Secure Short-Packet Transmission in Uplink Massive MU-MIMO Assisted URLLC Under Imperfect CSI
Tian Yu ,Xiaoli Sun ,Yueming Cai ,Zeyuan Zhu
1 Army Engineering University of PLA,Nanjing 210007,China
2 Unit 31401 of PLA,Jinan 250002,China
3 PLA Strategic Support Force Information Engineering University,Zhengzhou 450001,China
Abstract: Ultra-reliable and low-latency communication (URLLC) is still in the early stage of research due to its two strict and conflicting requirements,i.e.,ultra-low latency and ultra-high reliability,and its impact on security performance is still unclear.Specifically,short-packet communication is expected to meet the delay requirement of URLLC,while the degradation of reliability caused by it makes traditional physical-layer security metrics not applicable.In this paper,we investigate the secure short-packet transmission in uplink massive multiuser multiple-inputmultiple-output(MU-MIMO)system under imperfect channel state information (CSI).We propose an artificial noise scheme to improve the security performance of the system and use the system average secrecy throughput (AST) as the analysis metric.We derive the approximate closed-form expression of the system AST and further analyze the system asymptotic performance in two regimes.Furthermore,a one-dimensional search method is used to optimize the maximum system AST for a given pilot length.Numerical results verify the correctness of theoretical analysis,and show that there are some parameters that affect the tradeoff between security and latency.Moreover,appropriately increasing the number of antennas at the base station(BS)and transmission power at user devices(UDs)can increase the system AST to achieve the required threshold.
Keywords: average secrecy throughput;imperfect CSI;massive MU-MIMO;physical-layer security;short-packet
I.INTRODUCTION
1.1 Background
The International Organization for Standardization 3rd Generation Partnership Project (3GPP) has defined three major application scenarios for fifth generation(5G)–enhanced mobile broadband(eMBB),massive machine type communications (mMTC),and ultrareliable and low-latency communication (URLLC).Until now,supporting rate-hungry eMBB service has made great progress,while the research on URLLC service [1–3],such as smart factory,and smart wearable devices,is still in its infancy [4,5].For example,the control of robotic devices in a smart factory is very sensitive to delay(1ms)and reliability(1-10-8).Moreover,eavesdropping and tampering of commands received by robotic devices can cause serious factory accidents.The stringent requirements of URLLC and secure transmission have brought difficulties to the design of Internet of Things(IoT)networks supported by 5G.
The traditional human-to-human communications cannot meet the demand of URLLC,since this kind of large length of packet(LoP)(1500 bytes)leads to a longer transmission delay(20-30ms)[6].Recently,to meet the low-latency requirement,short-packet communication has gradually become one of the key technologies of URLLC [7].In 2010,Polyanskiyet al.derived expressions for the maximum achievable transmission rate and error probability (EP) in shortpacket communication under an additive white Gaussian noise (AWGN) channel from the perspective of information theory [8].Based on this,short-packet communication has been widely studied in different systems [9–12].[9] investigated a wireless energy transmission system for downlink energy transmission and uplink information transmission on the condition of a quasi-static Nakagami-m fading channel.[10]optimized the LoP allocation of the unmanned aerial vehicle(UAV)and the controller and the position of the UAV to minimize the decoding EP under a given delay.[11] considered a two-user downlink non-orthogonal multiple access (NOMA) system with finite blocklength (FBL) constraints and optimized the transmission rate and power allocation.[12] took packet errors,packet collisions and access control into consideration,and obtained an approximate closed-form expression of the average age of information(AoI).
With the development of 5G,people increasingly rely on wireless devices to share private information[13],while IoT networks are particularly vulnerable to eavesdropping [14] due to the broadcast nature of wireless communications.In IoT networks,secure transmissions guaranteed by traditional encryption algorithms are challenged by low complexity and largescale connection requirements.Moreover,longer keys will put tremendous pressure on resource-scarred IoT networks.As a promising technology,physical-layer security technology aims to use the characteristics of channel fading to reduce the ability of potential eavesdroppers to obtain confidential information [15].Recently,some scholars investigate physical-layer security issues in short-packet transmission scenarios[15–19].[17] analyzed the impact of FBL coding on physical-layer security through two scenarios.Specifically,in the single-antenna scenario,an approximate expression for average secrecy throughput(AST)was derived.In the multi-antenna scenario,the approximate expressions of AST in the two schemes of beamforming and artificial noise were derived.[18] investigated the secure short-packet transmission problem under NOMA system,and provided a scheme to increase connectivity and reduce time delay.At the same time,the author in [19] investigated the downlink NOMA based on the maximum ratio transmission (MRT) scheme under the Nakagami-m channel,and derived the closed-form expressions of the secrecy outage probability,connection outage probability,and effective secrecy throughput.
Recently,the emerging massive MU-MIMO has become an effective technology,which can enhance security performance with high spatial resolution [20–22].Specifically,massive number of antennas at the base station (BS) can focus energy and the transmission beam towards the directions of IoT devices.Based on the above theory,[23] investigated the secure transmission in simultaneous power and information transfer system.[24] took imperfect CSI caused by feedback delay and channel estimation error into consideration,and proposed a channel prediction scheme to alleviate the negative effect on the achievable system secrecy capacity.Besides,massive MU-MIMO can also reduce the reliability degradation caused by FBL,which drives the research of massive MU-MIMO technology in short-packet scenarios[25–27].[25]studied the linear minimum EP detection under a given pilot length,and improved the system reliability by optimizing the pilot length under a given delay requirement.[26] optimized the frame structure to minimize the EP by proposing a GSSM algorithm.[27] optimized the transmission power and frame structure to maximize the achievable data rate of the system.However,the issue of secure transmission on uplink massive MU-MIMO is still unclear,which is very important for the research of IoT.On the one hand,IoT devices are often equipped with a single antenna to transmit data.It is impossible to focus energy and the transmission beam towards the directions of BS.On the other hand,due to low complexity and massive connection constraints of IoT devices in uplink massive MU-MIMO,data information is easily leaked.
1.2 Motivation and Contribution
Previous works have investigated the implementation of URLLC and enhanced security performance in massive MU-MIMO scenarios,respectively.Actually,in IoT networks,many massive MU-MIMO scenarios need to meet URLLC and security requirements at the same time.Specifically,the imperfect CSI caused by the channel estimation error and the short-packet characteristics lead to the degradation of the system security performance.
