Preventing Hardware Trojans in Switch Chip Based on Payload Decoupling
Ke Song,Binghao Yan,Xiangyu Li,Qinrang Liu,Ling OuYang
1 Information Engineering University,Zhengzhou 450002,China
2 Tsinghua University,Beijing 100084,China
Abstract:Hardware Trojans in integrated circuit chips have the characteristics of being covert,destructive,and difficult to protect,which have seriously endangered the security of the chips themselves and the information systems to which they belong.Existing solutions generally rely on passive detection techniques.In this paper,a hardware Trojans active defense mechanism is designed for network switching chips based on the principle of encryption algorithm.By encoding the data entering the chip,the argot hidden in the data cannot trigger the hardware Trojans that may exist in the chip,so that the chip can work normally even if it is implanted with a hardware Trojans.The proposed method is proved to be effective in preventing hardware Trojans with different trigger characteristics by simulation tests and practical tests on our secure switching chip.
Keywords:network switching chip; active defense;hardware trojan;payload decoupling
I.INTRODUCTION
As the core component of electronic products,integrated circuit(IC)have been widely used in various fields such as information and communication,military and defense,health care,and artificial intelligence.Traditionally,ICs are small and simple to manufacture,so a single manufacturer can complete the entire process from design,manufacturing to testing.However,due to the increasing scale and frequency of ICs being updated as a result of incremental development,the current IC design and manufacturing process had become a highly globalized industry model,which required cooperation among different manufacturers to complete the entire process from design to final shape.This seemingly economical and efficient process has left a huge security risk for the IC.Untrustworthy entities are directly or indirectly involved in all stages of the life cycle of electronic devices or ICs,making it more and more likely that the chip will be embedded with a hardware Trojan.In addition,the spread of IP core reuse technology also makes the reliability of ICs unknown.
Hardware Trojans refer to malicious modules that are artificially added during the design or manufacturing of ICs,which can be activated under specific triggering conditions to achieve the purpose of the attacker’s acquisition of sensitive information or the destruction of key circuits[1].As a physical circuit structure,the hardware Trojan is more targeted and discreetly placed than software malicious code.Once the hardware device is manufactured,the hardware Trojan is permanent and cannot be removed by external means.Even if discovered,it can only be resolved by replacing it with new,secure hardware.To make matters worse,as attack techniques continue to improve,the potential locations and targets of hardware Trojans have become more diverse[2].Including special integrated circuits,microprocessors,network switching chips,digital signal processors,and even bit streams,may be modified and destroyed by hardware Trojans.Therefore,how to detect and prevent hardware Trojans has become the forefront of the IC security field.
Hardware Trojans detection is currently the most direct and common way to deal with IC security threats caused by hardware Trojans,and it is mainly divided into design stage detection and manufacturing stage detection according to the different detection stages[3].Among them,design stage detection,also known as pre-silicon stage detection,relies on functional verification[4,5],circuit design analysis[6]and formal verification[7,8]to test the module in the IC or IP cores from a third party to ensure the overall safety of the final IC design.In contrast,detection at the manufacturing stage is also called post-silicon detection,and can be classified into destructive and nondestructive methods according to whether the detection method will cause intrusion to the IC.Destructive detection methods typically use physical reverse engineering[9]to depackage the IC and scan for images of each layer,with the goal of getting the original design of the product and discovering hardware Trojans that may be hidden therein.Non-destructive detection methods,on the other hand,rely heavily on logic tests[10]and side-channel signal analysis[11,12]to find anomalous ICs behavior.In addition,with the rise of artificial intelligence technology,the use of machine learning techniques such as Decision Trees[13],SVM[14],neural networks[15],etc.to perform hardware Trojan detection has also become a popular approach.
However,the analysis and detection of hardware Trojans in ICs is becoming more and more difficult with the development of chip fabrication process,which requires a lot of resources and is difficult to obtain effective benefits.Destructive detection,for example,can only guarantee the safety of the IC under detection,but not universality.To make matters worse,new types of hardware Trojans are emerging,but the detection results need a reference design model or the behavioral characteristics of a known hardware Trojan to be confirmed.This makes the detection of hardware Trojans a long period of time and requires a large number of professionals to perform the detection.Therefore,it is a more economical and effective solution to employ proactive defense techniques against hardware Trojans rather than reactive detection techniques.Typical active defensive techniques that are currently receiving attention include obfuscation techniques and camouflage techniques[3].The former hides the true design structure and function of the IC by inserting a locking mechanism in the circuit,thus preventing the attacker from obtaining valuable information[16].The latter,on the other hand,adds camouflage units or dummy contacts in the design process to confuse the attacker so that the hardware Trojan cannot be easily implanted into critical parts of the circuit[17].
In summary,this paper proposes a hardware Trojan defense mechanism for network switching chips based on the idea of active defense technology.The mechanism encodes and encrypts the data entering the chip without affecting the normal data forwarding,so that the argot hidden in the input data cannot trigger the hardware Trojan that may exist in the chip,thus enabling the chip to work normally even if it is implanted with a hardware Trojan.The advantage of this method is that:(1)it does not depend on the type of Trojan horse,nor does it need to build a designed golden model,that is effective for different types of Trojans or even unknown Trojans.(2)compared with camouflage technique,it does not protect by increasing the difficulty of Trojan horse implantation,but based on the assumption that Trojan horse implantation risk can not be completely eliminated,the designed protection strategy has higher practical value and security in the case of increasingly diverse chip and IP sources and industry chain participants.(3)compared with obfuscation,it does not rely on a large number of hardware redundancy,and the security of obfuscation is proportional to the scale of hardware redundancy,and obfuscation is also a technology that interferes with Trojan horse implantation,with similar limitations as camouflage,and it can only protect functional modules designed by itself,but is limited to third-party IP.The main contributions of this paper are as follows:
1)We propose an active defense mechanism to prevent hardware Trojans in switching chips.2)On the basis of analyzing the triggering mechanism of Trojan horse in switching chip,we propose a payload decoupling-based active defense mechanism which is implemented by PRESENT encryption algorithm.3)We first analyze the effectiveness of the proposed algorithm in theory,and then verify it on simulation software and self-developed FPGA verification platform respectively.
The remainder of this paper is organized as follows:The Section II introduces the basic structure of the switch chip and the composition of the hardware Trojan.At the same time,we analyzes the possible region of the hardware Trojan in the switch chip.In Section III,the theoretical basis and specific implementation process of the payload coordination active defense mechanism is proposed.Section IV analyzes the effectiveness of the defense mechanism proposed in this article.The test results of our method on simulation and real platforms are presented in Section V.Finally,Section VI concludes the paper.
II.ATTACK PRINCIPLE OF HARDWARE TROJANS
2.1 Composition of Hardware Trojan
Figure 1 shows the basic composition model of a common hardware Trojan,which can be divided into two parts:the trigger and the payload.The former is responsible for detecting trigger conditions and activating the payload part upon receiving a specific condition(argot).The payload,on the other hand,is the attack unit of the hardware Trojans and is responsible for performing the attack operation.Normally,the trigger should be placed somewhere on the chip that is capable of receiving external input,while the payload can theoretically be located anywhere on the chip and may have more than one at the same time.Hardware Trojans parasitize the normal circuitry in a silent manner.At this point the circuit does not sense any abnormalities and the system can get a normal output after receiving excitation from the input signal through the host circuit.And when the Trojan trigger detection unit receives a specific input,it generates the activation signal required for payload activation.With the action of the multiplexer,this activation signal is transmitted to the location of the payload,enabling a pre-programmed malicious attack on the chip.
