Integration of Communication and Computing in Blockchain-Enabled Multi-Access Edge Computing Systems
Zhonghua Zhang,Jie Feng,Qingqi Pei ,Le Wang,Lichuan Ma
1 Shenzhen HTI Group Co.,Ltd,518040,Shen Zhen,China
2 State Key Laboratory of ISN,School of Telecomm.Engineering,Xidian University,Xi’an,710071,Shannxi,China
3 Shaanxi Key Laboratory of Information Communications,Xian University of Posts and Telecommunications,Xi’an 710121,China
4 School of Computer Science,University of Guelph,Guelph,Ontario,N1G2W1,Cananda
Abstract: Blockchain and multi-access edge computing (MEC) are two emerging promising technologies that have received extensive attention from academia and industry.As a brand-new information storage, dissemination and management mechanism,blockchain technology achieves the reliable transmission of data and value.While as a new computing paradigm, multi-access edge computing enables the high-frequency interaction and real-time transmission of data.The integration of communication and computing in blockchain-enabled multi-access edge computing networks has been studied without a systematical view.In the survey, we focus on the integration of communication and computing, explores the mutual empowerment and mutual promotion effects between the blockchain and MEC, and introduces the resource integration architecture of blockchain and multi-access edge computing.Then, the paper summarizes the applications of the resource integration architecture,resource management,data sharing,incentive mechanism, and consensus mechanism, and analyzes corresponding applications in real-world scenarios.Finally,future challenges and potentially promising research directions are discussed and present in detail.
Keywords:blockchain;multi-access edge computing;mutual empowerment;network architecture
I.INTRODUCTION
According to Cisco’s forecast, the number of devices connected to the Internet will increase to 27.1 billion by 2021, and the amount of data generated every day will reach 847 ZB.Traditional cloud computing systems use remote super integrated cloud servers to process uploaded data,thereby meeting the computing requirements of applications.With the rapid development of computer technology and the mobile Internet,new applications, such as autonomous vehicles, virtual reality (VR) and remote surgery, with ultra-low latency,low power consumption and a high Quality of Service (QoS) have gradually emerged [1–3].However, the remote transmission and large energy consumption of cloud computing make it difficult for the centralized processing mode of cloud computing to be applied to these new application scenarios.Therefore,the concept of multi-access edge computing was proposed[4–9].
Multi-access edge computing (MEC), as a supplement to cloud computing, relocates cloud computing capabilities to the edge of the network, enabling mobile devices to run these applications at the edge of the network.Similar to cloud computing,multi-access edge computing can provide computing capacity and data storage for services.multi-access edge computing has the characteristics of location awareness, low latency and support for heterogeneity.In particular,multi-access edge computing can provide good performance for computing-intensive and time-sensitive applications[10].However,due to the real-time,complexity,and heterogeneous nature of multi-access edge computing services,service migration can be attacked by malicious nodes.Therefore,the literature[11]emphasizes that data security and privacy are two of the research focuses of multi-access edge computing.
Blockchain is a decentralized distributed ledger database based on a peer-to-peer network.Blockchain is the underlying support technology of “virtual currency”, such as Bitcoin, and therefore it has received extensive attention from industry and academia [12–16].In a blockchain,any peer entity can conduct free transactions, participate in the forwarding and verification of transactions,and jointly maintain an orderly ledger of blocks containing transactions.
The decentralization,immutability,and openness of a blockchain can solve the security problems faced by multi-access edge computing.In addition,blockchain also plays an important role in other fields, such as medical care,logistics,smart cities,and the smart Internet of Things[17–20].Although the advantages of a blockchain make its application in other fields convenient, it still has a serious flaw, that is, its limited scalability; therefore, its application in these fields is still subject to some constraints[21].
To improve the performance gain of a blockchain,sufficient multi-access edge computing resources can be used to maximize its scalability.Therefore, by integrating the advantages of blockchain and multiaccess edge computing,a secure and reliable network architecture that combines network access, control,storage and computing can be constructed.Specifically, off-chain storage and off-chain computing at the edge can provide scalable storage and computing for a blockchain system.Therefore, combined with the resources and capabilities of multi-access edge computing, the serviceability of the blockchain can be reliably guaranteed; furthermore, combined with the immutability, transparency, openness, decentralization and traceability of the blockchain, the transaction certificate of multi-access edge computing can obtain complete protection and anticounterfeiting evidence.This article studies the integration of multiaccess edge computing and blockchain technology.First,this study introduces an overview of blockchain and multi-access edge computing,and then,it explains the motivation for the integration of the two technologies.
The key contributions of the work are listed below:
• An integration of communication and computation in blockchain-enabled MEC systems is firstly given and then accompanied by a summary of integration framework is outlined.
• An overview of the integration of blockchain and MEC is then given and a summary of key characteristics of blockchain and MEC are given, respectively.
• We introduce the resource integrated architecture of blockchain and MEC and then the relevant work on the blockchain-enabled MEC is researched.
• The challenges of the integration of blockchain and MEC is investigated and outline the open research issues.
In the rest of the paper, background of the integration of blockchain and MEC is detailed in Section II.Section III introduces the general architecture of the integrated blockchain and multi-access edge computing network.Section IV introduces the current research status of blockchain and multi-access edge computing at home and abroad.Section V summarizes the challenges faced by the current integrated blockchain and multi-access edge computing system.Section VI summarizes this article.
II.OVERVIEW FOR THE INTEGRATION OF BLOCKCHAIN AND MEC
2.1 Blockchain
2.1.1 The Concept of Blockchain
Blockchain originated from Satoshi Nakamoto’s Bitcoin.As the underlying technology of Bitcoin, it is essentially a distributed ledger database of a decentralized peer-to-peer network.Blockchain provides a decentralized, trust-building paradigm that does not require the accumulation of trust.The basic principle is derived from the “Byzantine generals problem”.Blockchain technology refers to the combination of data exchange, processing and storage technology formed between multiple participants based on modern cryptography, distributed consensus protocols, peer-to-peer network communication technology,and smart contract programming language.
2.1.2 Blockchain Architecture
The overall architecture of a blockchain system can be divided into the data layer, network layer, consensus layer, incentive layer, contract layer and application layer,as shown in Table 1
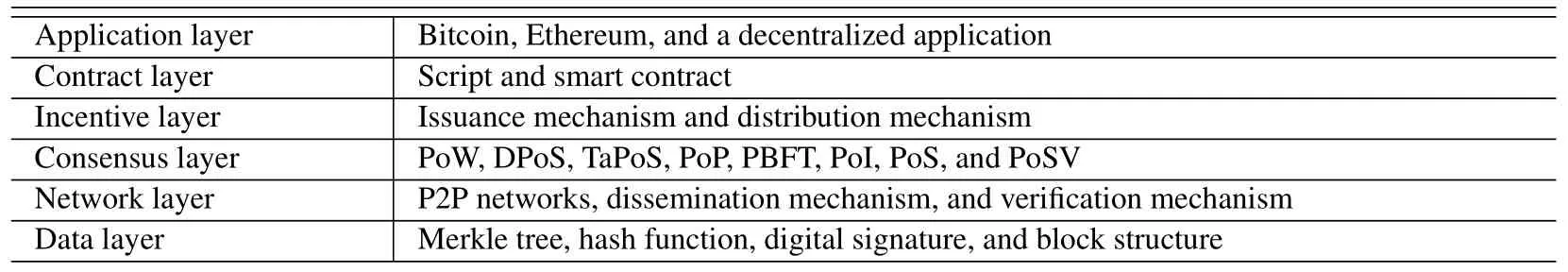
Table 1. Blockchain system architecture.
