An Efficient Three-Factor Privacy-Preserving Authentication and Key Agreement Protocol for Vehicular Ad-Hoc Network
Tao Xu,Cheng Xu,*,Zisang Xu
1 School of Electronic Engineering,Beijing University of Posts and Telecommunications,Beijing 100876,China
2 Key Laboratory for Embedded and Network Computing of Hunan Province,Changsha 410082,China
Abstract: As an indispensable part of the Intelligent Transportation System (ITS), the vehicular adhoc network(VANET)has attracted widespread attention from academia and industry.In order to ensure the security of VANET, vehicles need to be authenticated before accessing the network.Most existing authentication protocols in VANET adopt the Trusted Authority(TA)with centralized structure which is responsible for the authentication tasks of all vehicles.However, the large-scale network consume a lot of computing resources,which leads to unacceptable delay in message transmission in VANET.For reducing the computational cost of TA,an efficient three-factor privacy-preserving authentication and key agreement protocol was proposed in our paper.Different from before,the RoadSide Unit(RSU)no longer acts as an intermediate node but is responsible for assisting user authentication,which lead to the computational cost of TA is very low.Through formal and informal analysis,our protocol demonstrates excellent security.Compared with previous studies,our work emerges advantages and superiorities in the following aspects: computational cost, communication cost, security properties and functions,message loss ratio,and message delay.These data and evidence indicate that our protocol is an ideal choice for large-scale VANET.
Keywords:authentication;vehicular ad-hoc network;security;three-factor
I.INTRODUCTION
With the continuous development of society,the number of vehicles in metropolises has been increasing.In order to manage transportation systems efficiently and effectively, Intelligent Transportation System (ITS)have developed rapidly in recent years[1].As a subset of mobile ad-hoc network (MANET), VANET [2] is prospering in this environment.VANET includes the following three parts [3]: (1) On-Board Unit (OBU).OBU is a device installed on a vehicle that has certain computing, storage and communication capabilities.The OBU can communicate with the RoadSide Unit(RSU) or other OBUs in the communication range through the Dedicated Short Range Communication(DSRC)[4];(2)RSU.RSU is an infrastructure located along the road,with more computing power and communication capabilities than OBU,which can communicate with Trusted Authority (TA) via a wireless or wired channel;(3)TA.TA can provide system parameters and services for VANET.The authentication of all nodes in VANET is completed by TA.
VANET enables people to enjoy a more reliable and more comfortable driving experience, while also providing a variety of convenient services (e.g., traffic safety information, entertainment services, locationaware services, cooperative safety driving and etc).These services related to user life can easily cause serious security problems.Security problems has always been an important issue in VANET.Lai et al.[5]pointed out that even in the 5G era, the VANET still faces various security and privacy issues.In order to ensure the security of these services,a secure authentication and key agreement protocol is essential, otherwise, VANET will face various security risks (e.g.,impersonation attacks, replay attacks, tampering attacks, and etc).Due to the real-time requirement of VANET, it has higher real-time requirement than traditional MANET [6], which makes vehicles need to complete authentication and subsequent information exchange in a limited time.For instance, when the transmission time of the messages in VANET exceeds 500ms,cooperative safety driving system cannot work in time,so that accidents cannot be avoided[7].In addition, VANET is developing into the largest ad-hoc network in the world, Cui et al.[8] pointed out that the data shared in VANET indicate that the size and amount of requested data will continue increasing,the number of network nodes has exceeded 750 million and continues to grow [9].This leads to the fact that despite the TA has great computing power, the delay caused by authentication for all users is intolerable.Therefore,the authentication protocol in VANET must be efficient.Moreover,the authentication protocol also needs to provide anonymity for the purpose of preventing attackers from obtaining sensitive information from users.
In order to solve the security and efficiency of VANET, many different types of authentication protocols were proposed in the past decades.Raya et al.[10] proposed a protocol that protects the privacy of users,this protocol requires the vehicle to have a very large memory and computational cost,because the vehicle must preload a lot of key pairs and certificates in advance, and need to manage the keys.In order to overcome the above problems in [10], Lu et al.[11]proposed a novel scheme,which no longer need vehicles to store many anonymous certificates.According to[11],if the vehicle wants to access VANET,it must interact with the RSU to obtain a temporary short-term anonymous certificate assigned by the RSU.In order to obtain an anonymous certificate from the RSU,the vehicle has to make frequent requests to the RSU,thus this will be inefficiency and will cause a lot of computational cost.Hence,Freudiger et al.[12]proposed a novel scheme to solve Lu et al.’s problems by combining mix-zones with anonymous certificates in 2007.However, vehicles or RSUs still require to store massive anonymous certificates.Later, a novel privacypreserving authentication scheme based-on hash message authentication code was designed by Zhang et al.[13] in 2008.According to [13], although the anonymity is met, the management of the certificate is still a problem.In 2018,Miraj et al.[14]proposed a scalable and efficient PKI based authentication protocol to solve the problem of extra delay caused by large sized Certificate Revocation List (CRL), which still does not fundamentally address the shortcomings of PKI technology.
In order to address the certificate storage and management problems of the above schemes, some IDbased schemes are proposed.Zhang et al.[15] proposed an effective protocol by exploiting a Tamper-Proof Device(TPD),which loaded in vehicles to generate pseudonyms that protect real identities and store private keys.However, Lee et al.[16] pointed out that Zhang et al.’s protocol [15] is vulnerable to replay attacks and cannot satisfy non-repudiation, and they design an enhanced authentication protocol by using bilinear pairings.Unfortunately,Bayat et al.[17]found that Lee et al.’s scheme [16] cannot resist impersonation attack.In order to overcome the weaknesses of[16],Bayat et al.[17]proposed an enhanced authentication protocol in 2015.These protocols either have some security flaws or have high computational overhead, and cannot meet the requirement of performance of VANET.Li et al.[18] proposed an anonymous conditional privacy-preserving authentication scheme(CPPA)in 2019,which used message authentication code(MAC).Sandou et al.[19]proposed a lightweight authentication protocol which used public key encryption scheme in 2018 and Zhou et al.[20]proposed a lightweight pricavy-preserving authentication scheme(LPPA)in 2020.Althouth these three protocols improve the security and efficiency of the authentication protocol to some extent,they do not consider the burden of TA in large-scale network.
Recently, Chuang et al.[21] proposed a trustextended protocol, called TEAM.In TEAM, the authentication of the vehicle does not require the participation of the TA, and the TA only provides registration and system initialization services, which lead to the burden on the TA can be reduced.However,Zhou et al.[22] pointed out that Chuang et al.’s protocol[21] has some weaknesses such as insider attack, impersonation attack,suffer from privacy breach.Hence,in order to address these vulnerabilities, Zhou et al.[22] designed a novel authentication protocol based on TEAM in 2017.Unfortunately, in 2019, Wu et al.[23] revealed that Zhou et al.’s scheme [22] cannot resist identity guessing attack, impersonation attack and the user’s anonymity cannot meet.Zhang et al.[24] proposed a new CPPA scheme by using Chinese remainder theorem, called PA-CRT.In PA-CRT,TA is assisted in the task of generating and broadcasting group keys.
In 2015, Wang et al.[25] proposed a two-factor lightweight privacy-preserving authentication scheme by using user identity and biometric information.Some work[26–29]also suggested using smart cards for identity authentication.Paruchuri et al.[26]used smart card to authenticate messages in the VANET,and the smart cart stores the user’s private information(e.g.,real identity,public and private key,corresponding certificate and etc).Wong et al.[27]provided an authentication protocol that uses a hash function to authenticate users in a wireless sensor network.In 2017,Ying et al.[28] proposed a new protocol for using smart cards to authenticate users in the Internet of Vehicles,but Chen et al.[29]found Ying et al.’s protocol[28] is vulnerable to offline identity guessing attack,session linking attack and replay attack, thus Chen et al.[29]proposed an enhanced security authentication scheme that also utilized smart card in 2019 for the problems in[28].
