A New Double Layer Multi-Secret Sharing Scheme
Elavarasi Gunasekaran,Vanitha Muthuraman
Department of Computer Applications,Alagappa University,Karaikudi,India
Abstract: Cryptography is deemed to be the optimum strategy to secure the data privacy in which the data is encoded ahead of time before sharing it.Visual Secret Sharing (VSS) is an encryption method in which the secret message is split into at least two trivial images called‘shares’to cover it.However,such message are always targeted by hackers or dishonest members who attempt to decrypt the message.This can be avoided by not uncovering the secret message without the universal share when it is presented and is typically taken care of,by the trusted party.Hence,in this paper,an optimal and secure double-layered secret image sharing scheme is proposed.The proposed share creation process contains two layers such as threshold-based secret sharing in the first layer and universal share based secret sharing in the second layer.In first layer,Genetic Algorithm(GA)is applied to find the optimal threshold value based on the randomness of the created shares.Then,in the second layer,a novel design of universal share-based secret share creation method is proposed.Finally,Opposition Whale Optimization Algorithm(OWOA)-based optimal key was generated for rectange block cipher to secure each share.This helped in producing high quality reconstruction images.The researcher achieved average experimental outcomes in terms of PSNR and MSE values equal to 55.154225 and 0.79365625 respectively.The average PSNRwas less(49.134475)and average MSE was high(1)in case of existing methods.
Keywords: genetic algorithm;oppositional whale optimization algorithm;rectangle block cipher;secret sharing scheme;shares;universal share
I.INTRODUCTION
Rapid development of internet technology eased a lot of works for clients,yet it opened a Pandora’s Box in terms of uncovering individual’s confidentiality information.The exposure of individual’s information causes much inconvenience to the clients due to which there is a number of individuals started looking for securing their private information to overcome the security issues [1].Cryptography and secret sharing are the most well-known methodologies to safeguard the privacy of private information.Cryptography is a method in which the information is changed from a clear state to evident nonsense so that the authenticated units that have permission to encryption key can decrypt the cycle and gain access to the information in its original readable form[2].The main benefits of such encryption components are as follows:(1)Clients have the complete access control for the information shared rather than the service provider and(2)the security properties strongly rely upon cryptography methods,instead of conventional access control[3].Secret sharing is a process in which the shares are only partitioned so that even if a share gets exposed,it has no value or benefit.The superimposition of shares brings back the original secret image[4].
Secret sharing system was presented by Shamir and Blakley to autonomously secure a secret among a collection of members.Naor and Shamir conceived the concept of secret sharing to shield a binary secret image.In their study,Visual Cryptography(VC)concept was proposed [5,6].In Shamir’s polynomial-based SIS,for (k,n) threshold,the secret image is partitioned into stable coefficient for an arbitrary(k −1)-degree polynomial to acquire n shadows.These shadows are then additionally shared among n members[7,8].
These techniques accompany some issues that needs to be resolved.The created shadows in the above plans are irrelevant (containing noise) and straightforwardly excites the hackers when communicated in public channel.Thus it enables a security danger consequently.There is no assurance in VCS that every member is straightforward and untruthful members falsify shadows to spoof.When these two issues occur,there occurs an issue in the rebuilding of secret image[9].For certain applications,the secret image should be restored with high quality image.For instance,consider a war map (i.e.,military image) which should be shared among different solders to accomplish joint tasks[10].
Keeping in mind the above issues,following is the list of contributions made in the study which developed a robust and secured double layered secret image sharing scheme with block ciphers.The main contributions of the article are as follows.
• Security of the proposed secret sharing method is enhanced through dual layer secret sharing followed by the encryption of shares
• The first layer of share creation is simply made through threshold-based method.Here,the threshold is intelligently selected(based on maximum entropy)so that it not only depicts the secret data but also not destroy the quality of image during retrieval
• Universal share-based VSS is employed in this study to secure from dishonest participants and provide easier management of shares
• Finally,the shares are encrypted using block ciphers,where the key is selected in an optimal manner so that the secret data possess better quality after decryption.In this way,confidential data can be preserved securely with better quality.
The paper is organized as given herewith.Section I provides a detailed introduction about secret sharing and cryptography to maintain data confidentiality.Section II contains a wide range of literature works.In Section III,a brief representation of the proposed approach is given.Also,the experimental result and analysis are discussed in Section IV.Finally,conclusion is given in Section V.
II.RELATED WORKS
Saeideh Kabirirad and Ziba Eslami[11]demonstrated that a few methods do not meet the security requirements i.e.,with information on(n −1)or less shares,the significant data about the secret image can be retrieved only after restoration the calculations.The researchers further proposed an improvement which effectively improved the reported security faults.The authors demonstrated that the improved plan produced pseudorandom shares and outperformed the existing secure Boolean-based plans in computational expense.
Xiaotian Wu et al.[12] accepted secret sharing as an optimum method in reversible information hiding using the encoded images.The authors presented an essential model in which secret sharing was utilized for reversible information hiding in encoded images.At that point,the study proposed an image encryption algorithm in which Shamir’s secret sharing methodology was utilized.
Li et al.[13],proposed an encryption method using another additive homomorphism dependent on Elliptic Curve ElGamal (EC-ElGamal) to share the secret images over unstable channel.The method empowered short keys and preferable efficiency in the plans that are dependent on RSA or ElGamal.It had a low calculation overhead in image decoding in contrast to the techniques that utilize other additive homomorphic properties in EC-ElGamal.Elliptic curve boundaries were chosen to oppose the Pohlig–Hellman,Pollard’srho,and Isomorphism attacks.
Yogesh K.Meghrajani et al.[14]introduced a computationally proficient arithmetic multi-secret image sharing plan in which all the universal shares were utilized.Binary arithmetic plan used individual value choosing function at the time of encoding and decoding the secret images.The individual value choosing function upgrades the arbitrariness of shares and satisfies the threshold feature.Hence,the strategy achieved computational proficiency while fulfilling the threshold security models.