1.Data Layer
The data layer is mainly composed of the block structure, chain structure, Merkle tree, digital signature, hash function, asymmetric encryption and other cryptographic technologies.The data layer encapsulates data generated in different applications through transactions and blocks.A transaction between two individuals is packaged into a block after verification and is linked to the previous block through a block header, thereby forming an ordered linked list of blocks.The block header specifies the metadata,including the hash of the previous block, the hash of the current block,the time stamp of the block creation time,the nonce related to the upper-level mining competition and the root hash of the Merkle Tree formed by all the transactions in the block.
2.Network Layer
The network layer defines the network mechanism used in the blockchain.The goal of this layer is to propagate the data generated from the data layer.The blockchain network can usually be modeled as a P2P network, and its nodes are the participants of the network.By using the network mechanism,once a transaction is generated, it will be distributed to neighboring network nodes, and only valid transactions will be forwarded.The designed mechanism of the network layer realizes the distribution and decentralization of the blockchain and ensures that the nodes in the blockchain network can participate in accounting together.
3.Consensus Layer
The consensus layer mainly encapsulates the consensus mechanism of the blockchain.The consensus mechanism ensures that a consensus can be reached between untrusted nodes in a distributed environment.There are three main consensus mechanisms in the existing blockchain system: Proof of Work (PoW),Proof of Stake (PoS) and Practical Byzantine Fault Tolerance (PBFT).In addition, there are variants of the above consensus mechanisms,including the Delegated Proof of Stake(DPoS)mechanism,Transactions as Proof of Stake(TaPoS),the Proof of Stake Velocity mechanism(PoSV),Delegated Byzantine Fault Tolerance (DBFT) and others.In addition, there are many other consensus mechanisms, including the Proof of Importance mechanism (PoI), the Proof of Participation mechanism (POP), the Proof of Contribution mechanism(PoC)and others.
4.Incentive Layer
The main role of the incentive layer is to provide a certain reward mechanism so that nodes can actively participate in data verification and consensus, which is essential for the distributed blockchain system to maintain its overall operations without central authorization.Different blockchain systems have different incentives.In Bitcoin and Ethereum, Bitcoin and Ethereum are used as rewards to award nodes that add blocks to the chain.In addition to rewards, deposits and fines are also introduced into the blockchain system.
5.Contract Layer
The contract layer introduces programmable features into the blockchain.In the Bitcoin blockchain,scripting is used to realize the programmable characteristics of the blockchain.In most other blockchains,smart contracts are used.Smart contracts are a set of scenario-responsive procedural rules and logic that are implemented through decentralized and trusted shared script codes deployed on the blockchain.Under normal circumstances,after a smart contract is signed by all parties, it is attached to the blockchain data in the form of a program code and is recorded in a specific block of the blockchain after being propagated by the P2P network and verified by nodes.Smart contracts are digital, and they can solidify the transaction rules between accounts, facilitate the transfer of digital assets through atomic transactions,and store data.
6.Application Layer
The highest layer of the blockchain is the application layer.With its characteristics, blockchain technology can be applied to many fields,including cryptocurrency, the Internet of Things (IoT), smart cities,etc.Bitcoin, Ethereum, and decentralized applications are all typical blockchain applications.The development of these applications may change many fields, such as finance, management, and manufacturing.Furthermore, both academia and industry are seeking to deepen this technology and combine it with other different technologies, including IPFS, multiaccess edge computing, artificial intelligence, etc., toexplore infinite possibilities.
2.1.3 Key Features of Blockchain Technology
Blockchain is a data distributed ledger technology based on modern cryptography, distributed data storage, peer-to-peer communication, consensus mechanisms,smart contracts,etc.that is maintained by multiple parties.A blockchain can establish trust, perform transfers and has a transparent design,so the integrity, immutability and authenticity of data can be guaranteed.Transactions are stored in the blockchain in the form of blocks, and the block is a mechanism with a certain degree of trust that contains the confirmation, contract, storage, copy and other related information of a transaction.The key characteristics of the blockchain include decentralization,immutability,integrity, authenticity, nonrepudiation, openness and transparency,which are specifically manifested in the following aspects:
Decentralization:Decentralization is the most basic feature of blockchain technology.The blockchain no longer relies on central institutions to realize the distributed recording, storage and update of data.All the nodes in the blockchain system can participate in accounting.Damage to or an attack on any node in the entire blockchain system will not affect the operations of the whole blockchain system.
Immutability:A blockchain uses technologies such as timestamps, cryptography, and network-wide broadcasting and cannot be forcibly cracked via cryptographic means unless more than 51%of the nodes in the entire system are controlled at the same time.Otherwise,even if the data of a single node are tampered,the data on other nodes cannot be affected.Therefore,the stability and reliability of the data are guaranteed.
Integrity:The blockchain ledger is immutable,which means that it cannot be edited or deleted if data are added or a transaction has been completed.A particularly important aspect of blockchain technology that improves the integrity of data is the Merkle tree, which can ensure the integrity of the data in a blockchain.Authenticity and nonrepudiation: Authenticity and nonrepudiation mean that the origin of the transaction can be determined by the sender’s public key distribution, and the evidence of the sending action is represented by the data signature process involving the private key.
Openness and transparency:The blockchain system is open and transparent.In addition to the encryption of the private information of all parties to a transaction,the data are transparent to all the network nodes; that is, anyone or any participating node can query the blockchain data record or develop related applications through the public interface,which is also the foundation of the trustworthiness of the blockchain system.The blockchain data records and operating rules can be reviewed and traced by all the network nodes with high transparency.
Regarding their applications, blockchains are divided into public blockchains [22], consortium blockchains [23] and private blockchains [24].A public blockchain is a completely decentralized and open blockchain.Any user can anonymously read data, send transactions and confirmations, and conduct competitive accounting.Existing typical public chains include Ethereum, Bitcoin, etc.A consortium blockchain limits its management to a number of consortium members,and the permissions on the chain are established in accordance with the rules of the consortium.Existing typical consortium blockchains include Hyperledger Fabric, FISCO BCOS, Microsoft Coco,Enterprise Ethereum Alliance(EEA)and R3’s Corda.A private blockchain is used in a private organization.The permissions on the blockchain are formulated according to the rules of the private organization.Private blockchains are generally used within an enterprise.Table 2 shows a comparison of different types of blockchains.
