SecMVX:Analysis on the Vulnerability of Multi-Variant Execution
Bingzheng Li,Zheng Zhang,*,Xiaomei Wang,Sheng Qu,Jiangxing Wu
1 State Key Laboratory of Mathematical Engineering and Advanced Computing,Zhengzhou 450001,China
2 China National Digital Switching System Engineering and Technological R&D Center,Zhengzhou 450002,China
Abstract:As an active defenses technique,multivariant execution(MVX)can detect attacks by monitoring the consistency of heterogeneous variants with parallel execution.Compared with patch-style passive defense,MVX can defend against known and even unknown vulnerability-based attacks without relying on attack feature information.However,variants generated with software diversity technologies will introduce new vulnerabilities when they execute in parallel.First,we analyze the security of MVX theory from the perspective of formal description.Then we summarize the general forms and techniques for attacks against MVX,and analyze the new vulnerabilities arising from the combination of variant generation technologies.We propose SecMVX,a secure MVX architecture and variant generation technology.Experimental evaluations based on CVEs and SPEC 2006 benchmark show that SecMVX introduces 11.29%of the average time overhead,and avoids vulnerabilities caused by the improper combination of variant generation technologies while keeping the defensive ability of MVX.
Keywords:multi-variant execution; software diversity;cyberspace security
I.INTRODUCTION
In the process of system-level software development,due to the limitations of programming languages(such as C and C++)and the lack of security knowledge of software developers,software inevitably has such vulnerabilities as buffer overflow,dangling pointer,and memory leakage.For example,in the software development process,although the use of third-party libraries and reference to open source code and other code reuse methods can significantly improve development efficiency,it also brings about the problem of software homogeneity.Widely used in Internet programs and websites,OpenSSL is a open-source cryptography software library package.A severe security vulnerability named heartbled in its encryption code(cve-2014-0160)has caused a significant impact.The same vulnerability is widely spread by code reuse,which provides convenience for attackers and brings colossal cybersecurity risk.
Researchers have proposed a variety of measures to prevent software vulnerabilities.In response to control-flow hijacking attacks,early studies have proposed stacks[1],Data Execution Prevention(DEP)[2],Address Space Layout Randomization(ASLR)[3],and other defense methods that can effectively resist code injection attacks.However,these methods are easily bypassed by code reuse attacks such as returnto-libcReturn[4,5]and Return Oriented Programming(ROP)[6].Control Flow Integrity(CFI)[7]restricts the transfer of program control strictly under the predefined control flow graph at runtime and can resist code injection,code reuse attacks,and memory information leakage.However,it is not easy to find a balance between performance and security.Data-oriented Programming(DOP)[8]uses non-control data attack methods to achieve Turing complete attacks.It can bypass fine-grained control-flow integrity defense.Both offensive and defensive confrontations are declining,and passive defense methods are often easily bypassed by new attacks,unable to deal with the threat of unknown vulnerabilities.
Cox[9]first proposed in 2006 to use Multi-Variant Execution(MVX)to solve software security problems.As an active defense method,MVX uses software diversity technology to generate variant sets,distributes program input to multiple variants with the same function and different structure,executes in parallel,and sets checkpoints to detect attacks by comparing the execution states of variants.The attacker must attack all variants in MVX simultaneously without triggering voting detection,which is almost impossible.
In recent years,researches on MVX mainly focus on the realization of MVX security defense architecture mechanisms and the balance of security and performance.In 2017,Stijn[10]added a thread clock synchronization and parallel mechanism and used lockstep to sequence system calls in multi-threads,which solved thread scheduling in MVX basing on the GHUMVEE[11]and ReMon[12]MVX architecture.For the first time,multi-thread parallelism is supported in the software MVX architecture.
In 2019,Osterlund S[13]applied MVX technology to the operating system kernel for the first time.kMVX uses address space layout randomization to partitions the kernel memory space and construct two kernel variants.When the system call is executed,the two kernels process at the same time and the execution result is synchronously checked to determine whether there is a kernel memory leak.Generally,the existing MVX regards the kernel as a secure and reliable environment and is committed to solving the security problem of software in the userspace.However,kMVX shows that there are still vulnerabilities to be solved in the kernel,and MVX can also be applied to kernel security defense,thus providing a broader research perspective.
Voulimeneas A[14]first proposes DMON,a distributed ISA heterogeneous MVX,which make use of different hardware security mechanisms of arm and x86 to improve the security of MVX further.HeterSec[14]implements multivariate execution on heterogeneous ISA.Unlike DMON,which monitors and judges variant processes at the user level based on ptrace,HeterSec is implemented in Linux kernel,adding a dynamic kernel loading module to support synchronization communication of distributed variant processes at the user level.
Mimic defense[15]is an active defense technology against unknown vulnerabilities proposed by our scientific research team.The core idea is Dynamic Heterogeneous Redundancy(DHR).Compared with MVX,the dynamics and feedback mechanism makes the mimic defense system have an endogenous uncertainty effect.
