Secrecy-Enhancing Design for Two-Way Energy Harvesting Cooperative Networks with Full-Duplex Relay Jamming
Siyang Xu,Xin Song,*,Yiming Gao,Suyuan Li,Jing Cao,3,Zhigang Xie
1 School of Computer Science and Engineering,Northeastern University,Shenyang 110819,China
2 Engineering Optimization and Smart Antenna Institute,Northeastern University at Qinhuangdao,Qinhuangdao 066004,China
3 School of Mathematics and Information Science and Technology,Hebei Normal University of Science and Technology,Qinhuangdao 066004,China
Abstract:To guarantee secure information transmission within two sources,a full-duplex(FD)relay jamming scheme for two-way energy harvesting(EH)cooperative networks is proposed,in which the relay can achieve simultaneous information reception and jamming transmission.The EH relay node scavenges energy from two source signals,and then,uses the harvested energy for information relaying and jamming transmission by the power splitting(PS)protocol.Considering multiple eavesdroppers,the nonconvex optimization for maximizing the smaller bidirectional secrecy rates is formulated by jointly optimizing the power allocation and PS factor.Furthermore,an iterative algorithm based on successive convex approximation and alternate search method is proposed to solve this non-convexity.Simulation results verify the proposed iterative algorithm and show that the proposed jamming scheme can achieve substantial performance gain than other conventional schemes.
Keywords:physical layer security;two-way EH cooperative networks;FD relay jamming;minimum guaranteed secrecy rate
I.INTRODUCTION
Owing to the abilities to achieve high throughput and long-distance information transmission,wireless cooperative technology has been the focus to meet the performance requirements in the industrial and residential applications.Typically,the downlink communication between the source and remote destination with the help of a relay node is named as one-way relay networks[1].However,the bidirectional communication process requires four-time slots due to the half-duplex(HD)operation.To effectively mitigate the loss of spectral efficiency,two-way relay networks based on the physical network coding are proposed to reduce four-time slots to two-time slots[2,3].
Due to the broadcasting characteristics of wireless channels,the risk of information leakage will greatly increase.As an alternate to compensate for the complex encryption and decryption technology,physical layer security is recognized as a novel security paradigm by using the physical characteristics of wireless channels[4].Secrecy capacity is defined as the difference between the legal link and wiretapping link[5].To guarantee a positive secrecy capacity,the friendly jammer scheme can be implemented by the nodes of the networks to degrade the wiretapping link.With an external eavesdropper,the relay selection and jammer selection scheme is investigated to enhance the security performance for the conventional two-way relay networks[6].Following the study[6],the power allocation algorithm based on Stackelberggame is proposed to tradeoff between the friendly jammers and two sources[7].For the untrusted two-way relay networks,the power allocation problem is also investigated under the without jamming,friendly jamming,and Gaussian noise jamming scenarios[8,9].However,the friendly jammer schemes in[6-9]will degrade the received signal-to-noise ratio(SNR)of the legitimate user.And the jamming signals need to be shared beforehand to the legal nodes[10].With the development of SIC technology,the self-interference(SI)generated by FD operation can be eliminated to the noise level or even negligible,which promotes the development and application of FD technology[11-13].To ensure the secure communication of the nonorthogonal multiple access users,the FD relay transmits the jamming signal to the eavesdropper while receiving confidential messages in the one-way relay networks[14,15].In[16],the power allocation problem of the legitimate and jamming signals is investigated with different knowledge of the eavesdropping channel state information(CSI).Subsequently,the FD relay jamming is also implemented in downlink cognitive radio(CR)networks to secure the primary transmission[17].For the conventional two-way relay networks,the security of information exchange can be guaranteed by the FD relay jamming scheme in[18].However,the jamming power and relaying power come from the relay’s battery,which will exacerbate the power constraint problem of the relay node.
Normally,the relay nodes in wireless networks are powered by their batteries,which is hard to maintain persistent work.To keep the sustainable and longlasting power supply of the relay node,EH from radio frequency(RF)signals is proposed[19].Time switching(TS)and PS are two major EH architectures to perform information reception and EH[20,21].Furthermore,a non-linear EH model based on the logistic(sigmoidal)function is proposed to characterize the non-linearity of the diodes,inductors and capacitors[22,23].To reduce the computational complexity caused by the logistic function,the piecewise linear EH model is proposed[24].Yet,this EH technology introduces a paradigm shift in system and resource allocation algorithm design.Using the performance metrics of outage probability and max-min bidirectional information rate,joint power allocation and relay selection schemes are redesigned for TS or PS twoway relay networks[25,26].In[27],a hybrid relaying scheme that alters the relaying strategy depending on transmission power is proposed to maximize the sum throughput with causal energy arrival.
Recently,some works have considered both physical layer security and EH for two-way networks to satisfy the requirements of security,spectral efficiency,and energy efficiency.Introducing EH technology to provide the relaying power of the two-way relay node and friendly jammer is implemented to degrade the received SNR at the untrusted relay node[28-30].In[28,29],the power outage probability and closed-form lower bound expressions are formulated in TS twoway relay networks.In[30],variable and constant power transmission schemes at the jammer and relay are considered.With the total power constraint,the power allocation of two sources and jammer is optimized for PS two-way relay networks[31].In the presence of external eavesdroppers,the secure relay beamforming optimization is formulated to maximize the achievable sum-secrecy rate with transmit power constraint and EH constraint[32].In[33],the adaptive TS and PS schemes are proposed to maximize the secrecy capacity.Furthermore,the closed-form expression in terms of the eavesdropping probability when the main and wiretapping links experience independentκ-μshadowed fading is formulated[34].However,the non-jamming schemes in[32-34]cannot always guarantee secure decoding by the legitimate nodes.To cope with this problem,the friendly jammer is applied to PS or TS two-way networks,in which the jamming signal is transmitted in the multiple-access or broadcast phase[35,36].
Despite these advances in[32-36],there is still a need for research on constructing a novel jamming transmission scheme suitable for EH two-way relay networks to deal with the energy scarcity of the relay and secure transmission within two sources.For the friendly jammer scheme in[6-9,35,36],the legal receivers must be aware of the jamming signal in advance and the external jammers need to consume extra energy.With this mind,we propose secure two-way relay networks using FD relay jamming to remedy the shortcomings of the friendly jammer scheme,in which the relay nodes do not need to know the jamming signals in advance.Different from the FD relay jamming scheme in[14-18],both the relaying power and jamming power of the relay node can be harvested from two sources by the EH technology,which solves the power constraint of the relay node.Due to the introduction of EH technology and considering multiple eavesdroppers,the minimum guaranteed secrecy rate optimization and the corresponding solution algorithm need to be redesigned.To the best of our knowledge,the integration of FD relay assisted jamming,EH technology and joint optimization of power allocation and PS factor to achieve secure two-way relay communication have not been investigated.The main contributions of this paper can be summarized as follows.
