Physical Layer Security for UAV Communications:A Comprehensive Survey
Jue Wang,Xuanxuan Wang,Ruifeng Gao,Chengleyang Lei,Wei Feng,*,Ning Ge,Shi Jin,Tony Q.S.Quek
1 School of Information Science and Technology,Nantong University,Nantong 226109,China
2 Department of Electronic Engineering,Tsinghua University,Beijing 100084,China
3 China Academy of Electronics and Information Technology,Beijing 100041,China
4 School of Transportation and Civil Engineering,Nantong University,Nantong 226109,China
5 National Mobile Communications Research Laboratory,Southeast University,Nanjing 210096,China
6 Information Systems Technology and Design Pillar,Singapore University of Technology and Design,Singapore 487372,Singapore
7 Nantong Research Institute for Advanced Communication Technologies,Nantong 226109,China
Abstract: Due to its high mobility and flexible deployment,unmanned aerial vehicle(UAV)is drawing unprecedented interest in both military and civil applications to enable agile and ubiquitous connectivity.Mainly operating in an open environment,UAV communications benefit from dominant line-of-sight links;however, this on the other hand renders the communications more vulnerable to malicious attacks.Recently, physical layer security (PLS) has been introduced to UAV systems as an important complement to the conventional cryptography-based approaches.In this paper, a comprehensive survey on the current achievements of UAV-PLS is conducted.We first introduce the basic concepts including typical static/-mobile UAV deployment scenarios,the unique air-toground channel and aerial nodes distribution models,as well as various roles that a UAV may act when PLS is concerned.Then,we start by reviewing the secrecy performance analysis and enhancing techniques for statically deployed UAV systems, and extend the discussion to the more general scenario where the UAVs’mobility is further exploited.For both cases, respectively,we summarize the commonly adopted methodologies, then describe important works in the literature in detail.Finally,potential research directions and challenges are discussed to provide an outlook for future works in the area of UAV-PLS.
Keywords: physical layer security; UAV communications;static/mobile UAV deployment;air-to-ground channel;trajectory optimization
I.INTRODUCTION
Current achievements of the fifth generation (5G)technologies have provided significant advances in the conventional communication scenarios [1, 2].However,it is still challenging to support the communication demand in remote areas where the conventional communication infrastructure cannot reach (e.g., on the ocean) [3-5], or in the unexpected or emergency situations such as mass crowding or infrastructure malfunctioning due to natural disasters.Besides, the explosively increasing Internet-of-Things (IoT) devices and applications also require new coverage enhancing techniques.To handle these issues,an intelligent architecture with the aid of unmanned aerial vehicles(UAVs)has been considered as a promising new paradigm[6-10].Owing to the merits of high mobility and flexible deployment, UAV communications have been widely invoked for civilian,commercial,and military applications in a wide way [11-15].The role of UAV communications is becoming increasingly important in 5G and beyond networks,which is two-folds as concluded in [16]: 1) UAV-assisted cellular communications.As agile and flexible platforms, UAVs can help to realize the requirements of massive connectivity and ubiquitous coverage [17]; 2) Cellularconnected UAVs.The development of terrestrial cellular networks on the other hand supports higher data rate for UAV users, promoting new applications such as real-time video monitoring.A series of excellent survey works on UAV communications can be found in the literature[18-22].
While having promising merits, UAV communications may suffer more from malicious attacks.One the one hand, the high flying altitude of UAV generally leads to strong line-of-sight (LoS) links between UAV and ground nodes,or among the aerial nodes.A dominant LoS air-to-ground(A2G)or air-to-air(A2A)link is desirable for legitimate communications,however, it also poses opportunity for adversaries.An attacker could take advantage of the LoS propagation to enhance its eavesdropping quality,or improve its jamming efficiency.On the other hand,UAV may work in a shared frequency band with other systems in some cases.For example, most current UAV communication systems adopt the Industrial Scientific Medical(ISM) band defined by ITU-R (e.g., 2.4 GHz).The large amount of users,which operate in the same band but may come from different systems,will raise interference(unintended jamming)and privacy issues.For these reasons,communication secrecy in UAV systems have attracted increasing research attentions,not only from the academia but also from the industry[23].
Unlike the terrestrial communication infrastructures, UAVs usually have more stringent constraints on their on-board energy and computational capability.Besides, due to its high mobility, the topology of a UAV communication network could be highly dynamic.For these reasons, applying the upper-layer cryptography-based schemes for secure UAV communications might have practical limitation.Physical layer security(PLS),on the other hand,has been recognized as a promising way to realize information theoretic secure transmissions with low computational complexity [24, 25].The application of PLS techniques to UAV communications has attracted dramatically increasing research interests since the past few years.It should be noted that the conventional PLS techniques in general cannot be directly applied to the UAV scenario, where some important new issues that need to be specifically taken into account include:
·New design dimension:The mobility of UAV raises a new dimension for optimization, that is,the position or trajectory of UAV.As a matter of fact,position optimization and trajectory planning constitute a large portion of the related research works on UAV-PLS.
·New channel/network characteristics:The A2G/A2A channels have different characteristics compared with the terrestrial channels; the distribution of aerial nodes may have new forms(e.g., distributed within a three-dimensional(3D) sphere with minimum inter-node distance restriction); new physical conditions might need to be considered in the analysis and design, e.g.,the random jitter of UAV will affect the channel characteristics, and raise challenge for channel state information(CSI)acquisition in practice.
· New power consumption models: Energy efficiency(EE)becomes more important as the UAV systems are in general energy-limited.EE as a common design objective has been widely considered in energy-constrained systems such as IoT.However, as a new issue that should be considered, propulsion energy consumption of UAV,which is related to the UAV’s velocity and acceleration rate,renders the total energy constraint more stringent and coupled with practical mobility and trajectory design of UAVs.New power consumption models are required to account for these practical issues.
·New constraints:Practical kinetic models,as well as the existence of no-fly zones, pose new constraints on the feasible positions in trajectory optimization[26].
1.1 Comparison with Existing Surveys
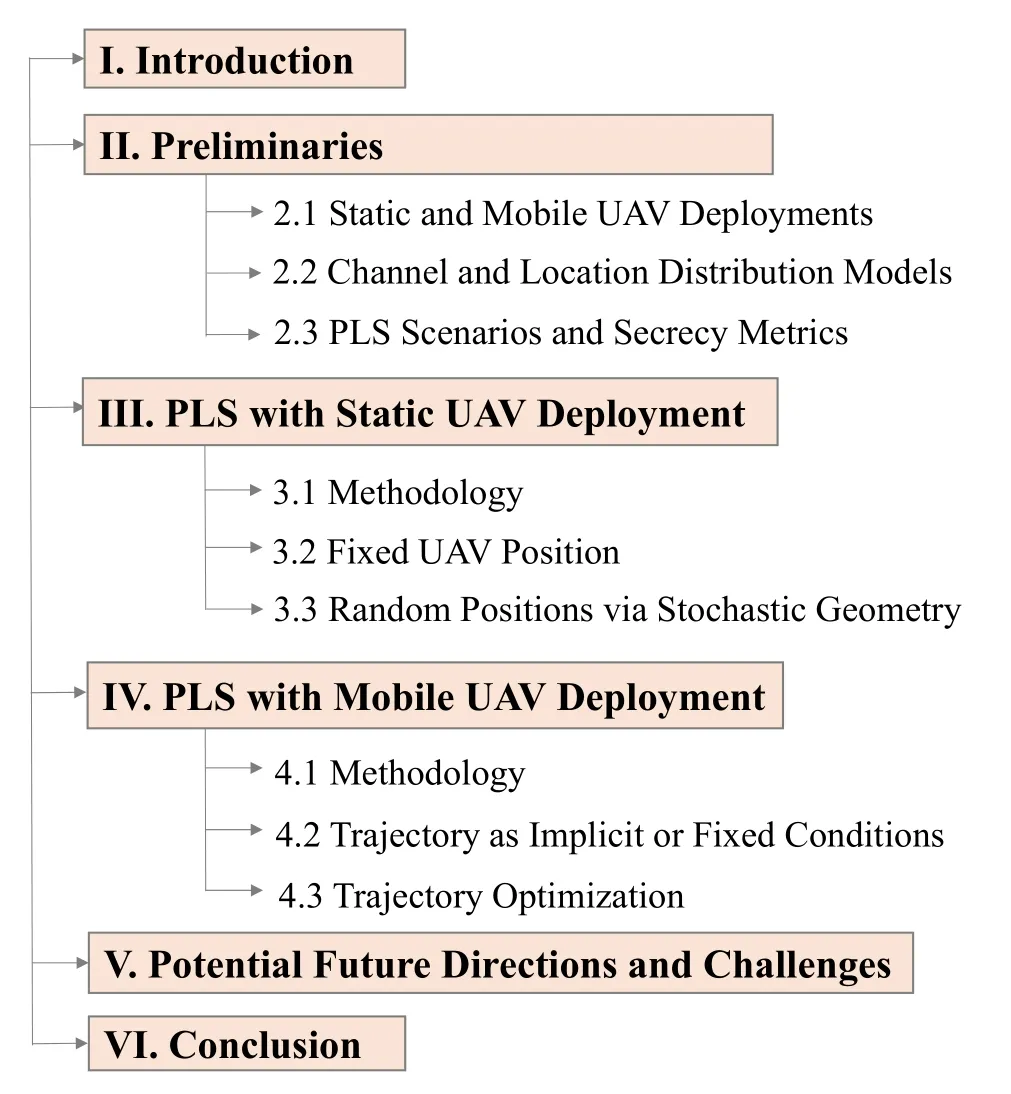
Figure 1.Organization of this survey.
Concerning of the above-mentioned issues in the field of UAV-PLS,a number of excellent survey works have been done [27-31].More recently, [32] described the combination of PLS and UAV with a detailed case study.In these works, important research directions were summarized, possible application scenarios were described,and future opportunities and challenges were discussed.However, we note that the existing surveys [27-31] mainly introduce UAV-PLS from a “big-picture” perspective.As magazine papers, only a few most representative references have been described,while the other(actually quite a large amount of) recent progresses, in various application scenarios of UAV-PLS, have been left undiscussed.This is also the case for[32], where after introducing the basic concepts of PLS, and discussing several interesting UAV-PLS application scenarios, the authors focused more on a specific case study to show the promising potential of employing UAV for PLS enhancement.However, for a researcher who needs to take a closer look at a specific research direction that he/she is interested,there still lacks of a systematic and comprehensive review of the large amount of existing technical contributions in the literature up to present.
To this end,we try to establish a framework for categorizing the large amount of researches on UAV-PLS,and under which, provide a comprehensive review of the most important existing works and latest research progresses.To our best knowledge,this is the first detailed comprehensive survey focusing on the PLS issue in UAV communication systems.
1.2 Organization of This Paper
This survey is structured as figure 1.In Section II,we first present necessary preliminaries for the subsequent discussion.Note that many existing works on UAV-PLS are largely fragmented: The UAV may play different roles, the secrecy metrics are various,and the design problem ranges from conventional resource allocation/power control/precoding design, to UAV-specific problems such as position/trajectory optimization.To describe these dispersed works in an organized way, we classify them into two major categories according to the deployment form of UAVs,namely static and mobile deployments.These two deployment forms generally have different application scenarios and analysis/design methodologies, which will be explained briefly inSubsection 2.1, and later described in detail in Section III and IV,respectively.InSubsection 2.2, we highlight the unique characteristics of A2G channels, as well as the location distribution models in UAV systems.These specific models render the analysis and design of UAV-PLS in general different as compared to that in the conventional terrestrial scenarios.InSubsection 2.3, we summarize the possible roles of UAV under the concept of PLS.Specifically, UAV may act as a legitimate communication node (transmitter (Tx) or receiver (Rx)),a helper (friendly jammer or relay), an attacker, or a monitor/hidder in the concept of covert communications.For different roles, the design objectives and secrecy metrics are in general different,which are described therein accordingly.
In Section III and Section IV,we survey the existing works for static and mobile UAV deployments,respectively.For each section, we first summarize the general design objectives and methodologies commonly adopted for the corresponding deployment form (inSubsection 3.1andSubsection 4.1), then provide detailed description of the corresponding works in the literature.The surveyed works are further categorized according to the analysis framework or design methodology they used.Specifically, for static UAV deployment, we consider two major research directions: 1) (Subsection 3.2) The UAV and/or the other communication nodes have fixed positions,and hence performance analysis and transmission design are conducted under a fixed typology.2)(Subsection 3.3)The positions of the communication nodes are randomly distributed in a target area.In this case, the spatially averaged long-term secure performance is the focus.Similarly,the literature related to mobile UAV deployment is also surveyed for two major research categories: 1)(Subsection 4.2)The UAV flies along a predetermined fixed trajectory, or along a trajectory not being explicitly specified.For this branch of research direction,the major objective is to investigate the impact of UAV moving on the system performance,while the trajectory itself is not a design objective.2)(Subsection 4.3)The trajectory of UAV is to be optimized.The so-called trajectory planning problem becomes a major research direction.It has been investigated for various scenarios and contributes the most number of works to the literature.
In Section V, we further introduce the important emerging directions in the field of UAV-PLS.Some cutting-edge techniques including reconfigurable intelligent surface(RIS),UAV swarm-enabled coordination, integrated UAV-satellite networks, mobile edge computing(MEC),and machine learning,etc.,are envisioned to enhance the PLS of UAV communications in the coming sixth generation(6G)era.At last,concluding remarks are provided in Section VI.
II.PRELIMINARIES
In this section,preliminary knowledge for UAV-PLS is provided.We first briefly discuss typical UAV deployment forms (categorized as static and mobile deployments)inSubsection 2.1.For both deployment forms,the channel and nodes location distribution models are in general different from that for the conventional communication scenarios(e.g.,cellular).This constitutes a major difference between UAV-PLS and conventional PLS works,and is therefore highlighted and discussed inSubsection 2.2.At last inSubsection 2.3,we describe different roles that a UAV may act, as well as the corresponding secure performance metrics,which provides necessary information for better understanding the subsequent literature review.
2.1 Static and Mobile UAV Deployments
2.1.1 Static Deployment
In some application scenarios,UAV may be deployed at fixed locations to provide coverage for a target area,when the terrestrial communication infrastructure is absent, damaged, or its capacity becomes insufficient due to user crowding.When only one ground receiver is considered, the optimal UAV position, obviously,should be placed as closely as possible to the receiver when UAV acts as a transmitter, or it should be determined jointly considering the locations of the transmitter and the receiver when UAV acts as a relay [33, 34].When multiple ground users need to be served,an important design objective is to guarantee coverage with minimum cost,e.g.,in terms of the power consumption or the required number of UAVs.This can be done by optimizing the UAV’s 3D position(xU,yU,zU) [35, 36].Furthermore, when multiple UAV transmitters are available, guaranteeing ground coverage can be formulated as a so-called disk covering problem.As the coverage region of the UAV forms a circular disk on the ground,the problem aims to cover the target area with minimum number of disks with minimum cost, which has been widely investigated in the literature[37-39].
As far as PLS is concerned,the UAV position should be determined jointly considering the locations of both the legitimate nodes and malicious attackers, as illustrated by an example scenario in figure 2a.In general,the UAV should be placed close to the legitimate nodes, and away from the malicious nodes, to guarantee channel superiority for the legitimate links to realize information-theoretical secure communication.However,the problem usually cannot be so easily formulated and solved.On the one hand,the location information of passive eavesdroppers (Eves) cannot be easily obtained.Although it has been assumed that the position of Eves can be detected by the UAV, via an optical camera or synthetic aperture radar (SAR)equipped on-board, see e.g., [40], the acquired Eve’s location could be imperfect.Besides, the fast fading channel of Eve, if considered, in general cannot be known for passive eavesdropping.In this case, designing secure communication without(or with partial of) Eve’s CSI is practically important.On the other hand,possible trade-off,which is not that straightforward,may exist if some sophisticated channel models are considered.For example, when blocking probability in the A2G channel is taken into account, increasing the UAV altitudezUmay reduce the blocking probability,meanwhile,the path loss is also increased.These effects need to be jointly considered for both the legitimate and malicious links, based on that, the UAV altitude should be carefully designed according to the secrecy performance metric of interest.Moreover, when multiple ground nodes (either legitimate or malicious)are considered,the aforementioned diskcovering problem will become more complex.These design issues will be reviewed and discussed in detail in the following Section III.
