Game Theoretical Secure Wireless Communication for UAV-assisted Vehicular Internet of Things
Bo Liu,Zhou Su2,,*,Qichao Xu
1 School of Mechatronic Engineering and Automation,Shanghai University,Shanghai,China
2 School of Cyber Security,Xi’an Jiaotong University,Xi’an 710049,China
Abstract: With the ever-expanding applications of vehicles and the development of wireless communication technology,the burgeoning unmanned aerial vehicle (UAV) assisted vehicular internet of things(UVIoTs)has emerged,where the ground vehicles can experience more efficient wireless services by employing UAVs as a temporary mobile base station.However,due to the diversity of UAVs,there exist UAVs such as jammers to degenerate the performance of wireless communication between the normal UAVs and vehicles.To solve above the problem,in this paper,we propose a game based secure data transmission scheme in UVIoTs.Specifically,we exploit the offensive and defensive game to model the interactions between the normal UAVs and jammers.Here,the strategy of the normal UAV is to determine whether to transmit data,while that of the jammer is whether to interfere.We then formulate two optimization problems,i.e.,maximizing the both utilities of UAVs and jammers.Afterwards,we exploit the backward induction method to analyze the proposed countermeasures and finally solve the optimal solution.Lastly,the simulation results show that the proposed scheme can improve the wireless communication performance under the attacks of jammers compared with conventional schemes.
Keywords: UAV-assisted vehicular internet of things(UVIoTs); jammers; offensive and defensive game;wireless transmission
I.INTRODUCTION
Recently,with the popularization of vehicles and the continuous development of wireless communication technology [1–5],the promising vehicular internet of things (VIoTs) has emerged,providing convenient,safe and comfortable driving services for mobile users.Especially,in VIoTs,mobile users can utilize the wireless communication technologies (e.g.,LTE,DSRC,5G) on vehicles to acquire desired data from the Internet,so as to enjoy the multimedia contents or make social interactions with each other.According to [6],by 2022,the global traffic will reach 77 exabytes(77×1018bits)per month,and more than 50%is generated from mobile multimedia streaming.Due to the limitation of resources,it is not enough to support a good deal of data demands,and the existing wireless network structure is insufficient to support such a large amount of mobile traffic[7].Therefore,it is pressing to improve the throughput of VIoTs to satisfy mobile user’s diverse wireless communication demands.
In the field of wireless communication,unmanned aerial vehicles (UAVs) have great potential,which is considered as the most effective way to change performance of VIoTs[8,9].It is envisioned that UAVs will become part of the fifth generation(5G)wireless network[10].Especially,UAV employed as a mobile communication platform in the air,has received extensive focuses [11–13].On the one hand,UAV can be used as a mobile relay to connect wireless equipment on the ground,broadening network coverage[14,15].On the other hand,UAV can be used as a mobile aerial base stations to provide reliable upstream and downstream communication for ground users and increase the capacity of wireless networks [16].As an aerial base station,UAV has a series of advantages compared with traditional base stations,including flexible networking,rapid movement,simplicity and efficiency.Specifically,UAV to ground vehicles (A2G) communication[17]is conducive to improve the communication quality.Moreover,due to its flexible position,UAV can improve the reliable connection for ground vehicles with lower transmission power.
With the assistance of UAVs,ground vehicles can experience more efficient wireless services by employing UAVs as temporary mobile base stations[18].However,in practice,jammers exist.Therefore,when UAV transmits data to ground vehicles,jammers will be used to interfere [19].In this paper,offensive and defensive game is used to model the relationship between jammers and UAVs,so as to finally achieve the utility maximization.The introduction of UAVs in VIoTs also raises up following challenges.
1) Due to the diversity of UAVs deployed as flying base stations [20–22],some malicious UAVs exist as jammers to attack the wireless link between normal UAVs and vehicles,giving rise to the degeneration of wireless communication performance.
2) Owing to the difference of vehicles’ wireless communication demands,the uniform or fixed wireless service mode of UAVs is inefficient.So,UAVs should flexibly provide wireless communication service for every vehicles based on their demands.However,There will be co-channel interference between different UAVs during transmission.
To resolve above challenges,in this paper,the jammers attack problem in the transmission process of UAVs is analyzed,and an offensive and defensive game based model for interactions between normal UAVs and jammers is proposed.In the process of wireless transmission when normal UAV acts as a temporary base station.Due to the interference of jammer and the co-channel interference of normal UAV,an algorithm of offensive and defensive game is proposed to analyze the above factors.Based on the target to maximize the utilities of both UAVs and jammers,an optimization problem is then formulated.Finally,an optimal policy set is searched with the game analysis,under which both normal UAVs and jammers can simultaneously achieve the optimal utility.The contributions in this paper are three-fold as follows:
• This paper proposes an offensive and defensive game based secure wireless communication framework.In UAVs network,considering jammer,the game theory is applied to UAVs communication,and the utility model is designed.
• In the process of UVIoTs,mutual interference factors of the channel between UAVs are taken into account,and the benefits of both sides are quantified.Besides,the utility matrix of different attacking and defending strategies is further calculated.
• Based on offensive and defensive game theory[23–25],this paper proposes an optimal strategies of offensive and defensive game set,where both parties through certain probability to choose their own strategy for making the other party lose the idea of changing strategy.