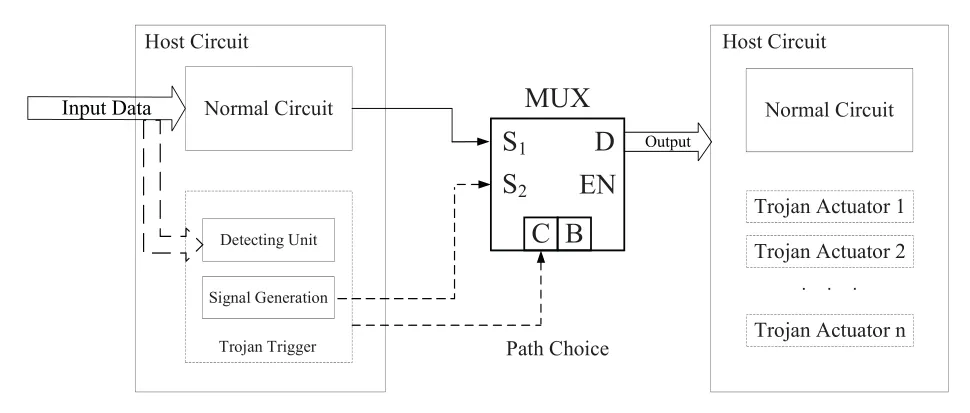
Figure 1.Hardware trojan basic model.
2.2 Switching Chip Structure
The network switching chip is at the core of today’s communication equipment by completing the forwarding processing of input data according to its characteristics.The structure of a typical network switch chip is shown in Figure 2,which mainly includes an interface unit,a combination and distribution unit and a forwarding engine.Specifically,the forwarding engine,as the core of the network switching chip,consists of hardware logic units including the parser,table lookup logic,modifier,etc.,as well as a variety of memory units that store the routing lookup table and cache data frames.
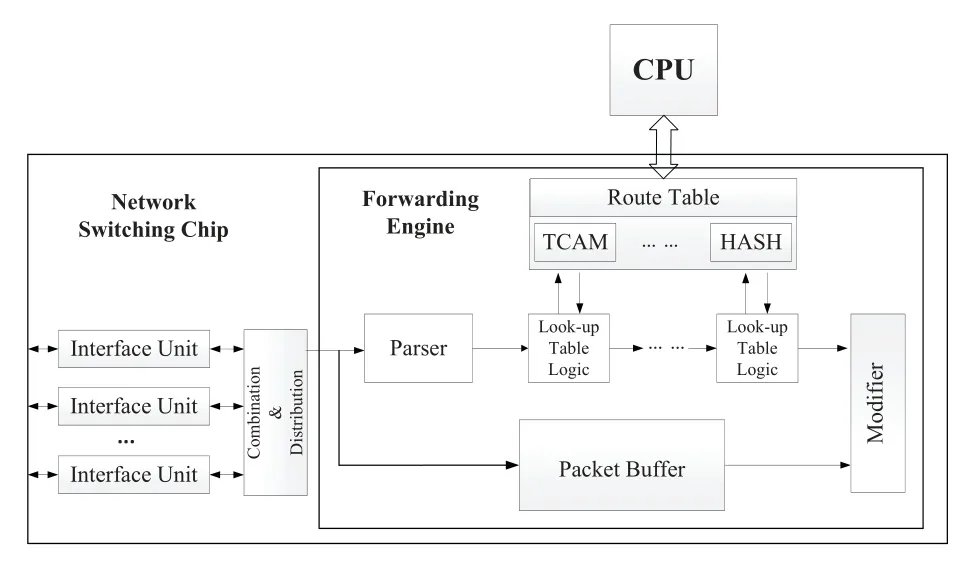
Figure 2.Typical architecture of network switch chip.
The network interface unit receives the data frames from each port,and after completing the physical layer parsing,the data link layer frames are converged to form serial data input to the forwarding engine(combination process).The data frames processed by the forwarding engine are sent to the corresponding destination port for output(distribution process).
The forwarding engine is internally connected to the CPU and a series of forwarding tables via a high-speed interface,and externally receives the data frame from the combination and distribution unit.The received data frame is cached into the packet buffer and the header of the data frame is sent to the parser along with its port information,storage address and other descriptors.
The parser parses the received descriptors and,based on the parsing results,classifies,identifies and extracts the key fields from the packets and sends them to the table lookup logic.The table lookup logic obtains forwarding information based on the values of the fields in the frame,a process that involves interaction with the CPU and the forwarding table and can be understood simply as a series of table lookup operations.After a step-by-step table lookup,forwarding information i.e.,processing operations,is finally obtained for the message,and descriptors for these operations are then sent to the modifier.The modifier fetches the data packet from the memory according to the descriptor to modify its data frame,such as replacing,adding,deleting the header field,and reencapsulating it into a new data frame for forwarding,or discarding and sending it to the CPU.
2.3 Analysis of Hardware Trojan Implantation in Switch Chip
In this section,according to the structure and working principle of network switch chip,combined with the structure of hardware Trojan Horse,the feasibility of Trojan Horse attack way and trigger way in switch chip is analyzed.
According to the purpose of attack,the types of attacks on network chips by hardware Trojan Horse can be divided into two categories:one is“destructive attack”aimed at causing failure,the other is“eavesdropping attack” aimed at obtaining confidential information.On the other hand,from the point of view of operation mechanism,the core position of hardware Trojan Horse defense lies in trigger,because Trojan Horse actuator will remain dormant if it does not receive trigger signal from trigger.Therefore,this paper focuses on the possible implantation of Trojan Horse triggers in switching chips.
Firstly,the activation path of Trojan Horse in network switching chip is analyzed.Hardware Trojan Horse needs external trigger to be activated,which determines that it must use network switch chip to interact with the external interface.The input/output interface of network switch chips mainly includes the external Ethernet interface and the internal CPU interface.Among them,the internal interface cannot communicate with external devices directly,so the hardware Trojan can only be activated through the Ethernet port and transmit stolen data
Secondly,the feasibility of hardware Trojan Horse implantation for network chip is analyzed.Hardware Trojan Horses are usually implanted through IP cores in the design stage.In addition,in the processing stage,they are also implanted through general modules of some chips.The function modules of the network switch chip,including Interface Unit,Combination Distribution Unit,Parser,Table Lookup Logic,Modifier and other components,are generally not implemented by IP core,so the possibility of the designer implanting Trojan Horse is very low.At the same time,because the attackers in the manufacturing process are not familiar with the details of chip design,it is also difficult to implant Trojan trigger and any implanted malicious programs are easy to detect.
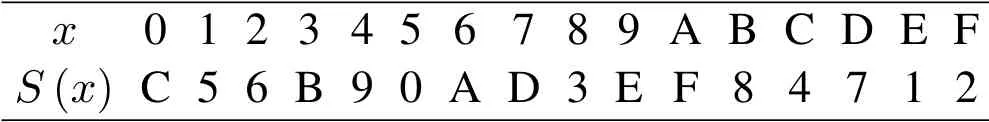
Table 1.S-Box substitution table(SA).
