MimicCloudSim:An Environment for Modeling and Simulation of Mimic Cloud Service
Liming Pu,Jiangxing Wu,Hailong Ma,Yuhang Zhu,Yingle Li
Information Engineering University,Zhengzhou 450002,China
Abstract:In recent years,an increasing number of application services are deployed in the cloud.However,the cloud platform faces unknown security threats brought by its unknown vulnerabilities and backdoors.Many researchers have studied the Cyber Mimic Defense(CMD) technologies of the cloud services.However,there is a shortage of tools that enable researchers to evaluate their newly proposed cloud service CMD mechanisms,such as scheduling and decision mechanisms.To fill this gap,we propose MimicCloudSim as a mimic cloud service simulation system based on the basic functionalities of CloudSim.MimicCloudSim supports the simulation of dynamic heterogeneous redundancy (DHR) structure which is the core architecture of CMD technology,and provides an extensible interface to help researchers implement new scheduling and decision mechanisms.In this paper,we firstly describes the architecture and implementation of MimicCloudSim,and then discusses the simulation process.Finally,we demonstrate the capabilities of MimicCloudSim by using a decision mechanism.In addition,we tested the performance of MimicCloudSim,the conclusion shows that MimicCloudSim is highly scalable.
Keywords:cyber mimic defense;mimic cloud service;simulation;dynamic heterogeneous redundancy
I.INTRODUCTION
For the past few years,in order to deal with uncertain threats in cyberspace,that based on unknown vulnerabilities or backdoors in the system,academician Jiangxing Wu led the research team to propose the theory and method of Cyber Mimic Defense(CMD)[1],and tried to develop innovative defense technologies,which could change“the game rules of easy-to-attack and difficult-to-defend”.
At present,the demonstration and network testing of CMD-based applications have been officially launched in relevant industries and institutions,such as:Mimic Web Server[2],Mimic Router [3],Mimic DNS[4].More and more researchers are paying attention to CMD technology.However,there is a shortage of tools that enable researchers to evaluate their newly proposed CMD-based defense mechanisms,such as scheduling and decision mechanisms.The evaluation of the new mechanism is mainly carried out by the methods of constructing physical software and hardware systems [5],or conducting the experiment in a real cloud data centre.But,there are mainly three shortcomings in the methods.First,the cost of construction and maintenance of physical environment is high,and the construction period is very long.Second,the repeatability,accuracy and controllability of experiments are also difficult to be guaranteed.The other thing is that a comprehensive evaluation of the newly proposed mechanism in a real data centre is extremely difficult,and the complex conditions may go out of the control of researchers.So,a feasible method of evaluation is to use simulator technology,which can identify invalid design and compare different solutions in the early stages of scientific research.
In fact,there are already some simulation tools for cloud environments,such as CloudSim simulation toolkit[6]and ContainerCloudSim[7],etc.However,they still have some limitations.For example,dynamic heterogeneous redundancy(DHR)[1,8,9]architecture and mechanisms related to scheduling and decision cannot be supported by them.Fortunately,Cloudsim is an extensible simulation framework.Therefore,we present a simulation tool called “MimicCloudSim”,which is built on top of CloudSim,and can simulate security defense mechanisms of the mimic cloud service(MCS).Some extensible interfaces are provided in MimicCloudSim to aid researchers in implementing new mechanisms easily.In addition,MimicCloudSim can also simulate the generation of user requests and return responses.After execution,it will generate information on the necessary to highlight the effects of the CMD mechanism.
The remainder of this manuscript is organized as follows.In Section II,related work is briefly reviewed.Section III,we analyze the technical selection and requirements of the simulator.Section IV,we present simulator architecture.Section V discusses the implementation details.Section VI gives an overview of our experiments.Finally,section VII summaries the contributions of the paper and indicates some future work.
II.RELATED WORK
This section briefly introduces the research status of CMD and simulator.
2.1 Introduction of CMD
CMD takes the “Dynamic Heterogeneous Redundancy” (DHR) structure as the infrastructure [1],which is composed of input agent,executor pool,multi-mode voter,scheduling policy,component set and executor set.Its structure and composition are shown in the figure 1.
