TVIDS: Trusted Virtual IDS With SGX
Juan Wang*,Shirong HaoYi LiZhi HongFei YanBo ZhaoJing Ma,Huanguo Zhang
1 Key Laboratory of Aerospace Information Security and Trust Computing,Ministry of Education,School of Cyber Science and Engineering,Wuhan University,Wuhan 430072,Hubei,China
2 School of Cyber Science and Engineering,Wuhan University,Wuhan 430072,China
3 Science and Technology on Information Assurance Laboratory,Beijing 100072,China
Abstract: Network functions such as intrusion detection systems (IDS)have been increasingly deployed as virtual network functions or outsourced to cloud service providers so as to achieve the scalability and agility,and reducing equipment costs and operational cost.However,virtual intrusion detection systems (VIDS)face more serious security threats due to running in a shared and virtualized environment instead of proprietary devices.Cloud service providers or malicious tenants may illegally access and tamper with the policies,packet information,and internal processing states of intrusion detection systems,thereby violating the privacy and security of tenant's networks.To address these challenges,we use Intel Software Guard Extensions (SGX)to build a Trusted Virtual Intrusion Detection System (TVIDS).For TVIDS,to prevent cloud service providers from accessing sensitive information about the users' network,we build a trusted execution environment for security policy,packets processing,and internal state so that cloud service providers and other malicious tenants can't access the protected code,policy,processing states,and packets information of the intrusion detection system.We implemented TVIDS on the basis of the Snort which is a famous open-source IDS and evaluated its results on real SGX hardware.The results show that our method can protect the security of the virtual IDS and brings acceptable performance overhead.
Keywords: network function virtualization; intrusion detection system; SGX; trusted execution environment
I.INTRODUCTION
In traditional networks,network functions run in proprietary physical devices instead of standard servers and virtualized environment.In that case,service providers must undergo a long product cycle and complex service deployment,resulting in high capital expenditures (CapEx)and operating expenses (OpEx).Meanwhile,it causes that network functions are hard to be customized and modified.Furthermore,hardware development makes a large barrier of entry for new vendors,innovation and competition.
Network Function Virtualization (NFV)[1-3] proposes to encapsulate network functions in virtual instances and deploy them on standard servers so that they do not have to rely on specific network devices.It changes the operation mode of traditional networks.Due to independence on proprietary physical devices,virtual network functions are easy to deploy and combine as different network services according to the needs of users and service providers.Meanwhile,it is easier to maintain and upgrade the virtual network functions .Despite these advantages,the security issues introduced by the virtualization of network functions,have attracted widespread attention [2,4-8].As a virtual security function,a virtual intrusion detection system (VIDS)is very crucial to future networks [9].However,VIDS faces more serious security threats due to running in a shared and virtualized environment instead of proprietary devices.Cloud service providers or malicious tenants may illegally access and tamper with the policies,packet information,and internal processing states of intrusion detection systems,thereby violating the privacy and security of tenant's networks [9-11].
Aiming at the challenges,we propose to use Intel SGX to build a Trusted Intrusion Detection System (TVIDS).We deeply analyze the architecture of existing IDS,Snort,and use SGX to protect its important code,data,states,and policy.Furthermore,we present to use the remote attestation mechanism based on SGX to measure and validate the integrity of VIDS.
Our paper makes the following contributions:
● We design a Trusted Intrusion Detection System (TVIDS)to protect the security of virtual intrusion detection system.In TVIDS,the key code,sensitive states,and policy are protected with the SGX enclave so that cloud service providers or malicious tenants can't access and tamper with them.
● To address the security issues for VIDS outsource,we propose a remote attestation approach based on SGX so that user can upload the private traffic through the secure channel between user and cloud service provider.
● We also present SGX performance optimization approaches to reduce the overhead impact due to system call with SGX enclaves.Furthermore,we prototype TVIDS on Snort,an open-source IDS,and evaluate its security and performance on real SGX platform.The results show that our method can protect the security of the virtual IDS and brings acceptable performance overhead.
The rest of this paper is organized as follows.Section II introduces the background and threat model.Section III shows the related work.Section IV proposes the overall design of our trusted intrusion detection system,a secure remote attestation approach,and performance optimization approach.Our implementation and evaluation are presented in section V and section VI.Section VII discusses the limitations and future work.The conclusion goes to Section VIII.
II.BACKGROUND AND THREAT MODEL
2.1 SGX
Intel Software Guard Extension (SGX)[12] provides a secure,isolated hardware-based container where a user can put applications to and then only the applications can access the memory address of the container.Intel calls this container an enclave.SGX assumes that everything on a system except CPU is not credible.That is,OS,driver,BIOS or virtual machine monitor (VMM)are untrustworthy [13].For an SGX program,the enclave is a secure black-box where it can run.Compared with TPM (Trusted Platform Module),SGX makes TCB (Trusted Computer Base)smaller while reducing the attack surface of programs and providing stronger hardware isolation [14,15].
2.1.1 Enclave
Enclave provides isolation protection for sensitive data and code.SGX allows applications to be specified the trusted part and untrusted part.The trusted part is loaded into an enclave for protection.Once the protected part of an application has been loaded into an enclave,SGX protects them from external software,no matter it is a malicious program or just a normal one.The code inside an enclave can only access the data and code which belongs to the same enclave.If multiple enclaves to work together is necessary,authentication between enclaves is needed.
CPU will check the trusted part before it is loaded into an enclave.In the compiling process of an SGX-enable program,the trusted part is measured and a private key will be generated to sign the measurement value.When the trusted part is loaded into the enclave,the CPU will measure it and store the result of measurement in a dedicated register in the CPU,and then the signature of the trusted part is verified.Only the verification succeeds,the enclave is allowed to be launched.This mechanism ensures that a tampered application can't be booted,and the program owner can perceive if enclave has been tampered with.
All enclaves are loaded into a physical memory called EPC at running time.The Enclave Page Cache (EPC)is a subset of DRAM that cannot be directly accessed by other software,including system software and SMM code.EPC is managed in pages.The control information of the page is stored in a hardware structure called EPCM.A page corresponds to an EPCM entry,which is similar to the page table in the operating system.It manages the basic information of the EPC page,including the usage of the page,the owner of the page,page type,address mapping,and permission attributes.The EPCM structure is used to perform access control on the enclave page during address mapping in CPU.Logically,it provides an additional security layer of access control in addition to “legacy” segmentation,paging tables and extended paging tables mechanisms.And this structure is consulted by the processor's Page Miss Handler (PMH)hardware module.The PMH mediates access to memory by consulting page tables maintained by system software,range registers,and the EPCM.
EPC is a physical memory area retained by the system for the enclave.It not only has additional access control but also provides a memory encryption mechanism.The trusted part of a program is run in plaintext in the CPU,but when it is replaced by the memory page in the EPC,it is encrypted and written in the ciphertext.The encryption and decryption process is executed by the memory encryption engine (MEE-Memory Encryption Engine)in the CPU.The MEE uses a complicated combination of Merkle trees,a tweaked version of AES Counter Mode,and a Carter-Wegman MAC construction.This uses a 128-bit confidentiality key,a 56-bit counter,a 128-bit integrity key (producing 56-bit MAC tags),and a 512-bit universal hash key (used in the MAC construction).These are generated at boot,placed in special MEE registers,and destroyed at system reset.The MEE operates on 512-bit cache lines,so each encryption takes four AES operations.And it is a hardware unit that encrypts and integrity protects selected traffic between the processor package and the main memory (DRAM).Therefore,if attackers use the eavesdropping bus or other physical attack methods to obtain the EPC data,they will only get meaningless ciphertext.
