BC-BLPM:A Multi-Level Security Access Control Model Based on Blockchain Technology
Xiang Yu,Zhangxiang Shu,Qiang Li*,Jun Huang
1 College of Computer Science,National University of Defense Technology,Changsha 410005,China
2 College of Electronic Engineering,National University of Defense Technology,Hefei 230037,China
Abstract:Traditional multi-level security(MLS)systems have the defect of centralizing authorized facilities,which is difficult to meet the security requirements of modern distributed peer-to-peer network architecture.Blockchain is widely used in the field of access control with its decentralization,traceability and non-defective modification.Combining the blockchain technology and the Bell-LaPadula model,we propose a new access control model,named BCBLPM,for MLS environment.The “multi-chain”blockchain architecture is used for dividing resources into isolated access domains,providing a fine-grained data protection mechanism.The access control policies are implemented by smart contracts deployed in each access domain,so that the side chains of different access domains storage access records from outside and maintain the integrity of the records.Finally,we implement the BC-BLPM prototype system using the Hyperledger Fabric.The experimental and analytical results show that the model can adapt well to the needs of multi-level security environment,and it has the feasibility of application in actual scenarios.
Keywords:multi-level security (MLS);access control;blockchain;multi-chain;smart contract
I.INTRODUCTION
With the development of computer network technology,digital resources (e.g.,electronic documents,videos,databases,or even services) have realized network-based interconnection on the whole.However,with the continuous expansion of network resources,a large number of high-value data assets stored in the network are likely to be the target of external or internal attackers to infiltrate and control.Protecting these resources from various security threats is a very important issue that has received widespread attention.Access control technology is one of the important technologies for network security.It is usually used to regulate access behavior to key resources or valuable resources of the network,such as data,services,computing systems,storage space,etc.It restricts access to users in the network by executing access rules,and prohibits unauthorized users from illegally accessing the network resources,thereby more effectively protecting the network infrastructure and data stored in the network.
The Multiple Level Security(MLS)[1],as a security policy based on mandatory access control,describes the ability of a computer or network system to handle different security level information and prevent users or resources from obtaining unauthorized information.It has been widely applied in government,military,banking,enterprise and other departments.In MLS,information is stored in objects,and each object is assigned a security level label.In addition,the subject usually represents the user or the currently active session(such as a process in the OS).Similarly,each subject is assigned A license that represents a security level label as well.Traditional MLS models in-clude Bell-LaPadula[2],Biba[3],Clark-Wilson[4],and Chinese Wall [5].Among them,the Bell-LaPadula model provides confidentiality protection,the Biba model and the Clark-Wilson model mainly provide integrity protection,and the Chinese Wall model provides protection for the system environment based on conflicts of interest.At present,most multi-level security access control systems are based on centralized architecture,such as MUSHI [6],3-D Correlation[7]and others.Centralized access control mechanism relies on trusted third-party provisioning permission management services.However,once the decision nodes in the system are maliciously attacked or controlled,it is easy to cause single-point failures,which makes the whole system face threats such as illegal,over-the-level access and malicious tampering of access logs,thus failing to provide credible and reliable access control service for honest visiting subjects.At the same time,the efficiency of centralized access control services will inevitably be affected by factors such as hardware infrastructure and network transmission bandwidth,there are problems of high construction and maintenance costs and low transmission efficiency,which cannot meet the needs of distributed network environment applications.
Blockchain technology can effectively solve the problem of insufficient centralized server for multilevel security system.The basic thought of blockchain technology is to use a distributed peer-to-peer network to ensure secure,transparent information transfer and storage of transactions.Information can be shared among multiple peer nodes without the intervention of the central manager,and data cannot be changed once it is linked into the public ledger of the blockchain.Through the consensus protocol,each transaction in the blockchain can have its own proof of validity,thus ensuring the Decentralization.
The blockchain features non-tamperable,decentralized,and time-series data,enabling multi-level secure access control based on blockchain technology to avoid single-point failures and provide nonrepudiation access logs,thus effectively securing the information system.With the promotion of smart contract[8]in the field of blockchain technology,it is possible to realize a more lightweight multi-level security policy through the coding and instantiation of smart contracts,and improve the flexibility of multi-level security access control.Therefore,the combination of blockchain technology and multi-level security access control has a promising application prospect.
To construct a distributed multi-level security access control mechanism,this work proposes a new multi-level security access control model BC-BLPM(Blockchain-based Bell-LaPadula Model) based on blockchain technology and Bell-LaPadula(BLP)model.The model introduces the concept of “multiblockchain”,which divides the operational data of different departments or organizations in the network environment through multiple sidechains,so that the data of different business organizations can be logically isolated;by using the blockchain as a third-party management intermediary,the single-point failures and untrustworthy problems that may be caused by traditional centralized authorization settings are eliminated;provides access control services for user equipment and network resources by writing BLP-based security policies in smart contracts and deploying them in blockchain network.After the execution of the smart contract is completed,the execution process will be written in the form of a transaction and will be irreversibly linked into the blockchain.
Compared to traditional MLS systems (such as MUSHI [6]),BC-BLPM has the following advantages:
1) Confidentiality:The BLP-based access control policy primitives ensure the legitimacy of access authorization.At the same time,BC-BLPM enhances the security of the pol-icy itself through the form of smart contract deployment.
2)Integrity:The data integrity of the access process is maintained by the entire network nodes or the designated restricted nodes.Once the data record is linked into the blockchain,it cannot be revoked or changed.
3)Availability:Through the distributed verification mechanism of the blockchain and the mandatory and automated execution rules of the smart contract,various malicious attacks such as replay attacks,identity forgery attacks and denial of service attacks can be effectively prevented.
4) Decentralization:The data from different organizations are maintained by different sidechains,and the operations between them are isolated from each other.The failure of a single service node in the network does not affect the user’s access,avoiding the problem of single-point failures.This advantage is not available in traditional MLS systems.
5) Auditability:All access behaviors from different users are recorded in the public ledger of the blockchain.Since the data storage of the blockchain has the characteristics of openness and transparency,the data in the public ledger is visible to all subjects,which facilitates the auditing of the legitimacy of user’s access within a period of time by authoritative institutions.
6)Scalability:The newly participating node can be added to the blockchain network by downloading the ledger copy of the original node.
7) Lightweight:User equipment and network resources can use BC-BLPM without any additional components.Meanwhile,the resource provider does not need to remain online in real time during the process of providing access control services.
The rest of the paper is structured as follows:Section II introduces the related work.Section III and Section IV describes the architecture and the implementation respectively.In Section V,we evaluate the performance and the security of the model through experimental and analytical methods.And finally,we have the conclusion of this paper in Section VI.
II.RELATED WORK
2.1 Bell-laPadula Model
The Bell-LaPadula (BLP) model[2,9]is a state machine model for the MLS environment proposed by D.Elliott Bell and J.Leonard LaPadula.It is the earliest and most popular MLS model.Since the introduction of this model,many research works have been carried out in various ways driven by actual demand,and many important research results have been obtained.And we here select the research results in recent years for discussion.For example,Zeng et al.[10]proposed a dynamic sensitive data flow security model for federated cloud systems that assigns cloud system entities different security levels for a given security grid based on BLP security rules and cloud security rules,and formalizes them.The method assigns a security policy to the entity movement process between different clouds.Tan et al.[11]proposed a centralized pervasive computing environment/multi-level security (CPCE/MLS) system was designed.In Ref.[11],By introducing a server storage terminal,a multilevel security access control mechanism based on BLP model,process creation monitoring mechanism and auditing are implemented that provide security for pervasive computing environments.In order to solve the problem of cooperation between IoT terminals and virtual machines,Dong et al.[12]designed a taskoriented IoT multi-level collaborative access control model VR-BLP.The model divides tasks into multiples through improved BLP state transition rules.The level limits the access between the virtual machine and the IoT terminal,and implements network isolation,process isolation,and shared memory isolation.In the context of medical big data security,Freitas et al.[13]proposed a BLP-based access control model for federal cloud workflow deployment,which divides medical services into multiple security states and performs specific security.Policies implement state transitions between different services.
In summary,the Bell-LaPadula model,as the most classic multi-level security access control model,has been widely applied in many different research fields such as computer systems and network security.From the perspective of confidentiality,the model controls the flow direction of data through the security policy of “no read-up” and “no write-down” to prevent data flowing from high-confidentiality subject to lowconfidentiality subject.Therefore,the MLS system based on the BLP security policy can effectively prevent illegal entities from stealing data,thereby maintaining the security state of confidential data,which is also the key to achieving multi-level security.Therefore,we choose the Bell-LaPadula model as the basic framework for the multi-level secure access control model.However,most BLP-based MLS systems still have authorization centralization,lack of auditing tools and data integ-rity protection mechanisms,etc.,and need to improve the traditional Bell-LaPadula model through external channels,which is reflected in many existing research[14–16].Compared with these improved methods,the biggest difference of this work lies in the adoption of blockchain technology,and the distributed execution of access control policy together with the immutable record of access behavior in the blockchain network,so as to overcome the inherent defects of Bell-LaPadula model.
2.2 Blockchain and Access Control
In recent years,the application and research of blockchain technology in cryptocurrency [17],identity management [18],reputation system [19],Internet of Things [20],cloud storage [21]and other fields have been deepening.A blockchain is defined as a decentralized,cryptographic-based arbitration network that does not require the participation of trusted third parties.In this network,nodes that are not trusted to each other can perform “end-to-end” interaction in an encrypted,verifiable form without a trusted intermediary.This interaction process is also called “Transaction”in the blockchain system.The transactions generated by the entire network in unit time are packaged into a“block”as a data record,the integrity of the data is protected by a hash function,and finally linked to the end of the chain-based ledger maintained by the entire network nodes.The verification of a transaction correctness relies on the distributed consensus protocol[22].
Traditional access control technologies such as rolebased access control(RBAC)[23],attribute-based access control (ABAC) [24],usage control (UCON)[25],etc.,and both of which need to introduce a trusted centralized authorization entity to provide access control services for users.The decentralization,non-tamperable,and time-series data of the blockchain determine its ability to play an independent trusted third-party role and provide access control services using its own data logging and consensus functions.Meanwhile,blockchains can also be used to transform existing access control models,decentralizing centralized authorization centers.In recent years,many research efforts have focused on the combination of blockchain technology and access control.
Some researchers have proposed storing and executing access control policies through blockchain transactions.Zyskind et al.[26]used blockchain to protect the user’s private data in a mobile service scenario involving untrusted third parties.Among the article,there are two types of transactions accepted by blockchain:one for access control management transaction Taccessand the other for data storage and retrieval transaction Tdata.Through the creation of these two kinds of transactions,the access control policy is stored on the blockchain and the response to the legitimate access request.However,implementing such access control requires the resource requester and the owner to be online at the same time,which is not desirable in practical application scenarios.Ouaddah et al.[27]focused on the access control problems existing in IoT devices and proposed the FairAccess model.As a distributed access control model implemented by blockchain,this model stores the access control policy in the blockchain with the form of a 2-tuple(resource,request) through the blockchain transaction,and can also be applied as a log database to provide auditing capabilities.The disadvantages of FairAccess are the same as in Ref.[26],which requires both resource requesters and resource operators to stay online at the same time.Similar to the first two schemes,Ma et al.[28]proposed to store key data on the blockchain and manage it by a group of trustees who are responsible for controlling access to such data.
Other researchers have adopted smart contracts as a storage vehicle for access control policies.Among them,Cruz et al.[29]proposed a blockchain-based RBAC model,which used Ethereum platform and smart contracts as the infrastructure to achieve crossorganization access control,and also proposed the concept of cross-organization role availability.Wang et al.[30]designed a data access control model for cloud storage architecture,providing data access and sharing services by calling smart contract interfaces.Azaria et al.[31]focused on the data privacy protection and access permission management of medical systems,proposed a model called MedRec suitable for electronic medical records.The model is implemented by Ethereum platform.By introducing the hierarchical relationship of smart contracts,the smart contract calling path of the tree structure is designed,enabling the patient or doctor to view/update/revoke the electronic medical record only by calling the top-level contract.But on the other hand,the hierarchical relationship of the multi-contracts also increases the storage overhead of the network nodes.Different from the Refs.[29–31],Maesa and Mori[32]combined the attributebased access control model and the blockchain technology to design a universal access control system for managing the calling permissions of smart contracts.Through the external ABAC infrastructure (such as PAP,PDP,PEP,etc.),the system embeds the policy into the smart contract through the XAMCL language,and implements a lightweight access control mechanism for the calling relationship of smart contract.
Until now,the combination of blockchain technology and access control technology is mainly concentrated in three application areas,namely,Internet of Things,cloud storage and medical systems.Most of these fields have open scenarios,that is,the scene where operating devices are not restricted.These scenarios are mainly concerned with the protection of privacy,and the flexibility of data sharing.The issues of confidentiality and availability in multi-level security are usually placed in the third place or even lower.Therefore,until now,neither the access control mechanism based on blockchain implementation,nor the existing access control model based on the blockchain improvement and the access control method with additional encryption means,have fully realized the requirement of multi-level security access control mechanism.In comparison,the access control model proposed in this work focuses on the MLS environment with higher requirements for data confidentiality and user operation legitimacy,through the “multi-chain”architecture and access control policy based on smart contracts,without infringing on MLS system under the premise of security properties,effectively limits the visitors access to network resources,so as to realize the decentralized multi-level security access control mechanism.According to the previous research,the access control model proposed in this work is the first one to consider the application of blockchain technology to multi-level security access control mechanism.
III.ARCHITECTURE
3.1 Overview
BC-BLPM is a decentralized multi-level security access control model that combines blockchain technology and BLP security policy primitives.It consists of the resource layer,access control layer,and transaction-forwarding layer as is shown in Figure1.In the resource layer,different types of data resources,e.g.,databases,electronic files,pictures and so on,stored in a medium such as a computer or a smart mobile device are accessed into the model via an encrypted data transmission channel.In the access control layer,A number of data processing nodes are responsible for forming blockchain-based access domains,which can be used as an abstraction of different business departments in a large enterprise or business organization,maintain different data resources respectively(i.e.,maintain the data resources stored carrier),and record access behavior requested from the outside by updating the distributed Ledger of the sidechains.In the transaction-forwarding layer,several high-performance data processing nodes establish communication relationships with gateway nodes of each access domain,and are responsible for packing,sorting,and forwarding blockchain transactions generated in the access control layer.
