Secure Transmission in Cognitive Radio Networks Using Full-Duplex Technique with Outdated CSI
Zhihui Shang ,Tao Zhang ,Guojie Hu ,Yueming Cai ,Weiwei Yang
1 College of Medical Information Engineering,Zunyi Medical University,Guizhou 563006,China
2 College of Communication Engineering,Army Engineering University of PLA,Nanjing 210007,China
3 The Sixty-third Research Institute,National University of Defense Technology,Nanjing 210007,China
4 Department of Communication Engineering,Rocket Force University of Engineering,Xi’an 710025,China
Abstract: This paper investigates the effects of the outdated channel state information (CSI) on the secrecy performance of an underlay spectrum sharing cognitive radio networks (CRNs),where the secondary user(SU)source node(Alice)aims to transmit the trusted messages to the full-duplex(FD)aided SU receiver (Bob) with the assistance of cooperative relay (Relay).Considering the impact of feedback delay,outdated CSI will aggravate the system performance.To tackle such challenge,the collaborative zero-forcing beamforming(ZFB)scheme of FD technique is further introduced to implement jamming so as to confuse the eavesdropping and improve the security performance of the system.Under such setup,the exact and asymptotic expressions of the secrecy outage probability(SOP)under the outdated CSI case are derived,respectively.The results reveal that i)the outdated CSI of the SU transmission channel will decrease the diversity gain from min(NANR,NRNB)to NR with NA,NR and NB being the number of antennas of Alice,Relay and Bob,respectively,ii)the introduction of FD technique can improve coding gain and enhance system performance.
Keywords: cognitive radio network;physical layer security;full-duplex;multiple antennas relay;secrecy outage probability;outdated CSI
I.INTRODUCTION
With the increasing demand for wireless communication equipment and services,spectrum resources are increasingly scarce.Cognitive radio networks(CRNs)has attracted the attention of a large number of researchers in the past decade,and it can effectively improve the scarcity and waste of spectrum resources[1,2].In CRNs,unauthorized secondary users(SUs)can directly access the spectrum allocated by the primary users (PUs) in the same frequency bands and spectrum idle,in which they cannot affect the quality of service (QoS) of the PUs [3,4].Compared to the three spectrum sharing methods,the SUs CRNs can coexist with the PUs under an underlay scheme,as long as the interference from the SUs is below a specified threshold[5].However,the sharing of spectrum resources is more likely to lead to the attack of malicious nodes,which thus faces security threats.
In order to solve the above-mentioned problems,the authors in [6] and [7] proposed the different protocols of the FD technique to maximize the secrecy rate,which,however,did not consider cognitive issues to improve spectrum efficiency.Thus,the physical layer security (PLS) research under the CRNs has entered people’s vision in recent years,which can strengthen the secure transmission of wireless communications[8-11].In an effort to further improve PLS of wireless transmissions,several techniques were proposed,such as zero-forcing beamforming(ZFB)[12-16]and fullduplex (FD) techniques [17-19].Particularly,beamforming can be used not only to eliminate the interference to the SUs and PU,but also to improve the secrecy performance of the system due to the more concentrated power to the malicious attackers[12,13].A secure beamforming design for a two-way CRNs was presented to improve the reliability performance by simultaneous information and power transfer in[14].A zero forcing-based iterative algorithm was proposed to study the secure beamforming design for the two-way CRNs[15].In[16],the authors proposed a zero-forcing jamming scheme to maximize the total secrecy rate in multiple-input-multi-output (MIMO)based CRNs.However,the above-mentioned papers all considered perfect channel state information(CSI),and gave no attention to the outdated CSI,which is resulted from the influence of the feedback delay.At the same time,FD technology is also employed to prevent eavesdropping by malicious attackers and to enhance spectral efficiency [6,17].FD relay was utilized in cooperative wireless communication system to enhance spectral efficiency and secure performance[18].The secrecy performance for a new collaboration ZFB transmission scheme with FD operative was analyzed in[19,20].In[21],the authors designed a new collaboration interference scheme with FD-SU overlay CRNs of perfect CSI to protect the secure transmission of PU.Perfect CSI of ZFB and FD techniques was assumed in these aforementioned works,which neglected the impact of the feedback delay on the secrecy performance of the CRNs.In the practical scenario,the perfect CSI is challenging to obtain and the outdated CSI is easy to deteriorate the QoS of the PUs and decrease the secrecy performance of the SUs.
As a further development,the work [22] studied the secure transmission in dual-hop randomizeand-forward (RaF) cognitive MIMO wiretap networks with outdated CSI where a transmit antenna selection/maximal-ratio combining scheme was proposed to maximize the total secrecy rate.The work[23] proposed a secure transmission scheme to reduce the interference to the PU in dual-hop decodeand-forward(DF)spectrum-sharing relaying networks with outdated CSI.Unfortunately,the aforementioned works did not carry out the related secrecy performance analysis of outdated CSI in FD aided CRNs.Motivated by this,in our paper,we will analyze the effects of outdated CSI on the secrecy performance of an underlay spectrum sharing CRNs with FD receiver.In order to improve the transmission quality,the transmit antenna selection-maximalratio combining-zero forcing beamforming/maximalratio transmission-selection combining-zero forcing beamforming (TAS-MRC-ZFB/MRT-SC-ZFB)scheme with FD receiver is designed in our paper.Moreover,considering the feedback delay,the received CSI at the transmitter (Alice,Relay and Bob)may be outdated,which may in turn deteriorate the performance of our considered scheme.In addition,our work also considers that the designed beamforming with FD operation will also be affected by the feedback delay.The contributions of our paper are summarized as follows:
• We propose a new TAS-MRC-ZFB/MRT-SCZFB scheme with outdated CSI.Then,the beamforming vectors of the jamming signals are designed at the FD Bob node such that they maximize the achievable secrecy rate of the system.Under this setup,the exact and asymptotic expressions for the secrecy outage probability(SOP)of our proposed scheme underlay CRNs with outdated CSI are obtained to evaluate the system performance.These newly analytical expressions for the asymptotic SOPs are used to analyze the secrecy diversity and coding gains.
• Moreover,it is observed that the outdated CSI of the SU transmission channel will decrease the diversity gain from min(NANR,NRNB) toNRwithNA,NRandNBbeing the number of antennas of Alice,Relay and Bob,respectively.Similarly,the outdated CSI between primary and SU links will also affect the SOP of the system.Based on the above reasons,we consider CRNs based on the outdated CSI by FD operation,in which it can effectively affect the system coding gain and further improve the system performance.
• Additionally,relatived to prior results,we investigate two different practical diversity combining techniques at Relay and Bob as well.The proposed scheme is compared with the existing work to verify the effectiveness of the former in improving system performance.That is because the collaborative ZFB scheme of the FD technique can mitigate the interference effectively and improve the secrecy performance of the considered networks.
The paper is organized as follows.Section II presents the system and channel model.Section III provides the closed-form expressions for SOP with outdated CSI.Section IV shows the asymptotic SOP analysis.The results and discussion are presented in Section V.Finally,conclusions are presented in Section VI.
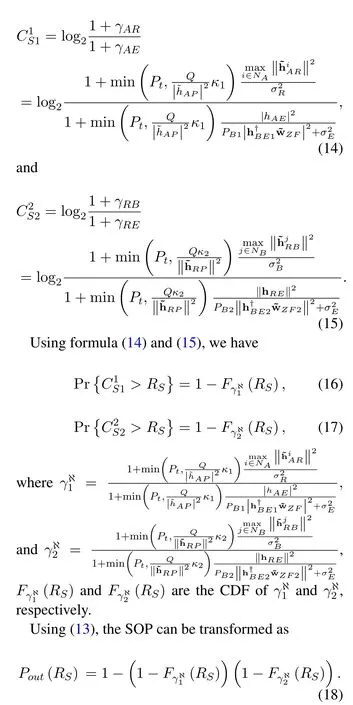
II.SYSTEM MODEL AND THE PROPOSED TRANSMISSION STRATEGY
We consider an underlay RaF spectrum sharing CRNs with FD receiver as illustrated in Figure 1 .Our designed model consists of aNAantennas source node(Alice),aNRantennas RaF relay node(Relay)and aNBantennas legitimate destination node (Bob),and a PU receiver node and a passive eavesdropper node(Eve)both equipped with a single antenna.In our paper,we mainly focus on the secrecy performance of the SU link and we make the following assumptions:a) the direct link does not exist in our system model due to the long distance between Alice and Bob and the severe shadowing effect.b) Since the secondary user transmission link is far from the PU transmitter,the interference from the PU transmitter is ignored.c)For simplicity,both main and secondary user transmission channels are assumed to experience quasi-static independent Rayleigh fading,and remain unchanged during each time-slot but vary independently from different time-slots.As in[22],the corresponding CSI of Alice to Eve and Relay to Eve are unknown at Alice and Relay,respectively.
