An attack-immune trusted architecture for supervisory aircraft hardware
Dongxu CHENG ,Chi ZHANG ,Jinwei LIU ,Dwei LI ,Zhenyu GUAN,* ,Wei ZHAO ,Mi XU
a School of Cyber Science and Technology,Beihang University,Beijing 100191,China
b Beijing Electro-Mechanical Engineering Institute,Beijing 100074,China
KEYWORDS Aircraft hardware;Dynamic integrity measurement;Supervisory control;System-on-a-Chip (SoC);Trusted computing
Abstract With the wide application of electronic hardware in aircraft such as air-to-ground communication,satellite communication,positioning system and so on,aircraft hardware is facing great secure pressure.Focusing on the secure problem of aircraft hardware,this paper proposes a supervisory control architecture based on secure System-on-a-Chip(SoC)system.The proposed architecture is attack-immune and trustworthy,which can support trusted escrow application and Dynamic Integrity Measurement(DIM)without interference.This architecture is characterized by a Trusted Monitoring System (TMS) hardware isolated from the Main Processor System (MPS),a secure access channel from TMS to the running memory of the MPS,and the channel is unidirectional.Based on this architecture,the DIM program running on TMS is used to measure and call the Lightweight Measurement Agent(LMA)program running on MPS.By this method,the Operating System (OS) kernel,key software and data of the MPS can be dynamically measured without disturbance,which makes it difficult for adversaries to attack through software.Besides,this architecture has been fully verified on FPGA prototype system.Compared with the existing systems,our architecture achieves higher security and is more efficient on DIM,which can fully supervise the running of application and aircraft hardware OS.
1.Introduction
Nowadays,as electronic hardware is widely applied in aircraft,attacks against aircraft hardware pose a serious threat to the safety of aircraft.Aircraft hardware is an important part in control and communication network.A vulnerable aircraft hardware may affect communication,navigation and aircraft control,and even lead to an air crash.Trusted and secure aircraft hardware is urgently needed.

Many architectures have been proposed to ensure the security of hardware,including software schemes,hardware schemes and some hybrid methods.Software solutions,such as sandbox1–4,can create a repository offering workspace for software to avoid the attacks from potentially malicious computing platforms.A sandbox can monitor and control the systems calls from untrusted components to prevent the leakage of the users’ data.Compared with the hardware implement,software schemes are easier to be ported,and thus are suitable for various kinds of equipment.However,software-based schemes are viable only when the system is booted rightly.If the kernel is distorted since the start phase,the attackers can read the files or get into the system with their own principles,and then these schemes can be ineffective,which cannot meet the strict security requirements of aircraft.
There are also security architectures based on hardware.In 2007,Trusted Computing Group (TCG) came up with the Mobile Trusted Module (MTM) Specification5.In MTM,the trustworthiness of hardware is realized via the Trusted Execution Environment(TEE).In system booting,TEE will run ahead of Trusted Platform Module (TPM),and the TPM will then build the trusted environment and the subsequent trusted chain.The hardware is trustworthy only when the TEE is secure and reliable.As MTM has strict requirements to the hardware providers,it is unpractical to be adopted in aircraft hardware.
The TrustZone hardware security features realized by ARM CPU provide a new method to construct security and trusted architecture for hardware6.For example,some researchers7presented a secure boot scheme with TrustZone and built a secure operation environment with independence against the attacks during the start phase including the attacks against hardware systems and attacks faced by hardware itself.Xiao et al.proposed a secure mobile hardware system with improved security by utilizing fingerprint identification and TrustZone8.Pinto et al.presented a series of virtualization technologies on the basis of TrustZone assistant environment9.The proposed scheme allows fast and safe switch between different client Operating Systems (OSs).Gonza´lez et al.constructed a two-step boot verification scheme on TrustZone10,to achieve the verification and record of the program’s integrity at the startup phase.The system’s startup trace and software will be checked while running to ensure its security.
TrustZone can provide a secure environment for the running of sensitive programs and data.However,the executing program in TrustZone’s secure area will interrupt other programs running in the OS.At the meantime,real-time system resources monitoring and process measurement will bring additional overhead.Besides,user processes and kernel programs in OS will share the ARM CPU core,which makes it difficult for the third-party to manage the monitor programs and the Dynamic Integrity Measurement (DIM) programs in TrustZone.So the security application design and common application development will be disjointed,which will increase the difficulty in aircraft hardware development.
Time of Check versus Time of Use (TOC-TOU) is a common problem in Static Integrity Measurement (SIM)11,in order to solve which DIM technology is proposed.A secure terminal hardware OS measurement architecture has also been presented12.The architecture integrates several functions including environment vulnerability scanning,dynamic security testing,system security configuration checking and application static.Hu et al.proposed a program integrity measurement information base utilizing predefined creation13.The whole process can be divided into preparation,running and blocking suspension,and then the process can be measured by real-time DIM with a better performance.Detken et al.designed a DIM architecture depending on Loadable Kernel Modules14,in which a set of dynamically adjustable benchmarks will be chosen as Reference Value Generator(RVG),and then the RVG and TPM can be called to accomplish the integrity of executing program.There was also a DIM scheme based on trusted computing15.The scheme can monitor and conduct real-time DIM on executing processes and modules as required,which basically solves the TOC-TOU problem.Maene et al.presented Atlas to defy system-level attacks utilizing hardware-based memory encryption16.Evtyushkin et al.proposed Iso-X to provide a secure execution environment for sensitive applications based on hardware17.This scheme is lightweight but function-limited,and it has little to do with the attacks against kernel modules.Mohd et al.proposed a run runtime-monitoring and trusted design against Trojans detection for resource-constrained devices18.But the scheme still faces the risks from kernel distortion.
