Research on construction of operation architecture based on complex network
You Chen ,Xing Wang ,Yuan-zhi Yang ,*,Cheng-wei Ruan ,Yi-peng Zhou
a Xidian University,Xi'an,Shaanxi,China
b Aeronautics Engineering College,Air Force Engineering University,Xi'an,Shaanxi,China
c 95910 Army,Jiuquan,Gansu,China
Keywords:Operation architecture Network centric warfare Topology Complex network
ABSTRACT Operation architecture plays a more important role in Network Centric Warfare(NCW),which involves dynamic operation networks with complex properties.Thus,it is essential to investigate the operation architecture under the informatization condition within NCW and find a proper network construction method to efficiently coordinate various functional modules on a particular situation,i.e.,the aerial combat.A new method integrating the physical level and functional level of NCW is proposed to establish the operation architecture,where the concept of network operation constraints unit and net constructing mechanisms are employed to avoid conflicts among different platforms.Meanwhile,we conduct simulations to assess the effectiveness and feasibility of the constructed operation architecture and analyze the influence of the network parameters.©2020 China Ordnance Society.Production and hosting by Elsevier B.V.on behalf of KeAi Communications Co.This is an open access article under the CC BY-NC-ND license(http://creativecommons.org/licenses/by-nc-nd/4.0/).
1.Introduction
As the main tool to describe complex systems,complex networks have been widely used in various fields in recent year,such as airline lines[1,2],power grids[3,4],social networks[5,6],biological networks[7,8]and ecological networks[9-11].With the development of information technology,networked warfare has become the basic mode of future warfare,which connects command&control(C2)network,sensor network and weapon network into a unified whole to realize unified command and situation sharing on the battle field.Operation architecture provides structural support for the technical application of networked warfare.
Although the extended application of complex network around the world can describe the long-term development of the field,there are few researches on the application of complex network in the military field.Weixin Jin[12]studied the system-of-systems antagonism model of networked warfare,gave the basic method of constructing combat network,and confirmed the distribution law of network nodes.Dongfeng Tan[13]proposed a new network based on the assumption of random combat,aiming at the problem that the classic Lanchester combat model could not clearly describe the local engagement relationship between the combat units in the battle.Anthony H Dekker[14,15]studied the construction and important technologies of Network Centric Warfare(NCW)with complex networks.Hunkar Toyoglu[16]proposed a novel threelayer commodity-flow location routing formulation and designed the distribution system in consecutive time periods for the entire combat duration.Shoulin Shen[17]studied the general structure of combat network and discussed the method of measuring network effect by using adjacency matrix.Qiang Zhang[18]constructed a multi-dimensions weighted operational network model to assess the influence of combat organizational structure on operational effectiveness dynamically.Mingke Zhang[19]added two assumptions(classification of nodes and changes of the attachment)and presented a topology model of the complex networks in network centric warfare based on BA model.Jinjun Li[20]established the network description model and characteristic parameter measurement index of the operational command architecture,and analyzed the influence law of the change of command span,command level and command mode on the overall characteristics of the command architecture.
Up to now,the researches about combat system with complex network have penetrated in many academic fields and the conclusions resulted from the researches are leading to a new solution towards the Network Centric Warfare(NCW)[21].NCW system,which contains many independent subsystems and key factors,is a dynamic evolving system in which the nodes and edges may change through different time-steps according to the continuously changing combat situations.And the interrelationships among different subsystems are more complex than any other system.Thus,we cannot use a static model to describe NCW system.In this paper,we consider the NCW system as a self-organized evolving system,and put forward one of the possible operation architecture models.We establish an operation architecture including C2 net,target detecting net,weapon launch net and communication net,which can break the limitation between single platform and realize the collaboration between nodes in different platforms.Besides,we propose some constraint rules and operators to describe the model in a concrete mathematical language.And the simulation results verify the effectiveness and feasibility of operation architecture.
The rest of the paper is organized as follow s:1)The NCW features associated with complex network and operation architecture model are analyzed in Section 2.2)The method to construct operation architecture in topology field is put forward in Section 3 to shape the NCW system.3)In Section 4,the specific steps of operation architecture construction are presented and the generalized operation loop is defined to evaluate the performance of operation architecture.4)Simulation and analysis are presented in Section 5.5)Finally,Section 6 concludes the paper.
2.Operation architecture analysis
2.1.Basic concept of operation architecture
In Network Centric Warfare,the operation architecture can be regarded as a complex network with different kinds of abstract functional nodes such as weapon,sensor,C2 and communication from the topology field.This special complex network mainly works with the circulation of the information,materials and energy among combat entities,and the organization of operation architecture changes all the time according to the combat situation.From this view,we can suppose that the operation architecture also contains the characters of several classic complex networks.
2.2.Operation architecture characters
The connection and operation rules of NCW can be described as“4D-4G-1L”mode which means.
4D:Physical Domain,Information Domain,Cognitive Domain and Society Domain,which represent the structure of NCW,flow of information, information processing and cooperativity,respectively.
4G:Information Grid,Sensor Grid,Shooter Grid and C2 Grid.
1L:OODA Loop.
On the basis of this mode,we need to apply the relative solutions of complex network to operation architecture.The distributed nodes in physical level should be transformed into a united system in functional level and we need to define some net organizing constraints to complete this transformation.The process can be seen in Fig.1.
The left side of Fig.1 describes the operation architecture in physical level,and the right side reflects the operation architecture in functional level.The net organizing constraints which contain constraint rules and constraint operators are defined based on the characters of complex network.We use the NOC(Net Organizing Constraints,a basic combat unit which contains four functional nodes and some constraint elements)units to realize the net organizing function and try to find a proper net organizing method.According to the characters of each kind of the functional nodes,we rebuild the operation architecture and the detailed description is given in the following chapters.
2.3.Operation architecture model
Traditional structure of distributed combat system is built based on the basic combat unit which is regarded as an agent that can execute a whole combat task(including sub-tasks such as:searching,targeting,tracking,weapon launching and so on)by itself.In this paper,we propose a new structure to improve the whole task utility.The basic unit of operation architecture is defined as a functional node which can realize its specific sub-task,and these units may belong to different platforms.The structure of distributed combat system,shown in Fig.2,can realize the separation of sub-system function in space domain,the single combat unit is divided into several functional parts to set them free,then the distributed nodes with outstanding specific performance are connected by a communication net to build a strong union combat system.
