A Fast Physical Layer Security-Based Location Privacy Parameter Recommendation Algorithm in 5G IoT
Hua Zhao,Mingyan Xu,Zhou Zhong,Ding Wang
1 Information Engineering University,Zhengzhou 450001,Henan,China
2 National Digital Switching System Engineering and Technological Research Center,Zhengzhou 450002,Henan,China
Abstract:The 5G IoT(Internet of Things,IoT)is easier to implement in location privacy-preserving research.The terminals in distributed network architecture blur their accurate locations into a spatial cloaking region but most existing spatial cloaking algorithms cannot work well because of man-in-the-middle attacks,high communication overhead,time consumption,and the lower success rate.This paper proposes an algorithm that can recommend terminal’s privacy requirements based on getting terminal distribution information in the neighborhood after cross-layer authentication and therefore help 5G IoT terminals find enough collaborative terminals safely and quickly.The approach shows it can avoid man-in-the-middle attacks and needs lower communication costs and less searching time than 520ms at the same time.It has a great anonymization success rate by 93%through extensive simulation experiments for a range of 5G IoT scenarios.
Keywords:cross-layer authentication; location privacy parameter recommendation;5G IoT
I.INTRODUCTION
Location-based services(LBS),which provide the 5G IoT terminals with highly personalized content customized by 5G terminals’ current locations,had become a popular application for devices capable of location detection.Since the terminals’ locations are essential to obtain LBS while the service provider is not trusted,reporting private location may lead to privacy threats.To preserve the terminal privacy,most of the location privacy protection focuses on kanonymity[1],which was defined as if a terminal’s location is indistinguishable from the location information of at leastK −1 other terminals.The spatial region which contains the terminal and anotherk −1 additional terminals’locations is usually called the k-anonymity spatial region(K-ASR).To tackle this major privacy concern,the centralized framework and distributed framework are proposed for LBS.The centralized privacy preserving framework in which a trusted third party is used to achieve k-anonymity is most commonly used.Quite a few mechanisms had been proposed based on centralized privacy preserving framework[2–4].Recent research on LBS privacy focuses on a distributed architecture that is suitable for 5G IoT scenarios[5–16].The distributed architecture in which mobile terminals communicate among each other via one-hop and/or multiple routing and constructs K-ASRs by considering terminals in the neighborhood of the querying terminal is popular.However,there are many unique limitations,e.g.,terminal legitimacy,terminal mobility,constrained transmission range,scarce communication resource,and limited energy of mobile devices.Terminal suffers long delay and huge communication overhead in searching terminals and forming K-ASRs.And the neighborhood terminal may be an illegitimate user who can intercept the sensitive location information.Moreover,owing to the lack of background information about the scenarios terminal is not able to choose appropriate privacy parameters to best satisfy the requirements of privacy protection.It lowers the anonymization success rate and degrades the quality of service.
In this paper,we propose a fast physical layer security-based location privacy parameter recommendation algorithm(PBPR)which provides three key features to enhance the security and efficiency of location privacy-preserving in 5G IoT environment.In general,the contributions of this paper can be summarized as follows:
1)We propose a “physical layer security-based cross-layer authentication protocol” for 5G IoT terminals to find collaborative terminals safely with preventing a man in the middle attack.(Section 4.1)
2)We propose a neighborhood-distributionperceptive scheme for our PBPR algorithm to enable terminals to update and share their neighborhooddistribution parameter periodically to nearby terminals.It helps them perceive the real-time terminal density in the neighborhood.(Section 4.2)
3)We introduce a“privacy parameter recommendation scheme” in 5G IoT to provide mobile terminals with the optimal matching privacy parameter for the scenarios in order to strengthen the location privacy security and enhance the anonymization success rate.(Section 4.3)
4)After an analysis of security capability and compared with the other two spatial cloaking algorithms,we experimentally evaluate our PBPR algorithm with different scenarios.It provides protection from manin-the-middle attacks and performs high anonymization success rate with less communication overhead and searching time.(Section V)
The rest of this paper is organized as follows.Section II summarizes related works.Section III depicts our system model.Section VI concludes this paper.