In this paper,the secure EH two-way relay networks using FD relay jamming is proposed in the presence of multiple external eavesdroppers,in which the FD relay can harvest energy from two sources and transmit jamming simultaneously.The transmission power of relaying and jamming can be harvested from EH,which solves the power constraint problem of the relay node.Moreover,the non-convex optimization for maximizing the minimum guaranteed secrecy rate is formulated to optimize the power allocation and PS factor,which can be solved by the proposed iterative algorithm.Simulation results demonstrate that the proposed algorithm has fast convergence rate and lower complexity.Besides,we compare the proposed scheme with other conventional schemes to demonstrate better output performance.
The remainder of this paper is organized as follows.The system model of the proposed secure EH two-way relay networks using FD relay jamming is presented in Section II.In Section III,an iterative algorithm is proposed to solve the formulated non-convex optimization.Simulation results are provided to prove the effectiveness of the proposed scheme in Section IV.Section V concludes this paper.
II.SYSTEM MODEL
In figure 1,the two-way EH cooperative networks consist of two sources(AandB),an amplify-andforward(AF)relayRandKeavesdroppers(Ekfork∈{1,...,K}).The eavesdroppers and two source nodes are operated in HD mode and equipped with a single antenna,while the relay is equipped with dual isolated antennas to achieve FD operation.Keavesdroppers are legitimate users whereas their services differ from two sources.Therefore,the perfect CSI of all channels is available.We assume that there is no direct link between two sources due to severe shadow fading.In addition,all channels are statistically independent and quasi-static flat Rayleigh fading.
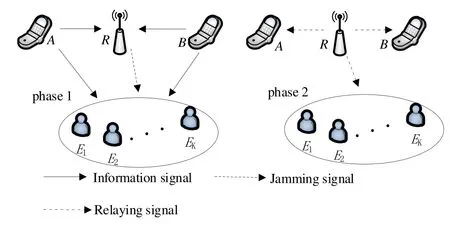
Figure 1.System model of the proposed two-way EH cooperative networks using FD jamming relay.
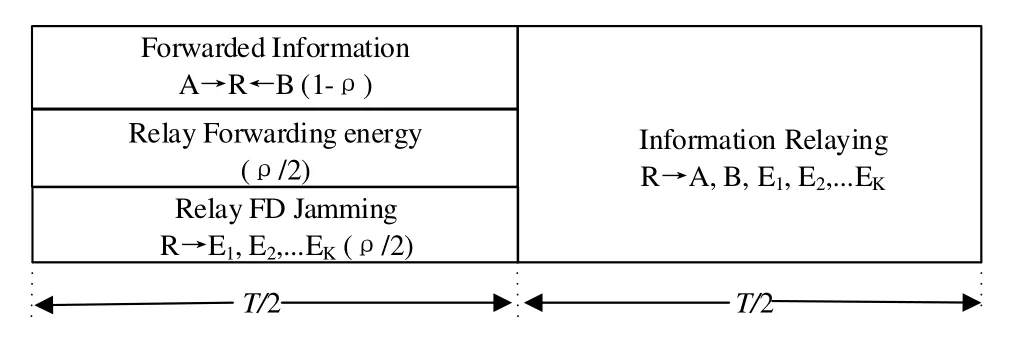
Figure 2.The entire transmission process of the proposed scheme.
As shown in figure 2,the total transmission process is divided into two equal phases.In the first phase durationT/2,the relay is operated in FD mode to achieve simultaneous EH and jamming transmission.Based on the PS protocol,the received signal is decomposed into the energy partρand forwarded information part(1-ρ).Particularly,the harvested energy is evenly allocated for information relaying and jamming transmission.Meanwhile,the eavesdroppers will also receive two source signals,while the jamming signal can degrade the reception of confidential signals.Based on propagation-domain interference suppression,analogdomain interference cancellation,and digital-domain interference cancellation jointly or separately,the SI generated by FD operation can be reduced to the noise level,which can be ignored[11-13].Therefore,we assume that there is a perfect SIC at the relay[18].
