A Sensing Layer Network Resource Allocation Model Based on Trusted Groups
Bei Gong,Xipeng Zhang,Shen He*,Nan Tian,Yubo Wang
1 Faculty of Information Technology,Beijing University of Technology,Beijing 100124,China
2 China Mobile Research Institute,Beijing 100055,China
3 91977 PLA(The People's Liberation Army)Beijing 10000,China
Abstract: There are many heterogeneous sensing nodes in the sensing layer of the Internet of Things,and the amount of data transmission is huge,which puts high requirements on the allocation of network bandwidth.At the same time,untrusted sensing nodes maliciously invade network resources.Therefore,how to confirm whether a sensing node is trusted and reasonably allocate network resources is an urgent problem to be solved.To resolve this issue,this paper proposes a sensing network resource allocation model based on trusted groups.Through the sensing node computing environment and behavior measurement,we can identify and exclude untrusted nodes,so the trusted group can be built.Then the network resources are distributed from a global perspective.Based on the available bandwidth of the link,a network resource fusion model of IPv4 and IPv6 is proposed.On this basis,a global network resource allocation model is further proposed.Afterwards,real-time monitoring of data transmission behavior ensures data security during transmission.Simulation experiments show that this mechanism can effectively optimize the bandwidth allocation in the data transmission process and has little effect on the running efficiency of existing network applications.At the same time,it can effectively guarantee the trust of nodes and achieve trusted data transmission.
Keywords: internet of things; trust measurement; link bandwidth; network resource allocation; data transmission
I.INTRODUCTION
The Internet of Things is a ubiquitous network built on the Internet,and it connect a large number of real-world terminal objects (RFID devices,sensors,smart terminals,etc.)through the sensing environment and the Internet to form a new application paradigm.The ITU's brief definition of the Internet of Things is: In the Internet of Things,anyone can connect anything at any time,any place[1]; the Internet of Things extends the interactive communication between humans and terminals to the connection between people and things,things and things,and people,which makes objects become more intelligent.The Internet of Things can programmatically realize the interaction between people,things and things and people and things,which has spawned a large number of new application scenarios and implementation technologies[2],which expands human understanding of the real world.From the perspective of internal needs and external presentations,the Internet of Things is an extension and extension of the Internet.Based on the existing network interconnection technologies and equipment,it integrates new wireless technologies.In particular,wireless sensing technology integrates the physical world with the virtual network world seamlessly[3,4].The essence of the Internet of Things is summarized as: effective sensing,extensive interconnection,in-depth intelligent analysis,processing,and personalized experience.Compared with traditional networks,the Internet of Things is more biased towards information sensing,reliable transmission,and intelligent analysis[5,6].The number of sensors in the Internet of Things is huge,and the sensing data needs to be integrated with Internet data to be transmitted and processed.The data in the Internet of Things comes from different types of heterogeneous networks.With the continuous expansion of the Internet of Things applications,the range of information acquired by the sensing network has become wider and wider,even involving government,military,and financial fields.The network resources allocating and the data trusted transmission that are brought about by the sensing layer become the problem that the application of the Internet of things needs to solve urgently,and it is also the hot spot of current theoretical research.
The core business of the Internet of Things is the collection of data,transmission of data,and feedback on the basis of data processing.The normal operation of the Internet of Things depends on the sensing of data.Considering that there are a large number of heterogeneous sensing nodes in the sensing layer,the communication protocols and communication modes between the nodes are very different.Considering the real-time and effectiveness of data transmission,the available network bandwidth protection during data transmission is extremely important.Leaving aside the service quality of computing and storage resources,effective network resource scheduling is still crucial to the real-time transmission of sensing data and feedback control based on sensing data.At the same time,with the wider application of the Internet of Things,especially with the development of sensing technology,the sense data has increased explosively.The current network scheduling and congestion control mechanisms are still in a one-to-one correspondence and cannot effectively address the timeliness and reliability of data transmission.At the same time,with the development of the Internet of Things,IPv6 has gradually integrated into the sensing layer of the Internet of Things.Therefore,the seamless integration of IPv6 and IPv4 network resources is also a challenge.
Therefore,in order to guarantee the trust of sensing nodes,on the basis of this,the fairness of the network bandwidth allocation and the timeliness of transmission in the process of sensing data transmission are fully guaranteed.This paper proposes an Internet of Things awareness network resource allocation model based on the measurement of sensing nodes.First,this paper proposes a trusted group construction mechanism based on the trust measurement of sensing nodes to ensure the credibility of the sensing computing environment.Then according to the data transmission requirements,based on the rapid and effective calculation of the available bandwidth,the multipathability of IOT is fully utilized to ensure the fairness of network resource allocation.Then,the data transmission behavior is monitored in real time to ensure the trust of data transmission process.Simulation experiments show that this model can effectively optimize the bandwidth allocation during data transmission,and has little effect on the operating efficiency of existing network applications.It can also effectively ensure the reliable operation of nodes and achieve reliable transmission of data.
II.RELATED WORK
2.1 Research on trust measurement of Internet of Things
Research on the trust measurement of the sensing nodes of the Internet of Things can not only improve the security of the Internet of Things,but also simplify the monitoring and prevention of additional costs.However,the current research on trust measurement of sensing nodes is not satisfactory.First,the current research on trust measurement focuses on a certain application field [7].It does not have universality.At the same time,there is a lack of trusted measurement model for the sensing nodes of the Internet of Things.The literature [8] believes that the trust measurement mechanism of the sensing nodes in the Internet of Things has a crucial role in the security of the Internet of Things.Research on the credible measurement model is imminent.At the sensing level,the literature [9] holds that the current credible measurement mechanism has the following challenges: (1)Lack of facility support,(2)limited node resources,(3)fragile wireless channels,and (4)heterogeneous multi-source nodes.The IoT node establishes a trust mechanism through trust measurement with the following challenges: The large-scale application scenario makes the node interactions have an unknown pattern; the distributed environment makes the previous centralized security policies for objects and terminals ineffective; the heterogeneous environment leads to the inability to use a unified trust measurement mechanism.
In the Internet of Things,the trust measurement for sensing nodes are based on past past behavior and state evidence.Literature [10] proposed a credible measurement method based on route evidence and random sampling.However,this metric method cannot measure the status of the node in real time,nor can it measure the behavior.Literature [11] proposes a trust value measurement model based on the role of node of the Internet of Things.The identity of the node in the sensing network is used as the evaluation basis of the credible measure of the node.However,the metric element of this method is too one-sided and cannot comprehensively reflect the credibility of the node.Literature [12] proposed a reliable measurement model based on intrusion detection,and realized the dynamic detection of node behavior.Although this solution implements the real-time measurement of nodes,it lacks active measurement and control mechanisms.Literature [13] studied the behavior of dedicated IoT nodes for medical treatment and established a distributed behavioral trust value measurement model with the advantages of accurate measurement and rapid response.However,the application of this model is too narrow and versatile.In order to ensure the stability of the node's trust measurement,the Kalman filter-based calculation method is also used in the node anomaly behavior measurement model[14],but the detection accuracy of this solution behavior fluctuates too much and the real-time response capability is poor.In order to smooth the trust measurement,the literature [15] proposed a network reputation model based on Gaussian distribution and reputation distribution fitting.The scheme can achieve node trust and smoothness,but lacks the objective trust measure of nodes.The literature [16] adopts the method of rounding the trust value,calculates the direct trust through the success rate of interaction,and proposes a credible assessment model of a hierarchical structure.The credible measurement model has achieved good results in the measurement of the level of the Internet of things.However,it failed to consider the real-time nature of node behavior trust evaluation.Literature [17] proposes a behavioral trust assessment model based on sliding windows from multiple perspectives such as information security,trusted systems,and trusted computing.The scheme can effectively reflect the process of trust decline,but the calculation method is cumbersome,it is a burden to the node,and its subjective trust measure fluctuates greatly,and the reference significance is limited.Literature [18] proposed a location-based trusted measurement model,which can effectively detect and isolate the nodes that have been attacked,but it is easy to leak the identity and location privacy of the nodes during the measurement process.Literature [19] proposed a low-cost and lightweight node-selective forwarding attack detection algorithm based on the analysis of data packet ID.The solution is faster,but the measurement dimension is less,and the credibility of the trusted metric is lower.Literature [20] combines the measurement of the trust value of nodes in the sensing layer with the trusted routing,and proposes a trusted routing scheme that takes into account the trust value of node behavior and transmission energy consumption.However,this solution puts too much emphasis on the energy consumption of routing and reduces the role of the node's trust measurement.
Due to the heterogeneity of nodes in the sensing computing layer,the universal security mechanism applicable to different types of nodes is the research focus in this field.Literature [21] discusses the universal security mechanism of heterogeneous sensing nodes.With data protection as the core,the security of sensing nodes is enhanced.However,the protection mechanism is too simple to handle different types of security threats.Literature [22] studied the compressive sensing mechanism applicable to sensing nodes and enhanced the security sensitivity of the compressive sensing stage,effectively deal with plaintext attacks,achieving a good balance between compression and security.However,this mechanism cannot deal with ciphertext attacks and has poor robustness.Literature [23] starts from the security risks faced by sensing nodes,and assesses the security risks that sensing nodes in the Internet of Things face in their application environment.In turn,security warnings were issued,taking full account of the dynamic nature of the Internet of Things and rigorous assessment of security risks.However,the lack of a response mechanism to security risks can only serve as a reference in the security protection process.Literature [24] proposed an attack detection mechanism based on distributed deep learning,which has a low false alarm rate and good scalability.However,this method requires a large amount of attack data and powerful computing capabilities,which is a burden on the cognitive computing node.
2.2 Research on network resource allocation model
In order to guarantee the timeliness and reliability of data transmission,the available bandwidth guarantee on the heavy load transmission path is extremely important.In order to achieve this goal,literature [25] built a virtual network on top of the physical network.Logically speaking,the virtual networks do not affect each other,and the polling system can be used to ensure the availability of bandwidth.Document [26] uses the virtual data center model to meet the bandwidth requirements of data transmission through this mechanism.However,because the virtual network and the virtual data center are logically mapped,when the data volume is huge,the efficiency and effectiveness of its network resource allocation scheme cannot be expected.
In addition,the computing network physical resources are fixed,which causes a waste of idle bandwidth.To solve this problem,literature [27] divides the bandwidth of different data centers according to the proportion.This scheme can not only improve the network utilization,but also ensure the fair distribution of link bandwidth,can fully use the same area of idle bandwidth,and effectively solve the problem of link congestion.Considering the fairness of bandwidth allocation,adopting the minimum bandwidth allocation mechanism can effectively ensure the fairness of bandwidth allocation.Therefore,literature[28] proposes three proportional bandwidth allocation strategies according to different application scenarios.Literature [29] proposes a bandwidth allocation mechanism from the perspective of game theory to improve the efficiency of bandwidth allocation,but the mechanism is easy to produce zero-sum effects.Literature [30] proposed a bandwidth-floating mechanism that uses a bandwidth-floating mechanism to improve utilization of idle bandwidth.
In the aspect of secure transmission path selection during data transmission,the literature [31] studied the routing security problem of multi-hop wireless ad-hoc networks in the presence of random eavesdropping attacks.Using a modified Bell-Ford algorithm to build secure routes through a distributed approach,but the search time is too long and the efficiency is low.In the area of low-altitude unmanned aerial vehicles,drones are vulnerable to routing attacks during communication.To address this issue,literature [32] proposes a location-based security routing mechanism that can effectively defend against routing protocols.However,this mechanism can only be deployed on specific hardware and software platforms and has poor generality.Document [33] proposes a routing mechanism based on trust similarity,and combines direct and recommended trusts to construct a trusted data transmission path.This mechanism can effectively detect selfish and malicious nodes.However,this mechanism lacks a dynamic update mechanism and has poor adaptive capability.
III.TRUST MEASUREMENT OF SENSING NODE AND TRUSTED COMMUNITY CONSTRUCTION
3.1 The trust measurement of sensing node
Nodes in the sensing layer of the Internet of Things can be divided into three categories from the perspective of applications: nodes for RFID applications (including RFID readers,RFID repeaters),nodes for fast mobile applications (including car networking,intelligent transportation,drones,etc.)and smart terminals (including wearable devices,mobile smart terminals,location service terminals,etc.).The trusted decision of different types of sensing nodes needs to take into account the commonness and difference of the nodes' trust.Therefore,the trusted decision of the sensing nodes includes two parts: 1.the trusted computing environment of the node; 2.the trusted behavior of the node.