II.RELATED WORK
There is a wide literature on preserving terminal location privacy during the use of LBS.Some concepts,such as False location[17,18],Space transformation[19,20]and Spatial cloaking[1][6][21][22],are used in these techniques.A large portion of location privacy mechanisms is based on spatial cloaking techniques which are borrowed from k-anonymity.The main idea of the spatial cloaking is to blur q terminal’s location into a cloaked area that satisfies the terminal’s privacy requirements,i.e.,the cloaked area contains at leastKterminals and minimum area Amin.There exist two types of the decentralized system.(1)The distribute framework in which mobile terminals establish point-to-point communication through a common infrastructure such as a base station(i.e.,the two terminals do not need to be within the range of each other)is widely used.For example,PRIVE[23]cluster terminals in a hierarchical overlay network based on the Hilbert space-filling curve and resembles a distributed B+-tree to support K-ASR construction.MOBIHIDE[24]form a hierarchical distributed hash table which indexes the locations of all terminals and the K-ASR are constructed by choosing random groups of k terminals.However,each mobile terminal needs to maintain a relatively complex data structure and communication protocol as well as long-range communication among terminals.Therefore additional computation and communication costs may be posed to mobile terminals with limited capabilities.(2)The other distributed system is the mobile P2P system in which mobile terminals communicate with each other via onehop and/or multiple routing.
Chow et al.[6]are the first to apply the group formation technique to the cloak single terminal’s location.In Chow’s method,the terminalUstarts the terminal searching by broadcasting a request to her neighbor terminals(the hop distance is one).IfUdoes not have at least k-1 terminals replying to the request she increases hop by one and broadcasts the request to the terminals within two-hop distance.Urepeats the process untilUfinds enough terminals.This P2PCloak algorithm is simple and it’s applied in many research of location preserving algorithm in mobile p2p environments[9–16].The drawback to this approach is that the terminal suffers from long searching time and a low success rate.In[7],Che describes the dualactive(DA)approach that the terminals not only actively collect but also disseminate location information to others.Che’s approach increases the anonymization success rate at the price of the high communicating cost to maintain the gathered location records.
To the best of our knowledge,the existing LBS privacy protection proposals for k-anonymity spatial cloaking in 5G IoT have the drawbacks as long delay,low success rate,and high communication overhead.In this paper,we focus on the K-ASR construction with shorter delay and higher success rate by means of detecting the terminal distribution with lower communication overhead.Moreover,the existing LBS privacy protection proposals do not take into the account legitimacy of neighborhood terminals.It is vulnerable to man-in-the-middle attacks,where the attacker can observe the communication between terminals and collect the private data transmitted.
III.SYSTEM MODEL
The system model of our PBPR algorithm can be defined in terms of network infrastructures and main entities.
As shown in Figure 1,there are two different types of network infrastructures in order to fulfill the location privacy-preserving in 5G IoT.
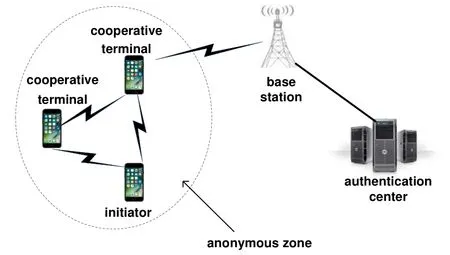
Figure 1.System model.
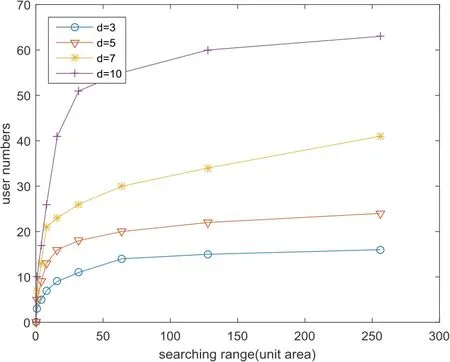
Figure 2.Relationship between searching region and cooperated peers.
1)The wireless network via which terminal can communicate with the authentication center.The mobile communication network is most often used.
2)An Ad hoc wireless network.It is created on the fly when terminals need to exchange information among each other in order to find enough terminals.The system consists of three types of entities.
1)A base station and an authentication center.With a cross-layer authentication processor embedded inside they have the ability to deal with physical layer random authentication parameters-based authentication.
2)5G IoT terminals who need the LBS and want to be anonymized.They are equipped with two wireless network interface cards;one is used to connect to the mobile base station to communicate with the LBS provider,while the other one is dedicated to communicating with other terminals via multi-hop.Each terminal can also locate himself with a positioning device,e.g.GPS,or some other assortment of techniques such as propagation time,time difference of arrival,and angle of arrival.
3)A set of terminals work as cooperators.They share the same cloaked region as their location to get the information from the LBS provider.
