Space/Air Covert Communications: Potentials,Scenarios,and Key Technologies
Mao Haobin ,Liu Yanming ,Zhu Lipeng ,Mao Tianqi ,Xiao Zhenyu,* ,Zhang Rui,3 ,Han Zhu,Xia Xianggen
1 School of Electronic and Information Engineering,Beihang University,Beijing 100191,China
2 Department of Electrical and Computer Engineering,National University of Singapore,Singapore 117583,Singapore
3 School of Science and Engineering,Shenzhen Research Institute of Big Data,the Chinese University of Hong Kong,Shenzhen,Guangdong 518172,China
4 Department of Electrical and Computer Engineering,University of Houston,Houston,TX 77004,USA
5 Department of Computer Science and Engineering,Kyung Hee University,Seoul,South Korea,446-701
6 Department of Electrical and Computer Engineering,University of Delaware,Newark,DE 19716,USA
Abstract: Space/air communications have been envisioned as an essential part of the next-generation mobile communication networks for providing highquality global connectivity.However,the inherent broadcasting nature of wireless propagation environment and the broad coverage pose severe threats to the protection of private data.Emerging covert communications provides a promising solution to achieve robust communication security.Aiming at facilitating the practical implementation of covert communications in space/air networks,we present a tutorial overview of its potentials,scenarios,and key technologies.Specifically,first,the commonly used covertness constraint model,covert performance metrics,and potential application scenarios are briefly introduced.Then,several efficient methods that introduce uncertainty into the covert system are thoroughly summarized,followed by several critical enabling technologies,including joint resource allocation and deployment/trajectory design,multi-antenna and beamforming techniques,reconfigurable intelligent surface (RIS),and artificial intelligence algorithms.Finally,we highlight some open issues for future investigation.
Keywords: artificial intelligence (AI);sixth generation (6G);space-air-ground integrated networks (SAGINs);space/air covert communications
I.INTRODUCTION
Space/air communications are recognized as a critical enabling technology for the future sixth generation(6G)mobile networks by providing broad coverage and seamless connectivity,which has been widely used in various applications,including disaster relief,maritime communications,and military reconnaissance [1-6].However,for space/air communication systems,the transmission of exploded private or confidential data is very vulnerable to security threats,such as eavesdropping,monitoring,and jamming,due to the inherently open and broadcasting nature of wireless signal propagation environment [7,8].In addition,the three-dimensional (3D) ubiquitous coverage of space/air communications makes it possible for adversaries to shelter themselves in complex geographical areas with difficulty to eradicate,which inevitably imposes severe security issues.Moreover,the mobility characteristics of space/air platforms,such as unmanned aerial vehicles(UAVs)and satellites,and the complex heterogeneous channels impact the network security performance in different ways.Therefore,the information security of space/air communication networks has become a serious concern,and consequently there is an urgent demand for effective methods that can guarantee high performance and secure transmission.
Traditionally,secure communication is mainly achieved by cryptographic techniques,working at the upper layer,where the same secret key is shared between two communication nodes so that the unauthorized nodes cannot decode the transmitted information accurately [8].However,the transmission delay between the space/air platforms and ground users is generally large due to the long signal propagation distance,especially for satellite communications.The implementation of cryptographic authentication schemes further increases the computing process delay [9],which violates the low latency requirements for future communications.Besides,the cryptographic security scheme suffers from high risk of being decrypted by malicious adversaries due to their increasing computational processing capabilities and speed [10].Different from the above approach,the lightweight physical layer security technology has emerged as an alternative security mechanism to guarantee secure transmission from the perspective of information theory [8],which has been widely investigated in space/air communications[11-13].Specifically,implementing physical layer security techniques achieves the maximization of the performance gap between the legitimate channel and the eavesdropping channel,thus enabling the minimization of the information leakage to the eavesdroppers.However,the above two methods encounter great difficulities to achieve complete communication security.The ultimate objective of secure communication is not only protecting the transmitted message content from eavesdropping but also preventing the legal transmission behavior from adversary detection [14].In certain scenarios,such as military applications,hiding the wireless transmission from detection is crucial since the exposure of the existence of transmission may provoke the enemy to locate,monitor,or even attack the signal source.Fortunately,the emerging covert communication technology,also known aslow detection probability communication,is promising to overcome this challenge by ensuring that the probability of transmission being detected is lower than an arbitrarily small value,thus achieving a more robust level of security.
A prototypical scenario for covert communications is that a transmitter(Alice)can convey information to its desired users(Bob)without being detected by a malicious adversary(Willie).The fundamental theory of covert communications reveals that at mostObits information can be transmitted covertly and reliably from a transmitter to a receiver innchannel uses over additive white Gaussian noise channel[15].Additionally,the authors in[16]analyzed the optimality of Gaussian signaling to achieve covert communications with an upper bound on the Kullback-Leibler(KL) divergenceD(p1||p0) as the covertness constraint,which also establishes a foundation for subsequent researches.Note that most existing works on covert communications concentrate on terrestrial networks.For instance,the authors in [17] maximized the system covertness under the constraint of outage probability via cooperative jamming by a full-duplex receiver.The authors in [18] developed an alternative algorithm to jointly optimize the transmit power and active beamforming of RIS to maximize the covert rate.The research on space/air covert communications is still in its infancy,while covert satellite communications has rarely been studied.There is a necessity to explore the mechanism of generic technologies as well as the unique features,such as the space/air unique environment of signal propagation and the mobility of space/air platforms,on the covert communication system performance and design to ensure the covertness attributes of future space/air communication systems.
Several tutorial and survey papers have been published on covert communications.The early exploration of covert communications was carried out in[19],where steganography working at the application layer and spread spectrum approach working at the physical layer were briefly reviewed.The fundamental limits and the guideline for jammer aided covert communications were also provided.In[20],the difference between covert communications and physical layer security,key challenges for the design of covert systems,and future research directions were thoroughly investigated.In[7],several basic concepts of secure communications,typical application scenarios of UAV-assisted covert communication networks,and some challenging problems and future research directions were introduced and discussed.In [21],a comprehensive survey on covert communications was conducted,where radio frequency based techniques,steganography based techniques,corresponding challenges,and open research issues were presented.The authors in[10]focused on the potentials and candidate methods for uncertainty design in UAV relay assisted covert networks,where the promising research directions were highlighted.
