Secure and Trusted Interoperability Scheme of Heterogeneous Blockchains Platform in IoT Networks
Xiao Liu,Mingyuan Li,Haipeng Peng,Shoushan Luo
School of Electronic Engineering,Beijing University of Posts and Telecommunications,Beijing 100876,China
*The corresponding author,email: penghaipeng@bupt.edu.cn
Abstract: With the rapid development of the Internet of Things(IoT),there is an increasing need for interaction between different networks.In order to improve the level of interconnection,especially the interoperability of users/devices between different nodes is very important.In the IoT heterogeneous blockchain scenario,how to ensure the legitimacy of the chain and how to confirm the identity of cross-chain information users/devices become the key issues to be solved for blockchain interoperability.In this paper,we propose a secure and trusted interoperability mechanism for IoT based on heterogeneous chains to improve the security of blockchain interoperability.In this mechanism,a primary sidechain architecture supporting authentication at both ends of the heterogeneous chain is designed.In addition,a distributed gateway architecture is proposed for cross-chain authentication and protocol conversion.The security and performance analysis shows that our scheme is feasible and effective in improving the security of cross-chain operations in IoT.
Keywords: authentication;blockchain Interoperability;heterogeneous chain;IoT
I.INTRODUCTION
The rapid growth of the IoT has increased the complexity of data and scenarios exponentially.As users/devices may belong to different IoT networks,secure and trustworthy communication between users/devices across different IoT networks is the core issue at hand.Blockchain technology provides a trust mechanism for IoT,unlike traditional IoT systems,it is a decentralized trusted distributed storage system that allows all nodes in the network to jointly own,manage,and supervise data through P2P networks,distributed consensus algorithms,cryptography,etc [1].The system can operate independently of trusted third parties and is unforgeable,tamper-proof,and traceable.
However,using blockchain technology to improve the security of the IoT is not sufficient;most IoT devices have limited computing power and storage resources,and complex encryption and decryption algorithms will consume a lot of computing power,resulting in slower communication,which further leads to poor interoperability between IoT devices [2].Thus,the introduction of blockchain cross-chain technology can enable secure and trusted asset transfer,information exchange,and application collaboration between complex IoT networks.Typically,each blockchain represents an independent IoT network,and interactions between different IoT networks become interactions between different blockchains.As a result,blockchain interoperability is becoming one of the key technologies for secure communication between different IoT networks [3].As a trusted intermediary between blockchain services,cross-chain technology simultaneously breaks the “silo effect” formed by the heterogeneity of consensus algorithms[4],encryption mechanisms [4–6],and ledger structures [7]between blockchain services to achieve interoperability between different blockchains and solve the problem of asset or information exchange between different IoT networks[8].At the same time,the structure and characteristics of blockchain systems have led to problems with different cross-chain approaches,such as the notary trust problem and the side/relay chain security problem[9].Therefore,cross-chain technology is also considered to be the foundation and core of building the Internet of Trust and the Internet of Value.
In this paper,we propose a cross-chain interoperability architecture for different IoT networks to achieve secure and trusted interoperability.Clearly,we build interoperability between heterogeneous chains by representing different networks of the IoT through blockchains.We add a specific role as a main chain for coordinating the communication between two heterogeneous side chains and connecting users/devices to the IoT blockchain belonging to each of them.However,it is important to address chain-to-chain identification and confirm the identity of cross-chain users/devices in the IoT.On the one hand,the IoT blockchain system is a multi-chain,interconnected system where the different systems are unknown and incompatible with each other.The usual design does not consider horizontal communication methods,but rather vertical development[10].If one wants to achieve mutual trust between different systems and two systems that are unknown to each other to be able to transact securely,then the identification of the unknown system and how to verify the validity of the chain is necessary.On the other hand,users/devices from different systems and different domains want to interact in the whole IoT blockchain system,and if the users/devices are not trusted,the whole IoT blockchain system will be affected.In cross-chain operations,how to verify the legitimacy of the user/device and thus determine whether the user/device is eligible for cross-chain operations also needs to be looked into.Hence,the above two challenges are the key issues that need to be addressed in the current secure interoperability of the IoT blockchain.
In sum up,there is a need to provide a more secure and trusted authentication method for IoT blockchain interoperability.Our work focuses on how to achieve interoperability of two heterogeneous blockchains,complete authentication based on the interoperability of two heterogeneous blockchains,and ensure the security,integrity,and validity of cross-chain operations.In this context,we propose a secure and trusted interoperability mechanism based on heterogeneous blockchains in the IoT.The user/device does not need to be re-authenticated with one authorization for one operation.The main contributions of this paper are as follows:
· Design and implement the built cross-chain architecture.Based on blockchain technology to achieve cross-chain interoperability of IoT users/devices,and also to achieve user/device authentication in the cross-chain process.It not only reduces the burden of the main chain but also ensures efficiency in the process of trusted authentication.
· Based on the architecture proposed above,we design a secure operation mechanism between heterogeneous chains to perform identity authentication during interoperation.Primary and secondary identity tokens are used to enhance the validity of cross-chain access between source and destination chains and avoid multiple accesses after one authorization.With the dual authentication of cross-chain transaction legitimacy and user/device identity legitimacy,the security of cross-chain access between source and destination chains is improved.
· A dynamic gateway structure is designed to adapt to this architecture,using decentralized clustering and a consensus mechanism to control the election of the leader gateway,so that when the leader gateway is threatened,other gateways can continue to work in its place and ensure the normal operation of cross-chain operations.
The rest of the paper is organized as follows.Section II reviews related work.Section III introduces the cross-chain architecture.Section IV details the crosschain secure access mechanism for two heterogeneous chains,including the designed dynamic gateway structure.Section V provides security and performance analysis.Section VI is the conclusion.
II.RELATED WORK
Cross-chain interoperability is a broader scope of research than cryptocurrency and value transfer [3].In terms of architecture construction,there are many studies on cross-chain interoperability architectures and communication protocols.Due to the limitations of the blockchain itself,researchers usually expand from the side chain and give more functions to the main chain.That is,most interoperability between blockchains is mainly constructed in the form of main and side chains [8,11].To meet the demand for cross-chain transactions,Y.Yu et al.[12] proposed a heterogeneous multi-chain architecture and an extensible multi-level partitioning model to achieve efficient cross-chain transactions through main and multiple parallel side chains.Y.Jiang et al.[13]suggested integrating multiple blockchains through a cross-chain framework to achieve efficient and secure IoT data management.T.Lin et al.[14] suggested using extensible cross-chain protocols with light clients and relays to enable inter-chain messaging while supporting high-performance large-scale blockchain cross-chain transactions.In[15],the problem of cross-chain communication is well done to provide the utility and scalability of large-scale blockchains by using a powerful interoperability and programmability platform across heterogeneous blockchains.For cross-chain interoperability,the exibility and cost of the platform are also crucial.A platform architecture for a multi-tenant lockchain system was proposed by I.Weber et al.[16].Each tenant has a separate blockchain.All tenants are anchored to a common blockchain.It is divided into long-lived blockchain and short-lived blockchain for long-term and short-term business requirements.For messaging,blockchain routing is mainly utilized for message transfer management.By transforming local transactions into standard cross-chain transactions,blockchain routers analyze and transmit cross-chain communications,breaking the isolation between different blockchains and enabling trusted interconnection between multiple blockchains[10,17].
