Design Framework of Unsourced Multiple Access for 6G Massive IoT
Chunlin Yan ,Siying Lyu ,Sen Wang ,Yuhong Huang ,Xiaodong Xu
1 China Mobile Communication Research Institute,Beijing 100053,China
2 ZGC Institute of Ubiquitous-X Innovation and Applications,Beijing 100080,China
3 State Key Laboratory of Networking and Switching Technology,Beijing University of Posts and Telecommunications,Beijing 100876,China
Abstract: In this paper,ambient IoT is used as a typical use case of massive connections for the sixth generation(6G)mobile communications where we derive the performance requirements to facilitate the evaluation of technical solutions.A rather complete design of unsourced multiple access is proposed in which two key parts:a compressed sensing module for active user detection,and a sparse interleaver-division multiple access (SIDMA) module are simulated side by side on a same platform at balanced signal to noise ratio(SNR)operating points.With a proper combination of compressed sensing matrix,a convolutional encoder,receiver algorithms,the simulated performance results appear superior to the state-of-the-art benchmark,yet with relatively less complicated processing.
Keywords: channel coding;compressed sensing;massive Internet-of-Things (IoT);sparse interleaverdivision multiple access (SIDMA);the sixth generation(6G)mobile communications;unsourced multiple access
I.INTRODUCTION
Multiple access is one of the core technologies of wireless communications and has enormous impact on the system capacity and network performance.From the first generation (1G) to the fifth generation (5G)mobile wireless communication systems,orthogonal multiple access (OMA) has been the primary access scheme especially for enhanced mobile broadband(eMBB) in 4G and 5G systems with large package size.For eMBB,control signalling such as scheduling grant can facilitate the link adaptation which is crucial for the data throughput.Control signaling also includes various messages exchanged during the initial access to wake up terminals from idle state to connected state.Due to the small percentage of control information compared to the large packet size of eMBB and the continuous traffic flows,the benefit of control signaling overwhelms its overhead.Hence,OMA works reasonably well for eMBB where the number of connected terminals is not large in general.
For the sixth generation (6G) networks,it is envisioned that the number of connections for massive Internet-of-Things (IoT) will be 10 −100 times more than that of 5G[1].The traffics of massive IoT are mainly small data packages sporadically generated.One typical scenario is the Ambient IoT currently being studied in the 3rd Generation Partnership Project (3GPP)[2].The traditional grant-based transmission of OMA is no longer suitable due to the excessive control overhead,access delays and device power consumption associated with the multi-step random access procedure and link adaptation.Therefore,a lightly-controlled transmission without connectionsetup or dynamic link adaptation is desirable.
To reduce signaling overhead,delay and terminal consumption,grant-free transmission was introduced which has two types:1)contention-free where the data is transmitted using pre-allocated signatures such as spreading sequences,interleaver patterns,scrambling codes,preamble,etc;2) contention-based where signatures are randomly selected by users.In the study on 5G multiple access[3][4],the contention-free type of grant-free was studied more thoroughly.
Considering the much denser connections of 6G massive IoT,contention-based grant-free seems more suitable as it can more efficiently handle the signature collision problem.Recently there has been some breakthrough in information-theoretic analysis of contention-based transmission which is also called unsourced multiple access[5][6].Drastically different from the traditional Shannon formula,Polyanskiy’s team at Massachusetts Institute of Technology (MIT)proved that the capacity bound of unsourced multiple access is much higher than that of OMA [7].Their theoretical work also reveals the potential of joint processing across multiple users for short-length blocks,which cannot be achieved by OMA where each user’s data is individually processed.
Inspired by the finding in [7],several unsourced multiple access schemes were proposed for massive IoT scenarios[8–10].The BCH/forward error correction (FEC) cascaded scheme [11] can tackle the collision and noise problems in Gaussian multiple access channel(GMAC)channel by using an BCH outer code and an inner forward error connection(FEC)code,respectively.In tree search-based compressed sensing(CS) approaches [12],the transmission code word is mapped to columns of CS matrix,e.g.,direct mapping of information bits to the symbol vector of multiple access codes.In[13]a sparse Kronecker-product coding scheme is proposed for unsourced multiple access.The data of each active user is encoded as the Kronecker product of two component codewords with one being sparse and the other being forward-errorcorrection coded.Its performance is very close to the random coding bound.In [14] a data only transmission scheme was proposed where a blind equalization performs the channel estimation without relying on reference signals.In CS preamble coding+sparse interleaver-division multiple access (IDMA)coding scheme [15],CS is employed for active user detection and channel estimation,while an iterative receiver is used for multi-user detection.
In sparse code multiple access(SCMA)[16],zeros are inserted in the codewords to reduce the cross-user interference and the complexity of maximum likelihood(ML)receiver.In[17],Reed-Muller codes based CS was proposed where multi-slot transmission strategy is used for random access.In[18][19]low-density parity check (LDPC) code is employed as channel coding scheme for sparse-IDMA where the multi-user detector is of belief propagation (BP) type.In addition,multi-slot transmission is used to reduce the computational complexity.Compared to traditional IDMA which typically allows 10 −20 users to transmit simultaneously,sparse-IDMA can support much larger scale of superposition transmissions,e.g.,200 −300 users.Also,sparse-IDMA relies on channel code optimization to improve the performance,whereas in 5G IDMA study the channel codes were limited to New Radio(NR)LDPC.
The main contributions are summarized below.
1.Performance requirements are derived from a typical application scenario of ambient IoT which can guide key parameter setting of unsourced multiple access,such as information block length,code rate of channel encoder,number of repetitions,size of CS matrix,etc.
2.A complete design is proposed where the CS and multi-user detection work together,e.g.,the results of CS for active user detection and channel estimation would be used for multi-user detection where collision probability is also considered.
3.Elementary signal estimator (ESE),instead of joint detection with belief-propagation,is used for multi-user detection of sparse-IDMA.In addition,smaller size of FFT-type compressed sensing matrix is used,resulting in better estimation of channel and active user detection.Hence,an overall performance closer to the capacity bound for unsourced multiple access is achieved,yet with reduced computational complexity.
4.The impact of channel coding scheme on the performance of sparse-IDMA is assessed via evolution functions.Compared to LDPC,the potential of convolutional codes in sparse-IDMA is clearly shown and verified by the simulation results.
