A Dynamic Bayesian-Based Comprehensive Trust Evaluation Model for Dispersed Computing Environment
Hongwen Hui,Zhengxia Gong,Jianwei An,*,Jianzhong Qi
1 School of Computer and Communication Engineering,University of Science and Technology Beijing,Beijing 100083,China
2 Shunde Graduate School of University of Science and Technology Beijing,Guangdong 528399,China
3 China Academy of Information and Communications Technology(CAICT),Beijing 100191,China
4 Department of Information Engineering,North China University of Technology,Beijing 100144,China
Abstract: Dispersed computing is a new resourcecentric computing paradigm.Due to its high degree of openness and decentralization,it is vulnerable to attacks,and security issues have become an important challenge hindering its development.The trust evaluation technology is of great significance to the reliable operation and security assurance of dispersed computing networks.In this paper,a dynamic Bayesian-based comprehensive trust evaluation model is proposed for dispersed computing environment.Specifically,in the calculation of direct trust,a logarithmic decay function and a sliding window are introduced to improve the timeliness.In the calculation of indirect trust,a random screening method based on sine function is designed,which excludes malicious nodes providing false reports and multiple malicious nodes colluding attacks.Finally,the comprehensive trust value is dynamically updated based on historical interactions,current interactions and momentary changes.Simulation experiments are introduced to verify the performance of the model.Compared with existing model,the proposed trust evaluation model performs better in terms of the detection rate of malicious nodes,the interaction success rate,and the computational cost.
Keywordst: dispersed computing; trust evaluation model; malicious node; interaction success rate; detection rate
I.INTRODUCTION
1.1 Motivation
Dispersed computing connects all networked computation points(NCPs)to provide services for users in a way of collaboration and sharing between nodes[1,2].Compared with fog computing[3],mobile edge computing[4],the dispersed computing makes use of idle resources in the network to realize the new vision of joint computing.The dispersed computing breaks through the traditional fixed Client-Server (C/S) architecture.When computing tasks appear,the task nodes and the NCPs that complete the task establish a provisional cooperative relationship [5—7].However,due to the high openness of dispersed computing,it brings two important challenges to the development of dispersed computing: there is no trust foundation between nodes,which reduces the enthusiasm of nodes to participate in collaborative computing; malicious nodes infiltrate task assignments for the purpose of obtaining resources and data,which will lead to the risk of user data leakage.Therefore,in the face of this new computing paradigm,users still remain skeptical and cautious.They are worried that they will be attacked by malicious nodes and cause privacy data leakage.
In order to solve these two challenges,it is first necessary to establish a trust foundation in dispersed computing environment to provide a basis for cooperation between nodes and help identify interacting objects.At the same time,it protects user data security through a trust mechanism,ensures resource sharing among friendly nodes,and effectively prevents malicious attacks and misconduct.The development of trust evaluation technology provides the necessary guarantee for users to complete information interaction and data transmission in untrusted networks.The issue of trust management has become a unique and important part of network service security[8,9].This paper aims to establish a new trust evaluation model in the highly dynamic and heterogeneous dispersed computing environment.This model can provide a reliable basis for task nodes to choose to cooperate with unfamiliar NCPs in dispersed computing environment,and can efficiently and accurately identify malicious nodes.In addition,the proposed model is designed to ensure the stability of network services in the event of human error and management vulnerabilities,as well as cyber attacks and sabotage.
1.2 Related Works
Trust is the evaluation node’s expectation of the service capability or cooperation probability of the target node,and the quantitative expression of the evaluation node’s prediction of the target node’s cooperation probability is the trust value[10,11].Comprehensive trust computations mainly includes: direct trust and indirect trust(recommendations based trust)[12].The comprehensive trust calculation process is to integrate the effective information of multiple evaluation indicators to make a more objective evaluation of the target node.The main methods of trust evaluation include:Bayesian inference model,weighted average model,fuzzy logic,information entropy model,game theory,cloud model,machine learning model[13].Trust evaluation techniques are widely used in wireless sensor networks(WNSs),peer-to-peer(P2P)networks,Internet of Things Scenario,Social networks,which plays an important role in establishing trust relationships,detecting malicious nodes,and ensuring network security.
