τ-Access Policy:Attribute-Based Encryption Scheme for Social Network Based Data Trading
Shamsher Ullah ,Lan Zhang,Muhammad Wasif Sardar,3,Muhammad Tanveer Hussain
1 School of Software,Northwestern Polytechnical University,Xi’an 710072,Shaanxi,China.
2 School of Computer Science and Technology University of Science and Technology of China,Hefei 230026,Anhui,China.
3 Department of Electronics and Electrical Systems,University of Lahore,Punjab,54000,Pakistan.
4 School of Science,Department of Mathematics,University of Management and Technology,Lahore,54770,Pakistan.
Abstract:The rapid development of social technology has replaced physical interaction in the trading market.The implication of this technology is to provide access to the right information at the right time.The drawback of these technologies is that the eavesdropper can remove the user from the network and can create proxy participants.In this paper,we discuss how a social network overcome and prevent these data trading issues.To maintain the security of data trading,we applied ABE technique based on DBDH to secure data trading network.Our proposed τ-access policy scheme provides the best solution for the betterment of data trading network in terms of security.
Keywords:ABE;privacy;integrity;data trading;PTI;τ-access policy
I.INTRODUCTION
In data sharing,Social Networks(SN)[1–10]such as Facebook,Twitter,WhatsApp,LinkedIn,AngelList and Google+,etc.play a vital role to transfigure the manner of the data and interact a hundred of millions of consumers across the globe.During this interaction,all the users are able to transform all the information in the world.Once the user enters the information to the SN,its privacy becomes loss and he/she not be able to recover.So the key problem of SN designs is the lack of user privacy because the user’s private data is out of control and the network is helpless to maintain the privacy of the consumers[11].The insiders of social networks intentionally or unintentionally release private information[12,13].Encryption is used to prevent this type of issue in privacy[12,14–16].The natural tool to protect privacy is cryptography.But in SN the obvious cryptographic schemes do not consent customers to scalably state their privacy.Customer’s famine to be able to share gratified with intact groups(such as with their friends,family,classmates,etc.).Attribute Based Encryption(ABE)is a strong cryptographic primitive,in which the privacy remains constant in any SN system[14].
1.1 Social Networking Service
On Social Networking Service(SNS)[17],whenever sensitive information needs to be shared between two or more parties,we use confidentiality known as“nondisclosure contract”.This contract help to formalize the relationship and provide legal remedies during confidential information proclamation.“Confidential Information” is the information which is not known to the public,or out of the public domain but is private to the company or individual who possesses it.From a commercial perspective,confidential information can include details of a company’s financial affairs,business operations or customer engagements.A key type of confidential information could be a Company’s Trade Secret(CTS),such as a method or technique of manufacture which gives the company an edge over other competitors.A person who has access to confidential information is generally obliged under the law to keep the information confidential and cannot usually disclose the information to third parties.If he disclose,he is said to have breached the obligations of confidentiality and is liable to legal action.In 2002 B.F.Cooper proposed the concept of data trading,in which he proposed trades by replicating sites data into another contacting site.A sitewill be replicated by siteand in returning step a copy of assortment of software documentation preserved by siteis warehoused at site.The network sites will be able to take the decision about the contact with the trade and its offer will be offered to another site,Figure 1[18].
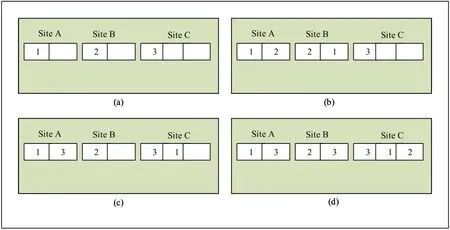
Figure 1.Data trading[18].
1.2 Social Networks Investment
Traditional investment has experienced a revolution due to the growth rate of Electronic Trading Services(ETS)that enable stockholders to use the internet to demeanor secure trading Figure 2[19].Technological innovations bypass human intermediaries,increasing competition and reducing transaction costs[20].
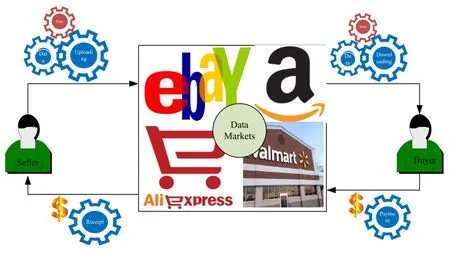
Figure 2.Network based data trading.
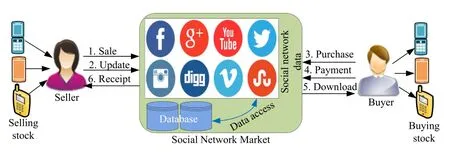
Figure 3.Trading market with social network.
1.3 Social Networks with ABE
A social network is capable to utilize attributes for authenticity except revealing attribute themselves,but the limitation is missing verifiability property[13].In 2010 M.Pirretti et al.,[10]proposed secure attributebased system,the author says that all the customers must expose large amount of private information(e.g.name,age,address,and sex,etc.)in a global.The similar attributes are shared in the group of people and friends,then they automatically allied with each other,and occurrence is created for undesirable parties to get private information from that system.Therefore,ABE based systems are suitable to provide customers controlled privacy[10].
II.RELATED WORK
Social Network Sites(SNS),such as Facebook,Bebo,(Myspace and Cyworld[21])etc.are increasingly attracting the attention of any type of organizations(academics,industry etc.)users intrigued by their affordances and reach.SNS have attracted millions of users simultaneously.User have investigated privacy threats associated with SNS[17].The limitation of this paper is that there is no privacy prevention techniques in which user’s privacy remain secured.The author has just investigate the privacy treats(personal information)[22].The connecting services of the social networks has increased and users are enrich to access the data from social web,but it face several types of security and privacy challenges[23].Z.Maamar et al.,proposed why web services need social networks.The focusing point of Z.Maamar et al.,scheme is only“trust”.The trust mainly related to the strength of the social relations that users have on top of their experiences to use the web services,with the lack of privacy issues[24].To maintain privacy,L.Zhang et al.,proposed message in a sealed bottle scheme,that provide privacy using symmetric key encryption.The proposed scheme is based on privacy-preserving profile matching and secure communication channel establishment mechanism in decentralized Mobile Social Networks(MSN)without any presetting or Trusted Third Party(TTP)[25].The lack of this scheme is that,without TTP the possibility of eavesdropping,eavesdropper is able to make match-able profile for eavesdropping[25].SNS[11,26–29],enhances the efficiency and allow the users to achieve fine-grained control to solve the single point of failure problem,performance bottleneck and find the matcher[30].In social network personal data protection is the notion of privacy.It has a fundamental rights,allocation of property rights,balancing consents,and user’s coordination[31].In 2005 A.Sahai and B.Waters first proposed the concept of ABE.Which was designed for access control of shared encrypted data[32].E.Luo et al.,proposed the hierarchical multi-authority attribute-based encryption scheme to implement the privacy preserving in MSN[33].In ABE algorithm,a customer keys and encrypted transaction texts(Cτ)are labeled with the sets of attributes and a particular keys(private,public and secret keys)and decrypt(Cτ)if it is matched between the attributes of the transacted cipher’s and the customer keys get transacted messagem.The proposed schemes in[34,35]are compromised that losing information will be minor.In 2013 B.Oleksandr,and S.Buchegger proposed“Encryption for peer-to-peer social networks”,the author addresses that peer-to-peer online social network doesn’t rely on centralized storage of user data.The external storage of this type of platform is free from any type of storage data and it safe.Therefore,encryption plays a fundamental role to maintain social networks security[36].S.Jahid et al.proposed“EASier”approach that supports fine-grained access control policies and dynamics group membership by using ABE[12].The proposed schemes having the lack of privacy and security issues,because it create a proxy participants.The proxy participants is capable to play the role of an eavesdropper.Once eavesdropper is enter to the trading environment,the whole system become insecure.
In ourτ-access policy,the access policy is encrypt transacted plaintext and decrypt data transacted ciphertext,to maintain the security of the user and its data during trading.There is a need of strong trust,security and privacy in today’s social network activities for data trading.Therefore our proposed scheme is fully trusted scheme which fulfills the trustiness,privacy,integrity,it grant full access to each other simultaneously.
Our Contributions:-Our major contributions as follows:
1.We designed a social network based on ABE,in which users use their PTI attributes to authenticate each other before communication.
2.Our proposed scheme has the ability to simultaneously provide the privacy protection and verifiability of users.
3.Based on Decisional Bilinear Diffi-Hellman(BDBH)hard problem,we provide progressive privacy and integrity levels corresponding to users increasing privacy and integrity requirements during their interactions.
4.Once the user creates a key then it can buying and selling to each other.
5.We use TTP to control all the key management(such as key exchange,key generation etc.).
6.τ-access policy is used to encrypt and decrypt the requests of the users.
7.We applied ABE algorithm on SN and data trading market to solve all the trading market issues such as organization maintenance,social contract,Employees Deviant Acts(EDA),misconception,lack of proper planning and evaluation,payment and data trading demands.
III.ROAD MAP OF THE PAPER
The rest of the paper is structured as follows.Section IV introduces preliminary knowledge of some social network data confidentiality schemes.Our proposed scheme is presented in detail in Section V.The analysis and performance is presented in Section VI and VII.We describe the security properties of our scheme in section VIII.In section IX and X,we finally describe conclusion and open direction.