In BC-BLPM,the access control layer is composed of multiple access domains,which realizes the isolation of business logic.That is,updating the data of the sidechain in one domain does not affect the others,which ensures the operational isolation of interdomain data.This is the key to achieving a multi-level security environment.For example,for a large enterprise,the isolation of operational data from various business units can minimize the risk of core data flows from high security units to low ones.At the same time,each access domain deploys a smart contract that includes access control policies.Through the execution of the smart contract,the calling process of the access control policy is completed.And the model creatively uses the combined public key algorithm system(CPK)as the verification component of the identity validity for the external access subject.The subject can verify the validity of its own identity information based on the cryptosystem.The model can be expressed in the form of a 6-tuple(AD,PL,ET,R,D,MR),where:
1)AD={ad1,ad2,...,adn},represents all access domain collections in the network that are added to the BC-BLPM access control layer.
2)PL={pl1,pl2,...,pln},represents all the set of access control policies that are deployed in the network.
3)ET={et1,et2,...,etn},represents the set of entities in the network,which can be divided into user entities and resource entities.Each type of entity can map clearance level or classification through function F.By combining public key algorithms to sign identity data,signature dataSigCPK{eti}(1 ≤i≤n) based on entity identity can be obtained.
4)R={r1,r2,...,rn},represents the set of access requests that all access-request entities are generating.Similarly,the different decision results of these request counterparts can be represented by the setD={d1,d2,...,dn}as well.
5)MR:F(ET)×R×PL →D,represents the mapping relationship between the access request and the decision result.The establishment of this relationship also requires the participation of the entity security level setF(ET)and the access control policy setPL.
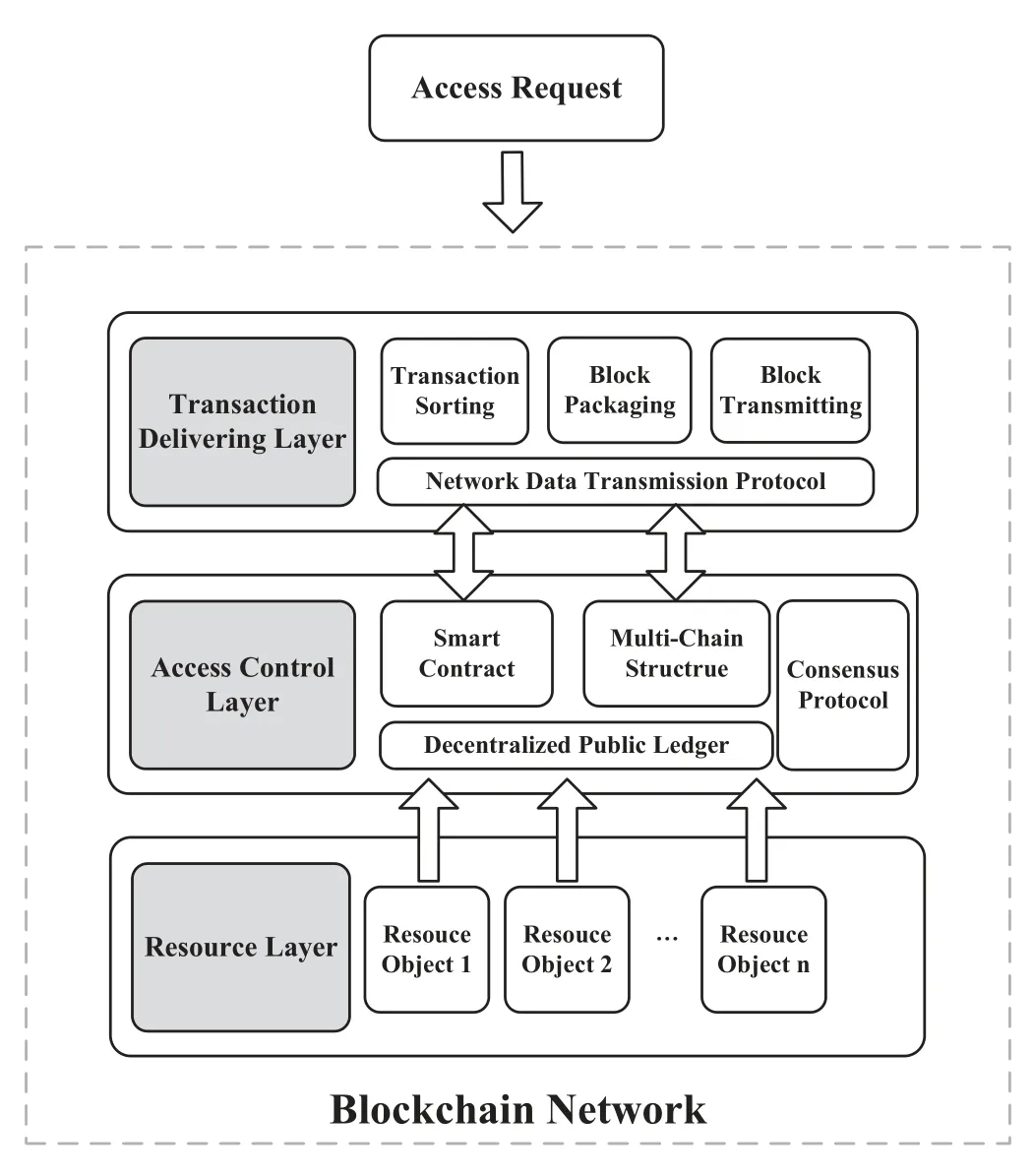
Figure1.BC-BLPM framework.
3.2 Access Control Policy
We reuse the security theorem of the traditional Bell-LaPadula model and establish the access control policy for multi-level security environments.Below,we describe the policy from three aspects:basic elements,security attributes,and state transition rules.
3.2.1 Elements
We first define the elements of the Policy:1)Subject and Object.One user is a subject,a specific data resource that exists in the network represents an object.Users can obtain permission to access a certain type of data resource by submitting an access request.
2)Access attribute set.The access attribute set is A contains two sub-elements,which isA=Ao∪Aϕ.RegardingAoas the access attribute set in the traditional Bell-LaPadula model,whereAo={r,a,w}is composed of 3 kinds of sub-attributes,rstands for readonly,astands for Write-only,andwstands for readwrite;Aϕrepresents the resource-shared attribute set between two different objects,whereAϕ={sd},and sd denotes a data-sending operation.
3)Security function set.Fis a set of security functions,andF={fs(s),fc(s),f(o)}contains 3 subelements,wherefs(s) represents the highest clearance level of the subject s,fc(s)represents the current clearance level of the subjects,andf(o) represents the security level of the objecto.
4)Current access set.B=S×O×Aindicates the current access set.The arbitrary element ofBisb,andb=(si,oj,x) indicates that one subjectsiperforms anxaccess behavior on another objectoj.
5) Access matrix.The access matrixMcontains a sequence of access attributes that record the subject’s access behavior to the object,i.e.Mij ⊆A.
6) Current system state.v=(b,M,f)∈Vrepresents the state value of the system,whereb ∈B,f=
7) State transition rule.The rule functionρ:R×V →D×V ∗,whereR=RA×S×O×Xrepresents the request set,X=A ∪F;D={yes,no,error,?}represents the system’s response set;VandV ∗represent the system state before and after the state transition,respectively.
3.2.2 Security Properties
The security properties of the policy are implemented based on the original security theorem of the Bell-LaPadula model,and are extended according to the actual elements of the policy and the access requirements of the subject.We give the following theorems:
Theorem 1.Simple-Security Property
Statev=(b,M,f)∈V,x ∈Aosatisfies the simple-security property if and only if∀(s,o,x)∈b,there are:①x=a;②x=rorx=w ⇒fs(s)▷f(o).
Here,▷means“dominate”,refers to the partial order between security levels or clearance levels.It means that,for∀(s,o,x)∈b,when the subject’s tries to access the object o with the access attributerorw,the highest clearance level of the subject’s must be higher than or equal to the security level of the object o,then the statev=(b,M,f)satisfies simple-security property.
Theorem 2.∗-Property(Star-Property)
Statev=(b,M,f)∈ V,x ∈ Aosatisfies∗-Property if and only∀(s,o,x)∈b,s ∈S/S∗whereS∗is a trusted subject,there are:①x=r ⇒fc(s)▷f(o);②x=a ⇒fc(s)◁f(o);③x=w ⇒fc(s)=f(o).
It indicates that,for∀(s,o,x)∈b,s ∈S/S∗,when the subject’s tries to access the objectowith the access attributer,the statev=(b,M,f)can satisfies the∗-Property only if the current clearance level of the subject s is higher than or equal to the security level of the objecto;when the subject s tries to access the object o with the access attributea,v=(b,M,f)can satisfies the∗-Property only if the current clearance level of the subject s is less than or equal to the security level of the objecto;similarly,when the subject s tries to access the object o with the access attributew,the statev=(b,M,f) can satisfies the∗-Property only if the current clearance level of the subjectsis equal to the security level of the objecto.
Theorem 3.Data-Flow Property
Statev=(b,M,f)∈V,x ∈Aϕsatisfies the Data-flow property if and only if∀(s1,o1,o2,x)∈b,s1∈S/S∗whereS∗is a trusted subject,there are:¬(fc(s1)◁f(o1))andx=s ⇒f(o2)▷f(o1).
It specifies the direction of data transmission between objects.When the data transfer action between two objects is involved,only meet the current clearance level of the operation subjects1is not dominated by the security level from the data-sending objecto1,and the security level of the data-receiving objecto2dominates the security level ofo1,the statev=(b,M,f)satisfies the data-flow property.
Theorem 4.Discretionary-Security Property
For the statev={v1∪v2∪...∪vn}andvi=(b,M,f)∈V,x ∈Aosatisfies the discretionarysecurity property if and only if∀(s,o,x)∈b,there is:x ∈Mij.
Forvj=(b,M,f)∈ V,x ∈ Aϕsatisfies the autonomous security property if and only if∀(si,oj,ok,x)∈b,there is:∃oj,ok ∈O,Mij ⊆Mik.
Theorem 5.Fundamental Security Property
The system can remain secure if and only if the initial state of the system is secure,and each state transition process satisfies simple-security property,∗-property,data-flow property,and discretionary-security property.
3.2.3 State Transition Rules
The execution of the policy will cause the transition of the system state.The state transition function is:ρ:R×V →D×V ∗,whereRis a set of requests andDis a set of decisions.TakeRkbe arbitrary element ofR,Dmbe an arbitrary element ofD,then the output ofρremains secure if and only if∀(Rk,v)∈(Dm,v∗)and the Initial statevis secure,such thatv∗is secure.According to this derivation principle,we present 4 types of state transition rules for the access control policy.
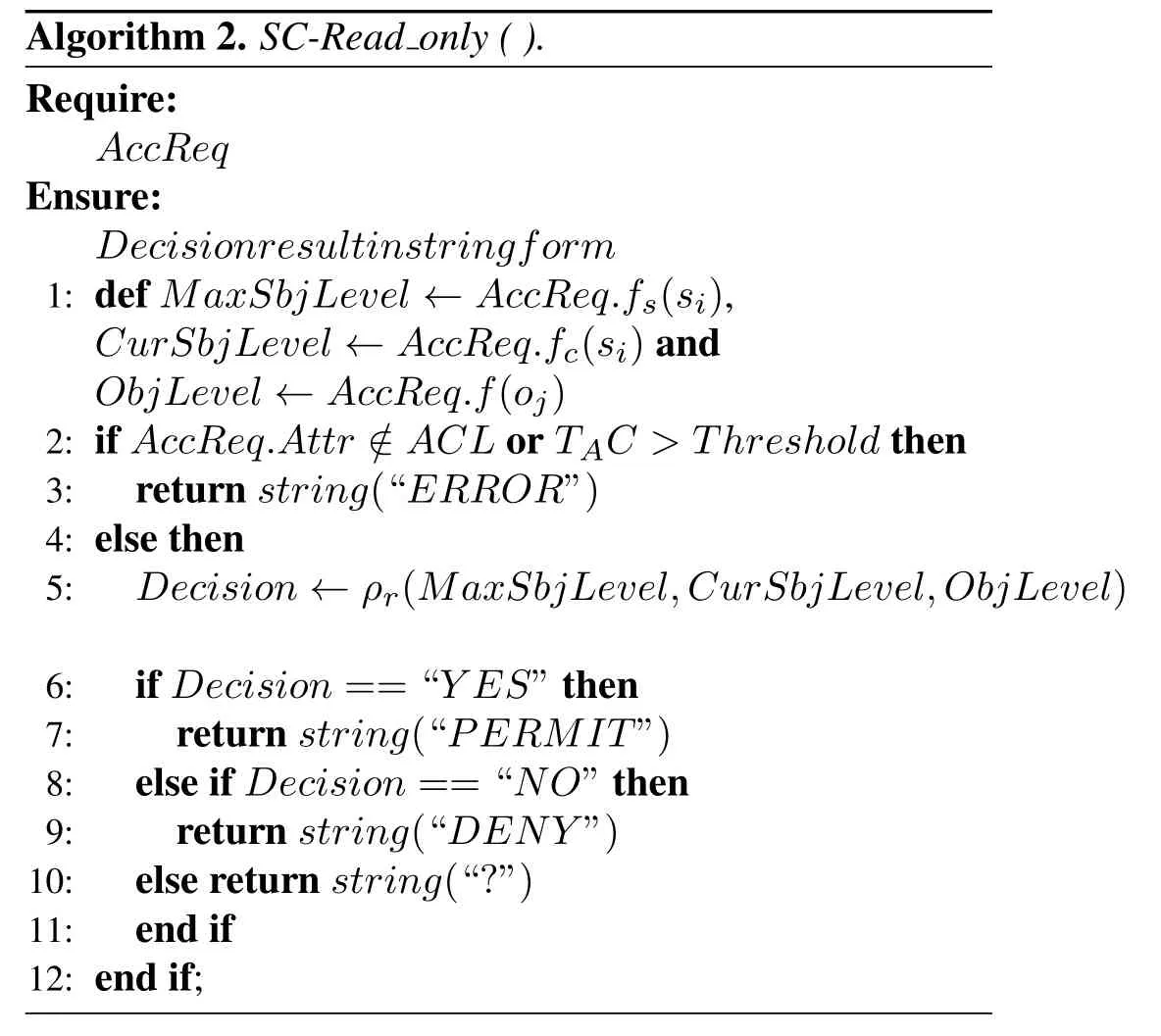
Rule 1.Read-only
Given the initial statev=(b,M,f)∈V,s ∈S/S∗,the process of state transition requestRk=(si,oj,r)is:

When the subjectsirequests to access the objectojwith the access attributer,the system first checks whether the request is legal,that is,whether it is in the scopeDom(ρr) of the rule,and if not,the “unknown” state (?,v) is returned.IfRk ∈Dom(ρr)is true,then the dominance relationship between the highest clearance levelfs(si) and the security levelf(oj)is judged.Iffs(si)can dominatef(oj),then the system continues to check if the access attribute r satisfies the requirements ofr ∈Mij.Only if these three requirements are met,the system can execute the access request and return to the“access permitted”state(yes,v∗=(b∗,M,f∗)),otherwise it returns the “access denied”state(no,v).
