Networked TT&C for Mega Satellite Constellations:A Security Perspective
Yafeng Zhan,Guanming Zeng,Xiaohan Pan
1 Beijing National Research Center for Information Science and Technology,Beijing 100084,China
2 Department of Electronic Engineering,Tsinghua University,Beijing 100084,China
Abstract: Satellite constellations are promising in enabling the global Internet.However, the increasing constellation size also complicates tracking,telemetry and command (TT&C) systems.Traditional groundbased and space-based approaches have encountered significant obstacles due to, e.g., the limited satellite visible arc and long transmission delay.Considering the fast development of intersatellite communications,synergy among multiple connected satellites can be exploited to facilitate TT&C system designs.This leads to networked TT&C, which requires much less predeployed infrastructures and even performs better than traditional TT&C systems.In this paper, we elaborate system characteristics of networked TT&C compared with traditional ground-based and spacebased TT&C, and propose the unique security challenges and opportunities for networked TT&C,which includes secure routing and trust mechanisms.Furthermore, since networked TT&C is a novel scenario with few relevant researches, we first investigate the current researches on secure routing and trust mechanisms for traditional terrestrial and satellite networks,and then accordingly deliver our security perspectives considering the system characteristics and security requirements of networked TT&C.
Keywords: mega-constellation; TT&C; network; security;routing;trust mechanisms
I.INTRODUCTION
In recent years, many mega-constellation projects have emerged in the world [1].SpaceX plans to build Starlink constellation composed of approximately 42,000 satellites to provide low-cost worldwide Internet connectivity services[2].Amazon plans to build the Kuiper constellation of approximately 3,236 low earth orbit (LEO) satellites [3].Oneweb plans to build a constellation composed of 882~1980 satellites and provide up to 595 Mb/s Internet data services with 32 ms latency [4].In addition, Telesat,Boeing, O3b, LeoSat and other mega-constellations plans have also been proposed [5].China Network Satellite Group integrates domestic constellation resources including Hongyun and Hongyan,and aims at building a Chinese version of Starlink[6].The megaconstellations are used in broadband Internet [7], Industrial Internet of Things [8], emergency communication [9] and other fields [10] and outperform traditional communication systems.Specifically, megaconstellations provide wide area coverage and high data rate for maritime communication, which breaks through the performance bottleneck: the traditional system based on terrestrial base stations has limited coverage area, while the traditional system based on geostationary earth orbit(GEO)satellites and medium earth orbit (MEO) satellites has limited data rate[11,12].
In order to ensure the normal operation of the constellation, to achieve highly reliable and timely data interaction between the ground mission center and the satellite,a TT&C system is generally adopted to monitor and control the operation of satellites.Tracking means that the ground mission center obtains and tracks the satellite’s spatial position; telemetry means that the ground mission center obtains and monitors the satellite’s operation status data, scientific detection data, load data, etc.; command means that the ground mission center controls the satellite to perform orbit adjustment, attitude adjustment, operation mode switching, fault diagnosis and other functions.The traditional TT&C system can be classified into the ground-based TT&C system and the space-based TT&C system.The ground-based TT&C system relies on the satellite-ground links (SGL) to complete TT&C information interaction,while the space-based TT&C system relies on the relay of the GEO satellite to complete TT&C information interaction.For the traditional small-scale constellation, the groundbased and the space-based TT&C systems are capable to meet the basic TT&C requirements.
Constellation TT&C has remained as an engineering application problem for a long time with few relevant academic researches.However, with the emergence of mega-constellations,the rapidly growing demand of satellite TT&C exhausts the resources of the ground-based and the space-based TT&C systems.A new TT&C mechanism and system architecture are needed to adapt to the TT&C demand of megaconstellations.Moreover, some new perspectives are needed to clarify the basic problems that the system may encounter and the future research direction, so as to guide the development of the mega-constellation TT&C system.Therefore,this paper proposes the networked TT&C, which transmits TT&C data on the constellation network and relies on only a few traditional TT&C resources such as ground stations and GEO satellites,thus solving the shortage of TT&C resources.Meanwhile,this paper points out several key security issues of networked TT&C,including secure routing and trust mechanism.As mentioned above,due to the lack of academic researches on satellite constellation TT&C, this paper first reviews the security researches on related scenarios in traditional communication networks.Considering the characteristics and security requirements of networked TT&C,this paper then analyzes the advantages and disadvantages of existing technologies, and gives future development directions and suggestions.
This paper focuses on security of the networked TT&C system, and the rest of this paper is organized as follows: Section II illustrates the architecture, system characteristics and security requirements of the networked TT&C, and gives a research overview of this paper.Section III investigates the existing researches on security of traditional TT&C systems.Section IV and V introduce the existing security studies on secure routing and trust mechanisms.Furthermore,according to system characteristics and security requirements of the networked TT&C, security suggestions and future research directions are given for networked TT&C.Finally,Section VI summaries this paper.
II.THE NETWORKED TT&C SYSTEM AND THE SECURITY
2.1 System Architecture
As depicted in Figure 1,the ground-based TT&C system consists of the satellite constellation, TT&C stations and the mission center.When the satellite is visible to the TT&C station,it transmits on-board telemetry data down through the satellite-ground link and receives remote command from the TT&C station[13].TT&C stations realize interconnection through the ground network.The mission center is connected with TT&C stations through the ground network to monitor and control operation of the satellite constellation.Since the satellite communicates with the TT&C station only when they are visible to each other, fulltime communication cannot be realized in the groundbased TT&C system.To solve this problem, deploying TT&C stations all over the world is considered,but there are still some limitations as follows.First,in order to meet TT&C demands of the mega-constellation,TT&C stations need to be deployed in high density all over the world, resulting in the shortage of groundbased TT&C resources.Second, global deployment of TT&C stations may not be feasible for all countries.Therefore,full-time communication between the satellite and the TT&C station cannot be realized completely.
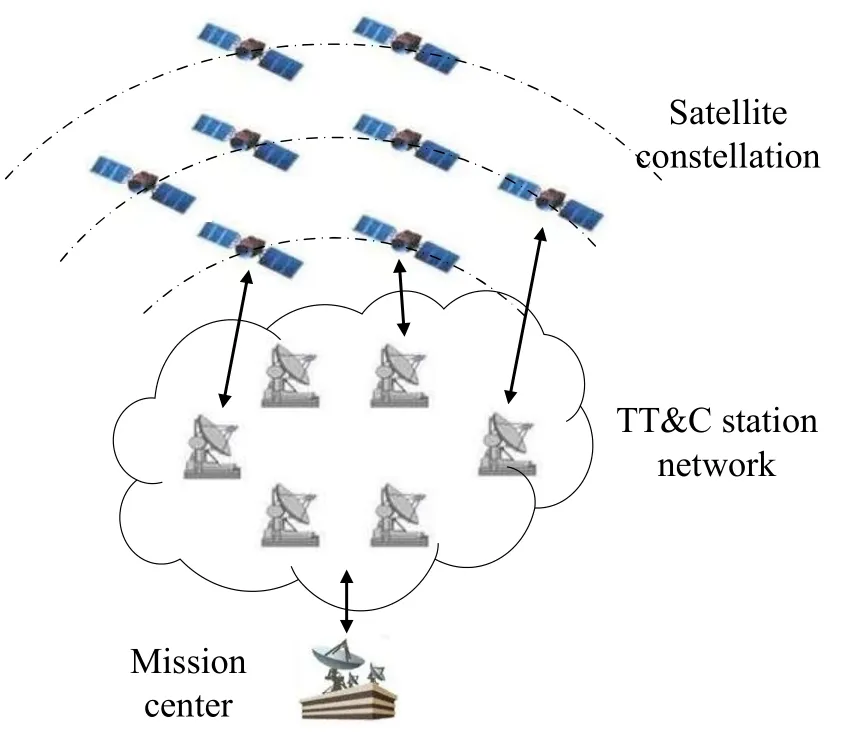
Figure 1.Ground-based TT&C system.
To achieve full-time communication between the satellite and the TT&C station,the space-based TT&C system is proposed.As depicted in Figure 2,the spacebased TT&C system consists of the mission center,the TT&C station, the satellite constellation and several relay satellites located in the geostationary earth orbit [14].Relay satellites are visible to broad areas on the ground due to the high orbit.When the constellation satellite is not visible to the TT&C station,TT&C data can be transmitted via the relay satellite;thus, full-time communication between the constellation satellite and the ground station can be realized[15].However,there are some limitations in the spacebased TT&C system.First,in order to meet TT&C demands of the mega-constellation,many relay satellites need to be deployed,resulting in the shortage of spacebased TT&C resources.Second,as relay satellites are located at the GEO orbit, there is long transmission distance between the relay satellite and the ground station as well as between the relay satellite and the constellation satellite.Thus,there is inevitably high delay in relay transmission, and timeliness of TT&C information cannot be well guaranteed.