IV.PRELIMINARIES
Data confidentiality policy is a set of rules and guidelines applied by statistics in Denmark when processing large volumes of data.The author,says that data confidentiality policy is a set of rules and guidelines applied by statistics Denmark when processing large volumes of data.They combined two fields one is statistics and another one data confidentiality policy.The implementation of statistics Denmark’s of the statutory rules and basics principles governing the processing data in a specific way which ensures that citizen and enterprises.The limitation of this book it just focuses on data confidentiality and ignores other security properties such as integrity,authenticity,non-repudiation,and unforgeability.The usage of confidentiality is to protect information from unauthorized parties.In the transaction,two parties could be read-only by the intended seller and buyer Figure 3,this is the first goal of cryptography.In general rules,data confidentiality provide strong privacy protection and avoid undesired disclosure[37].
An individual person must be confidentialised so that it is not possible to obtain new knowledge about individual person affairs from a statistical product.Its processing is regulated in the Public Administration Act(PAA),which regulates issues concerning the disclosure of data,and the regulation on European statistics.With reference to the first overall confidentiality principle of protecting the identity of the persons,enterprises,and institutions.We ensure in accordance with the data confidentiality policy adopted that statistical output confidentialised by two methods such as active and passive confidentiality.
4.1 Bilinear Mapping
LetG0andG1be two multiplicative cyclic groups of prime orderp.Suppose thatgis a generator ofG1.The properties of the bilinear map[38]are:
1:Bilinearity:e(ga,gb)=e(g,g)ab,∀g∈G,a,b∈.
2:Non-degeneracy:We haveg∈ G0,such thate(g,g)/=”1”.
3:Compatibility:An efficient algorithms to evaluate bilinear mapping.
4.2 Computational Assumption
Definition 1.DLP[39].Let g be a primitive root belong to Zp and h be a non-zero element of Zp,the hard problem DLP is:
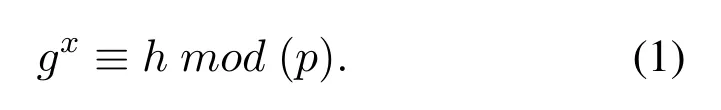
Definition 2.DBDH Assumption[40].Let G be a multiplicative cyclic group of order p,with generator < g >.The DBDH assumption is(g,ga,gb,gc),whereis:
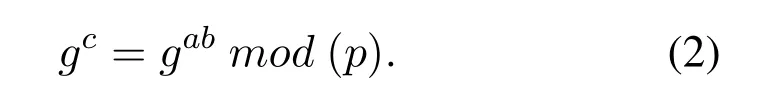
V.OUR PROPOSED SCHEME
Our proposed scheme based on ABE.The usage of ABE for data trading based on social network is provides security and privacy of the users(seller and buyer).To achieve this goal we use ABE cryptographic technique based on DBDH assumptions[41–43].
5.1 Attribute Based Encryptio n
We use ABE algorithm to recover the issues of confidentiality,maintenance organization,social contract,customer deviant act,misconception exclusion,planning,evaluation and payment.This algorithm follows DBDH assumptions.The flow of algorithmic construction is given in Figure 4.
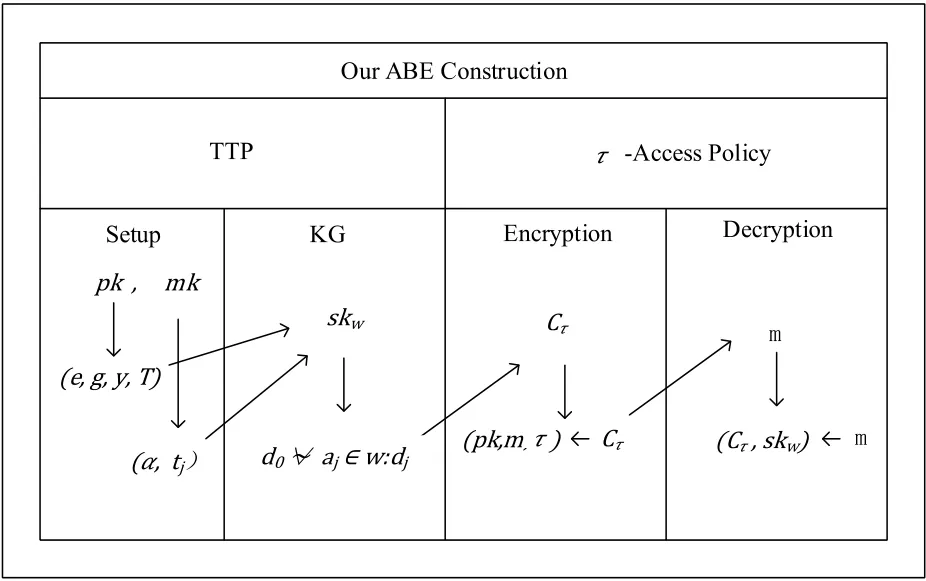
Figure 4.Algorithmic flow of our ABE construction.
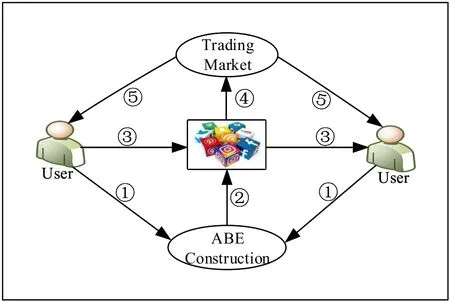
Figure 5.General flow of our ABE construction.
5.1.1 ABE Keys
In this section,we have two types of keys one is keys setup and another one is key generation.For key setup we use Algorithm 1 and for key generation we use Algorithm 2.Which are given below:
Algorithm 1,also known as initialization algorithm.In this algorithm,TTP set and initialize the public and master keys.The setup of these keys fully depends on security parameter known askand generatorgfrom the bilinear groupG0with the prime orderp.Afterkandg,TTP will build a symmetric bilinear map^e(step 2).In step 3,we check the satisfaction of our created policy in binary form.If it is satisfied then we will goto step 4.In step 4,we select two random exponentsα,βwhich belong to a fieldZpof order prime numberpand check each attribute belongs toω.If yes it generate a random elementtj∈Zpthen in step 5 we compute public and master keys in the form ofpkandmkfrom the public key elements and random element set which belong to a group of prime order.After the keys setup,the selected key is forwarded to key generation algorithm(Algorithm 2).Algorithm 2,use bilinear pairing with DBDH assumption and generate and computedjandskwkeys.