5.Realistic channel estimation and active user detection are carried out for sparse-IDMA and the performance degradation compared to the ideal channel estimation is shown.
II.THE REQUIREMENTS FROM AMBIENT IOT
Originally from Radio frequency identification(RFID) technology,ambient IoT requires no power or very little power,and may fulfill the vision of“100 billion interconnection”.Ambient IoT will adopt a cellular architecture that supports a larger scale expansion of system capabilities.The study on deployment scenarios of ambient IoT is a hot topic in 3GPP R19 System Aspect Working Group 1 (SA1).A total of 32 use cases have been identified,including typical indoor cases such as warehousing,medical,manufacturing retail,home furnishings,and outdoor cases such as power,supply chain distribution,airport,municipal,and animal husbandry.Based on the characteristics and performance requirements,these use cases can be grouped into four categories: inventory,environmental sensing,terminal positioning,and control commands.Among them,the inventory category is the most challenging in terms of connection density and thus will be the focus in the following analysis.Some key performance requirements of inventory category are listed in Table 1.
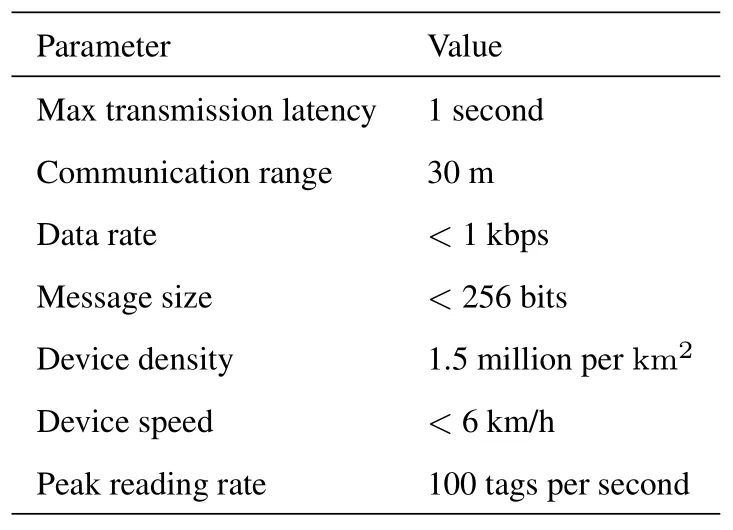
Table 1. Key performance requirements.
According to Table 1,the communication range of an indoor reader is 30 m.In a cellular set up,it means that the cell radius is about 30 m.Hence,the coverage area of a cell(or a reader)is about 2800 square meters.Considering 1.5 million devices per square kilometer,there are roughly 4200 devices in an cell.Although not all of these 4200 devices would transmit simultaneously,up to 100 devices of them would access the network per second when the reader should be able to process in one second.In a typical indoor inventory scenario,the floor area would be around 600,000 square meters.This implies that over two hundred readers (cells) would be deployed where significant inter-cell interference is expected.To overcome this issue,cell-free access can be considered in which each cell (reader) would try to decode devices in neighbor cells.A rule of thumb is that contributions of 3 times of devices in a cell would count for most of uplink received power.Hence,each cell(reader)roughly needsto decode up to 300 devices’data per second.
Similar to RFID,ambient IoT needs to have good coverage.While 30 m does not seem long,the requirement can be quite challenging considering the extremely low transmit power to maximize the battery life.That is why the typical deployment of ambient IoT is in low band,e.g.,800 MHz to ensure small pathloss,together with narrow bandwidth,e.g,smaller than 200 kHz to ensure the enough power spectral density.Because of the low data rate (e.g.,less than 1 kbps),binary phase shift keying(BPSK)or quadrature phase shift keying(QPSK)would be sufficient,allowing more efficient amplifiers and better coverage.
Low-band operation also means limited number of antennas on a reader,e.g.,2 or 4 may be typical.Hence,antenna technology would play minor role in improving the performance of ambient IoT,as opposed to eMBB operating in higher bands.It is also seen from Table 1 that the mobility speed of devices in inventory category is less than 6 km/h.This implies that at 800 MHz operating band,the small-scale fading would be slow-varying.
III.AN UNSOURCED SPARSE SUPERPOSITION SCHEME FOR AMBIENT IOT
3.1 Basic Building Blocks of Unsourced Multiple Access
Figure 1 and Figure 2 show the transmitter(of a user)and the multi-user receiver,respectively,for unsourced multiple access using CS and sparse-IDMA.LetKtotandKabe the total number of users and the number of active users,respectively,whereKa≪Ktot..In light of the performance requirements discussed in previous section,Ktot≤4200×3=12600,andKa≤300.Each active user hasBinformation bits to send.To facilitate the comparison with results in literature,in this paper we setB=100 which is within the value of 256 bits in Table 1.A user’s information bits are first partitioned into two segments e.g.B=Bp+Bd.The first segment is to generate preambles for CS of bit lengthBp.The second segment is to generate modulation symbols for multi-user (MU) detection of bit lengthBd.There are two approaches to transmit the second segment: single-slot vs.multi-slot.In the single-slot approach,all active users transmit simultaneously in a relatively long slot.In the multi-slot approach,each user would pick one of the short slots for transmission.
