Novel Private Data Access Control Scheme Suitable for Mobile Edge Computing
Wei Liang,Songyou Xie,Jiahong Cai,Chong Wang,Yujie Hong,Xiaoyan Kui
1College of Computer Science and Electronic Engineering,Hunan University,Changsha 410082,China
2School of Computer Science and Engineering,Hunan University of Science and Technology,Xiangtan 411201,China
3School of Computer Science and Engineering,Central South University,Changsha 410083,China
Abstract:efficient response speed and information processing speed are among the characteristics of mobile edge computing(MEC).However,MEC easily causes information leakage and loss problems because it requires frequent data exchange.This work proposes an anonymous privacy data protection and access control scheme based on elliptic curve cryptography(ECC)and bilinear pairing to protect the communication security of the MEC.In the proposed scheme,the information sender encrypts private information through the ECC algorithm,and the information receiver uses its own key information and bilinear pairing to extract and verify the identity of the information sender.During each round of communication,the proposed scheme uses timestamps and random numbers to ensure the freshness of each round of conversation.Experimental results show that the proposed scheme has good security performance and can provide data privacy protection,integrity verification,and traceability for the communication process of MEC.The proposed scheme has a lower cost than other related schemes.The communication and computational cost of the proposed scheme are reduced by 31.08% and 22.31% on average compared with those of the other related schemes.
Keywords:mobile edge computing(MEC);privacy protection;access control;anonymous authentication
I.INTRODUCTION
Mobile edge computing(MEC)is a decentralized computing architecture that collects,calculates,and transmits data through data nodes deployed at the edge of the network[1].Edge computing changes the traditional calculation method of the central node[2].This mechanism reduces the computing pressure of the central node by dividing a complete computing task into multiple parts and computing and aggregation by the edge device node.Edge devices have faster calculation and transmission speeds when processing data because they are closer to the data source,thereby reducing system delays and network bandwidth occupancy.
With the continuous expansion of the scale of the Internet of Things(IoT),computing delays and difficulties in data collection have become one of the problems faced by the IoT technology[3].Traditional central computing and cloud computing solutions can no longer meet the requirements of large-scale IoT for data computing and security[4].A new security option is to use the MEC technology to enhance the security and privacy of the IoT.MEC can provide faster response speed and improve the resource utilization of the IoT.
As shown in Figure 1,the development of MEC has enriched the scale and application scenarios of the IoT technology.By combining the IoT technology,MEC devices can collect,process,and label data conveniently and quickly.Edge computing is defined as any computing behavior that occurs between data processing centers and data sources.For example,smart me-ters are network edge devices between power grid data centers and users, and mobile phones are network edge devices between consumers and data clouds.Edge devices are mostly IoT devices.These edge devices are data generators,such as temperature sensors,smart alarm clocks,and smart routers.Edge devices also generate massive amounts of data with the expansion of the IoT scale.These data reflect the daily behavior of users and can provide users with more humanized services by analyzing these data.However,frequent data collection methods put the privacy of users at risk of leakage.If these data cannot be safely calculated,stored,and transmitted,then users and the system may suffer serious consequences.
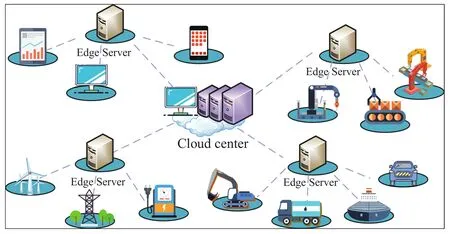
Figure 1.Mobile edge computing structure in the IoT.
The most common attack threats in the IoT are often concentrated at the edge of the network.Edge devices that lack good protection frequently become the main targets of attackers because IoT sensors are deployed at the edge of the network.An information sharing and transmission mechanism exist between devices in the IoT[5].This process frequently occurs in a public channel,and an attacker can intercept the information transmitted on the public channel.If secure access control and privacy data encryption mechanisms cannot be provided,then this information will be leaked.
This paper proposes a private data encryption and access control scheme suitable for the MEC environment based on ECC and bilinear pairing to address the security problems of data communication and encryption in MEC facilities.The main contributions of this paper are as follows:
·The scheme proposed in this paper verifies the freshness of each round of conversation through timestamps and random numbers.
·The private information of the proposed scheme is only available in the public cloud center(PCC),and the edge devices cannot know the specific information,thereby protecting the security of private data.
·Compared with other schemes,the communication and calculation costs of the proposed scheme are reduced by 31.08% and 22.31% on average,respectively,because ECC has the characteristics of small storage space and fast calculation speed.
The remaining content of this paper is organized as follows:In Section II,we briefly introduce the recent research work of edge computing in the IoT environment.Section III proposes the anonymous access control scheme of this paper.In Section IV,we analyze and compare the security performance of the proposed scheme.Section V compares the cost of the proposed scheme with other schemes.Finally,Section VI concludes and prospects the paper.
II.RELATED WORK
At present,many access control technologies have been proposed to solve the problems of access authorization,data integrity,verification,and privacy protection in the IoT.Tonyali et al.[6]encrypted the data information of smart meters through fully homomorphic encryption and multi-party calculations;then they aggregated the encrypted data into the gateway in a hierarchical manner with aggregated smart meters.This solution divides the actual numerical information into polynomial calculation shares,and will not expose the specific numerical information of the smart meter from data collection to storage.At present,symmetric key algorithms are commonly used in IoT to encrypt information and conduct secure communications.However,this method is more difficult to manage key[6].Mahmood et al.[7]proposed a communication identity authentication and key agreement scheme based on elliptic curve cryptography(ECC).Abbasinezhad-Mood believed that the scheme of[7]cannot provide forward security and meet the security requirements of IoT in terms of security and privacy[8].Hence,Abbasinezhad-Mood et al.[8]designed an improved MEC communication authentication scheme,which solves the problem of insufficient security in[7]and effectively reduces communication overhead and complexity.