In order to address the above problems,we proposed an efficient three-factor privacy-preserving authentication and key agreement protocol for Vehicular Ad-Hoc Network, which uses RSU to assist TA to complete the authentication,greatly reducing TA’s burden.Our protocol is also a three-factor authentication protocol.Each legal user can get a smart card containing the user’s biological information,which greatly improves the security of the protocol.In addition, our protocol can provide malicious users revocation in a multidriver environment.The main contributions of our work are given as follow:
• First, our protocol allows TA to undertake only a few computing tasks during the authentication process.The RSU assists the TA to complete user authentication,which greatly reduces the computational cost on the TA.
• Second, our protocol supports malicious user tracing and revocation, and enabling tracing and revocation of malicious users in a multi-driver environment.
• Third, we formally analyze the security of our protocol under the random oracle model and also give informal analysis.
• Fourth,we analysis the performance of our protocol and compare it with related work,proving that our protocol can provides better performance on many performance metrics than the related work.
The remainder of the paper is organized as follow:In Section II, preliminaries is introduced.Section III provides a detailed description of the proposed protocol.In Section IV,we discussed formal and informal security analysis.A performance analysis and comparison is shown in Section V.Finally, we conclude the paper in Section VI.
II.PRELIMINARIES
2.1 Elliptic Curve Cryptography
Elliptic Curve Cryptography(ECC)is widely used in authentication schemes in many different scenarios,including authentication schemes in VANET.In this paper, we also use ECC to obtain a secure protocol,thus we need to briefly review the ECC below:
LetGbe a cyclic additive group, whose order ispand generator isP, wherepis a large prime number andP ∈G.
LetEbe an elliptic curve equation:y=x3+ax+bmodp,wherea,b ∈R.
Next, we introduce two well-known computational problems that we use to design a secure authentication protocol.
• Elliptic Curve Discrete Logarithm Problem(ECDLP): If it is known that the pointsPandQon theEsatisfy the relationshipQ=kP,it is very difficult to calculate integerk ∈R
• Elliptic Curve Computational Diffe-Hellman Problem (ECCDHP): If it is known that the two pointsQandRon theEsatisfy the relationshipQ= mP, R = nP, it is very difficult to calculate the pointmnP, wherem, n ∈Rare two unknown integers.
For the purpose of the formal security proof in Section IV, we define the probability of an adversaryAsolving ECCDHP in polynomial timetasIn fact,this probability is so small that it can be neglected.
2.2 Fuzzy Extraction
In our protocol,in order to process the user’s biological information,we use a fuzzy extractor,thus we need to briefly introduce the fuzzy extractor.
Given a biometric valueBas input,the fuzzy extractor can extract a uniform random stringαfrom it, so the fuzzy extractor is a key generation technique.This is a technique of error tolerance,that is,if the two biometric values of input are slightly different(the Hamming distance between the two is less than or equal to a predetermined tolerance threshold),the stringαextracted from the two biometrics are the same[30].This technique consists of the follwing two procedures:
•Gen(.) is a generation procedure.In this procedure,based on the biometric informationBinput by the user,a biometric keyαand a public stringβcan be extracted from it.That is:
(α,β)=Gen(B)
•Rep(.) is a reproduction procedure.In this procedure,αcan be recovered according to the biometric informationB′close toBinput by the user and the corresponding public stringβ.That is:
α=Rep(B′,β)
Also, the fuzzy extractor also has some related definetions[31]:
• There is a high probability that the distance between two biometric valuesBandB′from the same people is low,which can be expressed as:
Pr[dis(B,B′)≤σ]≥1−εfn
whereσis the predetermined tolerance threshold and the“false negative”probability isεfn.
• There is a high probability that the distance between two biometric valuesB1andB2from the two persons is high,which can be expressed as:
Pr[dis(B1,B2)<σ′]≥1−εfp
whereσ′ <σandεfpis the probability of“false positive”.
III.PROPOSED PROTOCOL
In this section, we first introduce the network model and threat model used in our protocol, and then describe our protocol in detail.Our proposed protocol consist of six phases: system initialization phase,user registration phase,user login phase,user authentication phase, malicious user tracing and revocation,password and biometric key change phase.The first two phases are performed in secure channels,the others are performed in insecure channels.Table 1 illustrates the symbols in our protocol.

Table 1. Definition of notations.
3.1 Network Modle
The network model of our protocol is shown in Figure 1.
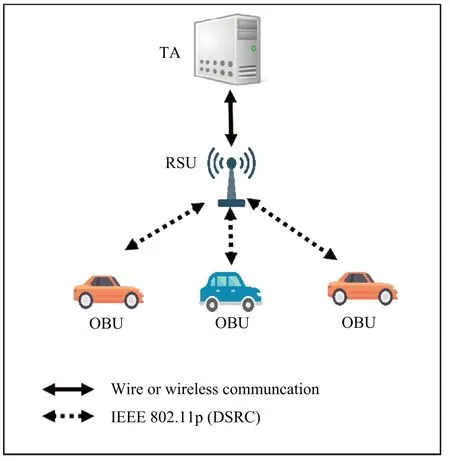
Figure 1. The network model of our protocol.
• TA is a fully trusted entity that provides system initialization and registration for users.It knows the location and the identity of all RSUs.It can also load system private key into each RSU by secure channel.
• RSU is located along the road and is equipped with Tamper-Proof Device (TPD).It cannot be compromised.The TPD is responsible for storing data and is able to perform encryption operations.RSU can communicate with TA via wireless or wired channel, and communicate with OBU via the DSRC protocol.Each RSU is able to share all traffic-related information with authenticated OBUs within its area and provide services for legitimate OBUs through the session key obtained in the authentication.
• OBU is a vehicle equipped various devices,which can communicate with the RSU via the DSRC protocol.But before the OBU communicates with the RSU, the vehicle user must be authenticated,and then the OBU and RSU obtain a session key to communicate with each other.
3.2 Threat Model
The threat model used in our protocol is as follows:
• An attacker can eavesdrop on messages on insecure channels and can modify or replay messages,as well as inject new messages.
• If an attacker gets the user’s smart card, he can extract all the information from the smart card.
• All authentication data in the RSU are stored in the TPD, which means after the adversary captures the RSU,it cannot extract any authentication data from it.
3.3 Our Proposed Protocol
3.3.1 System Initialization Phase
In this phase,TA performs the following process.
• The TA selects a cyclic additive groupGwith a order ofpand a generator ofP.
• The TA selects an elliptic curveE:y=x3+ax+bmodp,wherea,b ∈R.
• The TA generates a random numberxas the private key and calculates thePpub=xPas the public key,and publishes the public key.
• The TA loads its private keyxinto the RSU’s TPD by secure channel.
3.3.2 User Registration Phase
In this phase,the userUigoes to the TA to perform the following process to complete the registration.Thus,this phase is secure.
• TheUiimprints his biometric informationBion a special device to obtain (αi,βi) =Gen(Bi)through the fuzzy extractor and provides his own identityIDiand passwordPWito the TA.
• The TA generates a random numberyifor eachUi, then TA calculatesPIDi = h(IDi,yi),Ai =h(IDi, x)⊕αi,Ci = h(IDi, PWi,αi)⊕yi,Di =h(PWi,yi,αi),Ei=PIDi ⊕Ai.
• The TA gives theUia smart card with tuple
3.3.3 User Login Phase
In this phase,The OBU verifies the legitimacy of users through the following process.
• The userUiinserts theSCinto the OBU, enters theandand imprints his or her biometric informationThe fuzzy extractor extracts().
• TheSCcalculates
• TheSCverifiesIf the equation holds,the login is successful and theSCcalculatesand then user authentication will begin.Otherwise,theSCterminates the process and theSCsets an allowable error threshold to enhance security.Once the number of incorrect entries reaches the threshold, it will no longer accept any input from the user.
3.3.4 User Authentication Phase
In this phase, the OBU and the RSU can be mutually authenticated and generate s secure session key for data communication in the current session during the authentication process.Table 2 shows the process.The steps are as follows.