All the above DIM schemes rely on the protection in OS level.If the OS’s kernel module is embedded by viruses and Trojans,the DIM process will be unsecure.Besides,though the DIM is conducted,the system cost is too large,which is not suitable for aircraft hardware with limited resources.There were researchers19taking the advantage of TrustZone and proposing TrustShadow.They constructed a lightweight runtime system to hold a trusted execution environment utilizing a virtual memory system,which can defend against coldboot attacks.Though the independent system is lightweight,it still shares the same CPU sources with the main system and is hard to satisfy third-party development,so it is still not suitable for aircraft hardware.
Jintide20integrates three independent bare dies through Multi-Chip Package(MCP),which can support trusted startup and server oriented applications.Jintide obtains data through IO and memory tracing and compares it with the standard behavior model to detect malware attacks.Because of the inherent weakness of rule-based protection,there is no general rule to detect all attacks.Therefore,Jintide’s dynamic security detection is not complete.In a word,a more efficient and secure architecture suitable for aircraft hardware is needed.
In this paper,we propose an improved attack-immune super monitoring trusted architecture for aircraft hardware,and the contributions are shown as follows:
(1) We design a new trusted architecture for aircraft hardware to provide a stronger foundation for safety functions.We study the hardware applied in aircraft nowadays and give a viable and improved architecture for aircraft hardware,which can support trusted startup,DIM,cryptographic computation and many other functions.Compared with software solutions,our architecture can provide a more stable secure basis since the start phase from the physical level,which can resist more diverse attacks.
(2) We propose a new trusted startup scheme with a trusted measurement process and a DIM scheme based on our trusted architecture.With these processes,our architecture can provide security properties including attack immunity,interference-free DIM,third-party trusted escrow and super monitoring,which can greatly improve the safety of current aircraft hardware with flexibility and a small extra cost.
(3) We implement a prototype verification system on FPGA.The experimental results show that our scheme’s security in practice is consistent with the theory,while the memory and time costs are acceptable for aircraft hardware with limited resources.So our scheme can better meet the requirements of aircraft hardware for security and resources than state-of-the-art architectures.
2.Preliminary
2.1.Notations
In this paper,for binary stringsaandb,a||bpresents their string concatenation.
2.2.Trusted computing
Trusted Computing (TC) is a technology developed by TCG,and is aimed at enhancing the overall security,privacy and trustworthiness of various computing devices21,22.TCG defined that an entity can be ‘‘trusted”if it always behaves in the expected manner for the intended purpose.And the protection methods including sandbox and virtual machine are all based on the assumption that the hardware system can be trusted.The applications and software can be malicious,but the boot programs and system itself have to run in a right way to ensure that the protection methods can start and execute properly.
A platform for TC requires that it can strongly identify itself,its current configuration and running software,mainly using cryptographic tools.TPM is developed as the core for TC.TPM is a tamper-resistant module embedded in a platform,which can provide Roots of Trust(RoT).With this root,a chain of trust can be established.As a component proved by a trusted component to be trusted can also be seen as trusted,the components in a platform can be verified one by one from the RoT until the whole platform is proved to be trusted.TPM can provide the RoT for Measurement (RTM),the RoT for Storage (RTS) and the RoT for Reporting (RTR),which can together support the various security functions of TC.
2.3.Trusted startup
Trusted startup is a method that threads the measurement during the boot process.Trusted startup can guarantee that the system is booted with the right program,which is the precondition for all other security functions in systems.A typical trusted startup process is shown as follows:
Step 1When powered on,the RTM records an indication of its own identity in a trusted storage.
Step 2The RTM takes a hash of the next component to execute and store it in a secure storage,if the next component is legal,and then RTM will transfer control to that component.
Step 3Repeat Step 2 for each link in the trusted chain.
After the booting,any program in the chain can compare the stored values with the expected ones,making any program possible to verify its own integrity and the integrity of the component it relies on,and then the RTM can be immutable.
2.4.DIM
DIM is the integrity measurement during the execution of a computer platform23.SIM only verifies the integrity during the load time.But there are many runtime attacks including stack and heap based buffer overflows which cannot be detected in this way.So DIM was proposed to defend against the attacks during runtime.DIM can be combined with SIM to provide a more comprehensive protection for embedded systems.
2.5.Attack models
The attacks faced by security chips can be mainly divided into three classes:hack attacks,shack attacks and lab attacks.Hack attacks mean that an adversary can only perform software attacks,such as downloading viruses or malicious software to chips through physical or wireless connection,and then implementing attacks against the current system.Shack attacks mean that the attackers have physical access to the chip,connect the debug pins of the chip to attack,and passively monitor the input and output data of chips.Lab attacks mean that attackers can carry out reverse engineering and intrusive attacks on chips.Attackers in lab attacks can use the methods in hack attacks and shack attacks simultaneously,which has the strongest attack ability and poses a huge threat to the chip security.