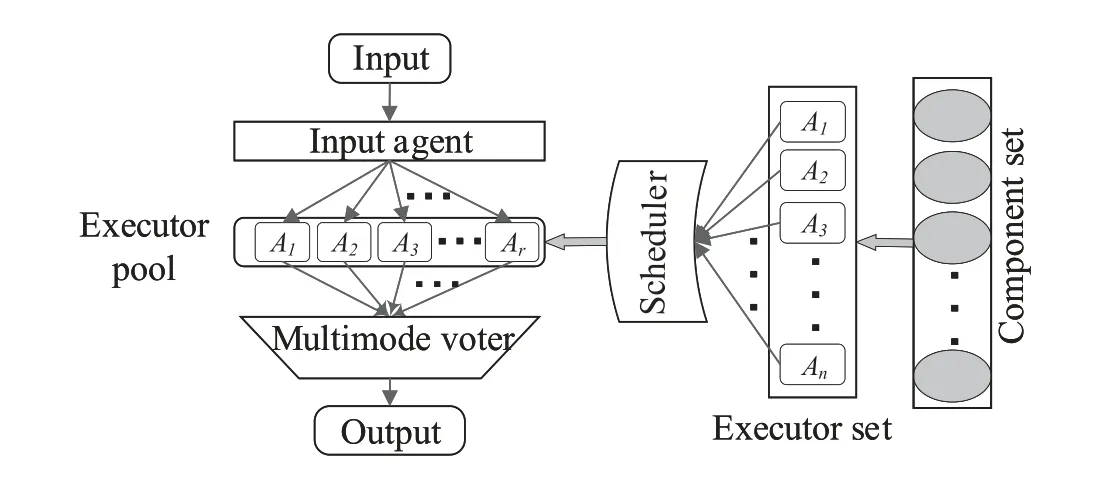
Figure1.Dynamic heterogeneous redundancy structure.
The DHR distributes the input to executors by input agents,and the results are voted by the multimode voter,and finally get a relatively correct unique output.The executors are required to meet the characteristics of dynamic heterogeneous redundancy,and they are functionally equivalent.However,there are no restrictions on the functional granularity and properties of the executor,which can be hardware and software entities or virtual unit of functionality.Among them,the dynamic makes the system behave as uncertainty to the attacker;the heterogeneity can avoid the same vulnerabilities or backdoors in different executors at the same time;the redundancy improves the reliability of the system.[1]shows that DHR is a generalized robustness control architecture with endogenous attributes of high reliability,high availability and high credibility.[8]shows that the DHR can greatly increase the difficulty of attack and enhance the security of information systems.
Currently,cloud services get accelerated popularization and application in different fields.At the same time,vulnerabilities and backdoors,which are widespread in both hardware and software components,are also accelerating their migration to the cloud[10,11].The security and credibility of cloud platforms are facing unprecedented challenges.The cyber mimic defense proposed by domestic researchers successfully overcomes the problems of traditional security methods.It shows great effectiveness when dealing with uncertain threats like unknown vulnerabilities and backdoors[1].
2.2 Simulator Research Status
In this section,related simulation toolkits are discussed.Currently,researchers have developed a variety of cloud-based simulators,as follows:
For grid computing,Buyya et al.[12]developed an event-driven simulation toolkit for heterogeneous Grid resources,which supports modeling of grid entities,users,machines,and network,including network traffic.Ostermann et al.[13]developed GroudSim,a toolkit for simulating scientific applications execution both on Grid and cloud infrastructures,which provides users with basic statistics and analysis after the simulation.
For cloud data centers,Calheiros et al.[6]developed a scalable cloud simulation toolkit,called CloudSim,that enables modeling and simulation of cloud systems and application provisioning environments.The toolkit supports both system and behavior modeling of cloud system components such as data centers,virtual machines and resource configuration strategies,and can be easily extended development.Kliazovich et al.[14]developed the GreenCloud,it is specifically designed to investigate power management schemes to achieve an energy efficient data center,and capture the energy details consumed by data center components(servers,switches,and links).Other cloud simulators include MDCSim[15],GDCSim[16],iCanCloud[17],etc.
For the current popular container cloud,Piraghaj et al.[7]developed an environment for modeling and simulation of containers in cloud data centers,called ContainerCloudSim,which provides support for modeling and simulation of containerized cloud computing environments.This simulator is an extension of the CloudSim.