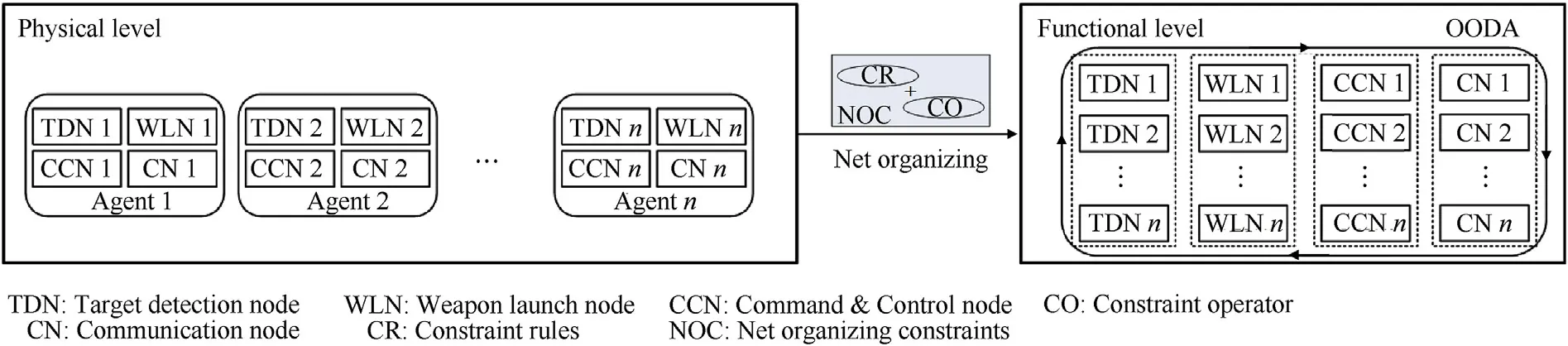
Fig.1.Operation architecture in physical and functional level.
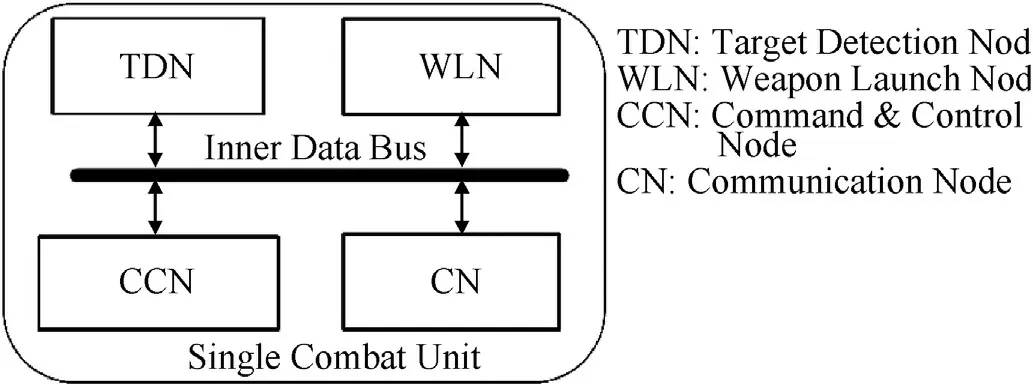
Fig.2.Basic combat unit with nodes in operation architecture.
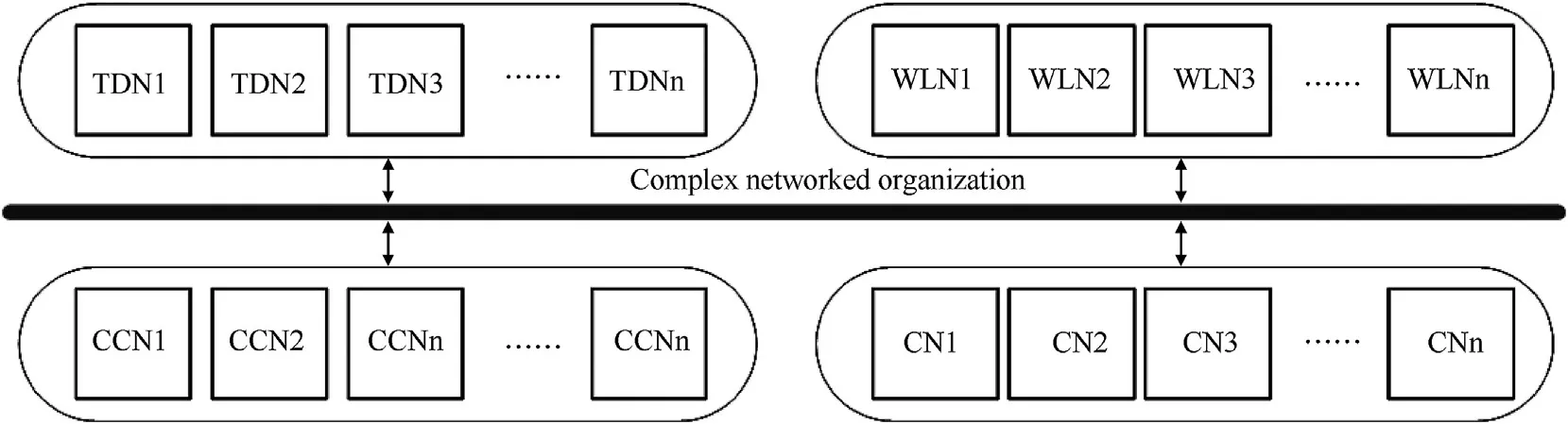
Fig.3.Operation architecture model.
As we can see in Fig.2,the basic combat unit,widely used in many distributed combat system today,consists of four functional nodes and an inner data bus.These four functional nodes can work in sequence to complete a whole combat task.This structure can be useful under the situation with fewer tasks,if there are more basic units,we should coordinate both the relationships between basic combat units and the relationships among different nodes in a basic unit.The complex combat task with many basic combat units may bring a lot of conflicts in space and time domain.In order to get a more flexible mechanism,we propose an operation architecture seen in Fig.3.The combined but free TDNs and CCNs can work together to build a full-dimension target detecting net,the WLNs and CNs can also work together to construct a more efficient shooting net,this model is called operation architecture.
Fig.3 shows the operation architecture model of distributed operations which is constructed by four different parts
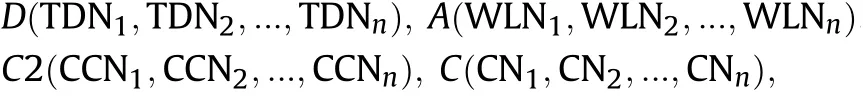
and every functional node has all the shared information,so the nodes can exchange their roles at any time within the setting constraints,and we consider the network of operation architecture undirected.Every part contains the same kind of functional nodes,but node with the same function may have different attributes and characters.