At present,researchers mainly evaluate the defense effect of MVX by establishing threat models and verifying attacks based on related vulnerabilities[16].The following shortcomings are:The first is that the assumptions are insufficient when establishing the threat model,and the security analysis and demonstration of the implementation of MVX is inadequate.The second is the lack of discussion on the defects in the implementation of the MVX.Will the simple combination of variant generation techniques bring safety gains? Is the greater the number of variants,the more secure in MVX? Our research shows that the MVX is not unbreakable and lists several possible exploits.During the implementation,an effective combination of variant generation technologies is required to construct a secure MVX.
To summarize,our contributions are threefold:
1)Analyze the security of MVX from the perspective of formal description.
2)We summarize the general forms of attacks against MVX,and analyze four specific attack exploitation techniques.
3)We propose SecMVX,a method for constructing a set of variants for a more secure MVX.
4)Our results show that SecMVX successfully reduces the attack surface in the MVX and costs little performance loss.
II.BACKGROUND
2.1 Formal Description of MVX
A technology that runs parallel by a set of variants with the same function but different structures is called multi-variant execution.The essence of software vulnerabilities is an abnormal transition of the program state caused by a series of program logic errors such as pointer out of bounds,buffer overflow.Attackers can illegally use those errors to access or damage the system without authorization.In software security,the MVX system distributes a given input to all variants for parallel execution.Assuming that the program is fully functional,for regular input,no abnormal transition of the program state will occur,and consistent output can be produced.For illegal input,due to the variants’ different program structures,the abnormal conversion of the program state will cause inconsistent program states between different variants,that is,inconsistent output results.By setting checkpoints reasonably and comparing the output results of multiple variants or intermediate states’signs,attack behaviors can be detected.
Define the checkpoint set[D0,D1,D2,...].When the program runs to a checkpoint(such as an I/O system call),a check of the program status is triggered.Define program execution as a set of state sequence transitions:[S0,S1,S2...].Assuming that the number of variants is 3,during the execution of MVX,the state of the MVX program at checkpointDiis expressed as:.From checkpointD0toDi,the execution of MVX is expressed as:The state sequence at the checkpoint is a subset of the entire MVX state sequence.
In the state sequence at the checkpoint,different variant process states are semantically equivalent,while non-semantic attributes are diverse.Assuming that the process’s semantics has nothing to do with the memory layout,the memory layout is a non-semantic attribute and can be diversified.Define the mapping functionMap()to represent the mapping from the stateof the variant process set[P1,P2,P3,...]to the stateof the original process[P0]at the checkpointDi.Define the conversion functionsTjandTo,whose function input is the input and state of the variant processPjand the original processPoat a specific checkpoint.Its output is the next state of the program execution.The state of the last checkpoint represents the final state of program execution.
Equivalence under normal execution.We can get the following equation:
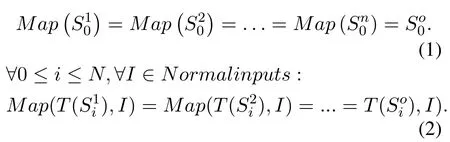
Assuming that MVX synchronizes all the variants at each checkpoint,the above equation represents the equivalent properties under normal execution.
•Equation 1 shows that all variants are in an equivalent initial state,which can be directly mapped to the original process’s state.
•Equation 2 shows that given regular input,the conversion function in all variants has an equivalent mapping relationship with the original process at each checkpoint.
•Equation 2 also shows that all variants produce the same output as the original process,thus ensuring semantic equivalence.
Attack detection:Assuming that the initial state of MVX is not attackable,Equation 1 is always satisfied.In MVX system,it is necessary to construct heterogeneity so that when an attacker tries to attack the program,the multivariate mapping relationship does not satisfy Equation 2.Equation 2 shows that if attack behaviors such as control flow hijacking and memory leak occur after checkpointDi,Equation 2 becomes invalid due to heterogeneous attributes.The sequence of variants statesat checkpointDimust be different.Whenever there is an inconsistency in the states of MVX variants,an attack is detected.
