IQR-based approach for DDoS detection and mitigation in SDN
Rochk Swmi ,Mynk Dve ,Virender Rng
a Department of Computer Engineering, National Institute of Technology, Kurukshetra, India
b Department of Information Technology, Delhi Technological University, Delhi, India
Keywords:SDN DdoS IQR Controller CPU utilization Packet_in
ABSTRACT Software-defined networking(SDN)is a trending networking paradigm that focuses on decoupling of the control logic from the data plane.This decoupling brings programmability and flexibility for the network management by introducing centralized infrastructure.The complete control logic resides in the controller,and thus it becomes the intellectual and most important entity of the SDN infrastructure.With these advantages,SDN faces several security issues in various SDN layers that may prevent the growth and global adoption of this groundbreaking technology.Control plane exhaustion and switch buffer overflow are examples of such security issues.Distributed denial-of-service(DDoS)attacks are one of the most severe attacks that aim to exhaust the controller's CPU to discontinue the whole functioning of the SDN network.Hence,it is necessary to design a quick as well as accurate detection scheme to detect the attack traffic at an early stage.In this paper,we present a defense solution to detect and mitigate spoofed flooding DDoS attacks.The proposed defense solution is implemented in the SDN controller.The detection method is based on the idea of an statistical measure -Interquartile Range (IQR).For the mitigation purpose,the existing SDN-in-built capabilities are utilized.In this work,the experiments are performed considering the spoofed SYN flooding attack.The proposed solution is evaluated using different performance parameters,i.e.,detection time,detection accuracy,packet_in messages,and CPU utilization.The experimental results reveal that the proposed defense solution detects and mitigates the attack effectively in different attack scenarios.
1.Introduction
In the generation of rapid deployment of cloud infrastructure for demanding applications,traditional network switching architectures are inefficient.This is because these architectures are difficult to reconfigure and program for changing requirements.The traditional switching networks are based on a strong coupling of data and control planes as these planes are tightly integrated with each other.Data plane include different forwarding devices such as routers,switches,etc.The control plane is responsible for implementing control logic for the forwarding decisions taken by the data plane devices.The network management tasks in these networks are complex,time-consuming,and costly.For example,in case of requiring an update or adding a new policy in the existing mechanisms,the essential modifications are to be made on all the forwarding devices in the entire network.Software-defined networking (SDN) technology has been developed recently to address such challenges.SDN enables the flexibility and automation in network configuration for current and future networks in order to improve the performance of the networks.SDN offers a centralized network intelligence in one network component (i.e.,control plane) by separating the control logic from forwarding devices[1,2].In SDN,the complete control logic is employed in the control plane that may consist of one or more controllers [3].The functions of the controller in SDN are to manage all the forwarding devices and to take the routing decisions.The communication between controller and forwarding devices is offered by an standard protocol such as OpenFlow [2,4,5].OpenFlow was developed by Open Net-working Foundation (ONF),and came into existence in 2008 [6].These properties of SDN provide a programmable,cost effective,and less time-consuming mechanism over traditional networks [7].However,this effective and intelligent technology also introduces several security vulnerabilities that already exist in traditional networks [8].The adversaries exploit vulnerabilities of traditional networks to launch various attacks.One of such popular attacks is known as Distributed denial-of-service(DDoS)attack[9].
DDoS is considered as one of the most disastrous attacks that target government and business organizations.It aims to disrupt the normal functioning of the network by sending a massive amount of network traffic towards the victim and makes the normal users suffer from the unavailability of the service or network's resources [10-14].DDoS attacks are growing rapidly with time.The prime goal of DDoS attacks is to exhaust or overload the resources of the victim machine.DDoS attacks attempt to violate the availability of the system.In SDN,since controller is the most sensitive and intelligent entity of the complete network,it is,therefore,the most favorite target point of the attackers [15,16].Although,DDoS attack also affects switch and switch-controller channel,which creates switch’s flow table overflow and switchcontroller bandwidth consumption.The controller exhaustion can collapse the entire SDN network.By default,if the switch receives a new packet and does not find any matching flow rule in its flow tables,a message is forwarded to the controller in the form of packet_in message for taking an appropriate routing decision.The controller then sends a flow modification rule (Flow_Mod) to the switch to update its flow table as per the latest received flow rules.This Flow_Mod rule avoids the transferring of packet_in messages coming from the same source to the controller.This is because switch can take decisions by following the rules placed in flow table.In case of spoofed flooding DDoS attack,the attacker sends a large number of packets from various random IP addresses to the switch.When the switch does not find any matching rule in the flow tables for the incoming packet,a large number of packet_in messages is sent to controller for handling.This flooding of packets intends to exhaust the controller's resources,which creates a disruption to use the controller's services for normal users.Since the controller manages the complete network,DDoS attacks on the controller can jeopardize the working of the entire SDN network.Therefore,a defense solution against spoofed flooding DDoS attacks for SDN is necessary to be designed,which can provide timely detection and mitigation of the attacks.Various defense solutions to defend against such DDoS attacks have been proposed for SDN in the literature [17-28].Most of the presented solutions are classified into two categories,i.e.,statistical-based and machine learningbased.Statistical-based solutions are more preferable in the aspect of performance over machine learning-based solutions[29].This is because machine learning methods create a heavy computational burden and have challenging data requirements.Thus,statistical-based solutions are more favorable for real-time scenarios and motivate us to work on designing an statisticalbased defense solution.Therefore,in this research work,an statistical measure-Interquartile Range(IQR)based defense solution is proposed to detect the spoofed flooding DDoS attacks.IQR is based on the idea of placing the data values in different quartiles.Data values that violate the IQR-rule are considered as outliers.These outliers indicate a situation of suspicious network traffic and the respective source hosts of suspicious traffic are marked as attackers.SDN is capable enough to take appropriate defensive action if any malicious behaviour is detected.Thus,SDN-in-built functionalities are utilized to mitigate the attack after the detection of attackers.SYN flooding attack is one of the most used DDoS attacks as it can target the bandwidth,memory,and CPU of the controller in case of a large number of requests.This is the reason that we selected this attack to evaluate the proposed solution in this work.In the proposed work,SYN flooding attack is launched with a number of random spoofed IP addresses as illustrated in Fig.1.This type of DDoS attack affects the controller with more dangerous effects than a non-spoofed attack due to flooding from a large number of sources.An analysis related to this study has been presented in Ref.[30].