Due to lower overhead of the pilot and no need for a dedicated feedback channel,time-division duplexing (TDD) operation instead of frequency-division duplexing (FDD) operation is widely investigated in massive MU-MIMO [28].Moreover,based on the analysis of massive MU-MIMO channel reciprocity in TDD mode,one of the most challenging problems is to obtain accurate CSI at the uplink transmission phase[29,30].However,to meet the extremely low-latency in the URLLC scenarios,the information slot is usually designed to be small.Since there is not enough channel length allocated for pilot and data,the CSI obtained by the receiver is imperfect.Without the accurate CSI,the security performance degrades severely.
On the other hand,when the LoP is infinite,the receiver can well average the interference and noise introduced by the wireless channel and achieve errorfree decoding.In URLLC,when the LoP is very short,the law of large numbers is no longer applicable,and the interference and noise in the channel cannot be averaged,which incurs transmission rate degradation and higher decoding error probability to make the communication performance worse.
As for now,how to characterize and optimize the security performance of URLLC under massive MUMIMO scenario and how to design the frame structure in order to balance the security-latency tradeoff remains unclear.The above issues motivate our work.
In order to solve the problems,we propose an analysis framework to comprehensively study the AST for short-packet communication in the massive MUMIMO scenario and design an artificial noise scheme to improve the security performance of the system.We summarize the main contributions of this paper as follows.
· We analyze an uplink massive MU-MIMO scenario under imperfect CSI.Moreover,we derive the approximate closed-form expression of the system AST,which reflects the system’s security performance in the case of moderate-blocklength(MBL),i.e.,102<LoP-pilot length<103.The expressions of the system AST under two asymptotic regimes,i.e.,infinite transmission power(ITP)and infinite length of packet(ILoP)are also derived.
· In particular,considering that the pilot length is often very small in the case of short-packet,we use the Fibonacci search method (FSM) to quickly obtain the optimal LoP (OLoP) for a given pilot length.The results obtained can be used to guide actual parameter design in industry.
· The numerical results provide a favorable basis for further optimization.There are some parameters that affect the tradeoff between security and latency,such as pilot length,LoP,while the tradeoff between security and reliability is affected by the number of bits transmitted per block.In addition,the system AST increases to an upper bound as the number of BS antennas and the transmission power of user device(UD)increases.
1.3 Organization and Notation
The rest of this paper is organized as follows.Section II gives an introduction of a uplink massive MUMIMO system model and provides a security performance metric.Section III derives the approximate closed-form of system AST,and further analyzes the system asymptotic performance in two regimes.Section IV provides some simulation results to validate the theoretical analysis.Finally,Section V concludes this paper.
Notations: (·)Tand (·)Hrepresent transpose and conjugate transpose.E(·)denotes expectation.[A]k,lrepresents the element of columnland rowkin the matrix A.CL×Kis anL×Kmatrix with complex elements.ILdenotes a identity matrix withLdimensional.In x~CN(µ,σ2),x denotes a random vector obeying a complex circular Gaussian distribution with meanµand covarianceσ2.Γ(s) represent the gamma function Γ(s)=Γ(s,x)is the upper incomplete gamma function Γ(s,x)=
II.SYSTEM MODEL
2.1 Network Model
Figure 1 shows an uplink massive MU-MIMO scenario,which includes a BS withL+1 antennas,Klegitimate UDs,and an eavesdropper (Eve).We assume that allKlegitimate UDs with known deployment locations are equipped with a single antenna for transmitting signals,and they are all active at the same time.The Eve equipped withMantennas is an untrusted device with strong eavesdropping capabilities(L≥M≥K) .In order to reduce eavesdropping performance and ensure reliable transmission,the BS adopts a full-duplex operation mode.Lantennas are used to receive the information transmitted by UDs,and one antenna (BS interference antenna) is used to impose artificial noise interference on Eve.As [31–35] stated,we assume that the BS can eliminate selfinterference.Since the number of UDs is often very large in massive MU-MIMO,zero-forcing(ZF)detection has better performance than maximum-ratio combining (MRC) detection in solving the interference problem between UD signals.Moreover,ZF detection can achieve a spectrum efficiency close to the optimal non-linear detection techniques [28].Based on this,we consider that both BS and Eve receivers adopt the ZF detection.
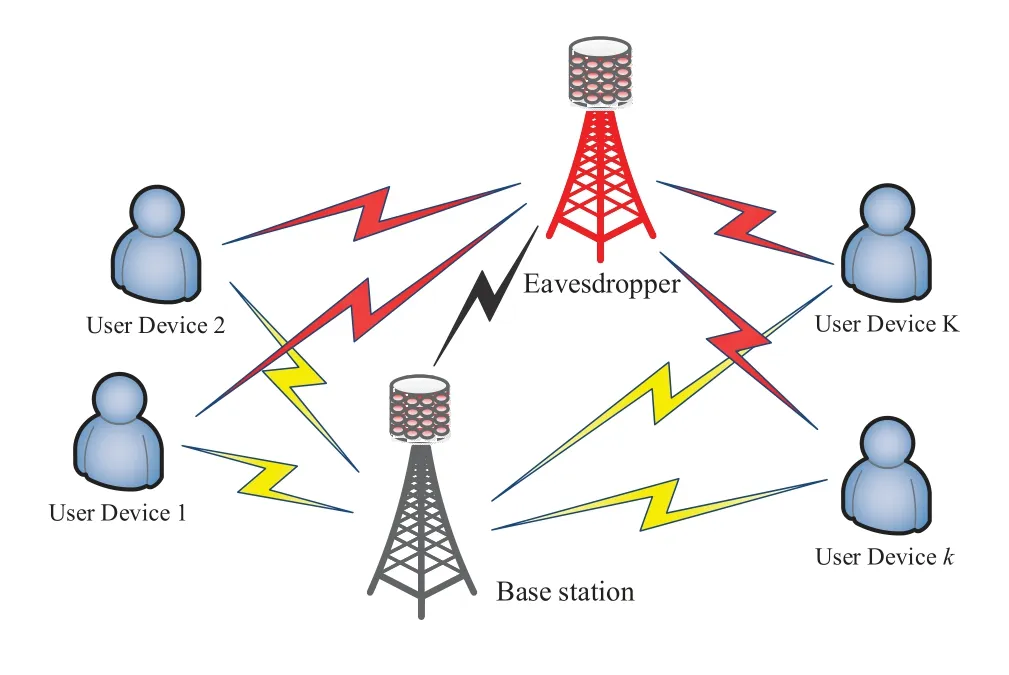
Figure 1.Uplink massive MU-MIMO with secure shortpacket communication model.
