CLORKE-SFS:Certificateless One-Round Key Exchange Protocol with Strong Forward Security in Limited Communication Scenarios
Xiaowei Li,Dengqi Yang*,Benhui ChenYuqing Zhang
1 Department of Mathematics and Computer Science,Dali University,Dali 671003,China
2 National Computer Network Intrusion Protection Center,University of the Chinese Academy of Sciences,Beijing 100049,China
Abstract: Certificateless one-round key exchange(CL-ORKE)protocols enable each participant to share a common key with only one round of communication which greatly saves communication cost.CLORKE protocols can be applied to scenarios with limited communication,such as space communication.Although CL-ORKE protocols have been researched for years,lots of them only consider what secrets can be compromised but ignore the time when the secrets have been corrupted.In CL-ORKE protocols,the reveal of the long-term key attacks can be divided into two different attacks according to the time of the long-term key revealed: the attack to weak Forward Security(wFS)and the attack to strong Forward Security (sFS).Many CLKE protocols did not take into account the sFS property or considered sFS as wFS.In this paper,we first propose a new security model for CL-ORKE protocols which considers the sFS property as well as the Ephemeral Key Reveal attack.Then,we give a CL-ORKE protocol which is called CLORKE-SFS.CLORKE-SFS is provably secure under the proposed model provided the Elliptic Curve Computational Diffie-Hellman (ECCDH) and the Bilinear Computational Diffie-Hellman problem(BCDH) assumption hold.The security model and the protocol may give inspiration for constructing oneround key exchange protocols with perfect forward security in certificateless scenarios.
Keywords:key exchange protocol;strong forward security;one-round;certificateless
I.INTRODUCTION
Certificateless cryptography[1]is a hot topic in cryptography and information security field.It is a combination of public key cryptography [2]and ID-based cryptography [3].Compared with public key cryptography,certificateless cryptography does not need complicated key management.Compared with IDbased cryptography,it can avoid the problem that the Key Generation Center (KGC) knows private keys of all users,i.e.,it can solve the key escrow problem.With these advantages,certificateless cryptography is widely used in academic fields and in practice.Key exchange protocol can enable two or more parties to agree on a shared key and establish a secure channel to communicate with each other which is an important cryptography tool in information security.Bring the certificateless cryptography into the key exchange protocol,certificateless key exchange (CLKE) protocols were present.The first CLKE protocol was proposed by Al-Riyami and Paterson[1].After that,the CLKE protocol becomes a hot research point because of the advantages of the certificateless cryptography[4–7].Communication round is limited when there are multiple interferences on the communication channel.So in such a complicate communication environment,the less communication cost is spent the higher the reliability of communication can be achieved.So the one-round key exchange (ORKE) protocol is present[8–10].ORKE achieves the minimal communication cost since it only needs one round communication in key exchange.The difficulty in designing ORKE protocol is that it needs to consider all of the security properties in only one round without any confirmation message returned.In recent years,new security properties have emerged such as the Forward Security property [11]and the Ephemeral Key Reveal resistance property [12]and so on.Among them,researchers pay much attention to the strong Forward Security (sFS) which comes from the forward security[13].Forward security means the session key of a session is secure even if the long-term keys of the participants have been corrupted when the session has expired(the ephemeral parameters are deleted in an expired session).Note,the time that the long-term keys are corrupted is after the session expired in the original definition of the forward security.It is also known as the weak forward security (wFS) since the adversary against wFS is passive in the target(test)session.sFS allows the adversary can be active in the test session which means he/she can corrupt one of the participants’long-term keys before the test session.It is a strong security property since it gives more abilities to the adversary[14].Bring sFS into ORKE protocols will be difficult since the minimal communication is provided.
There is no ORKE protocol with sFS in certificateless cryptography until now since it is more complicate in this scenario.The user in the certificateless cryptography has two private keys: an ID-based key and a private key which is related to the public key.The properties of these two keys are different and the keys are used in different ways.Meanwhile,considering the ephemeral key reveal attack and sFS in certificateless cryptography will be more complicated.So designing a certificateless one-round key exchange(CL-ORKE)protocol with sFS will be a tough and interesting work.
II.RELATED WORKS AND CONTRIBUTIONS
2.1 Related Works
In this section,we first introduce ORKE protocols and the security models for key exchange protocols in cryptography,then,we consider ORKE protocol in the certificateless scenario.
ORKE protocols are the ultimate goal of researchers in cryptography since they are complex but elegant to centralize all security attributes into one round of communication.This work goes back to the outstanding thesis of Diffie and Hellman,which is called the DH key exchange protocol [2].Lots of works have been done to enhance the security of DH key exchange protocol since the messages in DH are not authenticated.Among these works,MQV protocol proposed by Law et al.is an outstanding one [15].MQV was considered very secure and efficient at that time and it was chosen by the NSA as the main key exchange protocol.However,MQV is not secure in the CK model pointed by Canetti and Krawczyk so HMQV protocol was present by Krawczyk[13].HMQV solves the Unknown Key Share(UKS)attack[16]and Key Compromise Impersonation(KCI)attack[17]to the MQV.In HMQV,Krawczyk pointed out that any of the ORKE protocols did not provide the sFS aforementioned including HMQV.The key point to sFS is that the receiver needs to use some tricks to check whether the sender has the long-term key while the session is in progress.Taking this rule,Krawczyk used a signature method to authenticate the message and proposed the SIG-DH protocol [18],Gennaro et al.use RSA hard problem to provide the sFS and proposed mOT protocol [19].However,all of these protocols do not take the ephemeral key reveal attack into account which is modeled in eCK [12].Li et al.improved the mOT protocol and proposed mOT+ protocol [20].mOT+is secure against ephemeral key reveal attack and sFS attack.