IV.PHYSICAL LAYER SECURITY-BASED LOCATION PRIVACY PARAMETER RECOMMENDATION ALGORITHM
This section presents the proposed physical layer security-based location privacy parameter recommendation algorithm for location privacy-preserving in 5G IoT.
4.1 Cross-layer Authentication Protocol
The entire neighborhood terminals involved in the traditional LBS privacy protection proposals are considered legitimate by default,and will not attack other terminals or systems by collecting the location information of cooperative terminals.In fact,man-inthe-middle attackers may exist in 5G IoT scenarios and some scenarios mentioned in[25–27]that relaying communication is used to improve communication capacity.They are connected between legitimate terminals and base stations to intercept private information such as terminals’ location data.At present,there are many physical layer authentication methods[28–30]based on wireless channel features or radio frequency fingerprinting or watermarking signal,but they only perform physical layer authentication separately.The combination of physical layer security and existing 5G authentication mechanism can not only achieve enhanced cross layer authentication,but also integrate authentication and communication,ensuring the legitimacy of the terminal before the perception of neighborhood distribution without additional delay and overhead.
The specific cross-layer authentication protocol is as follows:the authentication center obtains the terminal’s identity information and group information during the terminal registration process.The terminal and the base station generate physical layer random authentication parameters through the physical layer key agreement mechanism.The base station reports these physical layer random authentication parameters to the authentication center.The authentication center uses the root key and physical layer random authentication parameters related to the terminal’s identity to generate authentication data and sends it to the terminal.The terminal uses the root key,physical layer random authentication parameters,and authentication data to authenticate the base station and the authentication center,then generates terminal authentication data and sends it to the authentication center.The authentication center authenticates the terminal with the root key,physical layer random authentication parameters,and the terminal’s authentication data.If the authentication is passed,it sends the group key to the terminal to encrypt subsequent neighborhood weighted density parameters and other information.
In the original high-level authentication,both the generated authentication message and the response message need to be transmitted in plaintext in the wireless channel,so that these messages can be obtained by a man-in-the-middle attacker.Since the security of high-level authentication is based on computational complexity,computers with high computational performance can further crack the authentication data.Therefore,as the frequency of authentication increases,the entropy of high-level key information will continue to decrease.Combining physical layer random authentication parameters with highlevel authentication makes the physical layer channel information part of the authentication information,which essentially provides information entropy for authentication.Using the strong coupling and correlation between the physical layer random authentication parameters and the wireless link,combined with the identity of the terminal in the 5G IoT,the strong binding of the terminal identity and the wireless link can be realized,which can identify and suppress the ”transparent forwarding”attack of the man-in-the-middle attacker in the 5G IoT,and ultimately ensure the security of the formation of the anonymous zone.
4.2 Neighborhood-Distribution-Perception Scheme
The terminal spatial distribution in 2 or 3-dimensional Euclidean space can be characterized by terminal densitydwhich means the terminal number presented in a unit area.IfDis defined as a continuous space,the mean user density expectationd∗can be estimated by maximum likelihood stated in(1):
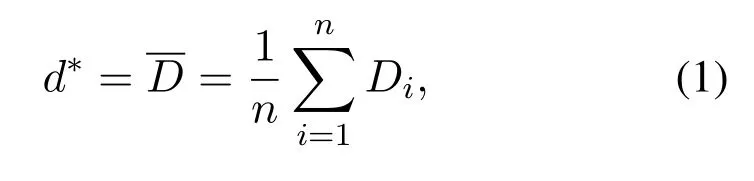
whereDiis the sample size of the terminal number in a unit area andD1,D2,...,Dnis the set ofDi.For a requiring terminaluinD,it is the terminal spatial distribution around terminal u that most influence the shape and size of the cloaking region,and hence,we propose the Neighborhood-distribution-perceptive scheme by formula(1).To this end,we have the following definitions.
Definition 1.The space around terminal u within transmission range of h hop is defined as the neighborhood zone D(u,h):
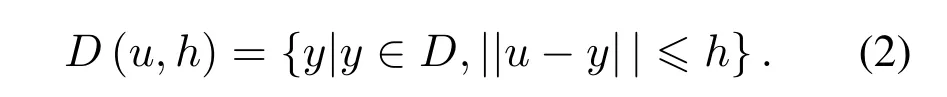
In particular,D(u,1)is called the unit area whereh=1.