Rule 2.Write-only
Given the initial statev=(b,M,f)∈V,s ∈S/S∗,the process of state transition requestRk=(si,oj,a)is:
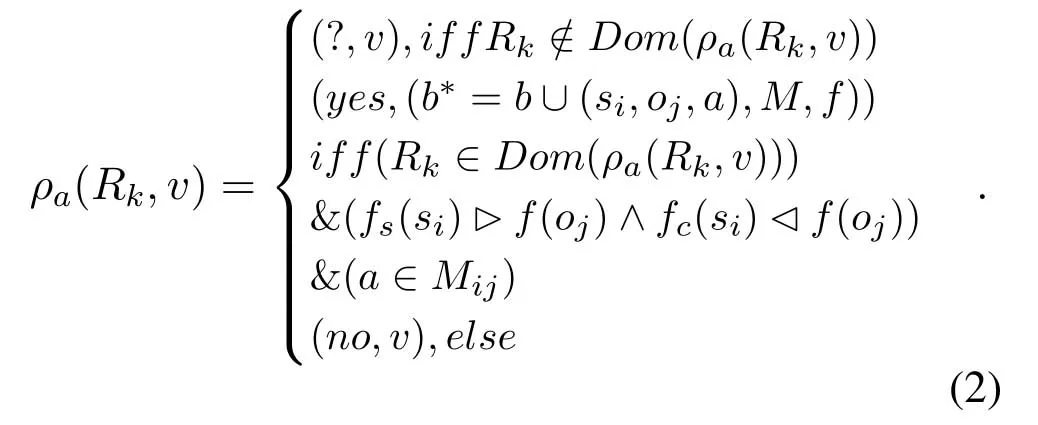
When the subjectsirequests to access the objectojwith the access attributea,the system first checks whether the request is in the scopeDom(ρa),and if not,the “unknown” state (?,v) is returned.IfRk ∈Dom(ρa) is true,it continues to judge the clearance level ofsiand the security level ofoj.If both of it meet the requirement of “writing up”,then the system checks whether the request attributeasatisfies the requirement ofa ∈Mij.Only if these three requirements are met can the access request be executed and the“access permitted”state(yes,v∗=(b∗,M,f))be returned,otherwise the “access denied” state (no,v)is returned.
Rule 3.Read-write
Given the initial statev=(b,M,f)∈V,s ∈S/S∗,the process of state transition requestRk=(si,oj,w)is:
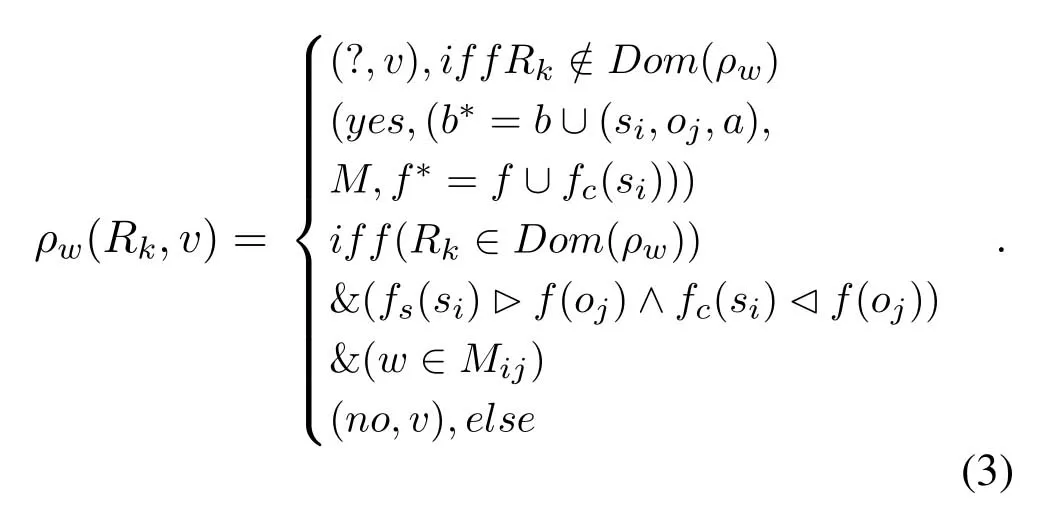
When the subjectsirequests to access the objectojwith the access attributew,the system first checks whether the request is in the scopeDom(ρw),and if not,returns the “unknown” state (?,v).IfRk ∈Dom(ρw)is true,then the dominance relationship between the highest clearance levelfs(si),the current clearance levelfc(si),and the security levelf(oj) is judged,iffs(si) is for the dominant relationship off(oi)while satisfyingf(oi)dominatesfc(si),it continues to check whether the request attributewsatisfies the requirement ofw ∈ Mij.Only if these three requirements are met can the access request be executed and the “access permitted” state (yes,v∗=(b∗,M,f∗)) be returned,otherwise the “access denied”status(no,v)is returned.
Rule 4.Data-Transfer
Given the initial statev=(b,M,f)∈V,s ∈S/S∗,the process of state transition requestRk=(si,oj,ok,sd)is:
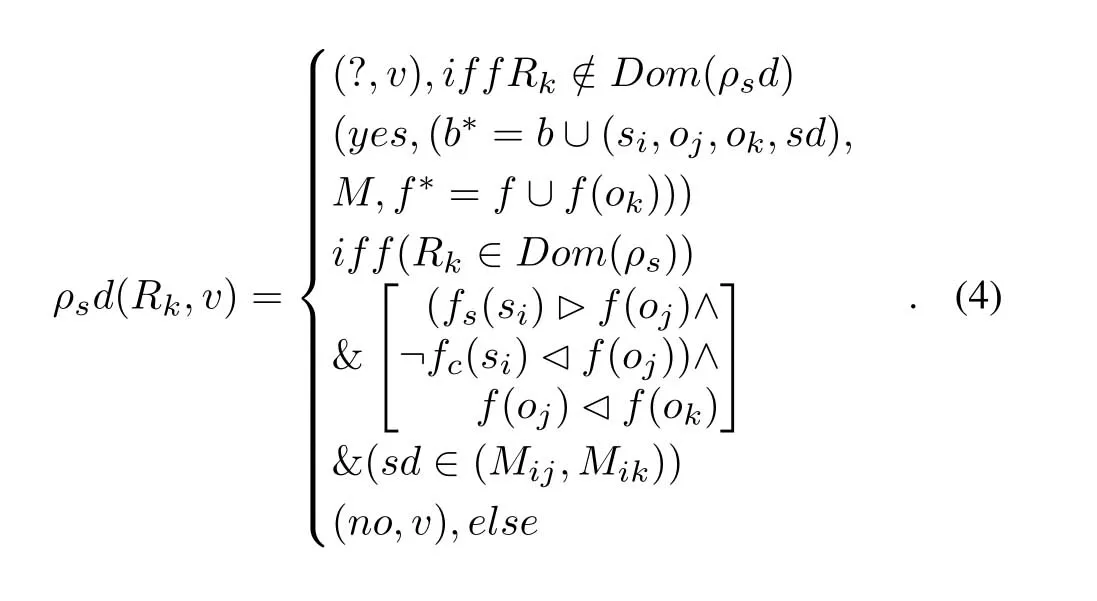
When the subjectsirequests to access the objectojandokwith the access attributesd,the system first checks if the request is in the scopeDom(ρsd),and if not,returns the “unknown” state (?,v).IfRk ∈Dom(ρsd) is true,then the dominance relationship betweenfs(si) andf(oj),fc(si) andf(oj),f(oi)andf(ok),and Whether the request attribute sd exists in the access control matrixMof two objects are judged respectively.Only whenfs(si) dominatesf(oj),fc(si) is not dominated byf(oj) andf(ok)dominatesf(oj),and the request attributesdsatisfiessd ∈(Mij,Mik),the request can be executed to return the “access permitted” state (yes,v∗=(b∗,M,f∗)),otherwise it returns the“access denied”state(no,v).
3.2.4 Combined Public Key Cryptosystem
The concept of combined public key cryptosystem(referred to as CPK system) was first proposed in 1999[33].The CPK system is based on identification and does not require third-party certification.It can manage large-scale keys with fewer parameters.Its security is based on the intractability of discrete logarithms.One of the basic ideas of CPK is to use a small matrix to combine a large number of public and private key pairs to solve large-scale key management problems.
The CPK key management system can be constructed based on either a general finite-field discrete logarithm problem or an elliptic curve discrete logarithm problem.Under the same security requirements,the elliptic curve discrete logarithm problem requires a smaller key size,which has the advantages of fast running speed and small storage space.Therefore,this paper builds on the CPK system based on the discrete logarithm problem of elliptic curves over a finite fieldFp(pis a prime number not equal to 2 and 3).
Given the elliptic curve cryptographic parametersT=(a,b,G,n,p),a random seed public key sequence matrix PSK and seed private key sequence matrix SSK can be constructed:
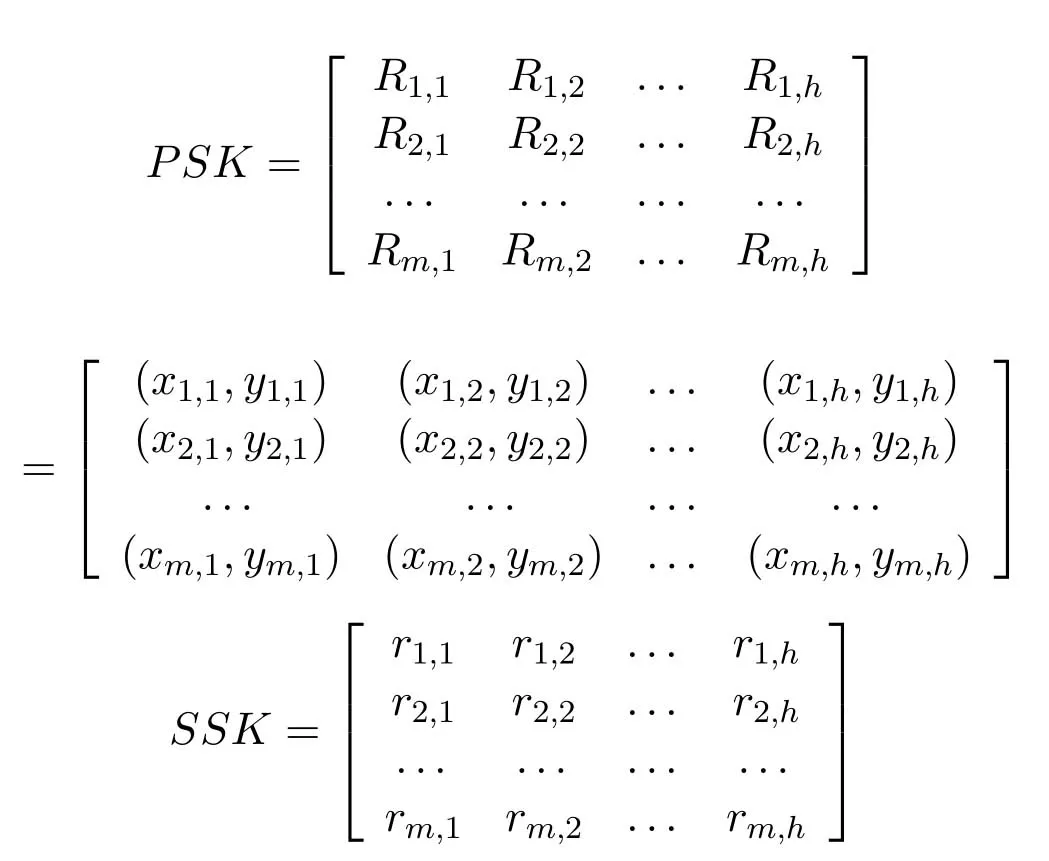
Wherer(i,j)isR(i,j)=(x(i,j),y(i,j)) for the discrete logarithm of the base pointG,i.e.R(i,j)=(x(i,j),y(i,j))=[r(i,j)]·G.Obviously,the elementsR(i,j)=(x(i,j),y(i,j)) andr(i,j)at any corresponding position in the two matrices ofPSKandSSKform a public and private key Yes,the combination of multiple points inPSKand discrete logarithms in SSK can also form a public-private key pair.Before the access control policy is implemented,theCPKsystem can be used to protect the identity validity of the subjects ∈S/S∗.The subject first uses the randomCPKseed private key sequenceSSK={r1,r2,...,rn}to generate its own signature ID private key,the generation steps are as follows:
(a)Calculate the hash value of ID using Hash algorithm to getDigestID=hash(ID).
(b) IfMAP0=DigestID,then calculate againMAPi+1=EK(MAPi)(i ≥0),whereEK(·) is a block cipher operation withKas the encryption key.Letinot exceed the number of SSK (marked aslen),get the sequence valueSeqIDSK=(MAP0‖MAP1‖..‖ MAPn−1),len × kbefore interception bits(kis the number of unit bits)are used as the selection sequence{av(1≤v ≤n)}.