However,how to ensure that the identity of the initiator of the transaction process cross-chain has not changed and whether there is someone impersonating.The use of blockchain can ensure the reliability and security of authentication.In terms of access authorization,currently,the most popular blockchainbased user authentication uses on-chain and off-chain collaboration to store user information and grant the user the appropriate permissions in different applications through smart contracts [18].In [19],by combining internal and cross-application transactions,the blockchain is used to form a directed acyclic graph,which is only locally visible to internal data,and crossapplication data is made public throughout the system and visible to all applications,thus enabling the sharing of interoperability information cross-chain.R.Qiao et al [20] proposed a smart contract based on a rational node value transfer mechanism deployment and execution scheme.This scheme enables autonomous dynamic cross-chain interaction between heterogeneous consortium chains.Information sharing is possible through collaboration between multiple cooperative healthcare consortium chains.
So far,many scholars have applied the interoperability of blockchain to cross-domain identity authentication in IoT.Master-slave chain-based trusted crossdomain authentication for IoT achieves trusted authentication and trusted interaction across chains by parsing cross-chain authentication requests through the master chain [21,22].Y.Jiang et al [22] proposed a framework for connecting different blockchains in IoT and constructed a decentralized cross-chain access model.The generation information of events is recorded through Tangle which operates as the backbone of all IoT devices.A notary mechanism is used for data sharing or transactions in IoT.However,the framework is suitable for the management of IoT devices with fewer resources.In the access rights scheme,multiple signatures,a more specific way to constrain user behavior,are used to support cross-chain value exchange for different types of token transfers.This ensures the security and scalability of the value exchange[23].In the IoT environment,to ensure the reliability of cross-domain authentication,N.Fotiou et al [24] proposed a solution for end-user and IoT device interaction,based on smart contracts that enable access control,authentication,and payment transactions.To save the computational overhead of authentication,W.Wang et al [25] proposed BlockCAM,a blockchain-based cross-domain authentication model that compares the hash of a user’s authorization certificate with the hash stored on the chain.R.Sharma et al [26] proposed a method for vehicle authentication and privacy protection in IoT,and the proposed decentralized framework can manage highly dynamic and large-scale data.
Considering the use of the main-side chain for identity authentication in the IoT environment to build a trusted authentication platform.However,as mentioned above,few papers adopting main-side chains focus on solving the trust problem between the initiator and responder in the cross-chain process.Therefore,this paper designs a cross-chain interoperability process with identity authentication to reduce the burden on the main chain.Compared with other crosschain interoperability authentications introduced in this paper,our cross-chain interoperability has better authentication efficiency and security in complex IoT environments.
III.THE PROPOSED CROSS-CHAIN INTEROPERABILITY ARCHITECTURE
In order to solve the cross-chain security and effectiveness in the cross-chain process,and to achieve identity legitimacy and cross-chain legitimacy.We propose a cross-chain interoperability architecture.The overall architecture is depicted in Figure 1.In the following sections,we will discuss the various modules of the proposed cross-chain interoperability architecture and cross-chain operations.
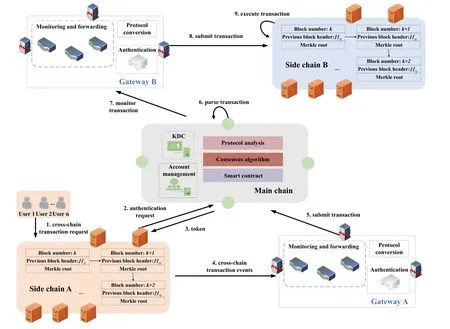
Figure 1. Cross-chain interoperability architecture.
3.1 Cross-Chain Interoperability Architecture
The four main modules are the source blockchain,the destination blockchain,the main chain,and the gateway.The source blockchain and the destination blockchain are the initiator and the receiver,respectively.The main chain is the sender,as well as manages the user/device information for each blockchain.The gateway is the authenticator of user/device identity and is responsible for monitoring and forwarding cross-chain events.
3.1.1 Source Blockchain
The source blockchain is the initiator of cross-chain transactions,i.e.,the side chain A.As depicted on the left side of Figure 1,the source blockchain is a P2P network of five nodes including a complete blockchain.The blockchain can be a private blockchain or a consortium blockchain.When a user initiates a cross-chain transaction,the source blockchain requests the main chain to authenticate the cross-chain user/device,thus obtaining the identity token granted by the main chain.The source blockchain then uses this token to communicate with its corresponding gateway.The source blockchain deploys an authentication smart contract and a cross-chain smart contract on each node.
3.1.2 Destination Blockchain
The destination blockchain is responsible for the execution operations of cross-chain transactions.Like the source blockchain,the destination blockchain can be a private blockchain or a consortium blockchain.As depicted on the right side of Figure 1,the destination blockchain is a P2P network consisting of three nodes,i.e.,the side chain B,which also has a complete blockchain.The three nodes are responsible for recording each transaction data into the blockchain.The destination blockchain also deploys authentication smart contracts and cross-chain smart contracts on each node.
3.1.3 Main Chain
The main chain helps the source and destination blockchains to communicate with each other.All application chains and their corresponding users/device information must be registered in the main chain before the cross-chain operation.In this way,when the source chain requests a cross-chain,the main chain analyzes the protocol of the cross-chain transaction and verifies the legitimacy of the cross-chain transaction.Then,this cross-chain transaction participates in the consensus of the main chain.In our main chain network,there is a key distribution center (KDC) node.When a user requests a cross-chain transaction,this node authorizes the user/device and further distributes the user/device’s identity token.Therefore,based on the characteristics of the main chain,we provide a cross-chain user authorization and trust communication service mechanism.
3.1.4 Gateway
As an intermediate node between the application chain and the main chain,the gateway uses a clustering approach to improve the trustworthiness.Here,the gateway not only acts as an authentication node to verify the identity of cross-chain users but also acts as a routing node to monitor and forward cross-chain information.Each application chain has its corresponding gateway cluster,and the application chain and the gateway are in a one-to-many relationship.In general,there is no uniform transaction format between heterogeneous chains.Therefore,the gateway is also responsible for the protocol conversion of cross-chain transactions.
3.2 Cross-Chain Operations
The following are the different operations performed by the proposed architecture.The operations include various stages of registration,authentication,and cross-chain interoperability.
3.2.1 Registration Stage
The main chain is an independent chain.In order to interoperate cross-chain,all application chains must send a request to the main chain to register the chain and a request to register a cross-chain service.In cross-chain transactions,the main chain can verify the legitimacy of the application chain based on the registration information.It can also verify the legitimacy of cross-chain transactions.At the same time,user/device identity is registered to the main chain in order to provide authentication and strengthen trust services in cross-chain transactions.The application chain,crosschain services,and cross-chain user/device identity registration are shown in Figure 2.
