OTFS-Based Efficient Handover Authentication Scheme with Privacy-Preserving for High Mobility Scenarios
Dawei Li,Di Liu,Yu Sun,Jianwei Liu
School of Cyber Science and Technology,Beihang University,Beijing 100191,China
Abstract: Handover authentication in high mobility scenarios is characterized by frequent and shortterm parallel execution.Moreover,the penetration loss and Doppler frequency shift caused by high speed also lead to the deterioration of network link quality.Therefore,high mobility scenarios require handover schemes with less handover overhead.However,some existing schemes that meet this requirement cannot provide strong security guarantees,while some schemes that can provide strong security guarantees have large handover overheads.To solve this dilemma,we propose a privacy-preserving handover authentication scheme that can provide strong security guarantees with less computational cost.Based on Orthogonal Time Frequency Space (OTFS) link and Key Encapsulation Mechanism (KEM),we establish the shared key between protocol entities in the initial authentication phase,thereby reducing the overhead in the handover phase.Our proposed scheme can achieve mutual authentication and key agreement among the user equipment,relay node,and authentication server.We demonstrate that our proposed scheme can achieve user anonymity,unlinkability,perfect forward secrecy,and resistance to various attacks through security analysis including the Tamarin.The performance evaluation results show that our scheme has a small computational cost compared with other schemes and can also provide a strong guarantee of security properties.
Keywords: high mobility condition;handover authentication;privacy-preserving;Tamarin;OTFS
I.INTRODUCTION
Communication in high-mobility scenarios such as high-speed trains and airplanes has the specific characteristic that a large number of users perform handovers in parallel and frequently[1].Current 5G networks use Orthogonal Frequency Division Multiplexing(OFDM)modulation,but user communications are also heavily affected by penetration loss and Doppler frequency shift due to the very fast running speeds of high-speed rail and airplanes[2].These characteristics in high mobility scenarios often lead to poor communication quality for users,and even lead to handover failures,resulting in users being unable to obtain network services[3].
Orthogonal Time Frequency Space (OTFS) twodimensional modulation [4,5] is considered as a promising technology for future 6G communication.OTFS modulation uses Delay Doppler (DD) domain to place information symbols,which can effectively combat the Doppler frequency shift phenomenon during user communication [6].Therefore,it is especially suitable for improving communication reliability in high mobility scenarios,such as high-speed rail communication networks with speeds exceeding 500 km/h and airborne communication networks with relative speeds exceeding 1200 m/s[7].
Under the above background,we design a user equipment handover authentication scheme in high mobility scenarios for future OTFS modulation-based 6G networks in this paper.We adopt the design idea of backward compatibility,that is,based on the current 5G network and facing the future 6G network.To achieve the goal of seamless handover for users,the mobile relay node (MRN) is widely used in current high-speed rail communication networks to assist communication [8].MRN helps users perform handover authentication with access points and authentication servers,thereby providing users with continuous network connectivity.
The existing handover authentication schemes in high mobility scenarios have some limitations.For those schemes that can fully guarantee various security properties such as user anonymity,unlinkability,and perfect forward secrecy,large computational costs are often required [9,10].However,those schemes with low computational costs often cannot provide rich guarantees of security properties [11].Another problem is that most of the existing schemes use complex cryptographic operations in the protocol design to ensure various security properties,which are not suitable for handover requirements in high mobility scenarios [12].In addition to requiring longer handover times,they are also incompatible with schemes already deployed in existing communication networks,and additional overhead is required to deploy these schemes,which limits their practicality.
In this paper,we propose a handover authentication scheme suitable for high mobility scenarios that not only guarantee various security properties but also have a small computational cost.Based on the idea of the key encapsulation mechanism(KEM)and data encapsulation mechanism (DEM),we design the authentication and key agreement protocol and handover protocol in our scheme based on the existing 3GPP standards.The contributions of this paper are listed as follows:
• We propose a handover authentication scheme with high security,low computational cost,and compatibility with existing standards.The security of the scheme can be improved by establishing a temporary shared key between protocol entities for authentication and session key generation based on the KEM.
• The proposed scheme provides strong security guarantees,which can guarantee the anonymity of users,can resist linkability attacks based on error messages and replay attacks,can achieve key forward/backward secrecy,and can also resist manin-the-middle attacks.
• We verified that the proposed scheme satisfies the above-mentioned security properties in the formal verification tool Tamarin,and we opensourced the protocol model to provide support for researchers in the community.
The rest of the paper is organized as follows.Section II reviews and discusses related work.Section III presents the system architecture and threat model.Section IV details the handover authentication scheme we designed,which consists of an initial authentication phase and a handover phase.Section V discusses the security of our proposed scheme and analyzes the security properties satisfied by the protocol in Tamarin.Section VI compares the computational cost and functionality of our scheme and other schemes.The conclusions are presented in Section VII.
II.RELATED WORK
Recently,some handover authentication schemes for high mobility scenarios have been proposed.3GPP has also formulated relevant standards [8,13,14] for the handover authentication of high-speed rail networks,but these schemes have some security problems such as replay attacks and linkability attacks.Caoet al.[15] proposed a group-to-route handover authentication scheme based on trajectory prediction.In this scheme,the MRN and the base stations on the route are aggregated into groups respectively to realize mutual authentication and key agreement between the two groups,which can improve the handover efficiency.However,although this scheme is resistant to majority protocol attacks,it cannot achieve security properties such as perfect forward secrecy and unlinkability.Maet al.[1] proposed two group prehandover authentication schemes in the 5G high-speed rail network scenario.The first scheme has less handover overhead but cannot achieve security properties such as user anonymity and perfect forward secrecy.The second scheme can achieve most security properties,but it has a significant handover overhead due to the extensive use of cryptographic operations on elliptic curves.To improve the security of handover authentication under the 5G high-speed rail network,Liet al.[16]proposed a handover authentication scheme based on trusted MRN.By deploying a trusted execution environment in the MRN to assist user equipment in authentication,the security and handover efficiency of the scheme are improved.However,they did not perform a formal security analysis of the proposed protocol,nor did they evaluate the computational cost of the scheme.
Moreover,there are many handover authentication schemes for other network scenarios.Xue et al.[9]designed an efficient handover mechanism for IoT in spatial information networks.This scheme reduces authentication delay by enabling satellites to authenticate users and improves handover efficiency by supporting batch verification.Although this scheme can resist various attacks,it has a large computational cost.For the handover scenarios of different types of base stations in 5G heterogeneous networks,Cao et al.[17]proposed a privacy protection handover authentication scheme based on user capabilities combined with the software-defined network (SDN) technique.This scheme has a small handover overhead and can provide good security protection,but there is no discussion on perfect forward secrecy.Zhang et al.[10]proposed a universal handover scheme suitable for 5G heterogeneous networks based on the properties of the chameleon hash function and blockchain.The scheme considers multiple scenarios of inter-domain and intradomain handover and can provide high-security assurance.However,this scheme does not discuss linkability attacks against users and has a high computational cost.Guo et al.[11] proposed an anonymous handover authentication scheme for fog computing,which achieves high handover efficiency by using lightweight cryptographic primitives and the cooperation of fog nodes.However,this scheme cannot achieve user traceability and does not discuss user linkability.