(c)We can use the selection sequence{av(1≤v ≤n)}to combine SSK to obtain the identification private key
The subject can use the generated signature private key to resign the blockchain transaction information to obtain the signature valueCPKSig.Then the verification of signature also be implemented using theCPKsequencePSK={R1,R2,...,Rn}=Assuming that the ID of the subject has been maliciously tampered after signature,based on the anti-collision property of the Hash algorithm,the verifier cannot use the ID’ (that is,the subject ID that has been tampered with) to restore the original identification verification public keyRv,so the validity of the signature cannot be verified.
3.3 Blockchain Component
The blockchain can be divided into two structures according to the type of participants:permissioned blockchain(including private/consortium blockchain)and permission-less blockchain.In a permission-less blockchain such as the Bitcoin system,each participating node can become a “miner”,each can generate transactions and maintain the blockchain by verifying the validity of the transaction.A transaction can be recorded in the blockchain only if the transaction is verified and committed by most of the“miners”in the network (in principle,more than 50%).In the permissioned blockchain,only authorized participants can become “miners”.Because of the authorization mechanism added in the permissioned blockchain,the unauthorized nodes cannot join to the network freely,which limits the scale and attributes of the application scenario,and is more suitable for some application scenarios that have high demand for system performance load and security confidentiality,such as government,banking,medical institutions,etc.As a multi-level secure access control model based on blockchain,BC-BLPM adopts the permissioned blockchain as the underlying architecture.This section describes the blockchain components of BC-BLPM,including transactions,blocks and smart contracts.
3.3.1 Transaction and Block Format
BC-BLPM uses two types of transactions,namely:①Access Record Transaction(ART);②Data Transfer Transaction(DTT).
The composition of the two transactions is shown in Figure2 and Figure3.The transaction headers of the two transactions contain common fields for blockchain trans-actions,such as transaction hash value TX Hash,transaction public key address TX Addr,subject’s private key signature TX Sig and subject-based CPK signature CPK Sig,and the transaction body contains payloads that characterize the transaction structure.As a write set of transactions,the payload fields of the transactions need to be populated by the transaction creators.
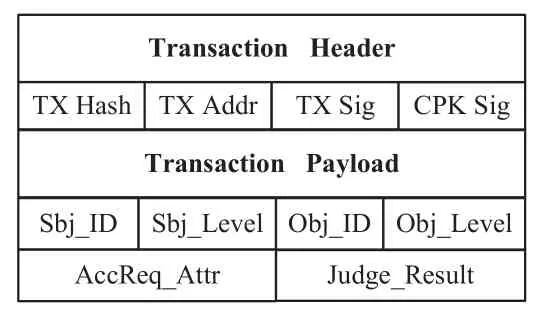
Transaction Header TX Hash TX Addr TX Sig Transaction Payload Sbj_ID Sbj_Level Obj_ID Obj_Level AccReq_Attr Judge_Result CPK Sig
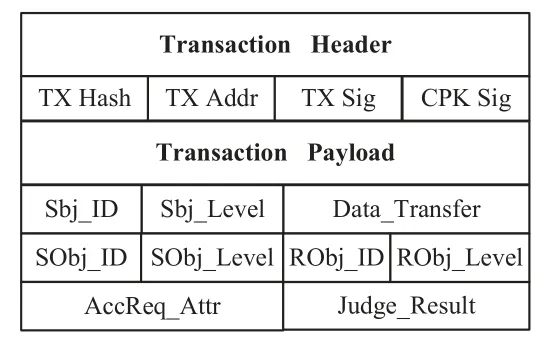
Transaction Header TX Hash TX Addr TX Sig Transaction Payload Sbj_ID Sbj_Level SObj_ID SObj_Level AccReq_Attr Judge_Result Data_Transfer RObj_ID RObj_Level CPK Sig
The ART transaction is responsible for recording the decision result of the access operation.The transaction body contains the following payload fields:
• Sbj_ID:The unique identifier of the subject,including the subject’s name,and IP address,MAC address,etc.
• Sbj_Level:The clearance level of the subject,consisting of the highest clearance level and the current clearance level.
• Obj-ID:The unique identifier of the object being accessed,including the name,IP address,MAC address,and the access domain number to which it belongs.
• Obj-Level:The security level of the object being accessed.
• AccReq_Attr:Access attributes requested by the subject,including read-only,write-only and readwrite.
• Judge Result:The judgment result of the access request from a subject,including“?”,“0”and“1”,where“?”indicates an illegal access warning,“0”indicates access is denied,and “1” indicates access is permitted.
Unlike the ART,the DTT transaction is responsible for recording the data transfer process between two different objects.In the DTT transaction body,the same fields as the ART transaction body are Sbj ID,Sbj Level,AccReq Attr,and JudgeResult,and Its unique fields are:
• SObj-ID:The unique identifier of the datasending object.
• SObj_Level:The security level of the datasending object.
• RObj_ID:The unique identifier of the datareceiving object.
• RObj_Level:The security level of the datareceiving object.
• Data_Tansfer:Data transferred from the datasending object to the data receiving object.
Data transfer operations are divided into intra-domain and inter-domain transfer modes.The inter-domain data transfer operation needs to record this data operation behavior in two different access domains,that is,to update the structure of the“independent”side chain,so according to The ID of the access control domain where the data receiving object is located divides DTT into two types of transactions:I DTT (Inter-domain Data Transfer DTT)and C DTT(Cross-Domain Data Transfer DTT).
As shown in Figure4,the block is normally divided into block header and block body[28,34].The block header is used to record the basic parameters of the block and is linked with the previous block in the blockchain by recording the“PreHash”value.The block body is used to record the transaction data and the metadata of the block mining and verification process.All transaction data is computed by the parallel hash of the Merkle tree and recorded as a unique index value in the Merkle root to the block header.It should be noted that,unlike the permission-less blockchain based on the workload-based block mining process(i.e.,the POW Protocol),the BC-BLPM model constructed by permissioned blockchain adopts a consensus mechanism for obtaining system consistency permissions to generate the block(we use the PBFT protocol in this work),therefore the block does not generate the target difficulty,random number and other fields required to execute the POW.
The transactions generated by the access behavior of different subjects form a chained data structure,as shown in Figure5.This structure generates a new block by packaging a certain number of transactions per unit time,and is linked by the hash of the block.Among them,the C_DTT transaction must be packaged by an independent block,which is determined by the update requirements of cross-domain transactions,and also facilitates the development of later audit work.
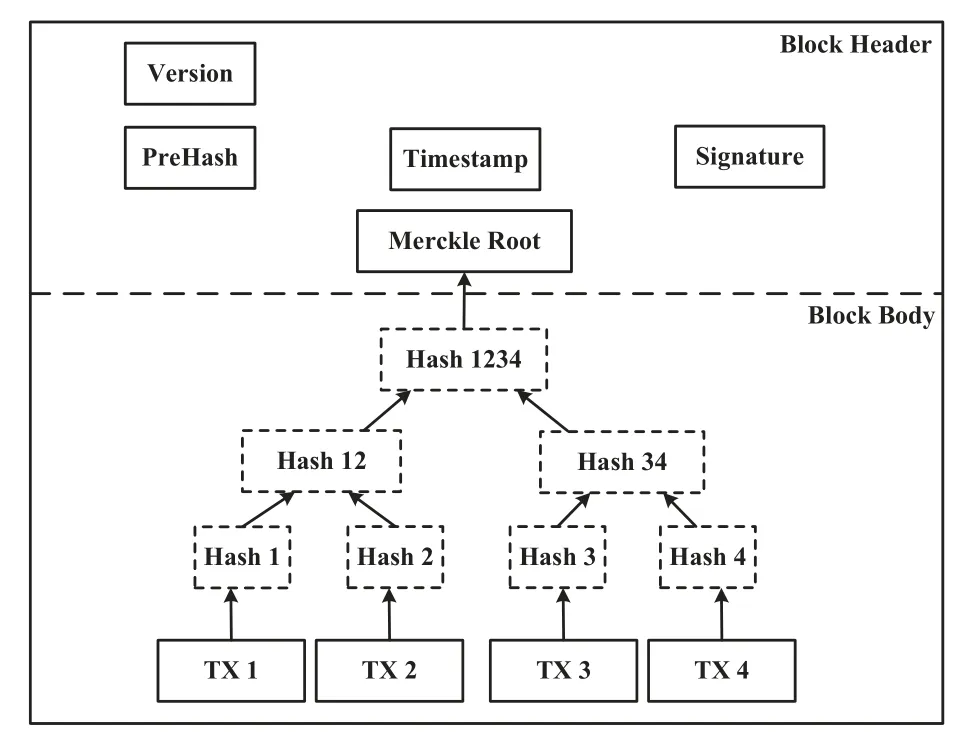
Figure4.Format of the block in BC-BLPM.
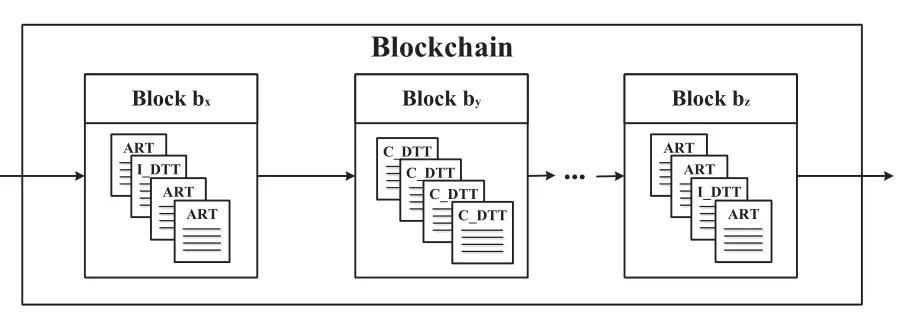
Figure5.Architecture of the blockchain ledger in BCBLPM.
3.3.2 Transaction Pool Structure
In order to ensure the continuity of the transaction packaging and on-chain process,so that each block can pack a fixed number of transactions as much as possible,and effectively reduce the delay generated by the block,this article uses the transaction pool to implement the sequential packaging process of transactions to blocks.The concept of transaction pool originally appeared in the Ethereum project,which means“a pool that temporarily stores transactions to be executed.” The working mechanism of the transaction pool is shown in Figure6:As long as a new transaction is generated,it will be first added to the transaction pool,whether it is generated by a local node or broadcast by other peer nodes.When the block needs to be packaged,the transaction will be extracted from this pool.
The transaction pool consists of transaction queues,including“queued”and“pending”sub-queues,where“queued” temporarily stores transactions that cannot currently be executed immediately,and “pending”stores currently executable transactions.When a large amount of transaction data is generated in a unit time,transactions exceeding the storage capacity of a single block are first stored in“queued”,and a certain number of transactions are selected to form a new block according to the order of the queue.The data structure of the BC-BLPM blockchain described in Figure5 shows that the record of the C_DTT transaction involves two different access control domains.And the transaction processing node needs to cross two different sidechains to execute the inter-domain of the block Update operation.Therefore,in order to ensure the synchronous update of transactions,this article deploys a transaction buffer pool composed of double transaction queues in the transaction transfer layer to separately process ART,I_DTT transactions within the domain and C_DTT transactions between domains.This transaction buffer pool working mode ensures that inter-domain transactions and intra-domain transactions are alternately chained.Due to the inevitable delay in the inter-domain transaction transfer process,the transaction buffer pool schedules the transaction queue based on the time stamp of inter-domain transactions.
3.3.3 Smart Contract Format
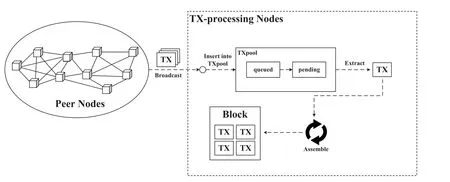
Figure6.BC-BLPM transaction pool structure.
The concept of a smart contract was first proposed by Nick Szabo [8]and was defined as a “transaction agreement for executing contract terms through computers”,that is,the contract was automatically executed by a code program.The essence of the smart contract is a computer algorithm that binds participants in the transaction processing platform with related transactions involved.In the blockchain,the smart contract refers to a program that can be automatically execute on the blockchain.It has the characteristics of programmability,atomicity,consistency,etc.The blockchain system can automatically execute the business logic of the blockchain by means of smart contracts packaged and deployed in its distributed nodes without the supervision of a third party.
In this work,smart contract is used as the policy execution carrier of the access control system,that is,the execution logic of BC-BLPM’s access control policy is written in the smart contract,and different operation interfaces are provided,so that the smart contract can perform corresponding policy according to different access requests.One thing to be clear is that the interfaces encapsulate the execution logic of state transition rules and are embedded in smart contracts to provide external calls to smart contracts.Any entity can perform access control policies in BC-BLPM by deploying and executing the smart contracts in the peer nodes of the blockchain system.The definition of a smart contract interface is:
•Initiate():This function is used to perform state initialization operations on the access domain and is executed by the system manager.
•Read_only(),Writeonly(),WriteRead():These 3 types of interfaces represent the execution phases of the read-only,write-only,and readwrite rules,respectively.The corresponding operations can be performed by inputting parameters such as subject and object information,and access requests.•Data_Sending():This function represents the execution phase of the data-transfer rule,and is also called by BC-BLPM according to the content of the access request.A data transfer operation for different objects is performed by inputting the access request of the subject,the identification information of the data-sending object and the datareceiving object.
IV.IMPLEMENTATION
The actual deployment architecture of BC-BLPM is shown in Figure7.This section describes the different interaction processes that BC-BLPM needs to complete during the deployment process.The interaction process can be divided into four phases:the initialization phase initializes the access domains by deploying smart contracts and CPK combination key suite;the access permission management phase completes access rights management for access-requesting users by executing the relevant policy interface of the smart contract;the data transfer phase implements the secure circulation of confidential data between the same domains or different domains;and the resource management phase provide convenience for the maintenance of resources.
