A Novel Improved Artificial Bee Colony and Blockchain-Based Secure Clustering Routing Scheme for FANET
Liang Zhao,Muhammad Bin Saif,Ammar Hawbani,Geyong Min,Su Peng,Na Lin
1 Shenyang Aerospace University,Shenyang,Liaoning 110136,China
2 University of Science and Technology of China,Hefei,China
3 University of Exeter,Exeter,UK
Abstract: Flying Ad hoc Network (FANET) has drawn significant consideration due to its rapid advancements and extensive use in civil applications.However,the characteristics of FANET including high mobility,limited resources,and distributed nature,have posed a new challenge to develop a secure and efficient routing scheme for FANET.To overcome these challenges,this paper proposes a novel cluster based secure routing scheme,which aims to solve the routing and data security problem of FANET.In this scheme,the optimal cluster head selection is based on residual energy,online time,reputation,blockchain transactions,mobility,and connectivity by using Improved Artificial Bee Colony Optimization(IABC).The proposed IABC utilizes two different search equations for employee bee and onlooker bee to enhance convergence rate and exploitation abilities.Further,a lightweight blockchain consensus algorithm,AI-Proof of Witness Consensus Algorithm(AI-PoWCA)is proposed,which utilizes the optimal cluster head for mining.In AI-PoWCA,the concept of the witness for block verification is also involved to make the proposed scheme resource efficient and highly resilient against 51% attack.Simulation results demonstrate that the proposed scheme outperforms its counterparts and achieves up to 90% packet delivery ratio,lowest end-to-end delay,highest throughput,resilience against security attacks,and superior in block processing time.
Keywords: improved artificial bee colony optimization; optimal cluster head selection; secure routing;blockchain;lightweight consensus protocol
I.INTRODUCTION
A comparatively new research field of ad hoc networks for flying vehicles,Flying Ad hoc Network(FANET)has emerged as a promising networking paradigm[1].FANET consists of Unmanned Aerial Vehicles(UAVs) as they can fly autonomously and remotely without any human assistance [2–4].In recent years,FANET has attracted more attention in civilian,and commercial applications,such as search and rescues operation[5,6],border monitoring[7],traffic control and management [8,9],and remote sensing [10],because of the adoptable,versatile and flexible nature of FANET.This made FANET an interesting field of research[11].
FANET can be perceived as a subset of Mobile Ad hoc Network (MANET) and Vehicular Ad hoc Networks (VANET).However,FANET has some unique features as compared with ad hoc on land.Such as distributed nature,3D mobility,high speed,frequent topology changes,node density,and resource constraint nature[12].The speed of UAVs is greater than that of MANET and VANET.Moreover,UAVs have total freedom of movement in three dimensions (3D)which leads to frequent topology changes.Most civilian UAVs are fitted with small batteries,providing a flight time of about 30-40 minutes [13].These features have a direct impact on the development of routing protocol for FANET[14].
The advanced applications are being designed for FANETs,but pose new challenges,including data security,traffic load balancing,mobility,congestion,and high error rates,which typically lead to the degradation of network performance.The wireless communication scheme is essential to build a flying ad hoc network for collaboration and communication between UAVs.Due to FANET’s highly dynamic nature,3D mobility and high speed results in low throughput,high delay and consumes more battery power of UAV[15].One solution for this problem is the cluster-based routing.Clustering is a strategy for grouping nodes in different clusters of the same geographical area [16].Each cluster has a cluster head(CH)and other neighboring nodes called cluster members (CM) are connected with CH to form a cluster[17].The,CH’s selection is among the most significant of all clustering tasks,where every node in the network can be a candidate for CH.The criterion of selecting a cluster head is probably random,or well-defined criterion based on various factors i.e.connectivity,residual energy,mobility and reputation.Hence,a well-defined criterion depends on objectives for maximizing the connectivity,maximizing residual energy,minimizing mobility,maximizing reputation should be designed,where this problem is a multiple objective optimization problem.To this end,it is a challenging task to select an optimal cluster head and objectives that are related to the problem.
In recent years,different CH selection approaches were presented.For example,Particle Swarm Optimization(PSO)[18],Ant Colony Optimization(ACO)[19],Grey Wolf Optimization(GWO)[20],and Artificial Bee Colony Optimization (ABC) [21]for clustering in ad hoc networks have also been proposed.The Artificial Bee Colony (ABC) algorithm is a new type of swarm intelligence algorithm proposed by Basturk and Karaboga[21];this algorithm has been modified by many studies to solve complicated problems in various fields of science and engineering.Similar to other population-based meta-heuristic algorithms,ABC meta-heuristics also faces some challenges,such as a poor exploitation process rather than exploration,and comparatively slow rate of convergence,especially in dealing with multi-modal optimization problems.
Furthermore,FANET security has become a critical issue and drawn increasing concern because UAVs can be employed as weapons.The key features of the most related works are compared in Table 1.At present,numerous researches have been conducted on the security of FANET.These studies have focused on communication privacy,integrity,and authentication through the development of trust management [22]and cryptographic protocols [23].However,ensuring the data immutability,data availability,and transparency of the network is still an open research problem in FANET.In cluster based routing the data immutability,data availability,and transparency is a crucial issue as members in the cluster solely rely on the CH for operational instructions,route discovery,and routing data storage.The distributed characteristics of FANET makes it suitable for blockchain.The combination of FANET and blockchain can provide the capabilities to make FANET routing data more secure,immutable,and transparent.The blockchain[24]is a decentralized and distributed data structure run by a consensus algorithm and distributed nodes.The application that runs previously through any trusted authority;in blockchain,it is possible to run that application without any trusted authority in a distributed environment [25,26].Without central authority,blockchain can assist to develop a distributed network of nodes,in which blockchain excludes the need to trust each node in the network.The consensus algorithm used by the blockchain ensures that the ledger is consistent and temper proof across all nodes in the network.