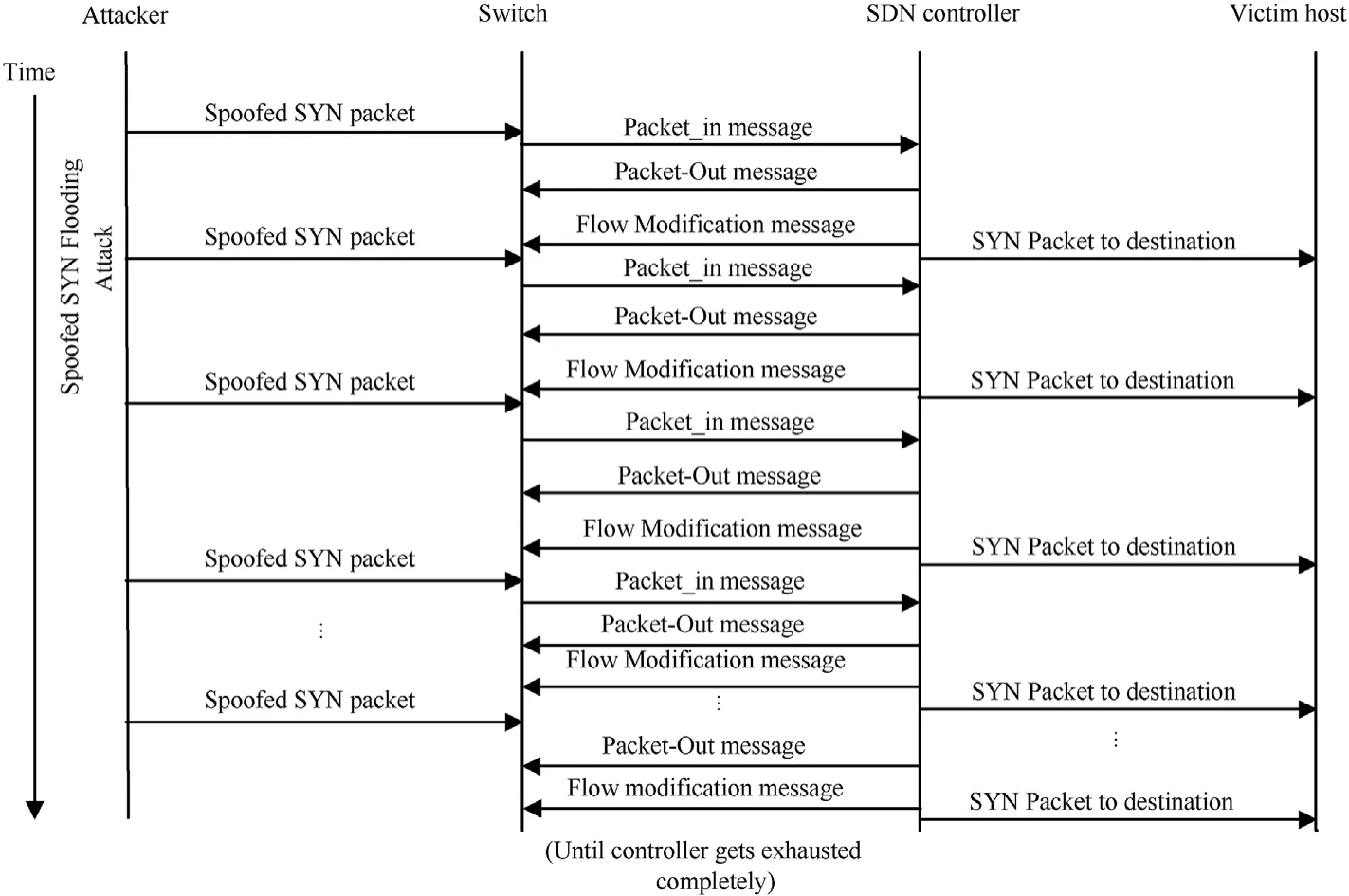
Fig.1.Spoofed SYN flooding attack in SDN.
The key contributions of the paper are summarized as follow:
-We propose and implement a defense solution to detect and mitigate spoofed SYN flooding attack in SDN.The detection method is based on IQR measure,which is applied on the receivedpacket_inmessages at a time interval followed by attacker detection.After attack detection,the mitigation is performed by blocking the identified attackers.
-We perform the experimental assessment considering different attack scenarios.The performance of the detection method(IQR)is evaluated in terms of detection time,detection accuracy in respect to the attacker's identification.
-The performance evaluation of the mitigation module is analyzed in terms of CPU utilization of controller andpacket_inmessages in three cases,i.e.,with no attack,under attack without defense,and with defense.
The remaining paper is organized in different sections as follows.Section 2 provides an overview of the existing SDN-based DDoS detection and mitigation mechanisms.Section 3 discusses our proposed defense solution,including its important modules.Section 4 introduces the simulation setup used for the experiments and presents an explanation of the evaluation results.The paper is concluded in Section 5.
2.Related work
In this section,relevant existing research works to defend against flooding DDoS attacks present in the literature are discussed.Flooding attacks are the most frequent DDoS attacks that slow down or crash the services by exhausting the resources of a system.SYN flooding attack is the most attempted DDoS attack among all the flooding attacks.Various defense solutions have been proposed and suggested in recent years to analyze the impact of DDoS attacks by the researchers.A few defense solutions are based on SDN specific network traffic and implemented in the SDN components.Mohammadi et al.[36] proposed a defense mechanism “SLICOTS" to defend the SDN network against SYN flooding attack.The detection logic is deployed in the controller.The proposed mechanism is implemented in OpenDaylight controller as an extension module.As per the proposed mechanism,a record is maintained with the counts of different types of TCP flags for a particular host.When the count of the records of respective host reaches threshold value,the malicious packet is dropped,and a flow rule is placed in the flow table to make the dropping of malicious packets.Kumar et al.[17]suggested a defense system named“Safety" that provides mitigation of SYN flooding attack.The proposed system is based on entropy variation for attack detection.The entropy is computed on destination IP and TCP flags.Performance is evaluated using CPU usage of the victim and controller,and attack detection time.One more entropy based defense mechanism was introduced by Kalkan et al.[18].The proposed mechanism named joint entropy-based security scheme (JESS) detects and mitigates the DDoS attacks.For attack detection,entropy is computed on the destination IP and different attributes of TCP layer.This is the first defense mechanism with the integration of joint entropy metric for SDN.It has the capability to mitigate unknown attacks also.The performance assessment of JESS is measured in terms of accuracy and false positive rate.Results indicate that JESS performs effectively with good performance results.Piedrahita et al.[34] presented a lightweight and fast DDoS detection mechanism named as FlowFence for SDN.The proposed detection approach is based on a congestion condition used to check the bandwidth utilization.The switches in the SDN network monitor the network traffic,and if the congestion happens,the controller is notified about the situation.The controller takes appropriate action against the congestion.The results indicate that FlowFence reduces the congestion in the network but does not prevent the attack completely.In Ref.[37],Buragohain et al.proposed a defense system,namely,FlowTrApp for data centers in SDN.The defense logic works on metrics,i.e.,flow rate and flow duration.These metrics decide the sending rate and flow duration used by normal hosts.The defense mechanism decreases the controller’s burden.In Ref.[22],an entropy based flooding DDoS detection technique is proposed for SDN.The proposed detection method is implemented on POX controller.The performance of solution is not measured using any standard metric.Also,it does not provide any mitigation scheme to reduce the CPU usage of the controller.Niyaz et al.[19] suggested a defense mechanism based on deep learning against flooding attacks(TCP,UDP,and ICMP)for SDN.The detection module is deployed on the POX controller.The performance assessment is done considering the parameters,i.e.,accuracy,precision,recall,and F-measure.Conti et al.[33] presented a detection approach for the detection of DDoS attacks in SDN.An statistical method,i.e.,cumulative sum and adaptive threshold is used as a detection method in the presented approach.Performance of the detection method is analyzed using detection time and detection accuracy.However,it does not provide any mitigation for the real-time attack situation.In Ref.[32],a timeseries based detection method is studied.Dehkordi et al.[25]presented an entropy and classification based detection mechanism against both the low and higher rate DDoS attacks.Results indicate that the detection mechanism achieves high accuracy but does not provide any mitigation solution,i.e.,it does not improve the performance of the controller.
