Intelligent Immunity Based Security Defense System for Multi-Access Edge Computing Network
Chengcheng Zhou,Yanping Yu,Shengsong Yang,Haitao Xu,*
1 School of Computer and Communication Engineering,University of Science and Technology Beijing,Beijing 100083,China
2 School of International Languages and Cultures,Yunnan University of Finance and Economics,Kunming 650221,China
Abstract:In this paper,the security problem for the multi-access edge computing (MEC) network is researched,and an intelligent immunity-based security defense system is proposed to identify the unauthorized mobile users and to protect the security of whole system.In the proposed security defense system,the security is protected by the intelligent immunity through three functions,identification function,learning function,and regulation function,respectively.Meanwhile,a three process-based intelligent algorithm is proposed for the intelligent immunity system.Numerical simulations are given to prove the effeteness of the proposed approach.
Keywords:intelligent immunity;security defense;multi-access edge computing;network security
I.INTRODUCTION
With advances in information and communication technology and the development of the Internet of Things(IoT),many smart terminal devices participate in the service.The traditional cloud computing model in terms of latency,bandwidth and data security drawbacks makes it no longer able to meet the growing needs of users.To address this issue,an edge computing model is proposed.Edge computing refers to a new computing model that performs computation at the network edge,where the network edge refers to arbitrary computation and network resources between the path from the data source to the cloud computing center[1].The edge computing model is the migration of some or all of the original cloud computing center's computing tasks to the vicinity of the data source for execution,and it is a complementary model to the original cloud computing model,rather than an alternative model[2].
The edge computing model has some distinct advantages.Since the data processing is done in the vicinity of the data source,the latency can be reduced and the service efficiency of the application can be improved.For latency-sensitive systems,the edge computing model works much better than traditional cloud computing models.At the same time,as the data is processed near the data source,the distance over which it needs to be transmitted is reduced,and the load on the network is reduced.There are also cost savings for users.
While the edge computing model plays a huge role,its security concerns cannot be ignored.The security issues of edge computing models include two aspects,the security issues in edge computing architectures and security issues for edge devices.Some architectures[3-5]address edge computing security,but there is no architecture or standard dedicated to edge computing security.And the security of edge devices is similar to that of ordinary devices,presumably including confidentiality and integrity.
In this paper,we consider an intelligent immunitybased security architecture for the edge computing network,and a security defense system is constructed based on the intelligent immunity.The main contributions are as follows,
·In the intelligent immunity-based security defense system,the edge computing servers can predicate the mobile users to be safe and be accessible to the edge computing networks.Then the system can achieve security,and the illegal users are quarantined.
·Similarity calculation is used to verify if the users are authorization,where a utility based threshold is used to obtain the threshold of similarity calculation.
·An intelligent algorithm is proposed for the intelligent immunity system to achieve security defense,which is a three process based algorithm.
The whole paper is organized as follows.The related works are given in Section II.We describe the system model in Section III.In Section IV,the intelligent algorithm is given for the proposed model.Section V gives out the numerical simulation results.The work is concluded in Section VI.
II.RELATED WORKS
With the development of the IoT and smart mobile devices,edge computing has also developed rapidly.Edge computing has been widely used in daily life,greatly improving the efficiency of information processing.However,the edge computing security has not been done well enough,ignoring the security threats of edge computing platforms.Xiao et al.analyzed different types of attacks,including distributed denial of service attacks,bypass attacks,malware injection attacks,authentication authorization attacks,and model attacks on four edge computing platforms[6].These attacks account for 82% of edge computing attacks.The security of edge computing has become the focus of research,and protecting the privacy of users is also a top priority.
There is also a lot of research on the security of edge computing.Gedik et al.anonymized identity information when aggregating statistical data or providing location-based services [7].Boutsis et al.explicitly approved applications such as the device's geographic location,contact list,and storage on the client to protect user privacy [8].However,most applications require a network,so it is easy to obtain user information.To solve this problem,Zhang et al.proposed an improved mobile support system to protect the network privacy of mobile users without affecting the communication performance [9].Xiao et al.utilized wavelet changes to ensure differential privacy,but the disadvantage is that the sensitivity is too high[10].To solve this problem,Xiao et al.proposed a partitioned histogram algorithm based on wavelet transform[11].The algorithm consists of wavelet tree structure stage and noise addition stage,which reduces complexity and improves accuracy.