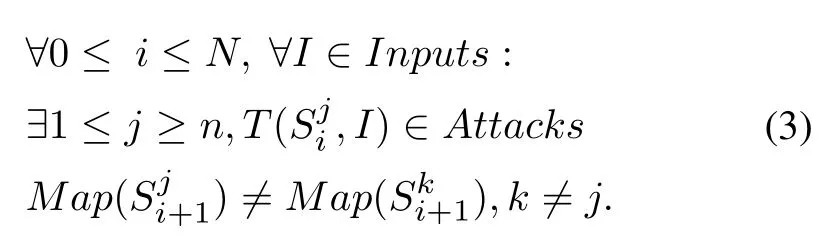
2.2 Variant Generation Technology
MVX uses variant generation technology to construct heterogeneity,which makes variants under attack inconsistent,thereby detecting attack behavior.Software diversity[17]is the basis of variant generation technology.Software diversity technology usually destroys the assumptions of a particular attack through randomization and has a defensive effect on the attack.Software diversity can be combined with MVX to construct variant heterogeneity.Software diversity can generate variants from different granularities.According to the classification of diverse technologies,the common variant generation technologies are shown as below:
•Instruction-level diversityincludes instruction set heterogeneity and instruction set randomization.Instruction set heterogeneity[13,18]generally use distributed technology to run variants on two different instruction set architectures(for example,x86_64 and aarch64).Executable flie formats and memory space layouts are different in different instruction set architectures,and attackers cannot use program vulnerabilities to carry out attacks.Dynamic binary translation(DBT)[19,20]system dynamically translate an executable binary code in one ISA into the binary code in a different ISA,which can be used to build instruction-level MVX.The MVX with heterogeneous instruction sets can also defend against attacks against micro-architecture vulnerabilities.Instruction set randomization[21,22]encrypts machine instructions and decrypts them during execution.The encryption algorithm is at risk of being cracked by an attacker when a single process is executed.In MVX system,different keys are used to encrypt machine instructions,making it impossible for an attacker to inject valid code.
•Memory level diversityincludes ASLR[3],stack layout randomization[23],heap layout randomization[24],data randomization[25,26]and other technologies.ASLR randomizes the heap and stack’s base address at runtime,combined with the -fPIE compilation option to generate position-independent code.The base address of the code segment and data segment can be randomized,but each memory segment’s content will not be randomized.The stack layout randomization rearranges the data variables in the stack with a finer granularity.The introduction of data and code padding can further increase diversity,and at the same time,eliminate the gadget code that ROP attacks rely on[27].Nevertheless,this technology needs the support of the compiler.Data randomization includes data layout randomization and XOR data randomization,so that attackers cannot read the real data stored in the memory.In recent years,the research of memory-level randomization technology has mainly focused on runtime randomization[28,29].However,due to the complexity of the implementation and excessive runtime overhead,it has not been applied to MVX.
•Function-level diversity including system call number randomization[30],library function mapping randomization[31],function parameter randomization[32],function block randomization[33]and other technologies.When the system call number is used alone for randomization,the random space of the system call number is small,and it is easy to be blasted by the attacker.(There are 436 system calls in Linux-4.19.104.)However,the system call numbers of different variants in MVX are different,and the attacker cannot initiate system calls.Library function mapping randomization maps library functions to random virtual addresses when the program is loaded and requires operating system support.The function parameter randomization is supported by the compiler,which disrupts the parameters’order,making it impossible for an attacker to use the function.Function block randomization increases the difficulty of ROP attacks.
Suppose the variant generation technology reduces the probability of a successful attack to the probabilityPwhen used alone.In that case,theoretically,using the n-variant generation technology can reduce the probability of a successful attack toPn.However,an inappropriate combination of variant generation techniques in MVX maybe destroy security assumptions and introduce a new attack surface.We will discuss attacks against MVX,analyzes the attack surface exposure problems of the combined use of variant generation technologies in Section III,and proposes methods to build more secure MVX in Section IV.
III.ATTACKS AGAINST MVX
Based on the defense principle of MVX,it can be known that the premise for an attacker to attack the MVX architecture is that each variant has exploitable vulnerabilities.As shown in Figure 1,there is a stack overflow vulnerability in the program,and an attacker can overwrite memory object C from memory object A.In MVX,the memory randomized variant generation technology is used to generate three variants with different memory space layouts.The memory object C of Variant 3 is located at the low address of memory object A.The attacker cannot attack Variant 3 and variants set containing Variant 3 in MVX system.However,in the multi-variant execution system composed of Variant 1 and Variant 2,although the address of memory object C is different,they are all located at the high address of memory object A.Attackers may still launch the following attacks:
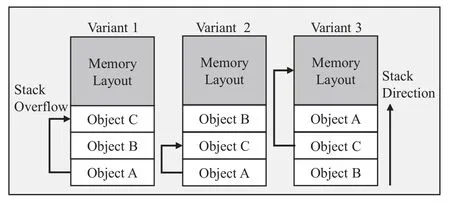
Figure 1.Stack layout of MVX.
1.Parallel attack:the attacker constructs input from memory object A to continuously write 2 offset target data across the boundary and simultaneously covers the memory object C of two variants.
2.Serial attacks:Perform two attacks separately.The first attack crosses the boundary by one unit covering the memory object C of Variant 2.The second attack crosses the boundary by two units to offset the memory object C of Variant 1.
The above attack will cause the memory object B to be overwritten,so the prerequisite for a successful attack is that the write to the memory object B will not trigger the check.Based on the above two types of attacks,this section analyzes the attack primitives commonly used by attackers and analyzes four possible attack techniques based on specific types of memory vulnerabilities.
3.1 Attack Primitives and Attack Targets
As shown in Figure 2,the attack primitives commonly used by attackers are as follows.
