Design and Implementation of Secure and Reliable Information Interaction Architecture for Digital Twins
Qian Wang,Wanwan Wu,Liping Qian,Yiming Cai,Jiang Qian,Limin Meng
College of Information Engineering,Zhejiang University of Technology,Hangzhou 310023,China
Abstract: In order to improve the comprehensive defense capability of data security in digital twins(DTs),an information security interaction architecture is proposed in this paper to solve the inadequacy of data protection and transmission mechanism at present.Firstly,based on the advanced encryption standard(AES) encryption,we use the keystore to expand the traditional key,and use the digital pointer to avoid the key transmission in a wireless channel.Secondly,the identity authentication technology is adopted to ensure the data integrity,and an automatic retransmission mechanism is added for the endogenous properties of the wireless channel.Finally,the software defined radio (SDR) platform composed of universal software radio peripheral (USRP) and GNU radio is used to simulate the data interaction between the physical entity and the virtual entity.The numerical results show that the DTs architecture can guarantee the encrypted data transmitted completely and decrypted accurately with high efficiency and reliability,thus providing a basis for intelligent and secure information interaction for DTs in the future.
Keywordst: digital twins,AES encryption,digital pointer,identity authentication,automatic retransmission,SDR
I.INTRODUCTION
Digital twin(DT)is a multi-dimensional dynamic virtual model established for physical entities by synthesizing the knowledge of various disciplines in the digital space [1].Virtual entities with the same attributes,behaviors,and rules as physical entities are constructed through data interaction,which can be used to detect the dynamics of physical entities in realtime and facilitate further analysis and calculation.The interaction systems of DTs are widely used in different areas such as industrial manufacturing,marine Internet of Things (IoT),smart aerospace and transportation,etc.,as shown in Figure 1 [2—5].And the information interaction architecture is the most fundamental infrastructure for DT systems,which can realize the real-time interaction between the physical entity and the virtual entity and must meet the requirements of low delay,high reliability and high security.The current research on DTs mainly focuses on theoretical modeling,key technologies,and specific applications [6—8],whereas the serious security issue brought by the data interaction in DTs is ignored.DT is like a double-edged sword,which facilitates the construction and management of intelligent manufacturing systems,but also the intrusion and attack of hackers,viruses,etc.With the popularization of industrial intelligent systems such as DTs,attacks against industrial equipments and softwares are increasing fast.DTs have become the key target of malicious intrusion,and the open-source channel for interaction between entities has become a weak link in security protection work[9,10].
Figure 1.Applications of digital twin interaction.
With the rapid expansion of the IoT,edge computing,and 5G networks,information security incidents have occurred frequently[11].For example,the most famous one is the “Stuxnet” virus incident in Iran in 2010[12],which caused a serious delay in power generation.And the Venezuela power system was attacked in 2019,leading to a large-scale power outage[13].In traditional networks where data is mostly transmitted in the form of plaintext,attackers can implement various attack means,such as eavesdropping,interference,tampering,forgery,etc.Moreover,the mobility of wireless terminals and the instability of network architecture bring a challenge to the transmission reliability,and even a huge threat to our life and property security.Nowadays,DTs are considered to be the key technology to achieve a deep integration of information and physical entities,and an effective way for the construction of intelligent manufacturing.Nevertheless,the application of DTs will certainly bring a lot of security risks.The ITU-T sector is drafting relevant security standardization,which categories threats and requirements into four groups [14].Therein,the most urgent one is to solve the interaction security between the twin entity and the physical entity.In this way,how to improve the safety,reliability and efficiency of data interaction is the main concern in our research.Combing with the security characteristics in information transmission,this paper thus proposes a comprehensive information security defense architecture for DTs.
II.RELATED RESEARCH
With the growing development in DT technologies nowadays,the security issue of DTs has attracted a lot of attention in both academics and industries.Gehrmann et al [15] proposed a DT-based industrial security architecture of automation control system,to illustrate the use of the DT replication model in data control of critical security processes.Seay [16] established a DT platform to quickly identify the network attacks and make timely defense through realtime simulations.So far,many studies have been done on the model construction and visual monitoring of DTs,but few focus on the security issue of information interaction in the DTs.In order to ensure the security of network transmission,data encryption is undoubtedly an effective method.For example,advanced encryption standard(AES)and triple data encryption algorithm(3DES)were simulated on the real platform[17,18],and the AES is proved to have better performance for a large amount of data and the advantages of fast encryption speed and low computational overhead.However,the security of AES encryption depends on the symmetric key.If the issue of the key distribution can not be well solved,the problem of data leakage will occur.Considering this,[19,20]carried out the research on asymmetric encryption.Among them,the rivest-shamir-adleman (RSA) algorithm uses the asymmetric private and public keys combined with the factorization of large numbers to greatly improve the transmission security.However,due to the complexity and low efficiency,the RSA algorithm is only suitable for the encrypted transmission of a small amount of data.Besides there is a phenomenon that the ciphertext is easily tampered or forged by a third party during the transmission process.For that reason,[21] proposed an encryptiondecryption scheme with data verification,which verifies the data integrity by calculating the ciphertext and key hash value.However,this method brings the collision when different ciphertexts have the same hash value after one calculation.Therefore,we need a data encryption scheme with high encryption efficiency,secure key distribution,and effective resistance to both active and passive attacks.
In addition,in order to improve the reliability of data transmission affected by the instability of network structure,an error control coding with feedback retransmission strategies is mostly used to correct errors in transmission[22,23].As is well known,automatic repeat request(ARQ)is a group of error control protocols for transmission over noisy or unreliable communication links.At present,the existing ARQ protocols include stop and wait ARQ (SW-ARQ),go-back N frame ARQ(GBN-ARQ),selective repeat ARQ(SRARQ),and hybrid ARQ (HARQ) [24].Specifically,the SW-ARQ is widely used in the physical layer,in which the sender waits to receive the feedback from the receiver before sending the next frame.This causes is a long delay so that the efficiency is very low.The GBN-ARQ and SR-ARQ generally used in the upperlayer protocol do not need to wait for the feedback and can send the data continuously,which increase the spectrum efficiency.More importantly,the HARQ is as the current research hotspot combines the forward error correction(FEC)and ARQ to improve the transmission reliability,which is mostly used in many practical applications.However,due to the high computation complexity or the difficult hardware implementation,a secure and reliable data transmission architecture is imperative for information interaction in DTs.The main contributions of our work are summarized as follows:
•The secure data transfer protocol based on the digital pointer and the AES encryption is proposed in consideration of the current era characteristics of big data.Specifically,at the transmitter side,the ciphertext through the AES encryption is combined with the hash-based message authentication code (HMAC).It is encoded by the Base64,and the corresponding digital pointer is added to the data header before sent to the wireless channel.At the receiver side,the digital pointer is first identified and used to obtain the key from the keystore.Then the HMAC is verified to check the integrity of the encrypted data.After successful authentication,decryption is performed to obtain the final plaintext.The designed secure transmission protocol can avoid the transmission of keys in wireless channels and ensure the efficiency of the data transfer.More importantly,the HMAC significantly reduces the collision after two Hash calculations.
