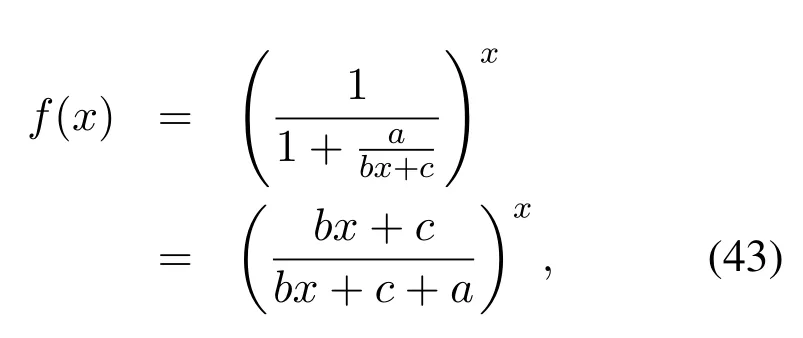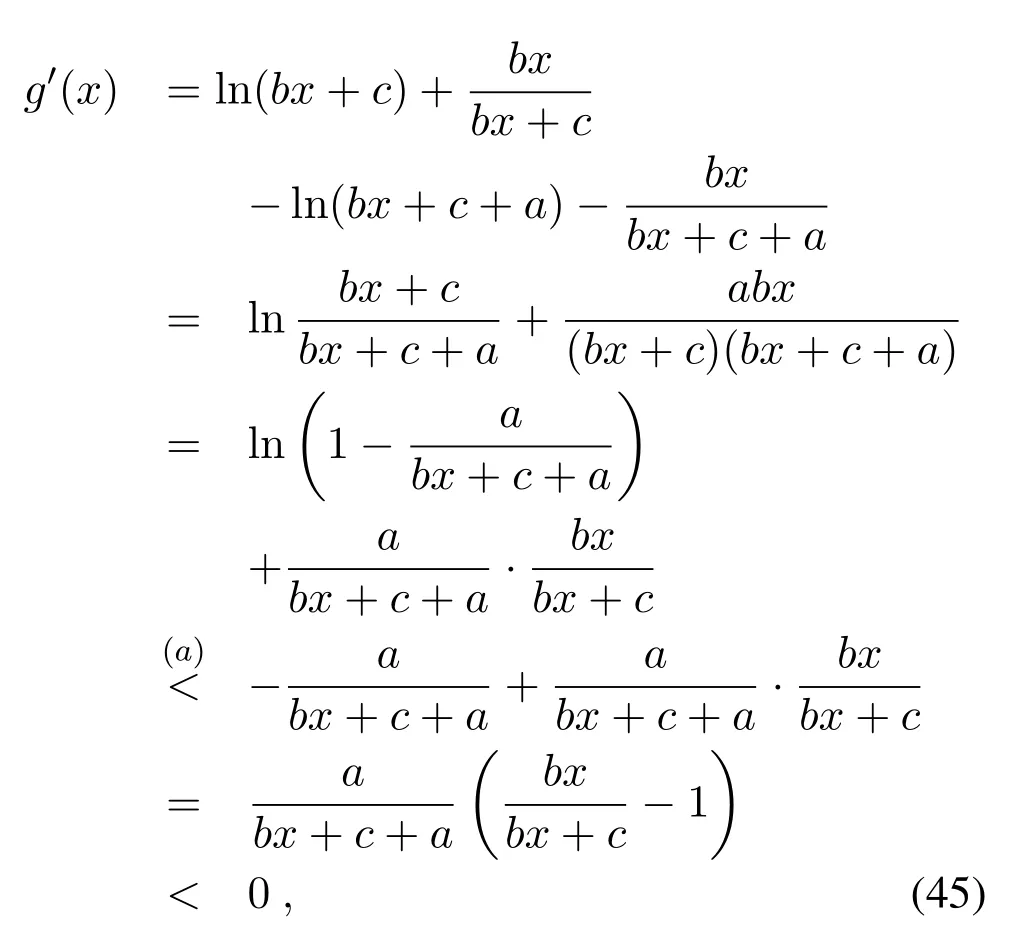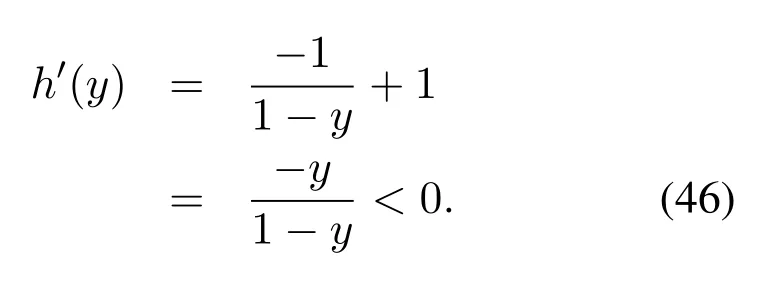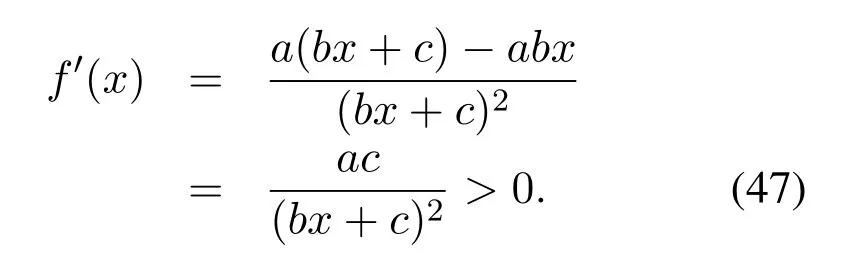Secure Transmissions in Wireless Multiuser Networks Using Message Correlation
Hongliang He,Libo Wang
1 School of Mechanical Engineering and Electronic Information,China University of Geosciences,Wuhan 430074,China
2 College of Information Science and Technology&College of Cyber Security,Jinan University,Guangzhou 510632,China
Abstract: Due to the openness of wireless multiuser networks, the private information transmitted in uplink or downlink is vulnerable to eavesdropping.Especially, when the downlink transmissions use nonorthogonal multiple access (NOMA) techniques, the system further encounters interior eavesdropping.In order to address these security problems,we study the secret communication in multiuser networks with both uplink and downlink transmissions.Specifically, in uplink transmissions,the private messages transmitted in each slot are correlated,so any loss of the private information at the eavesdropper will prevent the eavesdropper from decoding the private information in later time slots.In downlink transmissions, the messages are correlated to the uplink information.In this way,any unexpected users who lose the expected user’s uplink information cannot decode its downlink information.The intercept probability is used to measure security performance and we analyze it in theory.Finally,simulation results are provided to corroborate our theoretical analysis.
Keywords: physical-layer security; multiuser networks;user selection;message correlation;NOMA
I.INTRODUCTION
Wireless multiuser networks are widely deployed in our daily lives,such as cellular networks,machine-tomachine(M2M)networks,ad hoc networks,and sensor networks [1–3].Due to the broadcast nature of wireless communications,these networks are vulnerable to eavesdropping.Traditionally,information security is guaranteed by using cryptographic encryption techniques[4–6].However,key management and distribution become difficult and complex if there are a large number of users in the networks.Consequently,a supplementary method called physical-layer security has been proposed to achieve keyless secrecy recently[7–9].The basic principle of physical-layer security is to exploit the randomness of wireless channels and properly design the coding and the transmit precoding methods, so that the eavesdropper cannot decode the private information.As demonstrated in[10],physical-layer security can be achieved if the legitimate channel is better than the wiretap channel.Therefore,abundant works have been conducted to enhance security by improving the legitimate channel or/and degrading the wiretap channel, including the using of multiple-input and multiple-output (MIMO) techniques [11], artificial noise assisted techniques [12],and cooperative transmission techniques[13].
Security issues in multiuser networks can be divided into two main categories, i.e., uplink security and downlink security.In the uplink transmission,multiple users send their private information to the base station (BS) simultaneously [14].In some scenarios,users have limitations in terms of antenna and power, e.g., single antenna and low transmit power,so complex physical-layer security techniques are not suitable for them.To address this problem, a simple method called user selection scheme [15–19] has been studied in the literature.For example,an opportunistic user scheduling scheme was proposed in[15],which achieves the optimal multiuser diversity gain.In [16], the authors proposed another opportunistic user scheduling scheme and analyzed the secrecy outage probability and the ergodic secrecy rate.In [17],the authors investigated three different user selection schemes and analyzed the corresponding ergodic secrecy sum rate.In [18], information security is combined with energy efficiency,and the authors provided an iterative algorithm to maximize the secure energy efficiency.In[19],one user is selected to transmit private information, and other non-scheduled users send artificial noise,so that the optimal multiuser diversity gain is achieved.In addition,other methods like symbol phase rotation [20] and waveform designing [21]also have been employed to improve the security in the uplink transmission.
In the downlink transmission, multiple users receive the private information from the BS simultaneously.To improve the spectral efficiency, nonorthogonal multiple access (NOMA) techniques have been widely studied recently [22–25], which enable the system to support more users.However, if we use NOMA,the downlink transmission faces two security risks, i.e., the exterior eavesdropping and the interior eavesdropping.On one hand, the BS broadcasts the private information to users, so the eavesdropper also can receive the private information.On the other hand,successive interference cancellation (SIC) is used at the users,so the users with better channel quality can decode the information of users with worse channel quality.To address the exterior eavesdropping problem in NOMA, authors in [26] jointly designed decoding order, transmission rates, and transmit power.Also, in [27], the authors proposed an artificial noise aided beamforming scheme against the eavesdropper.Targeting at the interior eavesdropping in NOMA, a constellations rotation scheme is proposed in[28].