Different from the aforementioned works [7,10,19-21],we concentrate on the radio-frequency-based(RF-based)covert communications in space/air specified networks.To the best of our knowledge,this paper is the first overview of key candidate technologies and open problems of space/air covert communications.In this paper,considering the unique characteristics of space/air communications,we first introduce the covertness constraint model,performance metrics,and typical application scenarios in space/air covert communications in Section II.Then,we provide a brief summary of commonly adopted methods that introduce uncertainty into covert system design in Section III,which is followed by key candidate technologies to guarantee system covertness and improve communication performance in Section IV.Finally,we highlight the open problems worthy of future research in Section V.
II.BASICS AND TYPICAL SCENARIOS
In this section,we first present the basic covert constraint model in space/air covert communications.Then,a brief summary of key performance indicators for space/air covert communications is provided.Finally,we discuss several typical scenarios of space/air covert communications.
2.1 Covert Constraint Model
In space/air covert communications,Willie carries out the detection behavior to make a decision on whether Alice is transmitting signals by conducting binary hypothesis testing.The two generic hypotheses are modeled as follows:
whereiis the channel use index,i.e.,i=1,2,..,L,andLis the maximum channel uses.yw[i] andxa[i]are the received signals of Willie and the transmitted signals of Alice,respectively.nw[i] is the additive white Gaussian noise at the receiver.pais the transmit power of Alice andgawis the channel gain between Willie and Alice.Moreover,H0andH1correspond to the null hypothesis that Alice keeps silent and the alternative hypothesis that Alice is transmitting signals,respectively.
In general,Willie identifies the binary hypotheses by using a radiometer to measure the received signal power[22].In other words,Willie makes decisionD0advocating hypothesisH0if the average received signal power is lower than a predefined detection threshold.Otherwise,decisionD1in favor of hypothesisH1is made.Thus,there may occur two types of wrong decisions,namelyfalse alarmandmiss detection,due to the uncertainty of the received signal power or the inaccurate detection threshold value.To measure the detection performance of Willie,several practical indicators in existing works,also known as the covert constraint models,are summarized in the following.
•Detection error probability: Define the false alarm probability and the miss detection probability as PFA=Pr{D1|H0}and PMD=Pr{D0|H1},respectively.Then,the detection error probability is defined as the sum of the false alarm probability and the miss detection probability,i.e.,ξ=PFA+PMD,which is the most commonly used for covertness measurement[23-25].Note that the minimum of the total detection error probabilityξ*can be calculated mathematically according to the known distributions of uncertain variables in certain cases,such as the scenarios of cooperative jamming.Hence,the covert constraint model can be expressed asξ*≥1-ε,whereεis a predetermined small number arbitrarily close to zero and can be set manually according to the covertness requirement.
•Variational distance: In the cases where only the probability distribution of Willie’s channel observations can be obtained,the optimal detection error probability at Willie is given byξ*=1-VT(p0,p1)[15,26,27],wherep0andp1denote the probability distributions of the received signal under hypothesesH0andH1,respectively.VT(p0,p1)=‖p0-p1‖1is the total variational distance betweenp0andp1,where‖.‖1denotes theL1norm.Hence,in this situation,the covert constraint can be formulated asVT(p0,p1)≤ε.
•Relative entropy: When the maximum channel uses number is finite,the detection error probability usually involves the lower incomplete Gamma functions,making it more challenging to carry out further communication performance analysis[28].Moreover,the generally intractable computation of the variational distance results in its inconvenient application in real scenarios [16,29].Therefore,by exploiting the Pinsker’s inequality[15],the relative entropy(also known as the KL divergence) can be obtained as the upper bound on variational distance,which simplifies the analytical calculation of the covertness constraint.In other words,we have
Then,the constraint of covertness is transformed toD(p0‖p1)≤2ε2orD(p1‖p0)≤2ε2.Although the covert communication system under the two constraints has been widely investigated,their strictness on covertness requirement are quite different in different covert communication systems.For example,D(p1‖p0)≤2ε2is stricter as the covertness constraint thanD(p0‖p1)≤2ε2in the Gaussian signaling system so thatD(p1‖p0)≤2ε2achieves lower mutual information[16].
2.2 Performance Metrics
Similar to SAGINs,the performance metrics of space/air covert communications include the signal-tointerference-plus-noise ratio(SINR),system throughput,coverage probability,energy efficiency,handover rate,and etc.In the following,we provide the definitions of several commonly-used or potential performance metrics for space/air covert communication systems.
•SINRmeasures the strength of the desired signal to the unwanted interference and environment noise.We consider a scenario whereMspace/air transmitters are exploited to serveNground users.Assume that one user is only served by one transmitter.Hence,the SINR of the communication link between transmittermand usernis calculated as
wheregm,norgj,nis the channel gain between transmittermorjand usern.Pm,nis the allocated transmit power to usernby transmitterm,andPm,iandPj,nare similarly defined.Wandn0are the total system bandwidth and the noise power spectral density,respectively.
•System throughputdecipts the communication capacity of the space/air covert communication system.Adopting the Gaussian signal model,the instantaneous data rate of usernserved by transmittermcan be calculated as
in bits/s [30].The expected data rate over random channel realizations is given by
where E[·] denotes the expectation operation.Thus,the system throughput can be calculated as
•Coverage probabilityis defined as the probability that the received SINR is higher than a predetermined threshold [31].For a target SINR thresholdγ*,the coverage probability of usernserved by transmittermcan be expressed as
Denote the set of the users covered by transmittermasNm.To measure the capability to provide communication service for ground users of a specific transmitter,thenumber of served userscalculated by|Nm|=1{γm,n ≥γ*}can be used for the performance analysis,where 1(·) denotes the indicator function determining the value is 0 or 1.Moreover,the3D coverage densitycan be further defined to evaluate the coverage ability in space/air covert communications[1],i.e.,,whereVmis the volume of the covered region of a satellite,UAV,or airborne.
•Energy efficiencydemonstrates the number of information bits that can be successfully transmitted with unit energy consumption.Considering the characteristics of space/air platforms,the power consumption mainly composes of the kinetics-related energy consumptionPkin,the communication-related energy consumptionPcom,and the on-board circuit power consumptionPcir[30,32,33].Hence,the energy efficiency of transmittermis given by
Generally,Pciris neglected in existing works due to its relatively small value compared toPkinandPcom.Apart from the per-transmitter energy efficiency,the network energy efficiency can be similarly defined as the ratio of the system throughput to the total energy consumption.
