subset combination of sensors:

Next, we created the expected TDoA fingerprint map by generating every subset of sensor combinations (s) with a(s-1)×1 fingerprint vector. For example, for a five-sensor deployment, subsequently, we have five sets of training grids with a 4×1 feature vector, Fe=[ETDoA1,ETDoA2,ETDoA3,ETDoA4]T. The fingerprint calculated above was stored in the square that best matched its location. As shown in Fig. 3(a), the theoretically calculated fingerprint was stored in all squares of the surveillance area,and is denoted in white.
4.1.2. Augmentation of expected TDoA fingerprint map using real-world training data
In Section 4.1.1, we established a Two-Dimensional (2D) grid map from the theoretically calculated TDoA to obtain the aircraft location (lat,long). However, the abovementioned grid network only applies effectively for determining aircraft locations with highly accurate time synchronizations between all ground receivers and in a nonmultipath environment. To mitigate this issue,historically recorded aircraft location information received from ADS-B receivers deployed worldwide can be used to augment the grid and hence refine the theoretically expected TDoA vectors.The historical data available from the OpenSky network were used in this study to train the network and augment the grid with the actual TDoA. For each recorded message j from the OpenSky network, we calculated the Actual TDoA (ATDoA) as follows:

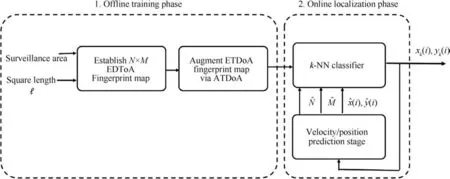
Fig. 2 Block diagram of our proposed ATBAS framework comprising offline training and online localization phases.
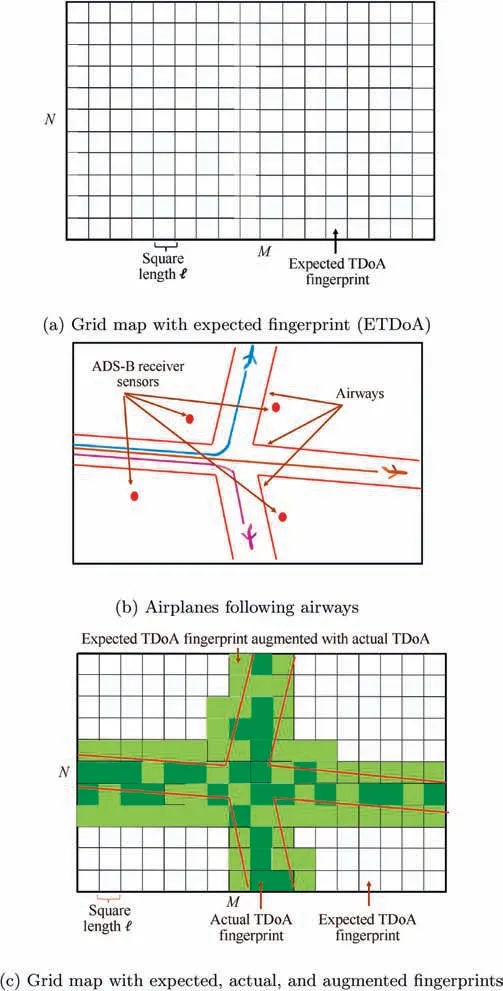
Fig. 3 Illustration of offline training phase.

Subsequently, the above mentioned fingerprint was stored in the square that best matched its location and replaced the theoretically calculated TDoA(ETDoA).If more than one fingerprint corresponded to the same square,the average of these fingerprints was taken and replaced the ETDoA. Two issues were encountered in this scenario.First,airplanes typically follow the routes identified by their widths,as shown in Fig.3(b).Therefore, the available training data only encompass airway regions. Hence, not all squares in the grid are directly augmented. Next, even in the airway regions, not all squares are augmented where not all aircraft messages are seen by the ground sensor receivers. As shown in Fig. 3(c), squares that are directly augmented are available only in the airway regions and are shown in green herein. To extend the augmented squares,the difference between the actual and expected fingerprints δjwas used to augment the neighboring squares with the expected fingerprint vectors. As shown in Fig. 3(c), cells with an indirectly augmented fingerprint are shown in light green.Algorithm 1 shows an overview of the offline training phase for one combination of sensors.
