BER Performance Analysis of Asynchronous NOMA with Arbitrary Phase Offset
Chang Liu,Sheng Wu,*,Chunxiao Jiang,Hongwen Yang
1 School of Information and Communication Engineering,Beijing University of Posts and Telecommunications,Beijing 100876,China
2 Tsinghua Space Center,Tsinghua University,Beijing 100084,China
Abstract: An asynchronous transmission scenario for non-orthogonal multiple access(NOMA)user signals with arbitrary phase offset is investigated in this paper.To improve the system performance in the user power-balanced conditions,we adopt a synthetic detection method at the receiver,i.e.,the jointly optimal maximal likelihood detection aided triangular successive interference cancellation(JO ML-TSIC)method.Analytical bit error rate(BER)solutions are obtained for a two-user case with the optimal,intentional onehalf symbol period time delay implemented between the user signals.Furthermore,closed-form BER solutions for the case using the triangular successive interference cancellation(TSIC)detection method are also derived for comparisons.Numerical results show that the JO ML-TSIC receiver for the asynchronous system outperforms the TSIC receiver as well as the synchronous successive interference cancellation (SIC)receiver in all the conditions concerned.The results also show that the superiority of the JO ML-TSIC receiver is strengthened when the signals experience flat Rayleigh fading channels compared to the TSIC and the synchronous SIC receivers.
Keywords:non-orthogonal multiple access(NOMA);asynchronous transmission;jointly optimal(JO)maximum likelihood (ML) detection; successive interference cancellation(SIC);bit error rate(BER)
I.INTRODUCTION
Multiuser non-orthogonal multiple access(NOMA)is a promising strategy to improve the system throughput in the future generation communication networks[1,2].In the literature,the majority of papers on NOMA contribute to solving the problems under the conventional presumption of synchronous users [3–5].Nevertheless,asynchronous NOMA is shown to be able to achieve superior system performance compared to the synchronous NOMA[6–12].In this sense,asynchronous transmissions create another dimension of freedom for NOMA users,beyond the common use of power-,frequency-and code-domain resources.There are mainly two categories of asynchrony studied in the existing literature on this topic.One category focuses on the scenario that a random time delay presents in each user’s signal,which is usually deemed as the uplink analysis where the user timing advance scheme is not properly applied [6,7,13].The other category focuses on utilizing artificial asynchrony to improve the system performance[8–12].Specifically,the optimal relative intentional time delay for a twouser asynchronous NOMA is shown to be a half symbol period [7,11].By applying this optimal time delay to a two-user NOMA,the user sum throughput can be maximized [7],while the mutual interference can be maximally suppressed using the asynchronous successive interference cancellation detection(SIC)at the receiver[11].
1.1 Related Work
Signal asynchrony brings great challenges to the design of multiuser detector at the receiver.The conventional jointly optimal maximum likelihood (JO ML)sequence detector [14,15]imposes high computational complexity for asynchronous signal detection,and thus,it may not be used in many practical scenarios.As SIC is deemed as the most economical detection technique for power-domain NOMA,a triangular pattern SIC (TSIC) detection scheme was proposed in[13]regarding the asynchronous signal structure to mitigate the interference from all the stronger users.The authors in[8]designed a pre-coded method matched with a whitening-and-decomposing detection scheme for downlink asynchronous NOMA.A message passing(MP)detection method was developed in[16]for users with equal transmission powers in the uplink,and the signal-to-interference-plus-noise ratio of the detector output was analyzed.In [17],an approximate MP-based detection method was proposed for uplink asynchronous code-domain NOMA.This method was shown to be able to obtain near-optimal performance while retaining low detection complexity.Besides,the authors in[12]utilized a trellis-based algorithm to decode the asynchronous user signals and improve the performance.A novel transceiver design was also proposed to reduce the computational complexity.Note that the detection method in [16]only applies for users with equal transmission powers while the method proposed in[17]is only efficient for nonoverloaded code-domain NOMA.Furthermore,implementations of the detection methods in [12]and [8]demand collaborated design at the transmitter.In contrast,the T-SIC detection method is not substantially restricted to any specific conditions,which makes it versatile to be used in many practical scenarios.Nevertheless,the TSIC detection method
Focusing on the theoretical performance,signal asynchrony also raises the difficulty of error rate analysis.Analytical solutions to the error rates for the users are very important for they can reveal insights on the system reliability and enable intuitive comparisons with other systems.As to the synchronous systems,the error rate performance of NOMA has been actively investigated for the SIC receivers in [18–26],and for the JO ML receivers in[27–29].Besides,it is shown in [30]that the JO ML detector achieves better performance compared to the SIC detector in the powerbalanced condition.In contrast,much fewer works on the error rate analysis for asynchronous NOMA have been reported in the literature.The bit error rate(BER)performance for uplink users withM-ary quadrature amplitude modulation in [13]was analyzed in an approximate approach.The authors in [11]derived the accurate BER solutions for two quadrature phase-shift keying users with a half symbol period asynchrony using T-SIC.Notably,results in[11]also showed that the accuracies of the BER solutions proposed in [13]are highly restricted.To the best of the authors’ knowledge,other works regarding the error rate performance for any other asynchronous systems are not available in the literature.