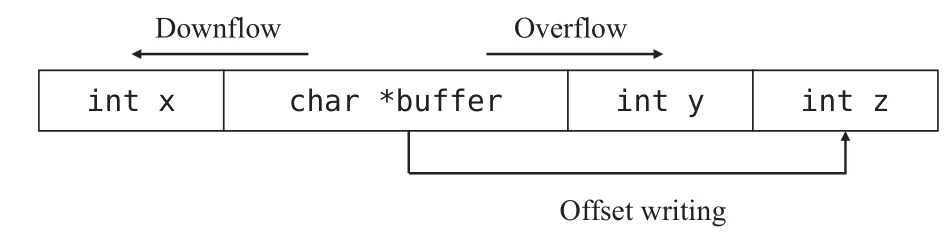
Figure 2.Attack primitives.
1.Overflow:construct super-long data and write to the upper buffer beyond the buffer boundary.The data stored in the upper-level buffer,the previous instruction’s pointer,or the output content of other programs can be maliciously tampered with by attackers.
2.Downflow:Construct ultra-long data to trigger the buffer to overflow.The lower buffer stores the next instruction’s pointer or the output content of other programs,which can be maliciously tampered with by attackers.
3.Offset writing:The attacker can write any value at any offset from a memory object.
The attack primitive triggers program state changes by illegally reading and writing target data in memory,gaining permissions,leaking memory data,or hijacking programs and executing malicious code.The following types of status changes indicate a successful attack:
1.Data tampering:Write the selected value to the selected object.For example,write the value 1 to auth_level to achieve privilege escalation.
2.Function hijacking:Write the address of the selected function to a specifci object.For example,write the address of the grant_access function to the return address to implement arbitrary code execution.
3.Data attributes:In some cases,the data constructed by the attacker only needs to satisfy specifci attributes to achieve the goal.Assume that the 32-bit value is_admin is used as a flag.Write any non-zero number to is_Admin implements the operation of raising authority.
In reality,attackers face many restrictions.For example,because the program checks the input data format,an attacker must write a value that is both the function address and a valid ASCII string.Due to the limitation of memory layout,the attacker can only overflow the buffer by a fixed number of bytes to avoid program crashes caused by tampering with non-target data.Due to the limitation of some memory variables,attackers can only write double word values.
3.2 Attack Exploitation
This section discusses attack exploitation techniques for MVX system.In specific attack examples,the combination of different variant generation techniques will introduce new attack surfaces.
3.2.1 Offset Return Attacks
As shown in Figure 3,there is an overflow vulnerability in-memory object A.The attack’s target is to overwrite the return address of the program and change the current return address to func1 to func2 to complete the control flow hijacking.In MVX system,ASLR makes the virtual addresses of func2 different in the three variants.Variant 3 uses stack layout randomization technology,and its stack layout is different from the other two variants.
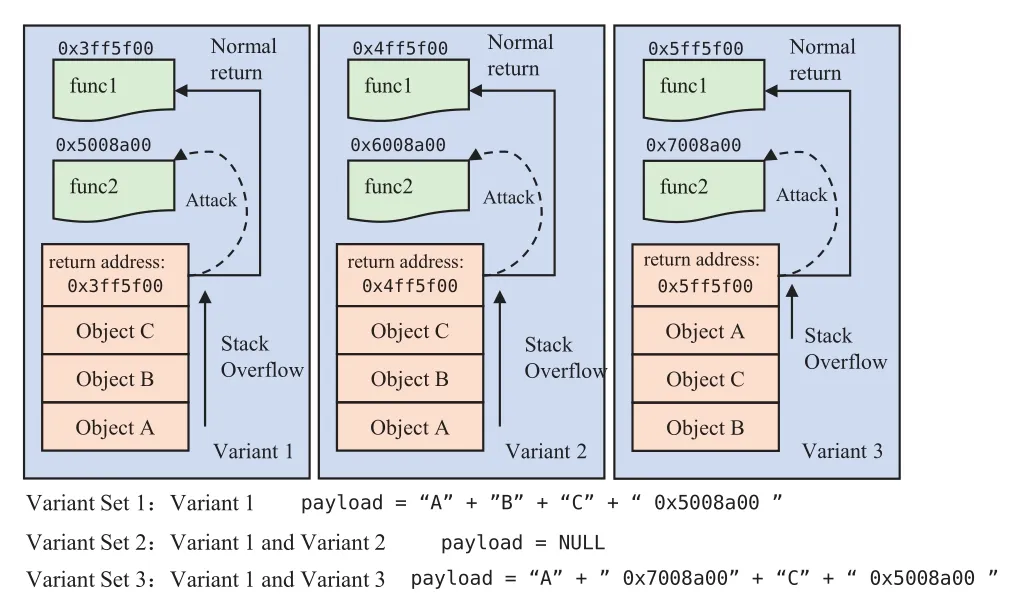
Figure 3.Offset return attack.