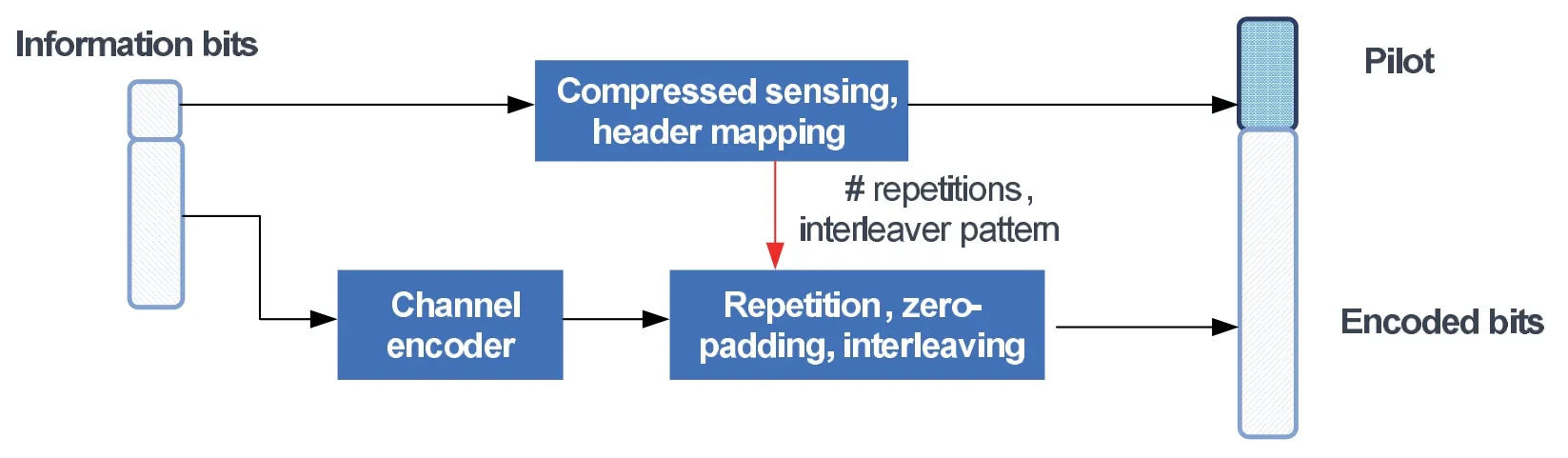
Figure 1. Transmitter for unsourced multiple access.
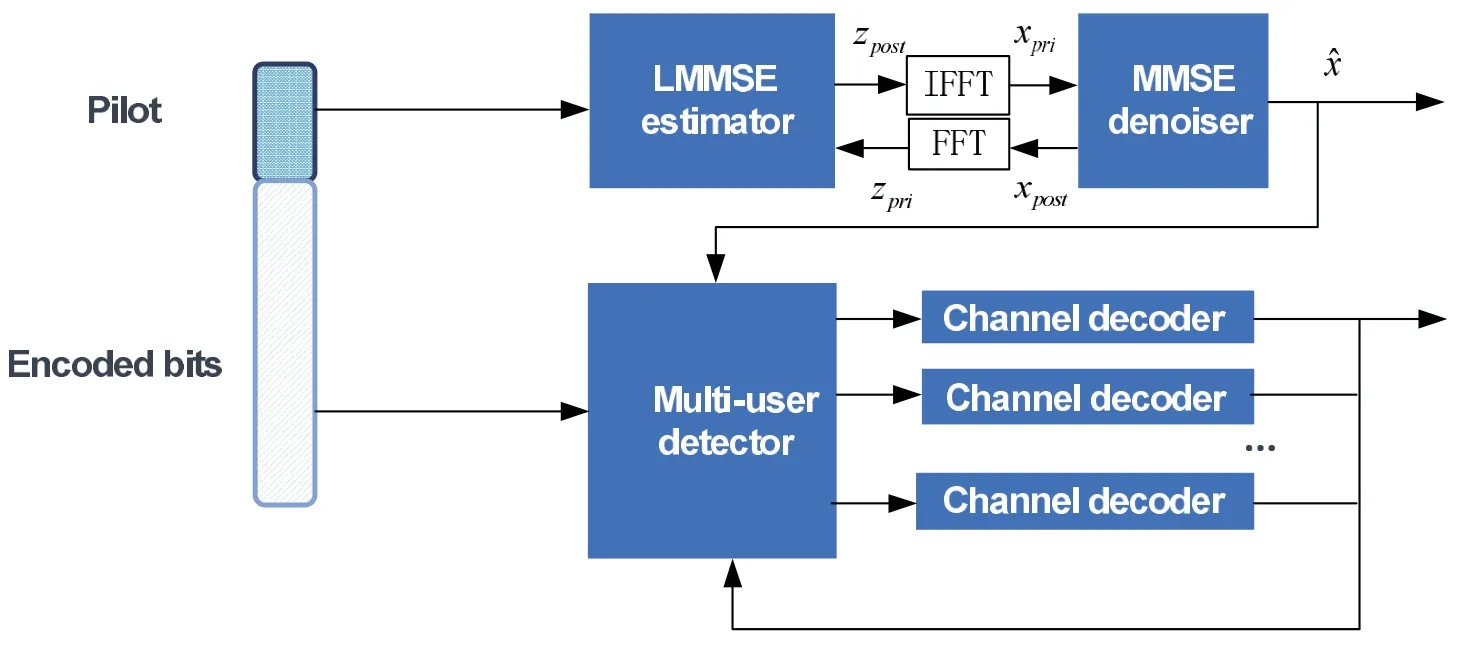
Figure 2. Receiver for unsourced multiple access.
By using compressed sensing matrix and channel coding,repetition,zero padding,the information bits will be mapped toNtchannel uses (e.g.radio resources) for transmission.The value ofNtdepends on the time duration and bandwidth.According to Table 1,the transmission duration is typically no greater than 1 second and the bandwidth is less than 200 kHz.In the simulation evaluation of this paper,Nt=30000 is assumed.In the case of BPSK modulation and 200 kHz system bandwidth,the transmission duration is 0.15 second which meets the requirement.Based on the previous discussion,the channel can be assumed constant within 0.15 second when the mobility speed is below 6 km/h and the operating band is 800 MHz.
It should be emphasized that the encoding process here is independent of a user’s identity (which is exactly the meaning of unsourced multiple access).The information vectoru(k)of thek-th active user,k∈{1,2,...,Ka} is split into two segments:u(k)=.The frist segmentup(k),whose length isBp,is used to encode the CS part.TheBd-bit vector that consists the rest of the information is used to modulate the multi-user part,whereBp≪Bd,andBd=B−Bp.The lengths of the encoded CS and MU parts equalNpandNdrespectively,whereNp+Nd=Nt.Ntis the total message length for each user.
For the CS part of the encoding process,the sensing matrixFpartialof sizeM×Nis listed below(elements in each column are normalized to meet the power constraint)
Usually,M<N.The received signal of CS part can represented as
wherexp∈CN×1is aKa-sparse signal vector whose non-zero entries correspond to the channels of active users to be estimated.In the case of GMAC,non-zero entries ofxpare 1.yp∈CM×1is the received signal,andn~CN(0,σ2I)is the complex Gaussian noise.M=Npwhich is essentially the spreading length of the preamble.N=which is the total number of permutations ofBpbits.Fpartialconsists ofMrandomly selected and reordered rows of the unitary discrete Fourier Transform (DFT) matrixF∈CN×N.The entries of the sparse signalxpis assumed to be independently identically distributed (i.i.d.),following Bernoulli-Gaussian distribution.