Although all the works discussed above can improve the security in the uplink or downlink transmission,they still face some challenges.First, in these works,the private information is independent with time, so the eavesdropping can be successful at any time.For example,even the eavesdropper does not overhear the information in the previous time slot,it still has opportunities to decode the information in the current slot.Second,most of the works assume that the legitimate users know the channel state information(CSI)or the additive white Gaussian noise (AWGN) of the eavesdropper.However, this information is difficult to obtain in practice because of the passive character of the eavesdropper.Moreover, in this case, the secrecy capacity defined as the difference between the capacity of the legitimate channel and the wiretap channel is difficult to acquire due to the unknown of the capacity of the wiretap channel.
Focusing on the problems discussed above, we jointly consider the security issues in the uplink and downlink transmissions in multiuser networks, and propose a novel message correlation scheme in this paper.We correlate the private information in the current time slot with the private information transmitted in the previous slots, so that the eavesdropper cannot decode the private information in the current slot if it has lost any private information in the previous slots.Similarly, we correlate the private information transmitted in the uplink and the downlink transmissions,so the eavesdropper cannot decode the downlink information if it has lost the uplink information.At the same time, the message correlation scheme also addresses the interior eavesdropping problem that exists in the NOMA technique, so the private information transmitted by the users with worse channel quality is protected.To the best of our knowledge, this is the first work to use message correlation in the multiuser networks to address both the exterior and interior eavesdropping problems.In addition, we exploit the intercept probability rather than the secrecy capacity as the metric to measure the security performance when without knowing the CSI and the AWGN of the wiretap channel.Here,the intercept probability is defined as the probability that the eavesdropper can decode the private information correctly.
The message correlation scheme based on XOR has been studied in some existing works [29, 30].However, compared with our work, the existing works focus more on point-to-point communications and ignore the cooperation between different users.We combine user selection and message correlation, so the security is further improved.Moreover, the existing works only considered exterior eavesdropping but our work deals with both exterior eavesdropping and interior eavesdropping.
The contribution of this paper can be summarized as follows:
• For uplink transmissions,we propose a user selection scheme to ensure that the SINR at the legitimate destination is higher than a target value,but the eavesdropper’s SINR has a certain probability to be less than the target value,which provides a good platform for implementing the proposed message correlation scheme.
• For downlink transmissions,we correlate the private information with that transmitted in the uplink,so the uplink information protects the downlink information.
• We obtain the closed-form expressions of intercept probability,which shows the security performance of the proposed scheme.
The remainder of this paper is organized as follows.In Section II, we present the system model.In Section III,we discuss the message correlation scheme in the uplink transmission.In Section IV, we analyze the intercept probability of the private information in the uplink transmission.In section V,we analyze the proposed scheme in the downlink transmission.Simulation results are given in Section V,and the paper is concluded in Section VII.
II.SYSTEM MODEL
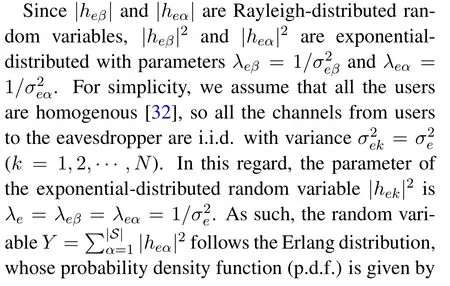
We consider a wireless multiuser network withNusers, a base station (BS), and an eavesdropper.TheNusers are noted asU1,U2,··· ,UN, and the eavesdropper is noted as Eve.The users and the BS intend to transmit private information with each other,while their communications are eavesdropped by Eve.For analysis convenience, we assume the system exploits the time division duplex (TDD) protocol, so the uplink channels,from the users to the BS,and the downlink channels, from the BS to the users, are reciprocal.Denote the legitimate channel from userUk, k=1,2,··· ,N,to the BS ashk,the wiretap channel from userUkto the eavesdropper ashek, and the wiretap channel from the BS to the eavesdropper is denoted ashbe.All channels are assumed to be independent.We consider the non-LOS(line-of-sight)multipath model with path-loss and fading, so all the channel coefficients are zero-mean complex Gaussian variables,and the envelope of the channels are Rayleigh-distributed.Specifically,the variance of channelhkis noted asthe variance of channelhekis noted asand variance ofhbeis denoted asSince Eve is passive,all the legitimate users and the BS do not know the CSI of the wiretap channels.We assume the BS knows the CSI of all the downlink channels,and the userUkknows the CSI of its own uplink channelhk,while the eavesdropper knows the channelhekfrom each user to itself, the channelhbefrom the BS to itself, and the channels from users to the BS, i.e.,hk.We consider the block fading model in this system,where the channels keep constant in one uplink and downlink transmission period but are independent and identically distributed (i.i.d.) across different periods.In addition,the basic communication protocols in the uplink and downlink transmissions have some differences,which are discussed as follows.
First,we discuss the uplink transmission,as shown in Figure 1.Before users transmit private information to the BS,the BS broadcasts three public parameters,H0,R0andH2,to all users,whereH0< H2andR0is the target transmission rate.If the channel from userUkto the BS satisfies|hk|2>H2,userUktransmits its private information to the BS.However,if|hk|2
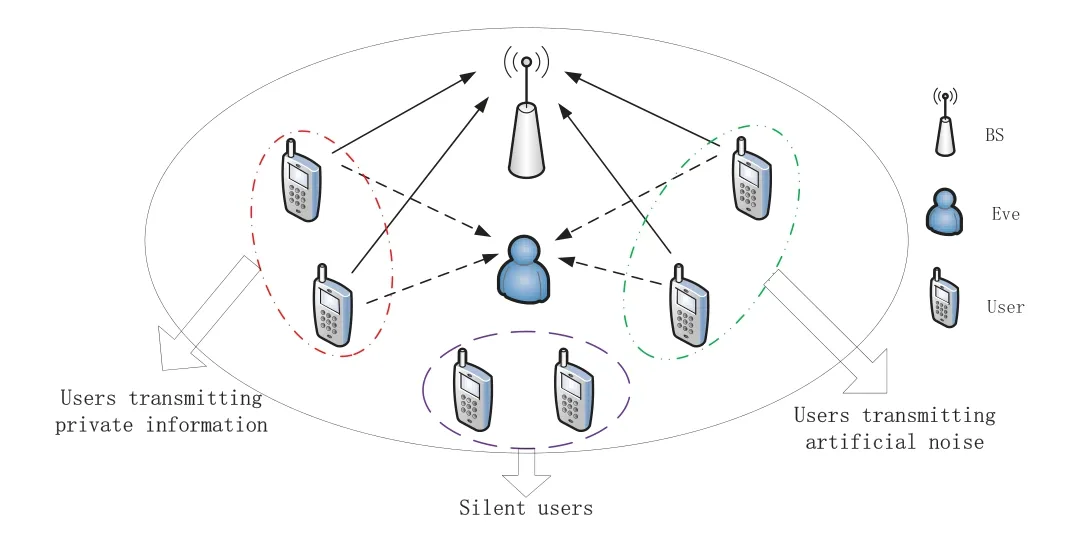
Figure 1. System model: uplink.
Next, we discuss the downlink transmission, as shown in Figure 2.In order to improve the spectral efficiency, we assume the BS exploits the nonorthogonal multiple access (NOMA) technique to transmit information to users.In this case,successive interference cancellation (SIC) scheme is used at the users to decode the information from the BS.Specifically, the userUkfirst decodes the message for userUjwithj < kand then cancels this decoded message from its received signal, while the information for userUjwithj > kwill be treated as noise.It can be seen that information for the users with worse channel quality can be decoded by the users with better channel quality.In addition,because only the users belonging to setBsend private uplink information to the BS,we consider that the downlink messages transmitted by the BS are tailored for these users.However,all other legitimate users as well as the eavesdropper can also receive these signals from the BS.
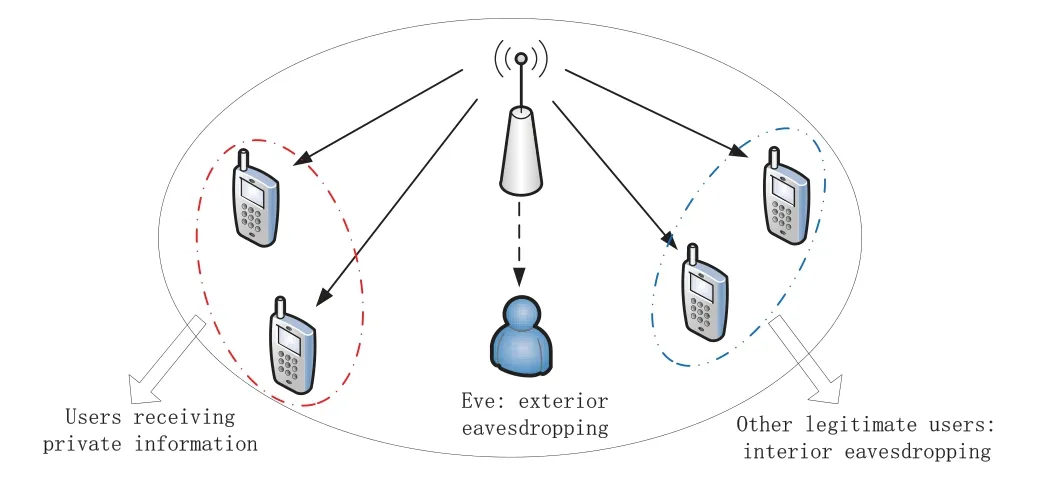
Figure 2. System model: downlink.