•The automatic retransmission mechanism combined with FEC coding,i.e.,HARQ is used to improve the transmission reliability in a lossy wireless environment.Specifically,real-time packet loss retransmission mechanism is adopted,where the data content is subcontracted and sent in groups to reduce the link overhead in response.And the cyclic redundancy check(CRC)-16 in combination with Reed-Solomon(RS) coding is used to solve the interference issue and enhance the ability of error correction.The designed reliable transmission protocol solves the problems of packet error,packet loss and repeat transmission,which can effectively improve the transmission efficiency.
•This paper builds an experimental DT information interaction system through the software defined radio(SDR)platform to verify the implementation of the designed scheme.The SDR platform combines the hardware USRP with the software GNU radio,which breaks through the hardware limitations and also makes the simulation results more intuitive and practical.Last but not the least,the system simulation verifies the efficiency,integrity,security and reliability of the proposed information interaction architecture in DTs.
III.DATA SECURITY AND RELIABLE INTERACTION SCHEME DESIGN
3.1 Overall Design
The data interaction process in the DTs is the wireless information exchange and control technology between the virtually designed twin model and the remote physical device.Undoubtedly,the interaction will bring security issues,such as cracking,intrusion,tampering and monitoring,due to the long-distance internet connections and complex mobile devices.Thus,the security mechanism is imperative to design for DT systems,which is normally divided into two types in wireless communications.One is the data encryption mechanism based on computing security,and the other is the physical layer security mechanism based on information theory[25].
For computing security,the AES encryption algorithm is used in our protocol design,due to its advantages of high efficiency and low cost.Even though the symmetric encryption AES algorithm is widely used,it has the security problem of key distribution.That is,a third party that obtains the encryption key,can decrypt all the ciphertext,leading to a disastrous consequence.To solve this issue,some researchers transmit the key by using an asymmetric encryption algorithm or directly connect the key by private negotiation.But this requires the exchange of control instructions between the sender and receiver,leading to a large interaction overhead.Therefore,in order to reduce the overhead,the protocol designed here prompts the recipient of key information by means of digital pointers.That is,recipients can search for the key in their own keystore based on the digital pointer.Users without the keystore cannot obtain the key information.Moreover,the keystore can expand traditional keys and enable the use of different keys frequently,since the same key used for too long will increase the possibility of leakage.In addition,the identity authentication technology is added to solve the issue that attackers may forge and tamper with ciphertext data.That is,the HMAC is considered by comparing the Hash values at both ends to check the integrity and validity of ciphertext data.
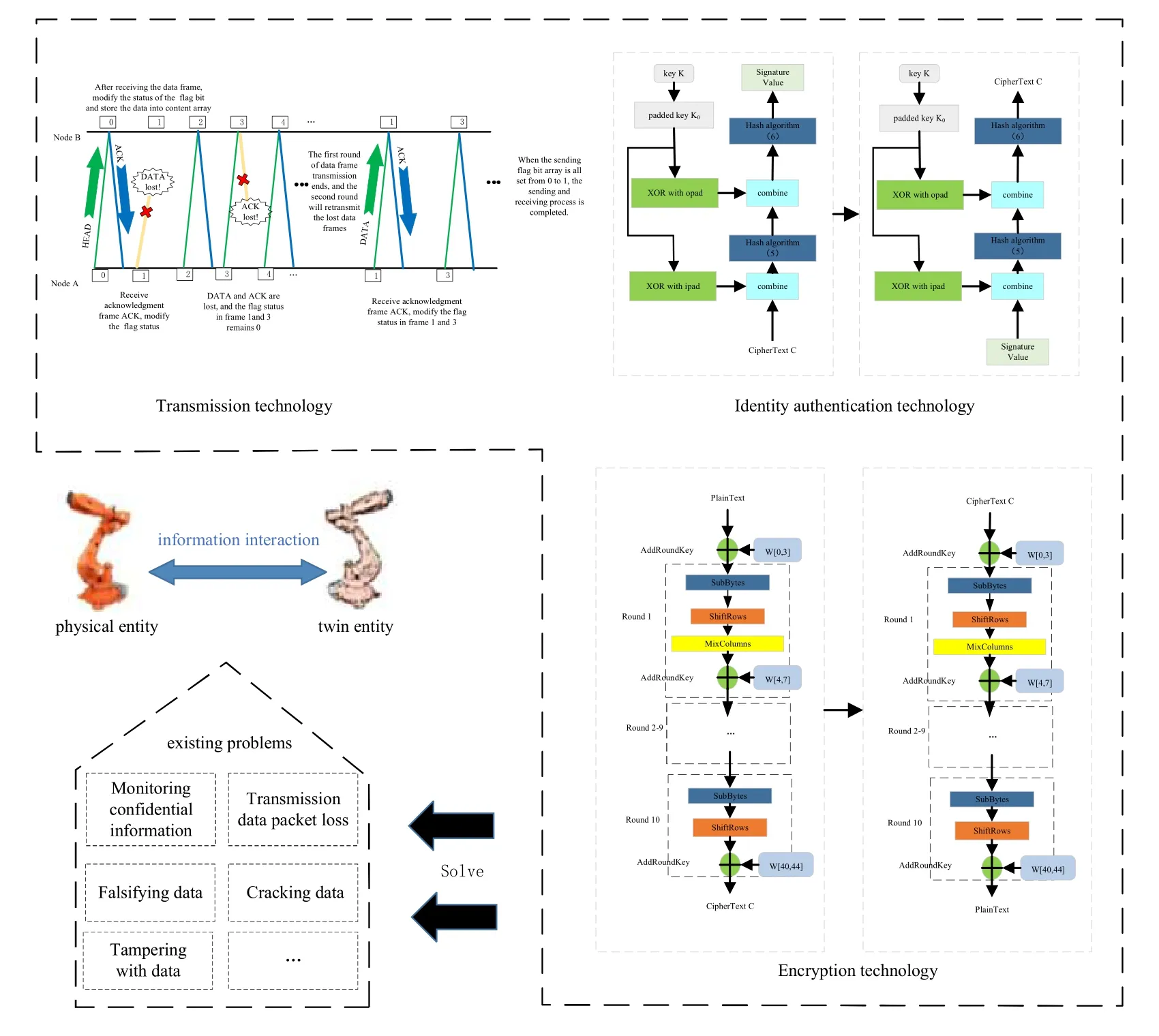
Figure 2.Data security interaction model for digital twin.
Note that the data security provided above is done at the upper layer of the protocol stack.In addition to computing security,the physical layer security mechanism based on information theory has also been shown to achieve excellent security performance,by designing a reliable data transmission system based on the imperfect characteristics of the physical layer [26].For example,noise interference and channel fading,which are normally considered as damages in wireless transmission,can be used to hide information from potential eavesdroppers [27].The physical layer security includes many aspects.For example,the multipleinput multiple-output technology can reduce the probability of eavesdropping,and the error control coding can be used to improve the security.Here,we apply the HARQ technique with RS-based FEC coding to achieve the bit error correction and data confidentiality.The main idea is to make full use of the imperfect characteristics of wireless channel,e.g.,noise,fading and interference,to prevent eavesdroppers from receiving the effective information and thus ensure the information confidentiality.And the channel code is designed adaptively based on the varying channel state information to achieve the error correction.Therefore,both the reliability and security of wireless data transfer are improved using the RS-based HARQ from the perspective of information theory.