1.2 Contribution
In this paper,we propose a synthetic detector for asynchronous NOMA to pursue higher BER performance,namely,the JO ML aided TSIC(JO ML-TSIC)detector.This proposed detector combines the advantages of the JO ML detector and the TSIC detector.On one hand,the participation of JO ML promises better performance over the pure TSIC detection scheme,especially when the difference between the user powers are insignificant.On the other hand,JO ML-TSIC follows the detection structure of TSIC,which suppresses all the interference from the stronger signals through interference cancellation.Note that the proposed JO ML-TSIC detector conducts symbol-by-symbol detection,so the receiver is much less burdened compared to the conventional JO ML sequence detector for asynchronous signals.Additionally,the intentional half symbol period delay proposed in [11]is employed to improve the performance of a two-user system.The main contribution of this work can be summarized as follows.
• Using the JO ML-TSIC detector,error rate performance for the uplink two-user NOMA is investigated.Exact BER for the stronger user is derived,and a highly accurate BER approximation for the weaker user is derived given arbitrary phase offset between the user signals.
• Closed-form BER formulas for the same system using TSIC detector are also derived for comparisons,where the formula for the stronger user is accurate,and that for the weaker user is highly accurate approximation.
• The accuracies of the obtained formulas are verified through simulation results.Results show that the JO ML-TSIC detector gains a large deal of benefit on the BER performance over the TSIC scheme when the user signal powers have insignificant difference.The results for the synchronous system with conventional SIC are also presented to show the comprehensive benefit gained by the proposed detector with intentional asynchrony.
1.3 Organization
The remainder of this paper is organized as follows.In Section II,the system model and receiver detection rules for two asynchronous NOMA signals with a half symbol period delay are illustrated.Section III calculates the BERs of the two users for the JO MLTSIC and the TSIC detectors.In Section IV,numerical and simulation results of the BER performance for the considered scenario are presented,and the results for the asynchronous systems are compared with those of synchronous NOMA using the conventional SIC detector.The results are discussed and some conclusions are drawn.Section V concludes the paper.
II.SYSTEM MODEL AND RECEIVER DETECTION PROCESS
Suppose there are two NOMA users,U1and U2,communicating with the base station,whose baseband signals are given by
whereDiandSirespectively denote theith information symbols of U1and U2and they both take values in{−1,1}equally likely,r(t) is the rectangular pulse shaping function with unit power,r(t)=0 fort /∈[0,T],andP1andP2are respectively the received signal powers of U1and U2.
We assume the channel is invariant within the transmitted symbol blocks,and the channel state information is known at the receiver.A timing delay command is applied to the signal of U2,which makess(t)arrives with a delay ofτ=T/2 compared to the time ofd(t).At the receiver,the composite user signal is given by
wherehd,hsare the amplitude gains of the wireless channels in which the signals of U1and U2propagate,respectively,ωcis the angular frequency of the user carriers,θ ∈[0,2π)is the relative random phase offset in the carrier of U2,cosθindicates an arbitrary signal correlation,andn(t)is the AWGN process with twoside spectrum densityN0/2.LetA1=be the received signal amplitudes andA1≥A2.The joint signal in thekth symbol period ofd(t)is given by
We assume that the receiver equips coherent detectors.The receiver adopts different sampling timings to detect the two user signals.As is shown in Figure 1,the symbol sequence of U2is delayed by 0.5T.The symbol detection needs to follow the order of TSIC given in [11]to suppress the asynchronous interference,e.g.,D1,D2,S1,D3,S2,and etc.The order is also marked by the arrows in Figure 1.When the JO ML-TSIC detector is used,the symbols of U1are assigned to the JO ML detector while those of U2are assigned to the single user detector.When the TSIC detector is used,symbols of both users are all assigned to the single user detector.