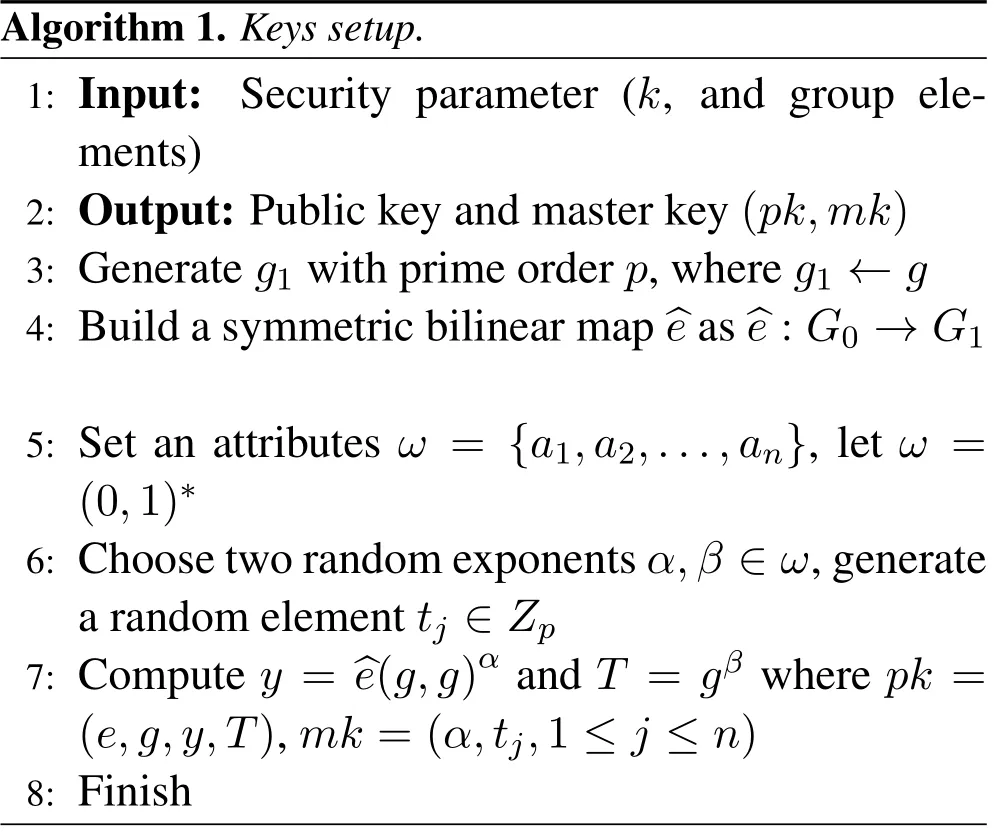
Algorithm 1.Keys setup.1:Input:Security parameter(k,and group elements)2:Output:Public key and master key(pk,mk)3:Generate g1 with prime order p,where g1 ←g 4:Build a symmetric bilinear map^e as^e:G0 →G1 5:Set an attributes ω={a1,a2,...,an},let ω=(0,1)∗6:Choo se two random exponents α,β∈ω,generate a random element tj∈Zp 7:Compute y=^e(g,g)α and T= gβ where pk=(e,g,y,T),mk=(α,tj,1 ≤j ≤n)8:Finish
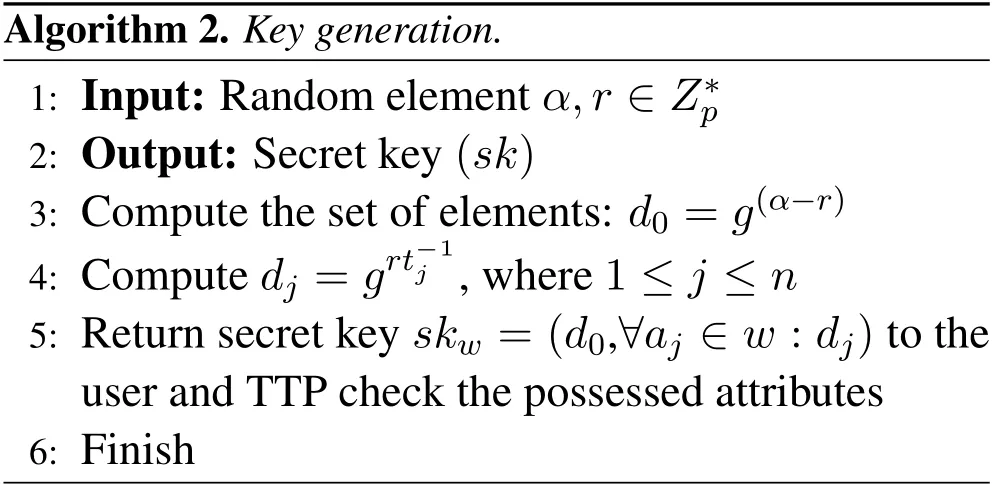
Alg orithm 2.Key ge Input:Rando Output:Secre neration.1:m element α,r∈Z∗p 2:t key(sk)3:Compute the set of elements: d0=g(α−r)4:Compute dj=grt−1 j ,where 1 ≤j ≤n 5:Return secret key skw=(d0,∀aj∈w :dj)to the user and TTP check the possessed attributes 6:Finish
In key generation algorithm TTP perform all the user’s requests.TTP successfully defend the users requests and protect any type of attack,such as collusion attack.To prevent this type of attack,TTP generate a random numberand set private elements of the user accessible(see step 2 of Algorithm 2).In the last step,TTP generate a secret keyskwto a user’s with possess attributew.User’s use this secret key and access the trading server under the supervision of TTP(step 3 of Algorithm 2).
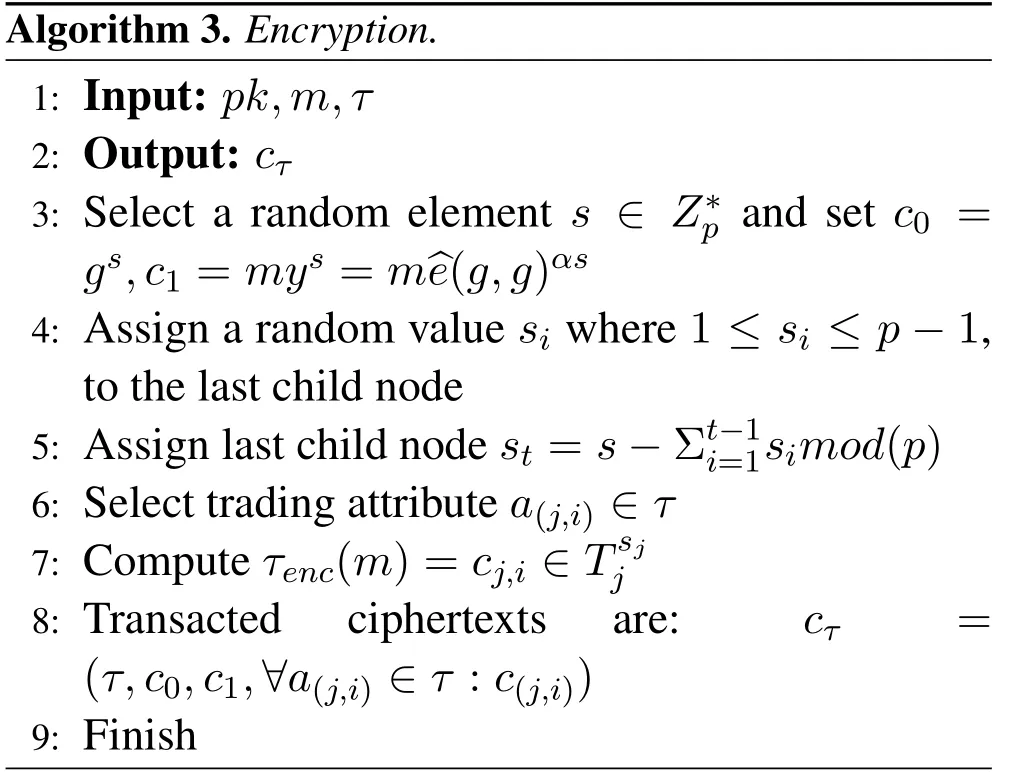
Algorithm 3.Encryption.1:Input:Output pk,m,τ 2:: cτ 3:Select a random element s∈Z∗p and set c0=gs,c1=mys=m^e(g,g)αs 4:Assign a random value si where 1 ≤si ≤p −1,to the last child node 5:Assign last child node st=s −Σt−1i=1simod(p)6:Select trading attribute a(j,i)∈τ 7:Compute τenc(m)=cj,i∈Tsj j 8:Transacted ciphertexts are:cτ=(τ,c0,c1,∀a(j,i)∈τ :c(j,i))9:Finish
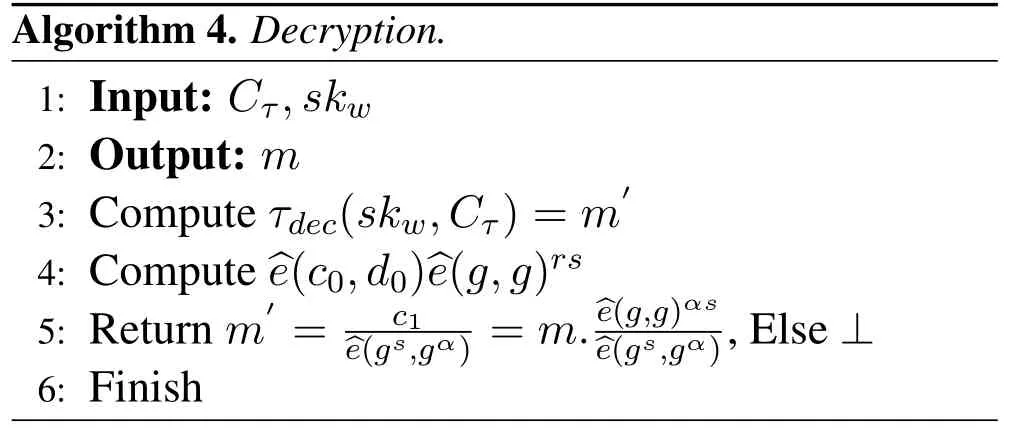
Algorithm 4.Decryption.1:Input: Cτ,skw 2:Output: m 3:Compute τdec(skw,Cτ)=m′4:Compute^e(c0,d0)^e(g,g)rs 5:Return m′=c1^e(gs,gα)=m.^e(g,g)αs^e(gs,gα),Else ⊥6:Finish
5.2 τ-Access Policy
In this policy,we combine two cryptographic techniques one is encryption and another one is decryption.Encryption is used to maintain confidentiality and decryption is used to verify the reverse of the transacted messagemin accurate.
5.2.1 Encryption
Encrypt(pk,m,aj)←Cτ:The encryption algorithm is performed by the seller(data owner).It takes public keypk,the set of the encryption attributesajand the transacted messagemas input.This algorithm outputs the encrypted transacted messagecτ.The algorithmic representation of encryption on attributes(pk,m,Cτ,skw)is described in Algorithm 3.
In this algorithm,if the users want to encrypt transaction messagem,then it select a random element of signature known asand set ciphertexts transactionc0,c1from the generator,signature,transaction message and public key(g,s,m,y)by using Bilinearity^e.In step 2,τ-access policy mark all the root nodes and assign a random value as a child node and transacted root node(step 3 and 4).In step 4,we select the required trading attributes under theτaccess policy.In step 5,we compute the transacted ciphertextsc(j,i)and assign the index value of the transacted ciphertexts to the left node and returncτas an output.
5.2.2 Decryption
Decrypt(Cτ,skw)←m:The decryption algorithm is performed by the buyer.It takes the secret keyskwas an input,the set of the decryption attributesbjand the transacted ciphertexts trading attributescj,i.This algorithm outputs the decrypted transacted cipher’s trading attributescj,i.The algorithmic representation of encryption on attributes(pk,m,Cτ,skw)is described in Algorithm 3.