•Handover rate,defined as the ratio of the handover number to the time period,i.e.,
represents the frequency at which a user handovers from one transmitter to another[34].On one hand,the handover occurs between the same type of transmitters,such as satellites,which provides different service durations and communication rates.On the other hand,necessary handover exists among the heterogeneous access networks.Although a few studies related to the handover methods in SAGINs have emerged[34-36],adaptive and efficient handover algorithms under covertness constraint are still worthy of further investigation.
2.3 Typical Scenarios
The applications of space/air covert communications facilitate the high-level secure data transmission in the upcoming era of the Internet of Everything.Figure 1 illustrates several typical scenarios classified by different roles of the transmitters in space/air covert communication systems,with the details given as follows.
Figure 1(a) describes the scenario where space/air platforms serve as base stations to provide full covert access to the ground users without backhaul links,which is potential in military operations within the marine,mountain,or desert areas [2].In this case,the proper selection and handover of accessing networks to balance security and quality of experience is significant for the confidential information transmission.To this end,intelligent handover decision-making methods,such as deep reinforcement learning,can be exploited to improve the overall covert communication performance in space-air integrated covert networks.Besides,the channel inverse power control technology can be exploited to maintain the received signal power at legitimate ground users as a constant value,and conversely make the received signal power at wardens vary randomly due to the channel fading[37].
Figure 1(b) decipts the scenario where the secret data are reliably transmitted with the help of relays,which is promising in the case that the direct Line-of-Sight (LoS) links between the space/air platforms and the ground users are unavailable due to the strong shadowing and obstacles.Although the relaying architecture expands the hiding coverage,the twophase transmission poses an even more serious security threat.In such a context,relay selection arises as a key and challenging issue to increase the covert communication rate.Especially for multi-hop relaying systems,data transmission route scheduling should also be subject to covert constraints.In this case,joint routing and communication optimization can provide a good balance between system covertness and data rates,but this remains a challenge.
Figure 1(c) shows the scene when space/air platforms act as users to perform specific confidential tasks without being detected by the adversaries [7],such as space-air-ground joint swarm warfare.During the task execution process,space/air platforms should keep the connection to the control nodes via wireless links.However,once the secret transmission behavior is detected by the enemy,legitimate platforms will undergo the risk of being attacked and the mission will be terminated.Therefore,the covert transmission between the nodes for performing tasks and controlling is also a critical issue.To enhance the system covertness,proactive random location variations created by the mobile characteristics of space/air platforms can be utilized to introduce uncertainty into the received signal power at wardens.In addition,probabilistic transmission strategy can also be adopted to mislead wardens to make wrong decisions.
Figure 1(d) describes a potential scenario where space/air platforms are employed as the wardens to achieve high detection performance.Benefiting from their high mobility and large detection distance,mobile space/air platforms can adjust the detection threshold value and change their positions dynamically according to the received signal strength.The repeated process of detection or adjustment of mobile wardens enables a more accurate determination on whether Alice is transmitting,which makes the legal transmission more vulnerable to exposure compared to traditional terrestrial static wardens.However,most existing studies related to space/air covert communication neglect this kind of scenario,which yet urgently requires further and in-depth consideration to provide more robust protection for covert data transmission.
Figure 1(e) presents an efficient covert application where a cooperative space/air-based jammer is utilized to generate artificial noise to increase the randomness in the received power of the wardens,which has been widely investigated in existing secure communication works [11,25,38].Note that the interference caused by the jamming significantly deteriorates the system throughput when it cannot be well eliminated,so the power of the friendly jamming should be carefully optimized to keep a good balance between covertness and communication performance.In addition,the energy efficiency of the jamming signals is also a topic worth thorough discussions.
III.SYSTEM DESIGN
The core idea of covert communications is to hide the transmission behavior from wardens by introducing uncertainty to their received power [22].In this section,we review several efficient solutions for communication covertness,including noise uncertainty,cooperative jamming,imperfect channel state information,location variations,and unknown transmission time.Note that these typical solutions can be utilized alone or combined to enhance the system covertness in the application scenarios mentioned in the last section.
3.1 Noise Uncertainty
The lack of exact knowledge of the background noise power is considered as noise certainty.Generally,the background noise composes of thermal noise,quantization noise,and imperfect filters noise,etc [39,40],which is influenced by the weather and temperature in the space/air environment,and the varying electronic component tolerances.Therefore,the random characteristic of the environmental noise power can be exploited to introduce confusion to the detection decision-making process,which can be practically exploited in the potential scenarios shown in Figure 1 to guarantee the random received power at wardens.Specifically,the commonly-used noise uncertainty models fall into two categories,one of which is the bounded model where the actual noise power in dB follows a uniform distribution within a finite interval,and the other is the unbounded model[39].
To measure the performance of noise uncertainty in covert system design,we consider a scenario where a UAV serves five ground users with a warden to detect the transmission.The maximum speed of UAV is 50 m/s and the flying altitude of UAV is set as 100 m.The maximum transmit power of UAV is 100 mW.The user association,UAV transmit power,and trajectory are jointly optimized with block coordinate descent technique [41].Meanwhile,a heuristic method that associates user based on received signal strength with the UAV flying directly from the departure position to the destination position is employed for performance comparison.The results in Figure 2 reveal that larger noise uncertainty brings more benefits on minimum user achievable rate,while the covert performance is limited to the constrained communication resource when the noise uncertainty is sufficiently large.
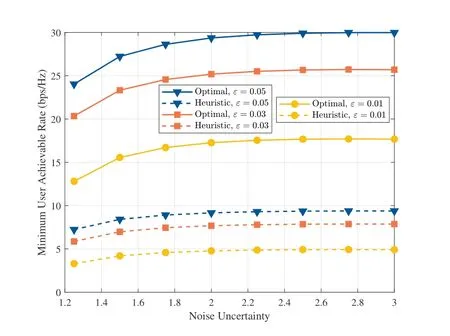
Figure 2.Performance of the minimum user achievable rate versus variance of the noise uncertainty for different allowed correct detection probabilities ε.