Other safety protection methods have also been proposed.Li et al.explored the interaction between vulnerable nodes and malicious nodes in fog computing as a non-cooperative differential game and quantified the security risk by solving the feedback Nash equilibrium[12].Wang et al.proposed to solve the security challenges through the physical layer,which has low computational complexity and resource consumption[13].Chen et al.proposed an edge based IoT secure access authentication method,which does not require any encryption algorithm at the terminal node [14].Fan et al.proposed an edge computing data sharing scheme,using CP-ABE to encrypt the data[15].Yuan et al.developed a reliable and lightweight IoT edge device by adopting the multi-feedback information fusion mechanism and adopted the feedback information fusion algorithm based on the objective information entropy theory to resist malicious attacks more reliably [16].Huang et al.encrypted user data through the access strategy and update strategy,and then transferred the encrypted data to the cloud server through the fog node to achieve fine-grained data access control and secure ciphertext update [17].Xu et al.[18]proposed a privacy-aware data offloading method to reduce the average time of data transmission and maximize privacy entropy,and use SPEA2 algorithm to achieve joint optimization.In order to protect the data in edge computing,Li et al.designed a privacy protection data aggregation based on the homomorphism of the Boneh-Goh-Nissim cryptosystem,which can not only protect privacy,but also provide integrity verification [19].To understand the problem that the edge cache is vulnerable to attacks,Xu et al.constructed a detection scheme based on the hidden Markov model(HMM),and gave the CPAttack model with malicious behavior observation[20].The HMM is used to detect CPAttack through Cache state observation sequence.But there is no research on CPAttack detection when malicious users frequently request unwelcome legal content.
III.SYSTEM MODEL
The edge computing network studied in this paper is divided into three layers from bottom to top,namely mobile user layer,edge computing layer and cloud computing layer,respectively(see Figure1).For mobile user layer,users can access into the edge computing network and enjoy the communication and computing services provided by the network service providers.The edge computing layer can provide edge computing services to the mobile users using the edge computing servers located at the base station.Compared with the cloud computing center,because the edge computing servers are located at the base station,they are closer to the mobile users that can provide faster communication and computing services to the mobile users.The cloud computing layer is mainly composed of the cloud computing center.
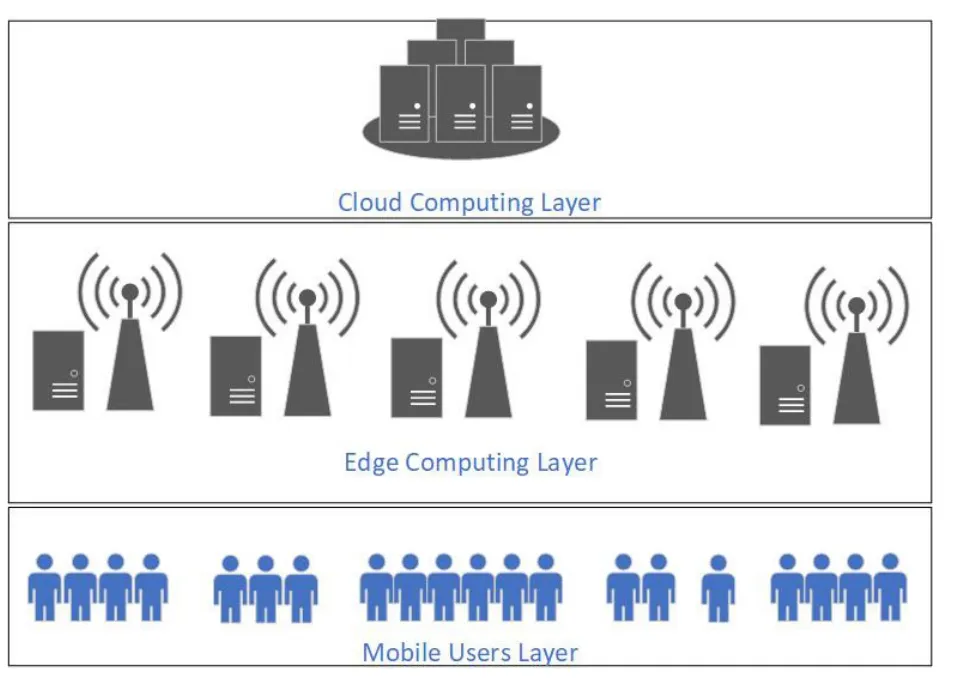
Figure1.Network model.
