C-V2X Equipment Identification Management and Authentication Mechanism
Shanzhi Chen,Qiang Li,Yong Wang,Hui Xu,Xiaoyong Jia
1 State Key Laboratory of Networking and Switching Technology,Beijing University of Posts and Telecommunications,Beijing 100876,China
2 State Key Laboratory of Wireless Mobile Communication,China Information Communication Technologies Group Corporation,Beijing 100191,China
3 Datang Microelectronics Technology Co.,Ltd,Beijing 100094,China
Abstract:Cellular vehicle-to-everything(C-V2X)is the most promising V2X communication technology which can greatly improve traffic efficiency and road safety.However,when vehicles are interconnected with the surrounding radio environment,the CV2X system will face various network security risks and threats,significantly impacting on traffic and life safety.This paper proposes a novel unified identification management framework and security authentication mechanism for the C-V2X equipment based on the security problems analyses of the C-V2X system and the existing security protection schemes.This paper also presents the security analysis and evaluation for the unified identification management and authentication mechanism.A experiment system is implemented to verify feasibility and effectiveness for the proposed mechanism.
Keywords:C-V2X; identification management; authentication
I.INTRODUCTION
The development of ICT(Information and Communication Technology)has been promoting the traditional industries.IoVs(Internet of Vehicles)is one of the typical examples,and it will significantly improve traffic efficiency and safety.C-V2X(Cellular Vehicle-to-Everything)is the most promising wireless communication technology of IoVs and has been standardized by 3GPP(3rd Generation Partnership Project)[1,2].C-V2X supports V2V(Vehicle to Vehicle),V2I(Vehicle to Infrastructure),and V2N(Vehicle to Network)communications to meet the requirements of commercial applications.C-V2X system supports the celluar communication mode and the short-range direct communication mode and provides high reliability,low latency,and large bandwidth communication capabilities.C-V2X system can support various scenarios such as vehicles cooperative driving,semiautomatic driving,extended sensor capability,remote driving,etc.It is the most important technology for intelligent transportation systems and automotive industry[1,2].
The C-V2X network and equipments face various security challenges due to the security risks of traditional cellular networks and the broadcasting characteristics of wireless channel.The information transmitted in the C-V2X system could be copied,forged,deleted,and modified by attackers,resulting in not only information leakage and even catastrophic consequences.An attacker may mimic authorized equipment such as a RSU(Road-Side Unit)and distribute wrong information to nearby equipments,causing a traffic jam or accidents[3].The attacker can also mislead other vehicles to change driving behavior(such as slowing down or changing lanes)and infringe on other vehicles’ normal driving.The attacker can launch an attack such as Man-in-the-Middle attack,tamper with the data transmitted in the C-V2X system,lead to some nasty results,and endanger the C-V2X application security.An attacker can monitor network data,obtain user’s location,route,and other sensitive information,then leak users’ privacy information,or even illegally track vehicles and directly threatens the user’s safety.
Furthermore,the C-V2X system brings-up many challenges due to heterogeneous nodes,various speeds,and intermittent connection,the security problems thus becomes more complicated[4].Many types of equipments work together in the C-V2X system,so that the security risks in one vehicle may spread to the other vehicles,or even to the whole network[5].Therefore,the security issue of the C-V2X system will be the important factor affecting its large-scale commercial deployments.It is vital to establish a C-V2X security protection system and strengthen the research and development of C-V2X security technology,standard,management,etc.
When a C-V2X equipment communicates via the PC5 interface(i.e.,using short range direct communication mode),the C-V2X equipment should authenticate the source of the received message to ensure the message’s legitimacy.The C-V2X system should support the integrity,confidentiality,and anti-reply protection of the message to prevent forged,tampered,or replayed transmission.The C-V2X system should keep the concealment of the real identity and location information to avoid the leakage of the user’s privacy.
A variety of network security technologies are integrated to enhance the security of the C-V2X system.IEEE 1609.2 defines a security message format and process of WAVE(Wireless Access in the Vehicular Environment).It uses digital signature and encryption based on PKI(Public Key Infrastructure)to realize secure communication between C-V2X equipments.The security management system based on PKI provides certificate issuance,certificate revocation,data management,and exception analysis functions.Blockchain is adopted to establish security trust between vehicles communicating through the PC5 interface[6].Some researchers partitioned the equipments into different security domains according to geographical position,and each domain has a unique security level[7].Some researcher suggested to establish data access control and encrypted data retrieval systems based on the equipment’s role and attribute.The equipment data can be encrypted and protected through access control policy and policy execution engine[8].Some researchers designed an intelligent key distribution method based on the vehicle location information.The communication key can be pre-distributed to the future location of the vehicle to improve the speed of encryption[9].C-V2X privacy protection includes user identity privacy and location privacy.Identity privacy is secured by group data signature scheme.Location privacy is secured by pseudonym change policy and location-based service[10].