In the second phase durationT/2,the relay broadcasts the superimposed signal after amplifying.Each source tries to decode the information signal transmitted by the other source.And the eavesdroppers will also receive the relaying signal and attempt to overhear it,but the decoding of each signal is hindered by the other source’s signal.In other words,the confidential signal of each source plays a role of the jamming in the recovery of the other source’s signal.However,two sources can remove their own information signal transmitted in the previous phase.
During the first phase,the received signal utilized for information processing can be given by
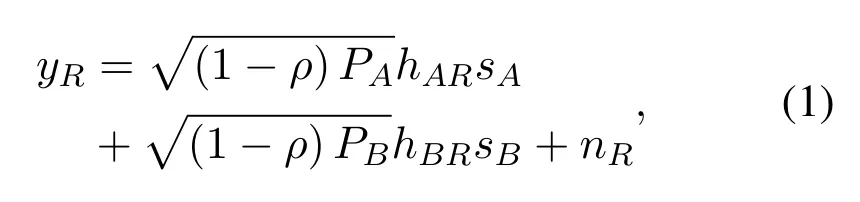
wherePAandPBare the transmission power of two sources;ρ∈(0,1)is the PS factor;hARandhBRdenote the channel gain from two sources to the relay;sAandsBrepresent the information-bearing symbols with unit power;nRdenotes the additive white Gaussian noise(AWGN)of the relay with zero-mean and varianceσ2.The total harvested energy is
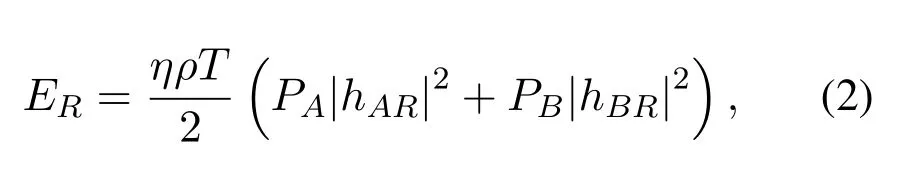
whereη∈(0,1)is the efficiency of energy conversion.Moreover,the harvested energy is divided into two equal partsERelaying=EJamming=ER/2,which are used for information relaying and jamming transmission.And the received signal at the eavesdropperEkduring the first phase can be given by
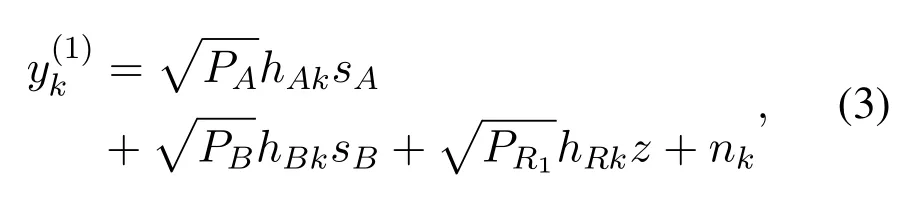
wherehAk,hBkandhRkdenote the channel gain from two sources and relay to thek-th eavesdropper;zrepresents the jamming signal with unit power;PR1=is the jamming power of the relay in the first phase;nkis the AWGN at thek-th eavesdropper.Based on expression Eq(3),the SNR atEkfor detectingsiduring the first phase can be given by
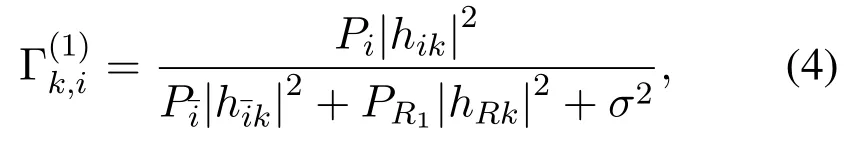
whereThe achievable wiretapping rate atEkduring the first phase isIn the second phase,the relay amplifies and forwards the received signals to two sources with the remaining harvested energy.Thus,the transmitted signal from the relay can be given by
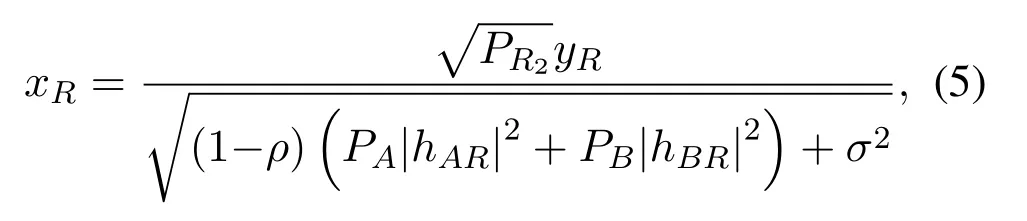
whereis the relaying power in the second phase.Due to channel reciprocity,we assume thathAR=hRAandhBR=hRB[19].Therefore,the received signal at the sourcesAandBare
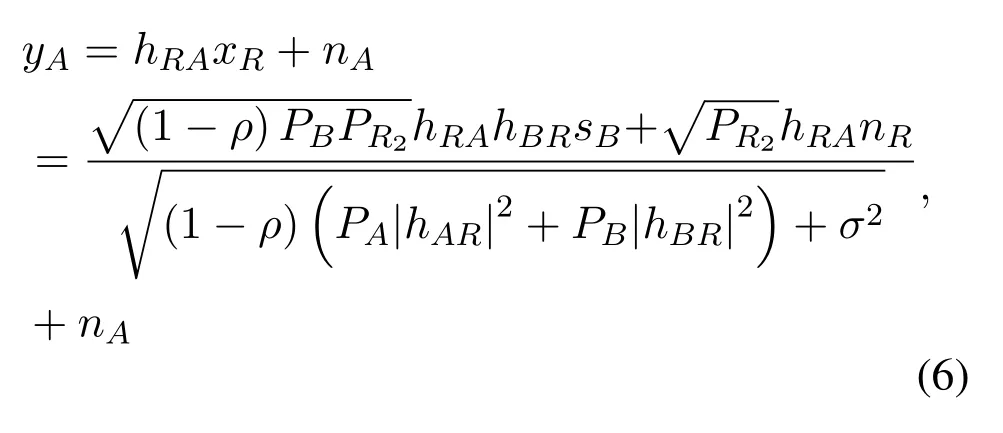
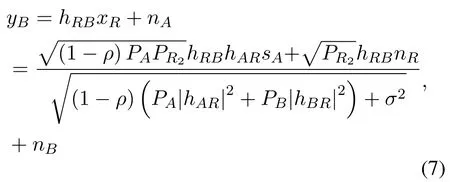
in which each source can eliminate the part related to its own signal using the SIC.The instantaneous SNR at source for detectingsican be given by
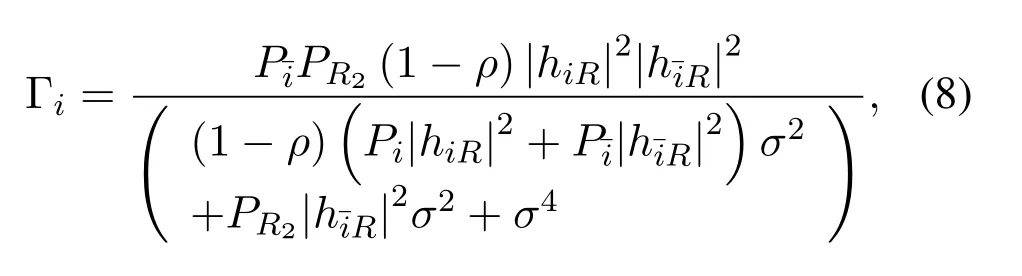
And the achievable rates at sourceiisRi=
On the other hand,the received signal atEkcan be expressed as
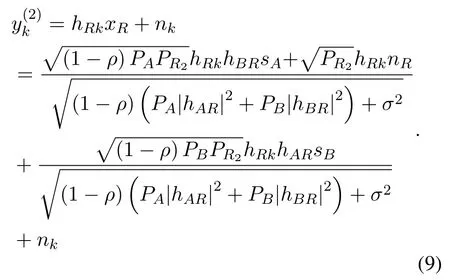
And the SNR for detectingsidestined for sourceiin the second phase can be given by
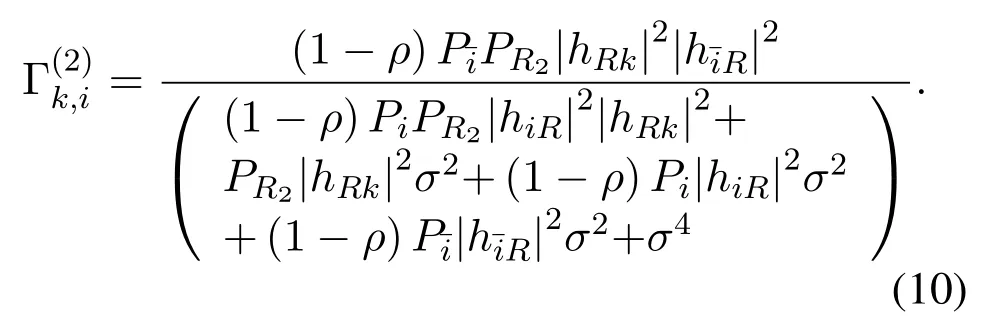
The achievable wiretapping rate atEkduring the second phase isAnd the total wiretapping rate atEkis calculated as the summation ofwhich can be given byRk,i=
III.PROBLEM FORMULATION AND PROPOSED ITERATIVE ALGORITHM
With multiple eavesdroppers,we first formulate the minimum guaranteed secrecy rate optimization,in which the main challenge of the optimization is the non-convexity due to the multiplication of variables.To circumvent this obstacle,the primal problem can be decomposed into two sub-problems.However,the domain of the two sub-problems still non-convex,which can be solved by utilizing successive convex approximation.Subsequently,the alternate search method is adopted to obtain final solutions after a finite number of iterations.