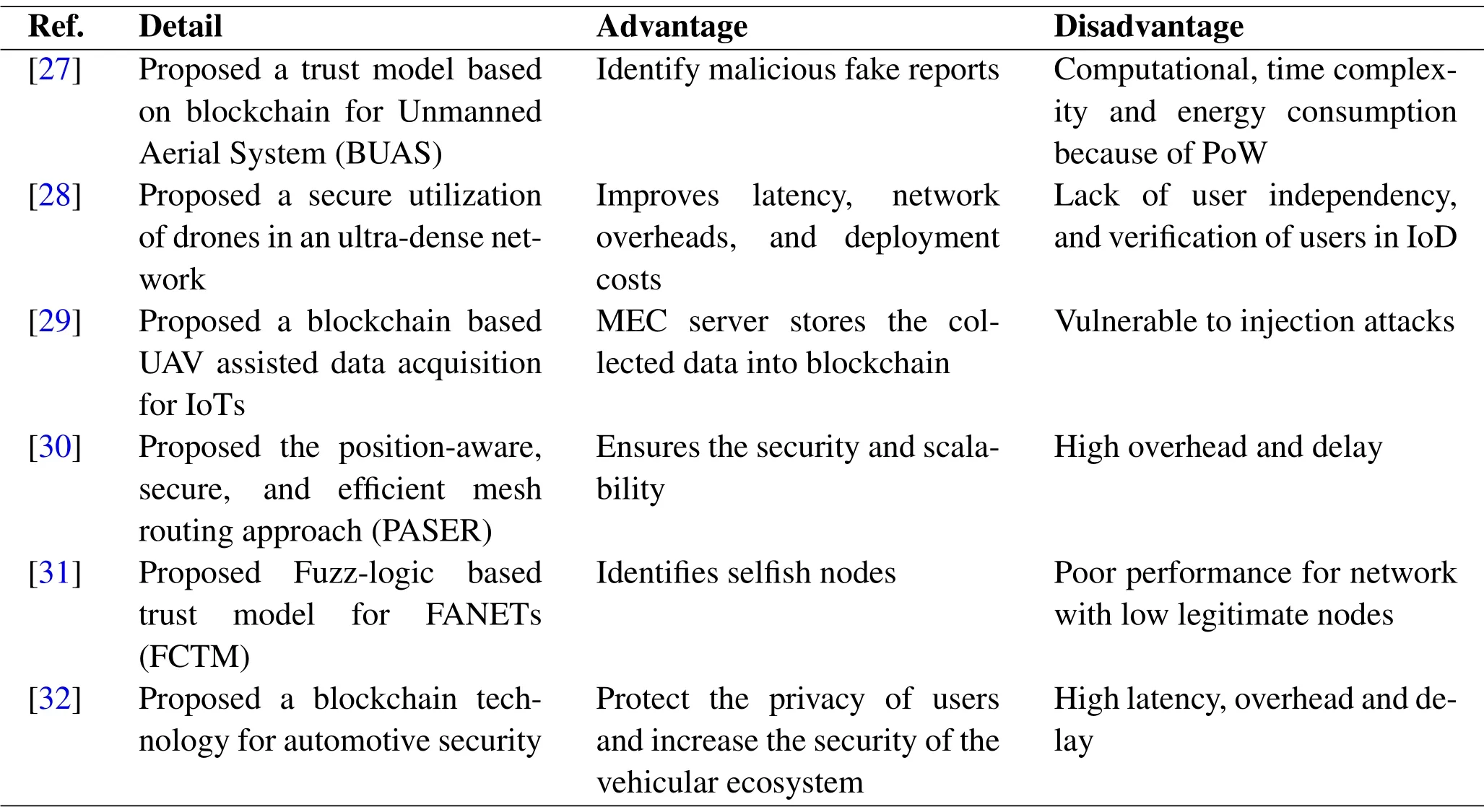
Table 1.Comparison of most related works.
The aforementioned studies give us motivation to develop an improved artificial bee colony and blockchain-based secure clustering routing scheme for FANET.In this paper,we proposed an Improved Artificial Bee Colony(IABC)algorithm for balancing the exploration and exploitation process.Moreover,convergence rate is fast in the comparison with the original Artificial Bee Colony(ABC)algorithm.Furthermore,an optimal cluster head selection algorithm is proposed using IABC.In the proposed scheme,the CH is responsible for inter-cluster,intra-cluster routing,and base station communication.Furthermore,CMs rely on CH for route discovery,packet forward-ing,and routing table storage.Therefore,routing data security and immutability are critical for CH to overcome this challenge we employed blockchain.However,for highly resource-constrained FANETs,traditional blockchain consensus algorithms are not suitable.Therefore,we proposed a lightweight consensus algorithm AI-Proof of Witness Consensus Algorithm which do not only comprises miners to verify blocks,but also requires a witness to verify block to append in the blockchain.The major contributions of the paper are listed as follows.
1.We proposed an improved artificial bee colony algorithm (IABC).The proposed algorithm is significantly better in exploration,exploitation and convergence.
2.We introduced the optimal cluster head selection algorithm using IABC.In the objective function,we considered different factors.The selected cluster head is optimal in terms of resources and security,which is also employed for mining.
3.A novel lightweight consensus algorithm is proposed,in which we consider the optimal cluster head as a super miner.The new block is verified by a randomly selected super mining node,and the concept of a witness for the new block is also proposed.This allows the algorithm to be more resilient against a 51%attack.
II.THE PROPOSED ROUTING SCHEME
Two significant challenges that FANET encounters are how to connect nodes together and how to adapt the dynamically changes in the network topology.The overview of the novel FANET routing scheme is depicted in Figure 1.In this scheme,the UAVs are employed as relay nodes for ground stations.For example,if two ground stations are not in the communication range of each other the FANET helps to establish a link between ground stations.After optimal cluster head selection and network formation,as described below the CHs locates the nearest ground station by sending a Hello Message if ground stations are in direct communication range or through edge UAVs.The second step is if a new block is generated,the CH invites a random witness UAV by sending its Public Key(PK)and the witness UAV verifies the new block by adding its digital signature.After successful block verification,the CH(super mining node)broadcasts a new block using Block Announcement Message.The third step is the ground station sends a data packet to CH and CH forwards the packet to the next hop by looking into its routing table until the packet reaches the destination ground station.
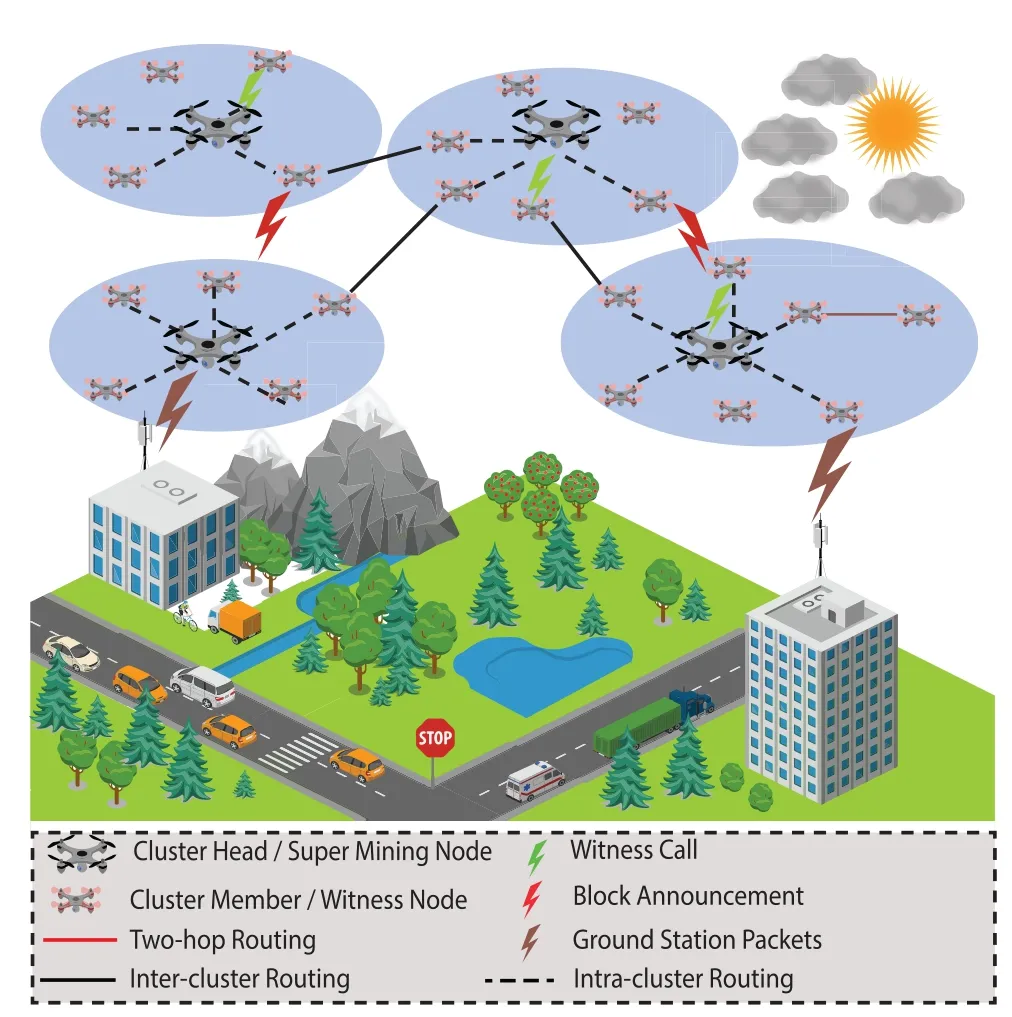
Figure 1.Overview of secure FANET routing scheme.