CCSA(China Communications Standards Association)has completed the standard about the C-V2X security certificates management system that defines the certificate format,security message format,and certificate management mechanism.There has not yet corresponding effective measures for security initialization before starting encryption communication between the equipments.The current security solution still lacks a mechanism providing secure identity credentials to the certificate authority.Due to the need of security management,the C-V2X system requires an unified equipment management method.This paper proposes a unified numbering and management framework to implement initial authentication for C-V2X equipment.
The paper’s organization is as follows:Section II analyzes the current C-V2X security mechanism and provides C-V2X equipment unified management and initial authentication architecture.Section III proposes a C-V2X equipment identification numbering method and explicitly describes the C-V2X equipment authentication mechanism.Section IV analyzes this scheme’s security and builds an experimental validation environment to verify the scheme’s feasibility.Finally,section V concludes the paper.
II.UNIFIED MANAGEMENT AND INITIAL AUTHENTICATION ARCHITECTURE FOR C-V2X EQUIPMENT
The unified identification management and initial authentication are necessary for the equipments accessing to the C-V2X system.Only the authenticated equipment can apply for a communication certificate and can build a mutual trust relationship with other equipment.
2.1 Unified Identification Management and Authentication Requirements for C-V2X Equipment
The C-V2X system includes various equipments such as RSUs(Road-Side Units),OBUs(On-Board Units),cloud platform,application services,and other necessary equipments.Each type of equipment has its own properties,functions,capabilities,etc.They face various security risks.Based on communication capability,all equipments work together to form a system.In order for convenient management of all the equipments with different categories and manufacturers,unified identification definition,allocation and management is necessary to provide secure credentials to the CA(Certificate Authority)system to generate certificate.
In cellular communication mode with Uu Interface(between the vehicle and base station),the security management generally depends on the security mechanism of mobile communication network,including access layer security and non-access layer security.There are different security protection measures in every network layer.The cellular mobile communication system can manage the signal and data security of CV2X equipments.The cellular mobile communication system will perform the access authentication and key management procedure for the C-V2X equipment.The C-V2X application layer will protect the application data with security and offer user privacy[11,12].
In the direct communication mode with PC5 interface,there is no technical specifications defining the security protection method for C-V2X system at network layer.Generally,digital signature and encryption are used to achieve secure communication between the equipments and to solve the C-V2X system security problems.The communication security between equipments can be realized by building security channels based on certificate authentication and key agreement.
Before the security channel is built,a digital certificate is generated by a certificate authority.The digital certificate binds a public key to the identity information of its legitimate owner,and is used to prove the legitimacy of the public key.The equipment needs to prove to the CA(Certification Authority)that if it is legal securely equipment and gets the CA certificate.However,there are not corresponding effective measures for security initialization before starting encryption communication between the equipments.The current security mechanism still lacks a measure which provides secure identity credentials to the certificate authority.In order to let the equipment to prove its legal identity to CA,and to establish a secure mutual trust relationship with CA before it gets a communication certificate,GBA(Generic Bootstrapping Architecture)[13],OAuth(Open Authorization)[14],DCM(Device Configuration Manager)and other different methods can be used in the AAA(Authentication,Authorizationand Accounting)process.
The C-V2X security management architecture include 3 layers(as shown in Figure 1),primary authentication layer,secondary authentication and authorization layer,and security management layer.Oauth,GBA and DCM work in the secondary authentication and authorization layer.DCM can also work in primary authentication layer.
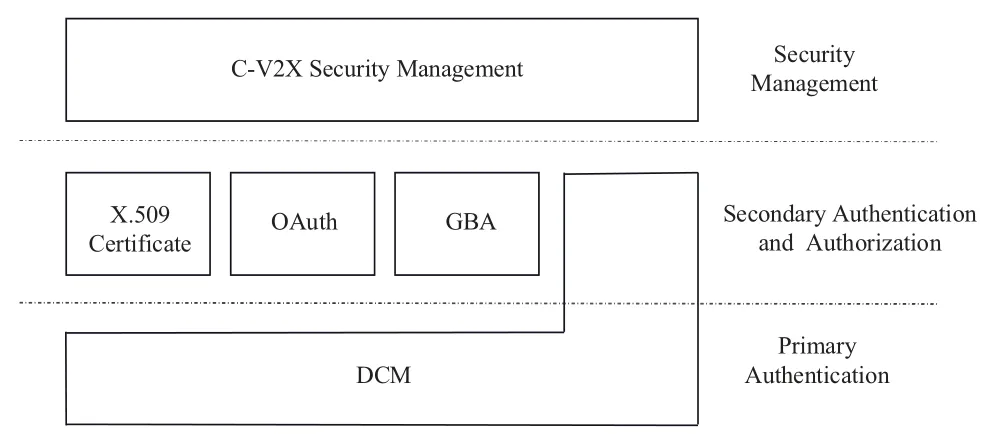
Figure 1.C-V2X security management architecture.