3.Constraints model
3.1.Constraint rules
When constructing operation architecture,we need to describe the model in a concrete mathematical language and some constraint rules are very important in NOC unit.We use the graph G(V,E) to depict the operation architecture,where V={v1,v2,...,vS}and E={e1,e2,...,eT}are the sets of nodes and edges,respectively.And each edge ei(i=1,2,…,T)can find two relative nodes(vj,vk).GD,GW,GC2,GCcan be respectively denoted as the non-empty finite sets of target detection entity,weapon launch entity,command&control entity and communication entity.
Definition 1 C2 network
We define C2 network as
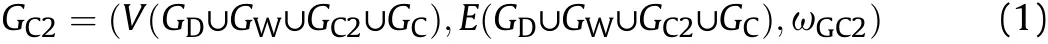
where ωGC2represents the command&control enabling relationships and it describes the relationships between the elements in set V and set E.For example,if(x,y)∈ωGC2,then there exists a connection edge between x and y.And ωGC2should obey the following conditions:
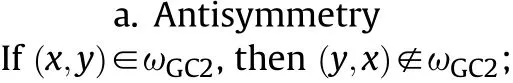
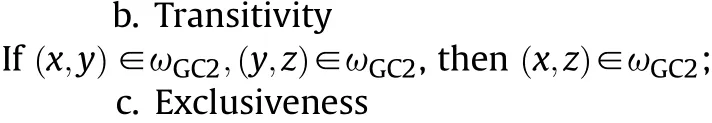
If y∈GD∪GW∪GC2∪GCand∃x∈GC2,then(x,y)∈ωGC2(when y∈GC2,y≠x,(x,y)∈ωGC2).
Definition 2 Target detection network
The target detection network is denoted as
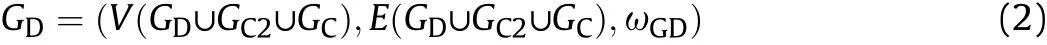
where ωGDrepresents the detection and C2 enabling relationships and it makes the elements in E match the elements in V.The constraints of ωGDare listed as follows:
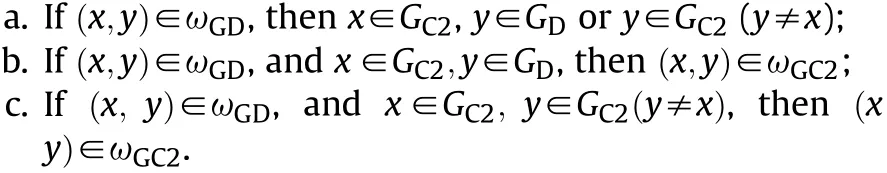
Definition 3 Weapon launch network
We also define the weapon launch network as
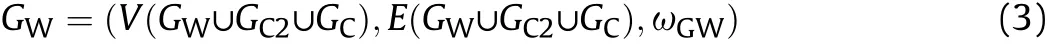
where ωGWis the weapon launching and C2 enabling relationships and it makes the elements in E match the elements in V.It also needs to satisfy the following conditions:

Definition 4 Communication network
GC=(V(GC),E(GC),ωGC)is the symbol of communication network,where ωGCis the communication and C2 enabling relationships and it makes the elements in E match the elements in V.It also needs to satisfy the following conditions:
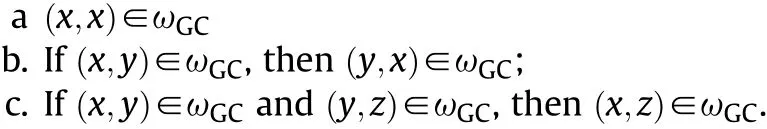
Definition 5 Operation architecture
Similarly,we define the operation architecture as
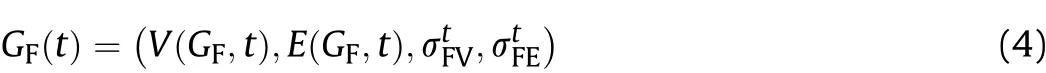
4 V(GF,t)=
5 E(GF,t)=E(GF,t-1));
6 GF(0)=(V(GF,0),E(GF,0),is the initial status of operation architecture.
3.2.Constraint operators
When the constraint rules are given,some operators are required to execute them.And the constraint operators are the execution part of NOC unit which play an important role in network construction.The operators are then given to describe the generating graph and they are listed as follows:
a.Let W be the set of x,and the definition del(x,W)=W∩﹁{x}denotes deleting an element from W.
c.If x,y∈V(GF,t),then define σtFE=edge_linking(x,y),
d e∈E(GF,t+1)=E(GF,t)∪{e}and GF(t+1)=(V(GF,t),E(GF,t+1),).Besides,edge linking(x,y)is defined as the connection of two elements.
e.If x,y∈V(GF,t)and e=(x,y)∈E(GF,t),then defineedge_deleting(x,y),E(GF,t+1)=E(GF,t)∩﹁{e}and GF(t+1)=(V(GF,t),E(GF,t+1),.We also define edge deleting(x,y)as the disconnection of two elements.
4.Operation architecture construction
4.1.Steps to construct operation architecture
The constraint rules and operators are put forward,then we need to describe the topology graph of operation architecture which contains C2 net,D&W(Detection&Weapon)net and C(communication)net.Different kinds of nets have their ow n special rules,and we can see the general topology graph in Fig.4.
From Fig.4,we can see that different kinds of operation nets should combine together with strict rules.The right side is the hierarchical structure of C2 net and the left side is the combat execution unit which contains detection and weapon nodes.In the left side,D&W nodes and C2 nodes are denoted as black circle and black rectangle,respectively.There is relationship denoted as N∝eKlbetween D&W nodes and C2 nodes,where N is the number of D&W nodes,l is the level of C2 net,K is a constant.
a.C2 net construction
C2 net owns some nodes which act as commander in the whole network.The information flow should correspond to the real situation.Here,we give a simple example of the structure of C2 net in Fig.5.We can easily find that C2 net is built in the form of tree diagram where the root node is the command center with the highest priority.
b.D&W net construction
From that moment nothing was the same for Steve. Life at home remained the same, but life still changed. He discovered that not only could he learn, but he was good at it!
D&W nodes represent task execution units,which are directly connected with C2 nodes in priority order to form a command and control relationship.The typical example of D&W net is shown in Fig.6.D&W nodes are described as the terminal execution units in operation architecture,they are directly connected to C2 nodes with different priorities.
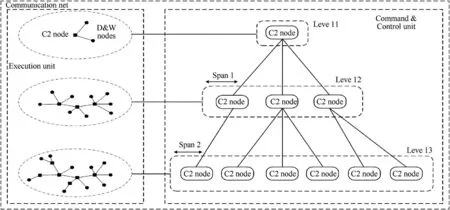
Fig.4.Operation architecture constructing description.
