Edge Caching in Blockchain Empowered 6G
Wen Sun,Sheng Li,Yan Zhang
1 School of Cybersecurity,Northwestern Polytechnical University,Xi'an 710072,China
2 School of Cyber Engineering,Xidian University,Xi'an 710071,China
3 University of Oslo,Oslo 0316,Norway
Abstract:The sixth generation(6G)of wireless cellular networks is expected to incorporate the latest developments in network infrastructure and emerging advances in technology.In the age of 6G,edge caching technology will evolve towards intelligence,dynamics,and security.However,the security problems of edge caching,including data tampering and eavesdropping,are seldomly considered in most literatures.In this paper,we consider the two-hop edge caching where the blockchain and physical layer security technologies are adopted to prevent data from being tampered with and eavesdropped.We design blockchain-based framework to guarantee the reliability of important data such as the frequency of contents and jointly optimize content caching probability and redundancy rate to maximize the secure transmission probability.Extensive simulation shows that our optimization scheme can significantly improve the secure transmission probability of edge cache network,whether facing the threat of independent eavesdropping or joint eavesdropping.
Keywords:blockchain;6G;edge caching;physical layer security
I.INTRODUCTION
As the fifth generation (5G) technology enters its final commercial stage,academia,industry,and regulatory agencies have set their sights on the research and development of the sixth generation (6G) of wireless cellular networks [1].By using a full-duplex wireless transmission method in the communication process,6G is capable of transmitting data at a rate of about 1,000 Mbps to users that exceeds their expectations[2,3].The vision of 6G is to build a large-scale connected complex network that can dynamically and rapidly respond to users' service invocations.In 5G network,operators use network slicing and other technologies to provide users with differentiated caching services,while 6G network will further improve user customized caching services by AI-driven prediction[4].For example,the edge caching in 6G is expected to predict the needs of users and adjust the pre-cached content at different periods even during commuting of users [5].The realization of this goal relies on the collection and analyzation of the users'historical data under the premise of protecting user privacy.As a distributed database,the blockchain can realize decentralized transmission and storage of data to prevent the data from being stolen or tampered.Therefore,6G is expected to provide customized caching services for users with the help of edge caching and blockchain technology[6].
In order to provide customized caching service,it is necessary to collect and analyze the information of users.In the traditional way,the collected data will be encrypted and saved to the database,which will make the data easy to be polluted or tampered with,and even leak user private information.Blockchain can record user information safely.The smart contract deployed on the blockchain will reliably calculate parameters required for edge caching and transmission depending on the data recorded on the blockchain.
With the successful practice of blockchain technology in various fields,the application of blockchain in caching networks to resist caching pollution and privacy leakage has attracted more and more attention [7,8].Blockchain technology exploits authentication technology and consensus mechanisms to maintain a distributed and tamper-resistant continuous ledger database.When applied in edge caching,the blockchain stores historical request information in distributed blocks and provides data integrity checking for ensuring that the information is not tampered with.In addition,distributed ledger technology can reduce settlement time due to its ability to speed up transactions.By recording edge service transactions on a large number of edge nodes without third parties or intermediaries participating in the edge service process,blockchain not only solves the problem of single point of failure,but also enables subscribers and service providers to independently process and verify the ledger[9].
Actually,there have been some works applying blockchain to caching networks.For example,Daiet al.[10]integrated artificial intelligence and blockchain into the 6G network and proposed a content caching problem authorized by blockchain to maximize the effectiveness of the system.On this basis,they developed a new caching scheme to realize flexible and secure resource sharing by using deep reinforcement learning.In order to prevent edge nodes from returning incorrect caching contents or viruses to mobile users,Xuet al.[11]proposed a trustworthy edge caching scheme based on blockchain.In this scheme,the blockchain monitors caching transactions between edge nodes and mobile users in a distributed manner,so that no entity can modify or reject the caching contents.Moriet al.[12]designed a secure caching scheme based on blockchain technology in wireless sensor networks.This scheme can not only securely collect data,but also replicate and store decentralized and cross-validated sensor data.
Note that the existing works on cache-enabled networks mainly focus on one-hop transmission scenario where the users are allowed to get contents from the nearest edge server.The existing works are based on the assumption that the information about content request frequency is credible.In fact,the important data may be forged or tampered by attackers,which has an adverse effect on the user privacy and the transmission efficiency.In this paper,we propose a twohop caching framework to maximize the secure transmission probability in blockchain empowered 6G.The main contributions of this paper are summarized as follows:
·Firstly,we design a 6G edge caching architecture driven by blockchain,which can improve the hit rate of edge caching while ensuring the reliability of data.
·Secondly,we use two-hop transmission and probabilistic caching strategy to improve the cache efficiency and make full use of cache resources in our scheme.The security of content transmission is considered in two scenarios:independent eavesdropping and joint eavesdropping.
·Thirdly,we jointly optimize the redundancy rate and content caching probability to maximize the secure transmission probability.Since the optimization problem is a nonconvex optimization problem,we decompose it into two parts:optimizing redundancy rate and optimizing caching probability.
·Fourthly,we conduct extensive performance evaluation through simulations to validate the theoretical analysis and compare the probability caching scheme with some existing caching schemes.The numerical results show that the proposed scheme in this paper is better than the existing caching schemes.
The rest of this paper is organized as follows.Section II discusses related works.Section III introduces the system model of this paper.Section IV presents our blockchain-based edge caching framework.In Section V,we analyze performance and show the optimization scheme for redundancy rate and caching probability.In Section VI,we provide and analyze simulation and numerical results.Finally,Section VII concludes this paper.
II.RELATED WORKS
2.1 6G Vision
The telecommunication infrastructure of the future is conceived as a large-scale connected complex mobile network capable of cultivating an intelligent social system that can respond to the surging demand of users anytime and anywhere.Therefore,the anticipated requirements for 6G in the future will inevitably lead to the evolution of mobile edge computing(MEC)to a platform supporting artificial intelligence (AI)and blockchain,which will be able to provide intelligent services to mobile devices through computationally efficient hardware infrastructures,caching technology and AI algorithms [13],[14].As the nextgeneration mobile communication network,6G will show its talents in fields closely related to human life,such as logistics,entertainment,healthcare,and smart cities,with ultra-high transmission rate and traffic capacity [15].The softwareization,virtualization,and edge cloudization of 6G networks spawns all kinds of emerging vertical services and also exacerbates some problems such as data privacy,network reliability,immutability,and security vulnerability[16].The scarcity of spectrum resources makes it very meaningful to improve the efficiency of spectrum utilization.Spectrum management is an effective way to improve the efficiency of spectrum utilization.The characteristics of blockchain enable the network to manage and share resources more efficiently.The potential of blockchain in various application scenarios for resource management and sharing is discussed in 6G[17].As shown in Figure1,blockchain can strengthen the quality of service (QoS) of 6G from different aspects.In edge caching,blockchain is conducive to audio and video applications by helping base station(BS)cache efficiently.In communication,blockchain can provide more secure and convenient services for smart network,IoV,etc.,such as spectrum sharing,IoV content distribution.In computing,applications such as multiple cloud joint computing,task allocation and smart grids can use blockchain and smart contracts to ensure security.
2.2 Blockchain Based Security Solution
Blockchain also plays an important role in preventing malicious users.Thanget al.[18]proposed a blockchain-based content delivery network architecture.This system will provide virtual identities for users and record users' request records.They ensure the security of these data using the blockchain's non-tamperability.The platform that maintains the database can use the data to get users' preferences.Guoet al.[19]proposed a blockchain based authentication system.A blockchain is used to store authentication data and log information.This provides trusted authentication between different platforms of the Internet of things (IoT).Recently,some researchers have considered the combination of blockchain and edge caching.Xuet al.[11]proposed a trusted edge caching scheme based on blockchain.They use blockchain to record cache transactions between edge nodes and mobile users to ensure that the information will not be tampered with.
2.3 Edge Caching
Many studies have shown that edge caching can effectively reduce the latency of cache-enabled network and improve system efficiency.Vuet al.[20]designed non coding and coding caching strategies to maximize system efficiency through optimization.Yenet al.[21]proposed a cooperative online caching scheme to reduce latency under the assumption that the size of cache space is limited and the probability of various content requests is uncertain.A probabilistic storage scheme is used for edge caching to improve the hit rate and content diversity.Blaszczyszynet al.[22]proposed probability caching schemes,and proved their effectiveness in improving hit rate.Serbetciet al.[23]extended the study in literature[22]to consider heterogeneous networks of BSs with different caching capabilities.Zhanget al.[24]proposed a task offloading scheme based on mobile edge computing to meet the computing needs of resource-constrained vehicles for autonomous driving.Researchers try to solve the security problems in wireless transmission through physical layer security(PLS)[25].Wyner[26]showed that adding enough redundancy to the original transmission rate can effectively prevent eavesdropping attacks when the legitimate channel is better than the eavesdropping channel.Sunet al.[27]consider resource sharing based on social-aware incentive mechanisms to make full use of edge resources.Zhanget al.[28]designed a probability caching scheme and prevented eavesdropping by adding redundant rates.They also designed algorithms to optimize redundancy rate and caching probability based on CSI information and the popularity of the content.