For more practical consideration,a UAV in general cannot be perfectly statically deployed.UAV hovering may cause shadowing effect[41],and inevitable UAV jitter may introduce new randomness to the channel[42].These effects will raise new challenges to the design of secure UAV communications, and will be specifically highlighted when we introduce the A2G channels in Subsection 2.2.
2.1.2 Mobile Deployment
Unlike the rotate-wing UAV which can stay at a fixed position during the service time, a fix-wing UAV has to keep flying.For example,it may fly along a circular route over the target area [33], or it may fly from an initial location to a final location(take-off and landing sites) according to predefined flight route [43].For these cases, the trajectory of UAV is considered as a fixed condition,other than an optimization dimension.When the flight route is fixed and known a priori,it is possible to exploit this information for efficient transmission design.As an example,the large-scale fading conditions over all time slots along the route now can be predicted.With such information,the transmission can be designed in a long-term manner, e.g., allocating power over all time slots during the flight via water filling-like approaches.
The trajectory of UAV could also be designed on purpose.For example, the user to be served is moving and the UAV is deployed for accompanying flight,or there exist multiple users separated in distance,such that the UAV needs to fly from one to another to accomplish data transmission/collection with completion time and quality of service (QoS) constraints.When PLS is considered, the flight trajectory should be designed avoiding the Eves’ locations.Different from static UAV deployment,now a series of positions over a continuous time duration need to be optimized.A commonly adopted analysis framework is transmission time discretization.As shown in figure 2b, the entire flight periodTis divided intoNequal-length time slots,whereT=Nδtwithδtrepresenting an unit time slot.It is usually assumed thatδtis sufficiently small such that the UAV can be approximately considered to be static within each slot.Via discretization,the UAVs’ continuous trajectory (xU[t],yU[t],zU[t]),0< t < T, can be approximately expressed aswhere(xU[n],yU[n],zU[n])denotes the UAV’s Cartesian coordinate in then-th time slot.In practice,the length ofδtshould be properly chosen, accounting for the trade-off between approximation accuracy and implementation complexity.
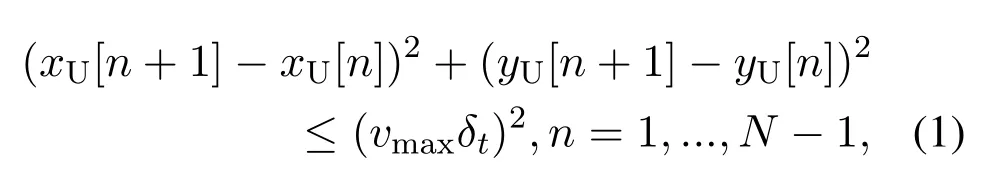
where (xU[0],yU[0]) and (xU[N],yU[N]) denote the initial and final coordinates of the UAV, respectively,for which the following constraint should be applied to guarantee the feasibility of the problem,(xU[N]-xU[0])2+ (yU[N]- yU[0])2≤(vmaxT)2.Another common constraint on the initial and final position is to guarantee that the UAV return to its take-off place.In this case,the constraint reads as(xU[N],yU[N])=(xU[0],yU[0]) [44].Similar to that for static deployment, the dimension of UAV altitude can be exploited to further enhance the PLS performance.In this case,the above constraints should be modified to 3D,which may render the trajectory planning problem more complex.Altitude-dependent fading of the A2G channel is the key information required for the design,which will be described in the following Subsection 2.2.
There exist other analysis and design frameworks.In[45],the UAV is moving but transmits only at fixed positions,termed as“stop points”.Given a target area and a flight route,the number and locations of the stop points are to be optimized.In some other works,UAV moving is implicitly reflected in the system model without being directly related to its physical positions.For example,in[46],UAV mobility will affect the corresponding link reliability, which is mathematically modelled as a Bernoulli process.These approaches will be discussed in detail later in Section IV.
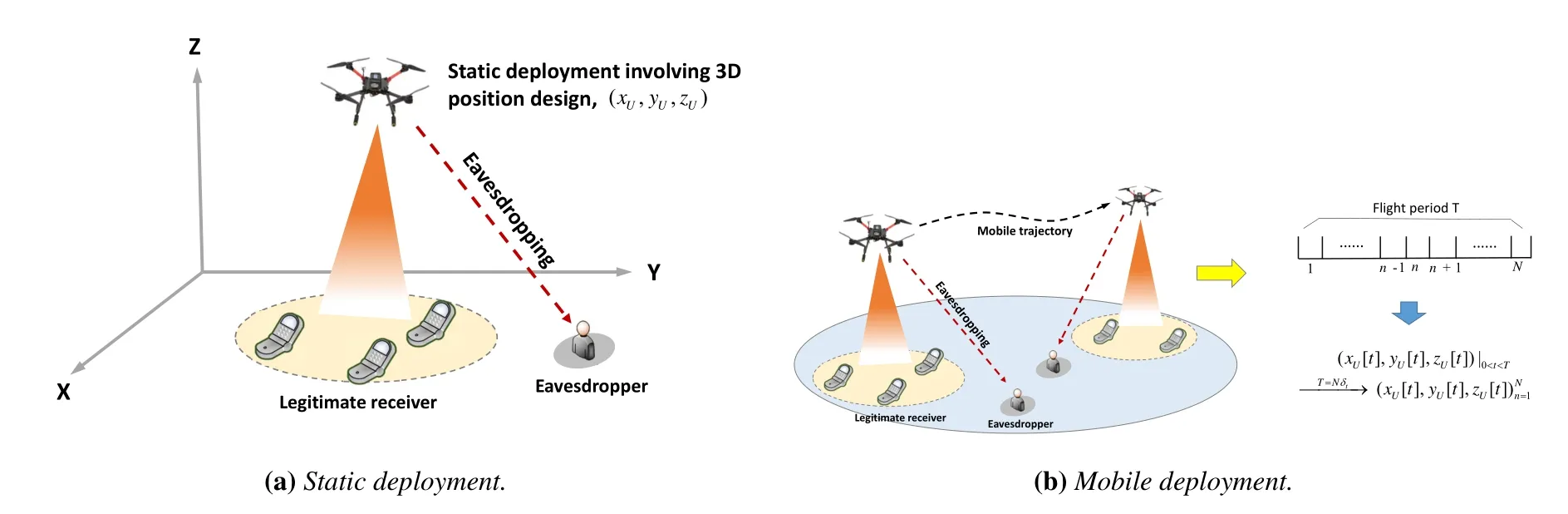
Figure 2.Example scenarios of secure UAV communications with static/mobile deployment.
2.2 Channel and Location Distributions
For both static and mobile UAV deployments, it is in general challenging to acquire instantaneous CSI of all involved nodes.Some reasons are as follows: The number of users(both legitimate and malicious)in the vast coverage area of UAV would be large;for mobile deployment,the fast moving of UAV results in highly dynamic fading channel, and will require very frequent CSI update and hence causes unaffordable overhead.Fortunately,the A2G channel(and A2A as well)has been recognized to be sparse scattering,and hence the large-scale path loss dominates the channel gain.As long as the location of a node is known,large-scale fading can be evaluated and PLS can be designed accordingly.In this subsection,we briefly introduce the commonly adopted channel model and location distribution models for UAV-PLS.For a more comprehensive survey of the existing UAV channel modelling approaches,the readers are referred to[47-49].
2.2.1 Path Loss Models
The A2G channels exhibit unique characteristics as compared to conventional terrestrial propagation channels, which may cause differences in the secrecy performance analysis and secure communication design.In general, the A2G channels behaves differently in different scenarios,e.g.,urban,rural,or overwater areas[49],for which various models have been proposed in the literature [50-53].In most of them,LoS propagation plays an important role.Nevertheless,the LoS link could be blocked in practice,and the blockage probability would be related to the UAV altitude.In general,higher altitude corresponds to larger LoS probability.Considering this effect,a probabilistic LoS/NLoS A2G channel model has been widely considered,e.g.,in[35,54,55],and described as
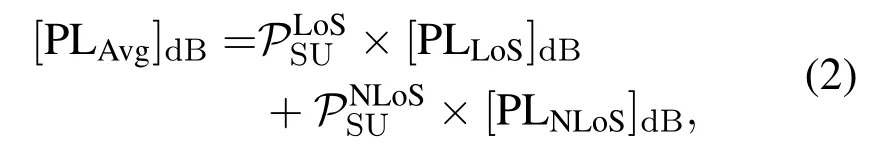
wheredenotes the LoS probability between a ground node(S)and UAV(U),which is given by
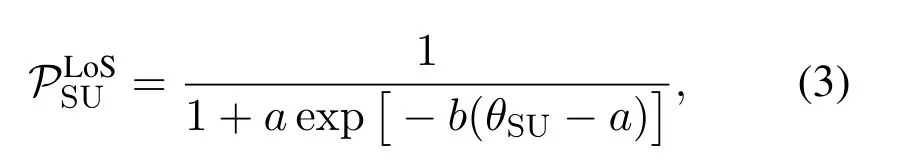
whereaandbare constants relying on the propagation environments,andθSUis the elevation angle,expressed asCorrespondingly,the NLoS probability is
[PLLoS]dBand [PLNLoS]dBin (2) are the path loss components for the LoS and NLoS conditions,respectively.These two terms are determined in different ways in the literature.In some works,they are simply assumed to be free space path loss(FSPL)with different offsets.In other works, the LoS and NLoS path loss components may have different path loss exponents, not only being different in the offsets [56, 57].For a more sophisticated modelling approach,the path loss parameters could be elevation angle-dependent[58].Specifically, it may decrease with the elevation angle.To describe this effect,it was suggested that the path loss exponent can be modelled as a decreasing function ofθSU.An example can be found in[59].
Note that the non-linear sigmoid form of LoS probability in (3) poses challenges in the analysis and performance evaluation.To tackle this problem, a piecewise-fitting model was proposed in [60], where the LoS probability was described as a piecewise linear function of the propagation distance between a UAV transmitter and a ground receiver.With this model,further analysis can be effectively facilitated.
The LoS/NLoS condition of the A2G channel link has been described in alternative ways.In [61], it is assumed that when the elevation angle is larger than a threshold, i.e., the user is located inside a disk area below the UAV, then LoS propagation dominates the channel.In the urban scenario, the LoS probability can also be determined according to the location and height distribution of the buildings [62, 63].Specifically,the locations of buildings are modelled as Poisson point process (PPP) on the ground, with their heights following Rayleigh distribution.Accordingly,whether the LoS link between a UAV and a ground user is blocked can be determined.
Finally, as for PLLoSand PLNLoSin (2), there exist more complex and specific A2G models in the literature, e.g., the floating intercept path loss model,the dual slop path loss model, the two-way path loss model, and the modified FSPL model, etc.[48].In practice,these models should be carefully selected according to the scenarios of interest.
2.2.2 Shadowing and Small-Scale Fading
Although it has been widely assumed that the largescale path loss dominates the UAV-related channels,shadowing and small-scale fading need to be considered for more precise performance evaluation.Similar to the path loss parameters,it has been shown that shadowing might also be affected by the elevation angle [64].Besides, recent measurements have shown that the airframe itself could also cause severe shadowing which cannot be neglected.During aircraft maneuvering, shadowing may last for a duration up to dozens of seconds,which has to be taken into account in mission-critical operations[65].
For small-scale fading, most conventional models,including Rayleigh, Rician, Nakagami-m, Weibull fading models,etc.,have been considered in the A2G scenario [66].Among them, Rician fading has been widely assumed in the presence of a dominant LoS link.Again, theK-factor could be elevation angledependent [59].Rician fading has also been considered for modelling the A2A channel link in[67].
2.2.3 Location Distribution Models
When explicit CSI is unknown, the location information of both the legitimate and malicious nodes is important in the secure communication design, especially when the large-scale path loss dominates the performance.PPP is usually adopted for describing the distribution of the ground nodes - this basically has no obvious difference compared to the terrestrial scenarios.However,the location distribution of UAVs shows some difference.When modelling the UAV locations in a swarm,it is necessary to consider an extra constraint that the inter-UAV distance should be larger than a safety threshold.To address this,some specific point process,e.g.,the Mat´ern Hardcore point process,has been introduced[68].Besides, different from the ground nodes,the UAVs can be deployed in 3D space.In[69],it was assumed that the position of UAV is uniformly distributed in a horizontal distance range, and also uniformly distributed in an altitude range.
Some works consider practical UAV mobility when describing its random location,reflecting its evolution over time.For example, in [70], a kinematic model has been applied to describe the location evolution of UAV.In[71],random waypoint mobility(RWPM)and uniform mobility (UM) models were adopted to describe the UAV location as a 3D-mobility movement process.The readers are referred to these papers and the references therein for more information.
At last, we introduce some widely adopted location error models, which are usually considered for robust design in the cases that the location of Eve cannot be precisely obtained.A bounded location error model has been considered in[72],where the real location coordinate q, is modelled by the known location coordinateplus an error vector Δq, such that q =+Δq.Δq could be randomly drawn from an uncertainty region Ψ,defined as Ψ ≜{Δq∈R2×1:||Δq||2≤ω2},whereωis the radius of the error disk.For the ease of analysis,ωwas modelled as a Gaussian random variable with zero mean and non-zero variance in [73].More information on the location error model is referred to the references therein.
2.3 PLS Scenarios and Secrecy Performance Metrics
As the last but an important part of the preliminary,we summarize the commonly considered PLS scenarios and the corresponding secrecy performance metrics.According to the role that a UAV may act, we classify the PLS scenarios into: 1)UAV acts as communication node(transmitter or receiver),2)UAV acts as helper(friendly jammer or relay),3)UAV acts as attacker(malicious jammer or Eve),and 4)UAV acts as hider or surveillant (in the concept of covert communications).While some secrecy performance metrics are common,there exist specific performance metrics which are more concerned in a certain scenario,as will be discussed and highlighted in the following.
2.3.1 UAV as Communication Node
The UAV may act as legitimate transmitter or receiver.In the presence of eavesdropping, a major design objective is to maximize the secrecy rate(SR),which has been widely considered in PLS and defined as
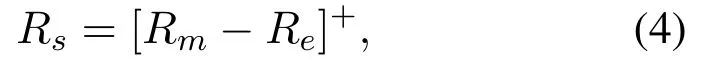
whereRm=log2(1+γm)andRe=log2(1+γe)are the achievable rate of the main channel and the wiretap channel,respectively,withγmandγerespectively representing the instantaneous SNRs of the legitimate link and the eavesdropping link.As long asRs >0,wiretap coding can be conducted to guarantee zero information leakage to Eve.
However, evaluating (4) requires knowledge of Eve’s instantaneous CSI, which is usually unavailable.Fortunately,in UAV communications,the channel and system performance are usually dominated by the large-scale fading due to sparse scattering,as previously discussed.In this case, (4) can be calculated with location information only,and optimal design to maximize the SR can be conducted.
For mobile UAV deployment where its trajectory is to be designed, average secrecy rate(ASR)is usually considered as the optimization objective.1The designer aims to maximizewhereRs[n]is the SR in then-th time slot andNdenotes the total number of slots during the flight period.A general form of the optimization problem is described as
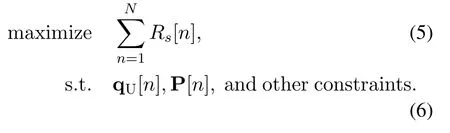
where qU[n] = (xU[n],yU[n],zU[n]) denotes the UAV coordinates in slotn,usually constrained by(1),P[n]is the power allocation at slotn.There may exist other practical constraints, e.g., constraints on the UAV kinematics such as acceleration.