The algorithmic representation of decryption on attributes(m,τ,Cτ,skw)is described in Algorithm 4.
In this algorithm,the user’s need to decrypt the transacted ciphertextscτusing its own secret key.Our proposed schemeτ-access policy,satisfy the originality of the transacted messagemotherwise it returns⊥.To get the originality of the transacted messagem,we use the following Eqs.(3),(4)and(5).
1.For every attributeaj∈w′,we compute(aj)from Eq.(3),bilinearityfrom Eq.(4),and transaction message(m)originality is from Eq.(5).
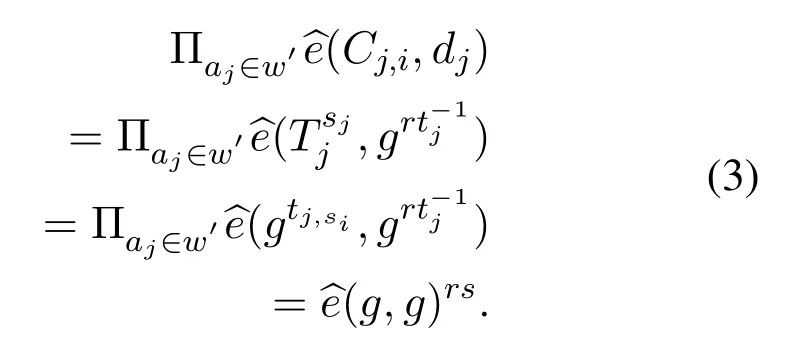
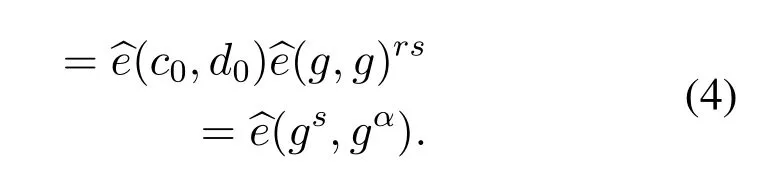
3.Returnm′,where
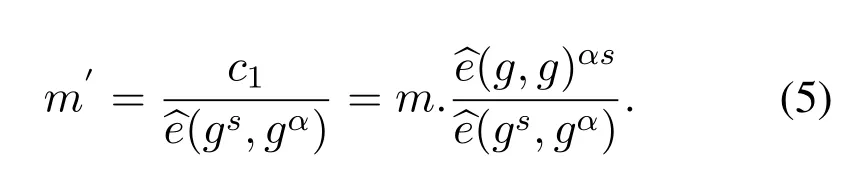
Finally,we can get the original transaction messagem.The algorithmic representation is shown in Figure 4.
VI.ANALYSIS
In this section,we focus to analyze the improving effect of our proposed attribute based encryption scheme for social network based data trading.
6.1 ABE Practice on Social Networks
In this section we describe the interaction of social network between customer manager and customers.All the customers record is stores in their own trading cloud.The detail analysis is shown below:
6.1.1 Setup
The customers(C1,...,n)want to connect to the data trading web server(Ts)and generates an account username and password(Un,p)which will be used to authenticate the customers to the server for logging in data trading database.Once a customer has registered for the service,it downloads a client bid which will run locally on their device.The user send request using its private key(dj)to an installed client bid corresponding to its attributes setωfrom TTP authority.
6.1.2 Key generation
In key generation(KG),to create an electronic service record for one of his customer,the manager sends a request for access to the customer data.The request is sent to the customer by encrypting it under his public key(pk)which is downloaded by the client bids.To access this bids the customer use their own username and private key(dj)from his own private key element setω.
6.1.3τ-Access Policy
Our proposedτ-access policy contains encryption and decryption algorithms.After being granted access by the customer,the manager makes an access request to the server base on the customer’s record.The manager will setτaccess policy to encrypt the customer record by using ABE technique.The trading manager then sends the Transacted Ciphertext(cτ)to the cloud.If a receiver who received(cτ)matches then user can download/upload it from/to the trading server cloud.This encrypted transaction file is decrypted at the receiver’s client-side and is available for reading.
•Encryption
In this policy,the trading market manager is able to encrypt(Enc)the Private Transaction Information(PTI)of the seller and buyer.If a trading market manager needs to encrypt seller PTI then the user will use private key of the seller,else it need to encrypt the buyer PTI than user will use the private key of the buyer.The encrypted and decrypted phase will send all these encrypted PTI files into trading market cloud.From this encrypted data,all the transactions of seller and buyer will also be handled.
•Decryption
In this policy,the trading market manager is able to decrypt(Dec)the PTI of the seller and buyer.If a trading market manager needs to decrypt seller PTI then it will use its public key of the seller,else it need to decrypt the buyer PTI then it will use the public key of the buyer.All decrypted transaction files of PTI file are sent to trading market cloud.From this decrypted phase all the decrypted transaction files of the seller and buyer are successfully transmitted to each other.The general flow ofτaccess policy w.r.t encryption and decryption is shown in Figure 6.
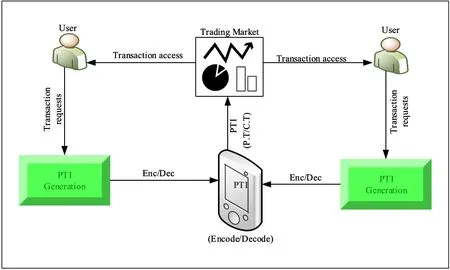
Figure 6.Flow of τ-Access Policy.
6.1.4 Query customer record
If a trading manager wants to query the customer,the manager send the authenticated trading transaction encrypted file under public key(pk)to the customer.In case of a fresh upload,customer decrypt the transaction plaintexts containing the authenticated trading data and creates a new encrypted file and a corresponding entry such that only the customer and the manager can mutually access all the transactions.Letσsis the attributes set of the seller andσbis the attributes set of the buyer.The set elements of each customer(seller and buyer)are:
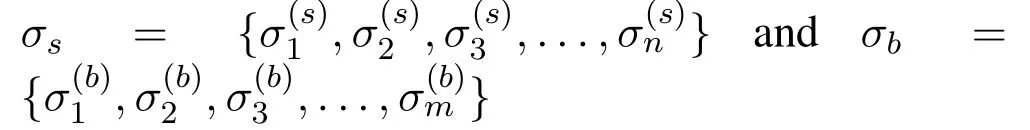
Nowσsandσbwants the selling and buying queriesandto a trading manager(TTP).The trading manager(TTP)apply algorithm(5)forTcqueries record.
6.1.5 Transaction query record
In customer transaction record,the buyer and seller use ABE and they are able to upload the requests into a trading market by using its social network.The trading market match all the contents of the customers with the social network and ABE.If it matches to each other,the transaction will be successful done otherwise it will generate transaction failure message and close all the requests of the customers and save computation from the cloud.For transaction query the trading manager(TTP)apply Algorithm 6.