In our scheme,we assume that an adversary has the ability of hack attacks and shack attacks.Based on the trusted architecture proposed in this paper,the firmware programs running on the TMS can resist software attacks.By closing the debug ports of the chip and verifying compliance of the data in interfaces communication,we can also defend against shack attacks.In lab attacks,a chip may need a special and comprehensive security protection design for the internal bus,various memories,cipher algorithm engine circuits,etc.Defending against lab attacks is beyond the research scope of this trusted architecture.
3.Trusted measurement for aircraft hardware
3.1.A new trusted architecture for aircraft hardware
To implement DIM and trusted startup for aircraft hardware,we design a new trusted architecture according to current avionics.Besides,we propose and implement a TMS to support the architecture.TMS can provide the same hardware functions as TPM,while a TMS is designed more suitable for aircraft and can provide specific software for DIM.
As the state-of-the-art hardware mounted on aircraft has applied the MB level SRAM and the CPU with a frequency up to GHz (e.g.MMC7000 on F-16),as well as multi-core CPU architecture(e.g.SOI 4 submitted by Rockwell),it is possible to implement a new SoC system with enough resources to contain a trusted architecture against the growing security risks.
As shown in Fig.1,a present MPS forelectronic hardware can integratenhigh-performance RISC CPU cores.Each CPU core has a working frequency up to GHz,and it integrates quite a number of data caches and many instruction caches,which can support high-performance program computing.Besides,the chip also combines SRAM memory for the storage of data and programs,DMA controller for data transmission acceleration between internal and external memory or interfaces,a set of interface control units for logic control and data transmission of various data interfaces and wireless communication circuit,and general modules such as bus arbiter,timers,POR,clock managers and interrupt controllers integrated in SoC chip.With these components,the chips in hardware can realize the complex functions assigned to MPS.
To achieve an appropriate trusted architecture for aircraft hardware,we extend the SoC system in Fig.1 by adding a small SRAM storage space,a suitable hardware control design on on-chip bus,non-volatile storage space (eFlash or off-chip flash) and a lightweight embedded CPU core.As shown in Fig.2,a new small SoC system,the Trusted Monitoring System (TMS),is framed with a dashed box.The lightweight RISC CPU has a working frequency lower than 200 MHz,and a cache is no longer needed here.

Fig.1 Main processor structure of mainstream intelligent terminals.

Fig.2 Trusted enhanced architecture of MPS in mainstream intelligent terminals.
Generally speaking,the working frequency of the TMS’s CPU core is 1/10 of that of MPS.So the area cost of the TMS is less than 1/50 of the chip,and the memory cost is also less than 1/50 of the MPS.Compared with the modules in mainstream MPS,the cryptography engine integrated by the TMS has a very small circuit size,which will not be larger than 1/100 of the sum of MPS functional modules’sizes.So by considering various factors in practice,the small SoC system should take less than 1/50 area of the entire chip.As MPS in current trusted architectures of secure avionics CPU are mainly established on the existing mainstream processors,our architecture can be implemented on existing hardware with only a little modification.
In our architecture,the on-chip SRAM2 generally has the capacity between 128 KB and 256 KB,which can support the TMS programs’running and save the chip space.Through Bus Bridge1,the TMS has full access to the devices on the main processor’s SoC system.Besides,by setting the Bus Arbiter properly,the TMS can regulate the read-write operation of the main processor SoC system’s on-chip bus slave devices.But the main processor SoC system cannot control the process on TMS.
The TMS has a physical noise generator and a cryptography acceleration engine,with which the trusted software stack can achieve some cryptographic service functions for security services.Due to the lack of mature eFlash IP cores in some deep submicron processes,we mark the on-chip eFlash with a dashed box.Depending on whether the ASIC process supports eFlash IP,we consider two situations for TMS security storage.One is that the ASIC process can support eFlash IP,and we can directly store sensitive data including Platform Configure Register (PCR),master key and trusted measurement root in the on-chip eFlash.Since the MPS has no access to the eFlash in TMS,the data can be stored safely,or if the ASIC process cannot support eFlash IP,the sensitive data and programs will be stored in the non-volatile External Memory.A boot program has to be stored in ROM to read the contents in the non-volatile External Memory into the TMS by Bus Bridge1.The boot program will also verify the contents’integrity,decrypt them and store them in SRAM2.The decryption key injection is performed by a trusted third party responsible for security implementation.
The key will be written into a One-Time-Programmable memory (OTP memory) before the aircraft hardware starts security function to ensure the security of data and programs in TMS.
3.2.Static trusted measurement process in system startup
Based on the trusted architecture proposed in Section 3.1,we give a new system startup scheme with trusted measurement process:
(1) TMS has to start prior to the aircraft terminal’s main processor.It should be judged whether the TMS has integrated on-chip eFlash.If an eFlash is integrated,the Static Measurement Program(SMP)can run directly from it.If not,the program and the data should first be loaded from outside the chip,and the integrity of them will be verified.After the verification,the program and the data will be decrypted and written to on-chip SRAM2.Then the SMP will start.
(2) In the measurement process,the integrity of the boot program of the terminal’s main processor SoC will be stored in External Memory and the SMP will measure it via Bus Bridge1.If the measurement passes,TMS will start the main processor of the aircraft terminal.By setting the DMA controller,the boot program will run and the image of the OS will be copied to SRAM1.
(3) The OS image will be read and measured by the SMP to verify if it is integrated.The process will execute through the path between the System Bus 2 and the SRAM1(The dotted arrow connecting SRAM1 in Fig.2).The process requires the SRAM2 to be a dual port memory.