For data center networks,Garg et al.[18]designed NetworkCloudSim,which can model parallel applications in a cloud simulation environment,and support modelling of real Cloud data centers and generalized applications,such as high-performance computing,ecommerce,and workflows.This simulator is also an extension of the CloudSim.
The above-mentioned various types of simulators are mainly designed for the research of cloud resource management,and power consumption,and system structure,and so on.There is no simulator dedicated to DHR mechanism research.
III.SIMULATOR REQUIREMENTS
At present,the research work of MCS is still in its infancy,which needs innovation and exploration in many aspects,for instance the theories,system design and implementation,and evaluation methods.This paper hopes to provide a set of special simulation tools for verification and evaluation of the MCS,which should share the existing research in the industry.
By the foregoing analysis of simulators,Mimic-CloudSim is extended based on the mature CloudSim.As the following reasons:
1) CloudSim is a relatively mature toolkit in the above simulators.It has good scalability and is widely used in the industry.Many simulators of cloud computing have been extended from CloudSim,for example:NetworkCloudSim and ContainerCloudSim;
2)CloudSim is suitable for simulating the events of user request and attack,because it is driven by discrete events;
3) CloudSim's component design makes it easy to build a DHR architecture.
In order to evaluate the CMD mechanism,MimicCloudSim should also meet the following requirements:
1) The system architecture of MimicCloudSim should meet the requirements of the DHR structure.As mentioned earlier,DHR is the core architecture of the MCS;
2)Support custom insertion related strategies or algorithms,such as input distribution,executor scheduling,mimic decision,etc,and can be easily replaced in order to compare and optimize related strategy algorithms;
3) Support the simulation of the entire mimic defense process,including network attack event generation,input distribution,task processing,output decision,etc.;
4)Support the simulation of vulnerability and backdoor,which can be exploit by attackers.
IV.SIMULATOR ARCHITECTURE
MimicCloudSim is mainly composed of CloudSim simulation engine,MimicController,MimicService-Proxy,ExecutorPool(E),Component set(C),User code,and interface specifications (such as generation specifications of executor and request),as shown in figure 2.
CloudSim simulation engine:provides cloud service infrastructure,including data centers,hosts,virtual machines,etc.,and supports functions such as resource configuration,execution time statistics,and operation monitoring.Responsible for the entire life cycle management of discrete events,include reception,distribution,and destruction.MimicCloudSim takes full advantage of CloudSim's environment and event processing specifications.The related components are described below.
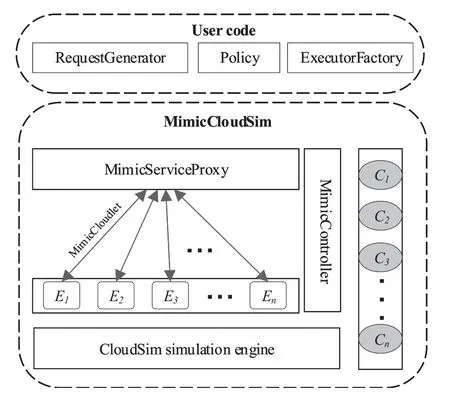
Figure2.Desired probability density function form of the proposed scheme.
MimicController:responsible for processing discrete events,controlling the actions of MimicServiceProxy.Providing interfaces of user strategies,and performing scheduling and decision.
MimicServiceProxy:responsible for receiving user requests,distributing requests to the executors according to the policies provided by the user,receiving the response results.
ExecutorPool:a set of executors,that are virtual machines of functionally equivalent and heterogeneous.Responsible for processing user requests and generating response results,representing the functional execution units of cloud services.
Component set:an executor is constituted many components.The components can be operating system,database,application server,etc.
MimicCloudlet:it carries contextual information,including request,response,and task status.
User Code:it is the user interface provided by MimicCloudSim,allows users to insert custom policies and algorithms.
V.DESIGN AND IMPLEMENTATION
We will present the design of MimicCloudSim in this section.
5.1 Design and Implementation Details
MimicCloudSim is built based on the CloudSim,and introduces DHR model.It implements the simulation event flow based on the CloudSim event engine,and provides the user interface to implement the function call.