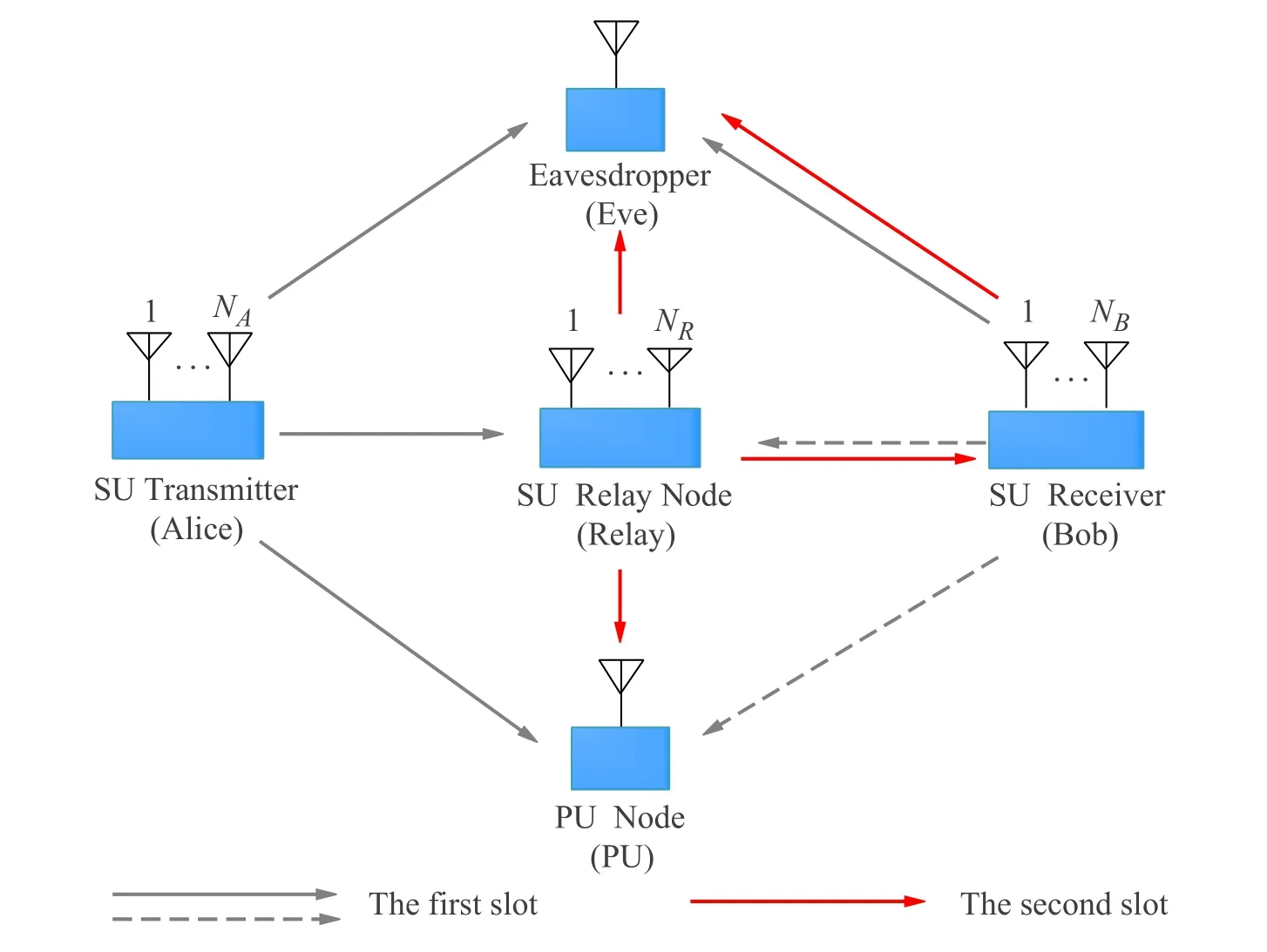
Figure 1. System model.
The data transmission process is accomplished over two time-slots.In the first time-slot Alice→Relay,Alice selects thei-th best antenna amongNAantennas according to the channel conditions between Alice and Relay.The FD Bob is designed to direct its beam to Eve and null Relay and PU nodes.The Bob utilizes the collaborative transmit beamforming to transmit the signal for minimizing the interference caused to Relay and PU.Eve is here as an eavesdropper of the dual role.The receiver at Relay node employs the TAS-MRC diversity reception.The Relay considered here is RaF relay because RaF relay outperforms DF relay in information processing [19].In the second time-slot Relay→Bob,Bob selects thej-th antenna amongNBto receive the signals from Relay.And the remainingNB -1 antennas,aided by beamforming,transmit the jamming signal to minimize the interference to the PU.The receiver at Bob node employs the MRT-SC diversity reception.To ensure the QoS for the PU,the transmit power of the Alice and Relay must be kept below a certain threshold so that the interference to the primary user is no greater than the interference temperatureQ.The channel coefficient of any two nodes follows a zero-mean complex Gaussian-random variables (CG-RV) with varianceλMN,such thathMN~CN(0,λMN).
2.1 Mathematical Model

2.1.1 In the Alice→Relay Link
The TAS-MRC-ZFB scheme is designed at Relay and Bob by using the outdated CSI.The instantaneous CSI foris available at Relay[26].Due to the existence of estimation error,the feedback error model of legitimate channel estimation at Relay can be formulated as
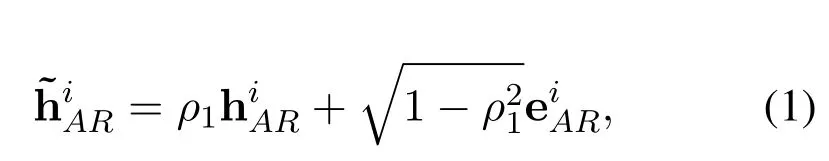
ZFB Collaborative Design at Bob: Due to the feedback delay between Bob and Eve,the CSI of the hBE1,whose value is available at Bob and used for designing the collaborative transmit ZFB weight ˜wZF,is assumed to be outdated,and the delayed channel is denoted by ˜hBE1.Eve is here as an illegal eavesdropper for legitimate users.The designed collaborative beamforming should meet two requirements: (i)it can directly point to the Eve;(ii)simultaneously,it causes no interference to Relay and PU.
Therefore,the beamforming design problem can be mathematically modeled as[30]
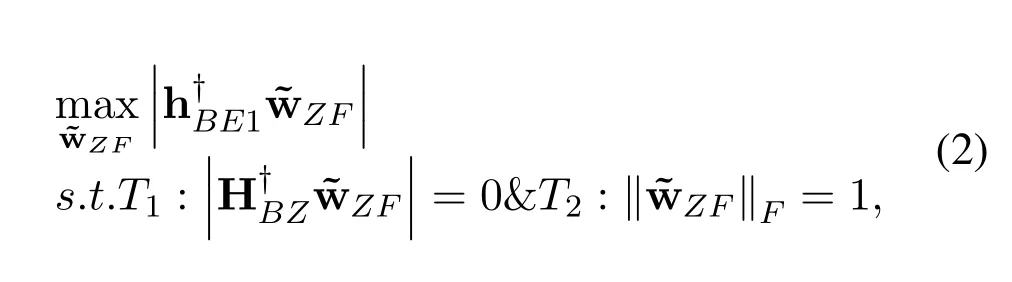
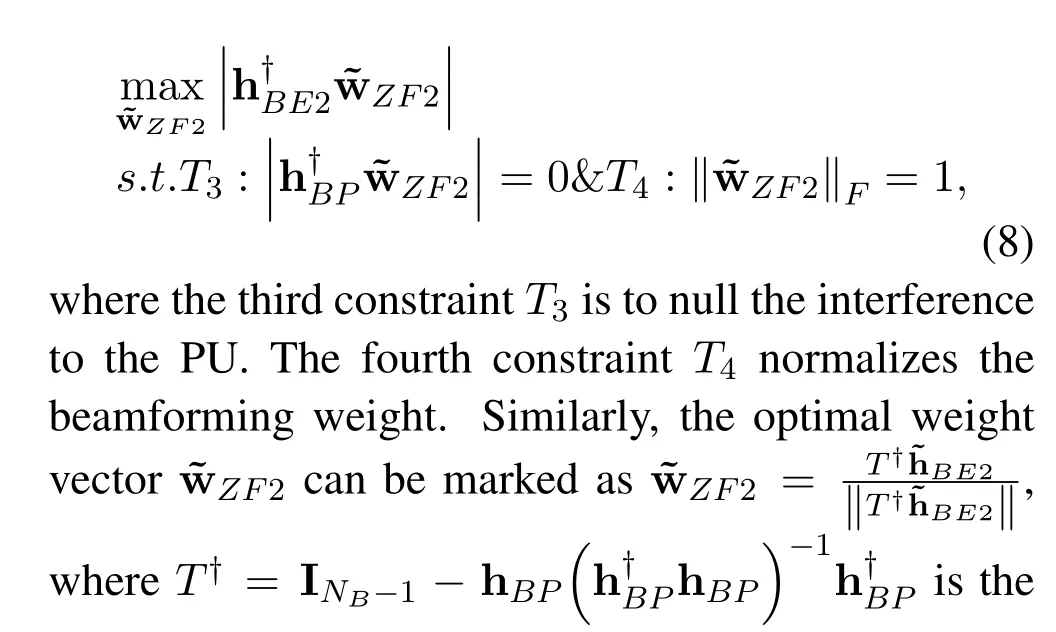
where‖·‖is theL2norm,and HBZ=[hBP,HBR].HBZis the actual interference channel estimate,which can be gathered by direct feedback from the Relay and PU with the help of collaboration between two systems or through indirect feedback by a band manager.The first constraintT1is to null the interference to the Relay and PU.The second constraintT2normalizes the beamforming weight.Now,using the projection matrix theory,the optimal weight vector ˜wZFcan be marked as
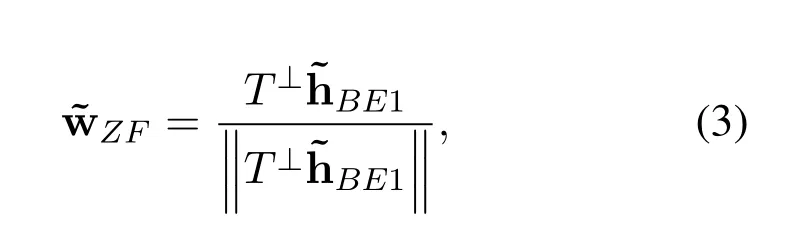
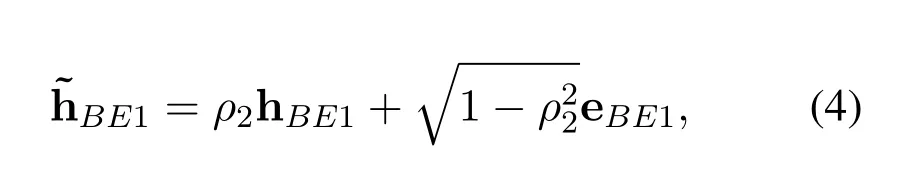
similarly,the parameter definitions ofBE1and hBE1are similar to(1).
Considering the outdated CSI,the corresponding signal-to-noise ratio (SNR) and SINR at Relay and Eve can be expressed as
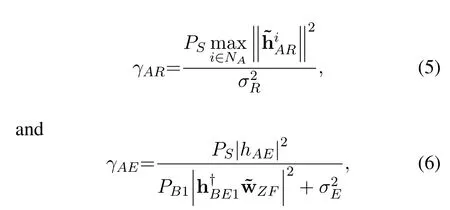
wherePSis the transmit power of Alice and it is limited by the PU interference temperatureQ.Ptis maximum transmit power via
whereκ1represents the power marginal factor at Alice.PB1is the transmit power of Bob.σ2Randσ2Eare the additive white Gaussian noise (AWGN) at Relay and Eve respectively.
2.1.2 In the Relay→Bob Link
The MRT-SC-ZFB scheme is designed at Bob by using the outdated CSI.The delay feedback error model can be presented as
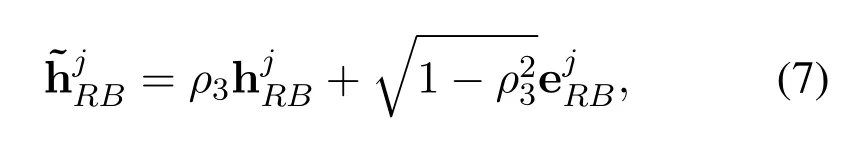
similarly,the parameter definitions ofare similar to(1).