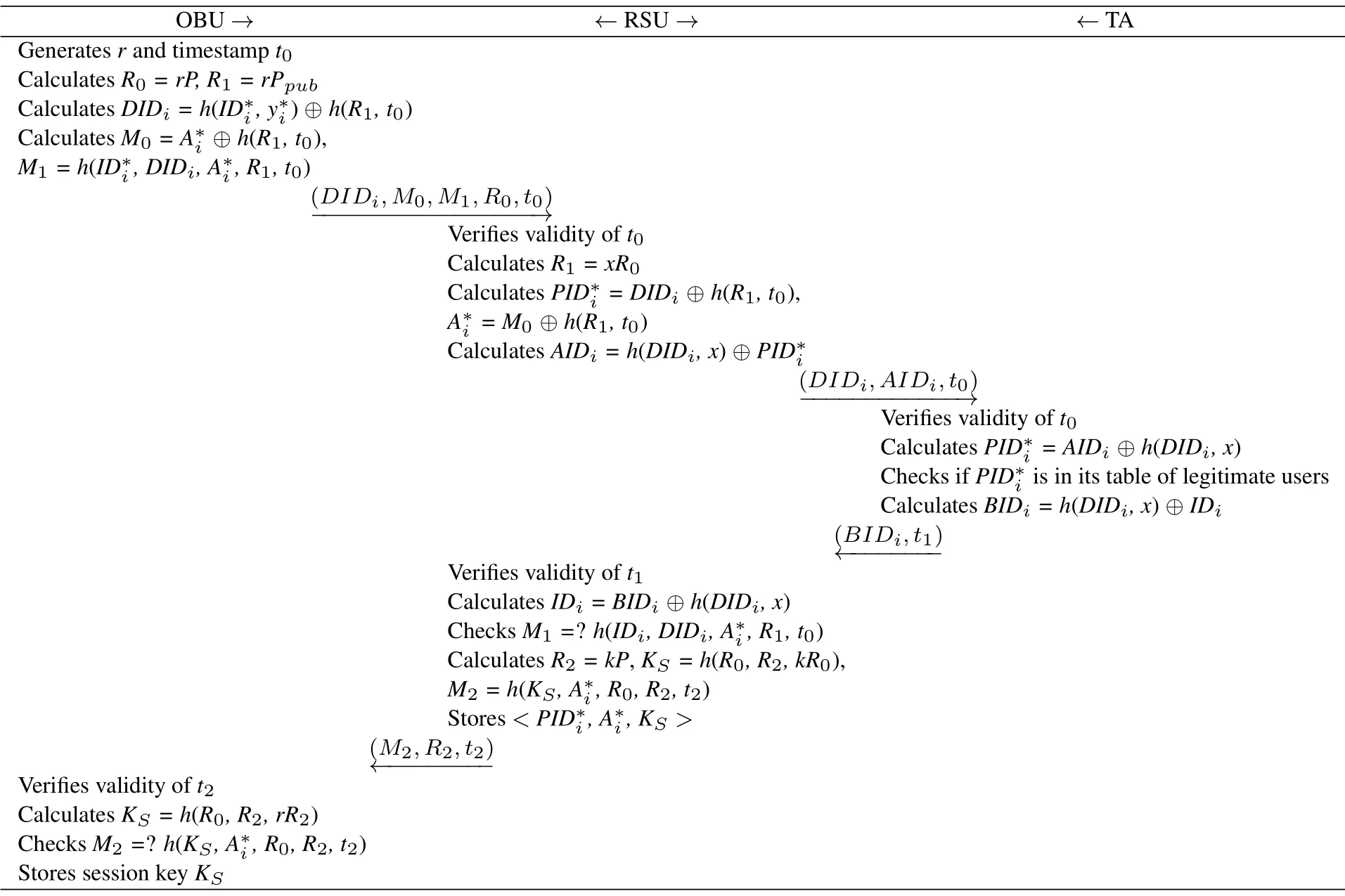
Table 2. The user authentication phase of our protocol.
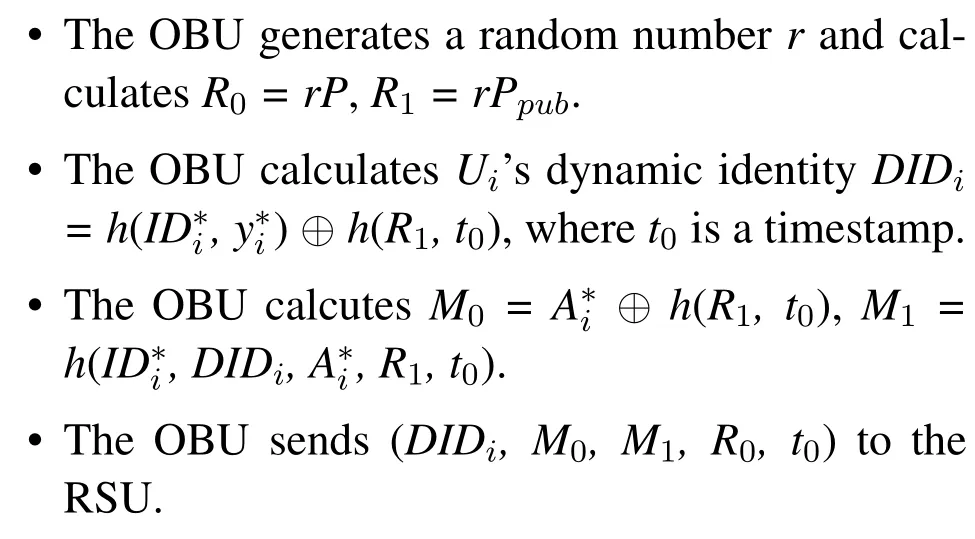
Step 1: OBU→RSU: (DIDi, M0, M1, R0, t0), the OBU performs as follows.
Step 2: RSU→TA: (DIDi, AIDi, t0), the RSU performs as follows.
• When the RSU receives message from the OBU attr1, the RSU must verifies that the received message has expired.Iftr1- t0≥∆t, abort the process;otherwise,continue.
• The RSU calculatesR1=xR0.
• The RSU calculates(R1,t0),0⊕h(R1,t0).
• The RSU calculatesAIDi=h(DIDi,x)
• The RSU sends(DIDi,AIDi,t0)to the TA.
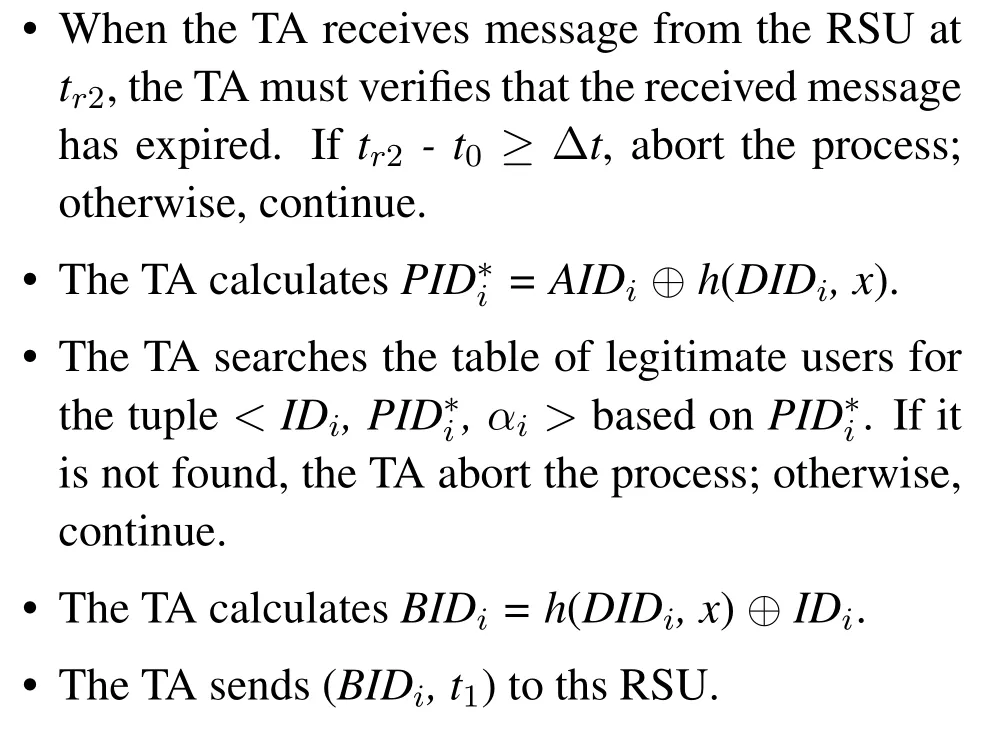
Step 3: TA→RSU: (BIDi, t1), the TA performs as follows.