Most of the existing statistical-based DDoS detection techniques utilized the concept of entropy in SDN.In this paper,we use IQR measure as a detection method.To the best of our knowledge,the IQR-based defense solution has been utilized for the first time in the SDN environment.More-over,few defense solutions provide the mitigation of the attacks in SDN.Our proposed defense solution detects the attack as well as reduces the impact of the attack on the controller.Details of some existing DDoS defense solutions are presented in Table 1.It also provides a theoretical comparison of existing defense solutions with the proposed solution.As per the comparison provided in Table 1,the research works [19,22,25,31-33] provide the detection of the DDoS attack.These works do not mitigate the DDoS attack,i.e.,do not reduce the impact of attack on the controller.But the proposed defense solution detects the attack as well mitigates the attack on the controller.Therefore,it can be said that the proposed work provides better performance as compared to other research works mentioned in Table 1.
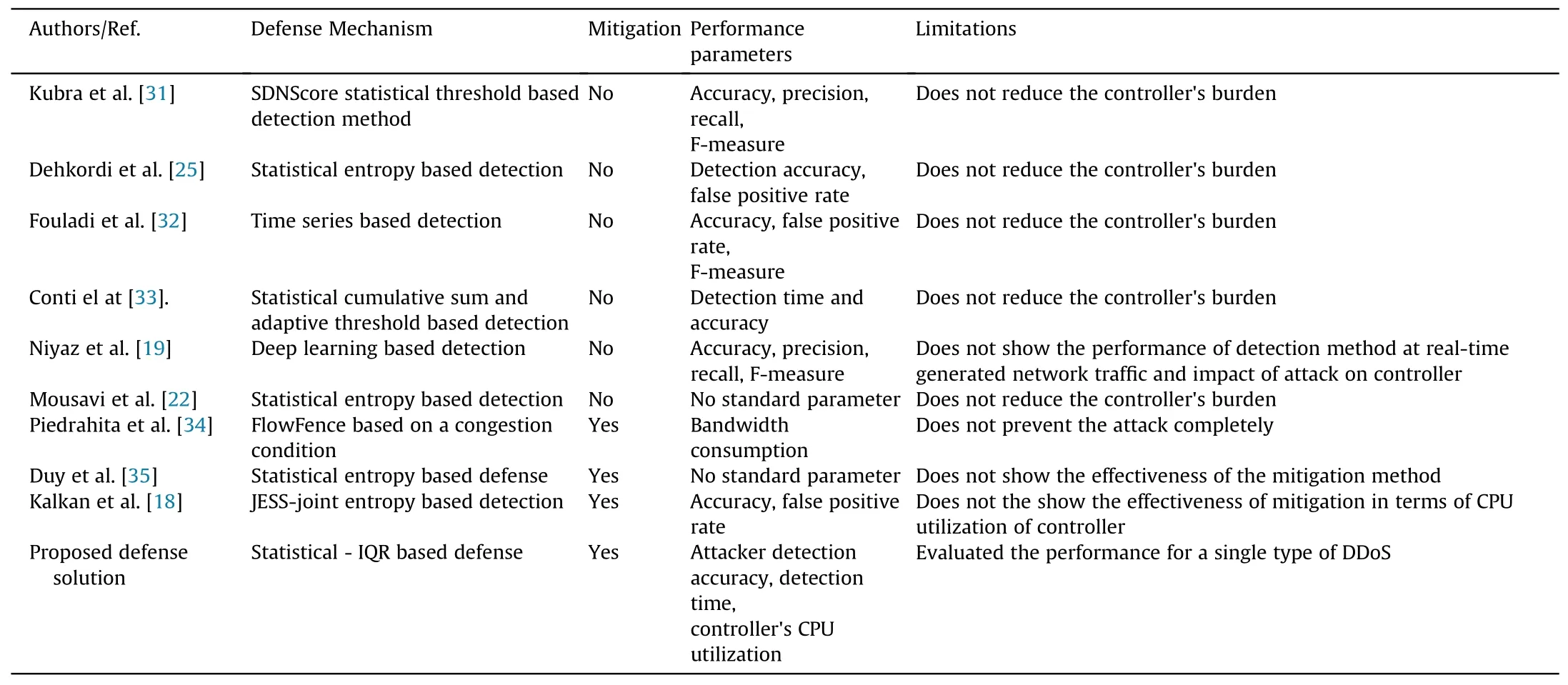
Table 1 Comparison of some existing defense mechanisms against DDoS attacks in SDN with the proposed defense solution.
3.Proposed defense solution
This section introduces the proposed defense solution that offers timely detection and mitigation of spoofed SYN flooding attack in SDN networks.Firstly,the base component of the proposed solution,i.e.,statistical measure -“Interquartile Range (IQR)" is discussed.Secondly,we present the designed architecture of the proposed solution and different modules in the form of algorithms.
3.1.Interquartile Range (IQR)
IQR is a popular outlier detection method.An outlier rep resents a value,which deviates from the overall pattern of data[38].Outlier detection has been widely used to detect anomalies.It can be defined in simple words as“something that is significantly different from others".There are various existing methods to identify the outliers,i.e.,Z-score,IQR(univariate)and Density-based clustering,distance-based outlier detection,isolation-forest (multi-variate).However,IQR is one of the most commonly used outlier detection methods.IQR can be defined as a measure of statistical dispersion.IQR is a univariate method in statistical modeling,which utilizes a measure “median" to locate the different data points.The use of measures like median,mean,and mode depends on two factors,i.e.,type of variability and presence of outliers.In the case of less variability and no outliers,mean and standard deviation are used as statistical measures to classify the data.But if there is a chance of much variability and outliers,median and IQR are preferred to use.
IQR is computed by dividing number of data points into different quartiles.A quartile is a type of quantile that exactly divides the number of data points (ordered in ascending manner) into four quarters,which are of approximately equal sizes.The data points are separated using three quartiles indicated byQ1,Q2,andQ3,mathematically.Q1,Q2,Q3 represent first,second,and third quartile,respectively.In simple words,it can be said that the middle 50%of ascendingly ordered data resembles IQR.Mathematically,IQR is defined as the difference betweenQ3 andQ1,as shown in Eq.(1).
The following steps are involved in determining the value of IQR.
1.Compute median (Q2) of the whole data.
2.Compute first(Q1)and third(Q3)quartiles by taking median of lower half and upper half of the data.
3.Compute IQR using Eq.(1).
In Ref.[39],Tukey et al.presented 1.5×IQR-fences to be used as IQR-rule to mark the possible outliers.According to the proposed IQR-rule (1.5 × IQR),two Eq.(2) and Eq.(3) are utilized as lower bound and upper bound,respectively.The data values that are below lower bound and that are above upper bound are flagged as outliers.
