A Trusted Attestation Mechanism for the Sensing Nodes of Internet of Things Based on Dynamic Trusted Measurement
Bei Gong, Yubo Wang,*, Xiangang Liu, Fazhi Qi, Zhihui Sun Faculty of Information Technology, Beijing University of Technology, Beijing 004, China China Electronics Standardization Institute, Beijing 00007, China Institute of High Energy Physics, Chinese Academy of Sciences
I. INTRODUCTION
Internet of things makes that plenty of terminal entity in the physical world is connected to the sensing environment via the Internet, and the rise of the Internet of things make the long gap between the terminals and the Internet to become smaller. After the rise of the Internet,the Internet of things once again opened a new information technology revolution [1].Internet of things makes that interactive communication will no longer be controlled by people and the end, but it will also contain interaction and communication between things and things, people and things, things and people in each other. And this change also makes objects more intelligent and programmatic to complete the interactive communication between people and things, things and things and people interact with each other so that it can produce new implementation techniques and application scenarios [2], and further promote the fusion of man, nature and the social environment. From the inner demand and the external presentation form, the Internet of Things is the reality of the world in the information world. It can be regarded as a bridge between the real world and the virtual world through information technology and map people and things in the real world into cyberspace [3-4].
Internet of Things has been widely used in industrial control, intelligent city, environmental protection and other areas [5-6]. In these areas, it is necessary to achieve Real-time feedback control based on the data collected by the sensing node, such as industrial control in the production line of field control, wisdom urban traffic, fire, water supply, power supply and gas related services, real-time monitoring of forest fire and so on. The premise of real-time feedback control is that the sensing node itself is trusted, otherwise the result of feedback control is unpredictable and will lead to catastrophic consequences. Therefore, it is necessary to confirm and track whether the sensing node is trusted, and it also needs to study the dynamic trusted metric mechanism and trusted attestation mechanism of the node.
The trusted measurement study of internet of things sensing layer node will not only improve the safety of the Internet of things,but also reduce the overhead due to untrusted in preventing and monitoring. However, the research on the trusted measurement of the existing nodes in the sensing layer of the Internet is not satisfactory. First of all, the current research on trustworthiness measurement depends on the specific application scenario [7].It not only has poor universality, but also lack trusted measurement model for object-sensing nodes in the internet of things. In the literature[8], it is considered that the trusted operation of sensing nodes relies on the real-time monitoring and measurement of the state and behavior of these nodes. Therefore, the research of static and dynamic metrics mechanism for sensor nodes is the key to ensure the trusted operation of sensor nodes. In the literature[9], it is believed that the current credible measurement mechanism has the following challenges in the sensing layer: (1) limited node resources, (2) heterogeneous nodes, (3)lack of facility support, (4) fragile wireless channel. However, the trust mechanism of the Internet of things sensing layer nodes through the trusted metric is faced with some of the following challenges: (1) it cannot use a unified credible measurement mechanism due to heterogeneous environment, (2) sensing node deployment and application patterns make the traditional security policy ineffective, (3)different application scenarios make the interaction between nodes exist unknown mode.
Therefore, in order to realize the real-time trusted monitoring and tracing of the sensing nodes, this paper proposes a trusted attestation mechanism of node based on dynamic metric.Firstly, a dynamic trusted metric model of sensing nodes is proposed, which quantifies reasonably the interaction between nodes,the behavior of nodes and the state of nodes.Finally, according to the characteristics of different sensing nodes, the overall prediction,feedback control and trusted measure can be dynamically applied to the sensing nodes, and the trusted value of the sensing nodes can be dynamically reflected. Then, on this basis, a revocable group signature mechanism of local verifier is proposed, which is used to complete the trusted proof of the node and prove the security of the mechanism under the standard model. The simulation results show that the trusted authentication mechanism proposed in this paper can effectively guarantee the trust of the node data transmission, realize the dynamic tracking of the node reliability, and have less impact on the system performance.The following sections are as follows: the second chapter introduces the related work and attestation process; the third chapter discusses the node dynamic trust measurement model;the fourth chapter talks about group signature mechanism and analysis the safety of it; the fifth chapter is the simulation experiment; the sixth chapter is the conclusion.
II. RELATED WORK AND TRUSTED ATTESTATION PROCESS
2.1 Related work
2.1.1 Trusted measurement related
research
In the Internet of Things, most of the research is to establish a trusted measure model of the sensor nodes based on the state of the nodes and the evidence of the behavior. Literature[10] illustrates a trusted metric model based on the state of data transmission. The model focuses on the reliability of data transmission,but lacks a measurement of the trusted state of the source node and the destination node.In the literature [11] demonstrates a credible measurement model, which is applied to the vehicle network. The defense of the attack is realized mainly through the metric of the identity factor. The credibility measure of the model is subjective and is only used to measure the security state of the object reference.Literature [12] constructs a trust metric model that can perform dynamic detection of node behavior on the basis of witch attack detection. In the literature [13-15], the author makes a discussion on how to measure the trustworthiness of the Internet-aware nodes in the car network application scenarios, and discusses the trusted metric mechanism of the vehicle-aware nodes and the trusted group network mechanism of the sensing nodes, but applied to the car network in the credibility of the application mechanism is too narrow, universal poor. The literature [16] comprehensively discusses the trust research mechanism and the access control mechanism of the Internet of Things in the industrial Internet, and makes a detailed discussion on the real-time measurement and control of the sensing nodes in the industrial Internet. However, the industrial Internet application scene is only an application of the Internet of things scene. The real-time measurement and access control mechanism is too much pursuit of computing efficiency, and portability is poor. In [17], the author makes a discussion on the trusted measurement mechanism of the sensing node of the Internet of Things in the family pension, and focuses on ensuring the reliable operation and timely response of the sensing node. Literature [18]mainly discusses the trust measurement mechanism of the nodes in the medical and health field. The trusted measurement mechanism mainly realizes the real-time monitoring of the node based on the identity authentication and the access control mechanism, but the mechanism is too dependent on the hardware of the equipment and the application prospect is too narrow. Document [19] achieves a trusted measure of wearable devices based on the user’s biometrics, but the mechanism is only applicable to the field of wearable equipment.Literature [20] in Internet video monitoring application field puts forward a trusted measurement model which is suitable for video surveillance equipment. This mechanism can be applied to the intelligent camera, but this calculation process is too complicated, energy consumption is too high, resulting in a significant reduction in the credibility of the node measurement results.
Literature [21] puts forward the multidimensional awareness node trust metric model,and the trust values of the measured nodes in this model contain three parts: supervisor trust, recommendation trust, and associated trust. The higher-level node that measures the node will query the node’s trusted recommendation to its neighbor node, and calculate the direct trust value of the node according to the node’s own state at the same time. Finally,the node trust value is calculated according to the association degree of the node. The model can effectively find malicious nodes, but the calculation process is too cumbersome, energy consumption is too high. Based on the cloud model, a trusted measurement model of the sensing node is proposed in the literature [22].The model can construct the measurement model according to the communication radius and the computational feature of the sensing node, which can effectively reflect the change characteristics of the node’s trusted degree,but the model needs to occupy a large number of communication channels and could significantly affect the normal data transmission. Literature [23] proposes a trust evaluation model based on node reputation, which is based on the Bayesian full probability model. However,the Bayesian full probability trust assessment process requires sufficient prior probabilities event, and the collection of the evidence is a very difficult process. In the literature [24],the trust metric model of sensing nodes is put forward from the perspective of game theory.The relationship between the interaction and trust between nodes is discussed from the countermeasure income model. However, the model is too concerned with the trust income and neglects the data transmission task of the sensing node, which leads to the disconnection from the practical application.
2.1.2 Remote attestation research
Remote attestation originated in TCG (Trusted Computing Group), which is the process of confirming the correctness of the information.By proving, the external validation entity can identify the protection capability, protection area and the source of the trust, and complete the identity of the platform authentication in the communication [25]. However, the remote attestation of TCG in the attestation process needs to provide the corresponding value in the platform configuration register,and it is easy to expose the platform configuration (such as the platform running software version, etc.), so that the platform is easily attacked by an intruder. At the same time, the measurement of the platform configuration is done at system startup. This attestation mode can only provide a static proof and cannot guarantee run-time integrity.
In order to overcome the shortcomings of TCG remote attestation, a large number of hybrid remote attestation models have been proposed. Based on the language-based virtual machine technology, a remote attestation model with complex, dynamic, high-level program attributes and platform independence is proposed by combining the remote attestation and the virtual technology with the semantic remote attestation model [26]. However, the semantic remote attestation model can only prove the relative high-level application without monitoring the identity of the platform, so the behavior information and identity information is not bound, and the model does not reflect the platform identity.
Another type of hybrid remote attestation model is a property-based remote attestation model [27-28] that passes the system configuration to a trusted third party (TTP), which is derived from TTP and issues the corresponding attribute certificate, so that the attribute certificate is sent to the verifier to prove the credibility of the platform when the authenticator needs to verify the platform trust. However, the mechanism requires TTP to generate the property certificate, thereby adding TTP to the TCB, increasing the complexity of the TCB. It is necessary to dynamically determine its corresponding attributes according to the system configuration, and how to support the attributes of the system without detailed description. The model can only verify the system configuration information and cannot reflect the dynamic behavior information of the system. Based on the RSA key system, the signature is relatively long and the computational complexity is high.
Seshadri et al proposed a remote attestation for embedded devices without prerequisites for TPM [29]. After that, they also presented a remote code integrity verification solution in conjunction with legacy systems. Pioneer [30],which included a two-stage challenge-response protocol, but the model added a network delay Δtnetworkand network latency is difficult to predict due to various unknown reason, so it is difficult to actually run. Besides, the model does not have proof of identity verification,and it is vulnerable to posing as an attack.
In recent years, some scholars have proposed a behavior-based remote attestation model [31-32]. The behavior-based remote attestation model defines a behavior measurement module to collect system-related behavior information and to verify the credibility of the system’s behavior history as a proof of the trust of the platform. But behavior-based teleworking uses a whitelist form in its trusted behavior anticipation strategy and requires that all actions be known, and in fact most of the behavior is unknown and that there are difculties in achieving it; and it is necessary to record the system behavior, increasing the overhead of the system and affecting the performance of the system.
2.2 Trust attestation process description
The trusted measurement model of nodes can calculate the trusted degree of node at any moment. The data transmission node needs to prove its own trust when transmitting data,which needs to send the information related to the node reliability to the remote node. The remote node inquires the node at the higher level of the node according to the information it receives whether it is an untrusted node, and decides whether to transfer data to the node based on the query results. The specific process is described as follows:
1. The data sending node formats its own trust, timestamp and other attributes into a remote proof vector;
2. The data sending node and its parent node complete the group signature of the remote proof vector (the group signature satises the revocable and forward security);