III.SYSTEM MODEL
3.1 System Architecture
The system architecture is shown in Figure 1.The scenario we consider is handover authentication under high mobility conditions.The entities in the system architecture include user equipment(UE),relay nodes(RN),access points (AP),and authentication servers(AS).The UE is user equipment that has a network access requirement on a high-speed train or an airplane.The RN is fixed on the train or plane and helps the UE to connect to the ground network.The AP is the access point for the UE to connect to the core network,which can be a terrestrial base station or a satellite.The AS is a server in the core network that authenticates the UE and generates keys and other information.
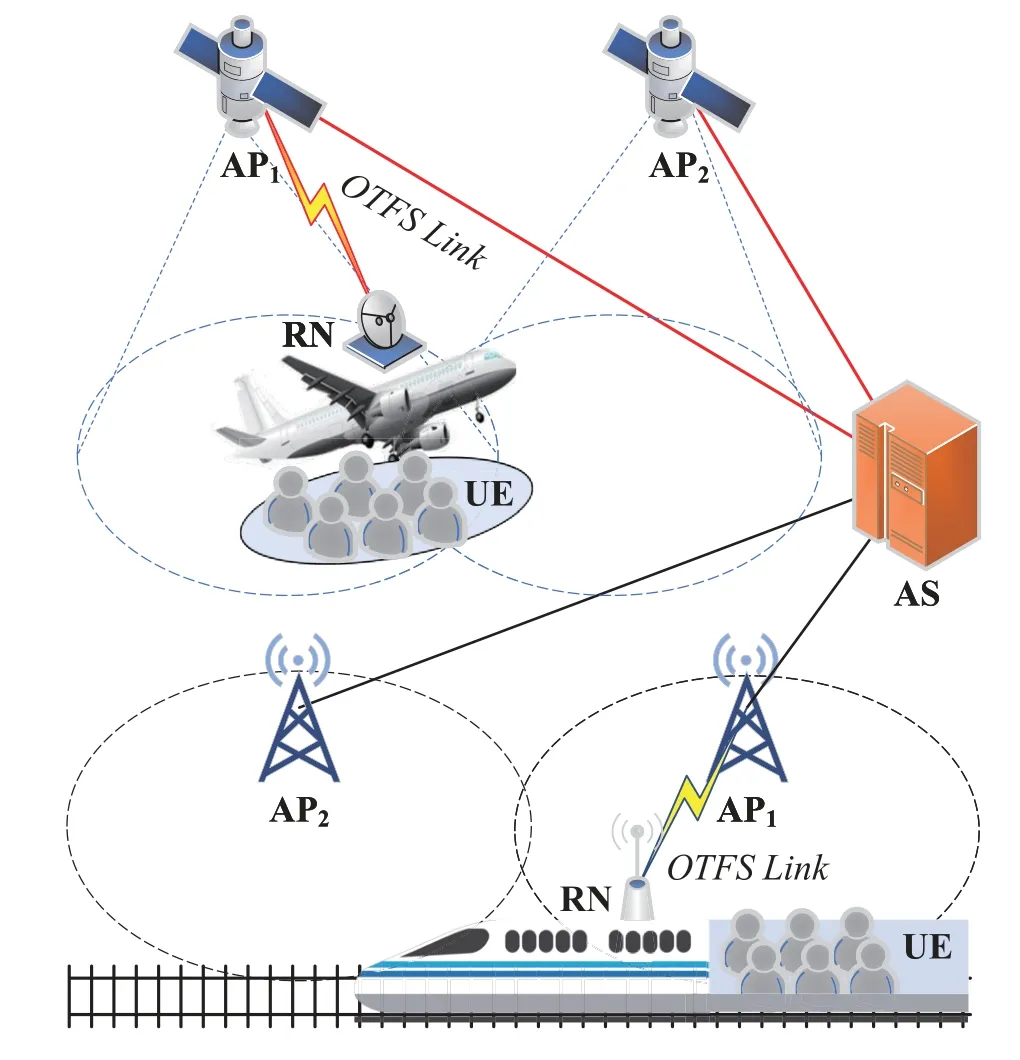
Figure 1. System architecture.
Since the UE is in a high-speed mobile scenario,frequent handovers are required.A large number of UEs performing handovers in parallel will cause huge communication delays,resulting in the unavailability of network services.Therefore,a relay node is introduced to solve this problem[8].Before the departure of the train or the plane,the UE and RN complete the initial authentication with the AS.When moving at high speed,only the RN performs the handover procedure,and the RN acts as an access point to provide network services for the UE.
3.2 Threat Model
The channel between UE and RN and the channel between RN and AP are wireless channels,where the channel between RN and AP is a radio link based on OTFS modulation.We assume that there are passive or active attackers in the wireless channel,possibly malicious users in our scenario.Attackers can eavesdrop,modify,and replay messages transmitted on the channel,or inject messages generated by themselves into the channel.We assume that the channel between AP and AS is a secure channel,which can guarantee the confidentiality,integrity and resistance to replay attacks of messages transmitted in the channel.The channel between the ground AP and the AS is a secure wired link,and the channel between the satellite AP and the ground AS is a secure OTFS link.
We further assume that the attacker cannot compromise the RN,AP,and AS entities in the network,which means that the attacker cannot steal the keys stored in the entities,such as the AS’s private key and the long-term shared key with the UE and RN.But the attacker can have a legitimate UE and communicate with entities in the network.
3.3 OTFS Link
We discuss the basic input-output relationships of OTFS systems following the literature [18-22].The information symbolx[k,l] is represented as a point in the two-dimensional delay-Doppler (DD) domain,where 0< k < N -1,0< l < M -1 represents the Doppler index and delay index,respectively.Symbolx[k,l] transforms into time-frequency(TF)domain through inverse symplectic finite Fourier transform(ISFFT),
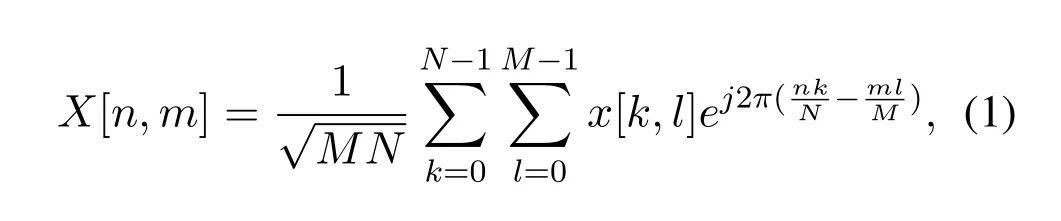
where 0<n <N -1,0<m <M -1 represents the time index and subcarrier index,respectively.