3.1 Intelligent Security Architecture of Intelligent Immune System for Security Defense
Based on the network model given in the above section,the intelligent architecture of the security defense system is given in Figure2,which also can be divided into three layers.Under the intelligent security architecture,the mobile users accessed the network can be divided into two major categories.One category is the users who have been authorized to access the edge computing network.The other users are the illegal users.To achieve security defense,the intelligent system is introduced into the system.Because the intelligent immune system needs to be able to determine whether the user's access to the edge computing network is legitimate,the intelligent immune systems are hosted on the edge computing servers.All the intelligent immune systems can form an intelligent immune network.To uniformly manage all the intelligent immune systems in the edge computing servers,the security defense system will be deployed in the cloud computing center.The security defense system masters the security situations of the whole network.There also exists a regulation system in the cloud computing center for coordinating the strategies differences between the security defense system and the intelligent immunity network.
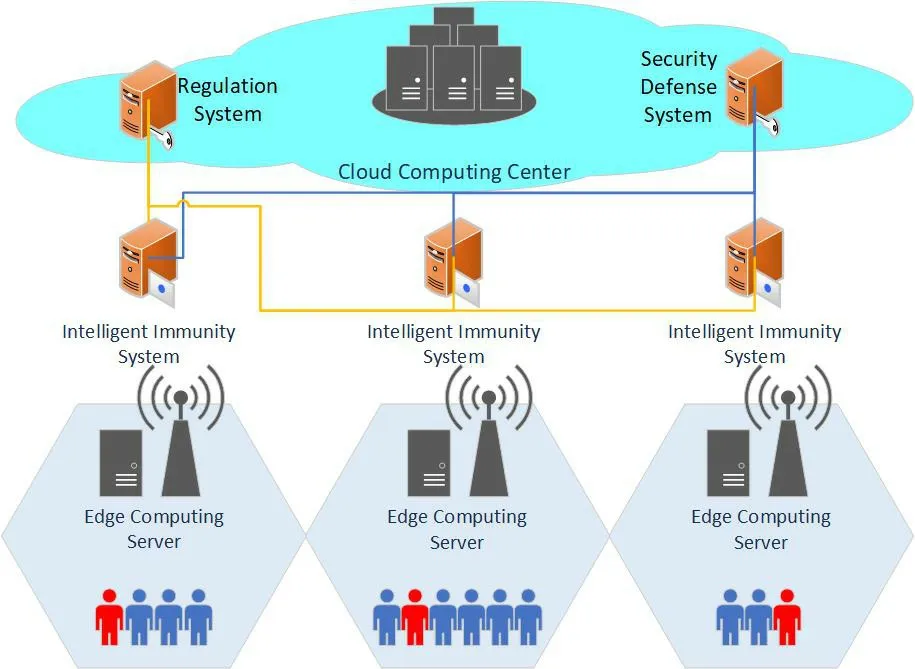
Figure2.Intelligent security architecture.
3.2 Intelligent Functions of Intelligent Immune System for Security Defense
The proposed security defense system of MEC networks can be regarded as an edge computing-based intelligent immune system,which makes full use of edge computing capabilities and cloud computing capabilities to complete security defense missions.There are three functions integrated with the proposed edge computing-based intelligent immunity system,as shown in Figure3.