III.SECURE UPLINK TRANSMISSION
In this section, we improve the security of uplink transmissions via user selection and message correlation.
3.1 User Selection
In the uplink transmission period,usersUβ ∈B(β=N −|B|+ 1,N −|B|+ 2,··· ,N) send their own private informationxβto the BS,and simultaneously,the users belonging to setSemit artificial noise.Then the received signal at the BS can be expressed as
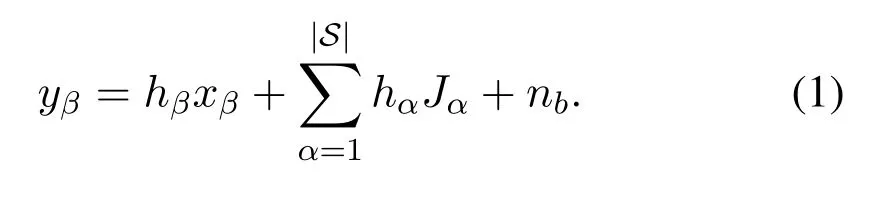
Here,nbis the complex AWGN with zero mean and varianceN0at the BS,xβis the private information from userUβwith powerPx, andJαis the artificial noise from userUα,which is a complex Gaussian random variable with zero-mean and variancePJ.Assume all the artificial noise from users in setSare independent and identically distributed.In this process,Eve also receives all the signals from the users,so the received signal at Eve can be expressed as
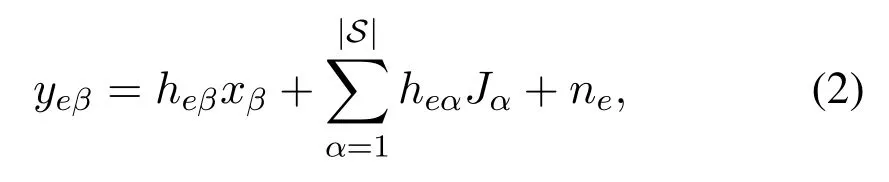
whereneis the complex AWGN with zero mean and varianceNeat Eve.Based on(1)and(2), the signalnoise-ratio(SNR)at the BS is obtained as
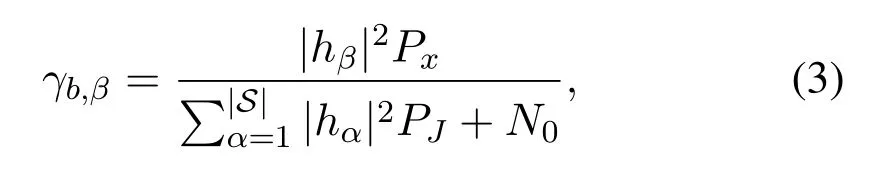
and the SNR at Eve is obtained as
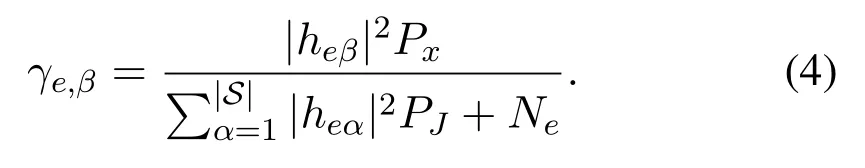
Observing(4),we can find that evenNe=0,the SNR at Eve will not tend to infinity due to the existence ofPJ.This indicates that the artificial noise transmitted by other users enhances the security.Based on(3)and(4),the capacity at the BS is obtained as
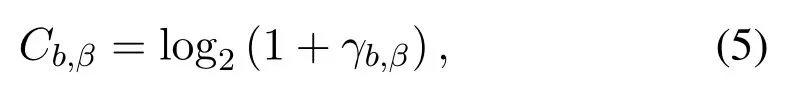
and the capacity at Eve is obtained as
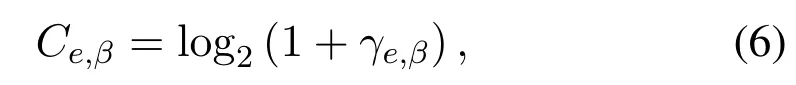
where the units of the capacity are bits/s/Hz.
Since all the users in setBhave the same characteristic|hβ|2> H2, and all the users in setShave the same characteristic|hα|2< H0,the SNR at the BS is larger than a constant,given by
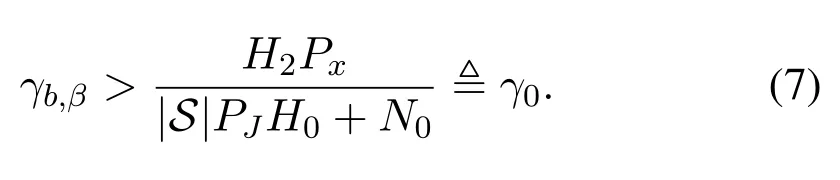
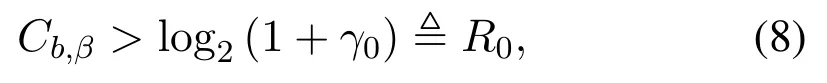
whereR0is designed as the target transmission rate,and we defineR0= log2(1+γ0).Observing(8),we can find that if all the uses in setBtransmit their own private information with rateR0, the BS can decode all the private information without error because ofCb,β > R0.However,the eavesdropper’s SNR,given in(4),is possible to be less thanγ0due to the randomness of the wireless channels, so the capacity at Eve is also possible to be less thanR0.In this case, Eve has a certain probability to lose the private informationxβ,and thus security is enhanced compared with the traditional scheme.Note that in our work, all the parameters in the expression ofγ0is known by the BS,soR0is easy to be designed by the BS.Moreover,parametersH2,H0,PJ,Px,R0andN0are all public,so all the users in the network including the eavesdropper know them.
3.2 Message Correlation
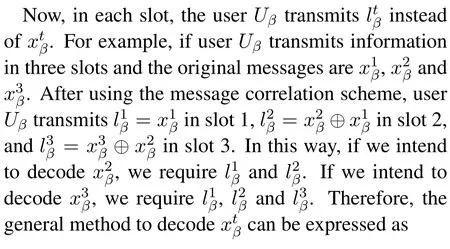
In last subsection, we have discussed the proposed user selection scheme.It can be seen that using this scheme, security in each slot is enhanced.However,we realize that the message transmitted by each user is independent with time.This indicates that the eavesdropper is possible to decode the private information in the current time slot even if it did not receive or successfully decode the messages transmitted in the previous time slots.To address this problem, in this subsection,we propose a message correlation scheme that correlates the message sent in the current time slot with the messages sent in the previous time slots.In this way, once the eavesdropper failed to decode a message transmitted before,it cannot decode the message transmitted in the current slot.Specifically, the message correlation scheme, as shown in Figure 3, isgiven as follows:
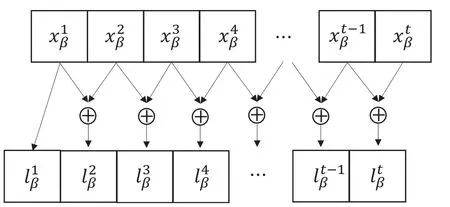

wheret= 1,2,··· ,∞is the index of slots in which the userUβtransmits private information,is the original private information that userUβintends to send to the BS in slott,is the message after using message correlation scheme, and⊕is the XOR operation.
“I know what you want,” said the sea witch; “it is very stupid of you, but you shall have your way, and it will bring you to sorrow, my pretty princess
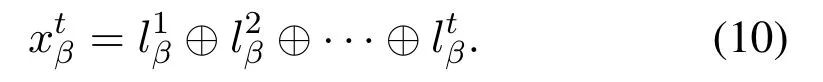

Now,we combine the user selection scheme and the message correlation scheme.In time slott, the users in setBtsend(β= 1,2,··· ,|Bt|)and the users in setStsend artificial noiseJα(α= 1,2,··· ,|St|), to the BS.Here,Btis the notation of setBin slott,andStis the notation of setSin slott.Then the received signal at the BS is given by
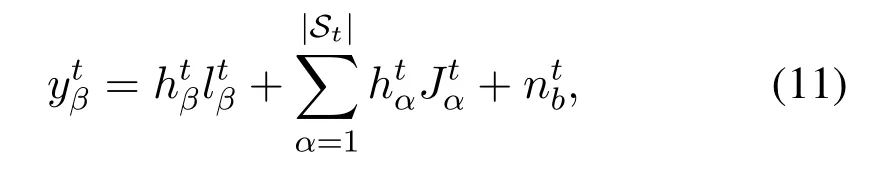
and the received signal at the eavesdropper is given by
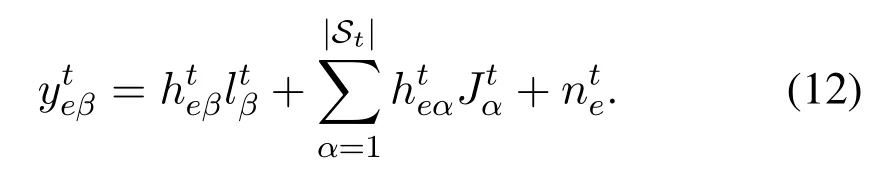
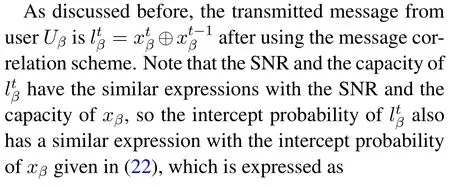
whereandare the channels in slott,and channelsor=1,2,··· ,N)in different time slots are i.i.d..Here,we assume the artificial noisein different slots is also i.i.d..In this respect, the SNR and the capacity ofat the BS and the eavesdropper have similar expressions with(3),(4),(5)and(6),so we do not provide them here to avoid repetition.