Definition 2.For a terminal u in D,the terminal density in the neighborhood,represented by du,is defined as the mean value of the terminal density in the D(u,h).In particular,the terminal number in D(u,1)is represented by Du.
A.Estimation of the terminal density in the neighborhooddu
Every terminal in 5G IoT calculates and stores herdulocally and sends it to terminals inD(u,1)periodically.By this way terminalucan receive thedisent by the peer terminals in herD(u,1)in whichnuis the number ofdithatureceives in a regular interval.This enables her to updateduaccording to(1):
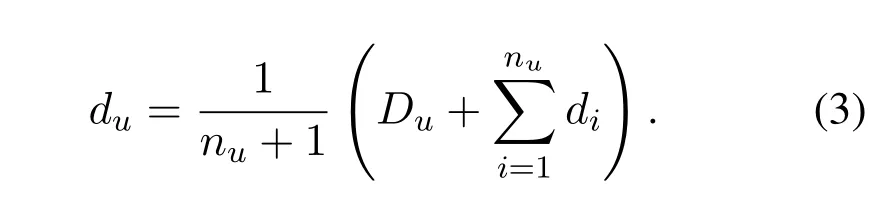
And every terminaluiupdates her newdiperiodically:
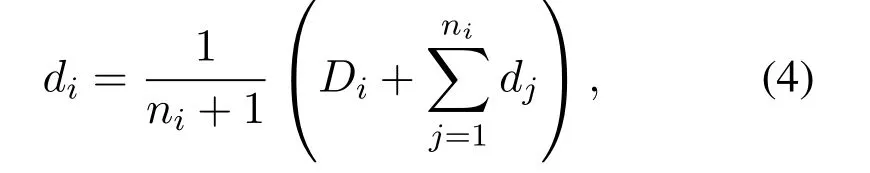
wheredjis the terminal density in the neighborhood thatujwas received from herD(uj,1).Here we replace thediin(3)by(4)anddjcan be replaced in the same way based on the terminal densities in the neighborhood thatujreceives around her:
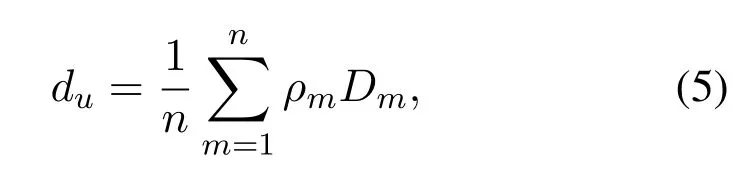
wherenis the total terminal number inD(u,h),DmisD(um,1)for terminalumand parameterρmis defined as the distribution influence factor.The further theumis fromu,the smaller theρmis becauseDmhas to be iterated more times to arrive and be used byu.Through exchanging theduin the neighborhood zone,terminalucan collect the sample sizeDmfrom remote terminals during the procedure of Neighborhood-Distribution-Perception.Compared with the terminals located far fromu,terminals located closely withuare more likely to be the candidates of the cloaked area,and hence herρmis much bigger in(5).
B.Occasion and frequency of sendingdu
Sendingduperiodically enables terminals to get the real-time spatial terminal distribution at the price of a higher communication cost.In the case that spatial terminal distribution is relatively stable inD,theduof every terminal is most often steady.It is a waste of communication resources sending thedufrequently in this situation.We suggest the strategy of updating and sendingdu.Every terminal keeps the latestdishe received from the neighborhood in a local table.She also sets a regular timer for updating herduwith the latest records periodically and broadcasts herduonly whenduchanges or she detects there are new terminals that appeared in the neighborhood.In this way not only can terminals calculate the real-timedubut also the communication cost is saved.
C.Neighborhood-distribution-perceptive scheme design
Algorithm 1 depicts the main idea of the neighborhood-distribution-perceptive scheme.
For every terminaluwe define the updating period as oftand local parameter table.During the updating period,ifureceive the newdifrom direct neighbors or she detects the terminal change in the direct neighborhood,which results in the updating of the local parameter table,she will recalculate herduaccording to formula(3).At the end of every updating period if herduchanges or there are new terminals coming up in the neighborhood she will broadcast herduencrypted by group key.