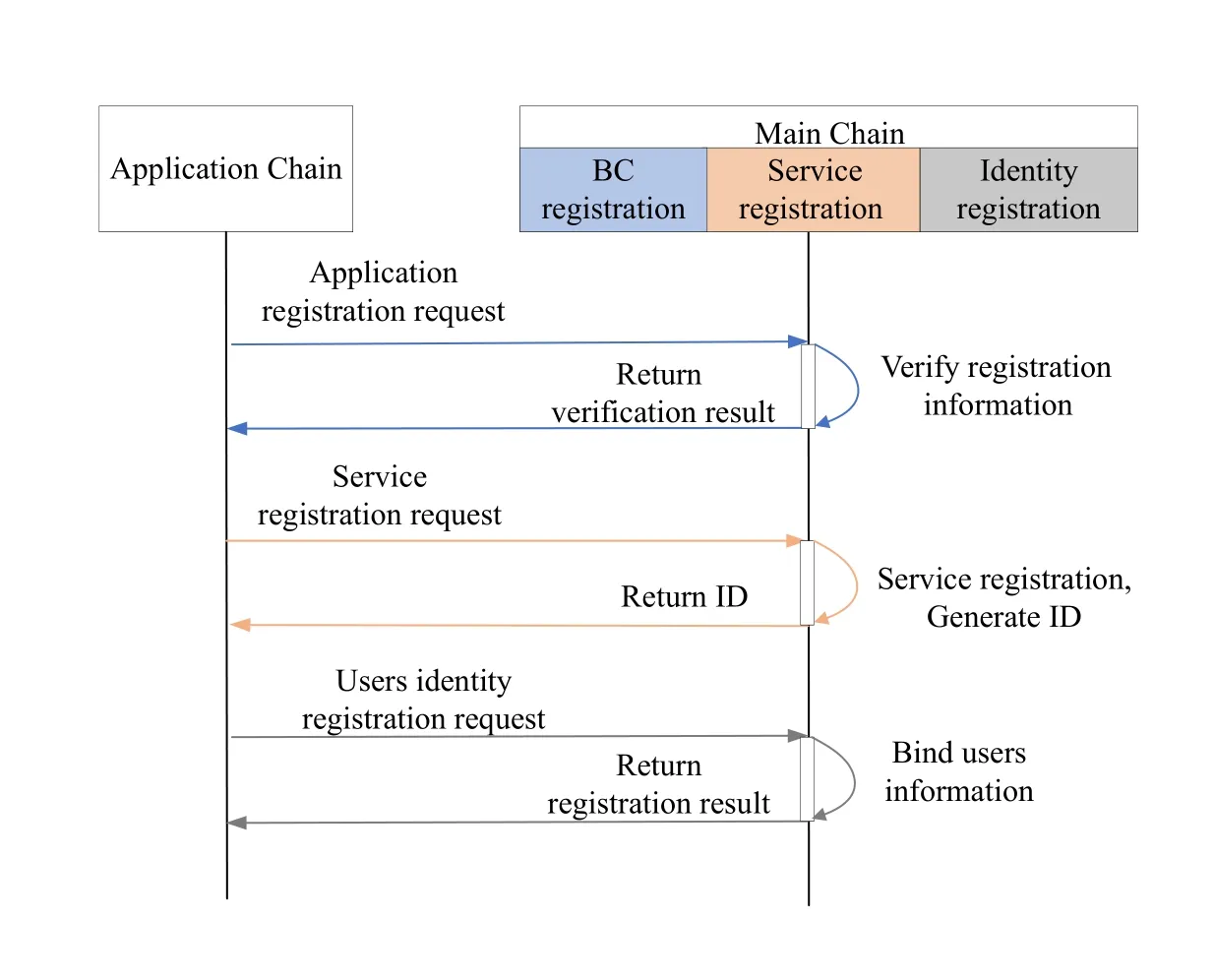
Figure 2. Registration process.
Only after the application chain is registered in the main chain,subsequent cross-chain operations can be performed.The registration information includes the anonymous ID of the application chain,domain address,public key,and other metadata,etc.The anonymous ID is generated by the existing public key of the application chain after hashing.In steps 1-3,the application chain administrator sends a registration request to the main chain.The main chain initiates a registration smart contract to validate the registration information on the chain.The result of verifying the registration is then returned to the administrator of the chain.
After the application chain registration is completed,in order to perform cross-chain operations,the administrator also needs to register the cross-chain service in the main chain.The registration service information is mainly the validation rules of the application chain.In the cross-chain operation stage,the main chain needs to verify the validity of the crosschain transactions of the application chain.In steps 4-6,the application chain administrator sends a service registration request to the main chain.The main chain initiates a service registration smart contract to complete the application chain registration and generates a unique ID.The main chain then returns this ID to the application chain administrator.
After the application chain is connected to the main chain,the application chain administrator registers the user information.Because users/devices can only perform cross-chain operations after they have registered their cross-chain identity in the main chain.The user/device’s identity registration information bound on the main chain is the user/device’s identity information on the chain.In steps 7-9,the application chain administrator sends users/device identity registration requests to the main chain.The main chain identity registration smart contract binds the user/device identity based on the cross-chain service ID of the application chain.The main chain then returns the registration result to the application chain administrator.
3.2.2 Authentication and Cross-Chain Interoperability Stage
The KDC in the main chain is responsible for the distribution of identity tokens.The cross-chain transactions applied by the users/devices on the chain can be performed multiple times with one authorization within the validity period.The user/device obtains a primary identity token from the KDC and authenticates with gateway A through the primary identity token.Only after gateway A has passed the user/device identity authentication for cross-chain operation,the operation to the main chain can be performed.The cross-chain interoperability communication really starts after the user/device is authenticated by the gateway A.Authentication and cross-chain interoperability are shown in Figure 3.
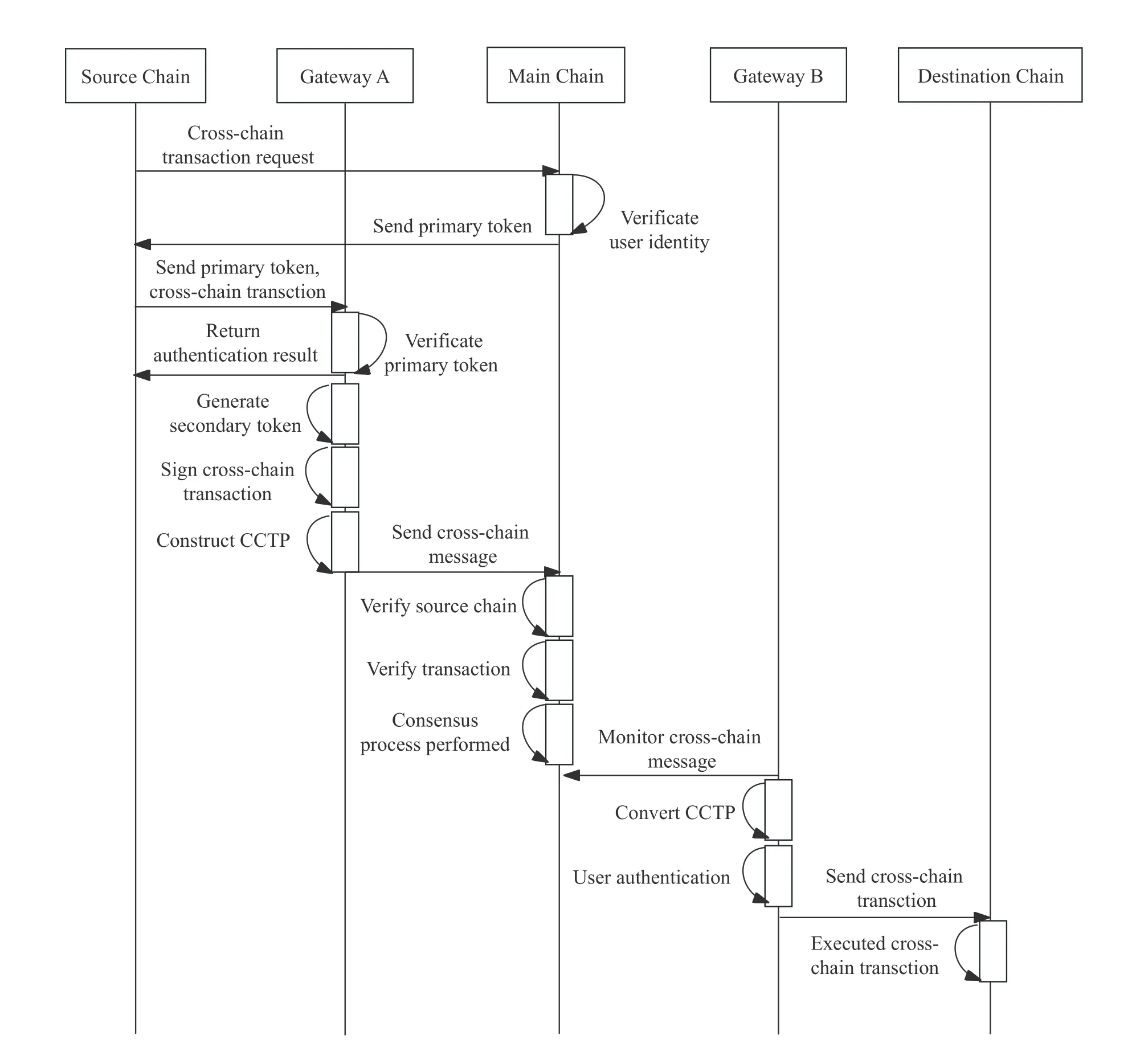
Figure 3. Cross-chain interoperability process.