3.2 Cooperative Jamming
In addition to the natural noise uncertainty,as shown in Figure 1(e),artificial noise with random transmit power can be intentionally emitted by a cooperative space/air-based jammer to jam the wardens so that the uncertainty of their received signal power can be efficiently increased [42].Although the jamming signals degrade the detection performance of wardens,the communication performance deteriorates as well.Fortunately,different from the uncontrollable random noise,the jamming power can be optimally adjusted to mitigate the interference as much as possible while guaranteeing the system covertness.Along with the optimizations of the positions of the space/air-based jammers,the stealth and quality of the transmissions can be further improved.The existing research works in open literature usually assume that the instantaneous jamming power is a random variable that follows uniform distribution within the interval from zero to the peak transmit power[25,38].
3.3 Imperfect Channel State Information
The wireless channel state is vulnerable to environmental conditions and the small-scale fading can result in random channel coefficients,which is promising to mislead the wardens into setting wrong detection threshold and making wrong decisions about their received power [22,43].Therefore,channel estimation techniques are necessarily required to acquire accurate channel state information from the point of warden’s view.However,the characteristics of high delay and fast fading of space/air signal propagation environments lead to the difficulty and challenges of accurate channel acquisition [44].Thus,imperfect channel state information becomes a practical solution to covert system design.Particularly,the channel uncertainty is widely modeled as zero-mean circularly symmetric complex Gaussian random variables[43-45]to further analyze the wrong detection probability of the warden.
3.4 Location Variations
Random variations of locations of space/air transmitters can lead to random received signal power at wardens,which can be naturally leveraged to mislead wardens to make wrong decisions on transmission behavior detection [22,46] with non-optimal detection threshold.Especially in air communications scenarios,the characteristics of high flexibility and controllable mobility of aerial platforms[30],such as UAVs,can be fully exploited to enhance the location variations and further improve the system covertness.Note that the location variations between two consecutive time slots must satisfy the maximum velocity constraints of the aerial platforms.In contrast,the exact periodic high-speed motion locations of communication satellites can be tracked in real-time through the broadcast ephemeris[9],which poses more serious threats to covert transmission.Apart from the above active location variations,the location estimation errors due to radar or camera positioning also entail similar uncertainty effects.For instance,the authors in[24] and [41] modeled the location estimation errors as Gaussian random variables,based on which the detection error probability is analyzed theoretically.
3.5 Unknown Transmission Time
With the rapid development of satellite communication technologies,full-time and full-region communication services are readily realized.However,the private data transmission duration is practically much shorter than a full day and the pre-arranged time of transmission between two communication nodes is likely to be unknown to the wardens.The authors in[14]have shown that Alice can secretly pre-arrange a choice of a single time slot out of multiple time slots to achieve reliable communications while leveraging the ineffectiveness of wardens’ detector.However,most of existing works assume that wardens are aware of the time slot in which Alice is possible to transmit.Probabilistic transmission not only brings uncertainty to wardens’ received power,but also offers the potential to improve the system energy efficiency,which still deserves future extensive investigations.
IV.KEY CANDIDATE TECHNOLOGIES
Although the covert constraints limit the transmission quality to some extent,the communication performance can be enhanced with other techniques,such as resource allocation.To facilitate the practical implementation,in this section,we investigate several key candidate technologies for balancing covert constraints and data rate in space/air covert networks,with the technical barriers and potentials briefly discussed.
4.1 JointResourceAllocationandDeployment/TrajectoryDesign
On one hand,the system covertness can be significantly improved by reasonable wireless resource allocation.On the other hand,with the increasing number of deployed space/air platforms sharing limited communication resources,the resultant inter-beam or cochannel interference degrades the overall communication performance greatly[47].Therefore,careful radio resource allocation strategies are desired for maintaining system covertness and increasing user data rates.
The communication resource is usually multidimensional,and the resources in different domains actually interact with each other.In the time domain,the existing works mainly concern the transmission time slot assignment in time division multiple access(TDMA)systems.The proper selection of transmission slots demonstrates benefits for improving the link quality and enhancing covertness.Besides,as mentioned in Section III,the random time schedule is also vital for covert data transmission.In the frequency domain,high spectrum-efficiency frequency reuse schemes are urgently needed to address the spectrum scarcity issue in future networks.To this end,cognitive radio (CR) techniques can be utilized as an effective method to improve the system capacity by allowing unauthorized users to opportunistically exploit the licensed spectrum [3].In addition,the transmit power control is also a critical issue in terms of communication performance and covertness.Effective power control schemes call for a good tradeoff between the communication rate and the probability of being detected.Generally,the power control subproblem can be separated from the original multi-dimensional communication resource optimization problem,which can be solved by exploiting water filling method or heuristic approaches including the particle swarm optimization and genetic algorithm,and so on [23].In addition,the transmit power optimization subproblem can also be converted to a convex problem by exploiting the successive convex approximation(SCA)techniques and a suboptimal solution can be obtained by solving the approximated convex problem[24,25,41].
Different space/air platforms ranging from low to high altitude have different maneuvering properties,which offers an additional optimization degree of freedom to achieve high covertness and communication quality.To be more specific,in the space domain,satellites usually operate in fixed orbits and have fixed trajectories.In the air domain,airships and balloons are capable of remaining almost stationary in the air for a long period.The former can be controlled manually using electronic propellers and motors,and the latter depends mainly on the wind to deploy[6].Aircrafts generally travel on a specific route for a fixed period of time.Different from these types of platforms,the aerial platforms at low altitudes,such as UAVs,provide more flexible 3D mobility to improve the covert transmission performance and have attracted tremendous academic attention.However,the deployment or trajectories,and communication variables are usually highly-coupled and require joint optimization [30],which results in the exponential growth of computational complexity.Moreover,the highspeed movement of the aerial platforms contributes to the dynamic 3D network architecture and the timevarying interference,which facilitates real-time communication resource allocation.Therefore,several optimization approaches,including convex optimization,heuristic search methods,matching theory,and artificial intelligence based methods,can be promisingly exploited to carry out the network optimizations[1].