Figure 2 illustrates the system structure of proposed secure FANET routing scheme.At first,we select a UAV with high residual energy to perform cluster head selection by employing the proposed IABC algorithm.After reaching a maximum number of cycles,IABC returns a list of optimal cluster heads or also called super mining nodes,and broadcasts in the network with cluster head ID.The second step is network formation,all UAVs except CHs send cluster join request to neighbouring CH,and the CH keeps updating the routing table.In the proposed scheme,we consider each update in the routing table as a blockchain transaction and transmits it to the blockchain module.The third step is to secure the routing data when the number of transactions reaches a specified threshold a block is created and it invokes the consensus algorithm to verify and append block in the blockchain.The consensus algorithm invites a witness node to be a witness of the block by adding a digital signature of the witness.After,a successful verification block is appended in the local chain and broadcast in the network to other CHs.
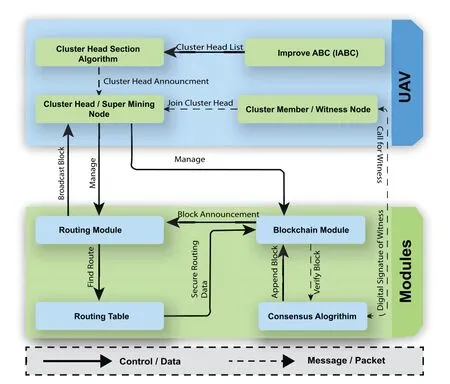
Figure 2.System structure of secure FANET routing scheme.
2.1 Improved Artificial Bee Colony Optimization
Artificial Bee Colony Algorithm is a meta-heuristic algorithm comprised of intelligent and foraging behavior of honey bee swarms.The algorithm comprised three essential phases: employee bee phase,onlooker bee phase,and scout bee phase.Every employee bee is associated with a specific food source; onlooker bees watch the wangle dance of employee bees in a hive to check the quality of food and scout bees search for food randomly [21].Various modifications have been presented to improve the efficiency of the original version of ABC.Following other meta-heuristic algorithms,standard ABC also suffers a few challenges,such as slow convergence speed during search and an unbalanced exploitation and exploration process.A new candidate solution is produced by updating its parent solution’s random dimension vector during the search process.Therefore,most likely,new candidate solution is similar to its parent solution,which leads to slow convergence.In addition,when addressing complex multimodal problems,ABC may easily fall into local minima[33].Therefore,a better optimization algorithm during the search process should balance exploration and exploitation.
In this context,we proposed two different search equations for coping with slow convergence rate and unbalanced exploration and exploitation process.The standard ABC can produce a new solution by utilizing Eq.1.In Eq.2,we proposed an improved search equation for the employee bee phase in which it utilizes the information of the global best solution,which helps to improve the exploitation process in the employee bee phase.The second part(xg,j −xi,j)of Eq.2 use the information of the global best solution.In Eq.2,xg,jis thejthelement of global best solution and first part of equation is similar to standard ABC algorithm,which works better in exploration.Hence,Eq.2 is more balanced in exploration and exploitation.
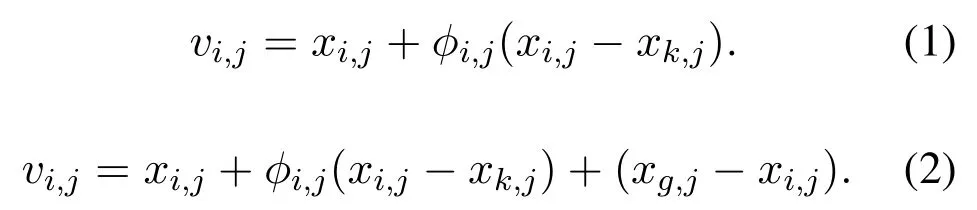
The onlooker bee also utilizes Eq.1 for producing new candidate solution in standard ABC,which is more likely to tend to slow convergence.The modified search approach MABC (ABC/best/1) is proposed in[34],in which the information of global best solution has been used to assist new candidate solutions.We employ the search strategy of Eq.3 for onlooker bees,which is helpful to achieve fast convergence compared with search equation Eq.1 of standard ABC,which only search in the neighborhood randomly.
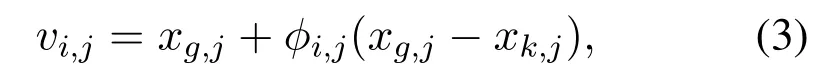
wherexg,jis thejthelement of global best solution,φi,jis random number between[-1,1],andxk,jis the randomly selected solution in population(ki),j ∈(1,2,....D)in a random index.
2.2 IABC-Cluster Head Selection
We proposed a cluster-based routing scheme,in which an optimal selection of cluster head (CH) is implemented based on our proposed IABC.CH selection is considered as one of the most pivotal tasks for clustering in FANETs because CH routes the data from Cluster Members(CM)and transmitting data to other CHs.We consider group of objectives to calculate the proposed fitness function described as follows:
•Residual Energy:The total remaining energy of UAV is residual energy described in Eq.4
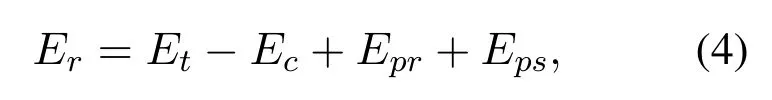
whereEris current residual energyEtis the total initial energyEcis the energy for processing one block in blockchain,Epris the packet receiving energy,andEpsis the packet sending energy.In the proposed scheme,the CH is responsible for inter-cluster and intra-cluster communication.Hence,the residual energy of CH is very crucial because low residual energy leads to frequent dead nodes and decreases the overall network lifetime.
•Reputation Ranking:The reputation ranking is based on the number of packets received,the number of packets dropped,and the number of packets forwarded.Therefore,a high reputation ranking can help to avoid malicious and compromised UAV to be selected as a CH.
•Total Online Time:Online time is the total time that each UAV takes part in the blockchain and network.The higher online time of CH indicates that CH has less probability to turn into a dead node which enhances trust and overall network lifetime.
•Numbers of Transactions:The numbers of transactions are the total number of new blocks append in the blockchain by individual UAV.The malicious and compromised UAV can hold or drop blockchain transactions.Hence,the number of transactions is useful to select a trusted CH.Trusted CH can reduce energy consumption and the number of transactions to be verified[35].
•Mobility:The mobility is course change and speed stability of a UAV compared with other UAVs in the network.The stable course change and low-speed help to form more stable clusters,reduces frequent link breakage,and control messages.
•Connectivity:The connectivity is the number of UAVs connected with any individual UAV in the network.The UAV with higher connectivity have a higher likelihood of being CH because high connectivity can reduce the number of uncluster UAVs and increases the packet delivery ratio.
Initialization Phase:The initialization of population is an important phase in any population based meta-heuristic optimization algorithm.In our proposed algorithm,each UAV is initialized with above mentioned parameters and considered as a food source.