3.1 Minimum Guaranteed Secrecy Rate Problem Formulation
WhenEkoverhears the source signalsi,the secrecy rate for the relay transmissioni→R→can be given bywhere[x]+=max(0,x).Since there areKwiretapping links for each source,the minimum guaranteed secrecy rate for both sources can be defined as
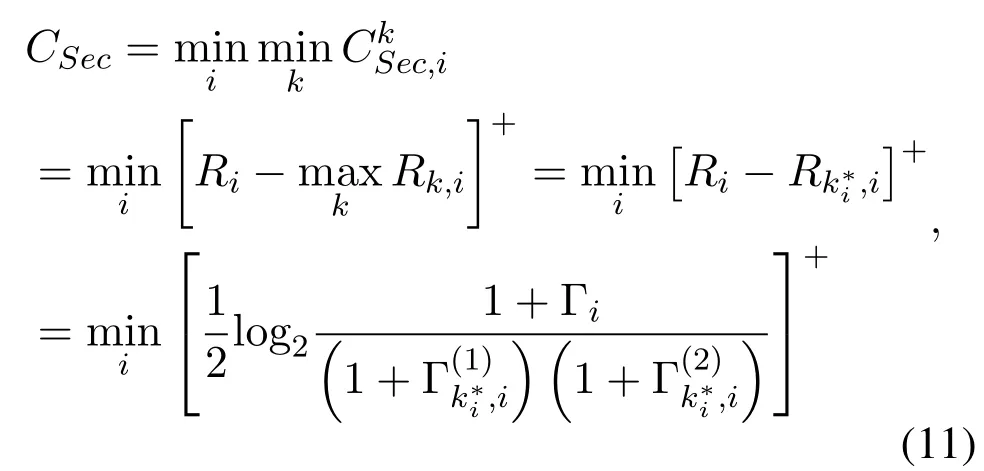
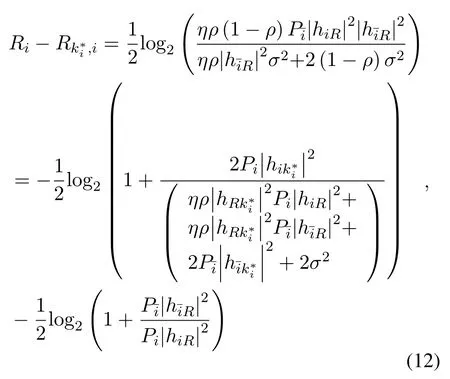
whereAlternatively,the eavesdropperis the one with the largest wiretapping rate for decoding source signalsi.SubstitutingPR1andPR2into Eq(4),Eq(8)and Eq(10),the expression of specificin high SNR can be approximated as
The optimization for maximizing the minimum guaranteed secrecy rate can be formulated as
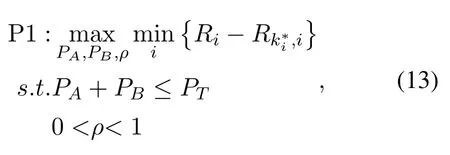
wherePTis the total peak transmission power andi∈{A,B}.It can be seen that the formulated optimization(13)is non-convex.To solve this problem,we first introduce an auxiliary variabletand rewrite the optimization as
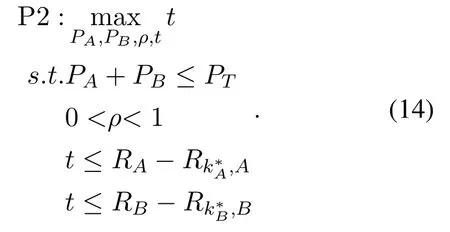
It can be seen that we have transformed the objective function into a linear function.Since the multiplication of the transmission power and PS factor,constraintst≤RA-Rk*A,Aandt≤RB-Rk*B,Bare non-convex.Thus,we decompose(14)into two subproblems with the fixed PS factor or the fixed power allocation.
3.2 Sub-Problem of Power Allocation
In this sub-section,we optimize the power allocation with the fixed PS factor.The successive convex approximation is utilized to convert the non-convex domain into convex.
The standard form of the difference of convex functions(DC)programming problem iswhereXis a convex set;f1(x)andf2(x)are two continuous,convex or quasi-convex functions.Based on[37],the approximate problem can be given by
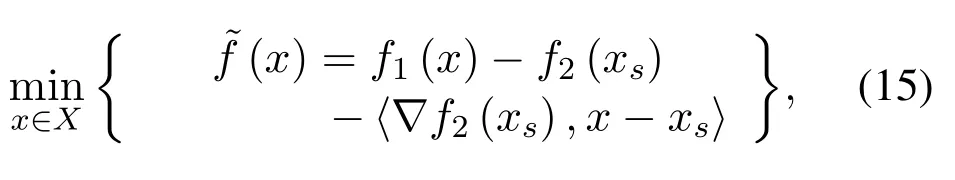
wherexsis the optimal solution of(s-1)-th iteration used fors-th iteration and∇f2(xs)is the gradient off2(x)whenx=xs.With a given initialization valuex0,a sequence of trial solutionsxsis generated by iteratively solving(15).
Based on DC programming,the optimization(14)with the fixed PS factor can be re-express as
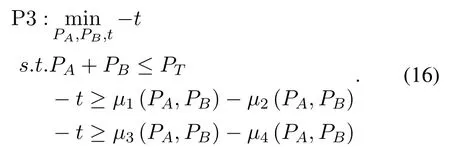
whereμ1(PA,PB)=-μ3(PA,PB)=(A1PAPB(B1PA+C1PB)),μ4(PA,PB)=-A=ηρ(1-ρ)|hAR|4|hBR|2/B=C=A1=B1=andC1=Since the Hessian Matrices ofμ1(PA,PB),μ2(PA,PB),μ3(PA,PB)andμ4(PA,PB)are positive semidefinite,the decomposed four functions are convex.Using the successive convex approximation,the optimization(16)can be transformed into
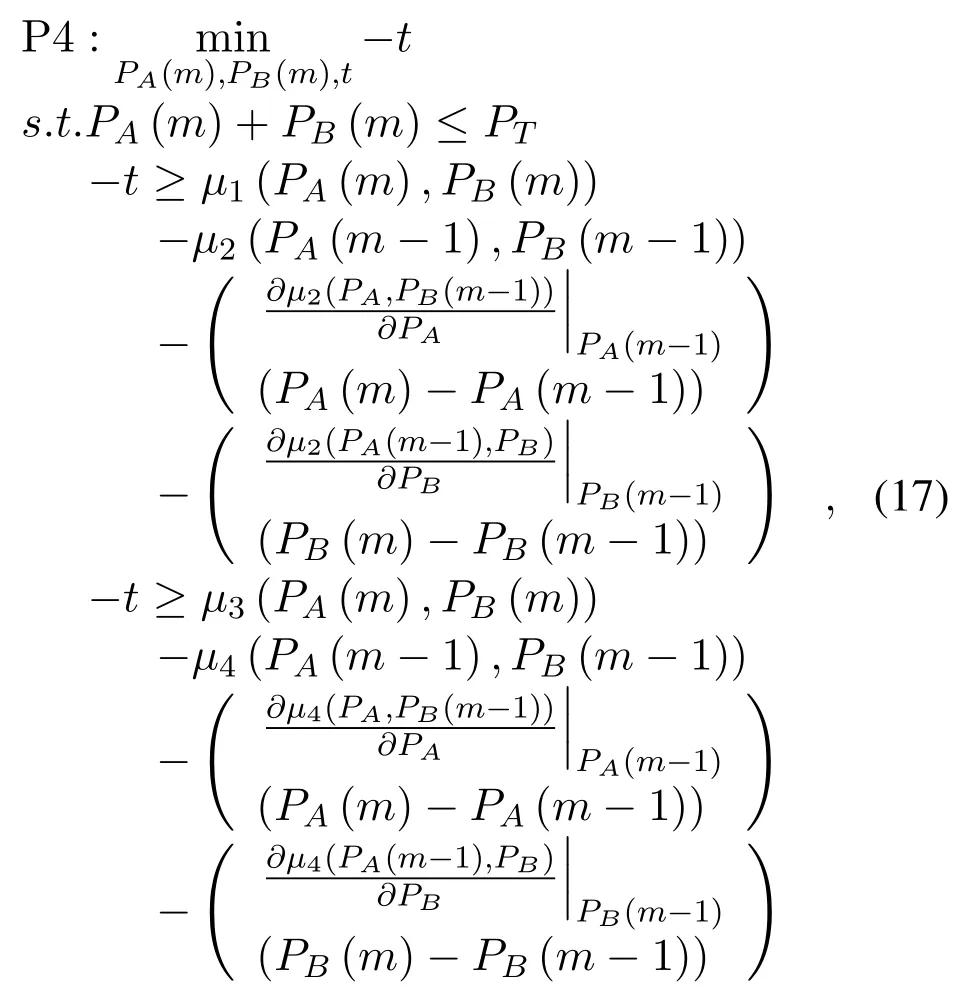
wheremis the iteration index.Andare the gradients ofμ2(PA,PB)andμ4(PA,PB).Currently,optimization(17)can be solved by convex programming.