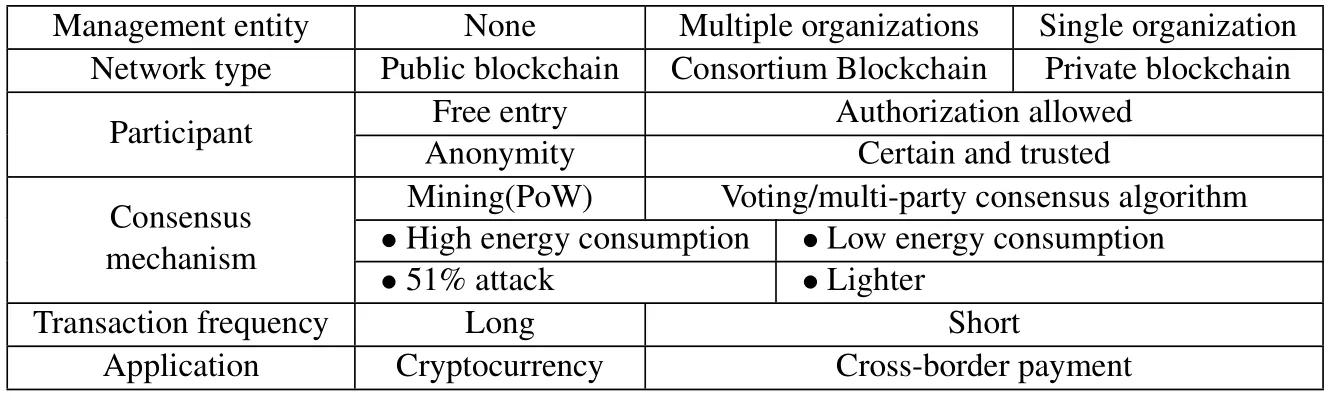
Table 2. Comparison of different blockchain types.
2.2 Multi-access Edge Computing
The concept of mobile edge computing (MEC) was first proposed by European Telecommunications Standard Institute(ETIS)in 2014.In 2016,ETIS officially changed the name of MEC to multi-access edge computing.MEC is a network architecture that provides services and cloud computing capabilities for users on the edge of the network.It is used to accelerate the rapid download of various applications on the network and allow users to enjoy intermittent high-quality network experience, with features such as ultra-low latency,ultra-high bandwidth,and strong real-time performance[25,26,6,27,28].
MEC refers to data processing close to the object or data source.Multi-access edge computing is essentially a distributed computing architecture that communicates,manages,stores and processes the massive amount of data distributed between a data source and the cloud in an effective and logical way.Edge nodes can be any computing and network resources from the data source to the cloud computing center path.In the multi-access edge computing model, edge nodes are not only data consumers,but also data producers[29–31].
In a physical and logical sense, compared to traditional cloud computing,multi-access edge computing can process and analyze data in real time at the edge of the network.Therefore, the data transmission distance is shorter, the response speed is faster, the energy consumption of the edge device is lower,and the bandwidth consumption is lower,which makes multiaccess edge computing suitable for processing computationally intensive and haptic-level responsive tasks.As terminal devices and edge servers are added to multi-access edge computing,the dependence of computing applications on cloud computing servers is reduced.Moreover,because the data are scattered at the edge of the network, the risk of a single-point failure and the data management costs can be reduced.In addition, the risk of leakage of personal sensitive information is correspondingly reduced.
2.2.1 Concept Differentiation
1.Fog Computing
The concept of fog computing has been proposed by Cisco in 2012.Subsequently,Cisco united Arm,Dell,Intel, Microsoft and Princeton University to form the OpenFog Consortium in 2015.Fog computing is defined as“a scenario where a huge number of heterogeneous (wireless and sometimes autonomous) ubiquitous and decentralised devices communicate and potentially cooperate among them and with the network to perform storage and processing tasks without the intervention of third parties.These tasks can be for supporting basic network functions or new services and applications that run in a sandboxed environment.Users leasing part of their devices to host these services get incentives for doing so” [32].MEC has the capabilities of cloud computing and the servers runs on the edge of networks.At the same time,it can execute specific tasks that traditional network infrastructure cannot perform.As the combination of MCC and MEC,fog computing is more promising in the context of the internet of Things.
2.Cloudlet Computing
Cloudlet computing was first proposed by Satyanarayanan et al.for computation offloading in 2009[33].Since the resources of the typical MCC over a Wide Area Network (WAN) are limits, the computation tasks need to be offload to resource-rice devices.It is defined as a ‘datacenter in a box’, which can be considered as a cluster of multicore computers paced anywhere.A cloudlet can realize selfmanagement, access control, connect to the Internet,and require little power.By providing computing resources for resource-constrained devices, cloudlet computing can satisfy the requirements of resourceintensive and latency-sensitive applications [34, 35].It can be further enhanced to give rise to MEC.
2.2.2 The Features of MEC
1.Low Latency
The latency to complete tasks is composed of three parts,namely computation,communication,and propagation latency.Firstly, when tasks are offloaded to MEC server, computing the tasks require a certain computation latency.However, the computation latency depends on the CPU frequency of MEC servers.Secondly,tasks are offloaded to MEC servers through wireless channel, so there exists communication latency, which relies on the transmit rate.Finally, the information-propagation distance for MEC server are typically tens of meters.Since cloud computing is employed far away from users, the propagation latency for MEC is shorter than that for MCC.Hence, MEC has low latency for processing offloaded tasks.
2.Energy Saving
Due to the limitations of physical factors, the energy stored by IoT devices is limited.However,in order to promote the rapid development of the Internet of Things, people still hope that IoT devices can perform some sophisticated tasks such as health monitoring,crow-sensing,and so on.It is a very challenge for powering the tens of billions of IoT devices, because frequent charging or battery replacement is impossible and unrealistic.By effectively supporting computation offloading, MEC technology is a promising solution for prolonging battery lives of IoT devices.In particular, for computation-intensive tasks that IoT devices cannot process, the tasks can be offloaded to MEC servers for execution through computing offloading,which can greatly reduce the energy consumption of IoT devices[36,37].
3.Privacy/Security Enhancement
MCC stores and processes data in a centralized manner.However, when a computing node in MCC is attacked or becomes a malicious node, the user’s private data will be leaked.MEC itself is a distributed architecture, user data is stored in a distributed manner when suspected,and the data is relatively close to users,which can well protect user privacy.Since MEC servers is the distributed deployment,they are difficult to be the target of attack.So MEC can enhance the security of data.
2.3 Feasibility Analysis of the Resource Integration of the Blockchain and MEC
Although multi-access edge computing has the advantages of low latency, low energy consumption, and high bandwidth, security issues are its biggest challenge.In the next-generation Internet, because multiaccess edge computing is interwoven in a variety of complex networks, such as P2P networks, wireless networks,and visualization networks,interactions between heterogeneous devices and edge servers may cause malicious behavior.Furthermore, in an edge network, data are divided into multiple parts and stored in different locations, which makes it easier to lose data packets or encounter storage errors; therefore, the integrity of data is difficult to guarantee.In addition, when managing heterogeneous edge networks,it is difficult to isolate management traffic from regular traffic, which makes it easier for attackers to control the network.In multi-access edge computing,another important security challenge is how to ensure the security and privacy of the computing tasks offloaded to edge servers.