Lots of researchers look for generic constructions for ORKE protocols.Boyd et al.provided a compiler to make protocol be with sFS from any secure protocol with weak forward security[21].Bergsma et al.[22]and Yang et al.[23]provided generic constructions for ORKE with sFS in the standard model which means it does not use the random oracle.Cremers and Feltz proposed a common construction for ORKE protocols with sFS property and a strong security model called[24].Yang and Lai expanded the common constructions from two parties to multiple parties for ORKE protocols with sFS[25].Yang et al.considered a more strong model than eCK and revised the protocol proposed in CT-RSA’16[26].The trick of Yang et al.is using the smooth projective hash function to generate the key pair and complete the key exchange.
The works mentioned above are in the public key scenario or in the ID-based scenario,now we introduce the certificateless one-round key exchange (CLORKE) protocols.Al-Riyami and Paterson proposed the first CL-ORKE protocol[1].However,it only considers the basic security of the key exchange protocol.Meanwhile,there is no formal security model in [1].Swanson proposed the first formal security model for analyzing certificateless key exchange protocol [27].Swanson showed that lots of CL-ORKE protocols were not secure in her model.Original CL-ORKE protocols were proposed using the bilinear pairing operation[28–30].Among them,Zhang et al.’s protocol is efficient since it only needs one pairing operation and five multiplications by each communication party[29].Considering a more efficient protocol,CL-ORKE protocols without pairing were proposed [31–36].Among them,He et al.’s protocol is efficient [33].The trick in [33]was using the proxy signature to accomplish the key exchange.Goya et al.proposed a strong security model for CL-ORKE which considers the wKS [37].Considering the ephemeral key reveal attack,Lin proposed a CL-ORKE and was provably secure in eCK model[38].Zhang did interesting work in CL-ORKE with sFS.Zhang proposed a certificateless one-pass and two-party authenticated key exchange protocol with the sender’s sFS and gave a security model for this scenario[39].However,only the sender’s sFS are provided in [39].In summary,none of these works address the problem of how to bring sFS (both of the sender and receiver’s sFS) in CL-ORKE protocols.
2.2 Motivation and Contributions
In scenarios with limited communication,the number of communication rounds is strictly limited.For authentication and key exchange protocols,one round communication is optimal.How to realize all security attributes in one round communication is a complicated problem.It is more complicated when considering it in certificateless environment.Although some of security models have been proposed for certificateless key exchange protocols,there is no such security model considering both of the attack to sFS and to attack to the ephemeral key reveal.To address this problem,we proposed the CLORKE-SFS protocol which is provably secure in a more strong security model.The contributions are as follows:
(1).We propose a new security model for CL-ORKE protocol which is a strong security model which considers the strong forward security and ephemeral key reveal attack;
(2).We propose the CLORKE-SFS protocol which is the first CL-ORKE protocol with sFS (both of the sender and receiver’s sFS).It is secure in the proposed model and a detailed security proof is given;
(3).CLORKE-SFS can be safely applied to limited communication scenarios which make secure communication can also be carried out in complex communication environments.
III.SECURITY MODEL
The security model is based on CK model [18]and eCK model [12].In the model,there are four types of participants: the honest userUiwho honestly runs the protocol,i ∈{1,n}; the Key Generation Center(KGC) who is responsible for distributing the key to a user; the adversaryAwho can control the communication channel,i.e.,he/she can listen,insert,delete,modify and replay any message in the open channel;there is also a simulator who simulates the protocol and answers the queries fromA.The simulator runs numbers of instances of the protocol.An instance of U is simulated as a random oracle ΠiU.Atries to get some useful information from the answers of ΠiU.
In order to give a more clear proof,we need to explain the keys used in the model.In a certificateless key exchange protocol,there are four kinds of keys:theID-based keywhich is issued by the KGC,theprivate keywhich is chosen byU,theephemeral keywhich is chosen in a session,and thesession keywhich are computed in a session.The ID-based key and the private key are also called thelong-term keys.
Our model captures ordinary security attributes in key exchange protocol such as the session key security and mutual authentication since it bases on the CK model,it also captures the following strong security attributes:
Weak forward security (wFS).The adversary cannot retrieve the session key of a session when the session is completed,even if the adversary gets both of participants’long-term keys.Note,in this case the adversary is passive in the target session key,i.e.,he/she did not launch active attacks,such as forgery,impersonation,replaying message and other active attacks.