In Variants Set 2,the func2 of Variant 1 and Variant 2 are mapped to different addresses,and the return address in the stack is offset by three units from the memory object A in the two variants.Since any attack can only use a single valid payload to cover the same value in the return addresses of two variants,the attacker cannot tamper with the return addresses of the two variants to func2 at the same time.In this variant combination,the address space layout is randomized without stack layout randomization,preventing control-flow hijacking attacks based on stack overflow.
In Variants Set 3,stack layout randomization is added in Variant 3,introducing a new attack surface in MVX system.The relative offset of memory object A of Variant 1 and Variant 3 differs from the return address.A single sufficient payload can be constructed,and the corresponding func2 address can be written into the return addresses of Variant 1 and Variant 3 to implement parallel attacks on MVX.In this variant combination,the stack layout randomization is added,but the control flow hijacking attack is introduced,which is called”offset return attack.”Similarly,randomization of the heap layout will also introduce a new attack surface.
3.2.2 Offset Data Attacks
Data randomization technology performs an XOR operation with the mask when data is written into the memory to hide the real data’s meaning.In MVX system,the data are illegally written by the attacker is different from the values obtained by the XOR operation of different variant masks,which leads to inconsistency.However,under certain circumstances,the attacker only needs to write random values to satisfy the data attributes,change the program’s state,and implement operations such as privilege escalation.
Assuming the program uses integers as Boolean flags,any value other than zero is”True.”The branch is judged as”False”during normal flow.Writing any non-zero random number can tamper with the branch.The attacker does not need to completely control variants’data consistency and only needs to meet specific data attributes to achieve the attack.The attacker uses a random value to overwrite the storage buffer length variable,likely increasing the buffer boundary.Increased buffer boundaries will lead to further memory corruption attacks.We call this type of attack an offset data attack.Offset data attack will cause the program to appear”data attribute”status change.
3.2.3 Data Padding Attacks
In MVX,due to different variants’ different memory layouts,once a payload writes the same data into the non-corresponding memory area of different variants,a vote will be triggered with significant probability.When the target of the attack is to tamper with the program’s user name,the user name variable addresses of different variants are different,and the user name in one variant may be overwritten.In contrast,the function pointer in the other variant is overwritten.The attack is discovered when the function pointer is called,and the states of variants are different.
Data padding can randomize the memory layout,but inserting data padding(meaningless 0x00)in the variant may introduce a new attack surface.If the attacker’s payload covers the target object of Variant 1 while covering invalid data filling in other variants,he can attack Variant 1 independently of other variants without triggering checkpoint detection.In turn,the entire MVX system can be attacked by serially attacking each variant.For example,before the trigger program accesses a function pointer,each variant’s function pointer is rewritten in turn.
In MVX system shown in Figure 4,the difference from Figure 2 is that there is only one memory object in the stack.Data padding is introduced to randomize the stack layout of the variants.Like the attacks analyzed in Section 3.2.1,the stack overflow vulnerability can be used to attack successfully.However,in this section,the return address written by the attacker covers the invalid padding in Variation 1.Data padding weakens the defense capabilities of MVX system.
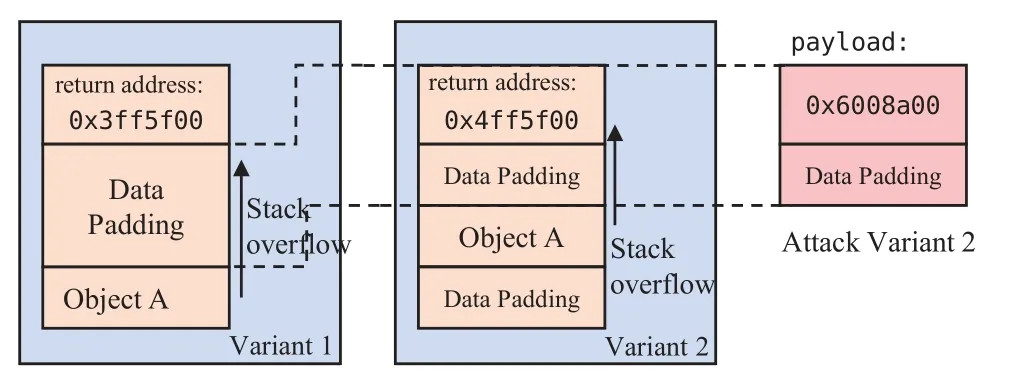
Figure 4.Data padding attack.
3.2.4 Cross-stack-frame Attacks
The application of stack protection technologies such as SafeStack[34]in MVX may lead to new attack exploitation techniques.After SafeStack is applied,the memory object on the unsafe stack is adjacent to the last function call’s hazardous stack object.The base address pointer and return address are located on the safe stack.The attacker can overflow from the nonsecure stack to the non-secure stack of the last function call without triggering a vote by rewriting the base pointer and return address.