Cheet al.[14] proposed a lightweight trust management method based on Bayesian and entropy for WNSs,calculated the direct trust value of the evaluated node through Bayesian inference,and then judge whether the direct trust can replace the global trust according to the confidence level of the direct trust.This method aims at reducing the weight of the algorithm and replaces the global trust value with the direct trust to a certain extent,which is very one-sided and subjective.Alqahtani et al.[15]proposed a trust management algorithm for P2P platforms,which divided into multiple levels of trustworthiness based on the quality of narrator and content.Gao et al.[16] modeled the trust relationship between users in networking social service as a two-dimensional vector,and proposed a semi-ring based trust propagation and fusion model as the building block of the trust inference framework.Yan et al.[17]proposed a novel blockchain-based decentralized system for trust evaluation in social networks,called Social-Chain.Considering that mobile devices usually lack computing resources to handle cryptographically difficult computations,the authors design a lightweight proof-of-trust-based consensus mechanism (Proof-of-Trust,PoT) instead of Proof of Work(PoW).This method provides a new exploration for trust evaluation in large-scale node networks.Alhussain et al.[18]proposed a data network-based intelligent trust management system that leverages the power of neural networks to provide recommendations on the trustworthiness of each peer,further detecting malicious collectives and their suspicious group members.The experimental results show that the identification accuracy of malicious nodes of the system is 62%-97%.Li et al.[19]proposed a multi-dimensional trust model for large-scale P2P computing,which incorporates multiple factors to reflect the complexity of trust.In order to avoid the subjectivity of multiple factor weights,the weights are dynamically assigned through a combination of weighted moving average and ordered weighted average algorithm.
Trust assessment is a complex calculation,and the accuracy and objectivity of assessment require researchers to continuously explore and improve.Specific trust attributes,the selection of different attribute weights,and the definition of trust boundaries will all affect the results of trust assessment.Therefore,smarter schemes are needed to find these weighting factors and thresholds that define the confidence boundaries.Machine learning-based methods are an effective exploration.Some scholars have tried to design a new trust feature classification algorithm with machine learning method,classify the extracted trust features and combine them to generate the final trust value [20].Ma et al.[21] proposed a trust assessment method based on machine learning-enabled IoT devices,calculated node trust attributes digitally,and designed a new algorithm based on machine learning principles to classify the extracted trust features,and combine them to produce the final trust value,which is used in decision making.Machine learningbased trust assessment technology still needs to break through some important challenges,such as improving the accuracy of trust assessment,realizing fine-grained trust representation,feature extraction and automatic learning of algorithms,model scalability[22].
Trust assessment has been widely used in different application scenarios,and its main security goals can be summarized in two aspects.One is to establish a trust foundation,and then establish a cooperative relationship between nodes.In various scenarios,cooperation and sharing between nodes are inseparable,including file sharing and storage,distributed computing,and collaborative applications.Trust assessment provides a basis for this.The second is to identify malicious nodes and predict malicious attack behaviors to provide important guarantees for maintaining network security.Although these works have achieved some good results for specific scenarios,but the malicious nodes detection rate and the interaction success rate need to be further improved.To the best of our knowledge,at present,there is currently no dynamic trust assessment model specifically used for dispersed environments,and our work aims to fill this gap.
1.3 Main Contributions
In this paper,a dynamic Bayesian-based comprehensive trust evaluation model is developed for dispersed computing environment.In the calculation of direct trust,in view of the fact that the credibility of history records decays with time,a time sliding window is firstly designed to replace the long history records with new interaction records in turn.Further,a weight assign factor is constructed based on logarithmic function,which can dynamically assign different weights according to the interaction at different moments.This method can fully reflect the attenuation of interactive records over time,and improve the accuracy and timeliness of trust evaluation.In the calculation of indirect trust,a random screening mechanism is established to curb the collusion of multiple malicious nodes(mainly collusion with evaluation nodes to provide false reports).First of all,by deleting the maximum and minimum values in the recommended trust,the possibility of malicious nodes exaggerating or devaluing the trust value of the evaluation node is avoided.The recommended trust value is selected through a sine function interval.Due to the randomness of this method,the purpose of destroying the collusion of malicious nodes can be achieved.In the calculation of comprehensive trust,a dynamic update formula is proposed to improve the robustness of the evaluation method and tolerate the impact of unexpected failures on the results,which comprehensively considers current trust evaluation value,historical information and instantaneous change of trust value.Through dynamic updates,the impact of unexpected factors (such as network failures) on node trust evaluation can be reduced.Our main contributions are summarized as follows.
1) We propose a dynamic Bayesian-based comprehensive trust evaluation model in dispersed computing,which mainly includes: design a weight assign factor and a time sliding window;design a random screening mechanism based on sine function;design a dynamic update formulation.
2) We implement our model in NetLogo Platforms.The experimental results demonstrate the effectiveness and efficiency of our model.
The remainder of this paper is organized as follows.In Section II,a comprehensive trust estimation model presented for dispersed computing is presented.In Section III,the experimental simulations are carried out.Finally,in Section IV,the conclusion is introduced.
