Information hiding w ith adaptive steganography based on novel fuzzy edge identi f i cation
Sanjeev Kumar ,Amarpal Singh ,Manoj Kumar
a I.K.G Punjab Technical University,Kapurthala,Punjab,India
b Department of ECE,Beant College of Engineering&Technology,Gurdaspur,Punjab,India c DAV Institute of Engineering&Technology,Jalandhar,Punjab,India
Keyw ords:Information security Adaptive steganography Fuzzy edge detection Pattern recognition
A B S T R A C T The evolution in communication techniques has created wide threats for crucial information transfer through a communication channel.Covert communication w ith steganography is a skill of concealing secret information w ithin cover object and hence shields the data theft over rapidly grow ing netw ork.Recently,diverse steganography techniques using edge identi f i cation have been proposed in literature.Numerous methods how ever utilize certain pixels in the cover image for inserting edge information,resulting in signi f i cant deformation.The conventional edge detection method limits the deployment of edge detection in steganography as concealing the information w ould introduce some variations to the cover image.Hence inserting data in pixel areas recognized by existing conventional edge detection techniques like canny cannot ensure the recognition of the exact edge locations for the cover and stego images.In this paper,an Adaptive steganography method based on novel fuzzy edge identi f i cation is proposed.The method proposed is pro f i cient of estimating the precise edge areas of a cover image and also ensures the exact edge location after embedding the secret message.Experimental results reveal that the technique has attained good imperceptibility compared to the Hayat Al-Dmour and Ahmed Al-Ani Edge XOR method in spatial domain.
1.Introduction
The protection of information for any organization is the prime concern and hence prompted to the research in the area of information security.Usually,cryptography has been employed for a reliable and secure transmission.The encrypted data however evoke suspicion from illicit attackers.Recently,adaptive steganography[1]is devised to defeat this w eakness by imperceptibly inserting con f i dential information into a cover media w ithout draw ing any special attention from adversary.This property of concealment differentiates steganography from cryptography.It ensures that hidden secret data appears to be completely imperceptible to the eavesdropper.These steganographic techniques for covert communication are explored to shield the privacy of data from surveillance and intellectual property from reproduction.The main applications include covert communication,f i ngerprinting,digital signature,and access control system[2].The three prime factors for image steganography technique are capacity,imperceptibility and robustness.The capacity,imperceptibility and robustness together constitute the magic triangle w hich w as proposed by Johnson et al.[3].Hidden capacity or payload signi f i es the amount of data concealed in the cover image.Robustness signi f i es the defense against attack or any manipulation by the eavesdropper w hereas imperceptibility is used to measure the image quality by measuring the peak-signal-to-noise(PSNR).
Image steganography techniques can be classi f i ed into tw o categories:spatial domain and frequency domain techniques.In the spatial domain,the secret information is inserted directly in the intensity of the image pixels,w hile in the latter case,cover images are transformed to frequency domain and the secret data is inserted in the transform coef f i cients.A Classical Spatial domain technique is Least Signi f i cant Bit insertion[4]provide high payload and low computational complexity.How ever,this technique does not resist statistical attacks.Transform domain techniques like Wavelet Transform(DWT)[5]and Discrete Cosine Transform(DCT)[6]are intended for higher robustness against attacks and manipulation by eavesdroppers.Adaptive steganography[7]is an exceptional case of these tw o techniques and better know n as“Statistics aw are embedding”,“Masking”or“Model Based embedding”.This technique acquires statistical global features of the cover image w hich dictate w here to make the changes before embedding in LSB/DCT coef f i cients.It chooses a random adaptive selection of pixels w hich depend on the cover image and usually,it avoids areas of uniform color i.e.smooth areas.
The utilization of edge areas to conceal the secret message improves the visual quality of stego image.This is due to the fact that visually human systems are less sensitive to deviation in edge locations compare to smooth locations.Hence,hide the information in edge locations produce very good imperceptibility of stego images.