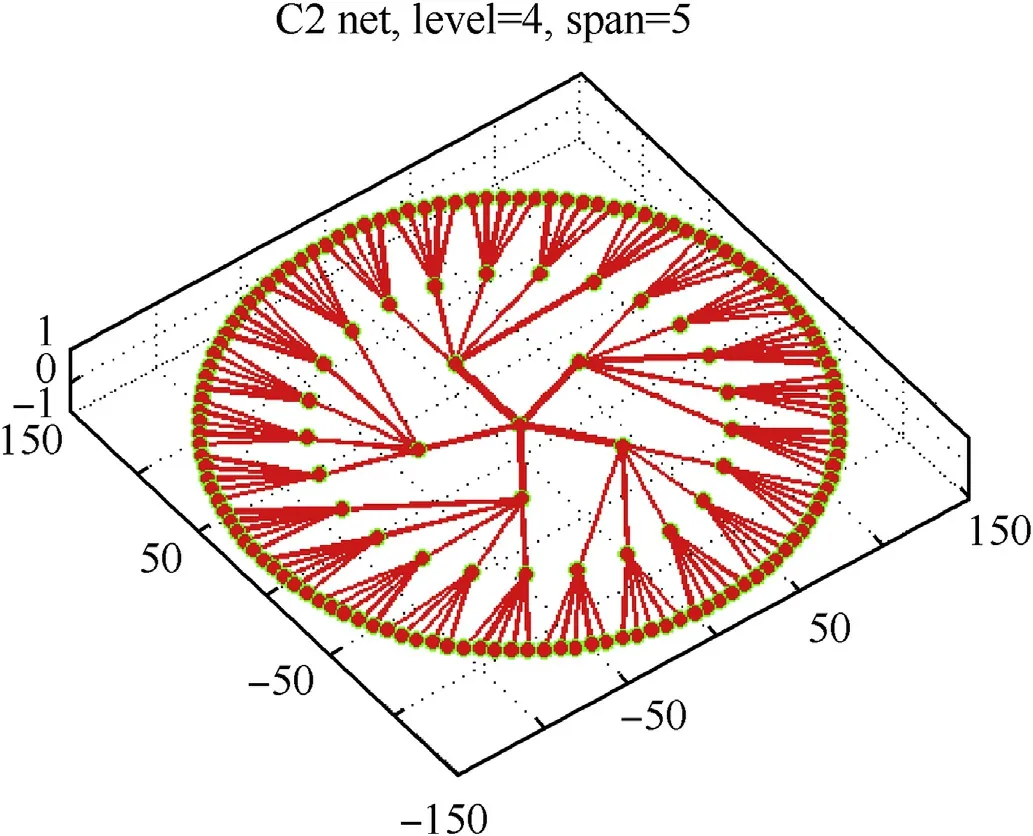
Fig.5.C2 net(level=4,span=5).
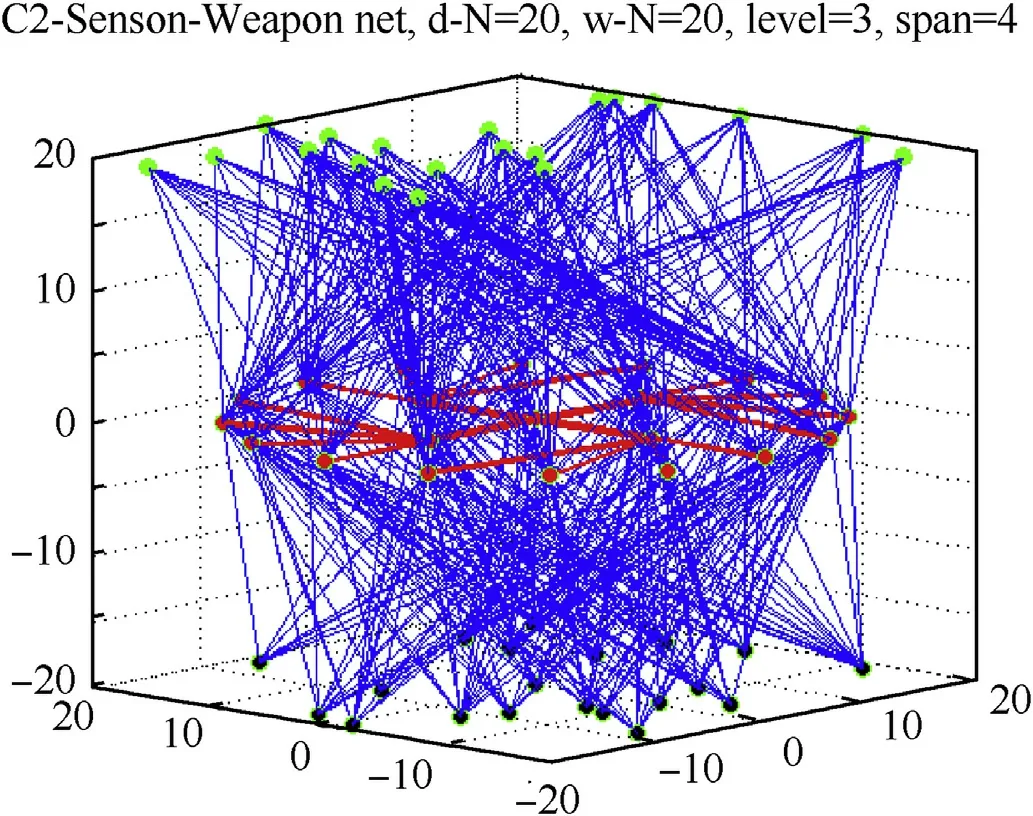
Fig.6.D&W net(d N=w N=20).
Cnet is a virtual net with no entities,it is used to connect C2 nodes and D&W nodes.Researchers have tried various models,such as random networks,small-world networks and scale-free networks,to describe a complex network.How ever,we cannot describe Cnet with only one of the three kinds of networks due to the special characters of combat restrictions.Random networks and small-world networks are effective in some degree to resist the deliberate attack,while they cannot reflect the different capabilities among different communication nodes,then much costs may be brought in.Scale-free networks can avoid the huge destruction when confronting a random attack,but it may lead to communication overload in some nodes and may even lead to a collapse in the whole operation net[22].Thus,a modified variable r1∈[0,1]is introduced to decide the proportion in net connection process,if r1=0,we adopt the random net connection mechanism,and if r1=1,the scale-free net connection mechanism would be chosen.If r1∈(0,1),we would use the fused mechanism.Simulation of C net can be seen in Fig.7.