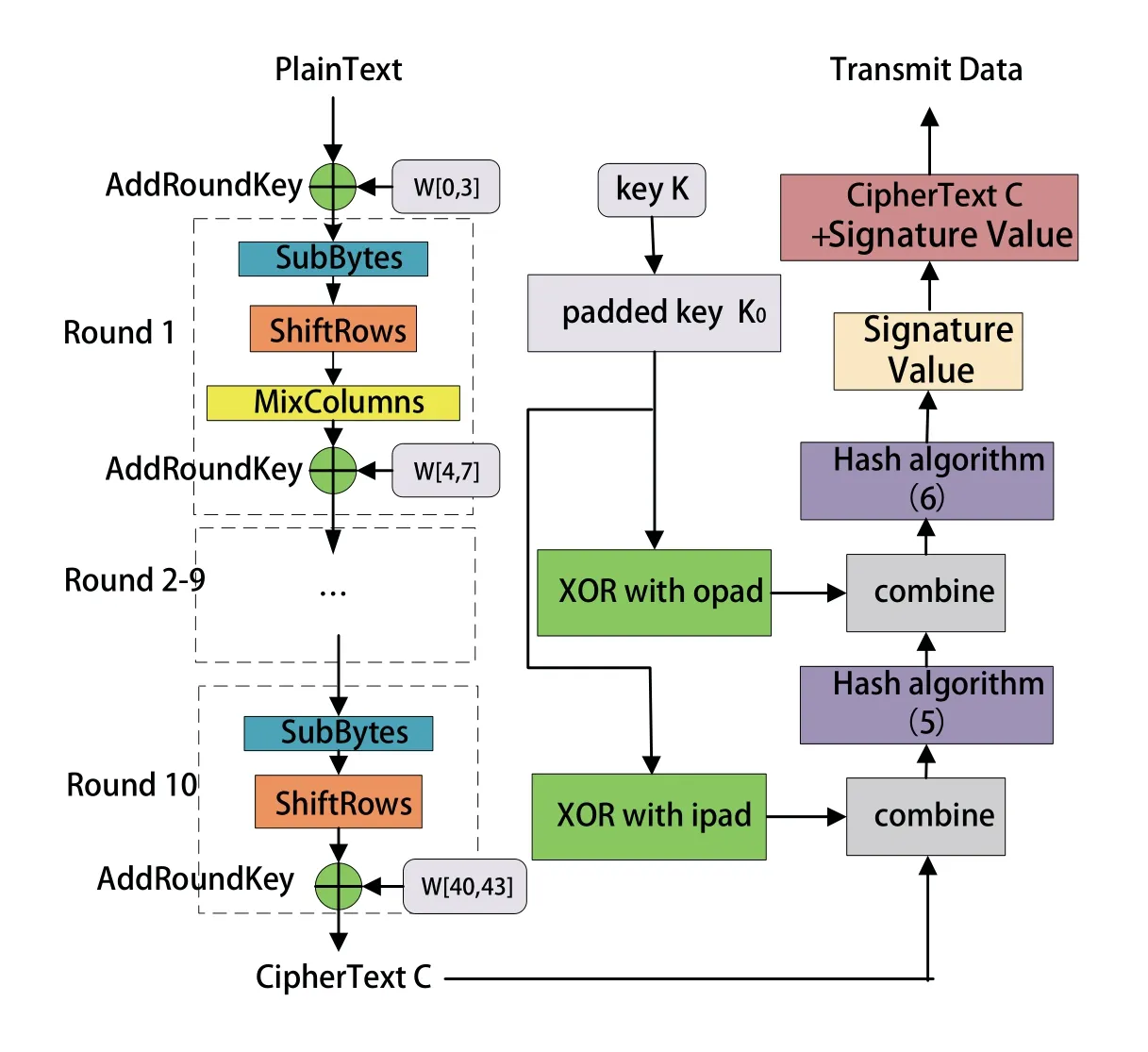
Figure 3.Encryption and authentication flow chart.
In brief,the data security interaction model for DTs is summarized in Figure 2.The design of this secure and reliable transfer protocol can guarantee both physical layer security and computing security.It integrates encryption,authentication and reliable transmission,enhancing the defense capability structurally.The combination of the encryption technology and the error control coding meets the secure transmission requirements for information interaction in DTs.
3.2 Secure Data Transmission Based on AES Encryption and Digital Pointer
This section discusses the scheme combining AES encryption algorithm and HMAC identity authentication technology.The AES algorithm used here is AES-128,which is an iterative encryption algorithm with 10 iterations.The initial round contains only AddRound-Key,and the final round does not contain MixColumn.And HMAC is a hash-based authentication technology,which can avoid collisions after two hashing calculations and ensure the data integrity while verifying the sender identity.In this way,the former encryption can ensure the security of data content,and the latter can ensure the security of data system[28].The specific operation flow chart is shown in Figure 3.
The specific AES encryption and identity authentication algorithms are described as follows.
1)Key generation
The 128-bit key denoted asKin Figure 2 consists of a 4×4 matrix in bytes,and each column of 4 bytes is arranged into vectorsw[0],w[1],w[2],w[3],which are used for AddRoundKey in the first round.Then thewarray is expanded tow[44]in the following way.
Ifiis a multiple of 4,it is calculated as
otherwise,it is determined by
where⊕denotes the XOR operator,andTis a special operator,including byte loop,byte replacement and round constant XOR operation.In detail,T(w[i −1])means that in the column vectorw[i −1],one first loops up the four bytes inside,then uses the S-Box for replacement,and finally XORs the four bytes inside with a round constant.
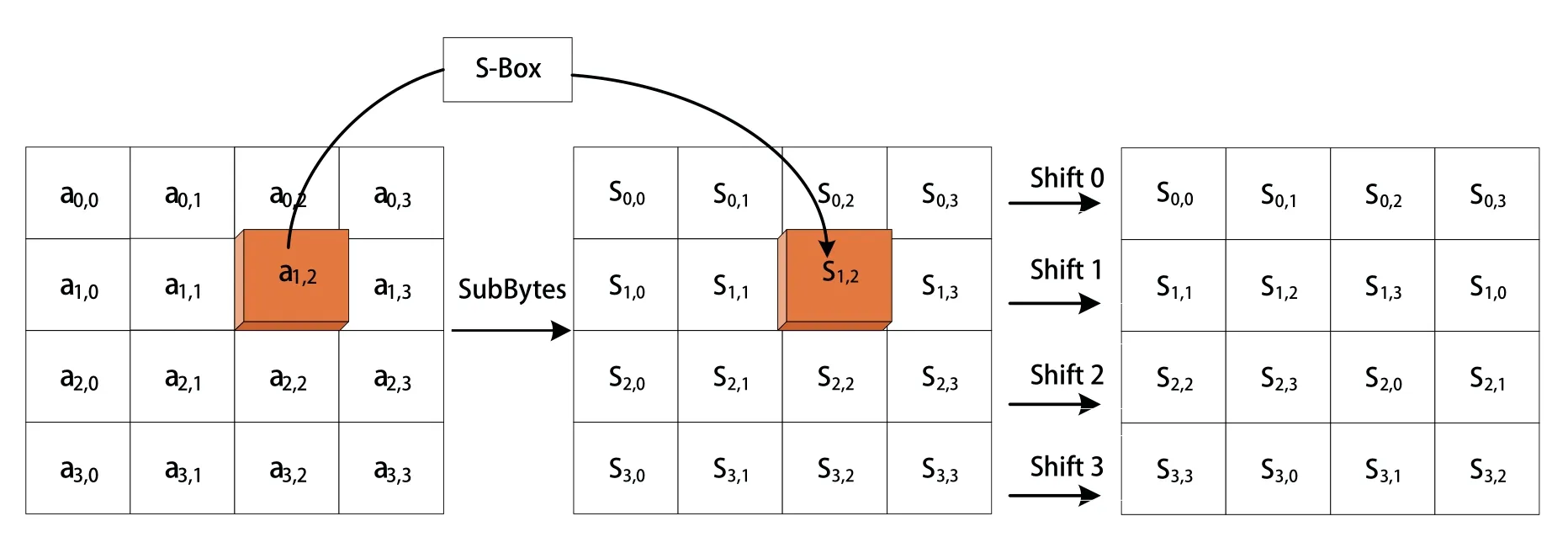
Figure 4.Conversion tables of SubBytes and ShiftRows.