GBA can provide an initial secure channel for equipments using the authentication and session method in mobile communication network and equipment.OAuth can provide a secure,open,and simple authorization service.DCM configures parameters for the equipment,apply and download the CA’s communication certificate on behalf of the equipment.Therefore,the equipment needs to prove its legal identity to DCM.The authenticated equipment can apply for a communication certificate from the certification authority through DCM and establish a security mutual trust relationship between C-V2X equipments.It promotes the security of the C-V2X system and forms a complete security system.DCM can provide C-V2X equipment initial authentication.It can also provide secondary authentication and authorization.The com-parative analysis of GBA,Oauth and DCM is shown in Table 1.
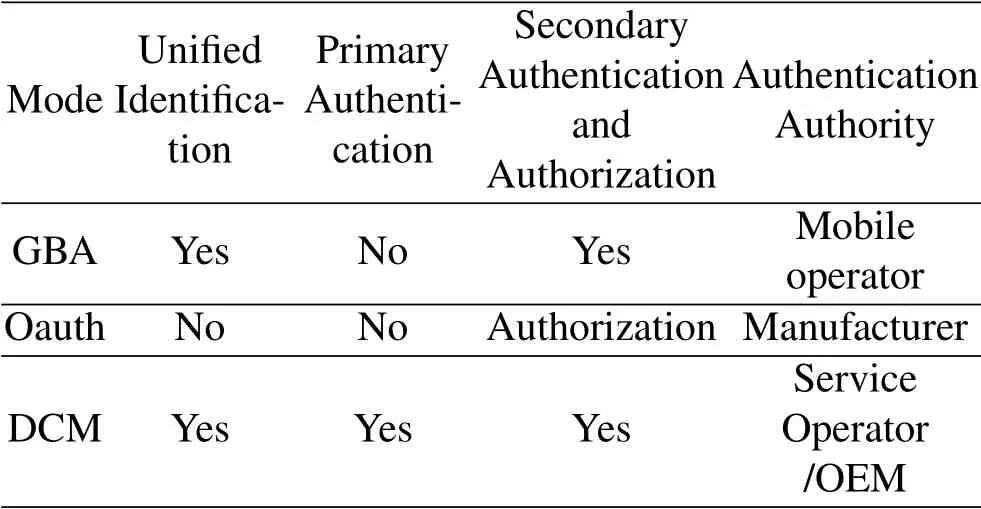
Table 1.Comparative analysis of GBA,oauth and DCM.
2.2 Unified Management and Initial Authentication Architecture for C-V2X Equipment
Registration and management architecture for C-V2X equipment is proposed to solve the problems of CV2X equipment management and security,as shown in Figure 2.The architecture includes VID(Vehicle Identification)registration center,VIM(Vehicle Identity Module),VID authentication unit,and VID authentication center.The VID registration center is responsible for assignment and management of VID which is used as the unique number of each C-V2X equipment.VID can be written in the VIM secure storage area and sent to the VID Authentication Center for pre-registration.A VIM is embedded in OBU,RSU and other C-V2X equipments to store VID,authentication algorithms and authentication data,is responsible for the authentication process with the VID Authentication Unit.VID authentication unit is deployed in AAA,which is responsible for authenticating the VID and get authentication vector from VID Authentication center.VID authentication center is deployed in the certificate authority to generate the authentication vector of the equipment and interact with the VID authentication unit in AAA to apply and download the authentication vector.
The C-V2X equipment manufacturer registers the C-V2X equipment in the VID registration center when the equipment is produced and prepared for accessing the C-V2X system.The VID registration center generates the equipment VID and sends the VID to the equipment VIM,as well submits the authentication keyKassociated with the VID to the VID authentication center.The authentication center submits the approved VID and the corresponding equipment information to the RA of the certification authority,and then the RA completes the preparation for generating the certificate.The equipment registration process is shown in Figure 3.
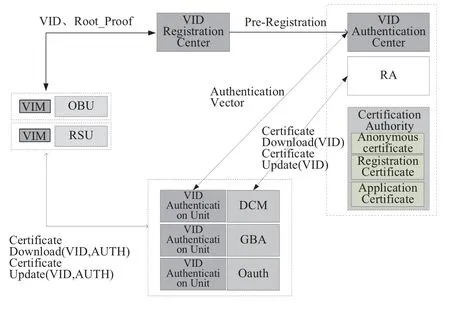
Figure 2.C-V2X equipment registration and management architecture.
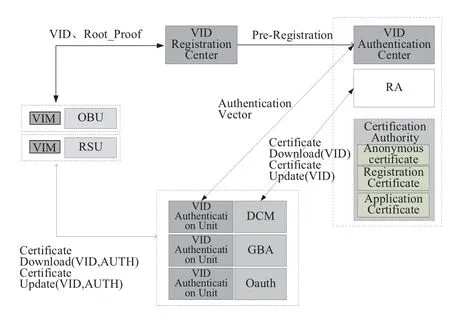
Figure 3.C-V2X equipment registration process.