4.2. Online localization phase
Our proposed online localization phase comprises two subcomponents: obtaining the aircraft location using the k-NN classifier; the velocity/position prediction stage to reduce the search area. k-NN is a known classification and widely used machine learning technique owing to its simplicity, low cost,and accuracy.35In k-NN, all available training data are recorded, while new unknown incoming data are classified according to distance measurement functions, such as the Euclidean distance between incoming data and recorded training data to obtain the k-NN.36
4.2.1. Aircraft localization using k-NN classifier
In Section 4.1,we constructed a TDoA fingerprint map in a 2D grid of M×N squares that contained the expected TDoA augmented with the actual TDoA.In the online localization phase,new incoming data messages were analyzed,as shown in Algorithm 2,to extract the feature vector Fincoof the TDoA values,where Fincowas calculated as follows:
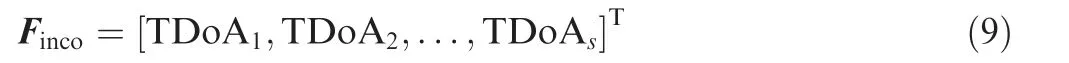
where TDoAirepresents the physical TDoA for each twosensor combination.In the online phase,we used the standard k-NN classifier,in which we obtained the closest k squares that matched the fingerprints of our training grid. First, we calculated the Euclidean distance between the received physical fingerprint Fincoand the relevant saved grid fingerprint, of a subset combination of sensors, as follows:
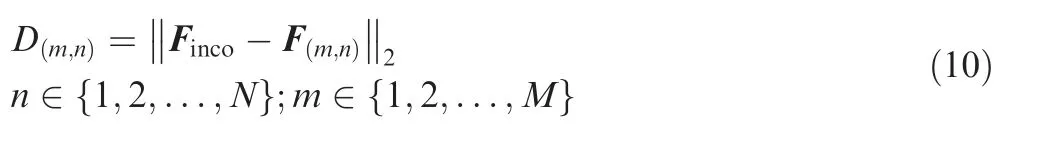
where F(m,n)is the TDoA feature vector of the training data, which was located in the square (m,n). Subsequently,the squares were sorted with Djin ascending order and the average longitude and latitude of the squares of the first k neighbors were used to obtain the longitude and the latitude of the aircraft. Fig. 4 shows the online localization phase. As shown in Fig. 4, the position of the aircraft obtained from the k-NN classifier (xk(i),yk(i)) was determined by taking the average five nearest neighbors, where k=5 herein.