·Identification
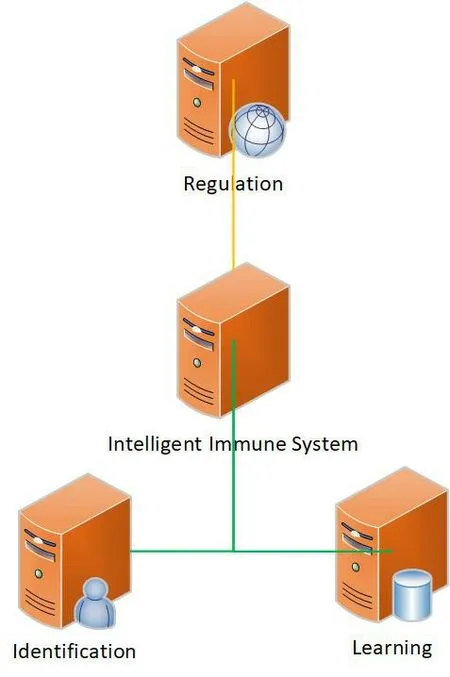
Figure3.Intelligent functions of the intelligent immune system.
Based on the intelligent immunity system,the security defense system of the MEC network can identify the authorized users who enter the MEC networks.The main resources for achieving intelligent immunity is the edge computing abilities coming from the edge computing serves.Using the edge computing abilities,the intelligent immunity system can find the unauthorized users,which will react with the intelligent immunity system.Then the un-authorized users will be removed from the MEC networks by the security defense system.Only the trusted or authorized users that cannot react with the intelligent immunity functions can access the MEC networks.The users who are reacted with and identified by the intelligent immunity system must be the un-authorized users that should be removed.
·Learning
·Regulation
If some users who have been cleared disagree with the decision result of the intelligent immunity system integrated in the MEC server,they can apply to the cloud computing center for re-determination.The MEC servers need to adjust their judgement results according to the decisions of the cloud computing center.In addition,the cloud computing center needs to re-evaluate the authorized users who are allowed to access the MEC networks at set intervals.Through the collaboration between the cloud computing center and the MEC servers,the accuracy of the security defense system can be improved.Based on the above intelligent functions,the logical model of the intelligent immune system for security defense can be illustrated as in Figure4.
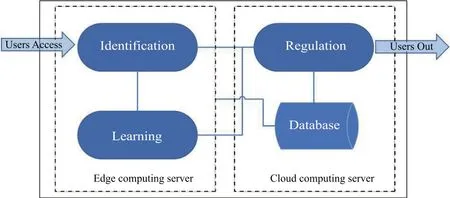
Figure4.Logic model of intelligent immune system.
IV.INTELLIGENT ALGORITHM
As described in the above section,the proposed intelligent immune system for security defense in our paper is integrated with three kinds of functions,identification,learning,and regulation,respectively.Based on these three functions,we can propose an intelligent algorithm for the security defense.The architecture of intelligent algorithm is given in Figure5.
·Authorization process.
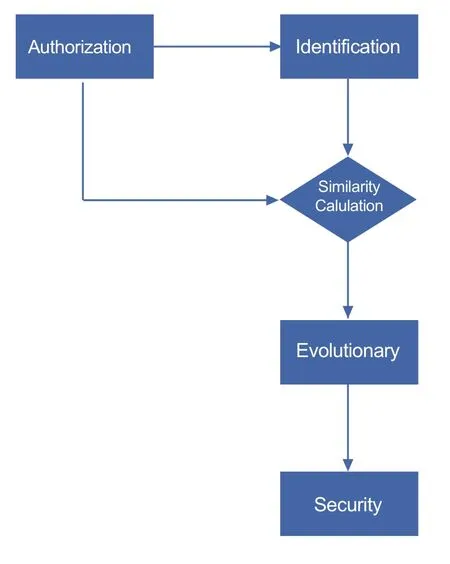
Figure5.Flow chart of intelligent immune algorithm.