Fig. 1. A remote attestation mechanism based on the trusted degree of the node.
The proof mechanism has the characteristics of node measurable, monitorable and extensible, which can effectively conrm the data source and improve the usability of the system.
As shown in Figure 1, the mechanism presented in this section first formats the proof data of the node into a remote proof vector and then select a revocable group signature mechanism. This mechanism can achieve the proof of security under the standard model and have the characteristics of no relevance back at the same time conform to the traceability,anonymity, some security requirements, such as correctness.
The main research of remote attestation mechanism based on the trusted degree of the node includes: 1 Remote proof vector formatting, node external proof content is based on the third chapter of the credibility and node-related description to abstract, and it at least should contain node credibility, timestamp, node computing environment and other attributes; 2 Signature algorithm, the design of the revocation of the signature method is under the standard model. The method has node traceability, which can effectively protect the anonymity of the node security needs. The method also has high security and practicability, and satises the backward association,and the signature algorithm has better environmental adaptability; 3 It can be based on remote attestation results to trace and track the authenticity of the node in real time.
III. THE DYNAMIC TRUSTED MEASURE MODEL OF SENSING NODE
3.1 Formal description of sensing node
According to computing power and energy,there are three types of nodes in a sensing network: ordinary nodes, cluster head nodes and data aggregation nodes. These three types of nodes assume different functions: ordinary nodes only collect and transmit data, cluster head nodes manage and measure ordinary nodes, and cluster head nodes also collect data from ordinary nodes and send data to data aggregation nodes, data aggregation nodes monitor all other nodes in a region and send data to the application layer of Internet of Things.According to the functions of different nodes,different nodes have different formal descriptions. The ordinary nodes should include the identity information, the computing environment and the data transmission status, so the formal description for the ordinary nodes can be described as follows:
(1) Identification
Node identifier contains two componentsidandpa,idincludes the network numberni, identity authentication keykand the permission informationpmandpais the physical address in sensing network, so node identifier can be formalized asID=(id,pa);
(2) Computing environment
The node computing environment contains hardware information and software information. Node computing environment can be formalized ashwis the hash value of the hardware information ,hois the hash value of OSloader,are the applications running on the nodes,are the protocols;
(3) Data transfer status
Ordinary nodes are only responsible for collecting and transmitting data, data transmission status includes the data that should be sent and the data that actually has been sent and timestamp. So, data transfer status can be formalized asdris the data that should be sent,dsis the data that actually has been sent,tbis the timestamp when data is sent,adis the destination address of data.
According to the above description,is the formal description of the ordinary node. Cluster head nodes and data aggregation nodes also have the attributes as identification, computing environment and data transfer status. Unlike ordinary nodes,the cluster head nodes manage and measure the ordinary nodes and the data aggregation nodes manage and measure the cluster head nodes, so the data transfer status of Cluster head nodes and data aggregation nodes can be formalized as follows.
(4) Data transfer status of cluster head node / data aggregation node:
The data transmission status of the cluster node and data aggregation node has a similar formal description, it can be formalized by the following sequence:represents a cluster head node / data aggregation node requests the data that the ordinary nodes/ cluster head nodes should send,timestamp,dr,ds,tb,adare the same with Formal description of ordinary node.
(5) The list of nodes maintained by cluster head nodes / data aggregation nodes
Cluster head nodes / data aggregation nodes manage and measure ordinary nodes/ cluster head nodes, and each node maintains an ordinary node / cluster head node list, the list can be formalized asL=(N,T).N=(w1,w2. ......wn) represents ordinary nodes /cluster nodes (wirepresents the hardware, software configure and other information),T=(t1,t2 . ......tn) represents the trust of each node, so the formal description of the cluster head node / data aggregation is(ID,NE,Ds,L). represents the
3.2 The trust measurement model for sensing nodes
If a new sensing node begins to work, its parent node (parent node may be the cluster node or the data aggregation node) needs to confirm whether its initial state is trusted. Its initial state is trusted, it can collect and transmit data,and at this time the parent node needs to confirm whether the node is trusted during operation by the dynamic measurement. Section 3.3 will elaborate the initial status measurement of sensing nodes, and Section 3.4 will elaborate the dynamic trusted measurement of the sensing nodes.
In the sensing layer, the measurement of the data aggregation node is achieved by the upper layer nodes. Therefore, this section discusses the trusted measurement process that the ordinary node and the cluster head node are regarded as measured nodes. Figure 2 describes the trusted metric fl ow of the nodes logically
As shown in figure2, measured nodes arerstly achieved the initial state measurement,and then measured nodes will be dynamically measured (because the initial trusted state of nodes is not represent for trusted behavior of nodes, which needs comprehensive node dynamic state to judge whether the node is trusted). Then the superior nodes feedback control according to the measurement results of measured nodes.
3.3 The initial state trust measurement for the sensing node
Before the sensing nodes start to collect and transmit data, it is necessary to confirm whether the initial state of each sensing node is trusted, the initial state trust measurement of each sensing node needs to conrm that the hardware and software of the sensing node has not been tampered with.