For a new incoming data message with less acquired sensors than the established fingerprint map, with the maximum number of deployed sensors, the appropriate set of sensor combinations was chosen.However,the accuracy of determining the aircraft position was degraded.
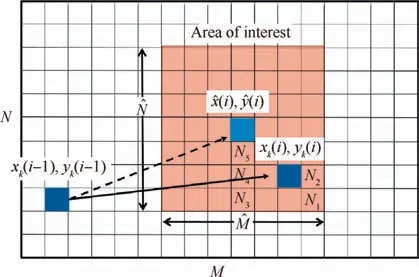
Fig. 4 Illustration of online localization phase.
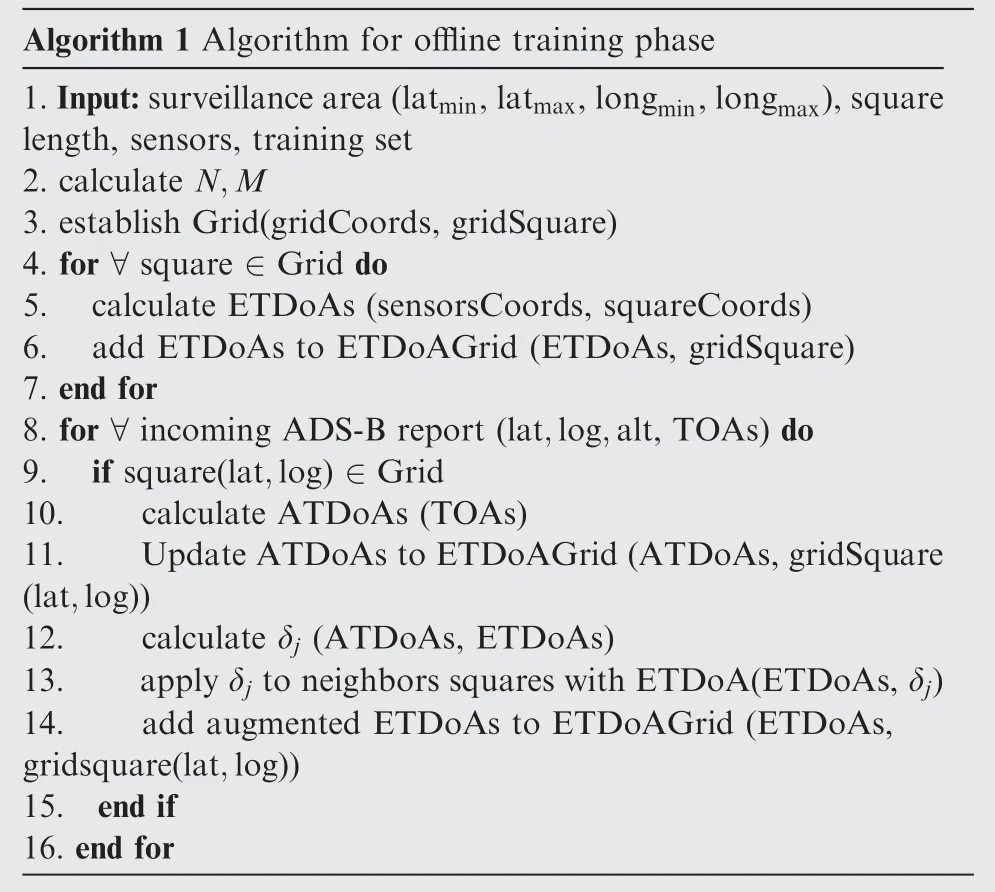
Algorithm 1 Algorithm for offline training phase 1.Input:surveillance area(latmin,latmax,longmin,longmax),square length, sensors, training set 2. calculate N,M 3. establish Grid(gridCoords, gridSquare)4. for ∀square ∈Grid do 5. calculate ETDoAs (sensorsCoords, squareCoords)6. add ETDoAs to ETDoAGrid (ETDoAs, gridSquare)7. end for 8. for ∀incoming ADS-B report (lat,log,alt, TOAs) do 9. if square(lat,log) ∈Grid 10. calculate ATDoAs (TOAs)11. Update ATDoAs to ETDoAGrid(ATDoAs,gridSquare(lat,log))12. calculate δj (ATDoAs, ETDoAs)13. apply δj to neighbors squares with ETDoA(ETDoAs,δj)14. add augmented ETDoAs to ETDoAGrid (ETDoAs,gridsquare(lat,log))15. end if 16. end for
4.2.2. Velocity/position prediction stage

As shown in Fig.4,the expected current position(^x(i),^y(i))was determined given the previous position(xk(i-1),yk(i-1)) obtained from the k-NN classifier. Furthermore, the current aircraft position using the k-NN classifier (xk(i),yk(i)) was determined by looking up the k-NN in the small area of interest rather than looking up all squares in the training grid.
The calculated expected position contains an error originating from the errors in the calculated expected velocities and k-NN estimator. Therefore, the expected error should consider the maximum error in the calculated expected position. This expected error depends on the square length. Fig. 5 shows the expected error at various values of square length with four sensors and k=5. As shown in Fig. 5, as the square length decreased, the corresponding expected error decreased. Algorithm 2 shows overview of the online localization phase.
5. Simulation results
5.1. Simulation environment
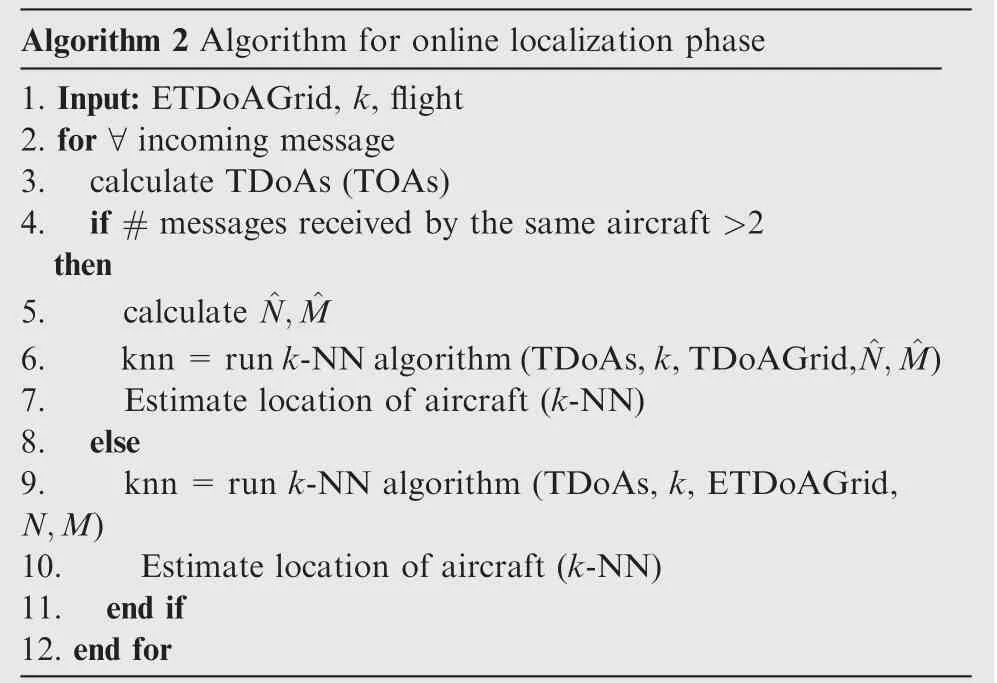