IV.SECURITY PERFORMANCE IN THE UPLINK TRANSMISSION
In section III,we have discussed the proposed user selection scheme and the message correlation scheme.In this section, we study the security performance of the proposed scheme.The intercept probability is employed to measure the security performance and we obtain its closed-form expression.
4.1 Security Performance with User Selection Scheme
Traditionally, physical-layer security is measured by the secrecy capacity, which is defined as the difference between the capacity of the legitimate channel and the capacity of the wiretap channel.The expression is given by
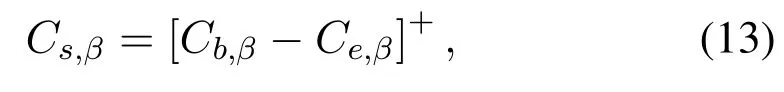
where [x]+= max(0,x).However, as shown in(4), the wiretap channelsheβandheαare unknown to us, so it is difficult to obtain the accurate value of the eavesdropper’s capacityCe,βand then the accurate value of the secrecy capacityCs,β.In this case,we exploit the intercept probability [31, 30] to measure the security of the proposed scheme.The intercept probability is defined as the probability that the eavesdropper accurately decodes the private information, which is independent with the CSI of the eavesdropper’s channel.Based on (6) and the definition given above, the intercept probability of messagexβis given by
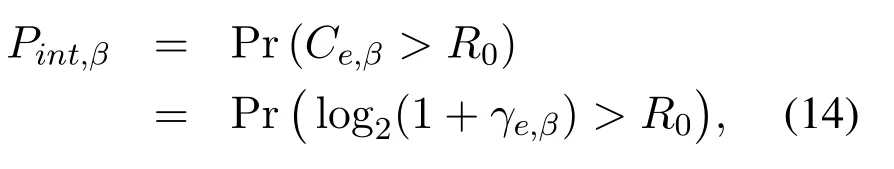
which is equivalent to
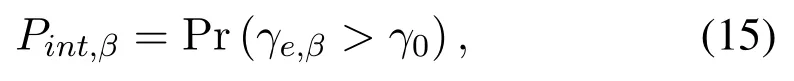
where the expressions ofγe,βandγ0are given by(4)and (7), respectively.As discussed before, we generally do not know the AWGN at Eve, so we consider the worst case thatNe=0,which turnsγe,βto
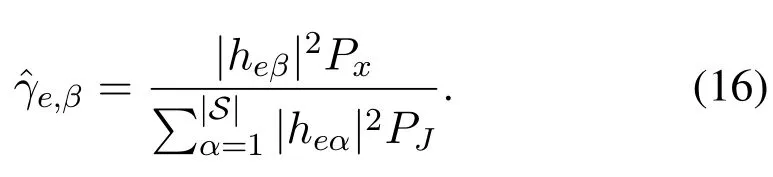

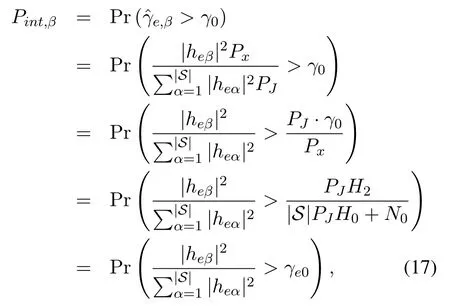
whereγ0is given in(7),and we define
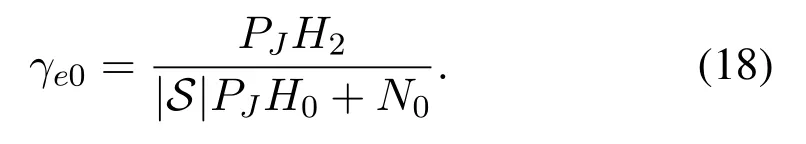
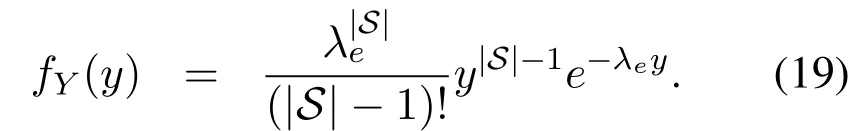
DenoteX=|heβ|2,and then the distribution ofZ=X/Yis obtained as
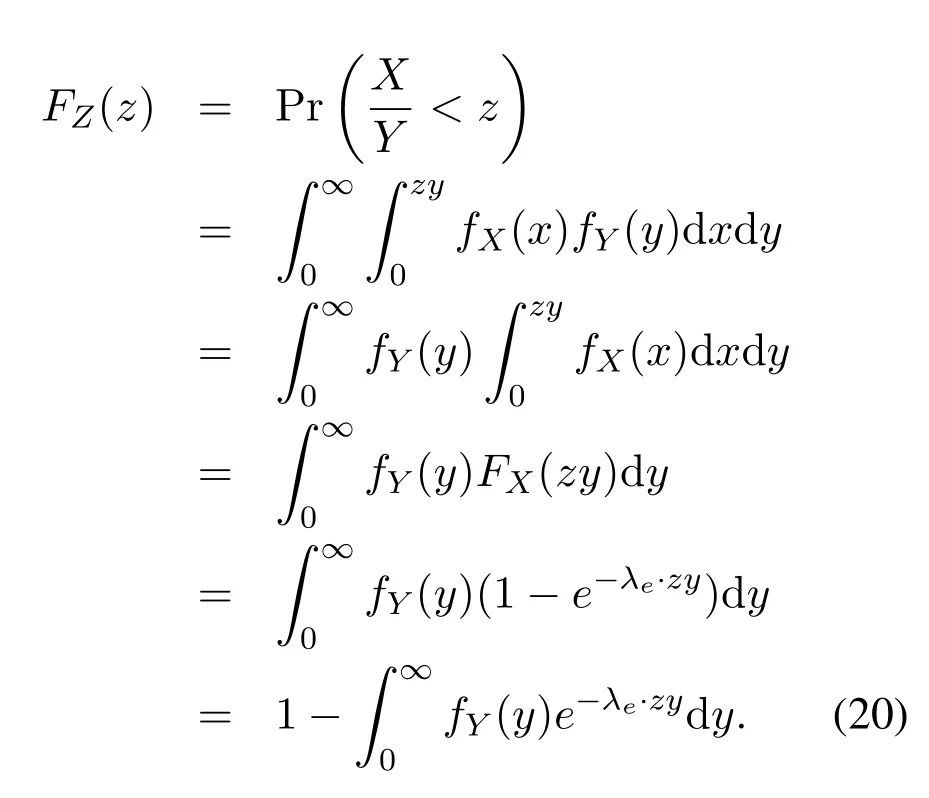
Substituting (19) into (20), we can further obtain the distribution ofZ=X/Yas
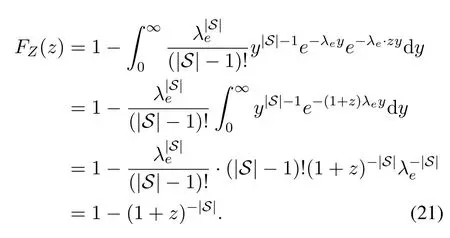
Combining(17), (18)and(21), we can obtain the intercept probability ofxβas
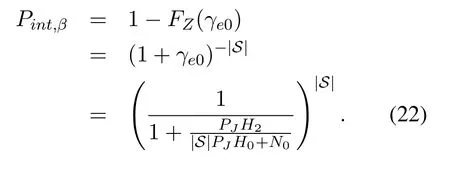
Specifically, the probability that Eve losesxβis obtained as
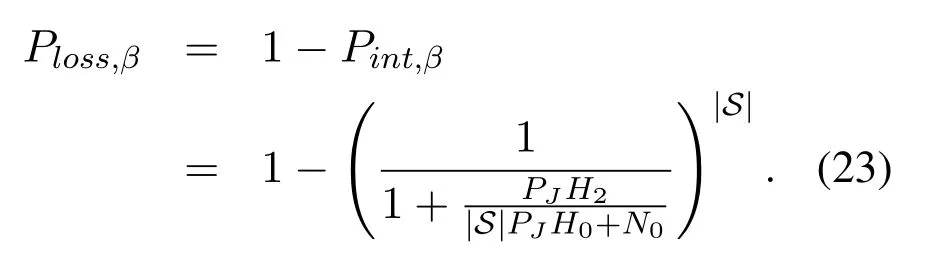
Note thatPloss,β >0 always holds as long as|S|≥1.In contrast, once any of|heβ|2≫|hβ|2,σ2eβ ≫orNe= 0 is satisfied in the traditional user selection scheme,the intercept probability ofxβis one.In this regard, the proposed user selection scheme improves security significantly.