The security defense system authenticates and authorizes users to determine which users can access the edge computing networks.Then,the intelligent immune system controls user access according to the access rules preset by the security defense system.Only the users who have been authenticated and authorized by the security defense system can pass the check of the intelligent immune system and access the edge computing networks.
·Identification process.
In the identification process,the intelligent immune system compares the relevant data of mobile users to check if the mobile users are authorized.A similarity calculation should be given to all the users to complete the identification process.Meanwhile,the cloud computing center will run the regulation function to check the correctness of the similarity calculation results.
·Evolutionary process.
“I’ll be home for Christmas. You can count on me...” My faithful clock-radio announced reveille as I slowly dragged myself out of a toasty-warm bed. I trudged8 across the snow-filled street and grabbed a quick breakfast in the cafeteria before reporting for duty on the medical-surgical unit.
By continuously performing the identification process,the intelligent immune system can improve its processing abilities based its learning and memory abilities.The capabilities of the intelligent immune system will evolve to increase the correctness of the identification.
·Security process.
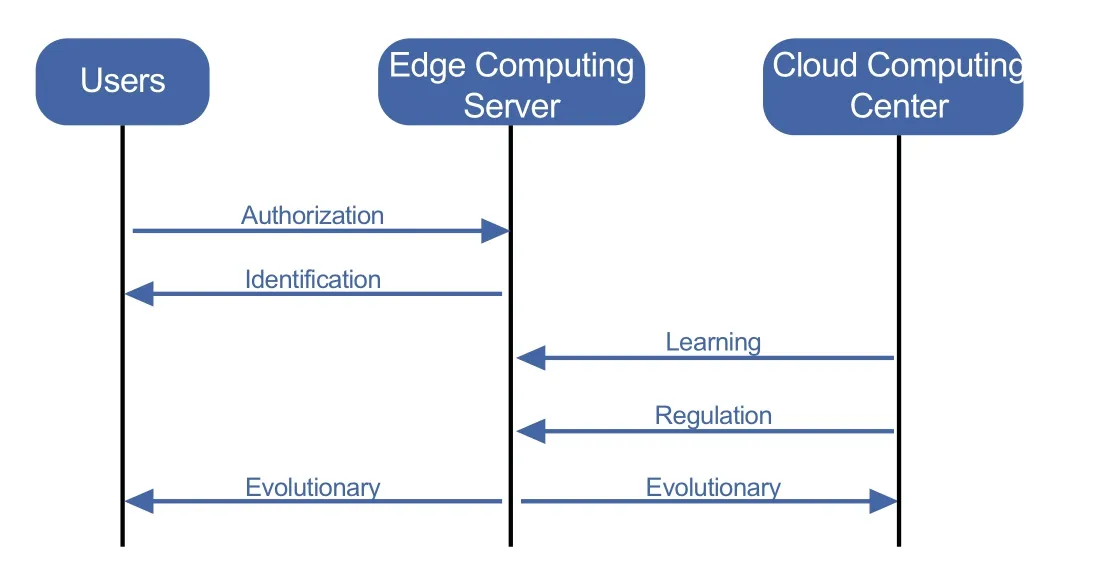
Figure6.Running process.