Algorithm 2 Algorithm for online localization phase 1. Input: ETDoAGrid, k, flight 2. for ∀incoming message 3. calculate TDoAs (TOAs)4. if # messages received by the same aircraft >2 then 5. calculate ^N, ^M 6. knn=run k-NN algorithm(TDoAs,k,TDoAGrid,^N, ^M)7. Estimate location of aircraft (k-NN)8. else 9. knn=run k-NN algorithm (TDoAs, k, ETDoAGrid,N,M)10. Estimate location of aircraft (k-NN)11. end if 12. end for
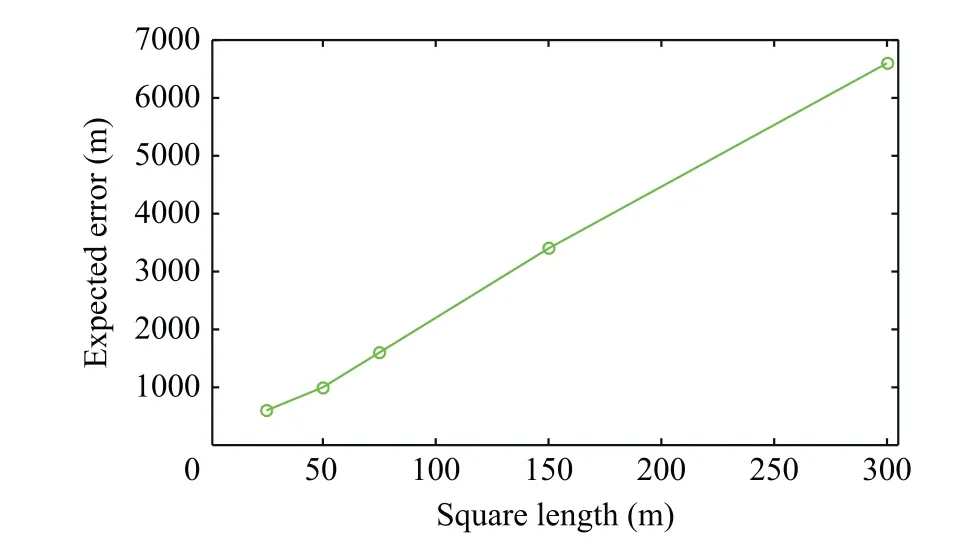
Fig. 5 Illustration of expected error at various values of square length.
In this section, we evaluated the performance of our proposed framework using MATLAB simulations. The data set used in the simulation was divided into two:training and evaluation sets.The training set was used to train the grid network and augment the expected TDoA fingerprint map using the actual TDoA.Meanwhile,the evaluation set was used to evaluate the performance of our proposed localization framework.Both training and evaluation sets were synchronized realworld ADS-B data messages obtained from the OpenSky network with ratios of 80% to 20%, respectively. We used approximately 1000000 ADS-B message reports of historical raw data from the data sets,and we extracted ADS-B message reports that were viewed by the same four sensors to establish the expected TDoA grid augmented by the actual TDoA.Table 4 shows the relative percentage of ADS-B messages viewed by the ADS-B sensors. For our grid design, we constructed a 2D grid over an average flight altitude of approximately 10 km and covered an area measuring 135km×210km. The number of squares was a tradeoff between the performance and computation time.
We calculated the average error as our metric to evaluate the performance of our proposed framework in terms of positioning accuracy. Average error was calculated as follows:
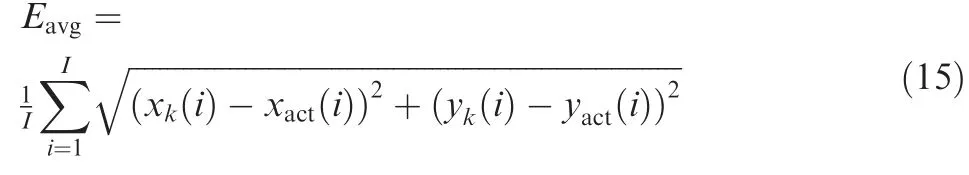
where (xact(i),yact(i)) and (xk(i),yk(i)) are the actual aircraft position and that obtained from our proposed k-NN classifier in x and y dimensions, respectively, and I is the number of ADS-B messages used in the evaluation set.