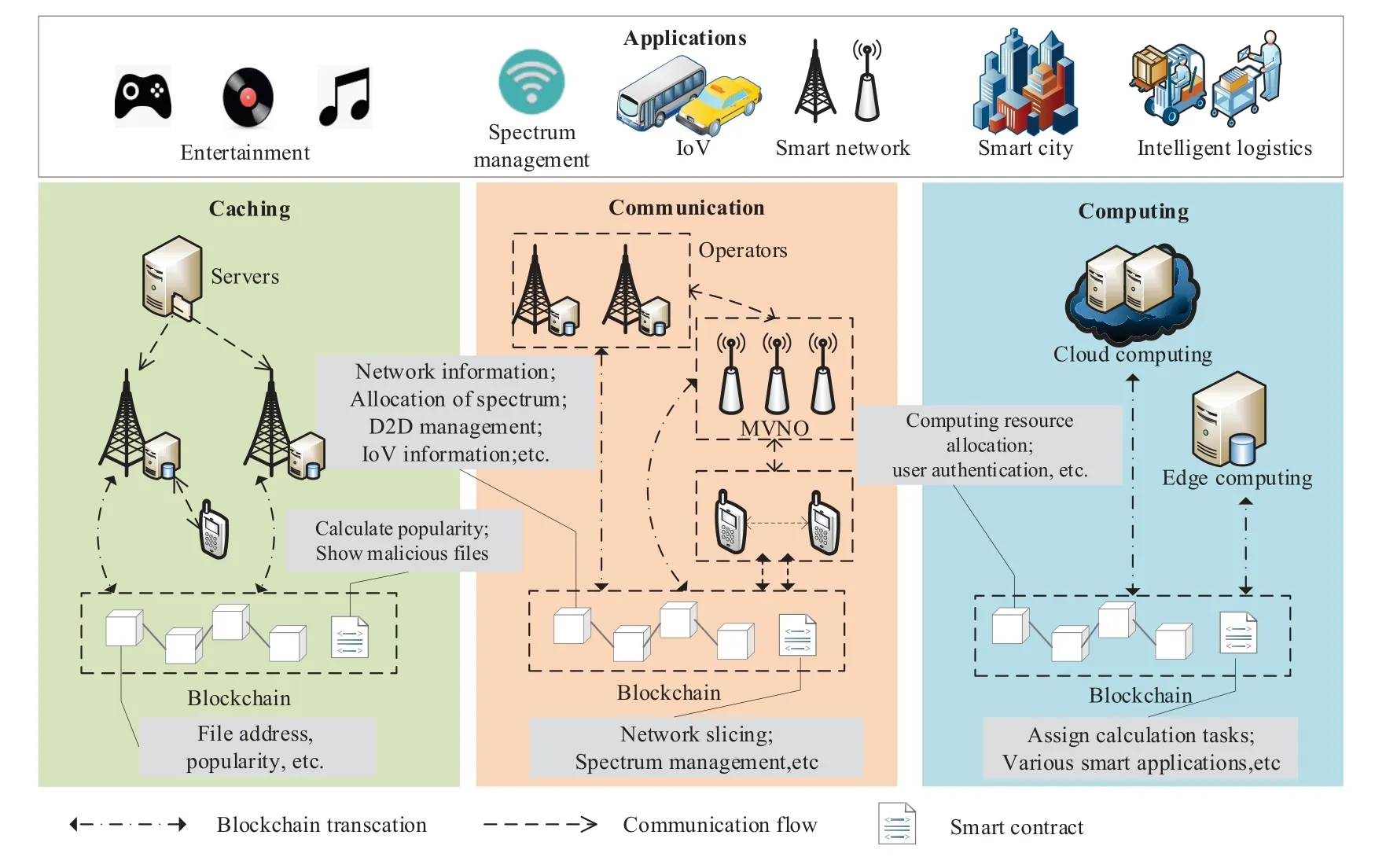
Figure1.Blockchain-enhanced 6G network framework
Note that the existing works on PLS of cacheenabled networks mainly focus on one-hop transmission model.This paper considers a more complex cache-enabled network with two-hop transmission model.In addition,we design a blockchain-based framework to guarantee the reliability of data such as content request frequency and jointly optimize the redundancy rate and content caching probability to maximize the secure transmission probability.
III.SYSTEM MODEL
3.1 Network Model
As shown in Figure2,we study secure transmission in a network with randomly distributed legitimate users,BSs and eavesdroppers.
The database of central server storesNcontents denoted byN={1,2,···,N}and the set of BSs isM={1,2,···,M}.Each of these BSs can connect to the central server and download content in off-peak period.For instance,BS1 can connect to the server to pre-cache some contents in Figure2.We assume that the set of legitimate users isI={1,2,···,I}and the set of eavesdroppers isJ={1,2,···,J}.When a BS receives a request for a content,the BS will transmit the content directly to the requester if the requested content has been pre-cached.For example,UE2 in the Figure2 can get the target content 1 directly from BS3.Otherwise,the BS will send a request to another BS or download the requested content from the central server and transmit it to the requester.This is how UE1 in the Figure2 gets the target content 2 from BS2.Legitimate users may be eavesdropped by eavesdroppers when they receive content.For example,when UE1 receives the information sent from BS1,Eve1 and Eve2 around BS1 try to intercept and decode the information.
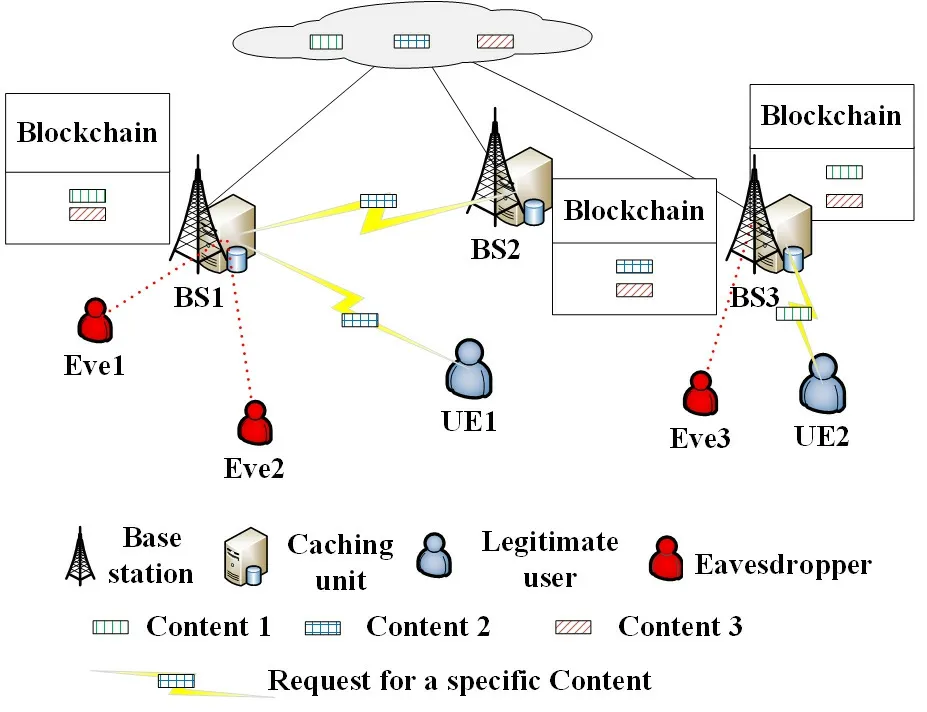
Figure2.An example of edge caching in the presence of eavesdroppers.
In this paper,the distribution of BSs,legitimate users and eavesdroppers follow the Poisson point process (PPP) in two-dimensional plane with density ofλb,λuandλe.The statistical channel state information(CSI) is available.We use standard distance-based path loss model,wherePis the power of the BS,lis the distance between a signal receiver such as legitimate user or eavesdropper and the target BS,andαis the path-loss exponent.ThenPl(−α)represents the power of the receiver to receive information,and we useσ2to refer to the noise power,then the signal-tonoise ratio can be expressed as
3.2 Caching Model
We assume all contents are of the same size and the rule of how often the contents are requested by users is described by the Zipf distribution.The probability of then-th popular content is requested by a user can be expressed as:
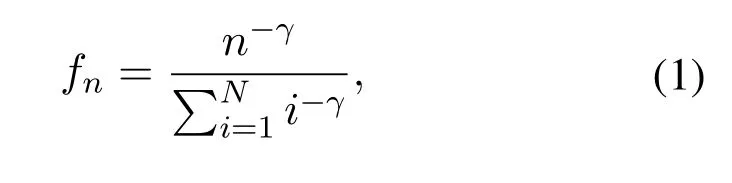
whereγrefers to the parameter of Zipf distribution.The popularity of contents is ranked by the request frequency of different contents collected by all BSs.The request frequency of a certain content refers to the number of requests for this content received by a BS in a period of time,which can be tampered (this will be considered in subsection 3.3).