(4) The embedded Operation System (eOS) will be started by the MPS.The kernel module of the eOS,LMA,will be loaded by the eOS.
(5) The DIM programs and the LMA in the MPS will interact with each other and exchange identity authentication data.They will verify if the program is integrated and loaded from the right address.Then the static trusted measurement process will end.
The process of static trusted measurement is shown in Fig.3.
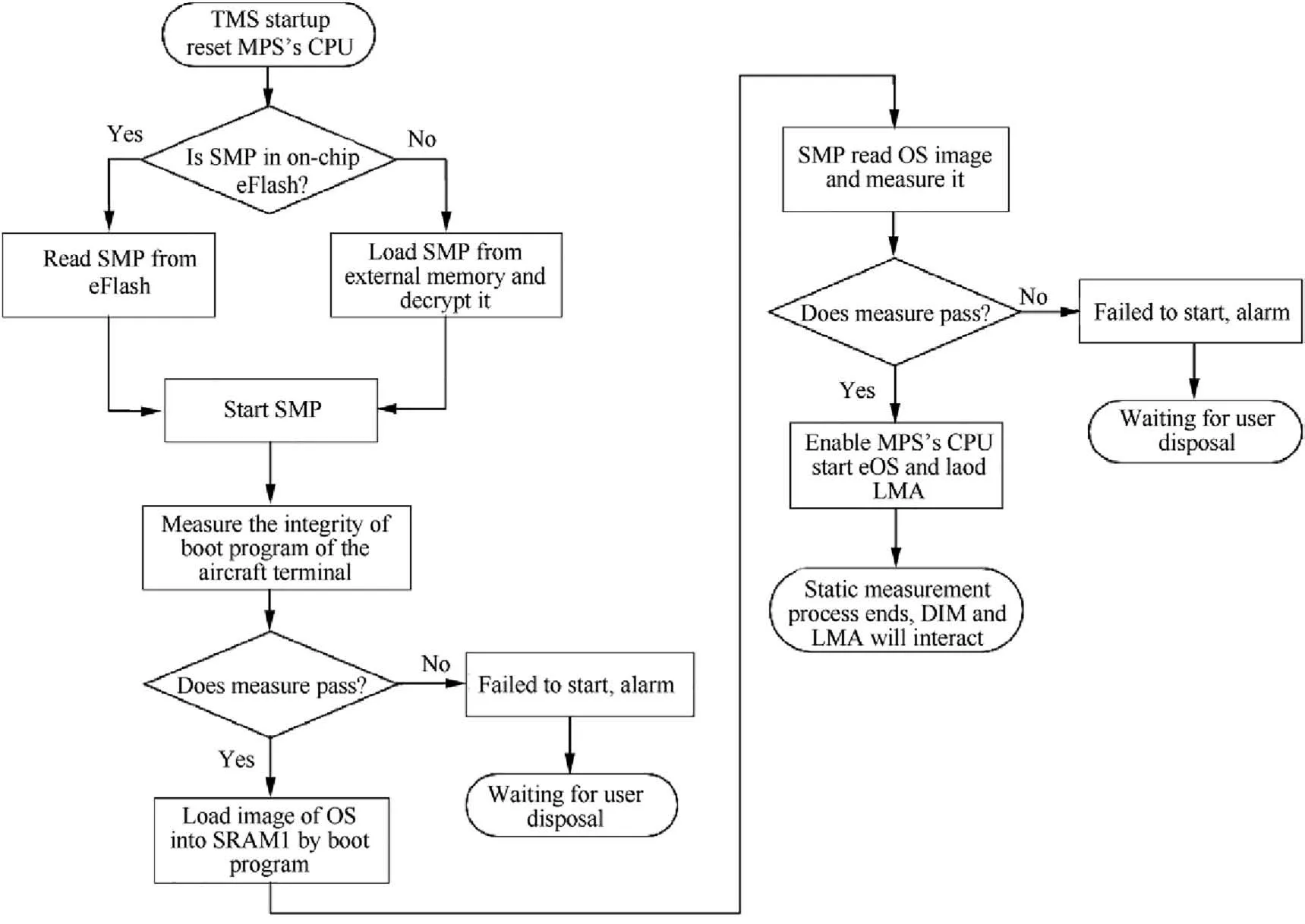
Fig.3 Flowchart of static trusted measurement process in system startup.
The TMS will continuously reset the MPS’s CPU since the beginning.Once the TMS proves that the OS image is integrated by integrity measurement,it will stop resetting to let the MPS’s CPU start.The CPU will load the OS image and run the system.Then the system will call the LMA kernel module again and the SIM will end.The key to transfer from SIM to DIM is that LMA is stored together with the OS image as a whole to measure the static integrity.Once the SIM is completed and it is confirmed that the OS image is not tampered,the MPS’s CPU will be enabled to work.