In order to get the complete operation architecture,we need to connect all the C2 nodes and D&W nodes with Cnet.First,we need to disconnect all the connections which contain some relationships of command and control among C2 and D&W nodes.Second,communication nodes should be chosen to connect the old nodes which were connected at first,and the chosen method also obey the fusion mechanism.In this study,we define the fusion mechanism as below:
①set a proper modified variable r2(r2∈[0,1])to decide the C nodes chosen mechanism,if r2=0,C nodes should be selected with exponential distribution,and if r2=1,power law distribution would be chosen.
②when searching for the node with maximum degree in circulation,the searching space cannot be set as all the elements of Cnet adjacency matrix which can be described as

We define the searching space as a random piece of A′i,where
The process can be seen in Fig.8,the designed fusion mechanism is aiming to soften the high pressure of the node which has gotten the highest degree number,and it can also change the phenomenon“the rich get richer and the poor get poorer”[23].
4.2.Generalized operation loop description
The operation architecture construction method is given according to the constraint above,and some essential analysis is needed to test the whole system in some degree.In this study,GOL(generalized operation loop)is brought in.
Definition 5 GOL is a concrete description of OODA loop which contains at least one complete NOC unit,but GOL can also contain several single functional nodes.It is a basic unit which can complete the whole OODA process.Its description can be presented in Fig.9.
From Fig.9,we can see that the execution units such as D&W nodes can communicate with each other,and in real combat,we need to define some characters about the GOL.
a.Number of GOL
The more basic GOL we get,the more stable the operation architecture will be.The operation architecture can make many other useable projects to continue the broken work with a new replaced GOL when being attacked.
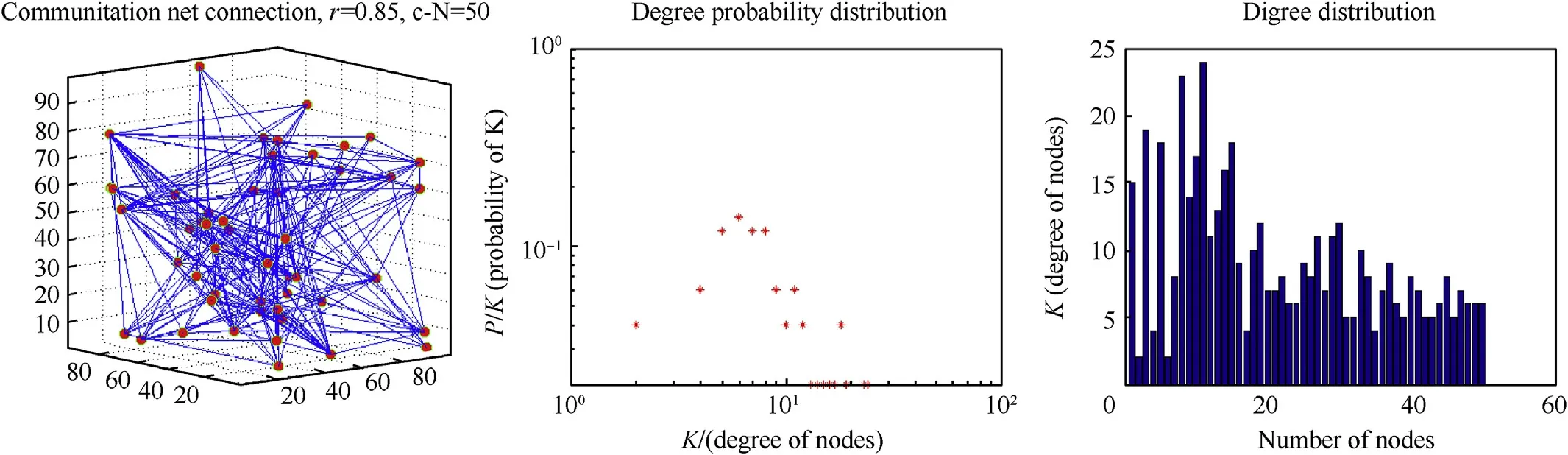
Fig.7.Cnet constructing sketch map.
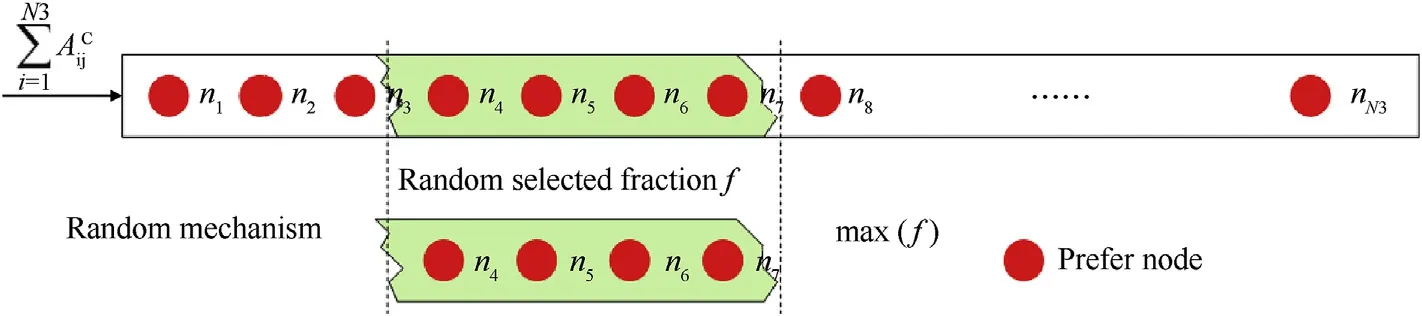
Fig.8.Node choosing method description.
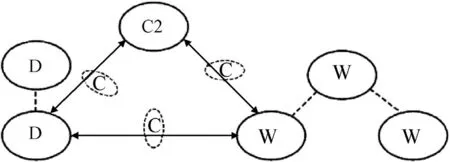
Fig.9.Description of GOL
b.Length of GOL
Length of GOL is determined by the number of D&W nodes.