SymbolX[n,m] is mapping through Heisenberg transform to the time domain continuous signals(t),
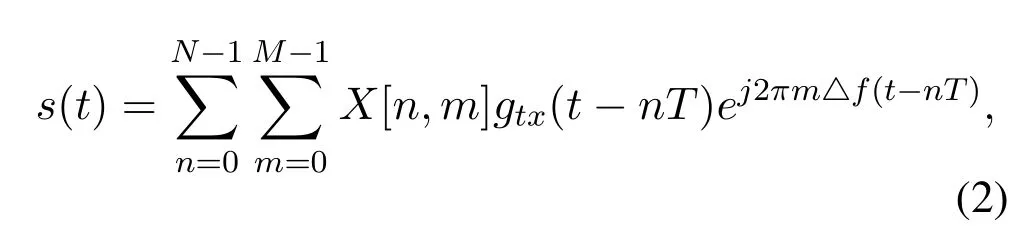
whereTand△frespectively represent the sampling interval in time and frequency,and the functiongtx()is the pulse-shaping filter.
After the signal is transmitted through the timevarying wireless channel,the received signalr(t) is represented by
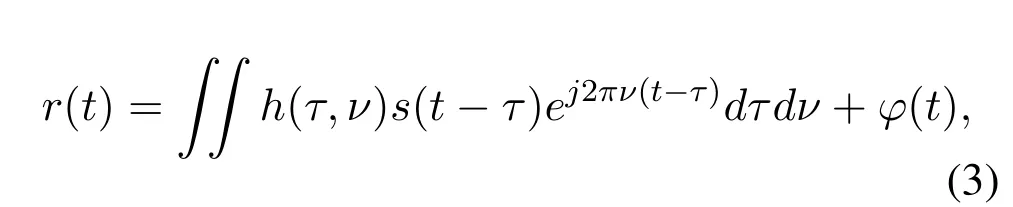
whereφ(t)is the noise signal,andh(τ,ν)represents the channel response in the DD domain,
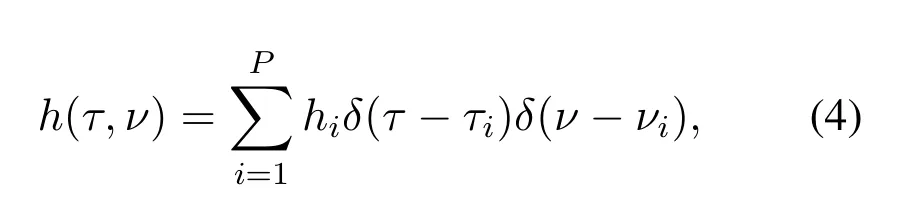
wherePrepresents the number of paths in the channel,andhi,τi,andνirepresent the channel coefficient,delay,and Doppler shift of a certain path,respectively.
The time domain signalr(t) is transformed into the symbolY[n,m] of the TF domain by the Wigner transform,
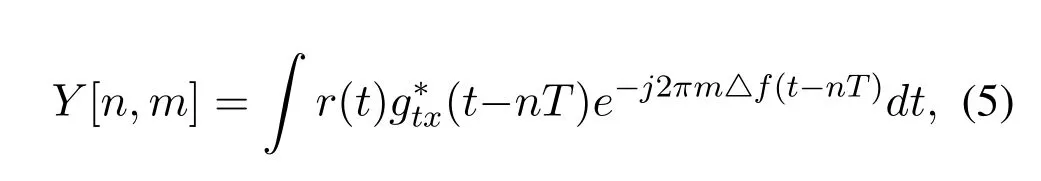
and then the symbolY[n,m] is transformed into the symboly[k,l]in the DD domain by the symplectic finite Fourier transform(SFFT).
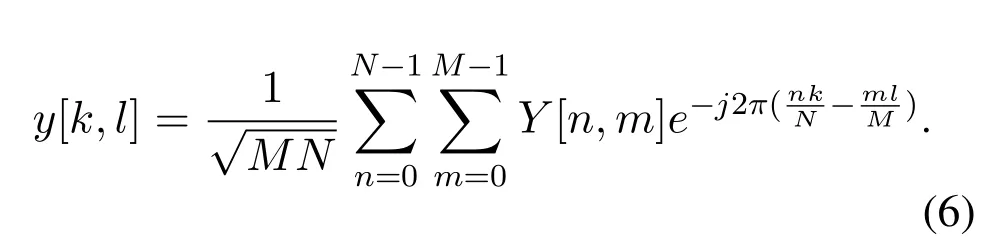
A secure OTFS link can be achieved through physical layer encryption.The two communicating entities obtain channel state information(CSI)through OTFS channel estimation[18,23,24]and generate a physical layer key on this basis,and then encrypt the transmitted information symbols before sending the signals(t).We assume in the threat model that the link between the satellite AP and the AS is a secure OTFS link,while the link between the RN and the AP is not assumed to provide physical layer security guarantees.
IV.PROPOSED SCHEME
4.1 Overview of the Scheme
Our proposed scheme consists of two parts: the authentication phase and the handover phase.The entities involved in the authentication and key agreement(AKA) phase are UE,RN,AP,and AS.The UE andthe RN implement mutual authentication with the AS based on the improved 5G-AKA protocol[14],respectively.At the same time,the RN and the UE perform mutual authentication with the help of the AS.Finally,the RN and the AP negotiate a session key KAP,and the RN and the UE negotiate a session key KS-RN,which is used to ensure the security of communication between them.
The entities involved in the handover phase are only RN,AP1,AP2and AS.The UE and the RN use the session key KS-RNnegotiated in the authentication phase for secure communication.The RN negotiates a new session key KAP2with the next target access point AP2in advance with the help of the AP1and the AS.Once the RN enters the service range of AP2,the RN can use the new session key KAP2to securely communicate with AP2,thereby realizing seamless handover for the UE.The notations used in our scheme are presented in Table 1.