In (22), we have obtained the closed-form expression of the intercept probability ofxβ,we now analyze the relationship between the intercept probability and different parameters.First, we study the effect of the number of users in the setSon the intercept probability.As demonstrated in Appendix VII,the intercept probability in (22) monotonically decreases with respect to the number of users in setS, i.e.,|S|.This indicates that if other parameters are given, the more users to send artificial noise,the higher security can be achieved.
Second, it also can be demonstrated from (22) that the intercept probability monotonically decreases with respect to the power of the artificial noisePJ,see Appendix VII, so increasing the power of the artificial noise can improve the security.However, as shown in(22), the intercept probability exists a lower bound whenPJ →∞,which is obtained as
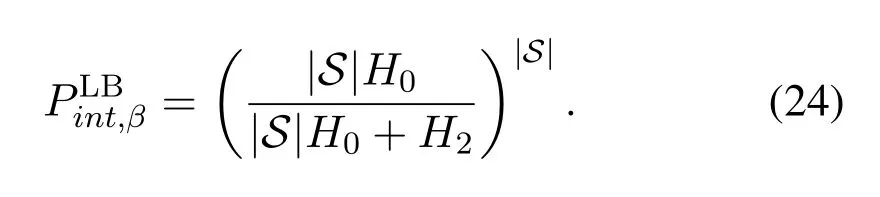
It can be seen that the lower bound of the intercept probability is totally decided by the parametersH0,H2and|S|.
Although (22) provides us the closed-form expression of the intercept probability ofxβ,it still is a random valuable due to the randomness of|S|.In order to eliminate the randomness of the intercept probability, we consider the average situation and assume the number of users in the network are large enough.For simplicity,we still assume all users are homogeneous,i.e.,all the channels from users to the BS are i.i.d.with variance=(k= 1,2,··· ,N).Thus,the number of users in setBapproximates to
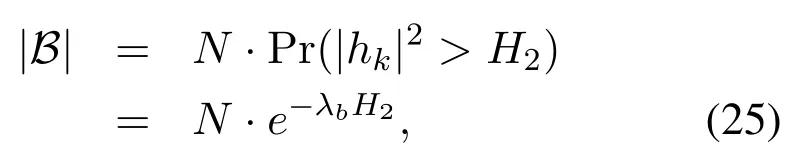
whereλb= 1The number of the users in setSapproximates to
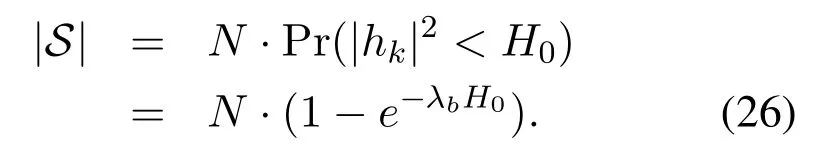
Note that both|B|and|S|are integers in practice,so if the result obtained in(25)or(26)is not an integer,we use the nearest integer as the result.In this regard,the intercept probability in large-scale multiuser networks is obtained as
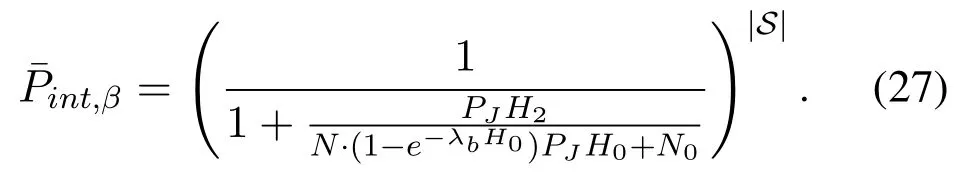
From(27),we observe that the intercept probability in large-scale multiuser networks is a constant decided byH0,H2and the power of the artificial noisePJ.
Moreover, in order to make sure that there are enough number of users to transmit private information, we consider the situation that the cardinality of setBcannot be less thanM, and the number of users to transmit artificial noise cannot be larger thanN −|B|,i.e.,|B|≥Mand|S|≤N −|B|.Therefore,the range ofH2andH0is obtained as
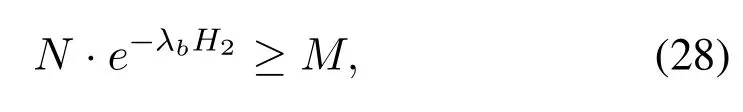
and
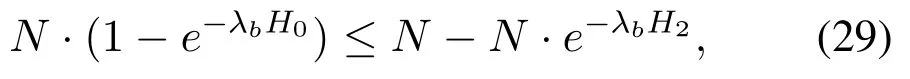
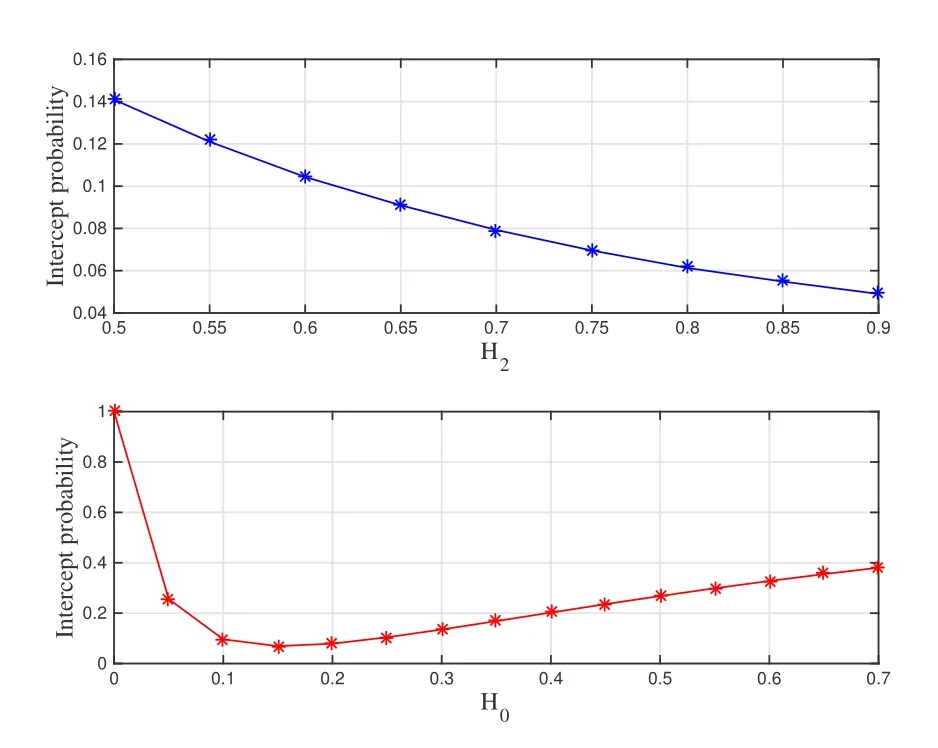
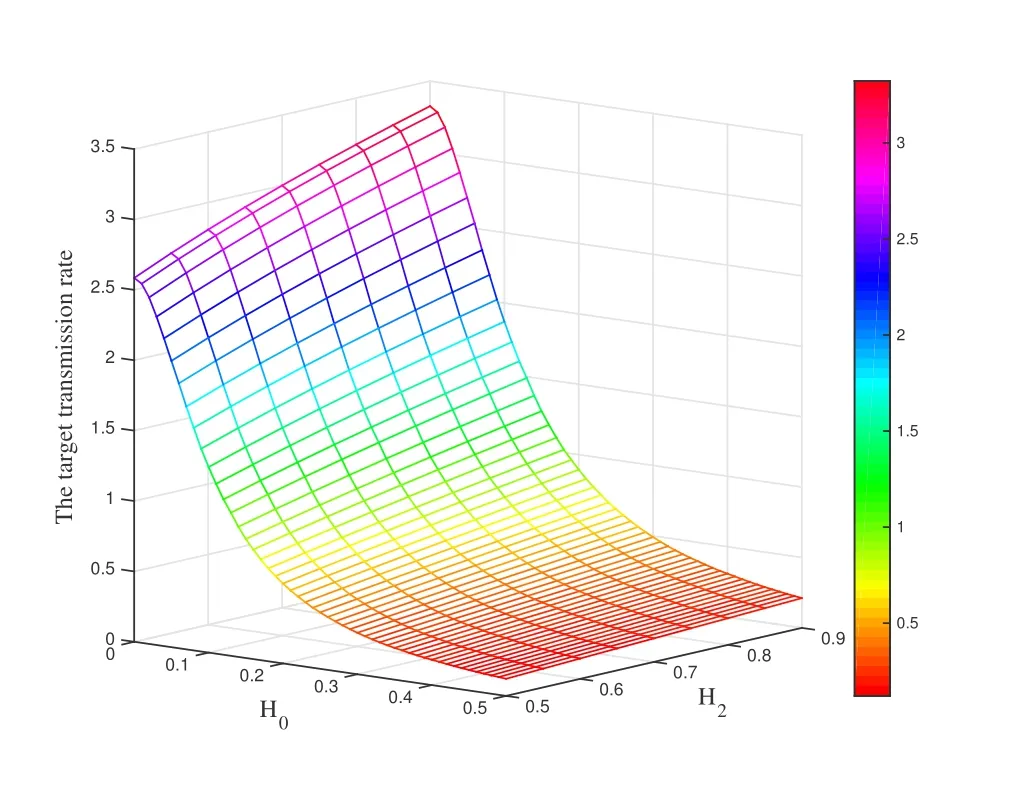
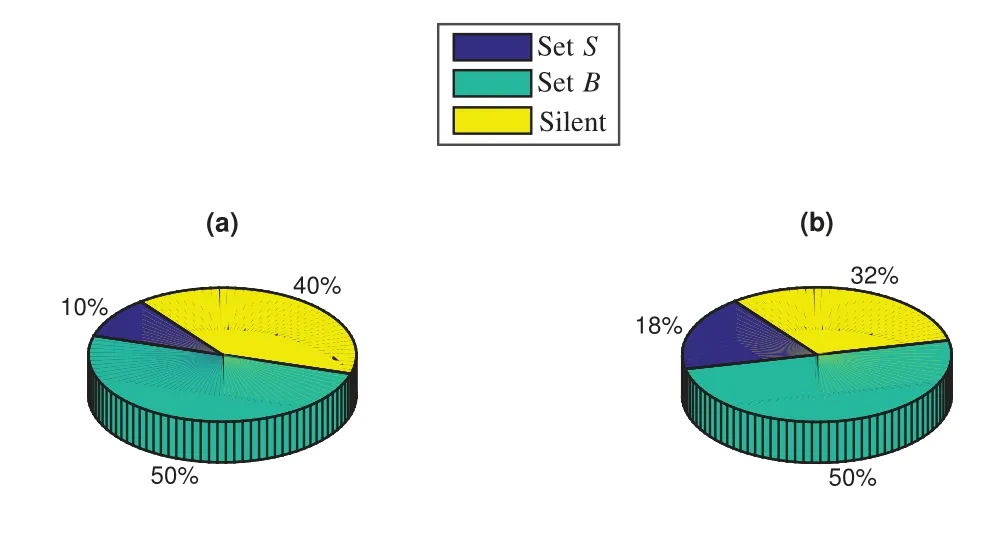
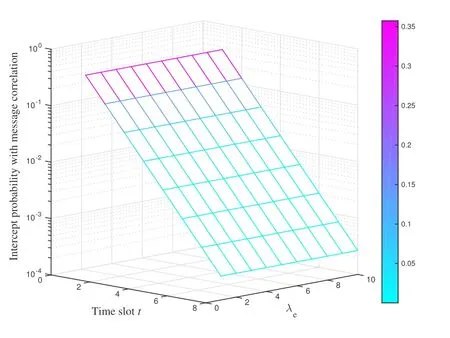
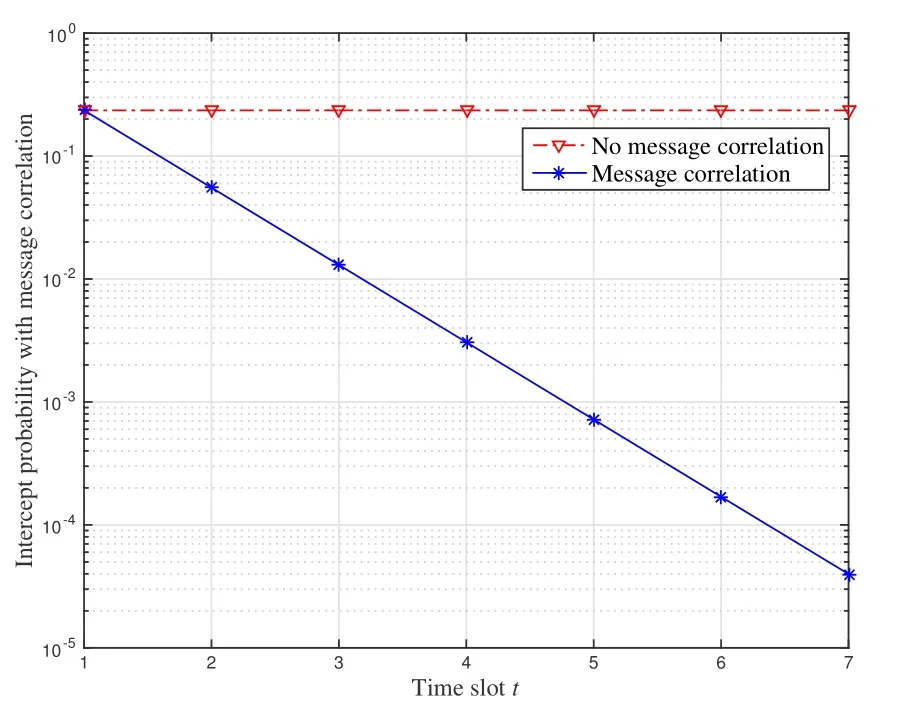
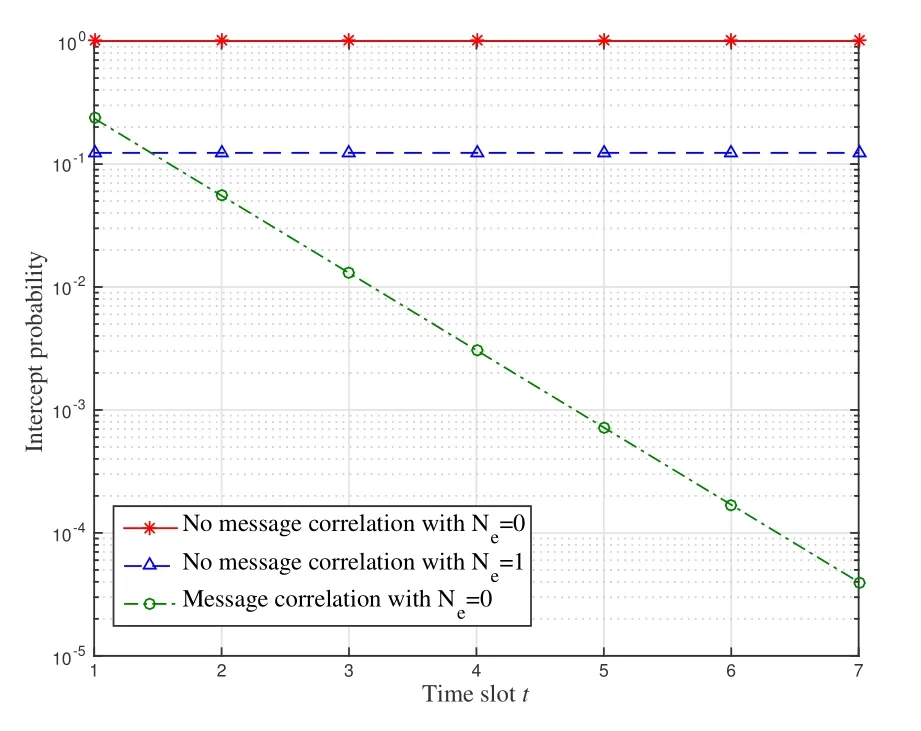
which are equivalent to 0< H2og(N/M)and 0 In the previous subsection, we have obtained the intercept probability of the private information when the message correlation scheme is not employed.In this subsection, we further analyze the intercept probability under the message correlation scheme. wherei= 1,2,··· ,t.Obviously, the intercept probability ofgiven in (31) is less than the intercept probability oforxβgiven in (30) due to the product oftnumbers between 0 and 1,i.e.,01.This indicates that the message correlation scheme can further improve the security on the basis of the user selection scheme. In this section,we study the secure downlink transmissions.We first discuss the security problems exited in the NOMA scheme,and then analyze the security performance when using the message correlation scheme. In the downlink transmission, without using message correlation scheme,the BS broadcasts the following signal to the users in setB: wheresβ(β= 1,2,··· ,|B|) with powerPβis the private information for userUβ, and we haveP1 wherenβ ∼CN(0,N0)is the complex AWGN at userUβ.Since we have|h1|2< |h2|2< ··· < |hB|2, the users employ successive interference