3.2.Architecture and functionalities
In this section,the working of the proposed defense solution is discussed.Fig.2 presents a flowchart of the overall architecture of the defense solution.The overall architecture is based on two working modules: detection module and mitigation module.The detection module is responsible for the detection of malicious traffic.The proposed solution utilizes the concept of outlier detection to identify malicious traffic.Detection method is based on IQR statistical measure acting as a classifier to classify the traffic into attack and normal classes.The key objective of the detection module is to identify the hosts that present significantly different behaviour.The host that shows anomalous behaviour is called an outlier host.As per the proposed detection method,the host from where a large amount of malicious traffic received is marked as an outlier host.There are two equations (Eq.(2) and Eq.(3)) for calculating IQR.To detect the spoofed SYN flooding attack,Eq.(3)is used in the proposed defense solution.The existing Eq.(3) adds some delay in the attack detection.Therefore,the equation is modified as per the requirement of the detection method.For the required modification,many experiments are conducted to determine an appropriate value ofupper bound.The selection ofupper bounddepends on the improvement in the attack detection time.The modified Eq.(3) is shown in Eq.(4),where y is a tuning parameter.In the proposed solution,tuning parameter is used to enhance the performance of the detection method in terms of responsiveness (attack detection time).

Fig.2.Flowchart for proposed defense solution.
The working logic of the detection method can be understood in the context of our work as follows.When network traffic is monitored in the case of spoofed SYN flooding DDoS attack,it can be observed that the victim host receives a large number of SYN requests from attacker hosts as compared to other normal hosts.These spoofed SYN requests are sent to controller aspacket_in.On the receiving a number ofpacket_inmessages,some important measures likeQ1,Q2,Q3,IQR,andupper boundare computed at a time interval.Theupper boundis utilized as a threshold to check the number ofpacket_inmessages received at the controller.It acts as an essential condition to decide if a host is suspicious or normal.In the normal (non-attack) scenario,thepacket_inreceived at the controller by switch are below theupper bound.Thus,there is no outlier (malicious behaviour) detected.However,in an attack scenario,the count ofpacket_inreceived is greater than theupper boundlimit.This kind of behaviour will be flagged as an attack scenario.The victim host and source of the attack are the output provided by the detection module.The source of the malicious traffic can be identified as an outlier.This logic is deployed as an attack detection method in the proposed solution.In the proposed work,source of the attack is located withdpid(datapath identifier)of the respective switch and itsin_port.When the attachment point of the attacker host (dpid,in_port) is identified,working of the mitigation module is started.
The proposed defense solution consists of three procedures:
PAcket_IN_HANDLER,DETECTION_MODULE,andMITIGATION.Pseudo-codes of these procedures are presented in Algorithms 1,2,and 3.Table 2 lists out different symbols and their respective explanations used in the proposed algorithms.

Table 2 Symbols and definitions.
3.3.Description of PAcket_IN_HANDLER procedure
Pseudo-code ofPAcket_IN_HANDLERprocedure is presented in Algorithm1.ThePAcket_IN_HANDLERprocedure is implemented as a modified version ofpacket_in_handler,i.e.,standard method of the SDN controller (Ryu).packet_in_handleris executed after the reception of thepacket_inmessage from the SDN switch.This method is responsible for the handling ofpacket_inmessages and installing the new flow rules in the switch to process the further incoming packets.Similarly,PAcket_IN_HANDLERprocedure is executed whenever apacket_inmessage is received at the controller.According to the proposed solution,rules are set in the switches in such a way that spoofed SYN packets are sent to the controller by default.In the proposed solution,two threshold values are used to check on the suspicious traffic.Firstly,upper_boundacts as a threshold for identifying if the respective host is normal or suspicious.After that,dcount(p)is used as a block threshold.The block threshold reduces the chance of permanent blocking of falsely detected hosts as suspicious.This is why,when an attack scenario is identified,corresponding dpid,inport(attachment point of the suspicious host)as the source of malicious traffic are stored in a suspicious state.The network traffic from such a suspicious host is allowed to the victim host until the block threshold meets its limit condition.The source of the victim host is permanently blocked when the block threshold reaches its threshold and marked as an attacker.We have considered the value of p as 5.In theupper_boundcondition,a tuning parameter (y) is also used to quickly detect the attack situation.
This procedure performs some major functions:
-Early detection of the blacklisted host and dropping the malicious packet without going through the whole detection process
-Maintains an info table(info)to store the information related to the incoming packet_in messages
-ExecutesDETECTION_MODULEprocedure after fixed time interval to check on the suspicious hosts.
3.4.Description of DETECTION_MODULE procedure
TheDETECTION_MODULEprocedure is an important part of the proposed defense solution.This procedure is responsible for two major functions: Checks and identifies the malicious hosts as outliers present in the info table (info);Maintains a blacklist table(blacklist) to store the information related to suspected and permanently blocked hosts.Pseudo code ofDETECTION_MODULEis presented in Algorithm 2.The necessary computations(i.e.,Q1andQ2) are made on the count ofpacket_inmessages received from different hosts to detect the malicious hosts.InDETECTION_MODULEprocedure,the IQR method is deployed to compute the thresh old (i.e.,upper_bound).All the hosts ininfoare checked againstupper_boundand if any of the host does not satisfy the threshold condition,a“suspicious scenario situation"is labeled,and then the victim host(dstip)with their respectivedpid,inportis inserted into the blacklist table (black list).After the victim host is detected,itsdpidof the corresponding switch andinportare identified as the source of the victim host.The source host is marked as an attacker and blocked permanently if it is under suspicion for p times.Then the attachment point(dpid,inport)from where attack traffic comes,is passed to theMITIGATIONprocedure.MITIGATIONprocedure is executed every time upon detection of the attacker host.Also,the entry of the located attacker host is removed frominfo.
Algorithm 1.Psuedo-code of PAcket_IN_HANDLER procedure
3.5.Description of MITIGATION procedure
After the processing ofDETECTION_MODULEis over,mitigation of the attack is performed.The pseudo-code of theMITIGATIONprocedure is presented in Algorithm 3.The primary function of the mitigation module is to prohibit malicious packets.This is achieved by SDN-in-built functionalities.As per these functionalities,a flow modification rule is installed in the flow table of switch,enabling the dropping of packets from the detected attachment point(dpid,inport)of the attacker host.The working flow of mitigation strategy is described in Fig.3.

Fig.3.Mitigation procedure after attacker's detection in the proposed defense solution.