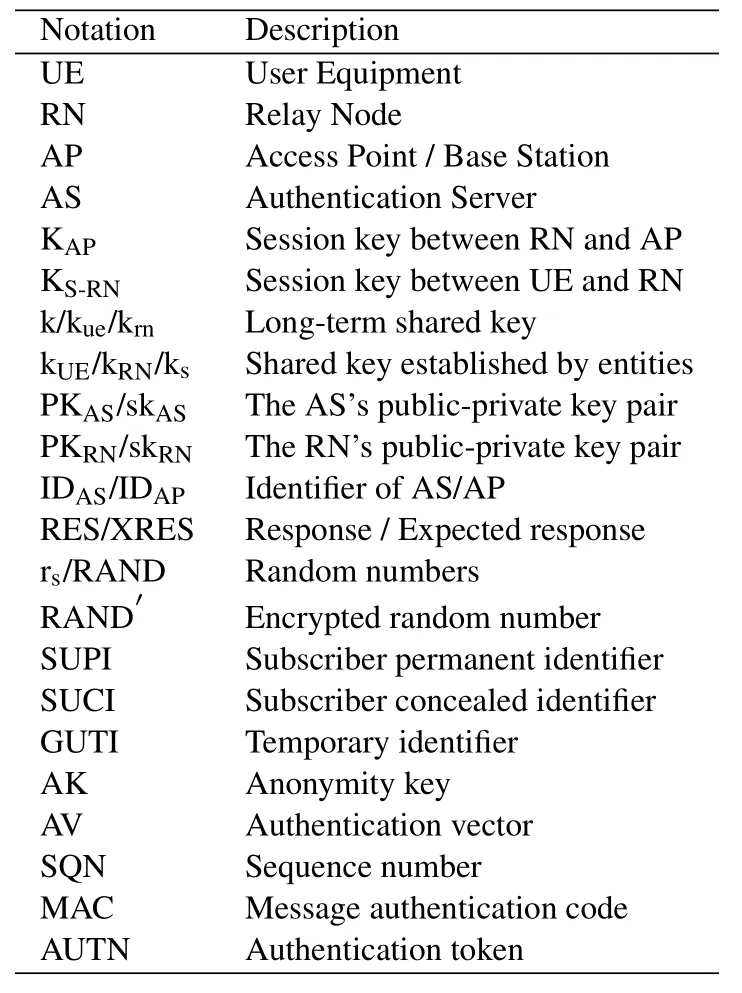
Table 1. Notations used in the scheme.
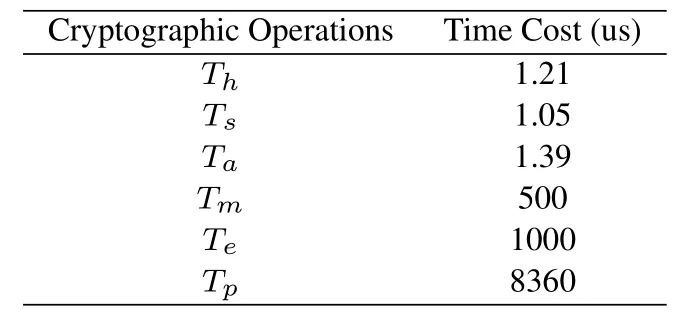
Table 2. The time required for cryptographic operations.
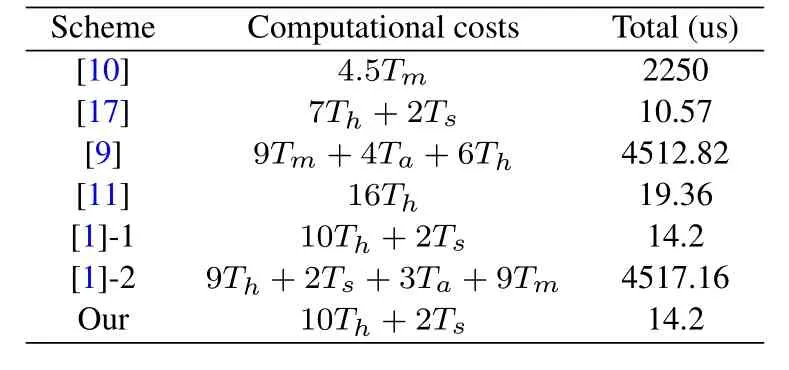
Table 3. Comparison of computational costs.
4.2 Design Idea
Our design principle is to be compatible with the existing 5G network while facing the future 6G heterogeneous network.Therefore,we design our handover authentication scheme based on the existing 3GPP technical standards[8,14,13].Before the plane takes off or the train starts,both the UE and the RN respectively complete the mutual authentication with the AS as the user equipment.The UE and the RN negotiate a session key for subsequent communication,and the RN and the AS negotiate a session key for communicating with the AP and completing the handover procedure.
To ensure the anonymity of the UE,3GPP TS 33.501 [14] adopts the Elliptic Curve Integrated Encryption Scheme(ECIES)[25]to encrypt the SUPI of the UE to obtain SUCI.ECIES is a hybrid encryption scheme that includes a key encapsulation mechanism(KEM) and a data encapsulation mechanism (DEM)[26].In each session,we use KEM to establish a shared key between protocol entities,and use DEM with the established shared key to encrypt and decrypt the communication data between entities.We generate authentication materials based on the established shared key to help entities complete mutual authentication and generate session keys between entities.Note that the shared key established each session is not the same as the long-term shared key stored between entities during the registration phase.The use of ECIES can not only realize the compatibility of our designed scheme with existing 5G networks but also help improve the security and efficiency of our scheme.
4.3 Initial Authentication Phase
In the authentication and key agreement phase,the UE completes mutual authentication with the AS with the help of the RN,and the UE also verifies the identity of the RN.The RN then completes mutual authentication with the AS and authenticates the UE with the help of the AS.Subsequently,the session key KAPbetween RN and AS and the session key KS-RNbetween RN and UE will be derived.The procedure of the protocol is shown in Figure 2,and the detailed steps are shown below.
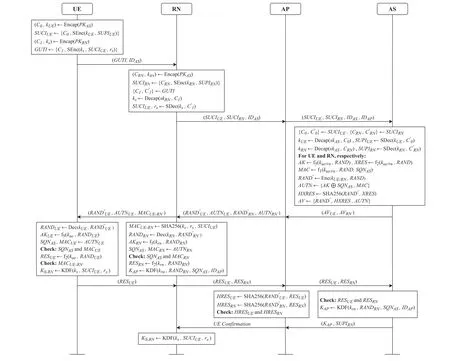
Figure 2. Mutual authentication and key agreement protocol.
Step 1: UE→RN:(GUTI,IDAS)
The UE takes the public key PKASas input,and uses the key encapsulation mechanism to generate a shared key kUEwith the AS.The UE then uses the data encapsulation mechanism to encrypt its identifier SUPIUEto obtain SUCIUE,which is used for authentication by the AS.In addition,the UE uses the public key PKRNas an input to generate a shared key kswith the RN,and generates a random number rstogether with the SUCIUEas an input to obtain the temporary identifier GUTI.The UE then sends the GUTI and the IDASof its authentication server to the RN.