Kumar et al.[9]proposed to combine cloud environment and mobile edge network technology to provide real-time and powerful data collection and processing capabilities for IoT.Mahood et al.[10]proposed an identity-based anonymous key agreement scheme.In[10],the smart meter connects to the public network in an anonymous way through the distributed private key to realize a safe and reliable identity verification mechanism.Kumar et al.[11]proposed a new authentication scheme based on ECC and time credentials.The protocol preserves the demand response in the IoT and allows the establishment of a secret session key between the MEC device and the remote control center after authentication.However,Chaudhry et al.[12]believed that the scheme of[11]can only accommodate a smart meter,which is uncertain in the actual deployment process and lacks a secure authentication mechanism on the remote-control end.Chaudhry et al.[12]further proposed an identity verification and response management scheme based on ECC and edge computing.The scheme only requires two exchanges of information to complete the identity verification process.The current centralized data management model also makes the IoT face more security threats when dealing with attacks from attackers.Kang et al.[13]combined edge computing technology with vehicle networks,con figured vehicle network nodes as blockchain nodes,and protected data storage and sharing between edge computing networks through alliance blockchain.Li et al.[14]proposed a data encryption,aggregation,and decryption scheme suitable for MEC.In this scheme,the edge server(ES)verifies and aggregates the encrypted information of the terminal device(TD)through a bilinear pairing algorithm,and sends it to the cloud for decryption.This scheme has better scalability and lower implementation cost.Blockchain is a new and secure distributed ledger[15].Gai et al.[16]designed an edge data model based on a permissioned blockchain and used smart contracts running on the blockchain to construct a security protection strategy and use group signatures and secret authorization to protect users’private data.[16]uses blockchain technology and edge computing technology to solve the security and privacy issues in the smart grid and can meet the high-performance requirements of the smart grid.Zhao et al.[17]implemented a MEC privacy data aggregation scheme based on bilinear pairing.Scheme[17]not only preserves the privacy of uploaded data but also implements batch operations.However,the communication and calculation costs of this scheme are high.Therefore,it is essential to provide a secure and efficient access control scheme for the development of mobile edge computing.
III.THE PROPOSED SCHEME
3.1 Communication Framework
Figure 2 depicts that the communication framework of MEC consists of terminal device(TD),edge server(ES),and public cloud center(PCC).TD can collect,calculate and measure user information in IoT and send it to ES for further processing.ES will verify the collected information and send the verified information to PCC.
The proposed scheme is divided into five phases:system setup,registration,data encryption and sending,verification,and decryption ciphertext.System setup and registration phases take place in a secure environment that the attackers cannot launch attacks.Data encryption and sending,verification,and decryption ciphertext phases occur in a public environment that the attackers can launch attacks.PCC is respon-sible for devices registration and information management in MEC.In the proposed access control scheme,each TD needs to be registered in the PCC.
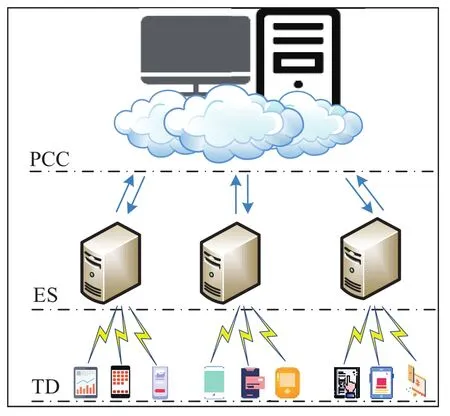
Figure 2.Communication framework.
3.2 System Setup
In this phase,PCCzgenerates system parameters{t,w,G,G1,e}through the secret parameter d,where t and w are two large prime numbers with d bits,G and G1are two cyclic groups of the order N=tw.Among them,e:G×G→G1has a bilinear mapping relationship and has the following characteristics:
·Bilinear:For ∀σ,ς∈ G,τ,υ ∈ ZN,there is e(στ,ςυ)=e(σ,ς)τυ.
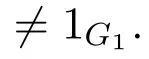
·Computability:For∀σ,ς∈ G,e(σ,ς)can be calculated.
Then PCCzchooses elliptic curve Ep(μ,ν),where the finite field is Fp,the subgroup G with prime order q of Ep(μ,ν)is selected by PCCz,and its base point is P.p is a large prime number,and that satisfies 4μ3-27ν20 mod p.PCCzselects the private key c∈Zq*and g∈G,then calculates KPCCz=cP as the public key.PCCzpublishes information{Ep(μ,ν),P,KPCCz}on public channel.Finally,we also define a hash function H:{0,1}*→G.The description of the proposed symbols is shown in Table 1.
3.3 Registration
In this phase,PCCzselects identity information IDj(j=1,2,...,n)for ESjand distributes private keys bj∈Zq*(j=1,2,...,n)and yesj(j=1,2,...,n)∈ (1,t)to ESj.Then,PCCzcalculates KESj=bjP and YESj=gyESj,where KESjis the public key information of ESj.ESjstores{YTDi,bj,yESj,KESj,h,IDj,IDi(i=1,2,...,m)}in the database.
PCCzdistributes IDi(i=1,2,...,m)to TDias the identity when TDiregistration.In addition,PCCzchooses yTDi(i=1,2,...,m)∈(1,w)and calculates YTDi=gyTDi.Finally TDisaves{yTDi,IDi}.
PCCzsaves{KPCCz,YESj,Ep(μ,ν),P,IDj(j=1,2,...,n)}in the database after completing registration.
3.4 Data Encryption and Sending
The specific implementation process of the proposed scheme is shown in Figure 3.
Step 1:TDi→ESj:M1={B1,B3,B4,B5,T1}
In this phase,TDi(i=1,2,...m)encrypts information and generates a corresponding signature,and then sends the information to ESj(j=1,2,...n).