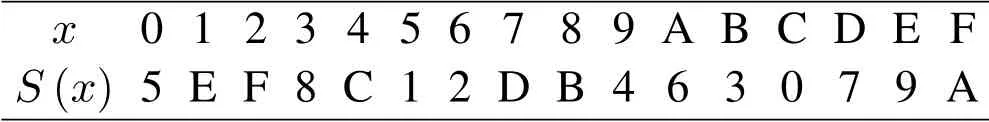
Table 2.S-Box inverse substitution table(SB).
Finally,the controllability and concealment of hardware Trojan Horse trigger code are analyzed.After combination,the data frame is cached into the packet memory,and only descriptor information is sent to the parser.Because the descriptor information field is short,most fields must conform to the relevant provisions of the protocol,so it is difficult to insert a code word to satisfy the requirement of Trojan Horse triggering probability.For routing table,although the implementation of IP core may lead to the possibility of being implanted into Trojan Horse,the probability of implanting Trojan Horse trigger is very low because it cannot directly contact with code word.Packet buffer,which also uses IP cores,caches all the data entering the switch chip,and the load information that may contain Trojan Horse activation code should also exist here.As the external raw input,these data have the best controllability for the attacker,so the packet buffer is the only component that can be conditionally implanted into the Trojan Horse trigger.
III.PAYLOAD DECOUPLING-BASED ACTIVE DEFENSE MECHANISM
3.1 Payload Decoupling-based Active Defense Mechanism
As discussed in Section II,packet buffer is the most likely component to be implanted into the hardware Trojan trigger,both in terms of the triggering needs of the Trojan and the operability of the Trojan implantation.Based on this,this paper proposes a packet buffer payload decoupling-based active defense technique.The switching chip structure with the addition of this active defense mechanism is shown in Figure 3.
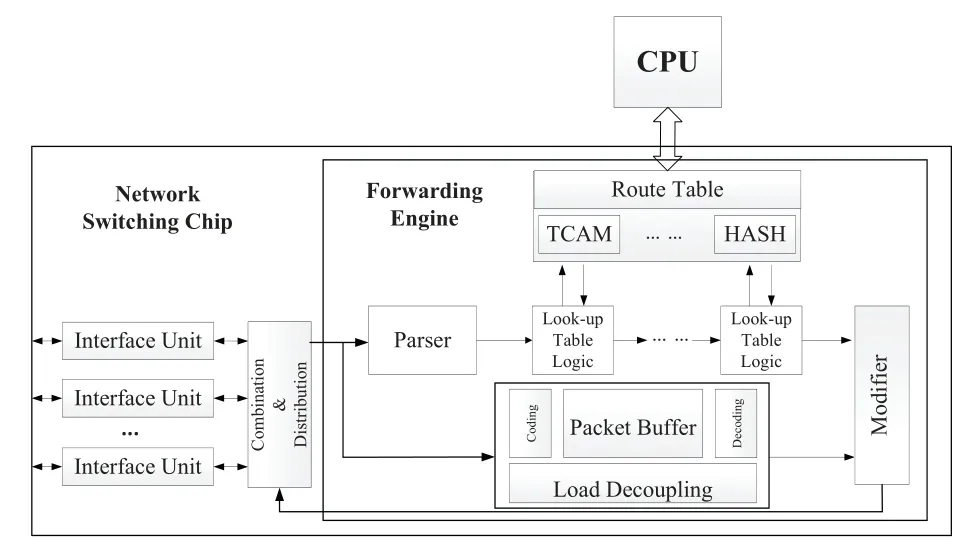
Figure 3.Switch chip architecture with payload decoupling unit.
The so-called decoupling is to destroy the hardware Trojan activation instructions hidden in the normal data,thereby eliminating the internal and external coordination conditions of the switching chip and avoiding the hardware Trojan from being triggered.The basic idea of decoupling is to change the value of the pre-selected field by encoding the data in the protection domain,and then decode the data to restore the original value when it leaves the protection domain.This process is transparent to the external operation of the chip.If there is a Trojan in the system,the instruction to activate the Trojan can be destroyed by the encode interference,thus blocking the attack path for the attacker to send a network message with special characteristics.
Plain coding methods include negation,XOR,etc.But these methods are so simple that an attacker only needs to change the“code word”in a very simple way,and it still triggers the internal Trojan payload logic.Therefore,we can learn from the methods in cryptography to destroy the high-order characteristics of the data.For example,the block encryption algorithm is used to encode the input data,and the corresponding decryption algorithm can be used as a decoding transformation.Some standard encryption methods such as DES,IDEA and AES,although the security performance meets the demand,considering the resource limitation of the network switching chip,their complete introduction will greatly affect the operating efficiency of the switching chip.Therefore,it is necessary to introduce lightweight algorithms with higher execution efficiency and less computational resource consumption.Based on PRESENT lightweight block cipher algorithm,this paper designs a de-cooperative algorithm suitable for chip-level.
3.2 PRESENT Algorithm
The PRESENT algorithm was proposed by Bogdanov et al.at the CHES2007 conference,which has excellent hardware performance and concise round function design[18].Compared with other lightweight block cipher algorithms such as Tiny Encryption Algorithm[19],MCRYPTON[20],HIGHT[21],Smart Encryption Algorithm[22]and CGEN[23],PRESENT has a simpler hardware implementation,so it is also called ultra-lightweight cryptographic algorithm.The PRESENT algorithm adopts substitution permutation network structure with 64-bit block length,supports 80-bit and 128-bit key lengths,and can iterate for up to 32 rounds.The round function of PRESENT algorithm consists of three parts:addRoundKey,sBoxlayer and pLayer.The substitution of sBoxlayer is completed by 16 4*4 S-boxes,which is the only non-linear process in the algorithm.
a.addRoundKey:64bit input is XOR with round key.Letbj,(0≤j ≤63)be the current state andki,j,(0≤i ≤63,0≤j ≤63)be the j-bit subkey of the round keyKi,then the transformation is as follows:
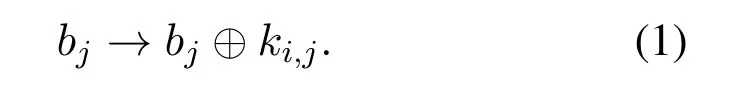
b.sBoxlayer:The result of addRoundKey and 64bit input is input into 16 4-bit to 4-bit S-box to get the result.For sBoxlayer,the current stateb63...b0is considered as sixteen 4-bit wordsw15...w0wherewi=b4∗i+3‖b4∗i+2‖b4∗i+1‖b4∗ifor 0≤i ≤15,The output transformation is as follows:
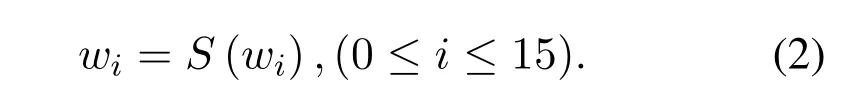
The substitution tables and inversion tables of S-box are shown in Table 1 and 2 respectively:
c.pLayer:The 64bit state of S-box substitution is rearranged by P-permutation matrix to enhance the diffusion effect of plaintext.The substitution tables of P-box are shown in Table 3.