Step 2: RN→AP:(SUCIUE,SUCIRN,IDAS)
The RN takes the public key PKASas input,generates a shared key kRNwith the AS,and then encrypts its identifier SUPIRNto obtain SUCIRN,which is used for authentication by the AS.Subsequently,the RN parses the received GUTI intoC1and,decryptsC1with its private key skRNto obtain the shared key kswith the UE,and then decryptswith the key ksto obtain SUCIUEand random number rs.The RN then sends SUCIRN,SUCIUE,and IDASto the AP over the OTFS link.
Step 3: AP→AS:(SUCIUE,SUCIRN,IDAS,IDAP)
After receiving the message from the RN,the AP selects the authentication server corresponding to the user according to the identifier IDAS.The AP adds its identifier IDAPto the message and sends the message to the AS.
Step 4: AS→AP:(AVUE,AVRN)
Upon receiving the authentication request sent by the AP,the AS first parses the SUCIUEand SUCIRN,and uses its private key skASto decrypt the message to obtain the shared key kUEwith the UE and the shared key kRNwith the RN.The AS then decrypts SUCIUEand SUCIRNusing the key kUE/RNto obtain SUPIUEand SUPIRN,respectively.
Subsequently,the AS calculates the parameters required for generating the authentication vector for the UE and the RN,respectively.The AS first generates a random number RAND,and then uses the key derivation functionf5to generate the anonymity key AK through the long-term shared key kUE/RNwith the UE or RN.The AS then uses the message authentication functionsf2andf1to generate the expected response XRES and the message authentication code MAC,respectively.SQNASis the sequence number generated by the AS for UE and RN to verify the freshness of the message.The definition of functionsf1,f2,andf5can refer to 3GPP TS 33.102[13].
Finally,the AS encrypts RAND with the key kUE/RNto obtain RAND′,and calculates the hash value of RAND′and XRES to obtain HXRES.The AS then generates the authentication token AUTN and constructs the authentication vectors AVUEand AVRNcorresponding to the UE and the RN according to the RAND′,HXRES,and AUTN,and sends them to the AP.
After receiving the authentication vector sent by the AS,the AP stores the RAND′and HXRES for subsequent authentication of the UE and the RN,and sends the RAND′and AUTN corresponding to the UE and the RN to the RN through the OTFS link.
Step 6: RN→UE: (RAND′UE,AUTNUE,MACUE-RN)
Once the RN receives the message from the AP,it first calculates the message authentication code MACUE-RNaccording to the shared key ks,which is used for the UE to authenticate the RN.The RN then sends a messageto the UE and starts to authenticate the AS.

Subsequently,the RN generates the authentication response RESRNaccording to Eq.(8),which is used by the AS and the AP to authenticate the RN.The RN then calculates the session key KAPwith the AP according to Eq.(9).
Step 7: UE→RN:(RESUE)
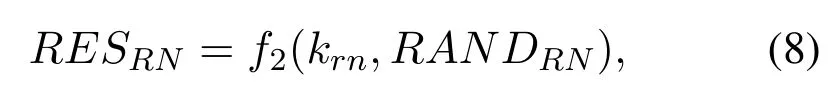
Once the UE receives the message from the RN,the UE needs to authenticate the RN and AS.The UE first decryptswith the shared key kUEto obtain RANDUE,and then uses the long-term shared key kUEwith the AS to generate AKUEbased on RANDUE.The UE parses SQNASand MACUEfrom AUTNUEusing AKUE,and checks whether MACUEsatisfies Eq.(10)and whether SQNASis fresh.

If the UE successfully authenticates the AS,the UE generates the authentication response RESUEaccording to Eq.(11)and sends the RESUEto the RN.
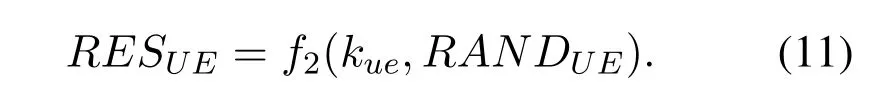
The UE authenticates the RN by checking whether the MACUE-RNsatisfies Eq.(12).If the authentication is successful,the UE calculates the session key KS-RNwith the RN according to Eq.(13).
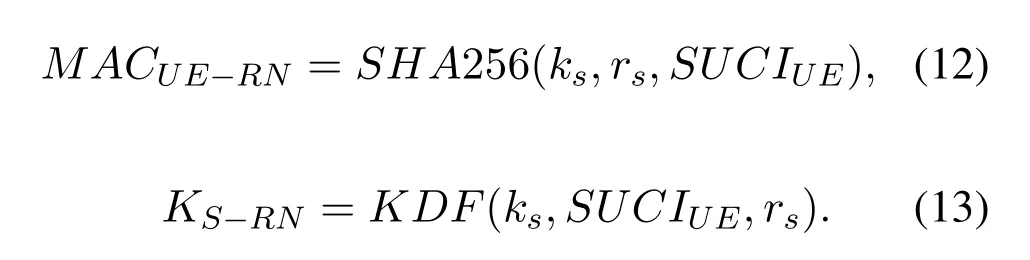
Step 8: RN→AP:(RESUE,RESRN)
After the RN receives the RESUEsent by the UE,it adds its authentication response RESRNand sends(RESUE,RESRN)to the AP through the OTFS link for authentication.
Step 9: AP→AS:(RESUE,RESRN)
Based on the received RES and the previously stored RAND′,the AP calculates the hash values HRESUEand HRESRNfor the UE and RN according to Eq.(14)and(15),respectively.The AP then compares the calculation result with the previously stored HXRESUEand HXRESRN,and if they are consistent,the UE and RN are successfully authenticated from the AP’s point of view.The AP then sends the (RESUE,RESRN) to the AS for further authentication.
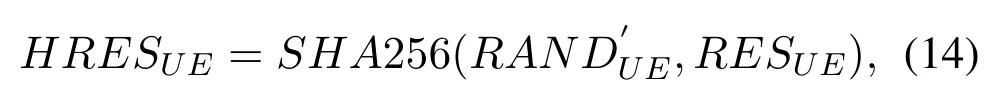
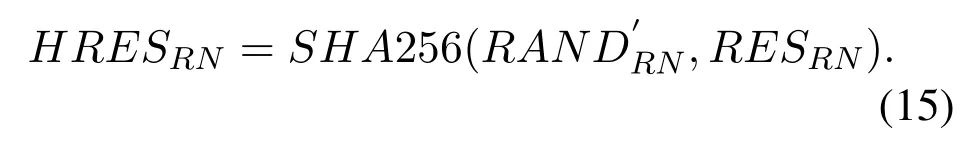
Step 10: AS→AP:(KAP,SUPIRN)
The AS compares the RESUEand RESRNreceived from the AP with the XRESUEand XRESRNit generated before.If they are consistent,the UE and the RN are successfully authenticated from the perspective of the AS.