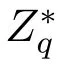
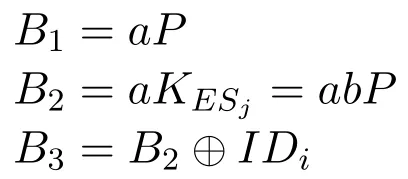
Then TDiuses the public key KPCCzof PCCzand the random number a to calculate the ciphertext of the information I:
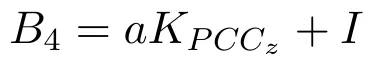
TDicontinues to calculate:
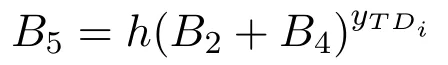
Finally,TDisends information M1={B1,B3,B4,B5,T1}to ESjfor verification.
3.5 verification
Step 2:ESjverifies TDi
After receiving the M1information,ESjgenerates a timestamp T2.If|T2-T1|≤ΔT,then ESjstarts the following calculations:
B6=bB1=baP
ID′i=B6⊕B3=baP⊕abP⊕IDi
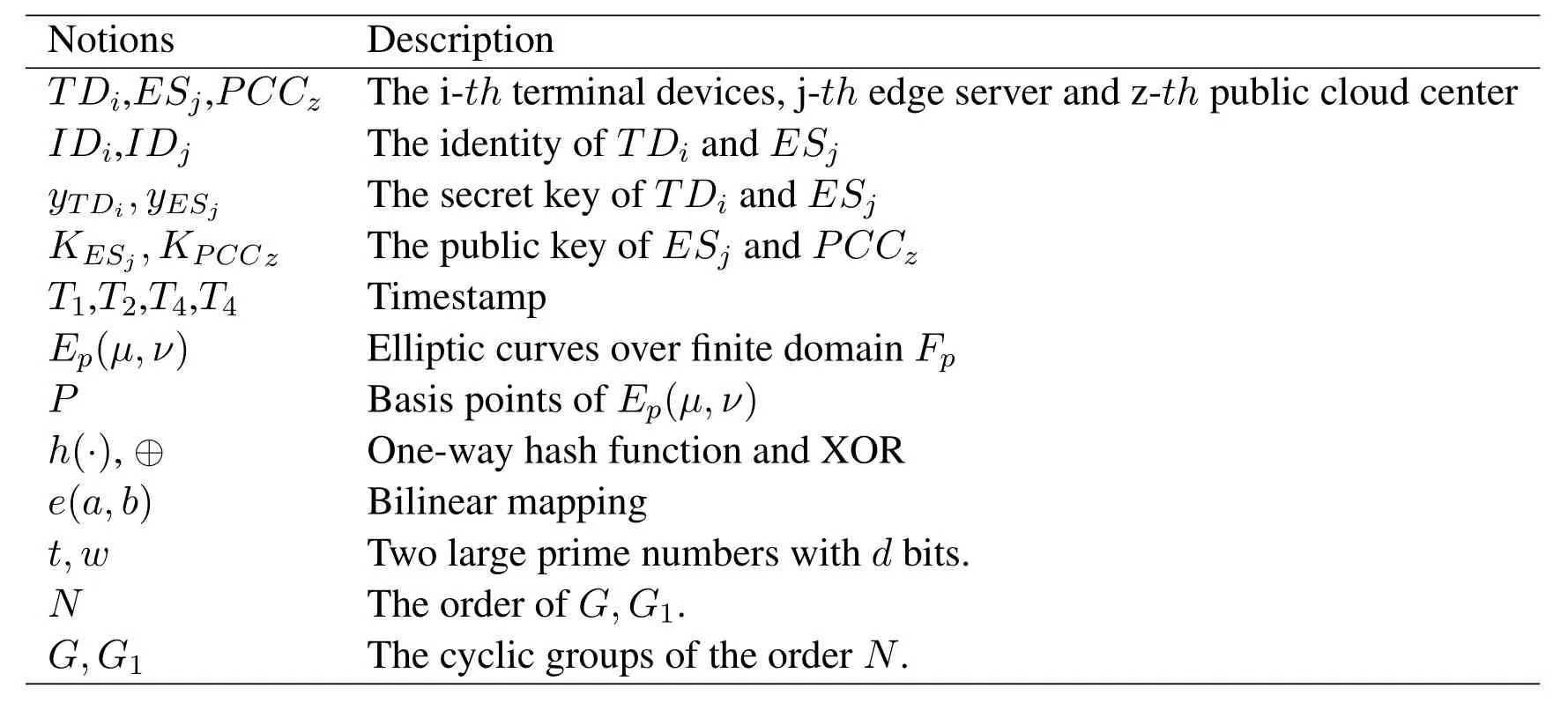
Table 1.Symbol description.
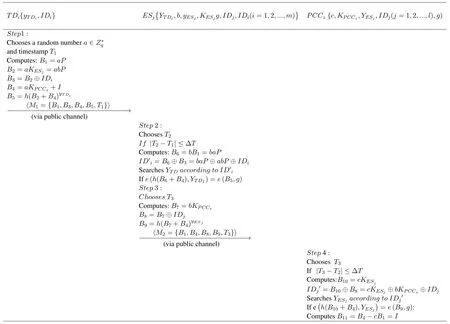
Figure 3.The implementation process of the scheme.
ESjfinds the corresponding key information YTDin the database according to the obtained IDi.ESjcalculates e(h(B6+B4),YTD).ESjverifies the effectiveness of the information M1={B1,B3,B4,B5,T1}through verification e(h(B6+B4),YTD)and e(B5,g)are equal.If the verification fails,the call will be terminated.
Step3:ESj→PCCz:M2{B1,B4,B8,B9,T3}
If ESjverifies e(h(B6+B4),YTD)=e(B5,g)successfully,ESjthen selects a timestamp T3and starts the following calculation:
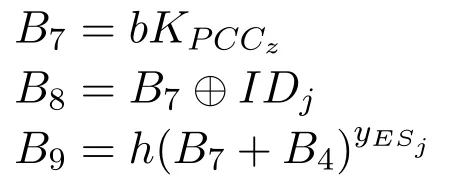
Finally,ESjsends information M2={B1,B4,B8,B9,T3} to PCCzfor verification and decryption of information I.