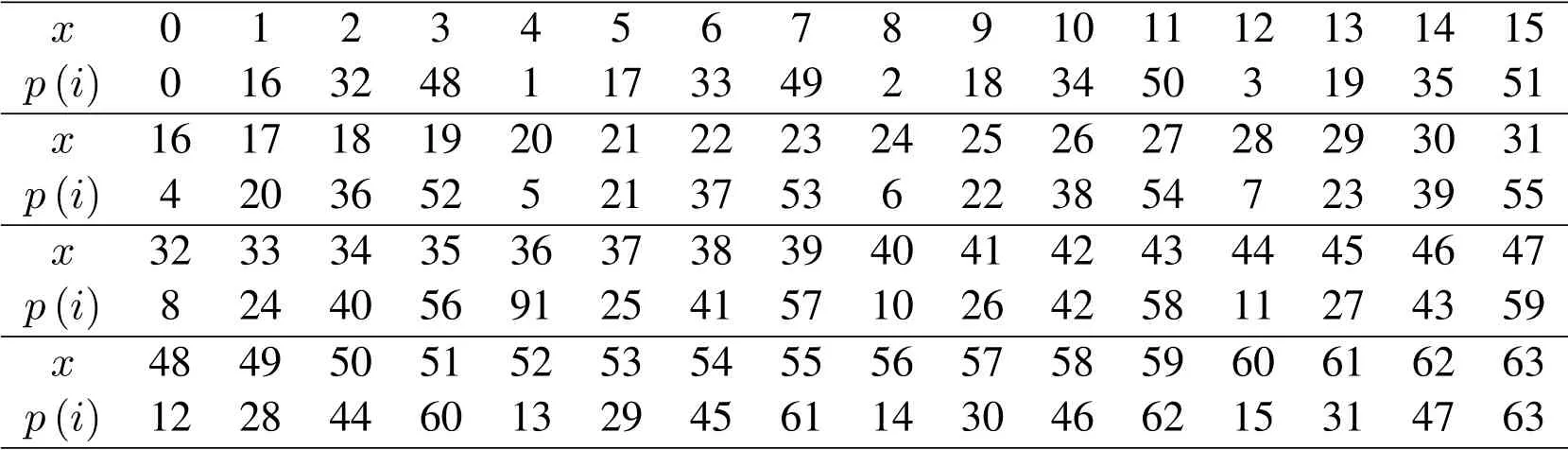
Table 3.P-Box substitution table.
3.3 Present-based Payload Decoupling Algorithm
The decoupling algorithm proposed in this paper includes the coding and the corresponding decoding,which are inverse to each other,and both have a common unknown random number called the key.The introduction of key is also of great significance to the decoupling algorithm,which can enhance the randomness of the output data and realize the unpredictability of the output results.The requirements of the decoupling algorithm include:
a.When the key is unknown,the attacker cannot control any number of bits in the output of the decoupling algorithm to make it equal to a specific value or have certain characteristics.
b.The output result is related to the key,that is,the same input results in different output because of different keys,and the output result is almost uniformly distributed in the whole value space when the key obeys the random uniform distribution.
c.When the key is unknown,it is difficult to construct two inputs so that the results of different key decoupling are equal.
d.The length of input and output data is equal in the variable code algorithm,and the output range space is larger than or equal to the input range space.
When using 128-bit key,two S-boxes are used to update the key,and 128-bit registers are needed,which adds additional gates and power consumption.Therefore,considering the application scenario of the chip in this paper,the 80-bit key is selected for payload decoupling.
1)Input Encoding
Considering the security of the algorithm and the complexity of the circuit implementation,the encoding part in this paper adopts a three-round function iteration structure.In each round of operation,the corresponding sub-keys are selected from the key register to participate in the operation,and the S-box substitution table in Table 1 is selected in the S-box substitution process.At the same time,the Tag_OPT selection label is set,and the label instructions are used to decide whether to decouple with the data,so as to facilitate the maintenance of the follow-up test verification process.
Two kinds of round functions are involved in the three-round operation of the decoupling algorithm:Round Function and Final Function.A common round function includes addRoundKey layer,sBoxLayer and pLayer as shown in Figure 4,while the Final Function,i.e.the third round operation,only needs addRound-Key instead of sBoxLayer and pLayer.
The flow chart of the algorithm for general round function is shown in Figure 5.Among them,addRoundKey is the XOR operation of input data and 64-bit sub-keys bit by bit.P64 represents the replacement according to the contents shown in Table 3,the input of the table is the location of each bit before the replacement,and the content of the table is the location of the bit in the 64-bit result after the replacement.The hardware design of the algorithm is implemented by hard connection.
2)Output Decoding
According to the related properties of PRESENT algorithm,its encryption and decryption processes are very similar.Therefore,the decoding algorithm also adopts a three-round round function iteration structure.Figure 6 is the flow chart of decoding algorithm.Compared with Figure 5,there are two changes:first,decoding is the inverse process of coding,so the Sbox inverse substitution table(SB)shown in Table 2 is used to replace the S-box substitution table.Secondly,the round key needs to participate in XOR module operation after the P64 replacement module.
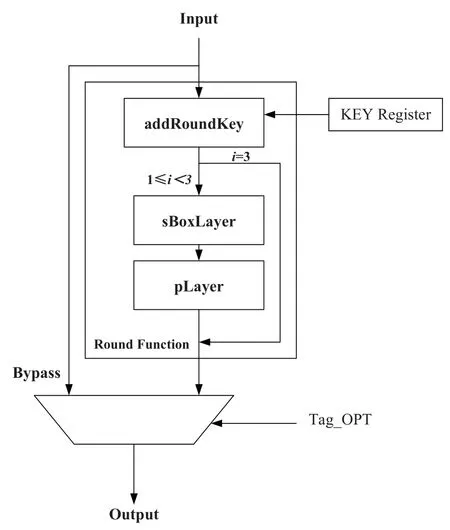
Figure 4.Data path structure of round function for decoupling algorithms.
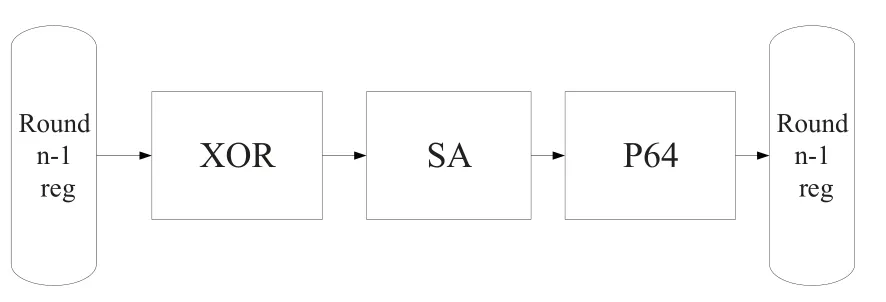
Figure 5.Coding Round Function Operational Flow Chart.