Xuehu Yan et al.[15]proposed a SIS plot for(k,n)threshold with different shadow validation capacities based on SIS itself,instead of data hiding.This was accomplished by applying Visual Secret Sharing(VSS) to polynomial-based SIS in which a screening activity was utilized.The plan had low generation and reconstruction complexity and no pixel extension with different shadow validation capacities.Also,it attained lossless restoration without secondary encryption.
Xiangru Liu et al.[16] proposed an optical multilevel authentication technique based on Singular Value Decomposition Ghost Imaging (SVDGI) method and(t,n) threshold secret sharing plan.SVDGI is a productive restoration technique in Ghost Imaging (GI)that changes the measurement matrix with the assistance of singular value decomposition.This action empowers the restoration of N-pixel image using a significantly lesser value than N measurement with less time and high quality.
Yanxiao Liu et al.[17] considered a cheating dilemma in bivariate polynomial-based secret sharing plan and suggested two cheating recognition algorithms.The first algorithm could distinguish the cheaters using m users who participate in the restoration of secret;the subsequent algorithms could accomplish high capacity cheater recognition with a coordinated effort from the rest of n −m users who are not associated in secret restoration.
Marek R.Ogiela and Urszula Ogiela [18] examined new opportunities to make threshold methods for secret sharing based on the utilization of numerical linguistic formalisms.Such strategies depend on well-known data parting threshold schemes that are stretched out by including an additional stage,during when the bit blocks of shared data are coded with the help of appropriately characterized context-free grammar.
Xuehu Yan et al.[19] considered Partial Secret Im-age Sharing (PSIS) issue and suggested PSIS design for (k,n) threshold based on image in painting and Linear Congruence (LC)-based SIS.The full secret image and the secret target part with its different parts would get restored by gathering any k or more shadow images.These could be additionally rebuilt without any loss by including all the implanted meaningful shadow images.
Elavarasi et al.[20] proposed a new real time biometric model based on Deep Learning (DL) architecture called Hierarchical Convolutional Neural Network (HCNN).At the beginning,the boundaries are attained from the given image for providing ROI to a subsequent level.Next,the resultant image comprises of upper region as well as lower eyelids along with skin,eyelashes,and sclera.At the next level,inside the ROI,H-CNN is employed to provide the real iris boundary with the help of learned features.
Xiaopeng Deng et al.[21] proposed a threshold multi-secret sharing system based on phase-shifting interferometry.K secret images that are to be shared,were initially encoded by Fourier transformation.Then,the encoded images were shared into many shadow images depending on the recording guideline of phase-shifting interferometry.
III.THE PROPOSED OPTIMAL DOUBLE LAYER SECRET SHARING SCHEME
The most ideal approach to ensure the secrecy of the data is to encode it with the help of cryptographic strategy,ahead of time i.e.,before sharing.Visual Secret Sharing (VSS) is an encryption method which is used to encrypt a message into at least two trivial images,called ‘shares’.Shares are stacked together to decode the secret message with the help of human visual framework.Prevention of cheating and security are modern characteristics of VSS methods.It also functions for certain members(frauds)to introduce false shares to restore the fake secret images in order to deceive the remaining members(victims).Further,any unknown person may reconstruct the fake secret images by delivering false share to deceive the actual members.VSS method is deemed to be a highly protective method in which the possibility of hacking is very less.Additionally,share management turns out to be a step-by-step and troublesome process with expanding number of secret images.Thus,in order to tackle the share management issues and to prevent the hackers from decrypting the message,the idea of universal sharing is presented.Under such conditions,the secret must not be uncovered without the universal share.This is probably achieved by the trusted party (coordinator).Hence,in this research work,an optimal and secure doublelayered secret image sharing scheme is proposed using universal share and rectangle block cipher.Here,the secret image is securely shared in two layers.The first layer involves threshold-based sharing whereas a unique threshold value is picked optimally for every distinct secret image.In the next layer,universal share-based secret sharing is performed after dividing the first layer shared images into quadrants.Prior to transmission,the created shares are once again encrypted with rectangle block cipher so as to enhance the security.Again,the encryption step is optimized with an optimal key selection strategy using Opposition Whale Optimization Algorithm(OWOA).This algorithm helps in the selection of key since the PSNR of decrypt share is almost similar.At the receiver end,the decrypt key is verified to decrypt the encrypted shares.This is followed by the reconstruction of shares with universal share for recovery at first layer.Then,in second layer recovery,simple XOR operation is performed to recover the original secret image.The schematic diagram of the proposed double layer secret image sharing scheme is given in Figure 1.
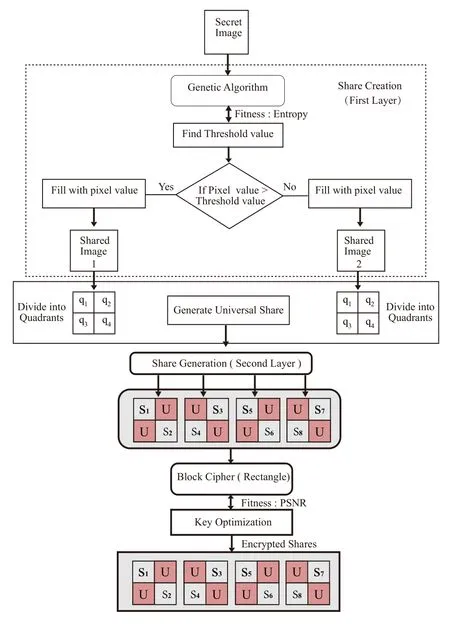
Figure 1. The proposed double layer secret image sharing scheme.