In this paper,to support low-latency communication,we consider that short-packets are used for information transmission between legitimate UDs and BS(Eve)[36].Based on this,the blocklength of channel coding is limited.Specifically,in this paper,each UD transmitsBinformation bits throughNchannel uses(CUs).
2.2 Signal and Channel Model
Generally,it is very difficult for a BS to obtain perfect CSI in the massive MU-MIMO system.Channel estimation errors,limited feedback overheads and feedback delay will all cause imperfect CSI.In this paper,we consider the case of imperfect CSI caused by pilot-assisted channel estimation(PACE),in which the transmission signal is composed of pilot and data.The UD sends the transmission signal to the BS.The BS completes channel estimation,obtains CSI and demodulates the data signal.In this model,the received signal at the BS and Eve can be expressed respectively as
Specifically,the legitimate channel matrix G and the eavesdropping channel matrix Gecan be be expressed as the following forms,respectively
2.3 Achievable Transmission Rate with Finite Blocklength
According to the Shannon information theory,when the LoP approaches infinite,the information communication rate can reach the Shannon upper bound.At the same time,on the basis of considering security,Wyner’s physical-layer security transmission theory gives a definition of secrecy capacity.However,this cannot be directly used as the basis for short-packet research,because the EP and information leakage at the receiver cannot be negligible.According to [37]and[38],the form of the lower bound on the maximal secure communication rate(MSCR)under PACE can be expressed as
Otherwise,we can simply setϵk=1.
It can be seen from (6) that when the LoPNapproaches infinity,the EP can be arbitrarily small[41].However,as the LoP gets smaller,the EP becomes less negligible.This poses a challenge to the reliability of transmission.Considering the influence of EP,an average EP is defined as=E(ϵk),which denotes the average EP ofkth UD.Therefore,the AST of thekth UD and the system AST can be expressed as
According to(7)and(8),we can clearly see that the LoPNis inversely proportional to the transmission rateR.For a given the number of bits transmitted per blockB,Rdecreases asNincreases,which means the transmission delay increases.On the other hand,In the case of a largeN,the average EPtends to 0,that is,reliability increases.In addition,when the transmission data is fixed,theNis positively correlated with the pilot lengthς.Therefore,the influence of LoP on AST in(7)and(8)is very important,which represents a tradeoff between security and latency.Similarly,Balso has a similar tradeoff relationship on security and reliability.In short,choosing the rightN,ςandBcan get the largest AST.
III.ANALYSIS FOR THE MODEL
In this section,we focus on the system AST of the system model with imperfect CSI.Firstly,we derive the expression of the signal-to-noise ratio(SNR)of the BS and Eve after ZF detection,respectively.Secondly,the system AST is derived.Furthermore,we obtain the asymptotic expressions of the system AST when the transmit power and LoP tend to be infinite.Finally,we use FSM to obtain the OLoP.
3.1 SNR of BS under ZF Detection
The estimation of the channel matrix at the BS is given by[42]and[43]as follow
Moreover,the data part at the BS can be expressed as
When the matched filter at the BS uses ZF detection,the detection vector can be expressed asand the processed signal at BS is
Thekth column of the received signalcan be applied to estimate the xk.Therefore,thekth UD’s SNR can be expressed as
Based on this,the probability density function (PDF)of thekth UD’s SNR received at the BS is
It can be seen that the PDF of thekth UD’s SNR is related to the pilot lengthς.Therefore,when the number of active UDsK,the transmit powerρt,and the UD deployment location are given,the processed SNR can be adjusted by changingς.
3.2 SNR of Eve under ZF Detection
According to the foregoing,Eve has strong eavesdropping capabilities and can obtain perfect CSI.Moreover,ZF detection is adopt at Eve,which can eliminate the interference among UDs.Here,the detection vector can be expressed asand the expression of signal at Eve with ZF detection is
Same as the processing at BS,thekth column of the received signal VeZFYe(d)can be applied to estimate the xk.Therefore,thekth UD’s SNR can be expressed as
whereφ=M-K+1.It can be seen that the PDF of thekth UD’s SNR is related to the interference power of the BS interference antenna.The greater the interference power,the worse the received SNR.Considering that all devices in the IoT scenario have low power consumption,the interference power cannot be infinite,and a reasonable choice of interference power can effectively reduce eavesdropping performance.
3.3 System AST
In imperfect CSI scenarios caused by channel estimation errors,the system AST can well characterize the system’s secure transmission capabilities.According to (7),the system AST of thekth UD at BS can be given as
Substituting (22)-(24) into (21),the lower limit ofA(y)is still not easy to handle.A reasonable approximation to the lower limit ofA(y) is uesd.We have observed that whenx<y,there isFurthermore,whenx<yandN→∞,=y(x)→1,whenN→0 can also getϵ→1.Therefore,the lower limit of the integral of(21) can be changed fromyto 0,which is expressed as
Proof.See Appendix A.
Substituting (26) into (20),the AST of thekth UD at BS can be expressed as
Proposition 1.IntheimperfectCSIscenario,thesystemASTcanbeapproximatedas
Proof.See Appendix B.
It can be learned from (28) thatis a monotonically decreasing function of the interference powerρis.The system AST is a monotonically increasing function ofρis.It shows that increasing the interference power can effectively suppress the eavesdropping capability.In addition,due to the complexity of the expression,it is difficult to carry out further theoretical analysis.We will analyze the system performance through simulation in the Section IV.
3.4 Asymptotic Performance of ITP
Proposition 1 presents an approximate closed-form expression for the system AST.However,the expression is too complicated to get any insight.Motivated by this,we now focus on the asymptotic regime of ITP,where the expressions can be derived.
When the transmit power tends to be infinite,the conditions for both legitimate and eavesdropping channels will become better.The AST under ITP can be characterized as
From (31),we know that when the transmit powerρttends to be infinite,the system AST cannot increase infinitely and has an upper bound because (31) has nothing to do withρt.In addition,in the ITP scheme,the system AST increases as the interference powerρisand the number of active usersKincrease.