Strong forward security (sFS).The adversary cannot retrieve the session key of a session when the session is completed,even if the adversary gets both of participants’long-term keys and he/she is active in the target session.
Ephemeral key reveal security.The adversary obtains the ephemeral keys in a session,however,he cannot retrieve the session key of that session.
The ability of the adversary is simulated as the following queries:
Execute(ΠiU,ΠjU′).The simulator runs the protocol and returns the output of ΠiUand ΠjU′between the ith session of U and jth session ofU′,i.e.,the messages transmitted betweenUandU′.
Send(ΠiU,m).By this query,Acan get the output of ΠiUafter it forwardsmto ΠiU.
Partial −private −keyreveal(IDU): Using this query,Acan get the partial private key ofU,i.e.,the ID-based key ofU.
Public −key −replacement(IDU,XU):Acan replace the public key ofUwith a new one which is chosen byA.
Long −term −keyrevealb(IDU):Agets the longterm-key ofUbeforethe test session executes.The long-term-key includes the ID-based key and the private key.
Long −term −keyrevealb(IDU):Agets the longterm-key ofUafterthe test session executes.
Ephemeral key reveal(ΠiU):Agets the ephemeral keys of U in a session,i.e.,the random values(nonces)chosen in the session.Note,the random values we mentioned here are not all of the internal secrets but only the random values chosen in one session.
Test(ΠiU) .This query is using to test the conclusion of the adversary,i.e.,whether he/she can guess the session key.When the adversary takes numbers of queries to the protocol instances,he/she should choose one session as the Test session.In this session,a random bitbis chosen and ifb=1 the real session key is returned,while ifb=0 a random value is returned.Aneeds to answer where the output of theTestsession is the real session key or the random value.The advantage thatAcorrectly guesses the bit b is denoted asAdvPA(k),wherePis the protocol andkis a security parameter.Then,AdvPA(k) = 2Pr|b=b′|−1 is the bit thatAguesses.
Note theTestsession should be afreshsession.A session is said to be afreshsession if:
(1).The session and its matching session have not been asked by theSession key revealquery;
(2).IfUis asked by both ofPartial-private-key revealquery and thePublic −key −replacementquery,thenEphemeral key reveal(ΠiU) cannot be asked and vice versa;
(3).IfUis asked byLong −term −key revealbquery,then any message comes from ΠiUshould be honestly chosen byU.
The definition of a matching session we used is from[24],i.e.,sessions who have the same session identifier are the matching sessions.A session identifier is a message flow that a user sends and receives in a session.The adversary against a certificateless key exchange protocol can replace the public key of the user with the value chosen by himself,ask for the ID-based key,ask for the ephemeral key and ask for the session key.However,the adversary cannot ask for both of the long-term keys (the ID-based key and the partial private key) and the ephemeral keys together in one session.It is reasonable since nearly all of key exchange protocols are based on this assumption unless there is another secure material such as a Trusted Platform Module (TPM) [40].Note,this limitation still works even ifAreplays an honest user’s message in a session and uses this message to another session which makes one message appear in two sessions.Although it seems two sessions,Acannot ask for the long-term keys to a session and ask for the ephemeral keys to another session since the two sessions are essentially the same conversation.
Security Definition
(1).In the present of a passive adversary,if two honest parties complete a CL-ORKE protocol run then both of the participants can compute the same session key.
(2).For any Probabilistic Polynomial-Time(PPT)adversaryA,AdvPA(k)is negligible.
IV.CERTIFICATELESS ONE-ROUND KEY EXCHANGE PROTOCOL WITH STRONG FORWARD SECURITY
In this section,we propose a new one-round key exchange protocol with strong forward security in the certificateless scenario which is called CLORKE-SFS.The protocol is shown in Figure 1.