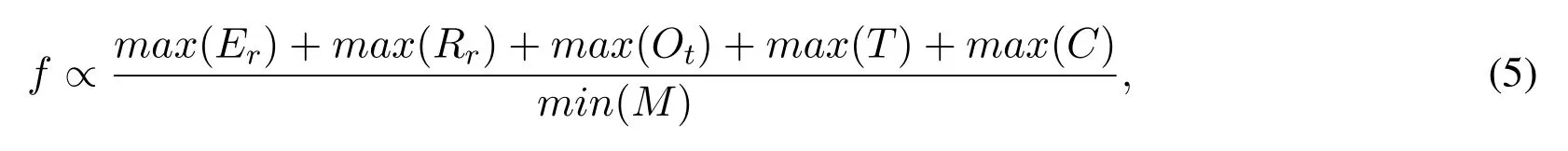
Fitness Function:The assessment of each food source in population and selecting optimal CH needs to have a fitness function.For the selection of optimal cluster head in our proposed algorithm,we constructed a fitness function inspired by [36].The major objectives of fitness function are that if UAV is selected as a CH,it should have maximum residual energymax(Er),maximum reputation rankingmax(Rr),maximum online timemax(Ot),maximum transactionsmax(T),minimum UAV mobilityand maximum UAV connectivitymax(C).The proposed fitness function can be described as
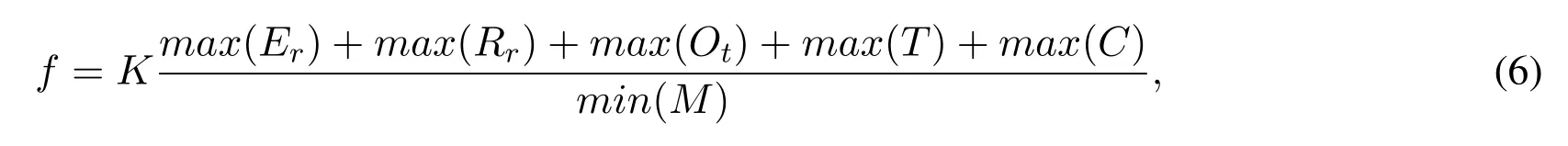
where K is a constant of proportionality,we assumed K=1.
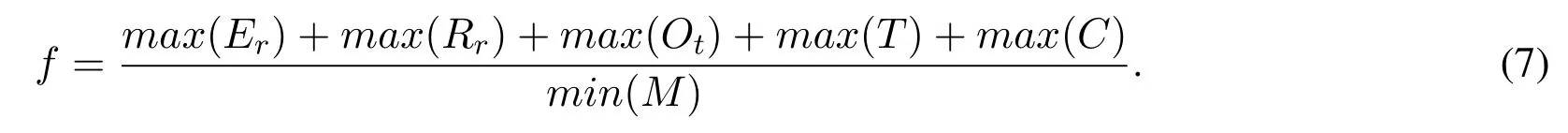
Therefore,we determine the fitness of solution using Eq.7.
Employee Bee Phase:Employed bees search for new food sources,it associates each employee bee with a food source.The number of employee bees are equal to the food source and each employee bee determines a new solution using Eq.2.After producing new solution,it calculates the fitness of proposed solution by using Eq.7 and applies greedy selection for selecting improved food source.At the end of this phase employee bee shares information with onlooker bee.
Onlooker Bee Phase:The onlooker bee selects a food source according to probability given in Eq.8 and determines a new solution by using Eq.3.The onlooker bee calculates the nectar amount in other words fitness of newly generated solution by using Eq.7 and applies greedy selection for selecting improved food source.
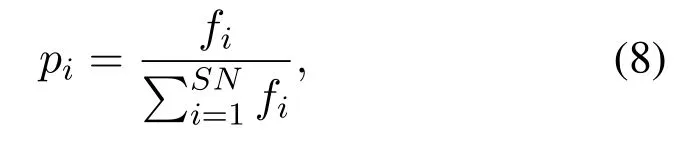
wherefiis the fitness ofithsolution in the population andi= 1,2,3,...,SNSN is the population size.Hence,fitness is proportional topi.
Scout Bee Phase:The scout bee randomly determines new food source using Eq.9,if a food source does not improve the fitness after repeated trails and food source it is considered as abandoned.
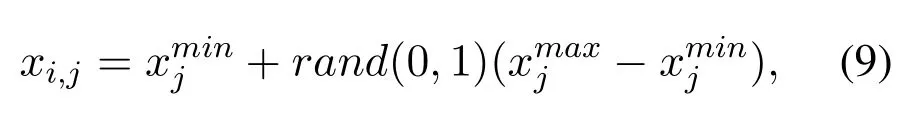
wherexi,jis new food source.xmaxjandxminjdenote the upper and lower bounds of abandoned food source,respectively.rand(0,1) is a uniform random number range between 0 and 1.The scout bee will replace new solution with abandoned food source.After reaching maximum number of cyclesMCN,the proposed IABC will return optimal cluster head.
Network Formation:After the selection of optimal cluster head,the next phase is formation of network.In our proposed solution,cluster head is responsible for handling packets from cluster members and forward packets to other cluster heads.Each UAV in the network is initialized with a UAV ID,which is used as a identification for UAV.Initially all UAVs except cluster heads in the network broadcastsJoin Cluster Message.When a cluster head receivesJoin Cluster Message,it updates its cluster member’s table.Each CH maintains three tables as follows.
•Cluster Member Table:The CH manages a cluster member table in which the information of direct neighbors of CH is stored,and intra-cluster communication is performed by utilizing the cluster member table.The entries in a table contain the Id of a neighboring UAV,connected or disconnected status,and updated information of parameters,i.e.the residual energy,reputation ranking,total online time,number of transactions,mobility,and connectivity of neighbors and CH update all information periodically.
•Two-hop Member Table:The cluster members broadcast their neighbors information periodically to the CH.Therefore,by utilizing the information of neighbors,the CH can collect information about UAVs located two-hop away and maintains a two-hop member table by adding two-hop un-clustered neighbors.
•Edge Member Table:The edge member table maintains the information of neighboring clusters.The edge UAV is connected with more than one CHs,which is used as a link between two clusters.The edge member table contain Ids of connected CHs,Id of edge UAV,which is connected with both cluster heads and link status.The intercluster communication is performed by utilizing an edge member table.
2.3 A Lightweight Consensus Algorithm
Blockchain is a distributed database,in which every node or majority of nodes should participate and agree in the decision of adding a new block of information in blockchain and should have a copy of that database.Blockchain is a distributed ledger with tamper-proof,decentralization and data traceability characteristics.Blockchain can be used to improve the trustworthiness and robustness of the routing information.We employ the blockchain to record the routing tables data described in Section 2.2 Network Formation.The process of participating and agreeing on a common or majority decision is called consensus.In this paper,we proposed an AI-based lightweight consensus algorithm suitable for UAVs.Currently,the mostly consensus algorithms used are not suitable for UAVs because these algorithms consume energy and processing power for reaching on consensus conclusion adding a new block in blockchain.The commonly used consensus algorithms are Proof of Work (PoW)and Proof of Stake (PoS) [37].In PoW algorithm,all mining nodes take part in the consensus process,and the node with more resources,i.e.,computing power or hashing power can commit new blocks in the blockchain.In PoS,the node with more stakes in the network has more chances to commit the new block in blockchain.The drawbacks of these algorithms are energy consumption and time delay for processing new blocks,which makes these algorithms unsuitable for UAVs because of having low battery power and less computing power.Blockchain comprises main three componentstransactions or blocks,consensus algorithmandchain.