3.5 Asymptotic Performance of ILoP
In order to get the performance comparison with the classic long-packet,we set the LoP approach to infinity.When the LoP tends to be infinite with(ς)>,according to (6),the EP is approximately 0(i.e.,ϵ→0).
Therefore,the AST at thekth antenna under ILoP can be characterized as
It can be found that whenT→0,the security performance of the system can be analyzed by solving the probability Pr(γk>) which represents the nonzero secrecy capacity.According to Pr(γk>),the expression for the probability of non-zero secrecy capacity is
It can be seen from (34) that when the LoP tends to be infinite,the system AST is related to the transmit power,pilot length,and interference power,and has nothing to do with the information leakage coefficient.Speaking of satisfying the nonzero secrecy capacity probability Pr,when the LoP tends to be infinite,is much smaller thanso the system AST can achieve the requiredwithout information leakage.
3.6 OLoP for a Given Pilot Length
It can be seen that the system AST is highly related to the selection of LoP and pilot length.In this part,we fix the pilot length and maximize the system AST by changing the LoP.According to[25],due to the complexity of obtaining the derivative of (28),the FSM algorithm is used to find the OLoP.
The FSM algorithm is a two-way contraction method with low complexity,which can search for the minimum point of a unimodal function by iteratively narrowing down the search range and converge quickly.Since (28) is a concave function,we set the objective function to -Tall(N),the error precision toerror=0.00001,and the initial search range to [na,nb],wherena=ς,nb=500.Due toFi(i+2)=Fi(i)+Fi(i+1),(28) should be calculated for at mosti+2 times.The complexity of the FSM isO,and the complexity of the exhaustive-search method(ESM)isO.The detailed procedure is given by Algorithm 1.

IV.NUMERICAL RESULTS AND ANALYSIS
In this section,we present numerical analysis of the above derived results.By comparing the theoretical analysis with the results of the Monte Carlo simulation,we can verify the accuracy of the derived theoretical value and get some useful insights that are put forward for the system performance.According to[17],unless otherwise stated,the simulation parameters are listed by Table 1,whereρtis the normalized transmission power.
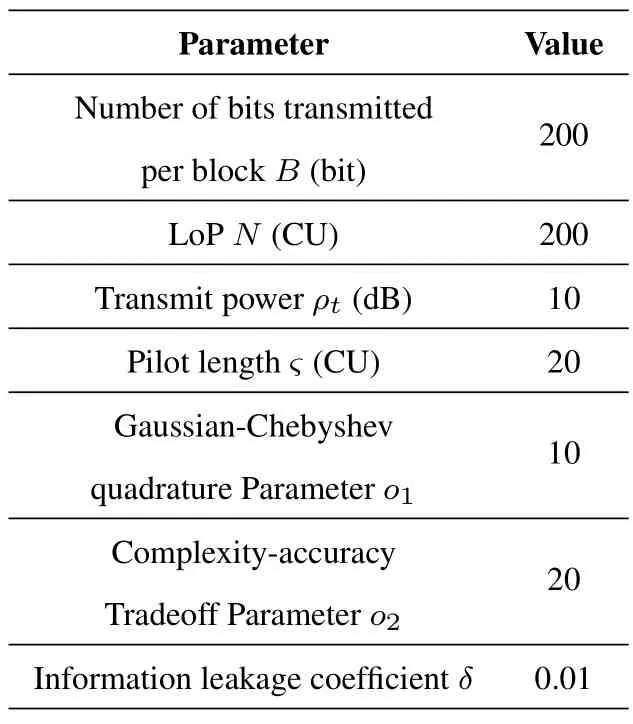
Table 1.Parameter setting in simulation and experiment.
Figure 2 shows impact of the LoP value on the the system AST.It is obvious that the theoretical value we derived and the Monte Carlo simulation value do not fit well when the LoP isN<150.On the contrary,the theoretical value and the simulated value are highly fitted atN≥150.This is because our approximation is relative to the case of the MBL.Secondly,the system AST increases first and then decreases as the LoPNincreases.This is because according to(6),the EPϵkof a single UD decreases monotonically asNincreases.However,the transmission delay increases monotonically asNincreases.That is to say,there is a tradeoff between the security and latency.A reasonableNdesign can greatly improve system performance.We can also see that the information leakage coefficient also has a significant impact on the security performance.As the information leakage coefficient increases,the system AST increases.This is because according to(6),ϵkis a monotonically decreasing function ofδ.
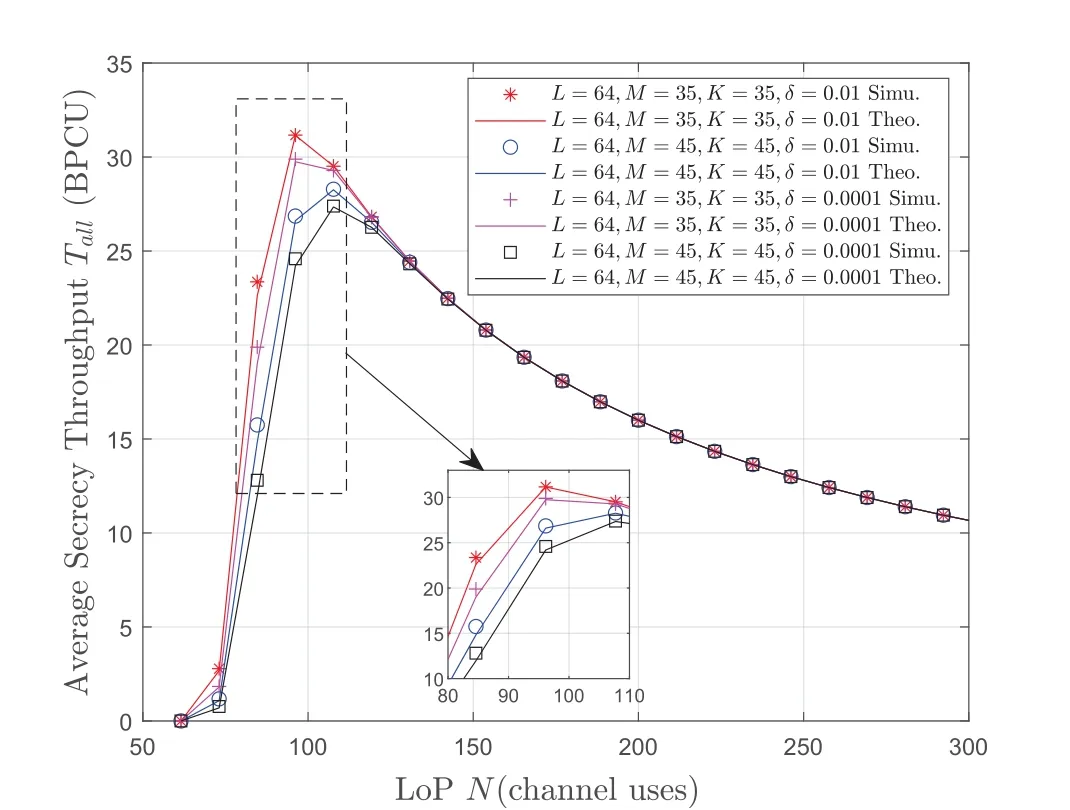
Figure 2.The system AST versus LoP under different antennas.