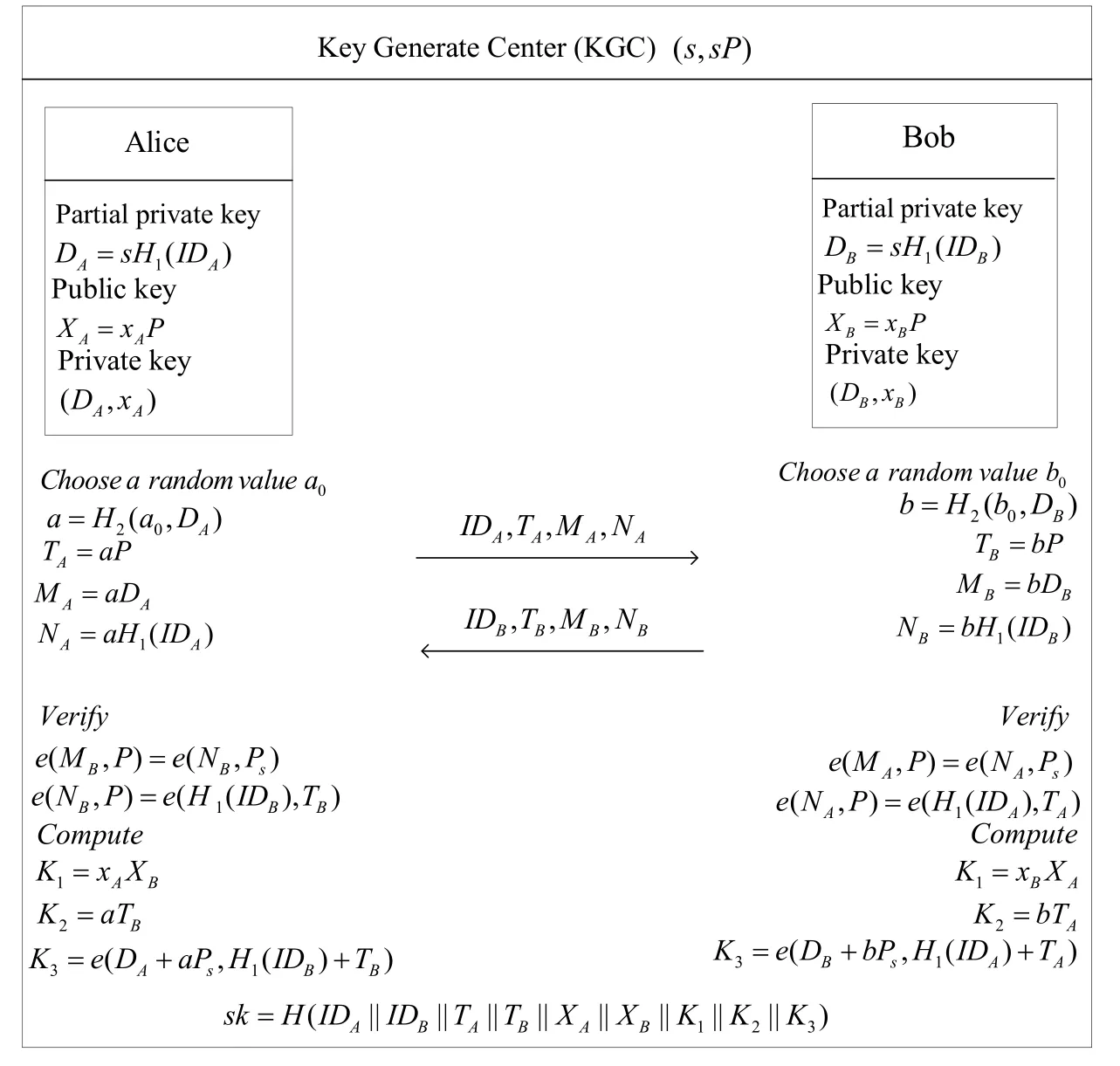
Figure 1.The CLORKE-SFS protocol.
Setup: Input a security parameterk,KGC provides the following parameters:
(1).LetG1be an additive group with a large prime orderq,Pbe a generator ofG1,G2be a multiplicative group with the same order asG1andeis a bilinear function:e:G1×G1→G2.There are three hash functions in the protocol:H1:{0,1}∗→G1,H2:{0,1}∗×G1→ZqandH:{0,1}∗2×G16×G2→{0,1}n,wherenis a given positive integer.
(2).KGC chooses a random numbers ∈Z∗qas its private key andPs=s·Pas its public key.KGC publishes parameters{G1,G2,P,H,H1,H2,e,q,sP}.
Set-partial-private-key:When a user U wants to register to KGC,he should provide his identityIDU.Upon receivingIDU,KGC computesH1(IDU)and letsDU=sH1(IDU)as U’s partial private key.
Set-secret-value:U randomly selects a valuexU ∈Z∗qand setsxUas the secret value of U.
Set-private-key:U sets(xU,DU)as his private key.
Set-public-key:U setsXU=xUPas his public key.
Key-agreement:Assume a user Alice with private key(xA,DA)and public keyXA=xAPand another user Bob with private key (xB,DB) and public keyXB=xBPwant to agree on a shared key with each other in a one-round scenario,they will take the following steps:
(1).Alice chooses a random valuea0∈ Z∗qas her ephemeral key and computesa=H2(a0,IDA),TA=aP,MA=aDAandNA=aH1(IDA),then sends (IDA,TA,MA,NA) to Bob.On the other side,Bob takes the similar operation,i.e.,chooses a random valueb0∈Z∗qas his ephemeral key and computesb=H2(b0,IDB),TB=bP,MB=bDBandNB=bH1(IDB),then sends (IDB,TB,MB,NB)to Alice.
(2).Upon receiving the messages (IDB,TB,MB,NB),Alice verifies whether these two equationse(MB,P) =e(NB,Ps) ande(NB,P) =e(H(IDB),TB) hold or not.If the equations do not hold,Alice refuses the messages.Otherwise,Alice computes the partial keysK1=xAXB,K2=aTBandK3=e(DA+a · Ps,H1(IDB) +TB).The session key between Alice and Bob issk=H(IDA||IDB||TA||TB||XA||XB||K1||K2||K3) .On the other side,Bob takes the similar operation,i.e.,on receiving the message (IDA,TA,MA,NA),Bob verifies whether these two equationse(MA,P) =e(NA,Ps) ande(NA,P) =e(H(IDA),TA) hold or not.If equations do not hold,Bob refuses the messages.Otherwise,Bob computes the partial keys,K1=xBXA,K2=bTAandK3=e(DB+bPs,H1(IDA) +TA) .The session key between Alice and Bob can be computed bysk=H(IDA||IDB||TA||TB||XA||XB||K1||K2||K3).