i=0,l=0;
Repeat(While l≤L):
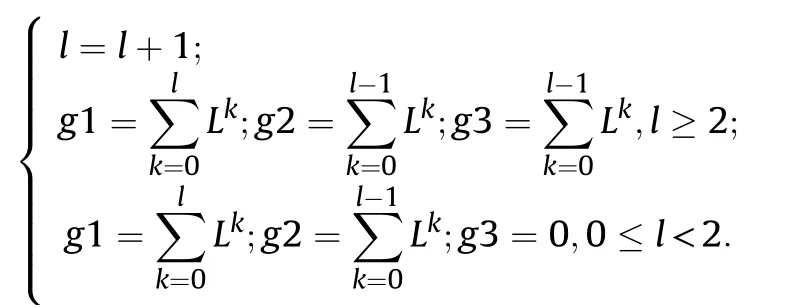
i=g3;j=g2+1;d=0;
Repeat(While i≤g2 and j≤g1):
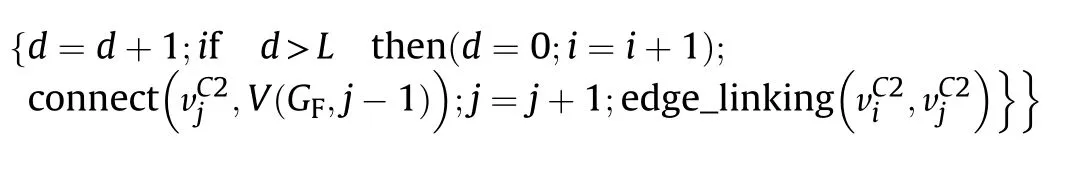
Step 3.Detection net organization
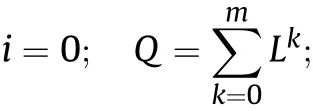
Excessive D&W nodes may lead to the attenuation of the information.So,we set 5 as the maximum number of the execution nodes in a basic GOL.
c.Evaluation indexes of GOL
4.3.Mathematical description
We can conclude the mathematical description of operation architecture construction as follow s:
Step 1.Initialization
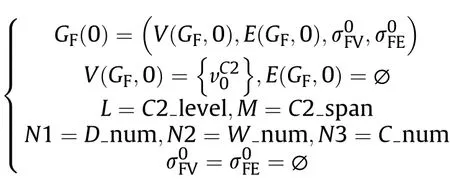
edge_linkingR(x,y)∝Random-Graph-Link-Mechanism;
edge_linkingSF(x,y)∝SF-Graph-Link-Mechanism;edge_linkingEXP(x,y)∝EXP-Graph-Link-Mechanism.
Step 2.C2 net organization
Step 4.Weapon net organization
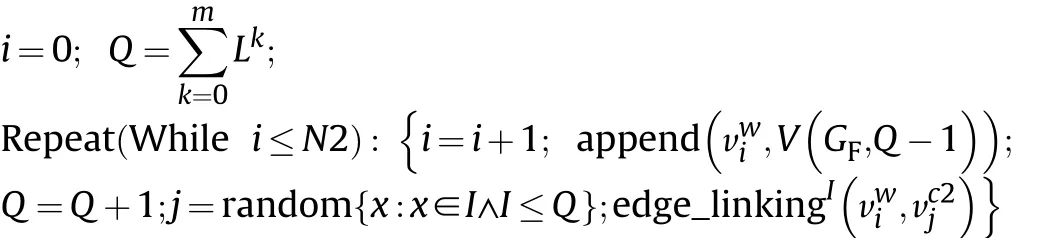
Step 5.Communication net organization

Step 6.Operation architecture organization

5.Simulation
We conduct two experiments to verify the effectiveness and feasibility of operation architecture.The first experiment assesses the model with some indexes such as degree distribution probability,number of GOL,invulnerability and information connectivity under attack,and the other experiment analyzes the network parameters r1 and r2,gives some suggestions to construct a better operation architecture.
Experiment 1:operation architecture assessment.
Set simulation condition:L=4,S=1,2,...,15,r1=0.85,r2=0.75,N1=40,N2=40,N3=30.The operation architecture can be obtained as shown in Fig.10,and we also analyze some features of the network as presented in Fig.11.
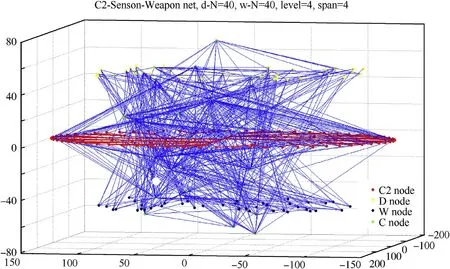
Fig.10.Operation architecture construction description.
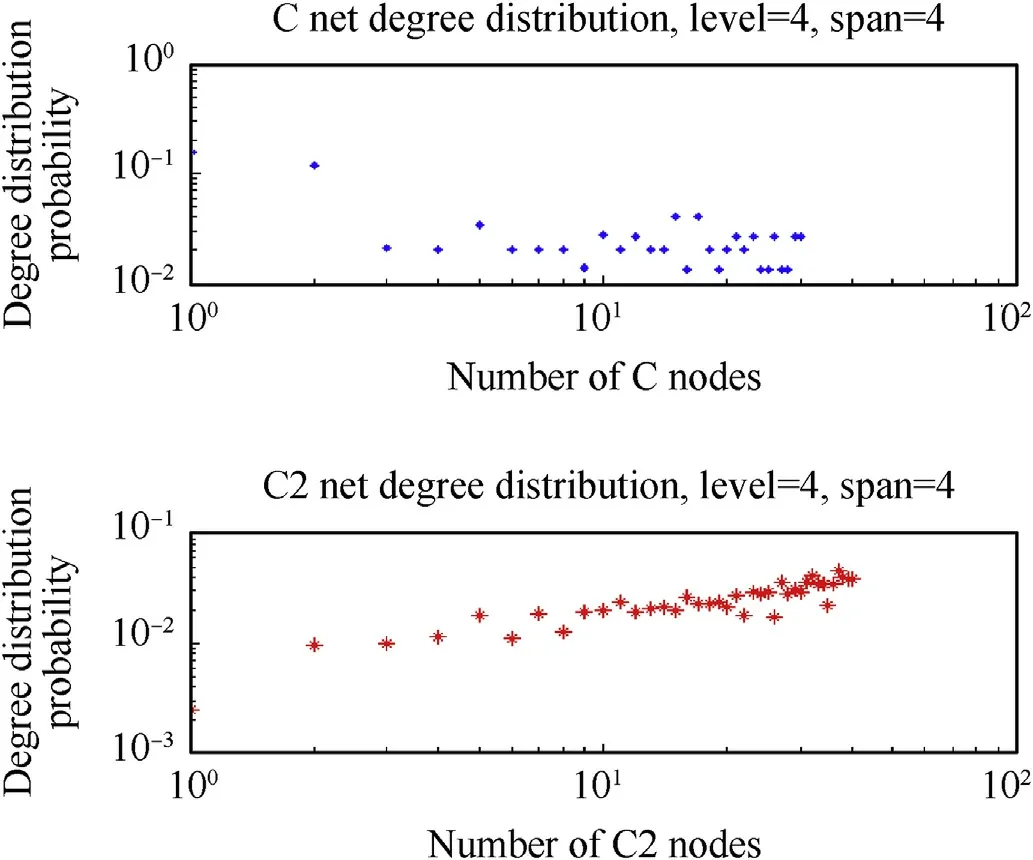
Fig.11.C&C2°distribution probability.