Although blockchain has great potential in Internet technology,it still faces many challenges,such as poor scalability, which limits its wide application in various fields.There has always been a “trilemma”problem in blockchain, that is, it is not compatible with the three characteristics of decentralization,security, and scalability.These three characteristics have their own unique technological development routes,and only one characteristic can be sacrificed to satisfy the other two characteristics.Specifically, decentralization makes the network powerless and unrestricted by censorship.Security involves nondeformation and general resistance to attacks,and scalability is related to the ability to handle transactions.At present,scalability issues, especially low throughput, high latency, and limited resources, hinder the feasibility of blockchain-based solutions in practical applications.
However, the integration of blockchain and multiaccess edge computing can enhance a system’s security, privacy, and autonomous use of resources, as shown in the following:
• MEC provides resources and capabilities for blockchain services
First, the distributed structure of multi-access edge computing provides new options for the deployment of blockchain nodes.Blockchain services and multiaccess edge computing services share edge server resources,thereby saving computing resources.Second, because multi-access edge computing is close to the user side,compared to traditional cloud computing systems,it can reduce the communication delay and energy consumption.Therefore, frequently used data, such as ledger data, account status, and business data, can be cached in edge nodes to improve the communication efficiency and reduce the data transmission delay.Finally, an multi-access edge computing platform integrates the operator’s network capabilities, and the blockchain applications deployed on the edge server can call these capabilities to form a characteristic blockchain service.
• The blockchain provides trust for multi-access edge computing
First, because multi-access edge computing multilevel collaboration can constitute edge intelligence and different edge nodes cannot be synchronized, multilevel collaboration can be achieved using blockchain services.Second, the decentralized multi-access edge computing infrastructure makes it such that the authenticity and integrity of data forwarding cannot be guaranteed, and the blockchain can assist the multi-access edge computing system to establish a complete and anti-counterfeiting mechanism.Finally, the computing, storage, and network resource sharing of geographically dispersed edge nodes can use the blockchain platform to conduct transactions in a unified manner to achieve their value.
Therefore, the integration of blockchain and multiaccess edge computing can build an efficient information value platform to promote resource sharing and the optimal allocation of resources.In this integrated system,the blockchain provides a trusted environment for multi-access edge computing services, and multiaccess edge computing provides resources and capabilities for blockchain services.
III.RESOURCE INTEGRATED ARCHITECTURE OF BLOCKCHAIN AND MEC
In this section,we summarize the general network architecture of the resource integration in blockchainenabled MEC.The proposed architecture is based on existing research and reflects the basic ideas and mechanisms of the integrated resource architecture,as shown in Figure 1.
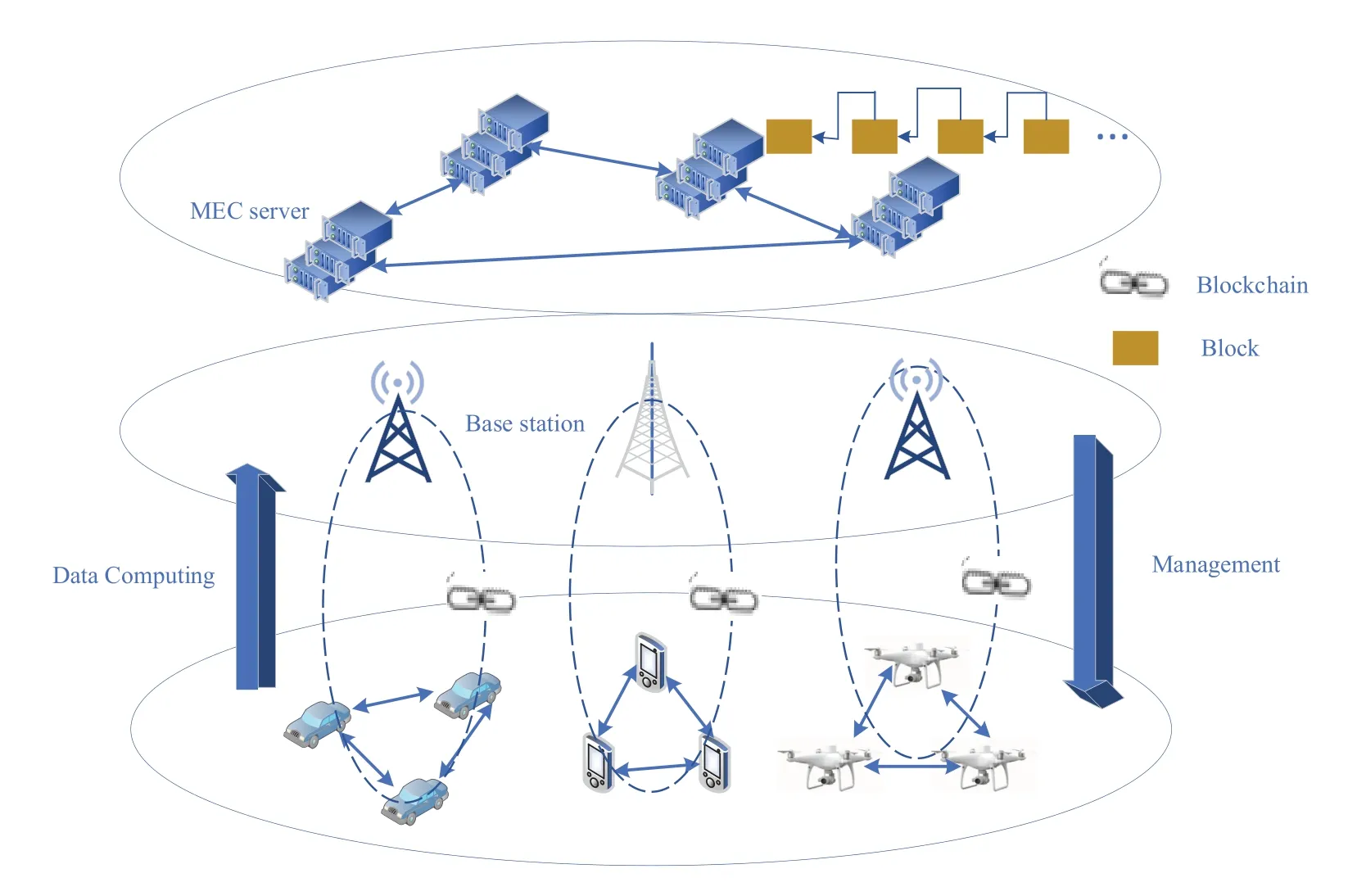
Figure 1. Network architecture of blockchain and multi-access edge computing.
1.Private chain composed of terminal nodes and edge servers:
In a cellular network,terminal equipment communicates with an edge server installed in a base station;in an Internet of Vehicles, a vehicle communicates with a central edge server in a roadside unit,or in an M2M network, one of the devices supported by the edge server communicate between them.Any of these three actions forms a private chain.Because the access control permissions of the private chain are strictly controlled and the identity is clear and trustworthy, there is no need to verify transactions (no PoW consensus mechanism or economic incentives are needed).Deploying a private chain in equipment with limited resources can reduce regulatory risks, reduce technical overhead,and reduce latency.