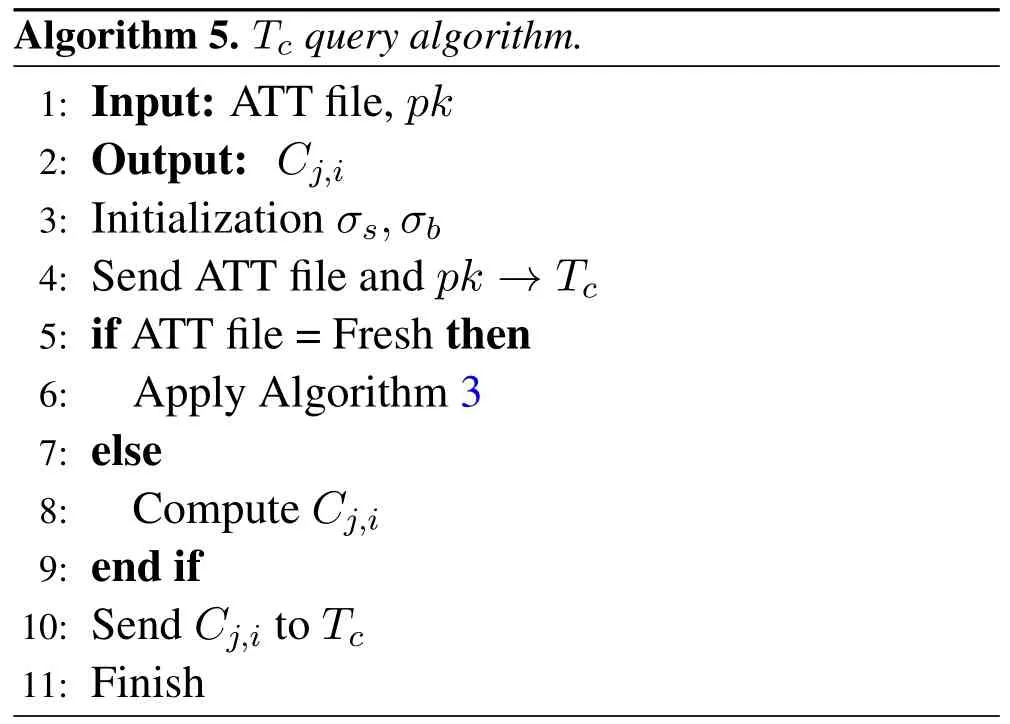
Algorithm 5.Tc query algorithm.1:Input:ATT file,pk 2:Output: Cj,i 3:Initialization σs,σb 4:Send ATT file and pk →Tc 5:if ATT file=Fresh then 6:Apply Algorithm 3 7:else 8:Compute Cj,i 9:end if 10:Send Cj,i to Tc 11:Finish
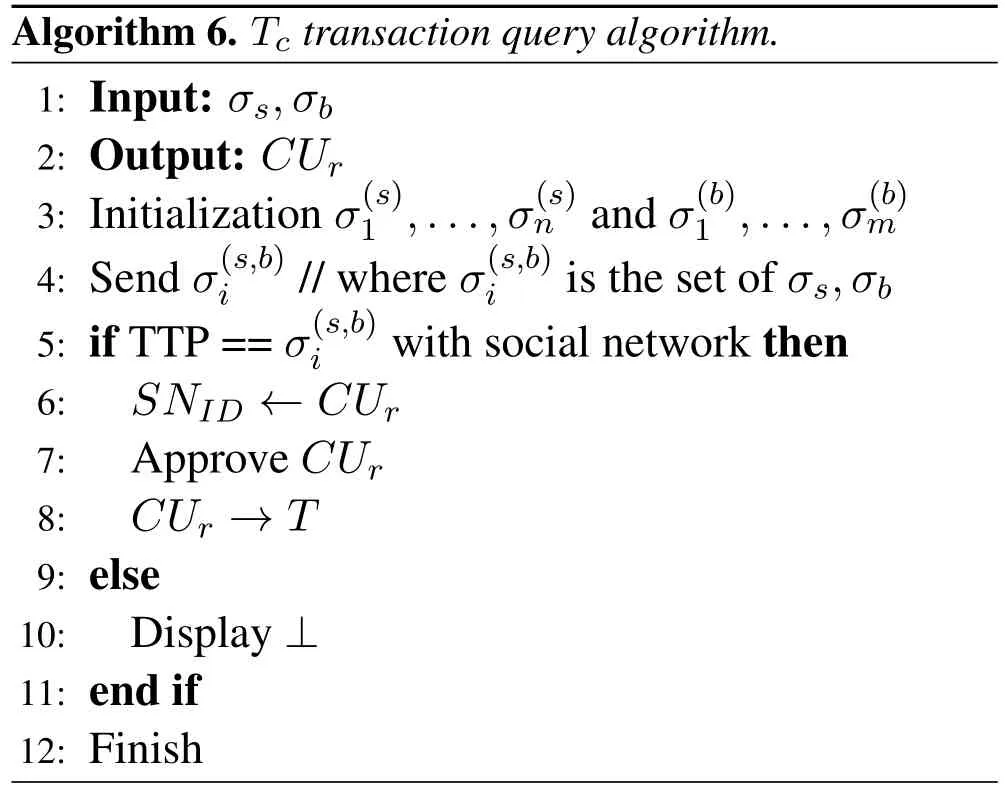
Algorithm 6.Tc transaction query algorithm.1:Input:Outputσs,σb 2:: CUr 3:Initialization σ(s)n and σ(b)m i//where σ(s,b)iis the set of σs,σb 5:if TTP==σ(s,b)iwith social network then 4:Send σ(s,b)1 ,...,σ(s)1 ,...,σ(b)6: SNID ←CUr 7:Approve CUr 8: CUr →T 9:else 10:Display ⊥11:end if 12:Finish
6.1.6 Successful transaction(Ts)
The customers send the public and private keys(dj,pk)with the transaction requests(r)to TTP.TTP use ABE encryption technique,to encrypt request(r)and generate transaction texts(Tt)and transaction ciphertextscτusing its private key(dj)and encryption and decryption.ABE send all the encrypted plaintexts transactions,public keys and encrypted plaintexts transaction withτpolicy into social network and trading market.Trading market match the customers transaction plaintexts with social network transaction plaintexts and transaction ciphertexts to each other using its own public key and secret keys and decide about matching all the terms.If all the terms matches to each other than transaction is done successfully,otherwise it discard the requests of the customers and display the“transaction failed”message(Figure 7 and Algorithm 7).
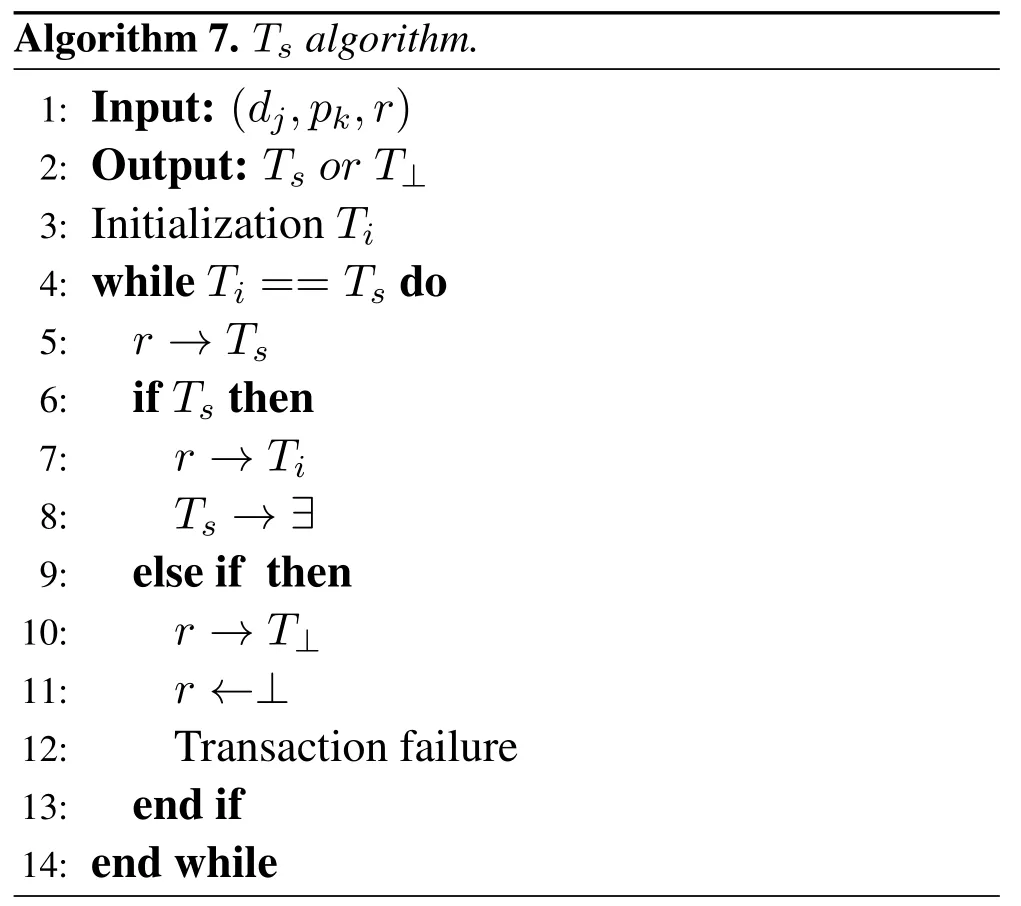
Algorithm 7.Ts algorithm.1:Input:(dj,pk,r)2:Output: Ts or T⊥3:Initialization Ti 4:while Ti==Ts do 5: r →Ts 6:if Ts then 7:r →Ti 8:Ts →∃9:else if then 10:r →T⊥11:r ←⊥12:Transaction failure 13:end if 14:end while
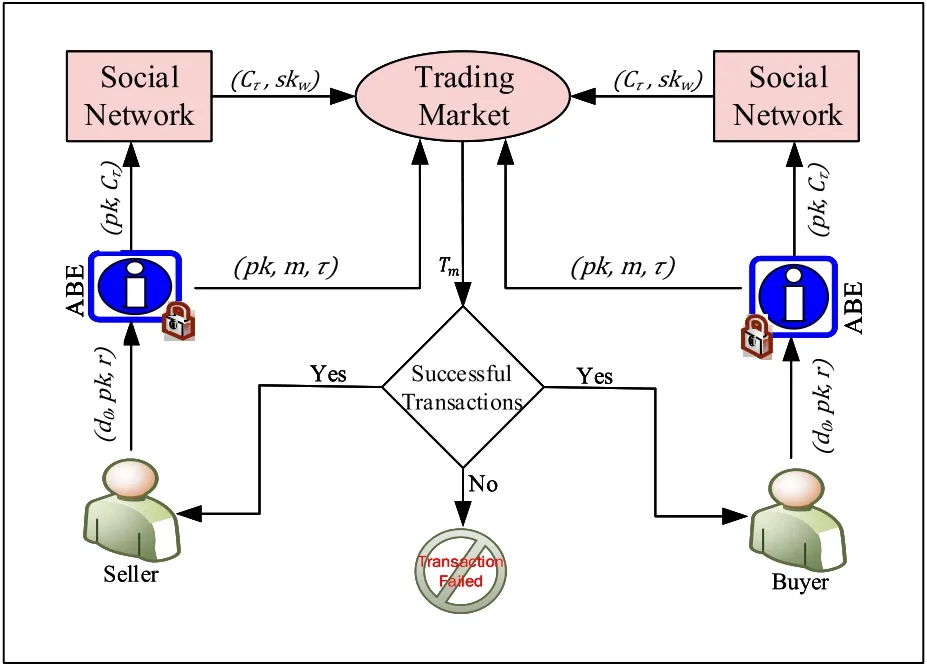
Figure 7.ABE based trading market.