3.6 Decryption Ciphertext.
When receiving M2={B1,B4,B8,B9,T3},PCCzselects a timestamp T3.If|T3-T2|≤ΔT,PCCzstarts the following calculation:
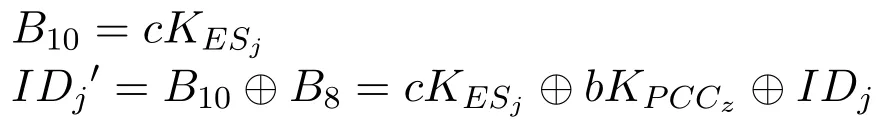
PCCzsearches the corresponding YESjaccording to IDj′.If e?h(B10+B4),YESj?=e(B9,g),PCCzverifies ESjsuccessfully.Then,PCCzcalculates B11=B4-cB1=I.Finally,the PCCzobtains information I.
IV.SAFETY ANALYSIS
In this section,we will analyze the security of the proposed private data access control scheme.
4.1 Formal Analysis
In this section,we will analyze the security of the proposed scheme through ProVerif.ProVerif is a formal protocol analytical tool that can find security problems in the protocol and verify the security of the key and correctness of the logic.ProVerif is widely used in protocol analysis and identity authentication fields.
The ProVerif notions are depicted in Table 2.In Figure 4,we also define the relevant parameters of the protocol such as ch and sch.ch represents a common channel in the normal communication process.sch represents the secret channel in the system setup and registration phases of the proposed scheme.We also define the base point P of the elliptic curve and the secret information I of the encoded TDi.Then we define the private key data yTDi and yEsj of TDi and ESj,respectively.KESj and KPCCz are the public key information of ESj and PCCz,respectively.We also define the related functions{h,xor,em,add,min,exp,bp}used in the scheme of this article.Finally,three queries are defined to inquire about the security of{I,yTDi,yESj}.
Figure 5 shows the ProVerif implementation process of TDiand ESjin the proposed scheme.
In Figure 6,the implementation process of PCCzis converted into the representation of ProVerif code.
Figure 7 shows the analytical results of ProVerif.The analytical results show that the{I,yTDi,yESj}information in the proposed scheme is safe in the communication environment defined by ProVerif.The attacker cannot obtain the value of{I,yTDi,yESj}from the attacker model defined by ProVerif.
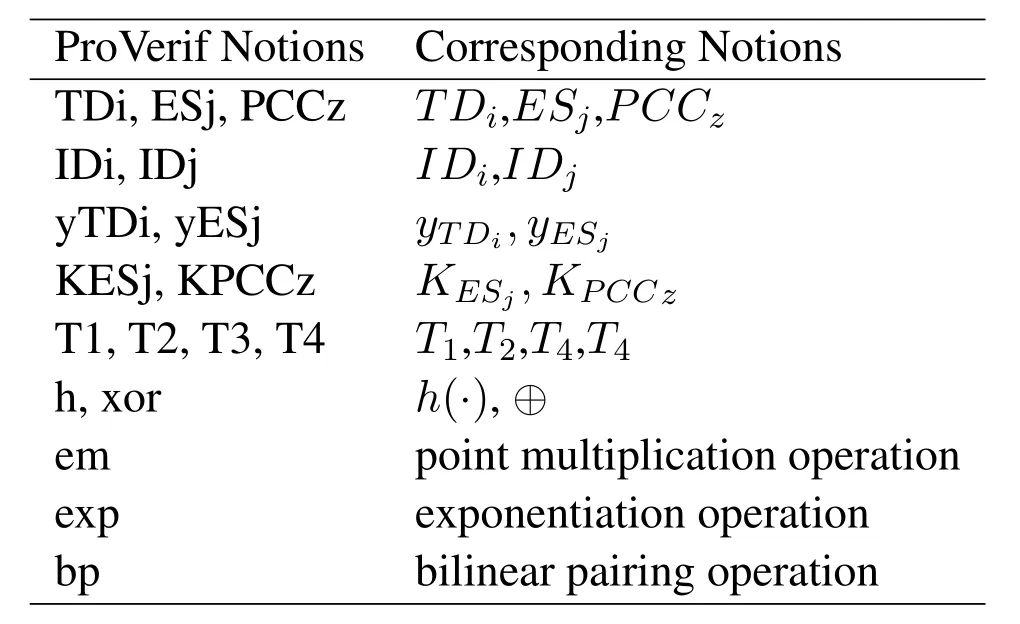
Table 2.The description of ProVerif notions.
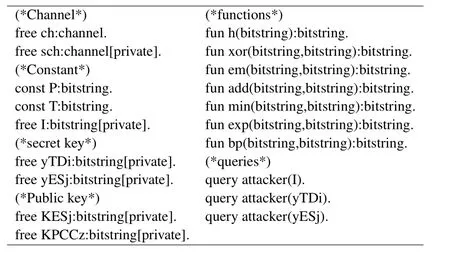
Figure 4.The code of Preset.