The partial DFT matrix in Eq.(2)can be rewritten as
whereSis a selection matrix consisting ofMrandomly selected and reordered rows of theN×Nidentity matrix.The above row selection involves a binary to decimal conversion and bit interleaving,e.g.,the row of the decimal index corresponding to the interleaved binary sequenceup(k)would be selected.By defining
together with Eq.(3),the system model in Eq.(2) can be rewritten as
The data partxd,kis generated by encoding the second segment,followed by repetition,zeropadding and interleaving.More specifically,is encoded with code rate ofRto obtain a (Bd/R)-bit vectorvd,k.Each bit in the vectorvd,kis then repeated several times,and then zero-padded to obtain a vectorxd,kof lengthNd.The repetition and interleaving pattern ofk-th user are determined by the first segmentup(k).Hence,the receiver can obtain the interleaver and repetition information about thek-th user after decoding the first segment.WhenKaactive users transmit simultaneously,the received signal in the data part can be represented as:
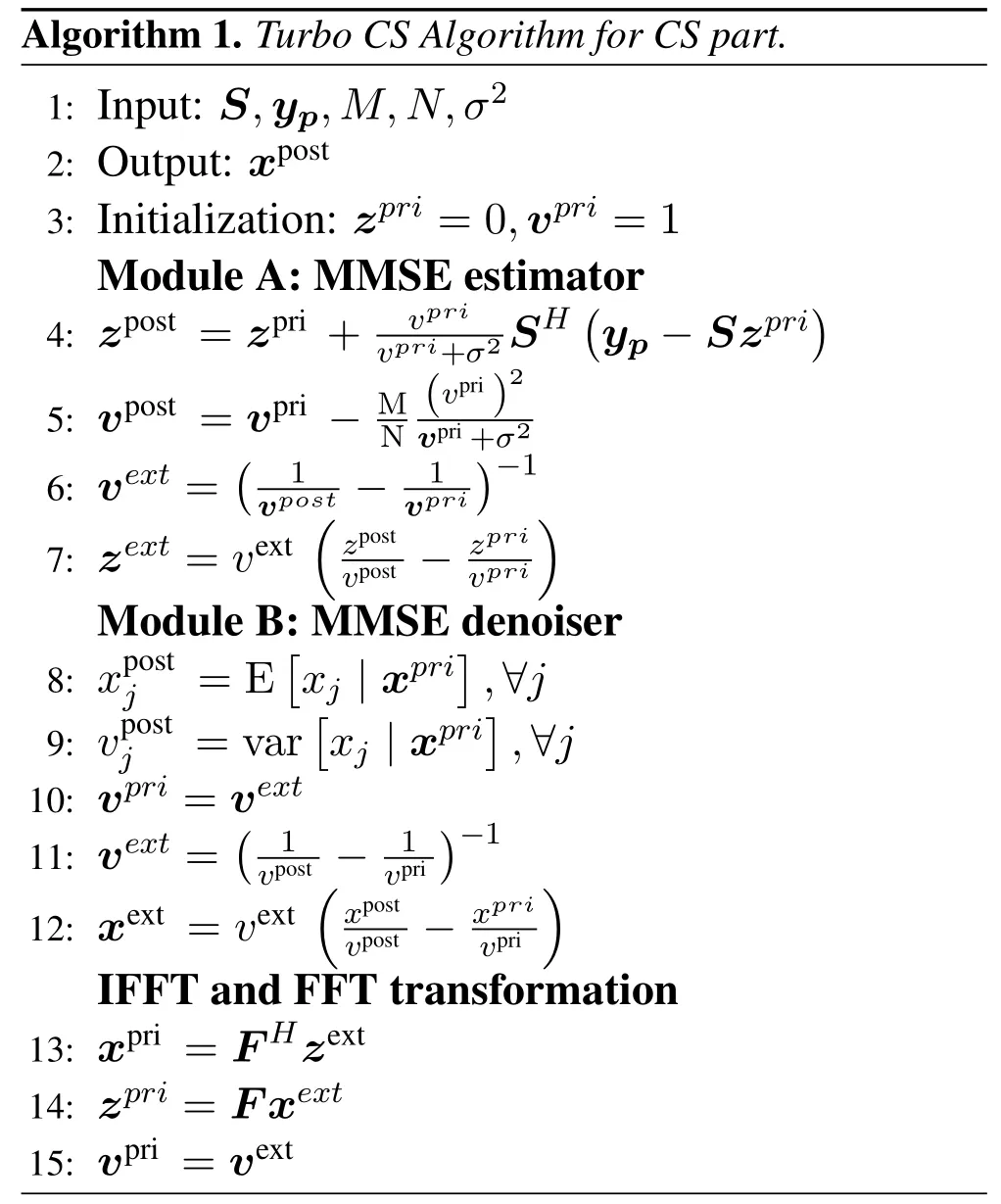
For CS receiver in Figure 2,turbo CS algorithm is employed for iterative detection.The algorithm contains two key modules: a minimum mean square error (MMSE) estimator and a MMSE denoiser [20–22].When multiple receiver antennas are employed,signals from different antennas can be combined by using spatial MMSE or maximal ratio combination(MRC) operations.For the multi-user detection part(e.g.,the second segment of data),another iterative algorithm is used where the extrinsic information propagates between multi-user signal estimator and channel decoder.More details will be elaborated in the next sub-section.
3.2 Signal Detection for CS
Besides MMSE estimator and MMSE denoiser,auxiliary modules in CS receiver include Fast Fourier Transform (FFT) and Inverse fast Fourier Transform(IFFT)for the signal transformation[20]as shown in the upper part of Figure 2.The Turbo CS algorithm can be described below.
CS matrix has two key parameters:MandN.Mis the number of rows which corresponds to the physical resources for the preamble.Larger value ofMmeans lower signal-to-noise ratio (SNR) operating point for CS.Nis the number of columns in the sensing matrix,which is essentially the number of CS (or spreading)sequences to be selected by users.For unsourced multiple access,larger value ofNmeans lower probability of signature collisions.From hardware implementation perspective,Ncannot be too large.Otherwise,the memory requirement and the processing complexity would be infeasible in practical engineering.On the other hand,Nneeds be sufficiently large to ensure low collision probability.