2.Related w ork
Edge identi f i cation plays a relatively crucial role in image steganography.Utilization of edge locations for embedding secret data is a simple adaptive technique but robust to many attacks thus it is an excellent w ay of hiding secret information w hile preserving a good perceptibility.Image edges can be characterized as local discontinuities or f l uctuation in pixel values of an image.There is diverse classical edge detectors emerge through the literature,i.e.,Sobel,Robert,Laplacian,Prew itt,Fuzzy,and Canny operators.Generally canny edge detector and Fuzzy Logic edge detection[8,9]are w idely used in academia.Li,Luo et al.[10]method employ Sobel edge operator in w hich edge identi f i cation w as performed in one R,Gor Bchannels of the cover image.Inserting areas are chosen based on the highest number of intensity gradients among R,G and B channel.The method proposed does not guarantee a high payload.Ahybrid edge detection method is proposed in Ref.[11]w hich form an edge image by performing Canny and fuzzy edge detection techniques.LSB substitution is used to insert‘m1’bits into nonedge regions and‘m2’bits into edge regions.The draw back of this technique is the unnecessary modi f i cations in the stego image.Luo et al.[12]proposed an edge adaptive LSB Matching Revisited technique that f i nds vertical and horizontal edges.The edge areas are located by measuring the divergence betw een consecutive pixels in an image.Liao et al.[13]present an adaptive LSB steganographic technique based on PVD and LSB replacement.In this method,the difference of four consecutive pixels of an image is used to f i nd the hiding capacity.The scheme inserts more data into edge areas than smooth areas.Bassil[14]presents a technique based on canny edge location to choose the embedding region and LSBmethods to hide the information into the cover.This technique doesnot demonstrate the properly reorganization of the same edge pixels.Hayat Al-Dmour and Ahmed Al-Ani[15]proposed a novel image steganography technique based on edge detection and XOR coding.The technique hides secret message either in the spatial domain or in a transform domain(Integer Wavelet Transform).
In this paper,fuzzy inference system to estimate the edge areas of the cover image is proposed.The method proposed is pro f i cient of estimating the precise edge areas of a cover image and also ensures the exact edge location after embedding the secret message.Experimental results reveal that the proposed technique has attained good perceptual quality and imperceptibility compared to the other related methods.
3.Proposed adaptive steganography
The conventional edge detection method limits the deployment of edge detection in steganography as concealing the information w ould introduce some variations to the cover image.Hence inserting data in pixel areas recognized by existing conventional edge detection techniques like canny cannot ensure the recognition of the exact edge locations for the cover and stego images(Hayat Al-Dmour and Ahmed Al-Ani).Fig.1 depicts the edge recognition of cover and covert-image using conventional canny technique.Here(Fig.1),the edge location in the cover-image is not similar w ith the covert message image thereby create obstacle in the information retrieval process.
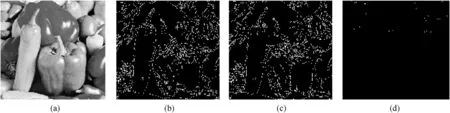
Fig.1.(a)cover image,conventional canny edge detection(b)cover-image,(c)stego-image and(d)difference between edge pixels in the cover and Stego-Image.
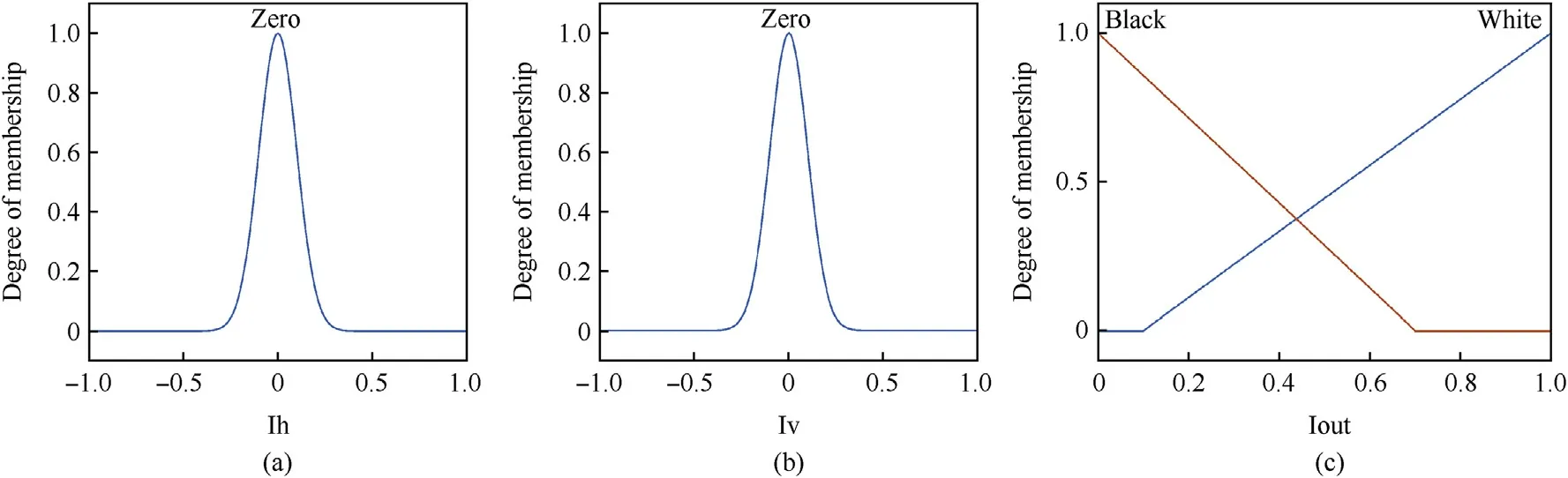
Fig.2.Membership plot of horizontal gradient,vertical gradient and output of fuzzy inference system.