3.1 Layer 1: Genetic Algorithm Based Threshold Creation
The proposed double layered secret image sharing scheme is composed of the execution of two different secret sharing schemes in two layers.The first layer is processed with adaptive threshold-based secret sharing scheme.In this layer,the threshold value is selected adaptively based on the randomness of image shares to be produced after the first layer.Here,Genetic Algorithm(GA)[22]plays a vital role in generating the optimal threshold value.
3.1.1 Threshold Selection by Genetic Algorithm
Genetic Algorithm(GAs)is a heuristic search and optimization algorithm which is stimulated by natural evolution process [23].This has been effectively applied in a wide range of real-world issues of huge complications.The proposed threshold-based share creation method applies GA to adaptively generate the optimal threshold value.At this time,a set of thresholds is randomly generated among which the optimal one is selected and stored during every iteration.All random threshold values are applied whereas the entropy value is calculated between the shared and secret images.The optimal threshold value is decided based on the maximum entropy value found from the shared images.Once the threshold value Th is found,share creation is executed for each pixel location (p,q) as given herewith.
where,X1(p,q) and X2(p,q) are the locations of the pixel shares and V represents the current pixel value of secret image.Likewise,the two images X1and X2are produced by performing the above thresholding procedure for all the pixel values.The obtained shares,from the first layer share creation method,are again shared with universal share-based share creation method.
3.2 Layer 2: Universal Share Creation Procedure
Universal share based VSS method is usually carried out to escape from dishonest participants and to ease the share management process that occurs in case when more secret images are to be shared.The proposed universal share-based share creation method is executed at the second layer of secret sharing,since it is applied to the image shares obtained from previous layer.At this stage,the image shares are further divided into four quadrants(X1→q1,q2,q3,q4& X2→q5,q6,q7,q8) and distinct shares (S1,S2,S3,S4,S5,S6,S7,S8) are created for every quadrant.
3.2.1 Steps in Universal Share Based Share Creation Approach
Let the input images(i.e.quadrants of shared images obtained from first layer)be,Q={q1,q2,...,q8}and the corresponding outputs denote the shared images.S={S1,S2,...,S8} denotes the steps involved in universal share-based share creation method which is detailed herewith.
Step 1: Generate Universal Share
Universal share U is generated by the encrypted combination of quadrants of two images X1and X2by XOR operation.Here,the encrypted combination is given below.
where,C denotes the block cipher and symbol ⊕represents the XOR operation.
Step 2: Share Construction
Using the universal share,the shares S={S1,S2,...,S8}are created using the formulas given below.
Therefore,the general formula for share creation with universal share is represented herewith.
The size of universal share and every created share remains in the form of one fourth of the original image.Therefore,the shares are organized(as shown in Figure 2)with universal share in such a unique manner so that the size of the shared images are similar to the size of original image.
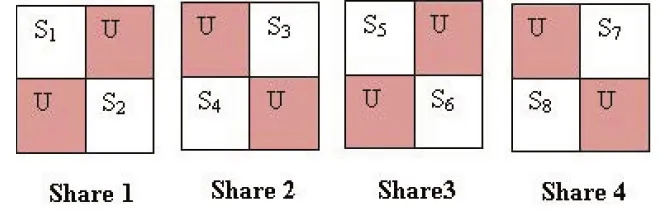
Figure 2. Organization of the quadrant share.
As a result,four shares are obtained.The obtained secret shares are further encrypted using optimal key rectangle block cipher.
3.3 Optimal Key Generation for Rectangle Block Cipher
RECTANGLE is an iterated block cipher with a key length of 80 or 128 bits for a 64-bits plain text or a block [24].RECTANGLE uses SP(SubstitutionPermutation)-network whereas the substitution layer includes 16 quantities of 4×4 substitution boxes (SBoxes) in parallel.Permutation layer contains 16-bit revolutions to provide better diffusion.Additionally,the RECTANGLE goes through a round change during when the SP-network cipher performs 25-rounds.During every round,out of the 25 rounds,there occurs three phases such as(i)Round key addition,(ii)Sub-Column S-box and(iii)Row shifting.In round key addition,the bitwise XOR of the round sub key with intermediate state is performed.Next,the parallel utilization of S-boxes to each column is done at sub-column S-box stage.At last,the row shifting is finished by left rotation to each row over different offsets.Here,the rotation offsets might be 0,1,12 and 3 for row 0 to row 3.
In a RECTANGLE block cipher,the keys are planned as either 80 or 128 pieces.On the off chance,when the seed key is 80-bit it is put away in an 80-bit key register first and then organized as a 5x16 array of bits.Likewise,for 128-bit seed key,it is arranged in a key register according to the size and then sorted out as a 4×32 array of bits.
However,the proposed optimal key RECTANGLE block cipher method selects the key optimally (especially in 80 bits or 128 bits)based on the decrypted image quality with the help of Oppositional Whale Optimization algorithm(OWOA).The proposed optimal key rectangle block cipher method helps the entire secret sharing scheme,since the optimal key is selected based on maximum PSNR value and does not visually modifies the secret image.
3.3.1 Key Optimization by Oppositional Whale Optimization Algorithm
WOA is a bio-motivated meta-heuristic optimization algorithm that mimics the food search characteristics of humpback whales [25].Humpback whales follow a bubble-netting system and communicate with other whales by producing sounds as soon as it finds a prey.After the prey is captured,it is attacked following swim-up mechanism.The humpback whale behavior can be numerically represented through multiple stages,for instance search for prey,bubble-net development,enclosing the prey and swim-up system to attack the fish.Here,the oppositional WOA is applied in producing the ideal keys for rectangle block cipher based encryption strategy.In oppositional WOA,contrary solutions are produced that may get the opportunity of drawing the solution nearby the ideal than the random initial solutions.It could be executed to upgrade the efficiency of customary optimization techniques.