In figure 3,The main component class design is shown,the components in the lower dotted line are provided by CloudSim as the basic support,the user code on the right is provided by the user.This article provides a simple implementation as an example of user code.The main components are described below:
1)CloudSim basic support components
The tool classCloudSimis used as the management controller.It is responsible for the whole lifecycle management of the simulator.It is also the main engine of discrete event processing.Its extension classMimicCloudSimis used as the drive controller of the MCS simulator.TheMimicCloudSimclass allows users to provide heterogeneous components and executors to the simulator in a custom policy.
As a data center simulation model,theDatacenterclass is responsible for data center resource management and schedules virtual machines (Vm) between hosts according to policies.At the same time,CloudSim provides theDatacenterBrokerclass as a user agent,responsible for managing virtual machine creation and destruction,and submitting related tasks(Cloudlet)to the virtual machine.
As a virtual machine simulation model,theVmclass is responsible for processing the task submitted by the user.The Vm needs to run in the Host.
As a task slice model,theCloudletclass describes the resource requirements,time consumption,input and output length of the task,and is the carrier of the task of the simulator.
In addition,CloudSim provides theSimEventclass as a discrete event model,which records the event type and time,event source and destination,the event data,and more.
2)DHR architecture components
Based on theDatacenterBrokerextension,theMimicControllerclass is designed as a mimic controller.The following properties are configured:mimicServiceProxyis used to control the input proxy,responseListcollects the executor output,executorFactoryrecords executor generator,anddecisionPolicysaves the decision policy.The class implements functions such as executor pool construction,requests control,results ruling,and discrete events processing control.
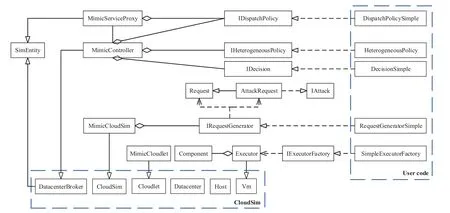
Figure3.MimicCloudSim class diagram.
Based on theSimEntityextension,theMimicServiceProxyclass is designed as a mimic service proxy.The following properties are configured:mimicControlleris used to report and feedback request messages,dispatchPolicyreceives allocation policies,and records response information.This class needs to handle the messages of request listening and request distribution sent byMimicController.
Based on theVmextension designExecutorclass as the task processing unit,multiple heterogeneous equivalent executors can form the executor pool.It configure the following properties:componentsrecord component set,leakrecords vulnerability of the executor.The class implements request processing and result output functions.
3) User interface This article defines multiple user interfaces,then users insert custom policies by implementing these interfaces.
·The interface for input allocation policy is defined asIDispatchPolicy.DispatchPolicySimpleis a implementation based on the direct allocation policy,and an example of user code.
·The interface for executor heterogeneity decision policy is defined asIHeterogeneousPolicy.HeterogeneousPolicyprovides a implementation of component-based heterogeneous decision,and a user code example;
·The interface for output decision policy is defined asIDecision.DecisionSimpleprovides a implementation based on traversal statistics,and a user code example.
In addition,define two auxiliary interfaces:request generation(IRequestGenerator)and executor generation(IExecutorFactory).User can custom request generator and executor builder.This article also provides a implementation.
4)MimicCloudlet
This paper is based on theCloudletextension designMimicCloudletclass as a task carrier module of MimicCloudSim,called “MimicCloudlet”,means mimic task slice.It configured with the following properties:requestto carry user request,responserecord executor processing result,executorassociation processing the task slice.The three have the following relationship:theexecutorprocesses therequestand records the result withresponse.In addition,thedecisionResultproperty is configured to record the output of the decision result,which is written byMimicControlleraccording to the decision policy.
5.2 MimicCloudSim Working Process
MimicCloudSim also defines some event messages to drive the simulator,they are encapsulated with theMimicTagsclass.The sequence of message is shown in figure 4.The italicized part of the figure (the blue font in the color map) uses CloudSim's components and event messages.
The work process is mainly divided into two stages:
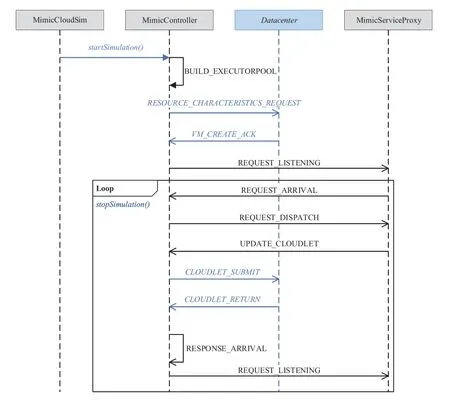
Figure4.MimicCloudSim event message sequence diagram.