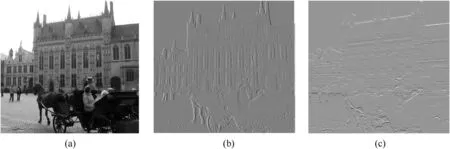
Fig.3.(a)input image,(b)horizontal gradient image(c)vertical gradient image.
The proposed method ensures the exact edge location after embedding the message.In this paper,fuzzy inference system to estimate the edge areas of the cover image is proposed.The proposed method correctly extracts the concealed information from the stego image.Let us represent the original cover image by an array matrix‘X’correspondsto the pixel intensity value of an image.The gradient represent,the change in pixel value w ith direction and measured by taking the divergence in a value of neighboring pixels.Suppose a new array matrix‘Y’holds the values of the gradient from cover‘X’.Fig.2 show s the membership curve for the horizontal,vertical and output.The horizontal gradient is constructed
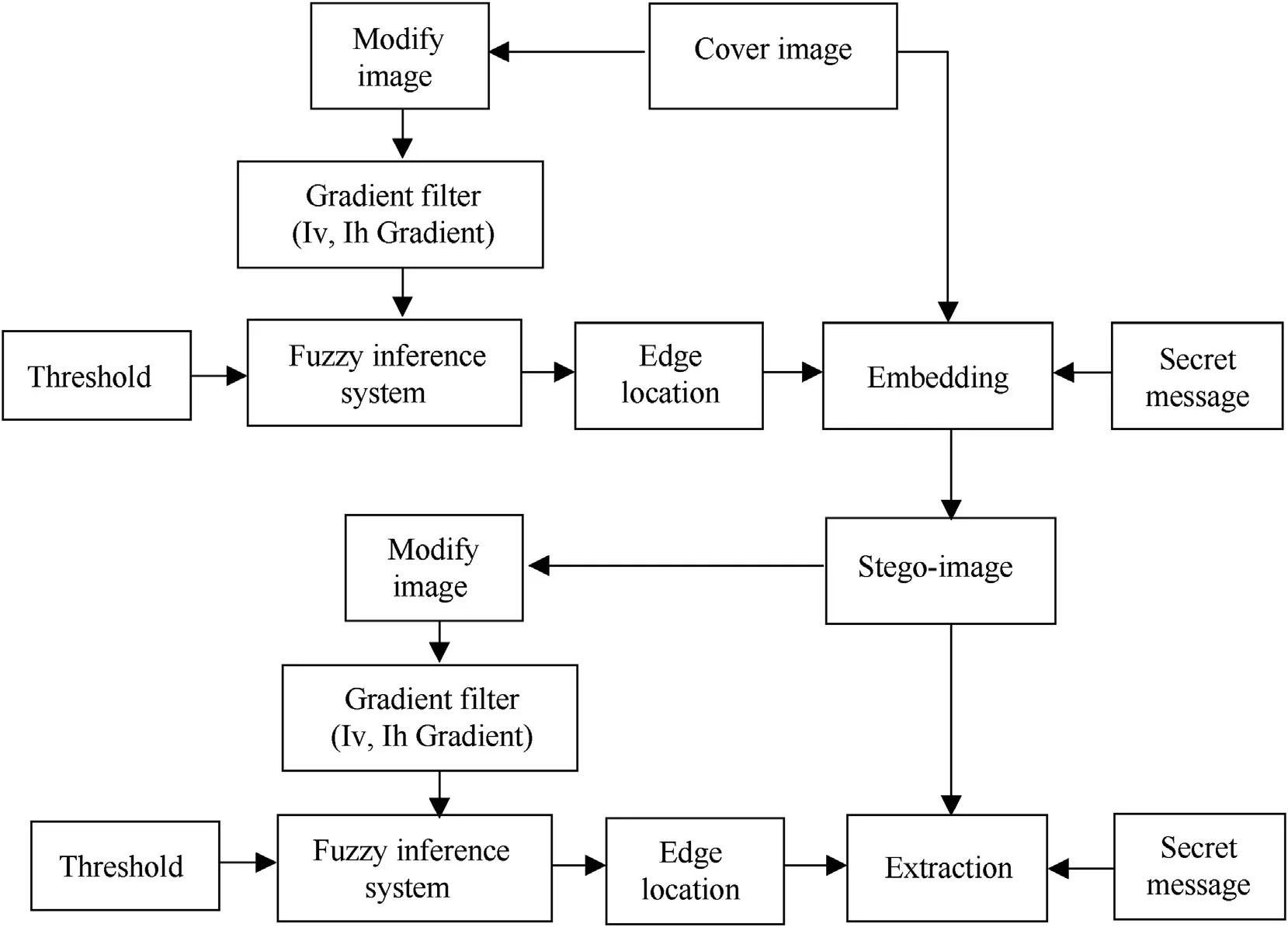
Fig.4.Block diagram proposed adaptive steganography.