Through the above three process,the whole network can be protected by the intelligent immune based security defense system.The running process of the proposed intelligent immune algorithm is illustrated in Figure6.A particularly important step in the above process is the similarity calculation.Through the similarity calculation,the authentication of mobile users is realized.We assume that the mobile users with higher similarity results would be considered as the illegal users.The similarity calculation for different mobile users will be affected by the probability for accessing into the edge computing network.The probability that mobile userienters the edge computing network is the ratio of the number of accesses to the edge computing network to the total number of mobile user visits.Each mobile user needs to apply for the time and frequency of accessing into the edge computing network in advance according to the services requirements.Letxidenote the accessing numbers of mobile useri,then the probability of mobile userifor accessing into the edge computing network is given as,
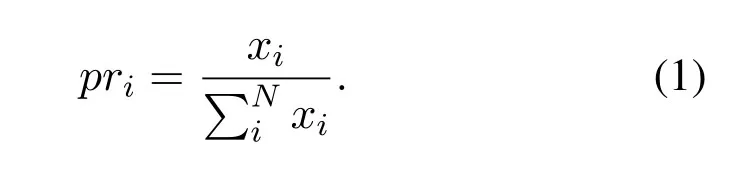
The intelligent immune system can identify the mobile users by comparing the probability of mobile useriand determines whether the mobile users are authorized users by calculating the similarity of the mobile users.According to the calculation results,intelligent immunity can be evolved.The similarity calculation function for mobile useriin this paper is given as,
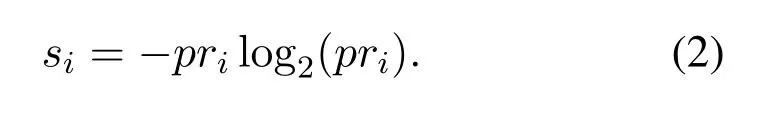
In the above function,we use logarithmic function to denote the similarity of mobile useri.If the accessing numbers of mobile userifor accessing into the edge computing network is large,the authorization information the users carry with itself would be less.For the similarity calculation,the smaller the probability is,the greater the similarity is.Based on the above assumptions,the mobile users will be recognized as the illegal users,if the similarity calculation results follow the following equation,

whereδis a threshold set by the edge computing server.In this paper,the threshold is assumed to be controlled by the edge computing server,which can be solved by the following equations,
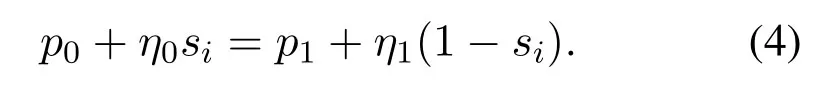
In the above equation,η0andη1are the unit cost for computing the threshold for each mobile user.p0andp1mean the profit earned from similarity calculation results.Based on(4),at the threshold point,there should be no differences between the legal users and illegal users.Solving(4),we can obtain the threshold can be given as follows,
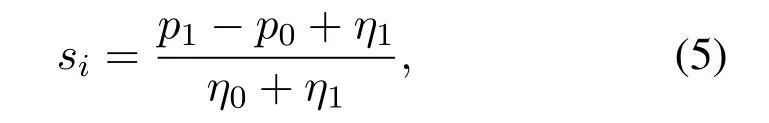
which is mainly controlled by the profit extracted from similarity calculation results and the unit cost for computing the threshold.Besides,the total profit earned from similarity calculation results is given as follows,
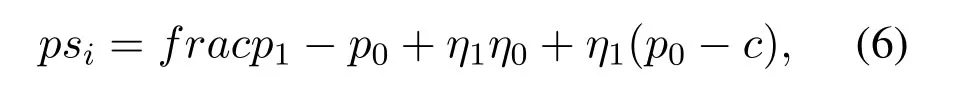
which can be seen as the profit earned from mobile users identification.In(6),cis the unit cost for similarity calculation.For the edge computing server,its objective is to achieve profit maximization,to maximize the objective function given in equation(6).Computing the first partial derivative of (6),we have the optimal unit profit earned from similarity calculation results can be set as follows,Then we can obtain the threshold for similarity calculation as follows,
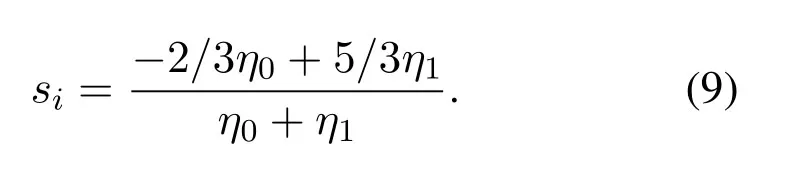
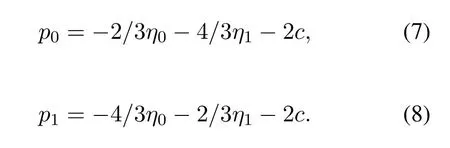
V.NUMERICAL SIMULATIONS
In this section,numerical simulations are given to verify the effectiveness of the proposed architecture and algorithm.In our simulations,there are four mobile users that are recognized by one edge computing server.The arrival numbers for the mobile users are 20,10,16,8,23,5,respectively.The other parameters setting is given in Table1.Based on the accessingnumber of each mobile user,we can obtain the probabilities and the similarity results as given in Figure7 and Figure8.In Figure7,the probabilities of mobile users are mainly given by the access numbers.The more times the mobile users access into the system,the higher the corresponding probabilities.But for the similarity calculation,the more times of access,the lower value of similarity calculation will be,which is shown in Figure8.