In addition to the SR,energy consumption is an important issue that needs to be specifically addressed in UAV communications,since the on-board energy budget is usually limited.For this consideration, secrecy energy efficiency(SEE)has been considered.It is defined as the ratio between the amount of secret bits that are successfully transmitted and the total energy consumption used to support such transmission,
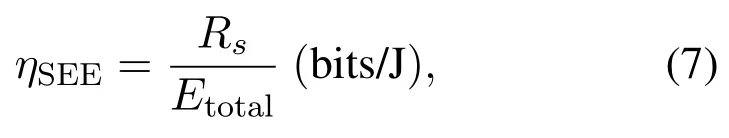
whereEtotalrepresents the total energy consumed by the UAV,which may include not only the communication energy, but also the energy consumed for hovering.It is usually assumed that the communication energy consumption is much less than the propulsion energy of UAV.In this case,Etotalin(7)solely depends on the UAV mobility parameters such as velocity and acceleration, while it is irrelative with the communication power consumption P[n][74,75].However,in the case that the trajectory is pre-fixed and cannot be controlled by the communication provider,the propulsion energy is excluded from the total energy[76].
Note that the problems (5) and (7) are in general non-convex.The widely-adopted methods to solve such problems are described later inSubsection 4.1.
When explicit CSI is not available but its distribution is known,secrecy outage probability(SOP)is another commonly adopted metric, which measures the probability that the SR drops below a pre-determined threshold.In UAV communications, SOP is considered when the system designer knows the locations of all nodes but cannot know their instantaneous fading,or when the designer cannot know the explicit locations but only knows the location distribution.Denote SOP asPoutand it can be expressed as
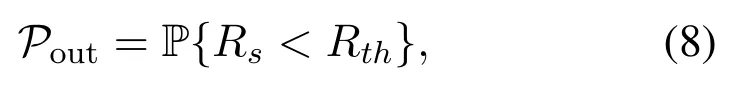
whereRsis the achievable SR defined in(4),andRthis the target SR threshold.In the literature, SOP is mostly considered for performance analysis with fixed UAV position or trajectory.When used as the objective for optimization, the corresponding variables to be optimized are usually low-dimensional,such as the one-shot UAV position or power allocation.Compared to the former problems (5) and (7), the complexity is much reduced.
Some variant forms of the outage probability has been discussed, e.g., the hybrid outage probability(HOP)which jointly considers the outage occurred in the main link and the outage induced by eavesdropping[54],the intercept probability(IP)which describes the probability that the SNR of the legitimate link is less than that of the eavesdropping link [41], and the secrecy connection probability (SCP) which describes the probability of non-zero secrecy capacity [60].In practice,outage analysis is usually followed by artificial noise(AN)-aided jamming design,which has been shown to be a practical solution for secure transmission when explicit CSI is unknown.As previously discussed,this constitutes an important research direction in the field of UAV-PLS,as explicit CSI acquisition in UAV communications is always challenging.
2.3.2 UAV as Helper
The UAV may act as helper to aid the secure communication between other communication nodes.When acting as a relay,the design objective basically has no much difference-the SR(4), ASR(5), SEE(7), and SOP(8)are still widely used as performance metrics.When UAV acts as a friendly jammer, new performance metrics appear for practical scenarios that the location information of Eve is unknown.In this case,the designer may try to reduce the outage probability in a suspicious target area.The union of all locations where jamming can be beneficial, that is, jamming helps to reduce the outage probability, is defined as jamming coverage[77].In practice,the design objective could be maximizing the jamming coverage area[45].Similarly,an intercept security area was defined as the union of locations where Eve’s signal to noise and interference ratio(SINR)is smaller than a threshold.Maximizing this area has been considered in[78].For a friendly jammer who cannot know Eve’s location information, these area-based performance metrics provide practical and effective design objectives.
2.3.3 UAV as Attacker
It is important to consider malicious UAVs,since their flexible deployment and mobility will render the attacking more powerful and harmful.Besides, the attacker may benefit from the high probability of LoS propagation.In most cases, the previously described secure performance metrics are still interested.Differently, now the impacts of new parameters such as the altitude of the UAV attacker, are specifically emphasized in the analysis.For example,the secrecy performance has been compared for two cases(Eve is on the ground or in the air) in [79], and the impact of UAV height on the SOP has been investigated in[80].
New constraints, objectives, or design framework also arise.For example,when a UAV transmits directionally to cover a disk area on the ground, the highrisk region for eavesdropping can be described as a cone below the transmitter.To guarantee PLS,3D constraint on Eve’s location should be considered for the case of UAV Eve.More specifically,the design should avoid any Eve appearing in this cone region below the legitimate transmitter [81].Moreover, considering a smart UAV attacker,its power,position,or moving trajectory could be dynamically adjusted to maximize its attacking efficiency.In this case,game-theoretical approaches are usually applied in the analysis and secure transmission design,see e.g.,[82-84].
2.3.4 Covert Communications and Wireless Surveillance
As an important branch in the studies of PLS, covert communications aim to hide legitimate transmission from detecting, while surveillance aims to identify the existing of unauthorized or malicious transmitters.The use of UAV brings opportunities and challenges for both: High probability of LoS channel links is beneficial for legitimate surveillance,while it becomes more challenging for a transmitter to hide itself.
Hypothesis testing is usually conducted for this scenario.With a certain detection rate guaranteed, the false alarm rate and miss detection rate are commonly adopted performance metrics.These are respectively defined as follows,
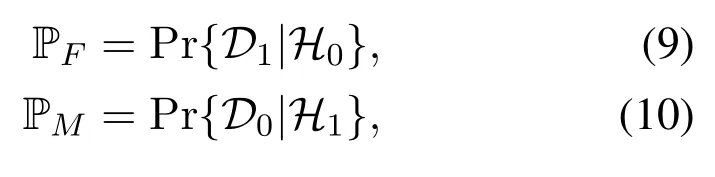
whereDandHdenote the decision and hypothesis,respectively, with the subscripts 0 (or 1) representing there does not exist (or exists) an unauthorized transmission.A common design objective is to determine an optimal detection threshold, which minimizes the overall detection error rate.When UAV is involved,the position or trajectory of UAV can be further optimized for this purpose[73,85-87].
III.PLS WITH STATIC UAV DEPLOYMENT
In this section, we review the existing literature on PLS with static UAV deployment.We first introduce the commonly adopted methodologies in this area,then describe the related works under two distinct research frameworks: 1)UAV will be deployed at fixed positions, which might be further optimized, and 2)the positions of UAVs(and/or other nodes)are considered to be random following certain spatial stochastic process,e.g.,PPP.In the latter case,the long-term performance evaluated over the possible location distribution of the involved nodes,as well as the impact of key distribution parameters(such as the node density)on PLS,are of particular interest.
3.1 Methodology
3.1.1 Common Analysis and Optimization Framework
As previously discussed, static UAV deployment has been widely considered for scenarios such as coverage enhancing for the cell edge and temporary hotspot areas.Basically,this scenario does not have much difference as compared to the conventional terrestrial communications,except for the following aspects:
· Unique A2G/A2A channels lead to new performance analysis results.A notable observation is that the performance may highly rely on the elevation angle of the propagation link, which may affect the LoS probability, the PL exponent, the RicianK-factor, etc., and subsequently result in different secrecy performance.
· UAVs can be flexibly deployed in 3D space.This introduces a new dimension that can be exploited.The 3D position optimization problem is in general non-convex,however,via proper transformation and approximation techniques, the original problem usually can be re-formulated as solvable problems.For example, in [88, 89], the 3D position optimization problem was formulated as quadratically constrained quadratic fractional programming (QCQFP), which was transformed into quadratically constrained quadratic programming(QCQP),and further approximated then solved with semi-definite relaxation(SDR).
· A UAV attacker could be more harmful.Specifically, in addition to conventional actions that a smart attacker can do,such as dynamic power adjustment and attacking strategy selection, a UAV attacker can further dynamically change its position for more effective attacking.For this scenario, game theory is usually applied to analyze the secrecy performance under smart attacks.For a survey of the game theoretic approaches in UAV systems,the readers are referred to[90].
3.1.2 Stochastic Geometry
The other research direction focuses on random network with randomly distributed nodes, and aim to evaluate the average secrecy performance.For this direction, conventional stochastic geometry theory provides a powerful tool.With the widely-adopted PPP model,the number of nodes within an interested area,as well as the inter-node distances,can be conveniently described by their distribution functions.Accordingly,the PLS performance can be evaluated in a stochastic manner,e.g.,in terms of outage probability,or SR averaged over spatially random locations.For modelling the UAVs’ positions, the distribution model might be further extended to 3D.Besides, new models are applied to account for the minimum inter-UAV distance requirement,such as the MHC point process.
3.2 Fixed UAV Position
For clear exposition, we summarize the PLS works with fixed UAV positions according to the roles of UAV(as previously described inSubsection 2.3).
3.2.1 UAV Transmitter/Receiver
We start from the works where UAV acts as transmitter or receiver.In [88], a basic three-node system model was considered, where a UAV BS transmits to a ground legitimate receiver(Bob),in the presence of a ground Eve.It was assumed that the position of all nodes are known,whereas the instantaneous fading channels are not.Therefore, non-zero secrecy capacity probability, i.e., the SCP described inSubsection 2.3, was considered as the performance metric.The 3D position of UAV BS was optimized with a two-step approach, which first optimizes the UAV altitude and then the horizontal position.The same design objective and optimization problem has been considered in[89],while with an extra practical constraint of obstacle avoidance.Multiple obstacles on the ground were modelled as semiellipsoids,and the deployment position of UAV should maintain a minimum distance to these obstacles in the optimization.UAV receiver was considered in[54,55], where a multi-antenna ground source transmits to a single-antenna UAV,in the presence of a multi-antenna ground Eve.Jamming is performed at both the source and full-duplex (FD) Eve.HOP was analyzed,and the optimal configurations of both the source and Eve were discussed according to the UAV altitude.It has been shown that there exists optimal UAV altitude that maximizes the secrecy performance(see figure 3).The reason mainly stems from the trade-off between the altitude-dependent path loss and LoS probability,as has been discussed inSubsection 2.2.1.
When multiple antennas are implemented, spatial dimension can be exploited and there will be more to be designed aside of the UAV position.For example,spatial multiplexing techniques can be adopted to serve more users on the same time-frequency resource,beamforming can be utilized to concentrate the signal power to a target user while reducing information leakage,and AN can be sent in the null space of legitimate channel links to degrade the Eve’s link quality.In[91],a multi-antenna UAV BS was used to serve multiple ground users with non-orthogonal multiple access(NOMA) and simultaneous wireless information and power transfer(SWIPT).Thanks to the antenna array implemented at the UAV,AN can be generated to jam the ground Eve simultaneously with legitimate information transmission.The sum rate of all users are maximized to find the optimal precoding and AN jamming vectors, as well as the SWIFT parameters such as the power splitting ratio.
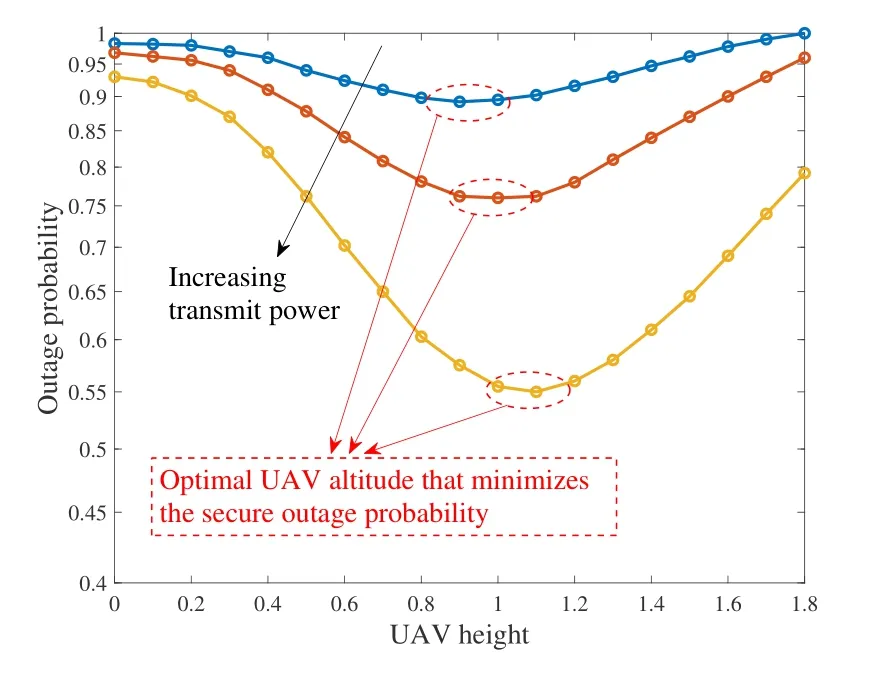
Figure 3.There exists optimal UAV altitude that maximizes the secrecy performance(reproduced from[54,fgure 4]).
For a multi-antenna UAV, UAV jitter becomes an important issue.Even when the position of the communication nodes can be known, the random jitter,which cannot be precisely predicted,may cause uncertainty in the knowledge of the LoS channel direction.Specifically, jitter will cause random variations in the azimuth and elevation angles of the LoS link, which will subsequently degrade the system performance.Fortunately, the maximum angle variation range can be guaranteed.According to this information,a robust design takes the worst-case performance into consideration.For example, the most harmful jitter angle is assumed for the legitimate node, and the most beneficial jitter angle is assumed for attackers.Together,these assumptions were used to evaluated the worstcase secrecy performance, and further adopted as design objective or performance requirement in[42,92].In general,the uncertainty caused by random jitter increases the transmit power required for secure communication.This is shown by the example in figure 4.
3.2.2 UAV Relay/Jammer
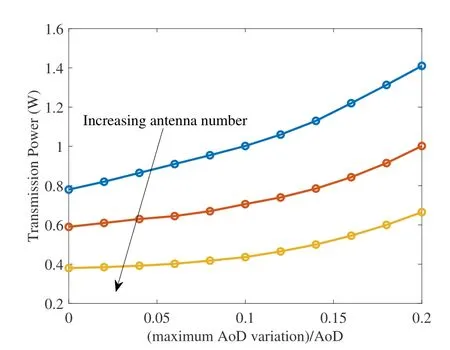
Figure 4.UAV jitter increases the transmit power required for secure communication(reproduced from[42,fgure 2(a)]).
The UAV may work as helper to aid the secure communications between legitimate nodes.i.e.,as relay or friendly jammer.In this case,the position of UAV and the relaying/jamming strategy should be jointly considered.For UAV relaying, a basic four-node model was discussed in [41], where a decode-and-forward(DF) UAV relay is deployed to aid the communication between a ground BS and Bob,in the presence of a ground Eve.Analytical expressions of the intercept probability and ESR were derived, and accordingly,the impact of the UAV altitude/power on the secrecy performance was discussed via numerical simulations.
Considering that the UAV helper is energyconstrained, efforts have been devoted to the area of SWIPT to allow the UAV harvest energy from information or jamming signals.In [58], a UAV relay receives energy from information-bearing signal sent by the ground source, as well as jamming signal sent by a FD destination.A more complex scenario has been considered in [93], where the UAV relay and legitimate receiver are both FD devices, thereby they can transmit and simultaneously perform jamming against multiple Eves on the ground.Robust design was conducted considering uncertainty in the Eves’ location information, and the position of UAV, together with jamming and SWIPT protocols, are jointly optimized to maximize the worst-case SR.