2)Data encryption
(1)SubBytes
The 128-bit plaintext also forms a 4×4 state matrix in bytes{aij}(0≤i,j ≤3),and each byte is mapped to a new byte through the S-Box defined by the AES encryption algorithm,as shown in Figure 4,whereSij(0≤i,j ≤3)represents the value of bytes after SubBytes.The essence of S-Box is affine change in finite field GF(28),so the correlation between input and output values of the S-Box is low,showing a non-linear relationship[29].
(2)ShiftRows
After SubBytes,the state matrix circulates to the left in byte units,and the corresponding rows from top to bottom move to the left by 0,1,2 and 3 bytes,as show in Figure 4,which can be expressed as
whereS′ij(0≤i,j ≤3)represents the value of bytes after ShiftRows.Each byte of the original matrix is distributed in different columns,which has a great diffusion effect on the subsequent MixColumns transformation.
(3)MixColumns
MixColumns transformation is realized by matrix multiplication.The state matrix after ShiftRows is multiplied by the fixed matrix to obtain the mixed state matrix,that is
where(0≤i,j ≤3)represents the result of Mix-Columns.The multiplication and addition here are binary operations defined in the finite field GF(28).
(4)AddRoundKey
AddRoundKey is that each column of the state matrix performs an XOR operation with the corresponding key vectorw[i],w[i+1],w[i+2],w[i+3](0≤i ≤40),and the key of each round is different,as shown in Figure 3.
3)Information Signature
The information signature means calculating the HMAC.First,padding the keyKwith 0 creates a stringK0of length B.Then we xorK0with the string ipad for B times,and combine with the ciphertextCto calculate the hash valueα,as shown in Eq.(5).Further,we xorK0with the string opad for B times,and combine withαby the hash operation to get the final HMAC valueβ,as given in Eq.(6).That is,we have
where,Hdenotes the SHA-1 algorithm.The main function is to generate a 160-bit (20-byte) hash value called a message digest,which can verify the data integrity[30].
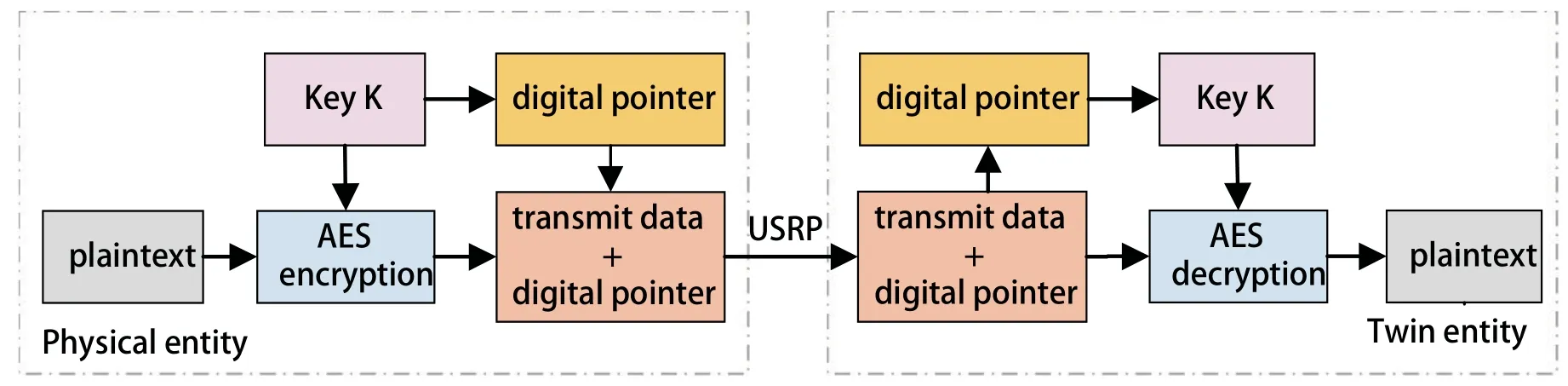
Figure 5.Encryption and decryption process diagram based on digital pointer and AES algorithm.
The ciphertextCis combined with the signature value to obtain the transmit data sent to the wireless channel.At the receiver side,the corresponding identity authentication and AES decryption are performed to recover the data.The inverse process is similar to the process of AES encryption and information signature,which is not described here.
Modern cryptography considers that any encryption algorithm is open,and the security depends on the key,so the confidentiality of the key is particularly important.Once the key is stolen by the attacker,the secret information will be stolen.So it is impossible to transfer keys over channels in order to guarantee the network security.In this paper,we use the keystore to expand the symmetric key to 512 keys and sort them by number.And the sender and receiver can synchronously update the keystore in real time to improve the data security.Furthermore,the receiver is guided to identify the key number by the digital pointer to avoid the key transmission in the wireless channel.This means that even if the third party attacker intercepts ciphertextC,the probability of obtaining information about plaintextMis 0,i.e.,P(M,C)=0.It is also worth emphasizing that the added digital pointer only takes up 3 bytes,which has little impact on the data transmission efficiency.
The AES encryption and decryption process based on the digital pointer is shown in Figure 5.The main steps are summarized as follows.The physical entity first obtains the keyKrandomly from the keystore and encrypts the plaintext by AES usingK.Then,HMAC is obtained by two hashing functions,which further combines with the ciphertext to form the transmit data.Finally,a 3-byte digital pointer corresponding to the keyKis added to the ciphertext data header,and the digital pointer and ciphertext data are sent to the wireless channel using the USRP based on automatic retransmission mechanism.At the receiving end,the twin entity identifies the digital pointer and obtains the keyKfrom the keystore.Then identity authentication is performed to verify the source and integrity of the ciphertext data.After the successful authentication,it uses the keyKto decrypt the ciphertext and finally obtains the plaintext.
3.3 ARQ-Based Reliable Data Transmission
To improve the transmission reliability,an automatic retransmission mechanism combined with RS-based FEC coding is considered here.After framing,RS(255,223) with the length of the code information as 223 bytes is used to encode the data,which can correct the burst error of 16 bytes,and generate 32 bytes check code added to the original information.The receiver performs CRC on each data frame to ensure the data integrity and feedbacks the ACK timely when correctly receiving the frames.After receiving the confirmation frame,the
sender stops sending the specific frame until all the frames are guaranteed received.This protocol enables the sender and receiver to know the status of data transmission in real time.