In steps 1-3,the on-chain user/device submits a cross-chain transaction request to the main chain.The KDC of the main chain performs identity verification based on this application chain and user/device information.After the user/device identity is passed,the KDC issues a primary identity token to the user/device.In steps 4-6,the user/device submits a request for a cross-chain transaction to the gateway A via the primary identity token.Gateway A performs user/device identity verification based on the primary identity token.After the authentication is passed,gateway A returns the authentication result to the user/device.
In steps 7-8,gateway A will generate a secondary identity token and sign the cross-chain transaction,as well as construct a common cross-chain communication transaction format and send it to the main chain.In steps 9-12,the main chain monitors the cross-chain messages and verifies the validity of the application chain.Meanwhile,the main chain network reaches consensus on the next block and records the crosschain transaction to the chain.The cross-chain transaction is stored in the destination chain queue of the transaction.In steps 13-15,Gateway B of the destination chain listens to the cross-chain messages and converts the common cross-chain communication transaction format.Gateway B authenticates the user/device identity.After the authentication is passed,the crosschain transaction is sent to the destination chain.Finally,the destination chain verifies the legitimacy of the transaction.After the authentication is passed,the cross-chain transaction is executed.
IV.THE PROPOSED CROSS-CHAIN ACCESS MECHANISM
4.1 Definitions
Definition 1.Application chain set
Each application chain registered in the main chain becomes a side chain of that main chain.Related concepts are present as follows:
ACis a set of all application chains registered in the main chain.
Definition 2.Cross-chain service set
Because the validation rules may be different for each chain,the main chain performs specific crosschain transaction validation through the cross-chain service.The service can be denoted as follows:
CSis a set of all application chain cross-chain services in the main chain.
Definition 3.Cross-chain user set
The user identity is registered in the main chain,and the token is issued to the user through the registration information.Related concepts are present as follows:
CUis a set of cross-chain users,each user is bound to their own application chain.
Definition 4.Cross-chain authorization request
Users can have different identities in different application chains,but the user is unique in each application chain.The user can be denoted as follows:
IDsis the source blockchain ID and is the initiator of the cross-chain transaction.is the user ID of the source blockchain,which is bound to the corresponding application chain.
Definition 5.Token
The token is to verify the legitimacy of the user’s identity,which is verified through the gateway in cross-chain interoperability.Tokens are divided into primary and secondary identity credentials.The token can be denoted as follows:
Tokenpridenotes primary identity credential.is the address of the source blockchain user.ADgwAis the gateway address connected to the source blockchain.
Tokensecdenotes secondary identity credential.is the public key of the source blockchain user.is the signature of the source blockchain user.
Definition 6.Cross-chain authentication request
The authentication process is specifically performed by the gateway,leaving the source blockchain and reaching the destination blockchain,and cross-chain interoperability can be performed securely only if both gateways are verified by both sides.So the authentication request is denoted as:
T.authentic1 executes the cross-chain authentication request of the source in gateway A.We defineinfoAuthas a triple.infoBCincludesIDd,,andinfoTrans.
T.authentic2 executes the cross-chain authentication request of the destination in gateway B.
Definition 7.Cross-chain transaction request
Cross-chain transaction requests mainly go through the transport protocol of the main chain.So the crosschain transaction request is denoted as:
CCIPis the transmission protocol from gateway A to gateway B.
Definition 8.Validation policy set
In cross-chain interaction,verify whether the application chain and cross-chain transactions are legal.It can ensure the security in the process of cross-chain transactions.So the set is denoted as:
V Pis to execute different verification policies according to different types of application chains in the chain.
4.2 Application Chain Related Registration
4.3 Authorization and Authentication

4.3.1 Authorization In the proposed cross-chain interoperability mechanism,user authorization is evaluated through Algorithm 1.Whether it is positive or negative authorization is recorded on the main chain.After the authorization result ends,Tokenpriis generated for a request that agrees to the authorization.TheTokenprirecords in detail the identity attribute information that needs to be satisfied during gateway authentication.The generatedTokenpriis also recorded on the main chain.The user’s cross-chain authorization request is tracked and traced through the chain to prevent malicious users from conducting illegal cross-chain operations or replay attacks.
The time complexity of the algorithm by querying theIDsandisO(1),the time complexity of generatingTokenpriwith AES-128 isO(n),and the time complexity of the algorithm by BFT [27] consensus isO(n2).Therefore,the overall time complexity of Algorithm 1 isO(n2).
4.3.2 Authentication
The identity authentication of users’cross-chain operations is realized through Algorithm 2.The user sends information such asTokenpri,cross-chain transactions to the gateway A.After gateway A receives the cross-chain message,it calls the function tokenValidate() to verify the validity ofTokenpri.The verification result is a positive authorization or negative authorization.If the authentication is positive authorization,the gateway A calls the function tokenGenerate()to generateTokensec.At the same time,gateway A signs theMerkleRootof the cross-chain transaction.

The time complexity of the algorithm for verifyingTokenpriisO(n).If the verification passes,the time complexity of the algorithm for generatingTokensecand signatureisO(n).So the time complexity of Algorithm 2 isO(n).
4.3.3 Cross-Chain Interoperability Protocol(CCIP)This paper designs a cross-chain interoperability protocol(CCIP).The gateway A builds the protocol after the gateway A generatesTokensecand signs.This protocol enables convenient interoperability between heterogeneous chains.In cross-chain transactions,it is not only necessary to verify the legitimacy of cross-chain operation users,but also the legitimacy of cross-chain transactions.The detailed structure of CCIP is shown in Figure 4.
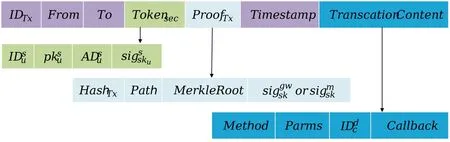
Figure 4. Structure of CCIP.
IDTxrepresents the identity of each cross-chain transaction,whileFromandToareIDsandIDdrespectively.ProofTxprovides validation of validity and existence.It includes the hash of each cross-chain transactionHashTx,hash sets of path nodesPath,root hash of transactions MerkleRoot,gateway signatureor main signatureTimestampis the time identifier of cross-chain transaction.TranscationContentprovides specific execution-type operations for transactions.It includes call functionMethod,parameters to call functionParms,destination blockchain contract identification,and callback function nameCallback.
4.4 Cross-Chain Interoperability
After gateway A builds CCIP,it transmits cross-chain data to the main chain through CCIP.The main chain verifies the legitimacy and existence of cross-chain transactions.The specific implementation is in Algorithm 3.The main chain parses CCIP to getIDs.ByIDsjudging whether this application chain belongs to the registration chain in the main chain.If so,the validation rules for this source chain will be retrieved viaIDs.The main chain calls the legitimacy verification function transacLegiCertify()to verify the legitimacy of cross-chain transactions.If it is legal,the main chain calls the existence verification function transacExistCertify()to verify the existence of the cross-chain transaction.Whether the above two verification results are true or false.The main chain records the verification result on the chain.In the case that both verification results are true,the relay chain generates a transaction signatureand recordson the chain.