Fig. 2. The trust measurement fl ow for sensing nodes.
According to the formal description of sensing nodes in section 3.1, compared with ordinary nodes, cluster head node computing ability is stronger, and it has higher energy. So the cluster head nodes manage and measure the ordinary nodes. Similar to the ordinary nodes, the data aggregation nodes manage and measure the cluster head nodes.Through the establishment of the trust chain from the ordinary node to the data aggregation node, it can ensure that the initial state of the sensing layer node is trusted. Givenis the hardware and software configuration information value of the sensing node, and the hash of hardware configuration ishw,the hash of osloader isol, the hash of operating system kernel isck, the expansion measurement hash of the applications in the node isGiven the expected measurement of hardware and software configuration information value stored in the upper node is
and the upper node will computeIfVis equal to 0, the sensing node is not trusted,otherwiseISTis defined as the initial state measurement function:
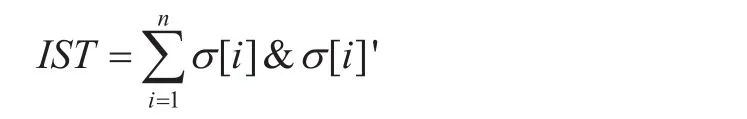
Given a threshold valueIt, ifIST>It, the sensing node can start to work.
3.4 The dynamic trust measurement model for sensing nodes
The sensing network of the Internet of Things includes data aggregation nodes, cluster head nodes and ordinary nodes. The dynamic measurement of these three types of nodes,monitoring the interaction between different nodes, measuring and analyzing the trusted measurement of the perceived network computing environment and the feedback control of the nodes are important prerequisite for ensuring the dynamic trusted operation of the perceived network. The main goal of modeling the dynamic trusted measurements of nodes is to quantify the interaction between different nodes, the behavior of the nodes and the state of the nodes. Finally, according to the relevant characteristics of different nodes, the overall trusted measurement, prediction and feedback control of nodes are achieved.
In a given sensing network area, the sensing node of the region isBased on the formal description of the previous node,consists of three types of nodes: (1) ordinary perceived nodes,This type of nodes is responsible for collecting and transmitting data; (2) cluster head nodes,the type of nodes is responsible for managing the ordinary sensing node of its communication range and acts as a relay node for data transmission; (3) data aggregation nodes, this type of node is a bridge between the Internet and the sensing network, and is responsible for managing data aggregation nodes in the region.
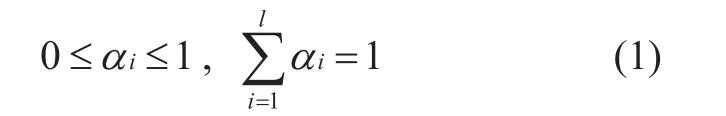
Definition 3-1Suppose that
is the trusted measure function of cluster head nodeηπfor ordinary nodeηi, andis calculated as follows:

According to Equation (2) represents the trusted measure ofηi, the trusted level ofηican be confirmed by the calculation result of Equation (2), the closer the trusted measure ofηiis close to 1, the higher the trusted level ofηπis, the higher the service priority within the communication radius ofηπ, which means the priority ofηπreceives and processes the data sent byηiis higher. The trusted measure ofηiis time-dependent, so it is necessary to mark the trusted measure ofηiwith the time stamp t.
Definition 3-2According the calculation result ofktrusted levels can be determined,(There are three types of trustworthiness in this paper: untrustworthy, pending and trusted), supposeis a set of service levels ofηiwithin the communication radius ofηπ,then the service level function calculation process is described as follows:
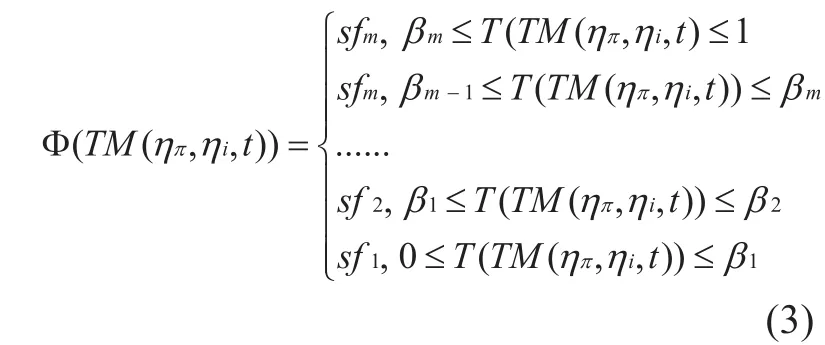
{sf1,sf2, .....,sfk} is determined by the actual need of perceived network, according to Equation (2) and Equation (3),ηπcan confirm the service level ofηiand thenηπclassifies the node service sequence within the communication radius according to node trusted, to make sure the data is trusted.
3.5 The trust measurement function
In order to achieve real-time feedback control of perceived nodes, the upper node of the sensing node needs to monitor the trusted state of its lower node in real time, so it is necessary to make real-time trusted metrics for perceived nodes. In order to be able to accurately reflect the real-time trusted state of the node,real-time trusted measure of perceived nodes from multiple dimensions is realized by sending behavior、trust risk and node validity to node data. The following is a detailed description of the node’s trusted measure function:
Definition 3-3Perceived node data transmission state metric function
The main task of a sensing node is to perceive and send data, so its data transmission status is an important indicator of whether its state is trusted, supposeηπrequiresηito send dr data packets in timeε,ηisent ds data packets actually(ds≤N ), Thenηπ’s calculated value forηi’s trusted in the data sending state at timeεis calculated as follows:

The repetition rate of the packet sent by the sensing node is an important basis for judging whether the sensing network is trusted, assume that R is the repetition rate sent by the sensing node data packet, andθis the malicious node threshold, The closer theRis toθ, the more entrusted the node data transmission status is.The trusted rate of the perceived node data transmission status based on the data packet repetition rate can be described as follows:
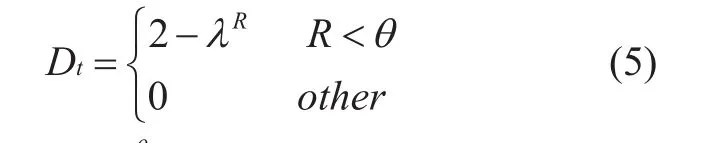
Whereλ>1,λθ=2,θis determined by the security policy of the perceived network.
The data transmission delay is also an important indicator of whether the node data transmission status is trusted, supposetis the delay whenηisends data toηπ. Iftis less than the delay thresholdγspecified in the sensing network, the data transmission state ofηiis trusted. On the contrary, iftis more than the delay thresholdγ, the possibility thatηiis a malicious node increases. So, the trusted interval of the sensing node data transmission state based on the data transmission delay can be described as follows:
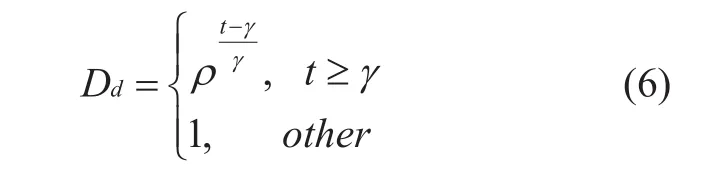
Whereρandγθis determined by the security policy of the perceived network.
Equation 4 to Equation 6 is a trusted measure of the state of data transmission for a time atηitime, in order to calculate the trusted state ofηi’s data transmission status more comprehensive and accurately, need to take a comprehensive look, at a period of time,ηi’s data transmission status. Assume inTwtime,ηπrequests n times to send data to nodeηi,Assume that the measure of the state of the n times data transmissions fromηπtoηiissupposeDt1 is the oldest measure of the past,Dtnis the measure of the current data transmission status, thencan be described as follow:

f(i) is the time decay function,f(i)∈[0,1],f(i) can smooth data which at different time by sending State trusted measure. As trust falls over time, the closer the metric to the current moment is, the higher the weight. The time decay function reflects the characteristics of the trust age lag. The time decay function can be described as follows:

The data transmission behavior trusted computing function proposed in this section based on the time attenuation function has the following advantages:
By introducing the time function, the data transmission state trusted measurement function proposed in this paper has the following advantages:
(1) The time decay function accurately reflects the characteristics of trust over time,making the calculation of the trusted level of data transmission state more accurate and close to reality;
(2) the introduction of the time recession function can reflect the influence of the historical confidence level of the node on the current confidence level, which can be used to calculate the confidence level of the nodes from a broader and more equitable perspective.
Risk and trust are interdependent, and trusting an entity is necessarily associated with the risk of failure of trust. Therefore, for the risk behind the perceived node’s trusted value, this paper solves the risk benefit theory in economic theory. According to the value of the functionthe risk function of the node’s trusted measurement value is described as follows:

Definition 3-4formula (9) is used to describe the influence of the uncertainty of the data transmission state on the trusted of nodes.Due to the uncertainty of data transmission status, the effect of risk on the transmission state of data of nodes is shown below:
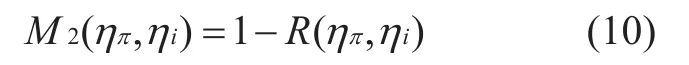
Definition 3-5If the set of nodes that have interacted withηiisReferring to the trust model in human relations,to assess whether a person is trusted, it not only needs to assess whether his own behavior is trusted, but also needs to refer to the trust of their interpersonal counterparts. The confidence level of people whose communicative object is highly trusted and whose communication object is obviously different. Similarly,the trusted measurement valveηiis also affected by its surrounding interaction nodes, so the interactive confidence measure ofηican be described as follow:
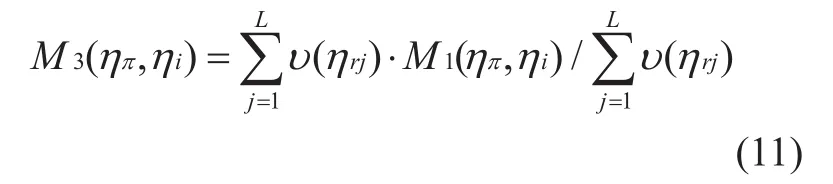
υ(αrj) is the interactive trusted factor function ofηi, and the analytic expression ofυ(αrj) is as follows:

From (12), ifηrjandηibelong to the same cluster, then the number of hops is 1, so; Otherwise,the number of hops is larger than 1, thenAt this time,υ(ηrj) is obtained by multiplying the data transmission state confidence metric of each relay node in the calculation communication path. Similar to the trust in human relations, as for direct interaction and after a number of relay interactions, the trust value is obviously different.(11)describes the influence of the communication distance and the number of relay objects on the trusted value of the node interaction,clearly reflects the effect of the distance and the number of interacting objects on the reciprocal confidence measurement ofηi.
Definition3-6,with the increasing application of Internet of Things, the attack on nodes in the perceived layer is endless, and the trusted operation of the sensing nodes is closely related to the trust of the nodes. Therefore, this paper acts the perceived nodes trusted measure as an important component of node confidence measurement, the evaluation function of the trust of nodes is described as follows:Logthe number of data transmission or interaction failures ofηiin theηπrecord,ηπenergize the nodes according to the trusted evaluation ofηi.The higher the trust ofηiis,the more trustedηiis respectively.
Definition 3-7Node activity degree is used to characterize the stability of running state of nodes in the perceived network. The more interactive objectsηihas, the more the number of successful interactions is and the more

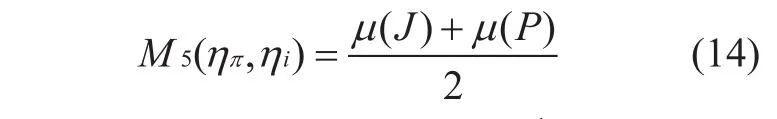
In view of the lack of global perspective of the traditional trusted measurement model, the use of simple mean method and direct value method can determine the trusted measured value, which could lead to a comprehensive consideration of various factors on the effect of the value of the trusted measurement. The trusted measurement value does not smoothly display the change in the confidence metric.
In order to more accurately reflect the change of the trustworthy measure of the node and to smooth the influence of each factor on the confidence measure of the node, this paper introduces the information entropy to smooth the measure of different dimensions, and the confidence level of the node is more realistic.
Definition 3-8According to Din the definition 3-3 - Definition 3-7, the information entropy calculation process for theidimension ofηiis described as follows:
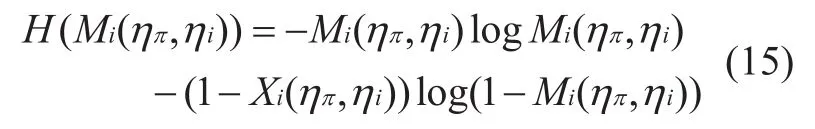
Definition 3-9Given differentMi(ηπ,ηi),Assumingβiis the confidence distinction ofthen the calculation ofαican be described as follows:

Given a differentiated degree of confidence,a different metric dimension weight can be obtained:

In equation (16),Mis the number of stages of rating given in definition 3-1. According to the formula above, obviously: 0≤β≤1iandat the same time, the weight ofcan be obtained according to the equation (16) and the equation (17). If the value ofinformation entropy is less thanρ, it will determine thatβiis 0. And the according to the equation (17), its classification weight is 0. This can effectively reduce the risk of perceived networks and improve the perceived network operation of its trust.So, the overall trustworthy measure of the node can be calculated according to Denition 3-1-Denition 3-9:

3.6 The feedback control of sensing nodes
According to (18), whenηπcalculates the dynamic confidence measure ofηiwhich namedperforms feedback control onηiaccording to different value ofTM(ηπ,ηi,t) forηito ensure that the operation of the cluster with the core ofηπis trusted
The measurement model of this paper is a step-by-step process. After the initial state measurement, the trusted measurement process of the sensor nodes is taken into account in the different clusters. The trusted measure of the cluster head node is completed by the data aggregation node, and its processing method is similar to that of the ordinary node receiving the measure of the cluster head node. In the previous section, the dynamic measure of a node is a trusted measure of the value at any time, and since any node is trusted, it is necessary to judge it with its historical confidence measure. So, we can give the calculation of the trusted value of the node within a period of time
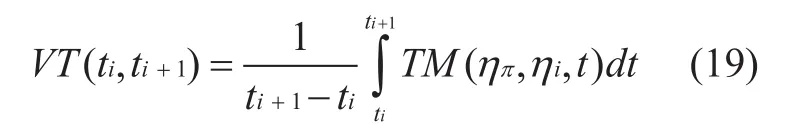
According to the formula (3-20), we can give the denition of a trusted node:
Definition 3-10For any sensing node, if the node is calculatedfrom a trusted value withintime period,meetsthis the trusted threshold specied by the sensing network, then the node is trusted.
Whether the node is trusted is determined by its superior node, if a trusted value calculated by a node in time [ti,ti+1] is lower than the trusted thresholdxed by the sensing network,the parent node further examines its trusted value at [ti-1,ti]. If the value ofVT(ti-1,ti)is not trusted as well, it will then reject the node. If the value ofVT(ti-1,ti) is trusted, the parent node further examines its trusted value at [ti+1,ti+2], thereby determining whether or not to exclude the node from the perceived network.
IV. DESCRIPTION OF THE SIGNATURE PROCESS
In order to describe the specific process of signature, therst step is to give the format of the remote attestation vector of node. Remote attestation vectors include trustworthiness,timestamps, node computing environments,and other attributes, which can be formally described asnode’s trusted measure,Tris the time window when proong,NEis the node computing environment, andARis the node’s other related attributes. Figure 3 describes the signature vector format:
4.1 Prerequisites
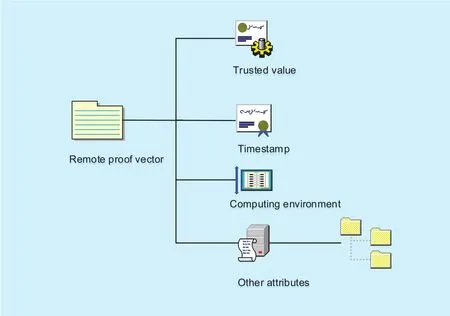
Fig. 3. Remote attestation vector format diagram.
GroupG1 and groupG2 is a multiplicative cyclic group of two ordersn=pq, p and q are large generous, and the generator of the groupG1 isg. The mappingset, which is the bilinear mappings of groupsG1 toG2 that satisfies both of the following properties:
(1) Computable bilinear: there is a computable mappingsalso a cyclic group of order) that all exists
(2) Non-degenerative: the generating elementgon the groupis the unit of the groupG1.
Define 4-2 Subgroup Decision Hypothesis
If the subgroup decision problem cannot be solved within the probability polynomial time,then the problem is a subgroup decision problem on the groupG.
Define 4-3 l-HSDH assumptions
If there is no probability polynomial algorithm within timetto deal with the probleml-HSDHwith the least probabilityt, then the assumption (l,ε,t)-HSDHbased on the groupGpset up.
4.2 Signature process
1. Key generation phase
Select a multiplication cycle groupG1 of multiplication cyclen=pq(p,qis a large prime. The generator isgandf() is defined as a mapping function of groupandis the combined order of the bilinear mapping. Assumes thatGpis the subgroup ofG1, which has the generator isg1 and the order isq. The superior node (the node for the group administrator) that needs to do the external proof selectand calculateI=e(g,g)x,J=gy.The group administrator selectsγ,δaccording to the attribute of its own node, and calculates the time windowaccording to the current timeti.The subordinate node of the group administrator calculates the trustworthinessvalue of the nodeαi.Select the trusted nodeα1,α2 ,.....,αmas a group signature member,calculateand then calculateω1,ω2,.......,ωm∈Gwhereωi=f(IDi) andIDiis the identity ofαi.The group public key isand the group administrator’s private key isAfter the group administrator selectsαid∈RZnfor their each group members and calculatesskid= (gx/(y+αid),gαid,γαid)∈G13, the next stage is to calculate the trusted valueof each nodeαi. If the result is untrusted, then it needs to calculateand the group administrator will put the group members ofinto the untrusted listUIL.
2. Signing Process
Given a timestampTr, the signed message isNEandARwith the string concatenation symbol isand calculateThen selectcalculatethen calculateandThe final output of the signature is
(2) This step is query whether the untrusted queryUILexiststhat makes the formhold. If the form holds, then that node is regarded as not trusted. Otherwise the node is viewed as trusted.
3. Signature Verification
(1) When the remote questioner re-and then verifies whetherandholds. If not, signature refused could be executed, otherwise it cannot transfer to step 2.
(2) This step is to query whether or notis present in the query untrusted listcan hold. If the form holds, then node is not regarded as trusted. Otherwise the node is view as trusted.
4.3 Program security analysis
Theorem 4-1the program in this section satisfies the correctness of the signature.
Proof: For any group members, the legitimate signature has the ability to verify:

Theorem 4-2For attackerAwith any probability polynomial computing power, the real computing environment and the simulated computing environment are indistinguishable for the attackerAat a given timet'. Assuming thatAdv(A) is the probability advantage that the attacker can solve the anonymity in the real environment andAdv(A,S) is the probability advantage of the attacker that solves the anonymity in the simulation environment, andεsis the probability that the attacker resolves the subgroup judgment, then
Proof:Suppose there is an algorithm B that can simulate the interaction between the challenger and the attacker to deal with subgroup decision problems. After the algorithmit needs to judgewhich one holds. The algorithmBfirst generates a public key based on the key generation method of the signature mechanism in this section, and then sends the group public key to the attackerA. In this case, regardless ofwhich one holds, because the algorithmBknows the group administrator’s private key, so the algorithmBcan answer all queries. And whenholds, the simulation environment is the same as the real computing environment.Given a signature momentTr*, the attackerAchooses a signature message and two signature identities. The attackerAdoes not query the corresponding signature key between group of membersin thethe untrusted list, and the signatures of the members of the group. The algorithmBselectsand outputs signaturethen sendsto the attackerA. Assumptions that the attackerAcan guess the identity of the signer, then the algorithmBsends 1, otherwise the algorithmBsends 0. Suppose thatAdv(B) represents that the algorithmBis used to solve the problem of subgroup decision, then the following relationship holds:

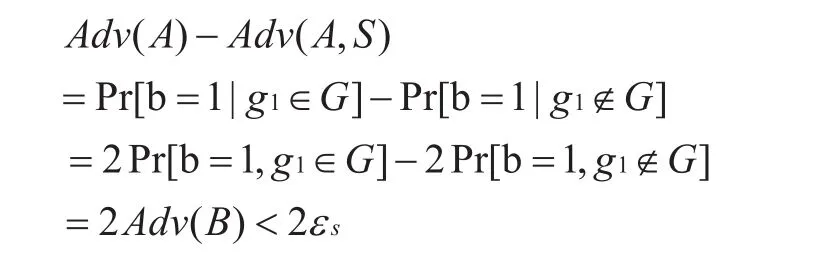
In summary, in the sub-group decision hypothesis, the actual computing environment and the hypothetical computing environment for the attacker from the probability is indivisible.
Theorem 4-3For any attacker, there exits an equationAdv(A,S)=0
Proof:Ifholds, then the attacker cannot calculate the signature key and identity of the signer according to challenge signatures. Althoughαidmay be used to answerthis means that the challenge signature and signer’s identity are statistically independent of each other.
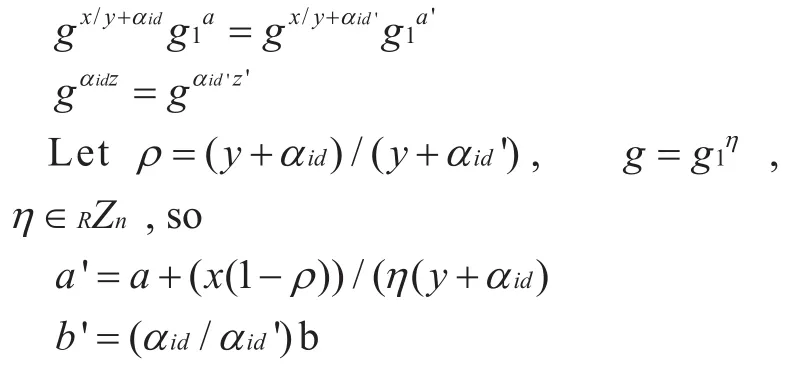
Based on the above calculation results, it is proved that the identity of the signer cannot be deduced fromc1', and for the attackerAc1 andc1' satisfy:
(1)
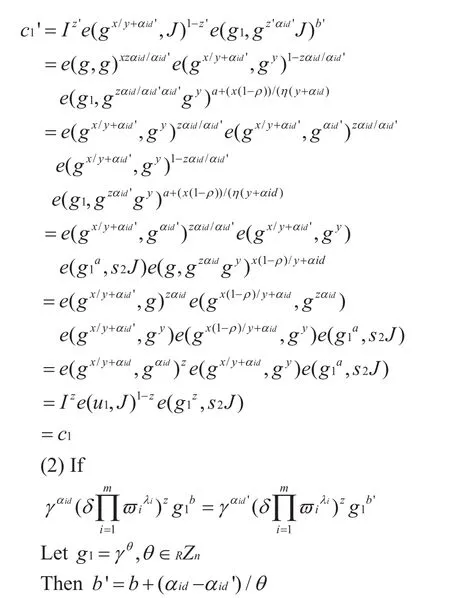
Based on the above calculation results, it is proved that the identity of the signer cannot be deduced fromc2', and for the attackerAc2 andc2' satisfy:

From the above calculation results,can be obtained. Although the simulation algorithm usingaidgenerates a challenge signature, the identity information and the private key of the signer cannot be calculated according to the challenge signature. Therefore,the probability that the attackerAcan calculate the identity of the signer in the simulation environment can be negligible. So theorem 4-7 can be obtained according to theorem 4-5 and theorem 4-6.
Theorem 4-4In a given timet, if there is no probability polynomial computing ability of the attackerAwho can deal with subgroup decision problems at least the radio ofεs,then for anyt'≈ttime , the attackerAcan solve the anonymity of the probability advantageAdv(A)< 2εs.
Thus, according to theorem 4-5 to theorem 4-7, this mechanism satisfies the anonymity of signature
Theorem 4-5The traceability theorem.If there is an attacker whose computational power is a probability polynomial, the attacker succeeds in breaking the traceability of the group signature within the given timet' at the probabilityε, then there is a timet' thatt'≈tcould hold. The probability that the attackerAcan break the double signature isε.
Proof:Because group signature can be regarded as a special case of double signature from mathematic point of view, on the basis of double signature, the non-zero interaction method is used to realize the anonymity and non-linkage of group signature. The use of unforgeable two-layer signature can achieve the characteristics of group signature tracking in this section.
If the challenger is imitated by the algorithmB, for example, the algorithmBand the attackerAinteract with each other to forge the signature, then the algorithm can do the following operation:
First, the algorithmBis used to set the system parameters of the double-layer signature, and the common parameters that generate the signature are made public. The attackerAqueries the signature private key of the group signature member from the algorithmB. The algorithmBadds the signature member to the algorithm in the process of double-layer signature. The signed private key of the group signaturecan be obtained, then transmittingto the attackerA.The attackerAqueries the algorithmBfor the untrusted flag of the signed member at the time stampTr.The algorithmBcalculatesthe attackerA.The attackerAqueries the algorithmBfor the group signature of the signature member message for message M. The algorithmBqueries the signature language of the double signature and obtainsThe algorithmBrandomly generatesand calculates the group signatureaccording to the generation algorithm of the group signature, which is obviously a useful group signature. AttackerAcan use the group public key and the list of untrusted nodes to verify whether the signature is valid.