2.3.1 Transactions and Blocks
The structure of the transaction is shown in Figure 3(b).The first entry is the transaction ID (TID).In contrast,the second entry is a pointer to the previous transaction of transaction generator UAV.The third is the public key(PK)of the transaction generator UAV.The fourth is a time-stamp when a transaction is generated.The fifth is the signature of the transaction receiver CH,sixth entry is the reputation of transaction.The reputation comprises three entries,1) total number of transactions of the generator,2) the receiver CH rejects a total number of transactions,and 3) the hash of PK that the transaction generator will use for the next transaction.The reputation field is used in the distributed trust algorithm presented by[35].The structure of the block is shown in Figure 3(a).The block consists of a block header and a block body.The header section contains,the hash of the previous block,witness signature and time-stamp and block body contains all transactions.
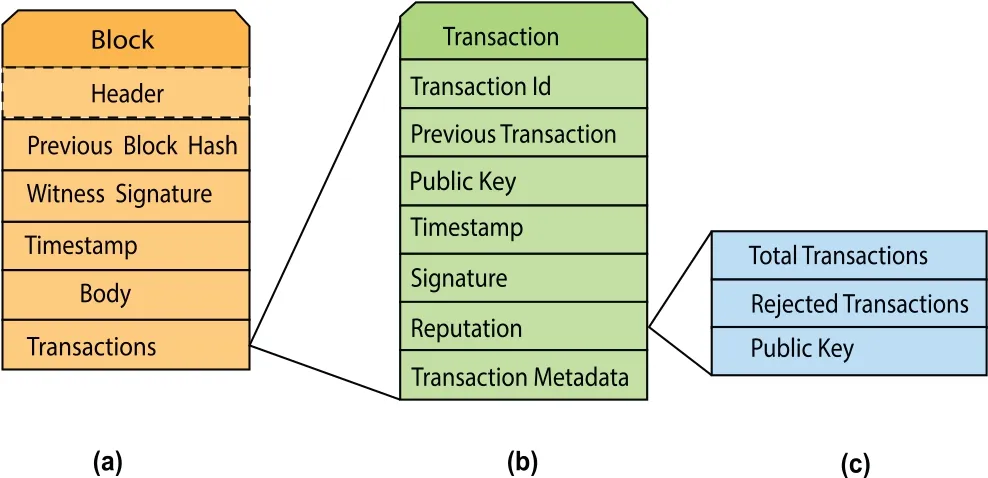
Figure 3.Structure of block,transaction and reputation.
2.3.2 AI-Proof of Witness Consensus Algorithm
The AI-PoWCA selects an optimal UAV called super mining nodes to add a new block in blockchain ratherthan allowing each node in the network to take part in the mining process(Proof of Work),or select a designated validator based on stakes in the network(Proof of Stake).Thus,there is no or limited competition in adding a new block.Super mining nodes are optimal miners in terms of lifetime,reputation,connectivity,and the number of transactions.The AI-PoWCA makes the requirement on computational power and memory capacity of the mining devices basic.The verification of a new block is not only verified by a super mining node,at least one random witness node,which is not a super mining node,is invited to be a witness of a new block using a digital signature generated by public and private key pair.
The optimal cluster heads selected by IABC act as super mining nodes,and cluster member nodes act as witness nodes in our proposed system.A 51%attack needs simultaneously attack both super mining nodes and witness nodes to gain hostile takeover.When a new block is committed,the super mining node broadcasts a new block in network,and all super mining nodes keep updated their blockchain ledger.Hence,the proposed algorithm greatly improves the security of blockchain.
2.4 Security Analysis
In this part,we conduct a security analysis to analyze our proposal.The comparison of AI-PoWCA with PoW,PoS,and PoA on attacks,energy consumption,and availability for FANET is presented in Table 2.
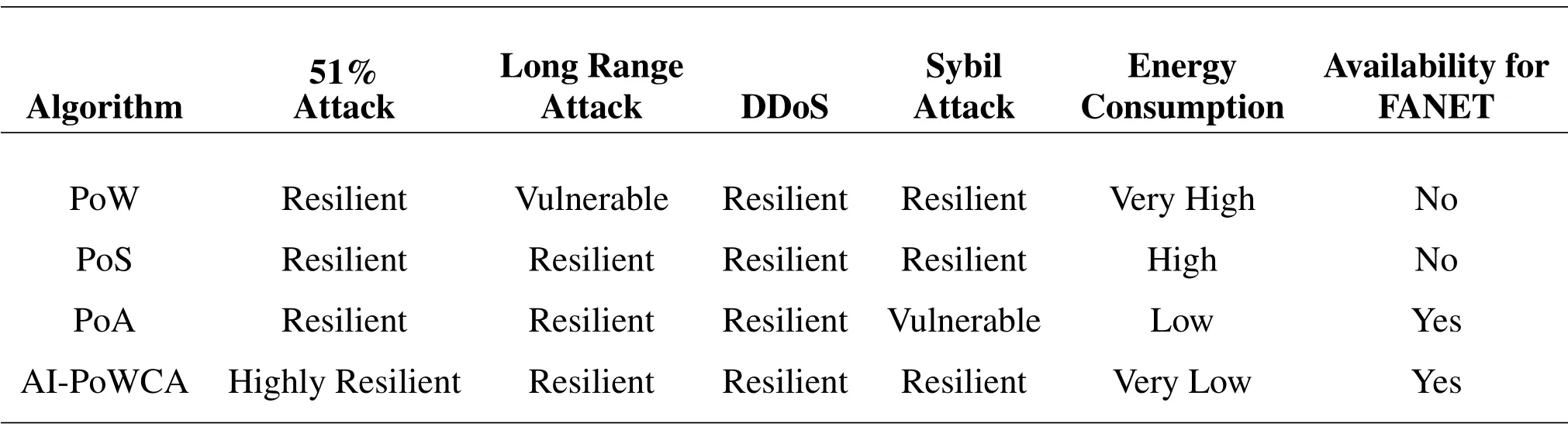
Table 2.AI-PoWCA comparison with existing algorithms.
2.4.1 51%Attack
51% attack refers to an attack in which a group of miners controlling over 50% of network mining hash rate or computing power to prevent new transactions from gaining confirmation.The proposed AI-PoWCA is highly resilient against 51% attack.The attacker needs to control all super mining nodes and witness nodes because a new block is verified by the witness node as well.
2.4.2 Long Range Attack
Long range attack is a scenario where the attacker creates a new branch on the genesis block and overtakes the main chain.The proposed algorithm is resilient against long range attack because AI-PoWCA maintains only the main branch.
2.4.3 DDoS Attack
DDoS attack takes place when a malicious node floods a network with extreme traffic.DDoS attack is possible through the centralized feature of the network.The proposed scheme is decentralized,and numerous UAVs are connected with each other in a distributed fashion.The attacker needs to control multiple UAVs at the same time.
2.4.4 Sybil Attack
In this attack,a node attempts to overpower the network through the use of different IDs.The AIPoWCA is resilient because all UAVs in the network are required to have a genesis block and authorized ID which prevents the attacker from introducing unauthorized UAV to the network.
III.EXPERIMENTS
In this section,we present the configuration and results of our proposed scheme.We conduct the experiments on PC intel core i5,1.9 GHz CPU,and 8 GB RAM.We first evaluate the proposed IABC,then compare the proposed routing scheme.The experimental code has been made open source(https://github.com/MuhammadBinSaif/FANETRouting).