3.3.DIM based on trusted enhanced architecture of aircraft hardware
After the trusted startup phase,DIM will continue running based on TMS.The integrity measurement structure is shown in Fig.4.The way to measure the programs running on MPS depends on whether a program is an eOS.For the eOS running on the MPS,LMA and eOS’s image can be directly read by the DIM programs of the TMS in real time.The image and the LMA will be read through SRAM1 monitoring channel and measured in real time.For other programs running on MPS,LMA will get the programs’names,sizes and code page’memory addresses.The information obtained by the LMA will then be sent to the DIM.The DIM will get the code page information in the SRAM1 with the memory addresses and sizes and then measure it.The measurement process can run independently from the main processor.Because the programs’ information is only needed during apps’ loading or exiting process,so the LMA has little effect on program running.Besides,the DIM programs will record programs that need real-time measurement.These programs’running information will be kept as a list,including code pages addresses,hash values of code pages and processes’ names.The DIM programs can start at all times according to programs on the list following the security policy.Besides the integrity of key apps,the integrity of the kernel module can also be measured dynamically.The parameters used in DIM are shown in Table 1.

Table 1 Parameters in DIM.
As shown in Fig.4,Mi(1 ≤i≤n) denotes the code page space of the executing programs.The measurement process can be denoted by

Fig.4 DIM Structure based on TMS.
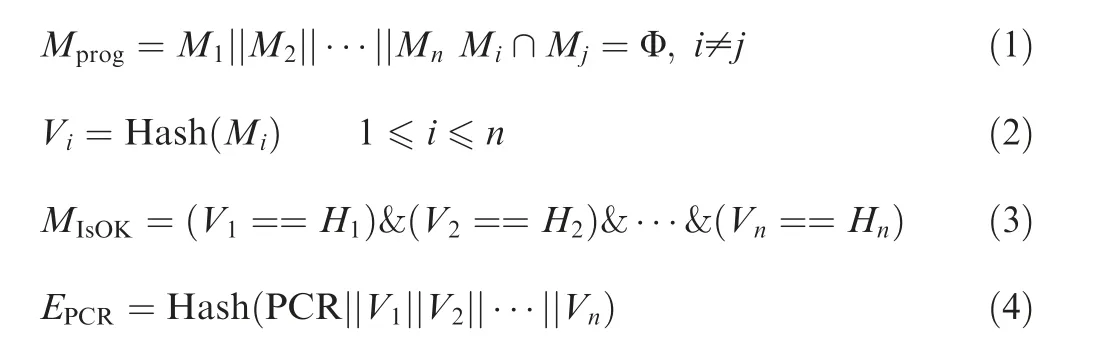
In these equations,Hipresents the hash value ofMi(1 ≤i≤n).The hash values will be calculated and stored according to the programs’ running information list before the measurement.Only whenViandHican match each other for all 1 ≤i≤n,MIsOKis true,otherwiseMIsOKwill be set to false.And finally in Eq.(4),all the hash values generated in this process will be extended to a PCR.The PCR can be utilized to generate a trusted chain which can be used in security policy’s verification.
4.Security properties of trusted enhanced architecture
This paper proposes a trusted enhanced architecture for aircraft hardware,and the architecture has the following security properties.
4.1.Attack immunity
In this paper,we mainly consider the attacks from hackers.It should be noted that the attackers can embed viruses,Trojans and other malicious programs to aircraft hardware via vulnerabilities,but they have no access to the hardware physically.So the attempt to tamper with chips directly and side channel attacks towards circuits are not discussed in this paper.
To achieve the immunity to malicious programs,the security programs will be physically isolated from the main processor SoC.The eOS and its programs have no access to the memory space of TMS.For the code and data in external memory which are needed by the TMS,we can assign separately controlled memory access addresses in the external memory via Bus Arbiter,allowing only programs in the TMS to process the code and the data.In these ways,we can ensure that the programs and SoC system on MPS CPU have no access to TMS’s secure programs,stored code and data,and then the secure programs in TMS can be completely immune to attacks from malicious programs.
4.2.Interference-free DIM
At the system level,the DIM programs in the TMS can get the sizes and the memory addresses of the programs in the MPS on the basis of information provided by hardware providers,including system configuration information and the types and characteristics of the main CPU and the eOS.With the addresses and the sizes,the DIM programs can read and implement real-time integrity measurement over the LMA,the OS kernel and key modules.
At the key app DIM level,the LMA will get a program’s name,code size and code page memory address as it is loaded,which will be written to a specific memory space.When a DIM is needed,the DIMprograms will read the information from the space and begin the measurement.After the measurement begins,the MPS CPU will no longer be needed,so the measurement process will not interfere with the key app programs and the eOS.
At the security level,the kernel modules and programs of the eOS and the key app programs all can be measured by DIM at all times,so the architecture is both secure and credible.
4.3.Third-party trusted escrow
In our architecture,the program development,operation and upgrade maintenance are all independent from the MPS.So the hardware providers are only needed in MPS development and verification processes,after which the TMS programming model can be opened to third parties.A professional and trusted third party can take over the design and development works.This trusteeship approach is beneficial to the formation of industry standards and the supervision from regulators,which will reduce the security risks.
The trusteeship is to ensure that the DIM is designed securely and evaluated by a professional organization,and this ensures that there are no design flaws in the DIM.In addition,the software program in MPS cannot access the system and data in TMS at will.At this time,TMS area is similar to TrustZone in ARM CPU,which further ensures the security of TMS system.
4.4.Super monitoring
The proposed architecture also supports emergency treatment under abnormal conditions.As shown in Fig.5,under normal circumstances,the master devices such as DMA controller,the main CPU and lightweight CPU will read and write interfaces through the bus arbitration logic and the decoding logic circuit in system bus.Once a system error happens and is captured by the TMS,the TMS will write a control command to Bus Arbiter via System Bus 2 to prevent the Bus Arbiter providing decoding service for the DMA controller and the main RISC CPU.According to peripheral type,response timeout and meaningless protocol data will also be sent out to prevent the MPS programs’crashing from peripheral denial of service.Then the TMS can control hardware functions including display output,network communication,photographing,recording and so on.