Parsing CCIP time complexity isO(n).QueryingIDsandvpihas a time complexity ofO(1).The time complexity to verify the existence of a transaction islog(n).The time complexity required to validate and generate the signature isO(n).Finally,the time complexity to upload by BFT consensus isO(n2).So the overall time complexity of Algorithm 3 isO(n2).
After the destination chain gateway B monitors the cross-chain message,it parses the CCIP.Call functions transacLegiCertify()and transacExistCertify()to verify the validity and existence of cross-chain transactions.If verification is valid,authenticate the user.Compare the source hash with the current hash value for a match.If true,gateway B generates signature information.Gateway B will perform protocol conversion on CCIP.Send T.excute() to the destination blockchain to execute the transaction.Algorithm 4 specifically describes the implementation process.
The time complexity for Gateway B to parse the CCIP and verify the legitimacy of the transaction isO(n).The time complexity of passing verifying the existence of the transaction islog(n).The time complexity of accessing the table isO(1).Raft[28] consensus time complexity isO(n).The check and signature algorithms have the same complexity as the previous algorithms.So the time complexity of algorithm 4 isO(n).
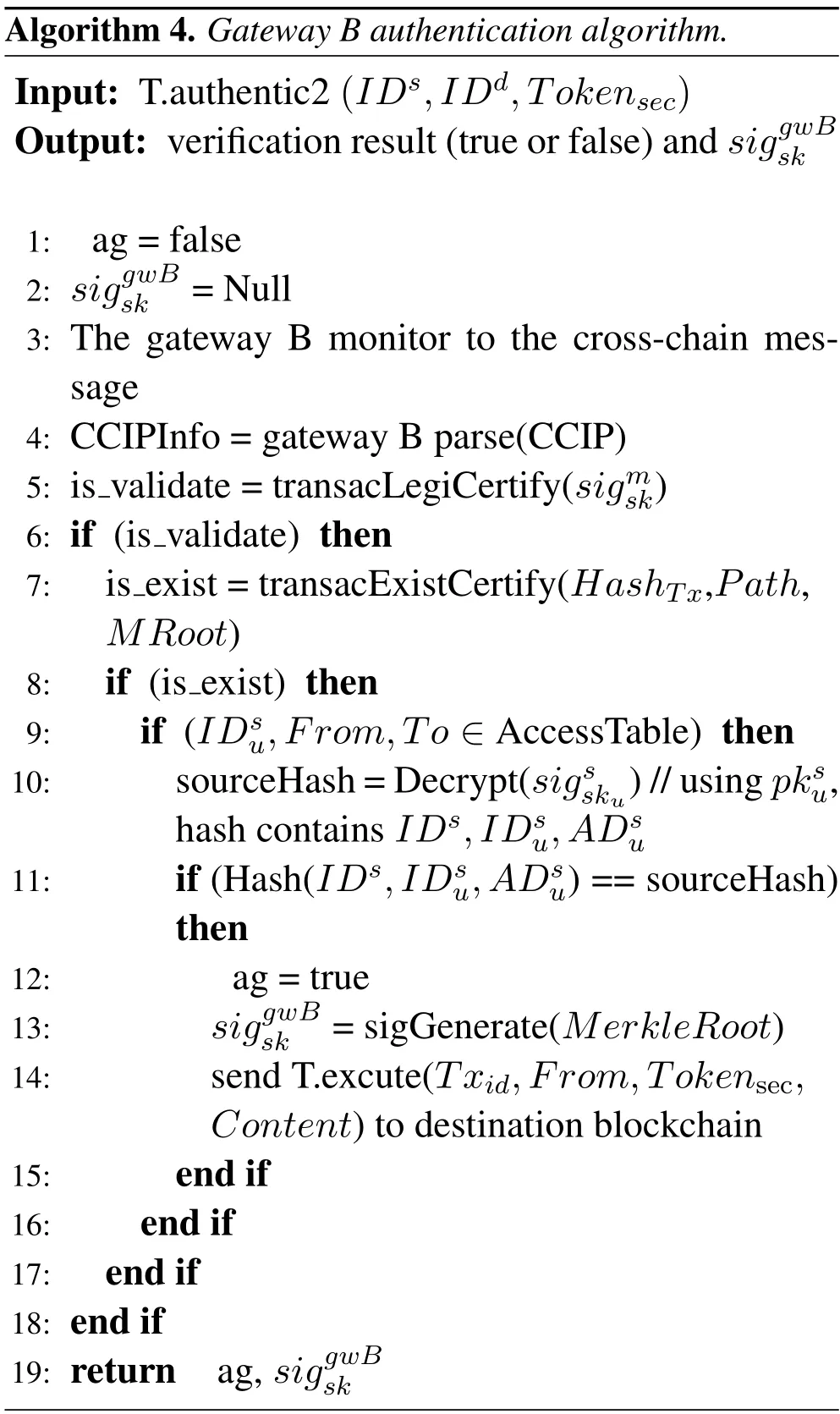
The cross-chain transaction reaches the destination blockchain.The destination blockchain performs signature verification on the gateway B.The verification is valid,and the destination blockchain executes the corresponding cross-chain transaction.After that,the main chain can uniformly return the receipt to the source blockchain and the destination blockchain.At this point,the cross-chain interoperability is complete.
4.5 Gateway Consensus Mechanism
In this paper,the main work of the gateway is authentication,signature,generation of secondary token,and protocol conversion.The cross-chain gateway adopts the clustering method.Each slave chain has its own gateway cluster.When the slave chain registers with the main chain,the main chain puts the gateways of the isomorphic chain in a pool.When a crosschain transaction occurs,protocol conversion is not required between homogeneous chains,but like heterogeneous chain gateways,the gateway needs to use a consensus mechanism to control the election of the main gateway.Once the main gateway is attacked and fails,other gateways can replace the main gateway.The gateway works to ensure the normal operation of cross-chain transactions.[28–30] are the most classic types of consensus algorithms in the blockchain.Considering the architecture of cross-chain interoperability in this paper,we adopt the consensus algorithm in[28]to conduct cross-chain transaction identity authentication,protocol conversion,etc.,so as to improve the efficiency and performance of the overall cross-chain transaction.As shown in Figure 5,it shows the cross-chain gateway model and its consensus mechanism.A side chain has corresponding gateway clusters.The gateway clusters for each side chain are independent of each other.
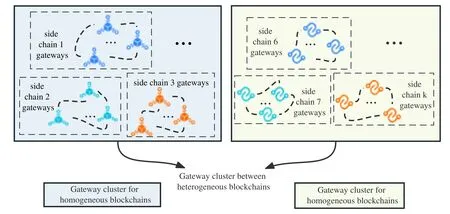
Figure 5. Cross-chain gateway model.
G1is the node of the gateway,which is divided into a leader node and multiple follower nodes.