V.SECURITY ANALYSIS
5.1 Security Analysis
The hard problems used in the security proof are defined as follows:
Definition 1.Elliptic Curve Computational Diffie-Hellman (ECCDH) assumption.For any PPT adversary A,given random input 〈P,xP,yP〉,where P,xP,yP are the random points of an elliptic curve and they are in a group G,then the probability that A can compute xyP is negligible.
Definition 2.Bilinear Computational Diffie-Hellman problem (BCDH) assumption.For any PPT adversary A,given random input 〈P,xP,yP,zP〉,where P,xP,yP and zP are the random points of an elliptic curve and they are in a group G,then the probability that A can compute xyzP is negligible.
Theorem 1.The proposed CL-ORKE protocol meets the security definition of the security model under the assumptions of ECCDH and BCDH.
Proof.The security proof is given in the random oracle model which means all of the Hash functions are considered as the random oracle and the output of the Hash functions are random to the adversary.The simulator controls Hash functions and it records all of Hash queries to Hash functions and the corresponding answers.Moreover,In order to give a correct protocol simulation to the adversary,the simulator initializes all of honest parties,including initializing the privatekeys and the ephemeral keys.The first condition in the security definition is trivial to prove,so we do not discuss here.In order to give a clear proof to the second condition,we divide attacks to the sessions into two cases: matching sessions and no matching sessions.
Matching sessions.If attacks are against matching sessions,it means the sessions are run by honest participants.In a matching session,the adversaryAcan not only eavesdrop the messages but also can makePartial−private−key reveal(IDU)query(query to the ID-based key),Long−term−key reveralb(IDU)query,Long −term −key reverala(IDU) query,Ephemeral key revealandSession key revealquery.However,Acannot make thePublic −key −replacement(IDU,XU)query and cannot forge messages either.All of these queries fromAcan be easily answered by the simulator since the simulator sets up all of the protocol participants and knows all of internal states of the matching sessions.We further divide the matching sessions into the following cases according to whether the attacks are from KGC:
Case 1.The attacks from KGCC.
In a CLKE protocol,KGC may want to get the session key of a session.However,it can only eavesdrop on the message between two parties other than launch an active attack.In this case,the simulator only needs to imbed a random ECCDH tuple〈P,xP,yP〉into the Test session and replace the public key of both participants with aP and bP.Note,KGC cannot replace the message so he cannot replace the public keys of any participant.The secrets that the KGC can get are the ID-based keys from thePartial −private −key −reveal(IDU) query.In this case,if KGC can win the game aforementioned,i.e.,distinguish between the random value and the session key in the Test session with non-negligible probability,then the simulator can break the ECCDH assumption.The simulator runs the protocol instances and answers the queries from KGC.If KGC chooses the target session (the session which the simulator chooses as the Test session) as the Test session and it can guess the bit b in the Test session,then it means KGC must have computedK1=xAxBP=xyPand asked toIDA||IDB||TA||TB||XA||XB||K1||K2||K3H.It means KGC have computed the real session key.So the simulator can getabPfrom the Hash records,i.e.,break the ECCDH assumption.However,as we know ECCDH problem cannot be solved in polynomial time.Suppose the probability that the simulator and KGC choose the same session as the Test session is bounded by the birthday paradox which is 1/q2s,qsis the number of total sessions.Suppose the probability that an algorithm solves the ECCDH problem in timetisAdvECCDHA(t).Then we can get the conclusion that the advantage that KGC wins the game in the Test query is:
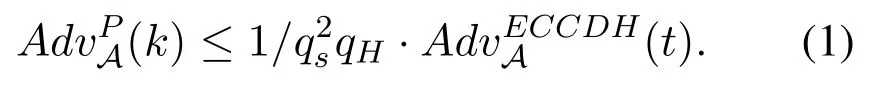
WhereqHis the number of queries toHfunction.
Case 2.The attacks from the adversary other than KGC.A also asks Long −term−key revealb(IDU)query to one party and impersonates other parties to communicate with U without the Ephemeral key reveal(ΠiU)query.
In this case,the adversaryAcan make the queries ofPartial −private −key(IDU),Long −term −key reveralb(IDU),Long −term −key reverala(IDU),Ephemeral key reveal(ΠiU) andSession key reveal(ΠiU).Note as mentioned in the security model,Acannot ask both ofLong−term−key reveal(i.e.,Long −term −key reveala(IDB) andLong −term −key revealb(IDB))andEphemeral key reveal(ΠiU)in a session.