WhenKa=300 andNp=212,the probability of collision-free for each user can be calculated by=0.9294.This means the collision probability is about 0.07 which cannot meet the requirement ofPeless than 0.05.To reduce the collision probability,larger size of compressed sensing matrix is needed which makes the computational complexity less affordable.Thus new paradigm for compress sensing matrix design and its detection is an important research topic.
3.3 Multi-User Detection for Unsourced Multiple Access
Iterative detection is typically used for unsourced multiple access.Here ESE can be applied for multi-user detection in unsourced multiple access [23–25].Figure 3 shows the transmitter and receiver for IDMA using ESE.
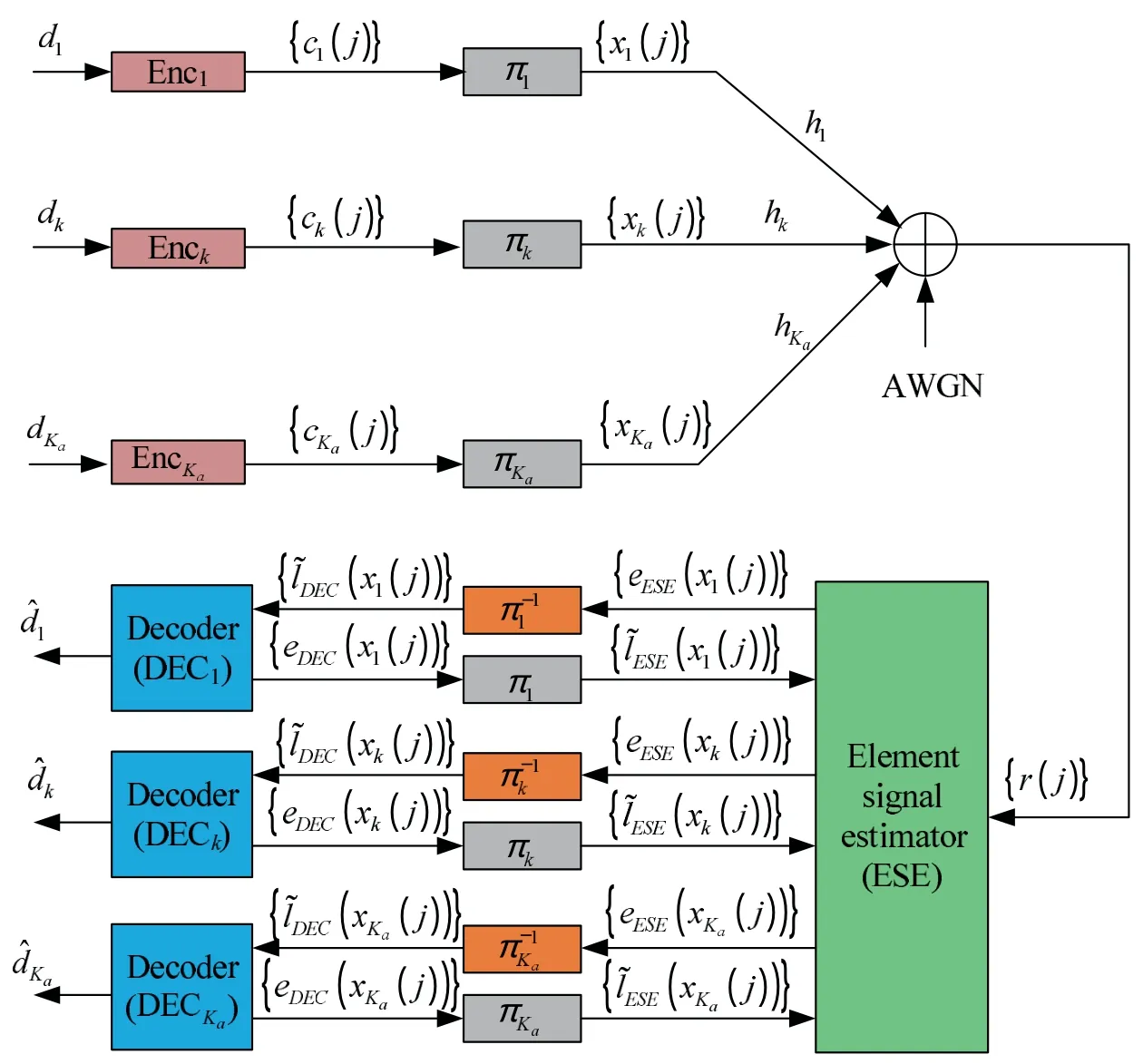
Figure 3. Transmitter and receiver for IDMA.
For simplicity,the subscriptdis omitted in this subsection.Hereck={ck(j)} andxk={xk(j)} denote the bits before and after the interleaving.The elements ofck(j)andxk(j)are either 1 or-1.The received signal can be represented asr(j)=+n(j),j=1,2,...,J.Herehkis the channel coefficient of thek-th user,n(j) is the additive white gaussian(AWGN)with zero-mean and varianceσ2=N0/2,andJis the length of the frame,e.g.,J=Ndin single-slot approach.For simplicity,GMAC channel is considered.Hencehk=1.
The received signal can be rewritten as[23]
where
denotes the interference part.The mean and variance ofxk(j),denoted asE(xk(j)) and Var(xk(j)),respectively,can be calculated according to the central limit theorem.
The initialization is done by settingE(xk(j))=0 and Var(xk(j))=1.The soft-input information for the channel decoder can be calculated as
The extrinsic information can be calculated as
This updated prior information will be used as the input in the next iteration.The above iterative detection is summarized as below.
1)Calculation of the means and variances of interference by using Eq.(9)and Eq.(10).
2)Calculation of the soft information using Eq.(11).
3) Carrying out the decoding (DEC) function to generate.
4)Calculation of the means and variances of the user’s signal using Eq.(13)and Eq.(14).
For the receiver with ESE+soft decoder,the performance can be analyzed by plotting the transfer functions betweenf(γ)andg(v)which can be calculated as below[26]for GMAC.