Each BS has limited caching capacityC.The caching capacity of the BS is not enough to cache all contents.A listA={a1,a2,...,an,...,aN}is the caching probability of all contents,anrefers to the probability that then-th popular content will be cached when a BS pre-caches contents.The listAhas the following restrictions:
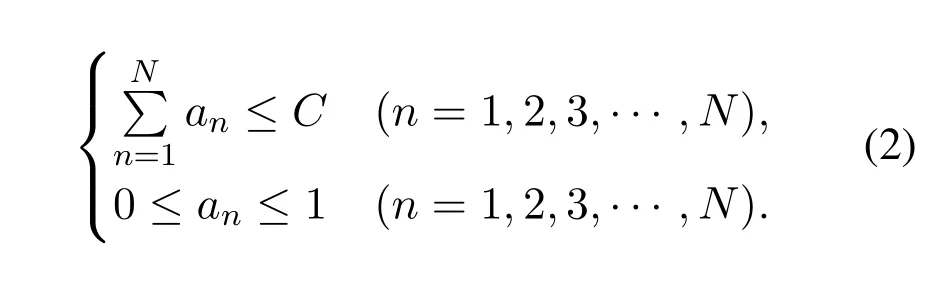
3.3 The Blockchain-based Edge Caching
User information and data analysis results,such as user request records,request frequency and caching probability,are very critical.If these data are tampered with or tainted,it will have an adverse effect on the efficiency of the scheme and the privacy of users.Blockchain,as a distributed database,can securely record user information.Through this design,we can cache appropriate contents at the edge according to the needs of users to provide users with better service.In addition,the anonymity of blockchain makes the recorded data only trace back to the public key representing user's identity,which can protect user's privacy.
By using blockchain and smart contract,we can obtain these characteristics:
·Tamper-proof:With the help of consensus mechanism and data storage structure Merkle,data in the blockchain cannot be tampered with.This ensures the basic data is reliable.
·Unforgeability:Each node has its own publicprivate key pair,thus they can add a digital signature to the messages they send.This prevents attacker from masquerading as legitimate node.
·Fairness:The data processing algorithm is deployed on the smart contract.Due to the consensus mechanism and non-tamperability,the algorithm will be executed fairly.
3.4 Performance Metrics
In this paper,we use connection probability and confidentiality probability as metrics to measure the performance of our scheme.RsandRvare used to express the original transmission rate and redundant transmission rate respectively.According to Shannon's theorem,we can deduce that the transmission capability of the legitimate user channel and the eavesdropper channel are expressed asIfCb ≥Rs+Rv,the connection can be successfully established.IfCe ≤Rv,we believe that the transmission is confidential,which means that the eavesdropper cannot eavesdrop the content.Hence,the connection probabilityPcand confidentiality probabilityPsare expressed as:
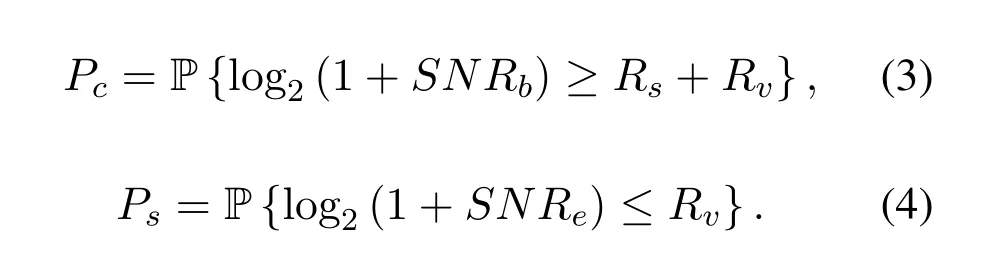
IV.A BLOCKCHAIN-BASED EDGE CACHING FRAMEWORK
4.1 Blockchain Framework
In order to solve the security problem in edge caching,we design a resource storage framework based on blockchain.In the proposed framework,we deploy blockchain on all BSs.The function of this framework includes recording and ensuring the reliability of important data such as the request frequency of different contents,and obtaining the redundancy rate and content caching probability according to recorded data.There are two types of participants i.e.BSs and users in our framework.BSs,as the full nodes in blockchain,have the opportunity to obtain the release right of data block and are responsible for the verification of data block.Users in the network are designed as light nodes that can publish transaction but not data block.In our framework,blockchain,data block and smart contract are very critical components.The details are as follows:
·Transaction:Legitimate users send request for certain content to BSs in the form of transaction.The transaction is a packet with sender's digital signature including sender's information,receiver's information and details of the request.
·Data block:We previously assumed that only full nodes i.e.BS can send blocks to the blockchain.There are two types of information recorded in the data block,i.e.,requests in the form of transaction in a period of time and parameters such as caching probability and redundancy rate calculated by calling smart contract.
·Smart contract:A smart contract is a set of commitments defined in digital form,including agreements on which contract participants can execute these commitments.In our framework,algorithms for computing redundancy rate and caching probability are deployed in smart contract.Depending on the recorded user request information,BSs can obtain these two parameters by calling smart contract.The calculation process is as follows:First,the popularity ranking of different contents is obtained according to the records in the block,and then the probability of different contents being requested is calculated.Secondly,the optimal caching probability and redundancy rate are calculated according to parameters such as probability of different contents being requested,transmission rate,and SNR.
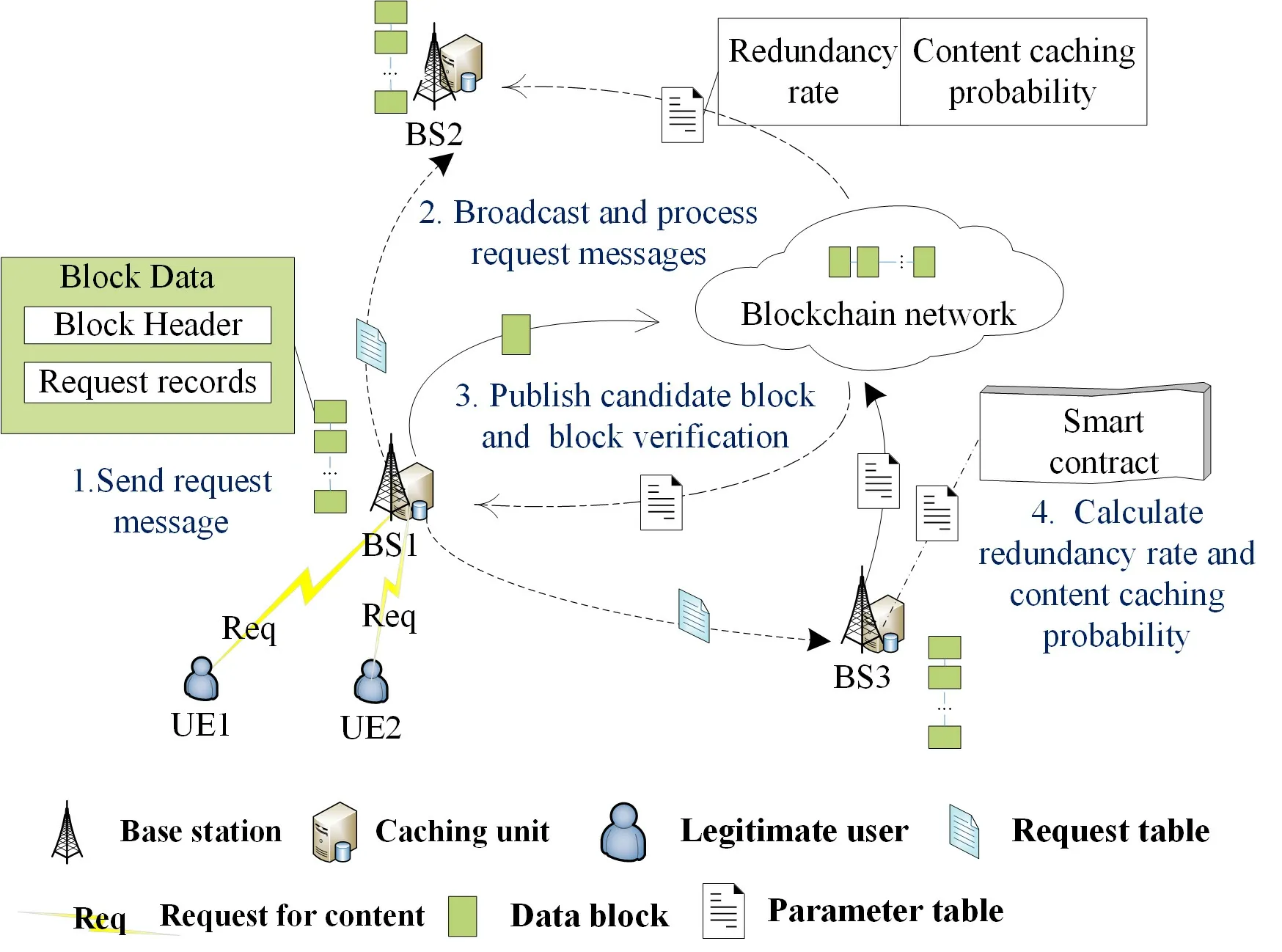
Figure3.Blockchain process in edge caching for keeping tamper-resistent historical requests from users.
·Consensus mechanism:Proof of stake (PoS) is a consensus mechanism in which the probability of accounting right obtained by a node is positively correlated with the coinage of the node.As compared with PoW,PoS consensus mechanism needs less computation,thus can update data quickly.Considering that redundancy rate and content caching probability are of great significance for secure transmission,it is very important to update these two parameters in time.
Figure3 shows the brief operation process of the blockchain framework.The specific process of the framework is as follows:
Step 1.Send request message:Requester such as user will send requests for some contents in the form of transaction.In order to ensure the traceability of transaction,each requester needs to add a digital signature generated using private key at the end of his transaction.