The transmission strategy first subpackages data every 216 bytes,and the number of packetsTotalNumis defined as
whereMis the total data size,and padding is used to fill in for the final packet whose size is less than 216 bytes.After subpackage,the frame is grouped according to the format,and then every 2 frames as a group are modulated for transmission.To facilitate data reorganization at the receiver,data frames are numbered.If the (m+1)thframe arrives before themthframe,it does not need to be resent after CRC check,thus improving the transmission efficiency.CRC-16 is used here,and the generator polynomial is defined asF(x)=x16+x15+x2+1.The data to be checked is represented as annthorder polynomialG(x),and the remainder obtained byG(x)/F(x) is the check value of CRC-16,which is placed at the end of the data frame in a 16-bit length.
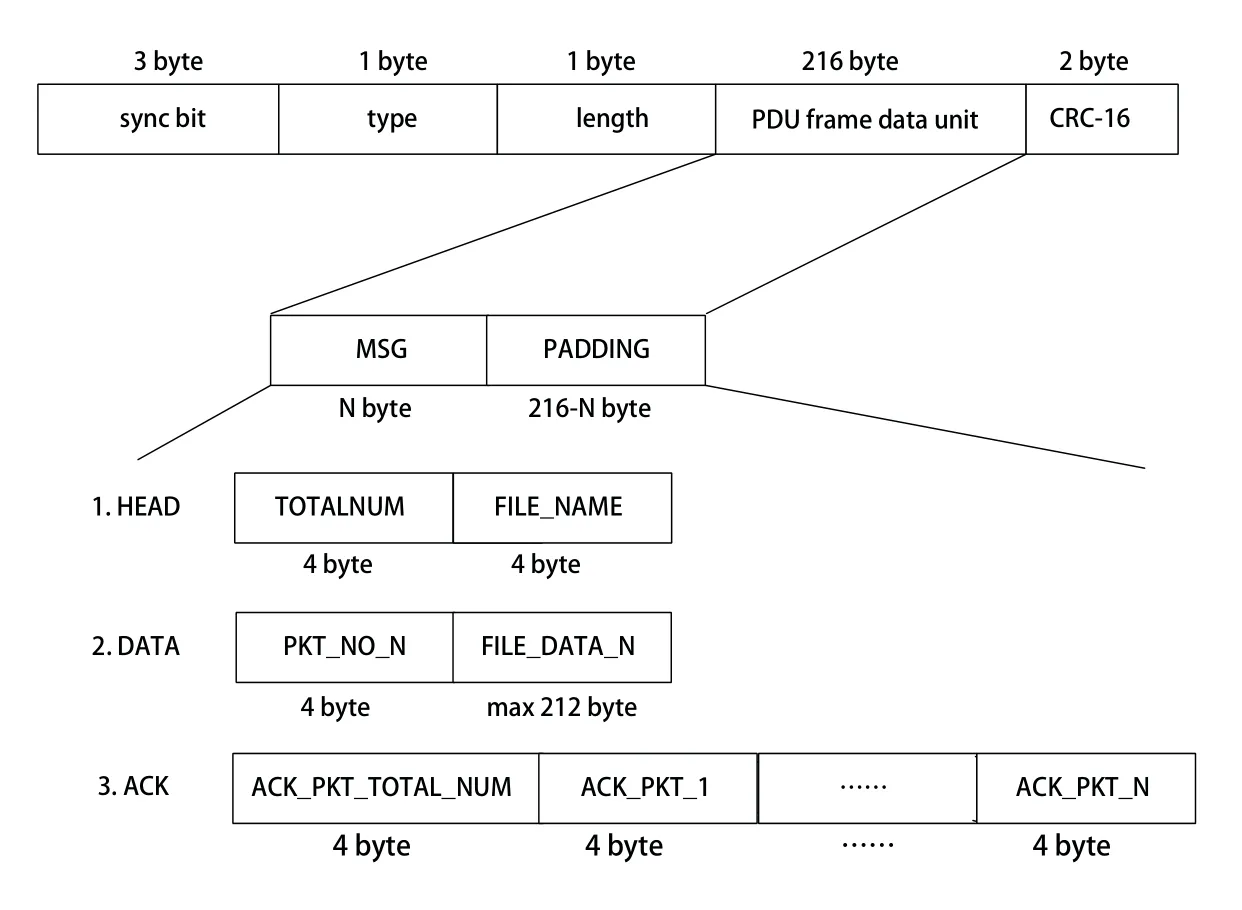
Figure 6.Data frame format.
The specific frame format is shown in Figure 6,and the functions of each field are shown in Table 1.There are three types of PDU data packets,namely HEAD,DATA,ACK.Specifically,HEAD indicates the name of the transmitted file and the number of packets,DATA indicates the frame number and data content after data segmentation,and ACK indicates both the amount and the serial number of acknowledgement received frames.
The overall transmission process of the node B and the node A in the automatic retransmission mechanism,as shown in Figure 7,includes the following steps:
Step 1: Node A sends data frames.
Before the transmission starts,the flag bit array and the content data are all initialized.
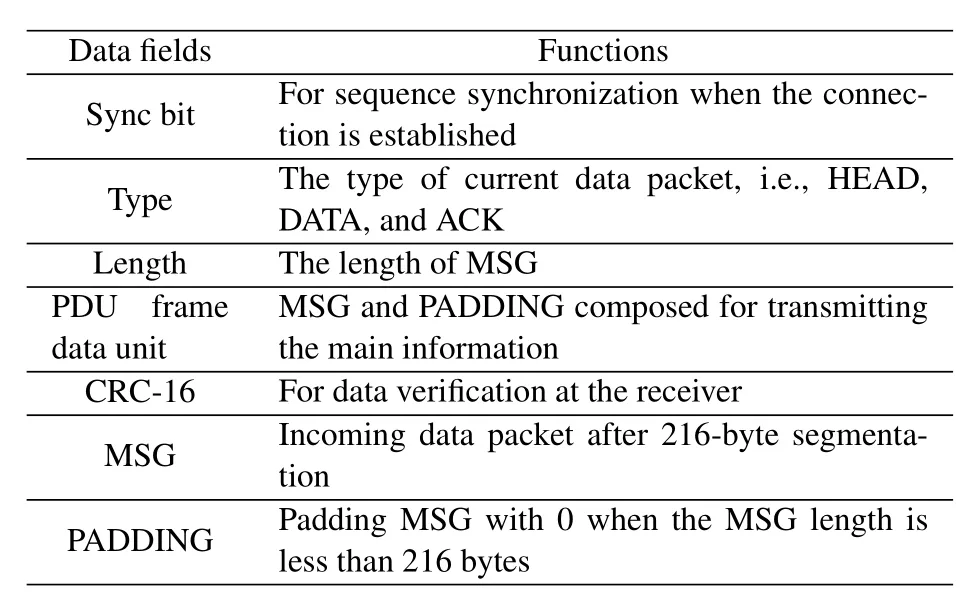
Table 1.Data field functions.
Step 2: Node B receives data frames.
After receiving the data frame,Node B modifies the flag bit from 0 to 1,and sends an ACK to the sender.
Step 3: Node A receives the ACK.
Node A receives the ACK,indicating that the frame is successfully sent.Then the flag bit of this sent frame is marked as 1 in node A.
Step 4: Fail to send data-data frame loss.
If the data frame is lost during the transmission,no acknowledgement frame is generated,and the frame will be resent in a new round.