2.1 Symbol Detection of U1
We first utilize a pair of orthonormal functionsandϕy(t)=sin(ωct) to extract the signal vector of(3),namely,,whose real and imaginary components are given by
2.1.1 Detection Rule of JO ML-TSIC
The symbols of U1are detected using the JO ML method under this condition.The JO ML detecting process is similar to the one depicted in [14],[27],which indicates that the detector selects the joint symbol constellation point that has the least Euclidean distance to the corrupted signal vector.The detection rule is given by
During this process,the symbols of U2cannot be correctly detected,we extractfrom the output of the JO ML detector.
2.1.2 Detection Rule of TSIC
The detection process of TSIC is equivalent to the symbol detection process for the single user case,the rule of which is given by
Note that the interfering signal from U2is treated as noise in this process.
2.2 Symbol Detection of U2
In the detection of U2,the JO ML-TSIC detector and the T-SIC detector follow the sample principle,which is the single user detection.Therefore,the following process generalizes the cases for the two detectors.Before the detection ofSk,the receiver must acquire decisions,and+1,re-modulate these symbols to yield(t),and then subtract(t)from the received signal.After subtraction,the remaining signal can be written as
Now alignvr(t)with the symbol timing of U2,and lett′=t−T/2.Focusing on thekth symbol period ofs(t′),the signal in(7)becomes
whereεk,εk+1denote the detection errors of thekth andk+ 1th symbol of U1,respectively,i.e.,εk=Dk−,εk+1=Dk−.The detection ofSkfollows the single user detection process.By calculating the correlation ofw(t′)with the basis function,the decision ofSkis made by following,
whereEk=(εk+εk+1)/2,εk,εk+1∈{−2,0,2},andNk,2obeys the Gaussian distributionN(0,N0/2).
III.BER PERFORMANCE ANALYSIS
3.1 BER of
Without loss of generality,we assume thatDk=1 is transmitted.Due to the symmetry of the signal constellations,the BER forθ ∈[0,π/2]is sufficient to scope the system performance[27,28].Due to the law of total probability,the BER ofcan be written as (10)
Then(10)can be written as
We have thatη1=η3=1/4 andη2=1/2.Expressions forp1,p2andp3will be derived for the JO ML-TSIC case and the TSIC case in two parts,respectively.
3.1.1PDefor JO ML-TSIC Detection
When using the JO ML detection,p1,p2andp3in(11)can be interpreted as the conditional probabilities that the estimateis detected in error given that=1,0 and−1,respectively.The decision boundary forDkhas two patterns for different values ofθ,which are shown in Figure 2.The constellation points for the noiseless joint signal in (4) are denoted byP1∼P6.Let(xi,yi)denote the coordinates of pointPi,the probability fractionpican be calculated as
andRbe=U1∪ U2∪ U3∪ U4.When cos−1[A2/(2A1)]<θ ≤π/2,the subregions divided in Figure 2b are defined as
withU4previously defined in (13d).We haveRbe=V1∪V2∪U4.Due to the symmetry,the coordinates of pointsA′,B′andC′are respectively the opposite values to those of pointsA,BandC,kA′B′=kABandkA′C′=kAC.NotekAC=kAB.As will be used in the following calculation,the values of these parameters are listed in Table 1 in terms ofA1,A2andθ.Consequently,by substituting the subregions ofRbeinto (12) and simplifying,one obtains the formula ofpias(15)
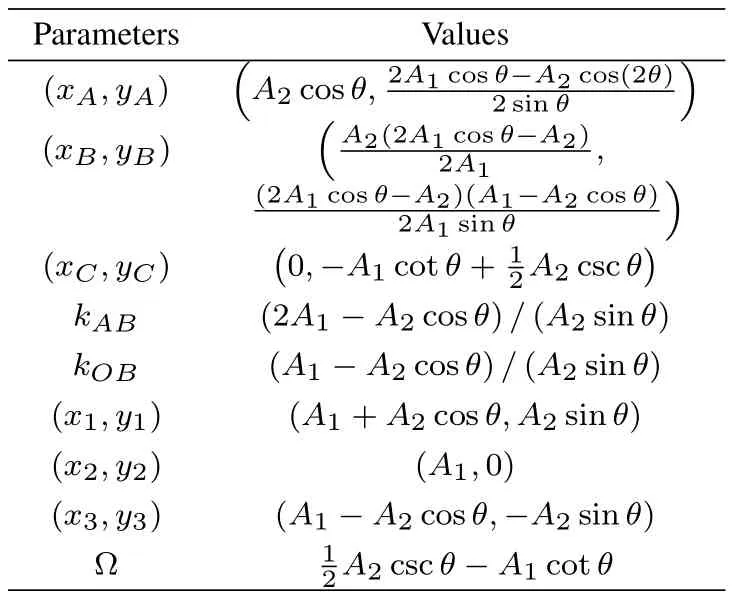
Table 1.Values of the parameters in(15).
where the parameters are given in Table 1.PDefor the JO ML-TSIC detector is thus achieved by substituting(15)to(11).