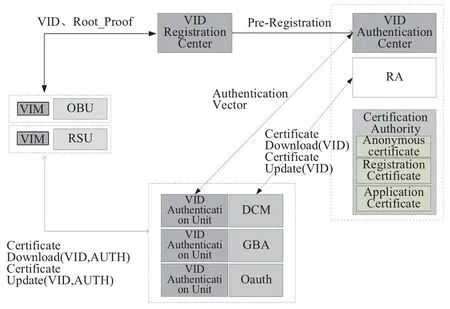
Figure 4.C-V2X equipment authentication architecture.
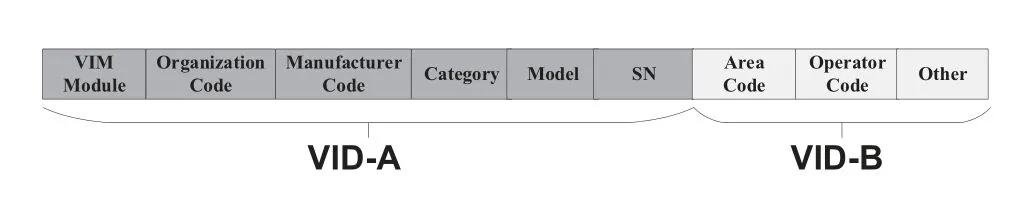
Figure 5.C-V2X equipment identification numbering method.
The VID authentication unit completes the authentication process in AAA.When the equipment accesses the C-V2X system and applies or updates the communication certificate,the equipment’s VIM sends an authentication request to the VID authentication unit.Only the certified equipment can apply and update the certificate.The VID authentication unit applies to the VID authentication center for the equipment authentication vectors.The VID authentication center receives the request from authentication unit and generates an authentication vector for each VID.Each authentication vector is suit for only one-time authentication between the VID authentication center(VID authentication unit)and VIM.The authentication vector in the VID authentication unit works in FIFO(First In First Out)mode.When the VID authentication unit applies for a VID authentication vector from the VID authentication center,it can request one or multiple VID authentication vectors at one time.The VID authentication unit can apply for the authentication vector when it receives the equipment authentication request or applies for the authentication vector in advance.When the equipment initializes its communication certificate,it initiates a certificate application to the VID authentication unit.The VID authentication unit selects the next new authentication vector from the vector-sets,and sends it to the VIM for identification authentication.The VIM calculates the authentication data and returns the result to the VID authentication unit.If VID authentication of the equipment is successful,the AAA issues the corresponding certificate to the equipment.The process of the equipment identification authentication is shown in Figure 4.
The C-V2X equipment needs to register only one time in the VID registration center when it is produced by the manufacturer; and it needs to perform the initial authentication process to prove its legal identity to CA one time when it is prepared for accessing the C-V2X system.Then,the C-V2X equipment has a unique identification and communication certificate,it can establish secure communication with other C-V2X equipments withnot relying on the system.Therefore,this architecture can well support the mobility of vehicles.
III.IDENTIFICATIONNUMBERING METHOD AND AUTHENTICATION PROCESS OF C-V2X EQUIPMENT
The VID registration center generates a unique ID to each C-V2X equipment according to the equipment information.The equipment authentication process is mainly divided into two steps:the VID authentication unit contacts the VID authentication center to apply for an equipment authentication vector; the VID authentication unit authenticates the equipment when the equipment accesses the C-V2X system.
3.1 Identification Numbering Method of CV2X Equipment
The C-V2X equipments are produced by different manufacturers,different commercial operators,etc.The VID registration center assigns a unique number as VID to each C-V2X equipment .A VIM is built into the C-V2X equipment as a security module to store VID and execution C-V2X equipment identification authentication process.The design of the C-V2X equipment identification numbering method is shown in Figure 5.
VID is composed of two parts:VID-A and VID-B,the numbering method is shown in Table 2.