Algorithm 1.Neighborhood-distribution-perceptive algorithm.1:Set du ←Du,t 2:while(t.peroid)do 3:if(du is different from last time or there are new neighbors coming)then 4:Form and encrypt ”m share” message by group key 5:broadcast”m share”message 6:end if 7:Receive the”m share”messages set M′8: m ←|M′|,Du ←D(u,1)9:if(m/=0)then 10:while(every received ”m share” message)do 11:Decrypt by group key 12:Read di in”m share”of terminal ui 13:Update the di in parameter table 14:end while 15:end if 16:if(di or Du is different)then 17:du ←(∑di+Du)/|Du|18:end if 19:end while
We define the broadcast messagem_share={di}wherediis the neighborhood terminal density of the terminaluj.
Every terminal in 5G IoT can get the real-time spatial terminal distribution information around her through Algorithm 1.The neighborhood-distributionperceptive scheme is the foundation of our PBPR algorithm.
4.3 Recommendation of Privacy Parameters and Searching Region
It is known that the bigger the privacy parameterkis,the stronger the privacy protection is.However,a biggerkalways results in the failure of finding enough cooperated terminals,particularly in the scenario where mobile terminals are few and scattered.How to choose a suitablekis important in k-anonymity.Ahamed mentions in the work[31]thatkis the key factor in the success rate as well as the security level of kanonymity.Based on our neighborhood-distributionperceptive scheme terminal is able to get the information of spatial terminal density in her neighborhood and estimate the appropriatekand the searching size of K-ASR.
Figure 2 gives the pictorial relationship between the searching region and cooperated terminals by changingdu.Every point on the curve means the increase of hops by 1.We observe that with the expanding of searching range more cooperated terminals can be found.Considers the increasing terminal number between every adjacent hop to gain,Nh,while considering the additional searching region to the communication costCh,the searching gain is donated by the slope of the curve segment between every hop,Nh/Ch.We notice that the searching gain becomes smaller along with the expanding of searching range and it is no more than 1 when the searching range is over 4 hops,which means the searching process costs huge communication resources for finding more cooperated terminals.So for a givendu,we recommend better performance of anonymization success rate can be achieved with lower communication resource wherek≤4·du.
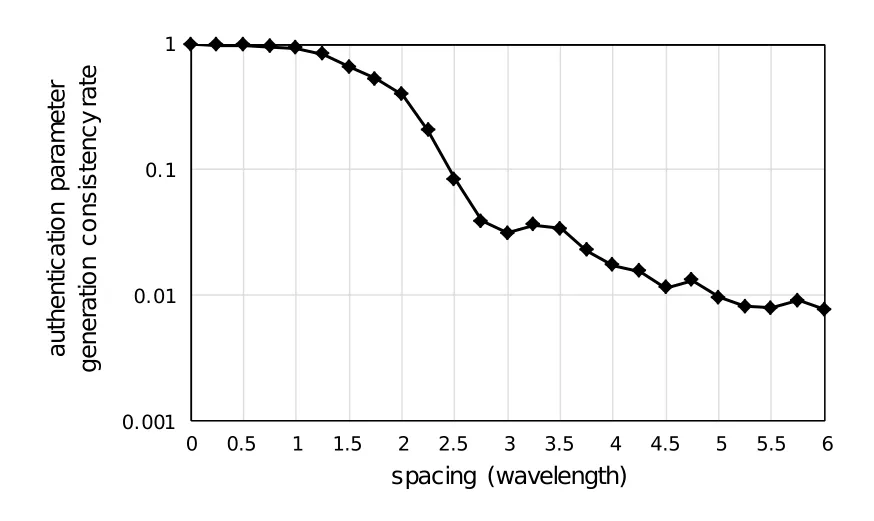
Figure 3.Authentication parameter consistency rate.
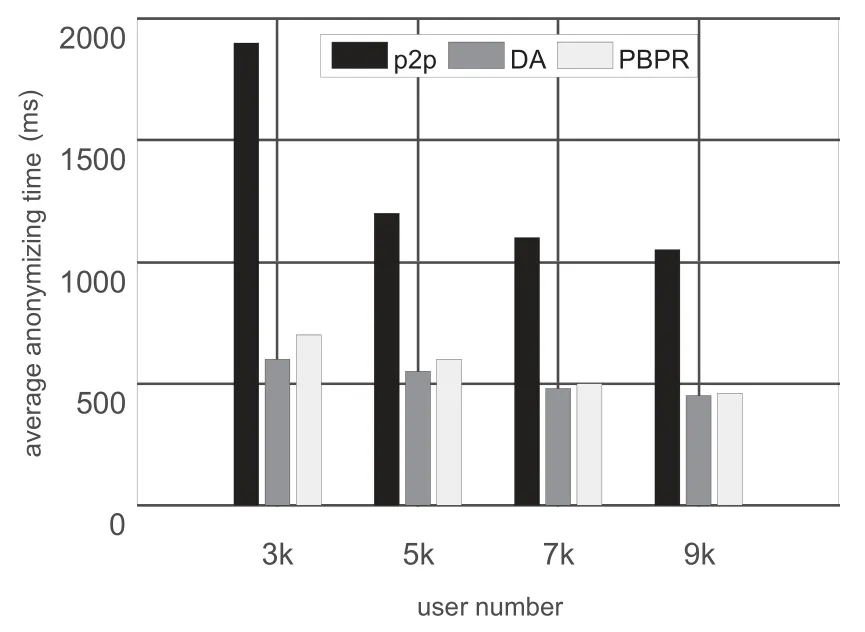
Figure 4.Average anonymizing time per query.