The AS then generates the session key KAPbetween the AP and the RN according to Eq.(9),and sends it to the AP together with the SUPIRN.
Step 11: AP→RN:(UE Confirmation)
The AP receives the session key KAPsent by the AS and uses it to communicate with the RN as the session key.Finally,the AP generates a UE authentication success message through the key KAPand sends it to the RN over the OTFS link.
Step 12: RN generates KS-RN
After the RN accepts the message sent by the AP to confirm the successful authentication of the UE,it generates the session key KS-RNwith the UE according to Eq.(13).
After the initial authentication and key agreement procedures are completed,the UE and the RN establish the session key KS-RN,and the RN and the AP establish the session key KAP,which are respectively used to ensure the security of their respective communication channels.
4.4 Handover Phase
In the handover phase,the RN establishes a new session key KAP2with AP2with the assistance of AP1using the session key KAP1and the shared key kRN.The KAP1is the session key established by the RN,AP,and AS in the authentication phase,and the kRNis the shared key established by the RN and AS in the authentication phase.The procedure of the handover protocol is shown in Figure 3,and the detailed steps are shown below.
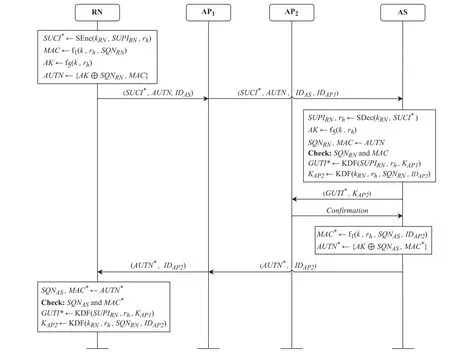
Figure 3. Handover protocol.
Step 1: RN→AP1: (SUCI*,AUTN,IDAS)
The RN generates a random number rhtogether with the identifier SUPIRNas input,and generates a new temporary identifier SUCI*using the shared key kRNestablished with the AS during the authentication phase.Then,the RN uses the functionf1to generate the message authentication code MAC based on the long-term shared keykwith the AS,the random number rh,and the sequence number SQNRN.Finally,the RN uses the key derivation functionf5to calculate the anonymity key AK,generates the authentication token AUTN,and then sends a handover request message containing(SUCI*,AUTN,IDAS)to AP1over the OTFS link.
Step 2: AP1→AS:(SUCI*,AUTN,IDAS,IDAP1)
AP1adds its identifier IDAP1to the message received from the RN,and then forwards the handover request message to the corresponding AS.
Step 3: AS→AP2: (GUTI*,KAP2)
After receiving the handover request message sent by AP1,the AS first decrypts SUCI*with the shared key kRNestablished with the RN to obtain the identifier SUPIRNof the RN and the random number rh.Then the AS generates AK based on the rhand the longterm shared keykwith the RN,and uses AK to parse AUTN to obtain SQNRNand MAC.The AS checks whether the MAC satisfies Eq.(16),and then checks whether the SQNRNis fresh.
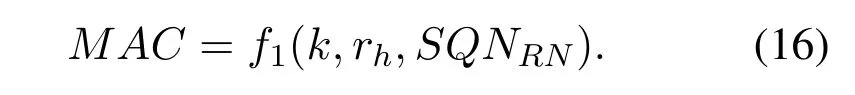
If the AS successfully authenticates the RN,the AS takes SUPIRNand rhas input and generates a new temporary identifier GUTI*for the RN according to Eq.(17).The AS then selects a new access point AP2and calculates the session key KAP2between the RN and AP2according to Eq.(18),and sends GUTI*and KAP2to the AP2.
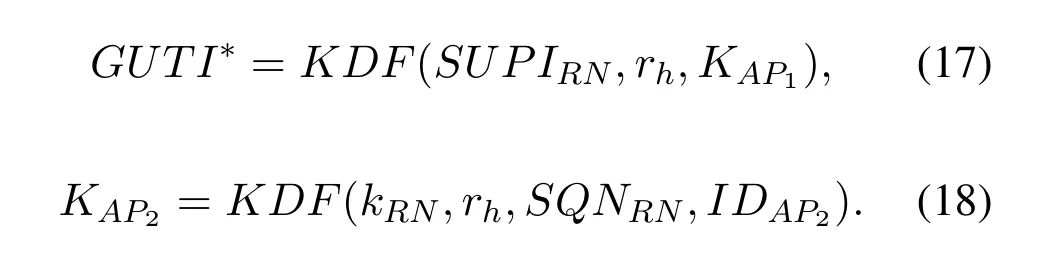
Step 4: AP2→AS:Confirmation
AP2stores the received RN identifier GUTI*and session key KAP2for subsequent communication with the RN,and then sends a key confirmation message and other related messages to the AS.
Step 5: AS→AP1: (AUTN*,IDAP2)
The AS generates a message authentication code MAC*according to Eq.(19),which is used for the RN to perform authentication.Note that the identifier IDAP2of AP2also participates in the calculation of the MAC*.Finally,the AS constructs AUTN*based on AK,SQNAS,and MAC*,and then sends it to the AP1together with IDAP2.
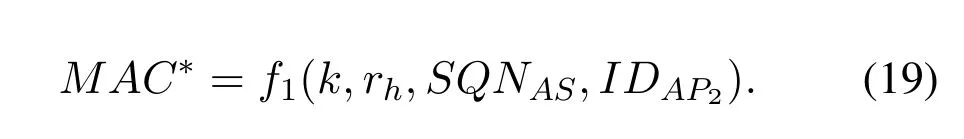
Step 6: AP1→RN:(AUTN*,IDAP2)
Once the AP1receives the handover response message sent by the AS,the AP1forwards the message to the corresponding RN over the OTFS link.
Step 7: RN generates KAP2
The RN uses AK to parse out SQNASand MAC*from the received AUTN*,then checks whether MAC*satisfies Eq.(19)and checks whether SQNASis fresh.If both verifications are successful,the RN generates the temporary identifier GUTI*according to Eq.(17)and calculates the session key KAP2according to Eq.(18)for subsequent communication with AP2.
After the handover process is completed,once the UE enters the service range of AP2,the session key KAP2negotiated in the handover phase can be used between the UE and AP2to ensure the security of the communication channel.
V.SECURITY ANALYSIS
In this section,we evaluate the security properties of the proposed scheme through the informal security analysis and formal verification tool Tamarin.