4.1 Initialization
In the initialization phase,the system managerm ∈S∗as a trusted subject,needs to perform the operation of adding resource objects and deploying smart contracts to the access domainAccDomx,thus completing the instantiation of theAccDomx.The steps to perform are as follows:
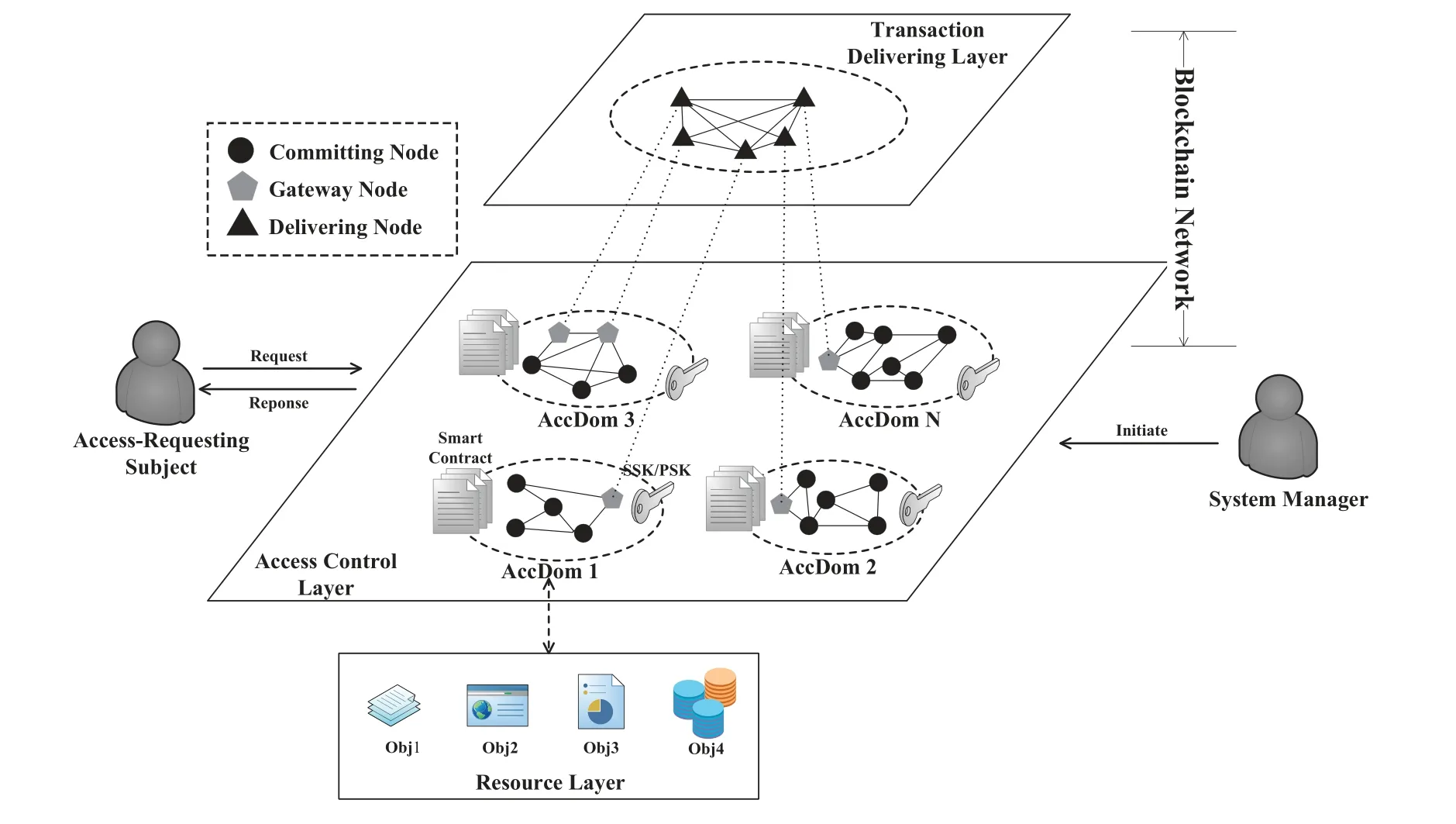
Figure7.Deployment architecture of BC-BLPM.
Step 1:The system managermspecifies an access domain identifierAccDomx.ID,and selects the resource objecto ∈Othat needs to join the access domain.
Step 2:Randomly generate N-level CPK public and private key seedsPSKAD/SSKADand deploy them in each access control domainAccDomx.
Step 3:Thenmencodes the smart contractSCand install it into the gateway node ofAccDomx,specifying the calling addressSC.Addrof the smart contract.
Step 4:As shown in Algorithm 1,by invoking theInitiate() interface of the smart contract,a founding blockGenesis_BlockofAccDomxis generated,which is responsible for defining the metadata of the access domain,and does not contain transactions such as ART or DTT in the block.InGenesis_Block,we need to add the signatureSig{Msg1,Msg2,...,Msgn}SKmwhich is generated by the private key ofm,N −levelCPK seed sequence{PSKAD/SSKAD}Nn=1,resource object identifieroj.ID,access domain identifierAccDom.ID,access control listACL,and current timestampTSto instantiate a new access domain.Note that theACLis a simplified first-order array containing access attribute elements,representing the“optional legal operation”,which plays the role of the access control matrixMijduring system execution(see Section 3.2(A)for the definition ofMij).

In Algorithm 1,it first needs to complete the definition of the resource object set and the access domain identification number,and package them together with the access control list and the signature of the manager to generate the proposal InitProp (as is shown in line 1 to 3).Then,through the execution of the consensus agreement,the decision result of the proposal from all nodes in the domain is obtained (see line 4 to 9);if the protocol is passed,the smart contract will generate theGenesisBlockand broadcast the event to the whole domain,otherwise will return an error message.Through the creation ofGenesisBlock,each node of the access domain will obtain the ledger copy of the blockchain,and will maintain the data integrity of the domain in the subsequent execution process.

?
4.2 Access Permissions Management
After the initialization of the system is completed,BCBLPM acts as an access permissions manager,provide access decision service for external access subjects.The process is as follows:Step 1:Before sending an access request to the access control domain,the subject first needs to download the CPK private key seed of the access control domain and generate a signature private key IDSK based on its own identification information.
Step 2:The subjectsi ∈Sissues an access requestAccReqto the gateway node in the access domain.
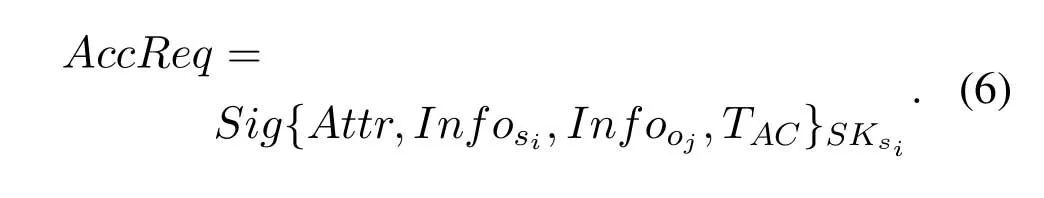
Attrrepresents access attributes,such as “readonly”,“write-only” or “read-write”,a single access request can only load one access attribute;Infosi={si.ID,
?
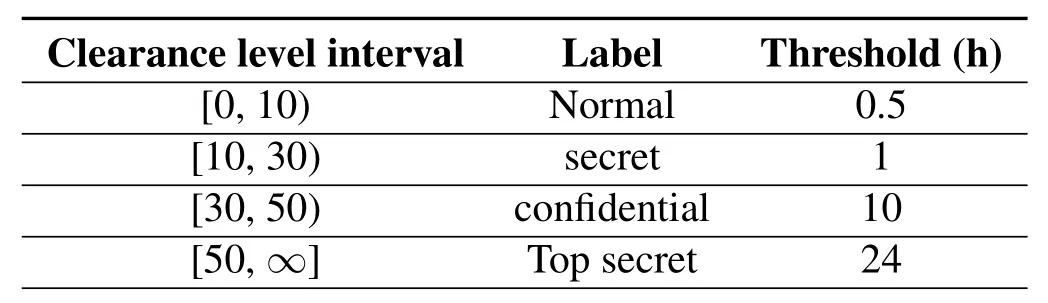
Table1.Correspondence between clearance level and access time.
Step 3:After receiving the access request,the gateway nodes first verify the correctness of signatureSig.If the verification fails,an error message is sent tosito end the interaction process.When the verification is passed,the gateway nodes broadcastAccReqto the remaining nodes in the access domain.
Step 4:After receiving the message,all the nodes in the domain extract the Attr element and call the policy interfaceRead_only(),Write_only() orWrite_Read()of the smart contract according to different access attribute values to get the decision result and send it back to the gateway node.Take theRead_only() interface as an example.Its implementation process is shown in Algorithm 2.It first defines the security level,determines the validity of the access attribute and the access request time (line 1 to 3),if the decision is passed,the result of the access requests will be obtained by the execution of the state transition ruleρr(lines 5 to 10).
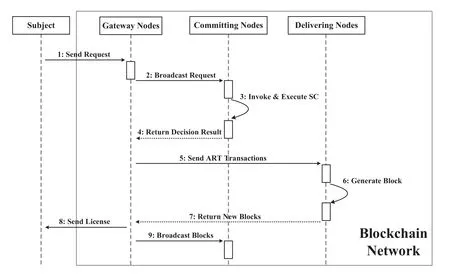
Figure8.Implementation process of access permissions management phase.
Step 5:The gateway nodes collect the proposal response and executes the consensus protocol.If passed,the AccReq and the decision result are packaged into an ART transaction and sent to the delivering nodes.
Step 6:The delivering nodes pack different types of transactions in a unit time into blocks,and return the blocks to the gateway nodes of the corresponding access domain.After receiving the block,the gateway nodes link the block into the public ledger of blockchain and synchronize the block to other nodes in the domain.
Step 7:Finally,the gateway nodes generate a temporary access tokenLicence(si,oj)and send it to the subject.Licence(si,oj)consists of the subject’s and object’s informationInfosiandInfooj,the access attributeAttr,the access time limitLCand the current timestampTS,and the signature of system manager is added as well.
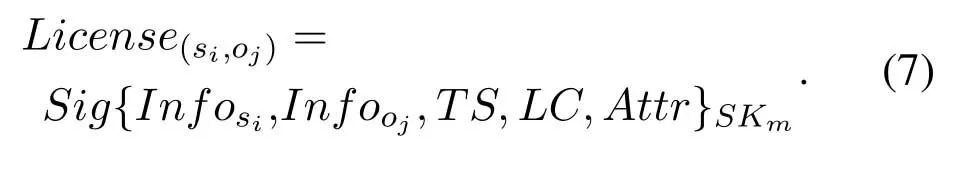
The implementation process of the access permissions management phase is shown in Figure8.
4.3 Data Transfer
During the access period,the subjectsi ∈ Smay transmit the data resources in the accessed object to other objects,thereby realizing data sharing between two different resource objects.The data transfer phase can be divided into intra-domain data transfer mode and inter-domain data transfer mode according to the different access domains involved.
4.3.1 Intra-domain Data Transfer Mode
In this mode,the subject sends the data resources in the accessed object to another resource object,and both of two objects are in the same access domain.Proceed as follows:
Step 1:The subjectsi ∈Screates a data transfer requestDataTransReqand sends it to the gateway nodes of the access domain where the objectojis located,WhereTS′represents the current timestamp,DataBufis a temporary“key-value”array that stores transferred data,the temporary access tokenLicence(si,oj)can be used as the identifier of the access period,Infookis the composition information of the data-receiving objectok,and finally,we need to add the signature ofsito the request.

?

Step 2:After receiving the request DataTransReq,the gateway nodes broadcast the request to the remaining nodes in the domain.This process is the same as step 2 of Section 4.2.All nodes in the access domain invoke the interfaceData_Sending()of the smart contract relying on the access attribute sd to get the decision result,and send it back to the gateway nodes.The invoking process ofDataSending() is shown in Algorithm 3.After the algorithm first completes the definition of the security level variables,it needs to determine whether the request time expires in the temporary license (line 1 to 3);if the request time is not expired,the decision result of the data transfer request will be obtained by executing the state transition ruleρsd(line 4 to 10).Finally,the decision result is returned.
Step 3:After receiving the decision result,the gateway nodes generate a transaction DTT and send it to the delivering nodes.The delivering nodes then package the transaction into a block and send it back to the access domain.
4.3.2 Inter-Domain Data Transfer Mode
In this mode,the subject sends data resources in the accessed object to another object belong to different access domain.The biggest difference between this phase and the inter-domain data transfer phase is that the block containing DTTs needs to be updated in the sidechains of the two different access domains.
The execution step 1-2 of the mode is the same as the corresponding step of the intra-domain data transfer mode.After the gateway nodes sendDTTto the delivering node,the delivering nodes need to determine theSObj_IDandRObjIDfields of theDTT.If the objects displayed in the two fields have different access domain identifiers,theDTTwill be packaged into two identical blocks,and the blocks are sent to different access domains according to the iden-tifiers in the fields.The two access domains finally perform an update operation of its respective public ledger after receiving the block.
The implementation process of the data transfer phase is shown in Figure9.
4.4 Resource Management
With the development of actual business,such as the adjustment of a business department in the government department or the change of business data,the resource management mode of BC-BLPM will also be adjusted accordingly.
4.4.1 Resource Addition and Revocation
The new resource objects may need to be added to the BC-BLPM along with the extension of the business logic,and the old need to be periodically cleared out.This process is performed by the system managerm ∈S∗.It is similar to the initialization phase that m needs to provide a new resource object setObj_SetNew or a set to be cleared Obj_SetRev,and generates a new block UpdateBlock by re-executing theInitiate()interface of the smart contractSC.The block is used to record the addition or undo behavior of the resource object.