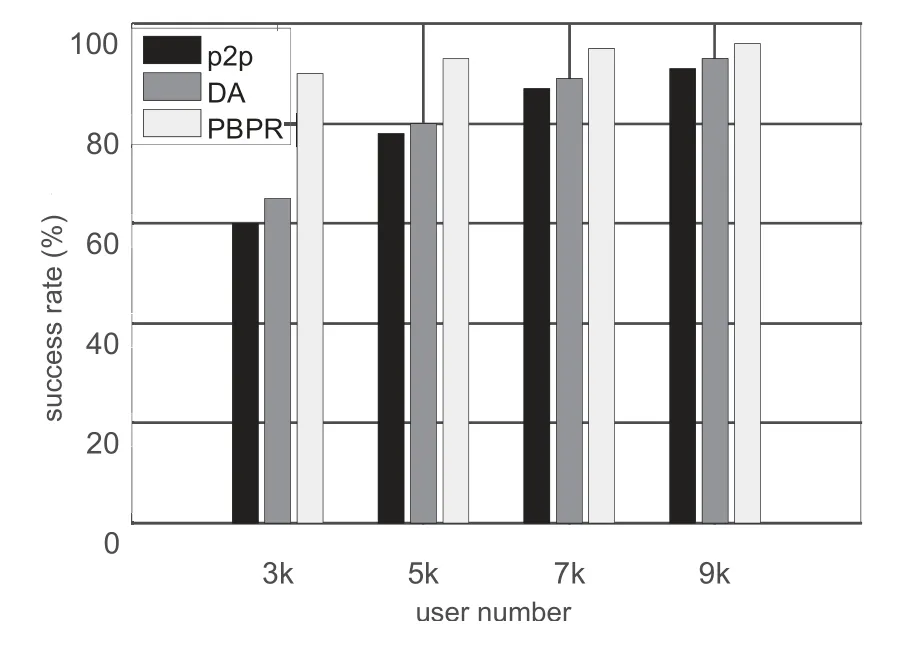
Figure 5.Anonymization success rate.
The size and shape of the K-ASR rely on the spatial terminal distribution in 5G IoT.If mobile terminals are independently and uniformly located inD,terminaluonly needshops to find k peers.However,if mobile terminals are located in the line,uhas to takek/duhops to find enough terminals in order to construct K-ASR.We recommend theas the initial searching hops,hinitial,and max(k/du,8)asthe end of searching hops,hend.
V.EXPERIMENTAL RESULTS
In this section,we evaluate the performance of our PBPR algorithm with a set of key features in the analysis of security capability and comparison with two existing algorithms,Chow’s P2PCloak[6]and Che’s DA approach[7].The simulated experiments are executed in a range of scenarios that are generated by the use of Generator of Network-based moving objects[32]and the realistic road network of the Germany city,Oldenburg.The experiments are implemented using JAVA and are run on Intel i5 2.3GHz desktop with 8GB of RAM.Table 1 summarizes the specification of our simulation.