IV.SECURE MULTI-VARIANT EXECUTION
Cases of attacks against MVX show that improper use of variant generation technology will create a new attack surface for attackers.This section discusses how to construct a secure MVX system.This paper combines randomization and deterministic layout and proposes a secure variant generation technology called SecMVX,which can effectively avoid the attacks described in Section 3.2 to defend against unknown vulnerabilities.
4.1 Design of SecMVX
Figure 5 shows a schematic diagram of the variant set structure.Variant 1 and Variant 2 use ASLR to relocate the stack base address,stack base address,data segment base address,and code segment base address.Two variants have different data random keys.The inner frame of the variant indicates the relative layout of the memory segment of the variant.The relative address offset of the same color’s memory segment in Variant 1 and Variant 2 is the same.In a single memory segment(stack,heap,or code segment),the same offset overflow of memory object A of different variants must fall on the same target object.This combination of variants prevents the attacker from launching an offset return attack.
As shown in Figure 5,Variants 3 and 4 turns on ASLR and data randomization like Variant 1 and Variant 2,and relative offset within the memory segment is fixed.The layout of the heap,stack,and data segment of Variant 3 and Variant 4 is different from that of Variant 1 and Variant 2 by using various compilation methods such as reverse stack,stack layout randomization,and heap layout randomization.This will further improve the ability of MVX system to defend against buffer overflow vulnerabilities.
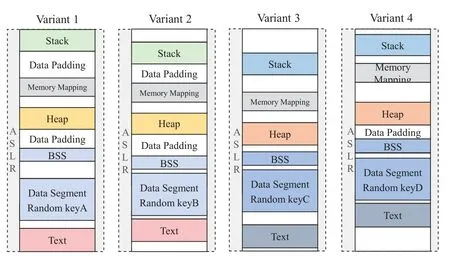
Figure 5.SecMVX variants set memory layout.
In order to defend against the offset data attack,the cross-check mechanism is added during the variant generation process,passing critical data(such as conditional branch judgment variables,user authority variables)to the monitor and checking whether the data values in each variant are consistent.Assuming that the memory variable is_admin is a conditional branch judgment variable,is_admin=0 is a regular user,and a non-zero value means that it has administrator rights.An attacker can hijack the branch by writing a non-zero value to all variants and gain administrator privileges.After the cross-check mechanism is enabled,the same value written to the memory address of all variant is_admin variables will be masked with the different variants’ keys.Different non-zero values will be passed to the monitor and detected as inconsistent.
4.2 Implementation
Based on MultiCompiler[34],this paper uses the secure multi-variant execution architecture described in Section 4.1 to improve the variant generation technology and builds SecMVX in the MVEE[35],a MVX system.The variant generation process of SecMVX is shown in Figure 6.Clang compiles the source code into LLVM IR.LLVM Passes performs stack layout randomization and data randomization conversion in the middle layer to generate two sets of twin variants IRs.Clang then compiles them to generate binary files and enable ASLR in the MVEE to build SecMVX.
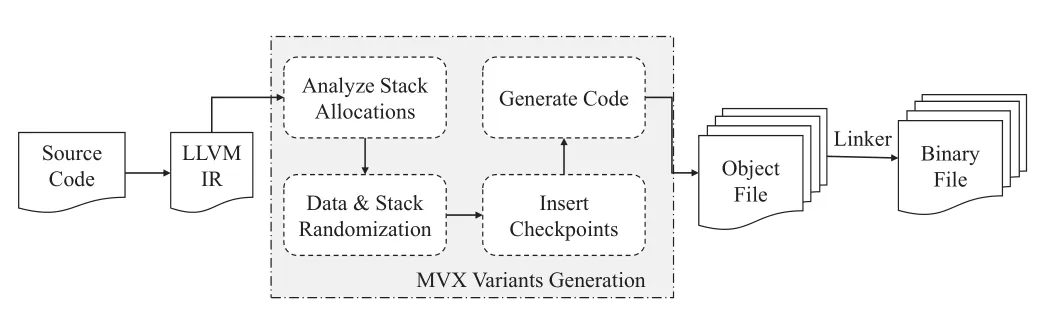
Figure 6.SecMVX variants generation.
4.3 Evaluation
4.3.1 Security
This article selects CVE vulnerabilities in open source programs to test SecMVX and evaluate the defense effect of SecMVX.Table 1 shows the detailed information and test results of related vulnerabilities.The first four CVE vulnerabilities have been tested in the MVEE.Attacks can be detected in the parallel execution environment of the two variant processes.SecMVX can also defend against such vulnerabilities,showing that SecMVX and MVEE have the same defense capabilities.
The wget network file download tool has a stack overflow vulnerability,numbered CVE-2017-13089.Since the fd_read function in the source code does not check whether the length parameter contlen is a negative number when writing HTTP response data(user input)into dlbuf,the attacker can construct a specific long long integer negative value,overwrite the write buffer,and cause a stack overflow vulnerability.Although the two variant processes using stack layout randomization and ASLR generation in MVEE can detect inconsistent outputs in I/O input and output system calls,attackers can still tamper with the return addresses in the stack of the two processes through offset return attacks.In SecMVX,when an attacker tries to hijack the control flow,it causes a segfault in one of the twin variant processes,thereby detecting the attack.This shows that SecMVX further reduces the attack surface of program vulnerabilities compared to MVEE.