Listing 1: Oppositional Whale Optimization Algorithm for Key Optimization
3.4 Secret Image Reconstruction
Secret image reconstruction method is not only just the reverse of the proposed secret sharing scheme but it is also an easier process than the latter.The received shares are in encrypted form and are decrypted by the application of appropriate key values.Once the shares are decrypted,the original secret image can be retrieved from the proposed secret image recovery method.As mentioned in the proposed double-layered secret sharing,the first layer secret reconstruction is initiated by offering a universal share.Then,a few strategies similar to the proposed sharing method is followed to recover the secret image quadrants(at first layer).Here,the image quadrants are found from the first layer and are merged.Then,a simple XOR operation is carried out to obtain the original secret image.The detailed structure of the proposed secret image retrieval scheme is shown in Figure 3.
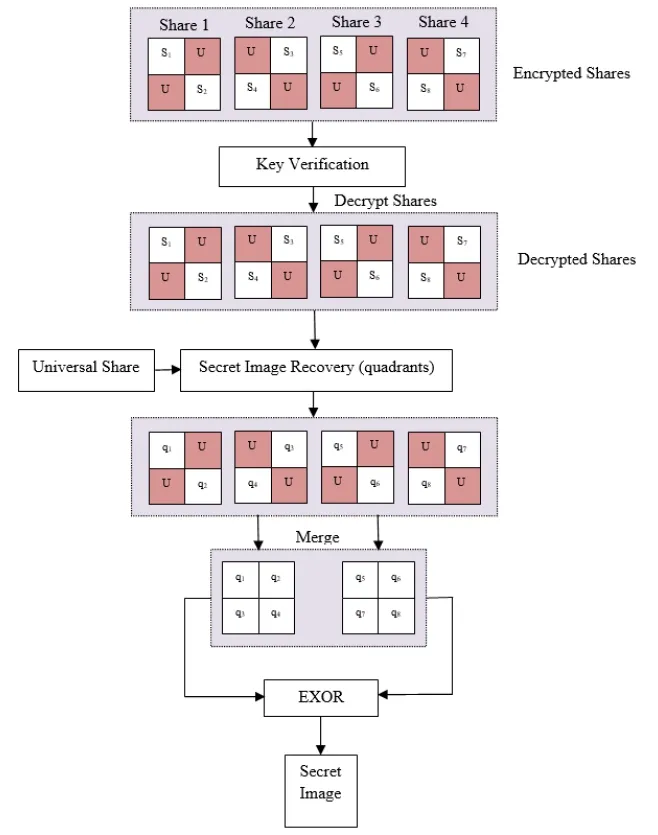
Figure 3. The proposed secret image retrieval scheme.
3.5 Steps in Secret Image Reconstruction Approach
Let the input be shared images S={S1,S2,...,S8}and the corresponding outputs are the secret image.The steps involved in secret image reconstruction method are as follows.
Step 1: Provide Universal Share
Initially,the universal share U is provided.
Step 2: Secret Image (Quadrant) Reconstruction:First Layer
Now,the secret images of the first layer(i.e.quadrants) are found with the details of universal share.Then the quadrants Q={q1,q2,...,q8} are derived as follows.
Step 3: Merge the Quadrants
In this step,the quadrants are merged together.The first four quadrants are merged together to form the first secret image whereas the remaining quadrants are merged to form the second secret image.
Step 4: Secret Image Reconstruction: Second Layer
This is the final step in which the merged images from Step 3 undergo XOR operation followed by the recovery of secret image.
IV.RESULT AND DISCUSSION
4.1 Experimental Setup
The researcher conducted the experiments and the results were obtained for the proposed double layered secret sharing approach.These experiments were conducted in a PC loaded with following configurations;MicrosoftWindows 10,64-bit operating system,Math Works MATLAB R2014b stage and 4 GB of RAM and CPU IntelPentium 1.9 GHz.
The experiments were conducted upon a database comprising 200 test images.However,only a few sample images such as ‘BoatsColor.bmp’,‘Zelda-Color.bmp’,‘barbara.bmp’,‘cablecar.bmp’,‘goldhill.bmp’,‘fingerprint 1.bmp’,‘fingerprint 2.bmp’,‘Iris 1.bmp’,‘Iris 2.bmp’ and ‘fingerprint 3.bmp’ is shown in Figure 4.Moreover,all the experiments were conducted for the given set of test images whereas the results for‘BoatsColor.bmp’,‘ZeldaColor.bmp’,‘barbara.bmp’ and ‘cablecar.bmp’ are detailed in the upcoming sections.

Figure 4. Biometric images.
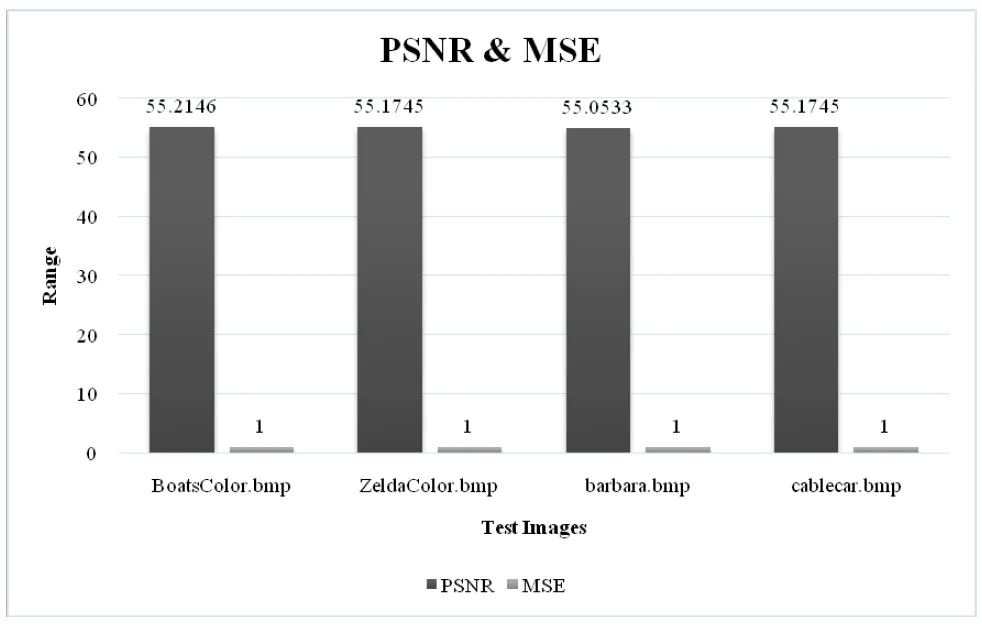
Figure 5. PSNR results of the proposed scheme.