5.2. Effect of grid design and selecting optimal k neighbors
In this section,we evaluated the effect of the grid design represented by square length and the number of nearest neighbors on the performance of our proposed aircraft localizationframework.Hence,we extracted ADS-B messages reports that were viewed by the same four sensors to establish the expected TDoA grid augmented by the actual TDoA. Fig. 6 shows the effects of the number of neighbors and the square length on the performance of our proposed localization framework. As expected, as the square length decreased, the corresponding average horizontal localization error decreased. For example,when the square length decreased from 300 to 150 m,the average error decreased from 351.8173 to 240.8065 m at k =5 neighbor. In other words, the localization accuracy enhanced by 31.55% as the square length decreased from 300 to 150 m. Furthermore, Fig. 6 illustrates the horizontal localization accuracy at different values of k. As shown, the positioning accuracy increased with k up to k=5.For k=6 or more,there was no noticeable improvement. For example, as k increased from 1 to 5,at ℓ=300 m,the corresponding average error decreased from 377 to 351 m,while at k=9,the average error was 350.5 m. Therefore, k=5 was used in the study.
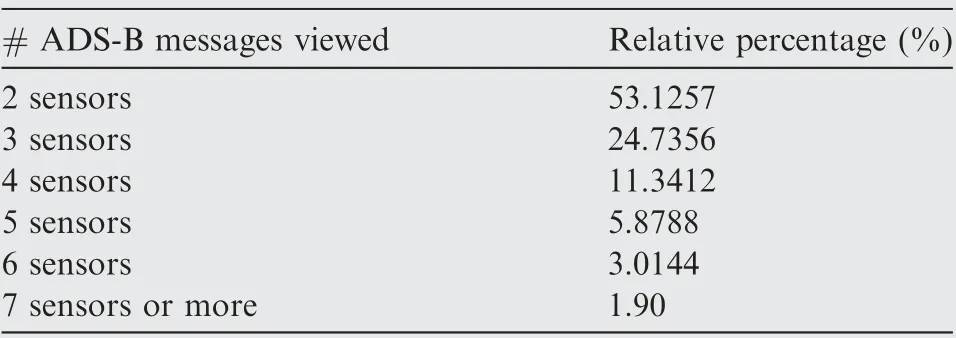
Table 4 Analysis of data from OpenSky network used in simulation section: Relative percentage of ADS-B messages viewed by a given number of sensors.
5.3. Comparison between proposed framework and other techniques in terms of positioning accuracy
In this section,we evaluate the accuracy in determining the aircraft position of our proposed ATBAS framework and compare it with other techniques in the literature, the MLAT technique,22and expected TDoA.13Fig.7 illustrates a comparison among our proposed ATBAS framework,proposed initial velocity/position prediction stage, MLAT technique,22and expected TDoA13at different values of ℓ. As shown, the error for MLAT was 209 m regardless of the value of ℓ, where the MLAT technique directly calculates the location of aircraft using algebraic equations. Meanwhile, the localization error of our proposed framework decreased as the square length decreased with positioning accuracy, which was much better than MLAT at lower values of square length. In more detail,the localization accuracy of our proposed ATBAS framework at ℓ=50 m was enhanced by 42.58% compared with the MLAT technique. Furthermore, the localization accuracy atℓ=25 m was enhanced by 56.93%compared with MLAT technique. As shown in Fig. 7, the positioning accuracy of the expected TDoA13decreases as the square length decreases with higher errors than the proposed ATBAS framework. Recall that the expected TDoA13does not involve any augmentation to the grid network from the real-world data. The positioning accuracy of our proposed ATBAS framework was enhanced by 38.77% and 48.86% compared to expected TDoA13at ℓ=50 and 25 m,respectively.Table 5 shows comparison among MLAT,22ETDoA,13and our proposed ATBAS framework atℓ=25 m and k=5. In addition, Fig. 7 illustrates the performance of our proposed initial localization technique using the velocity/position prediction stage at different values of ℓ.As shown, the error of our proposed initial localization technique decreased as the square length decreased but with higher values than our proposed framework.Recall that the expected current positions ^xkand ^ykwere determined by the previous positions obtained using the k-NN classifier, xk(i-1) and yk(i-1).Therefore,the error of our proposed initial technique was dependent on the accuracy of the k-NN and the designed grid map in the offline training phase. The error was used to determine the maximum error ^e. The positioning accuracy of our proposed framework can be further enhanced by using more sensors, reducing the square size, and using more realdata to learn the designed grid network.