We use SGX enclaves to protect the key code and data of VIDS.As a result,the important data of the virtual intrusion detection system will not be compromised or leaked at runtime,which ensures that the operating states of VIDS are protected.
2.1.2 Attestation in SGX
The attestation mechanism is a very important security mechanism provided by Intel SGX [4].Attestation is the process of validation that an application has been authenticated on the platform and protected by an enclave.An attestor can check and determine whether the SGX program is credible using by the received proof.The process of attestation will stop if the program is not trusted.
SGX provides two attestation methods [16],local attestation,and remote attestation.From the previous section we have mentioned,different security enclaves are isolated from each other which can't access each other.Although this ensures the security of the data within a container,it brings inconvenience for application interaction to some extent.Local attestation is the mechanism which allows the different enclaves on the same platform to interact with each other.Local attestation is usually used between two enclaves on the same platform.If they can finish the attestation successfully,the two containers can access each other.Remote attestation is used for cross-platform scenarios.It purposes to establish a secure session with a remote party.The verifier sends the relevant information including the container and its own platform to a remote party and then the remote party will check the information and validate it according to its own security configuration.
It is worth mentioning that the attestation mechanism provided by SGX enables an attestor to obtain the measured value of the code and data in the SGX container of an attested platform when an enclave is loaded.In this way,the verifier can determine whether the current container is running code and data as expected.In this paper,we use this mechanism to address integrity issue when a VIDS is used by a third party.
2.2 Intrusion detection system
An intrusion detection system (IDS)is a device or software application that monitors a network or system for malicious activity or policy violations.An IDS detects malicious behaviors by two methods.The first method is based on signature and the other method is based on the anomaly detection.Signature-based detection technology requires the prior definition of features that violate security policy events,such as header information,access frequency,etc..It is mainly to judge whether the collected information is consistent with the security features.This method is similar to anti-virus software.Anomaly-based detection technology takes another approach,which establishes a normal model in advance,and uses the various resource usage conditions under normal circumstances,such as CPU,memory,network,etc..or the hash of the file as a reference.In the actual use of the process,it is judged by whether it is in the normal patterns or not.In the actual application process,the signature-based detection method maintains a knowledge base which records all current possible illegal patterns.However,this knowledge base needs to be constantly updated,and at the same time,it is easy to miss because the unknown patterns which are not in the knowledge base can't be detected.For anomaly-based detection technology,it can't accurately judge the attack,but it doesn't need to update the knowledge base constantly,and it has better resistance to unknown attacks.However,it has a higher false positive rate because some legal behaviors may be mistaken for malicious attacks.A typical network-based IDS can be divided into the following important components: sniffer,preprocessor,rule engine,and so on.The sniffer is used to capture data packets from the network and the preprocessor performs some preprocess operations on the captured packets,such as assembly and decoding.The rule engine is responsible for processing the traffic according to the rules.
Currently,virtual IDS have been gradually deployed in commercial virtualized environments by service providers,such as Amazon AWS,VMware vCloud,VCE Vblock,Microsoft Azure,Google Cloud Platform.Furthermore,some enterprises also leverage outsourced virtual IDS to monitor their traffic.
III.RELATED WORK
ESTI NFV Security and Trust Guidance [5] proposed to provide trusted protection based on HSM (Hardware Security Module),TPM (Trusted Platform Module)[17],and vTPM (virtual Trusted Platform Module)[18,19].Marco De Benedictis et al.[7] discussed the challenges in applying one specific technology,Trusted Computing,to an NFV cloud-based architecture.Secure IDS [20] built an effective and secure Intrusion Detection System (IDS).It proposed to use TPM attestation and trusted computing to verify the URL request status.In addition,it improved access control mechanism for detecting and preventing web vulnerabilities.Though TPM can prove that the software and operating system are in a secure state and provide secure communication,it can't protect against access from hardware or side channels.Intel SGX provides similar functionality to TPMs,but with increased protections,because SGX provides a software isolation mechanism that protects against untrusted hardware and untrusted software [8].
OpenNetVM [21] ran network functions in lightweight Docker containers based on the NetVM architecture.It provided NF isolation based on container mechanisms,such as namespace and capability.NetBricks [22] leveraged a safe language (Rust)and LLVM [23] to build a zero copy soft isolation.It provided memory isolation software by using the typesafe language and achieved high performance by adoption LLVM as an optimization backend of compilers.However,these approaches cannot provide the high-security level protection for the virtual network function due to lacking the strict memory encryption and isolation mechanisms.
Furthermore,outsourcing NFs to a third-party service provider has emerged as a new trend which leverages the benefits of cloud computing and reduces network devices costs.However,outsourcing NFs to a cloud may leak enterprise network privacy and comprise the security of the enterprise network.Some works have addressed the issue of NFs outsourcing.Ladon [24] proposed a privacy-preserved firewall outsourcing framework based on Bloom Filters (BFs).However,BFs inevitably introduced false positives,for example,packets might accidentally be matched against a firewall rule.BlindBox [25] enabled Deep Packet Inspection over encrypted traffic without requiring decryption of the underlying traffic but it can't provide the performance required for packet processing and can't fit real-world market requirements.SplitBox [26] proposed an efficient system that allows a cloud service provider to privately compute network functions on behalf of a client,in such a way that the cloud does not learn the network policies.Although these works can mitigate the outsourcing security issue to some extent,the high-performance overhead still an obstacle to hinder its practical application.
Recently,Intel Software Guard Extensions (SGX)[12,27] has been proposed to protect VNFs [28,29].Trusted Click [8] proposed to use SGX to protect various Click elements,using these secure Click [30] elements to compose secure virtual network functions.ShieldBox [31] proposed to process encrypted traffic by using SCONE [14] (a shielded execution framework based on Intel SGX)and Click.In addition,ShieldBox added secure communication channels with remote attestation to existing Click architecture.LightBox [32] achieves very efficient in-enclave stateful middlebox processing with the high constraint enclave space.SafeBricks [33] built upon NetBricks [22],which can support modular and customizable network functions development such as Click,and leveraged SGX and Rust language-based enforcement.SGX-Box [34] used a high-level programing language,called SB lang for handling encrypted traffic in SGX-protection middlebox.They provided a few of API based on SB lang and automatically convert SB lang code to C/C++ code.However,none of these projects aims to support complex IDS such as Snort.
S-NFV [6] tried to use SGX to protect the Snort state.However,it ignored the policy protection and was implemented with an opensource simulator,OpenSGX [35] instead of real SGX platform.In addition,S-NFV simply put the entire Snort state into the SGX enclave without optimization compared with our work,which could cause larger performance.SECIDS [36] ran unmodified Snort with DPDK network layer,using Graphene-SGX (a shielded execution framework based on Intel SGX)[37] and SGX technology.SEC-IDS placed all snort code inside an enclave,however,has a large trusted computing base (TCB).An attacker only needs to exploit one vulnerability in the enclave code to circumvent the security guarantees of trusted execution.TVIDS decomposes the functions of VIDS and protects the important modules of VIDS,which reduces the trusted computing base.In addition,SEC-IDS ignored the security protection of virtual IDS outsourcing.Our work proposes the remote attestation approach based on SGX to address this issue.What's more,the performance of TVIDS is similar to SEC-IDS.