Step 4:RSU→OBU:(M2,R2,t2),the RSU performs as follows.

Step 5: The OBU performs as follows.
• When the RSU receives message from the RSU attr4,the OBU must verifies that the received message has expired.Iftr4- t2≥∆t, abort the process;otherwise,continue.
• TheSCcalculatesKS =h(R0,R2,rR2).
• TheSCverifiesM2=?h(KS, , R0, R2, t2).If the equation holds, mutual authentication is successful,andKSis used as the session key.
3.3.5 Malicious User Tracking Phase
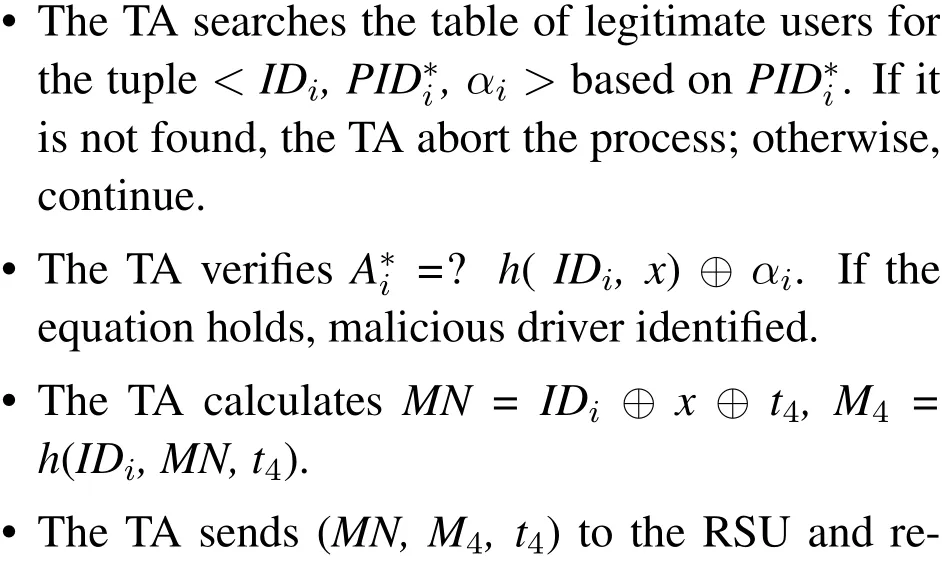
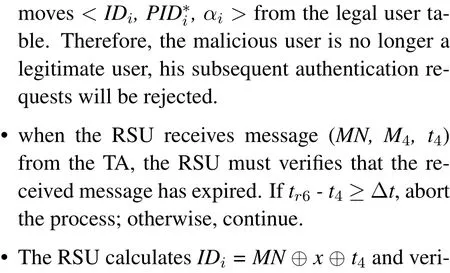
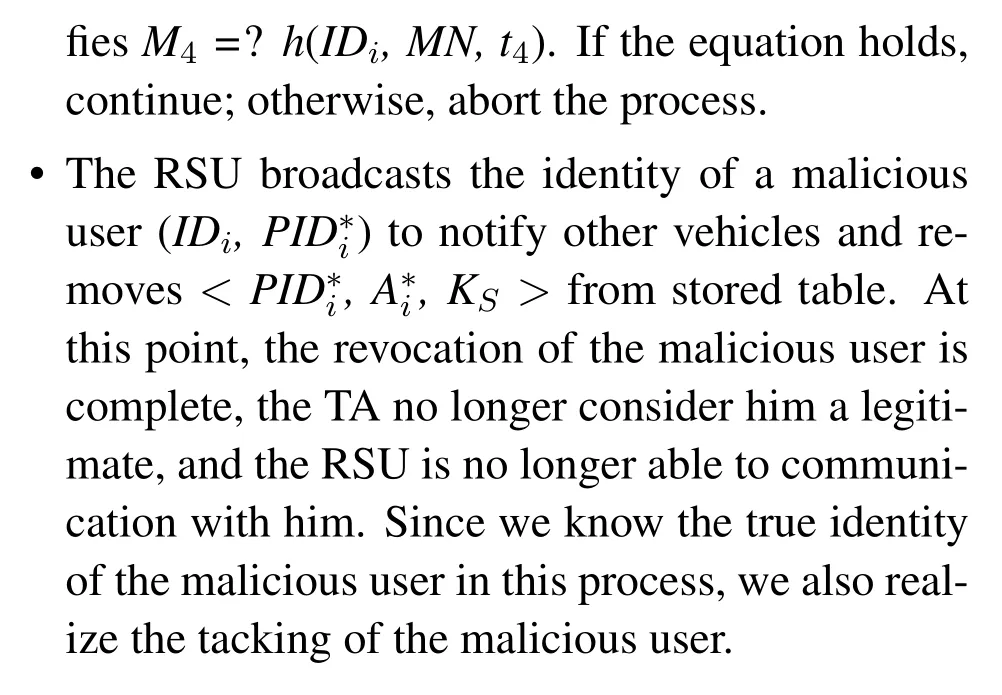
In this phase,once a vehicle is determined to be malicious,the following process will be performed to track the malicious vehicle.Table 3 shows the process.

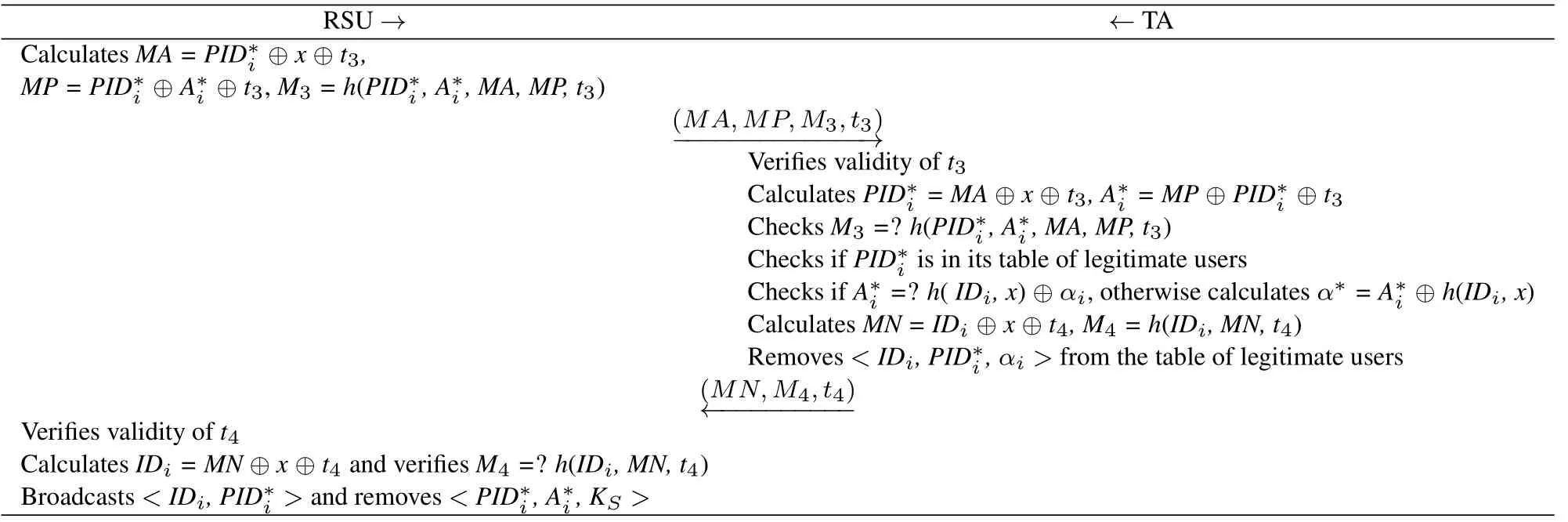
Table 3. The malicious user tracking phase of our protocol.