3.3 Sub-Problem of PS Factor
With the fixed transmission power,we re-express the optimization(14)as
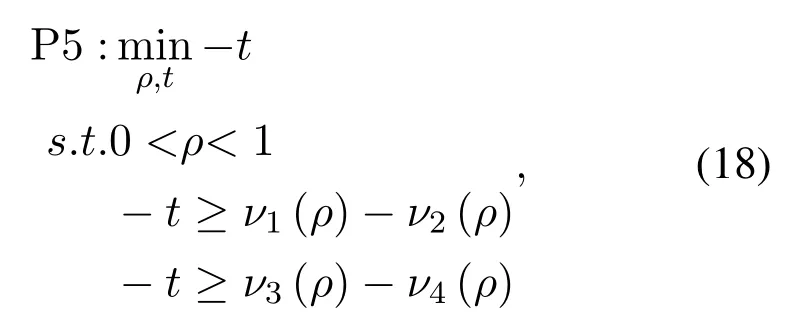
whereν1(ρ)=ν3(ρ)=ν4(ρ)=D1=ηPA|hAR|2|hBR|2/σ2,E=andG=It is easy to prove that the functions ofν1(ρ),ν2(ρ),ν3(ρ)andν4(ρ)are convex since the second derivatives are greater than zero.Based on Eq(15),the optimization(18)can be transformed into a convex problem by replacingν2(ρ)andν4(ρ)with their first-order Taylor expansion,in which the solution of the PS factor can be obtained by using convex programming.
3.4 Alternate Search Method for Final Solutions
The core of the alternate search method is that only one of the power allocation or PS factor can be optimized in each iteration,while the other is fixed.In other words,the final solutions of the joint optimization(14)can be obtained by solving the following twolevel optimization problem
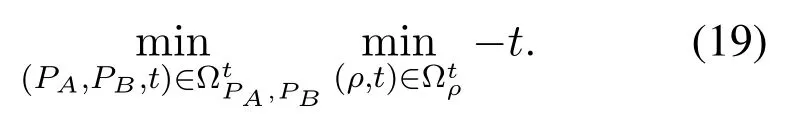
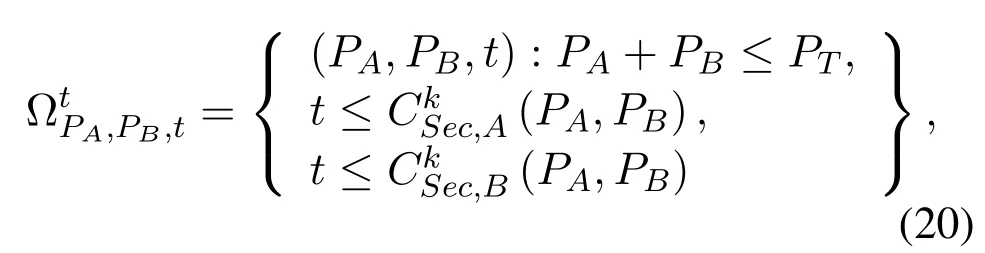
with the fixedρ.Moreover,is defined as
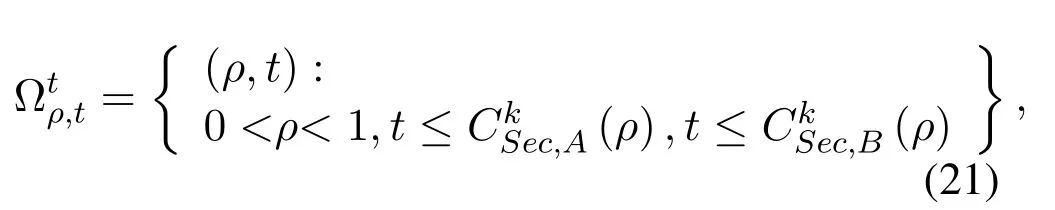
with the fixedPAandPB.Through the above subsection,both two non-convex domainsandcan be converted into two convex domains by using successive convex approximation.And two-level optimizations also changes from non-convex to convex.Thus,the alternate search method will iterate to approximate final solutions.The overall process of the proposed algorithm is shown in Algorithm 1.