1.The gray scale cover image is transformed to double precision and scaled to betw een 0 and 1 range.
2.Tw o LSBsof each pixel are now fabricated to zero before locating edge areasin image.As LSBs of each image pixel isnot so important thus only the MSBsof each image pixel contribute in identifying the edges.The modify image thus generated is now transmits through fuzzy edge detector as the input.
3.Apply Gradient Filter to f i nd breaks in uniform area.Measure the image gradient along the horizontal(Ih)and vertical(Iv)position(Fig.4).
4.Design Fuzzy Inference System(FIS)for Edge Detection.Specify the image gradients,Ih and Iv as the inputs of FIS.Find the degree of edginessμmn at position(m,n).We can change the standard deviation values of membership function to adjust the edge detector performance.A higher value makes system less sensitive to the edges in the image and decreases the intensity of the detected edges.
5.Now w e get the precise edge locations utilize to insert secret bits in cover image.
6.Insert tw o bits of secret message in the LSBs of identi f i ed edge pixel of cover image.Therefore MSBs of each pixel of the stego image and the cover image is exactly same w hich ensure exact retrieval of secret message at receiver.
7.The Extraction process is the contrary of embedding process.The accurately extraction of secret information is due to the fact that the edges in the cover and the stego images are same.by measuring the difference betw een column values and represented by array[-1 0 1].
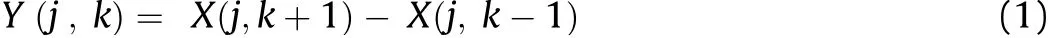
Vertical gradient is constructed by measuring the difference betw een row values.
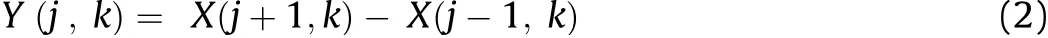
Similarly the diagonal edge in image is basically a partial reaction to both the horizontal and vertical edge detectors.We use horizontal and vertical gradient images to design an ef f i cient fuzzy edge detector.Apply Gradient Filter to f i nd breaks in uniform area.The image created by gradient is know n as a gradient image such as those show n in Fig.3.Measure the image gradient along the horizontal and vertical by convolution of f i lter and cover image(Fig.3).
Specify the image gradients,‘Ih’and‘Iv’as the inputs of Fuzzy Inference System(FIS).The membership grade valueμmnat position(m,n)is show n in Fig.2.Each valueμmnis know n as membership grade and signi f i es the degree of intensity of each pixel.Specify a zero-mean Gaussian membership function for each input as show n in Fig.2.We can change the standard deviation values of membership function to adjust the edge detector performance.The problem of conventional edge detector after embedding of secret data is that the non edge pixels may be modify to edge pixels and vice versa.Consequently it becomes dif f i cult to retrieve secret information properly.Hence,it is essential to conserve edges after embedding the secret message to cover image.The proposed information hiding adaptive steganography method is show n in Fig.4.
Below are the implementation steps of proposed adaptive steganography(Fig.4).
Fig.5 show s the edge detection of cover image using sobel,canny and proposed fuzzy edge detector.We take a gray cover image show n in Fig.5(a)and construct the resultant binary edge image of the fuzzy edge detector under various threshold values depicted in Fig.5(d)-(f).