Compared with the previous works,our work provides the protection of virtual IDS codes,policies,configurations,states and achieves acceptable performance overhead.In addition,our work also provides guaranteed protection for virtual IDS outsourcing.What's more,our implementation is based on the physical SGX platform.Last but not least,we propose an optimistic approach to minimize the performance overhead caused by SGX while protecting the security of virtual IDS.
IV.SYSTEM DESIGN
Aiming at building a trusted execution environment for a virtual IDS,we design a Trusted Intrusion Detection System (TVIDS)which can prevent malicious attack and cloud service providers from accessing sensitive information and data about the user's network while the users use the virtual IDS function.
4.1 Virtual IDS security requirements
A virtual IDS is an IDS function based on virtualization technology and deployed on a standard IT server.Users can leverage the virtual platform to run IDS as a virtual instance.They also can send their data packets to a cloud IDS service for processing,and then the IDS service will send back the results to the users.
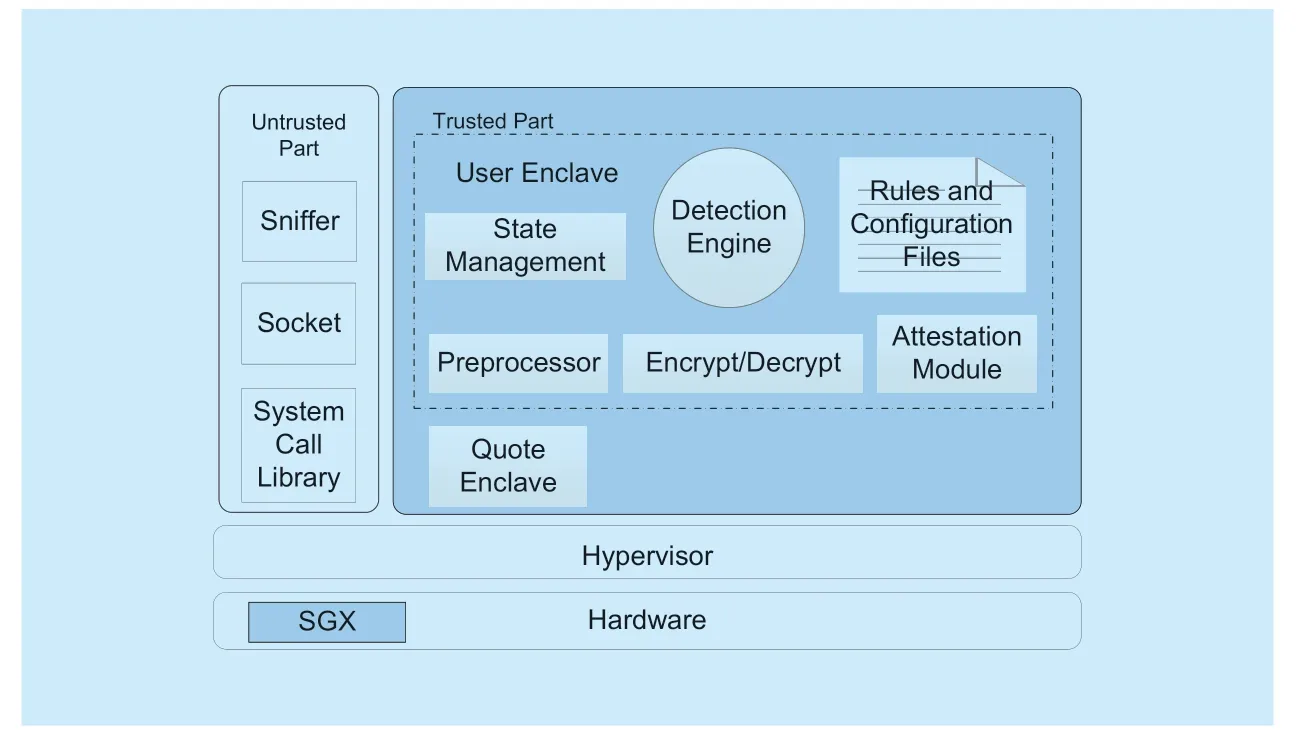
Fig.1.Architecture of TVIDS.
Compared with traditional intrusion detection devices,a virtual IDS faces security issues brought about by virtualization.First,as a physical device,a traditional IDS usually is configured through the dedicated serial ports,telnet,and TFTP methods locally.However,the virtual IDS function generally is a virtual instance which can be accessed by other virtual machines or the hypervisor located in the same platform.Secondly,changing the code in a physical IDS device is very difficult for adversaries,but a virtual network function runs in an open and shared virtual environment and its integrity is hard to be guaranteed.Finally,the network data privacy is easily comprised when users use the remote IDS service in a cloud.Therefore we propose to use SGX to provide security protection for a virtual IDS.
4.2 System overview
The architecture of TVIDS is shown in figure 1.The architecture is split into two parts: a trusted part and an untrusted part.The trusted part in an SGX enclave includes State Management,Detection Engine,Encrypt/Decrypt,Rules and Configuration Files,Preprocessor,Quote enclave,Attestation module.The untrusted part implements insensitive modules such as Sniffer,Socket,System Call Library.
Trusted Components:
1)State Management: TVIDS maintains important internal states in memory during the procession of work.For example,TVIDS will record connection statistics and session information which contain the source IP address,source port number,destination IP address,destination port number,connection states.If internal states are tampered with,the entire TVIDS will not work successfully.
2)Detection Engine: The detection engine is responsible for rules parsing and signature detection.It builds attack signatures by parsing IDS rules.When the traffic is sent to the detection engine,the detection engine will perform corresponding processing according to the rules.
3)Rules and Configuration Files: Rules define the abnormal patterns for traffic filtering.The configuration file defines how the IDS should respond to input traffic during processing.These responses are important parameters when IDS generates matching rules.
4)Preprocessor: The preprocessor performs some operations on the input traffic,such as assembling,decoding and so on.
5)Encrypt/Decrypt: This module mainly provides secure cryptographic operations for TVIDS.The main functions of this module include key generation,key storage,and secure encrypt/decrypt operations.
6)Attestation Module: This module is responsible for building secure communication between users and service providers,which will be described detailedly in Section 4.3.
7)Quote enclave: The quote enclave is used to make remote attestation for the virtual IDS which is protected with SGX.
Untrusted Components contain Sniffer,Socket and System Call Library.The sniffer is used to capture traffic from the network.The socket is responsible for sending or receiving data.The execution of the system call is prohibited in enclave hence the system call library is put outside of the enclave.
Before TVIDS is started,its integrity of key code and data will be validated so as to prevent it from being tamped with.
In the process of TVIDS initialization,TVIDS need to read and phase the user-defined configuration files.This configuration file defines how TVIDS responds to various packets during packet processing.What's more,this configuration file is an important parameter to generate TVIDS rules.Therefore,the security of the configuration file and rules are very important.To prevent the configuration file and rules from being tampered with,our system protects configuration file and rules in the enclave.