3.3.6 Password And Biometric Key Change Phase
In this phase,users can change their own password or lend their vehicle to others by changing their biometric key.The steps are as follows.
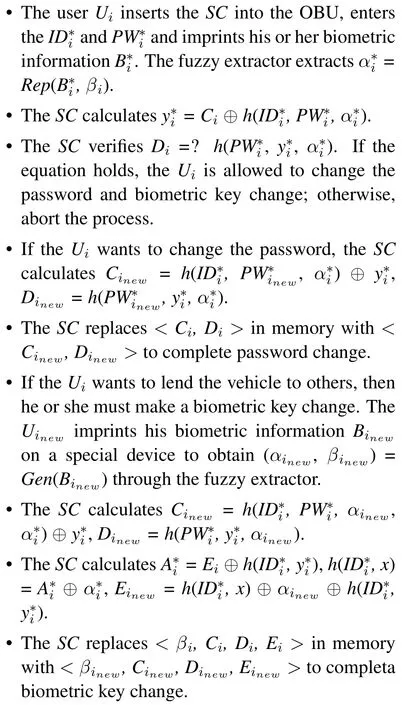
There may be questions about how to perform a new malicious users tracing and revocation after changing the biometric key.As described in Section 3.3.5,when performing malicious users tracing and revocation,the TA will find the user’s registered information< IDi,, αi >.Here, we believe in the assumption that once a user(owner)lends his car to someone else,then he must know and trust this person very well,thus the owner can provide enough information to track this new driver.
IV.SECURITY ANALYSIS
Our security analysis is divided into three subsections.In the first subsection,we introduce a security model.Based on this security model, we give formal proof of our protocol in the second subsection.Finally, we make a informal analysis of some other security requirements in the third subsection.
4.1 Security Model
Based on[31,32],we modify some details and make the formal proof for our protocol.
Firstly, we define the three participants in our protocol P: a userU, a RSUR, and a TA.If we do not need to distinguish them, they can all be represented asI.Each participant has many instances, and each instance has a number.For example,Uiis thei-thinstance ofU.So we can infer the concepts ofRj,TAk,It.Each instance is regarded as an oracle, and each oracle has three different states: if the input is correct,it is“accept”;if it receives an error message,it is“reject”;if there is no response to the input message,the oracle becomes⊥.
The abilities of the adversaryAare described below.
• Execute (Ui,Rj, TAk): This query simulates the entire authentication phase betweenUi,Rj, TAk.Acan obtains the transcript in the process.
• Send(Ik,Ij,m): This query simulates the process thatIjreceives a message fromIk.Ifmis correct thenIjwill make a response according to P.Otherwise,the query is aborted.
• Reveal (Ij): After this query,Acan obtains the session key ofIj,ifIjis partnering.
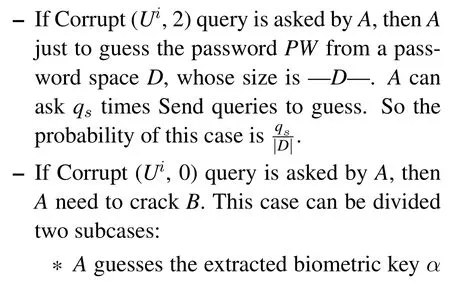
• Corrupt(Ui,z):This query simulates the situation of user’s information lost.This situation can be divided into three cases.
–z=0:This situation denotes user’s passwordPWis known by theA.
–z=1: This situation denotes all information in theSCis known by theA.
–z= 2: This situation denotes user’s biometricsBis known by theA.
• Corrupt(Ij): This query simulates thatAcan getIj’s all secret information.
• Test (Ik): This query is forUand RSU.Amust select a session to challenge.IfIkis accepted and is fresh which is explained below, the simulator chooses an unbiased coinb.Ifb= 1, the simulator returns the real session key.Otherwise, the simulator returns a random string with the same length as the session key.
Before we prove,we need to make some definitions.
Definition 1.Partnering: If two instances Ui and Rj are in the“accept”state and a session is established,there will be some elements: pidUi or pidRj is partner’s identity, sidUi or sidRj is session identity, and skUi or skRj is session key.If and only all the equations pidUi = Rj, pidRj = Ui, sidUi = sidRj, skUi =skRj hold,we say that Ui and Rj are partners.
Definition 2.Freshness: It(Ui and Rj)is fresh unless any of following happens:
•A Reveal(It)or Reveal(pidIt)happens.
•Before Test(It),a Corrupt(It)or Corrupt(pidIt)has been queried.
•The A queries all the kind of Corrupt(Ui,z).

4.2 The Formal Security Proof
Theorem 1.G is an elliptic curve cycle additive group on E with a large prime order p.D is user’s password space and |D| is D’s size.l is the length of the biometric key generated by the fuzzy extractor, and ls isthe length of the output value of the hash function.The probability of “false positive” for the fuzzy extractor is εfp.A is attacker andPis our protocol.A has the opportunity to break our protocolPwith qs Send queries,qe Execute queries and qh Hash queries.Then we have:
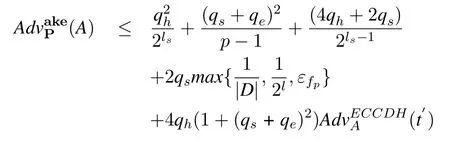
where t′ = t + (6qe + 4qs)Tm and Tm is the time for one scalar multiplication in G.
Proof.We use six gamesGito prove Theorem 1.Sun(1≤n ≤5)represents the event that adversaryAsuccessfully guesses thebin the Test query.Since there is only one user in our model,Adoes not need to guess the identity of the user.The details are described below.
• GameG0: This Game is the real protocol model with random oracle.We see that2Pr[Su0] - 1.WhenAspends queries or time exceeding the maximum limit or the game is stopped or aborted without response,a randomb′is selected.
• GameG1: This Game simulates all oracles,there are three lists are used in the proof.
–Lh: This list stores the answers to hash queries.
–LA: This list stores records ifAasked hash query.
–LP: This list stores transcipts in the P.
SoG1andG0can’t be distinguishable,we have:
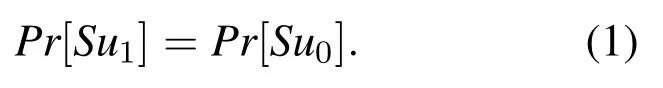
• GameG2: In this Game,various collisions in our protocol are simulated.Based on the birthday paradox, there are two different collisions in our protocol,we show them below:
– The maximum probability of the collisions of the hash function results is
– The collisions of random numbers have the probability.