II.COMPREHENSIVE TRUST ESTIMATION MODEL
In this section,we mainly consider how to build a trust evaluation model in the task allocation process of dispersed computing.All nodes in dispersed computing can be divided into two categories: task nodes that publish tasks and NCPs that have idle resources to provide computing services.The task node assigns all tasks to NCPs through the task matching algorithm of the middleware.In order to effectively identify the malicious attack behaviors of NCPs using trust relationships to obtain services or resources,task nodes need to complete a trust assessment for cooperative nodes(NCPs)each time a task is assigned.
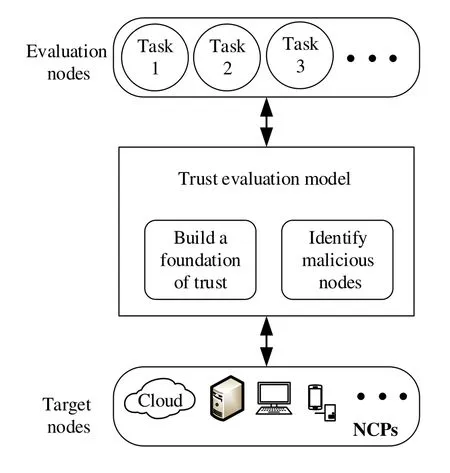
Figure 1.System model.
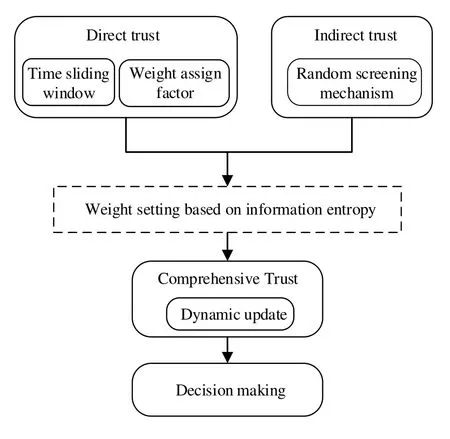
Figure 2.Flow graph of trust derivation.
In dispersed computing environment,task node is usually used as an evaluation node,and NCP that provide computing services is used as target node.The direct trust is the trust from task nodes to NCPs based on its previous cooperation experiences.Indirect trust is a combination of feedback and suggestions from other task nodes to the target NCP.The system model as shown in Figure 1.We aim to establish trust foundation and identify malicious nodes for dispersed computing environment through trust evaluation technology.
A new dynamic comprehensive trust estimation model will be proposed between task nodes and NCPs Figure 2 depicts the flow graph of trust trust evaluation.In this paper,we letxiandyjbe two nodes whereDTxi,yj(t) isyj’s direct trust aboutxi,ITxi,yj(t) isyj’s indirect trust aboutxi,andCTxi,yj(t)yj’s comprehensive trust aboutxi.Next,we will specifically give this paper the calculation method of the trust evaluation model.
2.1 Evaluation of Direct Trust
Assuming that each interaction has two results,the interaction is successful or the interaction fails.We userandsrespectively represent the number of occurrences of positive events and negative events.Then the calculation method ofrandsis as follows
whereTt0,t={ti|ti ∈[t0,t)}(tiis the moment when thei-th interaction is completed),and
In particular,in order to avoid interaction failures due to communication failures or network instability,a network detection function is added.After a period of interaction is completed,it is necessary to detect the operation of the network.If the interaction fails due to network failure,the interaction will not be recorded.Since the beta distribution function can be interpret equivalently the direct trust [15],then the statistical expectation of the direct trust of the nodexito the nodeyjis as follows:
The limitation of formula (3) is that it does not reflect the time decay of interactive recording[23].Because a record at any moment has the same weight,as time increases,the timeliness and accuracy of trust calculation will decrease.Therefore,we modify the formula(3).We first modify the time intervalTinto a sliding window
whereαis a positive constant.That is,we only pay attention to the interaction records that are away fromαat the current moment,and gradually ignore the influence of long-term information (the smaller theα,the more focused on the information close tot).Further,we introduce a time degradation factor based on a logarithmic function as follows
We get the updated direct trust value calculation formula
whereis called punishment factor.Obviously,for every additional failed interaction record,there is an exponential decrease in direct trust.