In the process of TVIDS boot,TVIDS generates detection engine.The kernel of TVIDS is detector engine and matching rules.After TVIDS completes the initialization,it works around detector and matching rules.Packet preprocessor performs some operations on the input traffic,such as assembling,decoding.Then the detection engine performs rules parsing and signature detection on the obtained traffic.To achieve the runtime security of TVIDS,we put packet preprocessor and detector engine into the enclave.
During the processing of TVIDS,it produces some records,such as the addresses of hosts.We call these records the internal states of TVIDS.The security of the internal state is very important because the correct of the state determines whether the entire TVIDS can work normally.In our system,enclave contains state management in order to ensure the normal work of the TVIDS.
In addition,except TVIDS inherent modules,we add two modules to the trusted part which are Encrypt/Decrypt module and Attestation module.The Encrypt/Decrypt module mainly provides secure cryptographic operations for the TVIDS.The Attestation module mainly provides the TVIDS attestation function in the process of remote connection.Both of these modules provide additional security functions for TVIDS.Last but not least,in the trusted part but outside the user enclave,there is a quote enclave which is provided by the SGX platform to provide credential during the remote attestation process.
4.2.1 Trusted boot
Trusted boot for the TVIDS is a basic security requirement,that means TVIDS should be able to achieve the integrity of key code and data.Once the integrity-checking has passed,the TVIDS can be successfully started.Our system offers the trusted boot with SGX's self-signed certificate and measurement mechanism.The enclave of TVIDS includes a self-signed certificate from the author,which is known as the enclave signature (SIGSTRUCT).The enclave signature contains several important information,such as enclave measurement value,enclave author's public key,enclave security version number and product ID of the enclave.The enclave signature information allows the Intel SGX to detect whether any part of the enclave file is tampered with.This process ensures that the code and data of the enclave are trusted and has been correctly loaded into the EPC.
The measurement value of the enclave is a hash value of the initial enclave internal information which includes code,data,memory layout,and page properties.Any change in the initial enclave internal information will result in a change in the measurement result.When the enclave is loaded into the EPC,the CPU stores the measurement value in a special register MRENCLAVE.After the load is completed,the CPU will compare the value in MRENCLAVE with the hash value stored in SIGSTRUCT.Enclave is only allowed to initialize by CPU when the two values match each other.
In order to sign the enclave,SGX provides the signature tool sgx_sign,which provides two signature method,a single-step method using the ISV's test private key and 2-step method using an external signing tool.The single-step method allows the signer to directly sign with the private key in the compilation environment.This method is mainly used in develop mode and debug mode.In the actual development process,we must use a 2-step signature.First,the signing tool generates the signature material for the enclave,copies the signature material to a secure hardware encryption module for signature,and finally copies back to the original platform.Second,sgx_sign tool signs the value with the enclave.TVIDS uses the 2-step signature method because the 2-step signature guarantees the security of the signing key and the signing process.
The TVIDS will be fully checked by CPU when booting.When the TVIDS internal information does not match the initial information,the TVIDS will not boot successfully.After the TVIDS boots successfully,TVIDS will ex-ecute network function while guaranteeing the security of the TVIDS sensitive information.

Table I.APIs for TVIDS state management.
4.2.2 State management and secure protection
IDS keeps on record the network communication state for tracking the traffic.We call these records the internal state of TVIDS.The security of the internal state is very important.If the internal state is tampered with,the entire TVIDS can't work normally.
TVIDS internal state is described by various data structures,such as link lists,hash tables,self-defined type and so on.These data structures related to state contains sensitive information and should be protected in the enclave.For example,we can use hash tables to store sensitive information related to the internal of TVIDS and put them in the enclave to protect.These tables can be used to mark specific sessions and hosts.We use the source IP address,destination IP address,source port,destination port to record the session and uses the IP address to record for a specific host.We extract the relevant data structures and code as an independent process running in the enclave.The code in the enclave and the rest of the code manage shared data with inter-process communication.
As shown in Table I,we design the relevant APIs in the enclave to protect and manage the state of TVIDS.The five functions of Init-State,StateCacheReset,SetState,CheckState,and CleanupState are used to initialize,reset,set,check,clear the data structures related to TVIDS state.We define these five APIs as five ECALLs.Our system enters the enclave via the Ecall function to perform state management functions.As shown in figure 2,we have designed a program called EState which manages and operates states.IDS_Main is the main part for IDS Initialization and processing which will call EState.State_API is designed as another independent process and uses the Ecall to call the function in the enclave to operate on the data structures related to the state.State_Module performs state management operations in the enclave and contains the data structures related to important state and their related operating code.When IDS_Main needs to operate on data structures related to state,sends its own request to State_API,then State_API completes the action in State_Module,and notifies IDS_Main of the result.
4.2.3 Trusted policy
For TVIDS,the policy defines how TVIDS works.If the policy is destroyed by attackers,TVIDS will work abnormally which causes great damage to users and businesses.Therefore,the policy should be protected with the SGX enclave so that cloud service providers or malicious tenants cannot access and tamper with them in TVIDS.
In TVIDS,policy processing runs across almost all procedures.In detail,one of the most important tasks in the initialization process is to build a four-level linked list structure.When TVIDS is started up,TVIDS parses the configuration file to generate a fast matching engine based on this four-level rule list.The purpose is to perform secondary classification on the rule linked list to improve the detection and matching efficiency of the rules.Matching rules are the core part of TVIDS during its life cycle.Matching rules are classified at different levels according to different attributes,and corresponding function on the linked list as a plugin.This kind of structure works efficiently and such an important data structure should be protected carefully.This data structure contains important security information.Therefore,we put this linked list structure in the enclave for matching rules to protection policy.
In addition,the configuration file is an important file for TVIDS.If TVIDS launched in IDS mode,it will parse the command line,read and parse configuration file during its initialization.Usually,this file is stored in hard disk in plain text.We use the SGX seal/unseal function to protect this configuration file.When starting in IDS mode,TVIDS firstly looks for the encrypted configuration file.If the encrypted configuration file does not exist,TVIDS does not start and returns an error.If the encrypted configuration file exists,TVIDS reads the encrypted file into the enclave and decrypts the encrypted configuration file.
4.3 Secure remote attestation
Virtual IDS can provide IDS outsourcing service.For example,users can send their traffic to the remote cloud provider to have a deep packet inspection.The user's network traffic contains a lot of sensitive information about its network.If the information is leaked,it will cause the user's privacy violation.Furthermore,users using the remote service provided by the service provider,should not only consider the risks in the data transmission process but also consider the risks from the service provider.The users need to be able to confirm the service provider's trustworthy.This will prevent the platform or software from leaking the user's data and ensure that the service the user is connected to is indeed what the user wants [38].
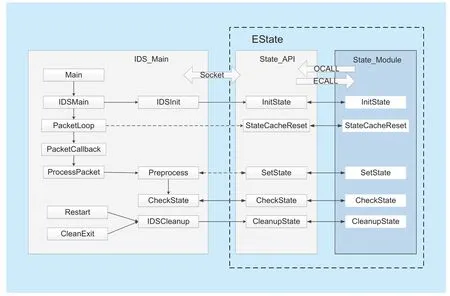
Fig.2.Architecture of trusted state.