ZFB Collaborative Design at Bob: The CSI of the hBE2,whose value is available at Bob and used for designing the ZFB weight ˜wZF2,is also assumed to be outdated,which is similar to (4).Therefore,the beamforming design problem can be mathematically modeled as
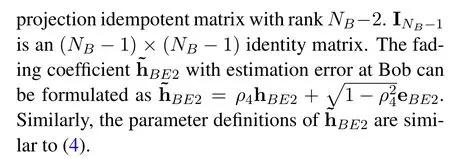
Due to the feedback delay,the corresponding SNR and SINR at Bob and Eve can be expressed as
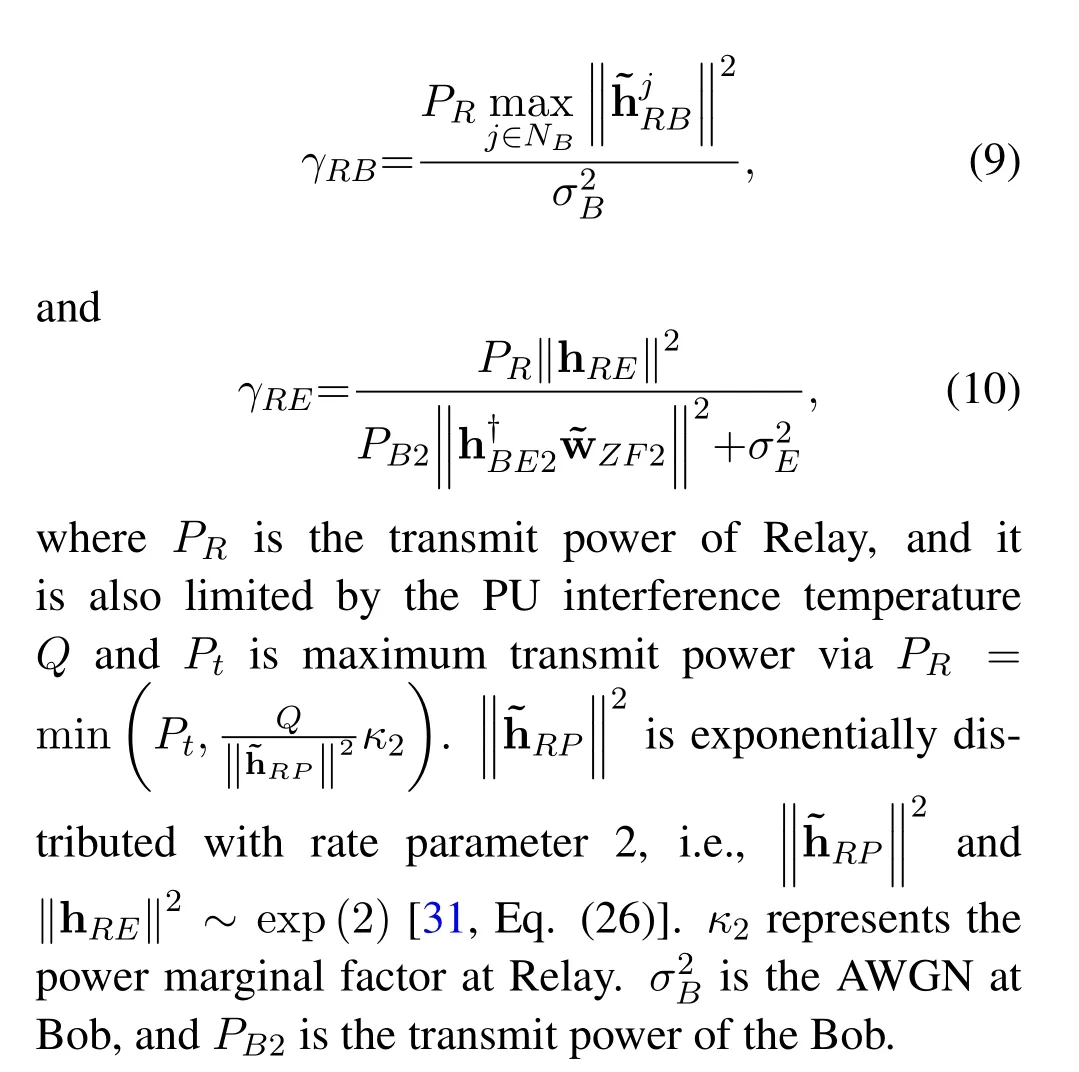
Considering that the CSI of the PUs and SUs links is outdated,it is difficult to meet the interference requirement at all times.In addition,we can use the probabilistic approach as in[32],where the Alice and Relay adapt their power such that the PUs can maintain a pre-selected outage probabilityP0.Furthermore,the closed expression ofκ1can only be obtained byP0.P0is expressed as
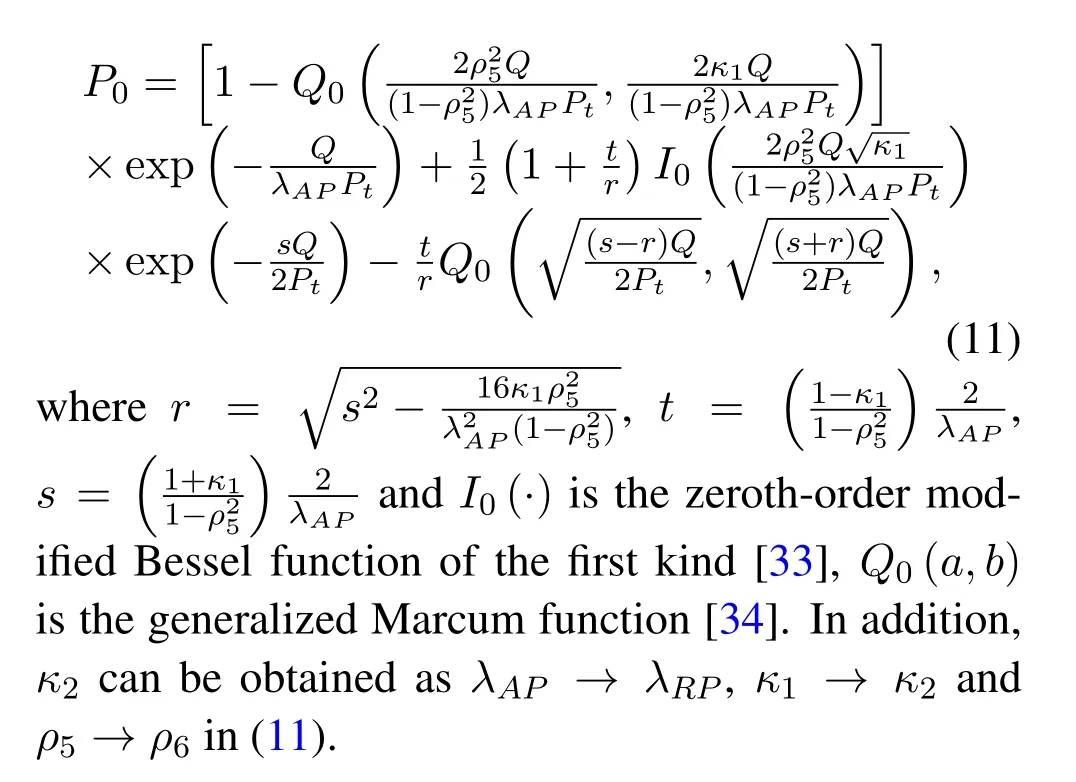
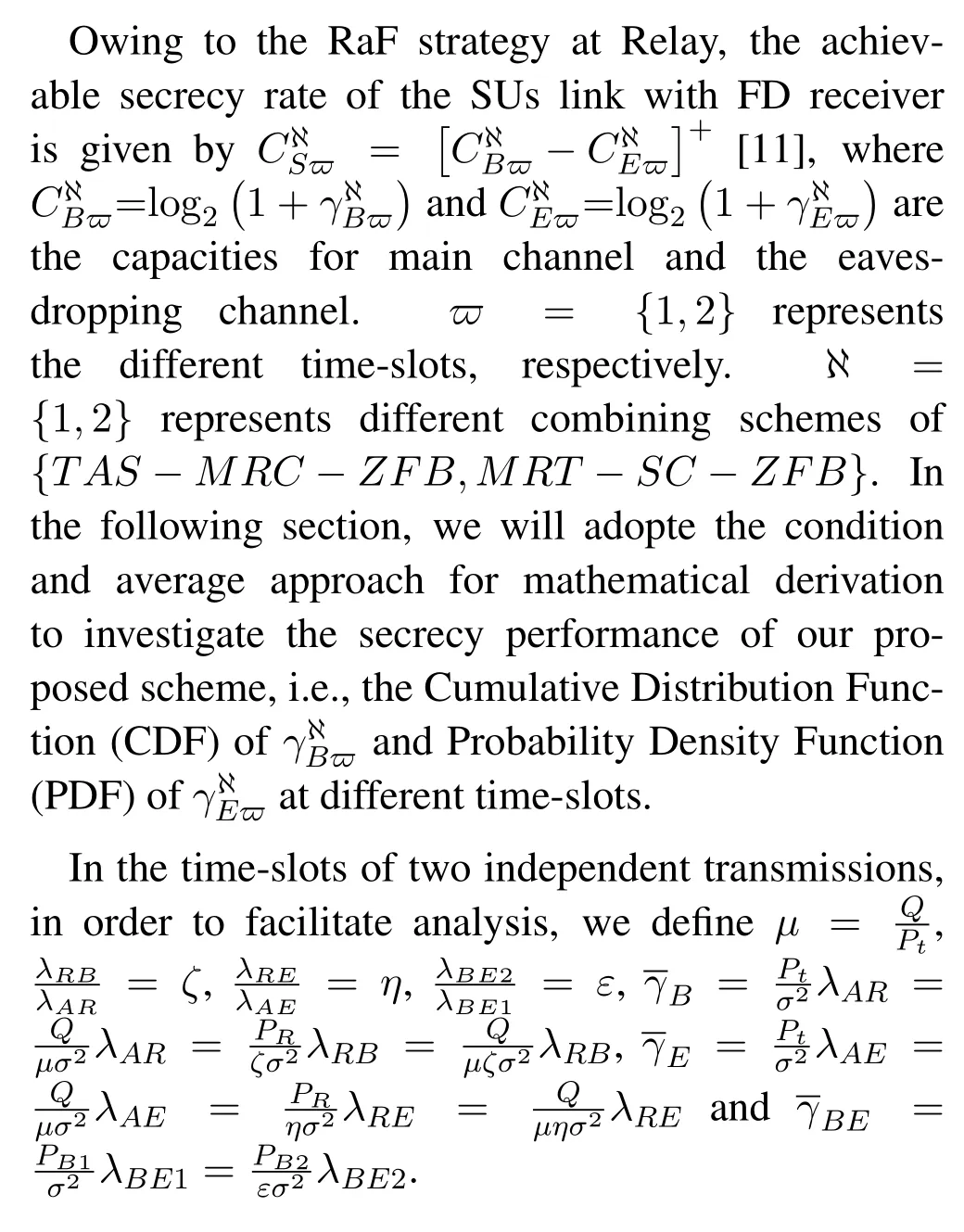
III.SECRECY OUTAGE PROBABILITY ANALYSIS
In this section,we investigate the SOP of our proposed scheme with outdated CSI.Specifically,we derive closed-form expressions for SOP.In our considered system,we give a pre-determined thresholdRS.IfCS ≥ RS,the perfect secrecy will be guaranteed.Otherwise,ifCS <RS,then the informationtheoretic security will be compromised.For the RaF spectrum sharing CRNs system,the SOP can be simplified to[35]
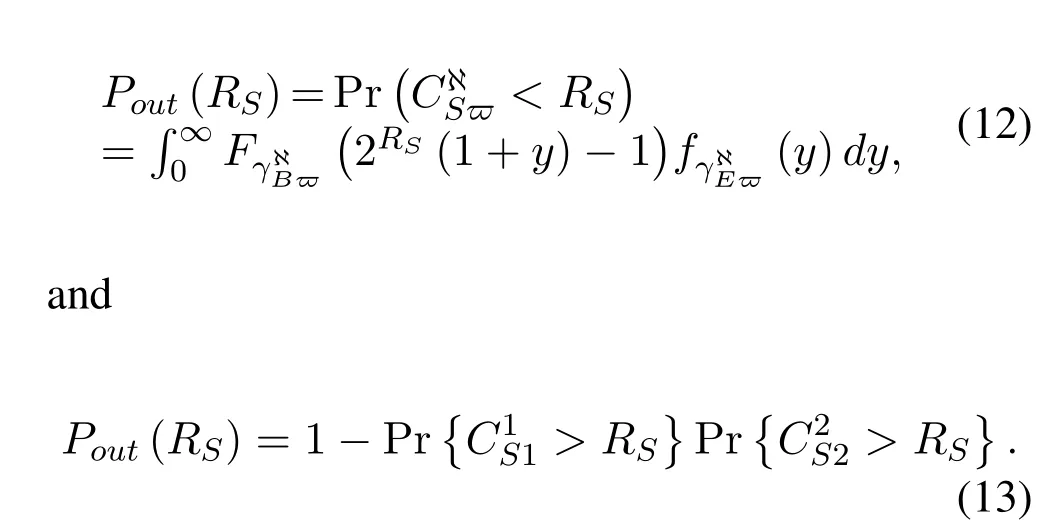
Next,we present a comprehensive investigation on each hopFγℵϖ(RS)in our proposed scheme with outdated CSI.