Since the intersatellite links (ISL) exist in the mega-constellation, the intersatellite network based TT&C system is proposed to realize TT&C in megaconstellations [6, 16], which is called networked TT&C [17].As shown in Figure 3, the system is mainly composed of the satellite constellation, the mission center, a few TT&C stations and relay satellites.The intersatellite network is constructed based on ISLs within the constellation, and TT&C data can be transmitted in the network by multi-hop relays.The satellite sends telemetry data to the TT&C station and receives command instructions from the TT&C station through the intersatellite network.Compared with ground-based and space-based TT&C, advantages of networked TT&C include the following points: First,only a few TT&C stations and relay satellites are required, which can hardly result in the shortage of TT&C resources.Second, full-time communication between the satellite and the TT&C station can be realized.Third,with low ISL delay,timeliness of TT&C data can be well guaranteed.Therefore, networked TT&C will be a promising future development direction for mega-constellations.A comparison of groundbased, space-based, and networked TT&C systems is given in Table 1.
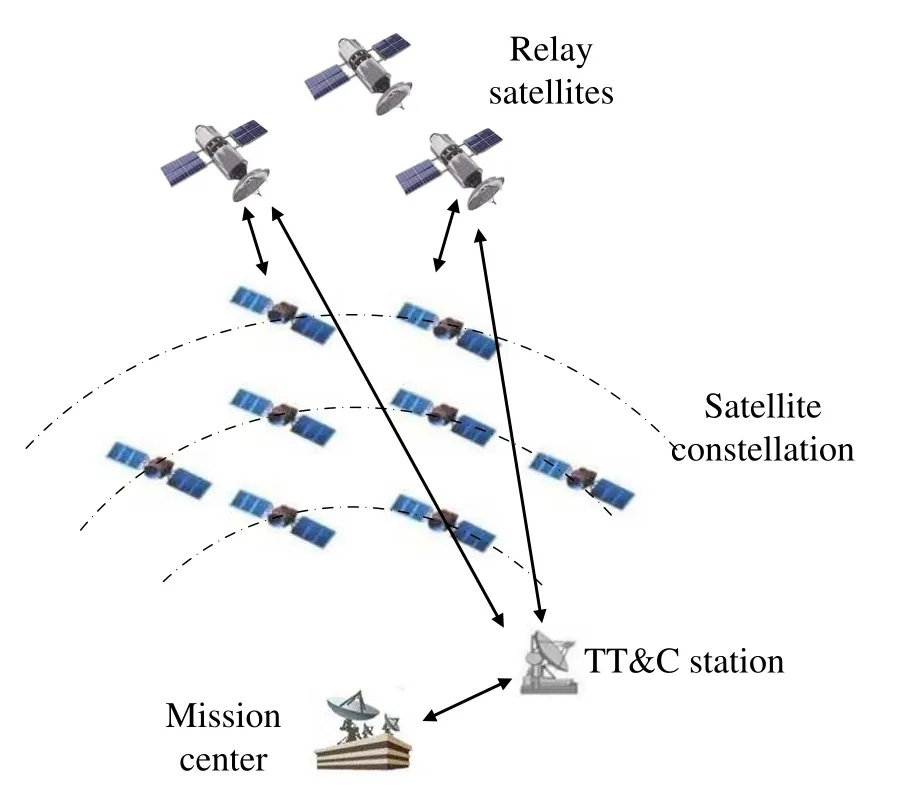
Figure 2.Space-based TT&C system.
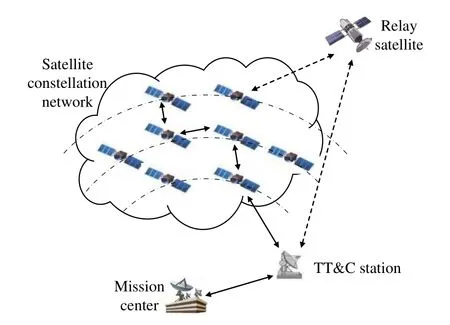
Figure 3.Networked TT&C system.
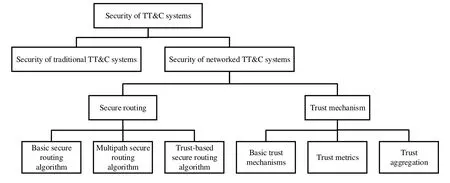
Figure 4.Research overview.
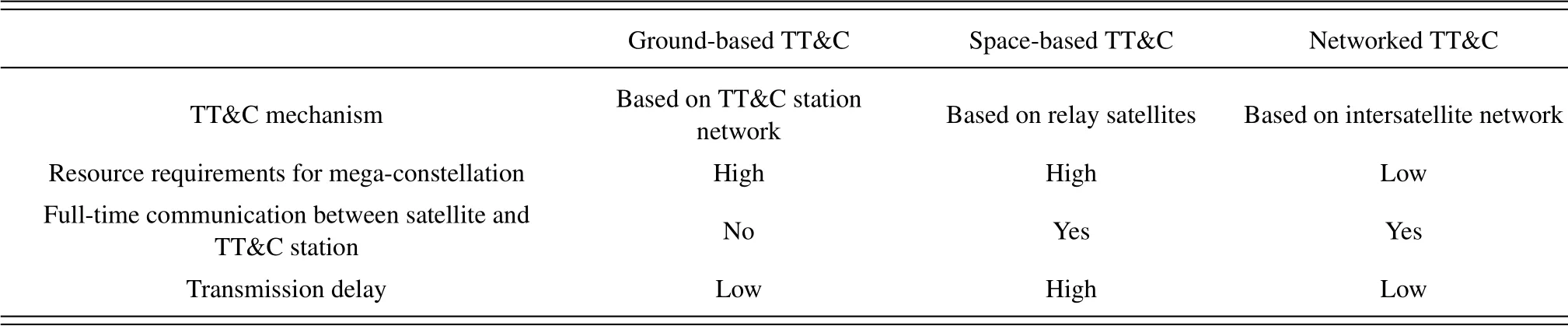
Table 1.Comparison of different TT&C systems.
For traditional ground-based and space-based TT&C, there are only a few or no relays between the satellite and the ground station.While for networked TT&C, the satellite and the ground station communicate through the multi-hop intersatellite network, which makes communication more vulnerable to attacks from malicious entities.Therefore,securityof the networked TT&C system is a significant problem to be solved.
2.2 System Characteristics
With the analysis and comparison in Section 2.1, we have explained the reasons why networked TT&C is more suitable for mega-constellations compared with traditional ground-based and space-based TT&C.Here we further discuss the system characteristics for networked TT&C, and accordingly propose potential challenges and opportunities on security.
1.Massive satellites: Traditional ground-based and space-based TT&C only support the constellation consisted of a few satellites,while networked TT&C supports the constellation consisted of massive satellites[18].
2.Networked transmission: Traditional groundbased and space-based TT&C adopt SGLs and GEO satellite relay links for data transmission,while networked TT&C adopts the ISLs in the intersatellite network for data transmission.Consequently,secure routing emerges as a new problem for networked TT&C and should be studied.
3.Satellite cooperation: With ISLs,satellites are no longer isolated from each other.Instead, satellites can cooperatively monitor abnormal and malicious behaviors.Consequently,trust mechanism should be studied.
Secure routing and trust mechanism are new security issues for networked TT&C.Actually, these security issues have been thoroughly studied for terrestrial and satellite networks.However, the current researches consider little about system characteristics of networked TT&C.Here the system characteristics compared with terrestrial networks are discussed in point 1 and 2,and the system characteristics compared with satellite networks are discussed in point 3 and 4.
1.Periodic dynamic change of topology: As satellites travel along fixed orbits,on the one hand,the network topology changes dynamically; on the other hand, the change of the network topology is periodic and predictable[19].
2.High propagation delay: Long transmission distances of ISLs lead to high delay[20].
3.Ultra reliability: TT&C data contains the operation status and command instructions of the satellites, which requires ultra-reliable transmission.In some emergency situations,any data loss may lead to serious consequences.For example, the loss of command data may lead to failure in the emergency orbit adjustment mission for avoiding satellite collision.
4.High timeliness: Untimely data transmission may disable the mission center to monitor and control the latest operation status of the satellite.Especially in the case of satellite emergency orbit adjustment,untimely data transmission may lead to serious consequences like satellite collision and destruction.
Accordingly, new perspectives should be proposed to guide future in-depth researches,which is the focus in the rest of this paper.
2.3 Security Requirements
The networked TT&C system is used to monitor and control constellation operation.Whether TT&C information security can be guaranteed affects the normal operation of the constellation.Security requirements of the system include:
1.Confidentiality: Ensure that information is not leaked to unauthorized entities.
2.Integrity:Ensure that information is not tampered with by unauthorized entities.
3.Authentication: Ensure that identities of network entities are not forged.
4.Availability: Ensure normal operation of network functions and prevent damage by malicious entities.
5.Timeliness: Ensure that data transmission is finished within a limited time.
Confidentiality, integrity and authentication are basic security requirements of the constellation communication system [21, 22], but they are not enough for the networked TT&C system.Since the TT&C data is used to ensure the normal operation of the constellation,the loss of even a small amount of data may have a serious impact on the system function.Moreover,in some cases,the TT&C system needs to complete some key tasks with near real-time requirement,so the data should be ensured to be transmitted within a limited time[23].