As shown in Figure 6.There are three roles in a gateway cluster of a side chain: leader,follower,and candidate.The leader node is responsible for receiving cross-chain messages and synchronization management of logs.After reaching a consensus with the follower node,it feeds back the cross-chain message result to the slave chain.The follower node is responsible for responding to the message log synchronization request of the leader node.The follower node is converted when the leader node is down and participates in the election of the new leader.If it obtainsvotes,it becomes the new leader node,otherwise,it converts back to the follower node,and each node at any time is in one of these three states.The election of the leader node is triggered by a timer.The election timer time of each node is different.The state at the beginning is the follower.After a node timer triggers the election,the term is incremented,and the state changes from the follower to the candidate.To initiate a voting request to other nodes,there are three possible situations:
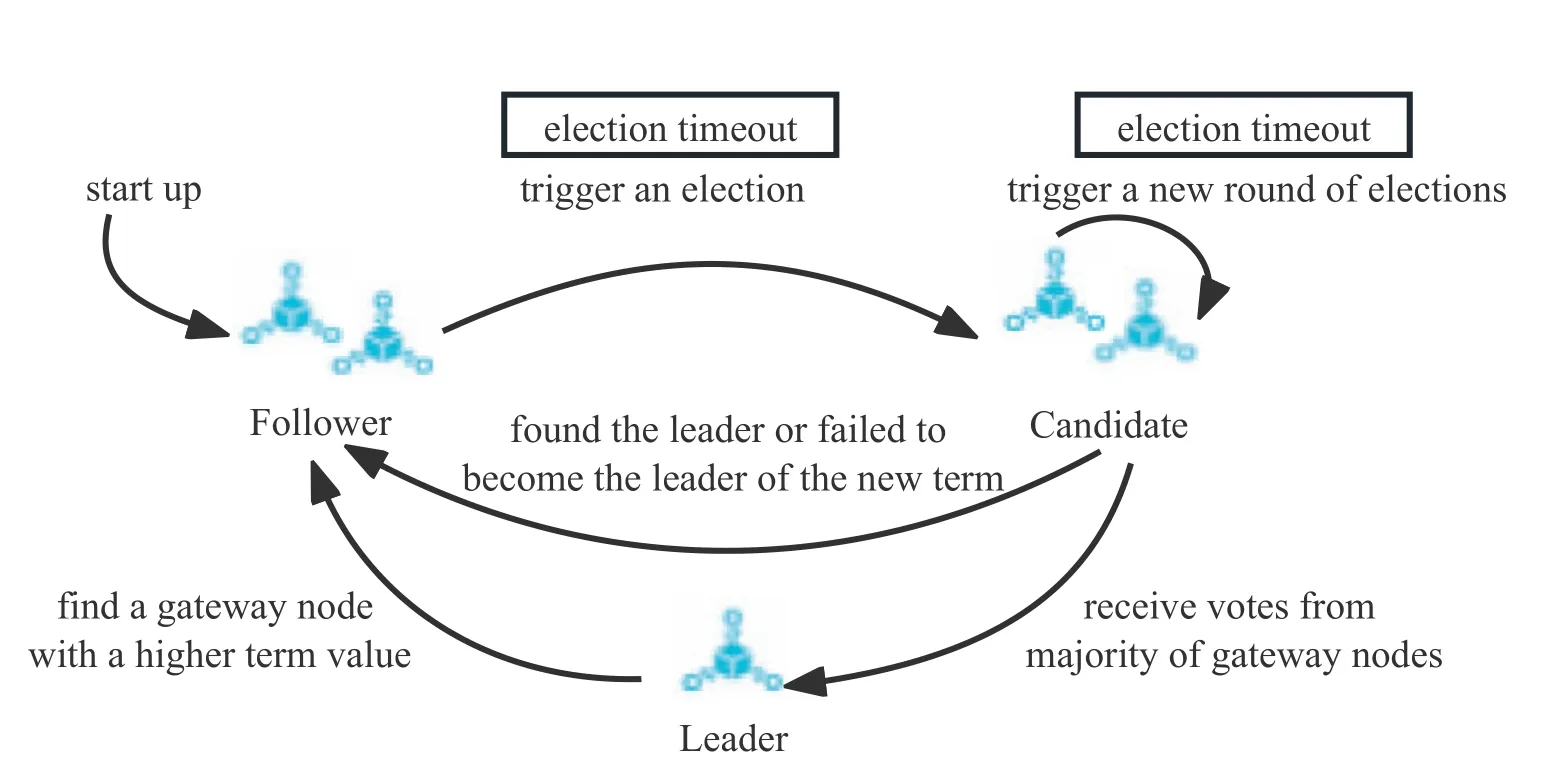
Figure 6. Gateways consensus algorithm flow.
· Candidate receives the votes ofnodes,changes from Candidate to Leader,and sends heartBeat to other nodes to keep the Leader running normally.
· During this period,if a voting request sent by other nodes is received,if the Term of the node is large,the current node will become a follower,otherwise the request will be rejected by keeping the Candidate.
· When the Election timeout occurs,the Term is incremented and the election is re-initiated.
V.SECURITY AND PERFORMANCE
5.1 Security Analysis
In this section we will evaluate our proposed blockchain architecture.During cross-chain transactions by users/devices,the system may encounter malicious attacks that attempt to obtain on-chain data and user/device information.It is proved that our blockchain interoperability architecture is wellsecured.
· Each user/device has a unique Mac address as an identifier.When a user/device registers in the main chain for the first time,its Mac address and related information are bound to its identifier that already exists under the blockchain network.In other words,a user/device can have only one unique identity under a blockchain network.Due to the decentralized nature of the blockchain,the user/device information of the main and side chains is not subject to attack by malicious nodes.
· Strong security authentication of primary and secondary tokens.The communication between the user/device and the main chain in the process of primary token generation effectively avoids manin-the-middle attacks to obtain token information through timestamps.Source chain gateway A,which verifies the user/device identity and ensures the legitimacy of the user/device identity.When the cross-chain transaction passes through the destination chain gateway B,the user/device identity is verified by the generated secondary token to ensure the legitimacy of the cross-chain transaction reaching the other party’s local blockchain network.
· Privacy and trustworthiness.During the authentication process,the user/device’s address,hash value,and other information are stored on the blockchain,which protects its privacy.At the same time,the index of the user/device contains its hash value,preventing tampering by semitrusted data servers and protecting its trustworthiness and integrity.
· DoS attack on single point gateway.When an attacker sends a large number of requests to gatewayG1,ifG1fails,other nodes in the gateway can operate normally at this time.This prevents the evil behavior of a single gateway.
· All gateways are subject to DDoS attack.Assume that the maximum number of requests that can cause the gateway to fail is r,all gateways will share the traffic,the number of gateways is n,corresponding to the number of attacks on each gateway is r/n,the distributed structure greatly reduces the degree of attack on the gateway.
We have compared the proposed scheme with existing blockchain interoperability schemes.The results are shown in Table 1.Although scheme[31]achieves decentralization,it does not consider cross-chain security and cannot perform interoperability between heterogeneous blockchains.Schemes[2]and[32]target interoperability between heterogeneous chains,both through a third party trusted by both parties to the transaction as an intermediary.Dos/DDoS attacks exist in all three scenarios above.
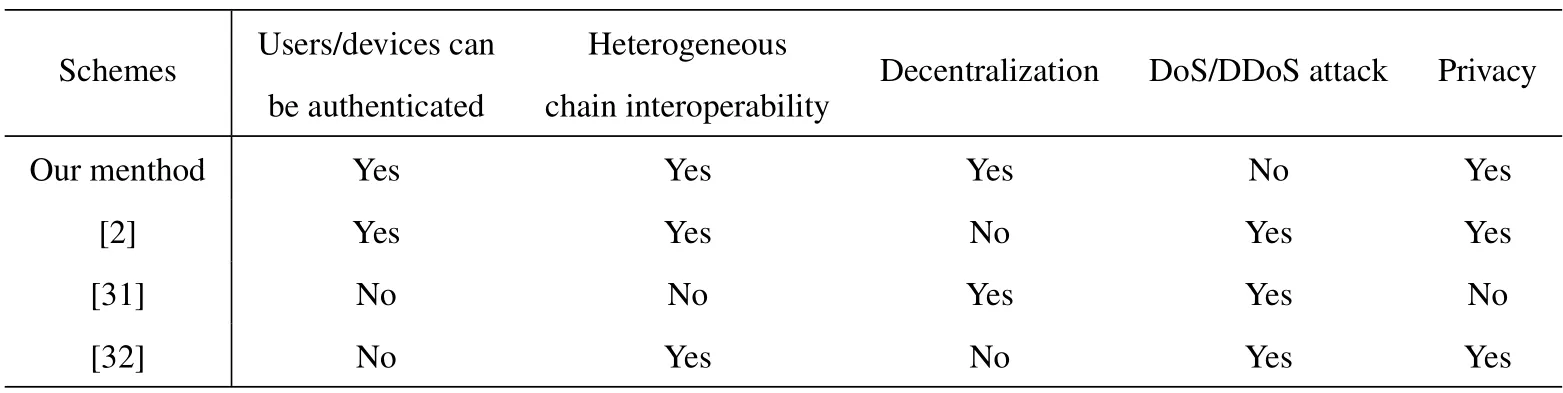
Table 1. Comparison of different schemes.