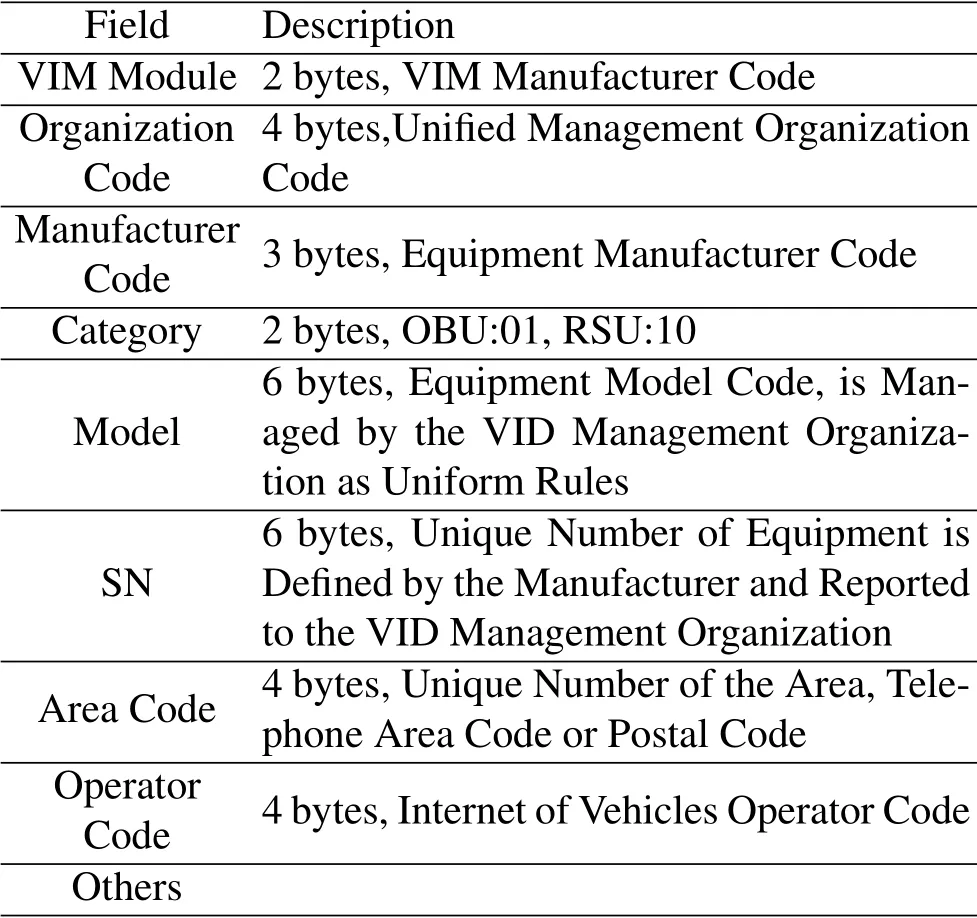
Table 2.VID numbering method description.
3.2 Distribution Process of Equipment Authentication Vector
The VID authentication center can establish a trust relationship with the VIM based on sharing keyKbetween them.The VID authentication center generates a separate SQN(Sequence Number)for each equipment.The SQN is maintained in the VID authentication center and VIM to prevent authentication data replay attacks.The VID authentication center generates new authentication vectors and distributes them to the VID authentication unit in AAA.The VID authentication unit communicates with the VID authentication center securely and reliably to get the equipmentauthentication vector and to perform VID authentication for the equipment.The authentication process is divided into the following two steps.
When the VID authentication unit sends a request to the authentication center to generate and issue an authentication vector of the equipment which needs authentication,the corresponding VID is brought in the request.A request can carry only one VID or many VIDs.The generation and distribution process of authentication vectors are shown in Figure 6.
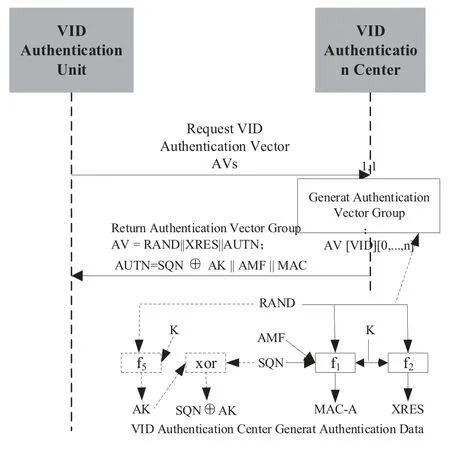
Figure 6.Generation and distribution process of C-V2X equipment authentication vector.
When the VID authentication center receives the request,it generates a set of ordered authentication vectors AV(1...n).Each authentication vector consists of a random number RAND,expected response XRES,and authentication token AUTH.The VID authentication center generates a new SQN and an unpredictable random number RAND for each authentication vector;the VID authentication center records and tracks the authentication counter SQN for each equipment.Then,the VID authentication center sends the ordered AV data to the VID authentication unit.The authentication vectors in the VID authentication unit is used in FIFO(First Input First Output)mode.The generation method of each data element is shown in Table 3.