Algorithm 2.Psuedo-code of DETECTION_MODULE procedure
Algorithm 3.Psuedo-code of Mitigation procedure
4.Simulation setup and performance analysis
In this section,the required network setup to carry out the experiments is discussed.The experimental topology is presented in Section 4.1.Section 4.2 provides a discussion of the considered parameters to evaluate the performance of the proposed solution and analyzes the performance results.All the experiments are performed on an SDN emulator -Mininetv2.3.0d6 [40].Mininet creates a virtualized network scenario consisting of hosts,switches,and links on a single Linux kernel and provides the flexibility of custom topologies.The OpenFlow supported Open vSwitch (OVS)v2.9.5[41]is used,which supports the virtual ports and routing of network traffic.In SDN network,a 64-bit identifier calleddpid(Datapath Identifier) is associated with each virtual switch(OpenFlow-based).Eachdpidcontains some virtual ports identified byin_port.Ryuv4.32[42]is utilized as SDN controller,on which the defense solution is implemented.A standard protocol “OpenFlow"v1.3 is used to make the communication between switches and controller possible.For generating TCP traffic,a Python based packet generation tool named Scapy [43] is used.For conducting experiments,attacker host is allowed to send attack traffic for 600 s.The detection module is executed repeatedly after every 25 s to check for suspicious hosts.Table 3 presents a brief overview of the setup details.

Table 3 Experimental setup.
4.1.Experimental topology
The experimental topology consists of 1 OVS and 21 hosts.All the hosts use a bandwidth of 100 Mbps.Open vSwitch is connected with Ryu controller.The simulations are con-ducted on different attack scenarios (as presented in Fig.4).Each attack scenario consists of number of attacker and normal hosts (non-attacker).In all the scenarios,every attacker sends the spoofed SYN packets at rates varying from 50 to 300(50,100,150,200,250,300)packets/second.These scenarios are discussed as below:
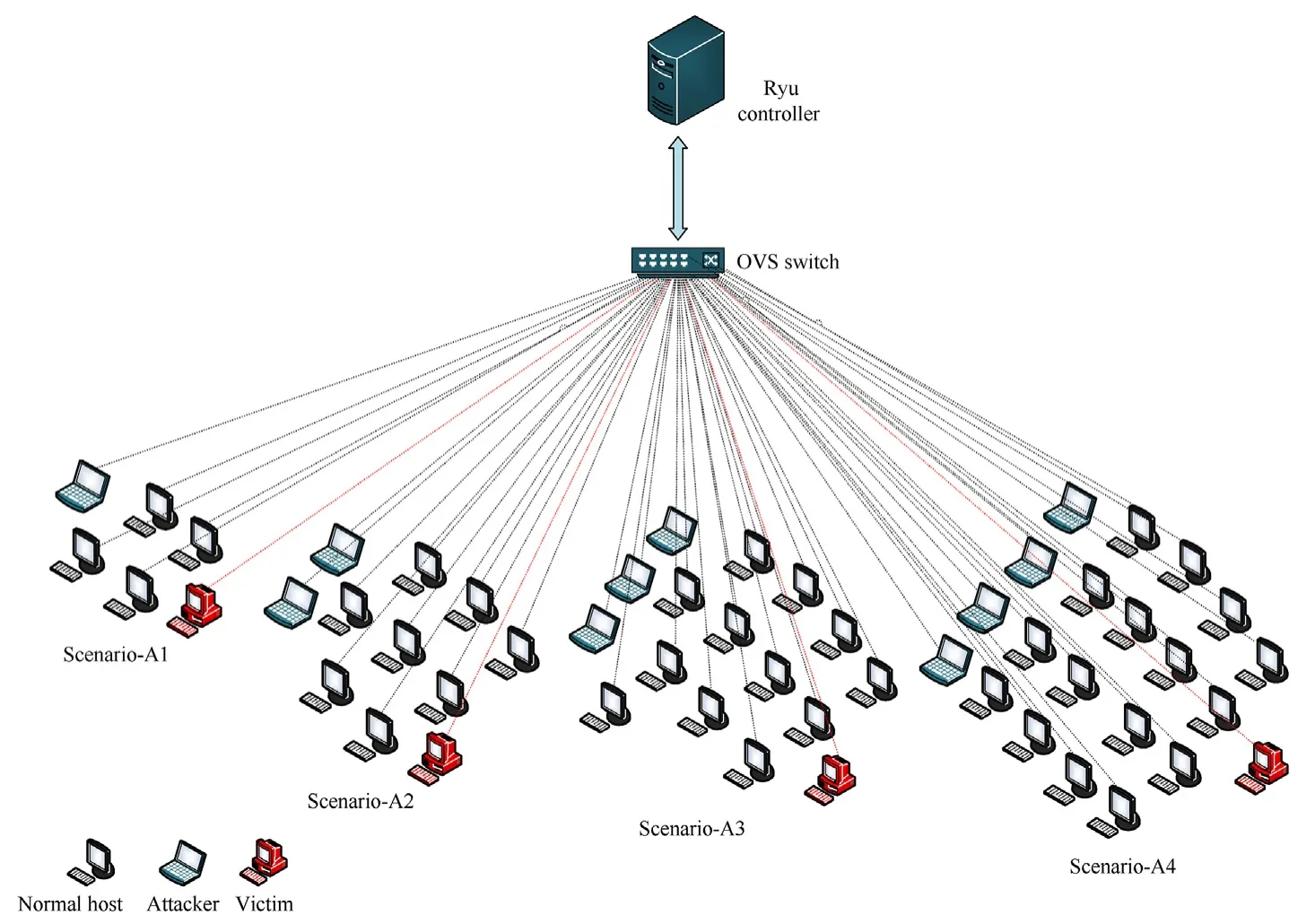
Fig.4.SDN topology used in the experiments.
-Scenario-A1:In this scenario,the number of attacker and normal hosts are 1 and 4,respectively.The attacker sends spoofed SYN packets at different rates.One host is considered as a victim.
-Scenario-A2: The number of attackers is 2 and 8 hosts act as normal hosts inScenario-A2.Each of the attackers sends the spoofed SYN packets at different rates as similar toScenario-A1.One host acts as a victim.
-Scenario-A3: In this scenario,3 hosts are used as attackers and 12 hosts are used as normal hosts.All the attackers send the spoofed SYN packets at different packet rates.
-Scenario-A4:In this scenario,the number of attacker and normal hosts is 4 and 16,respectively.The attack is simulated at different packet rates from all the attacker hosts.
4.2.Performance evaluation
This section discusses an analysis of the results of the proposed defense solution in respect of different performance parameters.
4.2.1.Evaluation parameters
The effectiveness of the proposed defense solution is measured using different evaluation parameters.The proposed solution is based on two working modules,i.e.,detection and mitigation.The detection module is evaluated in terms of detection time and detection accuracy.The impact of spoofed SYN flooding attack on the controller is analyzed in terms ofpacket_inmessages received and CPU usage of the controller under attack with mitigation strategy.The definitions of the evaluation parameters are as follows:
-Average attacker's detection time(AADT):It is defined as the time interval between the first SYN packet sent by the attacker and attack detection by the SDN controller.AADTis presented in Eq.(5).
wheretdetectioniandtlaunchiare the time of attacker detection and initiation of the first attack packet from theith attacker.nattactersis the number of attackers present in the network.
whereatrue,ntruerepresent the number of correctly detected attackers and normal hosts (non-attackers),respectively.afalse,nfalseare wrongly detected attackers and normal hosts,respectively.
-Attacker's detection accuracy(ADA): It is defined as the ratio of total number of correctly detected observations (attackers and normal hosts) over all the observations made by the detection method.ADA is shown in Eq.(6).