Step 5: Fail to send data-ACK loss.
If the ACK is lost,the sender cannot receive the acknowledgment frame,and the data frame will be resent in a new round.
When the flag bit array is all set from 0 to 1 in node A,it indicates that the transmission is completed,and all the data packets are successfully received.
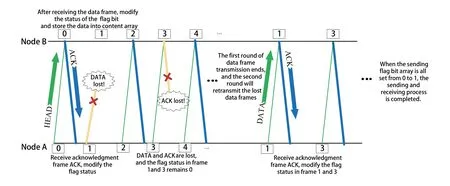
Figure 7.Schematic diagram of the interaction process of the automatic retransmission mechanism.
IV.SYSTEM IMPLEMENTATION AND PERFORMANCE ANALYSIS
4.1 System Implementation
Aiming at the above protocol design and system implementation,a physical simulation model is built by the SDR platform.Taking GNU Radio as the software programming and USRP as the hardware equipment,the block diagram of the transmission system is shown in Figure 8.The system consists of a pair of nodes,namely the physical entity A and the virtual entity B.Each node consists of a PC and one USRP E320.The working mode is full-duplex,that is,both nodes have the function of simultaneously sending and receiving based on the automatic retransmission mechanism.The system simulation parameters are given as follows: the sampling frequency is 1 MSamples/s,the bit rate is 500 Kb/s,the carrier frequency is 2.45 GHz for data transmission and 900 Mhz for ACK transmission,and the antenna gains for both nodes are 40 dB,and the modulation format is set to GMSK.
The GNU radio at the sender first gets the text files that are encrypted,signed,and added with digital pointer,and then implements the baseband signal processing such as packetization,error coding,and GMSK modulation.The processed signals are sent to the UHD-USRP module for parameter configuration before transmission.The signals enter the USRP external device to complete the up-conversion and DA convertion.Finally,through the RF front-end for frequency mixing,filtering and power amplification and other operations,the analog signal is sent into the wireless channel.
The USRP at the receiver receives the radio frequency signal and completes the down-conversion into the baseband signal.Then the GNU radio is used for GMSK demodulation and decoding.The received frame is subject to a CRC-16 check to see whether an ACK is fed back to the sender.And the transmission ends until the sender receives the ACK of all data frames.Data reconstruction is carried out based on the encoding of all the received data frames to obtain text files.Finally,after successful pointer identification,authentication and decryption,the plaintext is restored.
4.2 Performance Analysis
1)Security Analysis
(1)Ciphertext tampering
During the transmission,both the physical and virtual entities will calculate the hash value twice.If a third-party attacker maliciously tampers with the ciphertext,an error will occur in identity authentication.Thus,hash calculation can prevent ciphertext tampering and malicious forgery,and even avoid collision.
(2)Key attack
By analyzing the decryption leakage caused by the interception of the key and ciphertext,we can get the probability of the interception for the AES,RSA,PAES(pointer-based AES)given as
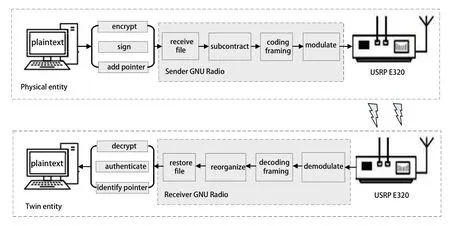
Figure 8.Block diagram of encrypted transmission model based on USRP and GNU Radio.
wherePkis the probability of the key being intercepted,andPeis the probability of the ciphertext being intercepted.Eq.(9) is due to the fact that RSA adopts asymmetric encryption so that its private key is not transmitted.And in Eq.(10),it is because that the P-AES keystore reminds the receiver through the digital pointer to avoid the key being transmitted in the wireless channel,so that the interception probability is also 0.Moreover,for P-AES encryption,even if the attacker obtains the communication data of both parties,it cannot decrypt due to the lack of the session key.Even a brute force attack can hardly decrypt the key.
Table 2 shows the key combination numbers of the AES encryption and the P-AES encryption in both 128-bit and 256-bit key lengths.The number of keys currently used by P-AES is 512,which can be expanded in the future.For example,the number of the key combinations for AES-128 is calculated as2128,i.e.,3.403×10e38,and it is 2128×512,i.e.,1.742×10e41 for P-AES-128.
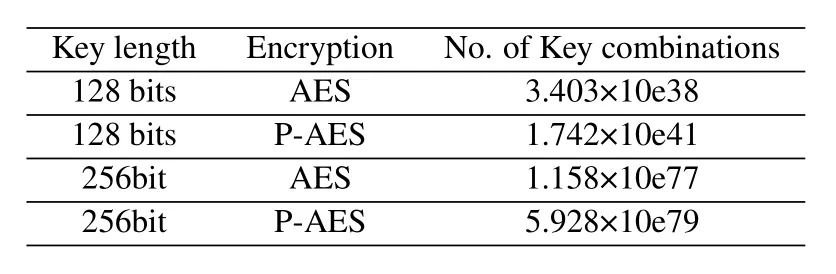
Table 2.Key combination comparison between AES and PAES.
It can be seen that given the same length,P-AES has better security against brute force attacks.Considering the processing speed of the latest supercomputer is 33.86×1015 FLOP/s,cracking the 128-bit P-AES key thus takes time:
Therefore,getting a key by checking all the combinations is impossible for one person.Even for the quantum computer with an exponential computing speed,an extension to keystore can overcome the issue of being cracked.Moreover,P-AES frequently uses different keys for encryption to further enhance the randomness.The protocol designed here also has the property of full forward secrecy,which means that a key can only access the data protected by it,and the cracking of one key does not affect the security of data protected by other keys[31].
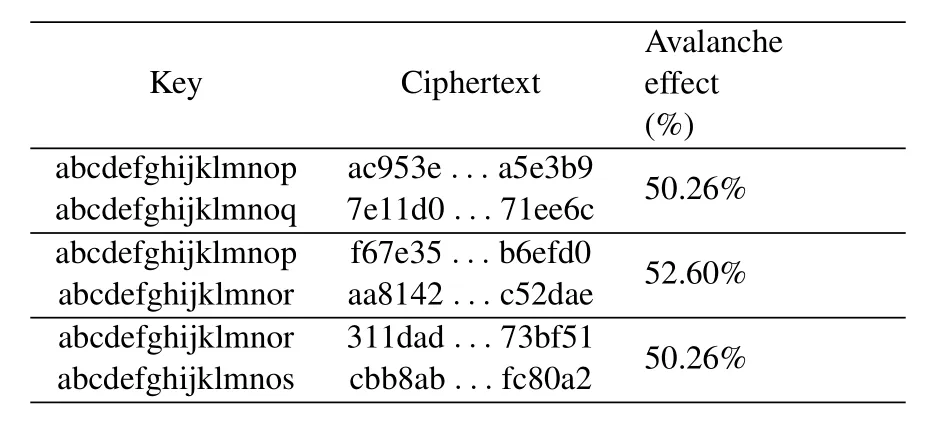
Table 3.Calculation of Avalanche effect based on different keys.
(3)Cipher attack
Avalanche effect is an important index to measure the security of encryption algorithms [32].It means that in a high-security block cypher,any slight change in the key or plaintext should cause a massive change in the output,thus preventing crypt analysts by analyzing the ciphertext to guess the plaintext and then crack the password.The avalanche effect is defined as
whereHamming distancerepresents the change of corresponding bits between two binary strings,andBlock sizerepresents the length of binary string.