As mentioned above,in matching sessions of honest parties,Acannot forge messages.SoAis most likely to replay the message from party A and asksLong −term −key revealb(IDB)to the other party B in the same session.In such case,the checking process of B (verifyinge(MA+NA,P) =e(NA,Ps)·e(H(IDA),TA) ) can be passed since the messages are indeed from A.We do not discuss the ordinary attacks to the CL-ORKE protocol since the attack in this case implies the case thatAonly forges message and does not askLong −term −key revealquery.Obviously,the abilities ofAin this case are stronger than that of other cases.In this case,the simulator imbeds a tuple< P,xP,yP,zP >a protocol instance,i.e.,the Test session.More specifically,sPandH1(IDA)are replaced byxPandyPandTBwhich comes from the instance of B is replaced byzP.SupposeAcan get the long-term keys of B fromLong −term −key revealb(IDB)query,i.e.,having the private keys of B(DB,xB).The purpose ofAtill cannot get the session key of the Test session with non-negligible probability.The detailed proof is as follows:
The simulator controls all of the Hash functions which means all of the queries to Hash functions must come from the simulator.So when a party with an identityIDBasks the ID-based key,the simulator first checks whether there is a record inH1.If there is no such record,the simulator chooses a random valuerBand puts a record< IDB,rB >inH1.Then,he computesDB=rB·xPas the ID-based key of B and put a record< IDB,rB,DB >in a list of ID-based key.Otherwise,there is a record inH1,then the simulator checks the list of ID-based keys and returnsDB.On receiving a query< a0,DA >toH2,the simulator cannot answer the query since he does not knowDA.In such case,the simulator randomly chooses a valuemAand puts a record< a0,DA,mA >in the list ofH2.In the same way,when queryingIDA||IDB||TA′||TB′||XA||XB||K1||K2||K3toH,the simulator cannot computeK3,then he randomly chooses a valuehi(i denotes ith query toH)as the answer to the query and puts a record in the list ofH.So the simulator can simulate all of the messages from any party correctly.Now,ifAchooses the Test session which the simulator chose,then the protocol instance is changed in Figure 2.
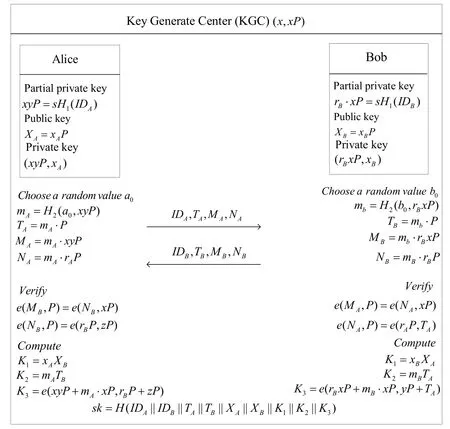
Figure 2.The simulation of the Test session.
In such case,ifAcan distinguish between the real session key and the random value in the Test session,then the simulator can break the BCDH assumption.IfAwins the game,then he must have computed the session key in the Test session,i.e.,Ahave computed,
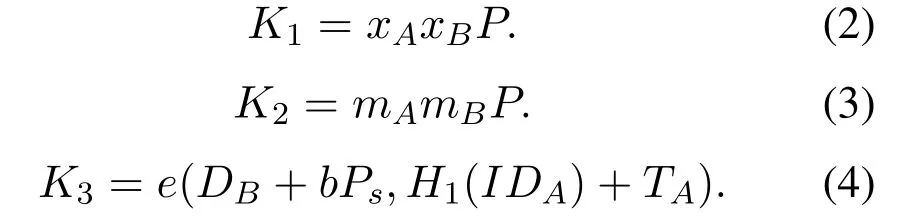
AndAhave also asked a queryIDA||IDB||TA||TB||XA||XB||K1||K2||K3to hash oracleH.Acan computeK1=xAxBP,K2=mAmBP,e(DB,H1(IDA) +TA) with the knowledge of(DB,xB),however,he cannot computee(bPs,H1(IDA)+TA).Note in this case,Aalso can askLong −term −key reveala(IDA),thenAgets the long-term keys of.However,Astill cannot computee(bPs,H1(IDA)+TA).Because if can computee(bPs,H1(IDA)+TA),then it means he can computeK3.K3can be transformed into the following form in the Test session:K3=e(DA+a·Ps,H1(IDB)+TB)=e(DA,H1(IDB)+TB)·e(a·Ps,H1(IDB)+TB)=e(DA,TB)· e(DA,H1(IDB))· e(a ·Ps,H1(IDB)+TB)=e(P,P)xyz·e(DA,H1(IDB))·e(a·Ps,H1(IDB)+TB)=e(P,P)xyz·e(xyP,rBP)·e(mA · xP,rBP+zP)=e(P,P)xyz · e(xP,yP)rB ·e(mA · xP,rBP+zP)=e(P,P)xyz · e(xP,yP)rB ·e(xP,P)mArB ·e(xP,zP)mA.