cancellation to decode the message.The specific process is provided as follows.Them-th user first decodesi-th user’s message wheni < mand then subtracts this message from the received signal.Other users’messages(i.e.,i>m)will be viewed as noise.In this way,the SINR of theβ-th user is From the principle of SIC, we can find that the users with good channel quality can decode the information of users with bad channel quality.This process brings interior eavesdropping. In addition,the signal for userUβis also possible to be eavesdropped by an exterior eavesdropper.Observe that the received signal at Eve is wherene ∼CN(0,Ne)is the complex AWGN at the eavesdropper.The eavesdropper can also use SIC to decode all the messages,so forsβthe SINR at Eve is We can find that the condition that Eve successfully decodessβisSNRe,β > SNRβ.IfN0=Ne, this condition can be simplified as|hbe|2> |hβ|2.Note that the eavesdropper may be much closer to the BS than the userUβ, so it is easy for the eavesdropper to satisfy|hbe|2> |hβ|2.In this case, the private information faces serious security problems. In order to address the interior eavesdropping and the exterior eavesdropping, we now discuss the proposed message correlation scheme.The basic principle is given as follows.We correlate the message to be transmitted in the downlink with the message decoded in the uplink,so that the eavesdropper will lose the message transmitted in the downlink if it failed to decode the message in the uplink. As discussed before, the uplink information from userUβisin slott,so the downlink information for userUβafter using the message correlation scheme is given by Here,is the private information that the BS intends to transmit to userUβin slott.In this respect, the transmitted signal from the BS to the users in setBtis given by Then the received signal at userUβin slottis expressed as According to the principle of SIC, we know that them-th user can decodei-th user’s message wheni Thus, even them-th user can decode thei-th user’s coded messageit cannot obtain the private informationdue to the lack of uplink informationIn this way,the exterior eavesdropping can be eliminated. In the case of using message correlation,the received signal at Eve is expressed as where we assumeN0=Ne.Since it is difficult to obtain the closed-form expression of equation(40),we analyze the upper bound of the intercept probability.Remember that all the users in setBsatisfy|hβ|2>H2,so the upper bound of the intercept probability is In this respect, the intercept probability ofis given by In this section,we provide simulation results to exhibit the security performance of the proposed scheme. We first evaluate the performance when the message correlation scheme is not used.The results are given in Figure 4,Figure 5,Figure 6,Figure 7,and Figure 8.In Figure 4, we show the intercept probability of private information changing with the power of the artificial noise in the uplink transmission period.The simulation parameters are set as:N= 30,N0= 1,H0∈{0.1,0.2},H2= 0.7, andPx= 10 dB.It can be seen that under the proposed user selection scheme,the intercept probability decreases with the increasing power of the artificial noise but tends to a lower bound.This is consistent with the theoretical result obtained in(24)and reveals that the effect of artificial noise on the security performance is limited.Observe that, compared with the traditional scheme, the proposed user selection scheme has significant superiority in the security performance,as the intercept probability in the traditional user selection scheme is 1 with the assumption ofNe=0. Figure 4. The intercept probability vs.the power of artificial noise. Figure 5. The intercept probability vs.H0 and H2: threedimensional. Figure 5 and Figure 6 show the effect ofH0andH2on the intercept probability of messages in the uplink transmission period.The simulation parameters are set as:N= 30,N0= 