5.2 Simulation Results and Analysis
In order to test the performance of the cross-chain interoperability mechanism based on heterogeneous chains proposed in this paper,a cross-chain experimental environment is built in this section.The hardware environment for this experiment is as follows: the processor is Intel(R) Core(TM) i7-1165G7@ 2.80GHZ with 2 cores,memory is 8G,the operating system is Ubuntu 16.04,and hard disk is SSD(M2)200GB.
During the performance evaluation,test the speed of the on-chain operation.For example,user authentication information is uploaded to the chain,and user transaction information is uploaded to the chain.Test the speed of operations off-chain.For example,protocol conversion,authentication information encryptiondecryption operations,etc.Blockchain read/write speed is not only related to hardware but also to the number of nodes in the blockchain network.In this paper,we use docker as the container of nodes and deploy each container to a laptop.The corresponding configuration is shown in Table 2,including the nodes of Fabric,Ethereum,and their respective gateway nodes,and a main chain.
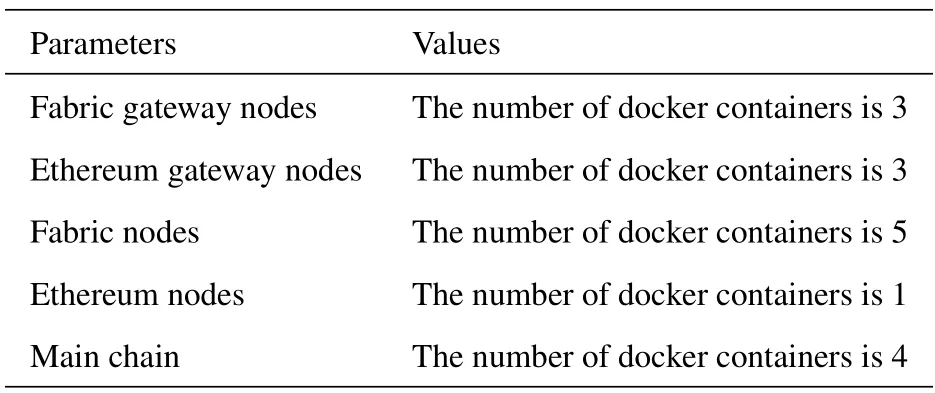
Table 2. Con g of machines.
5.2.1 Storage Overhead
In the IoT environment,the number of users/devices is huge and the stored information is exploding.For blockchain,the storage overhead of users/devices is an important concern.We analyze the variation of storage capacity of the KDC node in the main chain with the increase of authentication information.As shown in Figure 7,the difference between the storage capacity is small when user information is compared by algorithms with different lengths of AES-128,192,and 256.The storage overhead of the main chain is also only about 2MB when the authentication information is 2500.
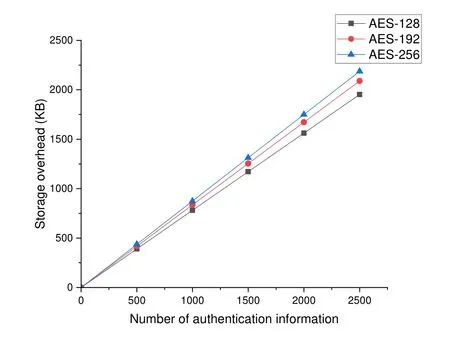
Figure 7. Number of authentication information.
The variation of the storage capacity of the main chain nodes with the number of IoT users is shown in Figure 8.It can be seen that the storage capacity of the number of users grows almost linearly.
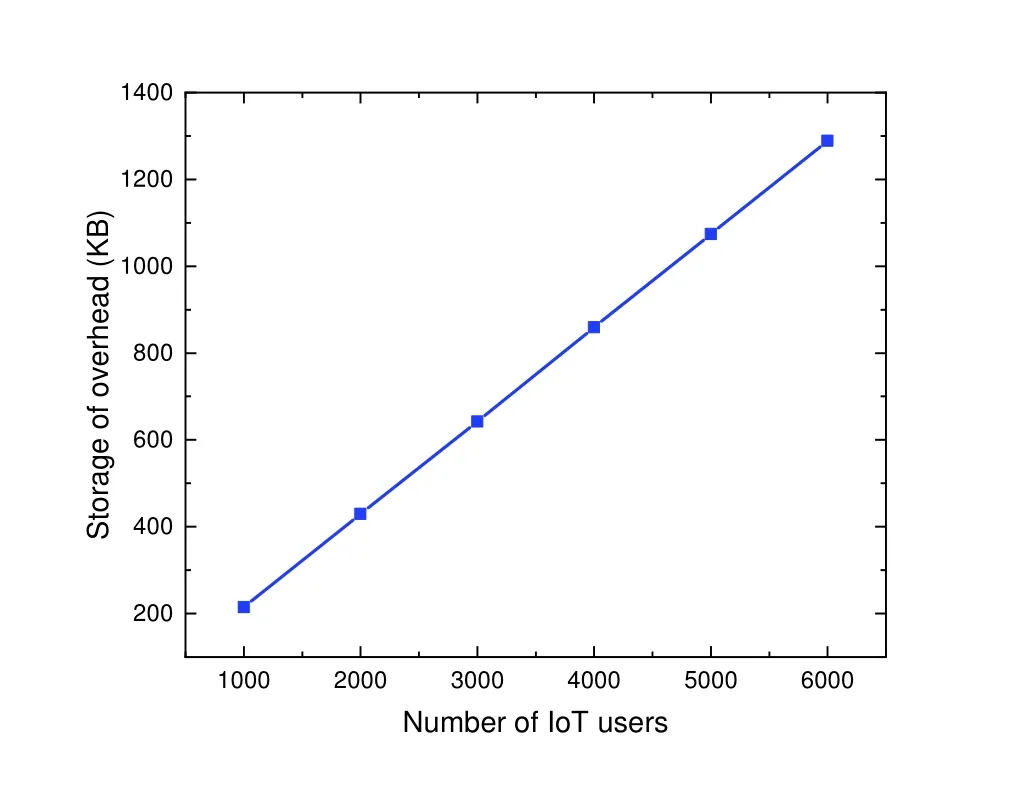
Figure 8. Number of IoT users.
5.2.2 Throughout
This section analyzes the system’s cross-chain authentication and cross-chain full-process operation throughput.The number of cross-chain interoperation requests sent each time is taken as the independent variable,and the number of cross-chain interoperation requests that the system can handle per second is taken as the dependent variable,considering the overhead of the cross-chain gateway,main chain,and side chain.
Cross-chain authentication request throughput test.For cross-chain authentication requests,the experimental process is to test the peak throughput of the system by gradually increasing the number of crosschain authentication requests sent.Side chain A calls the smart contract to initiate a user authentication request,then calls the corresponding plug-in to apply for the user’s primary token to the main chain,the main chain authenticates the request and stores the transaction information on the chain,and finally returns the user’s primary token to the user.The experimental results are shown in Figure 9.