The strict avalanche criterion(SAC)states that when any input bit is reversed,each output bit has a 50%probability of changing.SAC is a fundamental property for symmetric encryption,which provides a good reference index for secure encryption.This paper thus calculates the avalanche effect for the P-AES algorithm.Table 3 shows the avalanche effect with different keys,that is,the same plaintext “ABCDEFGHABCDEFGH”is encrypted by two keys that vary by one bit.In addition,Table 4 shows the case that different plaintexts are encrypted with the same key“abcdefghijklmnop”.It can be seen that the P-AES algorithm complies with the SAC.That is,it is difficult to crack the encryption algorithm and deduce the plaintext from the ciphertext.
2)Efficiency Analysis
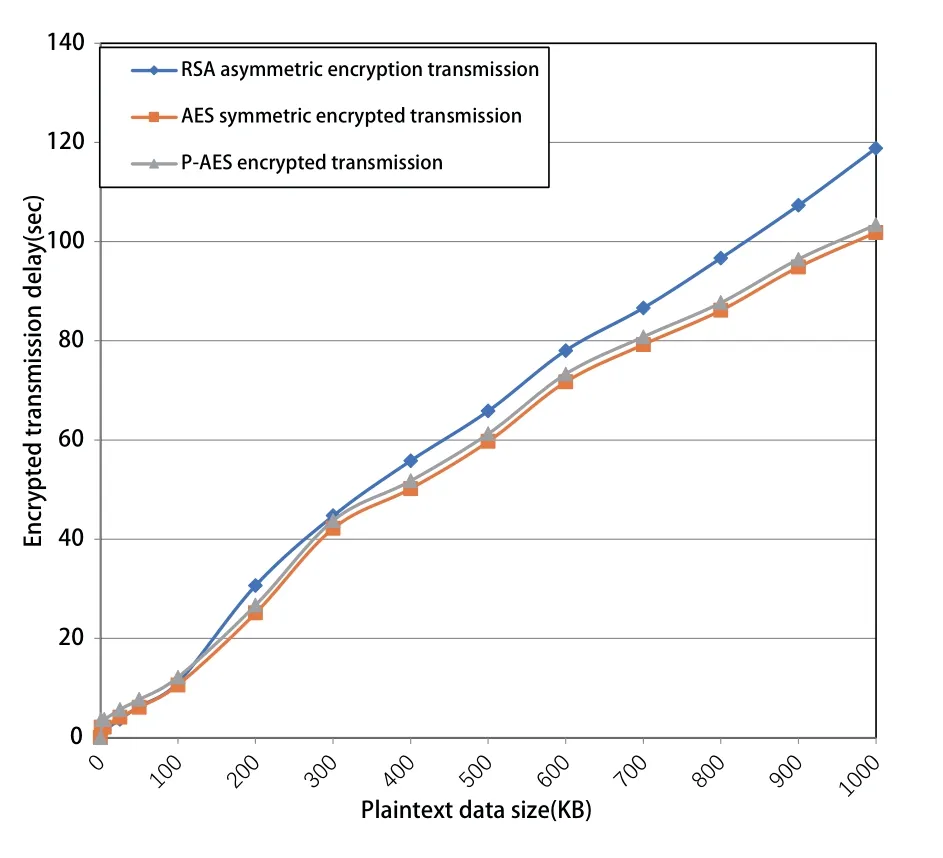
Figure 9.Comparison in efficiency for different encryption algorithms.
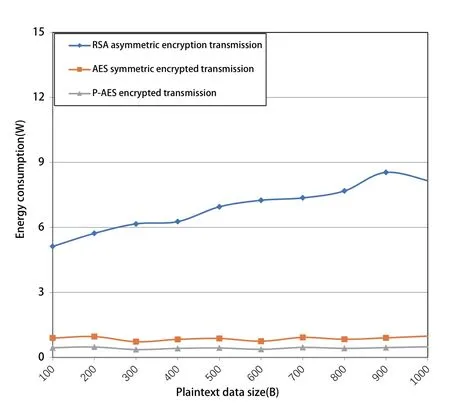
Figure 10.Comparison in energy consumption for different encryption algorithms.
To simulate the efficiency of different encryption algorithms,the DT transmission system based on the SDR platform is used to test the data encryption of different sizes.The efficiency comparison between the RSA,the traditional AES and the digital pointer-based AES(P-AES)is shown in Figure 9,where the overall encrypted transmission delay is taken as the performance metric.All the three methods are based on the same equipment setups combined with the same automatic retransmission protocol.We can see that the time difference is slightly a little for the small sizes of data packets.But the efficiency advantages of AES and P-AES are gradually obvious and almost consistent as the packet size increases.Note that the RSA algorithm ensures the data security at the high cost of time efficiency.Specifically,the security of RSA depends on the factorization of large numbers,which can not be cracked by brute force,thus guaranteeing the security.However,the key length is too long,so that the operation cost is very high,leading to a larger delay.Therefore,RSA is only suitable for small data packets,and a large amount of plaintext data should be encrypted by symmetric cryptography.
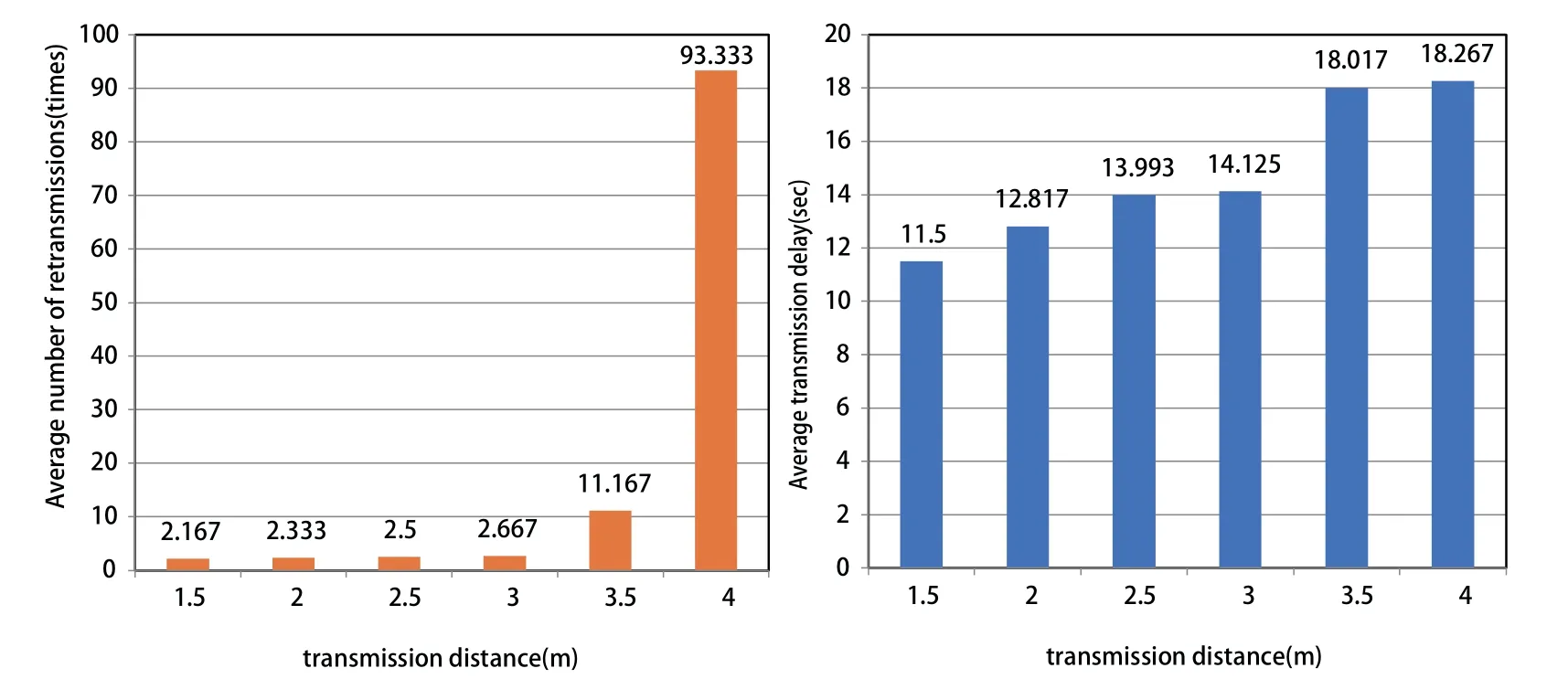
Figure 11.Network performance with transmission distance.