Startup phase:The user starts the simulator through thestartSimulation()function,thenMimicControlleris activated,andMimicControllersends a message to build the executor pool,and generates Vm,and then sends aREQUEST-LISTENINGmessage to informMimicServiceProxyto start listening for user requests.
Simulation phase:The simulator continuously listens for user requests.WhenMimicServiceProxyreceives the user request,it generatesMimicCloudletand assigns theExecutor.ThenMimicControllersubmitsMimicCloudletto Datacenter and receives the processing result,whileMimicControllermakes multi-mode decision on the processing result.In short,the simulator loops through the process of request reception,task assignment and processing,and result decision at this stage until all of user requests have been processed.
As you can see from the work process,each step action of the MimicCloudSim is driven by a message,and the system can control the simulation process in a single step.Therefore,MimicCloudSim can perform single-step tracking research on the MCS working process,which is difficult to achieve using a physical entity environment.
VI.EXPERIMENTS AND EVALUATION
This section evaluates the decision mechanism and performance of MimicCloudSim.The experimental device uses a Thinkpad T480 notebook computer,configured as:Intel Core i7 1.80GHz CPU and 8 GB RAM,the software system uses Ubuntu Linux version 18.04LTS and JDK 12.0.1,Java configuration is-Xms128m,-Xmx1024m.
6.1 Decision Mechanism Test
In[2,5],the researchers tested the decision of mimic defense Web server in a real experimental environment.We use the MimicCloudSim to verify the same mechanism in this paper.
In order to focus on the validation of mimic defense mechanism and simplify the process,the following definitions and assumptions are made:
Definition 1:If theleakproperty of executor is greater than0,says there are vulnerabilities in the executor.
Definition 2:If therequestproperty implements theIAttackinterface,the request is defined as an attacking request.
Assumption 1:If there are vulnerabilities in the executor,the probability of successful attackP=1.That is,if the attacking request detects that theleakproperty of the executor is greater than0,the attack must succeed.
In this paper,the definition of“k/n ruling”given in[19]is used to compare the processing results ofnexecutors.If there are at leastkexecutors of the output results are the same,the results of the k executors are taken as the final output,which is a relatively correct result.
The experimental design is as follows:three heterogeneous equivalent executors are configured,thekvalue is 2,the number of requests is 3,and all requests are attacks.If the attack is successful,the executor output“√”,otherwise the output is“×”.Based on the above configuration,test A and test B were carried out.The A experiment simulates the existence of vulnerabilities in the No.1 executor,and the B experiment simulates that both the No.1 and No.2 executor have vulnerabilities.
The experimental process is as follows:construct user code to callMimicCloudSim.init()to initialize the simulator,createDatacenterandMimicControllerentities,generate attacking requests,startSimulation()to start the simulation process,getCloudletReceivedList()to obtain simulation results.The detailed process is shown in figure 5:

Figure5.Code for simulation experiment.
The methods code of request and executor generation have been customized before the experiment.The input allocation strategy is realized by inheriting user interface IDispatchPolicy,and the output decision function is realized by inheriting user interface IDecision.The experimental results are shown in table 1.