The rest of this article follows.The related works are reviewed in section II.In section III,we present the system model.In section IV,the problem analysis is given.In section V,the game analysis of offense and defense between UAV and jammer is carried out,and the optimal strategy set of both sides is finally obtained.In section VI,the effectiveness of the proposed scheme is verified by simulation and in section VII we give the conclusion.
II.RELATED WORK
In this section,we retrospect relevant work,including UAVs communication networks,and countermeasures for jammer in wireless networks.
2.1 UAVs in Wireless Communication Networks
In recent years,the rapid development of the application of UAV,coupled with the inherent mobility and moderate height of UAV,makes UAV widely used in the field of communication due to its low cost,strong survivability and good maneuver ability.UAV can be used for both civil and military purposes.In the civil field,UAV can be used for mapping,disater monitoring,pesticide spraying,etc.In the military field,UAV can be used asreconnaissance plane,asreconnaissance and surveillance on the battlefield,etc.Wuet al.[26]propose a wireless power Internet of Things framework,which is supported by multiple UAVs.Some UAVs can be used as power bank to electricize Internet of Things devices.Zhanget al.[27]study a relay communication system,which can obtain the best place of UAV and solve the problem of maximizing the average accessibility rate by linear search with the aid of cached UAV.Xieet al.[28]research a communication network for wire-free power supply.It is a dual-user interference channel,in which two UAVs are mainly used to charge and collect information from low-power IoT devices on the ground.Mozaffariet al.[29]integrating a UAV user with a cellular connection and a UAV base station and introduces a new definition called a three-dimensional network.Liet al.[30]consider a relay UAV in wireless networks for two-way communication between a ground base station and a set of remote user devices(UE).Zhaoet al.[31]consider deploying the UAV as a relay node to assists in forwarding the computing tasks to the servers.Linet al.[32]consider UAVs as relay nodes and proposed the cooperative communication of multiple UAVs based on the implementation of the ground to assist vehicles to alleviate some problems that could not be avoided.However,these works have not taken full consideration of the interference of malicious UAVs.
2.2 Countermeasures for Jammers in Wireless Networks
Wireless communication technology has been widely used in various industries.However,due to various external factors,it will be subject to a lot of interference in the practical application,hence the interference becomes a big problem in the field of wireless communication.In addition to some unintentional interference in the communication process of network nodes,in reality,there are also some malicious interference sources.In this subsection,a serious of countermeasures for jammer have been studied in wireless networks.Keet al.[33]aim at the interfered wireless positioning system,an optimized power distribution strategy is proposed to improve its positioning performance,Moreover,the power distribution relationship will directly affect the accuracy of positioning and network life.Xuet al.[34]consider that a passive eavesdropper is used in a fading channel,it is proposed to use cooperation between multi-cooperative jammers to reduce the security loss which is caused by the relationship between the eavesdropping channel and the main channel.Liet al.[35]put forward a multi-user upline network which consist of a base station (BS),some users and a pirate listener.In this network,information is transmitted between the user and the base station,and the eavesdropper eavesdrops on the transmission between the two.Within a limited space,Tanget al.[36]consider the friendly interference between UEDs and a legal terrestrial link.Wanget al.[37]use an alternative N-antenna coadjutant jammer to study the security freedom of 2-user multipleinput multiple-output MIMO channel.In a wireless cellular network with mixed base stations,Chuet al.[38]investigate a secure wireless-powered device-todevice(D2D)communication network in the presence of multiple eavesdroppers.Wuet al.[39]consider the possibility of a wiretapping attack,considering the possibility of leaking private data while uninstalling the task.However,in these works,how to utilize the game theory to resist the jammer is not fully studied.
III.SYSTEM MODEL
In this section,first of all,we introduce the network model,then introduce the movement model,and finally elaborate the communication model of UAV.
3.1 Network Model
As shown in figure 1,the UAV communication network contains a jammer,a swarm of UAVs,and some vehicles.As the interference range of vehicles on the ground is small,the existence of malicious UAVs is mainly focused on in this paper.Compared with ground vehicles,malicious UAVs usually have fast speeds and cover wide ranges.
UAVs:We consider an area where UAVs are used to provide communications services.In practice,we can use UAVs as temporary base stations while flying to other areas to serve vehicles.Multiple UAVs can set up communication links and exchange information directly through peer-to-peer communication or information relay to inform other UAVs of their own and the current state of the network.The set of UAVs in the network is denoted asm={1,2...M}.UAVs are used to transmit data to vehicles on the ground.The UAVs and vehicles communicate with the vehicle via A2G link.Downlink communication is adopted between UAV and vehicle,and 802.11P communication protocol is adopted for all vehicles and UAV.UAVs act as aerial base stations to transmit data to vehicles,and each moving along a predetermined path during transmission.
Jammer:When UAV and vehicles are transmitting data,a malicious jammer is to jam the downlink to interfere with the data transmission between UAV and vehicles.It mainly affects the quality of data received by vehicles by sending disturbing data to them [40].Letj={1,2...J}denote the set of jammers in the network.The jammer is responsible for interfering with downlink and thus affecting data quality.
Vehicles:Vehicles receive data from UAVs and the jammer.Different UAVs interact with each other in the process of transmitting data to vehicles.In this article,we assume that each vehicle has access to data transmitted by UAVs and jammers.Letv={1,2,...V}denote the set of ground vehicles in the network.