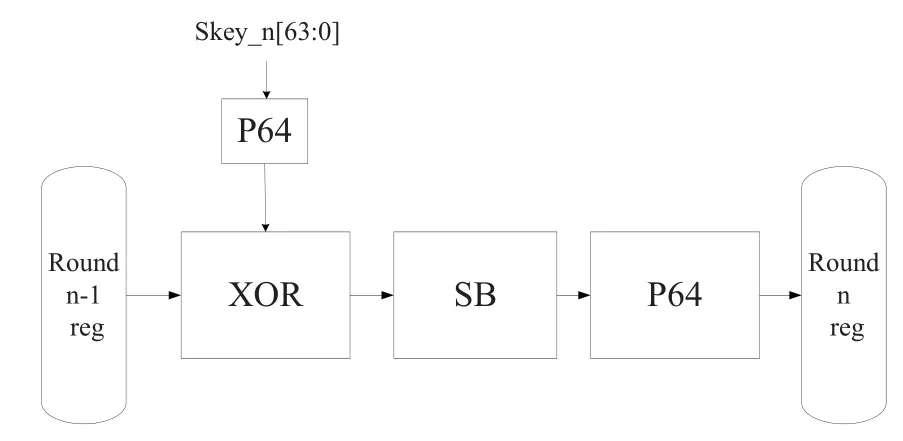
Figure 6.Decoding round function operational flow chart.
3)Key Management
Key management refers to maintaining the encoding key corresponding to each part of the input data,so that it can obtain the key used in the original encoding when decoding,so as to decode it correctly.This process involves the design of key update and maintenance mechanism.
For key update,if the key is fixed,the attacker can search and collide by constantly changing the value of the cryptographic field,traversing the whole value space,and triggering conditions will inevitably occur.Therefore,the life cycle of the key(the number of messages processed)must be less than the degree of the value space determined by both the cryptographic field and the key length.Once the randomized key generation mechanism is adopted,the key corresponding to the data frame arrived at different times will be different.Therefore,the system must have a key maintenance module to record the key values corresponding to each data frame and the coding algorithm used.It is necessary to store the key of the block coding algorithm used by each data frame in the buffer at the same time,and when the data frame is removed from the buffer,the decoding key needs to be synchronized to the decoding unit.
This paper considers the balance between performance and security,so the key expansion function is implemented by bit-shifting,which combines cyclic shift register and S-box permutation operation.The user-supplied key is represented ask79,k78...k0,after generating the round keyKi,the keyKi+1is updated by the following methods:
a)the key register is rotated by 61 bit positions to the left:
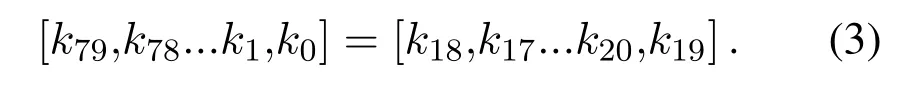
b)With the 4bit S-box of PRESENT,the highest 4bit input of the key K after the cyclic left-shift operation is replaced,that is:
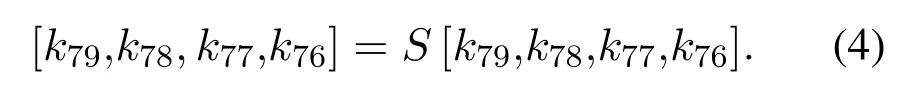
c)Bit-oriented XOR operations are performed with the current number of encryption rounds andk19,k18,k17,k16,k15:
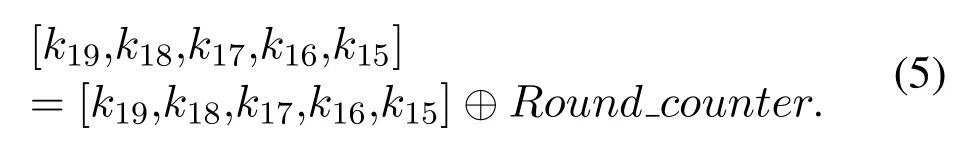
WhereRound_counteris the current number of encrypted rounds.
IV.ALGORITHM VALIDITY ANALYSIS
4.1 Statistical Distribution of Encoding Output
Ideally,the input data processed by the encoding algorithm should be changed randomly into an unknown number.Therefore,in order to maximize the entropy of the output results,we should make the probability of all possible output results equal for any input,that is,to obey the uniform distribution.As described below,the output value of the coding algorithm in this paper is evenly distributed between 0−264−1 for any given input value under the condition that the round key is evenly distributed.
Set the input data as a(64bit),and the round key of the first round as k.According to the PRESENT algorithm,the first step is addRoundKey.Let its output be b,that is b=a⊕k.For any bit biof b,its probabilities of 0 and 1 are respectively:
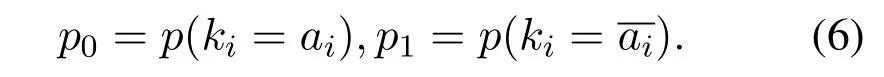
Since k satisfies a uniform distribution andp0=p1=1/2.Therefore,no matter what the value of a,b is uniformly distributed.Secondly,in the second step of the PRESENT algorithm,the block is divided into 16 4-bit small blocks,each of which performs 4-bit-to-4-bit bijective function.So when b is uniformly distributed,S(b)is also uniformly distributed.At the same time,the key in this design is generated by the random number generator,so it can also be considered that it is approximately uniformly distributed.In conclusion,the maximum entropy can be obtained by the algorithm.
4.2 Nonlinearity
The nonlinear transformation in the encoding algorithm is implemented in the sBox layer.Figure 7 shows the 4-bit input-output transfer function curve in the sBox of the present algorithm.
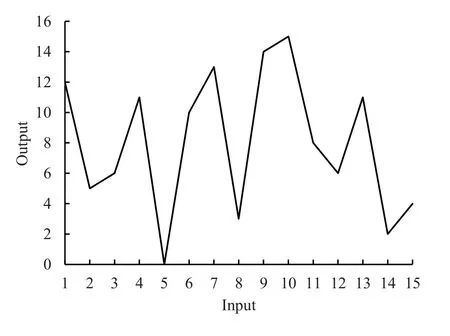
Figure 7.4-bit input-output transfer function curve in the sBox layer.
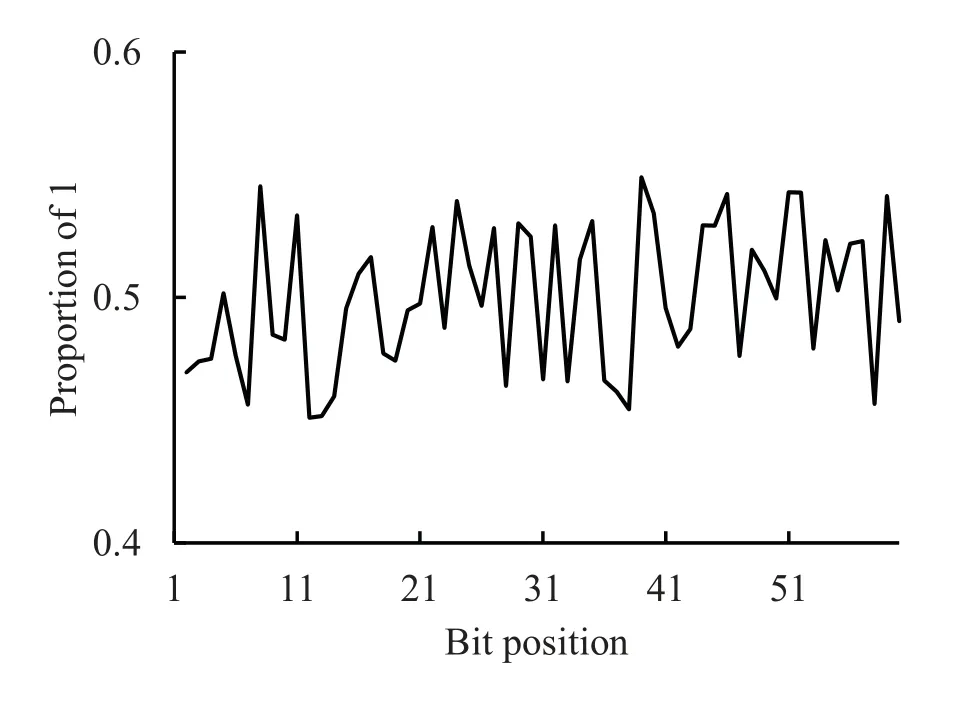
Figure 8.Experimental results of avalanche effect.