More effective relaying can be realized with multiple antennas implemented at the UAV, or when there exist multiple UAVs cooperatively aiding the transmission.With a multi-antenna UAV relay,a common design objective is to jointly optimize the information and AN precoders [94], similar to the previous case that UAV acts as a multi-antenna BS[91].When multiple UAV helpers are involved in the transmission,secrecy problem may arise from the inside-that is,UAV could be untrustworthy.The consideration is practical,since it is in general challenging to monitor the behaviour of every individual UAV in a swarm.For such a scenario,AF protocol should be applied,and the design involves intended jamming and relay selection,with which SOP and ESR have been analyzed in[95].In [96], the problem has been investigated from the attacker’s perspective.Considering a multi-hop transmission assisted by multiple UAV relays, the optimal jammer’s location, which is most harmful to the legitimate transmission, was analyzed.The work has opened up a new thinking direction-knowing the location which is most vulnerable to attacking can help the system designer make better prevention.
Aside of acting as relay,the UAV can be deployed as friendly jammer to improve the secrecy performance of legitimate communications.Mobility of the UAV can be exploited for efficient jamming.Clearly,if the location of Eve is known,it is better to place the UAV jammer as close as possible to Eve.Although it has been widely assumed that the Eve’s location can be detected by UAV via,e.g.,optical camera onboard[97],considering unknown/imperfect location information of Eve is of practical importance.In [45], a basic four-node system model, i.e., including one source,one destination, one Eve and one UAV jammer, was considered.Without knowing Eve’s location,the jamming coverage was defined as the area within which jamming can be beneficial to reduce the SOP,and the design aims to maximize the jamming coverage area by optimizing the UAV jammer’s position.A similar system model was considered in [78], where also an area-based metric, namely the intercept probability security region (IPSR) which describes the union of all positive security regions, has been used as the design objective to be maximized.For the example in figure 5, if Eve is located in the regions marked blue,it can be guaranteed that the interception probability is lower than a predefined threshold.Therefore, the design objective is to find the best jammer position that maximizes the blue area.The discussion on UAV friendly jamming was further extended to the classic multiple-input single-output multiple-Eve(MISOME)scenario in[56].With multiple antennas implemented at the friendly jammer, null space beamforming can be conducted while avoiding interference to the legitimate links.Optimization of the jamming power and UAV position have been investigated to maximize the transmission rate,constrained on the SOP requirement.
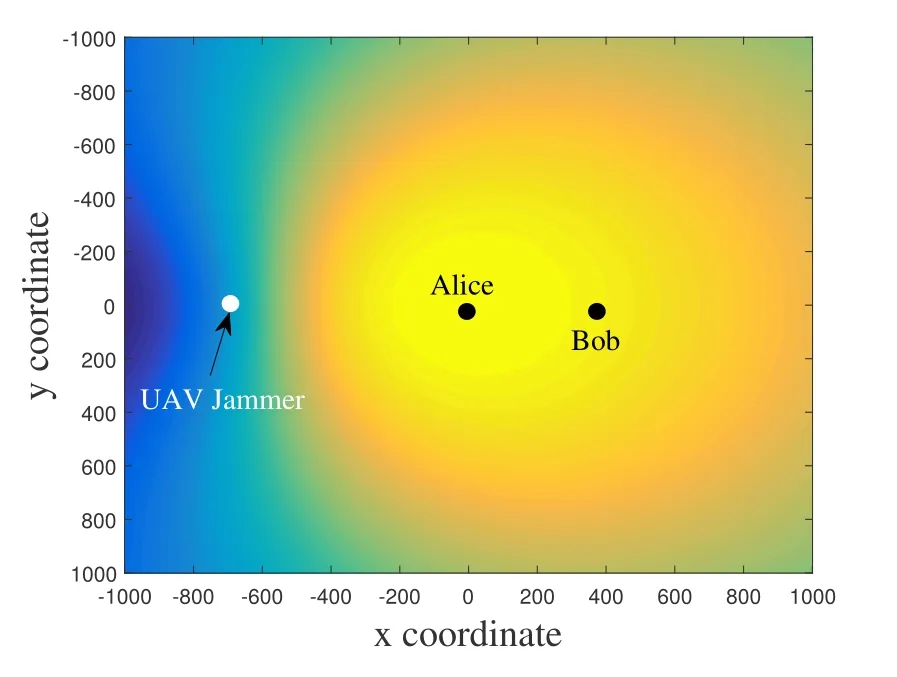
Figure 5.When the transmitter cannot know any information of Eve,the position of friendly UAV jammer can be optimized to maximize the area of a secured region(reproduced from[78,fgure 3]).
3.2.3 UAV Attacker/Suspicious UAV
Compared to ground attackers, a UAV attacker benefits from flexible and agile deployment,as well as better channel conditions.In[79],flying and ground Eves were compared,trying to overhear the communication between a UAV Tx and a ground Bob.Considering various channel fading characteristics, SOP and ESR have been investigated.Accordingly,it was shown that flying Eve in general could be more harmful.
When the UAV attacker is smarter, i.e., it can dynamically adjust its attacking strategy, gametheoretical approaches are usually applied.In [83],the UAV attacker may select from four action modes,namely eavesdropping,jamming,spoofing,or keeping silent, according to the transmission strategy adopted by Alice.On the other hand,to combat with the UAV attacker, Alice dynamically determines its transmission power.Game-theoretical analysis has been applied in a UAV network [98], where the Tx/Rx and attacker (jammer) are all UAVs.Taking into account the mutual-interference in multi-pair UAV communications, the legitimate Tx’s and the jammer dynamically adjust their transmit power to maximize their utilities, respectively, where the process is formed as a Stackelberg game.Also for a UAV network,cooperative relaying was investigated in[99],where the user association was formulated as a many-to-one matching game, and cooperative transmission was formulated as an overlapping coalition formation game,considering both selfish users and malicious UAV Eves.
In some cases,UAV is regarded as suspicious communication node,and the design is conducted from the eavesdropper’s (legitimate monitor) perspective.Related works are termed as legitimate eavesdropping[100]or proactive eavesdropping[101,102].In[100],a legitimate monitor aims to wiretap on the communication between a pair of suspicious Tx and Rx(aided by a suspicious UAV relay).The monitor performs jamming to guarantee that it has higher receive SNR than the suspicious Rx, therefore the suspicious messages are decodable at the monitor.However,the UAV relay can dynamically adjust its position to alleviate the impact of jamming.A similar scenario was investigated in[101],wherein the suspicious communication is between a UAV Tx and multiple ground receivers.In this case,the UAV dynamically adjusts its position given a certain jamming environment,to maximize the minimum achievable rate among all receivers,and the monitor accordingly optimizes its jamming power to maximize the eavesdropping rate.
3.2.4 Covert Communications and Wireless Surveillance
Covert communications and wireless surveillance have been widely investigated for UAV systems.In the concept of covert communications,UAV aims to hide its transmission from a malicious detector; while for wireless surveillance, UAV is adopted to monitor (or conduct legitimate eavesdropping on) the suspicious communications occurred in the environment.
For covert UAV communications, the LoS/NLoS condition of the detecting link plays an important role in the analysis.A basic three-node system model has been considered in [103], where a UAV Tx wants to hide its transmission from a ground warden (Willie),which locates right below the UAV.The probabilistic LoS/NLoS model is elevation angle-dependent,hence the link from UAV to Willie is always LoS,while the transmission to the legitimate receiver, Bob, has LoS or NLoS conditions depending on the UAV altitude.Hypothesis testing is conducted at Willie,and the UAV Tx optimizes its altitude and power, aiming to maximize the SNR at Bob while guaranteeing the detection probability below a certain threshold.The work has been further extended in [104] where 2D UAV position was optimized.Investigation has been conducted from Willie’s perspective in[105],where a more powerful Willie implemented with multiple antennas tries to identify the existence of UAV communications using beam sweeping.The optimal number of sweeping sectors was discussed based on closed-form expressions of the detection error probability.
For UAV-aided wireless surveillance,existing works are mainly conducted from the perspective of legitimate eavesdropping.That is, the UAV monitor aims to decode the suspicious message,instead of only detecting its existence.A basic three-node model was considered in [106], where a UAV monitor wants to decode the message sent by a suspicious Tx, in the meanwhile, it performs jamming to the suspicious Rx.This is similar to the proactive eavesdropping works described previously; however, with UAV being the legitimate monitor, its position can be flexibly adjusted to maximize the surveillance performance[106].Analysis of UAV surveillance has been extended to a four-node scenario[107],where the suspicious communication between source and destination is aided by a suspicious relay.It is also considered for a UAV network in [108], where the legitimate monitor,the suspicious communication nodes are all UAVs.From an opposite perspective,techniques against UAV surveillance have been discussed in[109].
For the reader’s convenience, we summarize some representative PLS works with fixed UAV positions in Table 1 and Table 2,2where the concerned scenarios,the roles of UAV and malicious nodes,as well as their position assumptions, the channel characteristics, the secrecy-related metrics, and the design objectives are highlighted, respectively.This may help the reader quickly identify the latest progress in his/her interested research direction.
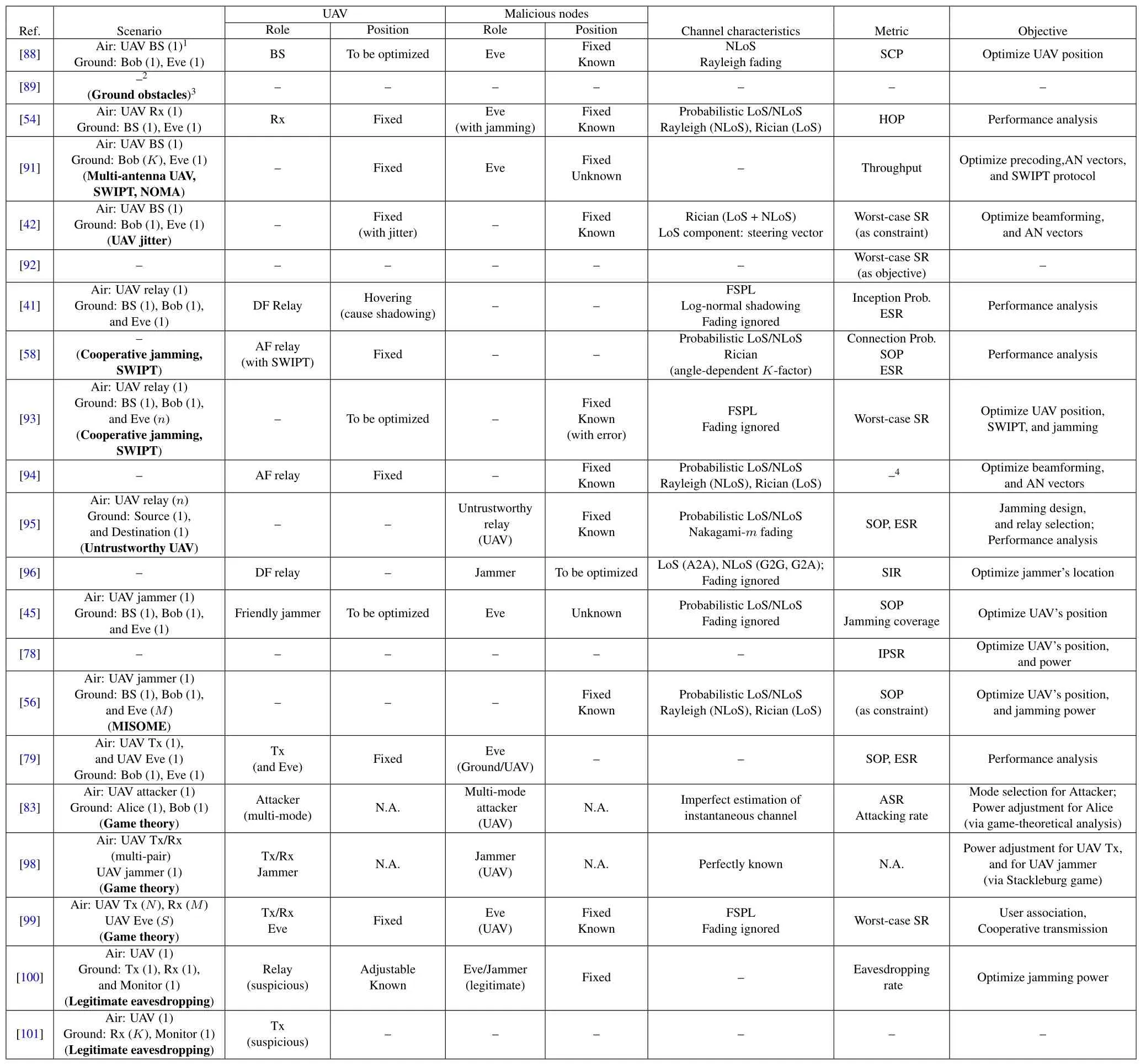
Table 1.UAV-PLS works with fxed UAV position part I.
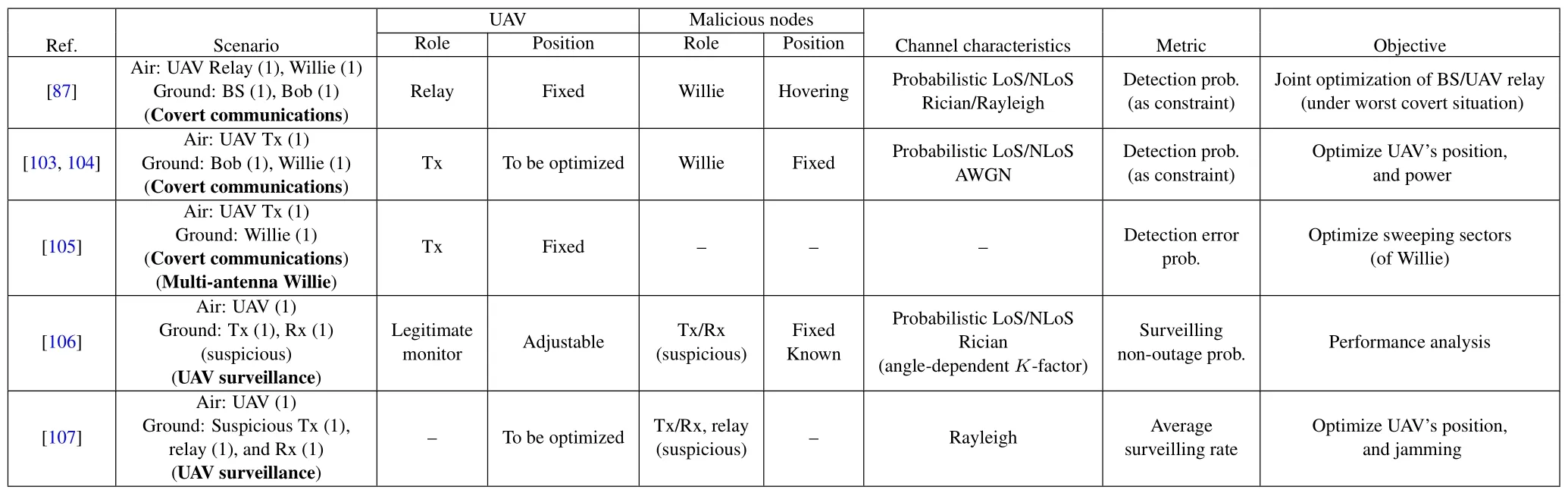
Table 2.UAV-PLS works with fxed UAV position part II.