According to different communication systems,processing capabilities and security requirements,private chains are usually divided into two types of structures.One type is centralized management.The edge server is responsible for adding new devices by creating startup transactions and deleting existing devices by deleting their ledgers.The edge server can only allow devices to communicate with each other through the shared secret key.The other type is distributed management.The devices participating in the private chain act as lightweight peer devices, receiving firmware updates or sending transaction summary files to other peer devices.Of these two types, the edge server is mainly responsible for local network control and provides a large amount of outsourced data storage and calculation for low-performance devices based on the local blockchain in a secure manner.
The heterogeneous edge computing network faces trust and adaptation issues in resource allocation,and private blockchain technology is widely used in mobile edge networks.[38]introduces deep reinforcement learning and consortium blockchain to construct the trusted and auto-adjust service function chain orchestration architecture.[39] proposes a blockchain decentralized interoperable trust framework for internet of things zones to establish trustworthy communication by making use of a private blockchain chain.A new technique and its implementation of private transactions in a blockchain are presented in [40].The paper [41] shows a blockchain-based malware detection framework to detect malicious mobile applications in app stores for smartphone devices.The paper [42] tries to leverage both public and private blockchain infrastructures to realize efficient,privacyenhancing,and accountable applications.A novel and cryptographically secure protocol[43]can be used for any member of a private blockchain to reveal private blockchain data to a valid external party.A mobile number portability processing system in the telecom domain with a solution designed in [44] using permissioned private blockchain technology.[45] compares the application of public and private blockchain through the experimental implementation of smart contracts for insurance services.
2.Blockchain architecture based on a P2P network:
Regarding edge servers, in addition to playing an important role in the local network, they also have the ability to store and forward messages to each other for data replication and sharing and collaborative computing capabilities.The edge server performs a task analysis on itself and its peers to realize the self-organization of adding or deleting edge nodes in the adaptive environment.Considering the processing power,a lightweight distributed consensus mechanism should be deployed in a P2P network to ensure low latency and high throughput requirements.For clouds with powerful computing and storage capabilities,distributed blockchain clouds can provide the most competitive computing infrastructure to achieve secure and on-demand access.Since the application range of P2P edge server networks and distributed clouds is much wider than that of local networks,they have received extensive attention from industry.In particular,Ethereum is one of the most popular P2P network architecture blockchains.
In a P2P network, fair resource allocation is complex and challenging.The paper [46] proposes a blockchain-based resource allocation schemes to manage the demand-supply of resources between the users and resource-providing companies in a secured and trusted environment.The paper [47] proposes a content selection algorithm of edge cache nodes, which adopts the Markov chain model to improve the utilization of cash space and reduce the content transmission delay.A framework for decentralized P2P energy management is developed in [48] to achieve scalable control, exploit the potential of smart loads,and utilize distributed energy resource controllability.Blockchain as a thriving technology is utilized in the P2P network due to its transparency, security, and rapidity in executing transactions [49].There are also many P2P blockchain systems for the management and trading of power resources.An energy storage sharing mechanism via blockchain is designed in[50].A P2P energy trading over Hyperledger Fabric 1.4 in South Korea is implemented in [51].The paper [52]uses the ciphertext policy attribute-based encryption scheme to establish a blockchain-based P2P energy trading approach with privacy preservation.The paper[53] proposes SynergyChain, which is a blockchainassisted adaptive model to improve the scalability and decentralization of the prosumer grouping mechanism in the context of P2P energy trading.
IV.RESEARCH ON THE RESOURCE INTEGRATION IN BLOCKCHAINENABLED MEC
4.1 Summary of Current Research
Table 3 briefly summarizes related work on the integration of blockchain and multi-access edge computing.We elaborate on these works in detail.
4.1.1 Architecture of the Integrated System of Blockchain and Multi-Access Edge Computing
Multi-access edge computing provides users with lowlatency and high-reliability network services by relocating resources to the edge of the network, but it faces serious security problems.Similarly,the decentralization,tamper-proof modification,and traceability of the blockchain provides users with security guarantees, but its scalability is restricted.An integrated blockchain and multi-access edge computing system can combine the two methods’ advantages and complement each other.
Therefore, the integration of blockchain and multiaccess edge computing can build an efficient information value platform to promote resource sharing and the optimal allocation of resources.In this integrated system,the blockchain provides a trusted environment for multi-access edge computing services, and multiaccess edge computing provides resources and capabilities for blockchain services
Previous studies [54], [55] have investigated the integrated architecture of mobile multi-access edge computing and blockchain and have proposed the deployment of blockchain technology in the multiaccess edge computing network layer.[54] proposed a three-layer distributed blockchain cloud architecture including a device layer, a fog computing layer and a cloud layer based on Software Defined Network(SDN)multi-access edge computing.The cloud layer is a distributed cloud based on blockchain technology that can provide secure access to the most competitive computing infrastructure.The fog computing node adopts a distributed security SDN controller based on the blockchain to provide users with low-cost computing resources and secure access control,thereby meeting the needs of user applications.The architecture model proposed in [55] is the same as that in [54].However,the application scenario in[55]is the IoT.In[55],the author combined the device layer and the fog layer from [54] into one layer, collectively called the edge layer; the central layer is the cloud layer composed of cloud servers.Similarly, [56] proposed a blockchain-based data management system architecture for IoT application scenarios.The architecture includes three layers: a consumer layer, a distributed storage layer and a blockchain layer.The storage layer is composed of IoT devices and edge nodes that store the data generated by the IoT devices.In addition,the blockchain layer is composed of edge servers that conduct access control and data verification.
In addition,unlike the abovementioned deployment of blockchain systems in multi-access edge computing from a technical point of view,IBM and Samsung Electronics jointly developed a decentralized peer-topeer telemetry architecture(ADEPT)from a commercial point of view[55][57].The architecture advocates the transfer of the decision-making power in the network from the center to the edge,enabling devices to gain greater autonomy and become a transaction point on the blockchain.The alpha version of the architecture adopted the Ethereum protocol, which has three types of peers: lightweight peers, standard peers and peer-to-peer exchanges.The processing capabilities of these three types are gradually enhanced.Lightweight peers perform messaging, retain light wallets with blockchain addresses and balances,and perform minimal file sharing.Standard peers retain part of the blockchain’s functions and support lightweight peers.Peer-to-peer exchange is a potential repository for a copy of a complete blockchain, which can provideblockchain analysis services.