It can be seen from the figure that the encoding has very high nonlinearity and irregularity.Therefore,it can destroy the nonlinear characteristics whose order is lower than it.For attackers,if they want to achieve higher-order nonlinear feature extraction,they need to use more complex logic.A typical method is to realize the inverse transformation of the sBox to counteract the influence of the sBoxlayer transformation.However,due to the irregularity of this transformation,it is impossible to find a logic circuit with a complexity much lower than that of it.Therefore,we think that to overcome the impact of the encoding process,attackers need to implement logic with the same complexity as the implementation of sBox.Meanwhile,due to the large-scale requirements of the logic circuit of Sbox(a 64 bit packet data needs 16 S boxes),for the concealment of Trojans,it can be considered that it is not feasible to use Trojan trigger logic in a certain scale chip.
Further,it is considered that the attacker takes the result after the inverse transformation of the first round transformation as the trigger condition.Because the attacker cannot predict the key,the impact of the last round of addkey cannot be directly eliminated.The only way is to use higher-order static features,that is to say,it is possible to construct a higher-order feature that remains unchanged before and after addkey.However,since multiple rounds of transformation are used in this implementation,the Sbox layer in the penultimate round will destroy this higher-order feature.Due to the existence of the addkey layer,the attacker cannot use the inverse S-box transformation again to eliminate the impact of the penultimate round of Sbox.Therefore,in order to ensure the safety,3 rounds of transformations are used in this algorithm to ensure that the coding process is highly nonlinear.
4.3 The Differences Brought by the Encoding Algorithm
In attacks,it is also very common to use the correlation between input data at different times to construct dynamic features as trigger conditions.Although the output value of the same data input at different times will be different due to the dynamic change of the key,if the difference between the encoded data and the original data is small,there may be accidents.
Considering the worst case,the input data changes only 1 bit after addkey,that is,the difference between two identical inputs after encoding is only a single bit.The PRESENT algorithm is designed to ensure that the sBOX has a difference of at least 2 bits for singlebit output,so the results after the first round of sBOX have a difference of at least 2 bits.
Moreover,pLayer makes the 4-bit output of the same sBOX be sent to different sBOXs of the next round.In this way,the change of each bit will cause a difference of at least 2 bits in the second round,that is,the minimum difference after the second round is 4 bits.By analogy,considering that our design uses three rounds of iterations,there will be at least 8-bit differences in every 64 bits.
V.EXPERIMENTAL SIMULATION AND ANALYSIS
In this section,experimental verification of our proposed decoupling-based active defense mechanism is carried out on simulation software(Matlab)and experimental platform(FPGA).Theoretically,the Trojan payload may be located anywhere inside the chip.Since the function of decoupling technology is to block the triggering of Trojans,our test mainly focuses on the triggering behavior of Trojans.The location and specific functions of the Trojan payload have nothing to do with this technology,which can be simply designed as a trigger counting logic to count the number of times the Trojan trigger logic output signal is triggered during the test.
5.1 Avalanche Effect and Diffusion
Since the decoupling algorithm in this paper uses block encryption,we first verify whether the encryption algorithm is effective.The test items include avalanche effect and diffusion.The avalanche effect is used to evaluate the randomness of encryption algorithms.If a certain block cipher or encryption hash function does not show a certain degree of avalanche characteristics,it is considered to have poor randomization characteristics,so that the cryptanalyst can only rely on the output to guess the input.Diffusion means that each bit in the cipher text is affected by multiple bits in the plaintext and has reached completeness.In order to reduce the experimental overhead,the key is kept unchanged during the test.Obviously,the performance brought by the dynamic change of the key in the actual scenario is more powerful.
Figure 8 shows the results of the avalanche effect.In the experiment,we randomly select a bit of the input data to flip,and count the proportion of 1 in each bit after the decoupling algorithm is processed.The experiment was performed 10,000 times to ensure unbiasedness.Figure 9 shows the results of the algorithm diffusion.Unlike the avalanche test,where only a single bit is changed,the number of bit flips in the diffusion test is 4 consecutive bits,and the other experimental parameters are the same as the avalanche effect test.From the experimental results,it can be seen that the proportion of 1 in each bit of the output has produced a significant difference,which proves that the algorithm we proposed has a strong avalanche effect and strong diffusion when the key remains unchanged.
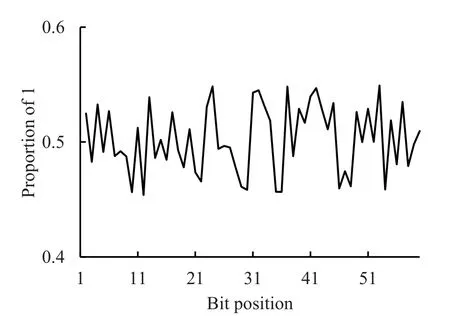
Figure 9.Experimental results of diffusion.
5.2 Simulation Results of Trojan Defense
We selected five common hardware Trojan trigger modes in the switch chip to verify the defense ability of the decoupling algorithm,including specific sequence trigger mode,sequence calculation trigger mode,repeating data trigger mode,Hamming weight trigger mode and Hamming distance trigger mode.
1)Specific Sequence Trigger Mode
This mode triggers the Trojan in the hardware by matching the specific bit sequence hidden in the input data.We randomly selected six different input data,corresponding to six different specific positions and specific bit sequences,respectively.In each group of experiments,the input data is fixed,and each operation is 10000 times under two conditions.Whether the bit value at the selected position in the result of decoupling is consistent with the input data is counted.At the same time,we also generate 10000 groups of random numbers randomly and match with the trigger characteristics of each group of experiments,and count the matching rate.As can be seen from Figure 10,the output data processed by the decoupling algorithm is consistent with the randomly generated data in terms of matching probability,which indicates that the decoupling algorithm has strong confusion,making the specific sequence set by the attacker similar to the random trigger mode,and cannot carry out targeted attacks.
2)Sequence Calculation Trigger Mode
The trigger condition of this attack mode is that the input sequence after some calculation matches the Trojan sequence.The experimental results are shown in Figure 11.Except for the trigger conditions,the experimental process and configuration are the same as the specific trigger sequence mode.It can be seen from the experimental results that the proposed decoupling algorithm can also obtain the same performance guarantee as random matching for this type of attack.