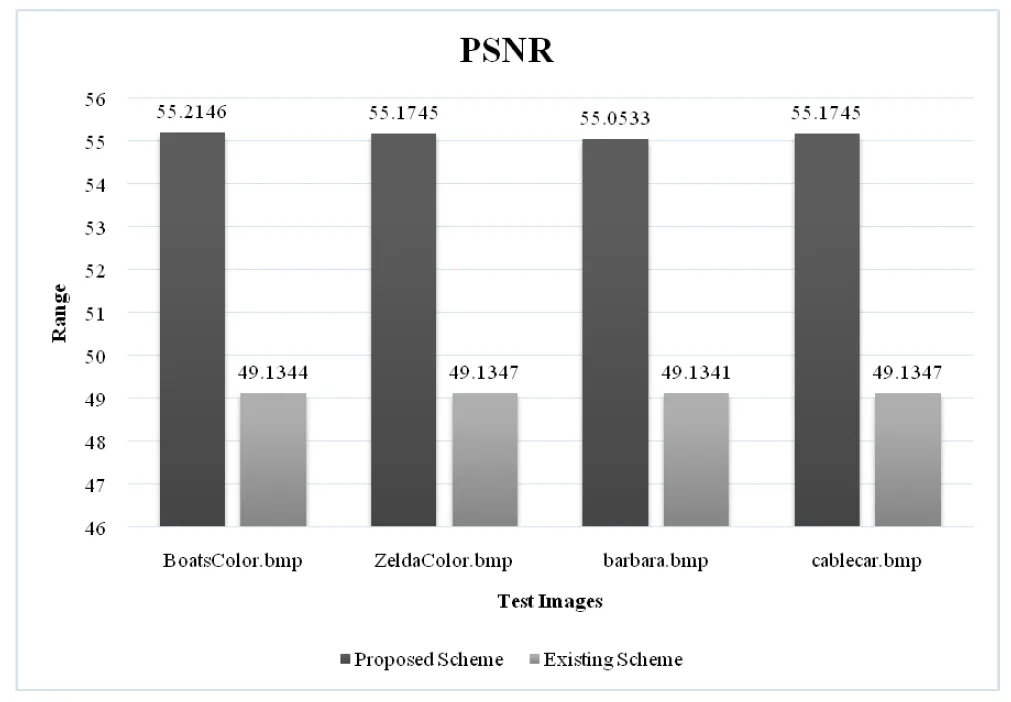
Figure 6. PSNR comparison between the proposed and the existing schemes.
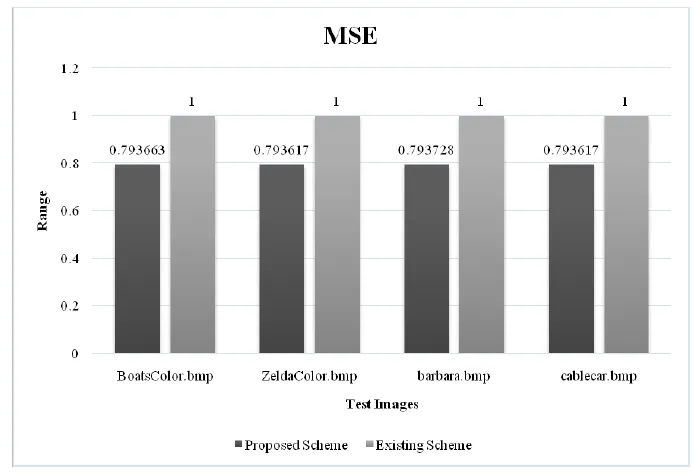
Figure 7. MSE comparison between the proposed and the existing schemes.
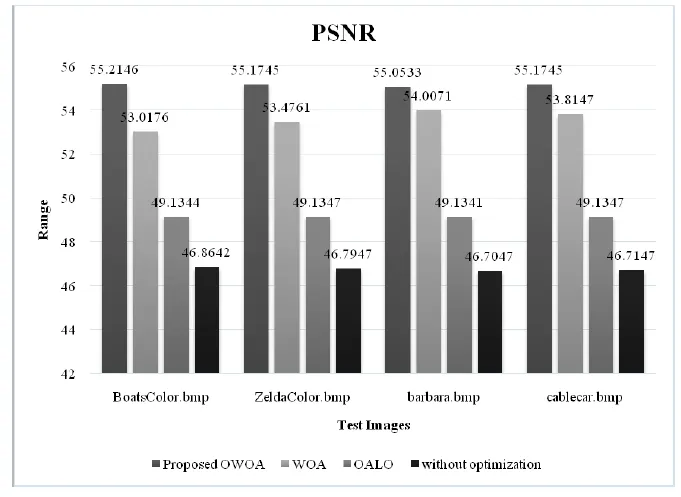
Figure 8. PSNR comparison between the proposed and existing schemes with and without optimization.