Assume that there are n sensing nodes deployed in a region (p1,p2,...,pn).There are two main organizational forms of sensing networks that the sensing nodes make up: centralized networking and distributed networking.The centralized networking is to select several nodes which has strongest computing power and highest energy levels.Those nodes manage the other nodes as the management node and are responsible for collecting and transmitting the sensing data of this area.In the distributed networking mode,the difference in computing power and energy level between nodes is not significant.Any node can serve as a relay node for data transmission and can also evaluate other nodes.Obviously,the above two types of sensing networks have differences in the node's trusted decision.The process of trusted node's trusted decision is described as follows.
3.1.1 Trusted decision of node computing environment in centralized networking mode
For centralized networking,assuming that the management node of (p1,p2,...,pn)ispπ1,pπ2,...,pπm.For a nodepi,it needs to prove to the management node that its own computing environment is trusted,which the attribute of any sensing node should include the node's hardware information,software information and network information.Therefore,the attributes of sensing nodes can be formalized as triadC=(H a,S h,Ne),whereHarepresents hardware information,Shrepresents software information,Nerepresents network information.Ha=(h0,h1,h2,...,hn),whereh0indicates the characteristic values of the data acquisition module and the data processing module of the sensing node ,andhirepresents the characteristic values of other hardware components (memory,motherboard,network equipment,etc.).Sh=(s1,s2,...,sn),wheresirepresents the characteristic values of the software running on the sensing node (including the operating bootstrap,operating system kernel,and key application programs).Ne=(ad,pa,c1,c2,...,ck),whereadrepresents a network address,pais the physical address andc1,c2,...,ckrepresents the current process of network communication.
According to the security requirement,the management node usesC=(H a,S h,Ne)as input,and determines whether the computing environment ofpiis trusted through the evaluation function of the environment trustM ce(C).The trusted computing environment of the management node is completed by the superior data aggregation node,similar to the ordinary node.And it is not described here.According to the sensing node attribute descriptionM ce(C),the three components in (H a,S h,Ne)are evaluated,so the security assessment function for each component is described as follows:
Definition 3-1 Hardware attributes component trust measurement function Mc e[ 1](Ha)
In the functionMce[ 1](Ha),h0' andhi' are the hardware information submitted by the sensing node when it is registered with the superior node at the initial time.The computation process of functionMce[ 1](Ha)represents that the data acquisition and processing module of the sensing node is not allowed to change ,but sensing nodes in the process of running may need to replace the hardware such as battery,memory card and so on.So other hardware can be allowed to be replaced ,and the degree of replacement of the hardware depends on the security policy of the superior nodes.
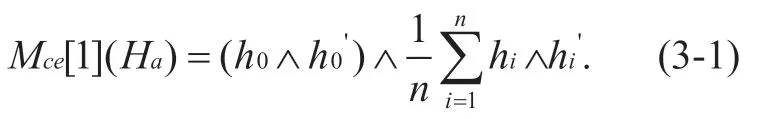
Definition 3-2 Software attributes component trust measurement function Mc e[ 2](Sh)
Assuming in theSh=(s1,s2,...,sn),s1toskrepresents operating system boot program,operating system kernel and key data acquisition and transmission programs,andsktosnrepresents other programs,thenMce[ 2](Sh)can be described as
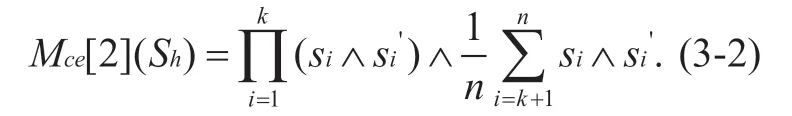
Wheresi' is the software information submitted by the sensing node when registering with the upper node at the initial time.
Definition 3-3 Network attributes compo-nent trust measurement function Mc e[ 3](Ne)
Given network attribute componentsNe=(ad,pa,c1,c2,...,ck),assuming thatad' andpa' are the network address and physical address of the current sensing node saved by the upper node,andf(ci)is an evaluation function of the process.Then,
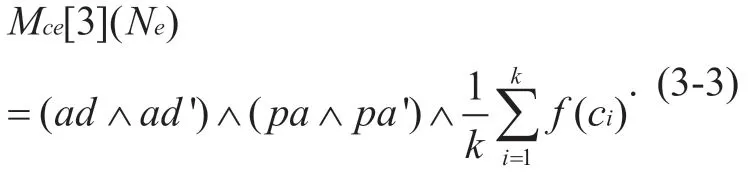
f(ci)can be described as follows: the evaluation function for effective evaluation of nodes is described as follows:
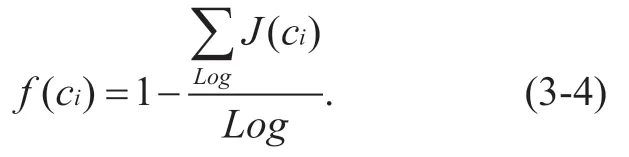
Definition 3-4 Calculation environment evaluation function M ce(C)
GivenMce[ 1](Ha),Mce[ 2](Sh)andMce[ 3](Ne),M ce(C)can be described as follows:
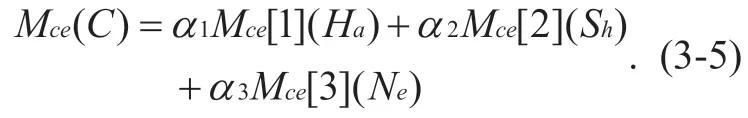
whereα1+α2+α3=1,α1,α2,α3is a weight factor,and its value is determined according to the Internet of Things environment.The value ofα1,α2,α3is usually 1/3.
3.1.2 Trusted decision of node computing environment in distributed networking mode
For a distributed networking approach (such as a car networking,drone,etc.),given a set of sensing nodes (p1,p2,...,pn),anypican evaluate whether the computing environment of the node which it is communicating with is trusted,and any node that communicates with it can make a trusted assessment topi.Assuming thatblt(p i,pj)is a two-way trusted evaluation function.Anyp i,pjcan use this function to perform a trusted evaluation of the computing environments of both parties.Therefore,it is necessary to consider multiple nodes to evaluate the computing environment of the node to determine whether the node is trusted,and then decide whether to transfer data to this node.The functionblt(p i,pj)can be described as follows:
The attributes of any sensing node can be represented by a triadC=(Ha,S h,Ne),since it is a point-to-point communication network,so there is no mutual trust between any two nodesp i,pj,andp i,pjneeds to assess the trust value of the communication process that establishes a connection with each other.Therefore,the evaluation and calculation process of the computing environment ofpitopjcan be described as follows:
After the two have established a connection,assuming that the communication process betweenpiandpjisc1,c2,...,cl,c1,c2,...,cxbelongs topi,cx+1,cx+2,...,clbelongs topj,permissions sets thatcx+1,cx+2,...,clfinish these operations are {prx+1,prx+2....prl} ,external process access permission thatpiallows ispu,then process evaluation functionf m(pj)can be described as:
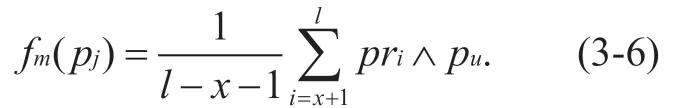
Similarly,if assuming that permissions sets thatc1,c2,...,cxcomplete these operations are {pr1,pr2....prx} and the external process access permission thatpjallows ispm,then the process evaluation functionf m(pj)can be described as:
Therefore,the following definition can be obtained according to formula (3-6)and formula (3-7):
Definition 3-5 Two-way trusted evaluation function blt (p i,pj)
Definition 3-6 Trusted evaluation function of node computing environment in Distributed Networking Mode B mc(C)
Assuming that the bidirectional trusted evaluation sequence of nodep j,pj+1,...,pkto nodepiat the momenttis {blt(p i,pj)[1],blt(p i,pj+1)[2],...,blt(p i,p k)[k]},therefore,the trusted assessment of the node'spicomputing environment can be described as follows:
3.1.3 Trusted decision of node behavior
In the sensing network,because the distance between nodes often changes and the communication is not reliable,the node is not sure about the observed phenomenon.The application environment of the sensing network is complex and varied,and it lacks very reliable parameters.Therefore,it should combine the expected behavior and the unintended behavior of the node to comprehensively judge whether the behavior of the node is trusted.Unintended behavior is not necessarily a malicious behavior.For example,a node plans to transmit data in a unit of time,but the data cannot be transmitted in time due to channel instability.This behavior is not a malicious act,but if the node does take malicious actions,and its trust value should be reduced accordingly.The data of the sensing node is monitored by the upper node in the centralized networking process,while the data of the sensing node is monitored by its surrounding nodes in the distributed networking.Therefore,its behavior can be deduced from the phenomenon observed by the monitoring node.
L1: The sensing node has completed the identification;
L2: At the momentt,the sensing nodepireceives the data packetd,and the data packet is sent to the target sensing nodepj;
L3: The next hop relay node of the packet ispk;
L4:Within the specified time windowt,the monitoring node finds thatpkhas received the data packetd,and the target ispj;
L5: Within the specified time windowt,the monitoring node does not findpkhas received the data packetd,and the target ispj;
L6: Within the specified time windowt,the monitoring node finds thatpjhas received the data packetd;
L7: Within the specified time windowt,the monitoring node does not find thatpjhas received the data packetd;
L8: The contents of the packet have not been tampered with;
L9: The content of the packet was tampered with;
So the expected behavior of the node can be described in Table 1:
Whether the behavior of the node is trusted requires a comprehensive evaluation of the expected behavior and unintended behavior of the node.Table 2 gives a description of the unintended behavior of the node:
Definition 3-7 Behavioral trusted evaluation function of sensing node in centralizednetworking at the moment t
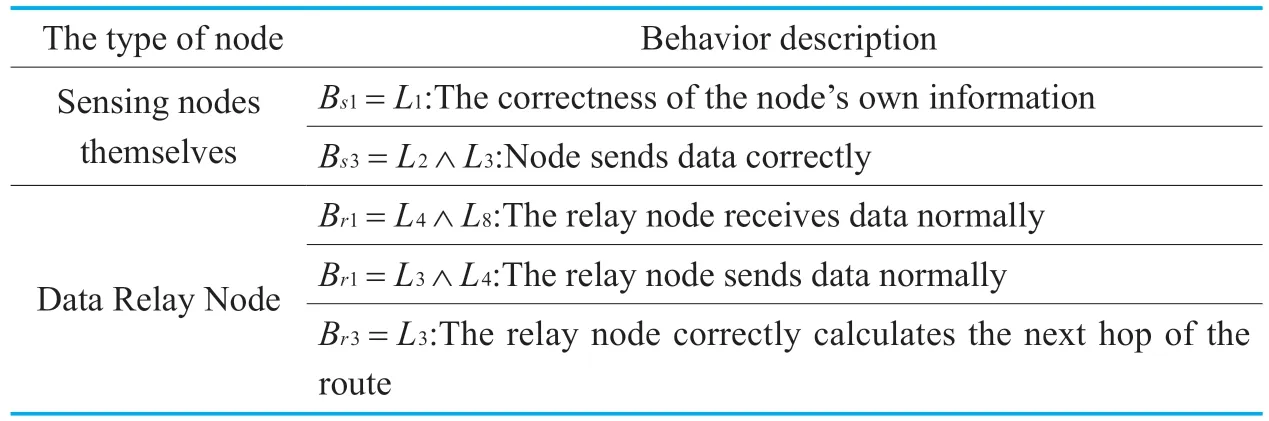
Table I.Node Expected Behavior Description.