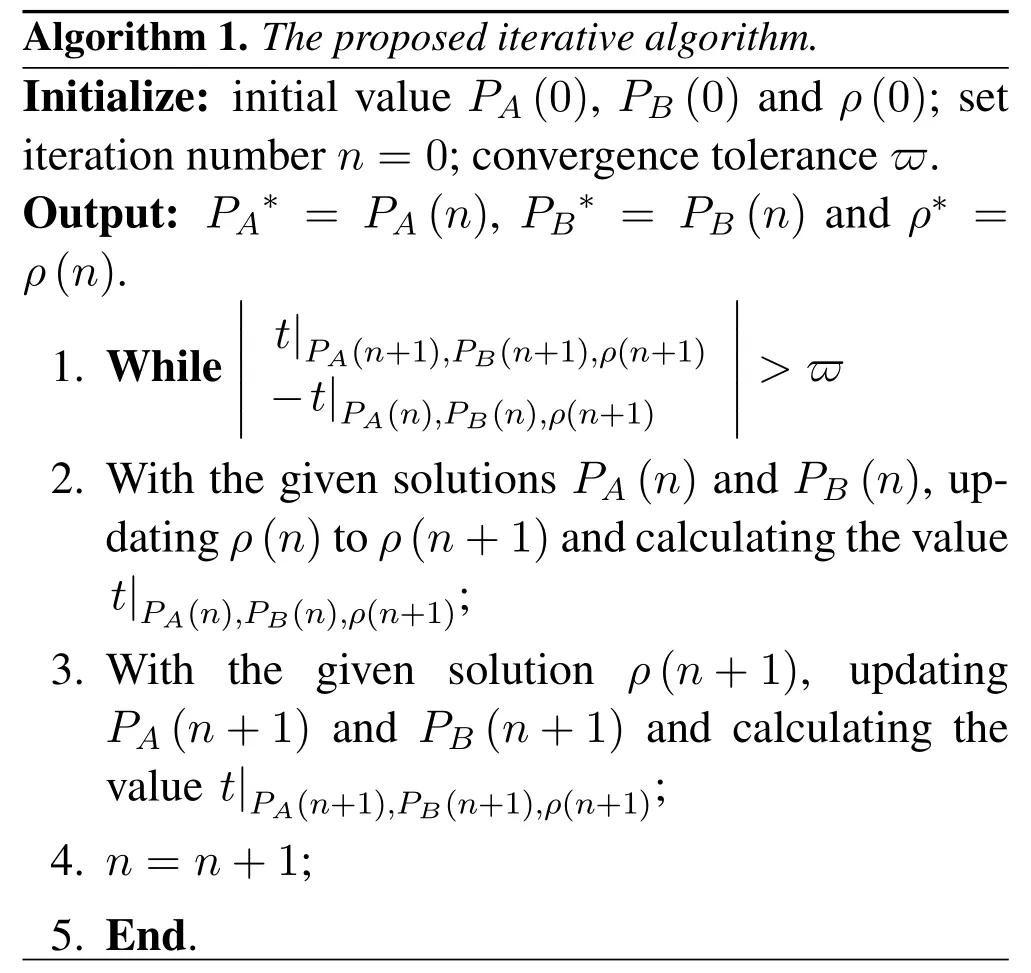
Algorithm 1.The proposed iterative algorithm.Initialize:initial value PA(0),PB(0)and ρ(0);set iteration number n=0;convergence tolerance ϖ.Output:PA*=PA(n),PB*=PB(n)and ρ*=ρ(n).1.Whileimages/BZ_289_1493_1778_1508_1824.pngimages/BZ_289_1493_1805_1508_1851.pngimages/BZ_289_1493_1833_1508_1878.pngimages/BZ_289_1493_1860_1508_1906.pngimages/BZ_289_1493_1887_1508_1933.pngt|PA(n+1),PB(n+1),ρ(n+1)-t|PA(n),PB(n),ρ(n+1)images/BZ_289_1989_1778_2004_1824.pngimages/BZ_289_1989_1805_2004_1851.pngimages/BZ_289_1989_1833_2004_1878.pngimages/BZ_289_1989_1860_2004_1906.pngimages/BZ_289_1989_1887_2004_1933.png>ϖ 2.With the given solutions PA(n)and PB(n),updating ρ(n)to ρ(n+1)and calculating the value t|PA(n),PB(n),ρ(n+1);3.With the given solution ρ(n+1),updating PA(n+1)and PB(n+1)and calculating the value t|PA(n+1),PB(n+1),ρ(n+1);4.n=n+1;5.End.
3.5 Computational Complexity Analysis
According to the preceding subsections,the proposed iterative algorithm is a nested structure of the alternate search method,successive convex approximation and convex programming.Therefore,the computational complexity for two convex sub-problems can be computed aswherel1andl2are the number of the inequality constraints of two convex sub-problems[38].For the outer loop of the alternate search method and successive convex approximation,the corresponding iteration numbers arenϖ,mδandjϑwhen the convergence tolerances are achieved.Thus,the overall computational complexity can be roughly estimated by
IV.SIMULATION RESULTS
In this section,simulation results are provided to prove the convergence of the proposed algorithm and the superiority of the FD relay jamming scheme.For the position of the nodes,two sources and relay are placed on a horizontal line,while the eavesdroppers are symmetrically placed on both sides of this line with the interval of 3m[39].The channel power gains between any two nodes(p,q)∈[A,B,R,Ek]fork∈{1,...,K}are modeled as|hpq|2=whereEk,dpq,βand|fpq|2denote the eavesdropper located in line with two sources,the physical distance between two nodespandq,path-loss exponent and fading coefficient.Here,|fpq|2is an exponential random variable with meanλpq.And we setλpq=1 for wireless channels andβ=2.5.The other default simulation parameters are set as follows:energy conversion efficiencyη=0.8,the distance between two sourcesdAB=100m the number of eavesdroppersK=10,the distance between sourceBandKth eavesdropperdBEk=30m,maximum transmission powerPT=30dBm,and noise power densityσ2=-100dBm.
With different numbers of eavesdroppersK=5,K=10 andK=15,the convergence behavior and achievable secrecy performance of the proposed algorithm can be observed in Fig.3.The solutions of the optimal algorithm are obtained by exhaustive search method.We set the search step of the exhaustive search at 10-4,which leads to a great amount of calculation.For a fair comparison,the stopping criterion of the proposed algorithm is also predefined asδ=ϑ=ϖ=10-4.Furthermore,the distances ofdARanddBRare fixed at 50m.It can be seen that the achievable secrecy rate of the proposed algorithm only has a small performance loss compared with the optimal algorithm.However,the proposed algorithm can quickly converge within 16 iterations.Besides,a larger number of eavesdroppers will degrade the minimum guaranteed secrecy rate.This is because the eavesdropping channels have a greater chance of becoming stronger.
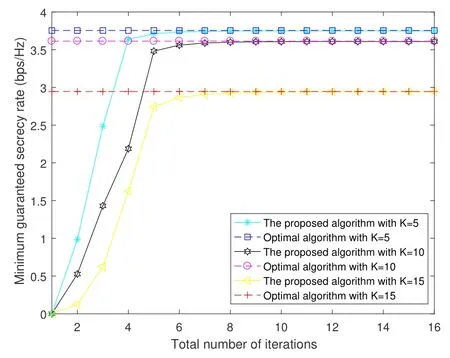
Figure 3.Comparison of the optimal algorithm and proposed algorithm versus the number of iterations.