SGX provides two attestation mechanisms,local attestation,and remote attestation.The remote attestation mechanism provided by SGX itself enables the SGX program to provide the remote entity with a data structure containing its own information,quote.Quote contains the code hash in the SGX program container,the container signer's public key hash,the program's security version number and the EPID (Enhanced Privacy ID)signature of the above.After the user uploads quote to IAS (Intel Attestation Server)for attestation to confirm that it is a secure SGX platform.However,it is not practical for the user to attest the SGX directly to the remote server,because the hash of the remote service cannot judge the code security and the service type of the remote server.Second,the process of interaction with IAS requires registration at the platform and remote API calls which is complicated.In order to meet the security needs of users in the process of remote connection,we propose a new attestation approach based on the SGX remote attestation.The process is shown in figure 3:
1)The service provider creates a service that is completely protected by enclave and generates a key pair in the enclave.The private key is stored in the enclave.The corresponding public key is used to apply for a TLS (Transport Layer Security)certificate,and submit the source code and the service type.
2)After receiving the request,the controller launches a remote certification of the SGX.The controller obtains the data structure quote sent by the service provider and sends it to the IAS for verification.After being certified by IAS,it can be proved that the platform is a security platform with SGX functionality.After confirming the security of the platform,we also need to confirm the security of the software.Therefore,we need to analyze the code to verify whether it is consistent with its statement and whether there are security holes.Before code analyzing,the controller calculates the hash value of the container code to see if it is equal to the value in the remote attestation result.
3)After the code analysis passes,the controller submits the certificate log and applies for a certificate from the CA (Certification Authority)using the service provider's public key.
4)The CA sends the certificate to the controller and records it in the certificate log.
5)The controller delivers the certificate to the service provider.
6)The user obtains the TLS certificate and queries the certificate log.If the certificate public key has a corresponding certification record,and the service statement in the certification record meets the expectations,the service can be considered to be secure and communicate with it.
The service provider's private key is always stored in enclave during its entire operation and all operations are executed within enclave to protect the private key's security.
Authentication log: This module is mainly used to record remote authentication and open queries to users.Because the controller has completed the SGX's remote authentication operation process,the controller has obtained the authentication results in addition to the IP address,MAC address,and other information of the service provisioning platform.The authentication result contains the information provided by quote,such as the container signer hash,container code hash,etc.,which can be used as the program provider identification,denoted as A; Besides,the public key used by the service provider to apply for the TLS certificate is known,and it is denoted as B.The service statement is denoted as S,and the time of the authentication request is T.Assuming that a record in the log is Arecord,then there is Arecord=(A,B,S,T),which means the service provider A passed the certificate at time T,and A declares the service S,and The public key of its TLS certificate is B.When the user obtains the certificate of the service provider,the public key in the certificate can be used to search the certificate log to determine whether it is a safe and reliable service and provides the expected service.
Certificate log: This module is used to record the issued certificate.Supposing a certain issued certificate is C,its issuance time is T,the record is Crecord,and Crecord=(C,T).And when the certificate expires,the record will be deleted and its corresponding entry in the certificate log will also be deleted.
Monitors: Monitors are primarily used to monitor the logging of authentication and certificates,including anomaly detection and consistency detection.When a suspicious situation occurs in the recording,a corresponding processing operation is performed.For example,in our approach,the records in the authentication log and the records in the certificate log should be in one-to-one correspondence.If the monitor finds that there is no corresponding certificate record for the authentication record or certificate record,the situation is abnormal and should respond.The logs are added one by one,and they should be continuous in terms of time.If the time is not incremented sequentially,it is also problematic and needs to be handled.
In our approach,if there is an internal attack on the service provider due to internal management or other issues,for example,a malicious internal worker wants to use a malicious program to replace a normal program.Because the connection is based on TLS,and the key is stored inside the enclave,if the internal attacker wants to provide TLS service,it must apply for a TLS certificate again,then it must go through code analysis,SGX remote authentication,and leave the corresponding record in the authentication log and certificate log.So it is difficult to analyze code successfully and the monitor can find some anomalies by analyzing the logs.For example,a platform suddenly changes the CA used to apply for a certificate.Similarly,by setting some security policies,some situations may be marked as anomalies and processed them when these conditions are triggered.In this approach,the user can use the SGX to protect the security of the service by querying the authentication log to find out whether the service it obtains is in the expectations.Finally,it can resist attack from inside the service provider.
4.4 SGX performance optimization
Enclave transition performed by Ecall or Ocall introduces high overhead.This is because CPU will perform operations such as update cache,copy parameters,check page access permission,and encrypt/decrypt memory page during each enclave transition.When the EPC capacity is not enough,pages in the EPC need to be swapped out which brings a lot of extra overhead.Each enclave transition imposes a cost of 8,400 CPU cycles 6 more costly than a typical system call,and the result will become 20 times with 48 concurrent threads compared to one [39].In addition,the time overhead of an empty Ecall function or Ocall function is about 3us.Enclave transition with the only transition between the trusted and untrusted areas will take such a large amount of overhead.In order to reduce the overhead introduced by SGX,there are two common methods currently.
1)Reduce transition between trusted and untrusted parts.For example,by minimizing the number of system calls in an enclave can reduce enclave transition.For these functions that cannot be implemented in the enclave,trying to rewrite these functions based on the library provided by SGX is a solution.For codes that cannot be modified,Ocall is used to complete this task.In addition,it is also possible to minimize meaningless Ecall or Ocall access.For example,the member of a data structure which protected in enclave does not need very high-security protection,but it needs to be accessed frequently outside the enclave.This will cause frequent Ecall operations and great additional expenses.Therefore,for this type of data,we can put it outside the enclave,or store its backup outside the enclave and synchronize it regularly.
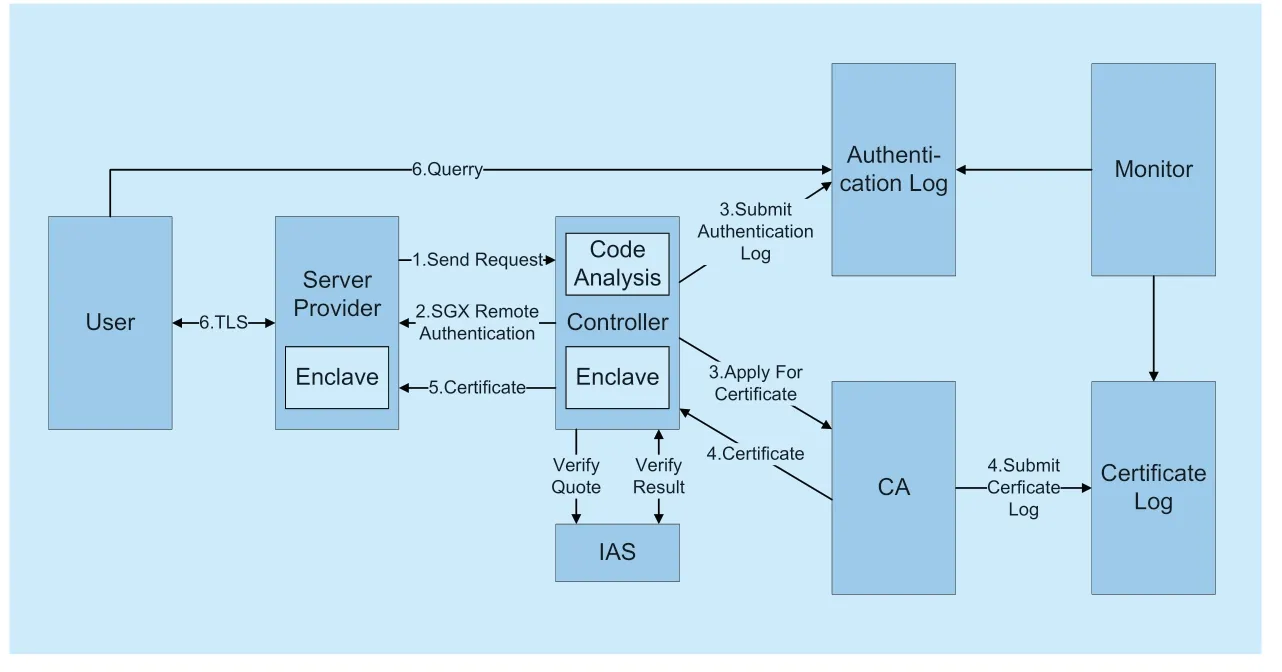
Fig.3.Remote attestation approach based on SGX.