In Figure 3,we set the number of bits transmitted per blockB=400bit,LoPN=400CU.Figure 3 reveals the impact of pilot length on system performance under imperfect CSI caused by channel estimation errors.Similar to the result in Figure 2,the system AST first increases and then decreases with the pilot length.This is because according to (10),as the pilot length increases,the error termgradually decreases,which brings about the gain of the system AST.As the pilot length increases,the amount of data information decreases during the information transmission process,resulting in a decrease in the system AST.Therefore,there is a tradeoff between the security and latency is affected by pilot length.In addition,whenς<30,as the pilot length increases,the system AST rises sharply,which is consistent with the simulation results in[46].
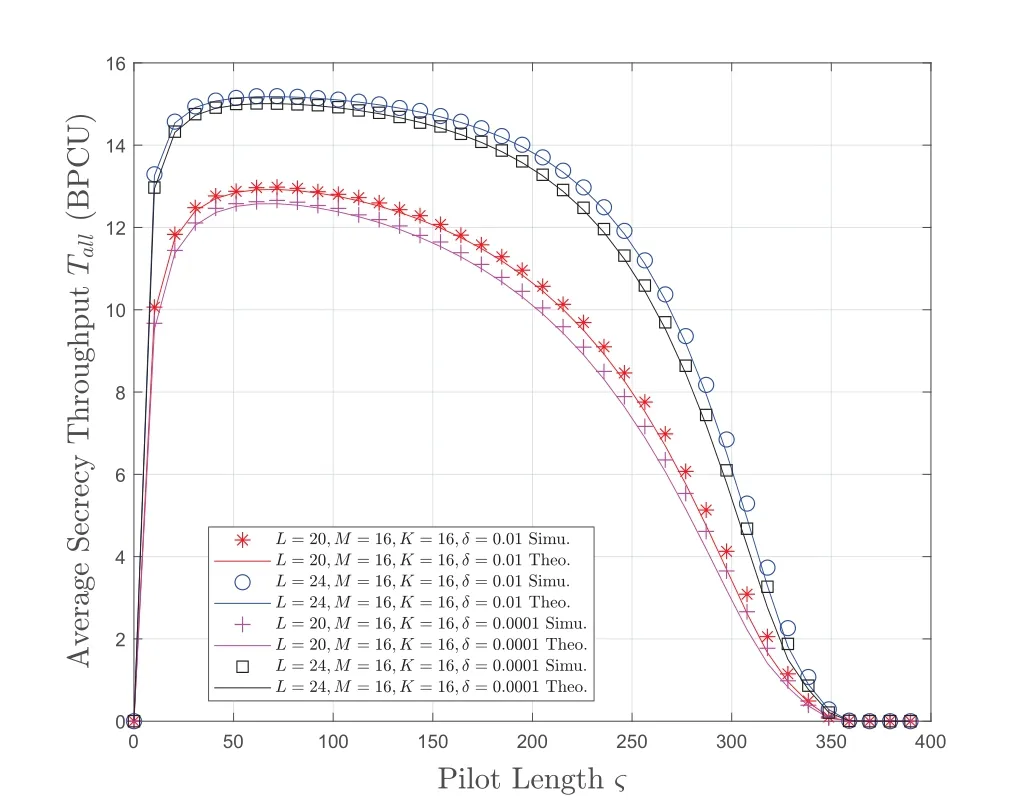
Figure 3.The system AST versus pilot length.
Figure 4 depicts the impact of transmit power on system AST under different number of BS antennas or interference power.It is obvious that the system AST increases monotonically with the transmit power.Whenρt→∞,the system AST tends to a fixed value,which is a good verification of our derivation in 3.4.In addition,whenρt=5dB,the system AST is close to the upper limit,which instructs us to reduce the transmit power as much as possible while meeting AST requirements in practice.We have obtained some conclusions,such as the system AST increases as the interference power increases.