2.4 Researches Overview
As shown in Figure 4, this paper first investigates the existing researches on the security of traditional TT&C systems,and then analyses the security of networked TT&C systems.Specifically, this paper summarizes the current researches on secure routing and trust mechanisms for terrestrial and satellite networks.For secure routing,basic secure routing algorithms use encryption, message authentication codes (MACs),digital signatures,hash chains,and time stamps to ensure basic routing security, while the multi-path routing algorithm and trust-based routing algorithm protect routing from disruption attacks.For trust mechanisms,the direct trust mechanism provides a basic way to estimate trust degrees,while the indirect trust mechanism introduces trust recommendation and propagation mechanisms to estimate trust degrees more comprehensively and accurately.The combination of direct trust and indirect trust is required for the basic trust mechanism.Meanwhile, some other issues of trust mechanisms, such as trust metrics and trust aggregation,would also affect the accuracy of trust estimation.Finally,according to the researches on secure routing and trust mechanisms for terrestrial and satellite networks,future research suggestions and perspectives are given considering the system characteristics and security requirements of networked TT&C.
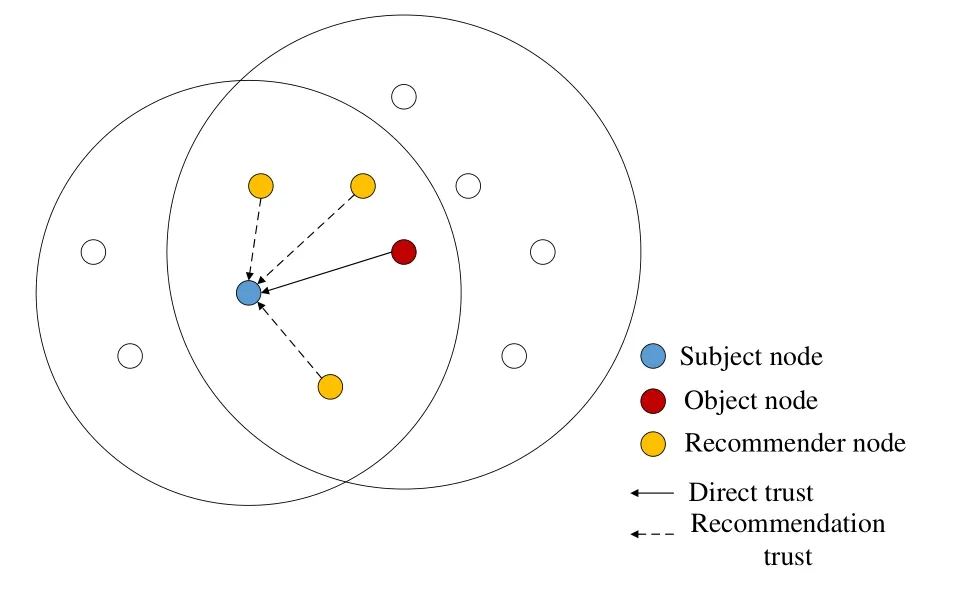
Figure 5.Topology structure of direct trust and recommendation trust.
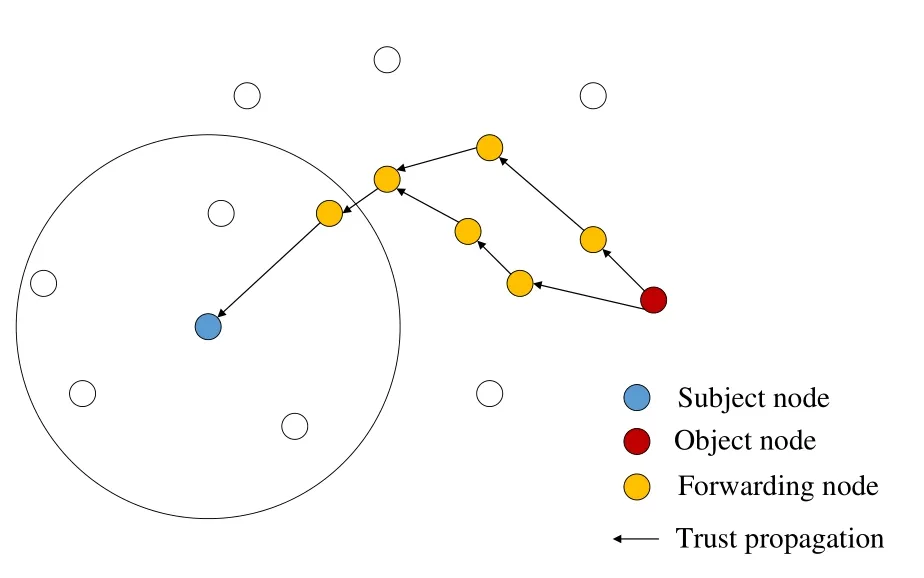
Figure 6.Topology structure of trust propagation.
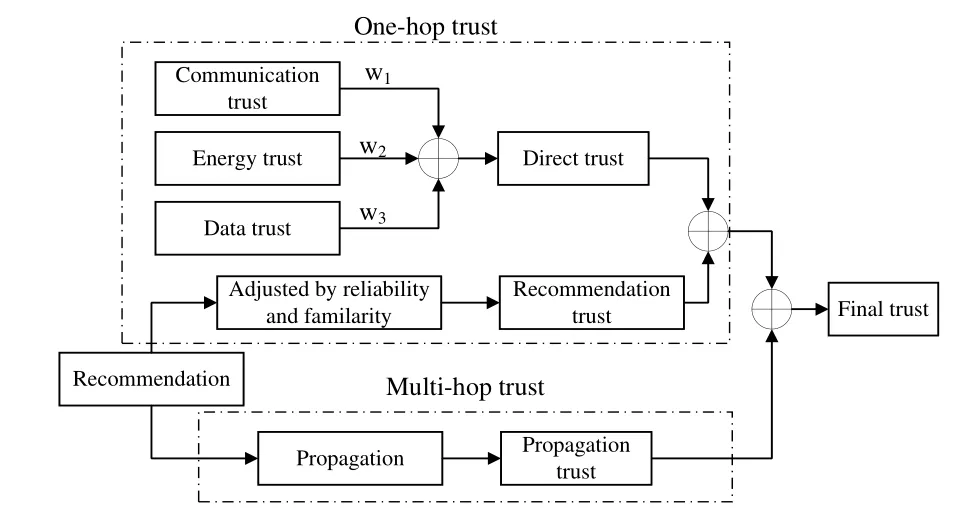
Figure 7.The structure of EDTM.
III.TRADITIONAL TT&C SECURITY
The traditional ground-based and space-based TT&C systems transmit data via the SGLs and the GEO satellite relays,which are mainly confronted with security threats of jamming, spoofing and eavesdropping on physical and data link layers[24].
Jamming refers to the scenario where a malicious jammer sends an interfering radio signal to occupy the channels and disable the reception of legitimate packets.In order to resist jamming attack, the spread spectrum technique is adopted, which includes frequency hopping spread spectrum (FHSS), direct sequence spread spectrum(DSSS),time-hopping spread spectrum (THSS), chirp spread spectrum (CSS), and combinations of these forms.Wanget al.[25] illustrated the characteristics on modulation mode,processing gain, spread bandwidth of different spread spectrum forms including FHSS, DSSS, THSS and CSS.And the resistance capacities for the narrowband jamming, single-tone jamming, multi-tone jamming and impulse jamming are analyzed.Gecgelet al.[26]proposed a jamming attack detection scheme for satellite telemetry and command communications based on machine learning which adopts a lightweight convolutional neural network.
Spoofing refers to the scenario where an adversary capture, alter, and retransmit a command packet in a way that misleads the recipient.Once established as a trusted user, the adversary may send false commands, causing the satellite to malfunction or fail its mission.Eavesdropping refers to the scenario where an adversary conducts an unauthorized real-time interception of TT&C communication.In order to resist the spoofing and eavesdropping attacks,the cryptography technique is adopted mainly for command authentication and telemetry encryption.In the 1980s, American Satellite Company adopted Data Encryption Standard (DES) to guarantee access to satellite command system merely for authorized ground station, which took the lead in incorporating DES-based command authentication system on commercial satellites [27,28].Consultative Committee for Space Data Systems(CCSDS)comprehensively recommended the encryption and authentication algorithms for TT&C communications.Specifically,the cryptographic key size and operation mode of encryption are elaborated;the hash message, cipher and digital signature based authentication algorithms are respectively demonstrated [29].Spinsanteet al.[30] numerically evaluated the command authentication and telemetry encryption scheme defined by the CCSDS standards.Considering the limited capacity of small satellites in the upcoming mega constellations, Sahaet al.[31] compared four commonly used cryptographic algorithms including Advanced Encryption Standard(AES),International Data Encryption Algorithm (IDEA), DES, Rivest-Shamir-Adleman (RSA), and a lightweight cryptographic algorithm of PRESENT.Performances on throughput,memory footprint efficiency,security and energy efficiency are compared, and eventually AES-128 is recommended as the cryptographic algorithm for small satellite TT&C.Murtazaet al.[32] presented a lightweight authentication and key sharing protocol for satellite TT&C communications.The reduction on the use of cryptographic algorithms and the number of messages exchanged makes the authentication protocol efficient in computational complexity, speed, and bandwidth utilization.