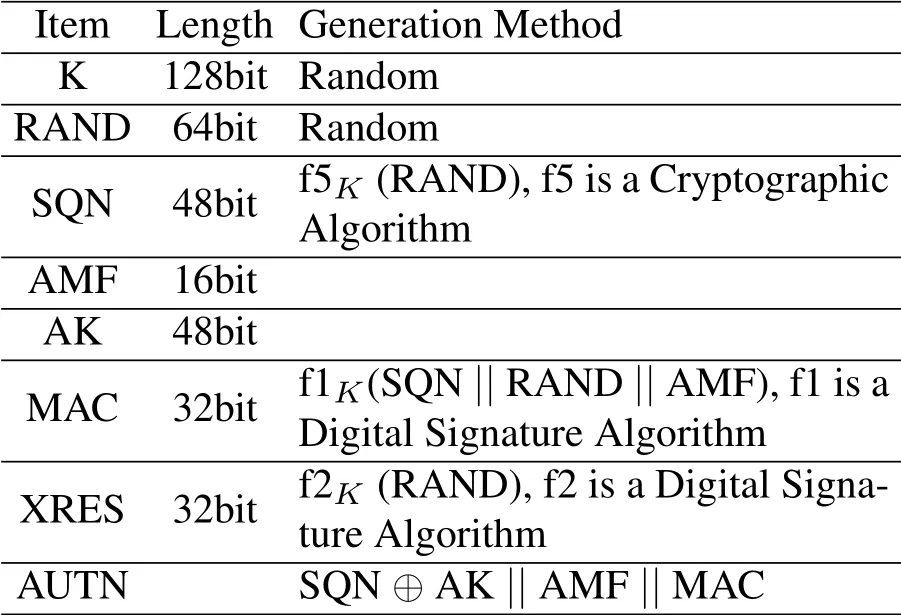
Table 3.Generation method of authentication vector data.
3.3 C-V2X Equipment Authentication Process
When the C-V2X equipment accesses the C-V2X system and applies for downloading or updating the communication certificate,the equipment must first be authenticated by the C-V2X system.The VID authentication center obtains the equipment VID and key K in advance from the VID registration center.The VID authentication center generates the authentication vector,and sends it to the AAA’s VID authentication unit.Then the authentication unit completes the authentication process for the equipment.The VIM needs to verify whether the authentication vector used by the VID authentication unit is the replay data.
1)The equipment reads the VID from the VIM and sends an authentication request to the authentication unit.
2)The VID authentication unit selects a new authentication vector,sends the RAND and AUTN to the equipment.The authentication vector is obtained from the VID authentication center.
3)The equipment sends the data to VIM after it receives RAND and AUTH.The VIM calculates the anonymous key AK and extracts the SQN; The VIM gets the MAC and compares it with the received MAC;If they are inconformity,the authentication fails; The VIM checks the SQN,if it’s in the correct range,the VIM calculates the RES and returns the RES to the VID authentication unit.
4)The VID authentication unit receives RES and compares it with XRES,if the compare result is the same,certification is thus successful.The authentication process is shown in Figure 7.
The logic of calculating and verifying for VIM RES is shown in Figure 8.
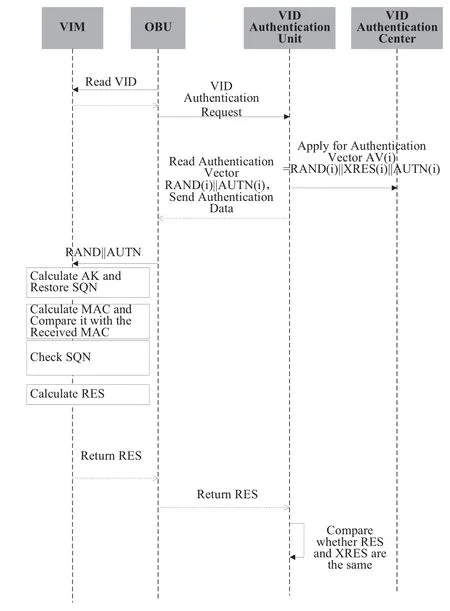
Figure 7.C-V2X equipment authentication process.
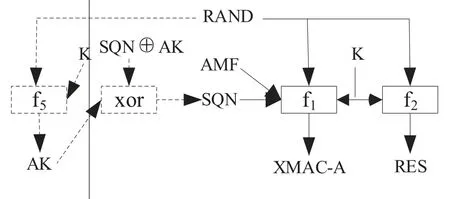
Figure 8.RES calculation and verification logic.
IV.SECURITY ANALYSIS AND EXPERIMENTAL VALIDATION
4.1 Security Analysis
The proposed architecture deploys a VID registration center in the C-V2X system,embeds a VIM in the CV2X equipment,deploys a VID authentication unit in the AAA,and deploys a VID authentication center in the certificate authority.Before the equipment applies for a communication certificate and establishes a secure communication with others,it must be certified by the AAA.C-V2X equipment can establish a secure and trust-worthy relationship with AAA and via authentication between them.The C-V2X equipment and the authentication center share the keyKstored in the secure storage area.Based on the keyK,the random number RAND,and the counter SQN,the authentication center generates the one-time authentication vector of the equipment,the vector includs challenge data and expected response data.
When the C-V2X equipment accesses to the C-V2X system,there exist mainly two security risks:First,malicious equipment tries to fake legitimate C-V2X equipment to apply for certificates from a certification authority and to establish secure communication with other C-V2X equipment.Second,malicious equipment eavesdrops on the authentication data in the open wireless environment,tries to replay the authentication response data to accesses the network.