3.2 Motion Model
UAV: A three-dimensional Cartesian coordinate system of the above three entity positions is applied.In the same way,we consider a time slot scene model to model the mobility of the UAVm.The position of the UAVmin the time period isqm(t):qm(t) =[xm(t),ym(t),hm(t)],where[xm(t),ym(t)]is the momentary horizontal frame of reference of UAVmin time periodt,hm(t) is the height of UAVmin time periodt.
Letvm(t)represent the speed of the UAVmin the time periodt.In the next time periodt+1,the position of UAVmisqm(t+1)=qm(t)+vm(t)∗ωm(t),whereωm(t)denotes the vector with respect totwhich is direction of the UAVm’s trajectory in time slott.||ωm(t)|| ≤Δt,Δtrepresents the time interval between two time slots.vm(t)≤vmax,vmaxrepresents the maximum speed a UAV can reach.
Vehicles: Within a small time slott,the location of ground vehiclevis (xv,yv,0).Here,we calculate the distancedm,v(t) between UAVmand vehiclev:dm,v(t) =
Jammer: The jammer flies at a fixed heightH,at which point the jammer can operate normally.The jammer’s initial position in the time periodtisqj(t)=[xj(t),yj(t),H].Letvj(t) represent the speed of the jammer in the time periodt.At the next time periodt+ 1,the position of the jammer isqj(t+1) =qj(t) +vj(t)∗ωj(t).Similarly,it is also a vector with respect totwhich is in the direction of the jammer’s trajectory at timet.||ωj(t)|| ≤Δt,Δtrepresents the time interval between two time slots.vj(t)≤vςmax.vςmaxdenotes the maximum speed a jammer can reach.At this point,the distance between jammerjand vehiclevisdj,v(t) =
3.3 Communication Model
Within time periodt,the location of the vehicles can be obtained by GPS.In this paper,a quasi-static packet fading channel model[41,42]is adopted,and the UAVto-vehicle and jammer to vehicle wireless channels are mainly LoS transmission links.In the above case,the channel depends on distance,and the channel does not change at each fading speed.In the time periodt,the channel gainαm,v(t)of UAVmand vehiclevcan be expressed as:
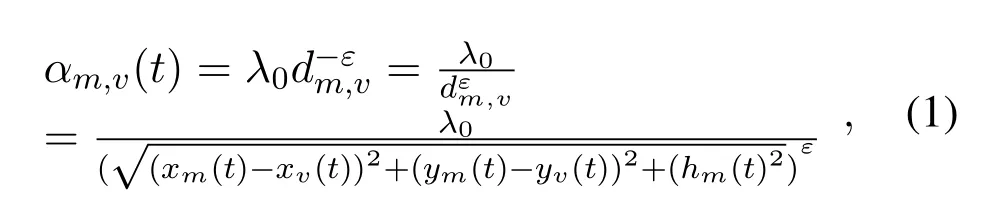
whereλ0is the channel power gain,which is related to the reference distance.dm,vis the distance between UAVmand vehiclev.εis greater than 1 which is the path loss index.Similarly,the channel gain of jammerjand vehiclevcan also be expressed as:

wheredj,vdenotes the distance between jammerjand vehiclev.
The transmission power transmitted by the UAVmto each vehicle is denoted aspm,m ∈{1,2...M}.We denoted the transmission power of the jammerjispj,j ∈{1,2...J}.The power of background noise is denoted asN0.As communication link jamming will occur between different UAVs,for a vehiclev,it should not only bear the communication link jamming of other UAVs,but also bear the malicious jamming signal of jammer,the SINR of vehiclevin time periodtiswhereαm,v(t)represents the channel gain of the transmission link of UAVmto vehiclev.βj,v(t) represents the jamming channel gain of jammerjto vehiclev.µ−{−m,v}(t)represents the sum of other normal UAVs in the area that interfere with vehiclevduring transmission.It is denoted as:
wherepm′denotes the power of other UAVs anddm′,vdenotes the distance between other UAVs and vehiclev.
IV.PROBLEM DESCRIPTION
In this article,due to the existence of jammers,UAVs may be interfered by jammers when transmitting data to vehicles.The purpose of this paper is to analyze the optimal transmission strategy of UAV in the presence of jammer.The transmission rate between the vehicle and the jammer and the UAV are analyzed in the offensive and defensive game,and finally how the UAV can adapt the transmission strategy to obtain efficient information transmission when the jammer exists in the article.
In order to obtain the Nash equilibrium between UAVs and jammers,we use the offensive and defensive game to analyze and model.In a local area,we considerMUAVs,Vvehicles,and one jammer.To transmit data to vehicles,a UAV aims to transmit the largest amount of data to ground vehicles in time periodt,and the jammer will also interfere with the downlink and affect the quality of the data.We can analyze the offense and defense game and treat the jammer as an attack and regarding the UAV as the defensive side,find its Nash equilibrium based on the utility function of both offensive and defensive parties.
When an jammer is sending interference information to the vehicle,according to the Shannon theorem,the data transmission rate received by vehiclevat this time isTγv(B) =Blog2(1 +whereBrepresents the allocated spectrum bandwidth.
When the jammer does not interfere,andwjis 0 at this time,thenβj,v(t) is 0,and the data transmission rate received by vehiclevisT′γv(B) =Blog2(1+
When the UAV transmits data to vehicles,the corresponding transmission cost cannot be ignored.We usecmto represent the transmission cost per unit power of the UAV.When the transmitted power magnitude ispm,the total cost transmitted by UAVmisTcm=pmcm.Similarly,the jammer has a corresponding transmission cost.We usecjto represent the transmission cost per unit power of the jammerj.When the transmitted power magnitude ispj,the total transmission cost of the jammerjisTcj=cjpj.