6.1.7 Maintenance of confidentiality
The customer’s confidentiality fully depends on seller and buyer private,public and secret keys.Therefore,eavesdropper must need to get all that keys.But it is hard for eavesdropper to get that keys due to DBDH.
6.2 The Usage and Analysis of Our Policy
In this section we describe how to solve all the issues with respect to privacy and security in data trading.The solution of these types of issues is shown in Figure 8,and our proposed schemes security properties are based on Theorems 1-10.The proof is given below:
Figure 8.Theorem representation in terms of security properties.
6.2.1 Confidentiality protection
Our proposedτ-access policy is used to protect data confidently in the desired trading strategies.Data confidentiality protection is based on Theorem 1 and the required solution of Theorem 1 is based on Eq.(6).
Theorem 1.τ-Access Policy can provide data confidentiality,this means the unauthorized users and trading servers cannot discover the content of the stored data.
Proof.The trading manager signs and encrypt his private data and send it to trading server as:
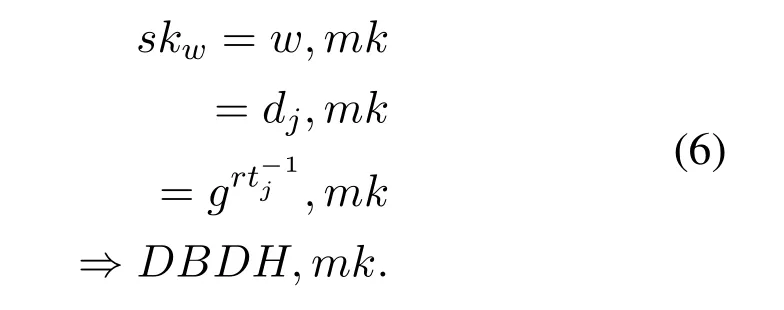
Is hard due to DBDH,and eavesdropper is failed in its eavesdropping.
In Key Generation(KG)algorithm,if eavesdropper want to break the confidentiality it must need to get secret key(sk).But from KG algorithm secret key is based onwwhich is computationally hard due to DBHD and our scheme confidentiality remain secure from all type of attacks.
6.2.2 Organization maintenance
Organization maintenance fully depends on Theorem 2.The usage of our proposedτ-access policy give theaccurate result of Theorem 2 in Eq.(7).
Theorem 2.Our proposed ABE scheme encrypt m,τ and send it to trading market with encrypted texts Cτ using τ-access policy.
Proof.A trading market manager/TTP is able to verify the accuracy of the encrypted textCτ.
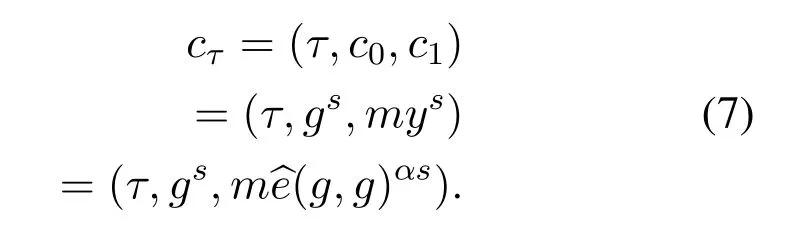
The trading server or cloud of the organization is safe from dummy customers’ requests,because all those customers which are making a burden in organization maintenance and send dummy requests to the trading cloud.The organization automatically discard all those requests which does not matches it information to the trading market customer information.In trading market the usage of public key and secret key plays the vital role for maintaining the organization life time.ABE does not allow irrelevant requests to social network and to trading market.The trading market manager will check the required information for the trading,if it match transaction will be allowed otherwise it will reject the request and save the data trading cloud from irrelevant buyer/seller known as eavesdroppers.
•Social Organization
In social network,login account of buyer and seller fully depends on its ABE.ABE get public,private and transaction message/requestrand generate a transaction ciphers with the transacted ciphertexts(Cτ).The user useτ-access policy and public key to access first the social network and then use social network for trading purposes.
•Trading Organization
The trading organization matches the ciphers,transaction message,public key and secret key.If they match all together then trading organization allow buyer and seller for its trading,otherwise it generates transaction failed message and discards all the requests of the buyer and seller.
6.2.3 Social contract
In social contract,ABE algorithms play the basics role.Our proposed ABE algorithm is able to maintain social network contract between buyer and seller.The implication of Theorem 3 is to maintain social network contract.
Theorem 3.ABE algorithm generates pk and encrypt transacted text(m)from the buyer and seller private data using τ-access policy and send it to the trading market through the social network.The usage of buyer and seller private data need to maintain the social network contract with trading market.
Proof.In our proposed scheme buyer and seller use the social network on which it is able to access the data trading cloud.Our ABE construction have the capability to avoid illegal customers’(buyers/sellers)requests and prevent the trading cloud from eavesdropping and from computation loading.On behalf of ABE,buyer and seller will be able to enter to the social network and trading market.Without ABE permission,directly access of the buyer and seller or the access from the social network is considered as illegal and ABE will discard all the buyer and seller requests and display the discard message⊥.
Therefore social network contract remains constant and gives the best opportunity to buyer and seller without any illegal buying or selling and also it reduces the computations of the trading cloud.
6.2.4 Customer deviant acts
Customer deviant act is the negation of positivity of buying or selling(trading).This act means just to bound trading market and seller and buyer really don’t want any type of trading.Therefore,Theorem 4 is used to avoid this type of acts during trading and safe the computation overheads over the trading cloud.
Theorem 4.During trading our ABE scheme avoids any type of customer deviant acts.
Proof.Ourτ-access policy generated after ABE algorithm,each information of buyer and seller is encrypted and decrypted using its own private data.Therefore,any type of deviant acts from the customer or employee is avoided by ABE algorithm.The impact of our proposed ABE scheme create a positive work environment for trading organization and its implementation has strong internal and external control from eavesdropper.
6.2.5 Misconception exclusion
In misconception exclusion,the goods do not mistakenly transfer or send to unrelated customers(buyer/seller).Theorem 5 is used to avoid misconception exclusion issues from data trading organization.
Theorem 5.Our proposed scheme avoids any type of misconception exclusion.
Proof.ABE algorithm is used to confiscate misconceptivity of the customers during buying or selling and all the information will be provided to buyer and seller.For information providing,our platform use two sub-platforms known as a social network and trading market under ABE algorithm.To follow the planning and evaluation of the trading organization,Theorem 6 will apply on every entity to provide planning and evaluation for all trading activities.
Theorem 6.Our scheme provides accurate planning and evaluation.
Proof.The buyer and seller are the two entities of the trading market.To access the trading market in accurate manner they need some accurate planning and evaluation.Ourτ-access policy construction makes capable all the buyers and sellers of the trading market.In which it is able to access the trading market any time and to access the transactions for selling and buying.If the seller plan to sell the required transacted data then the market manager will provide and evaluate it(in case:if these data are not available in the trading market then it will be provided by the manager).
In the planning and evaluation phase the disconnectivity will be avoided and accessibility of any type of transactions will be provided.
6.2.6 Payment
For successful payment,we use Theorem 7.In which every seller or buyer make honest and it revokes dishonesty.
Theorem 7.Our scheme provides a successful payment.
Proof.ABE revoked dishonest buyer and seller,due to incomplete private data,in which ABE cannot be able to generatepk,encryptmand decryptc.Therefore,the access of dishonest customers automatically revoked by usingτ−access policy.The main role of this phase is to prevent dishonest buyers and sellers.
The example is E-banking using social networks like WeChat,Alipay payment etc.
6.2.7 Data trading demand
Data trading demand plays a vital role in the trading organization.Therefore,our proposed scheme having Theorem 8,in which the demand for data exceeds for users.
Theorem 8.Our scheme provides data trading demands.
Proof.Data trading demands is based on a social network,in which the seller and buyer will drop its requirement.According to its requirements,trading manager will provide the transactions data and give him/her access using ABE algorithm.
6.3 Attacks Prevention
In attacks prevention,all types of attacks need to prevented.The most important attacks such as active attack and passive attack need to prevent during the selling and buying from both sides(seller’s side and buyer’s side).Our ABE construction using the concept of encryption and decryption.In Algorithm 3,the required transacted messagemis encrypted by using his public and private keys attributes and get transacted ciphertexts.And in Algorithm 4,take the decrypted transaction cipher’s and generate the originality of the transacted messagem.Therefore,our ABE construction prevents all types of attacks under the DBDH hard problem.
6.3.1 Active attack
Our proposed scheme Theorem 9 is used to prevent an active attack.
Theorem 9.Our proposed ABE scheme provides active attacks prevention.
Proof.To provide all the access of the data from the seller to buyer or from buyer to seller,ABE based on DBDH algorithm which uses private,public and secret keys.Therefore,the hacker or attacker activity w.r.t to hacking or eavesdropping is prevented and it is unable to make changes in transaction data Eq.(8).