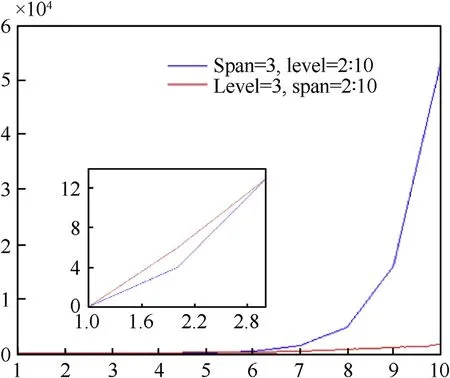
Fig.12.The number of GOL of different level and span.
Fig.10 shows the operation architecture which is consisted of a C2 net,a communication net and two execution nets.Fig.11 describes the degree distribution probability of C net and C2 net.From Fig.11,we can conclude that C net has some obvious characteristics of BA and ER net due to its construction method(r1=0.85,r2=0.75),and the characteristics of ER net come from the node choosing method we mentioned.Besides,only two nodes have high degree probabilities and others obey uniform distribution approximately.This kind of C net construction method can be useful to resist random and deliberate attack in some degree and the construction style can be modified by changing r1 and r2 easily.At the same time,we can get the degree distribution probability of C2 net and the nodes obey exponential distribution approximately.The results in C2 net are consistent with traditional C2 construction rule(the higher priority the node gets,the less execution unit the node connects).
The comparison of the number of GOL when changing level and span in C2 net is shown in Fig.12.We can see that with the increasing of the level and the span,the number of GOL presents a rising trend.And we can conclude as follow s:(1)When the value of level and span is relatively small,the change of span may have more influence on the number of GOL than that of level.When the value of level and span get greater,the change of level may lead to an exponential grow th of GOL.
(2)A large number of GOL may lead to a bad timeliness and an exponential grow th of GOL may increase the probability of a single GOL expansion and may lead to an attenuation of information transmission.
(3)According to the analysis,we can set a proper value of level which varies from 3 to 5.And we can set the value of span according to a specific task.
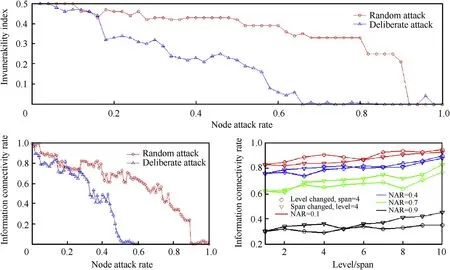
Fig.13.Evaluation indexes comparison.
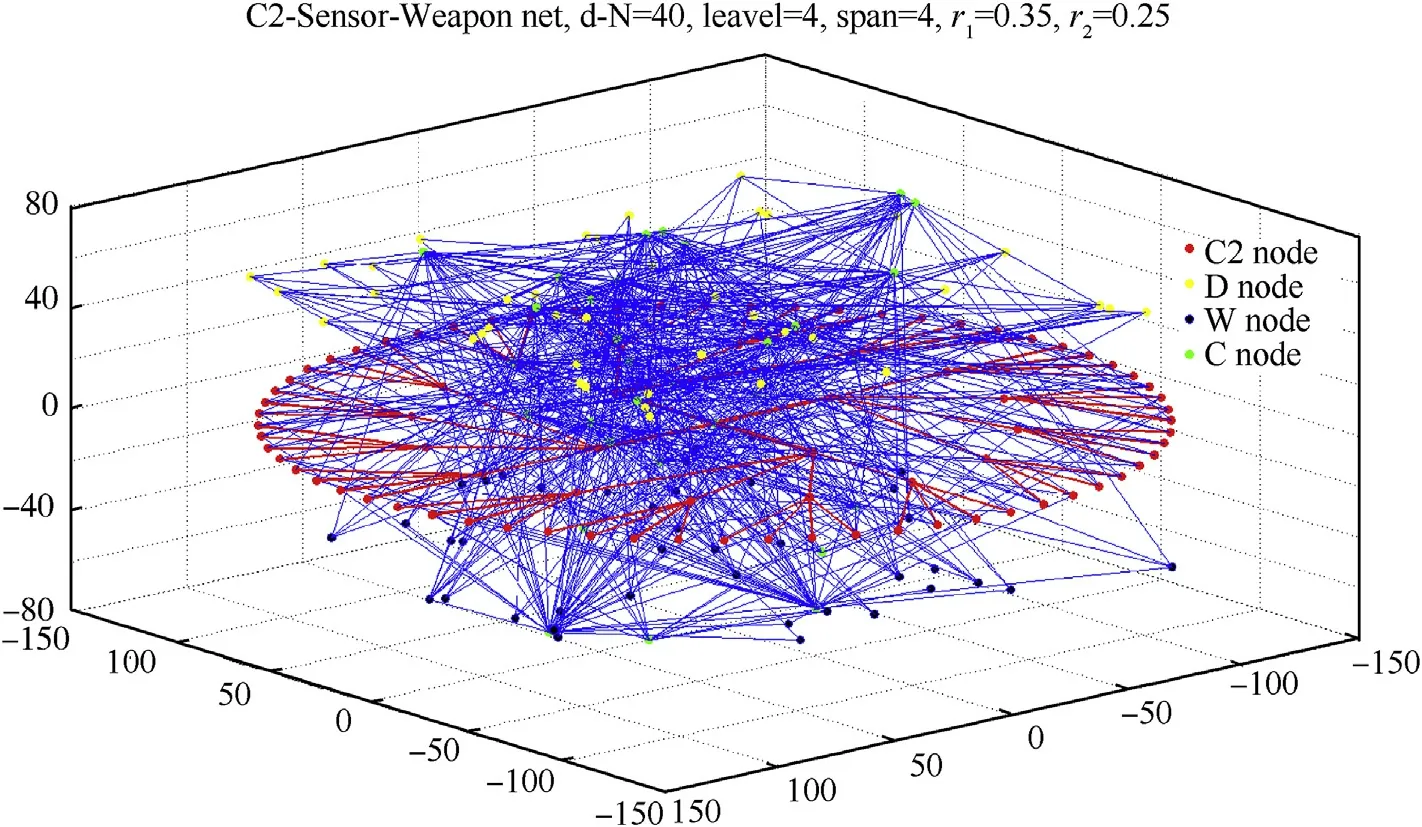
Fig.14.Operation architecture description.