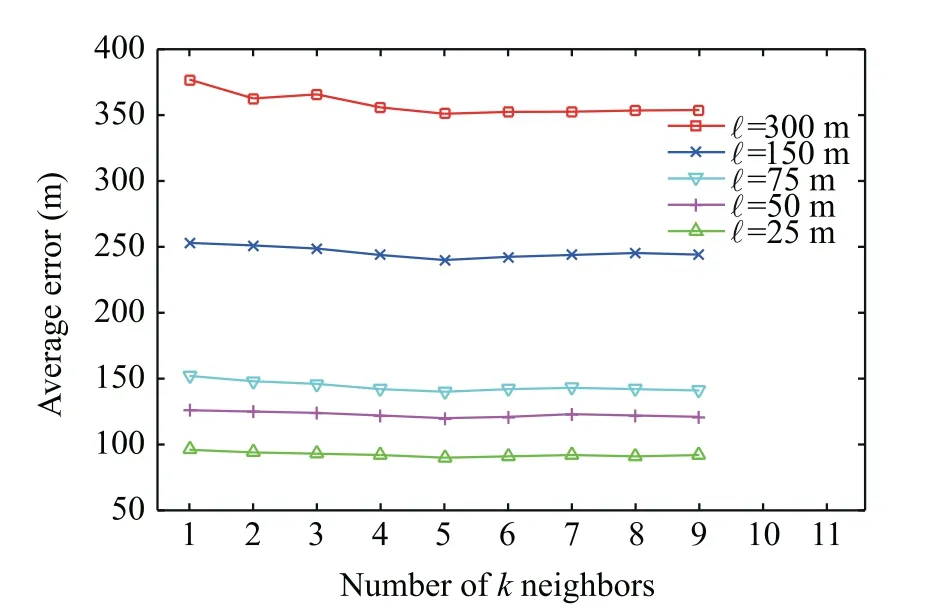
Fig. 6 Effects of square length and number of neighbors k.
5.4. Comparison between proposed framework and other techniques in terms of computation time
Determining the location of aircraft in real time is crucial in high-speed environments, such as in aviation. Therefore, the computation time was evaluated for our proposed framework and compared with other techniques.Ideally,the computation time should be short to achieve a high update rate. In aircraft localization techniques that use machine learning such as the k-NN classifier,13,37many parameters should be considered in the calculation of the computation time, such as the sizes of the surveillance area and square.In this study,we evaluated the computation time of the online localization phase.For theoffline training phase, the computation time depends on the sizes of the surveillance area and square, similar to the online localization phase.However,even larger grids and longer computation time of the offline training phase would not pose a problem in real-world settings. Fig. 8 illustrates the computation time of the MLAT technique,22expected TDoA,13and our proposed online localization framework for different values of square length.As shown in Fig.8,the computation time of the MLAT technique22was constant regardless of the value of ℓ. Recall that the MLAT technique directly calculates the location of aircraft using algebraic equations. Furthermore,the computation time of MLAT was comparable to that of our proposed framework at ℓ=300 m, whereas the relative computation time of the expected TDoA13was 150% higher than that of our proposed framework.Meanwhile,the relative computation time of our proposed localization framework increased with a lower rate than the expected TDoA13as the square size decreased. Recall that in our proposed technique,the location of aircraft is determined by looking up the k-NN at only the predicted area of interest owing to the use of the velocity/position prediction stage, while all available squares in the grid map are looked up in the expected TDoA13.For example, at a 25 m square length, our proposed framework reduced the relative computation time by 75%compared with a technique that did not use the velocity/position prediction stage,13as shown in Table 5. Furthermore, at a 50 m square length, the relative computation time was enhanced by 77%.
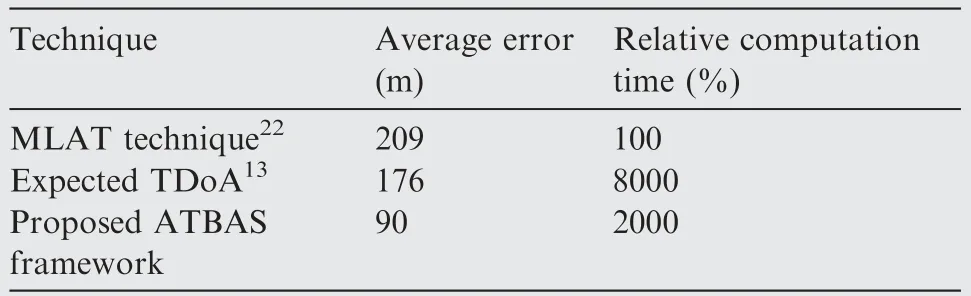
Table 5 Comparison among MLAT, Expected TDoA, and proposed ATBAS framework at ℓ=25 m and k=5.