Furthermore,we use the ROP vulnerability gadget detection tool Ropper[36]to scan the benchmark program,the MVEE programs,and the binary code of the SecMVX programs to compare the number of gadget codes and evaluate the effectiveness of SecMVX in defending against ROP attacks.After obtaining all the binary code gadgets,we classify the gadgets in the multi-variant execution program according to the following judgment rules:
1.In the source binary code,all gadgets are valid gadgets.
2.In MVEE binary code,if the same gadget has the same address in the two variants,it is a valid gadget; if the two variants’ gadget address is different,it is an invalid gadget.
3.In SecMVX binary code,the same gadget has the same address in the four variants and is a valid gadget;in the four variants,any gadget with a different address is an invalid gadget.
The experiment uses the SPEC CPU Benchmark 2006 CINT assembly part of the benchmark test program.The original program is compiled with the GCC-7 compiler,all program compilation options are-O0,and the experimental results are shown in Table 1.Both MVEE and SecMVX use memory lay-out randomization technology to generate variant programs,eliminating most of the gadgets in the program.SecMVX has four variant programs.Compared with MVEE’s two variant programs,its random space is more extensive,indicate that NOP code filling further eliminates ROP gadgets.
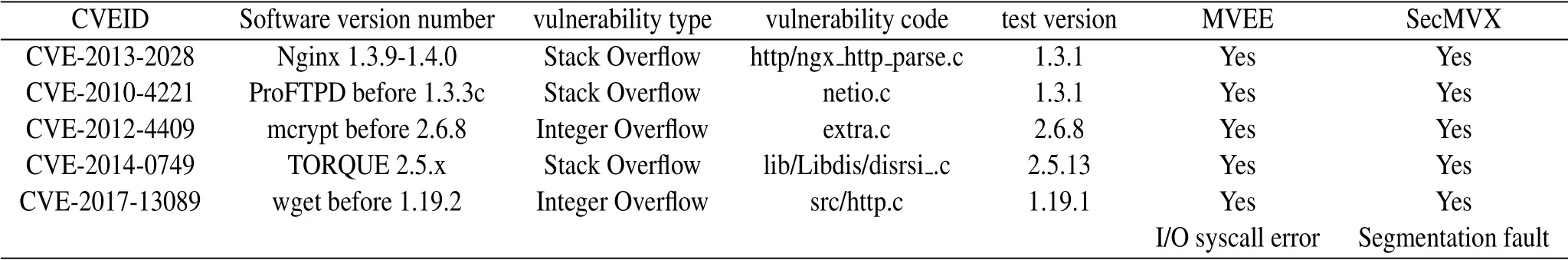
Table 1.Evaluation results based on real vulnerabilities.
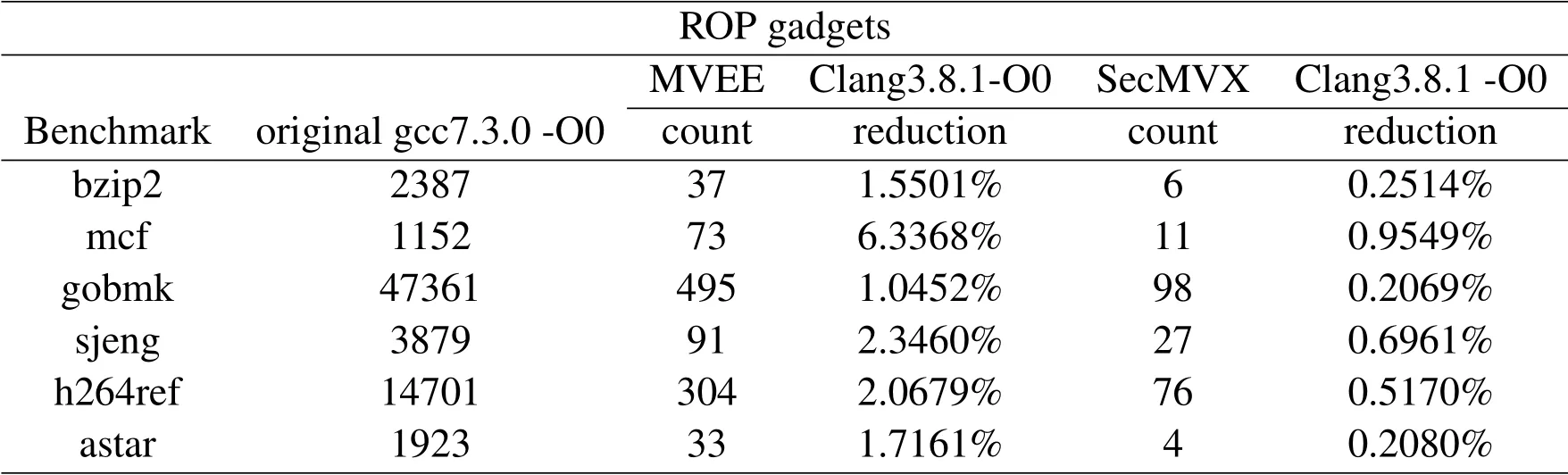
Table 2.ROP gadgets test results.