Apart from the above algorithms for particular security attacks, some scholars researched the TT&C security assessment system and the TT&C secure design guidelines.Fridet al.[33] proposed an assessment system for security level of satellite telemetry communications,which contains the module of attack graph building, the module for simulating intruder’s actions, etc.Ingolset al.[34] presented the guideline for securing the TT&C design and implement for small satellites.Ingolset al.[35] proposed a cryptographically-enforced role-based access control scheme that binds specific keys to specific rights on the satellite,so as to avoid dangerous command to be issued by a single person.
The existing researches on the traditional TT&C only consider the security issues on the physical layer and the data link layer.Since the SGL still serves as an indispensable part of the networked TT&C,the existing researches on the traditional TT&C are still applicable to the networked TT&C.However, the networked TT&C also relies on the intersatellite network for data transmission, which is rarely involved and considered in the traditional TT&C.Consequently there is rare existing relevant research on the network layer security of any TT&C system as far as we know.Therefore, we first investigate the existing researches on network layer security of satellite networks and terrestrial networks.And according to the characteristics of the networked TT&C, we analyze the deficiencies of the existing researches if they are migrated to the networked TT&C, and give further suggestions and perspectives to guide future in-depth researches.
IV.SECURE ROUTING
Different from traditional ground-based and spacebased TT&C, TT&C data is transmitted in the intersatellite network for networked TT&C.Therefore,secure routing should be guaranteed.Specifically,some security attacks should be considered as shown in Table 2 [36], which include eavesdropping, information tampering, identity forgery, information replay,routing packet dropping, routing packet selective forwarding, routing table overflow, black hole attacks,data packet selective forwarding, and path jamming[37].Different attacks degrade different aspects of network security including confidentiality, integrity,authentication, availability, timeliness, while undermine different routing processes including route discovery, data forwarding, and route maintenance.To ensure secure routing,basic secure routing algorithms based on encryption, digital signatures, MACs, hash chains,time stamps,multi-path routing algorithms and trust-based routing algorithms are widely used.
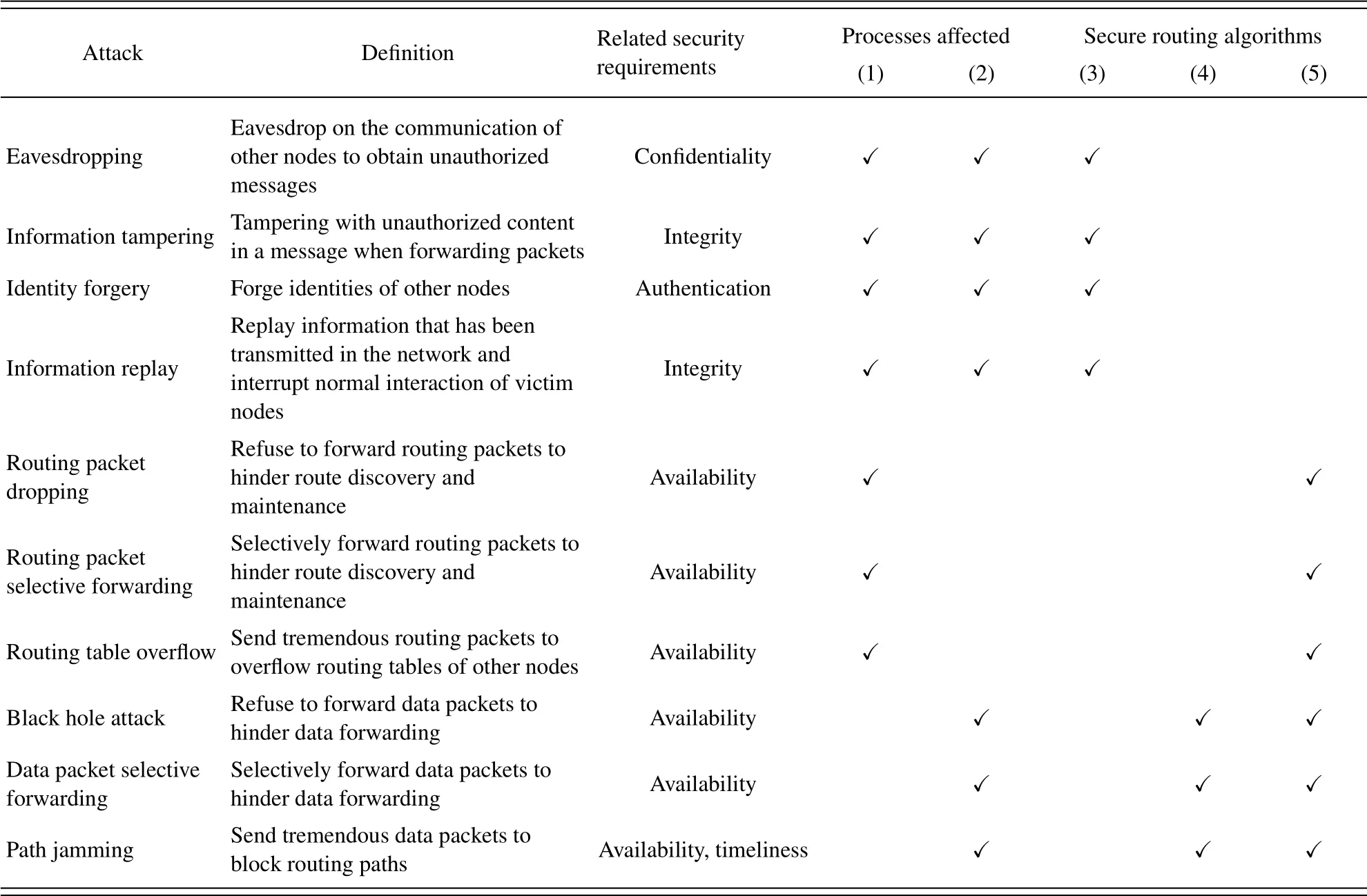
Table 2.Overview of routing attack.
4.1 Basic Secure Routing Algorithms
Basic secure routing algorithms refer to algorithms that use encryption, MACs, digital signatures,hash chains, and time stamps to protect the route from eavesdropping, information tampering, identity forgery, information replay and other attacks.The above security technologies have strong generality,which can not only be used in different routing algorithms but can also be used in processes of route discovery, data forwarding and route maintenance.Meanwhile, the multiple security technologies can also be flexibly combined according to specific security requirements to comprehensively protect routing security.
Yinet al.[38]discussed a three-layer satellite network composed of GEO, highly elliptic orbit (HEO)and LEO satellites and proposed a quality of service (QoS) guaranteed secure multicast routing protocol(QGSMRP).The algorithm uses hop-by-hop encryption to prevent routing packets from being eavesdropped and tampered and to prevent identities from being forged.In the process of routing packet forwarding,each intermediate node encrypts the packet using its private key.When receiving a packet, the current node uses the public key of the previous node to perform decryption.If the decryption fails,it is indicated that the packet has been tampered with or the identity of the previous node has been forged.Meanwhile,nodes that do not have access to the public key of other nodes cannot obtain the contents of the corresponding routing packets,thus preventing routing packets from being eavesdropped.
Huet al.[39]proposed a secure on-demand routing algorithm named Ariadne.The algorithm uses MACs to prevent messages from being maliciously tampered with and to protect the integrity of messages.Each intermediate node should attach a MAC to the forwarded routing packet.Suppose the sender and receiver share a pair of keys.The sender obtains the digest of the original message by the hash function and then encrypts the digest to derive the MAC.Similarly, the receiver first obtains the digest of the received message by the hash function and then encrypts the digest to derive the MAC.If the MAC of the received message is different from that of the original message, it is indicated that the received message has been tampered with.Meanwhile,if the pair of keys are not allocated in advance,they can be attached to the forwarded packet for verification of the corresponding MAC.
Sanzgiriet al.[40]proposed the authenticated routing for ad hoc networks (ARAN).When the routing packet is forwarded, each intermediate node needs to attach its own digital signature.The source node first uses a hash function to obtain the abstract of the original message and then derives a digital signature through private key encryption.Any node in the network that can obtain the public key can verify the message.First,the hash function is used to obtain the digest of the received message, and then the public key is used to decrypt the digital signature to obtain the digest of the original message.If the digest of the received message is different from that of the original message,it is indicated that the received message has been tampered with or the identity of the source node has been forged.