To demonstrate the benefits of joint optimization of resource allocation and deployment on covert transmission,we conduct a simulation where three UAV base stations are employed to serve several randomly distributed ground users assisted by a cooperative UAV-mounted jammer and two independent wardens attempt to detect the downlink transmission,as illustrated in Figure 3.The allowed flying altitude of the UAVs ranges from 200 m to 500 m.The maximum transmit power of both UAV base stations and UAVmounted jammer is set as 100 mW.In the simulation,we employ block coordinate descent based iterative algorithm to jointly optimize the user association,bandwidth allocation,UAV 3D positions,and transmit power to maximize the minimum user rate[48].Meanwhile,a heuristic method that associates users based on the K-means clustering method with each UAV base station positioned at the center of each cluster and the fixed altitude of 350 m is used for performance comparison.As can be observed,the performance of the proposed scheme labeled as‘Optimal’is distinctly better than that of the heuristic solutions in Figure 4.
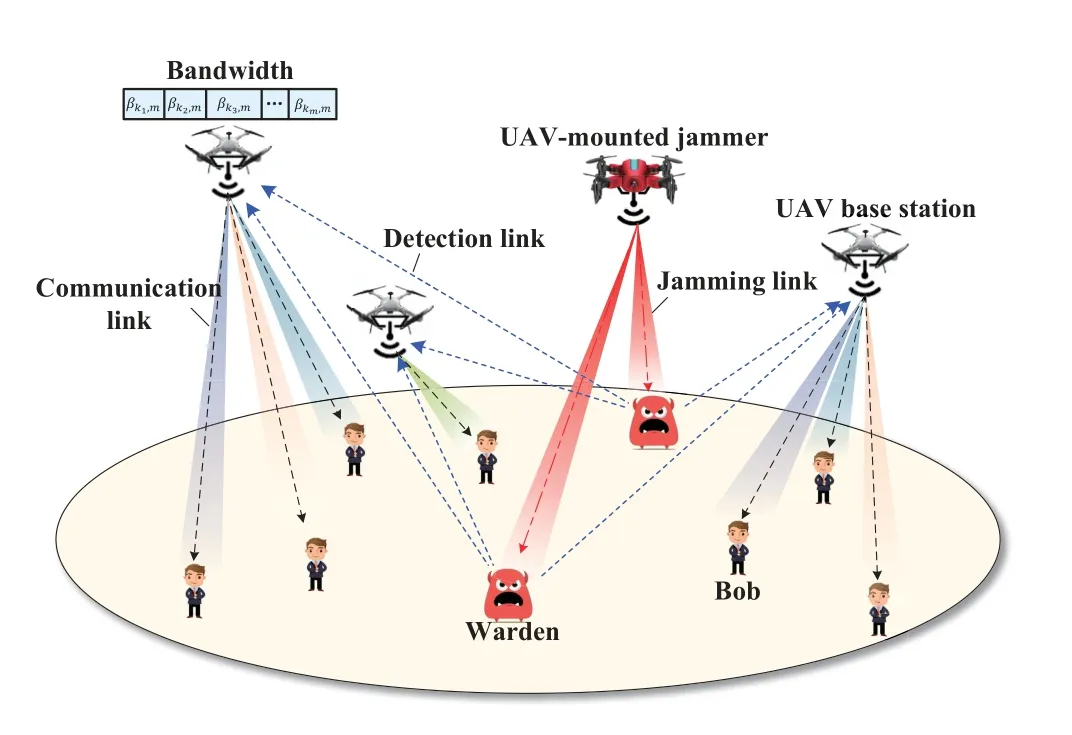
Figure 3.Illustration of the joint resource allocation and multi-UAV deployment.
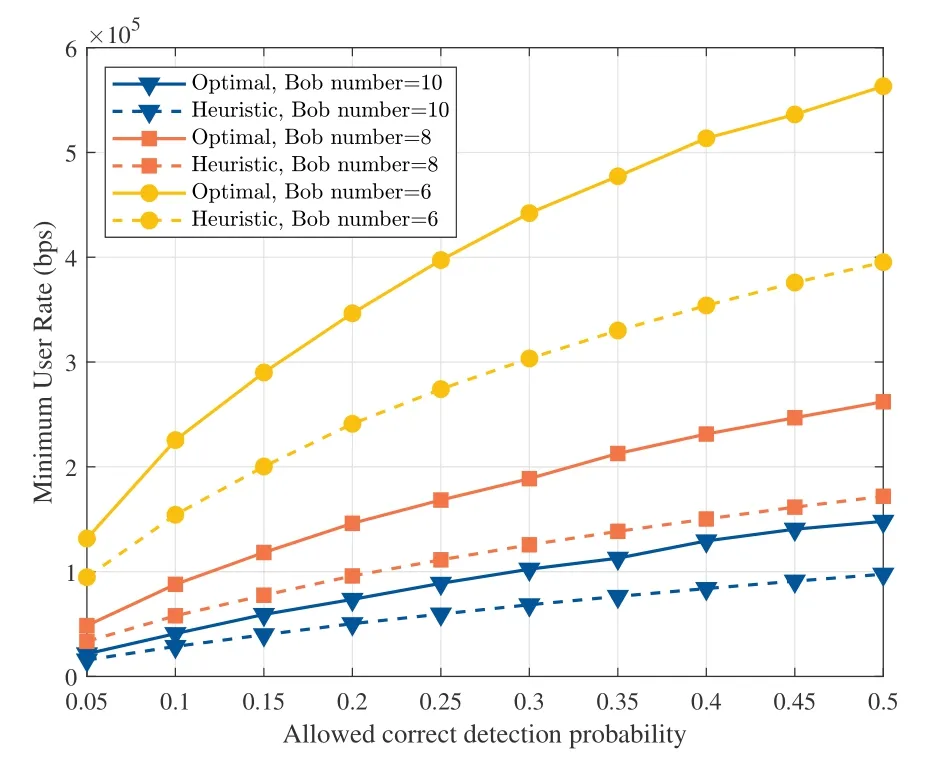
Figure 4.Performance of the minimum user rate versus variance of the allowed correct detection probability for different numbers of Bob.
At present,joint resource allocation and deployment/trajectory design have attracted tremendous academic attention.For instance,in [41],the authors jointly optimized the time slot allocation,UAV trajectory,and transmit power to achieve a high covert data rate while considering the location uncertainty of the warden.In order to maximize the effective throughput,the authors in [49] optimized the block length,transmit power,and the UAV relay location jointly under the two-phase covertness requirements.However,there is a scarcity of literature related to space covert communications.The authors in[50]proposed a penalty based SCA algorithm to maximize the minimum average covert rate via joint optimization of sensor association and the full-duplex UAV relay’s transmit power and trajectory.The authors in [51] optimized the RIS beamforming and the transmit power of Alice to improve the satellite covert signal quality under the constraints of limited onboard resources.