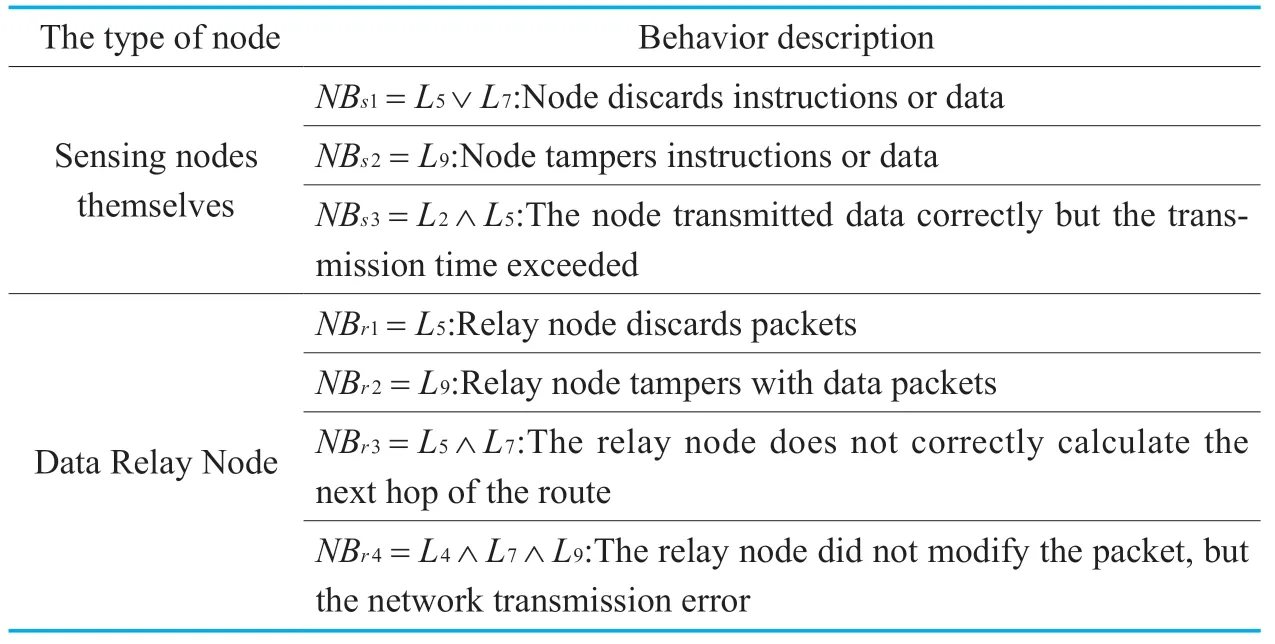
Table II.Node Unexpected Behavior Description.
According to the above description of the node's expected behavior and unintended behavior,in terms of the centralized networking mode,the management node combines intended behavior and unintended behavior to determine whether its lower-level node is trusted,and the management node itself needs to be determined by the upper node.Assuming that the sequence of expected behavior at the momenttisand the sequence of unintended behavior isIn a certain time window w,the time is up tot.According to historical statistics,the probability ofBsi,Briis Pr[Bsi] and Pr[Bri],and the total number of behavior sets monitored by the monitoring node at the timetisn,and the sequence of numbers ofBsiandBriare (x1,x2,...,xk)and (y1,y2,...,yl)respectively,
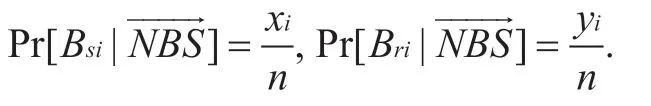
Therefore,according to Bayes formula,the evaluation function of behavior trust of the sensing node at the momenttis:
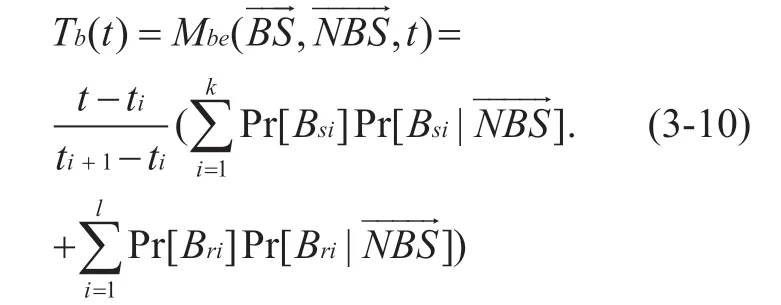
Definition 3-8 Behavior trusted decision function of sensing node in centralized networking mode
The trust assessment of the behavior of a node is an evaluation value at any time.Whether any node is trusted or not,it needs to be judged based on historical trust measurement.But whether or not a node's behavior is trusted requires a comprehensive consideration of the trust value within a time window Δt.Assume that this node is needed to be assessedmtimes within this time window,and the trust measurement sequence of its behavior is: {Tb1,Tb2.......Tbm}.Tb1is the measurement of the oldest behavior from now,andTbmis the measurement of the data sending behavior at the current moment.ThenT(t-Δt,t)can be defined as:
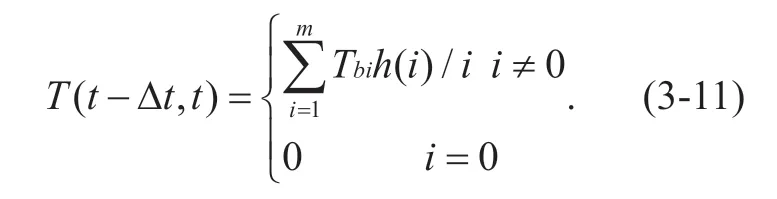
Whereh(i)is attenuation function andh(i)∈[0,1] .h(i)can reasonably weight trusted measurement at different time.According to the law that the data transmission behavior decays with time,the newly generated data transmission behavior should have more weights,so the attenuation function can be specified as follows:
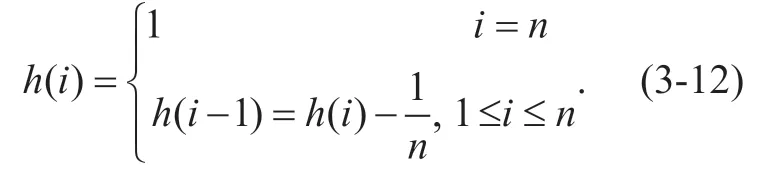
Definition 3-9 Behavioral trusted evaluation function of sensing node in distributed networking at the moment t
For distributed networking,the behavior of any nodepican be trusted assessment by its neighboring nodes,assuming that nodesp j,pj+1,...,pkat the momenttobserved that the expected behavior sequence ofpii sand unexpected behavior sequence isThe expected behavior sequence and unintended behavior sequence observed by each node may be different,so it needs to synthesize the behavior observed by all the different nodes to evaluate whether the node is trusted,and then the trusted evaluation function for its behavior at the momenttis:
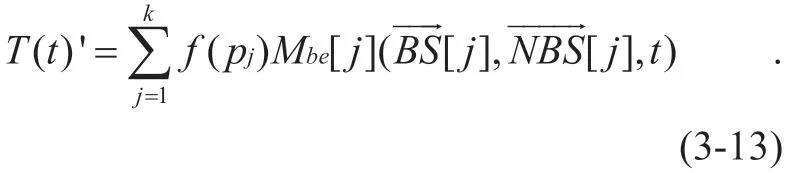
Definition3-10 Behavioral trusted decision function of sensing node in distributed networking
Assume that this node is needed to be assessedmtimes within this time window,and the trust measurement sequence of its behavior is:{Tb1' ,Tb2'.......Tbm' }.Therefore,whether a nodepiis trusted at a certain momenttcan be calculated as follows:
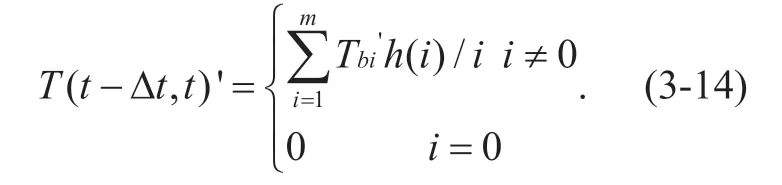
The calculation method ofh i()is consistent with formula (3-12).
Definition 3-11 Comprehensive evaluation function of the trust value of sensing node in centralized networking mode
Whether or not a node is trusted requires a comprehensive judgment of the computing environment and behavior of the node,because the trusted computing environment does not mean that its subsequent behavior is trusted.But if the computing environment is not trusted,the follow-up behavior must not be trusted.Therefore,for centralized networking,the final form of the node's trusted evaluation function at a time window is:
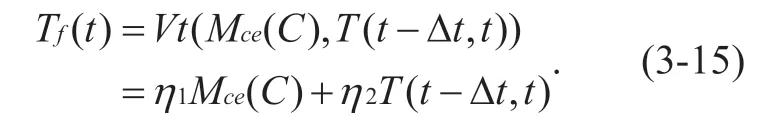
Definition 3-12 Comprehensive evaluation function of the trust value of sensing node in distributed networking mode
As for distributed networking mode,the final form of the node'spitrusted evaluation function at timetis:
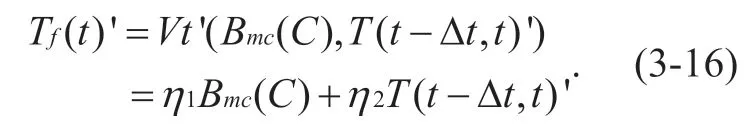
The definition ofη1,η2is the same as the definition in (3-15).
3.2 The trust logical grouping of sensing node
From a sociological point of view,sensing networks and social communities have certain similarities.The sensing computing layer is composed of different sensing networks.Similar to social communities,each sensing network is a collection of certain structures and functions,which can be seen as a community.The sensing nodes in this community adhere to common rules,share the same network resources,and often interact with each other,affecting the development of the community.This section will discuss how to build different logical groups on the basis of node credibility.
For the sensing node,its inherent characteristics are self-platform information,energy,and channel.Its task characteristics include its computing task,data transmission task,and current credibility.Let the nodepi's intrinsic feature vector beIC=(hs,en,ch),wherehsstands for the platform characteristic ofpi,enstands for the energy level ofpi,andchrepresents the channel ofpi.Let the nodepi's task feature vector beTC=(dt,T),wheredtrepresents data transmission task ofpiandTis the node trust value calculated from the trusted assessment.
3.1.1 Sensing node trusted logical grouping in a centralized networking mode
According to the networking mode of the sensing nodes,the construction methods of the trusted groups are different.For the centralized networking mode,there arensensing nodes {p1,p2,...,pn} in one area,wherepπ1,pπ2,...,pπmis a management node.According to the inherent characteristics and task characteristics of ordinary nodes,the management node logically groups ordinary nodes,and then the discrimination degree calculation function can be given:
Definition 3-13 Calculation function of the degree of trust value of the sensing node in the centralized networking mode
For anypπiin the management nodespπ1,pπ2,...,pπm,pπicalculates the trust value in the sensing nodes within its communication radius.For a centralized networking approach,pπisets the mathematical expectation of inherent characteristics in its communication radius asand the mathematical expectation of task characteristics is
If the sensing node to be evaluated ispi,then the sensing node's trust value calculation function should include the inherent feature similarity calculation functionfICand the task feature similarity calculation functionfTC.Then the node trust degree discrimination function can be described as:
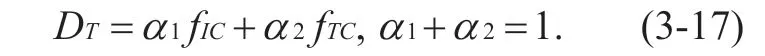
α1,α2depend on the network environment.Whenα1=α2=1/2,it can be seenfICandfTCis equally important.
The calculation offICdepends on the inherent characteristicsIC=(hs,en,ch)of evaluated nodepiand Intrinsic characteristicsof settings ofpπi.The calculation process is shown as follows:
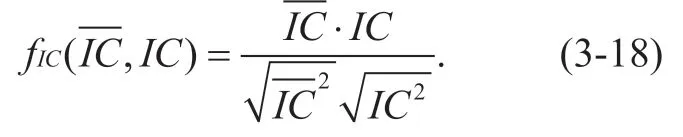
The calculation offTCdepends on the task characteristicsof evaluated nodepiand task characteristicsTC=(dt,T)of settings ofpπi.
The evaluation of data transmission tasksdtis mainly calculated through the successful data transmission rate.When a nodepireceives a request ofdrdata packets at a time,but the nodepionly forwardsdsdata packets,thenfTCcan be calculated as follows:
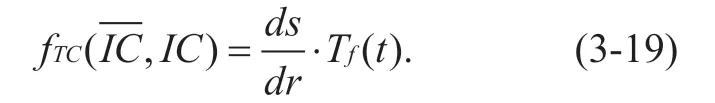
According to the calculation resultDT,a thresholdthis set bypπi.IfD T>th,then the nodepican join the group thatpπiis regarded as the administrator,otherwise the node cannot join.For thepπ1,pπ2,...,pπm,the node trust degree has been calculated by the upper node,and only the trusted management node can construct a logical group,then the sensing network of the centralized network can be divided into several groups through the node trust value discrimination function.
3.2.2 Sensing node trusted logical grouping in a distributed networking mode
Let n sensing nodes (p1,p2,...,pn)use distributed networking to build a trusted community.The nodepihas an intrinsic feature vectorIC[i] and the task feature vectorTC[i].Set the sensing node within the communication radius of nodepiis (p1,p2,...,pn)
Definition 3-14: Grouped trust difference function of sensing nodes in distributed networking mode.