-Number of packet_in messages:It represents the total number ofpacket_inmessages received at the controller.These are sent by the switch as they are unable to handle the spoofed packets.Packet_inis an OpenFlow message that can be captured on an OpenFlow port by monitoring the respective interface.
-Average CPU usage of the controller: It is defined as the CPU consumption of the running SDN controller.The CPU usage is calculated by monitoring the respective process id (PID) of the controller for a duration.In this work,CPU usage is monitored for the Ryu controller.
4.3.Simulation results
For performance evaluation of the proposed defense solution,many experiments are conducted on all the scenarios as discussed in Section 4.1.In this section,the performance of the proposed detection method is analyzed in terms of attacker's detection time and detection accuracy.We also analyze the impact of spoofed SYN flooding attack on the controller in terms of CPU usage and receivedpacket_inmessages for both the cases,i.e.,under attack with and without defense.
4.3.1.Performance of detection method in terms of attacker's detection time
The timely detection of any malicious behaviour is very important for the applications of cyber security.Considering this major aspect,we have evaluated the performance of the proposed detection method in terms of detection time.Fig.5 presents average attacker detection time to identify the present attackers in the SDN network with varying packet rates for all the scenarios.The detection time is computed by calculating an average of the time taken to detect each attacker in a scenario.These scenarios are indicated byScenarioA1,Scenario-A2,Scenario-A3,andScenario-A4.It can be seen that attacker’s detection time does not increase over 157 s for all the scenarios.Scenarios-A1 outperforms all other attack scenarios(A2,A3,and A4) over all the other packet rates in terms of attacker detection time.The detection time increases when the number of attackers is increased.The proposed mechanism achieves maximum detection time to detect the most aggressive attackers in the case of Scenario A4,i.e.,attack at the packet rate of 300 packets/second.It can be concluded from the achieved results that an increase in number of attackers and attack packet rate does not affect the detection time as much.Although,it takes less time to detect only one attacker at less packet rate than multiple attackers at a higher rate as shown in Fig.5.
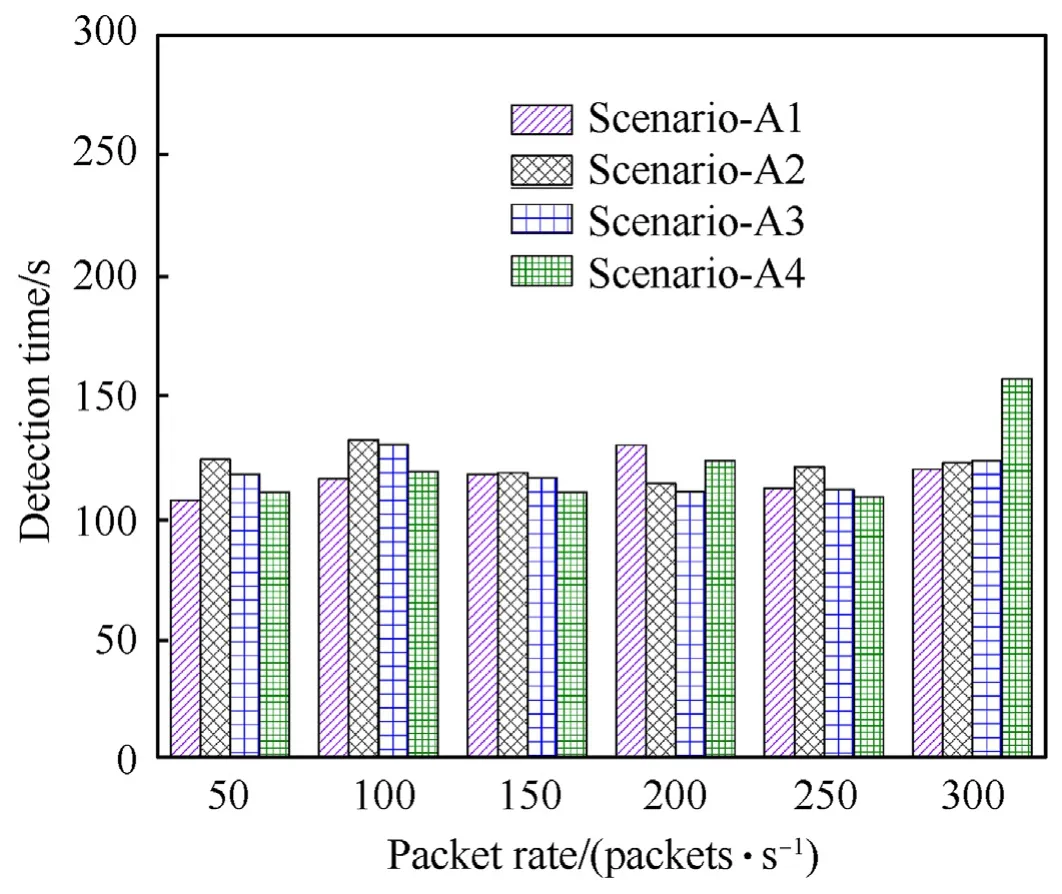
Fig.5.Average detection time to detect attackers with varying packet rates for different scenarios.
4.3.2.Performance of detection method in terms of attacker's detection accuracy
Accuracy is another important parameter to evaluate the performance of a designed scheme.We assessed the detection accuracy of the proposed defense solution in different attack scenarios,as shown in Fig.6.It shows the performance of the defense solution in terms of accuracy,considering the presence of both the attackers and normal hosts.Fig.6 shows the achieved accuracy concerning elapsed time and different packet rates.Fig.6(a) presents the achieved accuracy by the proposed solution in case of attackScenarioA1.It can be seen from the figure that the accuracy of the defense solution is perfect as 100% inScenario-A1at all the packet rates.Also,accuracy does not get affected by the elapsed time with the presence of normal hosts.Accuracy achieved by defense solution in case of attackScenario-A2is presented in Fig.6(b).It can be observed that in the case ofScenario-A2,the defense solution performs best by achieving 100%detection accuracy at the packet rates of 100,150,200,250,and 300 packets/second during the elapsed time.With the packet rate of 50 also,it achieves 100% detection accuracy initially.Later,accuracy decreases with time after some time has elapsed,and it reaches 90%.Similarly,Fig.6(c) and (d)present the accuracy variation as per the time and different packet rates in the case ofScenario-A3andScenario-A4,respectively.It can be observed from the results that in theScenario-A3also,accuracy remains 100%initially with all the packet rates.With the time elapsed,accuracy decreases to 93%at the packet rate of 50 packets/second.In the case ofScenario-A4,the defense solution performs with accurate detection of attackers and normal hosts at the packet rates of 50,100,and 150 during the elapsed time.Whereas the detection accuracy at the packet rates of 200,250,and 300 varies as per the elapsed time.Initially,the proposed solution achieves 50% accuracy at the rate of 300.After that,accuracy increases to its maximum of 100% with the detection of all the attackers correctly.Finally,it decreases to the maximum of 95%as per the time.With the packet rates of 200 and 250 also,accuracy decreases with the time duration and the proposed defense solution achieves the overall accuracy of 95%.The detection accuracy decreases after some time because after detection of all the attackers correctly,some normal hosts can be identified as attackers mistakenly.However,by considering all the attack scenarios with all the used packet rates,it can be concluded that the proposed defense solution achieves a maximum of 100% accuracy in case of(Scenario-A1).In the DDoS attack scenarios (Scenario-A2,A3,A4),the defense scheme performs better by achieving a maximum of 95% and a minimum of 93% accuracy concerning time and all the packet rates.The number of attackers and normal hosts are added incrementally with respect to the network topologies used in the different attackScenario-A2,A3,A3.This creates an increase in the transmission ofpacket_inmessages even from the normal hosts,making the normal hosts suspected as an attacker due to being detected as an outlier.However,the block threshold(β)avoids the permanent blocking of normal hosts.