SoG2andG1can’t be distinguishable unless the collisions happen.We have:
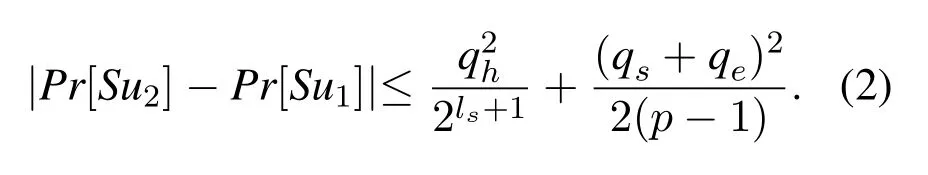
• GameG3:This Game simulates the probability ofAforging messages without random oracles.The simulator should check if((ID,*),DID),((t0,*),*),((ID,*),A∗),((ID,DID,A∗,*,t0),M1),((DID,*),*),((*,A∗,R0,R2,t2),M2)ϵLAand all messagesϵLP.If any of above fails, the query will be aborted.The probability for forging ((ID, *),DID), ((t0, *), *), ((ID, *),A∗), ((DID, *), *) are allandfor forging ((ID,DID,A∗, *,t0),M1), ((*,A∗,R0,R2,t2),M2).Thus,G3andG2can’t be distinguishable unless the above checks happen.We have:
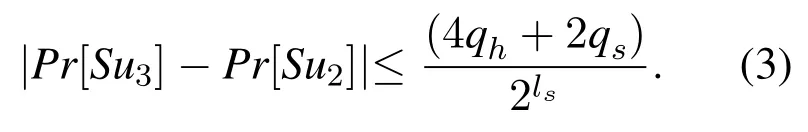
• GameG4:This Game combine the ECCDH problem and random oracles into the proof.When the session key is obtained byA, the security of the protocol P is broken.This meansAshoule ask((rP,kP,rkP), *) and theLAshoule contain the corresponding record.In order to discuss the security of the three-factor authentication protocol,we let theAget two factors at most.If theAget thePWandB,it is useless.So Corrupt(Ui,1)is necessary step.This game simulates two kinds of guessing attacks, the first is online and contains two cases, and the second is offline and contains one case.

So we can denoted the probability of off-line attacks as follow.
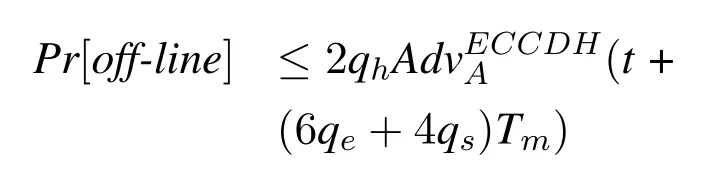
We denotet′ =t+(6qe+4qs)Tm,we have:
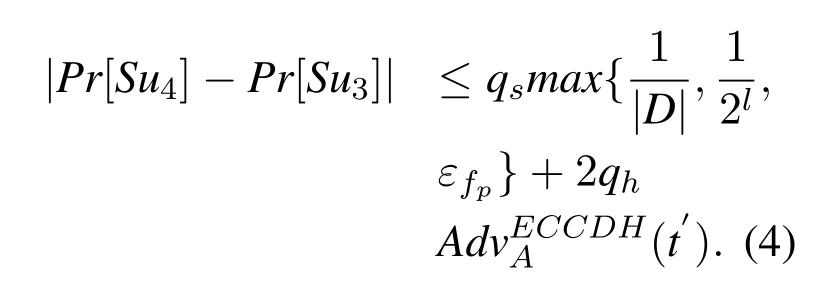
• GameG5: This Game consider the Semantic Security.Due toAcan only ask Corrupt (It) after Test(It)according to the definition ofFreshness,thus only previous simulations are be affected.Once the answers queried byAare from the old transcripts,then we are back in the off-line guessing attack simulation ofG4.If we can find (1,(rP,kP,rkP))ϵLAand the probability for gettingrPandkPin the same session is.We have:
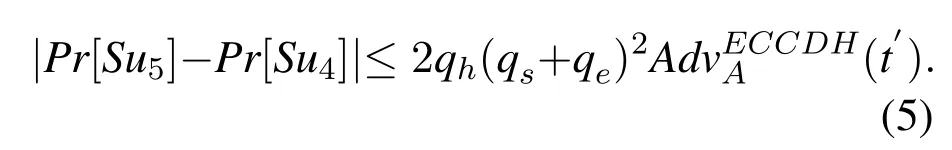
ThenAhas no advantage in guessingbandPr[Su5]=.
Therefore, we can deduce Theorem 1 from the above analysis:
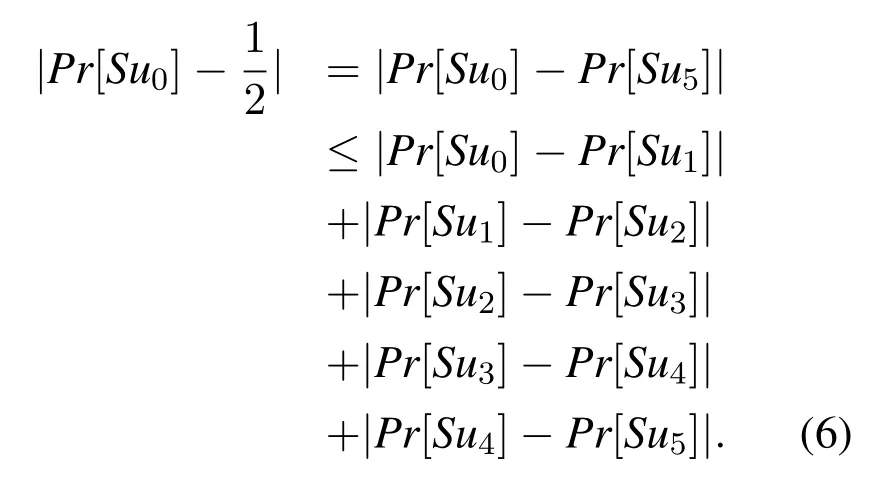
Hence,fromG0we will have:
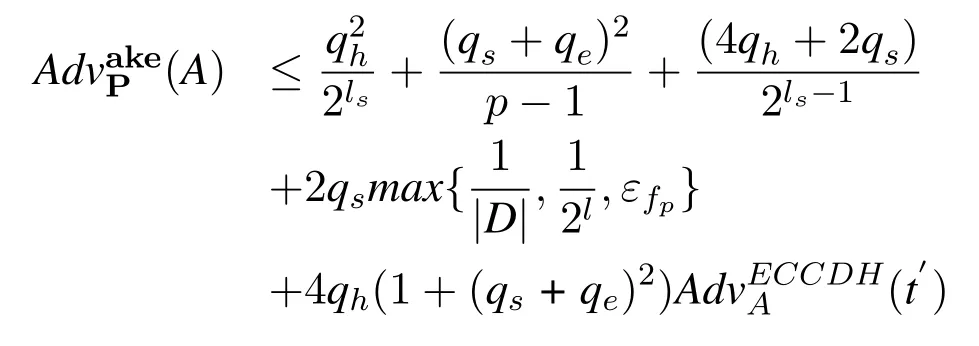
4.3 The Informal Security Analysis
4.3.1 Anonymity and Untraceability
In our protocol,the true identityIDiof the user is secure, because we only transmit the pseudo dynamic identity in the public channel.If the adversary intercepts the messagedue to theis protected by a one-way hash function and random numbers,the adversary cannot recover the user’s true identityfrom the intercepted message unless he breaks the hash function and guesses the random numbers.Thus, user anonymity is provided by our protocol.Furthermore, because we use random numbers,all messages transmited during the entire authentication process change every time, so the abversary can’t track a certain user.
4.3.2 Perfect Forward/Backward Secrecy
Our protocol provides perfect forward and backward secrecy because of the use of random numbers.The session key isKS = h(R0, R2, kR0), there are three paramatersR0=rP,R2=kPandkR0in it, and these three parameters involve three random numbers.Each time the session key is generated, then the three new random numbers are generated, so even if the current session key is obtained by the adversary,the previous and subsequent session keys are secure.
4.3.3 Resisting Replay Attack
In our protocol, all messages (DIDi, M0, M1, R0, t0),(DIDi, AIDi, t0), (BIDi, t1) and (M2, R2, t2) will be changed every time due to the existence of random numbers or timestamps.If an adversary attempts to launch a replay attack, the information sent will not pass the verification of any entity.Hence,our protocol resists replay attack.