Figure 9. MSE comparison among the proposed and existing scheme with and without optimization.
4.2 Experimental Results
The proposed scheme secures the secret images using double-layered secret sharing method.Here,the secret color images are shared as two layers.The first layer is threshold-based and the other layer is universal sharebased.The intermediate results of the proposed secret image sharing method for‘Barbara’image is given in Table 1.

Table 1. Secret image sharing results for‘Barbara’image.
In Table 1,the columns 2 and 3 represent the shares created in subsequent layers.Finally,the shared images were combined with the help of universal share and are shown in the last column.After combining the shares,four shares of similar size were obtained as a secret image.The final shares were then encrypted using OWOA-based optimal key Rectangle Block Cipher.Then,the encrypted images alone were transferred to ensure the security.The encrypted shares were retrieved through decryption with appropriate keys.The results for encryption and decryption processes of the secret shares are given in Table 2.
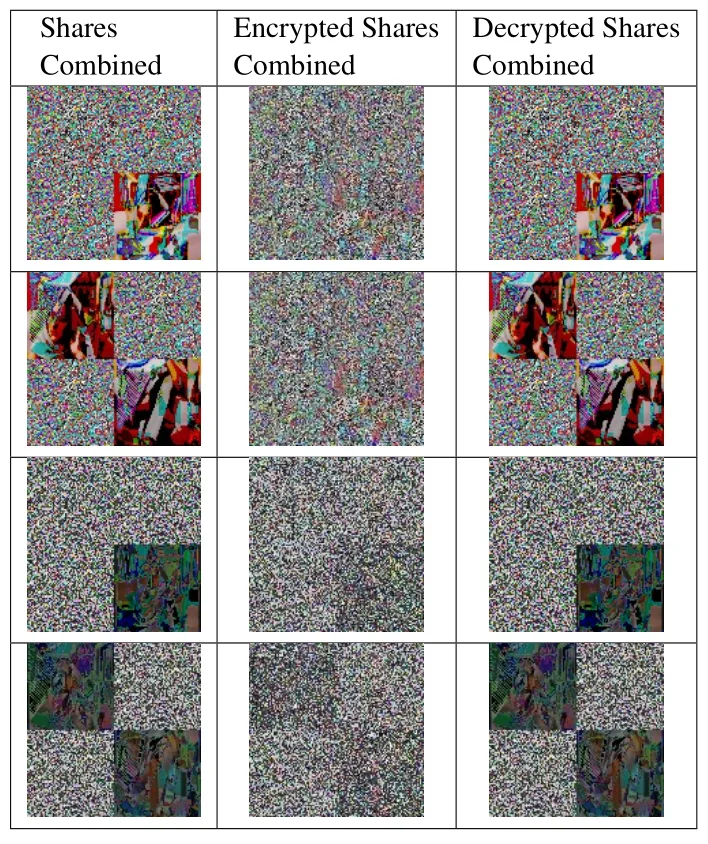
Table 2. Secret shares encryption results for‘Barbara’image.
At last,the decrypted and combined image shares were separated to produce the layer 2 shares.Based on layer 2 shares,share reconstruction process was executed to get the layer 1 shares.Then,the layer 1 shares were concatenated to produce the reconstructed secret image.Table 3 shows the step-by-step reconstruction process of the secret image.
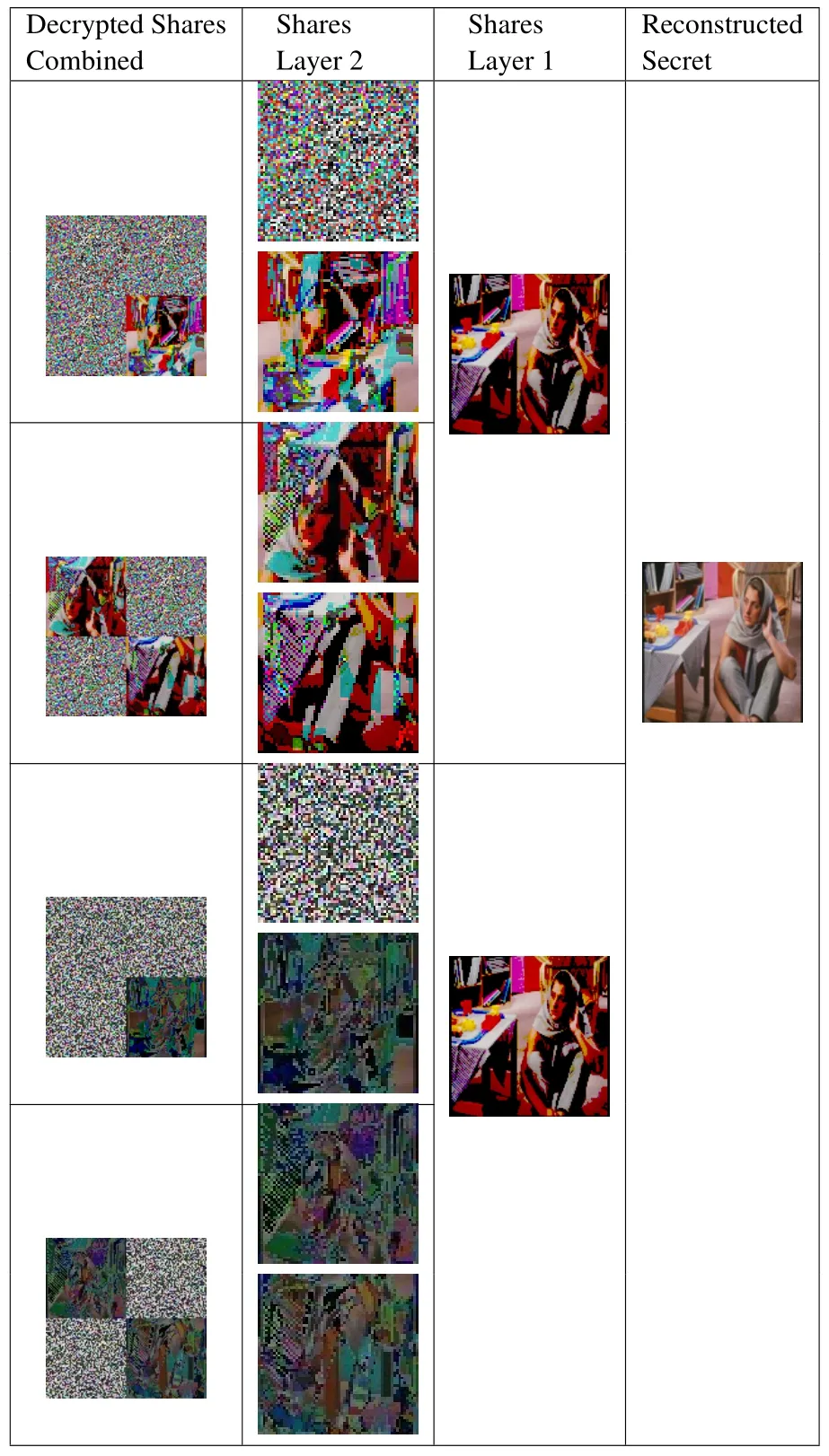
Table 3. Reconstruction result for Barbara image.