So with the knowledge ofrBandmA(the simulator controls all of the Hash records),the simulator can computee(P,P)xyzwhich means he can break the BCDH assumption.Suppose the probability that the simulator andAchoose the same session as the Test session is 1/q2sand the probability that an algorithm solves the BCDH problem in timetisAdvBCDHA(t),then the advantage thatAwins the game in the Test query:
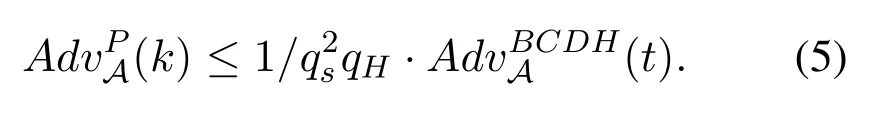
WhereqHis the number of queries toHfunction.
Case 3.The attacks from the adversary other than KGC.A asks the Ephemeral key reveal(ΠiU)query besides the Long −term−key revealb(IDU)query.
In this case,Acan get the ephemeral keys of both parties,i.e.,a0andb0.However,Astill cannot computea=H1(a0,DA) andb=H1(b0,DB) withoutDAandDBsinceAcannot ask both of the ephemeral key query and long-term key query.In this case,the simulator imbeds a tuple< P,xP,yP,zP >into the Test session to replay thesP,TAandTB.Suppose the BCDH assumption cannot be broken,thenAcannot break the security definition of the CL-ORKE protocol.The concrete proof is similar to that of Case 2.
No matching sessions.If attacks are against no matching sessions,it meansAcan forge messages to honest participants.As aforementioned,we only discuss the following case since it implies other cases.Aasks theLong −term −key revealb(IDU)query to one party and impersonates other parties to communication with U by forging the message by himself.In this case,supposeAhave askedLong −term −key revealb(IDB) and gets the private keys of B,i.e.,(DB,xB) .Then,Afurther choosesTA,MA,NAby himself and impersonatesIDAto communicate withIDB.There are two ways forAto forgeTA,MA,NA.The first way is thatAchoosesTA=aP,MA=bPandNA=cPby himself,thenAuses these messages to impersonate the party A to communicate with B.In this case,if the verification of(TA,MA,NA)can be passed,thenAcan getK3=e(DA+a ·Ps,H1(IDB) +TB) by asking aLong−term−key reveala(IDA) query to A since he already knows the valueaandDA.However,the verification of(TA,MA,NA) cannot be passed.The proof is as follows:
The simulator replacessPandH1(IDA)with random valuesxPandyPrespectively.Then the verification equations can be transformed into the following forms:
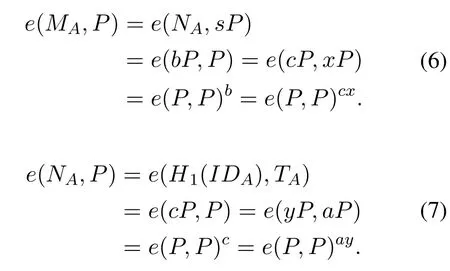
If the two equations hold,then the verifications of(TA,MA,NA) can be passed.Then,we haveb=cxandc=aywhich meansb=axy.Here we have to note,Amust know the valueaofTA,otherwiseAcannot computeK3in the session key.So in this case,ifAknowsb,then we haveb · a−1=xywhich meansxyP=b·a−1Pand ECCDH assumption is broken.IfAdoes not knowb,then we changeb=axybya−1=b−1xy.It means given three unknown values< b−1P,xP,yP >,Acan computee(P,P)b−1xywhich means the BCDH assumption does not hold.So under the ECCDH assumption and BCDH assumption,Acannot computeTA=aP,MA=bPandNA=cPby himself and pass the verification of the protocol.
SoAcannot forge a tuple(TA,MA,NA)chosen by himself and pass the verification of other parties.In order to pass the verification,Aneeds to make the second way.Atakes advantage of the messages sent by A,which meansAonly can make the replay attacks,then the verification can be passed.However,in such case,Acannot get the valueaofTA.It further meansAcannot computek3in the session key unless the BCDH assumption does not hold.The security proof in this case is similar to that of Case 2.
In summary,no matter what attacksAlaunches to the matching sessions or the non-matching sessions,supposelis a constant then the advantage thatAwins the game betweenAand the simulator is:
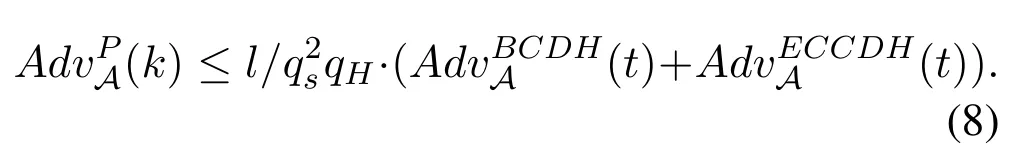
BecauseAdvABCDH(t)+AdvAECCDH(t)is negligible so Theorem 1 holds.The proposed CLORKE-SFS protocol can meet the security definition of the security model provided the ECCDH assumption and BCDH assumption hold.
VI.PERFORMANCE AND DISCUSSION
6.1 Performance
In this section,we make a comparison with some CL-ORKE protocols in computation cost and security properties.The detailed comparisons are shown in Table 1.The reason why we chose these protocols to make comparisons is that:(1).all of them consider the forward security; (2).every protocol is unique which represents each type of the CL-ORKE protocol.