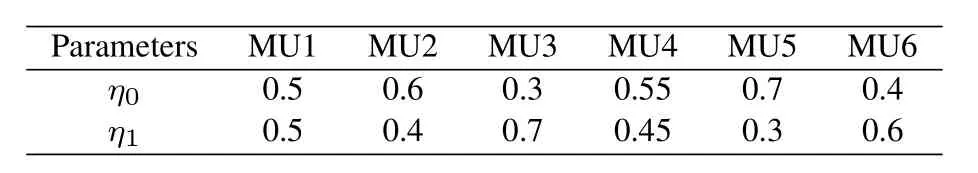
Table1.Parameters setting.
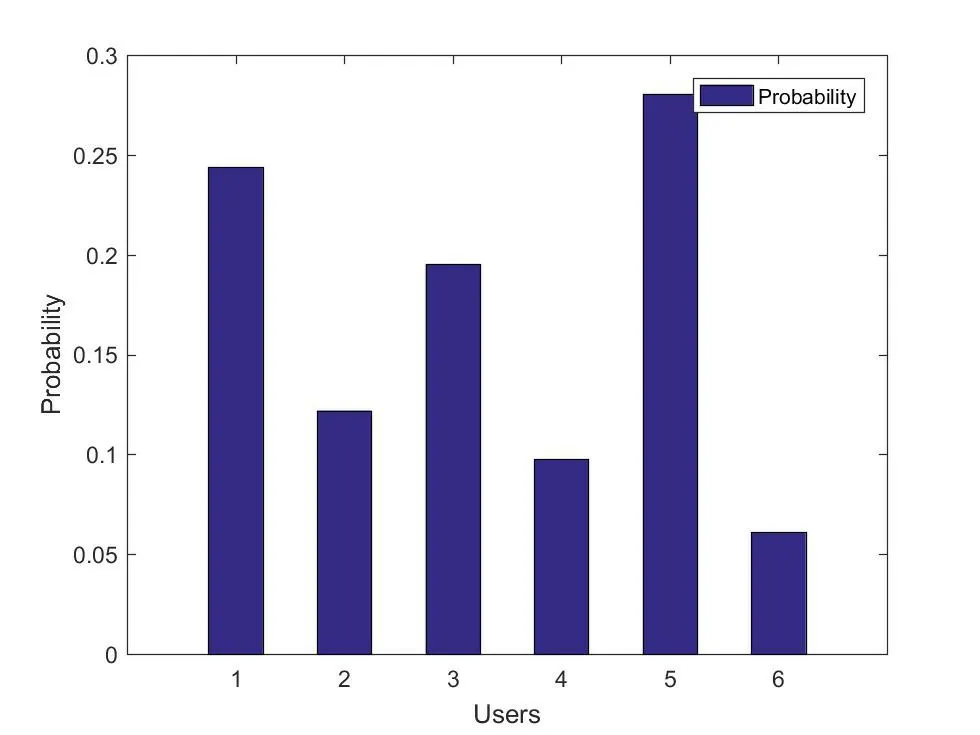
Figure7.Probabilities of each mobile user.
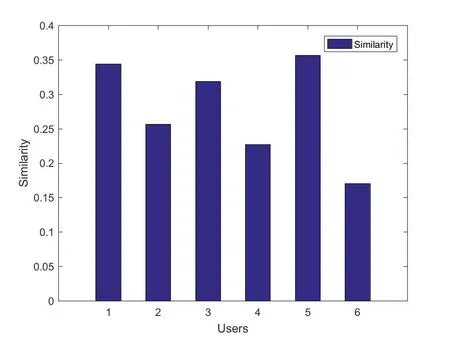
Figure8.Similarity calculation results.