3.1.2PDefor TSIC Detection
When using the TSIC detection,the decision boundary is theϕy(t)axis.Under this condition,the BER ofcan also be written as the weighted sum of three probability fractions shown in (11).This is raised by different locations of the constellation points with respect to the decision boundary for=−1,0,and 1.Based on(6),we have
By substituting(16)into(11),one obtains the BER of U1for the TSIC detector.
3.2 BER of
As has been discussed in Section II,Skis always detected using TSIC.In such manner,errorEkpropagates in the detection ofSkin (9) whenDkand/orDk+1are/is detected in error.However,the error probabilities ofandare not independent becauseSkis the interfering symbol in common.These error probabilities vary with the values assigned to{Sk−1,Sk,Sk+1},which means the decisionis influenced by symbols{Sk−1,Sk,Sk+1}in return.Therefore,the BER ofcan be written as(18)
Eq.(17)to(18)utilizes the symmetry of the error probabilities ofwhenSk−1=−Sk+1=1 or−1.Analysis for the probability in (18) is detailed in the Appendix,and the final expressions for the three probability terms involved are given in(20)-(29),respectively.Substituting(27)-(29)into(18)yields the BER of
wherePDeis the weighted sum ofp1,p2andp3given by(11).
The BER formulas for U2using the JO ML-TSIC detector and the TSIC detector can be calculated with the help of the probability fractionsp1,p2andp3given in (15) and (16),respectively.Specifically,when the JO ML-TSIC detector is utilized,the BER for U2can be obtained by substituting (15) into (19); when the TSIC detector is utilized,the BER for U2can be obtained by substituting(16)into(19).
IV.NUMERICAL RESULTS AND SIMULATIONS
In this section,numerical results of the average BER performance for the JO ML-TSIC and the TSIC detection methods are presented.Eqs.(11),(15),(16),(19)are used to calculate the BERs for the users.The results are averaged overθ ∈[0,π/2)to obtain the average BER performance.All the numerical results were calculated by Mathematica.Results of Monte Carlo simulations are also provided to verify the accuracies of the proposed formulas.All the simulations were implemented by Matlab.In all simulations,we assume that BPSK symbols are used,and the size of each symbol stream of a user sampled at the receiver detector is 103,and 106symbol streams are independently detected.The relative signal phase for the symbol stream of U2is uniform on [0,2π),and it changes independently in the next symbol stream of U2.Since the noise vectors sampled in the symbol detections of U2are linearly correlated to those of U1in the asynchronous case,these noise samples can be obtained through linear combinations of the noise samples that appear in the detection of U1as illustrated in the Appendix.We assume the noise has unit power for simplicity,so the values for the signal powers can be assigned straightforward given the user signal-to-noise ratios (SNRs).As a benchmark,the simulated average BER performance for uplink synchronous two-user NOMA using the conventional SIC detection scheme over the relative phase offsetθis provided to reflect the benefit of the one-half symbol period asynchrony.Analytical results are not given since the BER solutions to the synchronous BPSK two-user NOMA with arbitrary relative phase offset are not available in the literature.We use the synchronous SIC case to refer to such scenario in the following discussion for simplicity.