The C-V2X system is proposed to deploy the VIM,VID authentication unit,and VID authentication center.The VIM and VID authentication center share the keyK.The challenge-response authentication procedure is performed between the equipment and CA.Challenge-response data,namely authentication vector,is generated and maintained by the VID authentication center in the certification authority.The cryptographic algorithm can ensure that only the authenticated C-V2X equipment can complete the challengeresponse process and can establish a secure trust relationship.VID authentication center distributes the authentication vector to the VID authentication unit in AAA in a secure way.The VIM in the equipment completes the specific challenge-response process.The AAA acts as a proxy for CA which issues a certificate for the C-V2X equipment after the VID authentication unit authenticated the C-V2X equipment successfully.The equipment without sharing keyKwith the authentication center could not complete the challengeresponse process with the VID authentication unit,it could not achieve authentication,and it could not be accepted by the C-V2X system,as well it could not obtain the certificate to establish secure communication.
Random RAND and counter SQN are set in the authentication vector generated by the VID authentication center.The counter SQN is independently maintained by the authentication center and updated in a rolling manner to ensure that an authentication vector can realize only one challenge-response.When the authentication process is finished,the authentication vector is invalid.The random RAND makes the change of the data in the authentication process to prevent replay attack and cryptographic algorithm break.Therefore,even if the fake equipment obtains the authentication process data transmitted through wireless communication,it could not replay the authentication process and could not apply for a certificate to establish secure communication.
4.2 Experimental Validation
Based on our preliminary research,an experiment validation environment is built according to the unified management and initial authentication scheme of CV2X equipment proposed in this paper.The prototype system consists of the certificate authority,the AAA server,and the equipments(OBU,RSU,etc.).Due to the requirement to the unified management and initial authentication,security registration equipment(VID registration center)is deployed to the prototype system.A VIM is embedded in the OBU and RSU,and used for authentication with AAA at the initial stage while the equipment accessing the C-V2X system.A VID authentication unit is deployed to the AAA and gets an authentication vector from the authentication center through a secure communication way.A VID authentication center is deployed to the certificate authority to generate authentication vectors based on sharing key K with the equipment.The experimental validation environment architecture is shown in Figure 9(a).
The VID registration center is an offline equipment.The VIM is embedded into OBU /RSU through I2C(Inter-Integrated Circuit)interface to provide security service.The VIM includes security algorithm module and authentication module.It uses low-power security chip core,embedded operating system and C language development SDK(Software Development Kit).It provides key storage and identity authentication functions.The identification of the VIM is unique and can not be cloned.OBU /RSU writes data to VIM through SDK and executes authentication process.The VID authentication unit is programmed by java language and communicates with AAA through internal network.The VID authentication center includes registration module,authentication module,log viewing module,etc.The VID authentication center uses server computer,with Linux operating system,MySQL database and Java application,it communicates with the certificate authority through internal network.
When an OBU is produced and prepared to access the C-V2X system,the manufacturer regists the OBU in the VID registration center.The VID registration center generates a unique VID for the OBU.It uses the organization code,manufacturer code,category,model,and other information and it writes VID into the OBU VIM.The equipment registration is shown in Figure 9(b).
The OBU needs to apply for a communication certificate from the certificate authority,the VIM of the OBU applies to the VID authentication unit in the AAA for accessing authentication firstly.The authentication unit then checks whether there is an authentication vector of the OBU.If there is not an authentication vector of the OBU,it applies to the VID authentication center in the certificate authority for accessing authentication vector.The VID authentication center generates a random RAND and a counter SQN,it then generates the authentication vector of the OBU through running cryptographic algorithm according to the key K sharing with the OBU.The VID authentication center sends the authentication vector to the VID authentication unit through internal communication.The VID authentication unit parses the authentication vector and sends the challenge data to the OBU VIM.The VIM calculates the response data using the sharing key K and challenge data,sends the response data to the VID authentication unit.The VID authentication unit compares the response data with the expected data to judge the validity of authentication response.The OBU is allowed to access to the C-V2X system after a successfully authenticating.The certificate authority generates the communication certificate and distributes it to the OBU.Otherwise,the access request is rejected.The simulation of the authentication is shown in Figure 9(c).