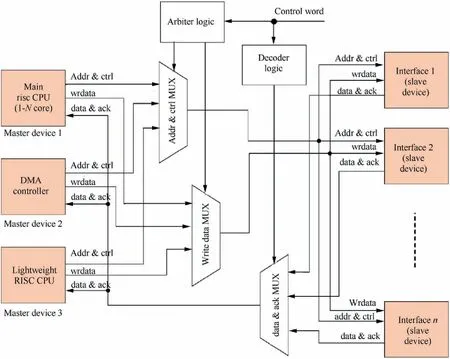
Fig.5 Control structure of peripheral interface based on bus arbiter.
Besides,the TMS can achieve more functions to ensure the security of the hardware,including executing identity authentication protocol at startup,monopolizing the mobile communication connection channel,upgrading the MPS image file safely,monitoring the current program pointer and resetting the main CPU.
4.5.Key management
In the proposed scheme,key management components including firmware measurement,Non-Volatile (NV) key storage,hardware PCR management and security strategy all follow the TCG’s mobile reference architecture specification.
For the firmware update in the TMS,since the data interaction between TMS and the external data of the chip will bring high risks.We will consider the key management here in two situations.First,if the users’ data are all transferred during the updating process and the NV keys corresponding to the firmware are replaced at the same time,all the states in trusted computing on the TMS will be lost.According to the security strategy,the firmware in the TMS will issue a new certificate for the device.Second,if the updating just adds some features to the scheme,the TMS will add nonce,firmware version number and date to the key management protocol,and verify the integrity of the firmware.These processes can guarantee that the states of trusted computing will be transferred to the new firmware instead of the old firmware to avoid being compromised by adversaries.
5.Principle verification of trusted architecture for aircraft hardware
5.1.Prototype design
We implement the trusted architecture for aircraft hardware on a single FPGA chip of Intel’s Cyclone V series (model:5CSEMA5F31C6N) integrated with ARM CPU hard core.The structure of the principle verification system is shown in Fig.6.
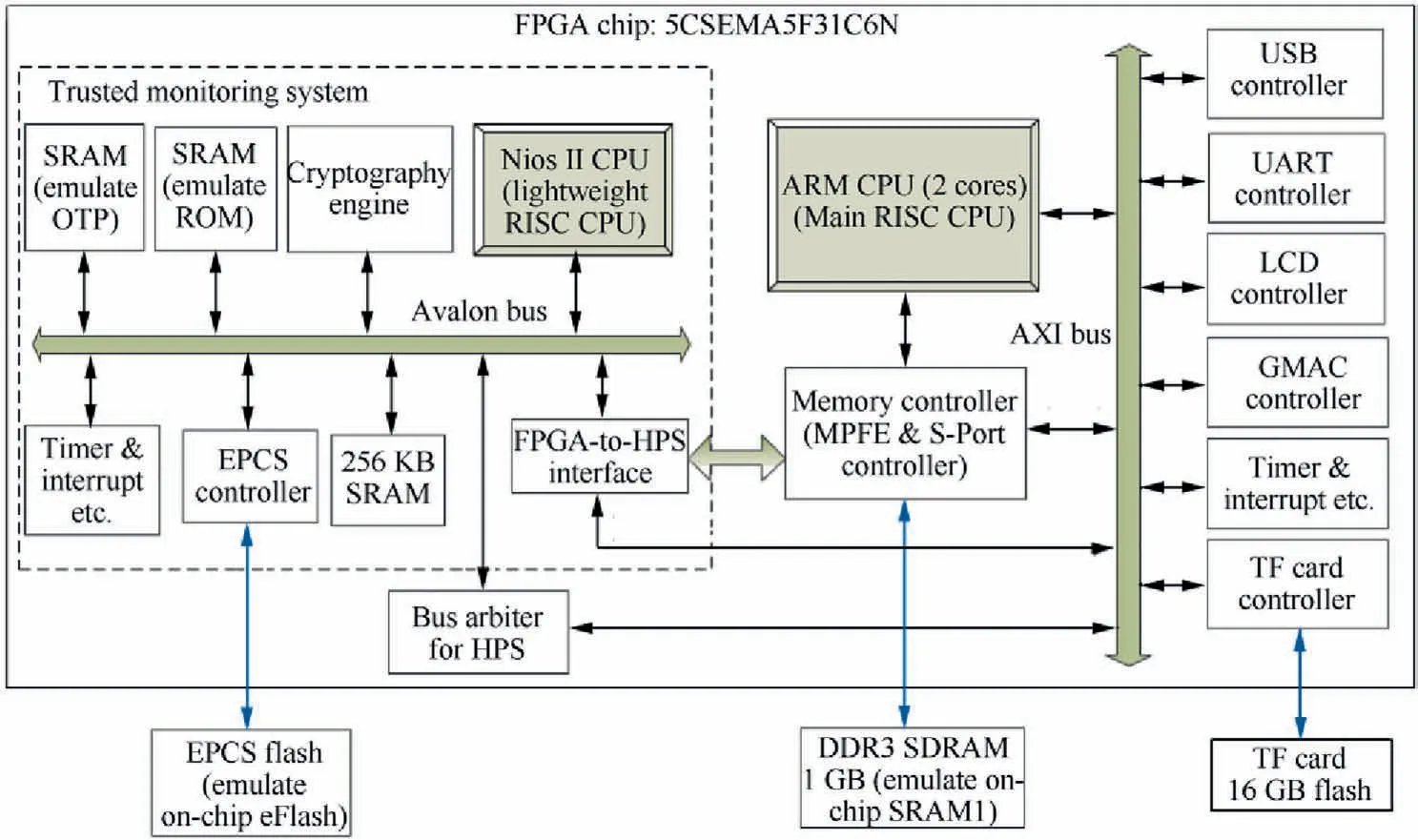
Fig.6 Structure of prototype design.