Figure 3 presents the average BER performance for U1and U2varying with the received user power ratio,namely,A20/A21,when the received SNR of U2is fixed at 6 dB.The BER curves for the two users under the same scenarios are respectively presented in two individual figures for clear illustrations.Firstly,we notice that the BER curves for all the three detection schemes have similar trends.With the increase of the received user power ratio,the interference from U2becomes weaker in the detection of U1,and the BER of U1monotonically reduces.As the receiver detector subtracts the recovered signal from U1in the detection of U2,the BER for U2also decreases,and gradually reaches an error floor.The final BER performance for the error floor approximately equals the BER of the single user case in the additive white Gaussian noise(AWGN)channel,which is=2.39×10−3.Next,we notice that by using the intentional 0.5Ttime-delay asynchronous scheme,it can achieve superior BER performance for both users employing the asynchronous signal detectors,compared to the synchronous SIC case.Observe that the BER of U1for the TSIC scheme is always onehalf of that achieved by the synchronous SIC scheme,which coincides with the conclusion drawn for the two-user QPSK case without arbitrary phase offset in[11].When using the JO ML-TSIC scheme,the BER performance for both users is improved.The improvements mainly focus on the case where users have fewer power difference.In addition,the figure also shows that the proposed exact BER solutions for U1have perfect agreements with the simulation results; the proposed asymptotic BER solutions for U2achieve very high accuracies compared with the simulation results,where only very minor deviations can be observed at 3,4,5 dB user power ratios.
Figures 4 and 5 show the average BER performance for the two users versus the SNR of U2exploiting the three detection schemes,when the user power ratios are 0 dB and 2 dB,respectively.Focusing on the results in Figure 4,it can be shown that the JO ML-TSIC scheme outperforms the asynchronous TSIC scheme as well as the synchronous SIC scheme by large margins with the increase of the SNR of U2.In such a power-balanced case,the slopes of the BER curves are mild due to the strong mutual interference,while those for the JO ML-TSIC scheme still has the largest slope of decreasing.Moreover,it is shown in the figure that the gaps between the BER curves for different detection schemes cannot be reduced,which indicates that the superiority of the JO ML-TSIC scheme cannot be achieved by simply improving the user SNR using other detection schemes.
As the user power ratio grows from 0 dB to 2 dB,the average BER performance for both users becomes more sensitive to the increase of the SNR of U2,the behaviors of which are described as follows.The BER of U1is lower than that of U2for the asynchronous detection schemes,while the BERs for both users converge in the synchronous SIC case.Within the considered range of SNR,the BERs for the JO ML-TSIC scheme are always one-half of those for the TSIC scheme in sketchy while the BERs of the two users for the synchronous SIC case are very close to the BERs of U2for TSIC.Therefore,the superiority of the JO ML-TSIC scheme has been well illustrated.Figure 4 and Figure 5 also show that the analytical results are in good agreements with the simulation results.Specifically,the BER approximations for U2are again very tight to the simulation results.
To gain more insights on the performance for the JO ML-TSIC,the TSIC detector and the synchronous SIC detection schemes,simulation results for the average BER performance over flat Rayleigh fading channels are presented in Figure 6,where the BER curves are plotted versus the received average user power ratio.The average SNR of U2is fixed at 20 dB.The channel coefficients,|hd|and|hs|,both subject to the normalized Rayleigh distribution.In all the detections,the receiver selects the user who has larger received power to detect in priority,i.e.,if|hd|2Pd ≥|hs|2Ps,it detects U1first; otherwise U2first.It is clear in Figure 6 that the BER curves for the users in fading channels have some similarities with those for the AWGN channel case.In general,using the asynchronous scheme can achieve better BER performance compared to the synchronous scheme.The asynchronous JO ML-TSIC scheme outperforms the asynchronous TSIC scheme by large margins.Notably,the gaps between the BER curves for U1using different detection schemes are enlarged compared to Figure 3,which indicates that the superiority of JO ML-TSIC is strengthened in the small-scale fading channels.Observe that by applying the JO ML-TSIC detection scheme,10 dB less user power ratio is needed compared to the TSIC scheme,and 7 dB less compared to the synchronous SIC case.The improvement on the BER performance achieved by the JO ML-TSIC detector for U2is relatively modest compared to that for U1,however,it converges faster to the error floor compared to the other two schemes.