4.3 Performance Analysis
In this stage,the performance of the proposed doublelayered secret sharing method was analyzed by computing the PSNR and MSE measures between the original and reconstructed images.The PSNR and MSE values attained from the proposed double-layered se-cret sharing model are shown in Table 4.
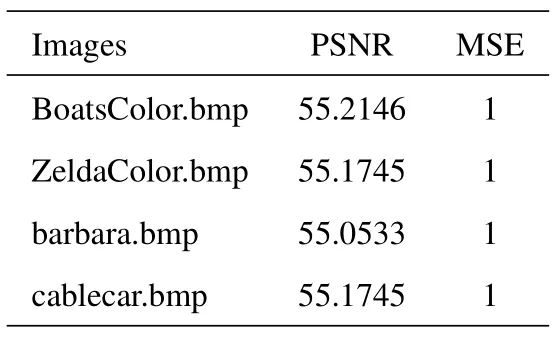
Table 4. PSNR and MSE values between original and the reconstructed images.
Between the PSNR and MSE values,shown in Table 4,PSNR value is better and higher than55.Also,the MSE value being 1 is very less for all the images.This shows the best capacity of the proposed technique during reconstruction.
4.4 Comparison
In this section,the results attained earlier from the proposed scheme and existing scheme (our previous work)were compared.This comparison is also inclusive of the proposed scheme applied with SIMON ciphers.Table 5 shows the results achieved from both PSNR and MSE metrics.The obtained values illustrate that the PSNR and MSE values got heavily increased in the proposed strategy in comparison with existing techniques.Furthermore,the PSNR values of ‘BoatsColor.bmp’,‘ZeldaColor.bmp’,‘barbara.bmp’and‘cablecar.bmp’were 55.2146,55.1745,55.0533,and 55.1745 respectively.The existing schemes achieved only the following PSNR values such as 49.1344,49.1347,49.1341,and 49.1347 respectively.However,the proposed method when applied with SIMON ciphers,the researchers achieved the PSNR values such as 50.3455,52.8943,51.7893 and 51.87934 respectively.Those values attained by the existing methods were lesser than the proposed outcomes.This indicates that the quality of reconstructed image obtained through the proposed scheme is better in comparison with existing schemes.Similarly,the MSE values were also less for the proposed method comparing to existing methods.
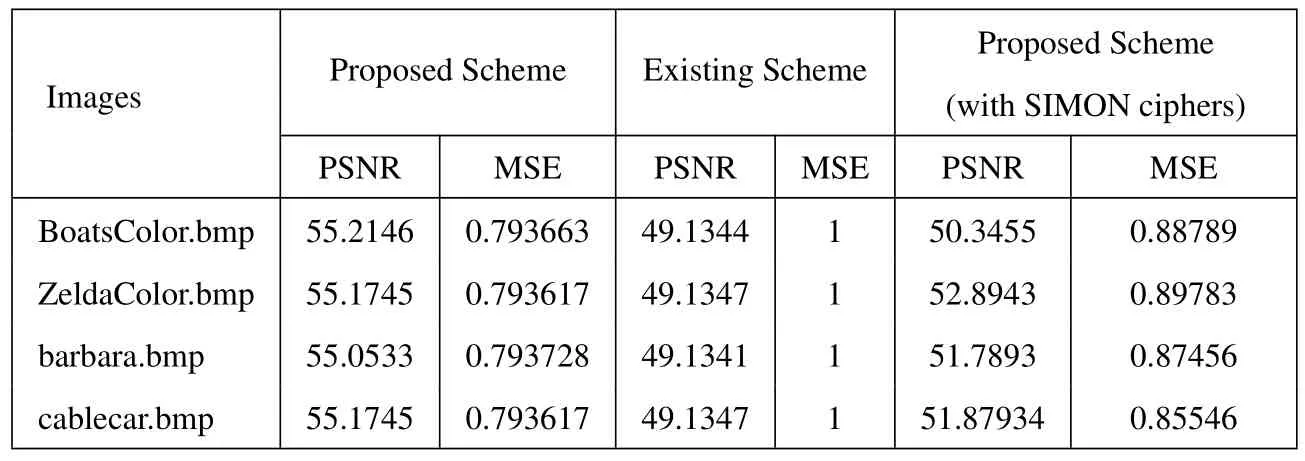
Table 5. Comparison between the proposed and the existing schemes.