As the SRAM in FPGA can store data when powered on,it can simulate the ROM and the OTP modules in our architecture(the ROM and the OTP in Fig.2).And in our implementation,the non-volatile memory eFlash is simulated by a configured flash chip in FPGA.
We construct a TMS on a FPGA chip utilizing SOPC technology and integrate it with a 32 bit Nios II CPU as the lightweight RISC CPU.The TMS will monitor a 32 bit ARM CPU which simulates the main CPU core.An embedded Linux OS will run on the ARM CPU and its image is stored in a TF card.Through the FPGA-to-HPS interface module,the Nios II CPU has direct access to the Memory Controller module.The access is in the way as a master device and the Nios II CPU has the ability of reading and writing DDR3 SDRAM program memory.Utilizing the Bus Arbiter for HPS module,the Nios II CPU can also get the access control permissions to peripheral modules in the ARM CPU system.
The photo of the prototype is shown in Fig.7,and an Altera (which has been taken over by Intel) FPGA chip of model 5CSEMA5F31C6N is set in the center of the circuit board.The prototype system supports keyboard input,USB OTG interface and network port.It integrates a variety of keys,nixie tubes,LED lights,and a 6 inch LCD display.A Linux system runs in the foreground of the MPS built on FPGA,and the trusted monitoring security program in the TMS automatically runs in the background.

Fig.7 Picture of prototype.
Compared with the architectures based on software schemes including virtual machine and sandbox,our design takes almost no process time of the main CPU and does not affect the software running on the MPS while resisting the attacks from malicious programs,and thus has a better performance in security and efficiency.
In terms of hardware architecture,when TMS removes the interconnection circuit with MPS,it is basically the same as the main logic circuit of the TPM module.These TMS-like TPMs are shown in Table 2.
In terms of software configuration,TMS embedded software system is a superset of software configuration in TPM.In addition to trusted computing related software,TMS also configures an active measurement software program.Generally,trusted computing software in TPM can only be passively called by system service programs,while the program in TMS can drive internal signals to reset MPS or disable external interfaces which MPS can access through interface drivers.The program in TMS can not only actively measure the key programs and sensitive data in MPS,but also carry out subsequent security processing.By referring to the structure of TMS,if we add necessary control interfaces and the same software programs as TMS to the TPM modules in Table 2,they are also competent for the trusted and active measurement functions of TMS.

Table 2 Comparison between TMS and TMS-like TPMs.
Different from Jintide20,the proposed scheme integrates TMS and MPS into a single bare die by a well-designed bus circuit.The method makes our scheme securer and more efficient,and can support real-time DIM mainly for terminal devices.The DIM can measure the integrity of the OS kernel and security apps in the MPS to detect the tampering attacks of malware.In addition,the unmodified secure apps will further detect the attacks of malware against other sensitive data of the whole system.Thus our scheme does not need to model the secure running state of CPU or create a behavior database,so the hardware cost is smaller and the efficiency is higher.
5.2.Trusted startup
In our implementation,the Nios II CPU can access the TF card through the connection between the FPGA-to-HPS interface module and the AXI bus.The Linux kernel image will be stored in the TF card and can be read by the Nios II CPU.The TMS can achieve the security functions including secure storage,integrity reporting functions and integrity measurement with the SIM program and the trusted software protocol stack.During the startup process,the ARM CPU will first be reset.After the reset,the TMS will measure the static integrity of the bootloader program code and the image data of Linux.If the measurement passes,the TMS will run the bootloader to load the Linux image,after which the ARM CPU will start and run the Linux system.The LMA will be called by the Linux system,and the TMS will get into the DIM stage.
5.3.DIM
In the DIM stage,the OS and user programs will run on a 1 GB DDR3 SDRAM,the main memory of the ARM system.The Nios II CPU and the ARM CPU can access the SDRAM efficiently.Utilizing the physical channel,the TMS can access the SDRAM and conduct measurement on the dynamic integrity of the MPS running on it.Following the properties mentioned in Section 4.2,we successfully conduct the interference-free DIM on key app programs and the kernel module running on the ARM CPU utilizing the DIM programs.The parameters used to evaluate time cost are shown in Table 3.
The test performance of our experiments is shown in Table 4.The actual measured time in Table 4 is the sum of:the time spent in the interaction between the DIM programs running and the LMA,the time spent in reading the data to be measured in the off-chip SDRAM,tsdram;the time from the hash hardware computing engine getting the input data to the result being returned,the dynamic measurement time increased by the competition among the DIM programs and the programs running in the Linux main system for the access to SDRAM,the time spent for the DIM programs to call hash engine interface,run the SDRAM interface driver and generate log report

Table 3 Parameters in time cost evaluation.