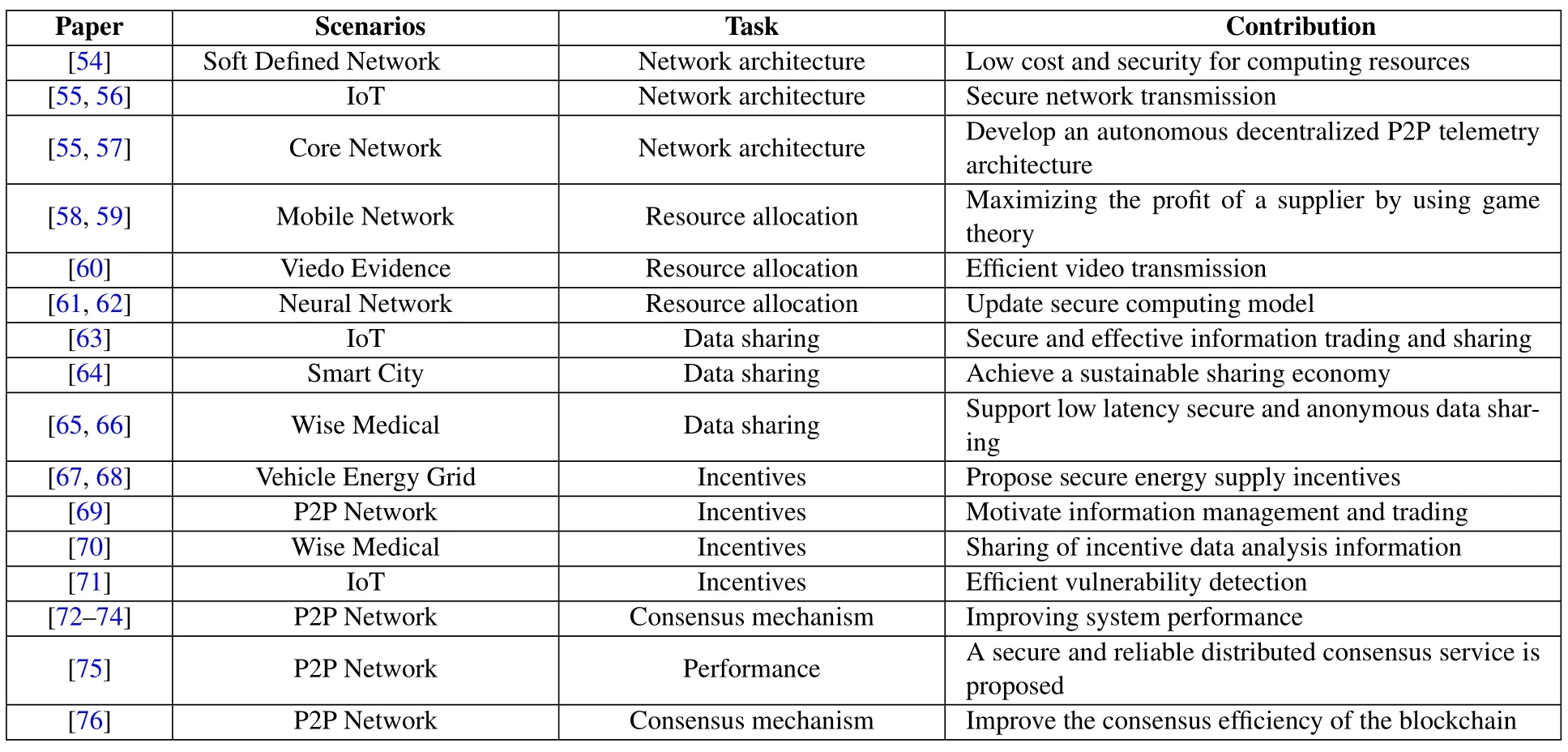
Table 3. Related works.
4.1.2 Resource Scheduling
1.Resource Allocation Strategy of Multi-access Edge Computing Based on Blockchain
The reasonable and efficient allocation of resources plays a very important role in blockchain-based multiaccess edge computing, and it directly affects the performance of multi-access edge computing services and blockchain services.Resource allocation includes computing resource allocation and wireless resource allocation.The computing resources mainly include CPU resources and memory resources in the user terminal and edge servers, and the wireless resources mainly include the number of subchannels,bandwidth,and power.
In [58], the authors offloaded PoW tasks in mobile devices to edge servers through wireless communication.Based on the two-stage Stackelberg game,the author determined the task allocation strategy and the service price between mobile devices and edge servers.Following the above research, auction and game theory solutions are widely applied by researchers to allocate resources in blockchain-based multi-access edge computing systems.[59] proposed a two-layer resource management model containing an edge layer and a cloud layer.That research used a Stackelberg game with multiple leaders and multiple followers to simultaneously maximize the remuneration for absenteeism and the profits of the service provider.[60] focused on the resource allocation of edge nodes in video storage scenarios and proposed an effective video transcoding and transmission method based on mobile multi-access edge computing and the blockchain.This method regards the resource allocation, content price determination and content quality level optimization as a three-stage Stackelberg game to achieve efficient video transmission.[61]proposed a resource allocation method based on evolutionary game theory and designed a dynamic mining pool selection strategy to ensure the stability of profits.In addition, [62] used an optimized auction scheme for edge resource allocation based on deep learning algorithms in which the multilayer neural network architecture is based on analytical solutions.The neural network uses miners’valuation to conduct training to maximize the revenues of the supplier and optimize the neural network parameters through the stochastic gradient descent(SGD)method.
2.Blockchain-based Multi-access Edge Computing Data Sharing
With the convergence of information technology and human production,the amount of data in the world has exploded.The value of data is not limited to personal use.The value of data is also reflected in public areas such as national security,social public interests,and overall industry innovation.
In [63], the authors proposed a distributed knowledge collaboration and sharing scheme applied to the IoT.In this scheme, smart edge devices are used to share data through consortium blockchains.In addition, the author uses cryptocurrency, smart contracts and a proof of transaction(PoT)consensus mechanism to improve the security of knowledge transactions and sharing.In[64],the authors focused on the realization of a sustainable sharing economy based on the Internet of Things in smart cities.A large amount of IoT data are generated and processed at edge nodes.Artificial intelligence will process and extract important event information, generate semantic digital analysis and save the results in the blockchain.The blockchain provides a series of sharing economy services,including handing over selected data to artificial intelligence for analysis and transacting important information derived from the analysis so that valuable Internet information can be fully utilized.Moreover,[65]and[66]proposed a blockchain-based sharing model for the secure sharing of medical data.The model structure designed in [65] includes a medical institution alliance server group,a medical record storage structure and a distributed database system.The alliance server group adopts an improved share authorization certification mechanism to achieve a consensus.Medical data are encrypted and stored in a distributed database,thereby reducing the pressure of high-frequency access to data on the blockchain.In [66], the authors proposed a safe treatment management framework, which uses IoT nodes and blockchain-based distributed mobile multi-access edge computing to support low-latency,safe,anonymous and always-available spatiotemporal multimedia treatment data in data sharing and communication scenarios.
4.1.3 Research on the Incentive Mechanism in a Blockchain System
In the blockchain,compared to the absolute core position of the consensus mechanism,the incentive mechanism is another subcore position based on the consensus mechanism.The incentive mechanism encourages nodes to participate in maintaining the security of the blockchain system through an economic balance and maintaining the sustainable operations of the system.