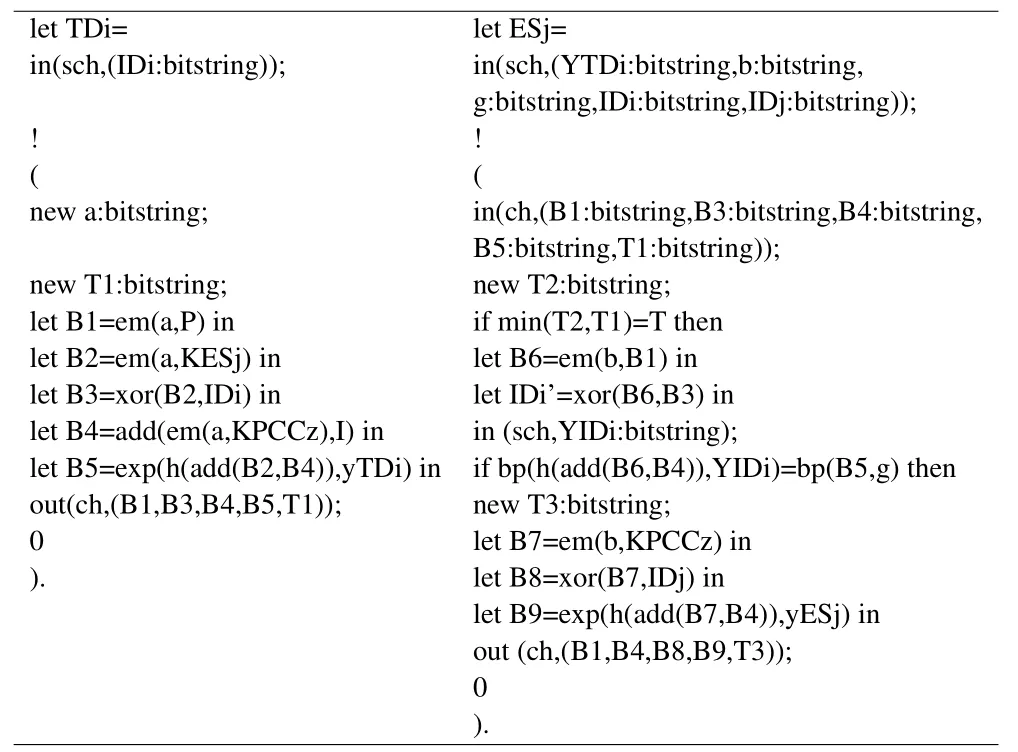
Figure 5.The realization process of TDiand ESj.
4.2 Privacy Protection
Privacy protection mainly protects the information of TDifrom being leaked.The mainstream attack methods include external and internal attacks.First,in an external attack,the attacker can eavesdrop on the information sent from TDito ESjand ESjto PCCz.We transmitted M1={B1,B3,B4,B5,T1}and M2={B1,B4,B8,B9,T3}information on the public channel,where the ciphertext information is B4=aKPCCz+I.We assume that the attacker obtains M1={B1,B3,B4,B5,T1}and M2={B1,B4,B8,B9,T3}information in the worst case;hence,the attacker can know information{B1,B3,B4,B5,B8,B9,T1,T3}.However,all random numbers are encrypted by the ECC algorithm in the proposed scheme.According to the mathematical problem of the ECC algorithm,even if the attacker is learning{B1,B3,B4,B5,B8,B9,T1,T3},it also cannot calculate the values of a,b,c and acP.Hence,the attacker intercepting{B1,B3,B4,B5,B8,B9,T1,T3}information cannot calculate TDiencrypted information I.
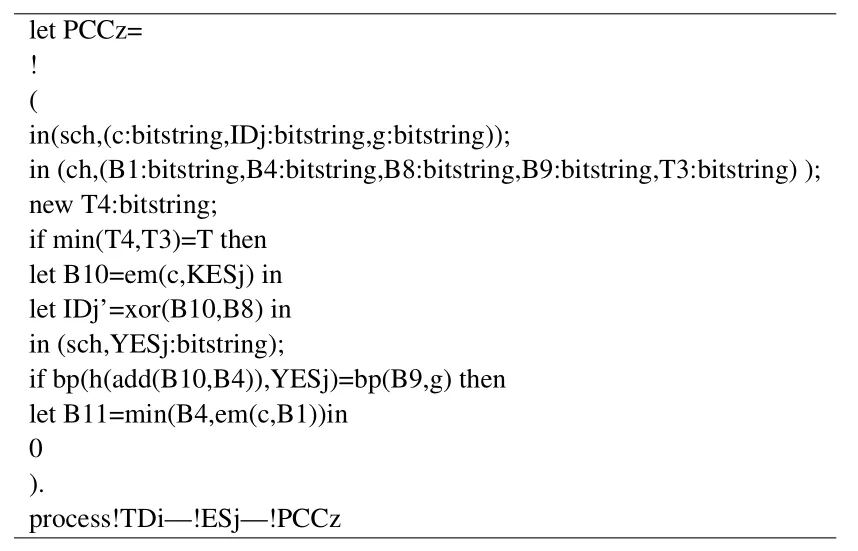
Figure 6.The realization process of PCCz.

Figure 7.The result of the analysis.
An attacker can also launch an internal attack on our scheme.Assuming that the attacker controls the terminal device TDiand the edge device ESj.Then,information{yTDi,IDi,YTDi,b,KESjh,IDj,IDi(i=1,2,...,n)}can be intercepted.The ciphertext information is B4=aKPCCz+I.The attacker cannot even obtain the values of a of TDiand b of ESjthrough intercepted information.Suppose that the attacker can control the values of a and b,and obtains the PCCzpublic key KPCCzin the public channel.According to the mathematical problem of the ECC algorithm,the attacker needs to know the value of c of PCCzto calculate B5.However,the attacker using {yTDi,IDi,YTDi,b,KESjg,IDj,IDi(i=1,2,...,n),PCCz,a,b} cannot also calculate the value of the encrypted information c and I in polynomial time.In addition,we have added the timestamp to the scheme to prevent attackers from trying to crack the ECC through their computational resources.Therefore,the proposed scheme can effectively resist internal and external attacks by attackers and can securely protect user privacy data.
4.3 Data Integrity
Ensuring the integrity of data is one of the keys to the safe and successful information transmission.If there is no integrity verification scheme,then an attacker could be able to tamper with and extract private information.In the proposed scheme,we will first calculate and verify|T2-T1|≤ΔT and|T3-T2|≤ΔT.These steps ensure that the current session is fresh.The proposed scheme will determine whether equations e(h(B6+B4),YTD)=e(B5,g)and e(h(B10+B4),YES)=e(B9,g)are true or not.e(h(B6+B4),YTD)=e(B5,h)is established on the premise that the identities of users IDiand yTDiare legal,and ESjcan find YTDistored in the database through IDi.If the attacker intercepts or tampers with the cipher text M1={B1,B3,B4,B5},then equation e(h(B6+B4),YTD)=e(B5,g)does not hold because the values of{B1,B3,B4,B5}is interdependent.The same attacker cannot tamper with M2={B1,B4,B8,B9,T3}.So,the ESjand PCCzof the proposed scheme can verify the integrity of each call information.