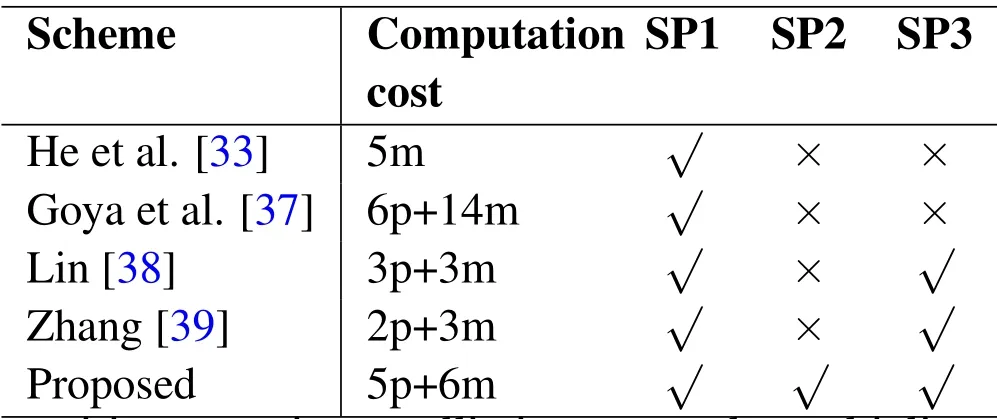
Table 1.Comparisons with related works.
p:pairing operation;m:elliptic curve scalar multiplication; SP1: weak forward security; SP2: strong forward security;SP3: resistant to ephemeral key reveral attack;
From Table 1 we can see,the proposed CLORKESFS protocol has more computation cost than that of[33],[38]and[39].However,only CLORKE-SFS has all of the security properties.If the other protocols meet the same safety standard as CLORKE-SFS,more computation cost will be added.
6.2 Advantages and Discussion
In this section,we discuss two aspects to show the advantages of CLORKE-SFS: the construction method for CL-ORKE protocols and the performance for CLORKE protocols.
Discussion on the construction method for CLORKE protocols with sFS.Actually,following the construction idea of Cremers and Feltz who proposed the compiler for one round key exchange protocol[24],the messages sent by a party should be authenticated then the sFS property could be achieved.The common trick is using a signature algorithm to guarantee the authenticity of the messages,especially the ephemeral public key.However,there is still a question that needs to be answered if we bring a certificateless signature algorithm into a secure CLKE protocol to make it realize the sFS property.The question is that the target certificateless signature maybe not secure in the model proposed in this paper.The security model enables the adversary can reveal the ephemeral secret key as well as the long-term key which is a strong challenge for the target signature algorithm.As far as we know,few signatures can resist the ephemeral key reveal attack and this is also the original intention of this paper.Moreover,we do not know the construction detail of the signature.When using the signature,users may have doubts about whether the signature algorithm has a backdoor.Even if the underlying signature algorithm is secure,more security assumptions are needed.
Discussion on the performance for CL-ORKE protocols with sFS.In fact,from the performance perspective,the proposed CL-ORKE protocol is not optimal,however,the key point of this paper is to provide a CL-ORKE with strong security.The one-round key exchange protocol with all of security properties is the ultimate goal of researchers in cryptography.It is a complicated job to complete the task.This is the motivation of the paper.Actually,compared to other certificateless key exchange protocols,the proposed CLORKE protocol only has two or three more bilinear pair operations than other schemes which cannot provide strong forward security.The few more computation cost is not so important compared with the advantages in communication round and the strong security properties.
VII.CONCLUSION
In this paper,we analyze existing ORKE protocols and give a CLORKE-SFS protocol for limited communication scenarios.The proposed CLORKE-SFS protocol takes into account the wFS security,the sFS security and the ephemeral key reveal security which are the three most important security properties in key exchange protocols.In order to give a detailed proof of the protocol,a security model for the CL-ORKE protocol is present.The security proof is given under the ECCDH and BCDH assumptions.The CLORKE-SFS protocol has the strongest security properties and the lowest communication cost which makes it suitable for limited communication scenarios such as longdistance communication.
ACKNOWLEDGEMENT
This work was supported by the National Natural Science Foundation of China (NSFC) under Grant(61902049,31960119),Joint Special Fund for Basic Research of Local Undergraduate Universities(Parts) in Yunnan Province under Grant(2018FH001-063,2018FH001-106)and Dali University Innovation Team Project(ZKLX2020308).
- China Communications的其它文章
- Joint Topology Construction and Power Adjustment for UAV Networks: A Deep Reinforcement Learning Based Approach
- Energy Model for UAV Communications: Experimental Validation and Model Generalization
- Joint Computing and Communication Resource Allocation for Satellite Communication Networks with Edge Computing
- An Intelligent Scheme for Slot Reservation in Vehicular Ad Hoc Networks
- Information-Defined Networks: A Communication Network Approach for Network Studies
- Deep Learning Based User Grouping for FD-MIMO Systems Exploiting Statistical Channel State Information