Based on the offensive and defensive game,we regard the vehicle and the UAV as the defender,and the malicious jammer as the attacker.At this time,the defender has two strategies,and the attacker also has two strategies.
Defender:
Stated1: No data transmission between UAVs and vehicles.
Stated2: Data transmission between UAVs and vehicles.
We utilizeδto control whether the UAV transmits.
Attacker:
Statea1: The jammer does not interfere with data
Statea2: The jammer does interfere with data.
We useηto control whether the jammer interferes.
In the article,Ω is used to represent the set of strategy and utility functions of UAVs and jammers,Ω ={M,J,{pm}m∈M,{pj}j∈J,{um}m∈M,{uj}j∈J}.The strategy set of UAVmcan be expressed as:

Correspondingly,the strategy set of jammerjcan be expressed as:

Among them,{pm}m∈Mand{pj}j∈Jrepresent the strategy set of UAVmand jammerjrespectively,and{um}m∈Mand{uj}j∈Jrepresent the utility function of UAVmand jammerjrespectively.
In this paper,we regard the offense and defense game used in this paper as a zero-sum game.The attacker and defender restrict each other by obtaining higher gains.At this point,the utility function of UAV is not only related to its own benefits and costs,but also related to the cost of jammer.
So the utility function of UAVmis:
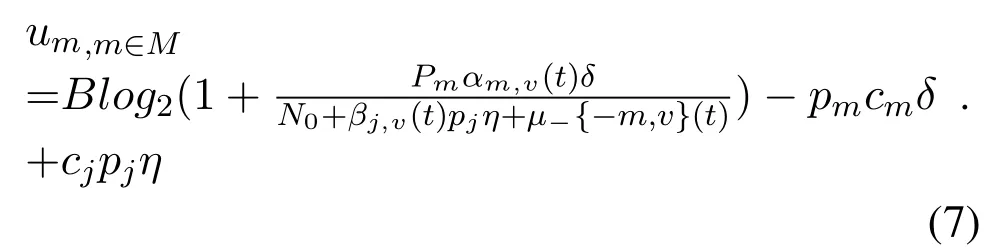
The utility function of jammerjis:
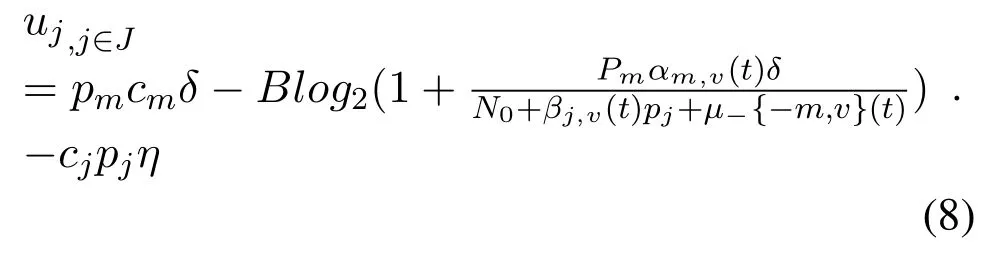
The utility function of the UAV is the data transmission rate between the UAV and the vehicle minus the data transmission cost between the UAV and the vehicle and add the cost of the jammer to interfere with the data transmission.Since the game is a zero-sum game,the loss of one party is the loss of the other party.Therefore,the utility function of the UAV and the jammer are the opposite,the sum of the utility functions of the jammer and the jammer is equal to 0.In this paper,UAV and jammer are opposite party,and both sides of any party policy change will affect their utility,so we use a zero-sum game to simulate the benefits of both,the characteristic of zero-sum game is that one party’s gain is the other party’s loss,only in this way can more reflect the extent of the opposition.Hence the zero-sum game can better reflect the antagonism between UAV and jammer,only in this way can both sides maximize their utility.
Therefore,the utility function of both sides when both sides know that one side chooses to determine a certain strategy and the other side also determines a certain strategy,so as to obtain the set of strategies that both sides want to choose.
V.GAME ANALYSIS OF OFFENSE AND DEFENSE
From section IV,we learned that UAV has two strategies to choose and jammer has two strategies to choose.The two sides have formed four corresponding strategies.The difference of these four strategies lies in that under each strategy,UAV and jammer do not choose exactly the same countermeasures.In the game analysis,we mainly consider some UAVs,one jammer and multiple vehicles.
5.1 The Utility Function Matrix for Both Offense and Defense
Case 1.When the UAV does not transmit data and the jammer does not interfere,then the utility function ofUAV m is: um,m∈M= 0Accordingly,the utility function of jammer j is uj,j∈J=0.