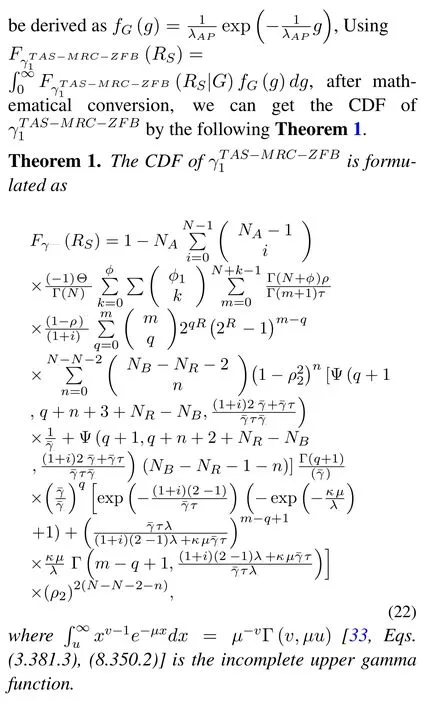
3.1 TAS-MRC-ZFB Scheme
In the first time-slot,according to(5)and[23],the conditional CDF ofwith outdated CSI is given by
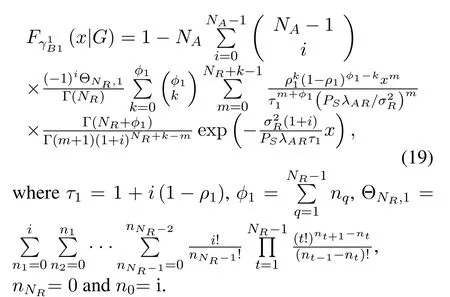
Similarly,from(6),the conditional PDF ofmay be derived as following Lemma 1.
Lemma 1.The conditional PDF of can be given by
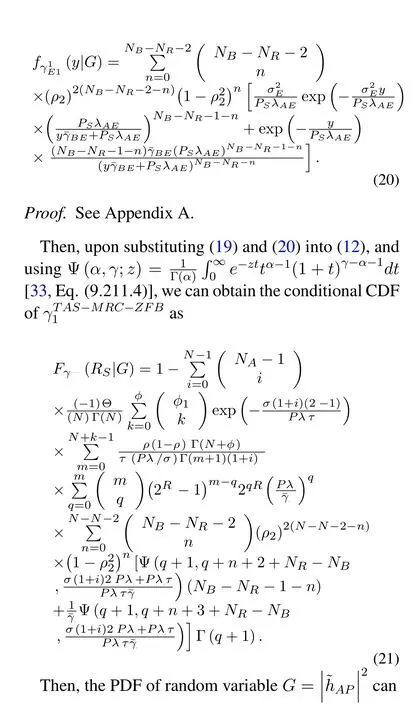
3.2 MRT-SC-ZFB Scheme
In the second time-slot,note that to solve the the conditionalFγ2B2(x|G1)with outdated CSI,a similar approach(by using(19))can also be appliedNA →NB,ϕ1→ ϕ2,τ1→ τ2,ρ1→ ρ3,PS → PRandλAR →λRB.In addition,ΘNR,2can be obtained as ΘNR,1→ΘNR,2in(19).
Similarly,the conditional PDF ofγ2E2with outdated CSI is in the following Lemma 2.
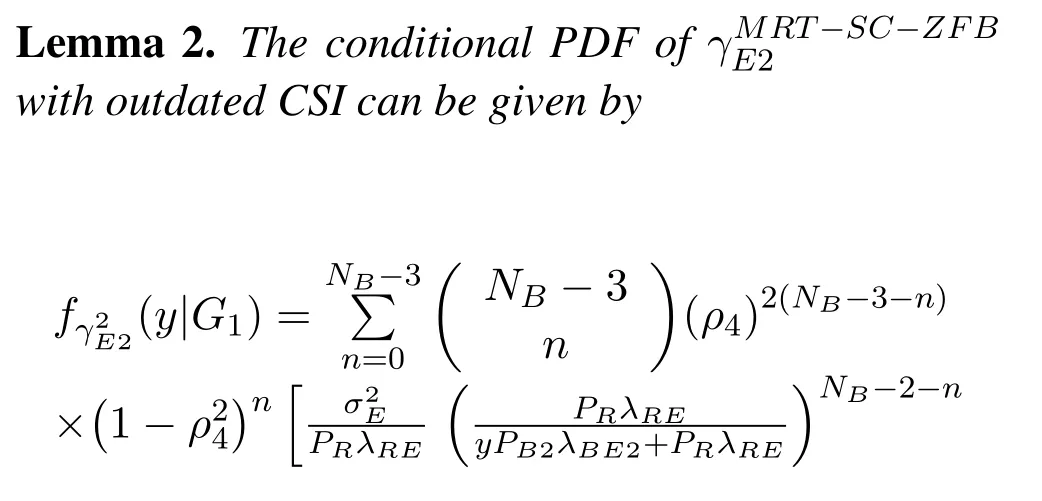
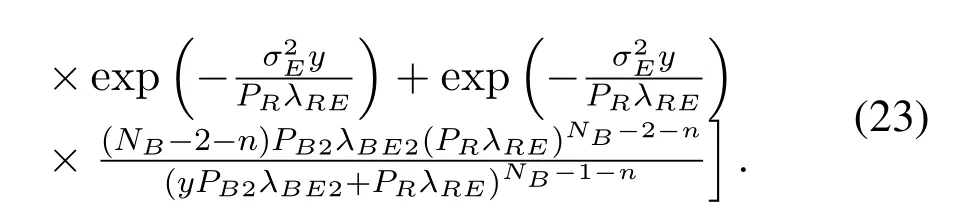
Proof.The proof process is similar to (20) and will not be described here.