2.2 Evaluation of Indirect Trust
In the calculation of indirect trust,we only select task nodes as recommendation nodes.Assuming that there arektask nodes denoted asST={x1,x2,···,xk},then the set of recommended nodes can be expressed asSre={xl|l=1,2,···,i −1,i+1,···,k}.First,we calculate the direct trustDTl,j(t) of the recommended nodexl ∈Sretoyj.Then we need to determine the weightωlof each recommended node as follows
The reliability of the recommended node plays an important role in the evaluation of indirect trust [24].If a recommending node maliciously raises or degrades the trust value of the target node for its own purposes,and sends a false report to the evaluation node,it will have a serious impact on the final trust evaluation of the target node [25].In particular,if multiple recommended nodes form an alliance and provide false reports with a common purpose,a collusion attack will be formed.This will affect the reliability of the overall trust evaluation mechanism,which in turn will affect the performance and security of distributed computing.In order to reduce the impact of the bad mouthing attack of a single node and the collusion attack of multiple nodes on the accuracy of trust evaluation,we must propose a method that can mitigate and prevent false reports.
In this paper,we introduce a random deletion mechanism to mitigate recommended nodes with evaluation node collusion.We construct a sine function-based non-negative piecewise function as following
where
andβis a positive number.We arrangekrecommend trust valuesDTxl,yj(t)in order of magnitude
whereν1,ν2,···,νk−1is a permutation of 1,2,···,i −1,i+1,···,k.Letting the set
whereη < k/2 is a positive integer number.Then we can getS={νi|f(vi)≥0,νi ∈S3}.We only select the elements in the setSas effective recommendation nodes,then the indirect trust of the evaluation device is calculated as follows
The structure of the setSplays an important role in preventing bad mouthing attack and collusion attack:
・ By removing the highest value and the lowest value(one or more,determined by the value ofη),the probability of a single node or multiple nodes providing false reports is reduced.False reports are often maliciously raising or degrading the true trust of the target node,and the setSis precisely to prevent false reports by removing suspiciously high or too low recommendation values.
・ When selecting effective recommended values,a sine function based set is constructed to achieve the purpose of decentralized point selection and random point selection.This reduces the possibility of successful conspiracy by malicious nodes.
2.3 Evaluation of Comprehensive Trust
We need to determine the relative importance of the two parameters of direct trust and indirect trust to the comprehensive trust calculation,that is,determine their weight.In order to avoid the subjectivity of artificially setting weights,we adopt a method based on information entropy.Information entropy can reflect the degree of disorder of the information,so the weight can be modified according to the difference between direct and indirect trust to achieve adaptive weight distribution
The entropy of direct trust (indirect trust) adopts the trust degreeDTxi,yj(t) (ITxi,yj(t)) and the corresponding suspicion 1−DTxi,yj(t)(1−ITxi,yj(t))of the target node measurement.The entropy of direct trust and indirect trust are calculated by the following formulas
Then we can separately define the entropy based weights of direct trust and indirect trust as following
Moreover,it follows from(6),(12),and(14),we have
Due to the dynamics and instability of the decentralized computing environment,the trust evaluation of nodes has brought challenges.A stable trust evaluation mechanism should be able to cope with the impact of sudden changes in node behavior(some unexpected situations) on trust evaluation.In order to make the trust evaluation method more robust,we propose a dynamic update method for the formula(15)as follows
whereγi ∈(0,1) andγ1+γ2+γ3=1.Note that the updated trust value contains three components of information.The first component reflects the role of current trust value.The second component (integral term)reflects the contribution of the target node’s trust value in the pastαtime.The third component(derivative) reflects the impact of the sudden changes in the trust value of nodes in a small neighborhood at timet.Different from the method in[26],we only take a time period close to timetin the integral term,instead of taking all the historical information.If the lower limit of the second integral term starts from the initial momentt0,the computational complexity will continue to increase over time.In fact,the farther away from the current moment,the lower the value of its information.Therefore,our method is more time-sensitive.
Compared with formula (15),the dynamically updated trust value(16)has two advantages.
・ The formula (16) comprehensively considered three factors: the current trust evaluation value,historical information and the instantaneous change of the trust value.At the same time,noting the decay of historical information value and the complexity of calculation,we only take the most recent valid time at the current moment.Compared with formula(15),the formula(16)reflects stronger timeliness.
・ Formula (16) can not only avoid the impact of sudden events on the trust value,but also enhance the sensitivity to current events.