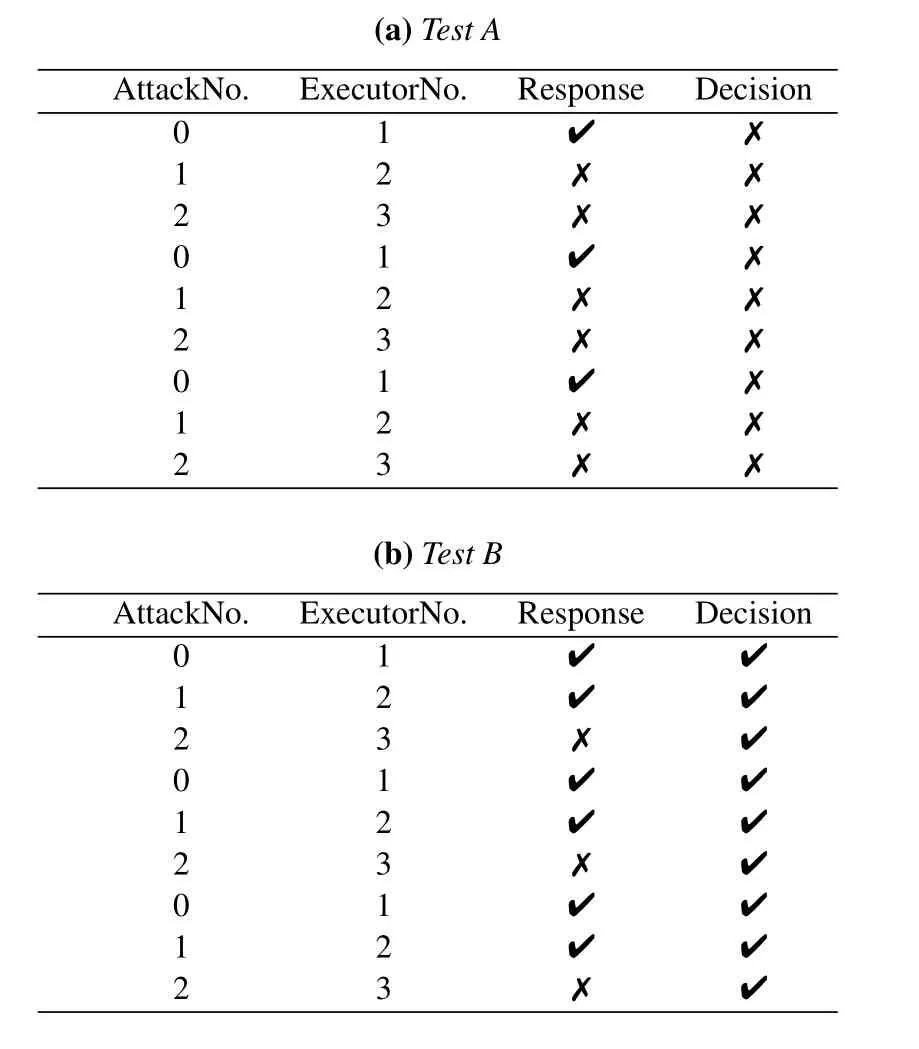
Table1.Decision mechanism test results.
It can be seen from table 1(a)that only the No.1 executor has a vulnerability,which was successfully attacked and output“√”.But,the other executors have no vulnerability,the attack on them failed.So,after the output decision,the output still is “×”,which indicates that the decision mechanism of the simulator has been effective,the output decision function of the controller has played a role,and MimicCloudSim successfully simulated the mimic defense mechanism.
It can be seen from table 1(b)that the No.1 and No.2 executors are all successfully attacked,because both them have vulnerabilities.Therefore,the result of the decision is also success,and output“√”.According to the analysis of mimic escape in [1],the phenomenon of mimic escape appears in test B.This shows that MimicCloudSim can simulate the related risks,which are pointed out in the theory of mimic defense.Thus,MimicCloudSim can be used to analyze the deployment risk related issues of mimic defense.
In addition,through the above experiments,we also verified the following new functions of Mimic-CloudSim:request and response generation;request distribution;executor generation and simple scheduling;user code interface mechanism and so on,these functions work well to get experimental results.
6.2 Cost and Convenience Discussion
In decision mechanism test,[2,5]use a real physical system to carry out experimental.So,it is necessary to invest in multiple server equipmens,install and configure a variety of heterogeneous components and so on.The configuration of[2,5]and MimicCloudSim experimental environment is shown in table 2.
As shown,[2,5]'s purchase list includes:at least 3 servers,multiple operating systems,databases and applications,their purchase cost will be high.Then,researchers need to install and configure them correctly.However,the installation and configuration process is complicated and time-consuming.MimicCloudSim only requires a laptop with Linux,and JDK.The server configuration is shown in table 3.
As shown,[2,5]adopt an enterprise-level dedicated server with high configuration and high price.But,MimicCloudSim uses a general-purpose laptop,and the price is moderate.