In Figure9,the threshold for similarity calculation is given.We can see that different mobile users would have different threshold to determine if the mobile users are illegal.Take mobile user 3 as a example,its similarity calculation result is about 0.325,with a threshold value 0.98.Then the defense system can consider the mobile user 3 as a legitimate user.But for mobile user 5,because its similarity is larger than the threshold,the defense system would consider user 5 as an illegal user.
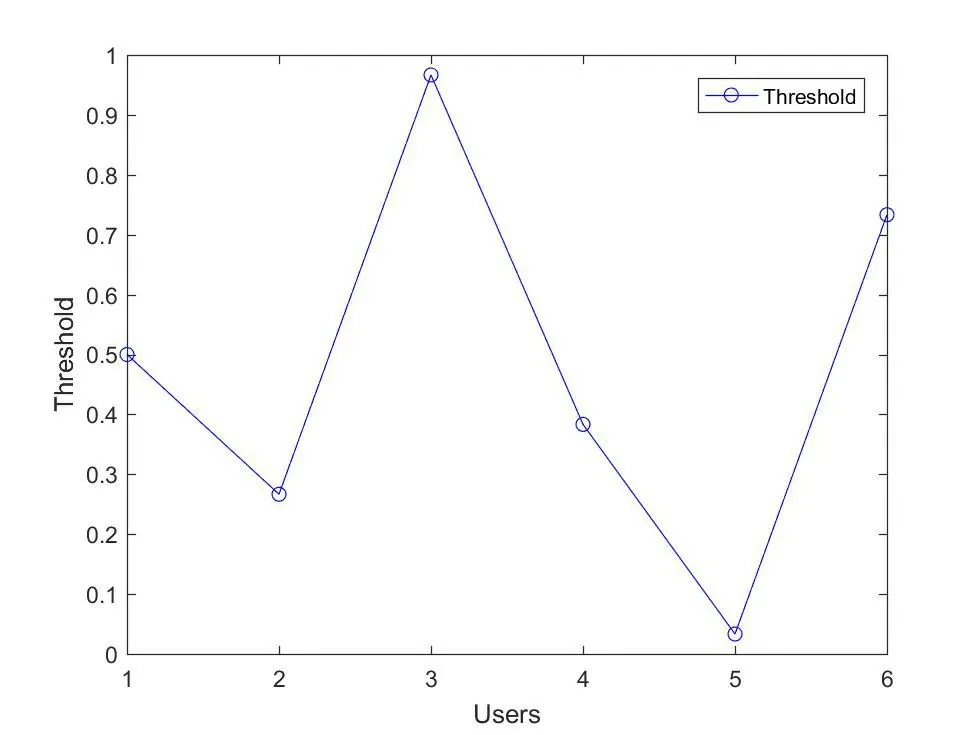
Figure9.Threshold for similarity calculation.
VI.CONCLUSION
In this paper,we have researched the security defense problem in multi-access edge computing networks,and proposed an intelligent immune system for the security defense system to achieve identification of mobile users.The architecture of intelligent immune system is given,and an intelligent algorithm is proposed.Through the application of security architecture and intelligent algorithm,the identification of different users can be realized.
ACKNOWLEDGEMENT
This work was supported by National Natural Science Foundation of China (No.61971026) and the Fundamental Research Funds for the Central Universities(No.FRF-TP-18-008A3).
- China Communications的其它文章
- Edge Caching in Blockchain Empowered 6G
- Spectrum Prediction Based on GAN and Deep Transfer Learning:A Cross-Band Data Augmentation Framework
- Layered D2D NOMA
- Fully Connected Feedforward Neural Networks Based CSI Feedback Algorithm
- Erasure-Correction-Enhanced Iterative Decoding for LDPC-RS Product Codes
- Power Allocation for NOMA in D2D Relay Communications