Case 2.The UAV carries out data transmission,but the jammer does not interfere.In this case,the benefits of the UAV are the transmission rate received by vehicles.The utility function of UAV m is:
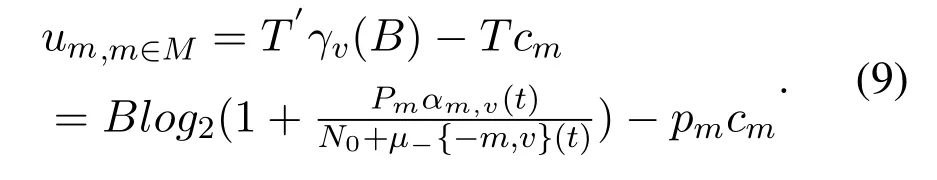
And the benefit of any party in the zero-sum game is the loss of the other party,so the utility function of jammer j correspondingly is:
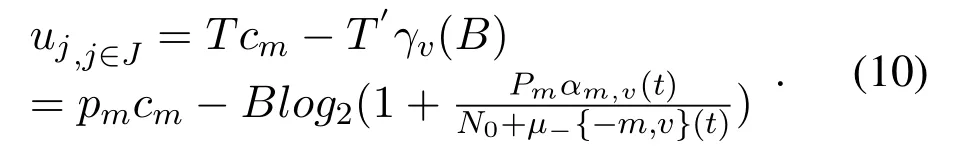
Case 3.The UAV does not transmit data,but the jammer does.In this case,the utility function of UAV m is um,m∈M=Tcj=cjpj.
According to the nature of the zero-sum game,the utility function of jammer j is uj,j∈J=−Tcj=−cjpj
Case 4.The UAV carries out data transmission,and the jammer also carries out interference.The utility function of UAV m is:
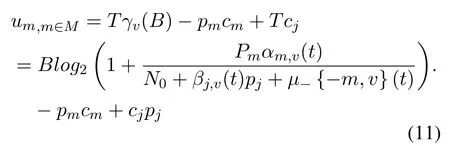
And the utility function of jammer j is:
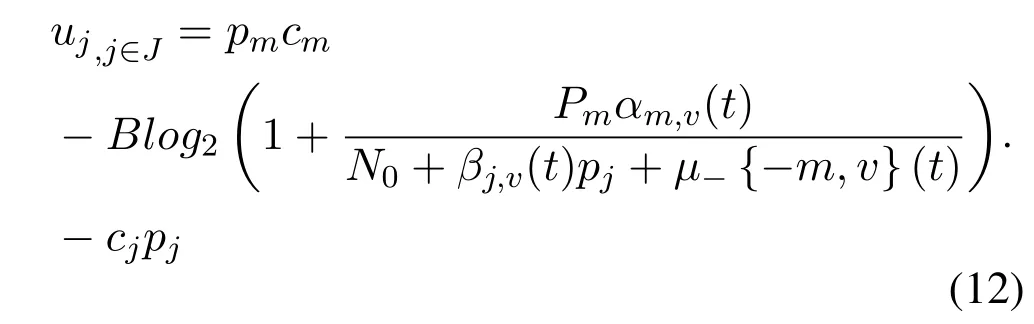
We assume that the utility of the data transmission rate obtained by the vehicle is greater than the transmission cost of the UAV,and then the UAV has a reason to carry out transmission,which is expressed by the formula as followsTγv(B)>Tcm.
Jammers are attackers and UAVs and vehicles are defenders.Table 1 shows the strategic matrix of the attack and defense game:
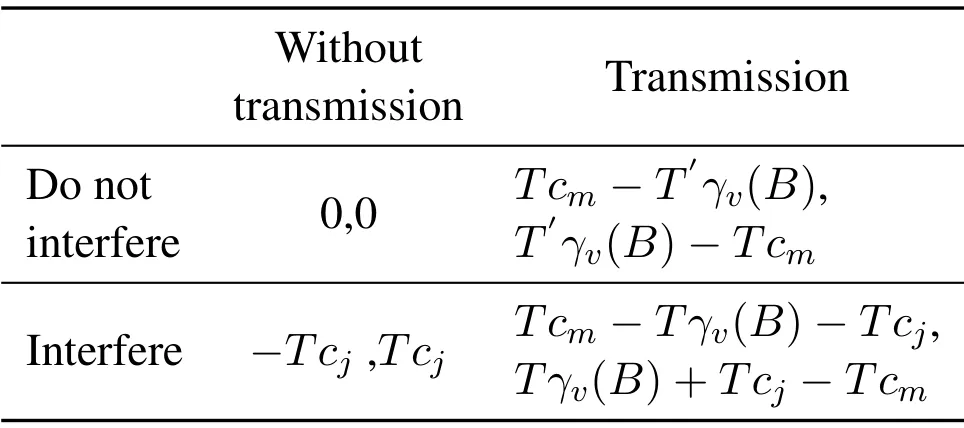
Table 1.Utility matrix under different strategies of the attacking side and the defending side.
Where rows represents the jammer’s strategy,and the columns represents the UAV’s strategy.
5.2 Mixed Nash Equilibrium Analysis
From the previous section,we take the offensive and defensive game as a zero-sum game,and we know from the previous section has several strategies of the attacker and defender.This paper assumes that players in the game are rational and rational player is to consider the cost.In the case of the same payoffs,the player will choose a low cost way of attack or defend.Therefore,both the attacker and the defender want to choose the appropriate strategy in this game to make their own utility optimal.
No pure Nash equilibrium strategy exists in the proposed game model,since each party has a strategy that makes its own side more profitable.For both parties,no one decides the effective strategy,because we take the mixed strategy Nash equilibrium (MSNE) as our solution.