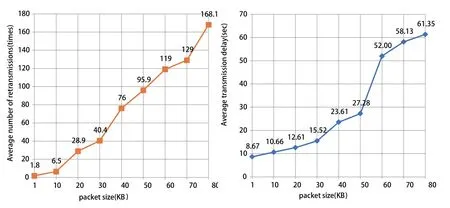
Figure 12.Network performance changes with packet size.
In addition,one of the main application scenarios for DT interaction is industrial manufacturing,which has a strict requirement on energy consumption.Thus,the analysis of energy efficiency for this proposed architecture is imperative.Figure 10 shows the numerical comparison of the energy consumption using the three encryption algorithms.We can see that the RSA algorithm has the highest energy consumption,because it has a long key length and the asymmetric operation efficiency is far lower than the symmetric al-gorithm.Note that the energy consumption of P-AES is lower than that of AES.The reason is that P-AES has the characteristic of a built-in key library which does not need to regenerate and store the keys every time,thus leading to a better energy consumption performance.
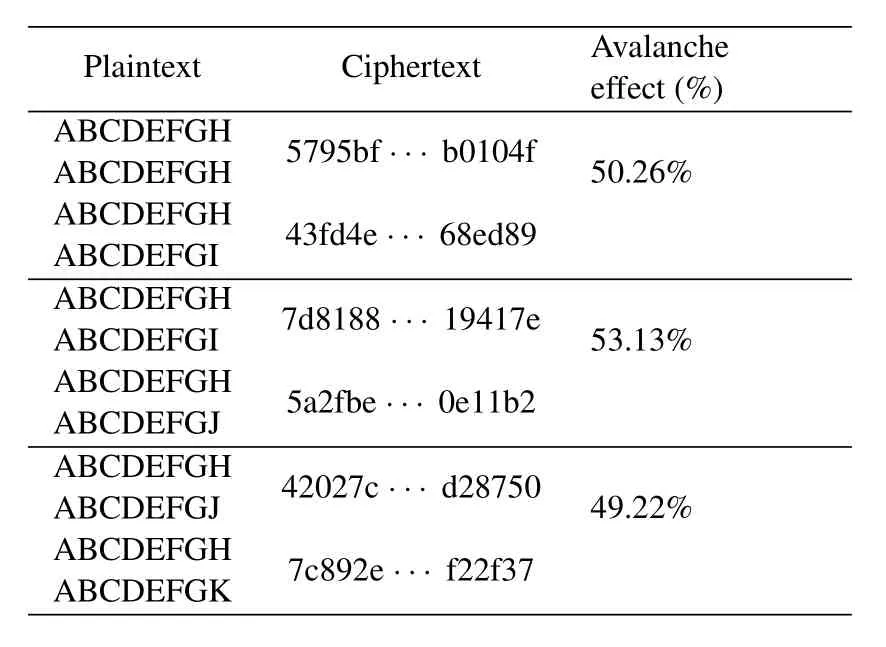
Table 4.Calculation of Avalanche effect based on different plaintexts.
3)Reliability
The reliability performance can be measured by transmission metrics such as retransmission times and transmission delay.The fewer retransmission times and lower transmission delay mean the higher reliability.Packet transmission is adopted with the assumption ofnpackets as a group,and thus the required number of groups(RNG)is defined asTotalNum/n.Assuming that it takest1s to send a set of data frames,andt2s to receive an ACK,and the number of retransmitted frames is defined asMsgNum,the expression of the transmission timeTis thus derived as
The SDR platform is used to test the influence of transmission distance and packet size on DT system reliability,as Figure 11 and Figure 12 show.To ensure the accuracy,each data is obtained by averaging 10 experiments.Figure 11 shows that we get the more times of retransmission and the longer transmission delay as the distance increases.When the distance exceeds 4 m,the DT system can no longer communicate to each other.After changing the antenna gain from 56 dB to 60 dB,the communication can continue.This implies that the antenna gain has a certain influence on the network performance.In brief,we can improve the transmission efficiency,i.e.,reduce the retransmission times by changing the transmission distance or the size of data packets as Figure 12 shows.
V.CONCLUSION
The DT technology promotes the new direction of industrial collaboration and internet development.Simultaneously,it will generate huge data sets and put forward higher requirements on data security protection.To solve the security problem of information interaction in the DTs,this paper proposes a trusted data interaction architecture that integrates encryption,authentication and reliable transmission,and combines physical layer security and information theory security to achieve the communication security.Using the digital pointer based encryption technology ensures the security of data transmission,and the automatic retransmission mechanism improves the reliability of ciphertext transmission.More importantly,the SDR platform is built to test the effectiveness of the DT architecture.The simulation results demonstrate that the model has high security and can achieve highefficiency encrypted transmission.In the future work,we will focus on the combination of multiple information security scenarios of anti-attack intelligent identification and active defense,and explore the DT interaction models that meet the requirements of multiscenario applications.
ACKNOWLEDGEMENT
This work was supported in part by the Intergovernmental International Cooperation in Science and Technology Innovation Program under Grants 2019YFE0111600,in part by National Natural Science Foundation of China under Grants 62122069,62072490,62201507,and 62071431,in part by Science and Technology Development Fund of Macau SAR under Grants 0060/2019/A1 and 0162/2019/A3,in part by FDCT-MOST Joint Project under Grant 0066/2019/AMJ,and in part by Research Grant of University of Macau under Grant MYRG2020-00107-IOTSC.
- China Communications的其它文章
- Quality-Aware Massive Content Delivery in Digital Twin-Enabled Edge Networks
- Edge-Coordinated Energy-Efficient Video Analytics for Digital Twin in 6G
- Unpredictability of Digital Twin for Connected Vehicles
- Endogenous Security-Aware Resource Management for Digital Twin and 6G Edge Intelligence Integrated Smart Park
- Digital Twin-Assisted Knowledge Distillation Framework for Heterogeneous Federated Learning
- A Golden Decade of Polar Codes: From Basic Principle to 5G Applications