III.EXPERIMENTAL SIMULATION
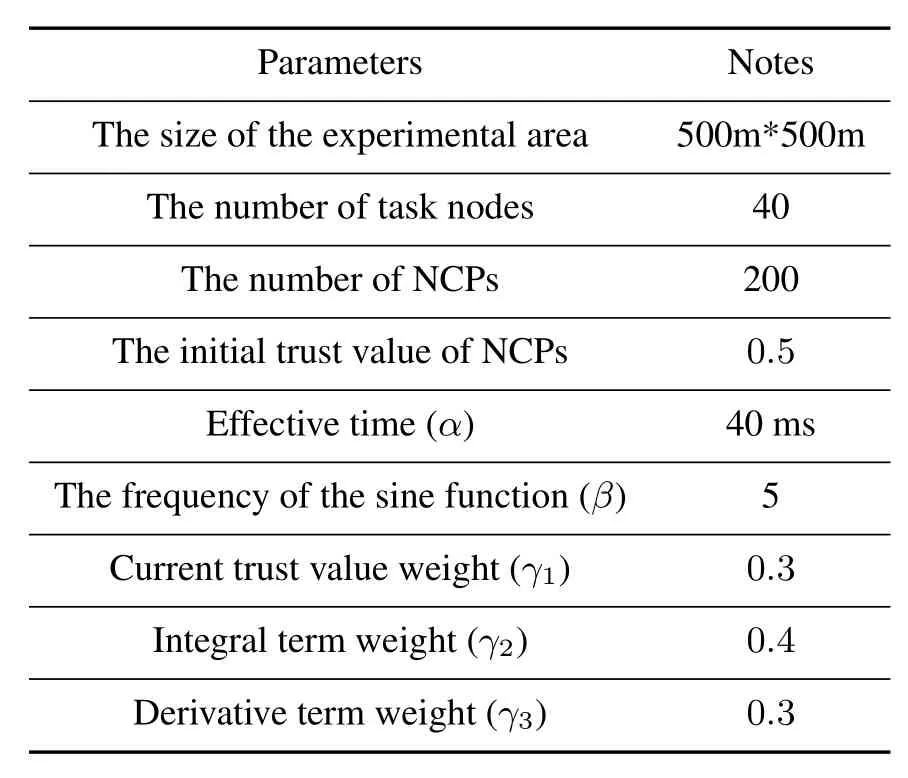
Table 1.Simulation parameters.
In this section,performance and security assessments of proposed model are validated on NetLogo.On the NetLogo platform,two types of nodes (task node as evaluation node and NCP as target node)are generated randomly in the area 500m×500m.All target nodes are assigned to evaluation nodes randomly.Each evaluation node stores the trust value of all target nodes that have interacted with itself.The simulation parameters are listed in Table 1.Two types of experiments are set up.First,the performance of proposed model is verified in terms of computational cost and malicious node detection rate.Then,the proposed model is compared with the existing works,dynamic trust evaluation model (DTEM) [27],decision tree algorithm(TEUC)[23],typical reputation-based framework for sensor networks(RFSN)[28].
3.1 Performance of Proposed Model
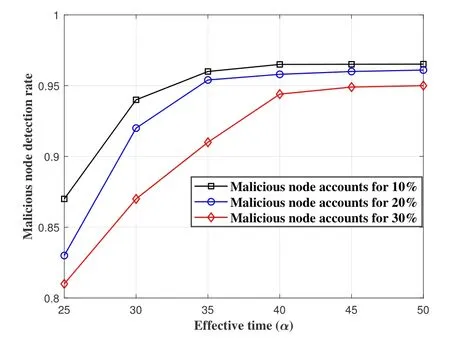
Figure 3.The detection rate of malicious nodes under different the effective time α.
Before evaluating the performance of the model,it is necessary to discuss the influence of key parameter values on the performance of this model.There are two key parametersαandβin our model.Due to the symmetry of the sine function,the value ofβin the indirect calculation will not affect the selection of valid data,which can prevent malicious collusion and ensure that the final evaluation result tends to a stable value.The parameterαrepresents the effective time for recording the interaction.Whenαis larger,the required calculation cost is larger; when the value ofαis too small,it may lead to insufficient collection of effective information,resulting in inaccurate evaluation.We set up a comparative experiment,keeping other parameters unchanged,αincreases from 25 ms to 50 ms (5 ms each time) to observe the change of the detection rate of malicious nodes with respect to the effective timeα.Figure 3 depicts the change of the malicious node detection rate with respect to the effective timeα.Whenαis less than 40 ms,the detection accuracy increases significantly;whenαis greater than 40 ms,there is no significant change in the detection accuracy.That is to say,historical information 40 ms ago has little effect on the accuracy of our model evaluation.