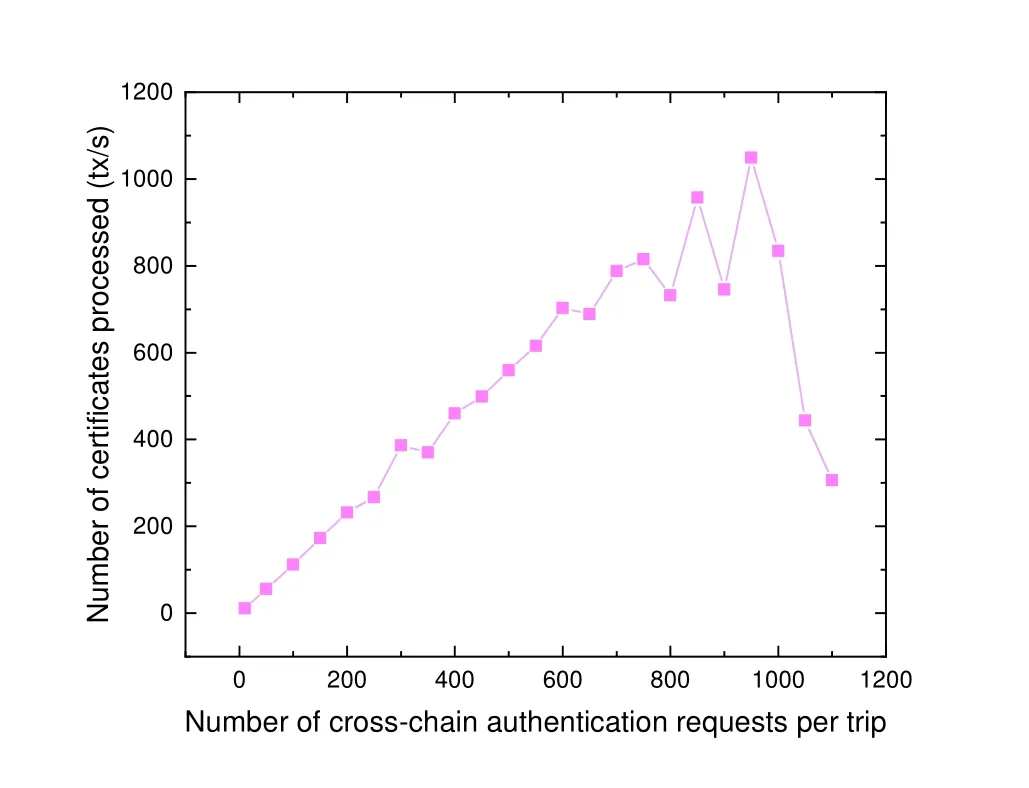
Figure 9. Cross-chain authentication throughput.
It can be seen that when the number of concurrent authentication requests increases from 10 to 950,the peak performance gradually increases from 11 TPS to 1049 TPS;the peak decreases from 950 concurrent requests due to the BFT consensus algorithm used in the main chain transaction test,which leads to a large performance overhead.
Cross-chain whole-process operation throughput test.The whole process of trans-chain operation requests includes trans-chain authentication requests and trans-chain transaction requests.The experimental process is to test the peak throughput of the system by gradually increasing the number of trans-chain transaction requests.After obtaining the primary token from the user on chain A,the cross-chain transaction smart contract is invoked to initiate cross-chain interoperability events.The experimental results are shown in Figure 10.
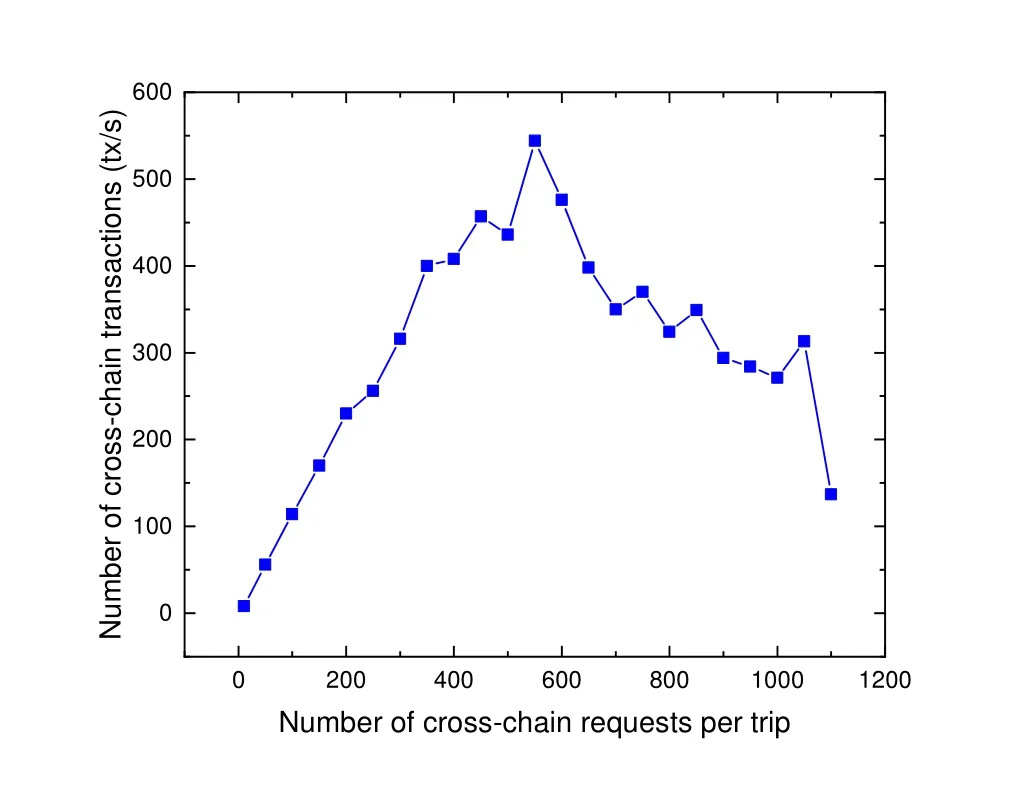
Figure 10. Cross-chain full operation throughput.
When the number of concurrent authentication requests goes from 10 to 550,the peak performance gradually increases from 8 TPS to 544 TPS;starting from 550 concurrent requests,the peak gradually decreases and the overall performance decreases significantly compared to the former,which is due to the fact that the upper chain needs to participate in consensus when the main chain verifies the legitimacy of cross-chain transactions to side chain A.In addition,users of sidechain A decrease one asset,and accordingly,users of sidechain B increase one asset.In this process,sidechains A and B use Kafka and PoS consensus algorithms,respectively,to process this transaction.As a result,it leads to a significant performance degradation.
VI.CONCLUSION
There is an urgent need for interaction between more and more IoT users/devices.Achieving the effectiveness and security of interoperability between different systems is very important for asset transfer,information exchange,and application collaboration in blockchain platforms.In this paper,we propose a secure and trustworthy interoperable system based on heterogeneous chains to realize interoperability between different blockchain systems in the IoT environment.The system consists of four main entities: main chain,side chain,gateway,and user.The process of user-initiated cross-chain requests is effectively performed with secure and trusted interoperability authentication.Simulation experiments show that crosschain interoperation is feasible and can improve the security and trustworthiness of the heterogeneous chain system.
ACKNOWLEDGEMENT
The research work is supported by the Shandong Provincial Key Research and Development Program(2021CXGC010107).
- China Communications的其它文章
- PowerDetector: Malicious PowerShell Script Family Classification Based on Multi-Modal Semantic Fusion and Deep Learning
- A Rigorous Analysis of Vehicle-to-Vehicle Range Performance in a Rural Channel Propagation Scenario as a Function of Antenna Type and Location via Simulation and Field Trails
- Intelligent Edge Network Routing Architecture with Blockchain for the IoT
- Privacy-Preserving Deep Learning on Big Data in Cloud
- Dynamic Task Offloading for Digital Twin-Empowered Mobile Edge Computing via Deep Reinforcement Learning
- Resource Trading and Miner Competition in Wireless Blockchain Networks with Edge Computing