4.2 Multi-Antenna and Beamforming Enabled Space/Air Covert Communications
With the explosive growth in the variety of privacy data,such as color photographs and high-definition videos during military reconnaissance tasks,the demand for high data transmission rates is increasing.However,the conventional congested sub-6 GHz bands are now unsatisfactory for supporting future wireless covert communications [52].The trend of shifting communication to higher frequency bands is becoming acceleratively evident.Thanks to the shorter wavelength in the higher frequency bands,the equipment of large-scale antennas (also known as multiantennas)in a small area turns to be cost-effective for the size and weight limited space/air platforms.Combined with beamforming,the multi-antenna technologies not only provide more degrees of freedom to further improve the system throughput but also increase the covertness due to the narrow directional beams[53].Therefore,the multi-antenna and beamforming techniques are emerging as promising technology for space/air covert communications.
Generally,beamforming is achieved by properly adjusting the phases and amplitudes of the antenna weights to form desired radiation patterns.The beamforming architectures can be classified into three categories according to the multi-antenna hardware structure,namely analog beamforming,digital beamforming,and hybrid beamforming [1].For the analog beamforming,only one radio-frequency chain is required to connect to all antenna elements and only the phases of signals on antennas can be controlled by phase shifting.Compared to analog beamforming,digital beamforming achieves higher performance with digital signal processing techniques,but it also brings high hardware cost and energy consumption due to the independent RF chain connected to each antenna element [54].The hybrid beamforming integrates the advantages of the analog beamforming and digital beamforming to achieve a tradeoff between the beamforming performance,power consumption,and hardware complexity,where a small number of RF chains connect to a large number of antenna elements.Due to the practical constraints of power budget on space/air-based platforms,the analog beamforming architecture and the hybrid beamforming architecture may be much preferable for covert transmissions[55].
Some multi-antenna and beamforming related covert communication studies have emerged.For instance,the authors in[56]investigated a multi-antenna relay assisted covert communication scenario,where relay beamforming and power allocation are optimized in sequence to maximize the transmission rate.The authors in[10]exploited a multi-antenna jammer with zero-force beamforming techniques to achieve the maximization of covert transmission rate between the legitimate ground transmitter and the UAV receiver.The authors in [23] considered a jammeraided multi-antenna UAV covert communication system,where the transmit power and jamming power were jointly optimized to maximize the user rate.Considering both the single data stream and multiple data streams,the authors in[57]maximized the achievable covert rate by joint optimization of the transmit power and analog beamforming.
Although these exisiting works have shone a light on multi-antenna and beamforming enabled covert communications,there still exist some other critical beamforming related technologies to call for thorough consideration.For instance,the exact locations of wardens and users are practically assumed to be unknown to Alice,which results in the difficulty of beam alignment.One possible scheme is to sweep the beam to enable opportunistic communication to users,while this scanning process may cause more suspicion form wardens.The authors in [58] optimized the number of beams,transmit power,and UAV flight altitude to maximize the throughput by exploiting beam sweeping techniques,where a warden and a user were randomly located in a line coverage area.Besides,the beamforming technique can be exploited in highly dynamic space/air covert mesh networks to further improve the system performance.However,on one hand,the imprecise beam direction can bring strong interference to other data stream transmission link which deteriorates the communication quality [59].On the other hand,the deflected beams can easily cause power leakage to wardens.Therefore,the real-time beam alignment becomes critical issue worth special consideration under this kind of scenario.In addition,the beam handover mechanisms under covert constraints deserves of future further research,especially for space-based covert wireless networks.
4.3 RIS Assisted Space/Air Covert Communications
RIS is a planar surface of electromagnetic material composed of massive programmable reflecting elements.The electromagnetic properties including the amplitude and phase of each reflecting element can be actively adjusted by a smart RIS controller so that the incident signal can be strengthened and arbitrarily steered to the desired direction.Integrating RIS as relays into space/air covert communication scenarios,the received signal quality at a legitimate user can be enhanced and the signal strength at illegal wardens can be weakened.Besides,different from the conventional active transmission schemes,RIS requires no additional RF chains [60],which avoids high energy consumption and hardware cost.Thus,it is ideal for equipment on strictly resource-constrained space/air based platforms to assist covert data transmission.
As depicted in Figure 5,RIS units can be conveniently deployed on spatial,aerial,or terrestrial platforms to enhance the space/air covert performance.First,the long transmission distance between the spatial transmitters and aerial or terrestrial users usually contributes to large path loss.The direct links between the satellites and user terminals in dense urban environments are possible to be blocked by various obstacles.Combined with the passive beamforming techniques,the RIS mounted on satellites constitutes a potential candidate to overcome the drawbacks of signal attenuation and blockage.Besides,satellite relay networks are becoming a promising architecture for cross-layer covert transmission due to less emission power between two communication nodes,whose implementation is yet hindered due to the limited onboard processing capabilities.Benefiting from the high efficiency and low processing overhead,the RIS placed on satellites can efficiently address such issues.Second,thanks to the appealing agility of aerial platforms,RIS can be mounted horizontally on the top and the bottom of aerial platforms,or even implemented as a coating layer on the sides of aerial platforms,which can help achieve 3D full-space,smart,and flexible reflection in the sky [61,62].Explicitly,on one hand,the adoption of RIS techniques on aerial platforms enhances the directionality of covert transmission and expands the hiding range.On the other hand,the mobile properties of aerial platforms can be exploited to further improve covert performance.Therefore,the joint optimization of passive phase shifting of RIS and the deployment or trajectory of aerial platforms attracts much research attention.In [25],the transmit power,trajectory of the aerial RIS relay and the UAV jammer,passive beamforming,and user association were jointly optimized to maximize the covert energy efficiency.The authors in[63]alternatively optimized the transmit power,RIS phase shift,and the trajectory of UAV-RIS to maximize the covert energy efficiency.In [64],a UAV equipped with a RIS acted as a relay between two nodes,and the power control,passive beamforming,and positioning were jointly designed to maximize the covert rate.Third,different from the aerial or satellite-mounted RIS,only half-space reflection can be realized by the RIS mounted on terrestrial building facades,but similar aforementioned metrics can also be achieved.The authors in [51] investigated the application of terrestrial RIS in satellite covert communication systems,where the benefits of RIS in terms of increasing the minimum achievable rate were demonstrated.