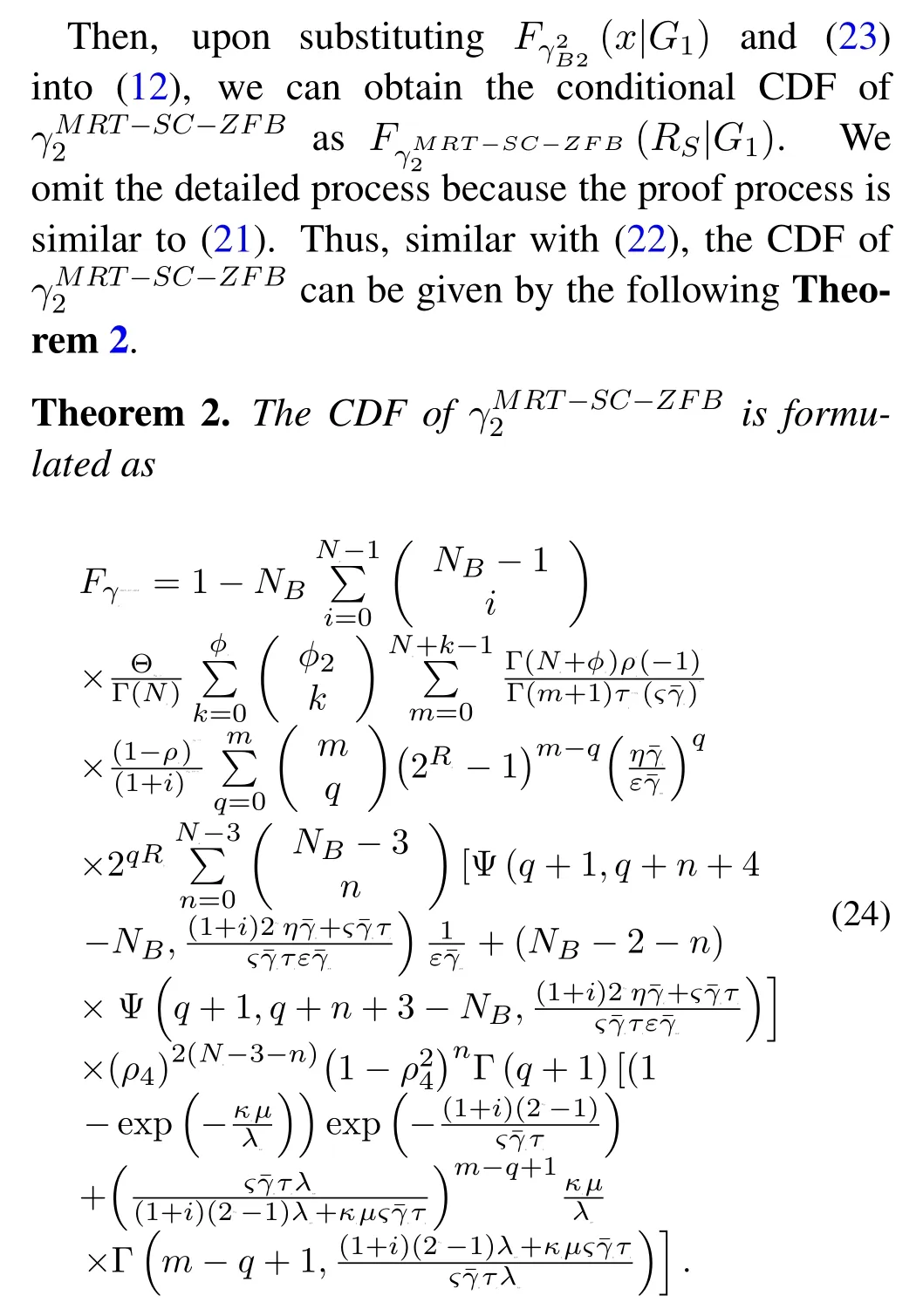
To this end,by substituting(22)and(24)into(18),we can easily obtain the final SOP of the proposed scheme.
IV.ASYMPTOTIC SOP ANALYSIS
In the above section,we have derived an exact closedform expression of the SOP and the complexity of the SOP expression limits the effective judgment of our proposed scheme on the system performance.Therefore,in order to further verify the effect of system parameters on the performance system of our proposed scheme,we will consider two special scenarios,that is,that is a scenario where Relay and Bob located quite closer to Alice and Relay,i.e.,the main transmission channel is better than the wiretap channel.2)→∞and→∞,that is a scenario where the main and wiretap channels have superior SNR,i.e.,Relay,Bob and Eve are located close to Alice and Relay,respectively.
4.1 Scenario I
In order to verify the effect of outdated CSI on the system’s secrecy diversity gain and secrecy coding gain,we analyze a special case of asymptotic SOP(ρ1,···,ρ41).
Corollary 1.When the CSIs for SUs link and collaborative beamforming link are outdated,the asymptotic expression for SOP of our proposed scheme with FD receiver under→∞and fxedis approximatedas
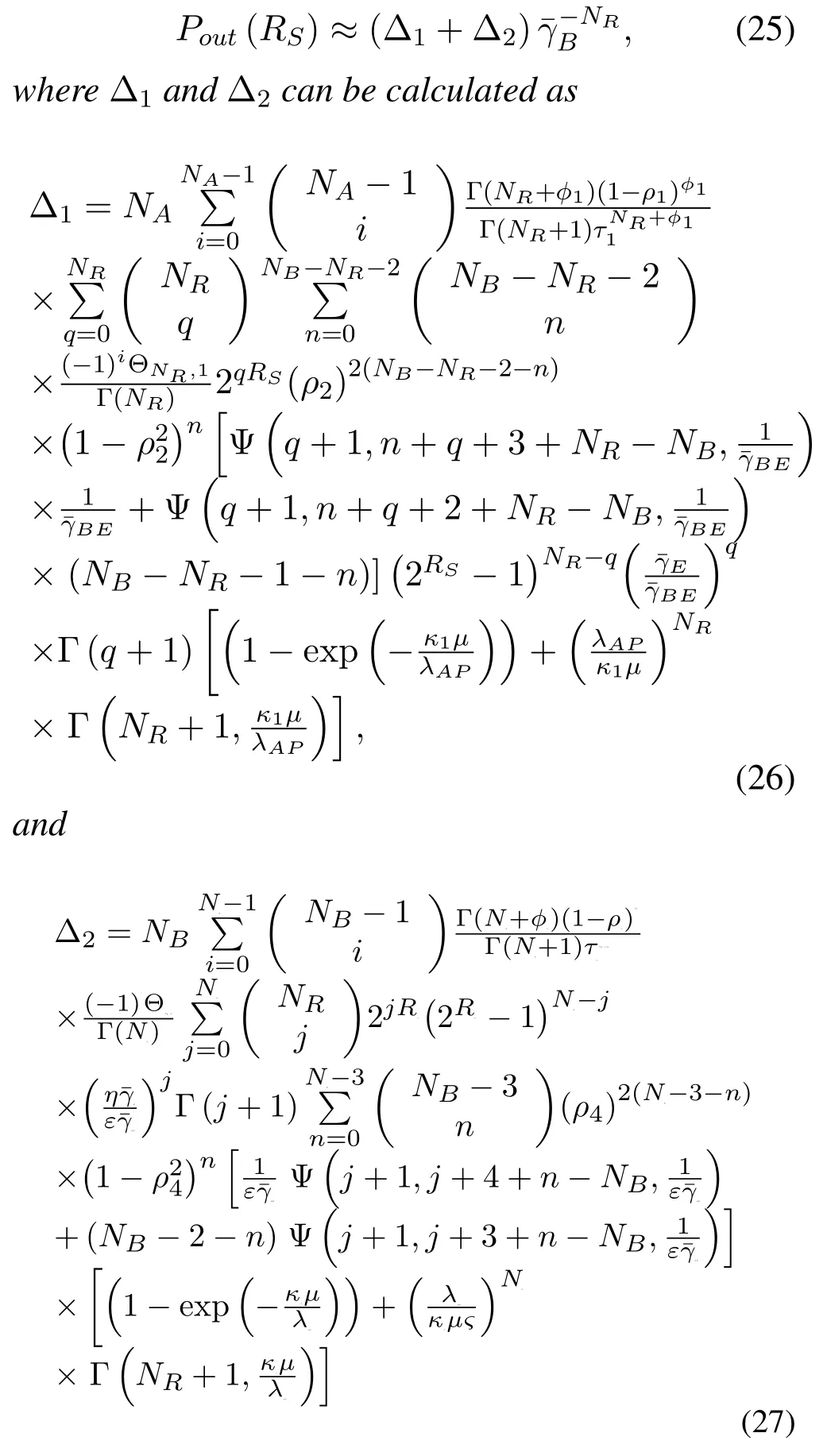
Proof.See Appendix B.
Corollary 2.When the CSIs for SUs links are perfect,the asymptotic expression for SOP under→∞and fxedis approximated as
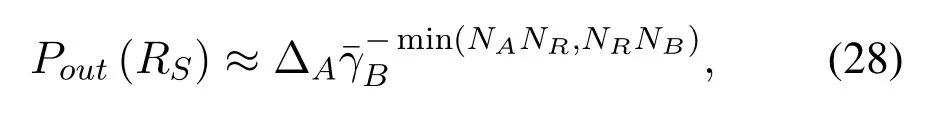
whereΔA can be rewritten as
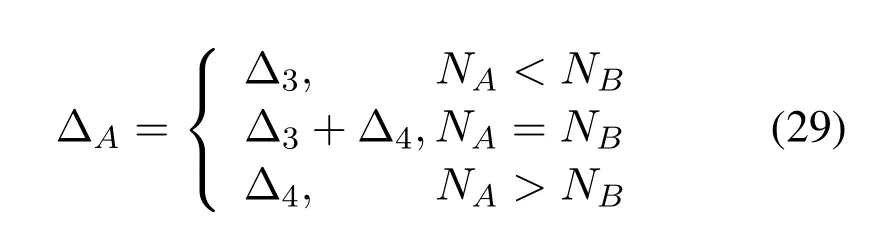
whereΔ3andΔ4can be formulated as
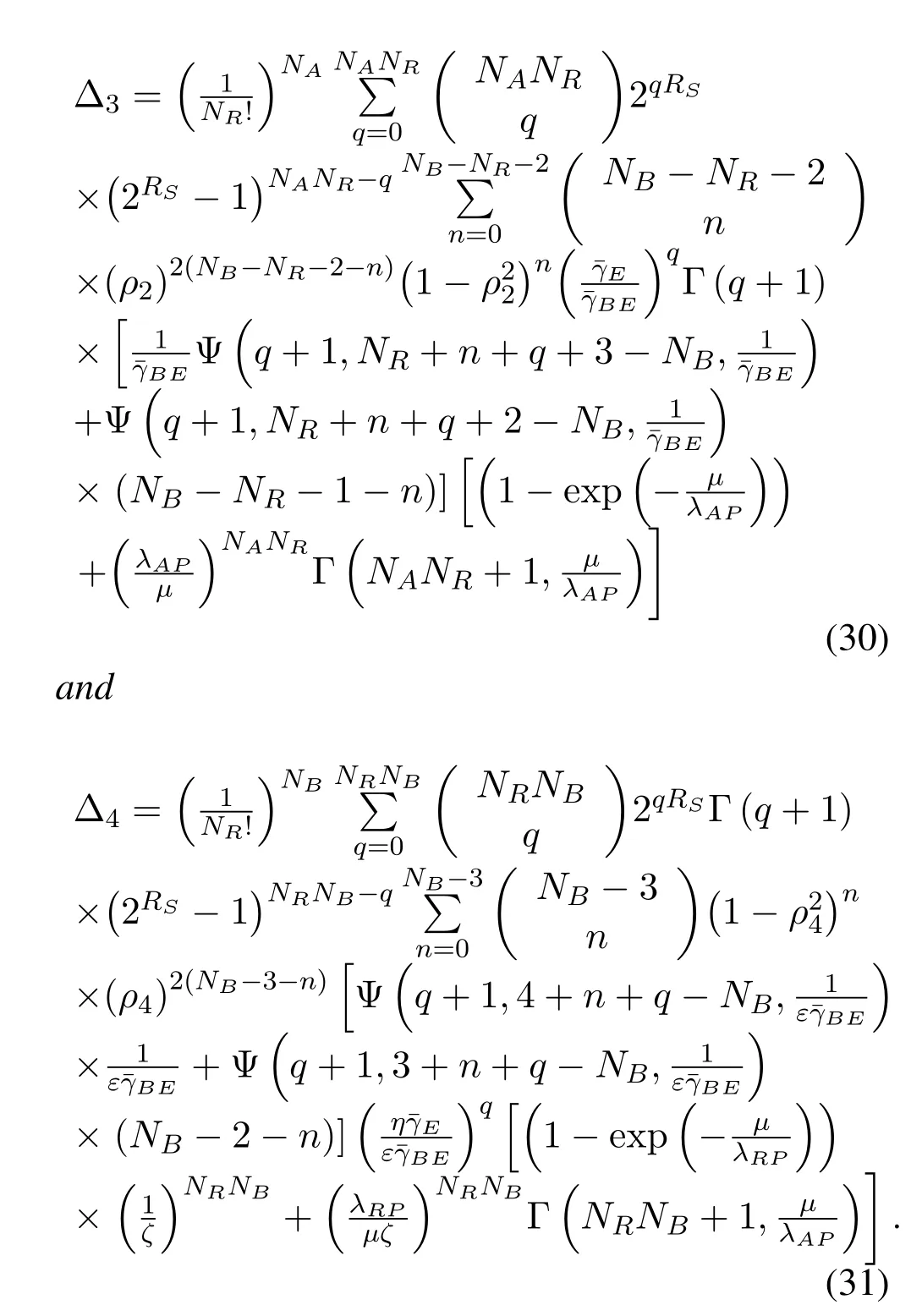
Remark 1.FromCorollary 1andCorollary 2,we can observe that our proposed scheme has two different secrecy diversity gains,i.e.,NR andmin(NANR,NRNB),for both perfect and outdated CSI.It is seen that the outdated CSI has a seriousimpact on the system and it will decrease the secrecy diversity gains frommin(NANR,NRNB)to NR.Therefore,the system performance can be enhanced by the security coding gain.In addition,the secrecy performance of our considered sysytem affects the communication quality of the wiretap channel and main channel through coding gain,i.e.,G=Δ-1/NR.From the above results,we can fnd that secrecy diversity gain improves with increasing the number of NR antennas.