Whether or not any nodepjjoins the logical group wherepiis located needs to be calculated according to the trust difference function.With knownandD T[i],the trust difference function can be calculated as follows:
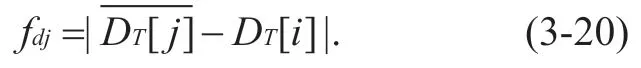
Nodepjsets a thresholdsd,iffdj<sd,join the group where nodepiis located.Figure 2 shows a schematic diagram of the logical grouping of sensing nodes of different networking modes in one area.
IV.NETWORK RESOURCE ALLOCATION MODEL BASED ON TRUSTED COMMUNITY
Due to the sensing heterogeneity of nodes,the communication protocols in the sensing network have IPv6 network infrastructure resources in addition to IPv4 network relat- ed resources,and can use IPv6 to transmit related data.Because IPv4 and IPv6 are not compatible,networks that use IPv4 and IPv6 protocols can only interact through regional border nodes.However,the differences between the IPv4 and IPv6 protocols result in the inefficient use of all network resources of the entire network during data transmission,resulting in a waste of some available resources.To address this issue,this section proposes a model for the integration of IPv4 and IPv6 network resources on the basis of perceiving the trusted group of nodes.The adopted network resources are used for unified allocation and scheduling.It can effectively solve the fairness of network resource allocation in the data transmission process,and can effectively guarantee the timeliness and reliability of data transmission.
This section describes the IPv4 and IPv6 network resource allocation model.The model is built on the perspective of the global network.The main symbol of the model is shown in Table 1.
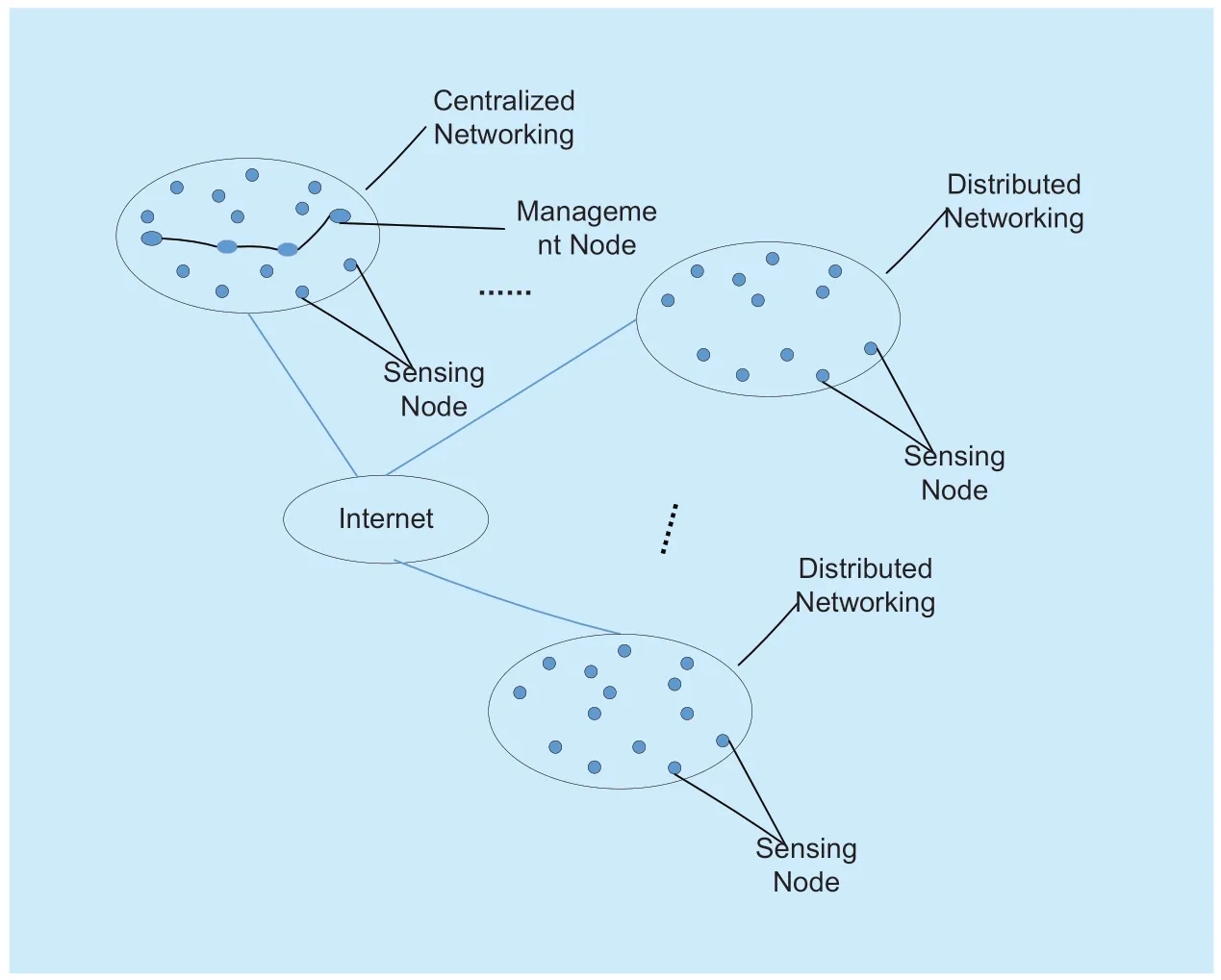
Fig.1.Sensing node trust logical grouping diagram.
In order to globally schedule network resources and collect network resource requirements at the time of data transmission,it is possible to periodically optimize the pre-allocation of network resources.In addition,the allocation of network resources from the perspective of the global network can ensure the fairness of network resource allocation,and can guarantee the timeliness and reliability of data transmission.
4.1 IPv4 and IPv6 network resource sharing allocation model description
In an area of the Internet of Things,all data is ultimately transmitted to the network layer through data aggregation nodes.All data transmission will go through IPv4 or IPv6 network.The relay node through which the data passes belongs to IPv4 or belongs to IPv6.Therefore,in the current deployment of IoT sensingnodes,there are both IPv4 networks and IPv6 networks.Through the technology,the unified management of IPv4 and IPv6 resources can effectively improve the utilization of network resources.Figure 1 first describes the logical integration diagram of IPv4 and IPv6 network resources within a region.The communities in this region are established based on the trusted community building model proposed in the section.
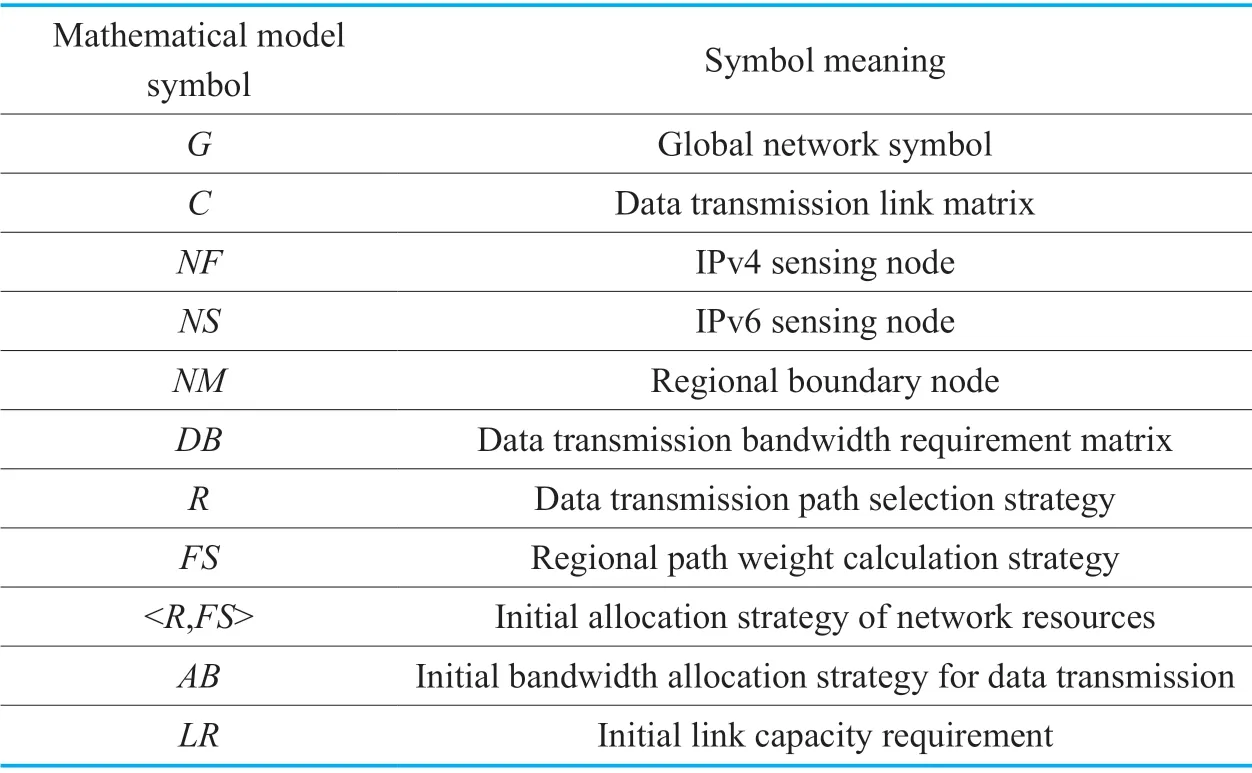
Table III.Global model symbols for IPv4 and IPv6 network resources.
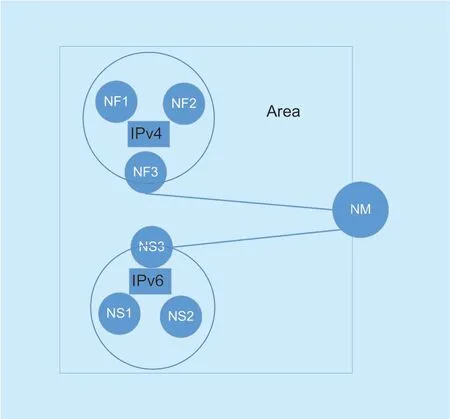
Fig.2.Network resource logic fusion diagram.