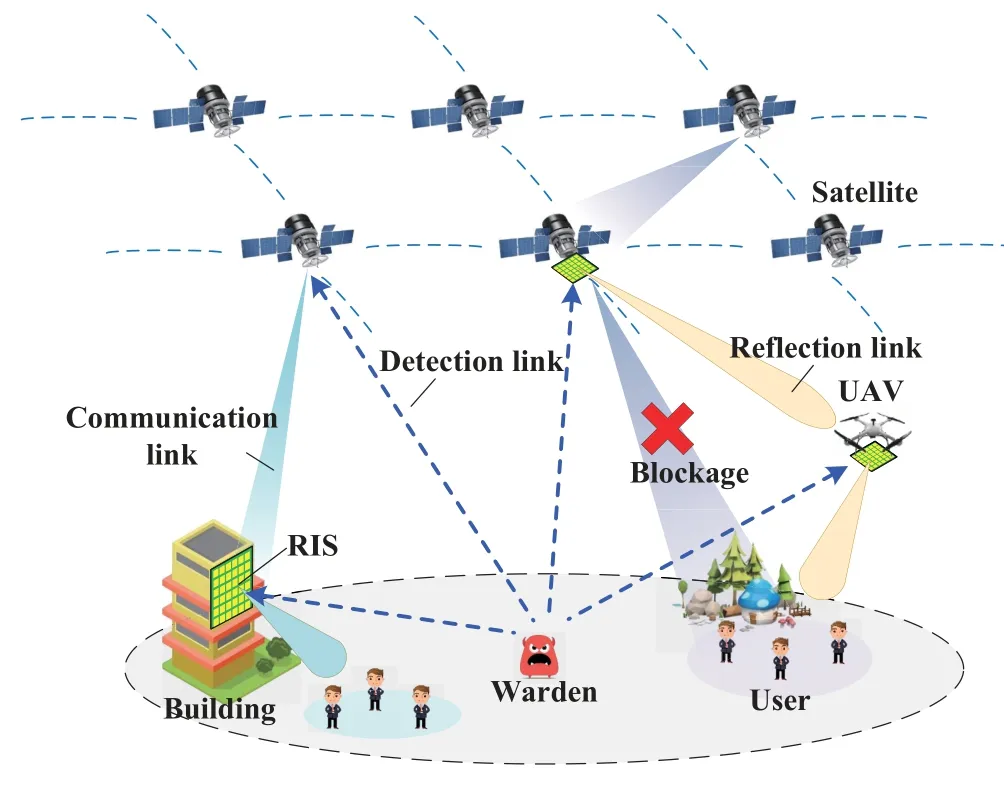
Figure 5.RIS assisted space/air covert communications.
At present,a greater amount of effort has been dedicated to aerial or terrestrial RIS aided stealthy transmission.Nevertheless,the practical analysis and optimization of RIS assisted satellite covert communications remain to be explored.Furthermore,the inherent uncertainty in the phase shift of the RIS can be exploited as an effective solution in the space/air covert communication system design [65],which enables the intentional confusion and degradation of detection performance at the wardens.However,it has usually been neglected in most available studies.
4.4 Intelligent Space/Air Covert Communications
Generally,existing studies derived and analyzed the optimal detection performance from the perspective of the wardens.However,some unexpected factors,including the uncertainty of the location of the wardens,the inexact channel state information,and the latency of static detection,result in the unavailability of the unactual system covertness to the legitimate user or network designers,which may contribute to the inaccurate covert performance or even the unachievable covert transmission in practical scenarios.Moreover,the future space/air covert communication networks composed of various devices at space/air/ground layers.The heterogeneous resource,self-organized architecture,and time-varying environments pose great challenges to covert communication design and optimization by the traditional model-based method.To some extent,intelligent algorithms assisted space/air covert communications is a promising technique to achieve covertness in real applications.
Artificial intelligence technologies employ computers or machines to mimic human thinking for problemsolving and decision-making,which encompass several research aspects such as machine learning and bio-inspired algorithms[66],and so on.Artificial intelligence empowered covert communication can harvest many benefits due to the powerful self-adaptation and learning capabilities.For instance,the deterministic channel model is the essential foundation for covert transmission establishment and performance evaluation,especially in multi-antenna covert systems.Owing to the significant advancements of machine learning,the acquisition of the channel state information from the surroundings of a radio link becomes possible.With the growing computing ability,machine learning methods can be employed on legitimate space/air platforms to obtain better channel state information,which will help signal shelter and further facilitate a practical covert transmission scheme.In addition,a more perfect channel estimation is also vital for the surveillance of wardens.Note that some works on public wireless networks,e.g.[67-69],can suggest a way for the application of machine learning for channel estimation in covert communications.
Additionally,due to the generally unavailable closed-form optimal detection threshold and intractable formulated optimization problems,it is challenging to obtain practical and high-performance solutions by conventional approaches,such as convex optimization.Benefiting from the superior interaction with unknown environments,as a critical subfield of machine learning,deep reinforcement learning(DRL)embracing the advantages of deep learning can overcome this challenge to achieve a satisfactory solution.In[70],a DRL method was developed to jointly optimize the UAV trajectory and the transmission time slot to shorten the task duration.The authors in [71] developed model-free DRL-based algorithm to optimize a UAV’s trajectory and transmit power to maximize the user average effective covert throughput.The authors in[72]proposed a distributed DRL algorithm to jointly optimize the trajectory and jamming power of the UAV,transmit power of devices,and bandwidth resources to balance the security level and training cost.With the implementation of DRL in space/air covert communication,the negative effects of the uncertainty of the network environment can be eliminated and actual covert performance can be practically achieved.