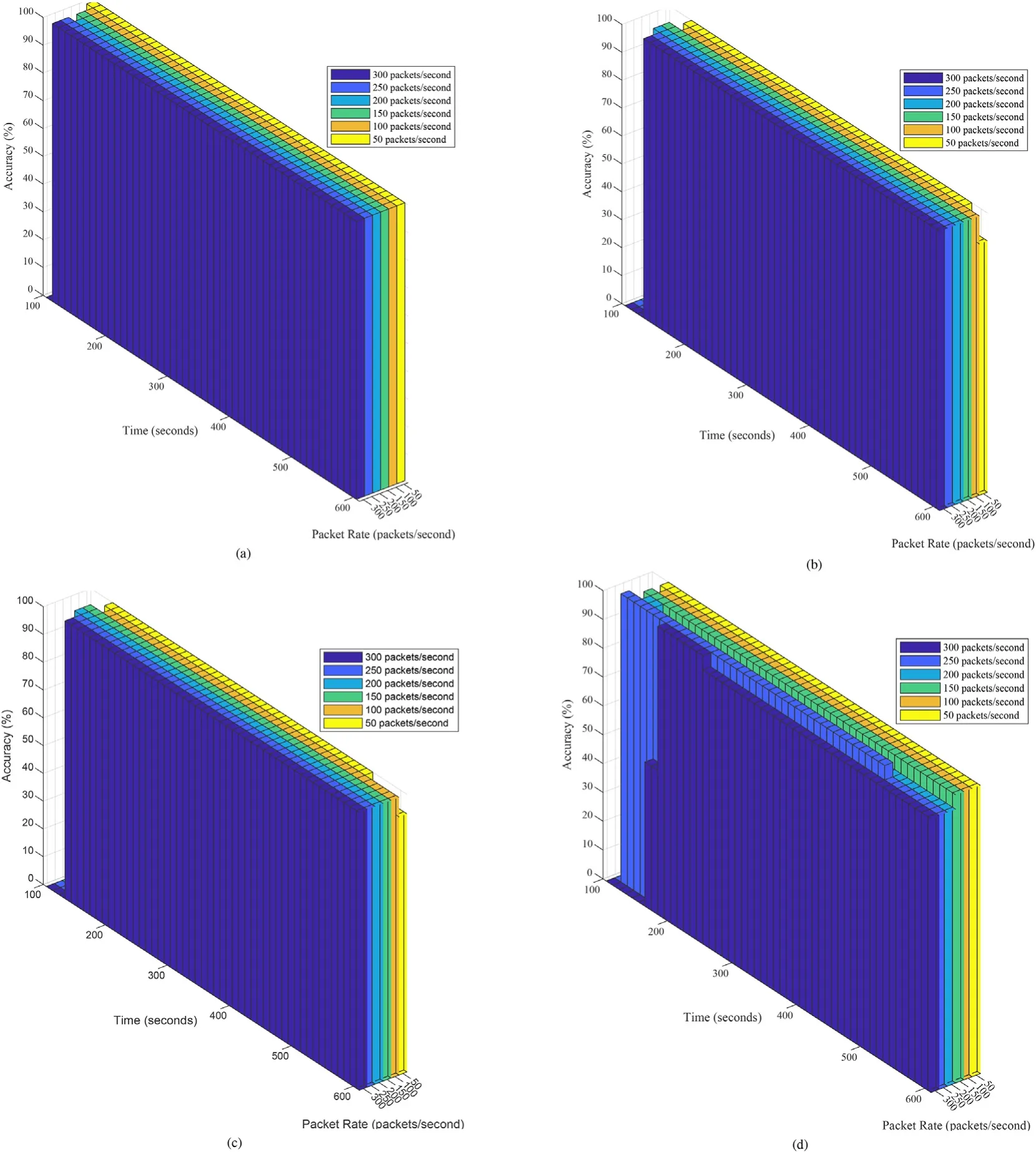
Fig.6.Detection accuracy of the proposed defense scheme.
4.3.3.Impact on controller in terms of packet_in messages
In the case of spoofed flooding attack,a large number ofpacket_inmessages is forwarded to the controller by the SDN switch.This flooding ofpacket_inmessages creates a huge CPU overhead on the controller to be handled.Thepacket_inmessages are important to analyze the impact of the attack on the controller.Reducing the controller’s burden is one of the prime requirements of the SDN network in case of flooding DDoS.Therefore,in our work,we analyze the performance of the proposed solution in terms of number of packet_in messages received at the controller.Fig.7 shows a comparison of packet_in messages received in the case of under attack without defense and with defense for all the different attack scenarios (Scenario-A1,A2,A3,A4) with varying packet rates (50,100,150,200,250,300 packets/second).Increasing the packet rate and the number of attackers intends to the increased number of packet_in messages on the controller.It can be observed from the results that total number of packet_in messages increases with more intensity with the increase of number of attackers as compared to increase in the packet rate,which overburdens the controller.This is ensured from the comparison of packet_in messages values of Scenario-A1UnderAttack,A2UnderAttack,Scenario-A3UnderAttack,and Scenario-A4UnderAttackat different packet rates.Average value of packet_in messages received in case of Scenario-A1UnderAttackand Scenario-A1UnderAttack With Defense at different packet rates are 39080 and 15171,respectively.The average value of packet_in messages received in case of Scenario-A2UnderAttackand Scenario-A2UnderAttackWithDefenseat different packet rates are 82766 and 33365,respectively.Similarly,the average value of the packet_in messages received in the case of Scenario-A3UnderAttack,Scenario-A3UnderAttackWithDefenseand Scenario-A4UnderAttack,Scenario-A4UnderAttackWithDefenseat different packet rates are 129964,51038,and 176486,62378,respectively.It can be seen that the proposed solution reduces the number of incoming packet_in messages at the controller after identification of the potential attackers.This happens because the proposed solution firstly detects the existing attackers and blocks the respective dpid and in_port of the attacker to drop the attack packets.This blocking mitigates the impact of flooding attack on the controller effectively.