Step 2.Broadcast and process request messages:When a BS receives a request,it will record the request if the signature in the request is verified.Then,the BS broadcasts the record of this request to all other BSs and pack the record into its candidate block.After a period of collection,the BS will call the smart contract to process these records to get the request frequency of different contents and the popularity ranking of all contents.The BS packs the request frequency of different contents and the ranking result into block.
Step 3.Publish candidate block and block verification:A BS is selected to publish its candidate block according to the PoS consensus mechanism.The BS will broadcast its block to other BSs and the rest of BSs need to complete the verification of the block.BSs receive the block and verify the data in the block.They will call the smart contract and use the records of requests in the block to recalculate the popularity ranking of contents.If the result of their calculation is consistent with the result in the block,then they believe the block is correct.When more than two-thirds of BSs in the network believe the block is correct,the block can be added to the blockchain.
Step 4.Calculate redundancy rate and content caching probability:After a period of time,the interval should be long enough to make the recorded historical data fully reflect the popularity of different contents in this region,a BS is selected to take charge of solving redundant rateRvand caching probabilityA.It needs to call the smart contract according to the records in all blocks to calculate the popularity ranking of contents,model the probability of contents are requested and getRvandA.When the result is calculated,it packsRvandAinto a block and broadcasts the block to other BSs.After the block is verified,it can be added to the blockchain.All BSs can query the values ofRvandAon the blockchain,which can ensure that the value of these two parameters are the same in them.
As mentioned above,a blockchain based framework enables us to record historical data safely and update important parametersRvandAeffectively.
4.2 Two-Hop Transmission Scheme
We consider two hop transmission scheme in this paper.Two hop transmission scheme can make full use of caching resources,which makes it possible for legitimate users to obtain the required resources from edge servers.Therefore,the two-hop scheme can effectively reduce backhaul traffic and alleviate network congestion.Noting that the two hop transmission scheme is potentially exposed to eavesdropping risk,thus in this paper,we design a framework based on blockchain to calculate parameters used for caching and transmission to obtain high secure transmission probability.
In our scheme,BSs will pre-cache content during off-peak traffic periods so that legitimate users can obtain some requested resources at the edge.In the blockchain framework,legitimate users send their requests to BSs in the form of transaction,and BSs pack all transactions in a period of time into a data block and publish it on the blockchain.The non tamperability of blockchain provides security for the records of requests.With the help of the request information recorded by the blockchain,BS calls the smart contract to update the optimal parameters such as caching probability of different contents and redundancy rate to achieve a higher secure transmission rate.
When a BS receives a request for a content from a user or another BS,it will choose its own action according to the situation.When a legitimate user wants to get a content,it first tries to connect to the BS closest to it.
1.Case 1:If the BS can be successfully connected and it caches the requested content in advance,the BS will directly transmit the content to the user.
2.Case 2:If the BS can be successfully connected and it does not store the requested content in advance,the BS attempts to connect to another BS closest to it.There are two cases:
·If the second hop BS caches the requested content in advance,it will transmit the content to the requesting BS,and the BS will then transmit it to the user.
·If the second hop BS does not store the corresponding content,it will simply reply a message to the first BS to indicate the situation.After the first BS receives the reply,it no longer attempts to connect to a new BS,but connects to the central server and downloads the content from the central server,and then transmits the content to the user.
Legitimate users use the pre-cached contents of BSs to obtain the requested content through at most two hops.For this reason,the probability that users can get specificn-th content securely is regarded as the sum of the probability that users can get then-th popular content securely at the first hoppn1and the probability that users can get then-th popular content securely at the second hoppn2.In summary,the probability of secure transmission can be expressed as:
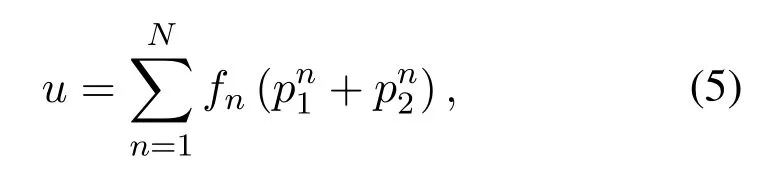
wherefnis the probability of then-th popular content is requested.
The secure transmission refers to the transmission when the user establishes a reliable connection with the BS and the confidentiality of the content can be guaranteed during the transmission.The event of obtaining then-th content in the first hop is equivalent to that the user can establish a connection with the nearest BS and the BS caches then-th content in advance,at the same time,the content will not be eavesdropped in the transmission.Thuspn1can be expressed as:

Then the event of obtaining then-th content in the second hop is equivalent to that the BS connected by the user in the first hop is secure but does not store then-th content,and the BS can be safely connected to another BS closest to it,and this BS contains the request content.Thepn2can be expressed as:
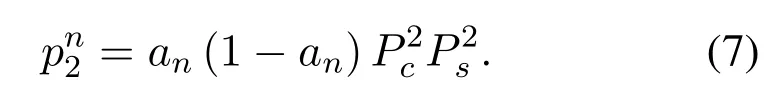
We consider two scenarios:independent eavesdropping and joint eavesdropping.In the independent eavesdropping scenario,each eavesdropper independently tries to decode the information.In the joint eavesdropping scenario,at most two eavesdroppers work together to decode the information.We will make further discussion on different scenarios in the next part.
V.PERFORMANCE ANALYSIS AND OPTIMIZATION
In this section,we mainly analyze performance and maximize the probability of secure transmission by optimizing the redundant rateRvand caching probabilityA.We consider the security of content transmission in two scenarios:independent eavesdropping and joint eavesdropping.
5.1 Independent Eavesdropping
Independent eavesdropping means that each eavesdropper independently decodes the information they intercepted.Secure transmission refers to establishing a reliable connection and ensuring the confidentiality of the transmitted content.Therefore,the secure transmission probability mainly consists of the connection probabilityPcand the confidentiality probabilityPs.In this section we first analyze thePcandPsrespectively.
5.1.1 Probabilities Analysis
A successful connection between a user and a BS occurs when the transmission capacity of the channel between them is greater than the sum of the original rateRsand the redundant rateRv.Then the connection probabilityPccan be expressed as:
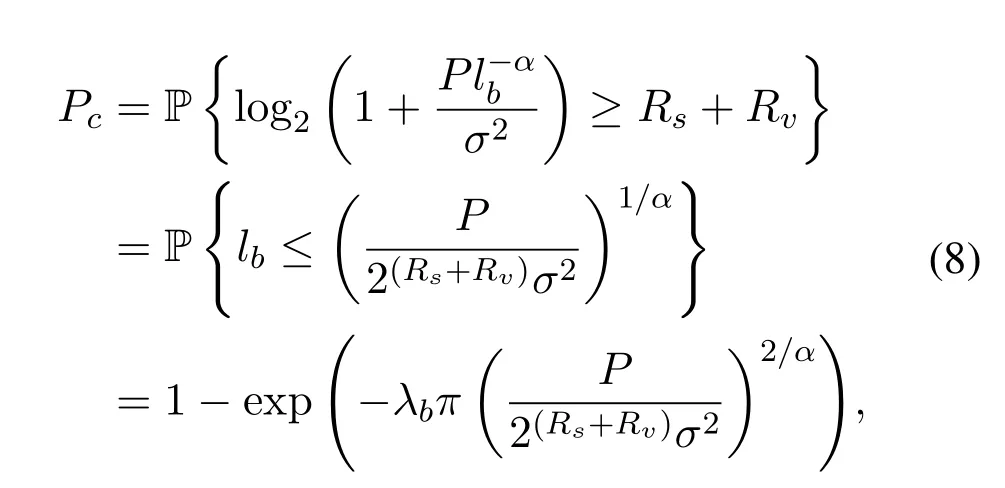
If the transmission capacity of the channel between the BS and the nearest eavesdropper is less than the redundancy rate,the transmission is confidential.The distribution of eavesdroppers follows PPP in 2-D plane with the densityλe.Thus,the confidentiality probabilityPsis:
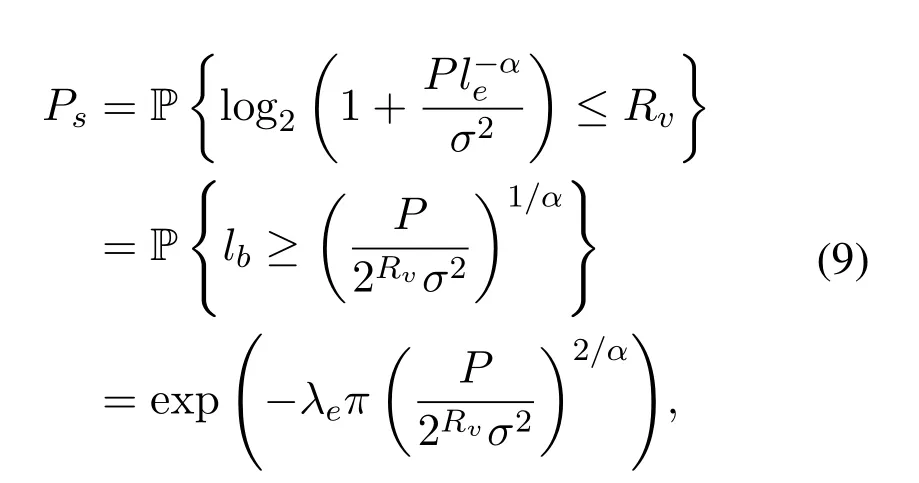
5.1.2 Optimization Scheme
In order to maximize the probability of secure transmission,we jointly optimize the redundancy rateRvand caching probabilityA.The optimization problem is defined as:
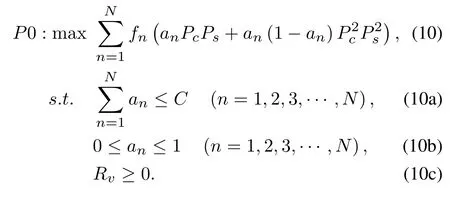
The constraint (10a) means that the total amount of contents cached by the BS cannot exceed the capacity of the BS.The constraint(10b)refers that every content may be pre-cached with different probability.The constraint(10c)indicates that the redundancy rate can only be positive.