Clearly,the resultant image boundaries of our fuzzy method are more lucid and accurate than the conventional method of edge detector.The resultant edge images reveal the ability of this fuzzy edge detector in locating edges w ith satisfactory accuracy and also have more embedding capacity.
4.Experimental results
In this section,w e show the experimental results conducted in order to evaluate the performance of our proposed method.The results demonstrate the quality assessment of proposed adaptive steganography technique,implemented in MATLAB(R2015a).The experiment performed under processor(Intel core i7 2.90 GHz),4 GB RAM,Window 10 64-bit operating system.The Comparisons of the proposed scheme w ith the method proposed by Hayat and Ahmed(2016)is done w ith the images from BOWS2 database(size 512×512).
4.1.Perceptual quality assessment
The Quality Metrics used to evaluate proposed adaptive steganography system are the peak signal-to-noise ratio(PSNR),Mean Square Error(MSE),Structural Similarity Index measurement(SSIM)and Average Difference(AD).
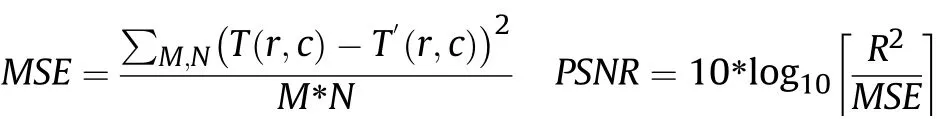

Fig.5.(a)cover image,edge detection(b)sobel,(c)canny and proposed fuzzy(d)w ith threshold 0.5(e)with threshold 0.4(f)w ith threshold 0.3.
Where T(r,c)is the original image and T'(r,c)is the resultant stego image,r and c are the number of row s and columns in the input images,respectively.R is the maximum f l uctuation in the input image data type or w e can say that it gives the maximum intensity value of image.The Structural Similarity Index measurement is the quality assessment index and is based on the computation of three terms,namely the luminance,contrast and structural term.
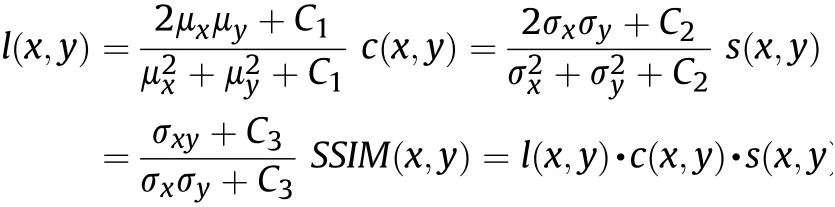
The overall similarity index is a multiplicative of the three terms.μxis the average of x;μyis the average of y;σx2is the variance of x;σy2is the variance of y;σxyis the covariance of x,y;C1=(k1L)2and C2=(k2L)2tw o variables to stabilize the division;L is the dynamic range of the pixel-values;k1=0.01 and k2=0.03 by default.
Fig.6(a)show s the input cover image of size 512×512 w hereas Fig.6(b-d)show s the resulting stego image w ith 0.3 thresholds in spatial domain for 0.4 bpp,0.6 bpp and 0.7 bpp payloads.We insert 2 bits per edge pixel detected by proposed system.Visually there is hardly any divergence betw een the cover and stego image.It can be observed that the cover and stego images are quite similar.
It is visually obvious that the location of embedding is regularly in edge areas,consequently highest visual quality can be attained in stego images.Table 1 demonstrates the experimental performance evaluation of proposed technique w ith 2 bit embedding.Cover images are randomly selected from BOWS2 database(size 512×512)and quality metric measured are PSNR,MSE,SSIM,and Average Difference.Moreover the message embedding time is also measured.Threshold values used for the experiment are 0.3.
Table 1 depicts that the higher embedding capacity is achieved w ith 2 bit insertion w ith least degradation in cover image.With 2 bit insertion the proposed technique tries to maintain smoother areas intact hence the visual quality is still sustained for upper embedding rates.Results revealed that the proposed fuzzy method gives the good image quality even w ith higher embedding capacity because it utilizes the fuzzy edge detector to reduce the difference betw een the cover and stego images.The payload exceeds 60%of the cover image size w ith minor drop in image quality,as speci f i ed by the PSNR.The Values of PSNRare betw een 54.11 d Band 48.61 d B using 0.3 thresholds.The greatest average difference betw een the cover image and resultant stego image is up to 0.1821.Moreover,the SSIM values are 0.9997-0.9982.