4.3.2 Performance
To evaluate the additional overhead that SecMVX brings to program operation,we use the CINT assembly in SPEC CPU Benchmark 2006.We separately run the benchmark program and SecMVX program three times to measure the average time and memory overhead.The experiment runs in Ubuntu 18.04,the CPU model is Intel Silver 4210,the memory capacity was 32GB,and the LLVM version was 3.8.1.
As shown in Figure 7,the average time overhead of calculating SecMVX using geometric mean is 11.29%.Compared with the MVEE using two variants in a multi-core environment,the net increase in the performance loss of SecMVX is smaller.At the same time,more significant security gains are obtained.In test samples,there is a sample 429.mcf that has a higher than average time cost.429.mcf is a memoryintensive program that requires a maximum of about 1.7GB of memory during operation.
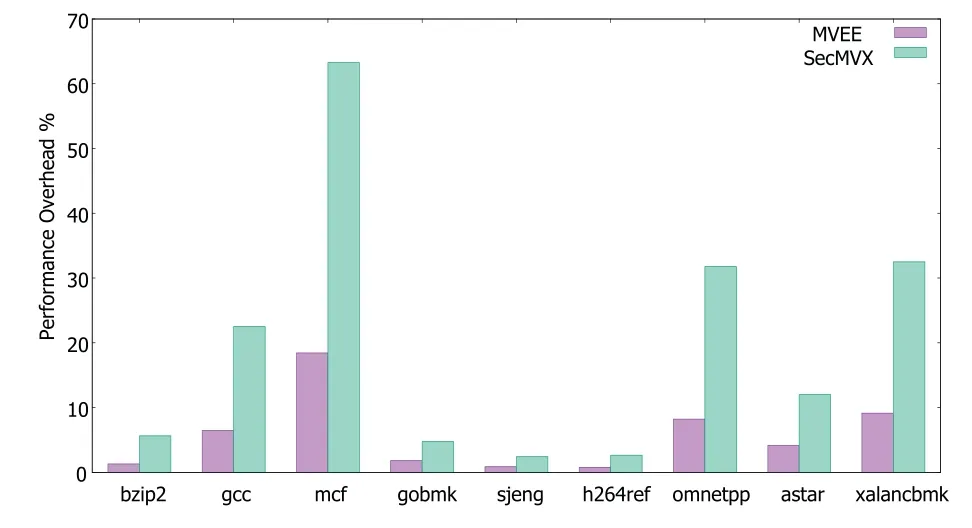
Figure 7.SPEC 2006 performance result.
The 429.mcf‘s memory is frequently accessed so that the checkpoints have been triggered more actively than other samples.In terms of memory overhead,the program’s memory usage is calculated when the program is running.We useVmRSSin/proc/PID/statusto count memory usage.The result shows that memory overhead introduced by SecMVX is close to 3x and 4x comparing with MVEE and baseline respectively.This is because MVEE and SecMVX are executed in a multi-process manner,so the memory overhead generally depends on the number of variant processes.
V.CONCLUSION
This paper analyzes the security problems of the combination of variant generation technologies in the execution of multiple variants,lists several possible attack techniques,and proposes SecMVX,a secure multiple variant execution architecture and variant generation technology.The experimental results show that SecMVX can avoid the vulnerabilities introduced by the improper combination of variant generation technology and bring more significant security gains under a specific performance loss.
The disadvantage of the research in this paper is that SecMVX bases on the existing architecture,relies on debugging methods such as ptrace to intercept system calls to set checkpoints,which is not well resolved in terms of the balance of security and system overhead.In the case of four variants,Since the random space of objects such as stack layout is small,it is possible to place some memory objects in the same stack layout of different variants.A randomization check mechanism will be added in subsequent work.
ACKNOWLEDGEMENT
This work was supported by National Key Research and Development Program of China(Grant No.2018YF0804003).
Supplement
This work was supported in part by the National Key Research and Development Program of China under Grant No.2017YFB0803204.
- China Communications的其它文章
- Two-Timescale Online Learning of Joint User Association and Resource Scheduling in Dynamic Mobile EdgeComputing
- SHFuzz:A Hybrid Fuzzing Method Assisted by Static Analysis for Binary Programs
- SecIngress:An API Gateway Framework to Secure Cloud Applications Based on N-Variant System
- Generative Trapdoors for Public Key Cryptography Based on Automatic Entropy Optimization
- A Safe and Reliable Heterogeneous Controller Deployment Approach in SDN
- Distributed Asynchronous Learning for Multipath Data Transmission Based on P-DDQN