Definition 1.As for the security game,a hybrid strategy Nash equilibrium is the probability distribution P over the pure strategy set S of any participant,i.e.,
For a jammer,we denote the probability that it does not interfere aspa0,so,the probability that it interferes ispa1.Again,we denote the probability that it does not transmit aspd0,the probability of its transmission is denoted bypd1.
According to the definition of MSNE,when the expected returns of UAVs and jammers are the same,players in the game become indifferent to the choice of strategy.Therefore,in the proposed game,when the expected utility ofa0anda1of the attacking party is equal,and the expected utility ofd0andd1of the defending party is equal,the mixed strategy makes the game parties under the two strategies not significant,i.e.,EU(pa0)=EU(pa1)andEU(pd0)=EU(pd1).
Based on the above description,we combine Table 1 to obtain Table 2:
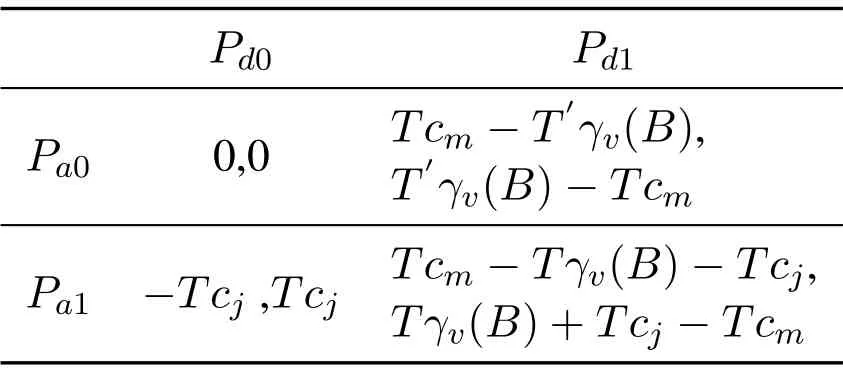
Table 2.Utility matrix under different strategy choices of the attacking side and the defending side.
In order to calculate the probability of the jammer as the attacker,the expected function of the mixed strategy is denoted by:
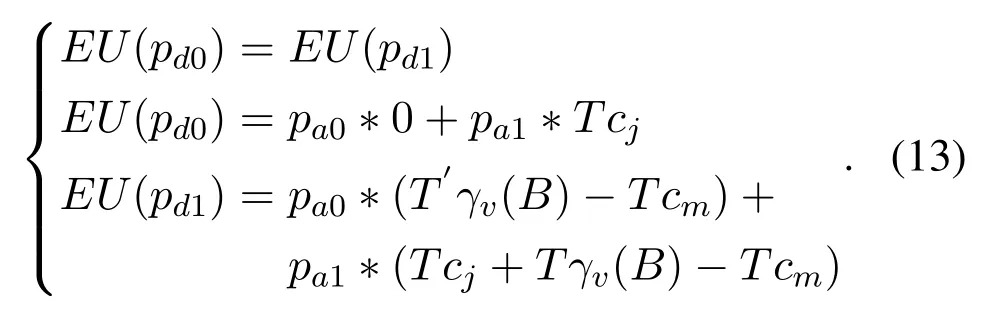
Similarly,the expected utility function of the mixed strategy in obtaining the probability of defender is denoted by:
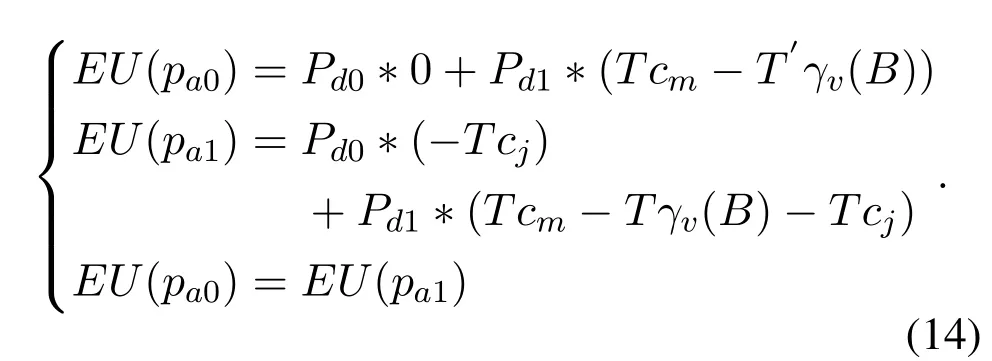
From the above formulas,The equilibrium result is obtained by making the expectation equal and the sum of the probabilities equal to 1.we can calculate the probability:
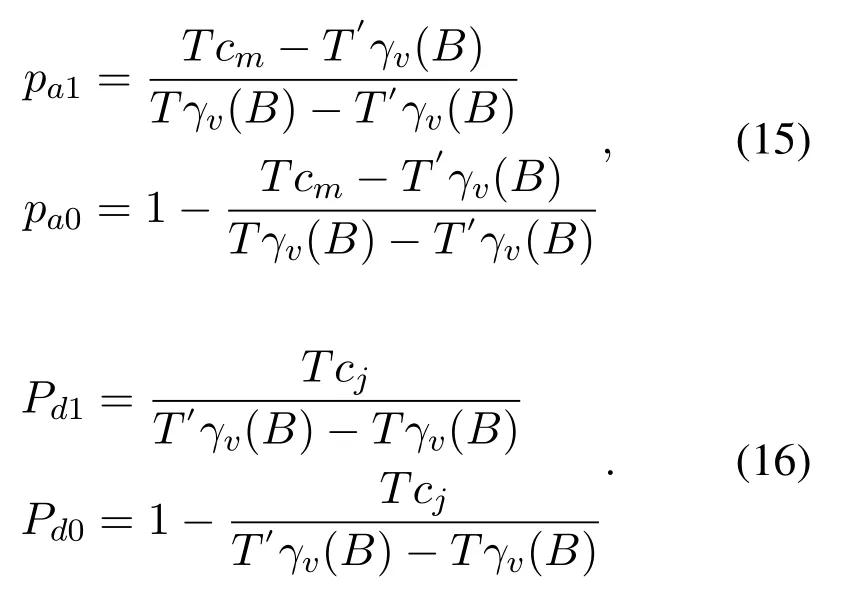
Based on the above calculated probability,we know that in the process of repeated game,both sides will eventually reach a mixed Nash equilibrium,namely the probability of formula.In this probability set,the utility of both parties can reach an optimal situation at the same time,which means that in this probability set,neither party will change the strategy to break the balance.