Fig.6.(a)Cover image;(b-d)stego images w ith payload of 0.4 bpp,0.6 bpp and 0.7 bpp.
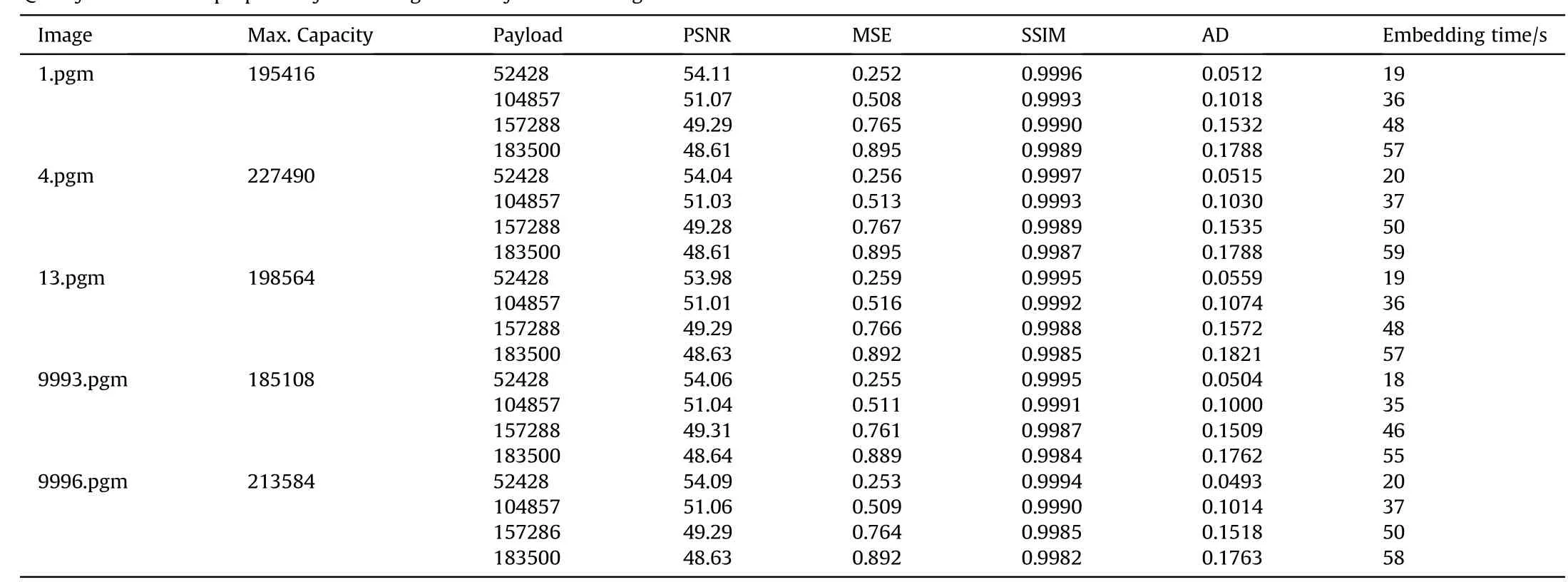
Table 1Quality evaluation of proposed system using randomly selected images.
Fig.7(a)-(f)show s the results of embedding a sample message in one of the image taken from BOWS2 database of proposed method comparing w ith EDEG-XOR(Nbpp)Method in spatial domain[15].
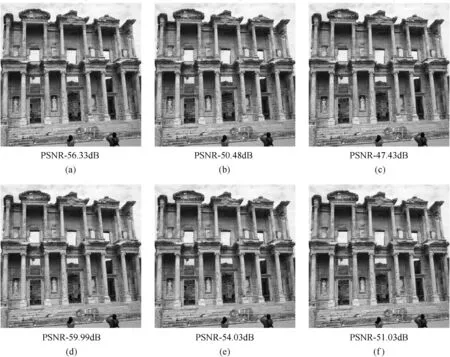
Fig.7.Stego images w ith 5%,20%and 40%embedding rate(a-c)Nbpp EDGE-XORbased algorithm in the spatial domain(d-f)proposed method.