4.3.4 Resisting Offline Password Guessing Attack
According to the user registration phase in Section 3.3.2, some password-related parametersCi =h(IDi, PWi, αi)⊕yi,Di = h(PWi, yi, αi) are stored in theSC.Because thePWiis masked with random numberyiand biometric keyαi,it is impossible for an adversary to guess the password.Thus,our protocol is secure for offline password guessing attack.
4.3.5 Resisting Impersonation Attack
When an adversary wants to imitate a legitimate userUito request authentication,he must generate a legitimate authentication request message(DIDi, M0, M1,R0, t0), whereDIDi = h()⊕h(R1, t0),M0(R1, t0),M1=h(1, t0).However,the adversary does not knowand cannot create a legitmate authentication request message,thus our protocol can resist impersonation attack.
4.3.6 Resisting Smart Card Loss Attack
For the user, the user cannot guarantee that the smart card will not be lost.If the user’s smart card is lost and obtained by an adversary, the information< G,p, P, βi, Ci, Di, Ei, h()>in the smart card may be extracted by the adversary.In this case, if the adversary wants to log in through a smart card,he must simultaneously guess the user’sIDi,PWiand obtain the biometric keyαiin polynomial time,which is impossible.Thus,he cannot log in successfully.Therefore,our protocol prevents smart card loss attack.
4.3.7 Resisting Man-in-the-middle Attack
When an adversary acts as a middleman to intercept messages (DIDi, M0, M1, R0, t0), (DIDi, AIDi, t0),(BIDi,t1)and(M2,R2,t2)in the public channel during the authentication process and modify or replace the message with own information and then forward it,the modified message cannot pass the receiver’s verification.Hence,man-in-the-middle attack is not valid for our protocol.
4.3.8 Resisting Insider Attack
During the registration phase, users go to the TA to register their key information.At this phase,the user’s password is entered in ciphertext.This makes it difficult for insider working at TA to get a user’s password and thus prevent misuse of password.As a result,our protocol is resistant to insider attack.
V.PERFORMANCE ANALYSIS AND COMPARISON
5.1 Computational Cost
In this subsection,we analyze the computational consumption of our protocol.For this purpose,we need to define the execution time of some cryptographic operations:
•Txor: the execution time required for a XOR operation.
•Tsm: the execution time required for a scale multiplication operator on ECC.
•Tsm−s: the execution time required for a small scale multiplacation operator on ECC.
•Th: the execution time required for a hash function operator.
•Tpa: the execution time required for a point addition operation on ECC.
When testing on the following hardware platform:CPU: Intel I7-4770 with 3.40GHz, Memory: 4G,OS:Windows 7,the execution time[33]of the abovementioned cryptopraphic operations is shown in Table 4.Compared with other operations,the execution time of the XOR operation is much smaller and can be ignored.

Table 4. Execution time of different cryptographic operations.
We analyze the entire authentication phase of our protocol and conclude that the total time consumed by OBU, RSU, and TA is 3Tsm+ 5Th+ 2Txor, 3Tsm+5Th+ 4Txor, andTh+ 2Txor, respectively.Table 5 shows the specific time.
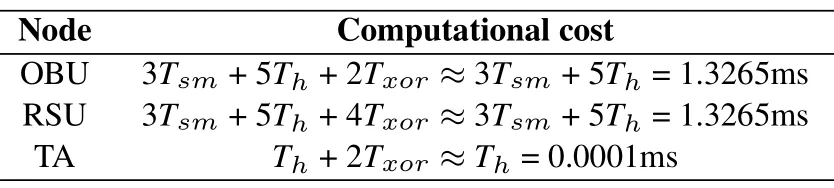
Table 5. Computational cost of our protocol.
5.2 Communication Cost
We define thath(.) used in our protocol is the SHA-256 algorithm,and the timestamps are 64 bits.In thestep 1,the OBU sends message(DIDi,M0,M1,R0,t0)to the RSU,which means that the OBU needs to send 256+256+256+256+64=1088 bits of data to the RSU.In theStep 2,the message between the RSU and the TA is (DIDi, M0, M1, R0, t0), so the data length to be sent by the RSU is 256 + 256 + 64 = 576 bits.In theStep 3, the TA sends|BIDi| + |t1|= 320 bits.In theStep 4,the RSU sends|M2|+|R2|+|t2|=576 bits.Table 6 illustrates the communication cost of our protocol.
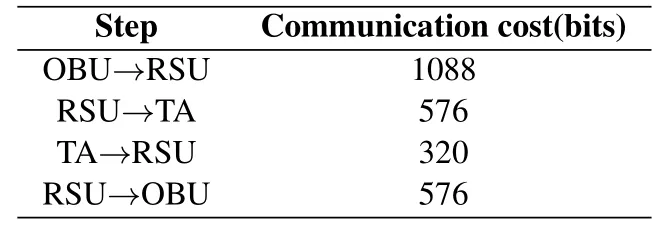
Table 6. Communication cost of our protocol.
5.3 Comparisons with Other Works
We compare our protocol with some recent works[34–37].For MAet al.[34], their three nodes are called User (U), Fog node (FN) and Cloud Server (CS).So the execution of the OBU is 3Tsm+4Th=1.3264ms,the FN is 4Tsm+ 4Th= 1.7684ms, the CS is 10Tsm+ 11Th= 4.4211ms.In the protocol of Zhonget al.[35], the execution time of the vehicle or the OBU is 3Tsm+ 7Th= 1.3267ms, the RSU is 3Tsm+ 6Th= 1.3266ms, the TA is 2Tsm+ 10Th= 0.885ms.In the procol of Cuiet al.[36], the generation and signing of the beacon (BGS), the single verification for a beacon (SVOB) and the batch verification for multiple beacons (BVMB) are the main time-consuming operations.The execution time of the BGS is 2Tsm+ 2Th= 0.8842ms, the SVOB is 3Tsm+ 7Th+ 1Tpa= 1.3285ms, the BVMB is 3Tsm+ 2Tsm−s+ 7Th+ 3Tpa= 1.3873ms.In the protocol of Alazzawi et al.[37], The execution time of the BGS is 2Tsm+2Th= 0.8842ms, the SVOB is 2Tsm+Th+Tpa=0.8859ms,the BVMB is 2Tsm+2Tsm−s+Th+2Tpa=0.9448ms.The comparison results are shown in Figure 2.Through Figure 2,we can find that our protocol has the least total computational cost and the computational cost of TA is almost zero.
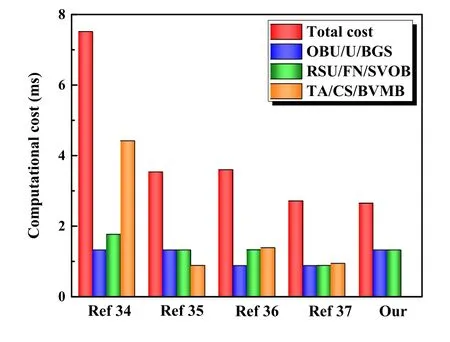
Figure 2. The comparison of computational cost(The computational cost of TA in our protocol is almost zero).
5.4 Comparisons of Communication Cost


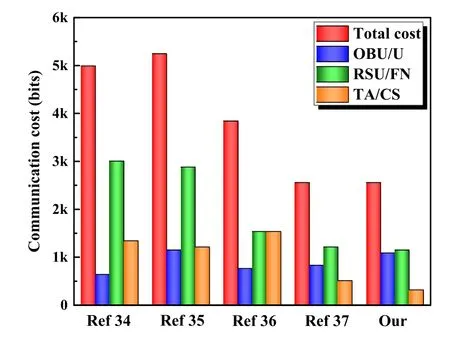
Figure 3. The comparison of communication cost.