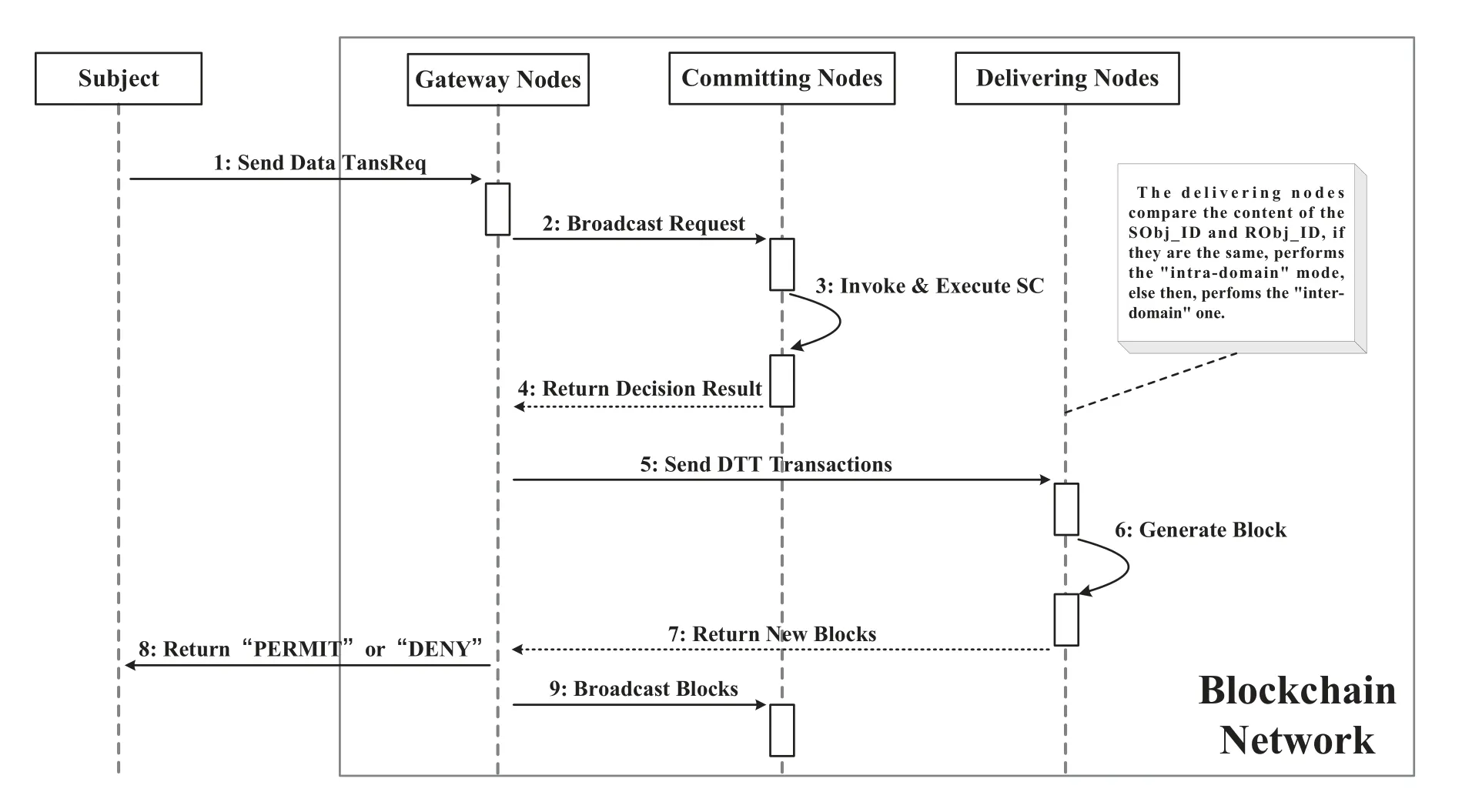
Figure9.Implementation process of access permissions management phase.
4.4.2 Node Revocation
When a node in the access domain is found to be maliciously attacked or invalidated,the system managerm ∈S∗can issue a null ART transaction (only fill in the node ID and the content of the “Node Identity Revocation” in theObj_ID and AccReq_Attrfields respectively)and record it separately in the sidechain of the access domain where the node is located to represent the revocation process of the node.
V.EXPERIMENT AND ANALYSIS
Here we set up a simple intranet environment and implemented the BC-BLPM prototype system based on Hyperledger Fabric V-1.1.0 [35].As an enterpriselevel permissioned blockchain infrastructure,Hyperledger Fabric provides PKI-based node and user authentication services,Gossip-based and gRPC-based distributed communication services,channel-based“multi-blockchain” services,and Chaincode-based smart contract encoding services,which are available for the functional requirements of the BC-BLPM infrastructure.We apply Channel to divide the access domain and encode the smart contracts based on Chaincode logic.On this basis,we separately evaluate the implementation effect and system performance of BC-BLPM,and analyzes the security of the model.In addition,the final part of this section compares our model with the existing multi-level security system,showing the similarities and differences between the BC-BLPM and the existing multi-level security model.
5.1 Experimental Environment
The experiment was carried out in 8 desktop computers configured with 3.40GHz Inter Core i5 CPU,8.00 GB memory and Ubuntu 16.04 OS.The computer set up virtual routing through the router to form a small intranet structure with multiple access domains.The experimental topology is shown in Figure10.Then we use the sandbox container tool Docker[36]to deploy virtual fabric nodes in each physical computer.The fabric node is divided into two roles:Peer and Orderer,where Peer is a common peer node responsible for generating and verifying transactions;Orderer is a transaction sorting and delivering node that is responsible for packaging transactions into blocks and distributing them to different Channels.We set VLAN 0 as the transaction delivering layer,deploy 4 virtual Orderers in the domain,and deploy the high-performance cluster data processing plugin Apache Kafka [37]to improve the efficiency of transaction sorting and delivering.The remaining VLANs are deployed single channel as separate access domains,that is,separate sidechains in each VLAN.
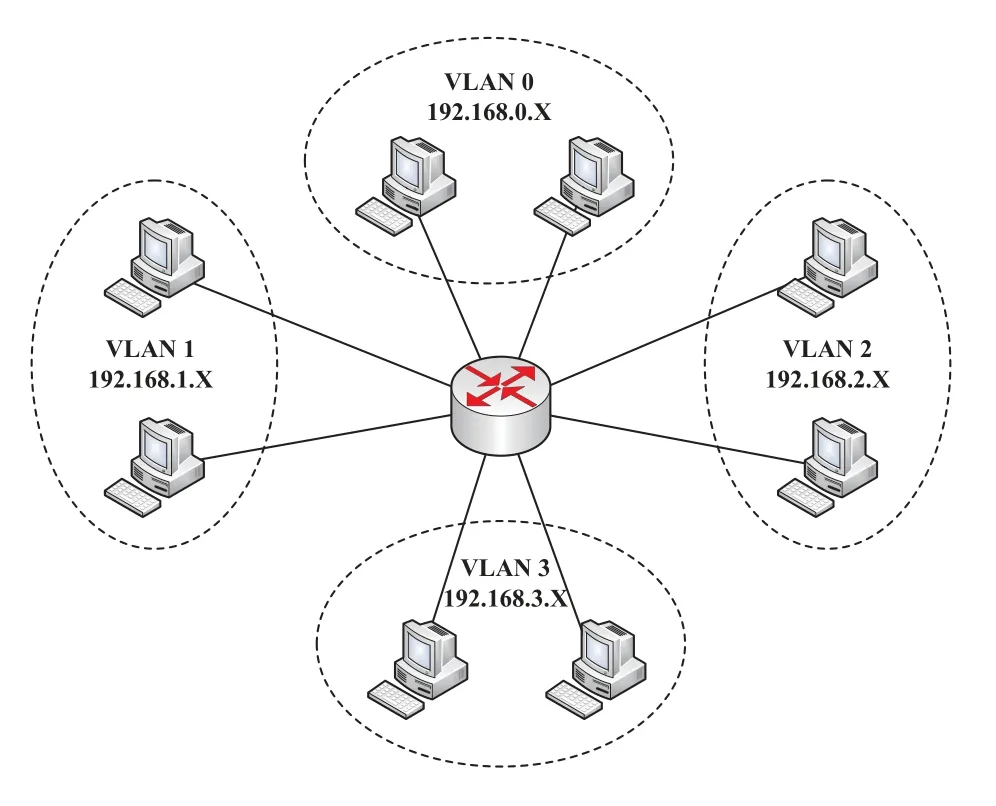
Figure10.Experimental topology.
The parameter settings of Fabric are shown in Table2.We specify that the average write-set length of each transaction is 20 bytes,each block contains 30 transactions,and the block size does not exceed 512 KB;Set the total capacity of the transaction pool to 1000TX(TX means transaction unit),in which“queued”queue is allocated 300TX and “pending” queue is allocated 700TX;GoLevelDB[38]is adopted as the blockchain state database for storing configuration information of blockchain ledgers in the local environment with multiple sidechains;the communication bandwidth between the nodes is 2 Gbps,and the communication link adopts the TLS security protocol;the consensus module adopts the PBFT protocol,that is,in each round of transactions execution,the number of honest nodes participating in transaction verification must be no less than 2/3 of the total number of nodes.
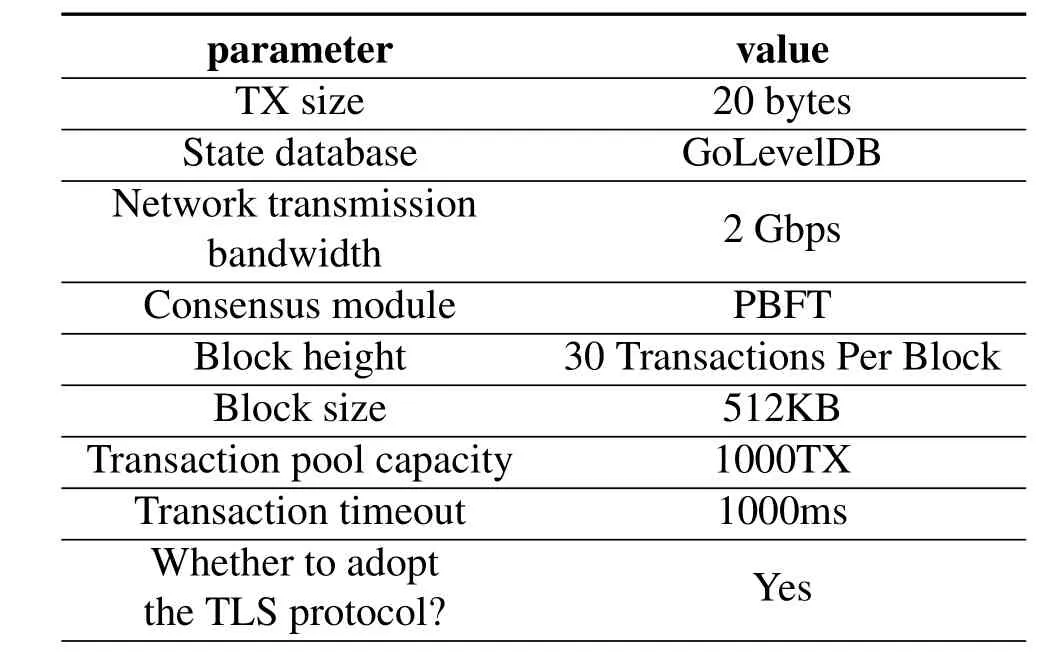
Table2.Parameter settings of Fabric.
We encode the policy execution interfaces required for BC-BLPM smart contracts through the Chaincode.As a smart contract paradigm for Fabric,Chaincode can be implemented in a variety of programming languages such as golang,java,node.js,etc.It is designed as a virtual container deployed in Docker,capable of communicating with Peer nodes via gRPC protocol,providing blockchain transaction logic based on the state machine model,and using the shim.ChaincodeStubInterface structure to achieve interaction with the blockchain ledgers.
In the experiment,we use the benchmark test tool Hyperledger-Caliper[39]to simulate the client nodes in the network and generate transaction requests to the blockchain network,each virtual client node plays the role of “external access-requesting subject”.A unified X.509 format certifi-cate is issued by the same certificate authority,and the subject clearance level is written to the “Extend” field of these certificates.The “resource object” is uniformly represented by a lightweight data file in the JSON format,and the security level label is represented by the unified key value of the file header“SecLevel-Value”.
We mainly examine the performance of BC-BLPM through the following indicators:
• Throughout:The number of transactions generated in the blockchain network per unit time,measured in units of TPS(Transactions Per Seconds).
• Latency:The time it takes for a message to be transmitted between nodes when a client completes a transactional interaction.We divide it into Average Latency (Avg Latency),Maximum Latency(Max Latency)and Minimum Latency(Min Latency).
• Hit ratio:The percentage of successfully generated transactions as a percentage of the total transaction requests.
5.2 Effectiveness Evaluation
In this experiment,we evaluate the execution results of different access control policies by setting different test cases.We set up two client nodes named Cli1 and Cli2,their current clearance levels are 3 and 2 respectively;three data files named Jfile1,Jfile2,and Jfile3 are set,and their security levels are 3,2,and 1 respectively.Jfile1 and Jfile2 are located in VLAN 1,and Jfile3 is located in VLAN 2.The resources and smart contracts are initialized in the two access domains respectively,whereACL=[r,a,w,sd]in VLAN 1 andACL=[r,a,sd]in VLAN 2.The security level satisfies the partial order relationship,e.g.3 ▷2 ▷1.
Through the data-flow API provided by Hyperledger-Caliper,5000 transaction request packets containing the same access attribute are sent for each group of experiments,and the sending rate is set to 50 TPS to check the execution effect of the policy.The experimental results are shown in Table3.
For the results of Table3,the Chaincode-based policies can automatically identify the request type and execute the corresponding blockchain transaction logic,and the hit ratio is generally above 85%.At the same time,the sd transaction across two access domains is significantly higher than the transaction in the same domain (as is shown in line 6,12,and 13),which is determined by the characteristics of the inter-domain data transfer mode.
5.3 Security Evaluation
Security as a basic evaluation indicator for an access control system is no exception in our model.BCBLPM requires a multi-level secure access control environment that requires the ability to withstand external or internal malicious attacks and data leakage.Therefore,we use the basic principle of information security level protection—CIA (i.e.,confidentiality,integrity,and availability) as an indicator of the security.Among them,confidentiality means that only authorized users can access data;integrity means that data cannot be tampered with and destroyed by illegal authorized entities during transmission;availability means that the access of data by legitimate users is not maliciously rejected.
5.3.1 Confidentiality
The access control policy of BC-BLPM is implemented by BLP-based security policy primitives.The policy based on the Bell-LaPadula model limits the flow of authority data,and can effectively prevent high-confidentiality data from flowing to users with low-confidentiality level.The security of the BCBLPM state transition rule needs to be verified,thus ensuring the overall confidentiality of the system.