1,Px= 10 dB,andPJ= 20 dB.It can be seen that the intercept probability always decreases with the growth ofH2but decreases first and then increases with the growth ofH0.Therefore,there exists a smallest intercept probability if we choose a properH0.The reason for this phenomenon is given as follows.WhenH0is small,few users transmit artificial noise,so the intercept probability is large.However, whenH0is large, the value ofγe,0in (18) becomes small, which benefits the eavesdropper, so the intercept probability is also large.In this respect, the design ofH0is the key to achieve the target security requirement. Figure 6. The intercept probability vs.H0 and H2: twodimensional. Figure 7. The target transmission rate vs.H0 and H2. Figure 7 shows the effect ofH0andH2on the target transmission rateR0.The simulation parameters are set as:N= 30,N0= 1,Px= 10 dB,andPJ= 10 dB.We can see that the transmission rate monotonically decreasing with respect toH0,but monotonically increasing with respect toH2.This indicates that if relatively high transmission rate is expected,we should choose largeH2and smallH0.Obviously, this result is consistent with the theoretical analysis given in (7).In addition, combining the results shown in Figure 5 and Figure 7,we observe that largeH0, e.g.,H0>0.2, not only increases the intercept probability but also decreases the transmission rate.In this respect, to ensure relatively small intercept probability and relatively high transmission rate,the value ofH0should be controlled in a proper range,e.g.,0.05≤H0≤0.25 in Figure 5 and Figure 7. Figure 8 provides the proportion of users in setS,setB, and the users keeping silence under differentH0andH2.The simulation parameters are set as:N= 30,N0= 1,Px= 10 dB, andPJ= 20 dB.We can see that if we designH2=0.7 under the condition of= 1, a half of users will transmit private information.Moreover,withH0=0.1,the proportion of users in setSis 10%,and withH0= 0.2,the proportion of users in setSis 18%.In this respect,we can fixH2to make sure enough number of users transmitting private information,and then controlH0to manage the number of users transmitting artificial noise so that the target intercept probability is achieved. Figure 8. Proportion of users in different sets.(a): H2 =0.7,H0 =0.1.(b): H2 =0.7,H0 =0.2. Figure 9 and Figure 10 show the intercept probability of the private information in the uplink transmission when the message correlation scheme is employed.Specifically, Figure 9 illustrates the relationship between the intercept probability, the average value of Eve’s channel quality,and the time slott.The simulation parameters are set as:N= 30,N0= 1,H0= 0.2,H2= 0.7,Px= 10 dB, andPJ= 0 dB.It can be seen that the intercept probability decreases obviously with the growth of the transmission slottbut is unrelated with the CDI of the eavesdropper’s channel.In Figure 10, we compare the security performance when using or not using the message correlation scheme.It shows that although the intercept probability in the first slot(i.e.,without using message correlation) is relatively large, about 0.25, the intercept probability after several slots is very small, e.g.,4×10−5in the seventh slot.This indicates that the message correlation scheme can significantly improve the security in a short time. Figure 9. The intercept probability after using the message correlation scheme vs.the transmission slot t and the average channel quality of the eavesdropper’s channel. Figure 10.The intercept probability after using the message correlation scheme vs.the transmission slot t. Figure 11 provides the intercept probability in downlink transmissions.The simulation parameters are set as:N= 30,N0= 1,H0= 0.2,H2= 0.7,Px= 10 dB,andPJ= 0 dB.First,when the AWGN at Eve is not ignored,e.g.,Ne=1,the intercept probability is about 0.1 by using the user selection scheme.However, when the AWGN at Eve can be ignored,i.e.,Ne= 0, security cannot