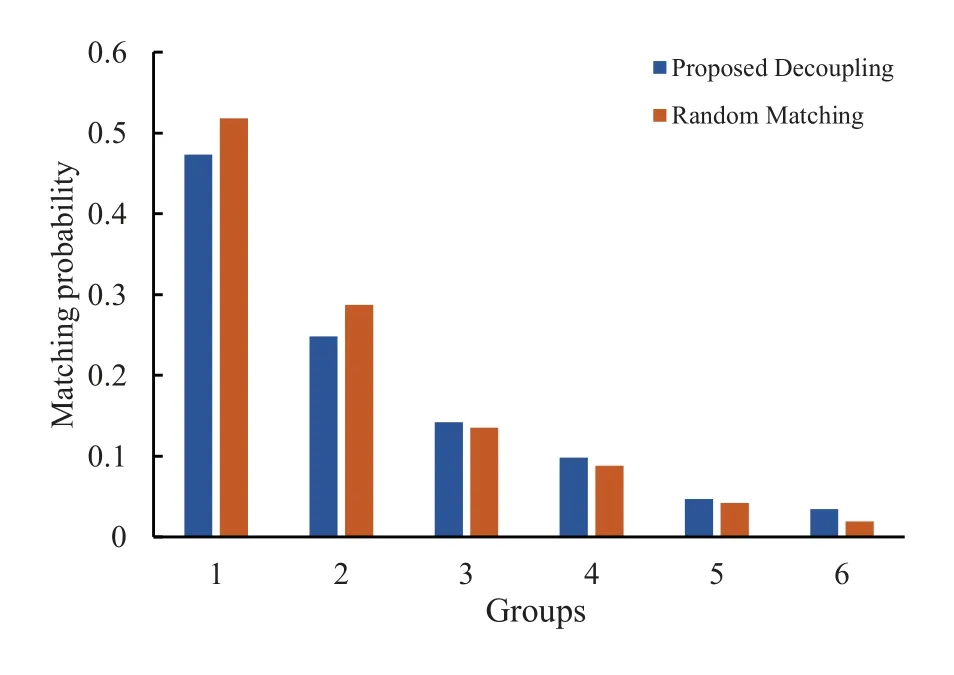
Figure 10.The comparison results of decoupling and random matching with the specific sequence trigger mode.
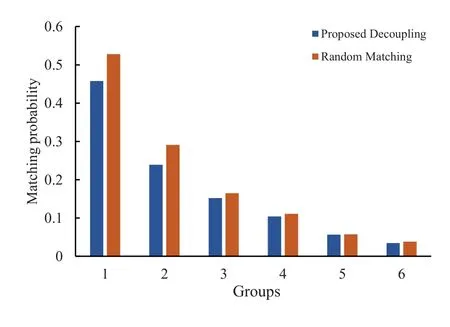
Figure 11.The comparison results of decoupling and random matching with the specific calculation trigger mode.
3)Repeating Data Trigger Mode
The attack pattern considers the matching relationship between the packet data,not the specific data sequence.That is,when the sequence composed of multiple data packets is processed,there is a specific relationship between different packets,and the cumulative occurrence times of this phenomenon are taken as the trigger condition.For example,the same packet appears several times in succession.The experimental results are shown in Figure 12.Except for the trigger conditions,the experimental process and configuration are the same as the specific trigger sequence mode.It can be seen from the experimental results that the proposed decoupling algorithm can also obtain the same performance guarantee as random matching for this type of attack.
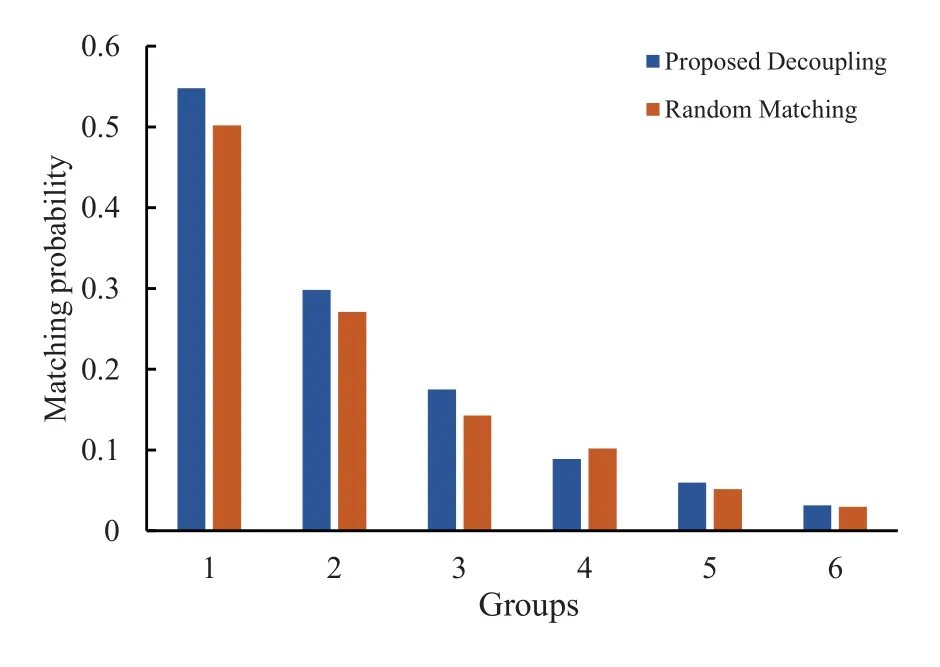
Figure 12.The comparison results of decoupling and random matching with the repeating data trigger mode.
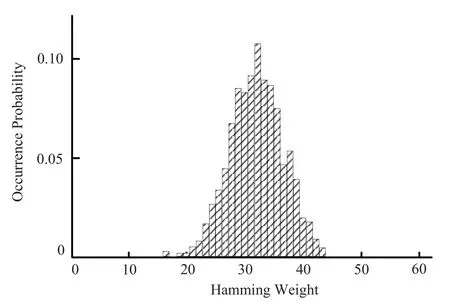
Figure 13.Hamming weight distribution.
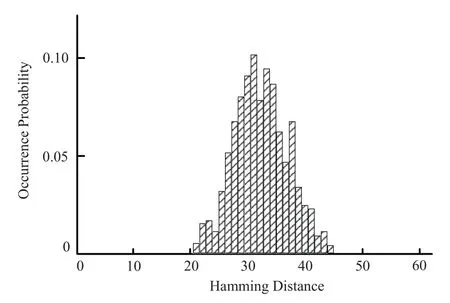
Figure 14.Hamming distance distribution.
4)Hamming Weight and Hamming Distance Trigger Mode
Hamming weight trigger mode activates the trigger signal by calculating the Hamming weight of the output data.In the experiment,several 64 bit data with fixed Hamming weight were input to obtain the statistical data of Hamming weight.In contrast,Hamming distance trigger mode activates the trigger signal by calculating the Hamming distance between multiple outputs.The experimental results of the two trigger modes are shown in Figure 13 and Figure 14 respectively.It can be seen from the figure that the Hamming weight and Hamming distance between the output data under the two modes conform to the Gaussian distribution with the mean value of 32,reflecting the antiattack ability of the de-cooperative algorithm to these two trigger modes.

Figure 15.FPGA validation platform.
5.3 Trojan Attack Test
Based on the above simulation experiment results,we further conducted a Trojan defense test on our selfdeveloped FPGA verification platform,as shown in Figure 15.The test process adopts the white box test plugging technology,which is,the Trojan horse is actively implanted into the tested chip,and then triggered by external data to calculate the success rate of the Trojan.