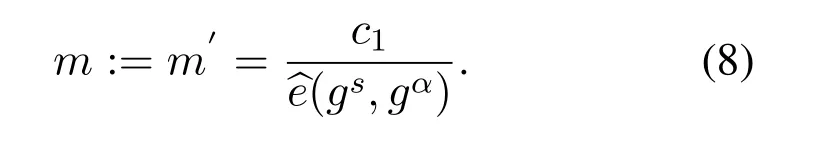
6.3.2 Passive attack
Our proposed scheme Theorem 10 is sued to prevent a passive attack.
Theorem 10.Our proposed ABE scheme provide passive attacks prevention.
Proof.In trading network,the prevention of passive attack is based on Eq.(9).
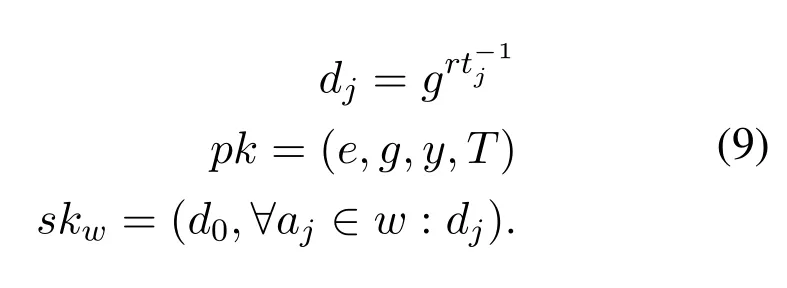
In passive attack,all the trading network is monitored by authorized users,and no opportunity to unauthorized(eavesdropper/hackers)to access the trading network due to ABE.In order to overcome this type of attacks powerful ABE algorithms is used to encrypt the transaction being transmitted using his/her own private,public and secret keys.
VII.PERFORMANCE EVALUATION
In evaluation,we compare our scheme with existing data sharing schemes[12,44–46],in terms of computations.The computational complexity is based on bilinear pairing on the group ofG0,G1,G2andZprespectively.Each attribute elements are selected fromG0,G1andZp.The required values of the groupG0,G1andZpare 44,124 and 24 bytes respectively.Our scheme transaction size in bytes is reasonable and it reduces the communication and computation overheads.The comparison analysis for total group elements size in bytes is given in Table 2.
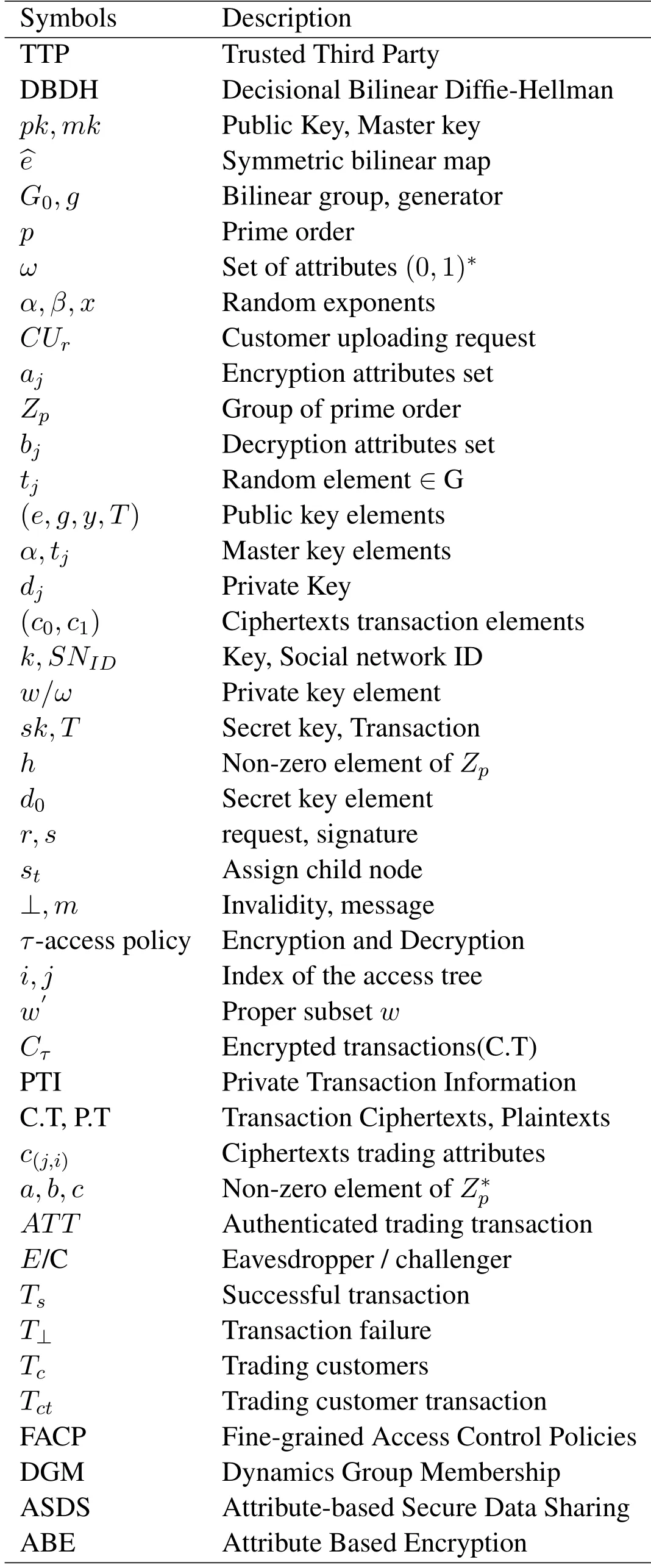
Table 1.Symbols and its description.
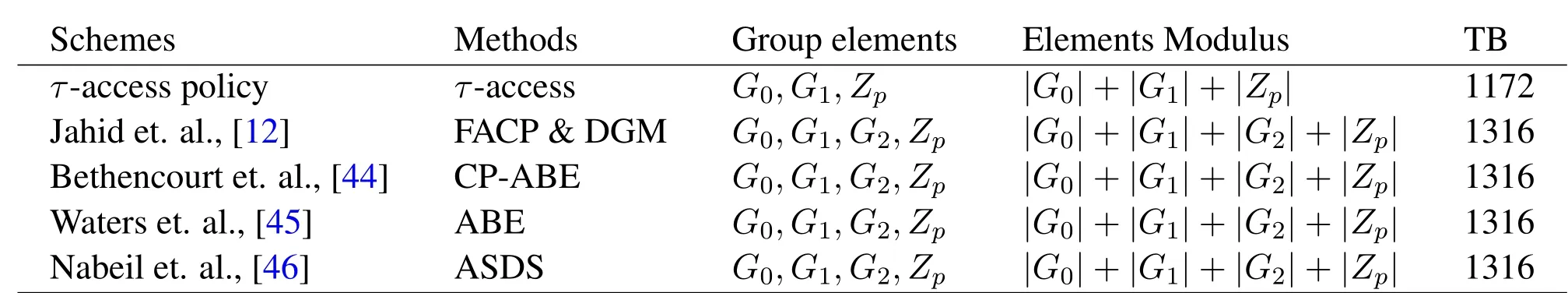
Table 2.Elements and its size in bytes.
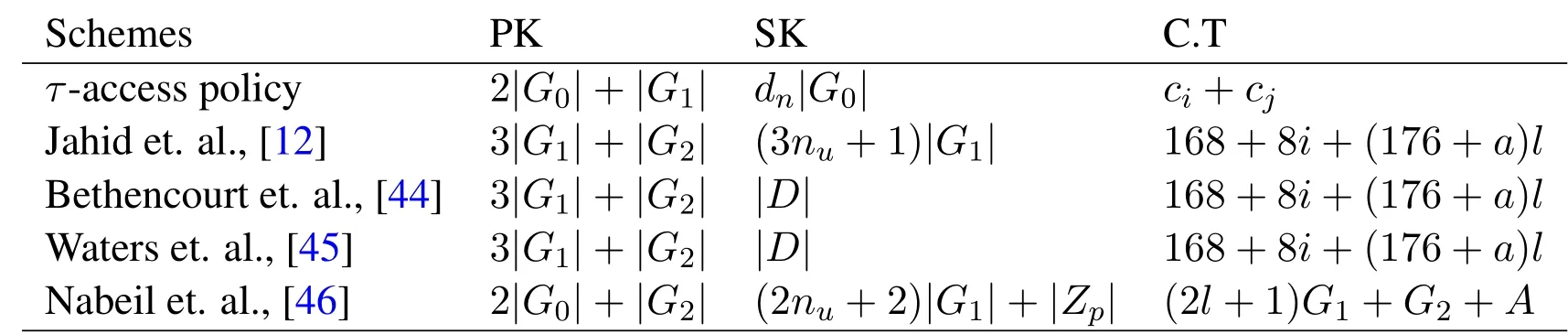
Table 3.Performance comparison.