Proof.Rule 1 maintains secure
Assuming that the initial statev=(b,M,f) is secure,when the access requestRk=(si,oj,r) is executed,the new state isv∗=vorv∗=(b∗,M,f∗).Ifv∗=v,the statev∗maintains secure because of the security ofv.Ifv∗=(b∗,M,f∗):v∗−v=((s,o,r),M,f∗)wheref∗=f ∪{max(fc(s),f(o))}andfs(si) ▷f(oi),so thatv∗−vsatisfies the simple-security property.Since v also satisfies simplesecurity property,v∗satisfies simple-security property.Sincef∗−f=max(fc(s),f(o)),where(f∗−f)▷f(o),sov∗satisfies the∗-property.From the above,we prove the security of Rule 1.
Proof.Rule 2 maintains secure
Assuming that the initial statev=(b,M,f) is secure,when the access requestRk=(si,oj,a)is completed,the new state isv∗=vorv∗=(b∗,M,f).Ifv∗=v,the statev∗maintains secure because of the security ofv.Ifv∗=(b∗,M,f):v∗−v=((s,o,a),M,f),wherefs(si)▷f(oi),so thatv∗−v
satisfies the simple-security property.Sincevalso satisfies simple-security property,v∗satisfies simplesecurity property.Sincefc(si)▷f(ok)in Rule 2,v∗−vsatisfies the∗-property.And sincevalso satisfies the∗-property,v∗satisfies the∗-property.From the above,we prove the security of Rule 2.
Proof.Rule 3 maintains secure
Assuming that the initial statev=(b,M,f) is secure,when the access requestRk=(si,oj,w)is executed,the new state isv∗=vorv∗=(b∗,M,f∗).Ifv∗=v,the statev∗maintains secure because of the security ofv.Ifv∗=(b∗,M,f∗):v∗−v=((s,o,w),M,f∗),wheref∗=f ∪{f(o)}andfs(si) ▷f(oi),so thatv∗−vsatisfies the simple-security property.Sincevalso satisfies simplesecurity property,thenv∗satisfies simple-security property.Sincef∗−f=f(o),thenv∗−vsatisfies the∗-property.Since v also satisfies the∗-property,v∗satisfies the∗-property.From the above,we prove the security of Rule 3.
Proof.Rule 4 maintains secure
Assuming that the initial statev=(b,M,f) is secure,when the access requestRk=(si,oj,ok,sd)is executed,the new state isv∗=vorv∗=(b∗,M,f∗).Ifv∗=v,the statev∗maintains secure because ofthe security ofv.Ifv∗=(b∗,M,f∗):v∗−v=((si,oj,ok,sd),M,f∗),wheref∗=f ∪{f(ok)}andfs(si)▷f(ok),thenv∗−vsatisfies the simple-security property.Sincevalso satisfies simple-security property,v∗satisfies simple-security property.Sincef∗−f=f(ok),wheref(ok)▷f(oj),v∗−vsatisfies the∗-property and data-flow property.Sincevalso satisfies the∗-property and data-flow property,v∗satisfies the∗-property and data-flow property.From the above,we prove the security of Rule 4.
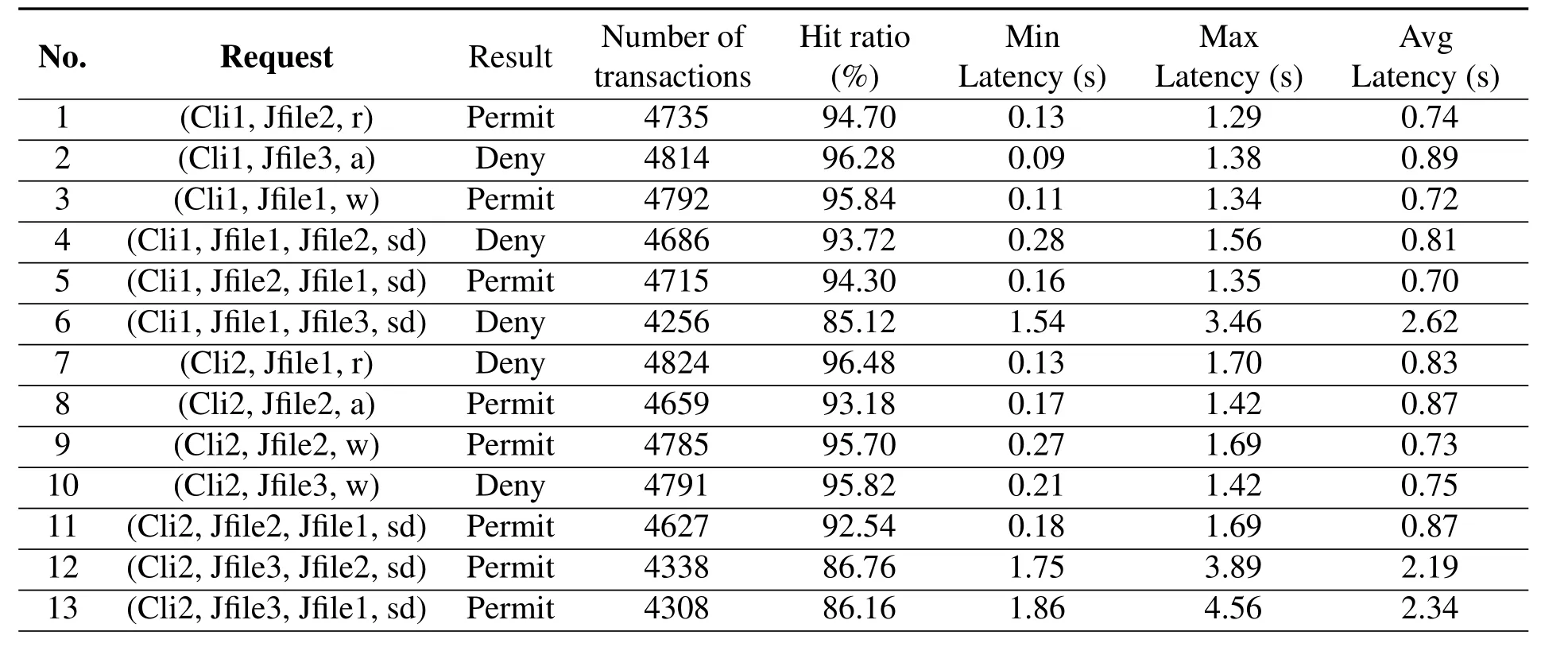
Table3.Execution results of different access control policies.
5.3.2 Integrity
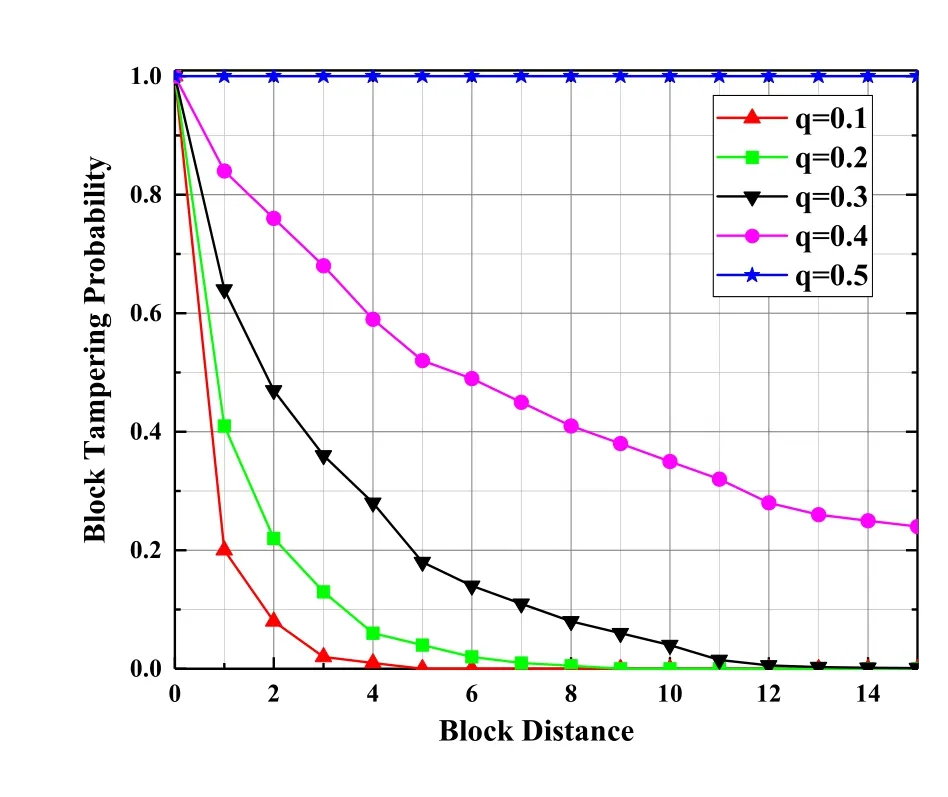
In the blockchain system,the blocks are linked to the end of the ledger in a time-sequential sequence by time stamping,and they are connected to each other by Hash values.BC-BLPM uses the blockchain to store the access records of the access-requesting subject.Each time a subject completes the access process in a specific access domain(i.e.,each time a smart contract is executed),a new data block is linked in the blockchain maintained by the domain.
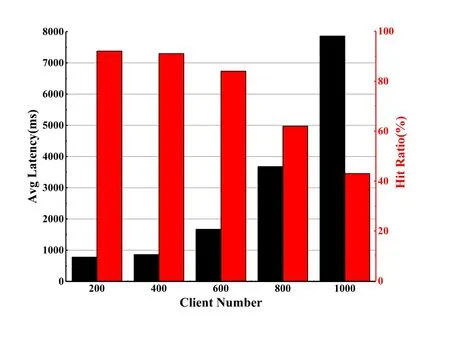
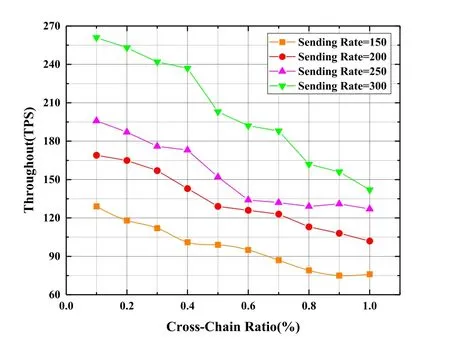
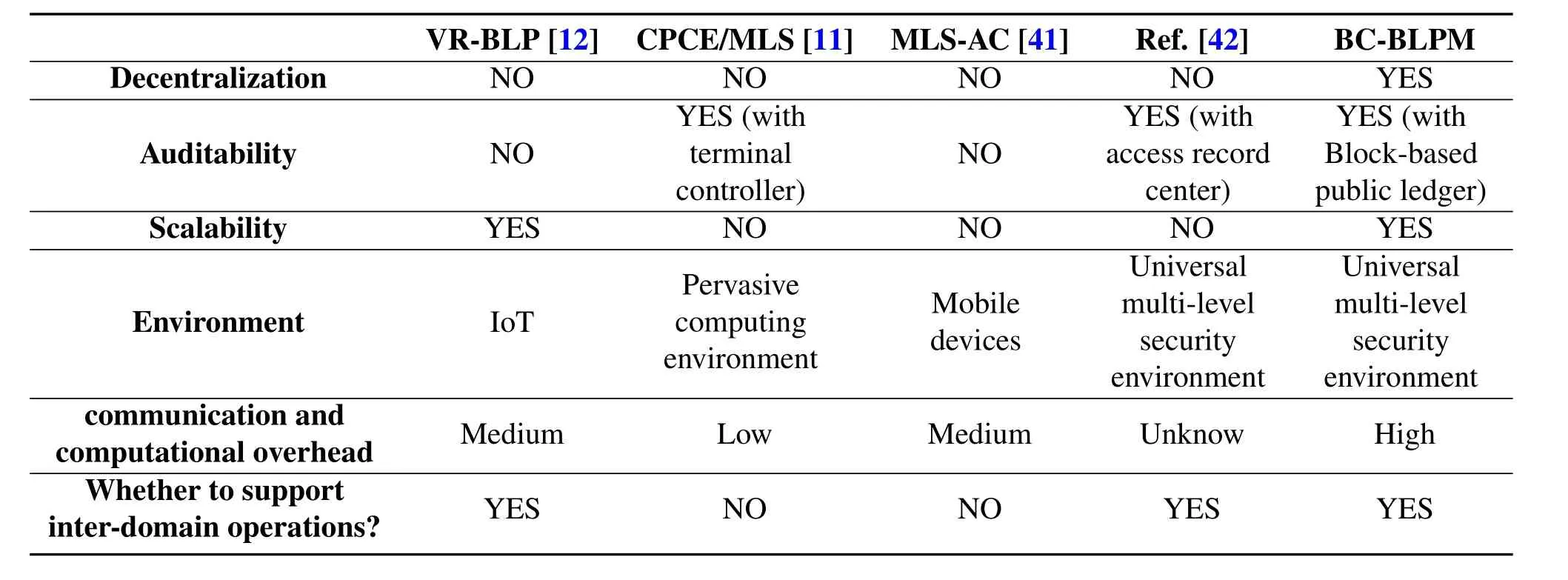
Since each block has a Hash value containing the complete block volume data and the PreHash value of the pre-order block,if an attacker illegally tampers with the data in a single block,it will cause the Hash value to change,so that the attacker must continue to change the pre-order Hash value of the block.And due to the full redundancy backup feature of the blockchain data,tampered blocks must be broadcast to the entire network nodes to make it effectively.After receiving the new blocks,these nodes will be able to detect that the block is invalid by traversing its own blockchain data backup,thus resisting forgery.In this way,the attacker must invade all distributed nodes that maintain the blockchain and continue to repeat the tampering process of the block data,which will greatly increase the cost of the attack.According to the analysis in Ref.[40],the probability of changing the content of a block in the blockchain is:assume that n is the number of blocks that the honest node finds during the average time(i.e.,the execution time of the consensus protocol),lis the number of blocks found by an external malicious attacker during that time.The competitive relationship between honest nodes and malicious attackers is a binomial random walk process,wherelis a negative binomial variable,equivalent to the generation process of n blocks(blocks discovered by honest nodes).The number of successfully generated blocks(generated by the attacker)whose success rate is set toq.Assuming that the probability of an honest node acquiring the next block isp,andq In summary,whennis 2,the tampering rate is less than 10%;whennis 4,the change tampering rate is less than 1%;nis 6 is lower than 0.1%.Therefore,as long as the length of the blockchain continues to grow,the tamper resistance of the blockchain will become stronger.In addition,since the data on the blockchain is publicly visible to all subjects,the access result is recorded on the blockchain,so that the policy is made public and transparent,and it is convenient for the third-party authorities to verify and audit the access records. The relationship between the probability that the attacker successfully tampered with the blockρaand the distancenof the block changes as shown in Figure11.Increase and gradually decrease.Conversely,when the probability that the attacker obtains ownership of the next node is greater than or equal to 0.5,the attacker can successfully tamper with the next block.That is to say,only when the attacker obtains more than 50%of the nodes on the blockchain can he control the data trend of the entire blockchain.Because there are many nodes in the blockchain,an attacker who wants to fully control 50%of the entire network will have to pay a huge cost,so it is difficult to break through,so a blockchain with a certain chain length can achieve very good anti-attack effects.In addition,in addition to the transaction signature TX Sig verification of the user identity in the BC-BLPM transaction,the CPK signature value of the subject also provides a verification mechanism for the integrity of the subject identification information for the BC-BLPM transaction.The implementation of the CPK signature mechanism relies on a new key pair generated based on the identity hash.The generation of this key pair needs to strictly meet anti-collision requirements,that is,different identity identification information hash generates different key pairs.The following is the proof of anti-collision of CPK seed key sequence selection: Figure11.Attacker’s probability of success. Proof.CPK seed key sequence selection has anticollision characteristics In the CPK system,the user ID first obtains a fixedlength hash value through a hash function,and then applies the row mapping algorithm to the hash value,and finally obtains the row coordinate selection sequence of the required length.At this time,the sequenceSis selected.The length islen×k.Suppose the length of the user identification islenIDbits,the block length of the block cipherEwith the encryption keyKislenBbits,and the length of the required sequenceSof the key islenSbits.Since the length of the user ID islenID,the size of the public and private key space must reach at least 2(lenID).Therefore,it is reasonable to limitlenID (a) WhenlenID ≤ lenB,because oflenB |lenS,solenB ≤ lenS,calculateMAPi+1=E(MAPi+1,K)(i=0,1,...,lenS/lenB −1),the output sequenceS=MAP0‖ MAP1‖ ··· ‖MAPlenS/lenB−1. (b) WhenlenID >lenB,by filling the user ID with 0 bits tolenID/lenB× lenBbits,you can get differentlenID/lenBGroupID0,ID1,...,ID(lenID/lenB−1),of whichIDi(i=0,1,...,lenID/lenB−1) The length islenB,calculateMAPi+1=E(MAPi+1,K)(i=0,1,...,lenID/lenB−1),the output sequenceS=MAP0‖ MAP1‖ ··· ‖ MAPlenID/lenB−1;iflenID/lenB The above two output results completely avoid the collision caused by intercepting the intermediate sequence to generate the sequence S that is ultimately required. 