4.4 Source verification
Source verification can prevent attackers from disrupting the normal communication process of the system by sending a large amount of malicious request information.In the scheme proposed in this paper,ESjuses IDito find the stored key YTDi.If the YTDiin the database cannot be found through the IDi,then ESjcan directly reject the communication request of the TDidevice.If PCCzfinds ESjwith the identity of IDj,and the repeated sending cannot pass verification information,then PCCzhas the right to reject the subsequent communication request of ESj.In our scheme,through calculating,PCCzknows which ESjsends the information in each communication round.Moreover,ESjknows which TDithe information processed each time comes from.Therefore,the proposed scheme provides a good way for the traceability of information.
4.5 Man-in-the-middle Attack
In a man-in-the-middle attack,the attacker can intercept and tamper with communication information,and replay this information to achieve the purpose of the attack.The proposed scheme transmits M1={B1,B3,B4,B5,T1}and M2={B1,B4,B8,B9,T3}to ESjand PCCzrespectively in the public environment.However,M1and M2do not reveal the keys and the random numbers of the sender.The transmitted information is encrypted through the ECC algorithm;hence,the attacker cannot obtain the private information through the intercepted M1and M2.Therefore,attackers can neither disguise the intercepted information as a legitimate session terminal nor send forged information to PCCzto increase the storage burden of PCCz.Thus,the proposed scheme can resist the man-in-the-middle attack.
4.6 Replay Attack
The attacker tries to resend the intercepted information to trick the system to pass the authentication.In the proposed scheme,we use the ECC algorithm and the random number a to encrypt I.The attacker only knows the transmitted information M1={B1,B3,B4,B5,T1}and M2={B1,B4,B8,B9,T3}.If the attacker wants to replay M1,M2,then the timestamps T1and T2cannot be authenticated by ESjor PCCz.We can ensure that every authentication message is fresh through the timestamp and random numbers.If the attacker wants to decrypt these information to obtain I,the attacker needs to know the value of a in B1=aP encrypted with ECC.However,according to the characteristics of ECC,the attacker cannot calculate a in polynomial time.Therefore,the proposed scheme can resist replay attacks.
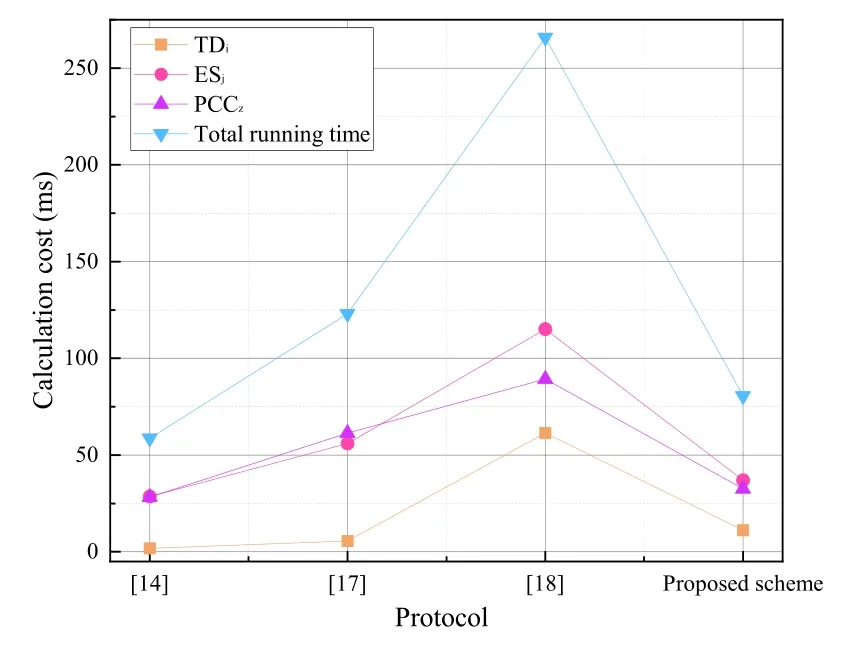
Figure 8.Calculation cost analysis.
V.COST ANALYSIS
5.1 Calculation Cost
In this section,we will evaluate the calculation cost of the proposed scheme and those of Li et al.[14],Zhao et al.[17],and Guan et al.[18].Fan et al.[19]tested the cost of cryptographic operations used in the authentication protocol on the win8 operating system,Intel(R)Core TM i7-4710HQ 2.50 GHz CPU,and 8 G memory.To analyze the calculation cost of the proposed scheme,we use part of the experimental data in [19]for cost analysis.Table 3 shows the calculation cost of various algorithms in the experimental environment set by[19].
The calculation cost comparison between the proposed scheme and other related schemes of[14,17,18]is shown in Figure 8.In the privacy data protection and identity authentication scheme proposed in this paper,TDicalculates signature information B4=aKPCCz+I,the calculation cost of Tem+Ta=2.2548 ms is required.The calculation cost of B5=h(B2+B4)yTDi∈G is Tmp+Tex+Ta=0.9978 ms.So TDineeds a total of 3Tem+2Ta+Tex+Tmp=11.2128 ms to calculate authentication information and cipher text information.After ESjreceives the request verification information and signature information of TDi,ESjcalcu-lates e(h(B6+B4),YTD)=e(B5,g)to confirm the identity of TDi,the calculation cost is 2Tbp+Ta+Tmp=28.0032 ms.Then ESjcalculates request verification information{B7,B8,B9}and send the information to PCCzfor verification.Where,B7=bKPCCz,B8=B7⊕IDjand B9=h(B7+B4)yESjrequire Tem+Tmp+Ta+Tex=3.2238 ms.So ESjneeds a total of 2Tem+2Ta+2Tbp+Tex+2Tmp=36.9612 ms.When PCCzreceives M2={B1,B4,B8,B9,T3}from ESj,PCCzstarts to verify ESj.This process requires Tem+2Tbp+Tmp+Ta=30.2292 ms.PCCzdecrypting information I requires Ta+Tem=2.2548 ms.So the total calculation cost of PCCzis 2Tem+2Tbp+2Ta+Tmp=32.4840 ms.The scheme of Li et al.[14],TDineeds 2Te2+Tmp+Te=1.7968 ms to encrypt and send information.ESjrequires Tbp+3Tm+Tmp+Tp-2Tm+2Tex=28.6599 ms to certificate TDiand aggregate the private data,PCCzneeds Tp+3Tm+Tmp+Tp-3Tm+Te=28.3162 ms to complete the process of verifying and extracting private data.