Therefore,MimicCloudSim is more convenient than the real physical environment,and has little investment.Researchers interested in CMD technology can easily build an experimental environment.
6.3 Performance Evaluation
Now,we evaluate the performance of Mimic-CloudSim.First,we increase the number of requests and measure the time-consuming growth of Mimic-CloudSim.Secondly,we increase the number of ex-ecutors and measure the time-consuming change of MimicCloudSim.
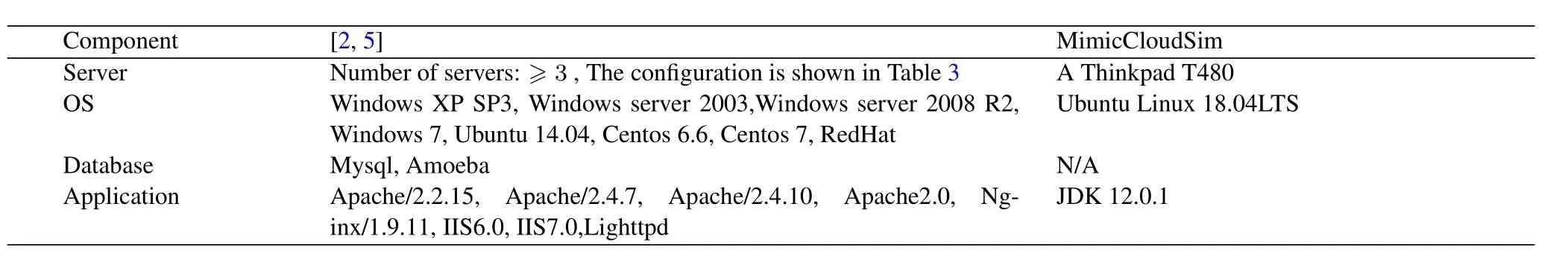
Table2.Test environment configuration.

Table3.Server configuration.
The test parameters for the requests are as follows:the number of requests is from 100,000 to 1 million,and the number of executors is 3.There are vulnerabilities in the No.1 executor.
The test plan is:perform 10 rounds of simulated attack tests,add 100,000 requests per round,and 3 simulation processes per round,take the average of the time spent in the 3 simulation processes.For example:when the number of requests is 100,000,perform 3 mimic defense simulations and take the timeconsuming average of 3 times.
The test parameters for the number of executors are as follows:the number of executors is from 10,000 to 100,000,the number of requests is 100,and there are vulnerabilities in the No.1 executor.
The test plan is:perform 10 rounds of simulated attack tests,add 10,000 executors per round,and 3 simulation processes per round,take the average of the time spent in the 3 simulation processes as the time spent in this round.
The results in figure 6(a) show that the time consumption of the MimicCloudSim has increased substantially linearly with the increase in the number of user requests.When the number of requests reaches 1 million,the simulation process takes more than 6 seconds.Consequently,it can be further considered that the time cost of MimicCloudSim for large-scale requests simulation is acceptable,and the number of supported requests can be greatly increased by optimizing the configuration of the Java memory stack and other aspects.This provides a way for researchers to perform coverage testing and evaluate new mechanism proposed for mimic defense.
The results in figure 6(b) show that the time consumption of the MimicCloudSim also increases linearly,when the number of executors increase.In addition,when the number of executors reaches 70,000,the time-consuming curve becomes steep,the growth of time-consuming speed up.When the number of executors reached 100,000,it took nearly 100 seconds.The figure 6(b) show that increasing the number of executors will lead to greater time consumption,MimicCloudSim is able to simulate such a large number of executors,and the time-consumption is acceptable.However,it is impossible to construct so many executors in a real system.This is also one of the advantages of the simulator.
As a result,the above experiments and discussions show that the functions and performance of Mimic-CloudSim can meet the needs of evaluation work and has excellent expansibility.This is far more convenient than building a real system.
VII.CONCLUSION AND FUTURE WORK
This paper presented a CloudSim-based system called MimicCloudSim for modelling and simulation of CMD mechanism.MimicCloudSim consists of the new features:(1)dynamic heterogeneous redundancy(DHR) structure,(2) request and response simulation,(2) request distribution,(3) response decision,(4) vulnerability and backdoor simulation,(5) easyto-use CMD mechanism implementation interface for user.We present the new functions by using a majority decision mechanisms,and tested the performance of MimicCloudSim.The results show,MimicCloudSim is highly scalable.