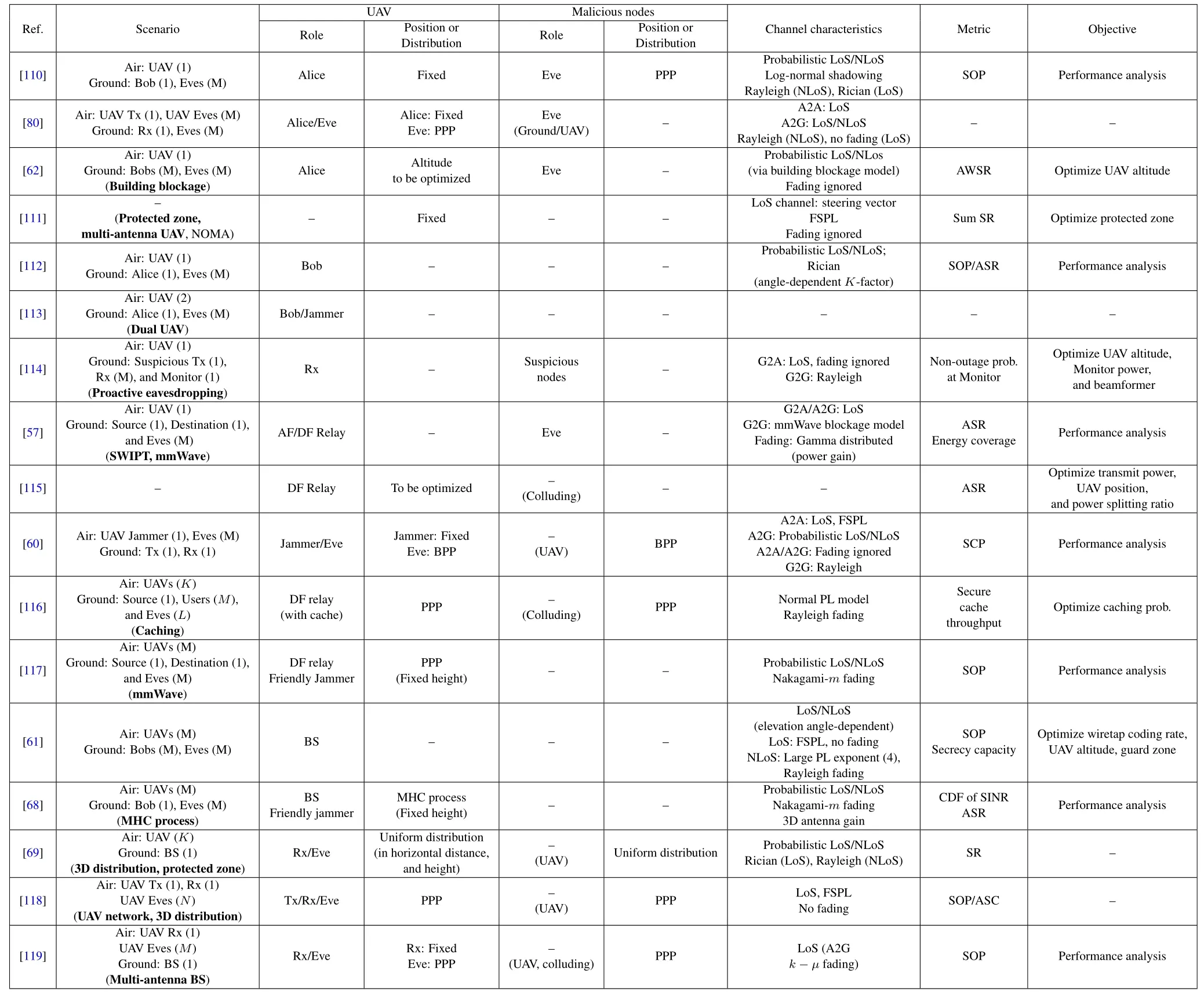
Table 3.UAV-PLS analysis via stochastic geometry.
3.3 Random Positions Via Stochastic Geometry
Stochastic geometry provides a powerful tool for performance analysis in random networks.In this case,the system performance is evaluated in a spatially large-scale manner, e.g., averaged over space.As far as UAV-PLS is concerned, stochastic point processes have been assumed for Eves, legitimate communication nodes,or UAVs in a swarm.We review the related approaches in this subsection.According to the different analysis frameworks adopted, we structure this subsection into two parts.Namely, 1) UAV has fixed position while the other nodes are randomly located,and 2) multiple UAVs in a swarm are randomly distributed in space.Similar to previous discussion, different roles of UAV have been assumed.This will be emphasized when necessary.
3.3.1 Random Network with Fixed UAV Position
For this research direction,UAV is deployed in a random network, where the positions of legitimate communication nodes and/or attackers are randomly distributed.The position of UAV,however,is considered to be fixed or to be optimized,according to stochastic geometry-based secrecy performance analysis.
When UAV acts as legitimate Tx, the classic threenode wiretap channel model has been extended to multiple-Eve scenario in [110], where the Eves are randomly located on ground following PPP.SOP was analyzed and the impacts of system parameters such as the UAV altitude and Eves’ density have been discussed.In addition to ground Eves, multiple UAV Eves were considered in[80].While the ground Eves are randomly distributed within a circle on ground,UAV Eves are randomly distributed within a sphere in 3D space.Multiple Bobs,multiple Eves,and multiple buildings in an urban scenario have been considered in [62].The locations of ground buildings are also modelled by PPP with their height following Rayleigh distribution.With this building-blockage model, LoS probability was evaluated, the average worst-case SR(AWSR)was analyzed,and the UAV altitude has been optimized accordingly.A multi-antenna UAV BS was considered in [111], which performs 3D beamforming to serve randomly distributed ground users with NOMA,in the presence of randomly distributed ground Eves.A novel idea of “protected zone” was proposed,which is defined as an area around the user that has been cleared from Eves.Aiming to maximize the sum SR, the optimal shape of the protected zone has been discussed.
Analysis has been extended for other roles of UAV,e.g., receiver [112-114], relay [57, 115], or jammer[60].Among these works,the general methodologies adopted are similar,i.e.,describing the inter-node distance distribution according to their location distribution,and further relating the distance to secrecy performance metrics.However,there may exist slight difference.For example,the UAV altitude would affect the stochastic properties of both legitimate and eavesdropping links when UAV is a transmitter, while it only affects the legitimate link when UAV acts as receiver.
3.3.2 Random UAV Positions
When multiple randomly located UAVs are concerned,the modelling of their position distribution shows some difference as compared to the modelling for ground nodes.First, UAVs may be distributed in 3D space; moreover, to avoid UAV collision, minimumdistance between UAVs needs to be guaranteed for practical consideration.
As a commonly adopted simplified scenario, all UAVs can be assumed to distribute within a disk area at certain height.In this case,2D point processes still can be applied.In[60],binomial point process(BPP)has been assumed to modelNrandomly distributed UAV Eves within a disk above the ground Tx.PPP has been used to model the location distribution of multiple UAV relays/jammers[116,117],in which the number of UAVs in an interested area is random rather than being fixed.An alternative method is to relate the UAV positions to the positions of ground nodes.In[61], multiple ground Rx’s are randomly distributed following PPP,each associated with a UAV Tx located right above its position.Further taking into account the constraint on inter-UAV distance,MHC point process was used to model the distribution of UAV BSs in[68],which can be viewed as a dependent thinning process of a standard PPP, with the thinning probability determined by the minimum distance requirement.Therefore, the average number of nodes in an interested area,as well as the inter-node distance distribution can be conveniently deduced using standard methodologies in stochastic geometry,and the secrecy performance can be correspondingly analyzed.
For 3D UAV distribution,different approaches have been used to describe the random UAV positions.In[69],the 3D position distribution of multiple UAV receivers was described in two dimensions: The horizontal distance to the ground BS and the UAV altitude.Both was assumed to be uniformly distributed within a certain range.This approach,albeit being simple and straightforward,does not provide tractable and concise analytical results.Therefore,secrecy performance was discussed in [69] mainly based on simulations.Extending PPP to 3D,the secrecy performance of an all-UAV network has been investigated in [118].It was assumed that multiple UAV Eves are randomly distributed within a 3D sphere area centered at the UAV transmitter.The number of Eves within the critical range as well as their distances to the transmitter can be conveniently described,and subsequently,SOP was analyzed for the considered network.
At the end of this subsection, it should be highlighted that in the works where random node distribution is considered, defining an area, where Eves cannot be located in, is another important and practical research direction.Such an area was termed as protected zone in [111], and termed as secrecy guard zone in[69,61].Details of these stochastic geometryrelated works are summarized in Table 3,3and the typical random UAV distribution models are illustrated in figure 6.
3.4 Summary of This Section
We summarize what we have learnt by now.
· There are two major categories for the PLS works with static UAV deployment: The communication nodes have fixed positions, or they are randomly distributed.For both cases, it in general has similar research methodologies as that have been adopted for terrestrial communications,e.g.,SR/SOP analysis and optimization techniques,or stochastic geometry-based analysis frameworks.Nevertheless, involving UAV nodes in the network would lead to difference for both.
· A common and important difference may stem from the unique characteristics of the A2G channel, which is usually considered to be elevationangle dependent.The elevation angle of a propagation link not only affects its LoS probability,but also has impact on the fading parameters such as the path loss exponent, the RicianK-factor,etc.These will subsequently affect the PLS performance when UAV is involved in the communications, as either legitimate or malicious node.Besides,the UAV itself may have direct impact on the propagation channel.For example,UAV hovering may cause shadowing to the channel, and UAV jitter may result in uncertainty in the channel conditions.These effects should be taken into account for robust PLS design.
· For the works focusing on fixed node positions,3D UAV position optimization is of particular interest.The corresponding problem is usually nonconvex,however,it has been shown that the problem can be effectively solved with standard transformation and relaxing techniques.
· Considering random node position distribution,conventional stochastic geometry-based analysis framework can be applied.As a reasonable simplification, it has been widely assumed that multiple UAVs may be distributed at the same height,therefore 2D PPP(or BPP)can be used to model their position distribution.This model can be extended to 3D,and extended to more practical scenarios incorporating the inter-UAV distance constraint via,e.g.,the MHC point process.
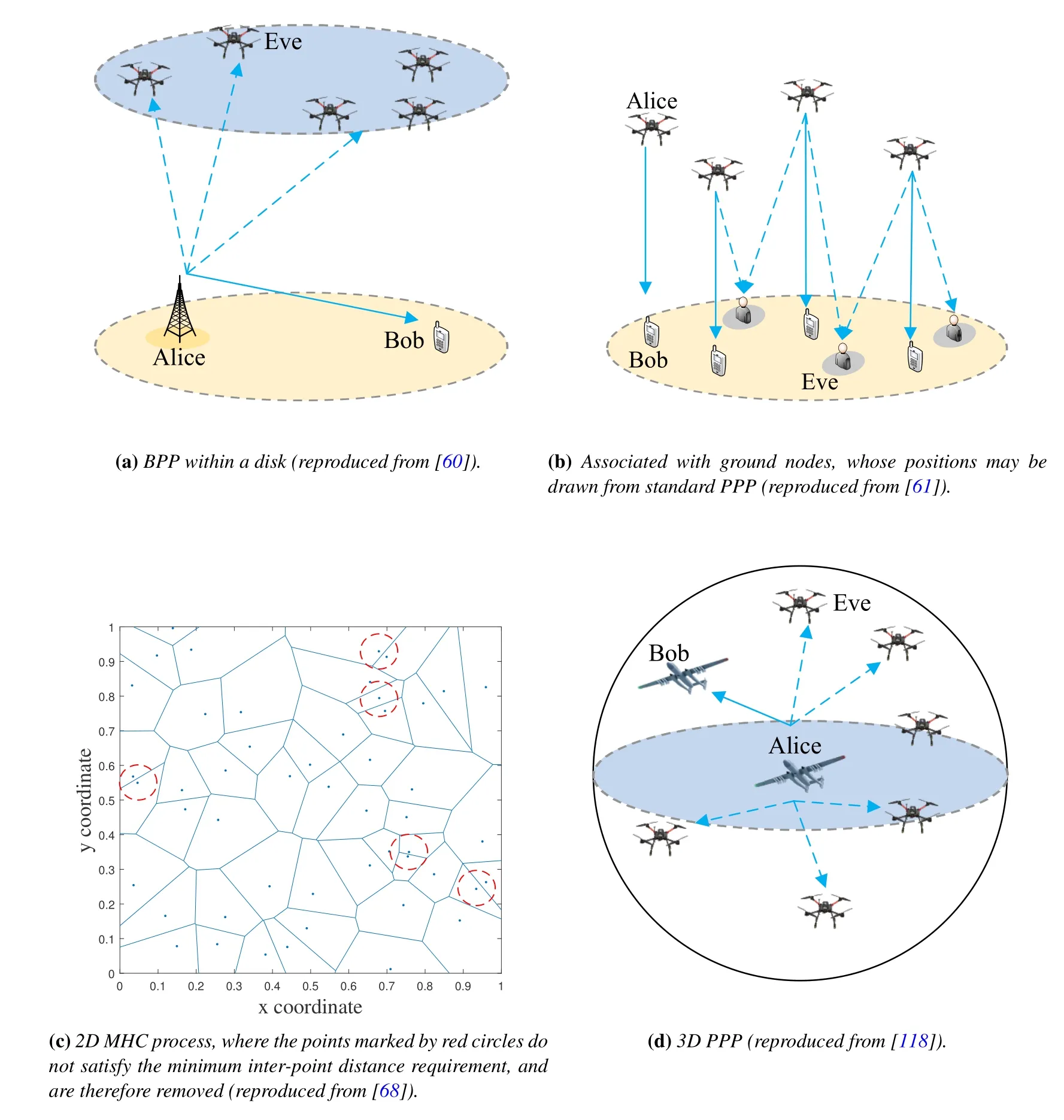
Figure 6.Typical examples for modelling the random UAV distribution.
· The analysis framework may be different when UAV plays different roles.As far as PLS is concerned, the key point is: Which link (legitimate link or attacking link)will be affected by the A2G channel, or which link has UAV involved and is therefore adjustable.Specifically,when UAV acts as a malicious attacker, it may smartly adjust its position for most efficient attacking.For this case,game theoretical approaches can be applied.
IV.PLS WITH MOBILE UAV DEPLOYMENT
In this section, we focus on the second research direction, where the UAVs are moving to provide ondemand service to multiple spatially distinct users(or moving users), other than being statically deployed.Related works are also classified into two major categories: 1) The UAV trajectory is not a design objective.It is either implicitly reflected in the analysis,or pre-determined as fixed conditions.2) Trajectory planning,which is actually one of the most important research directions in UAV communication.Following a similar structure of the previous section,we first introduce the common methodologies adopted for this research area.After that,existing literature will be reviewed in detail.
4.1 Methodology
4.1.1 Communication Process-Oriented Optimization Different from the static case, UAV communications with mobile deployment often form a temporal communication process corresponding to the flying period,and hence, one should account for the whole process for optimization.For the ease of analysis, this communication process is usually discretized into a series of states, and CSI prediction methods are necessary for such process-oriented optimization.Fortunately,the large-scale channel fading usually dominates the A2G channel,which is location-dependent and can be predicted for a given UAV trajectory.As for the performance metric,conventional secrecy metrics are still adopted, while they now need to be averaged over all the communication states during the flight.
4.1.2 Trajectory Optimization under Kinematics and Energy Constraints
For the process-oriented design, trajectory optimization would significantly affect the secrecy performance.Intuitively, the trajectories of UAVs directly affects the channel conditions of both the legitimate and eavesdropping links,rendering it an efficient new dimension for PLS enhancement.In practice,the trajectory is a function of continuous time, which leads to infinite variables and makes the optimization problem intractable.Most works divide the fly duration into many discrete time slots, and optimize the UAV position at each time slot rather than the continuous trajectory (as has been explained inSubsection 2.1).The trajectory optimization problem is usually nonconvex,some optimization methods such as the block coordinate descent (BCD) and successive convex approximation(SCA)methods are often adopted.