In [67], the authors combined the mechanism proposed in[68]with blockchain smart contract technology and proposed a k-anonymous location privacy incentive mechanism to encourage mobile users to participate in the k-anonymous anonymous collection.The service requester and service provider cooperate in accordance with the conditions of the smart contract.Service providers who pass the smart contract verification and join the k-anonymous collection will receive the corresponding rewards.In[77],the authors proposed a blockchain-based vehicle energy network(VEN)energy supply security incentive scheme.The program introduces a new licensed energy blockchain system in a VEN.Under the incentive of the pricing mechanism, the program establishes an incentive for electric vehicles to maximize their utility while simultaneously delivering renewable energy to different power load areas.Regarding the incentive model,the authors proposed an incentive mechanism for distributed P2P applications based on the blockchain that encourages user cooperation through cryptocurrencies such as Bitcoin [69].In this mechanism, users who help with a successful delivery are rewarded.The incentive mechanism combines a security verification method to prevent collusion between users and miners in the blockchain.In[70], the authors proposed a collaborative model incentive mechanism for sharing medical data through the blockchain.The author derives the topological relationship among participants,including data owners, miners, and third parties, and calculates the value and income distribution to achieve the effect of incentives.In[71],the authors proposed a blockchain-based incentive system named SmartRetro and introduced an automatic reward mechanism in SmartRetro that can encourage more distributed detectors to participate in vulnerability detection and contribute to the detection results.
4.1.4 Research on the Consensus Mechanism of the Blockchain-Enabled MEC System
As the core technology of the blockchain system, the consensus mechanism determines the characteristics of the blockchain’s decentralization,security,and scalability, which is the basis for the implementation of the blockchain.Blockchain is a promising technology for manmaging MEC services.However, blockchian system faces important challenges in terms of scalability .We review existing consensus mechanism in blockchain-enabled MEC systems.The existing consensus mechanisms in blockcahin-enabled MEC sys-tems are mainly divided into two categories,including authorized consensus mechanisms and nonauthorized consensus mechanisms.Table 4 summarizes the advantages and disadvantages of the current consensus mechanisms.
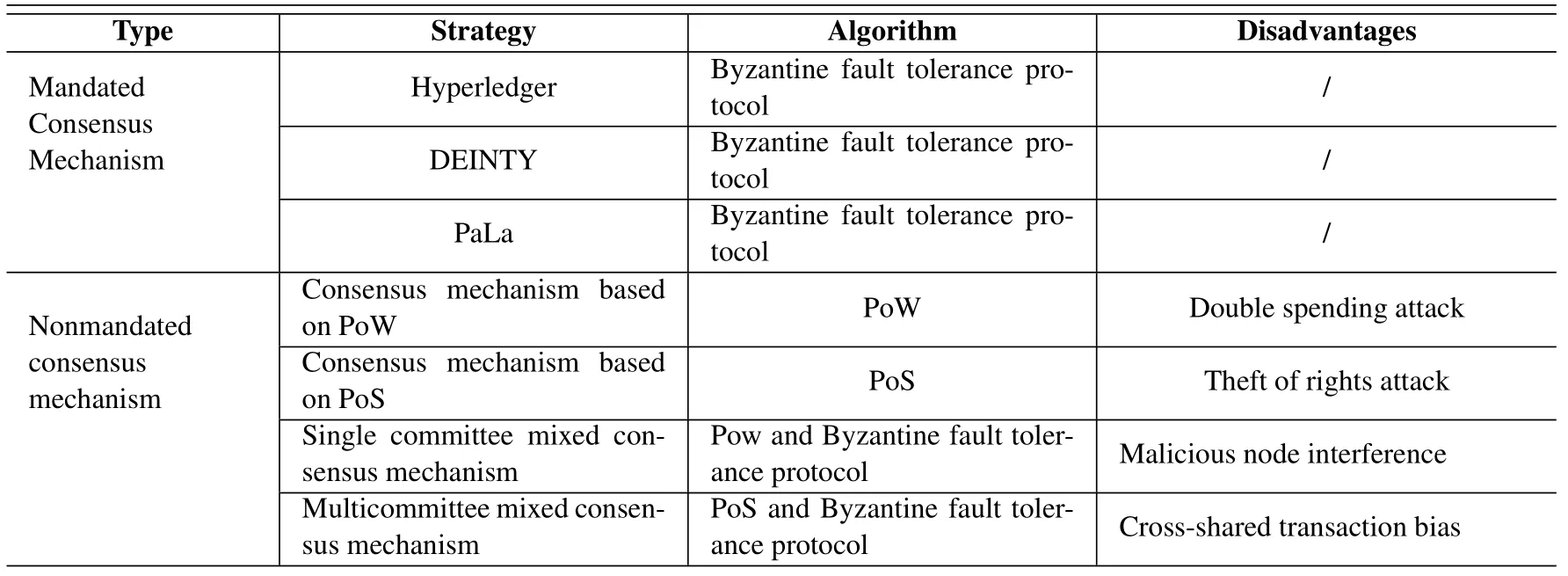
Table 4. advantages and disadvantages of the current consensus mechanisms.
PoW is the first consensus algorithm introduced into the blockchain.Although the PoW algorithm is very secure, it requires high computing power and a considerable amount of energy.In [78], the authors proposed a cooperative MEC-aided blockchain network to improve the effiency of PoW.The PoS [72] proposed by Ethereum is an improved version of PoW that changes the calculated hash value into the ownership of the number of currencies, reducing the consumption of resources.For PoS consensus mechanism, [78] proposed a allocation algorithm without knowing the network model to computation performance of the system.[73] further improved PoS and proposed a DPoS.In[5],the authors proposed a joint optimization scheme for the integrated blockchain and MEC systems to achieve the optimization performance of the two subsystem by using DPoS.This part of the consensus mechanism is relatively simple.[74] focused on the PBFT and its improvement and stated the scenarios used by Byzantine fault tolerance.In [79],the authors proposed partial Practical Byzantine Fault Tolerance protocol to minimize the latency of reaching consensus in integrated blockchain and MEC.
In addition to the above several classic consensus algorithms,many studies have proposed some improved or brand-new consensus algorithms.Yang et al.[80]introduced PoW computing power competition into DPoS;this method uses PoW to improve fairness and uses DPoS to reduce resource consumption, thereby improving the consensus efficiency of the blockchainenbaled MEC systems.
4.2 Application Scenarios of Integrated Blockchain and Multi-access Edge Computing
Blockchain and multi-access edge computing have the same distributed mechanism.Both are based on computing, data storage, and network resources, which makes them destined to be integrated.The mutual empowerment and mutual promotion between the two enable different applications to be fully developed.
4.2.1 Trusted Data Processing in the Internet of Vehicles
Integrated blockchain and multi-access edge computing technology provides credibility and efficiency for vehicle network communications.The data generated by the interactions between vehicles and vehicles,vehicles and drive test units, and vehicles and base stations are transmitted to the edge cloud in real time and transferred to edge servers [81].The blockchain service can provide real-time evidence based on the analysis and processing of credible data to support the credible execution of the business to solve the security, real-time and high reliability issues required in data processing[82].
4.2.2 Industrial Internet of Things
The Industrial Internet of Things can be deployed on an multi-access edge computing platform and serve as an application for users.On the multi-access edge computing platform, the data collected by the industrial Internet of Things terminal are uploaded to the platform for storage.The collected data include environmental data, such as regional atmosphere, water, and soil data.Storing industrial IoT data in the blockchain can ensure the immutability and authenticity of the data on the chain.Regulators can trace the source of the information at any time,and the data released through the blockchain can increase their credibility.