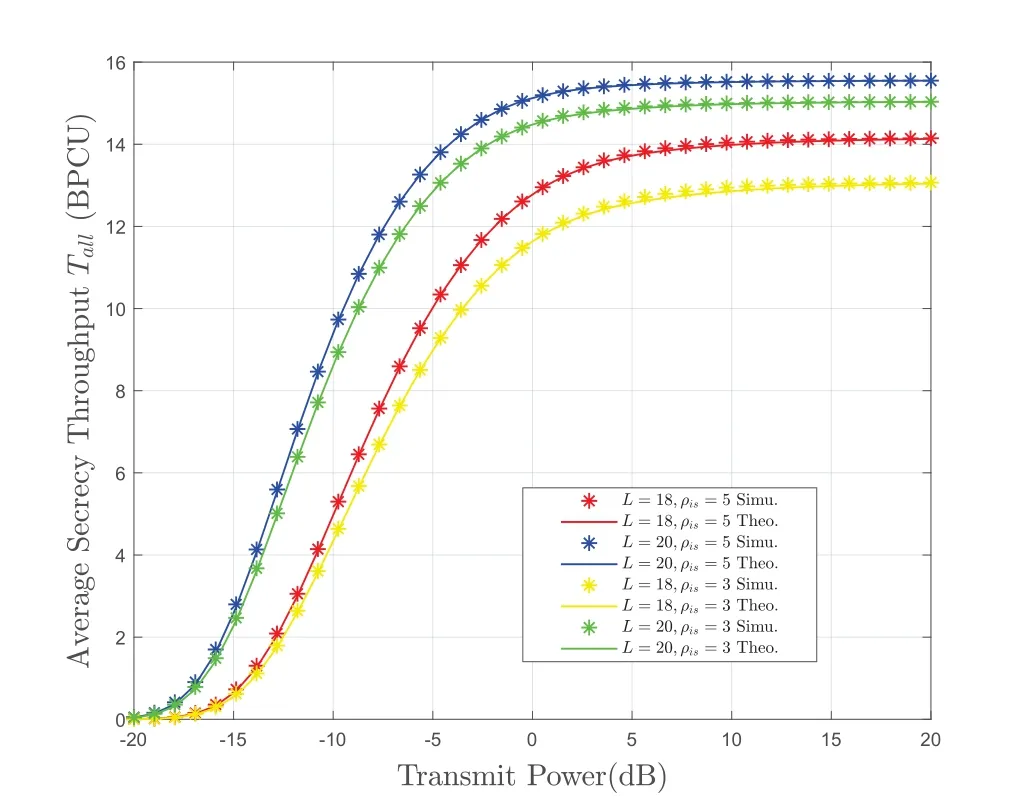
Figure 4.The system AST versus transmit power.
In Figure 5,the system AST increases first and then decreases with the number of bits transmitted per blockB.There is a tradeoff between reliability and the security performance of the system.This is because increasingBwill both increase the transmission rate under a given LoP and the packet EP according to(6).Therefore,WhenBtend to infinity,the EP tends to 1,and the system is insecure.The requirements of the transmission scheme design can be met by setting the threshold reasonably.
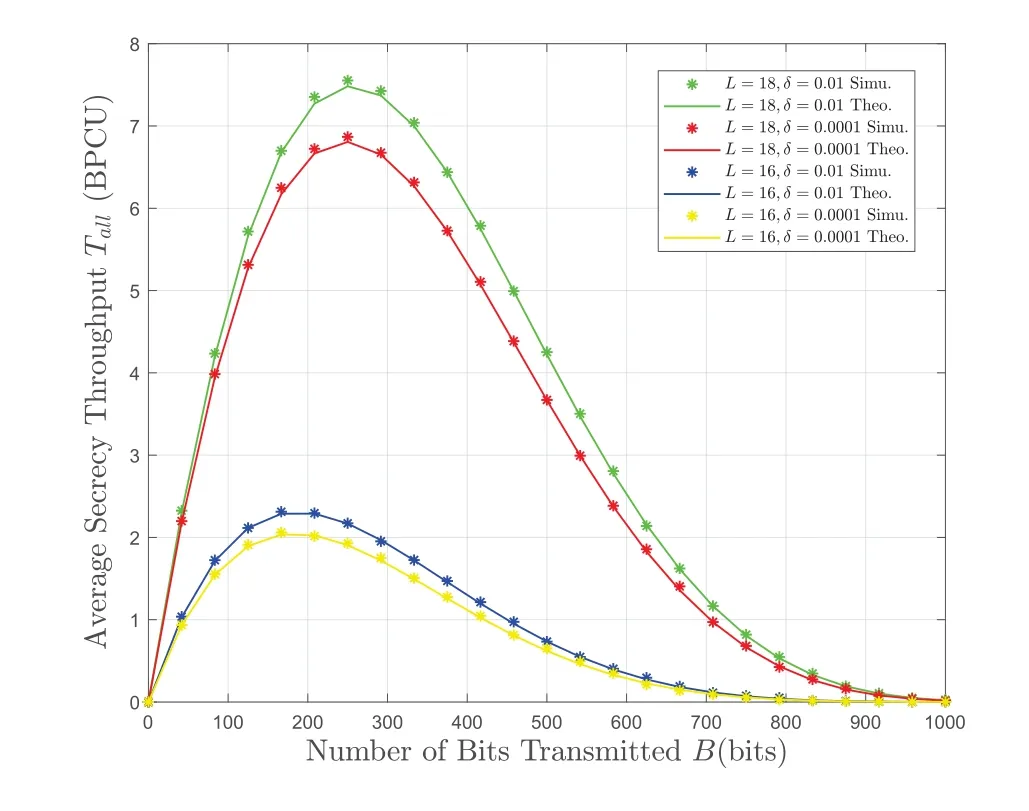
Figure 5.The system AST versus the number of bits transmitted per block.
Figure 6 shows how the system AST changes with the number of BS antennasL.In order to investigate the system AST in the case of massive IoT connection,we set UD to 35 and 45,and the number of Eve antennas to 50.At the same time,to ensure the orthogonality of the pilot sequence,the pilot length should be greater than UD [27],so we haveς=50.The system AST is an increasing function ofL,and gradually tends to a fixed valueBecause asLincreases,the diversity gain becomes larger and the eavesdropping performance gradually decreases.In addition,according to [40],when the number of antennas tends to infinity,the system AST is no longer a function ofL.Increasing the number of UDs can reduce the diversity gain of the Eve,and improve the system AST.Moreover,with a reasonable design of the number of antennas,the BS can quickly reach the maximum performance upper bound,which can effectively reduce the operator’s overhead.