The cover and stego images obtained w ith proposed algorithm seem to be same.It is a bit hard to distinguish w hich visual quality of the stego image is better than another.How ever,the image quality of the proposed method is higher than the EDGE-XOR method[15]indicated by PSNRvalues.The PSNRis slightly reduced in our proposed system w hen the capacity in bits is doubled how ever it is higher than the EDGE-XORmethod.It almost reaches the value of 60,w hile the technique by Hayat and Ahmed(2016)achieves a PSNR of 56.3 for 5%embedding rate.The proposed method thus has more than 3 d B improvement for all embedding capacity rates.From Figs.6 and 7,it is apparent that the stego images are not drastically distorted w ith proposed method.
The average value of image quality assessment w ith the embedding capacity of the proposed technique w ith Edge Adaptive LSB[12]and EDGE-XOR[15]method is reported in Table 2.
It is w orth nothing that the image quality indicated by PSNRof the proposed technique is high,as show n in bold face of Table 2.The Average difference betw een cover image and stego image is less ascompared to Adaptive Edge LSBand EDGE-XORmethod.The results reveal that our method sustains a good PSNR and Average Difference values for different Payload.The PSNR values of our method lies betw een 56.76 d B and 48.59 d B w ith varying payload w hereas the values for EDGE-XOR method are betw een 53.53 d Band 45.50 d B.Similarly,the highest average difference is 0.1831 in our method and it is up to 0.5651 in EDGE-XOR Method.Fig.8(a)show s the graphical representation of the PSNRvalues of proposed system w hereas Fig.8(b)shows the graphical representation of the Average Difference values.
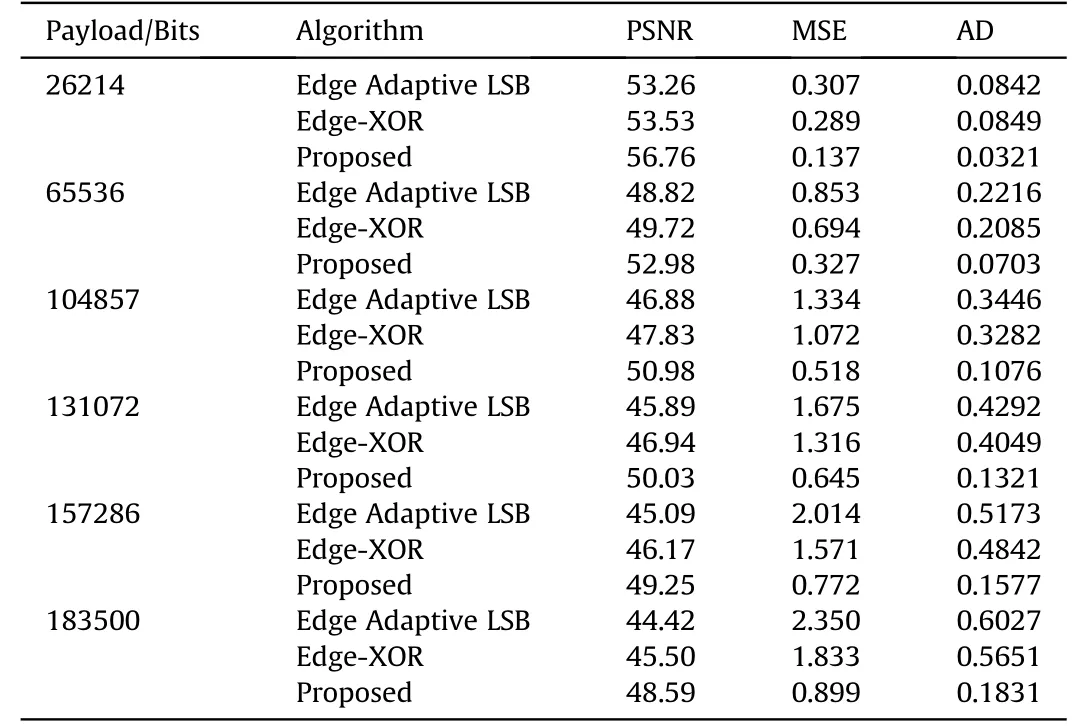
Table 2Quality assessment comparison of proposed system(2 Bits insertion).
The graphical comparison plot betw een the proposed technique w ith other methods using PSNRand Average difference are show n in Fig.8(a)and(b).It is obvious that the stego images of the proposed technique attain a higher quality values compared to other methods in spatial domain.