5.5 Comparisons of Security Properties and Functions
As for security,although MA et al.[34]can resist various attacks,it does not meet the conditions of privacy.Once the user becomes malicious, it cannot track the malicious user and it spends more time than other solutions.Zhong et al.[35]proposed a conditional privacypreserving authentication protocol,it can resist various attacks and can provide tracking for malicious users.The burden of TA or CS will increase significantly with the increase of vehicle density, and it is easy for TA to reach the bottleneck of computing resources,which leads to unbearable delay in message transmission in VANET.Cui et al.[36]assumes that RSU and TA can communicate via a secure transmission channel, which is an inappropriate assumption.Comparison of security properties and functions shown in Table 7.
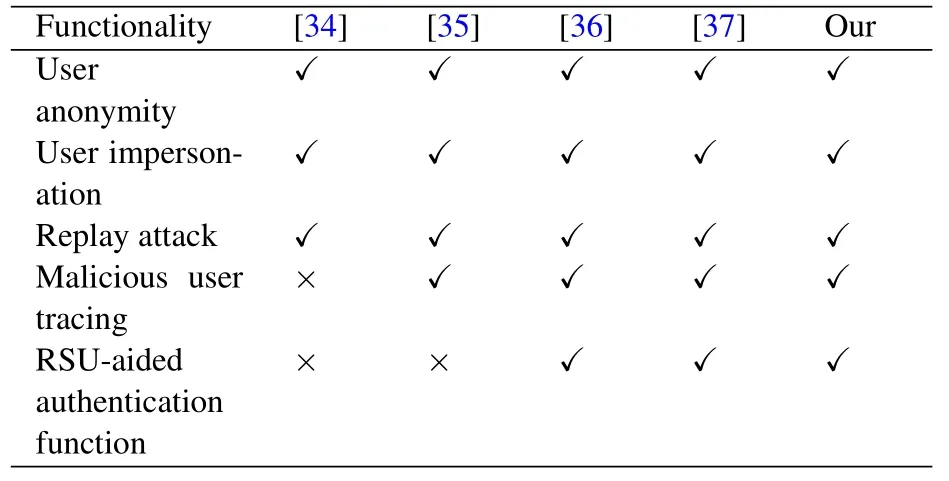
Table 7. The Comparison of security properies and functions.
5.6 Comparisons of Message Loss Radio and Delay
In this subsection, we use network simulator ns-2 to build VANET scenario to evaluate the message loss ratio and the message end-to-end delay of our protocol,and compared it with related work.Since our target environment is a large-scale network, we simulated a traffic scenario with a high vehicle density.Within the communication range of an RSU,30-300 vehicles can be associated with it.IEEE 802.11p to simulate the transmission protocol,and the bandwidth of the channel is 6Mb/s.
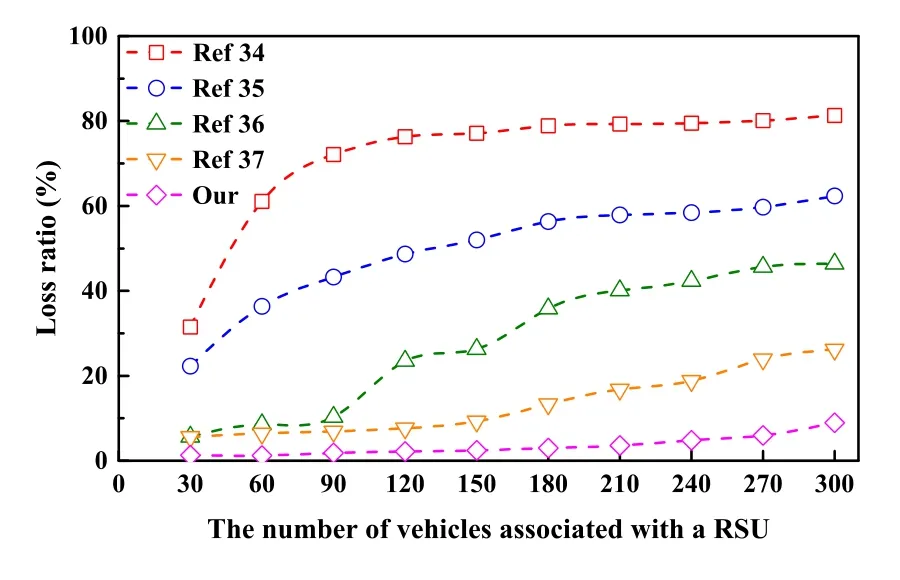
Figure 4. The comparison of Average loss ratio.
5.6.1 Message Loss Ratio
The average message loss ratio(LR)is calculated according to the formulate defined in literature[13]
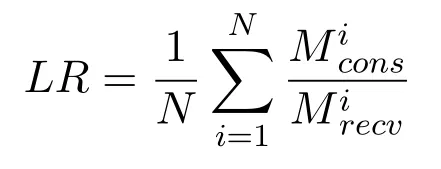
whereN,andand respectively represent the number of vehicle, the total number of messages received by the vehicle , the total number of messages consumed.We compare the proposed protocol with others work.The results are shown in Figure 4.Through Figure 4, we can observe that [34] has the highest loss ratio, and the [35], [36] rank in the middle.[37]significantly lower than the above three,but our protocol is still the lowest as the number of vehicles increases.
5.6.2 Message Delay
The average message delay(MD)is calculated according to the formulate defined in literature[13]
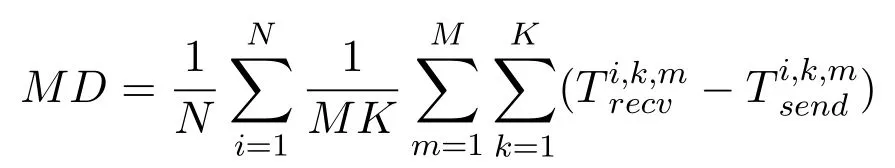
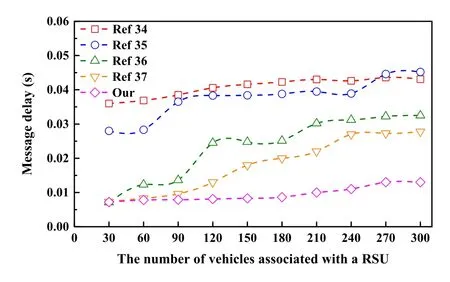
Figure 5. The comparison of Average message delay.
whereN,M,K,andrespectively represent the number of vehicles, the number of message sent byvehiclei, the number of adjacent vehicles within DSRC communication range ofvehiclei, the moment ofvehiclekreceives themthmessage fromvehiclei,and the momentvehicleisends themthmessage tovehiclek.The comparison results are shown in Figure 5.Through Figure 5,we can see the performance gap between[34]and[35]in message delay is small,and[36]and[37]is significantly lower than[34]and[35], but with the increase in the number of vehicles,[36]and[37]will rapidly surpass our scheme in message delay,and our protocol still maintains the lowest message delay.
VI.CONCLUSION
In order to meet the requirements of the high-density vehicular ad-hoc network environment, we propose an efficient three-factor privacy-preserving authentication and key agreement protocol.The RSU assists in completing the authentication of the vehicle during the authentication phase,the TA performs one hash operation and two XOR operations during the authentication phase,which greatly reduces the computational cost of the TA.
We demonstrates our protocol excellent security through formal and informal security analysis.Compared with previous studies,our work emerges advantages and superiorities in the following aspects: computational cost, communication cost, security properties and functions,message loss ratio,and message delay.In conclusion, our protocol is ideal for VANET due to its high efficiency and security.
ACKNOWLEDGEMENT
This work was supported by the National Natural Science Foundation of China under Grant No.61772185.
- China Communications的其它文章
- An Overview of Wireless Communication Technology Using Deep Learning
- Relay-Assisted Secure Short-Packet Transmission in Cognitive IoT with Spectrum Sensing
- Frequency-Hopping Frequency Reconnaissance and Prediction for Non-cooperative Communication Network
- Passive Localization of Multiple Sources Using Joint RSS and AOA Measurements in Spectrum Sharing System
- Specific Emitter Identification for IoT Devices Based on Deep Residual Shrinkage Networks
- Primary User Adversarial Attacks on Deep Learning-Based Spectrum Sensing and the Defense Method