In practice,UAV kinematics usually restricts the trajectory design.Particularly, both the velocity and acceleration cannot be arbitrarily set, whereas these parameters have their practical(physical)limits,respectively.These constraints will make the UAV positions in adjacent time slots correlated,complicating the optimization.Another practical constraint is the total energy of UAVs for both flying and communications.Considering the energy efficiency issue,the trajectory that is optimal for PLS enhancement might requires more propulsion energy consumption.Possible tradeoff should be exploited to strike the balance between performance and energy consumption.
4.2 Trajectory As Implicit or Fixed Conditions
4.2.1 Implicit Trajectory
In some cases, UAV moving is implicitly reflected in the analysis.Typical impacts include: 1) UAV moving may affect the CSI acquisition.This is usually reflected by time-correlated channel model[120],or unknown instantaneous CSI [82].2) UAV moving may affect the link reliability,which has been modelled as a Bernoulli process in [46, 121].3) When the UAV is not controlled by the system designer,mobility may cause random variation(constrained by its kinetic parameters,e.g.,speed and acceleration rate)in the UAV locations.This is usually described by a random mobility model in the analysis,as that in[122-124].
We respectively describe these three cases in more detail.First,UAV mobility causes auto-correlation in time-variant channels.Such a channel model has been considered in [120], where the auto-correlation coefficient,λ,is inversely proportional to the UAV speed.Legitimate eavesdropping was investigated therein for an all-UAV network from packet level, and the jamming power, as well as the adaptive modulation and coding (AMC) rate, were jointly optimized during the entire flying period to maximize the successfully eavesdropped data amount at the legitimate UAV Eve.
The fast moving of UAV may render the obtained CSI estimation being outdated, i.e., the channel aging effect [125].As stated in [125], when the UAV is not controlled by the system designer and moves randomly,the auto-correlation property in time would be time-variant, too, which is difficult to measure in practice.As a result, it is in general not easy to predict the channel conditions based on previous observations.In such scenarios,the impact of UAV moving on the propagation links,or the UAV moving itself,is usually described in a stochastic manner.
A commonly adopted model tries to relate the UAV moving to link reliability, which is the second case for implicit trajectory as previously described.In[46, 121], the reliability of UAV-related communication links was modelled as a Bernoulli process.When a link breaks down due to UAV moving, the corresponding transmission over this link fails and therefore causes outage.Specifically, with this model, a UAVaided selective relaying network was investigated in[46], where a ground control unit provides backhaul to multiple UAV Tx’s, communicating with a ground destination with the aid of multiple UAV relays,in the presence of multiple UAV Eves.Transmission over the backhual links may fail due to the moving of UAV Tx, where the failure probability is modelled with a Bernoulli process.On the other hand,all Eves are colluding to perform MRC of their eavesdropped signals;however, whether an Eve can participate in the MRC depends on its correspond eavesdropping link reliability, which is also modelled as a Bernoulli process.A similar system model was considered in [121], while the more general Nakagami-mfading was considered in the analysis.
The other way is to describe the position of a randomly moving UAV with physical mobility models.With such models,the position of a UAV is randomly updated in every slot, jointly considering the probability that the UAV stays still at the current waypoint,as well as its speed constraint in certain directions.In[122], UAV relaying was adopted to aid the communication in a hybrid satellite-terrestrial network,in the presence of a UAV Eve.The UAV positions are described with a stochastic mixed mobility model,where the vertical movement of UAV is described by a random waypoint mobility model (RWPM), which defines the probability that UAV stays at a waypoint;during the staying, a random walk model is used to describe the possible spatial excursion.With this model, the corresponding channel characteristics are described, and SOP is analyzed correspondingly.A simpler random mobility model has been considered in [123], where the propagation distance of UAVrelated links randomly varies within a range, constrained on the UAV velocity and the time slot duration.Therein, UAV acts as a friendly jammer to aid the covert communication between two ground nodes.
A random mobility model taking into account more practical constraints,i.e.,the smooth turn(ST)model,was adopted in [124, 126].Different from the previous models where the actual trajectory is not concerned,the ST mobility model generate random trajectory with practical smooth turns.With this model,secure communication between a ground Tx-Rx pair in the presence of multiple UAV Eves(with random trajectories)was investigated.This has provided a useful framework for secrecy analysis with uncontrollable or unknown UAV Eves.The ST mobility model,which is in accordance with the realistic UAV flying condition,makes the corresponding analysis being of great importance for practical designs.The implicit trajectoryrelated works are summarized in Table 4.
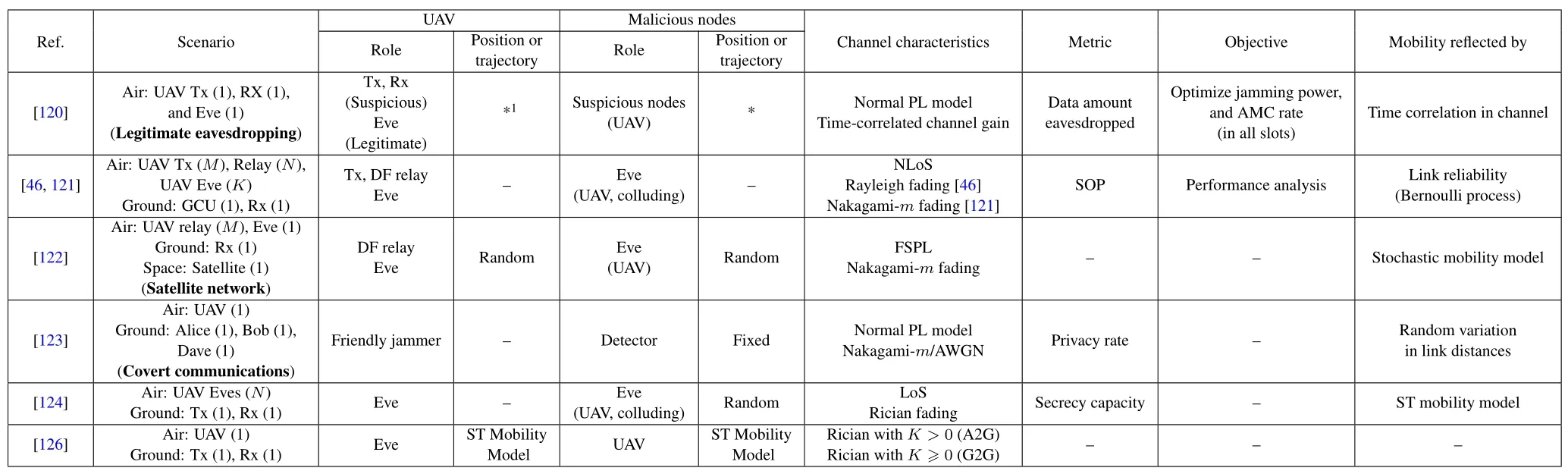
Table 4.UAV-PLS works with implicit or random trajectory.
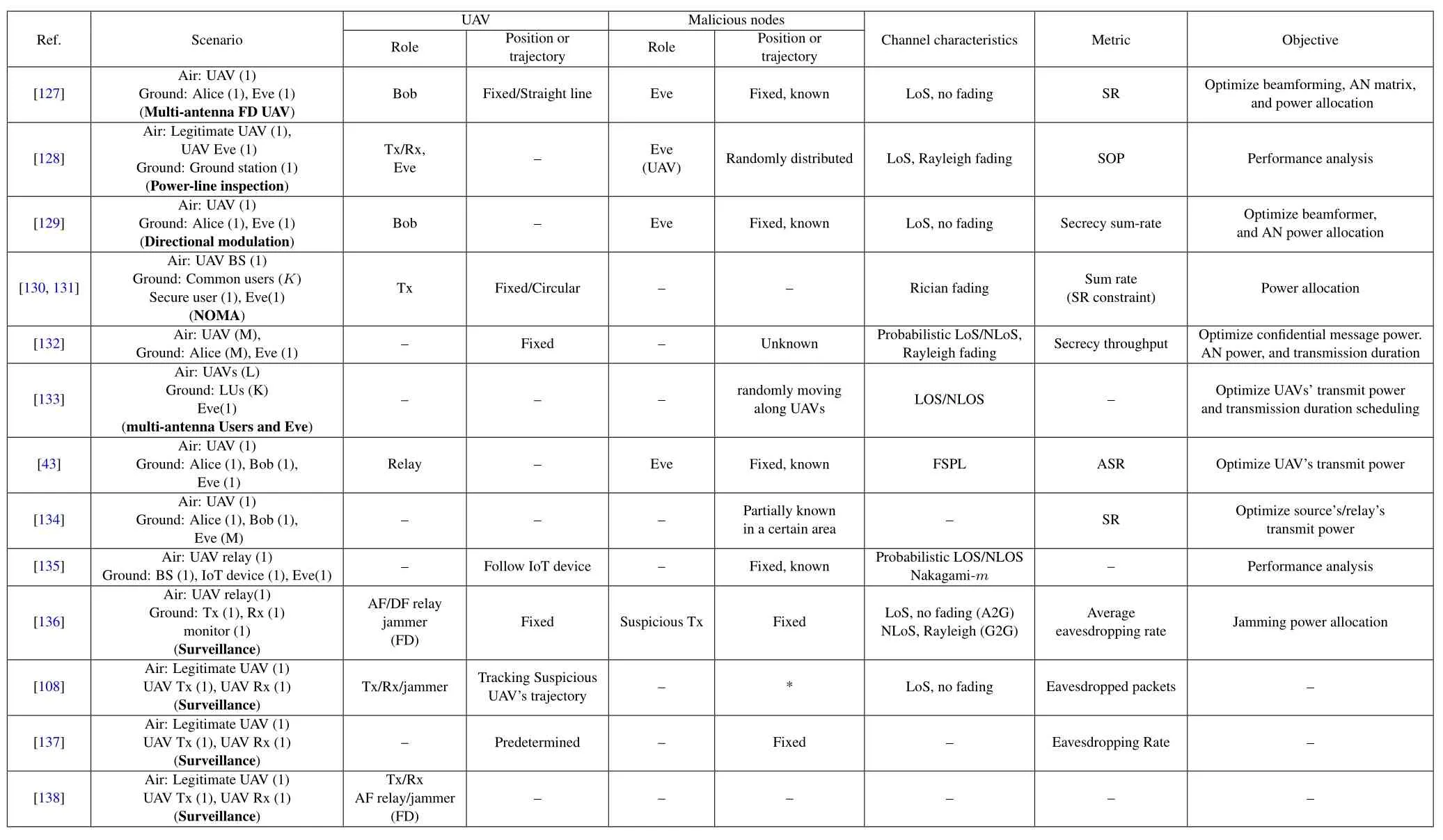
Table 5.UAV-PLS works with fxed trajectory.
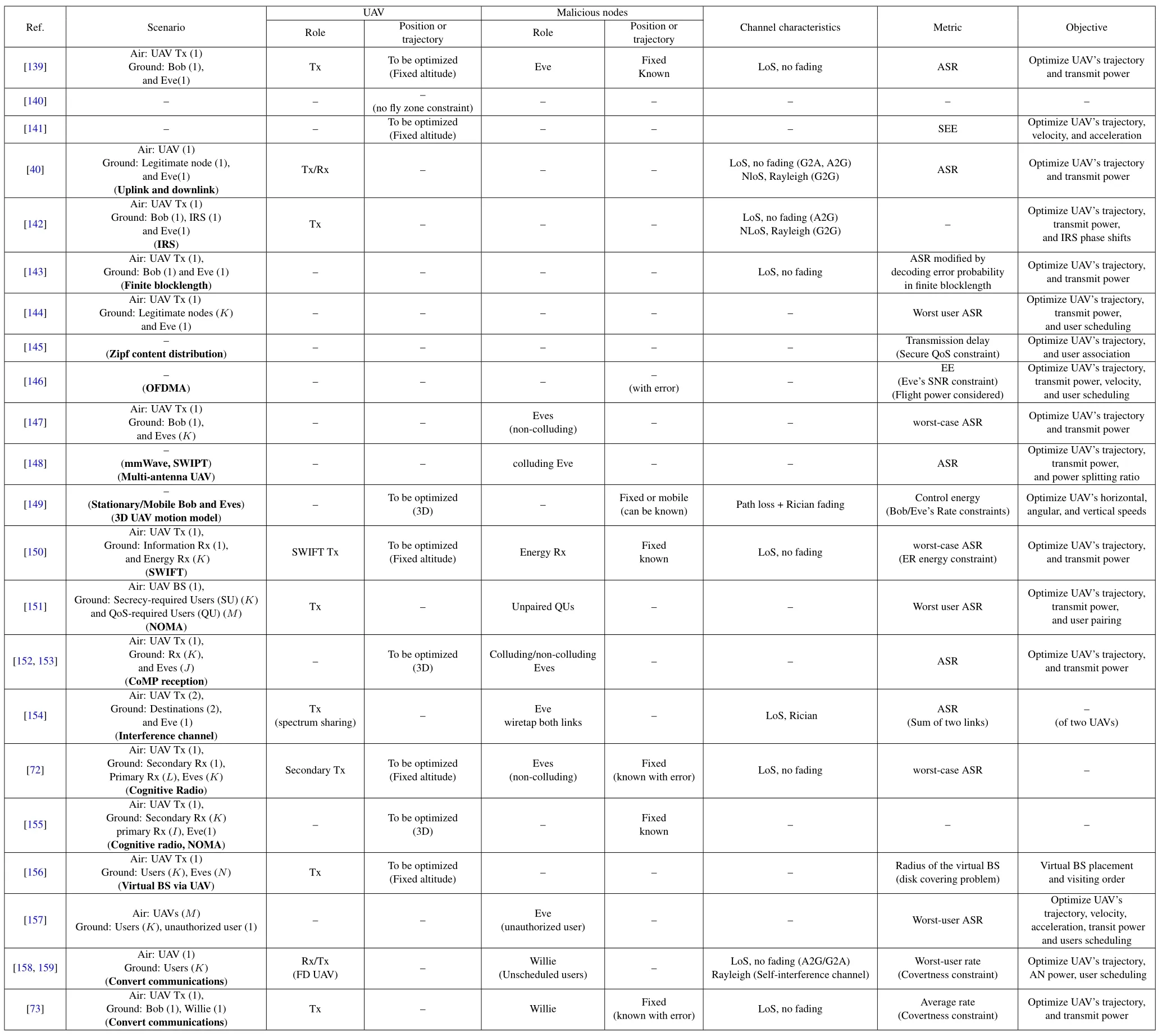
Table 6.Trajectory optimization part I:UAV as Tx/Rx.
Table 7.Trajectory optimization part II:UAV as relay,jammer,and dual-UAV case.
4.2.2 Fixed Trajectory
When the UAV trajectory is not controllable by the communication designer, it is considered as a fixed condition,under which the secrecy performance of the system mainly depends on properly-designed resource allocation.As an example,the transmission power can be adaptively increased when the UAV flies closer to the legitimate receiver, and reduced when the UAV is relatively far away from the destination.Such a trajectory-based water-filling-like approach can allocate power more efficiently for the legitimate communication,whereby it is possible to enhance the secrecy rate performance of the system.However, depending on the behaviors of the adversaries,more sophisticated transmission schemes might should be designed.
As typical application scenarios, the UAV may fly over ground facilities, e.g., highway, street, or power line, gathering sensing information and transmit it to a target receiver; or it may be scheduled to fly from a pre-determined take-off point to a landing site.For these scenarios,a fixed linear trajectory is usually assumed [128, 129, 127].In [128], SOP analysis has been conducted jointly considering the geometric positions of the UAV,as well as random location distribution of Eves,while in[129],beamforming and power allocation at a multi-antenna ground Tx has been investigated.In[127],a FD multi-antenna UAV Rx following linear trajectory is considered,where joint AN projection matrix and power allocation design was investigated to maximize the SR.