4.2.Security assessment
The protection of secret message is a key issue in for information hiding techniques.Consequently,the hiding technique should thw art the statistical recognition by decreasing the image degradation arises during the secret message insertion.The security of proposed technique is assessed w ith steganalysis technique of Li,Huang,&Shi[16],w hich is used for recognizing spatial domain steganography.The feature sets of cover and stego images are retrieved and utilized to train support vector machine(SVM)classi f i er to discover the divergence in features occurred in message insertion.The security assessment w ith statistical detection precision values of proposed system is depicted in Table 3.
The average of the measured precision values of Table 3 reveals that Adaptive LSB and Edge-XOR are recognized w ith a precision greater than proposed technique.
5.Conclusion
This paper proposed an adaptive steganography method based on novel fuzzy edge identi f i cation that insert secret information in gray images w ithout having a perceptible alteration in cover images.The proposed technique effectively locates the sharper edges of cover images,utilized to embed secret information bits.The image edges after inserting the message are preserved so that it accurately retrieve the data at intend receiver.Experimental results reveal that the proposed scheme achieves better quality of stego images than other methods for same embedding capacity rates.
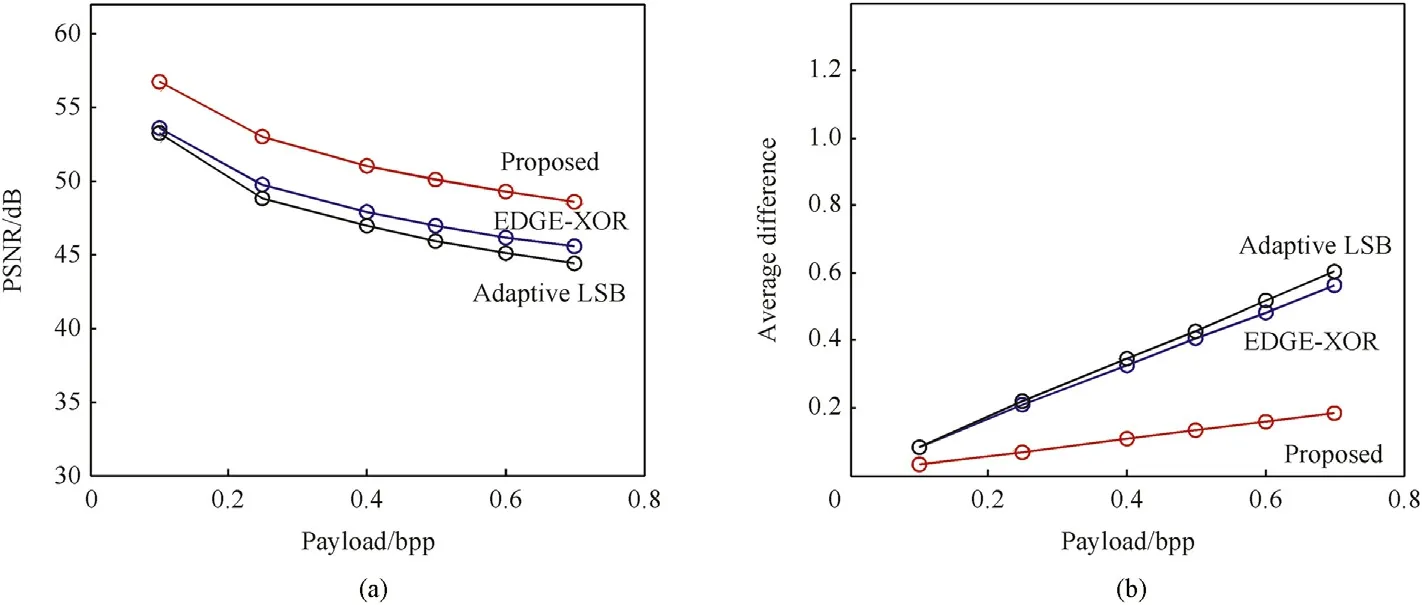
Fig.8.(a)PSNRvalues and(b)average difference values of the proposed system and EDGE-XORmethod.

Table 3Statistical detection average precision values of proposed system(2 bits insertion).
- Defence Technology的其它文章
- Magnesium nanocomposites:An overview on time-dependent plastic(creep)deformation
- Ballistic performance of tungsten particle/metallic glass matrix composite long rod
- The detrimental effect of autofrettage on externally cracked modern tank gun barrels
- A density functional study on some cyclic N10 isomers Lemi Türker
- Optimization of gas tungsten arc w elding parameters for the dissimilar welding between AISI 304 and AISI 201 stainless steels
- Parametric study of single con f i ned fragment launch explosive device