3.1 Performance Evaluation of IABC
We conduct the experiments on MATLAB R2020 to compare the performance of our proposed IABC with three well-known population-based meta-heuristic algorithms,particle swarm optimization algorithm[18],grey wolf optimization algorithm [20],and standard artificial bee colony algorithm[21].The effectiveness of the algorithms is evaluated by utilizing eight wellknown benchmark functions specified in Table 3.The first three functionsf1,f2andf3with30 dimensionsandrangebetween[-100,100]are unimodal functions.The high dimension of unimodal functions can help to examine the exploitation ability of proposed algorithms.The latter five multimodal functions fromf4tof8with local optima can help to investigate the exploration capability of the algorithm.All experiments were run with 30 population size,and 50 independent runs.The performance of solution accuracy and convergence of these three algorithms on each benchmark function is shown in Figure 4.

Table 3.The benchmark functions.
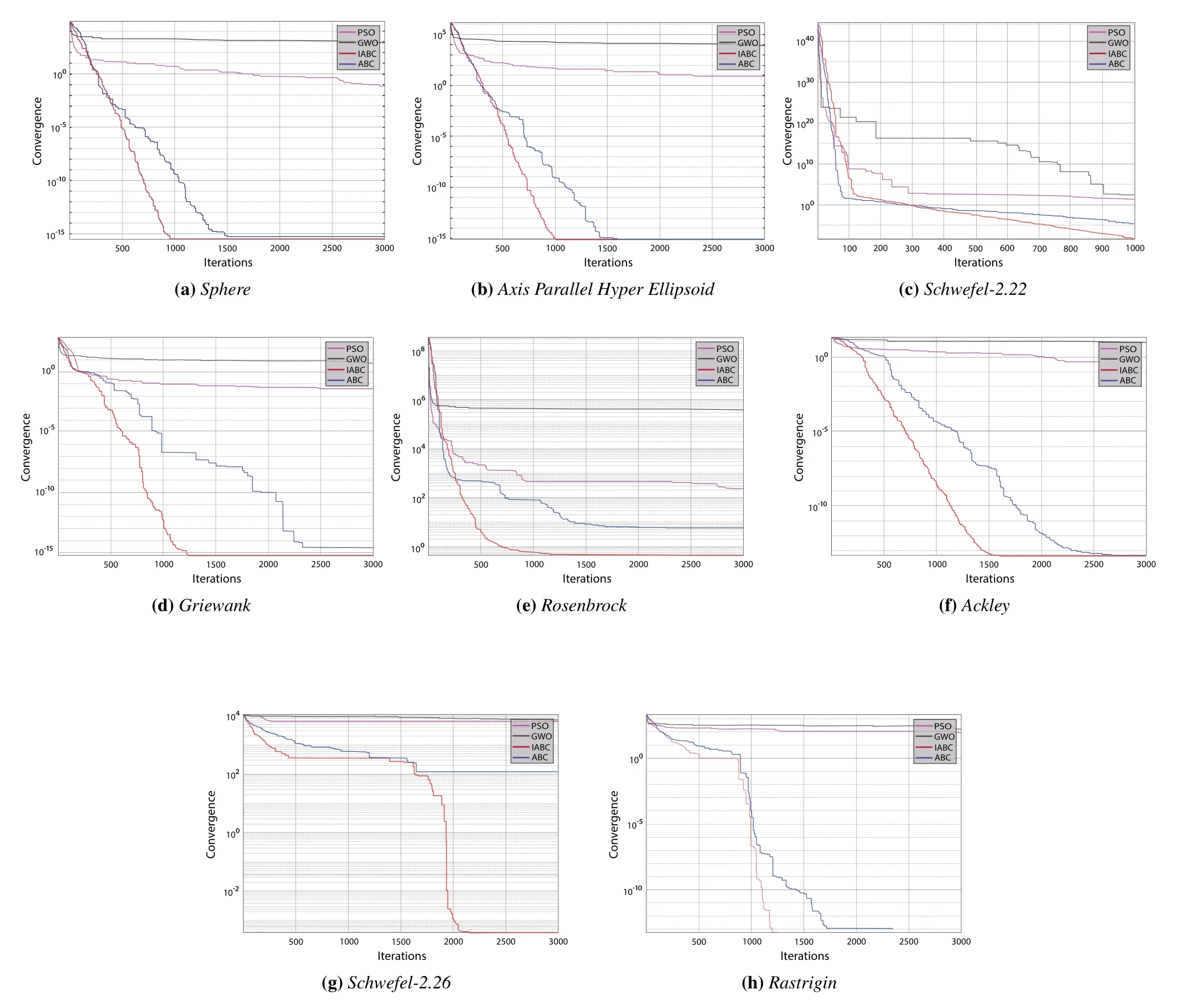
Figure 4.Convergence curves of IABC,PSO,ABC,and GWO on benchmark functions.
In case of unimodal functions fromf1tof3,as illustrated in Figure 4a,4b and 4c,curve continues downward shift and proposed IABC showed better performance in solution accuracy and convergence,especially inf1andf2.In case of multimodal function fromf4tof8,IABC gets global optima rapidly as shown in Figure 4d,4e,4f,4g and 4h,which shows that IABC have better exploration ability in the comparison with other algorithm,especially the original ABC.These experiments have verified that IABC is superior in terms of solution accuracy,convergence and balance in exploration and exploitation to its adversaries.
3.2 Simulation Environment and Network Analysis
All the simulation experiments are carried out on NS-3.As listed in Table 4,We adopt the random waypoint mobility model for 3D mobility of UAVs.We have evaluated the proposed routing scheme in different scenarios in terms of UAV node density within an area of 1500m×1500m and a communication range of 300m.The SHA-256 is used as the hash algorithm in the blockchain.The performance of the routing scheme is compared with meta-heuristic based routing schemes AntHocNet [38]and BeeAdHoc [39]in terms of packet delivery ratio (PDR),end-to-end delay(EED),and throughput.