In the presence of multiple randomly distributed ground users,circular trajectory is another commonlyadopted assumption.The UAV may patrol followinga pre-defined circular trajectory over the area that to be covered, providing service to the users distributed below[130,131].Providing that the trajectory is fixed and known in every transmission slot, the design in general has no obvious difference in the methodology.However,note that new parameters may affect the system performance,e.g.,the radius of the circular trajectory might should be designed according to the distribution area of the ground users.
For multiple users with fixed locations on the ground, data transmission can be provided by a UAV Tx in a “fly-hover-transmit” manner, in scenarios where the data requirements of users are not timesensitive.Specifically, the UAV Tx may hover right above one user for its data transmission.Upon accomplishment, the UAV flies to the next user following a fixed trajectory,and this process continues for all users in a sequential order.For such a scenario,UAV swarm-enabled secure communications have been investigated in [132, 133].In these works, an Eve is assumed to follow the projection of UAV trajectory on the ground, and large-scale CSI-based power allocation method was proposed to maximize the secrecy throughput in a whole-trajectory-oriented manner.
For most of the above-mentioned works, fixed trajectory implies that the time-varying coordinates of UAV (i.e., qU[n] in (5)) are no longer optimization variables,but being considered as fixed parameters in the optimization.However,when the UAV works as a relay, the fixed trajectory may still has impact on the constraints for optimization.For example, consider that the UAV relay flies along a fixed trajectory from the source to destination, and working in a “storecarry-forward” manner [134, 43].In this case, the trajectory implicitly affects the information-causality of the system.That is, in any time slot, the accumulated data amount transmitted in the downlink (from relay to destination) should not exceed the accumulated data amount received in the uplink(from source to relay).As the UAV trajectory directly affects the channel strength in every time slot,different power allocation schemes should be applied to guarantee the information-causality for different trajectories.
Other mobility model for the UAV relay has been considered.In [135], the UAV relay works in an accompany manner, i.e., it follows the trajectory of the ground device.Such accompanying mobility model is also suitable for the scenario of wireless surveillance/proactive eavesdropping, where a legitimate UAV monitor usually needs to follow the trajectory of suspicious users for effective surveillance.In[137],a UAV monitor was dispatched to overhear the suspicious communication between two UAV Tx/Rx.Meanwhile with eavesdropping, the legitimate UAV sends jamming signals to degrade the suspicious communications.The jamming power is allocated in the time domain during the flight, which, is directly affected by the accompanying trajectory.A similar scenario was considered in [138], where differently, the legitimate UAV may also work as a spoofing relay depending on its decoding status during the flight trajectory.More practical tracking models have been discussed in[108],where the locations of the suspicious nodes cannot be known a priori.The legitimate UAV needs to track the trajectory of the suspicious nodes,via either signal-based or vision-based methods.In this case,the specific tracking methods should be considered in the evaluation of system performance.
At last in figure 7, we summarize and illustrate the described UAV mobility models.From figure 7a to figure 7c,the UAV trajectories are considered as fixed constraints other than optimization variables;whereas in figure 7d,it shows a simple example for secure trajectory planning, where the UAV should try to keep away from Eve if the location of the latter is known.The large amount of secure trajectory optimization works are reviewed in the following subsection.
4.3 Trajectory Optimization
We now introduce the most important research direction in UAV-related communications, that is, trajectory optimization.There exist quite a large amount of works in this category.To allow the reader find his/her interested scenario conveniently,we structure this subsection according to the UAV’s roles,as that has been described previously inSubsection 2.3.
1)UAV Transmitter/Receiver:We start from the basic three-node wiretap model.A Tx attempts to send confidential messages to a legitimate Rx in the presence of an Eve, where the UAV may act as either Tx or Rx.PLS design is slightly different for these two cases: When UAV acts as Tx,its trajectory will affect both the legitimate and the eavesdropping links.Generally, the trajectory should be designed to be close to the legitimate Rx, while trying to keep away from potential Eves (as shown in figure 7d).On the other hand, when UAV acts as a Rx, its trajectory only affects the legitimate link.Nevertheless, by letting the trajectory be closer to the legitimate Tx, lower transmit power is expected,and hence,information leakage in the eavesdropping link can be reduced.
Such a three-node system model has been considered in[139-141,40].In[139],an algorithm was proposed to maximize the SR by jointly optimizing the UAV trajectory and transmit power over a finite horizon area.The same design metric and optimization objective were investigated in[140],where the authors further added no-fly zone constraints in the analysis.To strike the trade-off between secrecy throughput and the UAV’s energy consumption, [141]maximized the SEE while satisfying the general communication performance requirements.These studies mainly focused on the UAV-to-ground(U2G)case.In[40],the authors considered both the U2G and ground-to-UAV (G2U)communications, and maximized the ASE via trajectory and transmit power optimization.
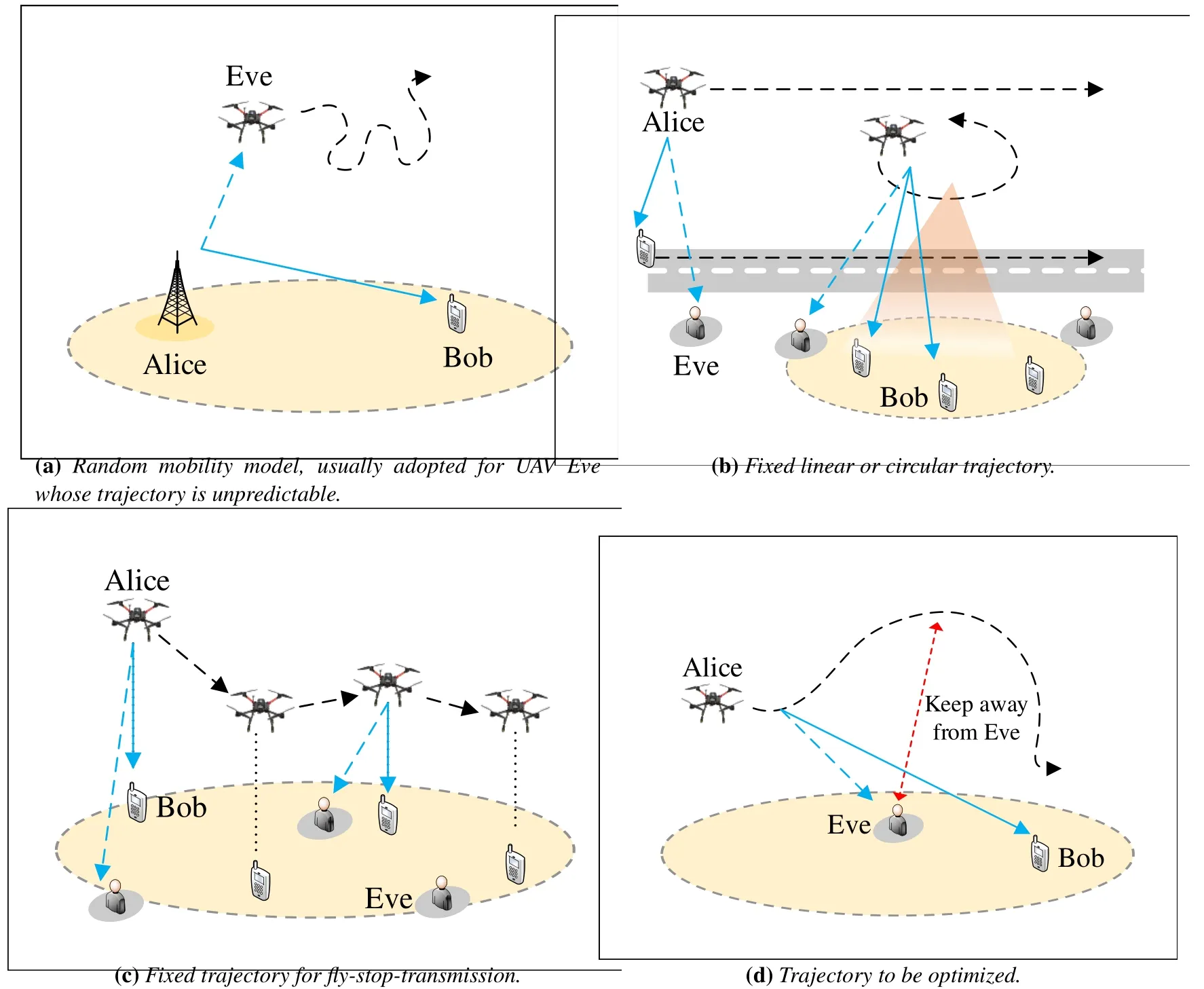
Figure 7.Typical trajectory models for the moving UAV.
The three-node model has been considered for some specific scenarios and combined with other techniques[142, 143, 81].RIS assisted UAV network was considered in [142], where the authors proposed an iterative algorithm to maximize the SR by jointly optimizing the trajectory, the transmission power and the phase shifts of RIS.For UAV-enabled secure communication with finite blocklength,an iteration algorithm was proposed to maximize the ASR in [143].By introducing the concept of mobile secrecy guard cone and with the aid of a 3D sectorized antenna model,the authors in[81]investigated ASR maximization for the UAV-enabled millimeter wave communication via,again,trajectory and power optimization.
More general multi-node scenarios were investigated in [144-147, 149, 191, 156, 157].Compared with the three-node model, new optimization targets and variables emerge.In the multi-user scenarios,the minimum SR among users is often considered for fairness.Besides, when the system serves multiple users via TDMA or FDMA protocols, user scheduling or association can be optimized to further enhance the secrecy performance.In [144], the minimum SR of ground terminals was maximized by jointly optimizing the UAV trajectory, downlink transmission power and user association.To satisfy the legitimate users’content requests and prevent Eve from eavesdropping,the authors in [145] proposed a latency-minimized transmission scheme, where the UAV trajectory and user association were jointly optimized.
For multiple Eves, worst-case SR is often considered for robust design, where the Eve with largest wiretap channel capacity is critical.For such a scenario, [149] considered a problem of securing UAV communication in the presence of stationary or mobile Eves, where the authors developed a model predictive control (MPC) based navigation scheme and minimized the energy expenditure of the UAV via online 3D trajectory planning.A UAV-aided multicasting system was investigated in[156], where the UAV disseminated a common file to multiple users in thepresence of multiple Eves.The UAV sequentially visited the locations of virtual BSs to serve the legitimate users in groups.The work first optimized the virtual BS locations,and then optimized the trajectory of the UAV via traveling salesman problem(TSP)algorithm.
For the multi-UAV case, inter-UAV interference and collision avoidance constraints should be considered.The work of [157] maximized the minimum SR of users by jointly optimizing user scheduling,UAVs’ trajectories and transmit power allocation under the propulsion energy and the inter-UAV interference constraints.In particular, curvature radius constraints were introduced to avoid the sharp swerve of UAVs.[154] investigated a UAV communication network from a cooperation perspective, where two UAVs transmit confidential messages to their specified ground destinations by sharing the same spectrum,and the two UAVs meanwhile act as cooperative jammers for each other.An iterative algorithm was proposed to maximize the system SR by jointly optimizing the trajectory and transmit power of both UAVs.
In some works, location error model was considered,where the exact locations of Eves were unknown.The worst-case SR was usually considered for this case.The authors in [146] investigated secure communication for UAV-OFDMA systems with multiplelegitimate users and a malicious Eve located in an uncertain region.To facilitate the secure communication and save the energy consumption,they maximized the SEE by jointly optimizing the transmission power,UAV’s trajectory and user scheduling.With a similar distribution model for Eves,the authors in[147]maximized the average worst-case SR.The case that multiple Eves distributed in a uncertain region was further considered in[191].
The UAV may act as a secondary transmitter in a cognitive radio (CR) network [192, 72].In the CR scenario, the UAV should be not only away from the Eves to avoid eavesdropping, but also away from the primary users to avoid interference.Imperfect location information of Eves was considered in[192],and the average worst-case SR at secondary receiver was maximized by joint trajectory and power optimization.[72] considered two different practical location estimation error models, namely, bounded location error model and probabilistic location error model.Correspondingly, two problems including worst-case ASR maximization and outage-constrained ASR maximization were formulated and solved.
Some advanced techniques can be incorporated into the UAV systems to improve security performance, such as NOMA, SWIPT, mmWave, and coordinated multiple points (CoMP) transmission[148,150-153,155].Considering the limited on-board energy, SWIPT has been adopted to provide energy for UAVs.Secure transmission for mmWave SWIPT UAV networks was investigated in[148].Considering both beamforming design and 3D antenna gain, the directional modulation (DM) technique based on random frequency diverse array(RFDA)is adopted to guarantee secrecy.In[150], resource allocation was studied to guarantee the secure communications of the UAVassisted SWIPT systems with multiple Eves, where the SR was maximized via jointly designing the trajectory and the transmission power.NOMA is seen as a promising technique in UAV networks to improve the spectral efficiency when serving multiple users.A downlink secure UAV-NOMA network was investigated in [151], where the users are categorized as security-required users (SUs) and quality of service(QoS)-required users (QUs), and the QUs potentially act as internal Eves.The minimum SR among SUs are maximized by jointly optimizing user scheduling,power allocation,and trajectory design,subject to the QoS requirements of QUs and the mobility constraint of UAV-BS.In [155], a moble UAV-enabled CR-NOMA system was considered.The 3D UAV trajectory and power allocation were optimized to maximize the worst-case ASR of all secondary users under the interference constraint at primal receivers.Secure UAV communication with CoMP reception was investigated in [152], where one UAV serves a set of coordinated ground nodes in the presence of several colluding Eves.In a similar scenario, [153] provided analysis for both non-colluding and colluding Eves.
2)UAV helper:We further introduce the trajectory optimization works where UAVs act as helper for PLS,i.e.,relay or friendly jammer.Similarly,we start with a basic four-node model,where a source intends to send confidential message to a legitimate Rx with the help of a UAV relay,in the presence of an Eve.Such a basic four-node model was discussed in[193,160,75,161].In[193],the authors investigated trajectory optimization under constant UAV’s transmission power.An effective algorithm by optimizing the increments at each trajectory iteration was proposed, which significantly improved the system’s SR.An alternating optimization approach was proposed in[160]to address the non-convex optimization problem.By jointly optimizing the communication resources,i.e.,power and bandwidth allocation,and the UAV’s trajectory,the accumulated SR was maximized.Considering a practical channel model,including both LoS and NLoS fadings,the authors in[75]aimed to strike a trade-off between the SR and the energy consumption of the UAV via maximizing the SEE, in which the communication scheduling,the source/relay power allocation,and UAV’s trajectory were jointly optimized.Under practical mobility and information-causality constraints,[161]focused on maximizing the SR via jointly optimizing the mobile relay’s trajectory and the source/relay transmission power.
The above works mainly assumed that the position of Eve was fixed and known.More practical and complicated assumptions on the Eve distribution were further discussed in [162-164].Assuming that the Eve is uniformly distributed on a line, authors in[162,163]investigated the optimal UAV trajectory design to maximize the sum rate,considering the buffer size limit on the UAV relay.The potential Eve’s locations were modelled as a disk area on the ground in[164],where the authors investigated robust design of trajectory and resource allocation.
For the multi-node scenarios, the previous analysis and design methods in general still apply, while more various optimization objectives, variables, and constraints appear.Considering UAV relayed wireless networks with caching,the authors in[165,166]proposed a novel scheme to guarantee secure transmission between data-requiring users and cache-enabled users.By jointly optimizing the trajectory and time scheduling, the minimum SR of the users without cache was maximized.The authors in[168]considered the UAV as a mobile relay to assist BS to disseminate information to multiple users in the presence of multiple Eves.The transmission power of BS and UAV, and the UAV trajectory were jointly optimized, to maximize the average worst-case SR.In[169],the authors investigated a UAV relaying network, where multiple adversaries tried to intercept the legitimate link, and their position information was uncertain.Considering both the worst-case SR and UAV propulsion energy consumption, the authors maximized the EE by optimizing the UAV/BS transmit power and UAV’s trajectory.A cache-enabled UAV-relaying wireless network was considered in [194, 195], where UAVs were employed as mobile relays to ferry the information from the macro BS to users,and both UAVs and D2D users were equipped with cache memory.In[194],user association, UAV scheduling, transmission power, and UAV trajectory were jointly optimized to maximize the minimum SR among users, while in [195], the cache placement was jointly considered with trajectory optimization.The study in[196]considered a CR system,where both information-causality and interference constraints were considered in the joint power and trajectory optimization.