5.3.3 Availability Many malicious attacks from outside or inside can restrict the availability of access control systems,such as denial of service (DoS) attacks,content tampering attacks,identity spoofing attacks,deleting attacks,and replay attacks,etc.The decentralized and anti-forgery features of the blockchain are significant for defending against content tampering attacks,identity spoofing attacks,and deleting attacks.Therefore,we mainly analyze the ability to resist DoS attacks and anti-replay attacks. In a replay attack,an attacker may attempt to spoof the object by intercepting the message sent by the subject to the object and sending it to the object again.BC-BLPM acts as an intermediary for message interaction between the subject and the object.After the completion of an interaction process,the blockchain network can perform distributed verification on the legitimacy of the message.Any duplicate message will not be verified by the honest nodes.In addition,all verification processes will be publicly and transparently recorded in the blockchain,and anyone can detect duplicate illegal messages by verifying the information in the records. In a DoS attack,an attacker may attempt to consume the resources of the victim by brute force means(such as a botnet attack),preventing legitimate subjects from accessing resources and requesting services.In BCBLPM,an adversary can initiate a DoS attack in two ways:1) the visitor sends a malicious access request to a device that exceeds its access rights;2) the visitor sends a large number of false access requests to the system.Since the BC-BLPM needs to execute the smart contract implemented according to the multilevel security access control policy to output the decision result for the access request,the first attack mode cannot afford effect.In the second mode,since the visitor needs to submit the access time variableTACin the access request,our model will judge the variable according to the access time threshold corresponding to the clearance level of the subject.Once the threshold is exceeded,the access request will be discarded,which greatly reduce the possibility of DoS attacks. As a blockchain-based implementation,the performance of BC-BLPM may be limited by the number of nodes,secure transport protocols,transaction request rates,concurrency rates,and inter-domain transactions,etc.Here we set the above parameters to study the effect of the relationship between the various parameters on the performance of BC-BLPM. Figure12 shows the impact of different number of nodes on system throughput.We first set up a test case containing a single client node and multiple nodes,using Hyperledger-Caliper to provide 5000 transaction request packets (such as “read-only” access requests)for the prototype system,and test the variation trends of system throughput for different node counts.It can be obtained from the experimental results that as the number of nodes increases,the system throughput generally shows an upward trend.On the other hand,from the perspective of transaction consistency check,the increase in the number of nodes means that the number of participating nodes in each round of consensus increases.Taking the PBFT protocol as an example,the access domain consisting of 9 nodes requires at least 7 honest nodes to participate in transaction verifying,while 24 nodes require at least 17 honest nodes.This change decentralizes the transaction verification process at the expense of the efficiency of the system operation,effectively avoids the problem of single point failure,and improves the fault tolerance of transaction verification. Figure12.System throughput changes under different node counts. In the actual operation of our prototype,a common scenario is that multiple client nodes issue access requests to network resources in parallel.Here we establish a 9-nodes access domain,and provide 5000 clientwide transaction request packets for each client.The experimental results are shown in Figure13 and Figure14.Among them,Figure10 shows the trend of the throughput of different transaction flow rates with the increase of the client nodes.In this scenario,the output of each set of experiments reaches the maximum value in the interval of input 10 to 100 respectively,and the input range of 800 to 1000 shows a downward trend.It can be seen from the results of Figure12 that as the number of concurrent requests of the client increases,the system delay and the transaction hit ratio also change,and the peak value is reached when the number of client nodes is equal to 1000,which directly leads to the deterioration of the system throughput. Figure13.System throughput changes under different client numbers. Figure14.System average latency and transaction hit ratio change under different client numbers. The data transfer process across different access control domains undoubtedly have an impact on the performance of our prototype.We demonstrate this effect through a simple experimental scenario:setting up 1 client node and 2 different access domains with 9 nodes each,providing 5000 access transaction request packets for each client.In addition,on the basis of keeping the total number of transaction requests unchanged,different proportions of inter-domain data transfer requests are randomly inserted.The experimental results are shown in Figure15.It can be seen that under the premise of the transaction sending rate unchanged,as the proportion of inter-domain transactions increases,the overall system throughput drops significantly.This is because the delivering nodes additionally generate a transaction block for the target domain when processing the cross-domain transaction.Assuming that the transmission distance from the delivering nodes to the gateway nodes of different access domains are equal,which results in the necessity for two access domains to perform the correctness verification of the block almost simultaneously.This incurs additional time overhead. Figure15.System throughput changes under different inter-domain(cross-chain)Transaction ratios. The experimental results show that the performance indicators of BC-BLPM are limited by the number of nodes,transaction request rate,transaction concurrency rate and cross-domain transactions.Therefore,in the actual production environment,it is necessary to comprehensively consider the above factors according to the actual system construction requirements,such as increasing the trustworthiness of transaction verification by increasing the number of nodes in the access domain,or improving the system throughput by controlling the request rate and the number of concurrentinteractions. Table4.Scheme comparison. In some high-confidence scenarios,especially in government departments and enterprises that put information security issues first,multi-level security issues have been the focus of researchers’ attention.BCBLPM is a multi-level secure access control model using blockchain technology,which has the advantages of decentralization,auditability and scalability.By comparing with the researches of the MLS system in recent years,the comparison results are shown in Table4.It can be seen that compared with the non-decentralized MLS system,the biggest advantage of the proposed architecture is that it can be audited through distributed deployment and blockchain-based management.Although there are disadvantages in commu-nication and computational overhead (interdomain data transfer,multi-client transaction request and other operations generate additional time overhead,affecting the system throughput),the characteristics of decentralization determine that the architecture can provide reliable MLS-based access control services in an untrusted network environment,which is critical for multi-level security systems. We focus on the centralized single-point failure problem of traditional MLS systems,combine BLP-based security policy primitives and blockchain technology,propose a blockchain-based multi-level security access control model BC-BLPM and implement decentralized multi-level secure mechanism.Based on the principle of confidentiality,integrity and availability of multi-level security,the model further introduces attributes such as auditability and scalability.We use“multi-blockchain”architecture to divide the network into different access domains,so that the resource objects of different organization or departments are logically isolated from each other,improving the efficiency of resource maintenance.Besides,the integrity of the data stored in sidechains is maintained by all nodes in the domain and cross-domain data interaction is permitted.The BLP-based access control policy execution interface is designed by using blockchain smart contract,so that any access-requesting subject must automatically and forcibly execute the policy,thereby further improving resource security.The experimental and analytical results show that the model has high reliability in terms of execution performance and system performance,and has the ability to deploy in the actual production environment.In the future,we consider studying the dynamic adjustment of the security label to further enhance the security and flexibility of our model.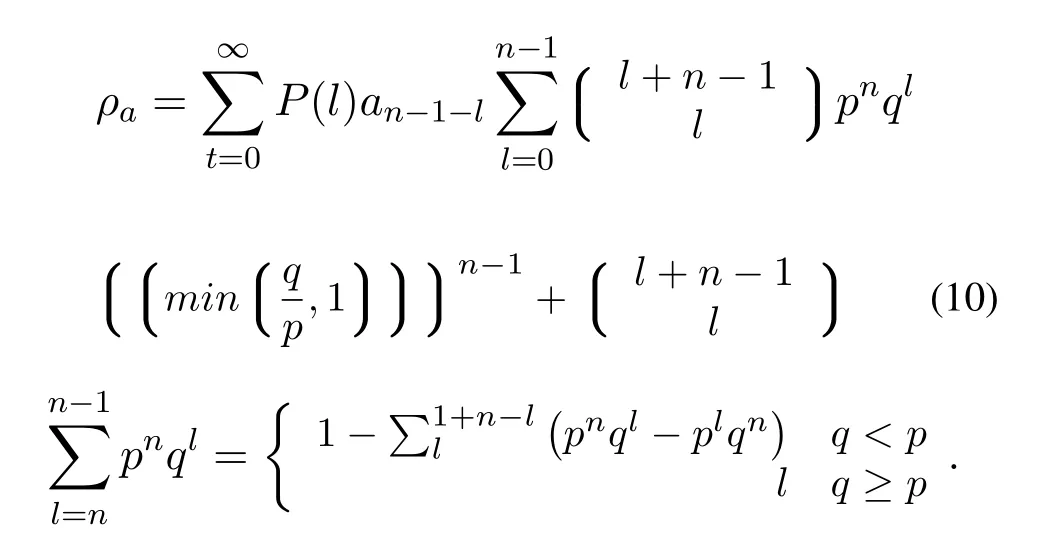
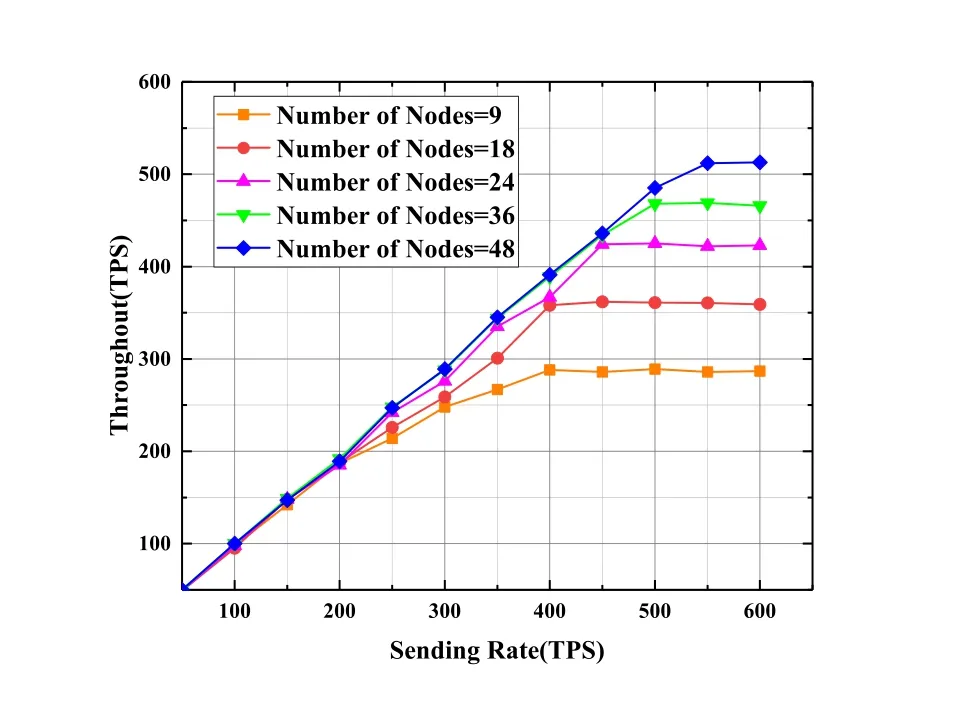
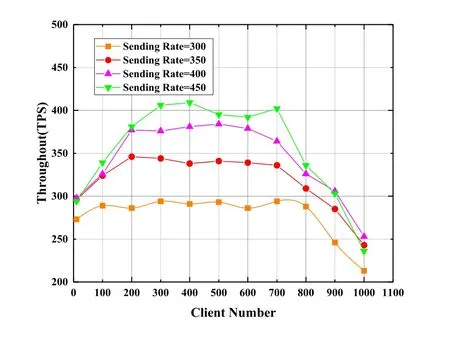
5.4 Performance Evaluation
5.5 Comparison with Existing Schemes
VI.CONCLUSION