5.1 Informal Security Analysis
5.1.1 Mutual Authentication and Key Agreement
In the initial authentication phase,the UE/RN authenticates the AS by checking whether the received MAC is equal to the MAC value calculated by itself according to Eq.(10)/(7).The AS authenticates the UE/RN by checking whether the received RES is equal to the XRES calculated by itself.Only the legitimate AS has the private key skASand the long-term shared key kUE/RNconsistent with the UE/RN.Therefore,only the legitimate AS can decrypt the SUCI to obtain the correct shared key kUE/RNfor encrypting the RAND and generate the correct MACUE/RN.Likewise,only the legitimate UE/RN can decrypt the RAND and generate the correct RESUE/RN.Therefore,the RN and AS can respectively calculate the session key KAPaccording to Eq.(9)for subsequent communication between the RN and the AP.The RN authenticates the UE through the AS,and the UE authenticates the RN by checking the MACUE-RN.Only the legitimate RN has the private key skRNto decrypt the GUTI to get the correct ksand rs.In this way,the UE and RN can calculate the session key KS-RNaccording to Eq.(13) for subsequent communication.
In the handover phase,only the legitimate RN and AS have the same shared key kRNand long-term shared keyk,so that the correct MAC/MAC*can be calculated to pass mutual authentication.Therefore,the RN and AS can calculate the new session key KAP2according to Eq.(18) for subsequent communication between RN and AP2.
5.1.2 User Anonymity and Unlinkability
To ensure the anonymity of the user equipment,the UE generates a temporary identifier GUTI based on its encrypted identifier SUCIUEand random number rsin each session with the RN.Only the legitimate AS can get the actual identifier SUPIUEof the UE.Therefore,no attacker can reveal the actual identifier of the UE.The RN also uses the encrypted identifier in the session with the AS,and the attacker also cannot obtain the actual identifier of the RN.
For the linkability of the user equipment,in addition to generating a temporary identifier GUTI for the UE in each session,various linkability attacks against the UE are also prevented by encrypting the RAND using the established shared key kUE[27].If the transmitted RAND′is modified or replayed by an attacker,the UE will output an error message when checking the correctness of the MACUE.This approach fundamentally solves linkability attacks against UEs based on failure messages [28],sequence number inference [29],and SUCI replay[30,31].
5.1.3 Key Forward/Backward Secrecy
Based on the session key Eq.(9),(13),and (18) between entities,we can infer that even if the attacker knows the session key of the current session,he cannot guess the session key of the previous session as well as the future session.Because parameters such as rs,rh,RAND,and SQN are different in each session,the session key generated for each session is also different.
Similarly,even if the long-term shared key between the UE and the AS is stolen by the attacker,the attacker cannot derive the previous session key.Because the generation of KAPrequires the participation of the RAND of the current session,and the RAND also needs to be generated using the shared key kRNestablished by the current session.The generation of KS-RNand KAP2also requires the participation of the shared keys established by them.
5.1.4 Resistance Against Replay Attacks
For the proposed scheme,replay attacks are prevented from two aspects.First,after verifying the legality of the entity by checking the MAC,the freshness of the message is also checked by the sequence number SQN.Second,random numbers such as rs,rh,and RAND are also introduced into the parameters for generating the session key,so that the session key is only bound to the current session.
5.1.5 Resistance Against Man-in-the-Middle Attacks When the attacker cannot know the secret information such as shared keys kUE/RN,kUE/RN,ksand random numbers rs,rh,RAND,etc.,they cannot forge a valid authentication request to pretend to be a legitimate protocol entity.Also,the attacker cannot generate a legitimate session key.Therefore our proposed scheme is resistant to impersonation attacks.On this basis,the attacker cannot pretend to be a legitimate AS to communicate with the UE/RN at the same time as a legitimate UE/RN to communicate with the AS,so our proposed scheme can also resist the man-in-themiddle attack.
5.2 Formal Verification Based on Tamarin
We evaluate the security of our proposed handover protocol with Tamarin.Tamarin is a powerful symbolic verification tool for analyzing security protocols [32].Tamarin takes the protocol and the security property as input.It outputs the conclusion that the protocol satisfies the security property or the counter-example that the security property does not hold.Tamarin is used by researchers in the community to analyze many protocols,including the 5GAKA protocol [28,33,34],and is a state-of-the-art tool for modeling operations such as Diffie-Hellman groups,asymmetric encryption,XOR,and more.
For the DEM paradigm,thesencandsdecfunctions from the built-in symmetric encryption theory can be used to model data encapsulation and decapsulation mechanisms.For the KEM paradigm,the builtin asymmetric encryption theory can be used,but the built-in asymmetric encryption functions cannot accurately describe the KEM paradigm.Because there are two output parameters of the Encap function,but the built-in function output parameter in Tamarin can only be one.To address this issue,we refer to the equation proposed by Wang et al.[27]to model the KEM paradigm in Tamarin,as shown in Eq.(20).
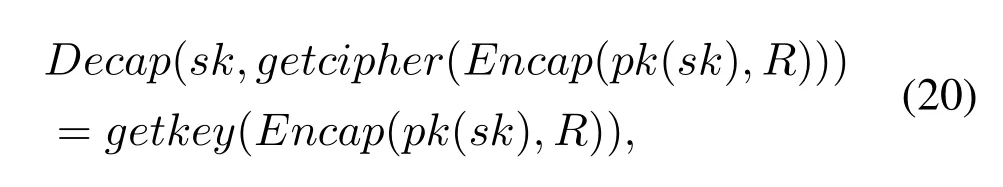
where R is a random number,indicating that the Encap function is a randomness algorithm.Therefore,the shared keys kUE/RNestablished in different sessions are also different.pk(sk)is a built-in asymmetric encryption function in Tamarin,representing a public-private key pair.The getcipher function takes the output of the Encap function as input and outputs the ciphertext encapsulating the shared key.The getkey function takes the output of the Encap function as input and outputs the shared key.
We analyze the security properties satisfied by the proposed handover protocol in Tamarin,and the source code of our protocol model is available on Github [35].The verification results of the protocol are shown in Figure 4.Our proposed scheme can achieve mutual authentication between the RN and the AS and achieve injective agreement on the session key.The attacker cannot obtain the real identifier SUPI of the RN under the condition that the RN or AS cannot be compromised,hence the scheme can achieve the anonymity of the user.Furthermore,the attacker cannot obtain the session key of the current session,and the scheme can achieve perfect forward secrecy.Even if the attacker obtains the long-term shared key in the current session,the session key established by the previous session is still secret.
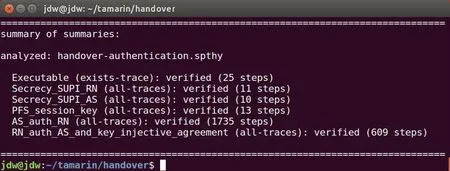
Figure 4. Verification results of the handover protocol.