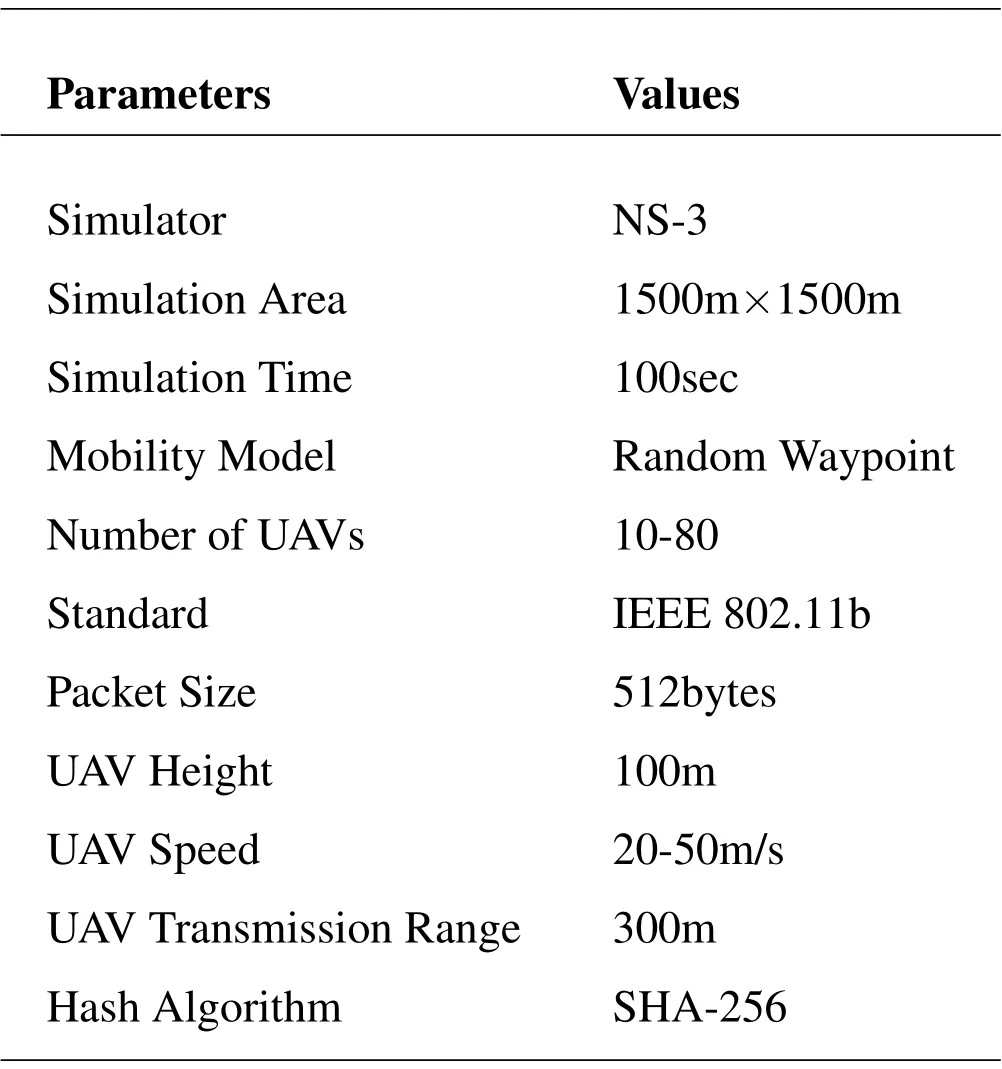
Table 4.The simulation parameters.
3.2.1 Packet Deliver Ratio
The packet delivery ratio(PDR)is a ratio of number of packets delivered in total to the total number of packets sent from source node.The PDR is calculated asPr/Ps,wherePris the total number of packets received andPsis the total number of packets sent by source node.As shown in Figure 5,we compare the PDR of our proposed FANET routing strategy with meta-heuristic based routing schemes,AntHocNet and BeeAdHoc.The graph illustrated that the proposed routing scheme achieves the highest PDR up to 90%for all network densities.From Figure 5,we can observe that with the increase of the number of UAVs,the packet delivery ratio of all schemes climbs up.The proposed routing scheme outperforms others in PDR,as we can justify this because of the optimal cluster head selection and formation of more stable clusters.
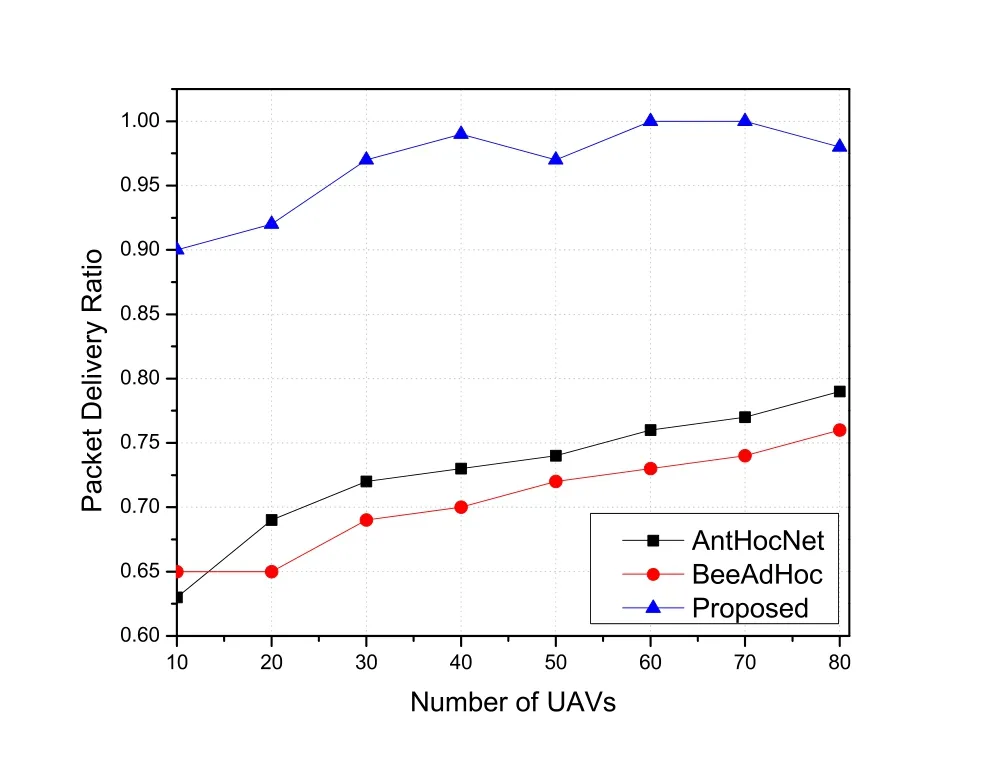
Figure 5.The packet delivery ratio.
3.2.2 Average End-to-End Delay
The end-to-end delay(EED)of each packet is the sum of the delays encountered by the transitional node on the way to the destination.The average EED depends on the sum of the total time taken to the number of packets received successfully at the destination node.
The efficiency of the network can be measured by the average EED,which is supposed to be as low as possible.As shown in Figure 6,we can observe that the average EED of proposed FANET routing scheme is significantly lower than compared with other routing schemes this is because the UAVs are distributed in clusters and each cluster head maintains its cluster which leads to lower overhead messages and EED.It can be observed from Figure 6 that the more number of UAVs interact in network,the higher the bandwidth will be used,and thus more congestion will occur,meaning that the average EED will increase substantially.
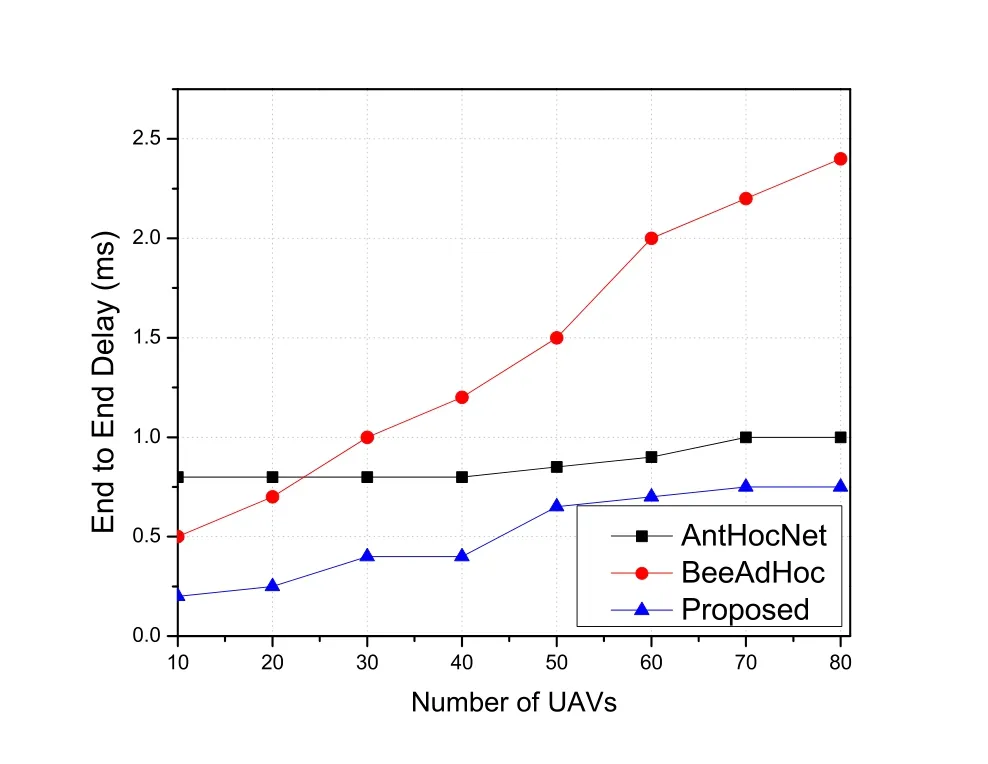
Figure 6.The average end-to-end delay.