Then,the experiments are designed in terms of malicious node detection rate and computational cost to test the performance of our model.First,assuming that there are two trust evaluation models,one of them is the model proposed in this paper,and the other is the comparison model (Model-II).In contrast,in Model-II,there is no random screening mechanism.In its indirect trust value calculation,the indirect trust values of all recommended nodes are adopted with the same weight.In this experiment,5%,10%,15%,20%,25%,and 30% of malicious nodes are added respectively.The malicious node recognition rates of the two models are compared as shown in Figure 4.Obviously,the malicious node detection rate of proposed model is significantly higher than that of Model II.This is because,in the screening mechanism,high and low malicious recommendations are first excluded,which reduces the possibility of collusion between the target node and the evaluation node,and increases the accuracy of the trust evaluation.At the same time,valid recommended values is taken randomly according to a certain interval construction method,which further reduces the possibility of collusion.The conclusion shows that the proposed model has excellent performance in terms of recognition accuracy as well as blocking malicious node attacks.
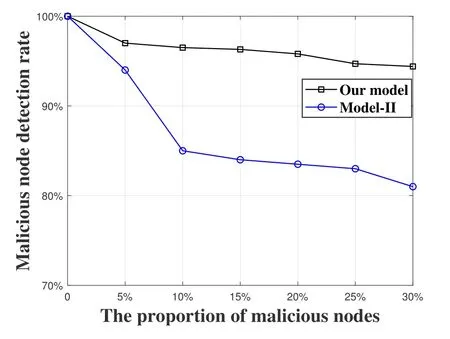
Figure 4.Comparison of the malicious node detection rate.
Similarly,the effect of sliding window and temporal degradation factor on the computational cost of the model can be verified.This model is compare with the model not having time sliding window and time degradation factor(Model-III).The results are shown in Figure 5.In the initial stage of the experiment,the two models use the same length of interaction records,so the computational cost is similar.However,as the number of interactions increases,the proposed only counts interaction records within the time period[t,t+α],while Model-III counts all interaction records.This will result in a cumulative increase in the computational cost of Model-III as the number of interactions increases.The time degradation factor is designed to further improve the sensitivity of the evaluation model to recent interaction records,thereby improving the accuracy of trust evaluation and reducing computational cost.
3.2 Comparison with Existing Work
In this subsection,the proposed model is compared model with existing work in terms of malicious node detection rate,interactive success rate,and computational cost.These three factors are important indicators to measure the performance of a trust evaluation model.
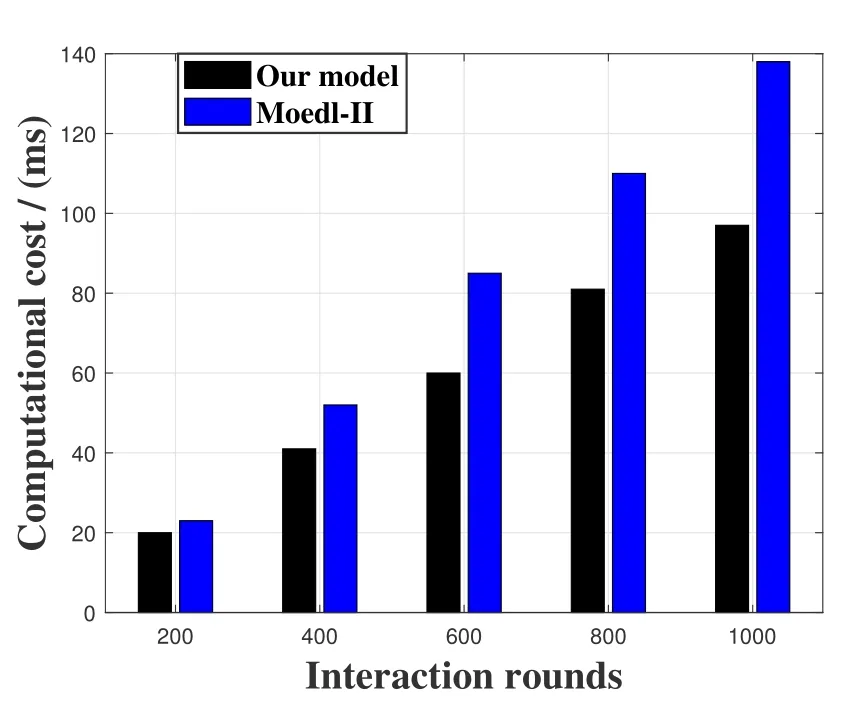
Figure 5.Comparison of computational cost.
3.2.1 Comparison of Malicious Node Detection Rate In the DTEC and the TEUC,the goal of preventing malicious attacks is mainly achieved by adjusting the reward factor and the penalty factor,which are improved versions of RSFN.In addition to the penalty factor,our model mainly introduces a random screening mechanism in the indirect trust value calculation,which greatly avoids the possibility of collusion attacks by malicious nodes.In contrast,the proposed model has the advantage of being more proactive in defending against attacks.The comparison of malicious node detection rate under four different models are realized as shown in Figure 6.As the proportion of malicious nodes increases,the detection rates of malicious nodes in the four models all decrease.The proposed model significantly outperforms the other three models.In the case of malicious nodes accounting for 30%,its detection rate can still reach 94.4%.