2)Reduce waiting time during execution of Ecall and Ocall.Both Ecall and Ocall calls are synchronous calls.The thread that initiated that operation will wait for the task to finish before continuing.In order to improve the overall efficiency of the program,a method which is similar to the asynchronous call is proposed.When the untrusted part performs Ecall operations,the thread writes requests and parameters directly to the queue.The Ecall operation is performed sequentially by a dedicated function module,and then the results are processed.In this way,when the untrusted part needs to perform the Ecall operation,it is possible to continue without waiting for the result returned by the untrusted part.This method allows the trusted and untrusted parts to execute asynchronously which reduces the caller's waiting time when the trusted and untrusted parts call each other.As a whole,this synchronous solution improves the execution efficiency of the program.
Both of these methods do not fundamentally solve the performance overhead caused by Ecall/Ocall,just try to reduce the impact caused by Ecall/Ocall.In order to solve the overhead problem from the SGX mechanism,we propose a new method.Take the Ecall operation as an example.When a thread needs to perform Ecall operation,it does not need to enter the enclave.The thread only needs to place the request and parameters in memory (slot).We design a special internal scheduling module in the enclave that reads and analyzes the content of the slot.After then,the internal scheduling module calls the corresponding function according to the content of the slot and writes the processing results to the slot.The thread reads the value in the slot and returns.The process is shown in Figure 4:
1)Write requests and parameters into the slot.
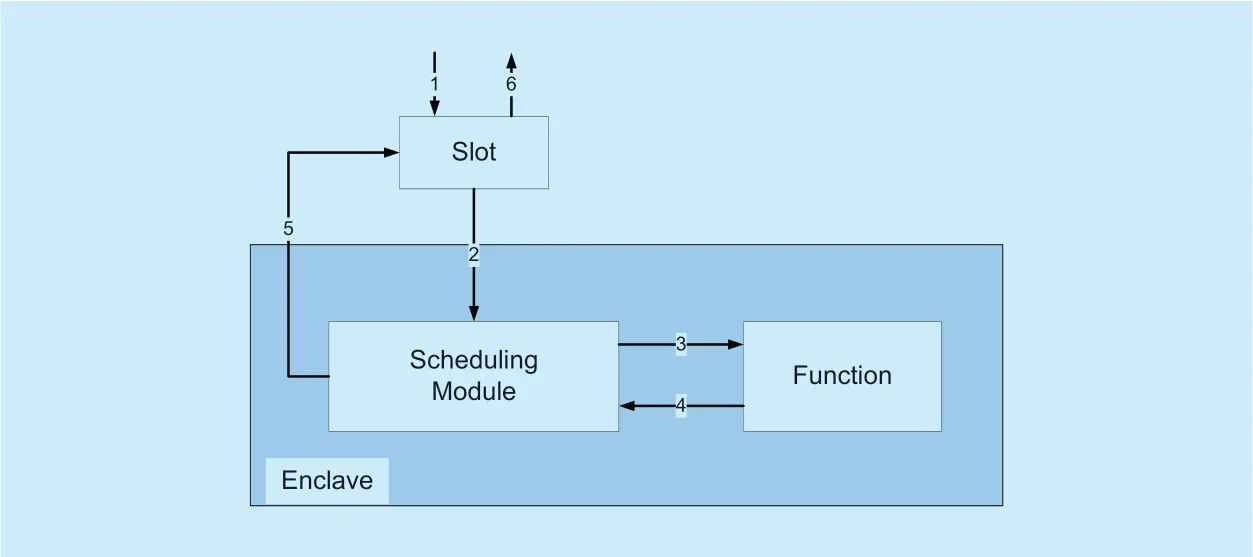
Fig.4.Optimized ecall.
2)Enclave internal scheduling module reads the content of the slot as long as it finds content in the slot.
3)Scheduling module calls the corresponding function according to the request and parameters.
4)Return results to the scheduling module.
5)Scheduling module writes the result back to the slot.
6)Thread gets the value in the slot and returns.
V.IMPLEMENT
We implemented our design on the basis of the Snort source code.We selected part of the Snort's state and matching rules for protection to verify the feasibility of our system,implemented the remote attestation approach between local and cloud services,and conducted the performance test.The operating system we use is Ubuntu 16.0464bit,the memory of 8GB and Intel Skylake processor of i77700hq.The version of Snort is 2.9.8.3 and the version SGX is 2.1.3.All of our experimental data were tested in actual SGX hardware mode.
The implement of secure boot is based on SGX self-signed certificate structure and self-safety check when enclave loading.The TVIDS with SGX will be fully checked integrity by the CPU each time when it is started.When the TVIDS internal code or data are changed or don't match the initial state,the TVIDS will not start successfully.
In our implementation,the state of our protection is the two hash tables ssn_tag_cache_ptr and host_tag_cach_ptr maintained by Snort while running.These tables are used to mark specific sessions and hosts.Snort uses the source IP address,destination IP address,source port,destination port to record the session and uses the IP address to record for a specific host.We extract the relevant data structures and code in the enclave to verify the feasibility of our system.
In order to verify the feasibility of Snort matching rules with SGX,we divide the Snort rules into two parts.We put two layers of Snort matching rules into the enclave for protection and adjust the data structure according to the actual situation.A new data structure,MiniSC,is created in the enclave.The structure contains RuleListNode point type rule_list,which is the first level mechanism in the Snort rule.In addition to RuleListNode type,it also contains the second-level node ListHead type,but only contains the basic data structure.In SnortConfig,we delete RuleListNode point type rule_list which is the first layer in the original linked list structure,because this layer has been reconstructed in the enclave.In addition,we delete the basic data type in the second layer,only contain the output plug-in,and add the attribute name,which is convenient to correspond with the second layer of the linked list in MinSC inside the enclave.
VI.EVALUATION
6.1 Evaluation of function
We conduct the function test of the TVIDS.We use Scapy [40] and TFN [41] to generate normal traffics and attack traffics.TFN is a tool to conduct various DDoS attacks such as ICMP flood,SYN flood,UDP flood,and Smurf attack.It can be used to control any number of remote machines to generate random anonymous denial of service attacks and remote access.Scapy is a powerful interactive packet handler based on python.It can forge or decode mostly protocols packets,send them online,capture them,match requests and replies,etc.