In figure 4,we investigate the influence of the pathloss exponent anddARon the minimum guaranteed secrecy rate.The distancedABis fixed at 100m,while the relay can move within sourceAand sourceBfrom 40m to 80m.As expected,the performance difference between the proposed algorithm and optimal algorithm is only 0.00315bps/Hz whendAR=60m andβ=2.3.With the varyingdAR,the minimum guaranteed secrecy rate of the proposed scheme tends to increase first and then decrease.And there is an optimal relay position that maximizes the minimum guaranteed secrecy rate.Moreover,the minimum guaranteed secrecy rate with different path-loss exponent can be maximized to 6.213bps/z whendAR=70m andβ=2.3.The minimum guaranteed secrecy rate is decreasing when the path-loss exponent increases.It shows that the deterioration of channel power gains will cause a reduction in the secrecy rate.
Figure 5 plots the comparison of the proposed scheme and other conventional schemes with varying energy conversion efficiency.The conventional schemes are equal power allocation with optimal PS factor,optimal power allocation with fixed PS factorρ=0.5,and equal power allocation with fixed PS factorρ=0.5.No matter how the energy conversion efficiency changes,the proposed scheme still has a nearoptimal solution compared with the optimal algorithm.The secrecy rates of the five curves have the same upward trend.It indicates that more energy will be harvested for jamming and relaying with the larger energy conversion efficiency.And the proposed scheme has the best secrecy performance compared with the other three basic resource allocation schemes.
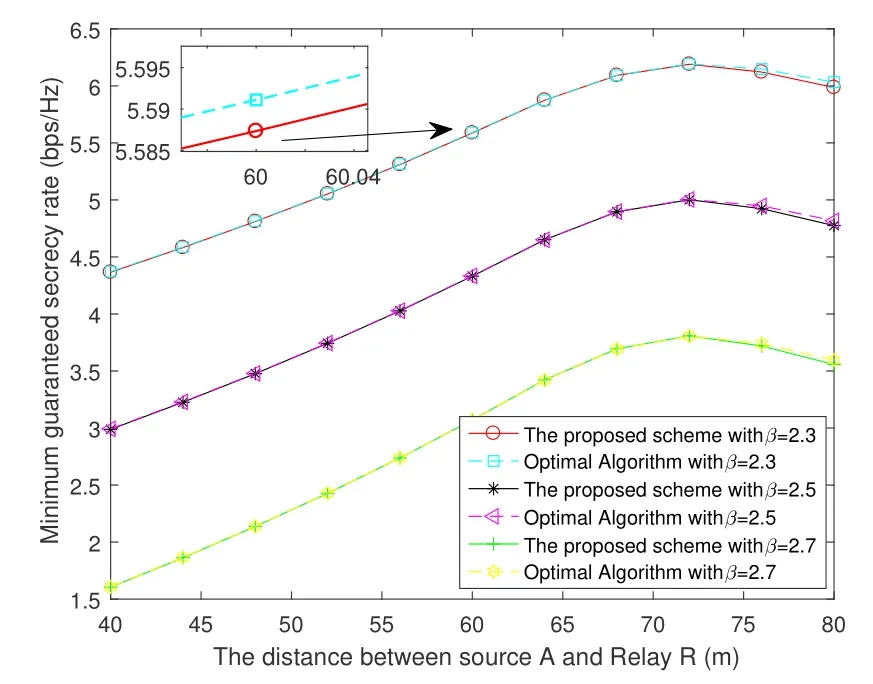
Figure 4.Comparison of the optimal algorithm and proposed algorithm with varying dAR.
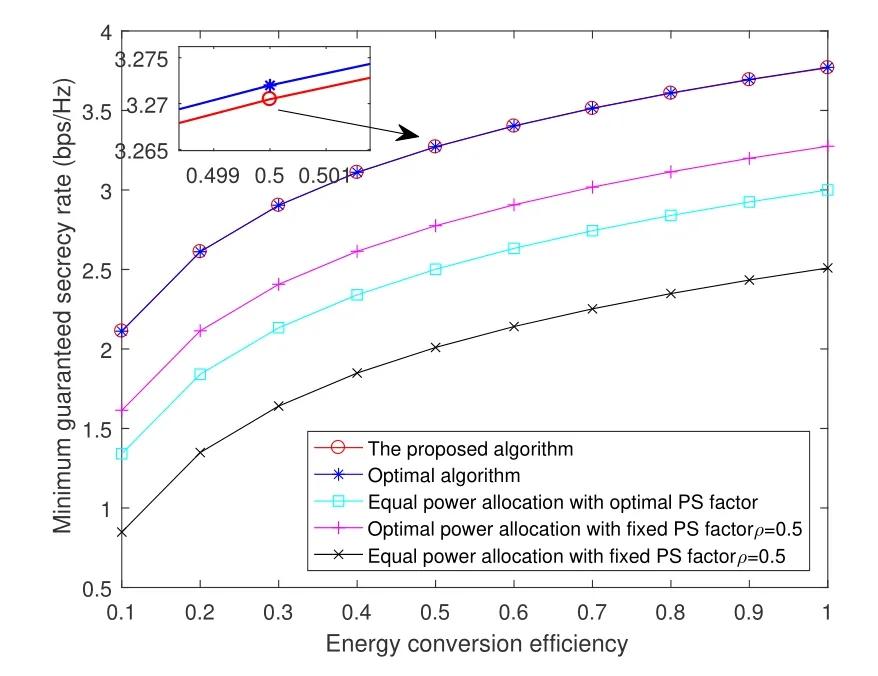
Figure 5.Comparison of the proposed scheme and conventional schemes with varying energy conversion efficiency.
Comparing with the three basic resource allocation schemes,figure 6 depicts the minimum guaranteed secrecy rate versus the distance between two sources.The relay is always placed in the middle location of the two source nodes,wheredABis varied from 80m to 120m.One can see that the proposed resource scheme also outperforms that of the other three schemes.With the increase ofdAB,the achievable secrecy rates of the five curves are decreasing.From the perspective of channel quality,the quality of confidential information at two sources and eavesdroppers both will deteriorate.However,the overall trend of the secrecy rate is declining,which indicates that the largerdABhas a more negative impact on the legal reception.
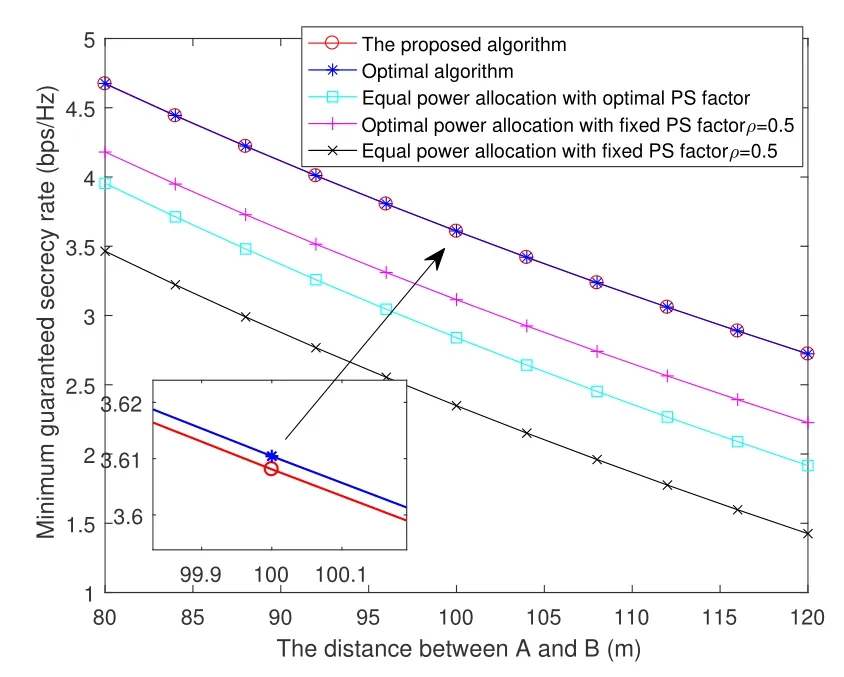
Figure 6.Comparison of the optimal algorithm and proposed algorithm with varying dAR.