This problem is a nonconvex optimization problem.The optimization ofAandRvis independent of each other.The problem is solved by decomposing it into two parts:optimizingRv(Eqn.(11)) and optimizingA(Eqn.(19)).The optimization problem ofRvcan be expressed as follows:
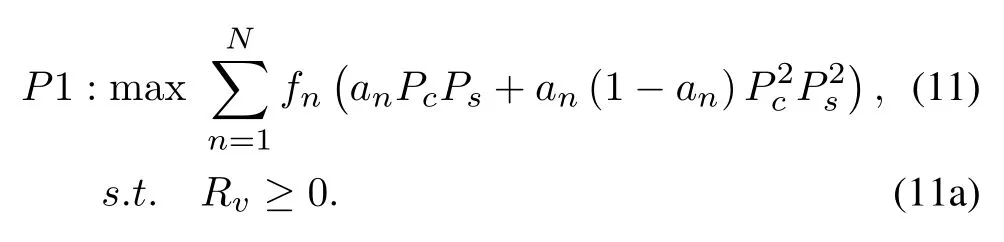
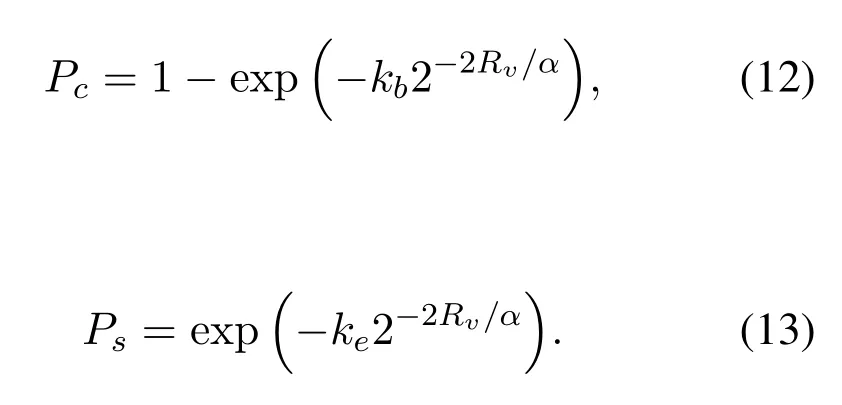
In order to get the optimal solutionwe first determine the concavity and convexity of the objective function.
Lemma 1.The expression PcPs is a concave function with respect to Rv when Rv >0,and the maximumpoint is
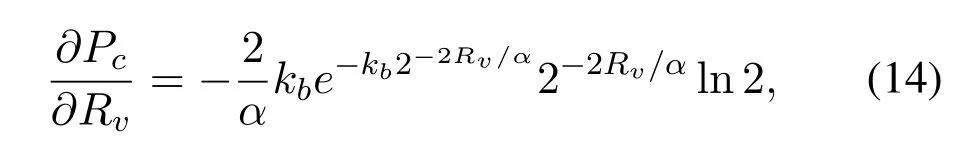
Proof.We compute the first derivative ofPcwith respect toRv:similarly,we can get the first derivative ofPswith respect toRv:
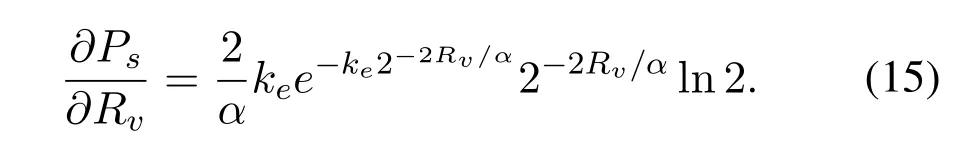
Now,we can get the first derivative ofPsPswith respect toRv:
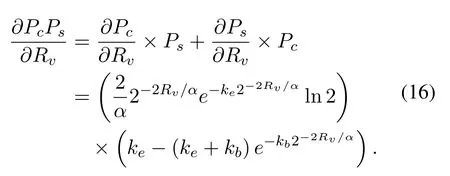
The result of Eqn.(16) consists of two formulas for multiplying.Theis always positive,thus whether the result of Eqn.(16)is positive or negative depends on the part after the multiplier sign.According to the characteristics of exponential function,the expressionis monotonically decreasing withRv,and we can obtain the solution that it is equal to zero as follows:
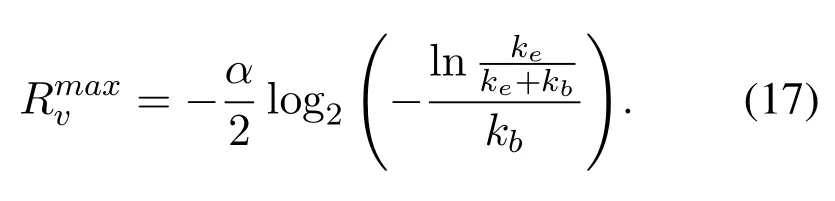
Theorem 1.The problem P1is a concave problemwhen Rv >0,and the maximum point is
Proof.We first find the first derivative of the objective function forRv:
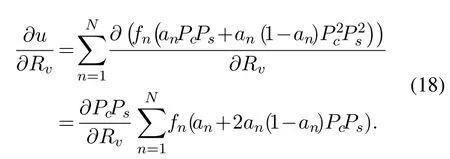
Observation shows that the part of the expressionother thanis always positive,thuswhether is positive or negative depends onAccording to our lemma 1,thePcPsis a concave function and the maximum point isThusis positive whenis negative whenwhenTheuis a concave function whenRv >0,and the maximum point is
At the same time,it can also be explained that the optimization ofRvand the optimization ofAare independent.
The optimization problem ofAcan be expressed as follows:
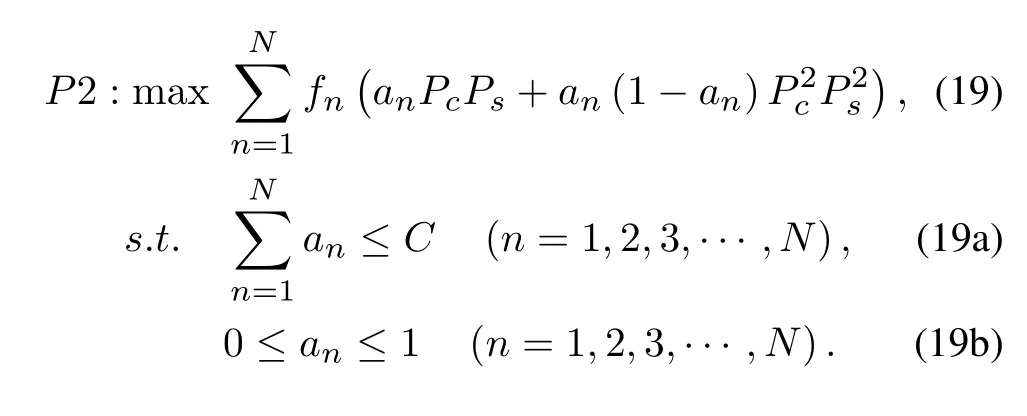
ThePc,Ps,andfnin the problemP2 are all independent of the variableA.Hessian matrix ofAis used to judge whether this multivariate function is a concave function.
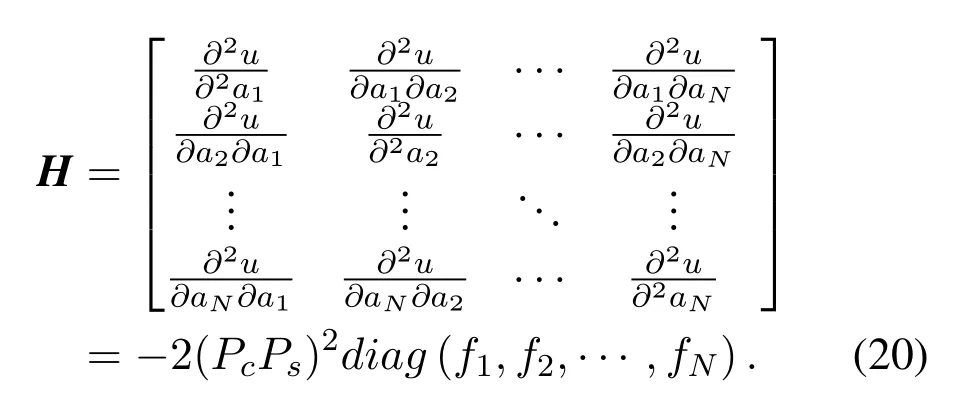
After calculation,whenanis in the interval[0,1],the Hessian matrixHis a negative definite matrix.This means that the optimization ofAis a convex optimization problem.It can be solved by calling thefminconmodule of MATLAB.
In summary,this optimization problem can be solved by decomposing the problem into optimization ofRvand optimization ofA.