Friendly jammer is another important role for UAV helpers to enhance the PLS.In general, the trajectory design should make the UAV jammer close to Eves while being away from the legitimate users.We first introduce the four-node model where a UAV jammer transmits jamming signals against eavesdropping in a ground wiretap system.By jointly controlling the transmission power of both the transmitter and the UAV jammer, the ASR was maximized in [170].By assuming an ellipse model for Eve’s unknown location,the authors in[171]investigated UAV-aided jamming for secure ground communications with the target of average secrecy rate maximization.Under the uncertainties of the nodes’locations,a robust joint design problem of optimizing the UAV’s jamming power and trajectory was formulated to maximize the average secrecy rate [172].The authors in [173] investigated the scenario where a UAV secured an underlay cognitive radio network(CRN)as a friendly jammer,and interfered the Eve who attempts to decode the confidential message from the secondary transmitter(ST).The transmit power and UAV 3D trajectory were jointly optimized to maximize the average achievable secrecy rate of the secondary system subject to the primary receiver interference power constraint.
Some works further considered the composite case,that one UAV can may act as jammer,communication node, or a relay simultaneously[174,176,175,177].Considering the limited on-board energy of UAVs,the power allocation between communication and jamming should be carefully designed.In[174],the UAV employed power splitting for transmitting confidential messages and artificial noise.By jointly optimizing the UAVs’ trajectory, the transmission power and the power splitting ratios, the ASR was maximized.FD UAV was considered in [176], where the UAV sent jamming signals to potential ground Eve, while receiving the confidential messages.The paper [175]considered a single UAV-enabled secure data dissemination system where the UAV secretly communicate with multiple ground users by TDMA protocol.AN was introduced to prevent confidential signal intended to scheduled users being overheard by unscheduled ones.To guarantee fairness, it maximized the minimum ASR among all users, by jointly optimizing the UAV trajectory, transmit power splitting ratio and the user scheduling.The authors in [177] investigated a UAV-enabled confidential data collection problem,and derived the reliability outage probability (ROP)and SOP.They maximized the minimum ASR by optimizing the UAV trajectory,AN transmit power,transmission rates and the sensor node scheduling, under the ROP and SOP constraints.
Cooperation between a UAV jammer and a UAV communication node can enhance the PLS, and their trajectories can be designed jointly.This is known as the dual-UAV scenario, which has addressed increasing research attentions recently.In this case,the inter-UAV distance constraint should be considered when designing their trajectories.A basic four-node model was considered in[179-181], where two UAVs acted as Tx and jammer, respectively.The authors in[179]adaptively adjusted the UAVs’ trajectories to maximize the ASR, where the constraints of the transmission/jamming power was considered with partiallyknown Eve’s location.In[180],the authors considered two jamming schemes,namely friendly UAV jamming and Gaussian jamming.With partial knowledge of Eve’s location, an optimization scheme with robust trajectory design and resource allocation was proposed to maximize the ASR.In[181],the authors maximized the SR via trajectory design and power control of both source UAV and jammer UAV.The work in[197]studied UAV jamming in a CR network.Under a given interference threshold at the primary receiver, the SR was maximized by jointly optimizing the UAV’s trajectory and the transmission power.
UAV jammer/Tx cooperation was further investigated for the multi-user or multi-Eve cases in [178,198, 44, 182-185], where user scheduling becomes another dimension to be optimized, and worst-case SR is usually the focus.To guarantee fairness for multiple users, joint trajectory, transmit power, and user scheduling optimization was conducted to maximize the minimum SR in [178].In [198], to maximize the worst-case ASR, the two UAVs’ trajectories and the BS/UAV jammer’s transmit/jamming power were jointly optimized.The work of [182] considered multiple location-unknown Eves.The authors in[44,183]developed a new algorithm based on the penality concave-convex procedure technique to handle secure communications for the dual-UAV enabled network.In [184], the authors considered both multiple users and multiple Eves,and maximized the minimum ASR over all users by jointly optimizing the UAV trajectory and transmission power.More powerful UAV jammer employing multi-antenna array was considered in [185], where energy-efficient secure UAVOFDMA communication to multiple users,in the existence of multiple Eves,was investigated.To maximize the EE, the trajectory, resource allocation, and jamming policy were jointly designed.Researches have been further extended to the multi-jammer case.The authors in[186,187]considered cooperation between multiple UAV jammers and a UAV Tx,where the jammers send AN signals to ground Eves via 3D beamforming.A multi-agent deep reinforcement learning approach was proposed to maximize the secure capacity by jointly optimizing the UAV trajectories, the transmit power and the jamming power.The paper[189] further considered a cooperative scenario with multiple source UAVs and jammer UAVs.
UAV jammer has also been integrated into UAV relay systems [199, 188, 190, 196].In [199], for such dual-UAV system with one UAV relay and one UAV jammer, the authors iteratively optimized their trajectories and transmit power to maximize the SR.In[188], the constraints of flight trajectory and power on both UAVs, as well as the information-causality constraint on the relaying UAV, were jointly considered in the optimization to maximize the SR.The paper[190]considered a multi-UAV communication network,where a novel joint friendly jamming and bandwidth allocation scheme was developed.
3)UAV Attacker and Covert Communications:As compared to the above roles of UAV, trajectory optimization works considering UAV attackers, and that for covert communications,are relative less.We introduce several representative works in this subsection.
The UAV attacker can be more harmful compared with a ground attacker,because of the high probability of LoS propagation, as well as its high mobility.The authors in [81] considered UAV Eve in a UAV millimeter wave communication system.The trajectory of the legitimate UAV Tx was designed to avoid UAV Eve appearing in a cone region below it.Considering UAV jamming attack,the authors in[200]investigated the 3D deployment and trajectory planning problem by dynamically adjusting the UAV’s trajectory to maximize the sum throughput with jamming.
For covert communications,a legitimate UAV communication node should try to approach the other legitimate nodes during transmission, so as to reduce the communication power and hence reduce the probability of being detected.Besides, AN can be employed for better covertness performance.In [158,159], a covert communication problem was formulated, where a UAV collects data from ground users and meanwhile generates AN to ensure the scheduled user’s transmission not being detected by unscheduled users.The UAV’s trajectory, AN power, and user scheduling were jointly optimized to maximize the minimum transmission rate,subject to covertness constraints.Covert communications in a UAV network was investigated in [73], where a UAV Tx intends to communicate with a ground receiver, while a ground warden wanted to detect the UAV’s transmission.The UAV’s trajectory and transmit power were jointly optimized to maximize the average covert transmission rate, subject to both transmission outage and covertness constraints.
4.4 Summary of This Section
We summarize what have learnt in this section:
· For mobile UAV deployment, the PLS design is usually conducted in a communication processoriented manner.In other words, the optimization now needs to span the entire period that communication happens.The trajectory of the UAVs,either being random,fixed,or to be optimized,introduces new constraints or objectives in the optimization for different PLS scenarios.
· When the UAV trajectory is not controllable by the communication designer and considered as a fixed condition, it is usually reflected in the constraints of optimization.For example, a certain fixed trajectory will directly impact the timedomain power allocation, or the informationcausality when UAV acts as a relay.
· Accompanying mobility model can be seen as a special case of fixed trajectory.A UAV Tx or relay may follow the trajectory of ground user to provide better service.For wireless surveillance,a UAV monitor may follow the suspicious nodes for better detection.In practice, the accompanying trajectory can be realized based on signal strength or vision,and the accompanying strategy can be jointly designed with the communication strategies,to enhance the PLS performance.
· Trajectory optimization contributes a major research direction in the UAV-PLS works.The optimization methodology for different scenarios can be similar, while the problem formulation can be largely different.Realistic constraints, such as collision avoidance inter-UAV distance, UAV propulsion energy, partial knowledge of Eve’s CSI,etc.,are usually introduced to make the problem formulation more practical.
V.POTENTIAL FUTURE DIRECTIONS AND CHALLENGES
5.1 MIMO, RIS, and UAV Swarm-Enabled CoMP
The multiple antenna technique plays an important role in the research of physical layer security [201].Specifically, when implemented at the transmitter, a multi-antenna array admits techniques such as secure precoding or null-space jamming, to enhance the secrecy rate or reduce the secrecy outage probability.While for a multi-antenna receiver, the combination gains it provided can reduce the requirement of transmit power, and hence reducing the chance of being overheard by Eves.On the other hand, the communication secrecy could be harmed if multiple antennas are deployed at the adversary nodes.However,due to the limited payload,a large amount of existing UAV-PLS works consider only single antenna onboard.To enhance the secrecy performance,it is desired to further exploit the spatial dimension.Thanks to the latest developments in radio technologies,it becomes possible to pack more antenna/reflection elements in a compact sized array.This has promoted the research on MIMO/RIS-aided UAV communications, where the PLS design problems need to be re-formulated.In particular, the design or MIMO precoding, AN matrix, or RIS phase shifters, needs to be considered in addition to the conventional optimization dimensions[202].Though there has already emerged some pioneer works on this research direction(some have been introduced in previous sections),the number of corresponding researches is still far less than its counterpart,where single-antenna UAVs were considered.Many research scenarios are yet to be extended to the MIMO/RIS case.
On the other hand, when MIMO/RIS-based UAV platforms are not available, single antenna UAVs can form a swarm-based virtual MIMO systems,performing CoMP transmission to ground users [203].This is becoming possible as the swarm coordination techniques are becoming mature.For such scenario, new PLS problems arise,e.g.,malicious UAV detection in a swarm.A malicious UAV is able to follow the legitimate UAVs to perform eavesdropping/jamming attacks more effectively,meanwhile,the attack could be more harmful due to the favorable A2A channels.The detection, surveillance, avoidance, and possible jamming of/on potential malicious UAVs in a swarm is an important issue that needs to be considered.Furthermore, possible attack on the control signals also becomes a critical issue[204,205],as the UAV swarmenabled communication highly relies on reliable signalling channels among them.
5.2 Integration with Satellite Networks
Both satellites and UAVs are important candidates for non-terrestrial network beyond 5G,which can be utilized to cover the blind zones of terrestrial cellular networks.In the current developing stage,both satellites and UAVs have their drawbacks,individually,in terms of latency or endurance.This problem can be alleviated by proper coordination between satellites and UAVs to form an integrated satellite-UAV network.As satellite transmission is more open than UAVs,this may lead to more serious secrecy problem,which should be carefully addressed in the PLS design[206].In such a scenario, the UAV may act as a helper to safeguard satellite communications thanks to its agile mobility[207].The heterogeneity of such a network,especially the signalling and data exchange overhead for coordination, as well as joint resource allocation,should be carefully modelled in the optimization.
5.3 More Powerful Helpers: Caching and MEC
In addition to the conventional roles of helper, i.e.,relay and friendly jammer as described above, UAV can be deployed as more powerful helpers, who can offload the user-desired data from the BS (caching),or it can offload computation tasks from the end-users(MEC).Flexible deployment of UAV is promising to make either caching or MEC more effective,however,secrecy issues need to be addressed.Possible impacts of caching on communication secrecy has been investigated from the following perspectives: The cache hit rate of a user may affect its communication link selection.That is, if the user cannot find its desired content in the UAV cache, it turns to the source node for the data.In the presence of Eve, different communication link selection subsequently results in different secrecy performance, as has been discussed in [208].On the other hand, when a user can acquire its desired content in UAV cache, the source nodes can be idle for transmission and therefore can be utilized for friendly jamming.This will help improve the secrecy performance, as has been investigated in [209, 210].In general,the feature of UAV caching is reflected by its deployment flexibility: For example,the number of UAVs required for secure transmission has been discussed in[209].As for MEC-empowered UAVs,computing would reduce the amount of data for further transmissions,thus provides better secrecy.However,this requires joint resource orchestration of both computing and communications.For the latest research works on secure UAV-MEC networks,the readers are referred to[211,212].There are still lots of works to be done in these research areas.
5.4 Machine Learning Approaches
When multiple UAVs are adopted in a partially unknown environment, the optimization of PLS would become much more complex.On the one hand, the UAV swarm control and communications design, as well as caching and computing if integrated, should be fully taken into account.However, some parts of which are hard to model due to interdisciplinarity.On the other hand, the optimization problem is usually non-convex with high-dimensional variables,it is challenging to design low-complexity methods to solve the problem with affordable performance degradation.The fast developing machine learning techniques provide promising and powerful tools for this tricky scenario.It is possible to derive a hybrid model and data-driven method to characterize the complex system, and use hybrid offline and online approaches to optimize the secrecy performance.For example,the UAV trajectory design can be promoted by reinforcement learning.Nevertheless, using machine learning approaches may raise new secrecy problem,in e.g., data gathering or parameter updating.Recently,a number of works have emerged in the area of machine learning-aided secure UAV communications[213-220,119].However,there still exist much more scenarios that machine learning may find its application,and a systematic design framework is still needed for the learning-aided secure UAV communications.
VI.CONCLUSION
The article surveyed important issues of UAV communications from the perspective of PLS.As necessary preliminary of the survey,we first introduced the typical application scenarios with static/mobile UAV deployment,the unique channel and location distribution models in UAV communications,as well as typical roles of UAV for PLS.After that, we provided an exhaustive review of the state-of-art research achievements on UAV-PLS,which were categorized into two cases: the UAV is deployed at static positions,and the UAV is moving during the communication process following certain trajectory.For each case, respectively,we have summarized the commonly adopted methodology in the analysis and design, and discussed important literatures in detail.Important research works have been summarized in tables to help a researcher quickly find the latest development in his/her area of interest.Finally, we have further shown several promising research directions and possible challenges for future researches.
ACKNOWLEDGEMENT
This work was supported in part by the National Key Research and Development Program of China under Grant 2020YFA0711301; in part by the National Natural Science Foundation of China under Grant 61922049, 61941104, 61921004, 62171240,61771264, 62001254, 61801248, 61971467, the Key Research and Development Program of Shandong Province under Grant 2020CXGC010108,the Key Research and Development Program of Jiangsu Province of China under Grant BE2021013-1, and the Science and Technology Program of Nantong under Grants JC2021121,JC2021017.
NOTES
1The ASR should not be confused with the ergodic secrecy rate(ESR),where the latter is obtained by taking expectation over all possible fading states of the involved channel links.Besides,is usually omitted when evaluating the ASR whenNis fixed as a constant.In this case,the ASR is equivalent to the accumulate SR.
2Different terminologies might be adopted in different works.For transmitter,it might be denoted as BS,Tx,source,Alice,etc.For receiver,it could be denoted as Rx,destination,Bob,etc.For convenience,in the tables,we keep consist with the term used in the corresponding original paper.
3In the table,when the number of nodes is denoted by“M”(which stands for“Multiple”),it indicates no explicit number is assumed,and the node positions are generated from an unbounded point process.
- China Communications的其它文章
- GUEST EDITORIAL
- Reducing Cyclic Prefix Overhead Based on Symbol Repetition in NB-IoT-Based Maritime Communication
- Packet Transport for Maritime Communications:A Streaming Coded UDP Approach
- Trajectory Design for UAV-Enabled Maritime Secure Communications:A Reinforcement Learning Approach
- Hybrid Satellite-UAV-Terrestrial Maritime Networks:Network Selection for Users on A Vessel Optimized with Transmit Power and UAV Position
- Energy Harvesting Space-Air-Sea Integrated Networks for MEC-Enabled Maritime Internet of Things