Furthermore,with the increasing complexity of the real-world space/air covert optimization problems,the bio-inspired algorithms are also envisioned as a candidate technology to obtain efficient solutions,which contains genetic algorithms,particle swarm optimization,ant colony optimization,and so on.For instance,the authors in[23]employed a particle swarm optimization based algorithm to optimize the transmit power to avoid the transmission detected by wardens and achieve high data rates.Nevertheless,the performance of the obtained solution by biologically inspired algorithms can not be guaranteed generally,which yields much attention to the improvement of the algorithm performance in the future.
V.OPEN PROBLEMS
Despite a few studies on covert communications,there are still many critical open problems that require indepth investigation for potential application scenarios shown in Figure 1.In this section,we prospect several future research directions in order to shed light on future opportunities.
5.1 Energy-Aware Space/Air Covert Communications
The system performance of space/air covert communication is limited not only by the strict covertness constraints and propagation environment,but also by the energy of the space/air platforms.These increasingly advanced and intelligent platforms may consist of a variety of sensors,which will inevitably lead to more energy consumption.Meanwhile,the trend toward miniaturization of platforms,such as UAVs and satellites,further limits energy consumption.In practice,since obtaining a higher covert rate inevitably requires higher transmit power,it is necessary to strike a balance between covert rate and power consumption.The covert energy efficiency issue was investigated in [63],where yet the kinetics-related energy consumption was not considered.Although[25]took the propulsion power consumption into consideration,the task operation duration was not optimized,which is vital in energy constrained communication system.Therefore,in order to improve the resource utilization rate and operation efficiency of platforms,energyaware space/air covert communications requires further thorough study.
5.2 mmWave/THz Based Space/Air Covert Communications
As the wireless communication techniques evolve from conventional microwave bands to millimeter wave (mmWave) and terahertz (THz) bands [73-75],the transmissions become highly directional,which is beneficial to covert communications.Besides,operating over the mmWave/THz bands increases the transmission data rates given much more available bandwidths and enables small-size transceivers due to the shorter wavelengths,which is beneficial to the space/air platforms in case of limited installation dimension.However,the channel model and propagation characteristics of mmWave/THz based space/air communications significantly differ from those of terrestrial RF communications.Thus,existing lowfrquency covert communication designs cannot be straightforwardly applied.Since directional communication is sensitive to movements,it may be difficult to perform real-time channel estimation or beam tracking.The authors in [25] examined the covert transmission performance over line-of-sight dominant THz frequenices while considering both largescale attenuation and absorption losses.However,mmWave/THz based space/air covert communications is still in its infancy,which needs more research efforts,especially considering the unique properties of the mmWave/THz channel and transceivers.
5.3 NOMA/RSMA Enabled Space/Air Covert Transmission
Improving spectral efficiency is a necessary measure to meet the ubiquitous connectivity requirements,and thus non-orthgonal multiple access(NOMA)technology is a potential solution.On one hand,NOMA allows multiple(covert and public)users to achieve access in the same spectral resource.On the other hand,transmissions of the public users can provide natural masking for covert user transmissions.Specifically,a public user can act as a friendly jammer with random transmitting power to mask the transmission of the covert user.The authors in[76]formulated a signomial programming problem to maximize the covert SINR by joint optimization of the flight height and transmit power of UAV with NOMA.However,the NOMA covert communication in satellite networks still remains vacant.In addition,rate-splitting multiple access (RSMA) as a bridge between orthgonal multiple access(OMA)and NOMA has received increasing attention in recent years,especially in satellite communications.The authors in [77] first investigated covert communications for RSMA,which,however,focused on terrestrial networks.The space/air covert communications assisted by RSMA is still blank and needs further exploration.
5.4 Cross Layer Design for Space/Air Covert Communications
With the increasing requirement for heterogeneous data traffic,cross layer covert transmission in spaceair-ground integrated networks is promising to guarantee the communication effieciency and security.In this case,the resource allocation in the physical and media access control layers and the routing in the network layer deserve joint design,while the two issues are highly coupled and the problem is challenging to solve [1,78].In addition,due to the highly dynamic network topology caused by the mobility of space/air platforms,the routing path is real-time changing and the communication resource is also time-varying.To guarantee the system covertness and enhance the communication performance,performing real-time cross layer design to manage the resources and update the routing paths is appealing and necessary.However,the current research concentrates on point-to-point covert communication and neglects multi-hop multiflow covert transmissions in SAGINs,which deserve dedicated efforts for further investigation.
5.5 Covert Scheme Against High-Performance Wardens
The existing works on covert communications mostly consider a single staic warden in the network,while there may be multiple dynamic heterogeneous wardens distributed in different regions of the SAGINs.In particular,the location information of wardens is difficult to obtain,and space/air wardens may move to different positions,which pose great challenges to guarantee considerable covert performance.Besides,different active and passive wardens may cooperate to minimize the overall detection error probability and further generate interference to deteriorate the covert system performance.Therefore,some auxiliary approaches,such as injecting jamming signals,are required to bring more uncertainty and ensure robust covert communication performance in the complex SAGINs.
VI.CONCLUSION
Integrating space/air networks with covert communications can yield considerable benefits for the highlevel security of confidential information privacy.In this paper,we provided a tutorial on space/air covert communications.First,we introduced the basics of covert communications,including the covert constraint model and covert performance metrics.Whereafter the typical application scenarios of space/air communication were also demonstrated.Then,several generic approaches for covert communication system design were summarized.Subsequently,we discussed several key enabling technologies for space/air covert communications in detail.Finally,several promising open problems were presented for space/air covert networks so as to inspire further investigation on these topics.
ACKNOWLEDGEMENT
This work was supported in part by the National Natural Science Foundation of China (NSFC) under grant numbers U22A2007 and 62171010,and the Beijing Natural Science Foundation under grant number L212003.
- China Communications的其它文章
- Improved Segmented Belief Propagation List Decoding for Polar Codes with Bit-Flipping
- Scenario Modeling-Aided AP Placement Optimization Method for Indoor Localization and Network Access
- Off-Grid Compressed Channel Estimation with ParallelInterference Cancellation for Millimeter Wave Massive MIMO
- Low-Complexity Reconstruction of Covariance Matrix in Hybrid Uniform Circular Array
- Dynamic Update Scheme of Spectrum Information Based on Spectrum Opportunity Incentive in the Database-Assisted Dynamic Spectrum Management
- Channel Estimation for Reconfigurable Intelligent Surface Aided Multiuser Millimeter-Wave/THz Systems