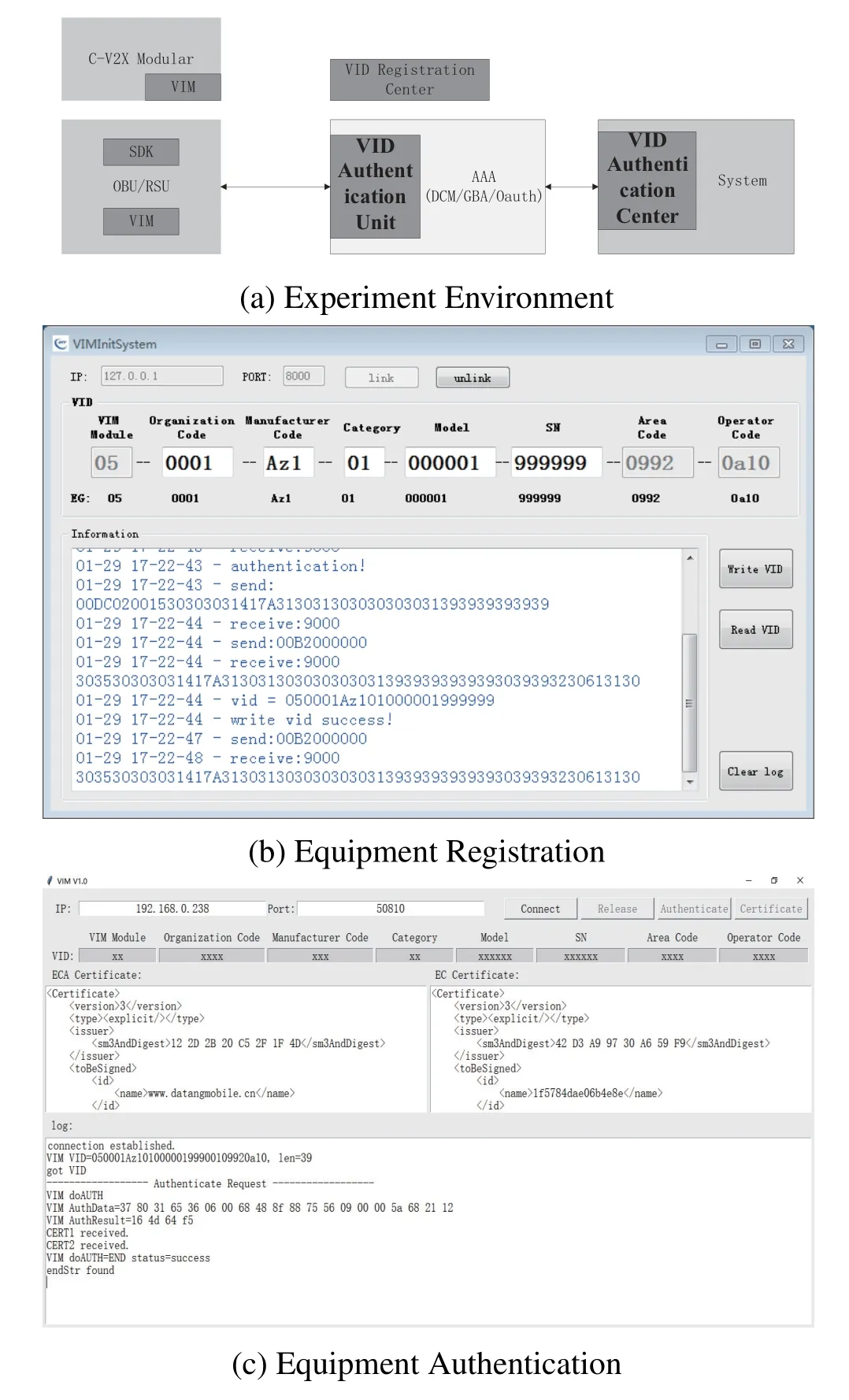
Figure 9.Experiment simulation system.
The experimental validation results show that the CV2X equipment can unify the identification management and initial authentication mechanismis feasibly and effectivly.The performance evaluations and optimizations of this scheme needs further study.
V.CONCLUSIONS
There are various kinds of equipments in a C-V2X system,including RSU,OBU,cloud platform,application server,etc.All the equipments work together through the Uu interface or PC5 interface.The C-V2X system thus faces many network security risks and threats.This paper proposes an unified numbering and management method for C-V2X equipment identification.Based on this,an initial authentication scheme is then proposed.Some new entities such as VIM,VID registration center,VID authentication unit,and VID authentication center should work together with the existing entities in the C-V2X system.When the equipment accesses the C-V2X system and needs to download or update the communication certificate from certificate authority,it sends an authentication request to the AAA first,and it continues the access process after the authentication is successful.This mechanism complements the current C-V2X system security scheme,and they works together to form a complete C-V2X system security system.
ACKNOWLEDGEMENT
This work was financially supported by The National Natural Science Foundation of China(No.61931005).Thanks to Professor Shi Yan(Beijing University of Posts and Telecommunications)and Professor Dake Liu(Hainan University)for their contribution to revision and improvement of this paper.
- China Communications的其它文章
- Two-Timescale Online Learning of Joint User Association and Resource Scheduling in Dynamic Mobile EdgeComputing
- SHFuzz:A Hybrid Fuzzing Method Assisted by Static Analysis for Binary Programs
- SecIngress:An API Gateway Framework to Secure Cloud Applications Based on N-Variant System
- Generative Trapdoors for Public Key Cryptography Based on Automatic Entropy Optimization
- A Safe and Reliable Heterogeneous Controller Deployment Approach in SDN
- Distributed Asynchronous Learning for Multipath Data Transmission Based on P-DDQN