5.2 Joint Eavesdropping
Joint eavesdropping scenario refers to a situation in which eavesdroppers work together to decode the information they intercept,we believe that the confidentiality of the transmission process means that the most threatening eavesdroppers fail to decode information cooperatively.It is expressed asPs=We assume that the distribution of eavesdropper and BSs satisfies the two-dimensional PPP,and the density of eavesdropper distribution in this network is lower than that of BS.According to the two-dimensional PPP distribution,the area of the ring between the adjacent eavesdroppers around the target BS satisfies the exponential distribution,and the signal strength decreases exponentially with respect to the distance parameter,so in fact,the gain provided by the third nearest eavesdropper can be almost ignored.This also applies to eavesdroppers farther away from the target BS.Therefore,we ignore the case of joint eavesdropping by more than two eavesdroppers to simplify the calculation.In other words,the new confidentiality probability expression is:Ps=P{log2(1+SNRe1+SNRe2)≤Rv}.
5.2.1 Probability Analysis
Consistent with the independent eavesdropping scenario,a successful connection means that the transmission capacity of the channel between the user and the BS is greater than the sum of the original rateRsand the redundancy rateRv.The distribution of BSs meets PPP and the density isλb.The connection probability is still expressed as:
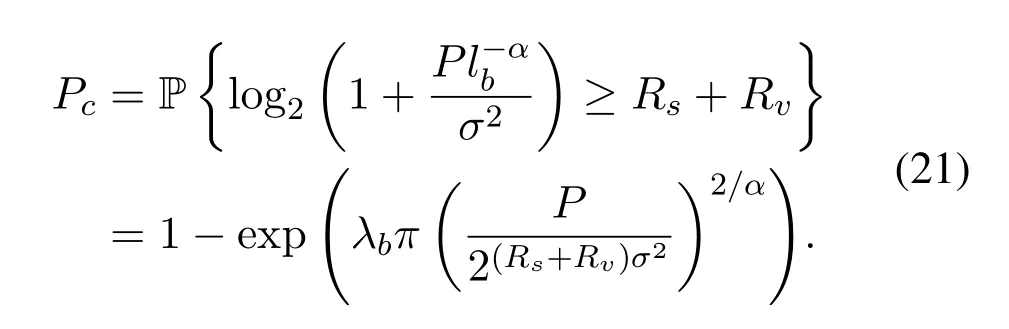
In the case of joint eavesdropping,at most two eavesdroppers cooperate to decode information.The successful eavesdropping event can be divided into two parts:the nearest eavesdropper completes the eavesdropping independently and the nearest two eavesdroppers complete the eavesdropping when the nearest eavesdropper fails.The probabilities of these two parts areps1andps2,respectively.In summary,the expression of confidentiality probabilityPsis
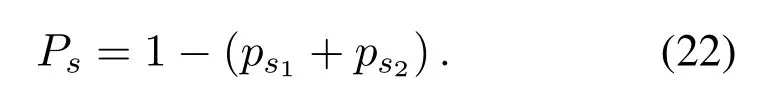
The event that the nearest eavesdropper succeeded in eavesdropping alone is similar to the eavesdropping success event in the independent eavesdropping situation.Similarly,this can be expressed as
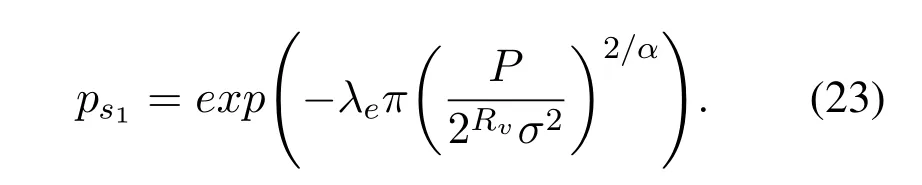
Formula (24) is the probability of the second case of joint eavesdropping.The integrated formula is the joint distribution of the distance between the two closest eavesdroppers and the target BS,which can be expressed asThe integration interval of the first integration is the range of the distancer1between the nearest eavesdropper and the target BS.The lower limit of the first integral is the minimum distance that the nearest eavesdropper fails to eavesdrop,and the upper limit is the minimum distance that two nearest eavesdroppers cannot cooperate to successfully eavesdrop.In fact,we assume that the second eavesdropper is always farther from the target BS than the first eavesdropper.The range of the distancer1isWe setd1=The integral interval of the second integral is the range of the distance between the second nearest eavesdropper and the target BS.The lower limit is the distance between the first eavesdropper and the target BS,and the upper limit is the maximum distance that the second eavesdropper can successfully eavesdrop when the distance between the first eavesdropper and the target BS are fixed.
Therefore,the expression of the second case is:
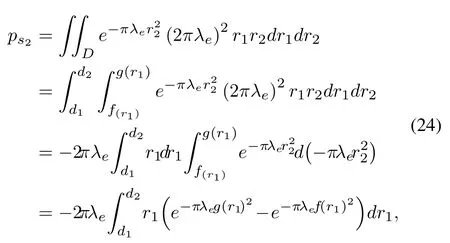
wheref(r1)=r1andg(r1)=r2refers to the distance between the second eavesdropper and the target BS.
5.2.2 Optimization Scheme
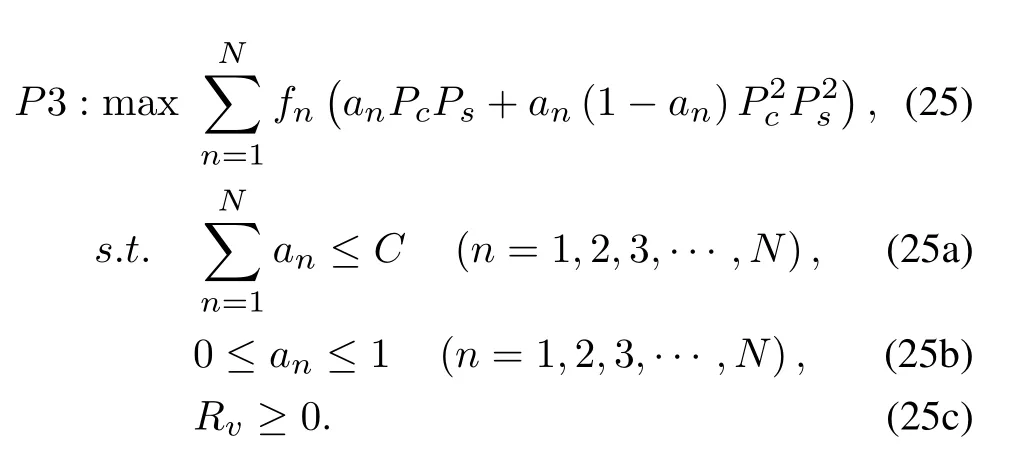
The optimization problem can be expressed as:This function is similar in form as Eqn.(10).The optimization of objective function is also a nonconvex optimization problem.The problem is divided into into two parts:optimizingRv(Eqn.(26)) andA(Eqn.(27))respectively.The optimization problem ofRvcan be expressed as follows:
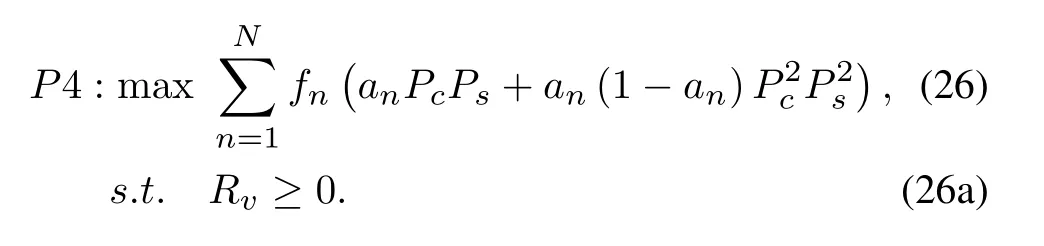
The expression of secrecy probability isPs=1-(ps1+ps2)in the joint eavesdropping scenario.Sinceps2is an integral expression with variableRvin its integrand,the first derivative ofPsaboutRvcannot be obtained as before to judge whetheruis a concave function.However,ps2≪ps1.The optimization ofRvis considered as a convex optimization according to Eqn.(16)if we ignoreps2.Since the first derivative of Eqn.(16) cannot be achieved,the following methods are used to approximate the optimal solution of the problem.The redundant rateRvis a variable with a lower limit of zero and no upper limit.The process of optimizing it can be divided into two stages:the forward and backward method is used to obtain a single peak interval,where the maximum point is located;then the bisection method is used to gradually approach the solution.The details of the algorithm are given in Algorithm 1,2.The optimization problem ofAcan be expressed as follows:

?
The optimization scheme in the joint eavesdropping scenario is almost the same as that in the independent eavesdropping scenario,and there is no problem just like that in the optimization ofRv.Hessian matrix ofAis used to judge whether the multivariate function is concave or not.
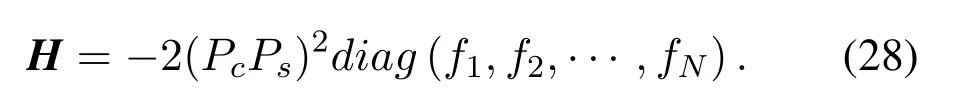
Obviously,this is still a negative definite matrix.It is proved that the objective function is a concave function.In other words,the optimization ofAis a convex optimization problem.It can be solved this by calling thefminconmodule of MATLAB.