V.CONCLUSION
In this paper,an uplink asynchronous two-user NOMA was considered,where the optimal one-half symbol period delay was implemented in the weaker user signal to pursue the maximum benefit of asynchrony.We employed the JO ML-TSIC method for asynchronous signal detection at the receiver.Analytical BER formulas for the two users were derived.Furthermore,the BER solutions using the TSIC scheme were also presented for comparisons.Results show that the JO MLTSIC receiver with the intentional time delay transmission scheme gains better BER performance compared to the TSIC receiver and the synchronous SIC receiver.The superiority of JO ML-TSIC on the BER performance for the users is striking when the received user powers are comparable.Under this condition,the differences between the BER performance achieved by these receivers cannot be reduced by improving the user SNRs.Simulation results verified the obtained analytical results.Moreover,it was shown through the results for the average BER performance over flat Rayleigh fading channels,the JO ML-TSIC receiver outperforms the TSIC receiver and the synchronous SIC receiver by larger margins compared to the cases for AWGN channel.
ACKNOWLEDGEMENT
This work was supported by the National Natural Science Foundation of China(Grant No.62022019).
APPENDIX
Recall that in(9),the errors of symbolsDkandDk+1add up in the detection ofSk.Given thatDkandDk+1are randomly assigned−1 or 1,the outcomes ofEk=(εk+εk+1)/2 are{−2,−1,0,1,2}.DenoteZ={Sk=1,Sk−1=1,Sk+1=1}.The probabilityin the right side of (18) can be derived as (20)
The probability in (20) is a sum of five terms.Focusing on the first term,P(Nk,2≥A1Ekcosθ+A2|Ek=0,Z) represents the conditional probability that nditional probability thatis detected in error givenEk=0 and eventZ.This probability does not equal toP(Nk,2≥A2) forEk=0 is dependent toNk,2.The reason thatEkis dependent toNk,2is because the noise sampleNk,2is linearly correlatedwhile the ranges ofare constricted given thatEk=0.By following a similar derivation to[11,eq.(5)],we obtain the correlation coefficients betweenNk,2andas{0.5 cosθ,0.5 sinθ,0.5 cosθ,0.5 sinθ}.The existing correlation makes an exact approach to such problem intractable.It is clear that with the change ofθ,the above specified correlation coefficients are always lower than 0.5.Now by ignoring the weak correlation between the noise samples and assuming independence instead[11],an approximation approach is utilized to yieldP(Nk,2≥A1Ekcosθ+A2|Ek=0,Z)≈P(Nk,2≥A2).Such approximation can also be used in the calculations of the remaining probability terms that have similar forms toP(Nk,2≥A1Ekcosθ+A2|Ek=0,Z) in (20).Consequently,we have
whereinP(Ek=0|Z)is calculated as
Similarly,one obtains
By substituting eqs.(22)-(26) into (21),the BER ofconditioned onZis obtained as (27)
Through some similar derivations,the second and third summands on the right side of (18) can be respectively obtained as(28)and(29)
- China Communications的其它文章
- Environment Information-Based Channel Prediction Method Assisted by Graph Neural Network
- Multi-Scenario Millimeter Wave Wireless Channel Measurements and Sparsity Analysis
- AG Channel Measurements and Characteristics Analysis in Hilly Scenarios for 6G UAV Communications
- Long-Range VNA-Based Channel Sounder: Design and Measurement Validation at MmWave and Sub-THz Frequency Bands
- A Novel Millimeter-Wave Channel Measurement Platform for 6G Intelligent Railway Scenarios
- A Geometry-Based Stochastic Scattering Channel Model for V2V Communications in Dense Urban Street Environments