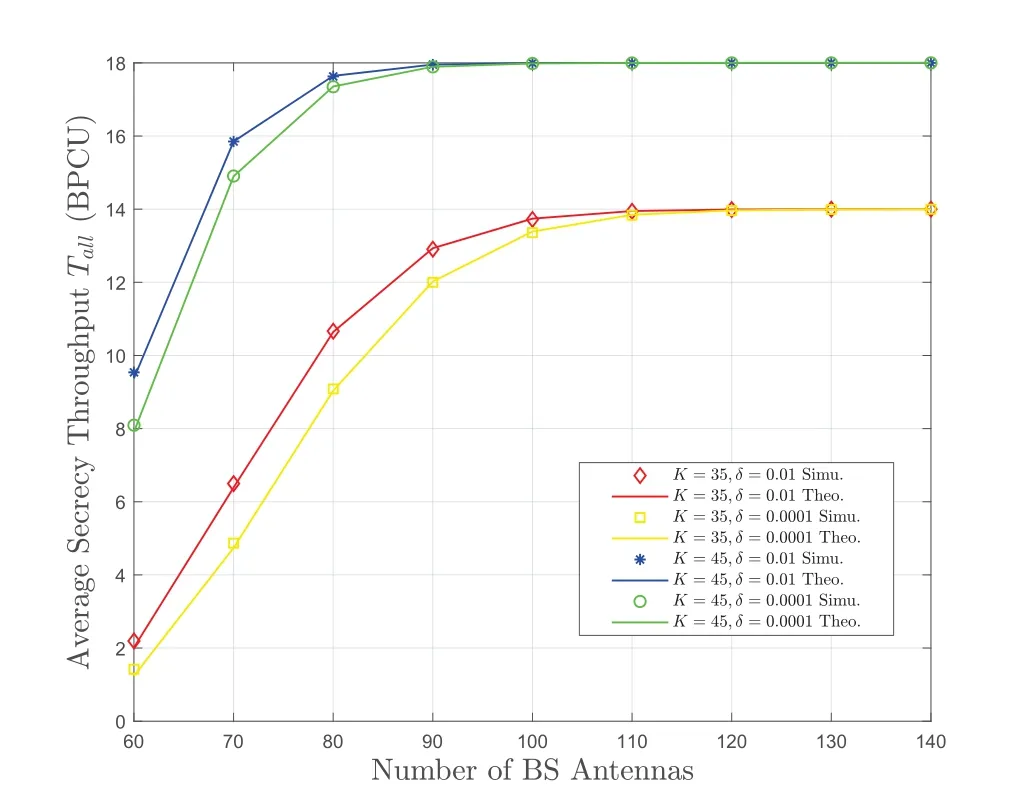
Figure 6.The system AST versus the number of BS antennas.
It can be seen from Figure 2 and Figure 3 that the loP and pilot length have an impact on the tradeoff between security and latency.For further research,in Figure 7,the system AST is obtained with LoP and pilot length as variables.When the LoP is given,the influence of the pilot length on the system AST is consistent with Figure 3,which verifies the correctness of Figure 3.In theNoςcoordinate plane,whenN≤ς,we set the system AST to 0.In addition,due to the constraints of the MBL scheme,LoP setting starts from 50.When 50 ≤N≤150,the theoretical value and the simulated value are not well fitted.WhenN>150,the theoretical value and the simulated value fit well,which verifies the correctness of the previous approximation.When the pilot length is given,the system AST is a quasi-concave function of continuous LoP,so an OLoPNcan be obtained,which increases with the increase of the pilot lengthς.In the same way,the optimal pilot length increases asNincreases.
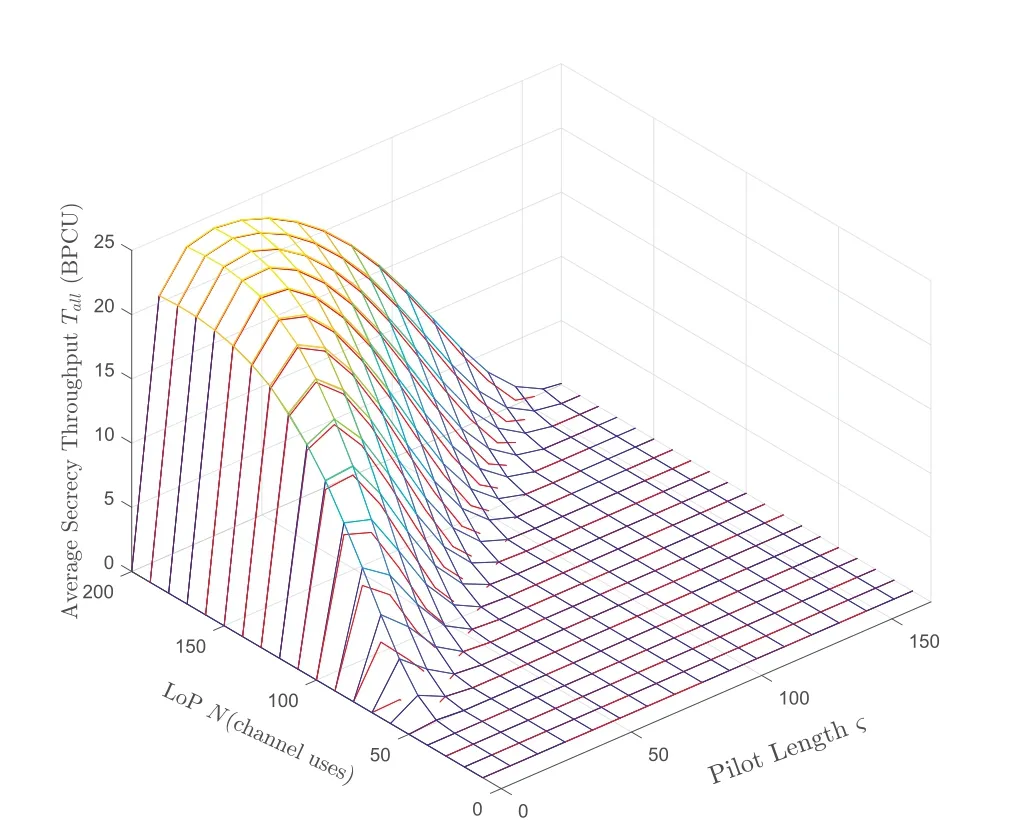
Figure 7.The system AST versus the number of LoP and pilot length.
Figure 8 shows the maximum system AST under different information bits transmitted per block,and compares the LoP determined by different onedimensional search methods.In Figure 8,the star markers represent the OLoP obtained by the FSM,the squares represent the OLoP obtained by the ESM,and the diamond represents the OLoP obtained by minimum delay method (MDM) which aims to minimize the transmission delay.The FSM matches the ESM very well,and the FSM greatly reduces the computational complexity.However,MDM can only achieve the optimal AST before the information bits are less than a certain value.For a given number of bits transmitted per block,the LoP accurately reflects the transmission delay.The optimal LoP is proportional to the number of bits transmitted per block.When the optimal LoP exceeds the LoP determined by the minimum delay,MDM cannot find the optimal AST.It is obvious that MDM obtains the lowest transmission delay at the expense of security performance.In the Internet of Things,without security,transmission delay becomes meaningless.In short,the FSM is significantly better than the other two algorithms.