5.5. Evaluation of trust of ADS-B using our proposed ATBAS framework
Measuring the trust of the aircraft position data contained in the ADS-B message reports is crucial owing to many reasons.For example, the inaccurate inputs used to determine aircraft position on board avionics such as the GNSS, inertial reference system,and flight management system.As mentioned previously, ADS-B is prone to spoofing attacks, in which attackers can change the actual ADS-B trajectory by manipulating ADS-B messages. In this section, we evaluated the performance of our proposed ATBAS framework for the verification of ADS-B message reports and detect spoofing or abnormal aircraft instruments. As mentioned herein, the aircraft position can be determined using two independent methods: position information contained in ADS-B message reports and that estimated from the proposed ATBAS framework.To verify the ADS-B position information and measure its trust, we first calculated the error between the position received using the ADS-B message reports and that estimated using the proposed ATBAS framework, ε. Subsequently, we compared this error with a certain threshold denoted as τ such that
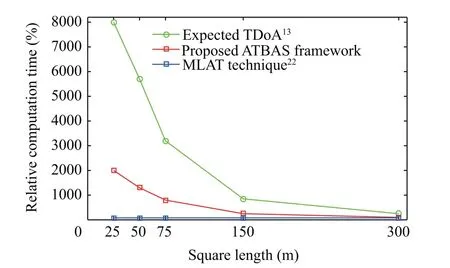
Fig. 8 Illustration of relative computation time for proposed ATBAS framework, expected TDoA,13 and MLAT technique.22

where T(i) represents the percentage of trust of ADS-B. This threshold technique to detect spoofing in ADS-B is applicable to other techniques reported in the literature such as expected TDoA13and MLAT techniques.22The setting of the threshold value depends primarily on the accuracy in determining the aircraft position of the proposed technique. For our proposed ATBAS framework and the EDToA technique, the accuracy depends on the square size, whereas for the MLAT technique,the positioning accuracy is constant regardless of the square size. Therefore, for each square size, a certain threshold exists for techniques whose accuracy depends on the square size.For better trust results, we set τ to be equal to 2^e. To evaluate the performance of our proposed framework for detecting spoofing or abnormal aircraft instruments, implementing realworld attacks was a possible solution. However, we simulated the attacks rather than implementing them in the real-world,owing to ethical and legal issues. Therefore, we simulated a scenario where the attacker gradually modified the position information contained in ADS-B messages. In the beginning,the attacker followed the actual trajectory of ADS-B. Subsequently, the attacker broadcasted manipulated ADS-B messages by gradually changing the actual aircraft trajectory.This scenario is considered as a complex attack that is difficult to detect, and is denoted as a ‘‘frog-boiling attack”.38
To simulate this scenario,we used the position messages of real trajectories of 200 flights obtained from the OpenSky network and subsequently added Gaussian noise with increasing values using 110 ADS-B messages (from 30 to 140). Fig. 9(a)illustrates the average error between the position received from ADS-B message reports and that estimated from our proposed ATBAS framework for different message numbers received from various flights. Additionally, Fig. 9(a) shows three threshold values: 180 m for the proposed ATBAS framework,352 m for the ETDoA technique,and 418 for the MLAT technique. Recall that the threshold level was set to be equal to 2Eavg. As shown in Fig. 9(a), up to message number 30, the error was within the threshold level for all the techniques.Starting from message 30 to 140,the error increased gradually and exceeded the threshold limit at message 52 for our proposed ATBAS framework,message 91 for the expected TDoA,and message 105 for the MLAT technique. Recall that the accuracy of determining the aircraft position for the MLAT technique is lower than that of the ETDoA technique,as illustrated in Table 5. Fig. 9(b) illustrates the corresponding average trust at different message numbers.As shown in Fig.9(b),the trust was 100% up to message number 30 for all the techniques and was 0% starting from message 52 to 140 for our proposed ATBAS framework.In other words,in our proposed ATBAS framework, spoofing was detected at average error 180 m or higher, while 352 and 428 m for the ETDoA and MLAT techniques, respectively. Therefore, the probability of detecting anomalies in ADS-B using our proposed ATBAS framework outperforms the ETDoA and MLAT techniques.