be guaranteed in the NOMA based downlink transmission if only the use selection scheme is employed.In this case,after using the message correlation scheme, the intercept probability in the downlink transmission is based on the intercept probability in the uplink transmission, which decreases obviously with the growth of the transmission slott.As depicted in Figure 11,just after several slots, the security can be enhanced significantly, e.g.,the intercept probability is less than 10−4after seven slots.Furthermore, it is worth noting that the intercept probability in Figure 11 reflects the security performance in both interior eavesdropping and exterior eavesdropping situations. Figure 11. The intercept probability in the downlink transmission vs.the transmission slot t. Transmission security in multiuser networks is studied in this paper.Different from the traditional schemes in which the private information in each slot is considered to be independent, we in this paper improve the security by correlating the private information transmitted in the current slot with the private information transmitted in the previous slots.Specifically, in the uplink transmission, multiple parameters are broadcast from the BS to the users to select different kinds of users transmitting private information or artificial noise.To deal with the exterior and interior eavesdropping problems existed in the NOMA based downlink transmission,we relate the transmitted information in the uplink and downlink by using the proposed message correlation scheme.As shown in the theoretical and simulation results, the security is improved with time and the uplink information can improve the security of the downlink information. ACKNOWLEDGEMENT This work was supported in part by the Fundamental Research Funds for the Central Universities(No.21620350), in part by the National Natural Science Foundation of China (No.62102167 and No.62032025) , and in part by the Guangdong Basic and Applied Basic Research Foundation(2020A1515110364). APPENDIX I This appendix is to demonstrate that the intercept probability in (22) monotonically decreases with respect to the number of users in setS.For notation simplicity,we assume wherea > b >0,x ≥1 andc >0, sof(x)>0 holds.In this respect,we have Obviously,the monotonicity off(x)is the same with the monotonicity ofg(x).The derivative ofg(x) is obtained as where step (a) is because the inequality ln(1−y)<−ywhen 0< y <1, which is demonstrated as follows.Denoteh(y) = ln(1−y) +y, and we haveh(0)=0.The derivative ofh(y)is obtained as This result means thath(y) is a monotonically decreasing function,so we haveh(y)=ln(1−y)+y APPENDIX II Assumef(x) =ax/(bx+c)witha >0,b >0,andc>0.The derivative off(x)is then given by Sincef′(x)>0,the functionf(x)monotonically increasing with respect tox.In this regard, the intercept probability given in (22) monotonically decreasing with respect toPJ.4.2 Security Performance with Message Correlation Scheme
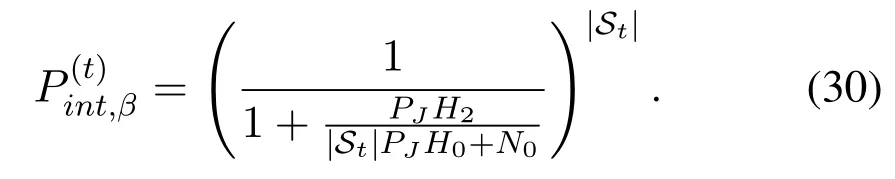

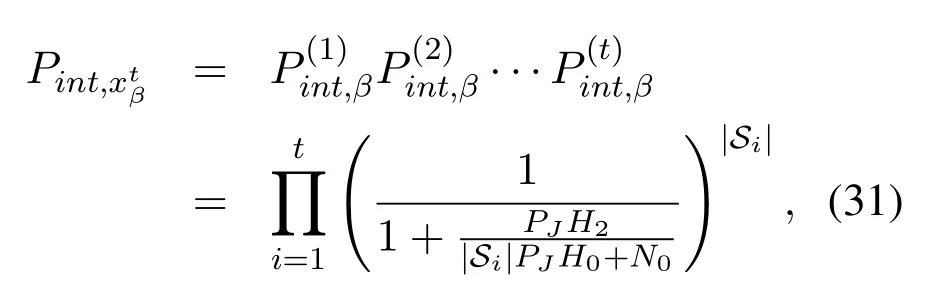
V.SECURE DOWNLINK TRANSMISSION
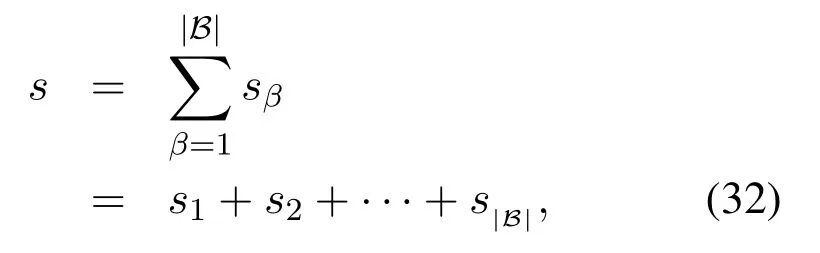
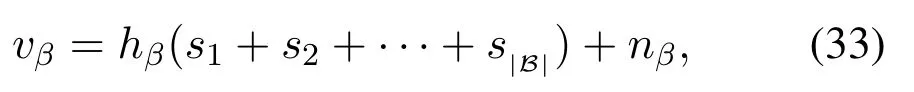
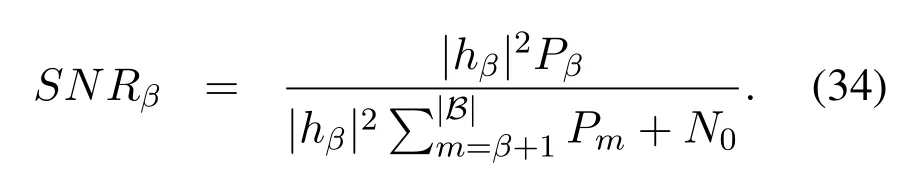
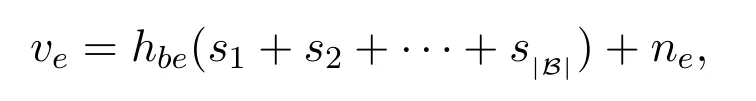
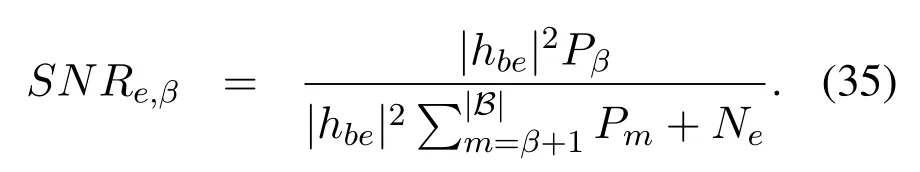
5.1 Message Correlation Scheme
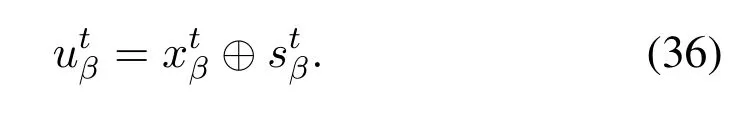
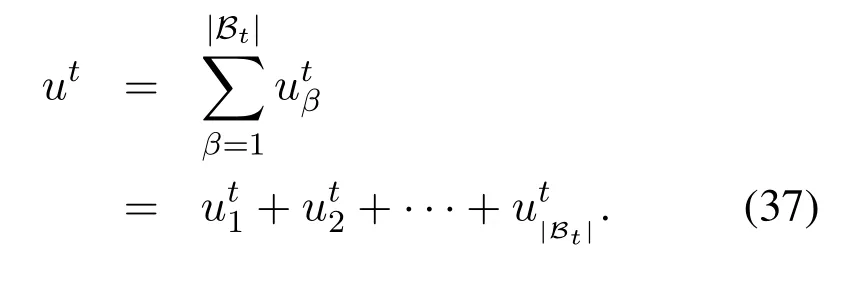
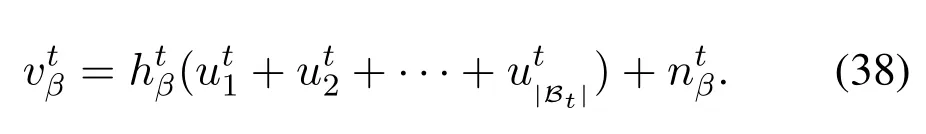
5.2 Using Message Correlation Against Interior Eavesdropping
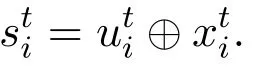
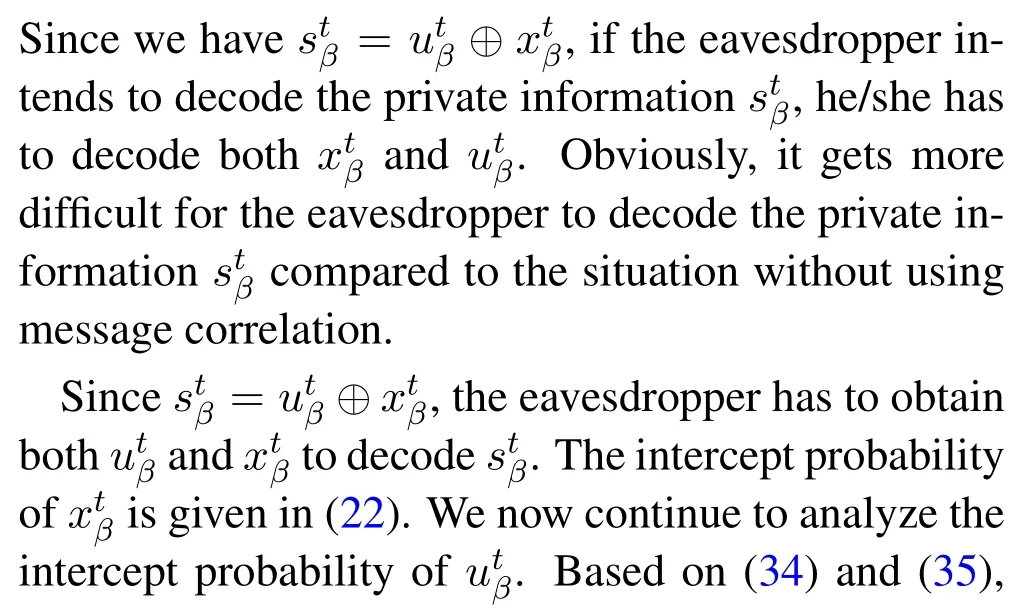
5.3 Using Message Correlation Against Exterior Eavesdropping
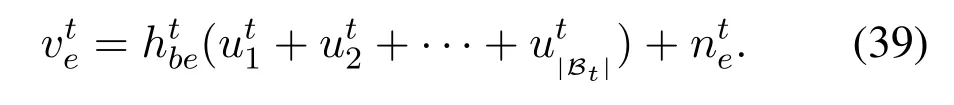
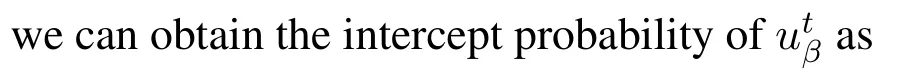
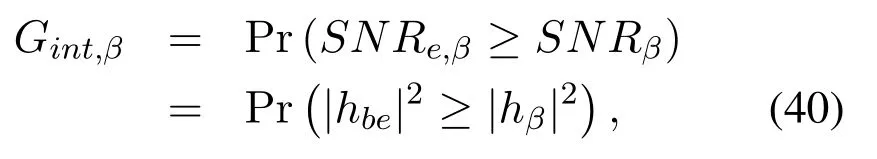
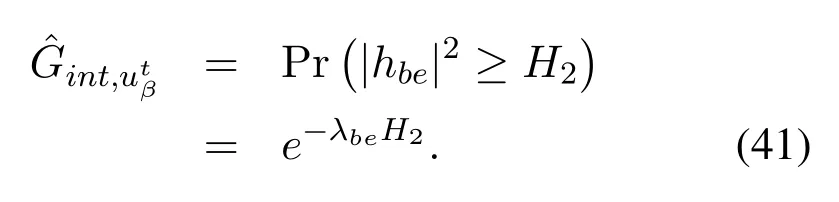
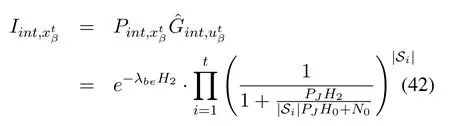
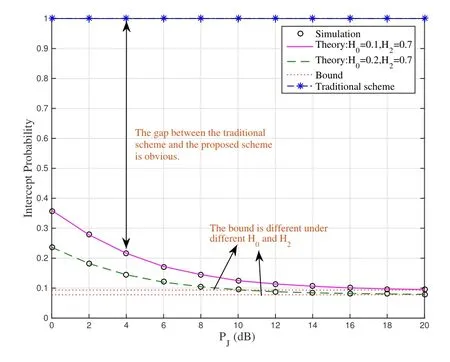
VI.SIMULATION RESULTS

VII.CONCLUSION