Figure 8.The OLoP under FSM and other methods.
Figure 9 compares the tradeoff between the system AST and the LoP under the perfect CSI obtained by the BS and the imperfect CSI when the pilot lengthς=20.In this figure,we set the number of BS antennas to 24.The system AST under the perfect CSI case is a quasi-concave curve,which is the same as our previous work [40].In the perfect CSI scheme,the system AST in the curve can reach 70 BPCU.This is because that all LoPs are used to bear information bits,and the system performance is greatly improved compared to imperfect CSI scheme.In the imperfect CSI scheme,due to the degradation of the system security performance caused by the channel estimation error,the same effect as the perfect CSI cannot be achieved.An effective method to approach the effect of system AST under perfect CSI is to increase the interference power and spatial diversity at BS.However,in IoT scenario,especially in the uplink massive MUMIMO,this performance improvement is limited by the radio circuit and battery life of the IoT device.
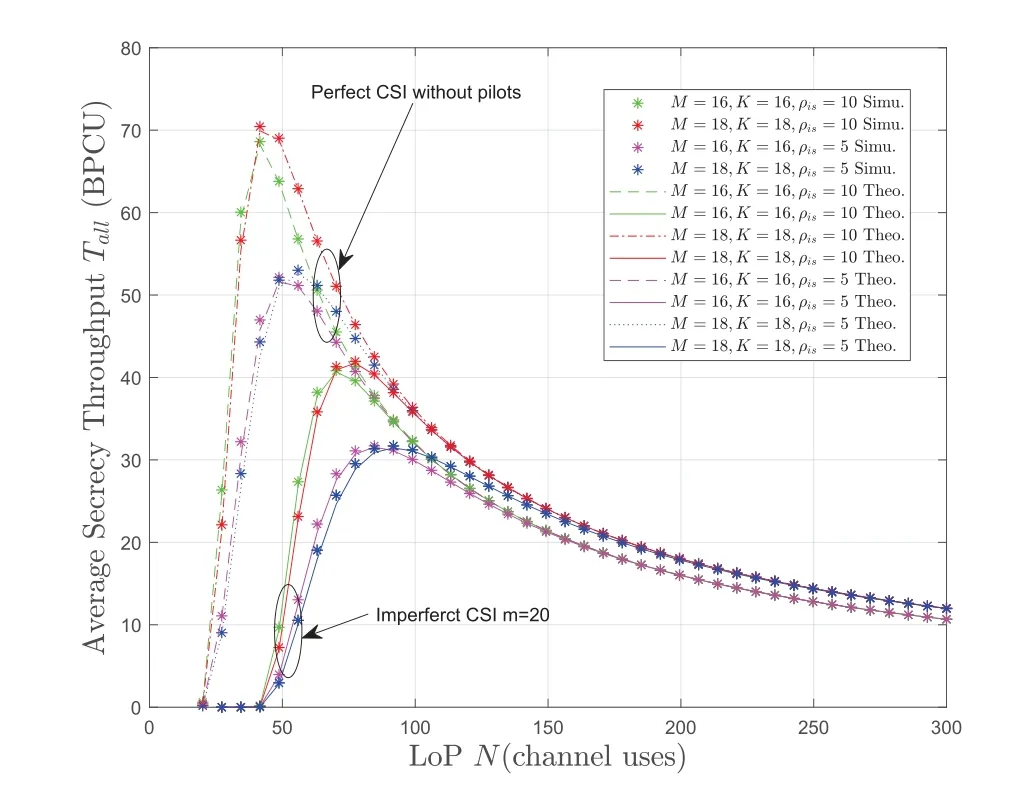
Figure 9.The system AST under perfect CSI and imperfect CSI.
V.CONCLUSION
In this paper,we have investigated the secure shortpacket communication in the uplink massive MUMIMO system under imperfect CSI,and derived the approximate closed-form expression of the system AST.In order to get more insights,the closed-form expressions under infinite LoP and infinite transmit power are obtained,and the OLoP under a given pilot length is obtained by using the FSM.Numerical analysis verifies our conclusions and provides insights.Reasonable selection of pilot length,LoP,and the number of bits transmitted per block can achieve better security performance.Appropriately increasing the number of BS antennas and transmit power at UDs can increase the system AST.A promising future direction is to consider the physical-layer security issues caused by imperfect channel reciprocity under imperfect CSI.
ACKNOWLEDGEMENT
This work was supported by the National Key R&D Program of China under Grant 2018YFB1801103 and the National Natural Science Foundation of China under Grant(no.62171464 and no.62122094).
APPENDIX
A Proof of Lemma 1
After some manipulations,the expression of (25) is given by
To derive the closed-form expression of (A.1),we first take MBL scheme into consideration.When the LoP is 102<N-ς<103,the parameter|d|in(24)will be quite large.Given the pilot lengthς,it is an increasing function ofN.Based on this,the first-order Riemann integral approximation is given by
Finally,substituting (A.1) into (A.2),(26) can be gain.
B Proof of Proposition 1
By using the partial integration method,(27) can be written as
By using the Gaussian-Chebyshev quadrature [47],Ξ1can be expressed as
According to [17],o1is a sufficiently large value,χ(y)andχ′(y)in Ξ2can be approximated asχ(y)≈ζ1(1+y)-1,χ′(y)≈ζ1.Therefore,Ξ2can be expressed as
The proof is complete by substituting (B.1)-(B.5)into(8).
- China Communications的其它文章
- Spatial Modeling and Reliability Analyzing of Reconfigurable Intelligent Surfaces-Assisted Fog-RAN with Repulsion
- An Efficient Federated Learning Framework Deployed in Resource-Constrained IoV:User Selection and Learning Time Optimization Schemes
- ELM-Based Impact Analysis of Meteorological Parameters on the Radio Transmission of X-Band over the Qiongzhou Strait of China
- IoV and Blockchain-Enabled Driving Guidance Strategy in Complex Traffic Environment
- Multi-Source Underwater DOA Estimation Using PSO-BP Neural Network Based on High-Order Cumulant Optimization
- A Privacy-Preserving Federated Learning Algorithm for Intelligent Inspection in Pumped Storage Power Station