From the above results,it is clear that the reconstructed image quality of the proposed technique is proficient than the existing strategies.
At last,the proposed approach was analyzed with and without other optimization methods.Both PSNR and MSE values were compared for the proposed method with and without other optimization methods and the results are shown in Table 6.
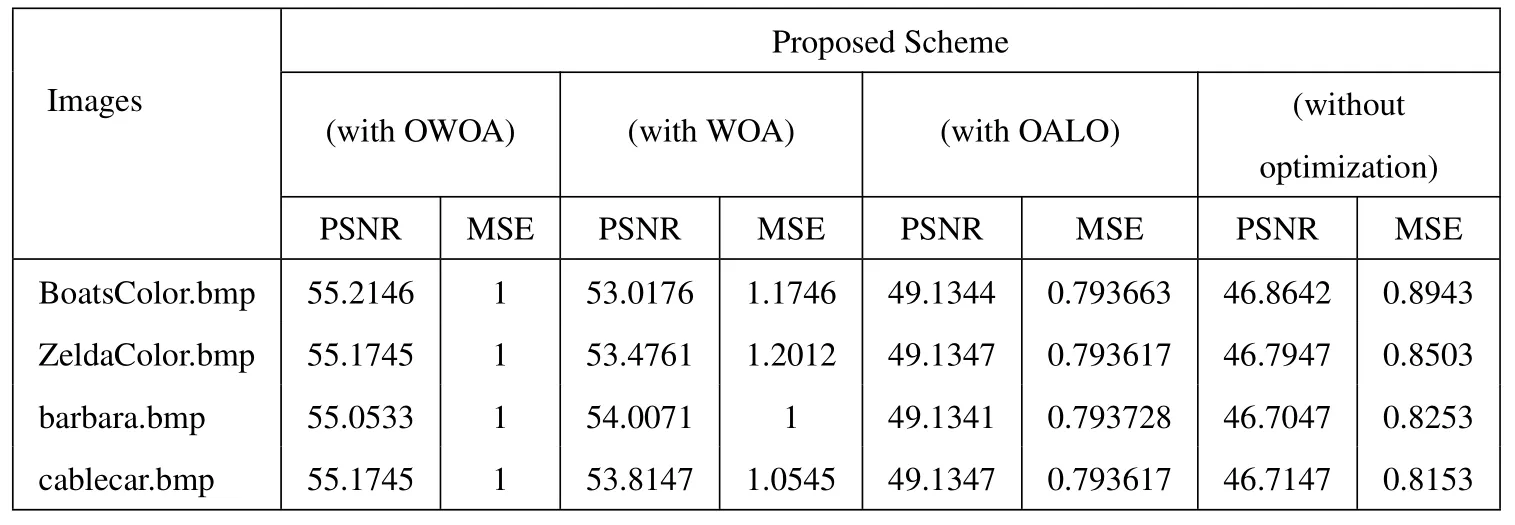
Table 6. Comparison of PSNR and MSE values for the proposed method without and with other optimization methods.
Table 6 shows the resultant of PSNR and MSE values attained for the proposed double-layered secret sharing scheme with OWOA-based Rectangle Block cipher,with WOA,OALO optimization method and without any optimization methods.Out of the obtained PSNR values,the PSNR ofthe proposed scheme with OWOA was outstanding than other schemes.Also,the PSNR values of’BoatsColor.bmp’,’ZeldaColor.bmp’,’barbara.bmp’ and ’cablecar.bmp’were 55.2146,55.1745,55.0533,and 55.1745 respec-tively for the proposed method with OWOA.Further,the PSNR values were 53.0176,53.4761,54.0071,53.8147 for WOA;and 49.1344,49.1347,49.1341,49.1347 for OALO and 46.8642,46.7947,46.7047,46.7147 for without optimization.From the above values,it can be inferred that the PSNR values were high for the proposed method and the maximum PSNR was 55.2146.These values were also attained for’BoatsColor.bmp’,when processed through the proposed scheme.Compared to all above optimization methods,the approach with no optimization methods produced the least PSNR value.To conclude,it is clearly proven that the PSNR value for the proposed scheme is high.This indicates the achievement of a better quality image during secret image reconstruction.The proposed scheme outperformed all other methods in terms of performance.
V.CONCLUSION
In this research work,a robust and secure doublelayered secret image sharing scheme with universal share and rectangle block cipher was proposed.Here,the secret sharing is done at two layers and both the layers use a novel share creation method.To be specific,the first layer(threshold-based)uses Genetic Algorithm method for threshold selection whereas the second layer(universal share-based)uses specific calculations.At last,the shares are encrypted through Opposition Whale Optimization algorithm (OWOA)based optimal key rectangle block cipher while the key is selected optimally using OWOA.The performance of the proposed scheme was analyzed against existing approaches with and without optimization methods.The researcher conducted the experimentation and maximum PSNR value i.e.,55.2146 was achieved from the proposed scheme.This value was far better than the existing methods.The result established the efficiency of the proposed scheme in producing high quality secret reconstruction image.In future,the proposed secret sharing scheme should be enhanced in order to avoid the usage of additional encryption methods.
ACKNOWLEDGEMENT
This research work has been supported by RUSA PHASE 2.0,Alagappa University,Karaikudi,India.
CONFLICT OF INTEREST
The authors express that they have no conflict of interest.
- China Communications的其它文章
- Design Framework of Unsourced Multiple Access for 6G Massive IoT
- 6G New Multiple Access Technology
- OFDMA-Based Unsourced Random Access in LEO Satellite Internet of Things
- Cluster-Based Massive Access for Massive MIMO Systems
- A Joint Activity and Data Detection Scheme for Asynchronous Grant-Free Rateless Multiple Access
- The Extended Hybrid Carrier-Based Multiple Access Technology for High Mobility Scenarios