According to the analysis,tsdramandwill change linearly as the measurement memory size changes.will be fixed as the hardware and software environment of the TMS gradually become stable.can be reduced to 0 by introducing a dual-port SRAM to the chip to avoid competition in the design and implementation of the SoC system.can also be negligible as the LMA keeps a list of the addresses of kernel processes,sensitive data in memory and key app processes because the DIM programs can quickly obtain the contents to be measured according to the addresses.So the above formula can be simplified to

The main time cost depends on the running performance of DIM on the Nios II CPU,hash hardware engine processing rate and SDRAM interface rate.
The results show that the architecture can be used to detect attacks,if the Linux system kernel is embedded by malicious programs that aim at distorting key app processes,the LMA process or the specified kernel module,and the DIM programs can alarm within actual measured time in Table 4.
5.4.Third-party trusted escrow and super monitoring
As shown in Fig.6,the proposed architecture completely simulates the hardware system of the key modules in Fig.2,which can support super monitoring and third-party escrow as mentioned in Section 4.
In the principle verification system,the third party can load programs to the EPCS Flash linked to the TMS through a specific JTAG port,and whereby realize the deployment and application of security escrow.The time required for security escrow application is shown in Table 5.

Table 4 Measurement performance of processes and data in accessible memory of Linux system.

Table 5 Time required for security escrow application.
In our experiments,we factor three situations:
(1) The measurement and recovery of application exceptions.If the DIM detects that a key app running on MPS has been distorted,it will resume the program.The escrow program in the TMS will terminate the key app and warn the user to reload the app.In our experiment,a Vim program was chosen to be distorted,and the DIM would detect the error and alert the LMA to stop the Vim program.We repeated the process ten times and the average time cost is 351.4 ms.
(2) The secure update of the MPS image.Upon receiving
the update order from the user,the LMS will inform the TMS to perform an update following the data flow shown in Fig.8 by red dotted lines.The TMS will reset the ARM CPU by hardware logic and communicate with the network port through the Bus Arbiter.Then an identity authentication protocol is executed.If the protocol passes,the TMS will receive the image file and measure its integrity and timestamp.When confirming that the document is legal,the TMS will start the ARM CPU and perform the MPS startup process(The integrity of the image file was no longer measured.).In our experiment,we repeated the process ten times and the average time cost is 21500 ms

Fig.8 Structure for Security Escrow and Super Monitoring.
(3) The super monitoring to MPS.The escrow program can control the communication between the MPS and the external interfaces to avoid illegal operation and the leakage of sensitive data.When the DIM detects that a key app is distorted,the escrow program will turn off the USB,UART and GMAC interfaces on the MPS side through the Bus Arbiter.On the MPS side,the programs on the ARM CPU will receive busy signals when accessing these interfaces.When the key app is recovered from the security backup,the LMA will inform the TMS to release the locked interface.In our experiment,we repeated the process ten times and acquired the average time used in key app recovery,and the average time cost is 127.4 ms.
As shown in Fig.8,the virtual switch layer is mainly composed of the system bus on the MPS side and the interface circuit between the slave device and the bus.The open and close of slave devices can be controlled by the Bus Arbiter.
6.Conclusions
This paper proposes an improved attack-immune super monitoring trusted architecture for aircraft hardware.We discuss the properties of DIM and trusted startup under the proposed architecture in details.The architecture can support the noninterference DIM of user programs and OS kernels.Compared with the existing schemes that integrate the current OS kernels with the process integrity measurement programs,our architecture performs better in security and efficiency,and can support third-party trusted escrow and super monitoring of hardware MPS,which can better meet the requirements of aircraft hardware for both security and resource.
We implemented a prototype verification system on FPGA.The experimental results show that our scheme’s security performance in practice is consistent with the theory.And the memory and time costs are acceptable for aircraft hardware with limited resources.By expanding the LMA,our scheme can be further enhanced to integrate more secure and trusted functions.The internal bus interconnection structure can also be optimized,which will be done in our further research.
Declaration of Competing Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Acknowledgements
This paper was supported by the National Key Research and Development Program of China (No.2017YFB0802502),by the Aeronautical Science Foundation (No.2017ZC51038),by the National Natural Science Foundation of China (Nos.62002006,61702028,61672083,61370190,61772538,61532021,61472429,and 61402029),by the Foundation of Science and Technology on Information Assurance Laboratory (No.1421120305162112006),by the National Cryptography Development Fund(No.MMJJ20170106),by the Defense Industrial Technology Development Program (No.JCKY2016204A102),and by the Liaoning Collaboration Innovation Center For CSLE,China.
 CHINESE JOURNAL OF AERONAUTICS2021年11期
CHINESE JOURNAL OF AERONAUTICS2021年11期
- CHINESE JOURNAL OF AERONAUTICS的其它文章
- Parameter effects on high-speed UAV ground directional stability using bifurcation analysis
- Supersonic flutter control and optimization of metamaterial plate
- Review of in-space assembly technologies
- Utilisation of turboelectric distribution propulsion in commercial aviation:A review on NASA’s TeDP concept
- The influence of inlet swirl intensity and hot-streak on aerodynamics and thermal characteristics of a high pressure turbine vane
- Full blended blade and endwall design of a compressor cascade