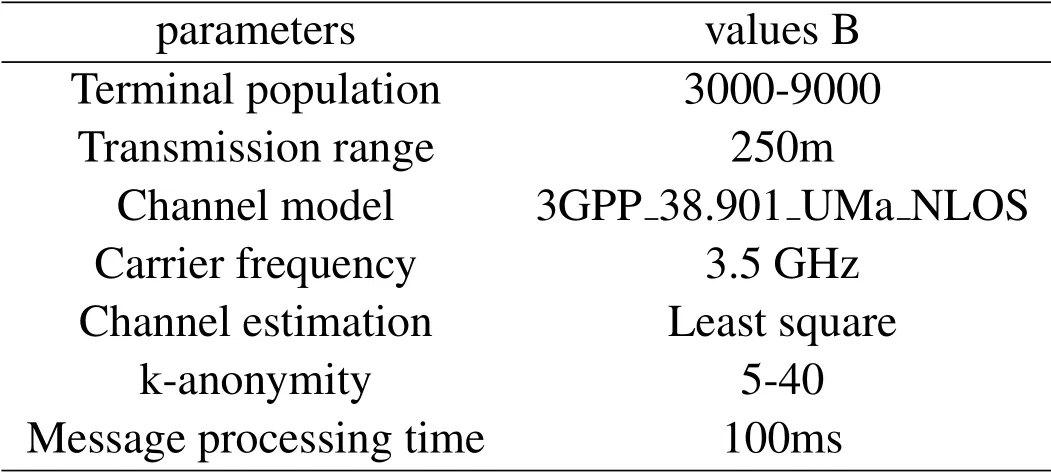
Table 1.The Specification of experiments.
According to the running environment,the total number of mobile terminals is from 3k to 9k.The values of k and transmission range are generated following the uniform distribution.Without losing generosity,we consider the message processing time to be 100ms,and the length of the message is 64 bytes.
5.1 Evaluation of Authentication Parameter Consistency Rate
Authentication parameter generation consistency rate:This refers to the consistent proportion of physical layer random authentication parameters generated by channel estimation and quantization of the terminals and man-in-the-middle attacker.The value of the authentication parameter generation consistency rate can directly reflect the defense degree of PBPR algorithm against man-in-the-middle attacks and embody the security increment.
It is assumed that the channel model between the 5G Base Station and the Mobile Station is 3GPP_38.901_UMa_NLOS and there is no noise at the receiving end of the terminal and the man-in-themiddle attacker.Figure 3 shows the authentication parameter generation consistency rate versus the distance between the terminal and the man-in-the-middle attacker(The unit is carrier wavelength).We can see that the authentication parameter generation consistency rate of the proposed scheme is below 10−2when the distance between the legitimate user and the illegal eavesdropper is 5 times the carrier wavelength.It shows that while ensuring normal communication,PBPR algorithm makes full use of the advantages of diverse spatial characteristics,rich channel characteristics,and high position sensitivity brought by physical layer technologies such as 5G large-scale antennas,large bandwidth and high-frequency bands to complete the generation of random authentication parameters.Based on the above,the algorithm can achieve good anti-eavesdropping performance with low cost and complexity.
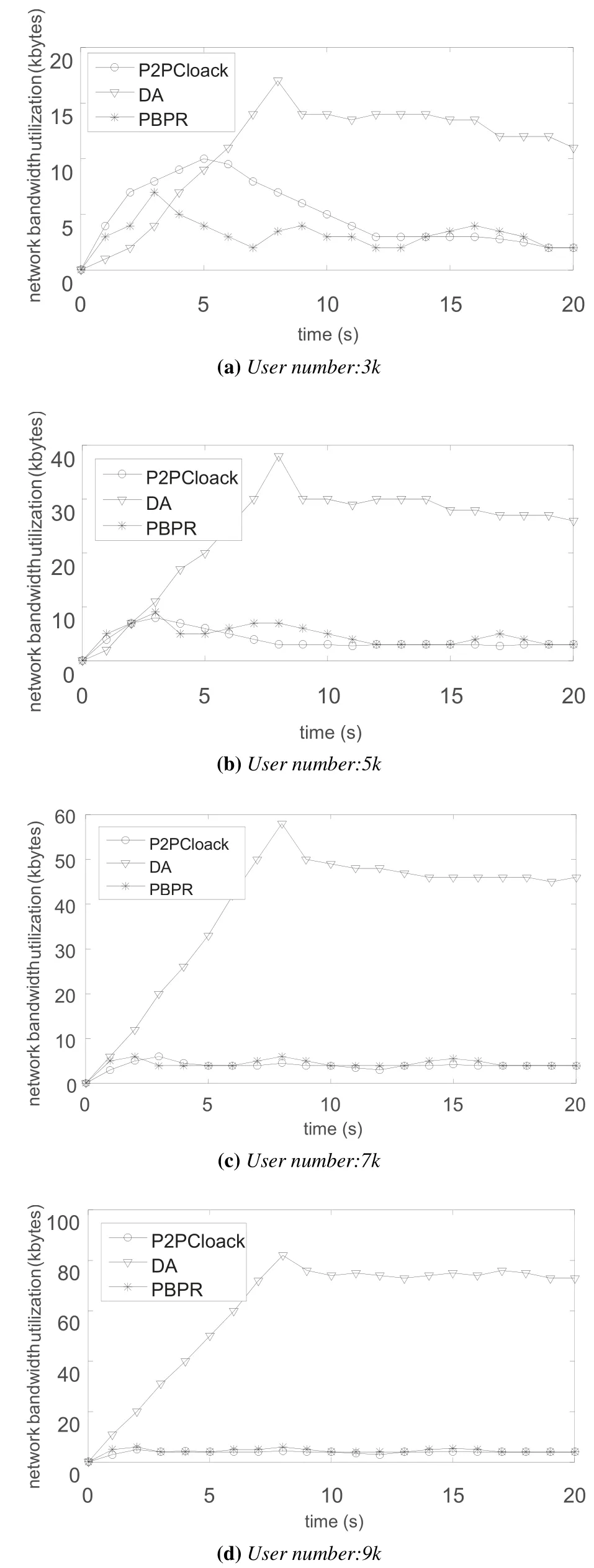
Figure 6.Network bandwidth utilization.