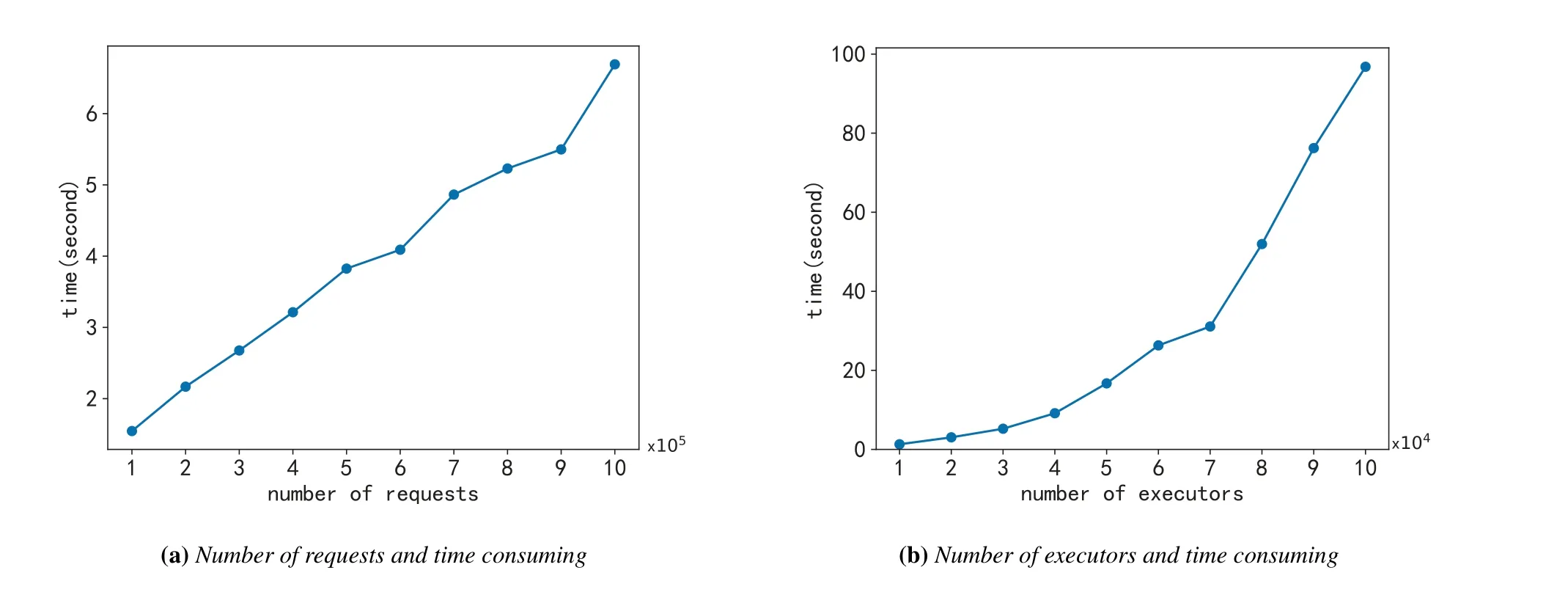
Figure6.MimicCloudSim performance test results.
In future work,we will continue the research work on following aspects but not limited.Firstly,we will provide visualisation results display.We will improve the dynamic scheduling function of the mimic cloud service,which is currently only a simple implementation.We also want to extend our idea and methodology to simulate other mimic applications and security technologies,such as mimic DNS system [4]and MTD technology[20-22].
ACKNOWLEDGEMENT
This work was supported by the National Science and Technology Major Project of China(No.2018ZX03002002) and the Foundation for Innovative Research Groups of the National Natural Science Foundation of China(No.61521003).
- China Communications的其它文章
- Edge Caching in Blockchain Empowered 6G
- Spectrum Prediction Based on GAN and Deep Transfer Learning:A Cross-Band Data Augmentation Framework
- Layered D2D NOMA
- Fully Connected Feedforward Neural Networks Based CSI Feedback Algorithm
- Erasure-Correction-Enhanced Iterative Decoding for LDPC-RS Product Codes
- Power Allocation for NOMA in D2D Relay Communications