HereKis the average number of users whose nonzero symbols occupying the same resource.vis the mean of Var(xk(j)) andtis the index of iterations.γis the signal-to-interference-plus-noise ratio at the output of the detector and also the post-SNR at the input to the decoder.For sparse-IDMA a large number of zeros are padded,thus the multi-user interference can be diluted sufficiently.For example,the average number of users multiplexed on the same resource is around 6 forKa=250.
If the curves off(γ) andg(v) do not cross,the iterative detection can converge.However,when there is crossing,the iterative detection will be stuck at the crossing point.
It is noted that in[15]a belief propagation(BP)type of multi-user detection is used for signal detection ofKausers which tends to have high computation complexity.
3.4 Channel Coding Aspect and Detection Complexity
As a very preliminary study,performances of sparse-IDMA with LDPC codes of 5G NR and convolutional codes(CC)have been evaluated.The rationale of considering convolutional codes is as follows.Unsourced multiple access is featured by short-length packets.e.g.,100 bits where convolutional codes may have advantages over random codes such as turbo or LDPC which typically rely on long interleavers or large parity check matrices to perform well.For unsourced multiple access,decoding and multi-user detection need to cooperate closely,e.g.,their transfer functions need to match each other,so that the iteration can converge to a satisfying point.Powerful channel codes for singleuser case may not fare well in this case.Note that Polar codes are not considered in this paper due to the incompatibility to iterative receiver.Although softoutput decoding for Polar codes does exist,significant performance degradation is observed compared with conventional decoding schemes of Polar codes[27].
In [14] a joint detection is applied for the signal detection of sparse-IDMA whose complexity tends to be significantly higher than that of ESE.Taking the example of 28000 samples for data transmission,the complexity of the multi-user detection (compared to ESE)is proportional to the number of inner iterations(within BP) and the mean of the column weight.ForKa=250 the mean of column weight(average number of users occupying the same resource)is around 6,and when the number of iterations is 5,the total complexity of BP for sparse-IDMA is about 30 times of that of ESE.WhenKais a small value,the complexity of sparse-IDMA using BP may be reduced (when the mean of column weight is 2),however,it is still ten times of that of ESE detector.
IV.PRELIMINARY EVALUATIONS
Some key simulation parameters are listed in Table 2.BPSK modulation is used.The channel is AWGN.The channel code rateR=1/2 for both LDPC and convolutional codes.The code length (physical resources)of CS isNp=2000.The physical resources of multiuser detection isNd=28000.Hence,the total physical resources isNt=30000.
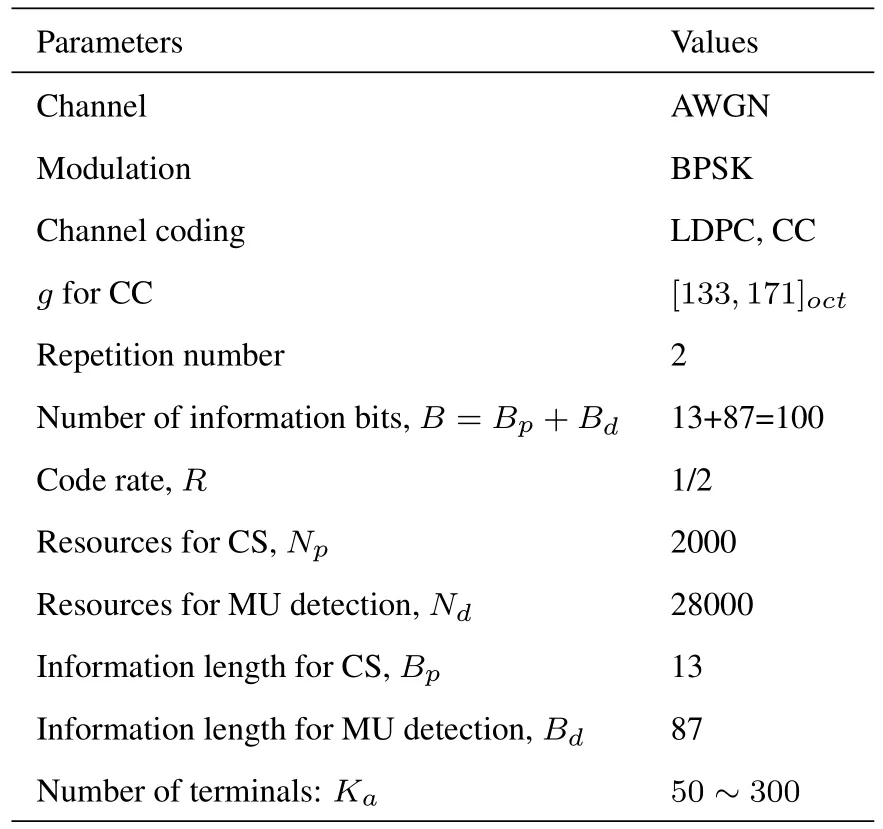
Table 2. Simulation parameters.
In Figure 4 the detection error probability vs.chip level SNR is illustrated forKa=300 by using Turbo CS algorithm with different values of FFT size.The required SNRs for detection error probability of 0.01 are -16.2,-12.8,and -9.5 dB for FFT size values of 4096,8192 and 16384,respectively.Thus larger FFT size results in higher probability of detection error.By reducing the FFT size the required SNR can be reduced significantly.To improve the performance of sparse-IDMA,a CS matrix with a small FFT size is preferred.