4.2 Scenario II
Now,the approximated SOP expression for our proposed scheme under outdated CSI can be analyzed in the followingCorollary 3.
Corollary 3.When the CSIs of our considered system is outdated(SUs links and collaborative ZFB link Bob→Eve),the asymptotic SOP of our proposed schemewith outdated CSI underisgiven by
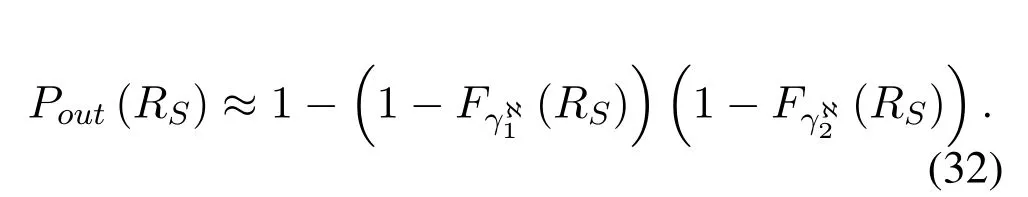
By approximately solving (22) and (24),it is easy to obtain (33) and (34) .Further,substituting (33)and(34)into(32),we can easily obtain the fnal result under Scenario II.Where
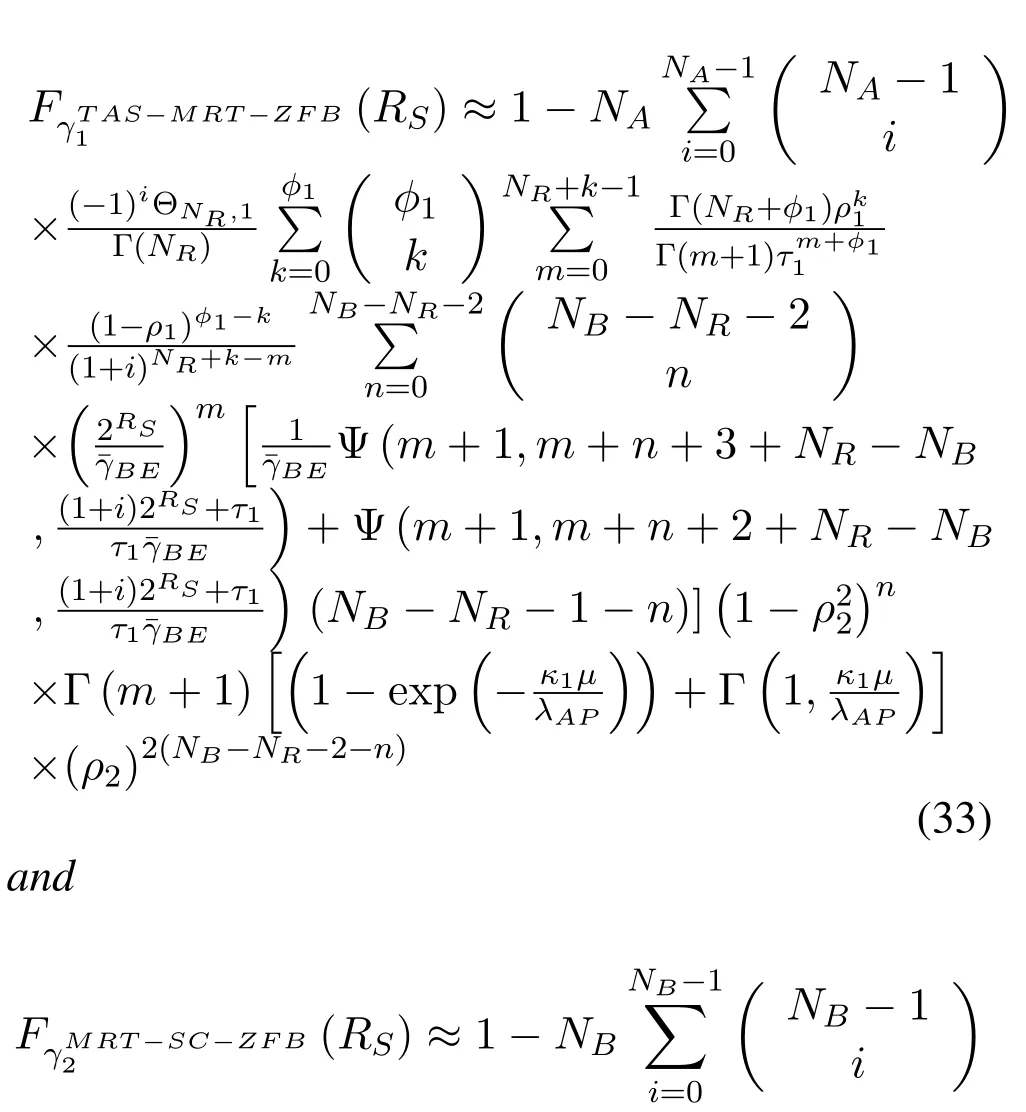
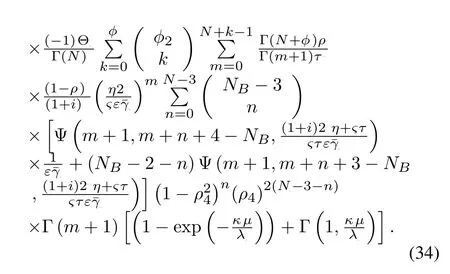
Remark 2.We can observe from Corollary 3 that the proposed scheme withachieve the secrecy outage floor under outdated CSI and we cannot get the secrecy diversity gain.Therefore,the secrecy performance of our considered system would be affected by the security coding gain for Scenario II.
4.3 Comparison of Different Scenarios
It is pointed out in Table.1 that the SOP of the different scenarios highly relies on the diversity order and coding gain and thus has a significant impact on the secrecy performance.Similar to Δ1and Δ2,Δ3,···,Δ6represent different fixed values,and these values are not deduced in detail here.It is observed that the FD and HD operation schemes with outdated CSI will decrease the diversity gains of the TAS-MRC-ZFB scheme fromNANR →NRand the MRT-SC-ZFB scheme fromNRNB →NR,respectively.
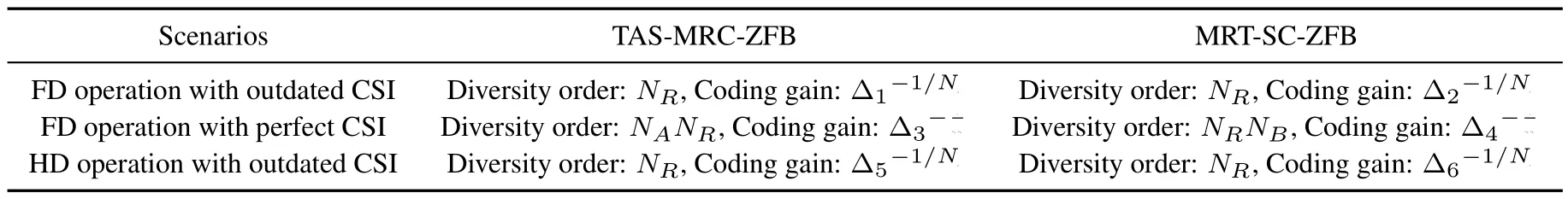
Table 1. Comparison of different scenarios.
V.NUMERICAL RESULTS
This section deals in providing the numerical results to testify the secrecy performance of our proposed scheme with outdated CSI.Our interest is in examining the effects of the number of(NA,NR,NB),ρd,QandP0.We set,RS=2bit/s/Hz,ς=η=ε=1 andPS=PR.dMNrepresents the distance fromMtoN,in whichdMN=1.We setλRE=λRP=2,and all other channel link variances are 1.The transmission signal-to-noise ratio is defined as SNR.Moreover,we clearly found that the analytical curves are completely in conformity with the Monte Carlo simulations’results,which further verify the analytical derivations.
Figure 2 presents the SOP versus SNR for the two different combining schemes with outdated CSI.From both figures,we find that the SOP decreases with increasing the number of time correlation coefficientρdandQ.It is also observed that the SOP curves for any value ofρdandQtend to be different fixed values.Whenρd=1,the system performance is better than that ofρd=0.5.That is because when the time correlation coefficient increases,the CSI of CRNs is close to perfect.In our considered scheme,the FD destination node knows the perfect CSI of the Eve node,so the ZFB design maximizes the transmission of directional interference signals to the Eve node.The considered scheme of our paper validates that our designed beamforming can mitigate the interference effectively with outdated CSI.Furthermore,the SOP deteriorates due to the outdated CSI.However,the FD operation can effectively affect the system coding gain and further improve the system performance.Finally,compared with the existing former scheme,the proposed scheme is verified to improve the system performance.