Figure 2 logically describes the logical fusion relationship between IPv6 and IPv4.In the figure,there are IPv4 networks and IPv6 networks in the area.NMrepresents a set of regional boundary nodes (more than one boundary node in a region,the above diagram is only a schematic diagram).Each area has an IPv4 and IPv6 network inside.If data is transmitted from one area to another,the original data node generated by the data may be located within the IPv6 or IPv4 network of the area.First,the data first reaches the border node of IPv6 or IPv4 (NMshown above).When this area is used as a relay area,the border node receiving the data will select an optimal internal transmission link from this area to transmit the data.This section first describes the link model,which is described as follows:
DefineJto be an internal path hop count (length)for IPv6 or IPv4 networks.The maximum amount of data transmission of linkiin the path is represented byLci..Then the maximum data transmission amount of this path depends on the minimum value ofLci,so the data transmission amountLcof this path can be expressed as:

The above formula describes only the theoretical maximum data transmission volume of the link.The actual load of the link should be considered in the actual transmission process.Therefore,leturibe the actual load rate of linki.Therefore,the actual remaining bandwidth of linkican be expressed asLci(1 -uri).Then,the actual available bandwidth of the data transmission path can be expressed as:
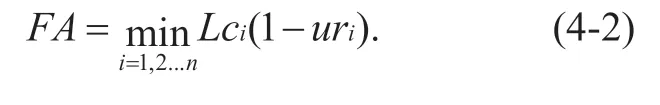
Equation (4-2)gives a rough estimate of the actual available bandwidth during data transmission,but does not give the available bandwidth at a specific time,and is limited to qualitative description during actual use.In order to more accurately describe the available bandwidth of the data transmission path,the definition of the available bandwidth within a period of time is further introduced.First,set the node on the path toNodei,and define the state function of the node at a certain time as follows:
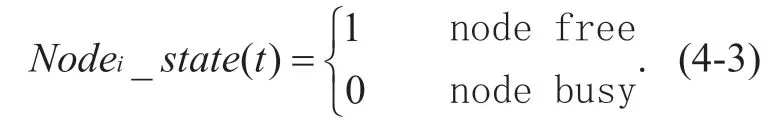
Then for a given time window [ti,ti+1] ,the link idle rate between nodeNodeiand nodeNodei+1can be calculated as follows:
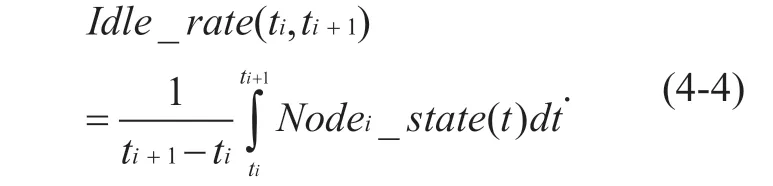
Then in the time window [t i,ti+1] ,the available bandwidth of the link between the nodeNodeiand the nodeNodei+1point can be calculated as follows:
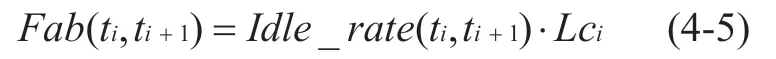
When the link between nodeNodeiand nodeNodei+1is idle and a new data packet arrives,Nodeiwill send the data toNodei+1immediately.Therefore,when the link between nodeNodeiand nodeNodei+1is idle,the data transmission delay is 0.In the actual data sending process,since data packets are sent in sequence,any one data packet is transmitted immediately after theNodeiis received,which means that the data link is in an idle state.According to the description of formula 4-5,given a data transmission path,the above node fromNode1toNodeN,Then,the available bandwidth of the path is related to the linkLciwith the smallest capacity on the path.The available capacity of actual data transmission on the path in the time window [t i,ti+1] is:
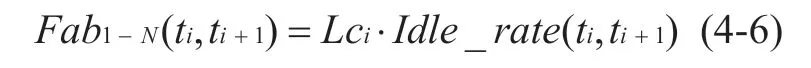
According to the above description of the link model,when data is sent to a regional boundary node,the boundary node first queries the actual data transmission available capacity of IPv6 and IPv4.Then,according to the actual data transmission availability of IPv6 and IPv4 and the network delay,the actual amount of data transmission shared by the IPv6 and IPv4 networks is determined.Set the available capacity of actual data transmission on [t i,ti+1] within IPv6 and IPv4 toV6_Fab1-N(ti,ti+1)andV4_Fab1-N(ti,ti+1)(computing method and formula 4-6 are consistent).Assuming that the total amount of data sent isDM,then the amount of data forwarding for IPv6 and IPv4 in the area can be calculated as follows:
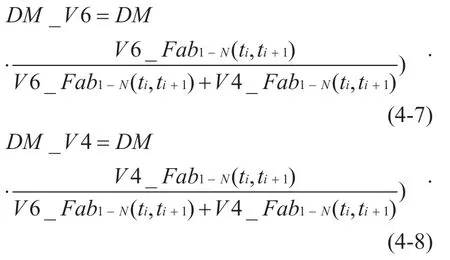
According to Equations 4-7 and 4-8,when the data reaches the border nodeNM,theNMqueries the actual link capacity of IPv6 and IPv4.According to the actual link capacity,the data is transmitted through IPv6 and IPv4,respectively,so that IPv4 and IPv6 resources in one area can be fully utilized.
4.2 Global network resource model description
The previous section describes how IPv4 and IPv6 network resources within a region are allocated uniformly.This section discusses network bandwidth allocation from a global network perspective.Figure 3 describes the global network from logic (this diagram is a schematic diagram,NMirepresents a network area not only represents a border node).The links betweenNMirepresent the communication paths between the regions.
Therefore,using the global model symbol can mathematically describe the global network data transmission logic link diagram.The global network model can be represented asG=<NM,L>,whereNM={NM1,NM2,....,NMN} represents a different area in the global network.AA represents the number of links in the network.Different areas in the transmission process include go and return.Therefore,the links in Figure 3-2 should be bidirectional.After transformation,we can see Figure 3-3.The global network model has changed from an undirected graph to a directed graph.In order to more accurately describe the link characteristics between areas,if there are multiple transmission paths between two areas,the path in the same direction is combined into one path.InG=<NM,L>,this section usesRCto indicate the data transmission capacity ofL,RCiis the data transmission capacity ofLi,and this section combines the links with the same direction into one link.
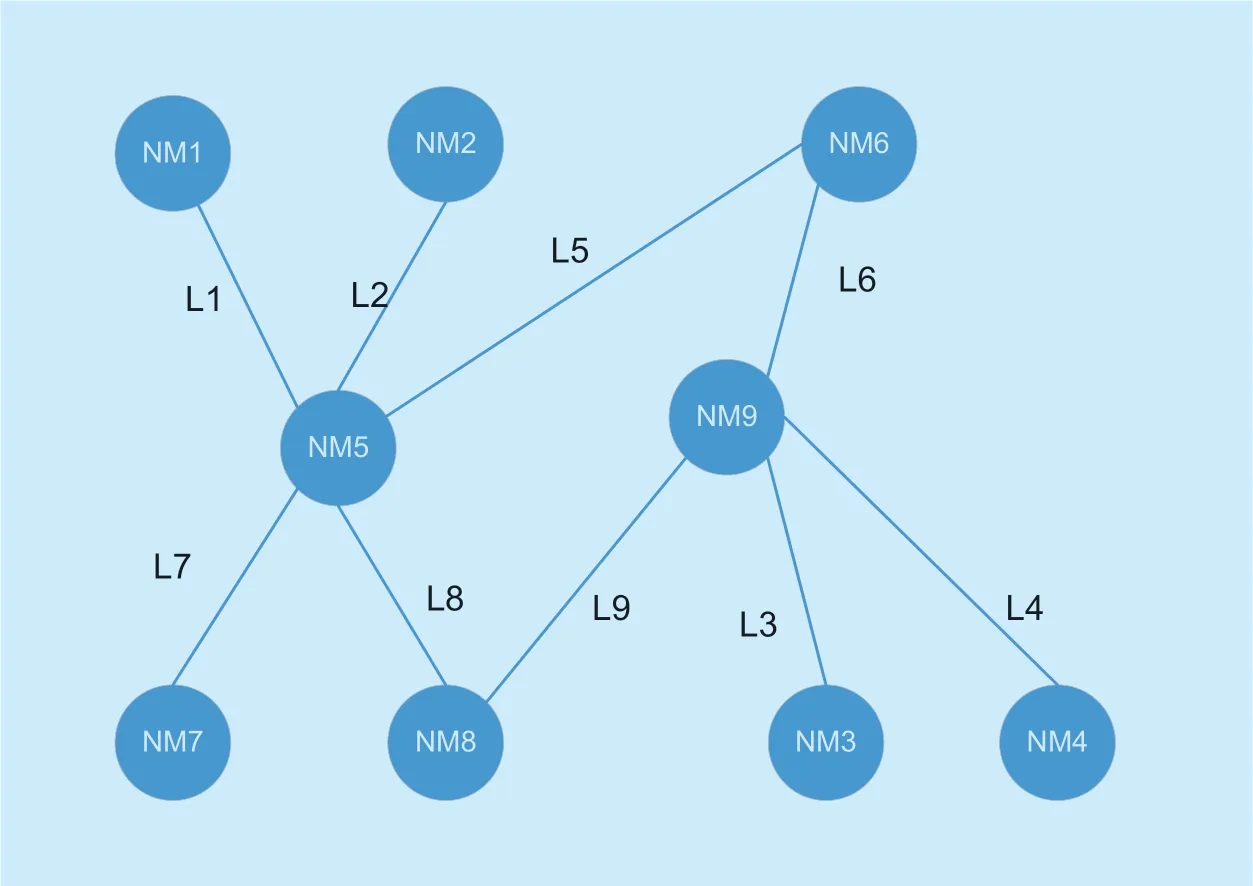
Fig.3.Global network data transmission logical link diagram.
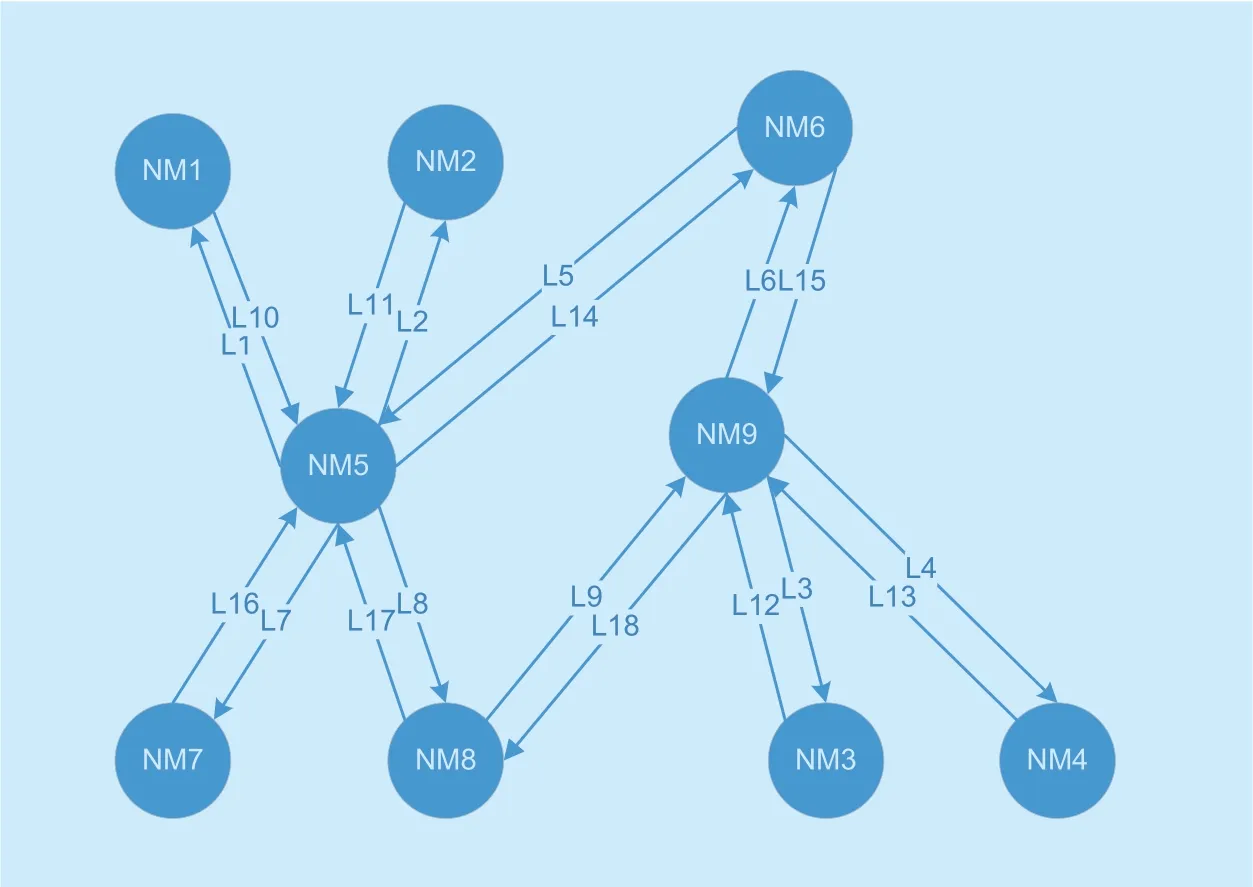
Fig.4.Global network data transmission logical link directed diagram.
In order to improve the environmental adaptability of the model,in the actual network environment,the link capacity of outbound and backhaul varies greatly.In actual environments,RCneeds to be adjusted according to different scenarios.