4.2.3 Smart Medicine
In view of the weak infrastructure of the current medical platform, such as the low level of medical services and medical security problems, the application of a blockchain to achieve intelligent monitoring of health information and management of medical equipment can improve public health security.In addition,edge computations can effectively solve the traditional problems of the high cloud computing time delay and low throughput, and the combination of a blockchain and edge servers can speed up the development of the industrialization of smart medicine.
4.2.4 Video Evidence
Customarily, a video of a campus area is stored in a surveillance video with various units.Each unit of interest is likely to be adversely affected by fake video data.Therefore, the video memory demand of using a block chain to make the video tamper-resistant reputable to another requires special features,and the video card memory card needs to be able to be stored in a potential blockchain technology,which can reduce the cost of video memory card, make video evidence convenient, and improve the credibility of the video.However, video files are generally large and difficult to store directly in the blockchain.We can use multiaccess edge computing to assist the blockchain in storing video summary data.
4.2.5 Sharing Economy
Users that have equipment,data and computational resources can share and upload their transaction records at the same time through a chain of adjacent blocks on an edge server to guarantee that the transaction data cannot be tampered and ensure the safety of transaction data.Through sharing, idle scattered resources can be effectively used so that enterprises can quickly accumulate more data, improve the user experience,and promote the development of the sharing economy.
V.CHALLENGES OF THE RESOURCE INTEGRATION IN BLOCKCHAINENABLED MEC
5.1 Data Security and Privacy
The initial design of the blockchain has the two problems of security and privacy.Multi-access edge computing also faces many security challenges in terms of edge data, edge networks, edge infrastructure, and edge applications.Although blockchain and multiaccess edge computing have complementary advantages, due to the complex integration of multiple different technologies, this brings new security and privacy challenges to the integration of the blockchain and multi-access edge computing.Some works have been studied on the data security and privacy of the blockchain-enabled MEC systems.
The authors in [83] proposed a dynamic computation offloading for blockchain-enabled MEC framework,aiming to achieve the best privacy performance and mining profits while minimizing offloading latency and energy cost.In [84], the authors proposed a new decentralized health architecture, which integrates blockchain and MEC for data offloading in terms of user’s privacy and data security.The recent work [85] presented a novel decentralized healthcare architecture by using blokchain and MEC to enhance the system security and improve the data retrieval rate.However,the data security and user’s privacy schemes are not robust enough.
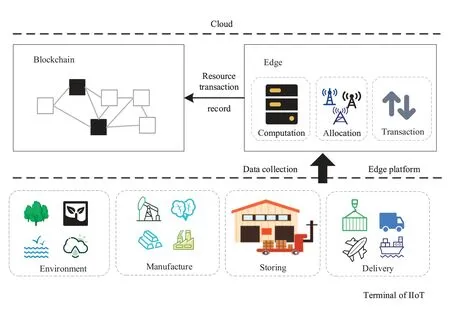
Figure 2. Application of an integrated multi-access edge computing and blockchain system to the IIoT.
5.2 Identity Authentication Management
In traditional multi-access edge computing,there is no authentication system for terminal devices and no trust mechanism.Malicious terminals can access the system at will to spread viruses and software attack information.The identity authentication system based on PKI/CA is currently the most commonly used identity authentication method,but it has certain shortcomings: once the centralized digital certificate authentication center CA suffers a security attack or fails,it will affect the certificate users.User certificates can only be authenticated by their own root certificates and cannot be authenticated by different CAs.A blockchain-based identity authentication system can be built to authenticate IoT terminal devices,avoid single points of failure,and eliminate the dependence on the CA.Moreover, the tamper-proof data feature of the blockchain can improve the security of a device’s identity and reduce the credibility costs.However,the blockchain is a global network, and the restriction of the identity system control between countries is a great challenge for cross-border connections and complementary information.
In [86], the authors proposed a blockchain-based group-authentication scheme for vehicles with decentralized identification, aiming to enhance the security of interactions and data analysis.In the scheme,MEC is used to store the tamper-proof blockchain to achieve decentralized authentication.The authors in[87]proposed a new security framework for distributed applications, which includes blockchain-based mutual authentication to provide secure services with users.In[88], the authors designed a group signature scheme,which can settle the problem of consensus algorithm being attacked for blockchain-enabled MEC systems.Meanwhile, the authors also proposed a efficient authentication scheme to store key materials to address the tedious steps of authentication of mobile devices when they change groups in blockchain-enabled MEC systems.However, the existing identity authentication management schemes are very inefficient when the performance of the blockchain system is limited[89].
5.3 Lightweight Protocol Design
The integrated blockchain and multi-access edge computing system has large numbers of edge nodes and connections and massive amounts of data.The secure access service of edge nodes should meet the demand for a high throughput.With the rapid development of the Internet of Things, due to the limitations of the computing, storage, and battery resources of terminal devices, the long distance, high latency, and high energy consumption of existing cloud computing technologies cannot meet the needs of the IoT applications.In addition, in mobile networks, due to the wireless connections and movement, edge nodes will have frequent access or exit situations across them,leading to changing topological and communication conditions, making them vulnerable to account hijacking, insecure systems and components and other threats.For edge nodes with limited resources, research on lightweight consensus mechanisms,authentication protocols, and secure communication protocols is an important challenge of the integration of blockchain and multi-access edge computing.
In [90], the authors designed a lightweight blockchain-enabled RFID-based authentication protocol for MEC systems, which is not only very efficient in terms of communications and computation but also supports many security and functional features.The authors in [91] proposed a fast faulttolerant blockchain protocol for wireless edge computing, which can ensure the fast data aggregation by using a spanner as the communication backbone.However, the efficiency of the existing work is low,which affects the performance of the integration of blockchain and MEC.
VI.CONCLUSION
This article systematically introduces the integration of blockchain and multi-access edge computing and explores its general network structure.In addition,this article summarizes the current achievements and research directions regarding the network architecture,resource management,data sharing,incentive mechanism, and consensus mechanism.With the advent of 6G communication technology, how to perfectly integrate blockchain and multi-access edge computing with 6G networks and the industrial Internet of Things is a question worthy of discussion by researchers in the future.Finally,this article analyzes the challenges faced by the current integrated system to provide references for later researchers.
ACKNOWLEDGEMENT
This work is surported by the National Key Research and Development Program of China (No.2020YFB1807500), the National Natural Science Foundation of China(No.62102297,No.61902292),the Guangdong Basic and Applied Basic Research Foundation(No.2020A1515110496),the Fundamental Research Funds for the Central Universities (No.XJS210105, No.XJS201502), and the Open Project of Shaanxi Key Laboratory of Information Communication Network and Security(No.ICNS202005).
- China Communications的其它文章
- An Overview of Wireless Communication Technology Using Deep Learning
- Relay-Assisted Secure Short-Packet Transmission in Cognitive IoT with Spectrum Sensing
- Frequency-Hopping Frequency Reconnaissance and Prediction for Non-cooperative Communication Network
- Passive Localization of Multiple Sources Using Joint RSS and AOA Measurements in Spectrum Sharing System
- Specific Emitter Identification for IoT Devices Based on Deep Residual Shrinkage Networks
- Primary User Adversarial Attacks on Deep Learning-Based Spectrum Sensing and the Defense Method