VI.SIMULATION RESULTS
6.1 Simulation Settings
?
In this section,we show the performance of the proposed caching scheme and compare it with the existing schemes.In our simulation process,without special instructions,the parameters in the two-dimensional model are set as follows:SNR==30dB,path attenuation indexα=4,both in the eavesdropper channel and in the legitimate channel.We set the distribution density of eavesdroppersλe=1/km2,the distribution density of BSsλb=100/km2.In order to carry out the simulation,we assume that the number of contents in the content library isN=10,and the storage capacity of the BS isC=5.Without losing generality,the legitimate user is assumed to be at the origin of the coordinate in the simulation[29].In the blockchain-related simulation,we used the Ethereum client to build an actual blockchain and deployed our smart contract on it to ensure authenticity.We assume that the block size is 3239 bytes,which contains 19 transactions,the size of each transaction is about 170 bytes,and the proportion of shares held by each participant in the PoS consensus mechanism is a uniformly distributed random number in(0.05,1)[30].
6.2 Simulation Results
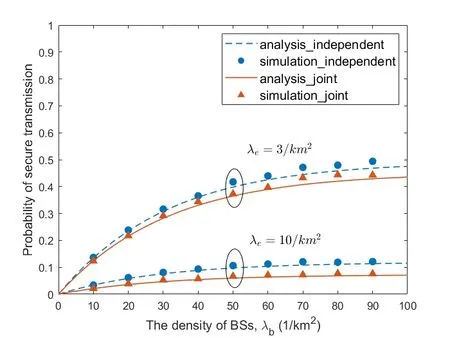
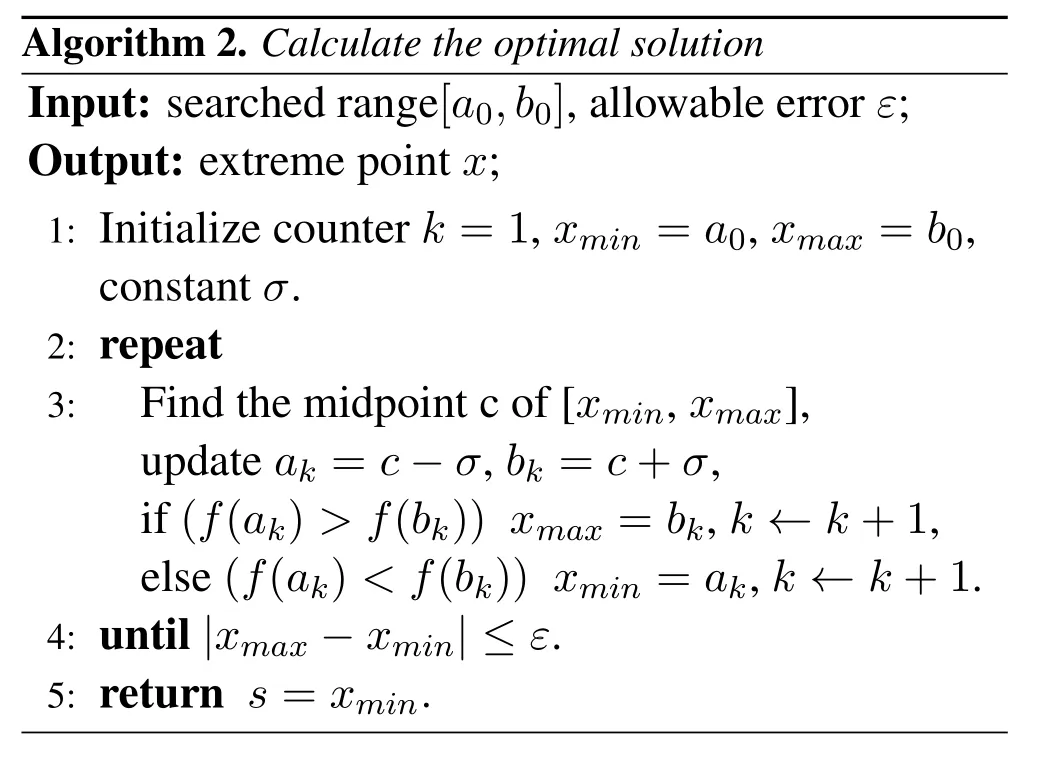
Figure4.Simulation results and analysis results under different BS density in independent eavesdropping scenario and joint eavesdropping scenario.
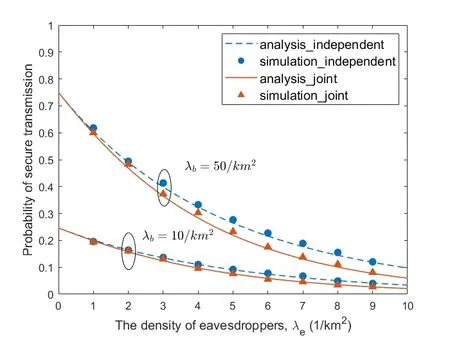
Figure5.Simulation results and analysis results under different eavesdropper density in independent eavesdropping scenario and joint eavesdropping scenario.
Figure6.The secure transmission probability changes with redundancy rate Rv under different transmission rate Rs in the independent eavesdropping scenario.
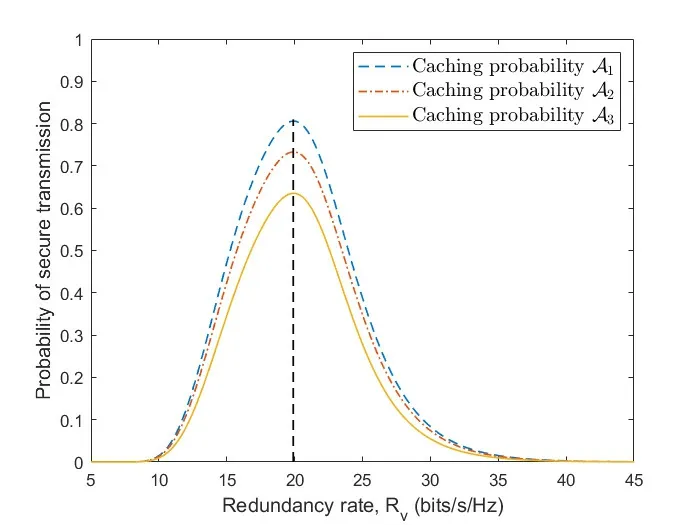
Figure7.The secure transmission probability with different caching probability A changes with the redundancy rate Rv when Rs=3(bits/s/Hz) in the joint eavesdropping scenario.
Figure4 and Figure5 respectively show the secure transmission probability changes with BS density and eavesdropper density in independent eavesdropping scenario and joint eavesdropping scenario.We use Monte Carlo methods to obtain our simulation results.Each simulation result was obtained through 10,000 iterations.From the figure we can see that the simulation results are consistent with the theoretical analysis results,which shows that our formula is reasonable.We observe that the probability of secure transmission increases as the BS density increases and decreases as the eavesdropper density increases.When the BS density increases,it means that users have a greater chance to get the requested content from BS.However,when the density of eavesdroppers increases,it means that the risk of eavesdropping is also increased in the process of content transmission.We find that the probability value in the independent eavesdropping scenario is slightly higher than the probability value in the joint eavesdropping scenario,which is because the risk of content being eavesdropped in joint eavesdropping is higher than independent eavesdropping.Figure6 shows that the probability of secure transmission changes with the redundancy rateRvunder different transmission ratesRs.We find that the probability of secure transmission first increases withRvand then decreases withRv.The probability of secure transmission is a concave function as we demonstrated in the previous chapter.The value of the maximum point of each curve in Figure6 iswhich also validates our previous analysis.From the comparison of the three curves,we can see that when the value of the transmission rateRsis smaller,the corresponding optimal redundant ratewill be larger.At the same time,the probability of secure transmission is higher when the transmission rateRsis smaller under the same redundancy rateRv.Even if they are under the condition of optimal redundancy rate,the value of the curve is still larger under the condition of lower transmission rateRs.This shows that when the original transmission rateRsis low,it has advantage in secure transmission.Figure7 shows that the probability of secure transmission changes with the redundancy rateRvunder different caching probabilityAin joint eavesdropping scenario.As indicated by the vertical dotted line in the figure,we find that when the transmission rateRsis fixed,the value of the optimal redundancy rateRvis not affected by the caching probabilityA.This verifies our previous conclusion:the optimization ofRvandAis independent of each other.Figure8 illustrates the comparison of the performance of the scheme and some existing schemes,including most popular caching scheme (MPC) and uniform caching scheme(UC).MPC scheme is that BS stores the most popular contents as much as possible.In UC scheme,probabilities of all contents stored by BS is 1/N.The figure shows the secure transmission probability of the three schemes changes with the parameterγ.First of all,we can see that the probability of secure transmission of UC does not change withγ,becauseγdoes not affectAin this scheme.In contrast,asγincreases,the number of requests for the most popular contents in the model will occupy a larger proportion.Therefore,the value of the secure transmission probability of MPC will gradually increase.Secondly,we find that our scheme is better than the other two schemes.When theγis smaller,the gap between the curves is larger.But with the increase ofγ,the curve corresponding to our scheme and MPC scheme gradually becomes consistent.The reason is that as the number of requests for the most popular content in the model occupies a larger proportion,the optimization result of our scheme forAis to increase the probability of storing these content.The value of the probability of these top-ranked contents approaches 1,and the rest of the other contents approaches 0.This result is similar to MPC scheme.Figure9 shows that the secure transmission probability changes with theλbin three schemes.As can be seen,our scheme is always better than the other two schemes.This phenomenon is consistent with Figure8.At the same time,whenγ=0.5,the performance of MPC may be better than UC.This is inconsistent with Figure8.The reason is that Figure8 is a simulation result obtained when the BS density is 100/km2.When the performance of MPC in the figure is better than UC,the density of BSs is less than 100/km2.Figure10 shows the comparison of the probability that the requested content can be searched in the case of one-hop and twohop.From the figure we observe that the probability in the case of two-hop is always greater than that in the case of one-hop.At the same time,we find that with the increase of BS density,the gap between the two curves first increases,and finally tends to be stable.The reason is that as the density of BSs gradually increases,the main factor limiting the probability is no longer the density of BSs but the caching capacity of BS.Figure11 shows how the failure probability of the whole system changes with the failure probability of each BS affected by the attack.The security of PoS consensus mechanism is directly related to the shares held by each node in the system.Specifically,we believe that the whole blockchain system can work if the proportion of shares held by honest nodes in the whole system is more than 51%.We assume that the proportion of shares held by each BS in the system is a single uniformly distributed random number in the interval (0.05,1).From the figure,we can see that the failure probability of the whole system is always 0.1% of the failure probability of each BS in the centralized system.With the decrease of failure probability of each BS,the failure probability of blockchain system decreases more rapidly compared to the centralized system.In addition,with the increase of the number of BSs in the blockchain system,the security of the whole system will be significantly improved.This means that the security performance of the whole system will be greatly increased if a small amount of security resources are invested in each BS.Figure12 shows the relationship between the number of transactions and occupied storage space.Legitimate users only send and do not store transactions.Transactions data is stored in the blockchain deployed on all BSs.Therefore,the main overhead is the storage overhead of BSs.The Ethereum client is uesd to build an actual blockchain and our smart contract is deployed on it.We examine the storage overhead of deploying blockchain nodes as the number of interactions increases.Every time we generate 1,000 transactions that interact with BSs.Figure12 shows that every 1,000 interactions will incur about 1Mstorage overhead.Compared with the security brought by the blockchain,the overhead of this scale is acceptable.