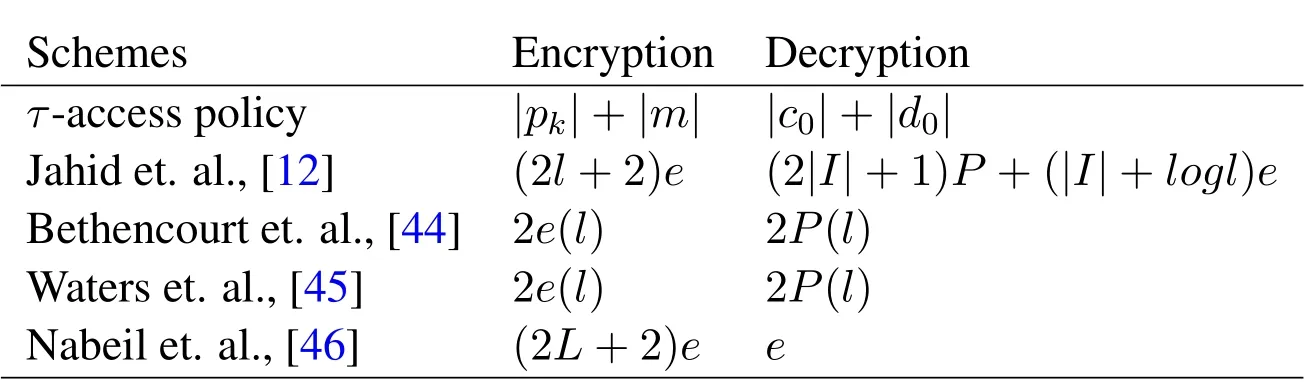
Table 4.Encryption and decryption comparison.
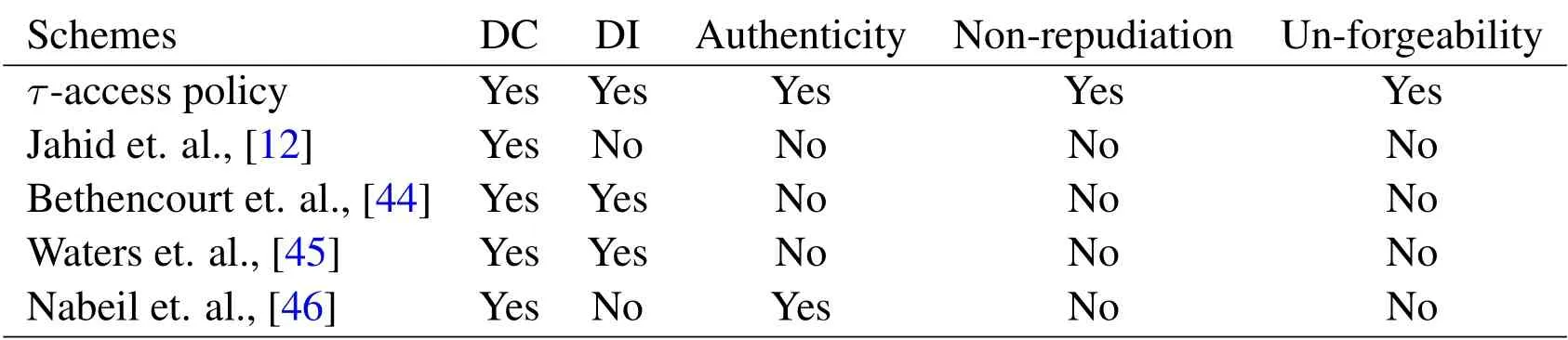
Table 5.Security properties comparison.
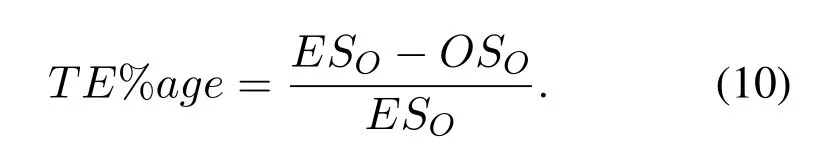
WhereTEstands for Transaction Efficiency and%agestand for percentage,ESOstands for existing scheme operation andOSOstands for our scheme operations.The efficiency of our proposed scheme in terms of total elements size is 77.73% and existing schemes efficiency is 75% which is calculated from Eq.(10).
VIII.SECURITY PROPERTIES
The security of our proposed scheme is based on DBDH[41].It provides strong security such as,data confidentiality,data integrity,authenticity,nonrepudiation,and unforgeability.
8.1 Data Confidentiality
For designing a secureτ−access policy scheme,we consider the case of malicious adversaries w.r.t confidentiality.The confidentiality property means that if an eavesdropper has some information about the original plaintext,he/she should not learn about the ciphertext.This security notion obliges the computational im-possibility to discriminate between two messages chosen by the eavesdropperE.
Initialization:EavesdropperEselect a set of encryption attributes,where(corresponds to the set of encryption attributes)to be used for encryptingC.Tas a set of attributes,whereω=0,1∗.NowsendtoC.
Setup:The challengerCrunτ−access policy encryption algorithm(Algorithm 3)and send public key elements(e,g,Y,T)toEand keep secret keyd0:
•For session generation eavesdropperEsend request for a queries(qi)
•EavesdropperEsendqitoτ−access policy key generation algorithm(Algorithm 2)and send the resulting secret keyd0to eavesdropperE.τ−access policy key generation does not satisfy the encryption attributes set,which remain constant data confidentiality property due to DBDH hard problem.
Definition 3.τ−access policy fulfills data confidentiality property if there is no eavesdropper that can succeed the security game of data confidentiality with non-negligible advantage.
8.2 Data Integrity
In our proposed scheme,TTP verify that the sending transaction messagemof the users is original or not.If eavesdropper change the transacted ciphertextsctoc′,som′will be received insteadm.So Eq.(5)is used to hold data integrity property and revoke intruder for such types of changes of transacted ciphertexts.
Initialization:EavesdropperEselect decryption attributesc′insteadc,to be used for decrypting the challengeC.Tas a set of ciphertexts attributesc0,1∈C.T,whereC.T=ci,j.Now the resulting originality of message by usingτ−access decryption algorithm(Algorithm 4)isτdec(skw,Cτ)=m′.So eavesdropperEgotm′instead ofm.So ourτ−access policy decryption algorithm fulfill data integrity property.
Setup:The challengerCrunτ−access policy decryption algorithm(Algorithm 4)and send secret key(skwto decryptCτ:
•For session generation EavesdropperEsend request for a queries(qi)
•EavesdropperEsendqitoτ−access policy decryption algorithm(Algorithm 4)and send the resulting secret keyskwto eavesdropperE.τ−access policy decryption algorithm does not satisfy the decryptionτdecon ciphertextsCτ,which remain constant data integrity property due to DBDH hard problem.
Definition 4.τ−access policy fulfills data integrity property if there is no eavesdropper that can succeed the security game of data integrity property.
8.3 Authenticity
In Algorithm 2,the private key computing from Eq.(11)is hard.Our scheme is used to maintain authenticity and revoke eavesdropper attacks.TTP generate a random numberα,and set private elements of the user accessible only to exact user(step 1&2 of Algorithm 2).

Definition 5.τ-access policy fulflils authenticity property if there is no eavesdropper that can succeed the security game of authenticity.
8.4 Non-repudiation
When dispute occur,TTP can determine the original signaturesof the users.To generate the correct signature of the user,it uses its own private key,then TTP easily judge the verification between the users and revoke any type of disputes.The compactness of Eq.(12)is based on bilinear pairing.

Definition 6.τ−access policy fulfills non-repudiation property if dispute occur,the user can not be able todeny.Eq.(12)revoke his/her deniability and nonrepudiation property is hold.
8.5 Un-forgeability
The originality of the user’s is based on its own private key.In Eq.(11),due to private key usage users cannot be able to forge.Therefore,the users cannot be able to forge and unforgeability property is hold.
Definition 7.τ−access policy fulfills unforgeability property.Due to Eq.(11)unforgeability property is hold and the user is not be able to forge.
IX.CONCLUSION
In this paper,we have leveraged the concept of theτ-access policy to design a social network privacypreserving scheme for data trading.The usage of social networks having a lack of security in data trading platforms.To maintain the security of data trading,we applied the ABE technique based on DBDH to secure the data trading network.The proposedτ-access policy scheme provides the best solution for the betterment of the data trading network in terms of security.Our proposedτ-access policy scheme provides security properties such as confidentiality protection,organization maintenance,social contract,customer deviant act,misconception exclusion,planning and evaluation,payment,and data trading demands.The efficiency of our scheme is 77.73% as compared to existing schemes and it is more suitable for data trading markets and trading strategies
X.OPEN DIRECTION
In the future,it is openly challenging for researchers to implement aτ-access policy for any type of trading organization using social network strategies.
- China Communications的其它文章
- Two-Timescale Online Learning of Joint User Association and Resource Scheduling in Dynamic Mobile EdgeComputing
- SHFuzz:A Hybrid Fuzzing Method Assisted by Static Analysis for Binary Programs
- SecIngress:An API Gateway Framework to Secure Cloud Applications Based on N-Variant System
- Generative Trapdoors for Public Key Cryptography Based on Automatic Entropy Optimization
- A Safe and Reliable Heterogeneous Controller Deployment Approach in SDN
- Distributed Asynchronous Learning for Multipath Data Transmission Based on P-DDQN