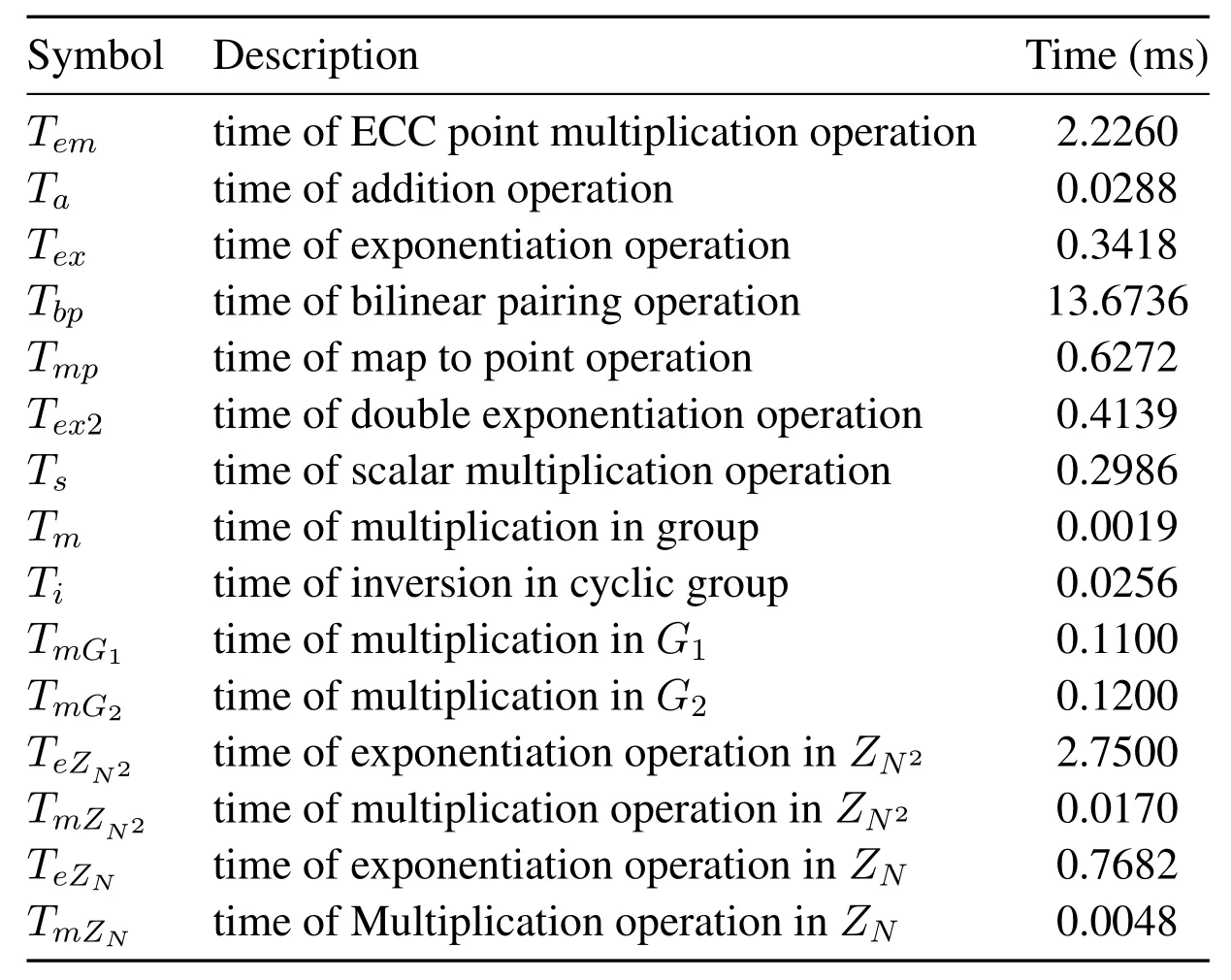
Table 3.The calculation cost of various algorithms.
In the scheme of Zhao et al.[17],the terminal needs 5.627 ms to calculate the information for data generation and encryption.ESjneeds 56.06 ms to calculate the verification information and aggregated data,and PCCzneeds 61.3249 ms to authenticate and decrypt the ciphertext of the information sent by ESj.In the scheme of Guan et al.[18],the terminal needs 61.447 ms to calculate the ciphertext and signature information,and ESjtakes 115.1822 ms to establish the bilinear parameters and aggregate and sign the secret information.Finally,PCCzneeds 89.2348 ms to calculate the bilinear parameters during authentication and decrypt the user’s private information.The computational cost of the proposed scheme is reduced by 22.31% on average compared with those of[14],[17],and[18].The detailed data of this part is shown in Table 4.