Figure 3 and 4 present the SOP versus average SNR for our proposed scheme under different(NA,NR,NB),ρd,NRandQwith outdated CSI.In Figure 3,when (ρ5,ρ6)=1 is fixed,as increasing time correlation coefficient (ρ1,···,ρ4) of SU transmission link,the SOP of our proposed scheme also decreases.The effect of changing the number ofNRantennas on the system performance is significantly better than that ofNB.This is because the secrecy diversity of our proposed scheme isNR,which is mainly determined by the number ofNRantennas(seeCorollary 1) in the condition that the time correlation coefficients of our considered system are fixed.When(NA,NB)andρdare fixed,with the increment ofNR,the secrecy performance becomes worse.This is because the number of antennas transmitting interference signals to Eve at Bob is reduced.In Figure 4,whenρd=1,the system performance is the best under perfect CSI.Due to the existence of the power margin factorκ1andκ2,the transmission power is limited when the performance appears flat andκ1,κ2are still further reducing.In Figure 3 and 4,we observe that the ZFB weights of outdated CSI at Bob have a greater impact on system performance than the perfect CSI of the Bob and Eve link,which aggravates the outage performance.
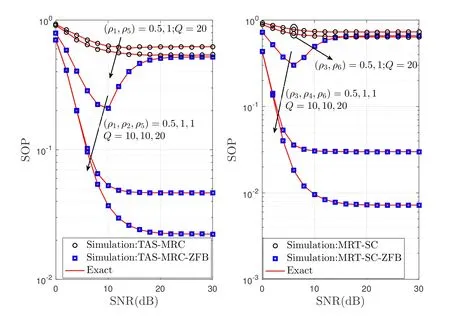
Figure 2. The SOP versus system mean SNR for the two different combining schemes under different correlation coeffcient ρd and Q with outdated CSI whenBE1=BE2=10dB,(NA,NR,NB)=(2,2,5)and P0=10%.
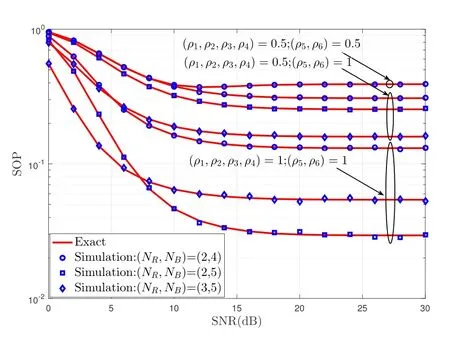
Figure 3. The SOP versus system mean SNR for different correlation coeffcient ρd and (NR,NB) when NA=2,BE1=BE2=10dB,P0=10%and Q=20dB.
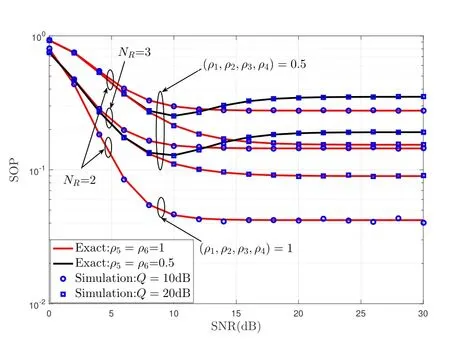
Figure 4. The SOP versus system mean SNR for different number NR,Q and ρd when E1=BE2=20dB,(NA,NB)=(2,5)and P0=5%.
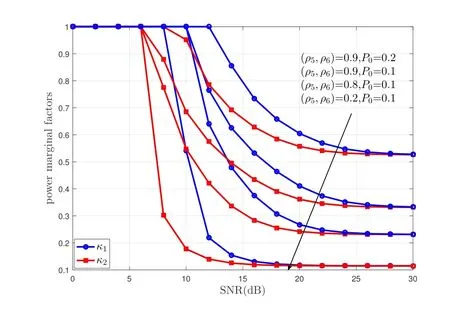
Figure 5. The power marginal factors κ1 and κ2 versus system mean SNR under the different(ρ5,ρ6)and P0.
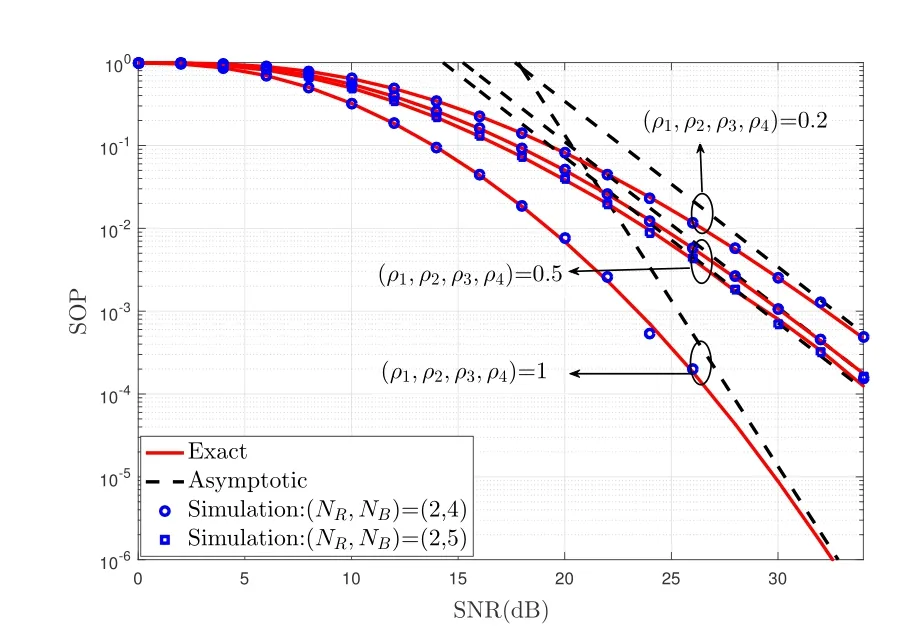
Figure 6. Exact and asymptotic SOP versus system mean SNR for different number(NR,NB)and(ρ1,···,ρ4)under Scenario I when(ρ5,ρ6)=1,NA=2,BE1=BE2=10dB and P0=10%.
Figure 5 presents the effects of the power margin factorsκ1andκ2versus SNR under various preselected outage probability of PU (P0) and time correlation coefficients (ρ5,ρ6).In Figure 5,it shows that the power margin factorsκ1andκ2decline with the increase of SNR.It also shows that in the low SNR regime,the power margin factors(κ1,κ2)=1 because the interference to the PU is less than the preselected outage probability value of PU.In addition,when(ρ5,ρ6)andP0are fixed,κ2is better thanκ1at a certain SNR,which is because the average value of the PU link inκ2is 2,i.e,λRP=2.Besides,it is also observed from this figure,the smaller the pre-selected outage probability value(P0)and the correlation coefficients(ρ5,ρ6),the better the QoS for PU.
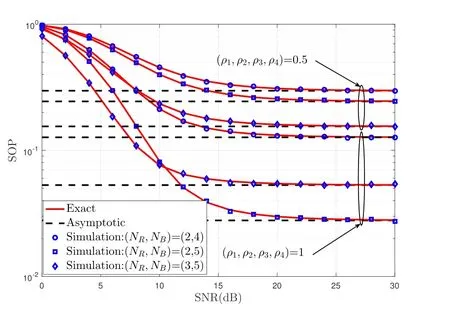
Figure 7. Exact and asymptotic SOP versus system mean SNR for different number(NR,NB)and(ρ1,···,ρ4)under Scenario II when B E1=BE2=10dB,B/E=1dB,NA=2,(ρ5,ρ6)=1 and P0=5%.
Figure 6 and 7 plot the SOP versus average SNR for our proposed scheme under two different scenarios.As depicted in two figures,it shows that the SOP decreases with increasing the number of (NR,NB) and(ρ1,···,ρ4),and the system performance becomes better.In Figure 6,it can be found that some of the asymptotic curves are parallel.This is because they have the same secrecy diversity gainNRunder Scenario I.It is also observed that when the CSI is perfect,the diversity gain of min(NANR,NRNB)can be achieved (seeCorollary 2).Therefore,it is not difficult to find that the correlation coefficientρdhas a great influence on the SOP of the system.In Figure 7 the results show that the SOP curves for any value of (NA,NR,NB) and (ρ1,···,ρ4) tend to be different fixed values.When (ρ1,···,ρ4)=1,the SOP is minimum and diversity order achieves the maximum valueNRwhich is a situation of perfect CSI.However,it is difficult to achive the perfect CSI in actual physical scenario.In addition,the SOP of the system tends to the secrecy outage floor,which validates the theoretical analysis conclusion ofCorollary 3.Finally,the SOP curves for our proposed scheme match well with the simulation results,indicating the correctness of(32).
Figure 8 presents the SOP of system versusρ1andρ3with outdated CSI under ZFB scheme.As shown in Figure 8,one can notice that the(ρ2,ρ4)has a great influence on the SOP of our proposed system.Thus the secrecy performance of(ρ2,ρ4)=1 is better than that of(ρ2,ρ4)=0.2,0.5.When maximizing(ρ2,ρ4),the FD destination node knows the perfect CSI of the Eve node,so the ZFB design maximizes the transmission of directional interference signals to the Eve node.We also observe that the SOP decreases when the correlation coefficientρ1andρ3increase.That is because whenρ1andρ3increases,the CSI of CRNs is close to the perfect.