VI.PERFORMANCE EVALUATIONS
This section is mainly about the use of MATLAB software to evaluate the performance of the proposed scheme,we first introduced the simulation scene,as well as some parameters,then according to these parameters given the simulation results,and finally analyzed.
6.1 Simulation Setup
In the simulation,we consider a UAV-assisted VIoTs consisting of a jammer,30 vehicles.The number of UAVs follows the uniform distribution in[10,50].The value of the power size and the transmission cost per unit of power for UAV data transmission are 6Mb and 12,respectively.In addition,the power size of the jammer interference data is between 5 Mb and 9 Mb,and the price value per data size is between 4 and 8.Each normal UAV and jammer has a fixed horizontal distance of 8 meters from the vehicle.The height of UAV and vehicles is between 2 m and 7 m,while the height of jammer is fixed at 2 m,and the channel power gain is 0.009.Based on the above conditions,the expected return of the optimal strategy set obtained by the proposed method is greater than that obtained by random probability.
6.2 Simulation Results
In this subsection,we first evaluate the change in the optimal decision probability of interference and noninterference in jammers as the number of UAVs in figure 2 increases.Figure 2 shows the change of the optimal decision probability of jamming and non-jamming of jammers under different UAVs.From figure 2,it can be seen that with the increase of UAV quantity,the more obvious the jamming effect is,the greater the probability of the interference is,the better the jamming degree is.At this time,the optimal jamming strategy of jammer selection also increases with the increase of the number of UAV.
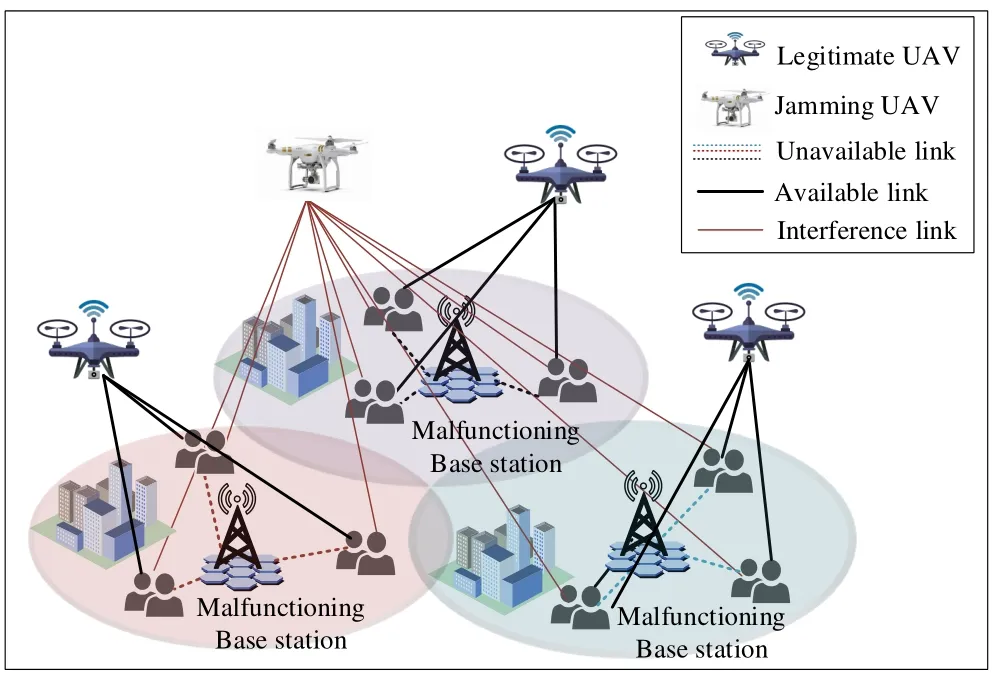
Figure 1.Transmission between UAVs and jammers and vehicles in UAV communication networks.
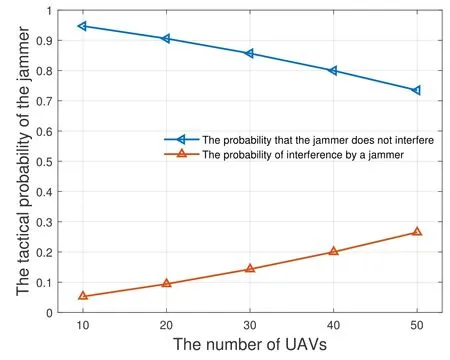
Figure 2.The jammer strategy varies with the number of UAVs.