Manelet al.[41]proposed the secure ad hoc on demand distance vector routing(SAODV).SAODV uses the hash chain to verify hop counts of routing packets.The hash functionHis a one-way function and it is difficult to carry out reverse calculation.For the hash chainh0,h1,...,hN,we havehi=H[hi+1].A routing packet carries a hash value initially set ashN.Each time the packet is forwarded, one hash function operation is performed on the hash value.Assume that the current hash value in the routing packet ishN-2,and hash value verification is performed ash0=HN-2[hN-2].According to operation times of hash functions,the current hop count isN -(N -2)=2.Due to the unidirectionality of the hash function, hop counts can be prevented from being tampered with.
For the abovementioned secure routing algorithms,including QGSMRP based on encryption, SAODV based on hash chains, Ariadne based on MACs, and ARAN based on digital signatures, routing messagesof these algorithms are attached with time stamps.The time stamp records the message sending time.If a message is beyond the valid period,it will be discarded to prevent information replay attacks.
A comparison of secure routing technologies including encryption, MACs, digital signatures, hash chains,time stamps is shown in Table 3.
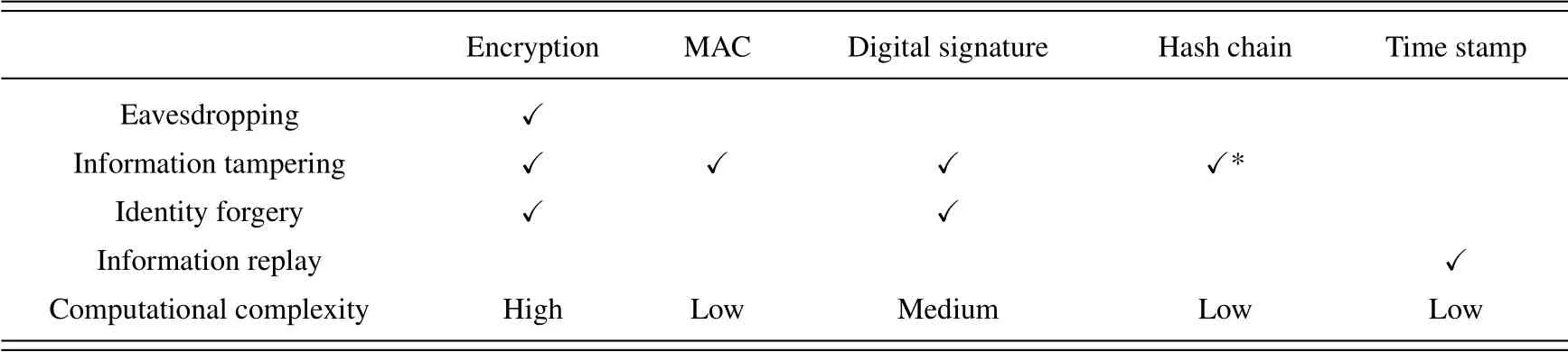
Table 3.Comparison of basic secure routing technologies.
4.2 Multi-Path Routing Algorithms
Black hole attack, data packet selective forwarding,and path jamming are prone to bring the risk of path failure.In order to improve the failure-resistence of routing,the multi-path routing algorithm uses multiple paths to transmit data.Specifically, multi-path routing algorithms are classified into backup multi-path routing, traffic distribution based multi-path routing,and stochastic multi-path routing according to different ways of path utilization.
The backup multi-path routing selects multiple unrelated paths to reduce the risk of simultaneous failure of the paths.[42-45]focus on selecting the most unrelated multiple paths in space.Rostamiet al.[42]proposed an algorithm based on ant colony optimization to find the two shortest and maximally shared risk link group disjoint paths,thereby minimizing the risk of simultaneous failure of paths.The algorithm is divided into three parts: graph transformation, paths discovery, and graph reverse transformation.In the WSN many-to-one communication scenario, the onehop neighbor node of the sink node is called the root node,and the two-hop neighbor node is called the subroot node.When it is difficult to find a completely node-disjoint path, the Sub-branch Multi-path Routing Protocol (SMRP) proposed by Challalet al.[43]relaxes the restriction of path coupling,and uses paths with the same root node but different sub-root nodes for multi-path routing.The Split Multi-path Routing (SMR) proposed by Leeet al.[44] is an on-demand routing mechanism.On the basis of obtaining the shortest delay path,SMR takes the path which is maximally disjoint with the shortest delay path as a backup, thereby improving the failure-resistence, and reducing the overhead and delay caused by rerouting.The jamming-resilient multi-path routing proposed by Pu [45] selects the two paths with the largest spatial distance between nodes on the basis of comprehensively considering the link quality and traffic load of the paths.JarmRout has better performance than traditional algorithms in terms of packet delivery rate and packet transmission delay.The maximally nodedisjoint,edge-disjoint paths and paths with the largest spatial distance between nodes improve the robustness of routing by reducing the paths’ spatial correlation.Mustafaet al.[46]select a group of fault-independent paths with the smallest simultaneous failure probability based on the path availability history, so as to ensure the end-to-end availability to the greatest extent.
The traffic distribution based multi-path routing optimizes the traffic distribution ratio of different paths,so as to minimize the traffic affected by path failure.Tagueet al.[47] modeled path failure as a random process, and optimized the flow distribution of source nodes to avoid attacks and maximize network throughput.The traffic allocation problem is modeled as a lossy network flow optimization problem based on portfolio selection theory.The distributed secure multi-path routing algorithm proposed by Leeet al.[48]minimizes the throughput loss when subjected to single-link attacks by optimizing the flow distribution ratio of the paths,and uses lexicographic optimization to solve multi-link attacks, thereby increasing the required resources that the attacker needs to destroy the route.
The stochastic multi-path routing stochastically transmits data on different paths, and selects the optimal strategy to avoid the failed paths.Sarkaret al.[49]proposed a secure and energy efficient stochastic(SEES)multi-path routing algorithm.The path selection of different time slots is modeled as Markov decision process and the randomness of path selection reduces the impact of path failure.Sarkaret al.[50]proposed a random multi-path routing algorithm based on zero-sum game.At each decision stage,the source node determines the optimal path and path switching strategy based on the available path, the remaining bandwidth of the path, and the attacker’s strategy, so as to avoid the attacked path to the greatest extent to ensure data transmission security.Comparison of the multi-path routing algorithms is shown in Table 4.
4.3 Trust-Based Routing Algorithms
Traditional routing algorithms often consider delay,hop counts and other performance factors when selecting the optimal route.Trust-based routing algorithms estimate the trust degree by observing the behavior of network nodes and consider trust degrees as a factor for path selection.The higher the trust degrees of nodes on the path are,the more likely is the path to be selected.Alternatively,if the trust degree of a node is lower than a certain threshold,it will be isolated by the network.
Liet al.[51]adopted the strategy of static configuration and dynamic adjustment to adjust the route automatically when the network topology changes.The trust degree is evaluated according to routing packet forwarding rate, data packet forwarding rate and aggressive behavior.Panet al.[52] evaluated the trust degree according to the RREP and RREQ forwarding rates, and adopted the sliding window mecha-nism to guarantee the low computing overhead and the timeliness of trust evaluation.Eventually the optimal path with low delay, light traffic and high trust is selected.Yuet al.[53] combined the trust mechanism and the authentication mechanism to design a routing algorithm for multi-layer satellite network.For trust evaluation, routing packet forwarding rate and abnormal behavior are mainly considered.Wanget al.[54] proposed the lightweight trust-based QoS routing algorithm (TQR).TQR adopts a hybrid trust mechanism combining direct trust and recommendation trust, where the direct trust degree is evaluated according to data packet forwarding rate and the overall trust is the weighted sum of the direct trust degree and the average recommendation trust degree.The optimal path is selected by comprehensively considering the trust degrees and the path delay,which guarantees the security and satisfies the QoS requirement.Dinget al.[55]embedded the trust mechanism into AODV routing,and evaluated the trust degree according to attacking behavior,forwarding behavior and residual energy.If the trust degree of node A evaluated by node B is lower than a certain threshold,it would be reevaluated according to the trust evaluation from node A’s neighbor nodes,which improves the robustness of the trust mechanism.Caiet al.[56] designed a centralized trust evaluation mechanism and the trust degree of each node is evaluated comprehensively by all its neighbor nodes,which guarantees the impartiality and accuracy of trust evaluation.Meanwhile,load balancing mechanism is applied to prevent the high-trusted path from congestion while other paths remain idle for a long time.Comparison of[51-56]is shown in Table 5.