The achievable minimum guaranteed secrecy rates of the six schemes versus different system parameters are shown in figure 7 and figure 8,respectively.The adaptive PS and TS two-way EH relay schemes are proposed in[33].However,there is no introduction of jamming to improve the minimum guaranteed secrecy rate of the two-way EH relay networks.For the friendly jammer schemes,an external jammer can transmit jamming to the eavesdroppers in the multiple access phase and broadcast phase in[35]and[36].
From figure 7,it is observed that the proposed scheme outperforms that of the other five schemes versus the total transmission power.AsPTincreases,the relay can harvest more energy.On the other hand,two sources can receive a stronger signal from the other source,and the power of jamming will also increase.In consequence,the secrecy rates of six curves are improving with the increasePT.From four schemes in[33]and[36],the PS schemes are better than TS schemes.This is because TS schemes have a longer vulnerable time for eavesdropping compared with PS schemes.In other words,the eavesdroppers can over the confidential signal from two sources in the first phaseT/2 for PS protocol,while(1+α)T/2 for TS protocol.Furthermore,the jamming transmission scheme in the broadcast phase[35]cannot significantly improve the minimum guaranteed secrecy rate,which proves that the transmission of jamming in the multiple-access phase is more effective.
The minimum guaranteed secrecy rates of the six schemes over different locations of eavesdroppers are shown in figure 8,wheredABis fixed at 100m.AsdBEkincreases,the channel quality of the eavesdropping link decreases,which leads to an increasing in the secrecy rate.However,the proposed scheme can always achieve the highest secrecy rate,which is similar to the simulation result in figure 7.WhendBEkis greater than 28m,the friendly jammer scheme in[35]begins to show its superiority compared with the without jamming schemes in[33].Moreover,the TS-TWR without jamming scheme in[33]has the lowest minimum guaranteed secrecy rate.
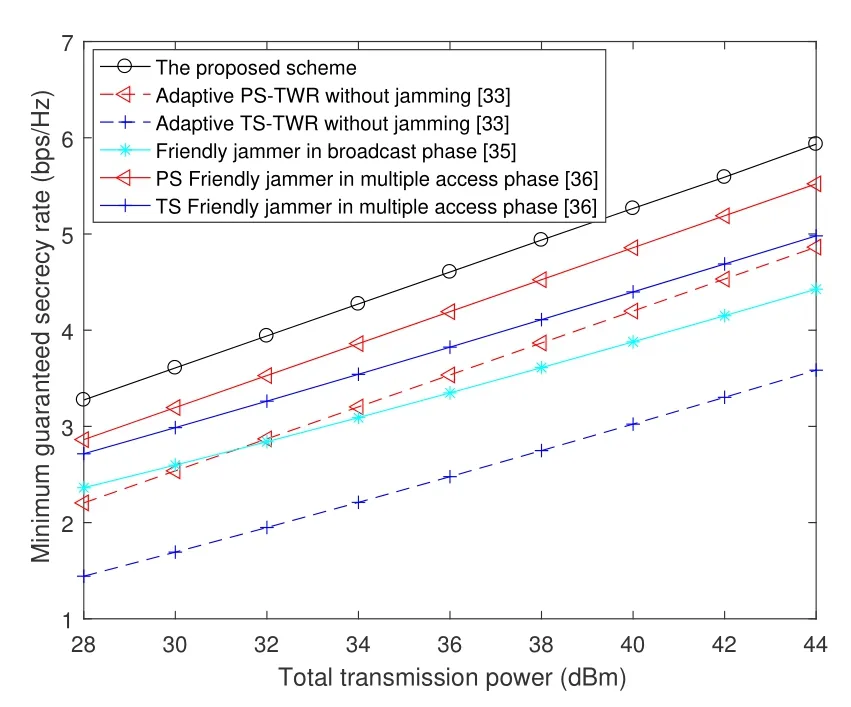
Figure 7.Minimum guaranteed secrecy rate versus total transmission power comparing with other schemes.
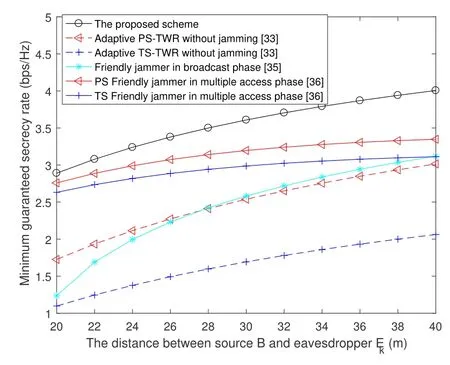
Figure 8.Comparison of the proposed scheme with other schemes under different location of eavesdroppers.
V.CONCLUSION
In the presence of multiple eavesdroppers,a novel FD relay jamming scheme suitable for EH two-way relay networks is proposed to guarantee secure information transmission and solve the energy scarcity problem of the relay.For the proposed scheme,the relay is operated in FD mode to achieve simultaneous information reception,EH and jamming transmission.Subsequently,the non-convex optimization of the minimum guaranteed secrecy rate is formulated,in which the primary non-convex problem can be converted into the approximate convex problem by the proposed algorithm.Simulation results illustrate the superiority of the proposed scheme in terms of the minimum guaranteed secrecy rate.
ACKNOWLEDGEMENT
This work was supported in part by the National Nature Science Foundation of China under Grant 61473066 and Grant 61601109,in part by the Fundamental Research Funds for the Central Universities under Grant No.N152305001,and in part by the Natural Science Foundation of Hebei Province under Grant F2017501039.
- China Communications的其它文章
- AI Assisted PHY in Future Wireless Systems:Recent Developments and Challenges
- Adaptive Maxwell’s Equations Derived Optimization and Its Application in Antenna Array Synthesis
- A 16-QAM 45-Gbps 7-m Wireless Link Using InP HEMT LNA and GaAs SBD Mixers at 220-GHz-Band
- A Wideband E-Plane Crossover Coupler for Terahertz Applications
- Terahertz Direct Modulation Techniques for High-speed Communication Systems
- A Semi-Blind Method to Estimate the I/Q Imbalanc of THz Orthogonal Modulator