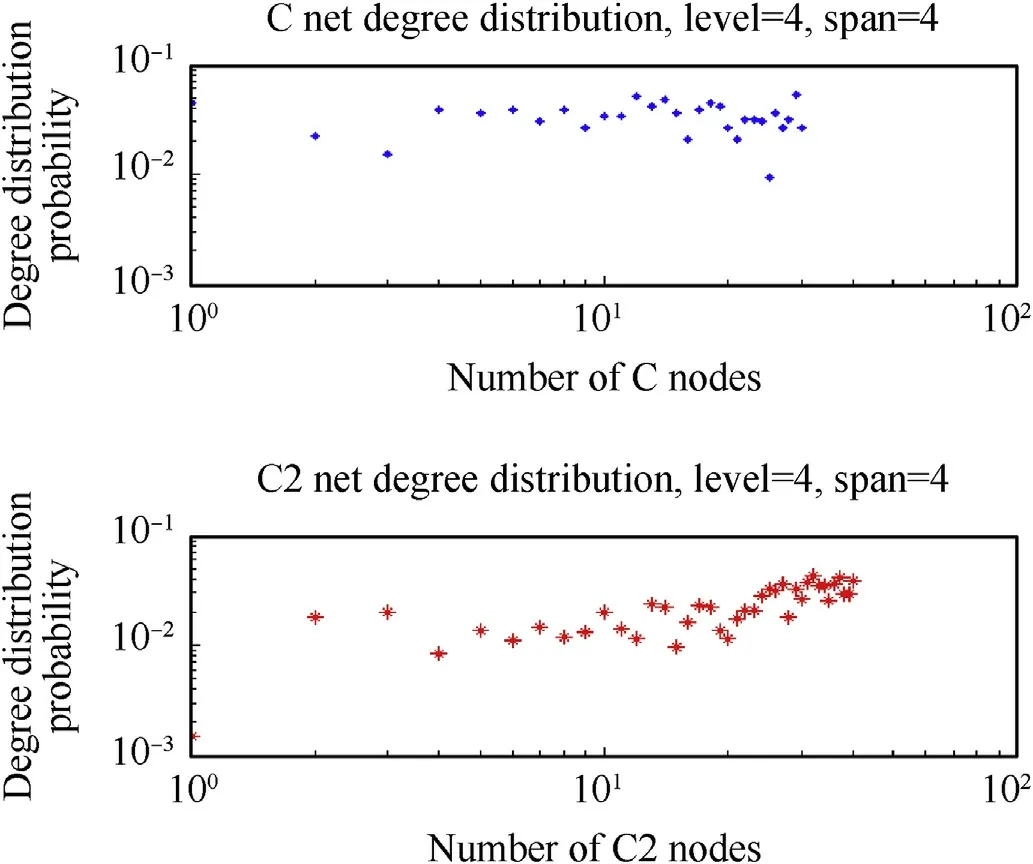
Fig.15.C&C2°distribution probability.
The evaluation of operation architecture in the level of invulnerability and information connectivity is presented in Fig.13.The first sub-figure describes the invulnerability of operation architecture under random attack and deliberate attack.We can easily find that operation architecture may become more reliable under a random attack.The following two sub-figures describe the information connectivity rates of operation architecture under attack.With the changing of NAR(node attack rate),the information connectivity rate may have relationship with the change of level and span.When NAR=0.1 and NAR=0.4,the change of the span may have a greater influence on the information connectivity rate than that of level.But when NAR gets larger,the results are the opposite.
Experiment 2:influence analysis of network parameters.
Set simulation condition:L=4,S=4,r1=0.35,r2=0.25,N1=40,N2=40,N3=30.
The operation architecture with the parameters of experiment 2 is shown in Fig.14.The degree distribution probabilities of C and C2 net are presented in Fig.15.From Fig.15,we can conclude that C net has more ER characteristics due to its construction method(r1=0.35, r2=0.25),and most nodes obey uniform distribution approximately.Different from experiment 1,we pay more attention to the influence caused by the modified variables r1 and r2 in this experiment.r1 and r2 can change the net construction style in some degree.
The comparison of the characteristics of GOLw hen r1 and r2 are changing is shown in Fig.16.From the first and the second subfigures,we can find that there is a proper range from 0.4 to 0.8 for r1,as well as the ranges from 0.1 to 0.2 and from 0.4 to 0.6 for r2.When r1 and r2 are in the intervals,we can obtain more GOLs,and the operation architecture can be more stable.The third and the last sub-figures show the comparison of max GOL length influenced by r1 and r2.From those sub-figures,we can see that with the increasing of r1 and r2,the length of max GOL shows an increasing trend,but r2 may have more influences than r1,in the last subfigure,the average length is longer than that in the third subfigure.Thus we should set the value of r1 within the interval we mentioned above,and r2 should be set smaller than r1.
6.Conclusion
In this paper,we propose a method to construct operation architecture based on complex network.Aiming at the limitations of traditional single platform operations,this paper combines nodes distributed on different platforms and propose a novel method to construct operation architecture based on complex network theory.Some constraints of operation architecture are also proposed.In order to evaluate the feasibility and effectiveness of operation architecture,the evaluation index of operation architecture is put forward.The effectiveness of the proposed operation architecture is verified by simulation analysis,and some characteristics are analyzed to acquire different influences with various parameters and the proper construction parameters of this new structure are obtained.The proposed method provides a novel way to construct an operation architecture which is suitable for modern combat under information situation,and provides theoretical support for the application of network warfare in the future.
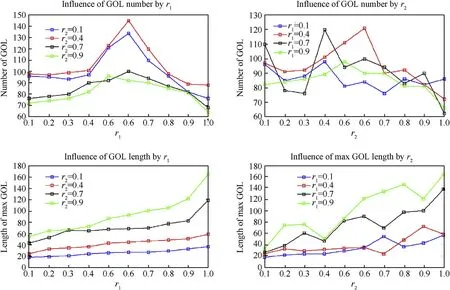
Fig.16.Evaluation indexes comparison.
According to the experiments,we can get the following conclusions:1)the final net connection result is influenced by many factors such as combat scale,connection mechanism,the number of nodes,modified variables and the setting constraints rules.2)operation architecture may be more efficient with fewer levels and more spans.3)the invulnerability of operation architecture can be improved by setting a proper value of NAR according to the combat conditions.4)the modified variables should be set with their value intervals.
Acknowledgements
The work described in this paper was fully supported by a grant from the National Natural Science Foundation of China(No.61472443).
- Defence Technology的其它文章
- An approach for predicting digital material consumption in electronic warfare
- Initial alignment of compass based on genetic algorithm-particle swarm optimization
- The non-isothermal gravimetric method for study the thermal decomposition kinetic of HNBB and HNS explosives
- A non-myopic scheduling method of radar sensors for maneuvering target tracking and radiation control
- Estimating the metal acceleration ability of high explosives
- Shaped charge penetration into high-and ultrahigh-strength Steel-Fiber reactive powder concrete targets