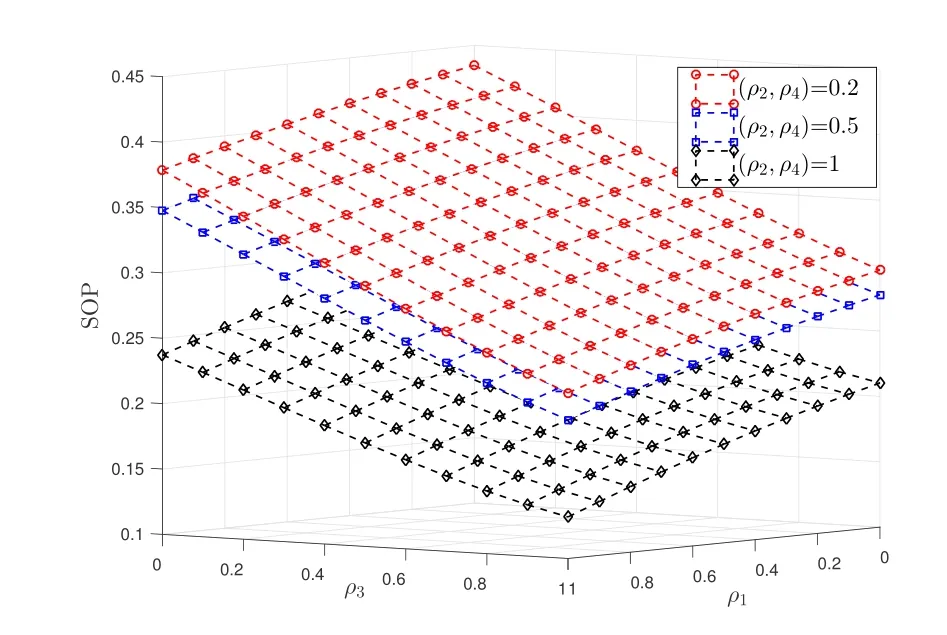
Figure 8. The SOP versus ρ1 and ρ3 with different correlation coeffcient (ρ2,ρ4) when BE1=BE2=10dB,(NA,NR,NB)=(2,2,4), (ρ5,ρ6)=1,P0=5% and Pt=Q=20dB.
VI.CONCLUSION
We put forward a new underlay RaF spectrum sharing model with FD receiver and studied the effects of outdated CSI on cooperative relay node with TASMRC-ZFB/MRT-SC-ZFB scheme.We derived the closed-form expressions for the exact and the high SNR regime asymptotic under two different scenarios and analyzed the effects of the time delay on the secrecy performance of our considered system.We also investigated the impact of key parameters on the system secrecy performance with a passive eavesdropper under outdated CSI and the secrecy diversity gain of our considered system with outdated CSI decreased from min(NANR,NRNB) toNR.Our results have shown that outdated CSI has a negative impact on the diversity and coding gains of the system.However,the FD operation could effectively affect the system coding gain and further improve the system performance.Additionally,we found that the proposed scheme outperforms better performance than the existing former scheme.The analysis performed in this paper will be of great use in designing the practical spectrum sharing CRNs systems that are subject to channel estimation errors.
ACKNOWLEDGEMENT
This work was supported by the National Natural Science Foundation of China (No.62201606 and No.62071486),the Project of Science and Technology Planning of Guizhou Province (No.[2020]-030),the Project of Science and Technology Fund of Guizhou Provincial Health Commission (gzwkj2022-524),the Project of Youth Science and Technology Talent Growth Guizhou Provincial Department of Education (No.KY[2021]230),the Key Research Base Project of Humanities and Social Sciences of Education Department of Guizhou Province,and the Project of Science and Technology Planning of Zunyi City(No.2022-381 and No.2022-384).
APPENDIX A
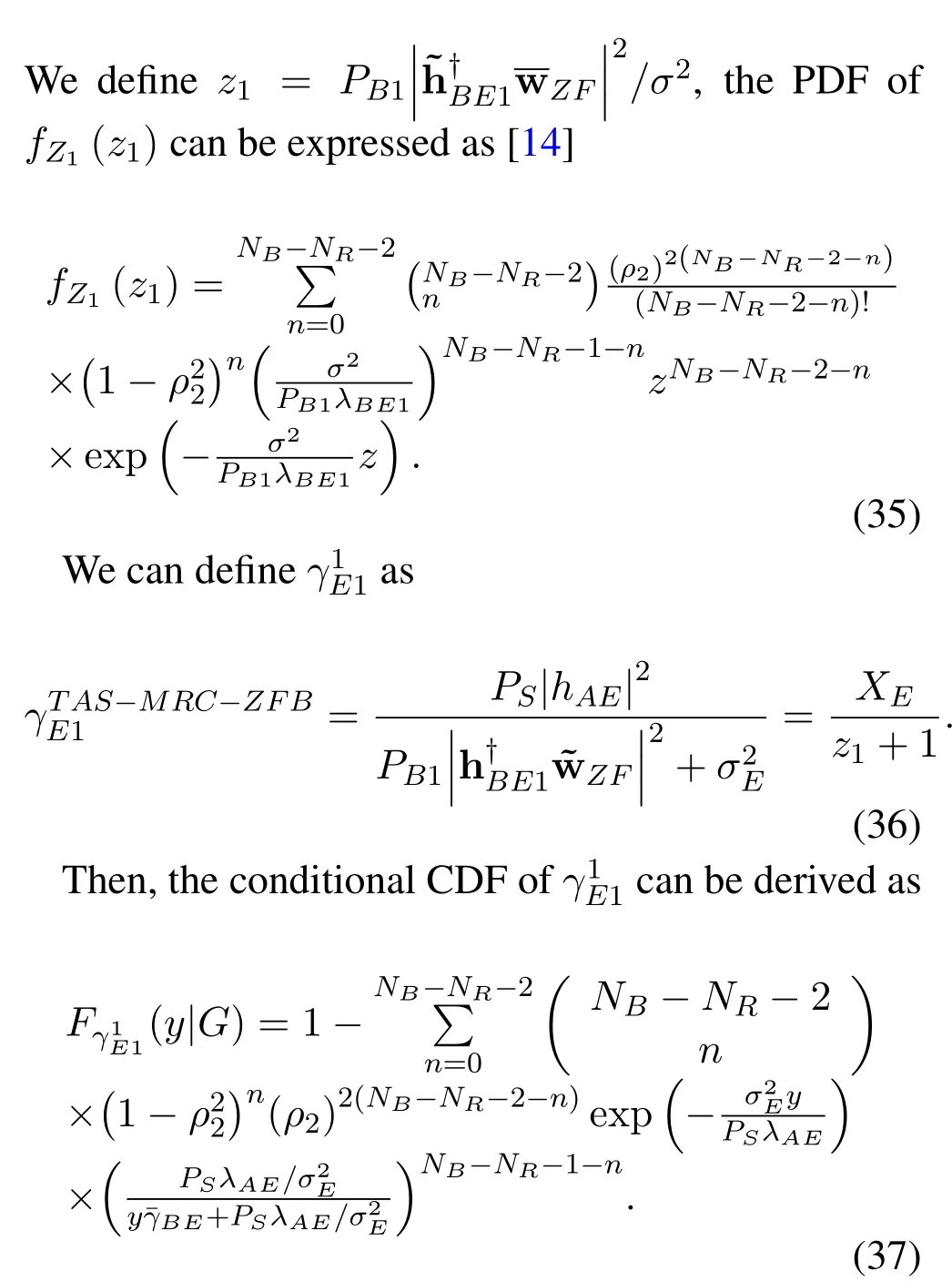
Finally,the(y)inLemma 1can be obtained by taking derivative in(37).
APPENDIX B
In the frist time-slot,using (19),when,the(x|G)can be approximated as
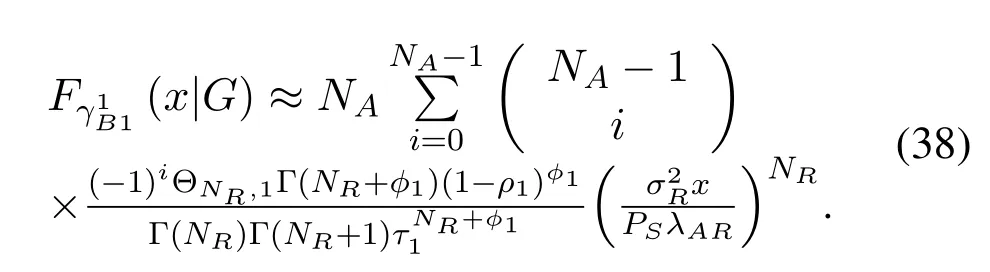
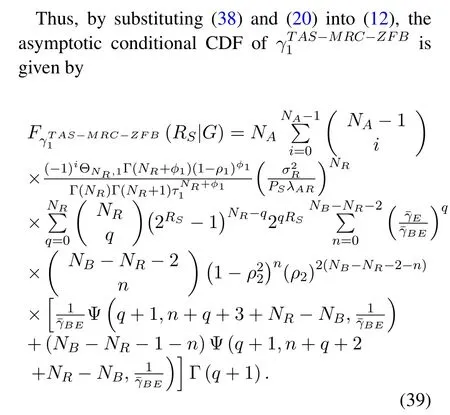
UsingfG(g),after mathematical conversion,we can get
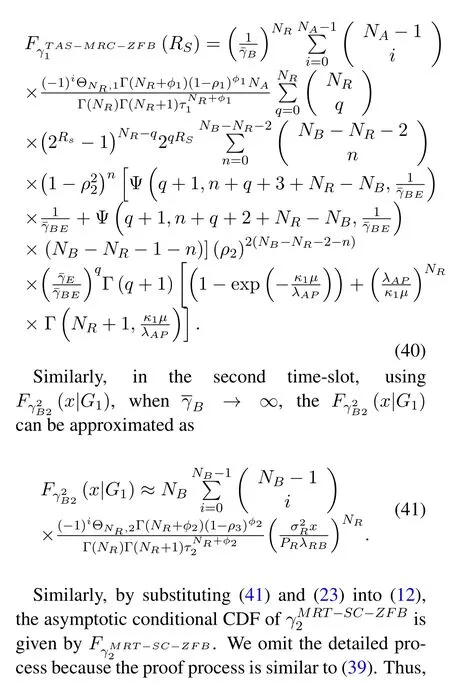
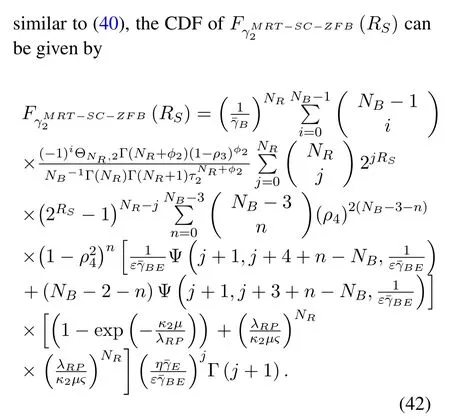
Now,using(40)and(42),we obtain(26)and(27).
- China Communications的其它文章
- Secrecy Transmission of NOMA-OTFS Based Multicast-Unicast Streaming
- Orthogonal Time Frequency Space Modulation in 6G Era
- Joint Multi-Domain Channel Estimation Based on Sparse Bayesian Learning for OTFS System
- BER Performance Analysis of OTFS Systems with Power Allocation
- OTFS-Based Efficient Handover Authentication Scheme with Privacy-Preserving for High Mobility Scenarios
- Channel Estimation for OTFS System over Doubly Spread Sparse Acoustic Channels