VI.PERFORMANCE EVALUATION
In this section,we analyze and compare the computational cost and functionality of our proposed scheme with previous ones.
6.1 Computational Cost
Our proposed scheme consists of an initial authentication phase and a handover phase,where the initial authentication phase occurs before the departure of the train or plane,and the handover phase occurs during high-speed movement.In such a scenario,the main factor affecting the user communication quality is the handover phase.Therefore we mainly evaluate the computational cost of the handover phase.
To facilitate comparison with other schemes,we consider the cost of the following operations as in other schemes,and other operations such as XOR are ignored.A one-way hash or MAC operationTh,a symmetric encryption/decryption operationTs,anelliptic curve point addition operationTa,an elliptic curve scalar multiplication operationTm,a modular exponentiation operationTe,and a bilinear pairing operationTp.Since the time required to perform these operations on computing platforms with different computing resources is different,we refer to the simulation time of predecessors to compare the computational cost,and do not distinguish the computing power between RN and AS.Table 2 shows the time required for the above cryptographic operations,tested in[1]using the OpenSSL library on an Intel(R)Core(TM)i7-7500U CPU 2.70 GHz processor.
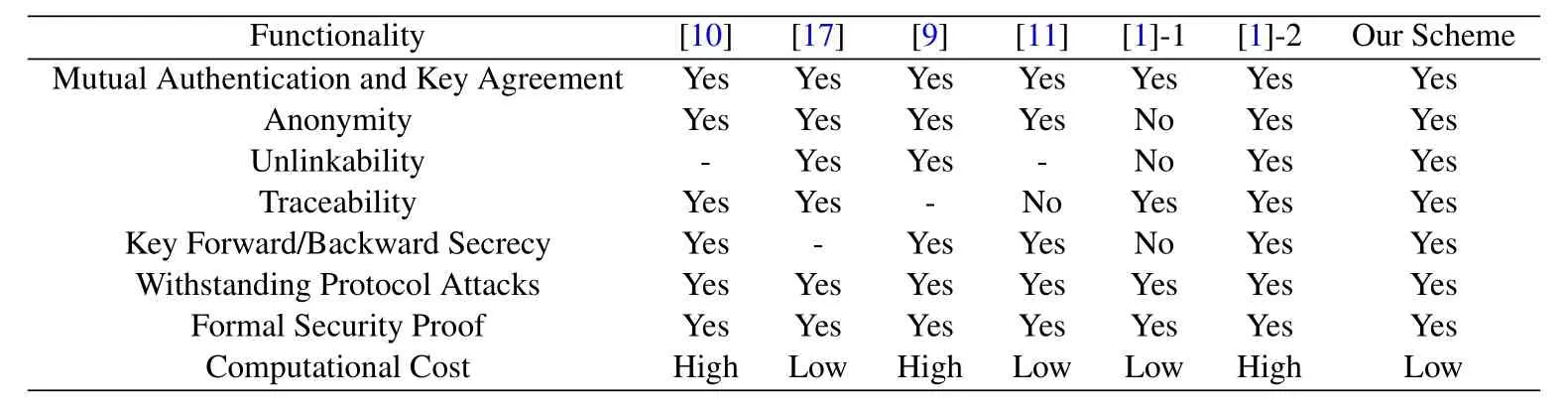
Table 4. Comparison of functionality.
The comparison results of the computational cost required in the handover phase are shown in Table 3.Due to the elliptic curve cryptography operations,the computational costs of schemes[10],[9],and[1]-2 are relatively large.In contrast,the computational cost of our scheme and schemes [17],[11],and [1]-1 is relatively small.We did not consider batch access in the comparison.In the scenario of group handover of user equipment,our scheme can achieve better performance.Since our scheme establishes a session key between UE and RN in the initial authentication phase.Therefore,in the handover phase,only the RN needs to negotiate a new session key with the target AP without the participation of the UE,so our scheme does not cause additional computational costs.
6.2 Functionality Comparison
Table 4 shows how our proposed scheme compares with other schemes in terms of functionality including security properties.The“-”symbol indicates that there is no discussion of such properties in the scheme.Overall,compared with other schemes,our proposed scheme has strong security guarantees and also has a small computational cost.Schemes [10],[9],and[1]-2 can provide similar security guarantees as our scheme,but at a higher computational cost.Schemes[17],[11],and[1]-1 have similar computational costs to our scheme but cannot provide the same strong security guarantees as our scheme.
As for the formal security analysis,Scheme [1]also analyzes the security properties satisfied by the scheme in Tamarin.But they did not prove the user’s anonymity in Tamarin,that is,whether the attacker can obtain the user’s real identifier SUPI.Schemes[9]and[10] use the AVISPA tool [36] to analyze the security properties of the protocol,and scheme [17] uses the Scyther tool [37] to analyze the security of the protocol.Scheme [11] theoretically analyzes the security of the scheme in the Real-Or-Random (ROR)model,without using formal verification tools such as Tamarin,AVISPA,or Scyther.
VII.CONCLUSION
In this paper,we propose an efficient handover authentication scheme with user privacy protection for the handover requirements of high mobility scenarios.According to the characteristics of high mobility scenarios,we negotiate the session key between UE and RN and the session key between RN and AP in the initial authentication phase based on the KEM mechanism for subsequent communication.Therefore,the UE and the AP can be decoupled in the handover phase,thereby greatly improving the handover efficiency and achieving the seamless handover of the UE.Our security analysis including the formal verification tool Tamarin demonstrates that our proposed protocol has strong security guarantees and is resistant to multiple attacks.Moreover,the performance evaluation compared with other schemes shows that our scheme can provide strong security guarantees while also having a small computational cost,which is very suitable for high mobility scenarios.
ACKNOWLEDGEMENT
This work was supported by Natural Science Foundation of China(No.62002006,U2241213,U21B2021,62172025,61932011,61932014,61972018,61972019,61772538,32071775,91646203),and Defense Industrial Technology Development Program(No.JCKY2021211B017)
- China Communications的其它文章
- Secrecy Transmission of NOMA-OTFS Based Multicast-Unicast Streaming
- Orthogonal Time Frequency Space Modulation in 6G Era
- Joint Multi-Domain Channel Estimation Based on Sparse Bayesian Learning for OTFS System
- BER Performance Analysis of OTFS Systems with Power Allocation
- Channel Estimation for OTFS System over Doubly Spread Sparse Acoustic Channels
- Iterative Receiver for Orthogonal Time Frequency Space with Index Modulation via Structured Prior-Based Hybrid Beliefand Expectation Propagation