3.2.2 Comparison of Interaction Success Rate
The comparison of interaction success rate under four different models is illustrated as shown in Figure 7.The interaction success rate refers to the proportion of NCPs that successfully complete task in a task allocation,which is a key aspect of measuring DCOMP performance.In this experiment,the proportion of malicious nodes is fixed at 20%.In the proposed model,a time window and Logarithmic attenuation function are introduced to quantify the dynamic changes in direct trust over time,random screening mechanism is proposed to solve the problem of malicious recommendation problem in indirect trust computing.Compared with the other three models,the proposed model has a higher interaction success rate.
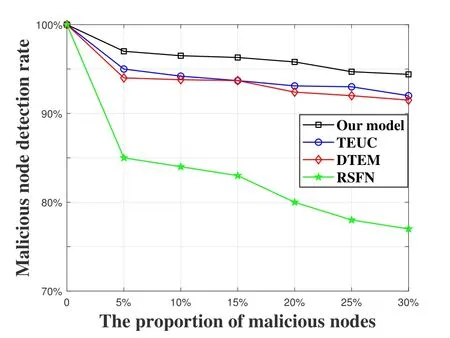
Figure 6.Comparison of malicious node detection rate under four different models.
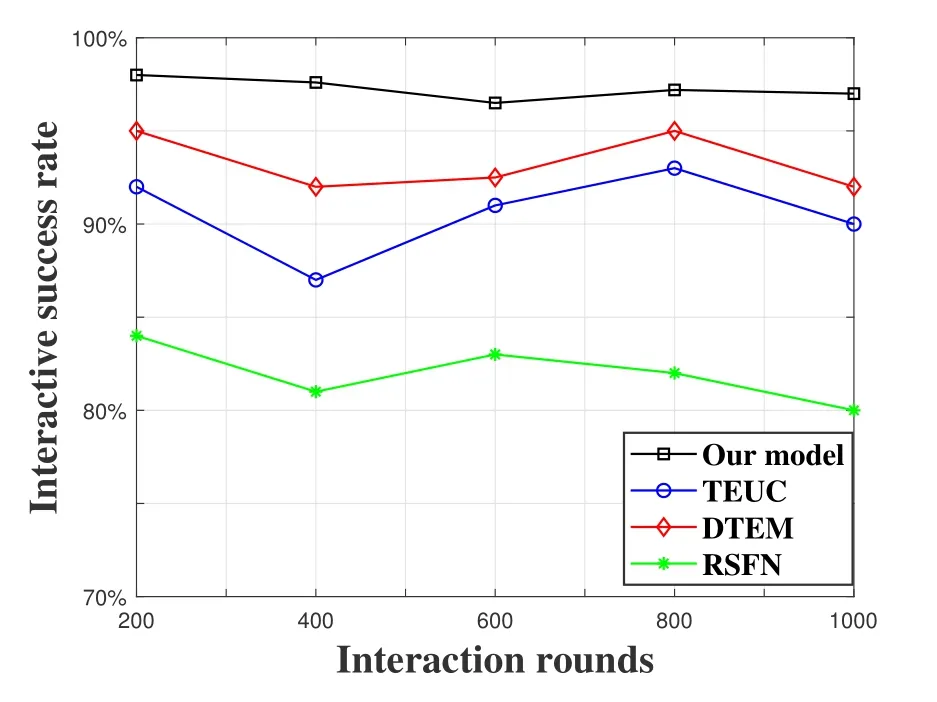
Figure 7.Comparison of interactive success rate under four different models.
3.2.3 Comparison of Computational Cost
The comparison of computational cost under four different models is described is shown in Figure 8.The computational cost of RSFN is significantly higher than that of the other three models,because the other three models all design sliding windows to gradually discard invalid historical records,while RSFN takes all interaction records into account in each calculation.As the number of interactions increases,the computational cost of RSFN will grow faster and faster.The computational cost of the proposed model is lower than that of TEUC and DTEM,mainly reflected in the random screening mechanism of indirect calculation,which can not only alleviate the collusion of malicious nodes,but also reduce the computational cost.