Attack traffics generated by TFN contains UDP flood traffic,SYN flood traffic,ICMP flood traffic and the other types of attack traffic.In our evaluation,we send attack traffic and normal traffic to TVIDS in different proportions.From example,the attack rate 20% means that the attack traffic to normal traffic is 1 to 4.Then the TVIDS processes the traffic according to the rules.The result is shown in Fig 5.The result shows that TVIDS is as effective as Snort.TVIDS can detect attack traffic successfully.In addition,TVIDS can take active defense measures according to the rule sets.
6.2 Protection of snort's state
We tested the three APIs that were commonly used to measure performance by invoking the time contrast of the API using SGX and without using SGX.The results are shown in Table II:
From the experimental results,we can see that SGX will bring additional time overhead for the program,which is caused by the additional security mechanism provided by SGX.Our experimental results show that some APIs with relatively short operating times are particularly expensive.We think it is a proportional problem because the operation itself is short and the additional overhead introduced by SGX is fixed.For example,the program needs to be switched between trusted and untrusted parts,resulting in a higher percentage of the overhead time.The extra costs of the two APIs CleanupState and InitState that operate on a long time are lower from the percentage,and it can prove this point to some extent.Such a result doesn't mean that SGX will bring a high delay for the entire process because only important data and its associated code need be put in the enclave for protection.The reasons are as follows:
1)All the enclaves on the platform will be loaded into the EPC to run,and the current EPC supports the maximum capacity of 128M;
2)Enclave is a trusted computing base.Large capacity will increase its attack surface,even if without considering other security threats.Too much code in enclave also increases the introduction of bug,and because of SGX's security feature,the bug of enclave often causes greater problems.SGX gives us security guarantees and additional performanceoverhead simultaneously,but its performance loss is acceptable compared to the excellent security it offers.Good code structure can reduce the performance loss caused by SGX in the actual programming process.

Table II.Time cost of state API.
In section 4.4,we propose a new optimization approach.We use this approach to optimize several APIs in Snort state protection.
The results are shown in Table III.Through comparative analysis of the experimental results,it can be found that the implementation efficiency has been improved after the optimization.
6.3 Protection of snort's policy
Snort will generate a four-level list named rule lists based on the configuration during the initialization,and then parse the rule lists to produce a quick match table which is also a four-level list structure.Snort will quickly match the table back to the rule lists after the analysis,which will constitute the Snort matching rules.The matching rule of Snort is a multi-layer structure of the list structure.We protect the two layers to verify the feasibility of the protection matching rules.The method is similar to state protection.Since Snort is a looped program and the matching rule is the core data structure.It is difficult for us to evaluate its performance in time,so we selected CPU and memory usage for evaluation.We set snort to alert all TCP packets flowing into any local port and output the packer complete information in the terminal.The data rate in the network is about 5Mbit/s.
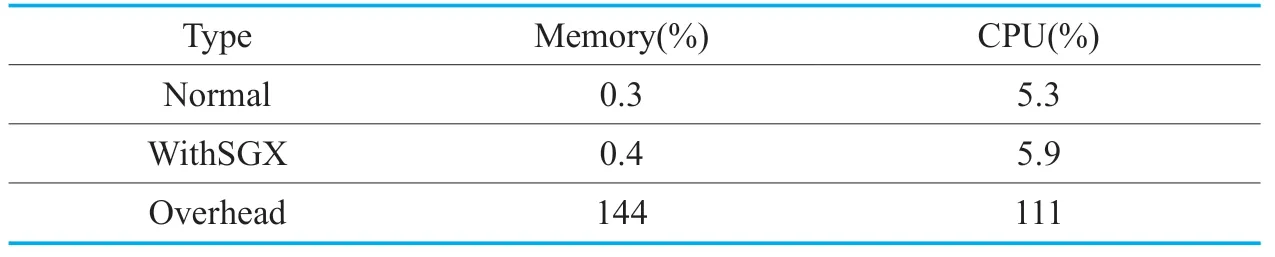
Table IV.Resource overhead of trusted policy.
As is shown in Table IV,the final experimental result shows that the CPU occupancy rate of the unmodified snort is about 5.3 percent in our experimental environment.The sum of the CPU occupancy rates of the trusted and untrusted parts of snort is about 5.9 percent after our changes.The memory usage is also increasing from 0.3% to 0.4%.However,the increase rate is within the acceptable range.
6.4 Evaluation of remote attestation
Remote attestation is used for session authentication and secure session channels.We verify the performance of remote attestation in time cost and CPU overhead two aspects.The object we tested was the party that was certified in the remote attestation.As shown in figure 6 and figure 7.From the beginning of the certification to the completion of certification,the time cost is 60ms to 69ms,and the CPU occupancy rate is 17% to 26% during the 20 experiments.The results show that the overhead of remote attestation is within the acceptable range.
6.5 Evaluation of throughput
In part,we evaluate the packet processing capability of TVIDS.We measure the throughput between two computers in two cases.In the second case,we put a part of state processing function and data into the enclave.
As shown in figure 8,the result shows that SGX slows down the packet processing slightly because TVIDS consumes more memory and CPU.In addition,the throughput may get worse if we put more code into the enclave.
6.6 Security analysis
TVIDS uses Intel SGX to protect the code,state,and policy of VIDS.Packets are encrypted so that attackers from the cloud can only intercept encrypted traffic.Attackers cannot get the contents of the packets and can only observe the size and time of packets.TVIDS also protects the state and policy of VIDS in such a way.The system is divided into trusted parts and untrusted parts.The trusted part stores sensitive data,state and policy in the enclave.The operating system,drivers,BIOS and VMM cannot obtain the code and data in the enclave.Using SGX security mechanisms,TVIDS protects against security threats,such as data leakage,code tamper,and compromise policies,targeting VIDS in an untrusted cloud environment,to realize the security of VIDS internal states and policies.The untrusted part provides the trusted part with the interface of the system call and implements the packets transfer between the trusted and untrusted parts.
VII.DISCUSSION
7.1 Limitations
TVIDS has some limitations that are mainly caused by using SGX.
First,the available memory of enclaves provided by SGX is limited.Hence,we must control the size of sensitive code and data.In our implementation,we protect the two hash tables and matching rules in the enclave.However,when the number and size of the programs are increased,more pages are required to be swapped in and out.In order to ensure security,the system should protect the integrity and confidentiality of the pages,which may result in high system overhead.

Fig.5.Evaluation of function.