3.2.3 Throughput
The throughout is described as an amount of data transferred from source to destination during a time period.We can observe the real transmission efficiency of the network from this metric.Figure 7 depicts the throughput of proposed FANET routing strategy in different scenarios.We have simulated the proposed routing scheme on different network density and compare with meta-heuristic based routing schemes AntHocNet and BeeAdHoc to find out the influence of UAVs density on throughout.From Figure 7,we concluded that the network utilizes more throughput as network density grows,in which the our scheme achieves the highest throughput(249 kbps)in the scenario with 80 UAVs and the lowest (129 kbps) in the scenario with 10 UAVs.
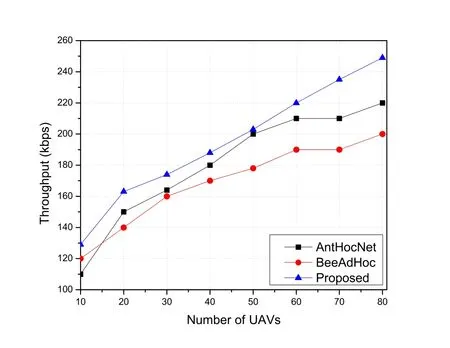
Figure 7.The average throughput.
3.2.4 Block Generation Time
The processing time is the total time consumed by a super mining node to verify a new block.Due to resource constrained nature of UAVs,we adopted a distributed trust algorithm proposed in[35],in which number of transactions to be verified in a block is decreases as UAVs build-up a trust table based on number of transactions verified and number of transactions rejected of source node by super mining node.On the other hand,in the classic blockchain we must verify all transactions inside a block which is computationally expensive task.The average processing time of AI-PoWCA is illustrated in Figure 8,which concludes that as the number of blocks increases the processing time is gradually increased.
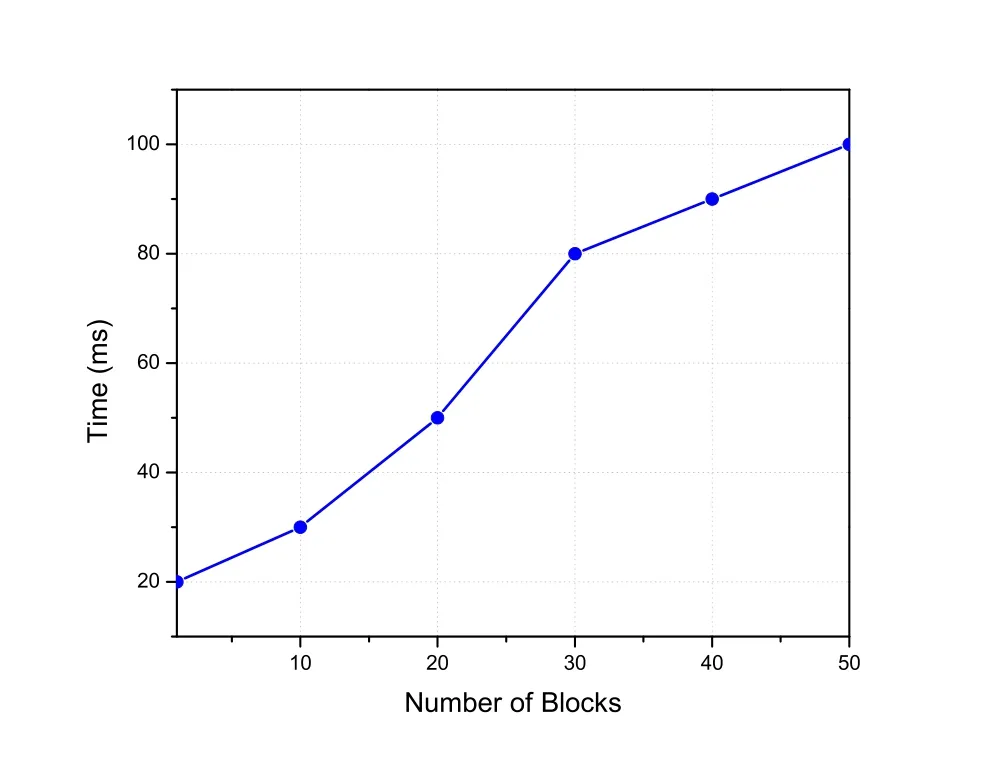
Figure 8.Block processing time.
IV.CONCLUSION
In this paper,we proposed a novel cluster-based secure routing scheme for FANETs,which intends to simultaneously deal with the problem of optimal cluster head selection and routing data security.Initially,IABC is presented to balance exploration and exploitation capabilities as well as the convergence rate of standard ABC,and we evaluate performance on scalable unimodal and multimodal benchmark functions.The comparison with PSO,GWO,and ABC shows that IABC outperforms these existing meta-heuristic algorithms.Further,IABC had been utilized to minimize the fitness function for CH selection based on residual energy,reputation,online time,connectivity,transactions,and mobility.In addition,we present a lightweight consensus scheme for blockchain which utilizes the optimal CH for mining,as known as the super mining node.We also introduce the concept of witness for block verification to make this scheme highly resilient.Last,extensive experiments are conducted to compare our proposed scheme with metaheuristic based AntHocNet and BeeAdHoc in terms of end-to-end delay,packet delivery ratio,throughput,and block processing time,where the results show the proposed scheme is superior in all scenarios and AIPoWCA takes a fraction of time for block processing.
ACKNOWLEDGEMENT
This paper is supported in part by the National Natural Science Foundation of China (61701322),the Young and Middle-aged Science and Technology Innovation Talent Support Plan of Shenyang (RC190026),the Natural Science Foundation of Liaoning Province(2020-MS-237),and the Liaoning Provincial Department of Education Science Foundation(JYT19052).
- China Communications的其它文章
- Joint Topology Construction and Power Adjustment for UAV Networks: A Deep Reinforcement Learning Based Approach
- V2I Based Environment Perception for Autonomous Vehicles at Intersections
- Machine Learning-Based Radio Access Technology Selection in the Internet of Moving Things
- A Joint Power and Bandwidth Allocation Method Based on Deep Reinforcement Learning for V2V Communications in 5G
- CSI Intelligent Feedback for Massive MIMO Systems in V2I Scenarios
- Better Platooning toward Autonomous Driving: Inter-Vehicle Communications with Directional Antenna