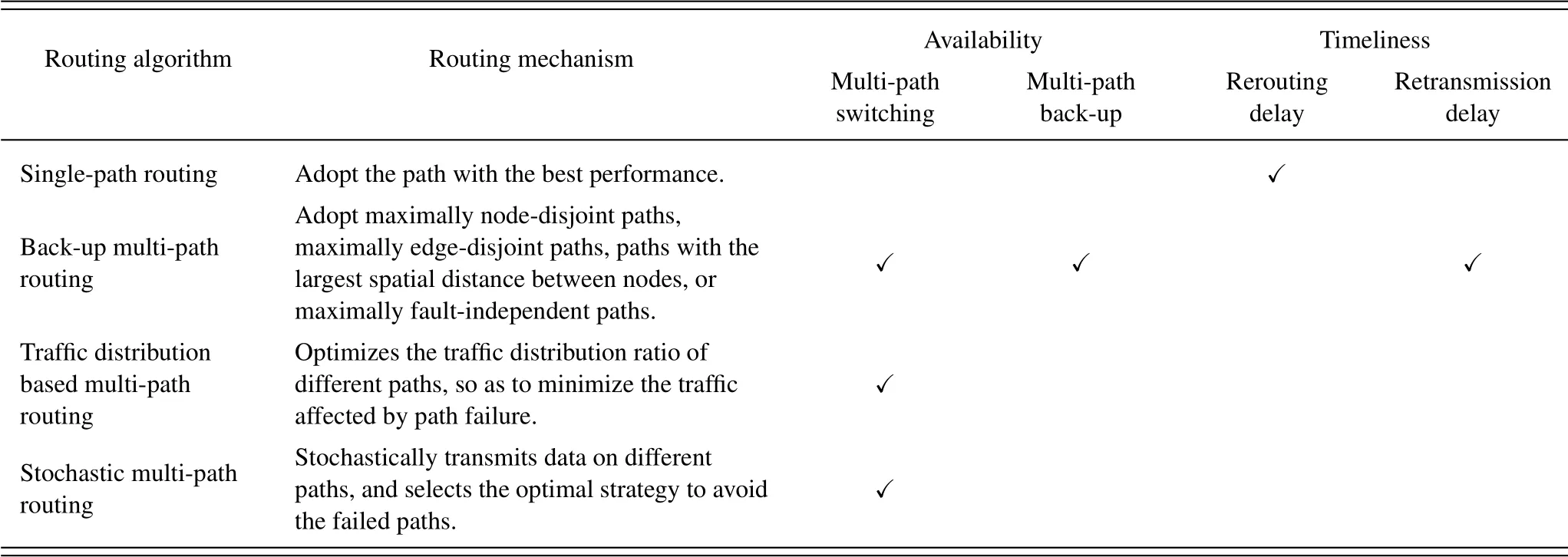
Table 4.Comparison of multi-path routing algorithms.
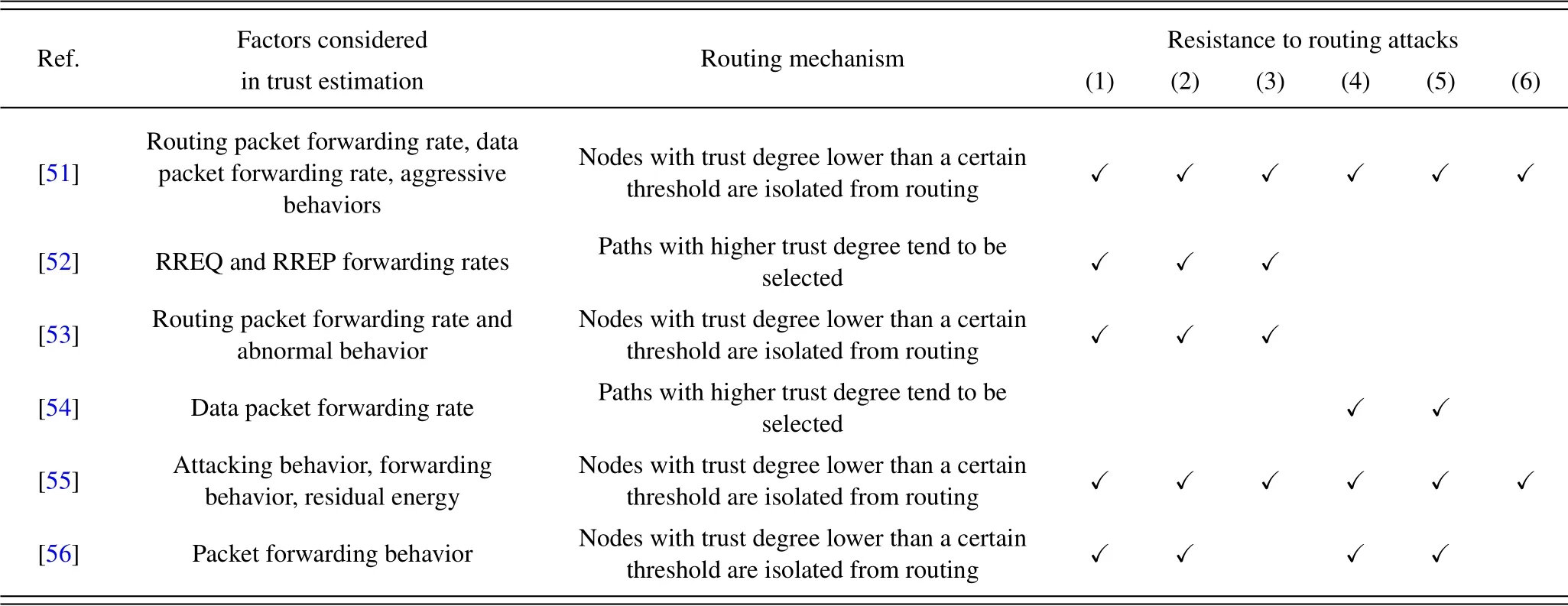
Table 5.Comparison of trust-based routing algorithms.
In fact, secure routing is only one of the applications of the trust mechanism, which is a larger topic.In addition to considering different node behaviors according to specific application scenarios,accurate estimation methods are also critical for trust mechanisms,which will be introduced in the Section V.
4.4 Security Perspectives for Networked TT&C
The basic secure routing algorithm, the multi-path routing algorithm and the trust-based routing algorithm complement each other and protect routing security comprehensively.The basic secure routing algorithm can resist eavesdropping,tampering,and forgery attacks,while the multi-path routing algorithm and the trust-based routing algorithm can resist disruption attack.For networked TT&C,security suggestions and future research directions are given as follows:
Multiple security technologies including encryption, MACs, digital signatures, hash chains, and time stamps should be combined.These security technologies protect routing from eavesdropping, tampering,identity forgery,information replay and other attacks,and ensure basic routing security.
Traditional single-path routing has a high risk of path failure, which is not enough to meet the ultrareliability requirements of TT&C.From the perspective of failure tolerance, multi-path routing uses multiple paths to transmit data,which improves the relia-bility of routing.Although multi-path routing avoids the problem of rerouting caused by path failure,due to the long transmission delay of the ISL, when the active path fails, multi-path routing needs to retransmit the lost data on other backup paths.The introduced retransmission delay reduces the timeliness of TT&C.A possible solution to further improve the timeliness of TT&C is to introduce data redundancy and transmit data copies on multiple paths simultaneously.When part of the paths fail, the receiver can still use the redundant data transmitted on the normal paths to recover the original data,thereby avoiding the introduction of retransmission delay.Based on this idea, we have designed a failure-tolerant and low-latency redundant multi-path routing algorithm, and have verified that our proposed algorithm outperforms the traditional routing algorithms in reliability and timeliness[57].
The trust-based routing algorithm needs to consider the trust degree on transmission delay.In networked TT&C, due to high ISL delay and high timeliness requirement of TT&C information, malicious nodes may deliberately increase the transmission delay of TT&C information,thus destroying information timeliness.Therefore, trust estimation should particularly consider the behaviors on transmission delay.
V.TRUST MECHANISMS
Traditional ground-based and space-based TT&C support small-scale constellations with a few satellites,which means that cooperation among satellites can not be utilized for security protection.In contrast,the intersatellite network enables networked TT&C to realize mutual monitoring within the mega-constellation.In this way,abnormal and malicious behaviors can be cooperatively detected, and accordingly trust degrees for each satellite can be evaluated and propagated so as to form a secure network environment with trust mechanism.
In this section, trust mechanisms for traditional communication system will be introduced.Particularly, the direct trust mechanism provides a simple trust estimation method,while the indirect trust mechanism introduces trust recommendation and multi-hop propagation that improve utilization of observation information of network nodes’behaviors to realize more accurate trust estimation[58].Meanwhile,some other issues,such as trust metrics and trust aggregation,also have a significant impact on the accuracy of trust estimation.
5.1 Basic Trust Mechanisms
The direct trust mechanism only considers trust in the range of a single hop obtained by direct observation and does not consider the mutual trust recommendation.Specifically, a node uses its direct observation of other nodes’ behaviors to estimate trust degrees.Subsequently,direct trust mechanism serves as the primary trust mechanism that provides the basic monitoring of malicious behavior.Due to the limited observed information of a single node,estimation accuracy still needs further improvement.Particularly in the satellite network with dynamic topology changes,neighbor relationships between nodes are constantly changing such that a single node can only obtain limited observation data within a limited span of time, which consequently decreases trust estimation accuracy.However, the indirect trust mechanism based on trust recommendation and multi-hop propagation can estimate trust degrees more accurately.Hence the combination of direct trust and indirect trust is the most promising scheme for trust mechanism.