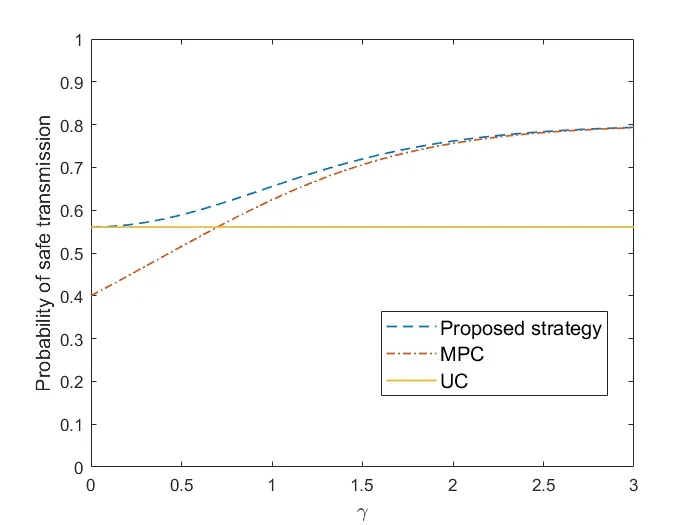
Figure8.The comparison of the performance between our scheme and the existing MPC and UC schemes under the condition of different γ in the independent eavesdropping scenario.
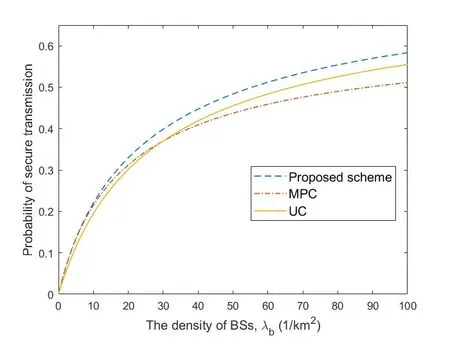
Figure9.The comparison of the performance between our scheme and the existing MPC and UC schemes under diffrent λb in the joint eavesdropping scenario when γ=0.5.
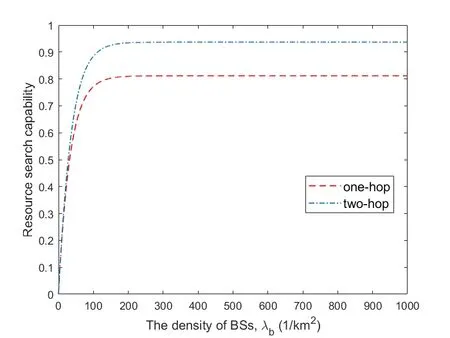
Figure10.A comparison of the probability that the requested content can be found in the case of one-hop and two-hop.
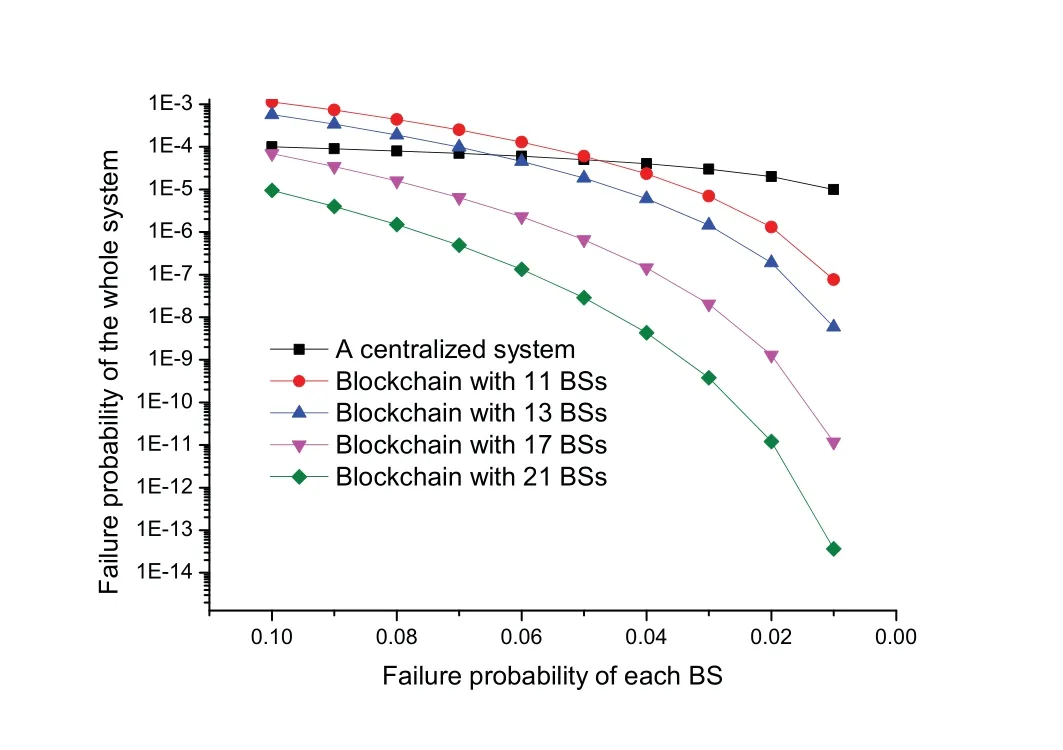
Figure11.The relationship between the failure probability of the whole system and the failure probability of each BS in different systems.
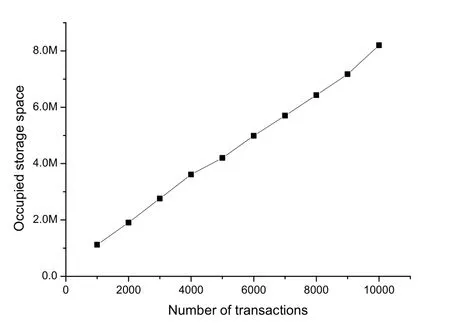
Figure12.The relationship between the number of transactions and occupied storage space.
VII.CONCLUSION
In this paper,we considered two-hop transmissions in a cache-enabled network in the case of independent eavesdropping and joint eavesdropping.We proposed a blockchain based framework to protect the security of historical data and the privacy of users.We jointly optimized the redundancy rate and content caching probability to maximize the secure transmission probability.Through the simulation results,we verified the rationality of our analysis,and that our scheme is superior to the existing schemes.
ACKNOWLEDGEMENT
This work was supported by the European Union's Horizon 2020 research and innovation programme under the Marie Skłodowska-Curie grant agreement No 824019,in part by Special Funds for Central Universities Construction of World-Class Universities (Disciplines),and in part by China 111 Project(B16037).
- China Communications的其它文章
- Spectrum Prediction Based on GAN and Deep Transfer Learning:A Cross-Band Data Augmentation Framework
- Layered D2D NOMA
- Fully Connected Feedforward Neural Networks Based CSI Feedback Algorithm
- Erasure-Correction-Enhanced Iterative Decoding for LDPC-RS Product Codes
- Power Allocation for NOMA in D2D Relay Communications
- A Game-Theoretic Perspective on Resource Management for Large-Scale UAV Communication Networks