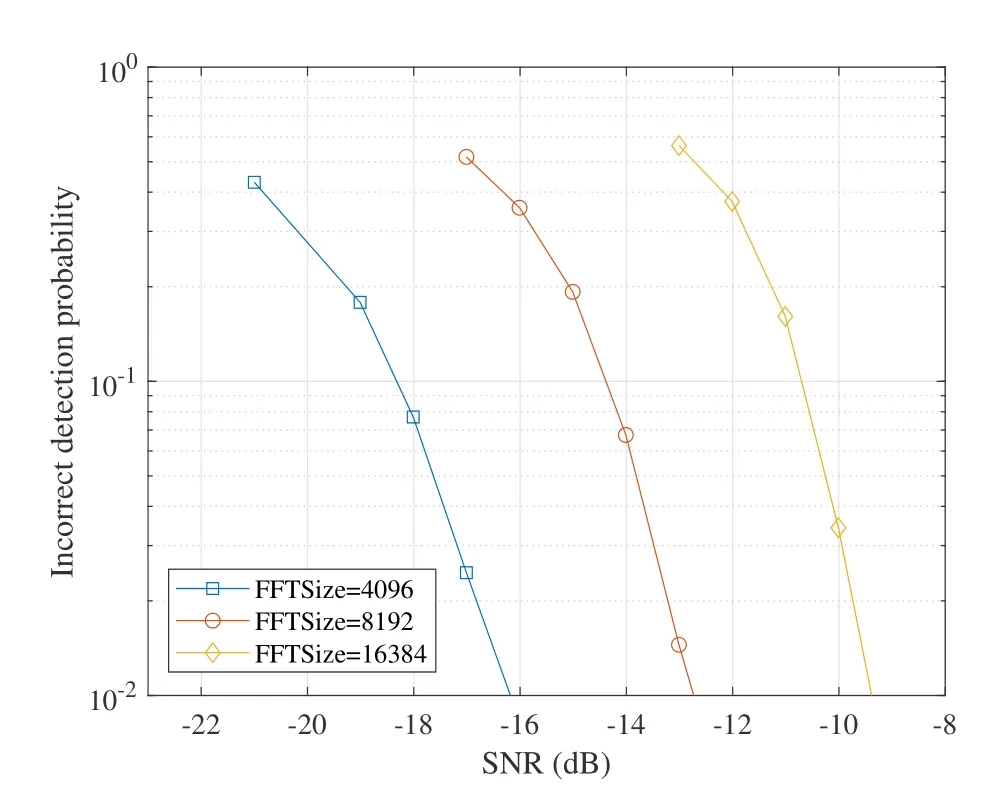
Figure 4. Performance of CS with different FFT sizes.
In Figure 5,the evolution functions of LDPC and convolutional codes for sparse-IDMA are compared atEb/N0=3 dB.The convergence of iterative detection can be characterized by the interplay betweenf(γ)andg(v).WhenKais 250 and 200,the value ofKcan be regarded as 6 and 4,respectively.No crossing is observed betweenf(γ) for CC andg(v) withK=6.This implies that sparse-IDMA using convolutional codes can reach convergence atγ=−1.77 dB.However,crossing point is observed betweenf(γ)for LDPC andg(v) wherevis about 1.This implies that sparse-IDMA by using LDPC cannot converge.By reducing the value ofKfrom 6 to 4,sparse-IDMA using LDPC can reach convergence as Figure 5 shows.
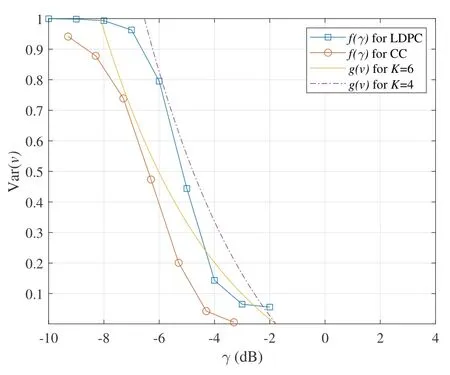
Figure 5. Evolution functions of LDPC codes based and convolutional codes based for sparse-IDMA system. is set to-1.77 dB,corresponding to Eb/N0=3dB.
Figure 6 shows the estimated channel for different cases.The left figure is for Case I and the right figure is for Case II.Parameters for these cases are illustrated in Table 3.Here SNR1is the SNR defined only by CS signals and SNR2is the SNR defined only by sparse-IDMA signals.For Case I,SNR1is not high.Thus the active user detection and channel estimation are not very accurate.The number of detected active users is 249.And the smallest value of estimated channel is about 0.2.SNR1in Case II is higher,leading to the improved performance of active user detection and channel estimation.The number of detected active users is 250 and the smallest value of estimated channel is about 0.6.
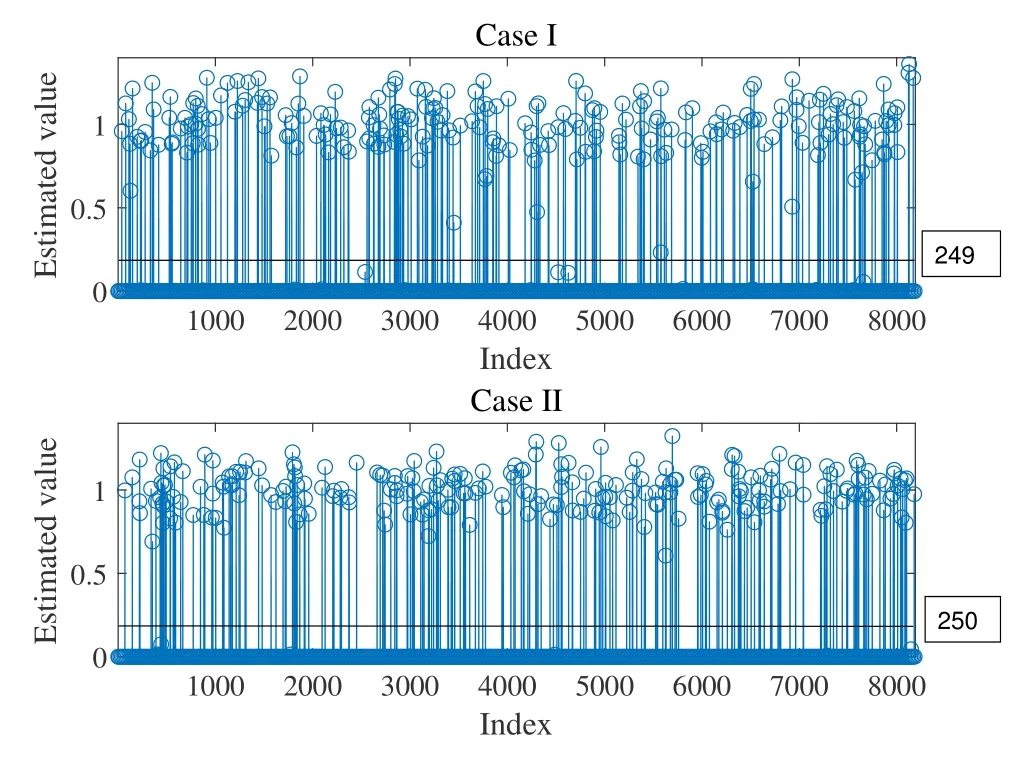
Figure 6. Real channel estimation and real active user detection for Ka=250.