Different from the attack types used in simulation test,we redesigned four more complex Trojan trigger type that are more suitable for hardware,including false trigger,fixed mode,static high-order mode and dynamic mode.The specific trigger conditions are shown in Table 4.
The experimental parameters and results are shown in Table 5.We test the Trojan trigger results of the four attack modes when the de coordination algorithm is turned on and off.It can be seen from the table that when the de-cooperative algorithm is turned off,the Trojan horse placed in the switch chip can be triggered many times.In contrast,when the de-cooperative algorithm is turned on,the Trojan horse is not effectively triggered under the four trigger modes.
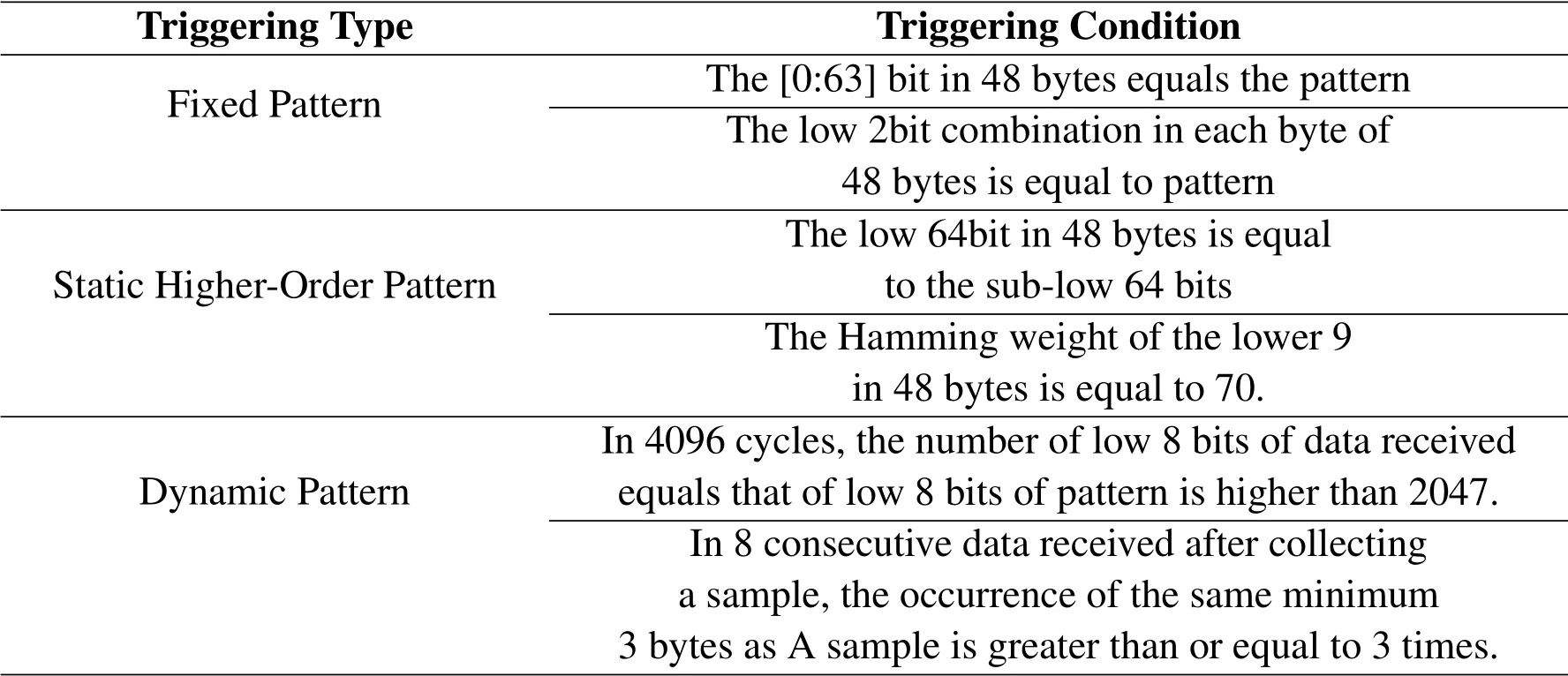
Table 4.Triggering type and triggering condition.
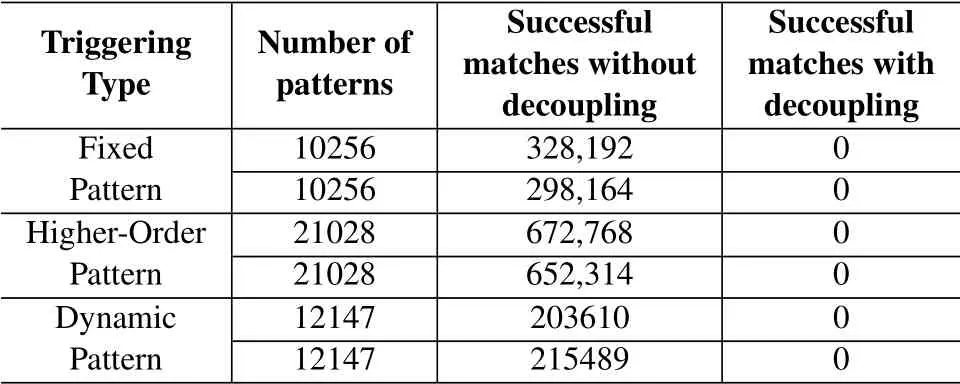
Table 5.The experimental parameters and results.
In summary,it can be seen that the proposed hardware Trojan defense mechanism of payload decoupling can effectively block the activation of argot ofTrojan triggers for various types of attacks on the basis of good availability of the algorithm,and keep the hardware Trojan payload in sleep state.
VI.CONCLUSION
Aiming at the possible hardware Trojan in IC chips,this paper proposes an active defense mechanism of hardware Trojan in network switch chips based on payload decoupling.The core idea of the algorithm is to encode the data into the chip,change the trigger instructions of the hardware Trojan hidden in the data,so that the hardware Trojan in the chip cannot get the activation information and has been in a dormant state,which ensures that the chip can work normally even if it is implanted into the hardware Trojan.
The decoupling encoding mechanism proposed in this paper is based on the analysis of the network switching chip,but its principle is to block the possible hardware Trojan trigger conditions by encrypting the original data,and does not depend on the specific circuit architecture.In addition,there are memory modules inside all chips,which are also in line with the Trojan implantation position analyzed in this paper.Therefore,the mechanism and coding algorithm proposed in this article can be applied to many integrated circuit chips,which are of great reference value in effectively responding to and defending against increasingly rampant hardware Trojan of IC chips.
- China Communications的其它文章
- Two-Timescale Online Learning of Joint User Association and Resource Scheduling in Dynamic Mobile EdgeComputing
- SHFuzz:A Hybrid Fuzzing Method Assisted by Static Analysis for Binary Programs
- SecIngress:An API Gateway Framework to Secure Cloud Applications Based on N-Variant System
- Generative Trapdoors for Public Key Cryptography Based on Automatic Entropy Optimization
- A Safe and Reliable Heterogeneous Controller Deployment Approach in SDN
- Distributed Asynchronous Learning for Multipath Data Transmission Based on P-DDQN