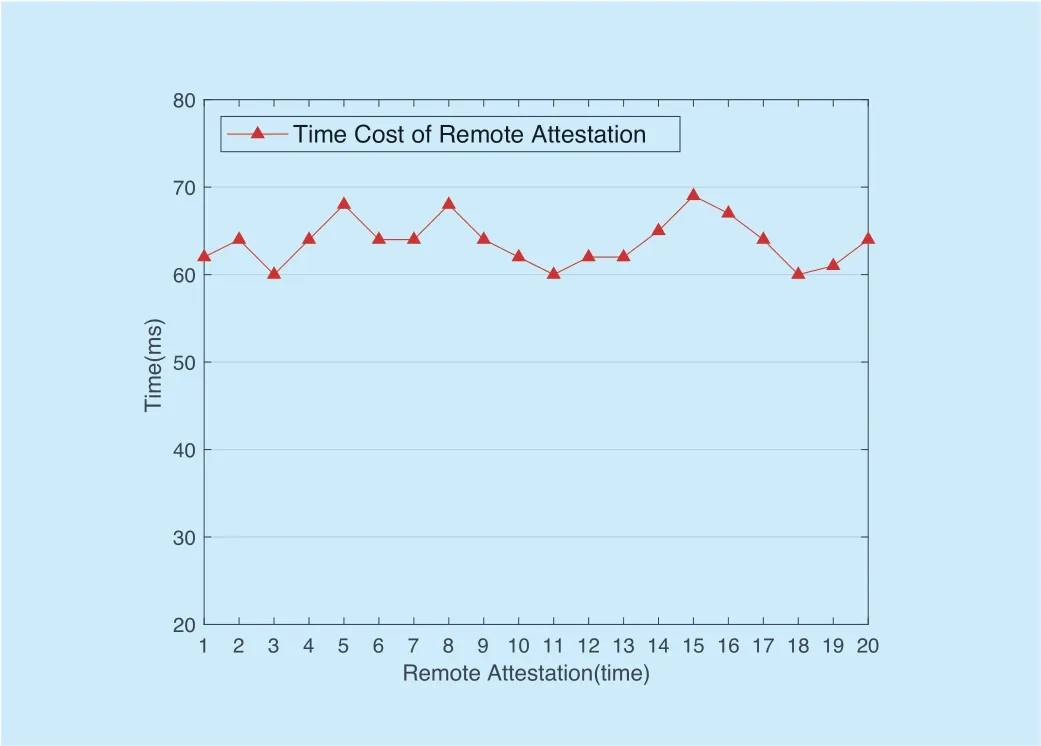
Fig.6.Time cost of remote attestation.

Fig.7.CPU usage of remote attestation.
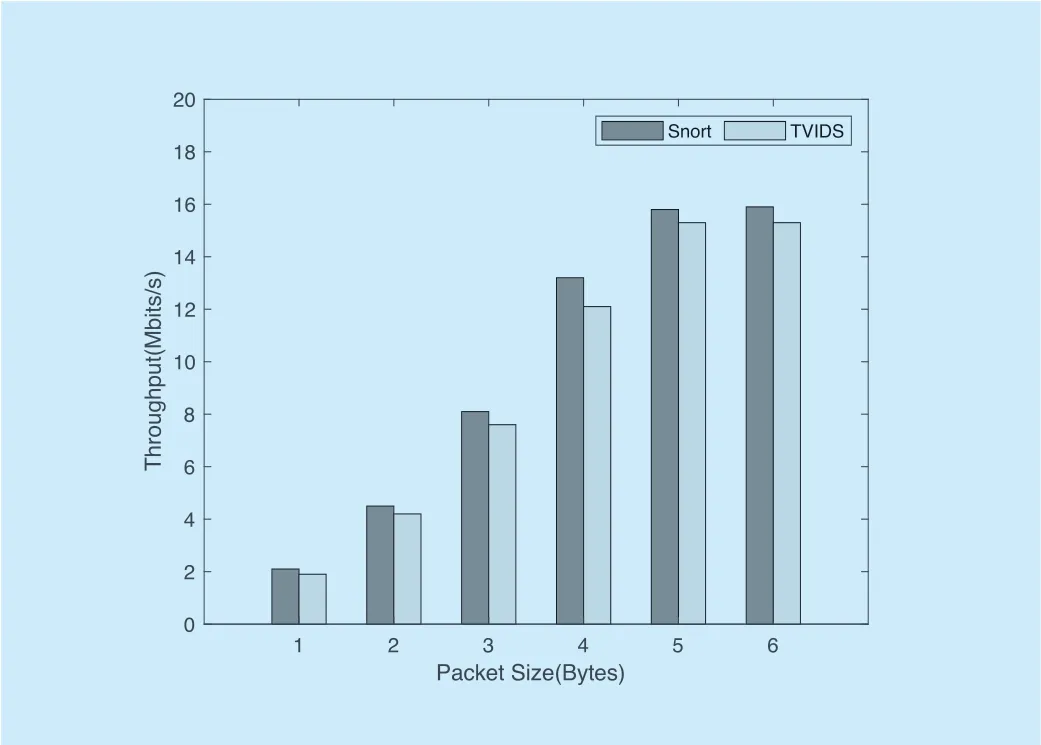
Fig.8.Throughput of TVIDS.
Secondly,the execution of system calls is prohibited inside the enclave.To execute a system call,the executing thread has to exit the enclave.Such enclave transitions are expensive.Thought we have proposed SGX optimization method which decreased the overhead to some extent,it still brings non-neglectful effect.
Finally,TVIDS cannot prevent side-channel attacks on SGX.There are various types of side-channel attacks,such as cachebased side-channel attack [42],TLB-based side-channel attack [43],attacks based on the CPU internal structure [44].Though a number of potential solutions [45-47] have been proposed in recent work,their impact on application performance is often non-trivial.Developing targeted solutions is a potential future work.
7.2 Future work
TVIDS run the critical components of off-theshelf security software,such as Snort,inside SGX enclave.However,detaching components from large and monolithic security software without breaking their functionality is very challenging.In the future,we plan to build a lightweight and trusted IDS architecture based on SGX.By decomposing modules of IDS into related small elements,it's easy to build a new security function and put its key modules and elements into an enclave so as to achieve a desirable tradeoff between security and performance.
In addition,we plan to make TVIDS support hot swapping in order to dynamically modify configurations in the future.Hot swapping is a method that can realize new configurations without stopping the current system.One solution for supporting hot swapping is launching a new enclave and put both new modules and old modules into the enclave.Another solution is to put each module in a separate enclave.However,some issues should be considered for the above solutions.For example,the frequency of enclave transition can introduce additional performance overhead.
VIII.CONCLUSION
Network Function Virtualization has become the mainstream of the future network.However,the security issue has emerged as one of the obstacles in its business applications,especially for virtual security function,such as virtual IDS.In this paper,we use SGX to build a trusted execution environment for virtual intrusion detection systems.We put the key code and security policy of IDS to the SGX enclave so as to run them in a trusted isolation hardware sandbox.Furthermore,we provide a remote attestation approach to guarantee the security of virtual IDS outsourcing.We have implemented our trusted virtual intrusion detection system in a real SGX platform and evaluated its performance overhead in processing the packets and attestation.The results show that our method can protect the security of the virtual IDS and brings acceptable performance overhead.
ACKNOWLEDGMENT
This work is sponsored by the National Natural Science Foundation of China granted No.61872430,61402342,61772384 and the National Basic Research Program of China 973 Program granted No.2014CB340601,and Foundation of Science and Technology on Information Assurance Laboratory (No.KJ-17-103).
- China Communications的其它文章
- A Satellite Communication System Transmission Scheme Based on Probabilistic Shaping
- Application of Neural Network in Fault Location of Optical Transport Network
- Distributed Optimal Control for Traffic Networks with Fog Computing
- A Real Plug-and-Play Fog: Implementation of Service Placement in Wireless Multimedia Networks
- New Identity Based Proxy Re-Encryption Scheme from Lattices
- A Sensing Layer Network Resource Allocation Model Based on Trusted Groups