Indirect trust composes of recommendation trust and propagation trust.As shown in Figure 5,the node that evaluates the trust degrees of other nodes is defined as the subject node, the node whose trust degree is evaluated by other nodes is defined as the object node, and the node within the one-hop coverage of both the subject node and object node is defined as the recommender node.On the basis of evaluating the direct trust of the object node,the subject node comprehensively considers the direct trust of the recommender nodes to the object node,which is defined as the recommendation trust.For the subject node beyond the one-hop coverage of the object node, the trust can only be derived by multi-hop propagation.As shown in Figure 6,the forwarding node within the one-hop coverage of the object node directly evaluate the trust without propagation.Along the trust propagation path,the trust degree of the object node will be adjusted according to the trust degree of forwarding nodes on the next hop to the previous hop.
Asuquoet al.[59]designed a distributed trust mechanism for satellite mobility-aware DTN.The direct trust between nodes is determined by data forwarding rate and energy consumption rate.Due to the connection sparsity in DTN network, the subject node indirectly evaluates the trust of the object node that did not encounter before through the recommendation of other nodes.Specifically, based on the trust degree of the recommender node to the object node,the subject node determines the indirect trust degree comprehensively considering the recommendation credibility and familiarity.Analytical and experimental results presents that the trust mechanism can resist data dropping attacks and colluding attacks.
The efficient distributed trust model (EDTM) proposed by Jianget al.[60] comprehensively evaluates trust degrees from three aspects: direct trust, recommendation trust and propagation trust, as shown in Figure 7.For direct trust, EDTM considers communication trust based on the data forwarding rate, energy trust based on the energy consumption rate and data trust based on the data value distribution.For recommendation trust, EDTM considers the trustworthiness of recommendation messages and the familiarity of recommender nodes to object nodes to adjust the recommendation trust degrees from different recommender nodes.For the subject node and the object node within a single hop,the one-hop trust degree is a weighted sum of the direct trust degree and the recommendation trust degree.For the subject node and the object node beyond a single hop, the multi-hop trust degree is derived from trust propagation.The trust degree propagated along the chain needs to be adjusted according to the reliability of each intermediate node.
EDTM comprehensively considers direct trust,recommendation trust and propagation trust, which has excellent performance among current mainstream trust mechanisms.However, some trust calculation methods of EDTM are still relatively simple.Based on the basic architecture of EDTM, Zhanget al.[61] improved the calculation details and proposed the distributed and adaptive trust evaluation approach(DATEA).For communication trust, DATEA introduces the aggregate reputation model on the basis of subjective logic and uses trust degrees of multiple historical moments to obtain the trust degree of the current moment.For single-hop trust, EDTM calculates the weighted sum of direct and recommendation trust degrees, but no detailed method is given for determining the weights, whereas DATEA introduces the concept of node activity.Specifically, the higher the node’s activity is, the higher the weight of the node’s trust is.For trust updating,EDTM only considers trust at current and previous moments,while DATEA takes the weighted average of trust degrees at current and multiple historical moments as trust degree prediction at the next moment, and the weights are determined by the induced ordered weighted averaging algorithm.Due to its more complete trust calculation methods,DATEA has better performance than EDTM in trust estimation and malicious attack detection.
[59-61] introduce trust recommendation and propagation mechanisms that make full use of observation information from different nodes,enhance the reliability and robustness of trust estimation,and obtain better performance than that of the direct trust mechanism.Table 6 compares the above trust mechanisms.
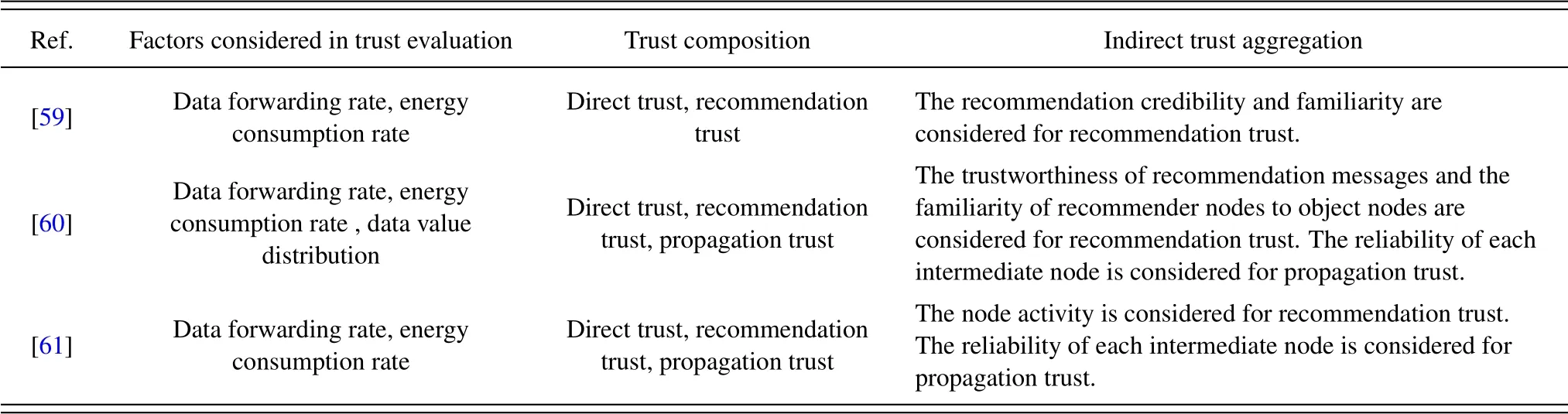
Table 6.Comparison of basic trust mechanisms.
5.2 Trust Metrics
The trust degree is generally calculated based on the statistical information of node behaviors.Bayesian inference regards the trust degree as a random variable satisfying a Beta distribution or a Dirichlet distribution,and estimation of the trust degree is the distribution expectation.However, confidence levels of trust estimation depend on historical data volume of node behaviors.The concept of uncertainty is introduced in subjective logic,which not only estimates the trust degree but also determines the uncertainty of estimation.
Bayesian inference regards the trust degree as a random variable satisfying a certain distribution, and the parameters of the distribution function will be updated as statistical information is accumulated.For calculation of binary trust,the trust degree is regarded as a Beta distribution random variable in the interval[0,1].Without any prior information about node behaviors,the Beta distribution degenerates to a uniform distribution in the interval [0, 1].Bayesian estimation of the trust degree is the expectation of the Beta distribution as
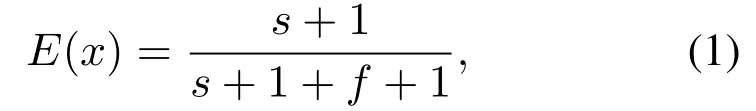
wheresis the number of observed normal behaviors,fis the number of observed abnormal behaviors.
Denoet al.[62] obtained the Beta distribution by combining the number of normal behaviorssand abnormal behaviorsfobserved by the subject node,and the number of normal behaviorssrand abnormal behaviorsfrobserved by recommender nodes.Finally,the distribution expectation is derived as the estimated trust degree as
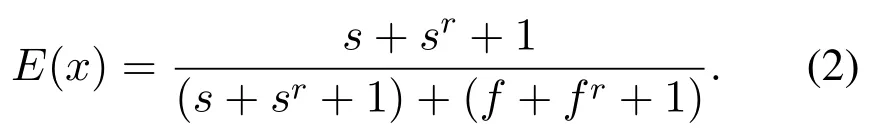
The basic idea of Ganeriwalet al.[63] for trust estimation is consistent with that of Deno, except that behavior informationsr,frobtained from recommender nodes needs to be adjusted according to the subject node’s trust degrees to recommender nodes.Thirunarayanet al.[64]generalized the Beta distribution in the multidimensional situation and proposed a Bayesian inference method based on the Dirichlet distribution for multivalue trust computing.With the accumulation of observed behavior information,the parameters of the Dirichlet distribution are updated.
The traditional single-dimension metric for measuring trust is simple and intuitive, but it cannot reflect the confidence level of trust estimation.Generally,a large data sample has a high confidence level for trust estimation, while a small data sample has a low confidence level.The concept of uncertainty is introduced by subjective logic, which estimates trust degrees more thoroughly and reflects the characteristics of human’s subjective cognition.
Josanget al.[65] used the quaternary variable(b,d,u,a) to measure trust degrees, which satisfiesb+d+u= 1, wherebis the trust degree,dis the distrust degree,uis the uncertainty degree,ais the trust degree without prior information, and the final trust degree isb+au.