4.3 Regional communication link matrix
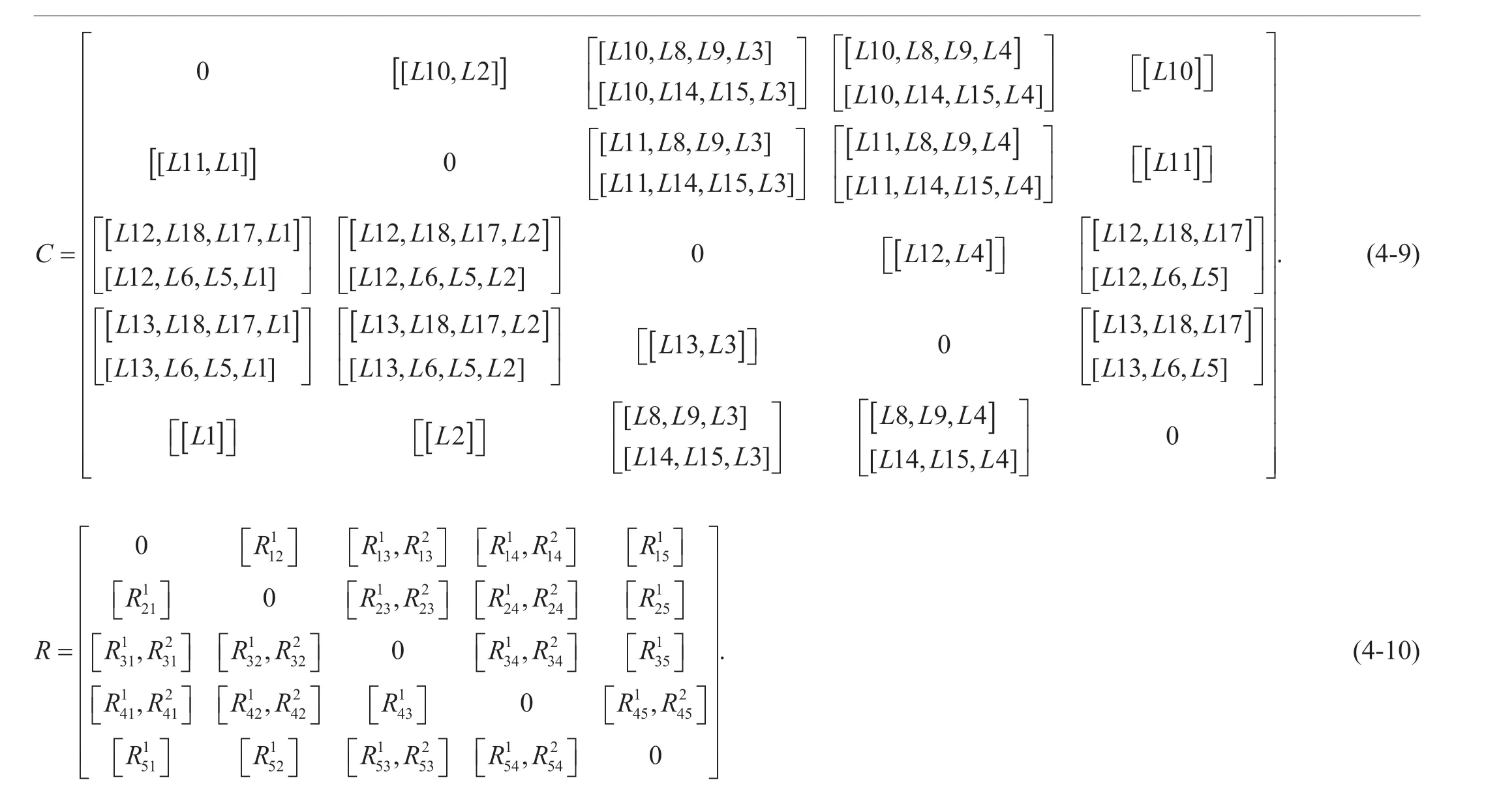
According to the above description of the global network data transmission logic and Figure 4,the communication links between different areas can be confirmed.The logical path between any two regions can be obtained through the logic description of the previous section,and any one logical path includes multiple links.According to Figure 3 the communication link matrix C can reach any area subset.In this matrixC,Cijrepresents the communication path from zoneitoj(NMilogically represents a certain zone),and the elements of matrixCsatisfy the following constraints: Firstly,Cijis a set of links of a series of links.The order of the links is from the initial area,and the number is gradually increased.The optimal communication link is preferred.Second,all link combinations do not contain loops,and the self-loop in the same area is 0.SelectNM1toNM5area as a demonstration,available regional communication matrix is (4-)shown in the bottom at next page.
In the data transmission process,network traffic between areas is the core of data transmission.Therefore,according to matrixC,all communication links betweenNM1andNM5can be confirmed.Because data transmission needs to consider the timeliness and reliability of data,the minimum bandwidth required for data flow is selected when selecting a link and the specific delay must also be considered.The link selection in this section follows depth-first traversal of the graph.Therefore,it can be seen that the time complexity of adding one area for data traffic scheduling isO N(3),and the time complexity of reselecting a data transmission link isO N().
4.4 Global network resource allocation strategy
The data transmission in the sensing layer of the Internet of Things is the transmission between the area and the area.The data transmission bandwidth requirement matrixDBis the bandwidth requirement between the area and the area,that is,the area bandwidth requirement matrix.There areNaareas,DBijis the bandwidth requirement from areaito areaj.The global network link logic descriptionGis a directed graph,soDBijandDBjihas different link sequence,and the bandwidth is also different.The bandwidth requirement of the area to the area can be decided based on the amount of data sent,or it can also make decisions based on the link load between different regions.
When the description of the logic descriptionGand bandwidth requirement of the global network link is given,the data transmission links of any two regions can be logically arranged from the matrixG,and various network resource allocation solutions can be obtained according to the logic arrangement of data transmission links.According to the definition of the global model symbol,Rpath select strategy matrix,which has the same dimensions as the communication link matrixCof any area subset.The difference is that all possible path paths inCare listed,and a deterministic path selection strategy is given byR.
Therefore,according to the area communication link matrixCfrom the areaNM1to the areaNM5,a feasible qualitative path selection strategy matrixRcan be calculated.IfRijα=1 in the matrix,it meansRijαis chosen as data traffic communication path.Otherwise,Rijα=0 shows that the path has no data flow,so the matrix can be represented as (4-10)shown in the bottom at this page.
The regional path weight calculation strategyFSis mainly used to confirm the network bandwidth allocated on different paths.FSis also a policy matrix,which can be described as (4-11)shown in the bottom at next page.
The elementsFSijβinFSare data flow loads for the optional pathRijα,soFSijβandRijαshould satisfy the following equation:
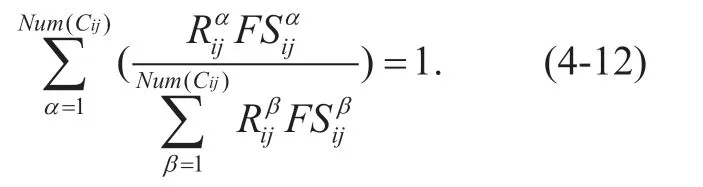
The initial bandwidth allocation strategy for data transmission of the pathAB(the matrix,RandFSare of the same order matrix)can be calculated from the matrixRand the matrixFS,andABijcan be calculated byDBijandCij:
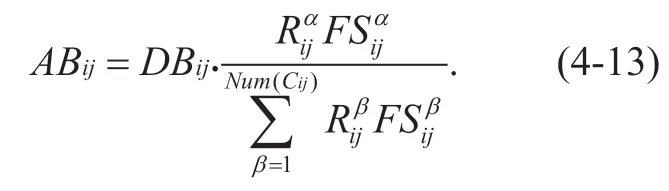
At the same time,the sum ofABijisDBij,which can be obtained by the above formula.c <R,FS>constitutes a network resource allocation strategy.Any pair of elements can calculate the bandwidth allocation on a certain path.
4.5 Data communication link capacity calculation
When a network resource allocation policy <R,FS>is given,the initial link capacity requirementLRrequired for data transmission can be calculated,and the number of elements inLRdepends onL.Given <R,FS>,LRirepresents the sum of the data transmission bandwidth required for all areas that pass through the link.Without loss of generality,in the global network data transmission logical link directed graph shown in Figure 4-3,CLis a link-related matrix,and the element 1 inCLrepresents the data communication link through a certain data linkLi,and the element with 0 means the data linkLiis not passed.According to Figure 3-3,there are a total of 18 data links,so the matrix formed byCLis as (4-14)shwon in the bottom at this page.
Given the matrixCL,DBand <R,FS>,LRcan be calculated,the calculation method can be described as follows:
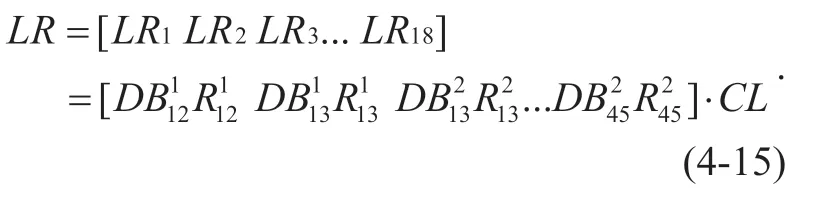
After calculatingLR,by calculating the ratio ofandRCi,the actual data traffic loadLmon the link can be anticipated.
4.6 Global network status monitoring
Given the matrixLRand the policy <R,FS>,the data link load and network resource usage can be calculated.LetLNbe the total number of links inis the average load of the data link (mathematical expectation)and its calculation method is described as follows:

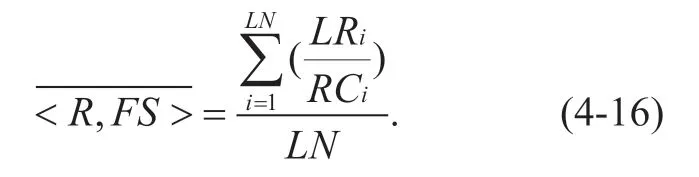
So the variance <R,FS>can be calculated according to formula (4-16),the calculation process is described as follows:
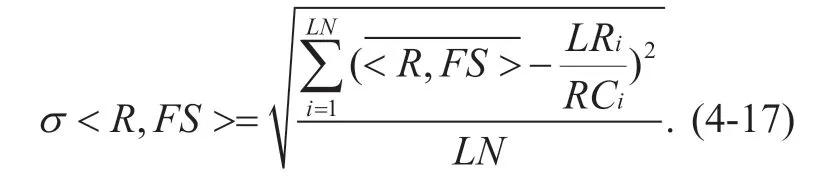
The range ofσ<R,FS> is [0,+∞),The closer to 0 the value ofσ<R,FS>,the more balanced and fair the network load.At the same time,the link's congestion status can be judged according to the value ofRC i-LRi,if.If the link status is normalBased on the above conditions,the number of congested links on a communication path can be calculated.Its calculation formula is described as follows:
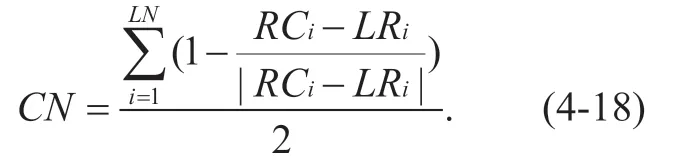
The link congestion rate can be calculated based on the number of link congestions.The calculation formula is as follows:
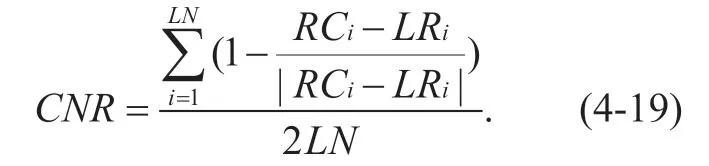
When the value ofCNRapproaches to 0,there is no congestion in the link.At this time,the overall efficiency of the network is the highest,and the data communication and jitter status can be neglected.
4.7 Global data transmission support technology
When it is confirmed that the initial allocation policy of the network resource is <R,FS>,the bandwidth on the data transmission path can be calculated from the i-th column of the matrixCL,and the allocation set of the link according to the bandwidth required for transmission is set toLBm.Calculatingcan allocate bandwidth to the linkLifairly according to the state of global network resources.At the s ame time,satisfies the following formula:
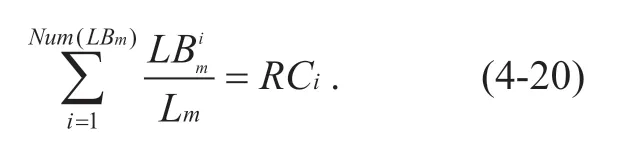
Given a matrixCLand set that the row associated within the matrix isCLRijα,according toCLRijα,it can be calculated that the link set ofpassing isLijα.Formula(4-20)can calculate the minimum bandwidthRCiin the data transmission process.In order to protectit can be guaranteed by the following calculation:
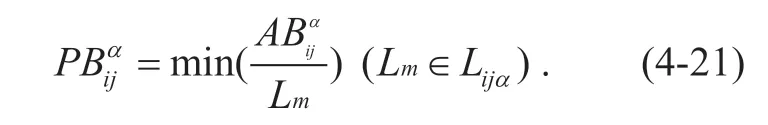
According to formula (4-21),the minimum bandwidth ofDBijcan be guaranteed
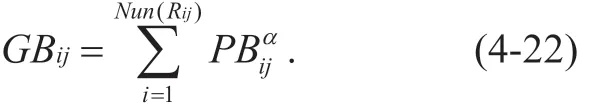
Even if the policy <R,FS>is given,it may still fail to meet all the bandwidth requirements of the global network.The part of the bandwidth that cannot be satisfied can be calculated by the following formula:
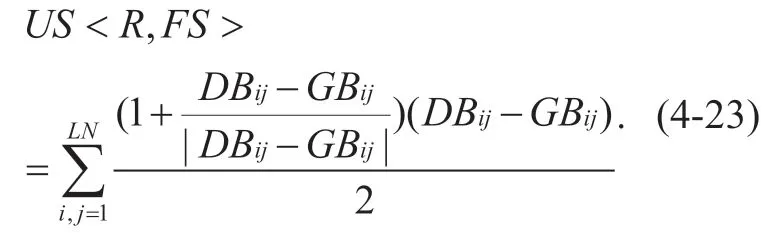
The range ofUS<R,FS>in equation (4-23)is [0,)+∞,and the ideal value is 0.When it is greater than 0,there is room for further improvement in global network resource allocation.