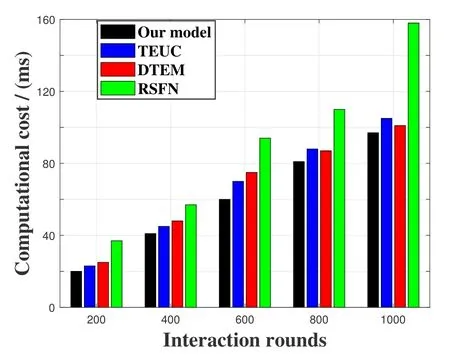
Figure 8.Comparison of computational cost under four different models.
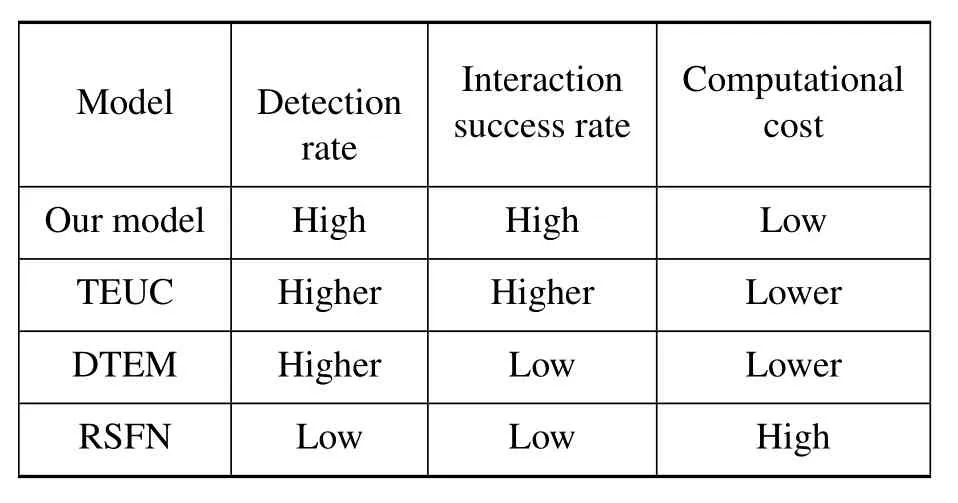
Table 2.Comparison of existing work in terms of performance.
The experiments in the above three subsections are quantitatively compared with the existing work in terms of the detection rate of malicious nodes,the interaction success rate,and the computational cost.The advancement of our model can be summarized as shown in Table 2.
IV.CONCLUSION
In this paper,a novel trust evaluation model is proposed for dispersed computing environment,in which task nodes serve as evaluation nodes and NCPs serve as target nodes.In the calculation of direct trust,a logarithmic decay function and a time sliding window are introduced to solve the problem of the dynamic change of trust value with time,which improves the accuracy of trust evaluation.In the calculation of indirect trust,a random screening mechanism is innovatively proposed,which can reduce the possibility of single attack and collusion by malicious nodes as well as reduce computational cost.In particular,some unstable network failures will also affect the accuracy of node trust assessment in a highly dynamic dispersed computing environment.Therefore,based on the historical information,current information,and instantaneous changes,a method to dynamically update the comprehensive trust value is proposed.In this way,the influence of external fault factors on the comprehensive trust evaluation of nodes is avoided,thereby improving the detection rate of malicious nodes.Through the simulation experiments on the NetLogo platform,the performance of the model is verified in terms of malicious node detection rate,interaction success rate and computational cost.Compared with existing trust evaluation models,the proposed model shows good performance in terms of the detection rate of malicious nodes,the interaction success rate,and the computational cost.As a future work,we will expand the performance evaluation indicators of the model,and deeply study the impact of our model on the throughput,energy consumption and other aspects of the dispersed computing network.Further,the emphasis will be laid on research on trust evaluation-based security threat warning system in dispersed computing environment.
DECLARATION OF COMPETING INTEREST
The authors declare that they have no conflict of interest concerning the publication of this manuscript.
ACKNOWLEDGEMENT
This work was supported in part by the National Science Foundation Project of P.R.China (No.61931001),the Fundamental Research Funds for the Central Universities under Grant(No.FRFAT-19-010)and the Scientific and Technological Innovation Foundation of Foshan,USTB(No.BK20AF003).
- China Communications的其它文章
- Quality-Aware Massive Content Delivery in Digital Twin-Enabled Edge Networks
- Edge-Coordinated Energy-Efficient Video Analytics for Digital Twin in 6G
- Unpredictability of Digital Twin for Connected Vehicles
- Endogenous Security-Aware Resource Management for Digital Twin and 6G Edge Intelligence Integrated Smart Park
- Digital Twin-Assisted Knowledge Distillation Framework for Heterogeneous Federated Learning
- Design and Implementation of Secure and Reliable Information Interaction Architecture for Digital Twins