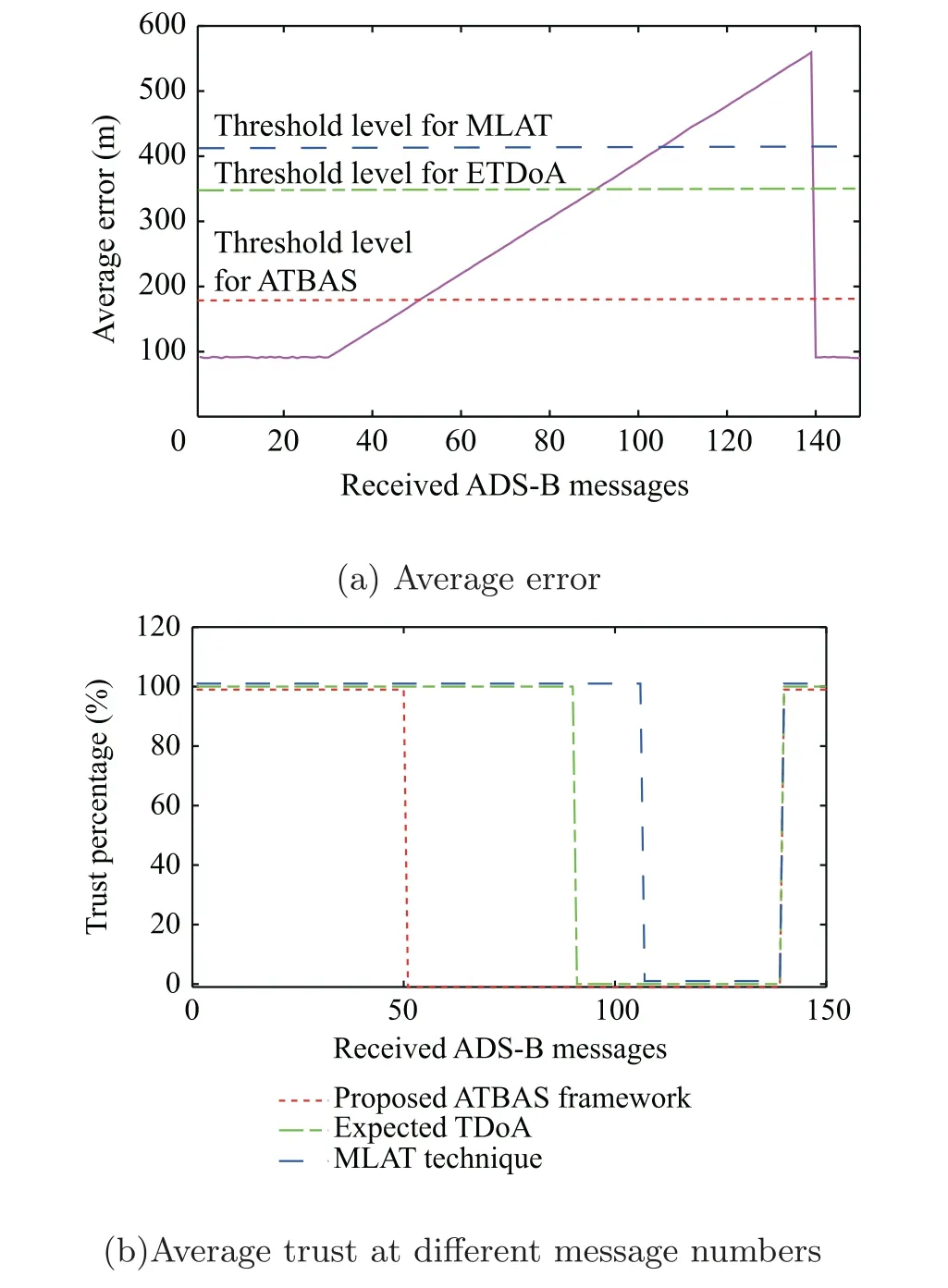
Fig. 9 Illustration of trust for a spoofing attack in ADS-B with results obtained at k=5 and ℓ=25 m.
6. Conclusions and future work
In this paper, we proposed an accurate method for the localization of aircraft using the actual TDoA-based augmentation system framework, which used historical real-data from the OpenSky network to train our TDoA grid network.The accuracy of our proposed ATBAS framework was superior to the surveillance accuracy of MLAT and theoretically calculated TDoA fingerprint map techniques.Additionally,the proposed ATBAS framework was less dependent on the geometry of sensor deployment and time synchronization. Furthermore,the proposed ATBAS framework reduced the computation time compared with the technique using the expected TDoA.Consequently, our proposed framework is suitable for mitigation of potential security threats in ADS-B, jamming, and spoofing without using additional sensors. The proposed framework could obtain the location of aircraft regardless of the position received from ADS-B messages in case of jamming in ADS-B. Furthermore, spoofing could be detected by measuring trust percentage from comparing the position received from ADS-B and that estimated from our proposed ATBAS framework.In future studies,we plan to consider other inputs for detecting spoofing attacks in ADS-B, such as the received signal strength and to measure the correlation between aircraft motions and the ADS-B intent. Additionally, we plan to enhance the positioning accuracy by using more sensors and real data to learn the designed grid network.
 CHINESE JOURNAL OF AERONAUTICS2021年2期
CHINESE JOURNAL OF AERONAUTICS2021年2期
- CHINESE JOURNAL OF AERONAUTICS的其它文章
- Recent active thermal management technologies for the development of energy-optimized aerospace vehicles in China
- Electrochemical machining of complex components of aero-engines: Developments, trends, and technological advances
- Recent progress of residual stress measurement methods: A review
- Micromanufacturing technologies of compact heat exchangers for hypersonic precooled airbreathing propulsion: A review
- Towards intelligent design optimization: Progress and challenge of design optimization theories and technologies for plastic forming
- A combined technique of Kalman filter, artificial neural network and fuzzy logic for gas turbines and signal fault isolation