Table 3. Parameters for case I,II and III with FFT size 8192
Figure 7 shows the performance of multi-user interference vs.number of iterations in different cases.It can be seen that the estimated channel is not equal,which somehow facilitates the iterative detection,e.g.,smaller number of iterations is needed compared with that of ideal channel estimation case.All cases can achieve convergence after 10 iterations.Compared with ideal channel estimation and ideal active user detection,realistic channel estimation and active user detection shows performance degradation about 1.2 dB in terms of SNR2.
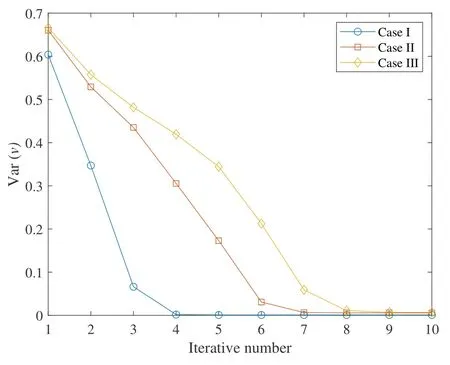
Figure 7. Multi-user interference vs.iterative number by using CC,Ka=250.
Figure 8 shows the requiredEb/N0forPe≤0.05 with different values ofKa.The value ofEb/N0is calculated as
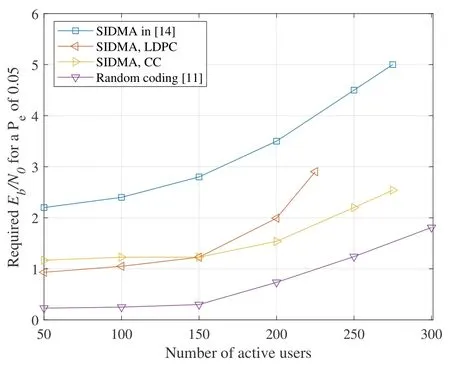
Figure 8. Required SNR vs.Number of active terminals.
HereP1is the power for CS parts with length ofNp,andP2is the power for sparse-IDMA part with length of.Hereis the length of non-zero values amongNddata.And we fixKb=just as what is done in [15].For simplicity we chooseP1which achievesPe=0.01 for CS part andP2which achievesPe=0.04 for sparse-IDMA part.
It is found in Figure 8 that the performance of sparse-IDMA in[15]is worse than the simulation result of this paper because a smaller FFT size is applied and different channel coding is employed in our scheme.The performance of sparse-IDMA with CC is superior to that with LDPC becausef(snr) of CC is better than that of LDPC just as Figure 5 shows.The performance of sparse-IDMA and IDMA is evaluated in[15]where sparse-IDMA is preferred.
V.PRACTICAL ISSUES IN UNCOORDINATED/UNSOURCED TRANSMISSION
In the academic study on unsourced multiple access,hardware impairments are often neglected,such as frequency offset due to the drifting of the crystal oscillator.In unsourced multiple access the multi-user signals are superposed together.When there is frequency offset which can vary between different terminals,the estimation algorithms designed for single user case cannot be used.The severe multi-user interference makes the signal-to-noise-plus-interference very low,thus estimation of the frequency offset for multi-user is a challenging work.There is also multi-cell interference in practice which may leave some unsourced multiple access schemes not workable or performance significantly degraded.The impact of multi-cell interference on unsourced multiple access should be considered.
Multi-path fading channel should be considered as well.So far AWGN channel has been assumed in many studies on unsourced multiple access,while in wireless communications multi-path fading channel exists.CS often assumes that the channel is constant within a code block.However,channel fading would make CS detection more challenging.Another difficulty is channel estimation over multi-path fading channel where several path coefficients should be considered.
Multiple-antenna can improve the performance greatly via transmitter-diversity or receiver-diversity.It may be difficult to equip multiple-antenna in transmitter due to the cost constraint and low band frequency applied.However,for base station multiple receiver antennas are possible.Multiple antenna at receiver can improve system performance,but,the computational complexity also increases.Thus how to make a balance is a research topic.
5G LDPC codes are binary codes.Non-binary LDPC is the extension of binary LDPC.Because nonbinary LDPC has better performance than that of binary LDPC for small code length [28],and it is verified in this paper that channel coding has significant impact on the performance of unsourced multiple access,non-binary LDPC can be studied for unsourced multiple access in future.
Coverage and energy efficiency are important requirements for 6G applications.To extend the signal coverage or achieve high energy efficiency,low peak-to-average-power-ratio(PAPR)waveform is preferred.Candidate waveforms include single-carrier or constant envelope orthogonal frequency division multiplexing [29].The later has a PAPR of 0 dB,leading to the wide coverage.Low PAPR waveform is one promising research topic for unsource multiple access.
VI.CONCLUSION
In this paper the requirements of 6G massive IoT were proposed with ambient IoT as a typical use case.The stringent requirements called for unsourced multiple access where a framework of transmitter and receiver processing was discussed.Two key processes were elaborated and simulated jointly.One is called sparse-IDMA where a large number of zeros are added to reduce the multi-user interference after user-specific interleaver,and the other is CS for active user detection and channel estimation.With suitable combination of CS matrix,convolutional codes,Turbo CS receiver,ESE algorithm,a superior performance was achieved,compared to the state-of-the-art proposals,yet with relatively less computation complexities.Future work was outlined which includes feature enhancements such as multi-antennas,channel coding and sensing matrix optimization,as well as practical design aspects such as frequency offset estimation,CS for multi-path fading channels,etc.
- China Communications的其它文章
- 6G New Multiple Access Technology
- OFDMA-Based Unsourced Random Access in LEO Satellite Internet of Things
- Cluster-Based Massive Access for Massive MIMO Systems
- A Joint Activity and Data Detection Scheme for Asynchronous Grant-Free Rateless Multiple Access
- The Extended Hybrid Carrier-Based Multiple Access Technology for High Mobility Scenarios
- Design and Implementation of Nonlinear Precoding for MIMO-SDMA Toward 6G Wireless