Figure 3 shows the number of evenly distributed between 10 to 50 of three different schemes of the expectations of UAV.The blue bars are the expected value of the UAV under the optimal strategy.The orange bars are the expected value of the UAV under a random decision.The yellow bars represent the UAV’s expectations under fixed decisions.In simulation,we set the probability that the UAV do not transmit data is 0.1.It can be seen from figure 3 that UAV has the highest expectation under the optimal strategy obtained by the proposed game,which proves the feasibility of proposed security game.From figure 3 we can also see that as the number of UAVs increases,the expectation of UAVs decreases.Because we consider that when a UAV is transmitting data to a vehicle,the common channel interference of other UAVs will also affect the data quality transmitted by UAVs.
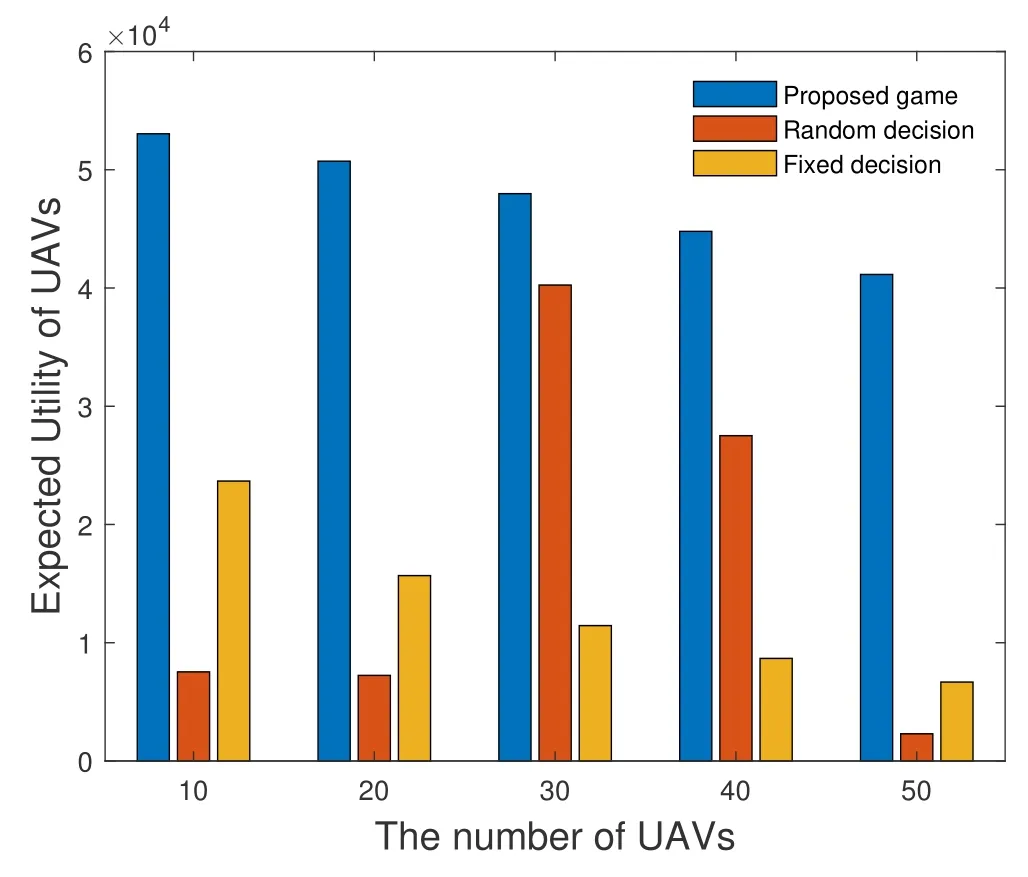
Figure 3.The relationship between UAV expectations and the number of UAVs.
VII.CONCLUSION
In this paper,we have proposed a game theoretical secure data transmission scheme in UVIoTs.Specifically,we exploit the offensive and defensive game to model the interactions between the normal UAVs and jammers,where the strategy of the normal UAV is to determine whether to transmit data,while that of the jammer is whether to interfere.Based on the presented game,we then have formulated two optimization problems,i.e.,maximizing the both utilities of UAVs and jammers.Afterwards,we exploit the backward induction method to analyze the proposed countermeasures and finally solve the optimal solution of the optimization problem.Lastly,the simulation results have shown that the proposed scheme outperforms conventional schemes under the attacks of jammers.For the future work,we will investigate the privacy preservation in the UAV-assisted VIoTs.
ACKNOWLEDGEMENT
This work is supported in part by NSFC (nos.U1808207,U20A20175),and the Project of Shanghai Municipal Science and Technology Commission(18510761000).
- China Communications的其它文章
- Joint Topology Construction and Power Adjustment for UAV Networks: A Deep Reinforcement Learning Based Approach
- V2I Based Environment Perception for Autonomous Vehicles at Intersections
- Machine Learning-Based Radio Access Technology Selection in the Internet of Moving Things
- A Joint Power and Bandwidth Allocation Method Based on Deep Reinforcement Learning for V2V Communications in 5G
- CSI Intelligent Feedback for Massive MIMO Systems in V2I Scenarios
- Better Platooning toward Autonomous Driving: Inter-Vehicle Communications with Directional Antenna