Wanget al.[66]proposed a subjective logic-based method to evaluate the trust of binary events containing original evidence information.Consider the binary event〈r,s〉withrpositive results andsnegative results, whose certainty isc=c(r,s).Then, the trust degree of the binary event is estimated as follows:
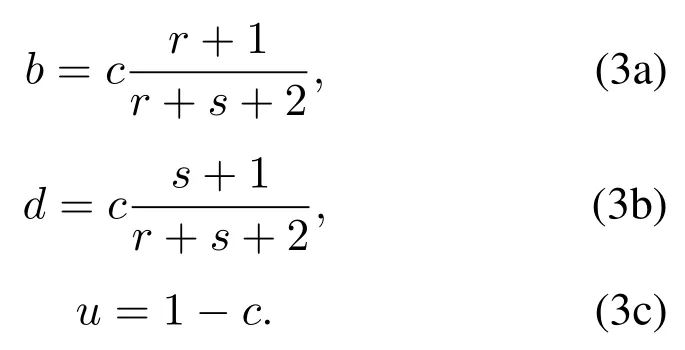
Zhanget al.[61]estimated the trust degree by evaluating the success data forwarding rate.Suppose the number of successful forwarding packets issand the number of unsuccessful forwarding packets isf;then,the trust degree is estimated as follows:
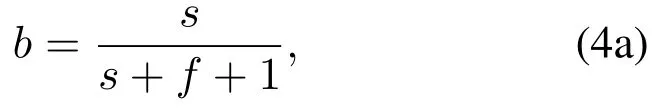
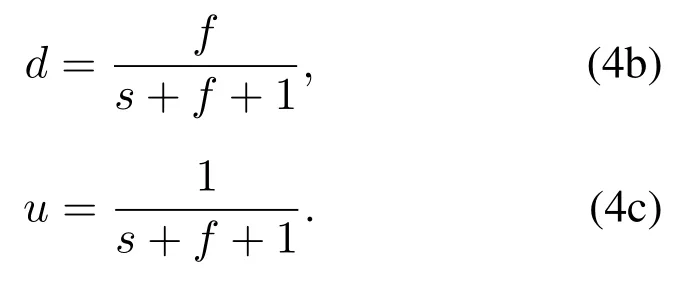
The uncertainty decreases with the increase of the sample sizes+f, which reflects the influence of the sample size on estimation confidence.
5.3 Trust Aggregation
Trust aggregation refers to the process of aggregating multiple trust degrees into one trust degree, including aggregating trust degrees obtained from different types of observation information and trust degrees provided by different nodes.The method of the weighted sum realizes the simplest and most direct trust aggregation by setting different weights to trust degrees and performing summation operations.However, the weighted sum method is not suitable when the uncertainty of trust estimation and conflicting evidence of node behaviors exist.Therefore, fuzzy logic and D-S evidence theory are introduced to achieve trust aggregation.
For recommendation-based trust mechanisms, the subject node needs to aggregate recommendation trust degrees from multiple recommender nodes.The weighted sum is often the simplest and most direct method.Wanget al.[54]took the average of recommendation trust degrees from all recommender nodes as the total recommendation trust degree.Tormoet al.[67] took the weighted sum of recommendation trust degrees as the total recommendation trust degree.Specifically, the weight of the recommendation trust degree from each recommender node is determined according to the following parameters: First,the subject node’s trust degree to the recommender node.Generally, the weight is positively proportional to the trust degree.Second, the similarity between the subject node and the recommender node.Usually,the weight is positively proportional to the similarity.Tormoet al.[67] evaluated similarity based on service preference and recommendation behavior.Chenet al.[68]evaluated similarity from three aspects: friendship similarity, social contact similarity, and community of interest similarity.
Fuzzy logic imitates the uncertain concept judgment and reasoning thinking mode of human brains,applies fuzzy sets and fuzzy rules to reasoning, and solves regular fuzzy problems that are difficult to address by conventional methods.Traditional Boolean logic belongs to binary logic, which is used for deterministic logic reasoning.Fuzzy logic belongs to multivalue logic, which is used for uncertain logic reasoning.Fuzzy logic uses linguistic variables and membership functions to measure trust.
Rajeswariet al.[69] proposed a routing trust estimation method based on fuzzy logic.The method consists of three steps: fuzzification,fuzzy inference and defuzzification.In the process of fuzzification, deterministic metrics of node residual energy and link reliability are fuzzified into fuzzy logic metrics of three linguistic tags: lower,average and higher.In the process of fuzzy inference, the fuzzy logic metric of the trust degree for each path is obtained based on fuzzy inference rules.In the process of defuzzification, the fuzzy logic metric of the trust degree for each path is transformed into a deterministic metric to realize the evaluation of the path trust degree.
Heet al.[70] proposed an adaptive trust mechanism based on fuzzy logic that is suitable for a variety of wireless networks.The mechanism uses a multicriteria fuzzy decision-making model.First, the model determines the trust factors that need to be considered,such as the initial trust degree,the direct trust degree,the indirect trust degree,the forgetting factor,the network environment and so on.Then, fuzzy linguistic variables are used to measure the degree of interaction between factors,and the influence matrix between factors is obtained.Finally, the weight of each factor is calculated by matrix operations.
Dempster-Shafer evidence theory,also known as DS theory,is a complete theory dealing with uncertainty.The Dempster composition rule can fuse and aggregate trust degrees of multiple entities[71].
Fenget al.[72]proposed the node behavioral strategies banding belief theory of the trust evaluation algorithm (NBBTE).Observing behaviors of nodes in wireless sensor networks, NBBTE evaluates the trust degree according to multiple factors.Then, the trust degree is transformed into a fuzzy metric in the trust space containing four cases of the evidence hypothesis as empty,trusted,untrusted and uncertain.Recommendation trust degrees from different recommender nodes are aggregated using the Dempster composition rule.Meanwhile,Dempster composition rule is modified to enable aggregation of direct and indirect trust degrees.
Sunet al.[73] proposed the D-S evidence theorybased trust ant colony routing algorithm (DSTACR).To relieve the impact of the evidence conflict between different nodes, DSTACR uses D-S theory to aggregate different evidences, which enhances the reliability of trust estimation.DSTACR regards the trust degree as a heuristic function and takes it as the consideration factor of routing selection and realizes the ant colony routing algorithm with high robustness.DSTACR can effectively identify and isolate malicious nodes in the network, which stabilizes routing performance under malicious attacks.
5.4 Security Perspectives for Networked TT&C
The direct trust only adopts direct observation information to evaluate the trust degree, which is easy to implement.However, the relatively insufficient observation information reduces the accuracy of trust evaluation.The indirect trust adopts indirect observation information to evaluate the trust degree,which has higher complexity.Specifically,fuzzy logic is required for uncertain judgement and D-S theory is required for combining contradictory information.However, the sufficient observation information improves the accuracy of trust evaluation.For networked TT&C,security suggestions and future research directions are given as follows:
Direct trust,recommendation trust and propagation trust should be comprehensively considered.Concerning networked TT&C,satellites are densely connected by ISLs.Therefore, recommendation trust and propagation trust can be easily transmitted and derived.However,the ISL connections among satellites are periodic and intermittent, which means direct trust can not be derived completely throughout the orbital period.Therefore, the recommendation trust and propagation trust necessarily complement the trust evaluation of direct trust.
The data forwarding delay should be considered in trust estimation.Due to high ISL delay and high timeliness requirement of TT&C information, malicious nodes can destroy the timeliness of TT&C information by deliberately increasing the data forwarding delay.Especially in emergency situations, the undermined timeliness may cause severe consequences like satellite collision accidents.Therefore,the data forwarding delay should be considered to distinguish and isolate malicious nodes.
Considering the predictable topology dynamics of the satellite network and different connecting duration among satellites,uncertainty should be introduced to estimate and aggregate trust degrees.The confidence level of trust estimation is greatly affected by the amount of behavior observation samples.For networked TT&C,satellites have fixed orbits and the constellation topology is periodic, which means the connecting duration among satellites can be precisely predicted.The longer the intersatellite connection is,the more certain the trust estimation achieves.Consequently,the trust degrees that are more certain should be designed with higher weights for trust aggregation.
VI.CONCLUSION
As the size of satellite constellations keeps expanding,the traditional ground-based and space-based TT&C systems are confronted with great challenges.In order to support TT&C for mega-constellations,this paper has proposed networked TT&C,which has low resource requirements for mega-constellation, achieves full-time communication between satellite and TT&C station, and has low transmission delay.Compared with the traditional ground-based and space-based TT&C systems, this paper has illustrated the system characteristics and security requirements of networked TT&C.Accordingly,new security challenges and opportunities for networked TT&C have been illustrated as secure routing and trust mechanisms.For each security issue, this paper has investigated the current researches on traditional terrestrial and satellite networks.Finally, security perspectives to guide future researches have been delivered with consideration on system characteristics and security requirements of networked TT&C.
ACKNOWLEDGMENT
This work was supported by the National Natural Science Foundation of China under Grant 61971261/62131012 and Technology Project of the State Grid Corporation of China under Grant 5400-202255158A-1-1-ZN.
- China Communications的其它文章
- GUEST EDITORIAL
- Reducing Cyclic Prefix Overhead Based on Symbol Repetition in NB-IoT-Based Maritime Communication
- Packet Transport for Maritime Communications:A Streaming Coded UDP Approach
- Trajectory Design for UAV-Enabled Maritime Secure Communications:A Reinforcement Learning Approach
- Hybrid Satellite-UAV-Terrestrial Maritime Networks:Network Selection for Users on A Vessel Optimized with Transmit Power and UAV Position
- Energy Harvesting Space-Air-Sea Integrated Networks for MEC-Enabled Maritime Internet of Things