4.8 Global network resource allocation model
Ifσ<R,FS>is 0 andCNRis close to 0,global network resource allocation achieves optimal load balancing and highest usage efficiency of network resources.At the same time,the closer to 0 the value ofUS<R,FS>,the more reasonable the allocation of network resources.Therefore,the global network allocation process needs to consider the value ofσ<R,FS>,CNRandUS<R,FS>comprehensively.It uses the following formula to describe the distribution model:
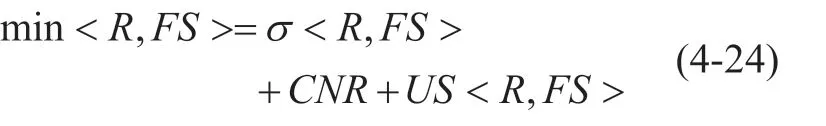
The constraint is that all policy elements must belong to the matrixRandFS,where=1 or=0.At the same time,as for randomit satisfies
If a minimum <R,FS>can be got,then the optimal solution of the above plan can be obtained.In this case,<R,FS>can be used as the optimal network resource allocation strategy.From a global point of view,the distribution of network resources during data transmission has a tremendous impact on the timeliness and reliability of data transmission.Therefore,from a global perspective,the unified planning and scheduling of network resources in different regions,the optimal solution of network resource scheduling from a global perspective,and the guarantee of data transmission are of great significance.
V.EXPERIMENTAL SIMULATION
5.1 Link validity assessment
This article simulates a network environment through.NetLogo simulation software and verifies the effectiveness of the proposed model.The verification simulation process mainly includes the initialization of the global network,the initialization of the regional network IPv4 and IPv6,the calculation of theglobal network resource allocation policy,the abstract description of the IPv4 and IPv6 local network resources,and the final calculation of the environmental adaptability.
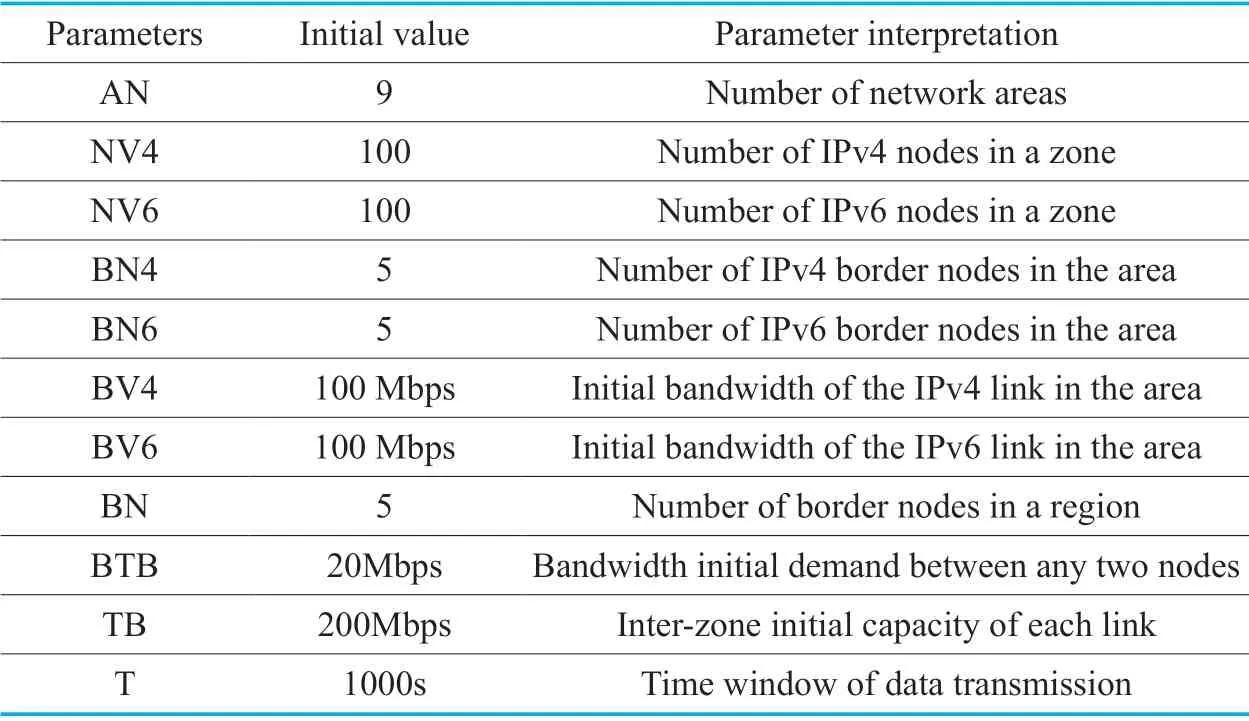
Table IV.Experimental parameters.
When the global network is initialized,after the parameters are set,the data transmission link matrixC,data transmission bandwidth requirement matrixDB,and data transmission path selection policy matrixRcan be calculated through the network model in Section 4.3.According to the three initial matrices,when the amount of data transmission is different,different network resource allocation strategies can be calculated.Then,an intra-area IPv4 and IPv6 network convergence strategy is determined according to the network resource allocation strategy,thereby ensuring the timeliness and reliability of data transmission.Then,the network resource allocation status can then be monitored based on the initial allocation policy for network resources <R,FS>,the initial bandwidth allocation policy for data transmissionAB,and the link capacityLR.Table 4 is the experimental parameters of this article
In order to verify the correctness and validity of the model in this chapter,experiments in this section will be compared with common network resource allocation algorithms such as equivalent multipath protocol (ECMP)and shortest path priority protocol (SPF).According to Figure 2,the simulation is transmitted from area 1 To area 4,there are 5 border nodes in each area.Under the premise of ensuring that at least one link node in each area works,disable the border nodes on the link from 1 to 10 in order to simulate multi-path data.In the transmission environment,the selection of data transmission paths in the process network will be less,and the bifurcated bandwidth will change in turn.In order to verify the trusted node selection mechanism in the data transmission proposed in this chapter,the simulation is transmitted from zone 1 to zone 4,and the number of the untrusted boundary node (assuming data is transmitted to the untrusted node,the data will be lost)is from 1 to 10 processes.After the trusted node was selected,the experimental results of the successful rate of data transmission are shown below:
According to figure 5 to figure 7,as the disabled node 1 increases to 10,the link load balancing degree of the shortest path priority model gradually decreases.At the same time,the total number of data links and the number of idle data links in the global network will gradually decrease.Since the shortest path preference scheme only selects the shortest data link,the link load balance value in the shortest path priority scheme decreases as the link load balance value decreases.The load of the selected link in the shortest path priority scheme will increase.The solution of this paper and multipath solution will optimize the link load as the load balancing rate changes.Therefore,the link balance and the link load degree are better than the shortest path priority solution.However,if the bandwidth is not limited,the inter-area link load will increase and the link load in the area will also decrease.Therefore,when the number of disabled nodes increases,the load balance degree of the multipath solution and the solution of this paper will increase.The solution of this paper can better optimize the load of the link and can distribute the network resources more reasonably.Therefore,the load balance degree of the scheme in this paper is lower than that of the multipath solution.Especially when the bandwidth can meet the maximum data transmission requirement,the network resource allocation in this paper does not generate a congested link and all data transmission requirements can be satisfied.
In summary,by using this solution in the Internet of Things,data transmission network can better improve the utilization of existing network resources,and network resources can be more equitably distributed.At the same time,if the current network resources cannot meet the data transmission requirements,the data transmission needs can be guaranteed by reducing the network load and reducing the data transmission guarantee bandwidth.
5.2 The effectiveness of trusted measurement
The node trusted measurement proposed in this paper are based on the trust value measurement of the computing environment,and are based on the measurement of the trusted behavior of the nodes,the use of active trusted measurement to ensure the credibility of the node,in order to ensure the credibility of most of the nodes in an area.
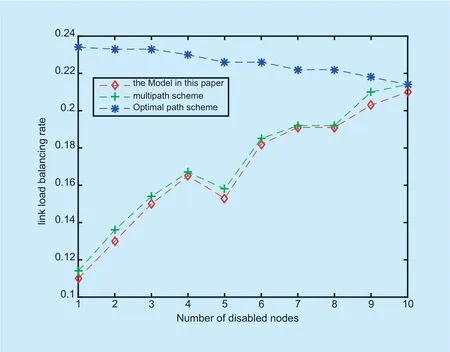
Fig.5.Link load balancing rate in experiments.
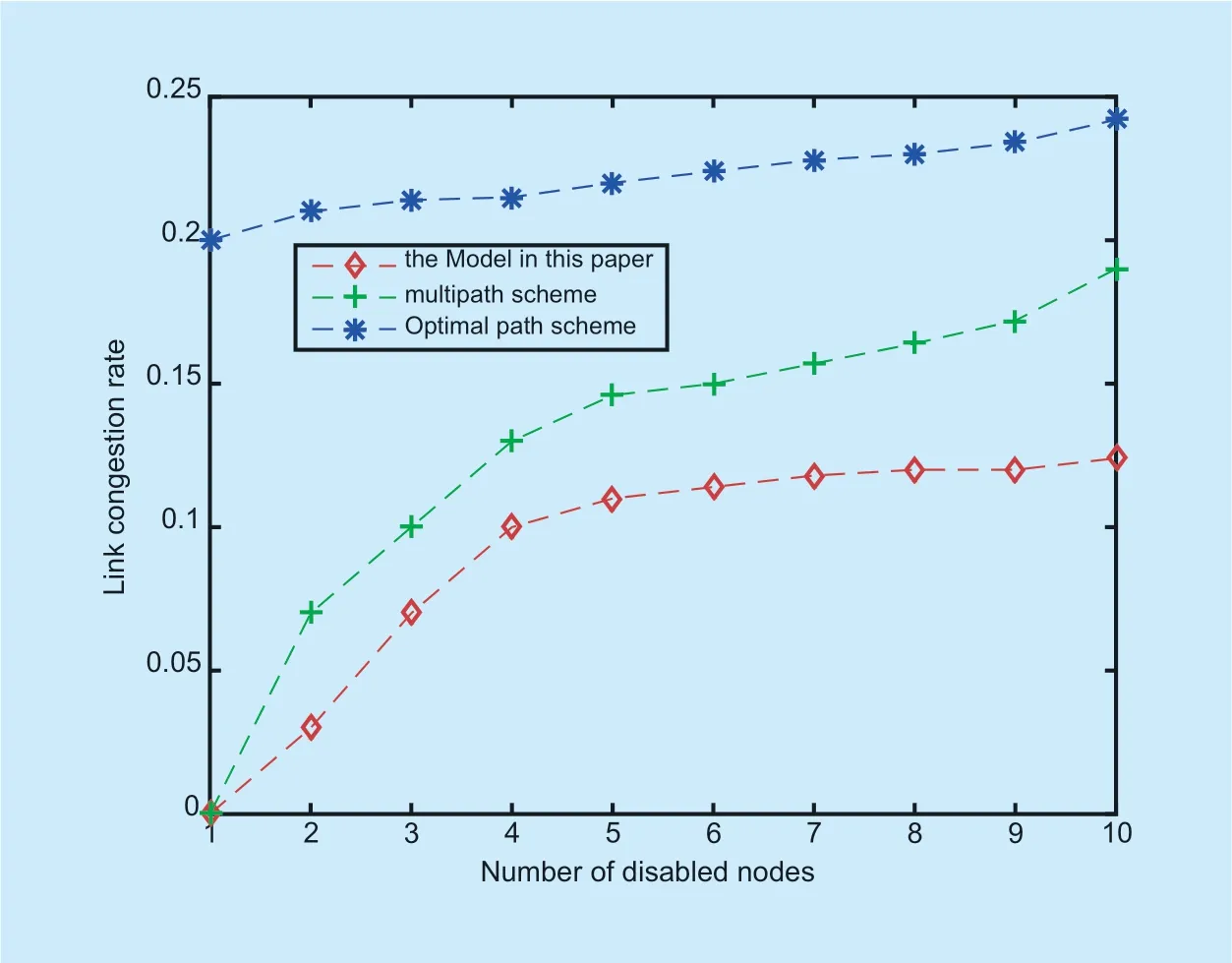
Fig.6.Link congestion rate in experiments.