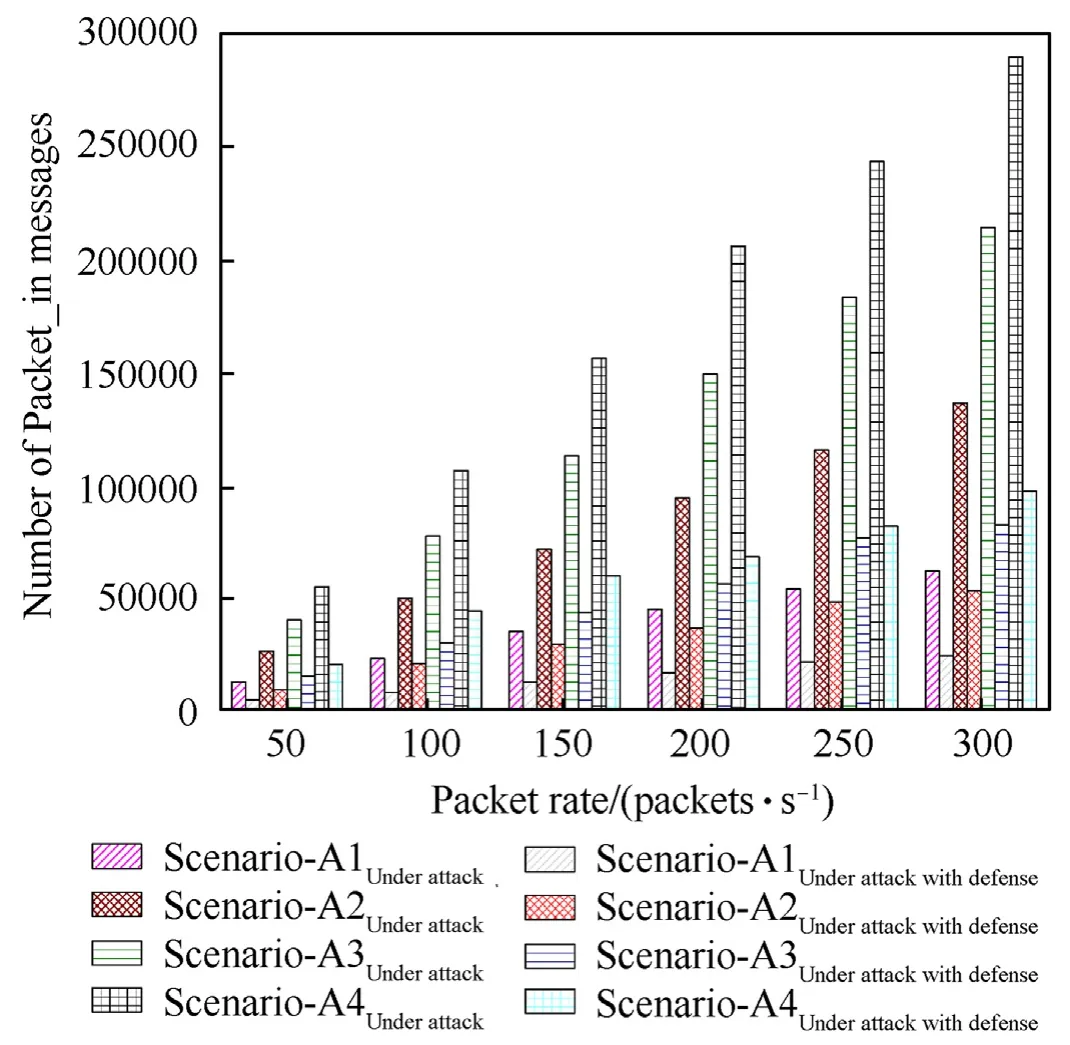
Fig.7.Number of packet_in messages with varying packet rates for different scenarios.
4.3.4.Impact on controller in terms of CPU usage
The controller manages all the crucial functionalities for the entire SDN network making it the most attractive target point of the attackers.Spoofed flooding attacks exhaust the CPU on the controller by forwarding a large number ofpacket_inmessages as discussed in Ref.[30].This exhaustion of the controller degrades the performance of the network.Thus,the controller's CPU usage is one of the essential factors to be per second forScenario-A1,Scenario-A2,Scenario-A3,andScenario-A4,respectively.The monitored CPU utilization for the case of without attack remains consistent at a very less amount for all the scenarios.It can be seen in Fig.8(a)that the CPU usage lies between 16.43%and 30.1%at an increasing packet rate.The proposed solution reduces the CPU usage up to a maximum of 62.35%and a minimum of 37.07%in case of Scenario-A1UnderAttackWithDefense.The attack Scenario-A2UnderAttackWithoutDefenseconsumes the controller's CPU between the range of 26.45%and 40.15%.The solution decreases the CPU consumption up to a maximum of 57.11%and a minimum of 51.68%as shown in Fig.8(b).The CPU utilization for Scenario-A3UnderAttackWithoutDefenselies between 31.06%and 51.53%.Fig.8(c)shows the performance of the mitigation solution under the running attack traffic (Scenario-A3UnderAttackWithDefense),which reduces the CPU usage up to a maximum of 56.91% and a minimum of 50.99%.The average CPU usage of the controller in case of Scenario-A4UnderAttackWithoutDe-fensevaries between 36.10% and 66.34% as shown in Fig.8(d).The improvement in the CPU consumption observed in the case of Scenario-A4UnderAttackWithDefensevaries between 42.43% and 57.58%.The proposed solution reduces the CPU consumption in the case of attack.The CPU usage initially goes at a higher value,and then it decreases suddenly.It happens because the defense solution detects the attackers present in the network and then instructs the switch to drop the attack packets by blocking the correspondingdpid,in_portof the attacker.It can be concluded that the proposed defense solution is capable of mitigating the DDoS attack traffic coming from attackers and reducing the impact of attack on the controller’s CPU.

Fig.8.Average CPU usage with varying packet rates for different attack scenarios.
5.Conclusions and future work
The SDN controller is the most attractive target point of the DDoS attackers due to its centralized nature.Currently,securing the controller from such attacks is the biggest challenging task in SDN.In this paper,we presented an statistical measure Interquartile Range(IQR)based technique to secure SDN networks from spoofed SYN flooding attack.The detection logic is applied to thepacket_inmessages received at the controller in every fixed time interval.After detection,mitigation is performed by blocking the identified attackers.The performance of the proposed defense solution is evaluated in terms of detection time,detection accuracy,packet_inmessages,and CPU utilization of the controller.The proposed defense solution is capable of timely detection as well as mitigation of the attack at the switch itself.The proposed solution has been designed to detect a single type of DDoS attack.Further,the defense solution is not evaluated on a large scale of normal hosts (nonattacker).In future,we aim to evaluate the proposed solution for various DDoS attacks on a larger scale in SDN.
Declaration of competing interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
- Defence Technology的其它文章
- Structural design of the fluted shaped charge liner using multi-section optimization method
- An aerial ammunition ad hoc network collaborative localizationalgorithm based on relative ranging and velocity measurement in a highly-dynamic topographic structure
- Molecular simulation study of the stabilization process of NEPE propellant
- Damage assessment of aircraft wing subjected to blast wave with finite element method and artificial neural network tool
- Experimental and numerical studies of titanium foil/steel explosively welded clad plate
- Effects of connection types and elevated temperature on the impact behaviour of restrained beam in portal steel frame