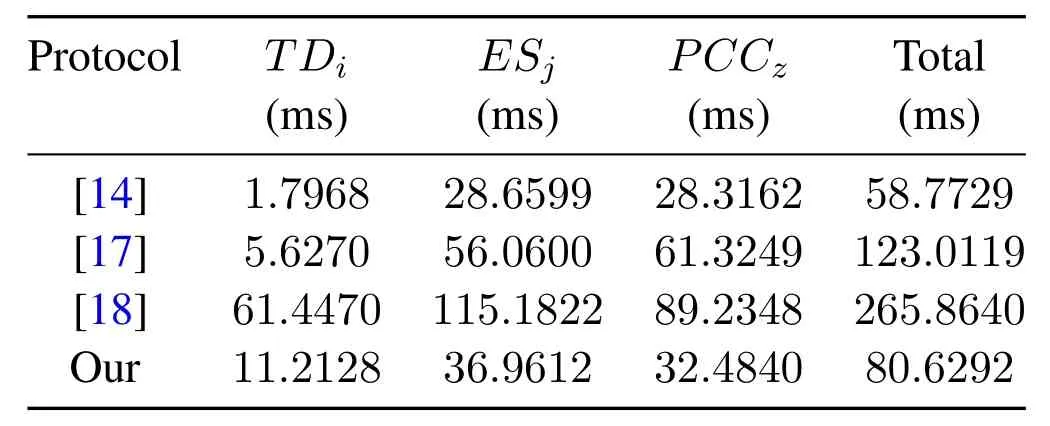
Table 4.Calculation cost of different schemes.
5.2 Communication Cost
In the proposed scheme,assume that the length of TDi,ESj,and PCCzis 160 bits,the length of elements in G is 1024 bits,the ECC encryption algorithm is 320 bits,and the timestamp is 32bits.Figure9 shows a communication comparison between the pro-posed scheme and the other related schemes[14],[17],and[18].
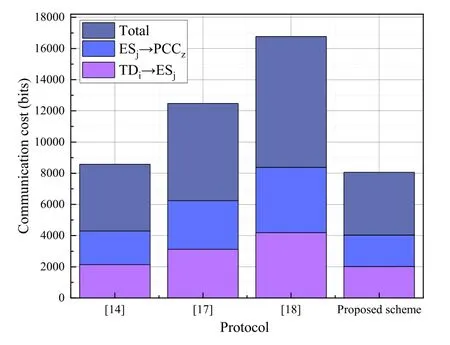
Figure 9.Communication cost analysis.
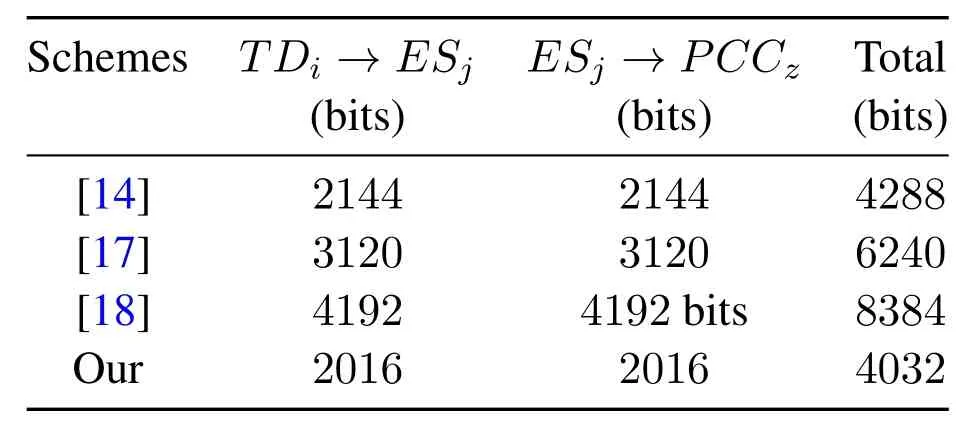
Table 5.Communication cost of different schemes
The communication cost of TDi→ESj:M1={B1,B3,B4,B5,T1}is 320+320+320+1024+32=2016 bits.The communication cost of ESj→PCCz:M2{B1,B4,B8,B9,T3}is 320+320+320+1024+32=2016 bits.In the scheme of[14],the process of TDi→ESjrequires 2144 bits,and the process of ESj→PCCzrequires 2144 bits.In the scheme of[17],the process of TDi→ESjrequires 3120 bits,and the process of ESj→PCCzrequires 3120 bits.In the scheme of[18],the process of TDi→ESjrequires 4192 bits,and the process of ESj→PCCzrequires 4192 bits.The communication cost of the proposed scheme are reduced by 31.08% on average compared with[14],[17],and[18].The detailed data of this part is shown in the Table 5.
VI.CONCLUSION AND OUTLOOK
The emergence of edge computing solves the problems of high latency,network instability and insufficient computing power in traditional IoT and cloud computing.However,the network edge devices in the IoT have many security problems in data transmission and identity authentication.So this paper propose a privacy data protection and identity authentication scheme based on ECC and bilinear pairing to solve this problem.The proposed scheme has the capabilities of privacy protection,data integrity verification,and information traceability.The proposed scheme encrypts the identity of the terminal device and the generated private information through ECC and realizes the anonymous access and data transmission.Through the ECC algorithm and random numbers,the proposed scheme can effectively protect the security of the information I.The scheme proposed in this paper has better security performance,and also has certain advantages in calculation and communication costs compared with other schemes.In future work,we will study the problem of data aggregation and secure transmission of edge computing in a large-scale IoT environment.In this scenario,the edge devices of the IoT will generate massive amounts of data and information.Our future work will focus on how to solve the privacy and security issues in this scenario.
ACKNOWLEDGMENT
This work was partially supported by the National Natural Science Foundation of China under Grant 62072170 and Grant 62177047,the Fundamental Research Funds for the Central Universities under Grant 531118010527,the Science and Technology Key Projects of Hunan Province under Grant 2022GK2015,and the Hunan Provincial Natural Science Foundation of China under Grant 2021JJ30141.
- China Communications的其它文章
- A Key Management Scheme Using(p,q)-Lucas Polynomials in Wireless Sensor Network
- Pilot Allocation Optimization Using Enhanced Salp Swarm Algorithm for Sparse Channel Estimation
- Put Others Before Itself:A Multi-Leader One-Follower Anti-Jamming Stackelberg Game Against Tracking Jammer
- DCGAN Based Spectrum Sensing Data Enhancement for Behavior Recognition in Self-Organized Communication Network
- On Treatment Patterns for Modeling Medical Treatment Processes in Clinical Practice Guidelines
- Hybrid Recommendation Based on Graph Embedding