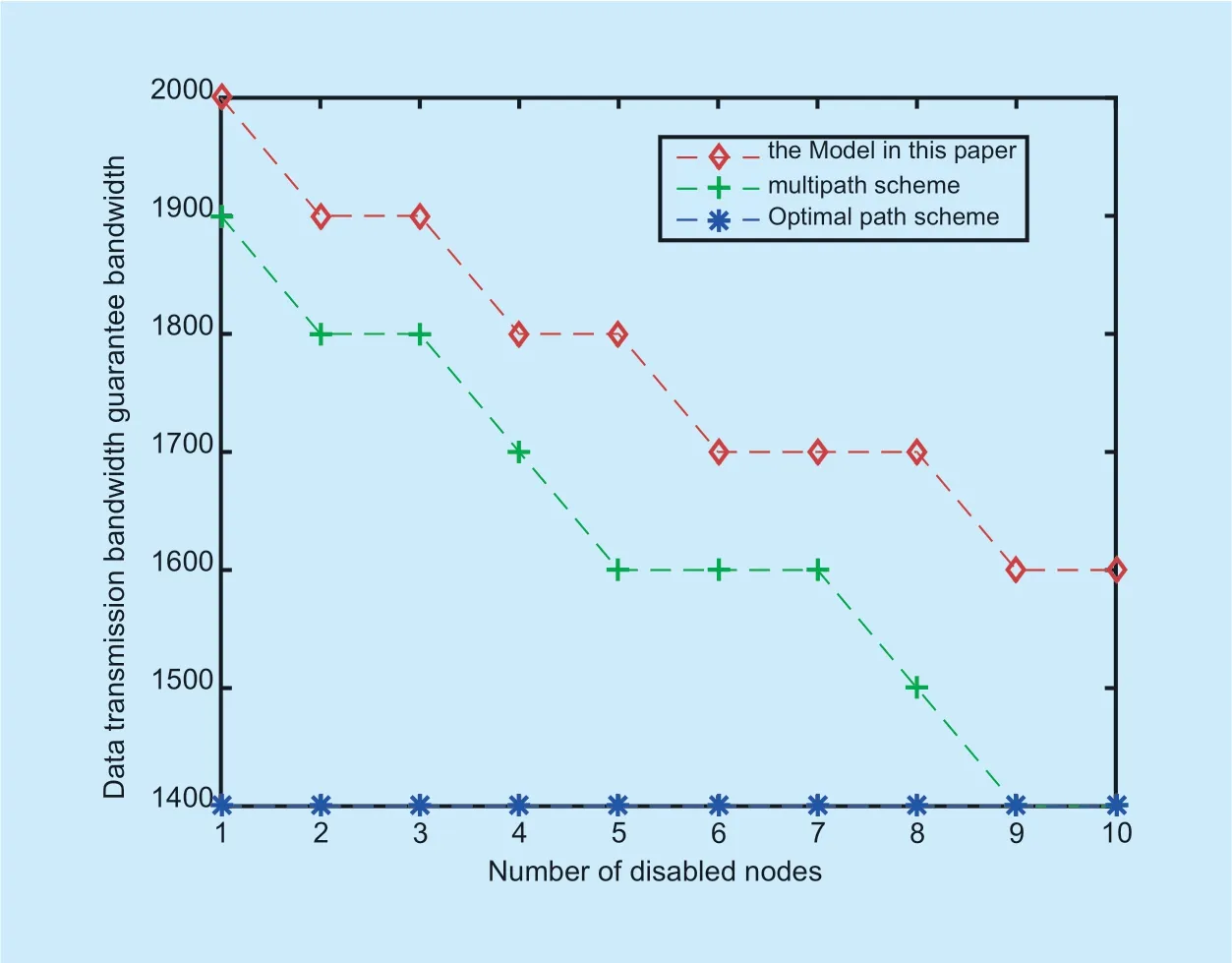
Fig.7.Data transmission bandwidth guarantee bandwidth in experiments.
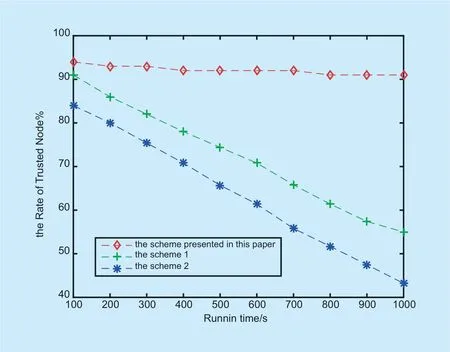
Fig.8.Comparison of the ratio of trusted nodes when malicious nodes occupy 5%.
In view of the current diversification of attack means for sensing networks and the proliferation of various malicious programs.For a region's sensing network,it is difficult to protect all nodes from attacks.However,the trusted measurement model discussed in this chapter can effectively identify attack behavior and malicious nodes,and can respond to attacks at the earliest time,thus ensuring the normal operation of unhacked nodes in the IoT deployment area.Because the simulation experiment cannot simulate all the attacks on the nodes of the Internet of Things,this section of the simulation experiment chose to focus on a representative attack,verifying the correctness of the model proposed in this section,the effectiveness of the response to the attack and the adaptability of the model environment.The following malicious behaviors are the focus of this section:
(1)Forged node identity,data hijacking,identity theft,parallel conversation,and asynchronous attacks;
(2)The spread of malicious programs in the sensing network;
(3)Implement a denial of service attack on a sensing network;
In order to verify the effectiveness of the proposed scheme,we compared the proposed scheme1-scheme2 with the defense mechanism of the nodes mentioned in [34-35].In the simulation experiment,first assume that the percentage of malicious nodes in a region is 5% and 10% respectively.The ratio of trusted nodes is as follows:
Through the simulation results above,it is found that when the proportion of malicious node users in a region increases,compared with scheme 1 and scheme 2,it can be seen that the sensing node trusted measurement scheme can effectively identify untrusted nodes and isolate untrusted nodes.The trust rate of the sensing node in this area can effectively protect the nodes in the area that have not received the attack.
5.2 Data transmission trust evaluation
Finally,under the premise that the proposed scheme improves the validity of network resource allocation,the validity of the trusted node selection mechanism in data transmission proposed in this paper will be verified.After using the trusted node selection,the data transmission rate is shown as follows:
It can be seen from Figure 10 that the success rate of data transmission is significantly higher than that of the multipath scheme and the shortest path priority scheme when encountering untrusted nodes.Therefore,the proposed scheme has better timeliness of data transmission and can be effective complete data protection at the same time.
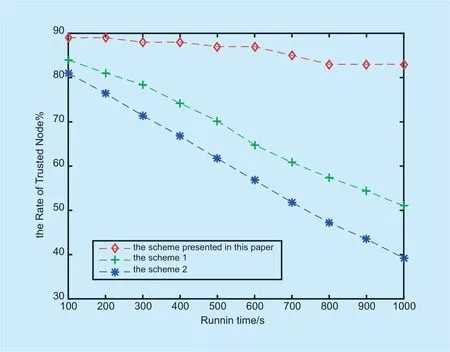
Fig.9.Comparison of the ratio of trusted nodes when malicious nodes occupy 10%.
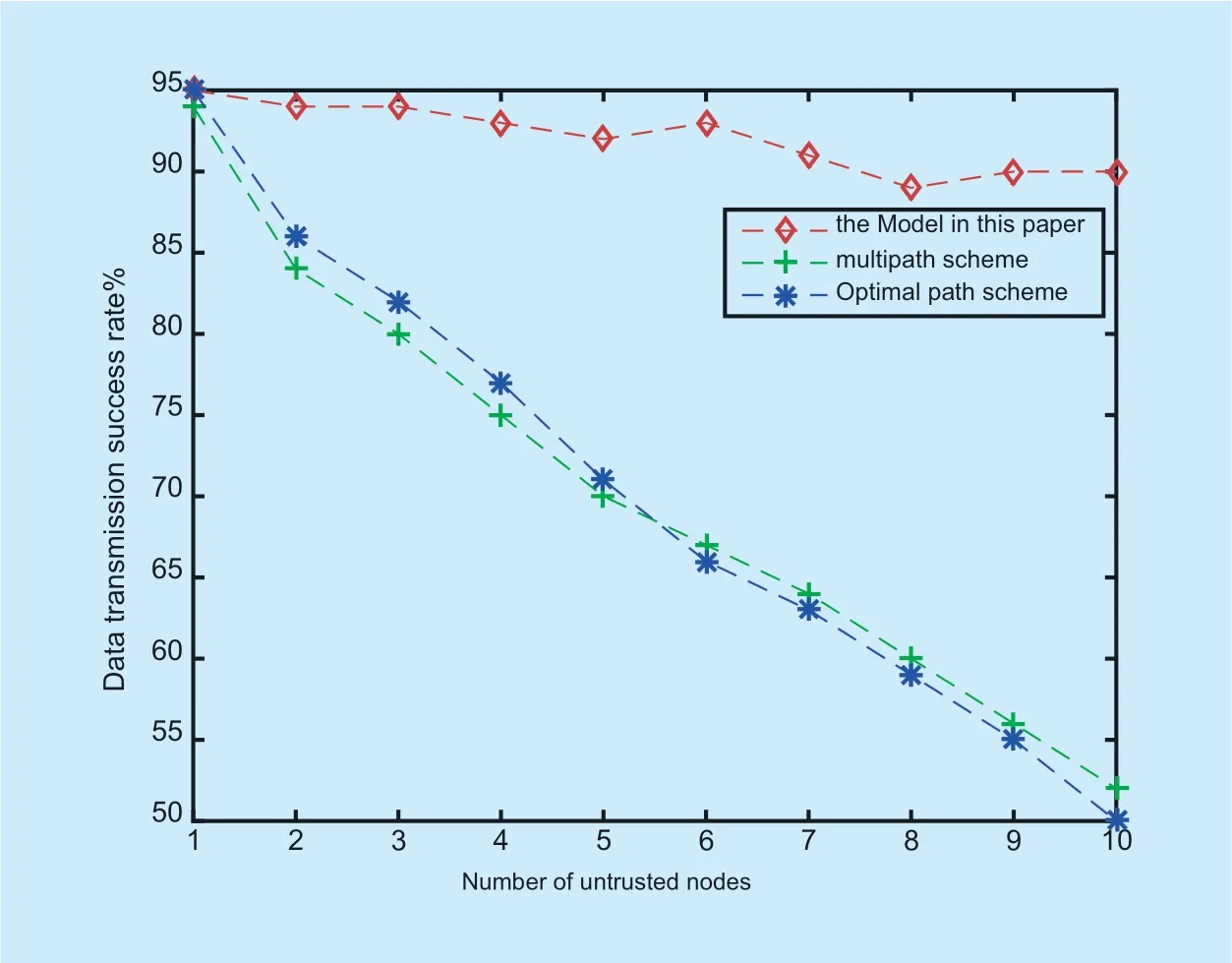
Fig.10.Data transmission success rate.
VI.CONCLUSION
This paper proposes a network resource allocation model based on the trust value measurement of sensing nodes in the sensing layer of Internet of Things,which builds a trusted group on the basis of trust measurement to ensure the trust of the computing environment.Then,according to the requirements of data transmission,a network resource allocation model was established rationally and efficiently.This model fully considers the multipathability of the network,ensures the fair distribution of the limited network resources at the sensing layer of the Internet of Things,and can achieve data security in the transmission process.The simulation experiment shows that the proposed model can effectively optimize the bandwidth allocation in the data transmission process,and has little effect on the operating efficiency of the existing network applications.At the same time,it can effectively guarantee the reliable operation of the nodes and realize the reliable transmission of data.
ACKNOWLEDGMENTS
This work was supported by the National Natural Science Foundation of China Research on Dynamic Trusted Running Mechanism of IoT Heterogeneous Nodes: 61971014,The research of the trusted and security environment for high energy physics scientific computing system: 11675199.
- China Communications的其它文章
- Distributed Optimal Control for Traffic Networks with Fog Computing
- TVIDS: Trusted Virtual IDS With SGX
- New Identity Based Proxy Re-Encryption Scheme from Lattices
- A Real Plug-and-Play Fog: Implementation of Service Placement in Wireless Multimedia Networks
- A Novel Shilling Attack Detection Model Based on Particle Filter and Gravitation
- Application of Neural Network in Fault Location of Optical Transport Network