5.2 Evaluation of Average Anonymizing Time Per Query
Average anonymizing time per query:This is the mean time between the terminal’s initiating a query and generating a cloaked region.It indicates the response time of the anonymization procedure.
Figure 4 shows the average anonymizing time for each anonymization request.Compared with P2PCloak,the anonymizing time of DA and our algorithm is about 520ms and reduced by 50%.DA algorithm uses a little shorter time than our algorithm because it gathers terminal information before request launches with more communication overhead.
5.3 Evaluation of Anonymization Success Rate
Anonymization success rate:This is a ratio of the number of times that the anonymization algorithm can find enough terminal location information to satisfy the terminal’s k-anonymity privacy requirement to the total number of queries.
Figure 5 shows the anonymization rate of the three algorithms in four scenarios.It shows that all algorithms can achieve a higher success rate as the terminal number grows.However,our algorithm presents a better success rate owing to the recommendation of privacy requirements and searching range,in particular in the scenario with fewer terminals.The average success rate of our algorithm is above 93%.
5.4 Evaluation of Network Bandwidth Utilization
Network Bandwidth Utilization:It measures the network bandwidth utilization involved in a query’s whole anonymization procedure.Figure 6 presents the network bandwidth utilization comparison.In general,P2PCloak and our algorithm use little communication resources and exhibit a smooth curve.For P2PCloak,the curve rises slightly during the terminal searching.Terminals in our algorithm only broadcast message in one hop neighborhood and there are fewer messages exchange afterduis stable.As a result,the curve of our algorithm just ascends a little in the neighborhooddistribution-perception stage.On the contrary,for the DA algorithm,the curve increases significantly from scenario 1 to 4 because of the exchange of the location records.
VI.CONCLUSION AND FUTURE WORK
In this paper,we exploited the privacy issue of LBS and presented a fast physical layer security-based location privacy parameter recommendation algorithm for 5G IoT.By cross-layer authentication,exchanging neighborhood distribution information,and the recommendation of privacy requirements,our algorithm improves security capability and achieves a higher anonymization success rate without additional communication cost.The extensive experiment demonstrates the PBPR algorithm can work safely in 5G IoT.We will work on saving computing resources and reducing signaling overhead by asymmetric implementation architecture to improve the terminals’energy efficiency in 5G IoT.
ACKNOWLEDGEMENT
This work has been performed in the Project ”Research on Basic Theory of Cyber Mimic Defense”supported by Innovation Group Project of the National Natural Science Foundation of China(No.61521003),and partly supported by National Natural Science Foundation of China(No.61772548),key universities and academic disciplines contruction project and Key Scientific and Technological Projects in Henan Province(Grant No.192102210092).
- China Communications的其它文章
- Two-Timescale Online Learning of Joint User Association and Resource Scheduling in Dynamic Mobile EdgeComputing
- SHFuzz:A Hybrid Fuzzing Method Assisted by Static Analysis for Binary Programs
- SecIngress:An API Gateway Framework to Secure Cloud Applications Based on N-Variant System
- Generative Trapdoors for Public Key Cryptography Based on Automatic Entropy Optimization
- A Safe and Reliable Heterogeneous Controller Deployment Approach in SDN
- Distributed Asynchronous Learning for Multipath Data Transmission Based on P-DDQN