So:

Verifyingc2*can get:

Therefore, according to above calculation process, the follows can be got.

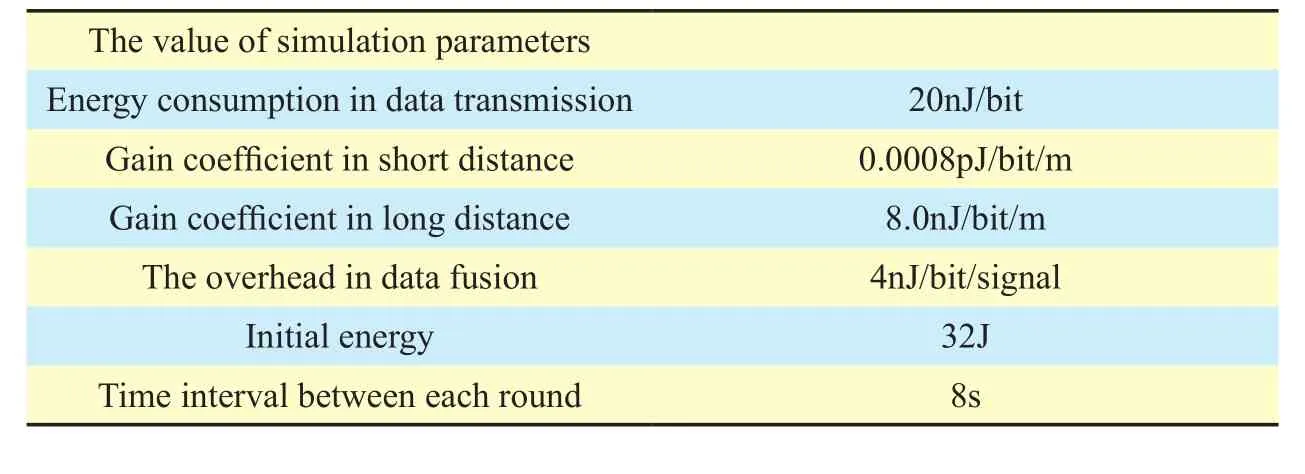
Table I. The parameters of experimental simulation.

Fig. 4. The distribution of sensing nodes.

Fig. 5. The rate of trusted data in the first malicious nodes rate is 30%.
V. EXPERIMENTAL SIMULATION AND QUALITATIVE COMPARISON
5.1 Experimental simulation
This section uses NS2 to simulate the process of the remote attestation and the attack behavior on the platform of Ubuntu. It can verify the validity of the mechanism which is proposed in this paper. In this section, the experimental range is 200m * 200m and the coordinate of the base station is (85, 84). This experiment randomly places 50 nodes in the selected range. The communication radius of cluster head nodes is 300m and the communication radius of ordinary nodes is 150m. The physical parameters of this simulation have been shown in Table 1. The distribution of nodes in sensing network is shown in Figure 4.
In the simulation of this experimental, it mainly studies two kinds of malicious nodes.The first malicious nodes will maliciously discard the data packets in the transmission and the second malicious nodes will send a large number of data packets which are erroneous,obsolete and unrelated, such as the flood attack. According to the test of nodes radio in different types, the trusted rate of data reception of this mechanism has been proposed in this experimental. In different rate of malicious nodes, the trusted value of data which is received from nodes has been shown from Figure 5 to Figure 7. In those figures, Mechanism 1 presented in literature [31] refers to the mechanism transmits data with traditional remote attestation and Mechanism 2 presented in literature [33] refers to the mechanism with traditional attestation of sensing nodes. The experimental results are as follows:
According to these figures, when the first and the second malicious nodes rate are 30%,the trusted rate of data can be guaranteed effectively with the remote attestation mechanism of nodes in this section. It is due to the trust of nodes has been confirmed before the data transmission and the trust of nodes will be confirmed again according to the time window after the data reception in the mechanism which is proposed in this section.
Although the energy consumption of the mechanism which is proposed in this section is higher than the Mechanism 1 and Mechanism 2 in Figure 8, considering the balance of safety and energy consumption, the computational complexity of the mechanism which is proposed in this section is higher than Mechanism 1 and Mechanism 2 and the energy consumption compared with the Mechanism 1 and Mechanism 2 in unit time increased less than 3%. Therefore, the mechanism which is proposed in this section will not affect the service life of sensing nodes obviously.
5.2 Qualitative comparison of trust measurement model in this paper and other models
This paper proposes a trusted measurement model for the sensing nodes in the Internet of Things. In order to realize the real-time measurement of the trust of nodes in different dimensions, this model is based on the initial state measurement of nodes, and takes the trust measurement of data transmission behaviors of nodes as the core. Also, this model combines the risk assessment with the trust calculating method in sociology. In order to realize the real-time tracking and feedback of the trusted state of nodes, the model is based on the trusted values of nodes and proposes a measurement method combining active measurement and passive measurement in different dimensions. The method determines the trusted degree of nodes which have historical trusted value from the vertical time dimension,and the misjudgment rate is low.
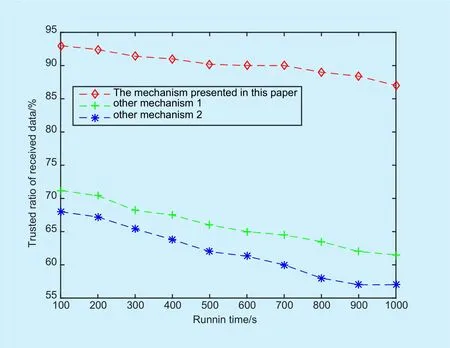
Fig. 6. The rate of trusted data in the second malicious nodes rate is 30%.
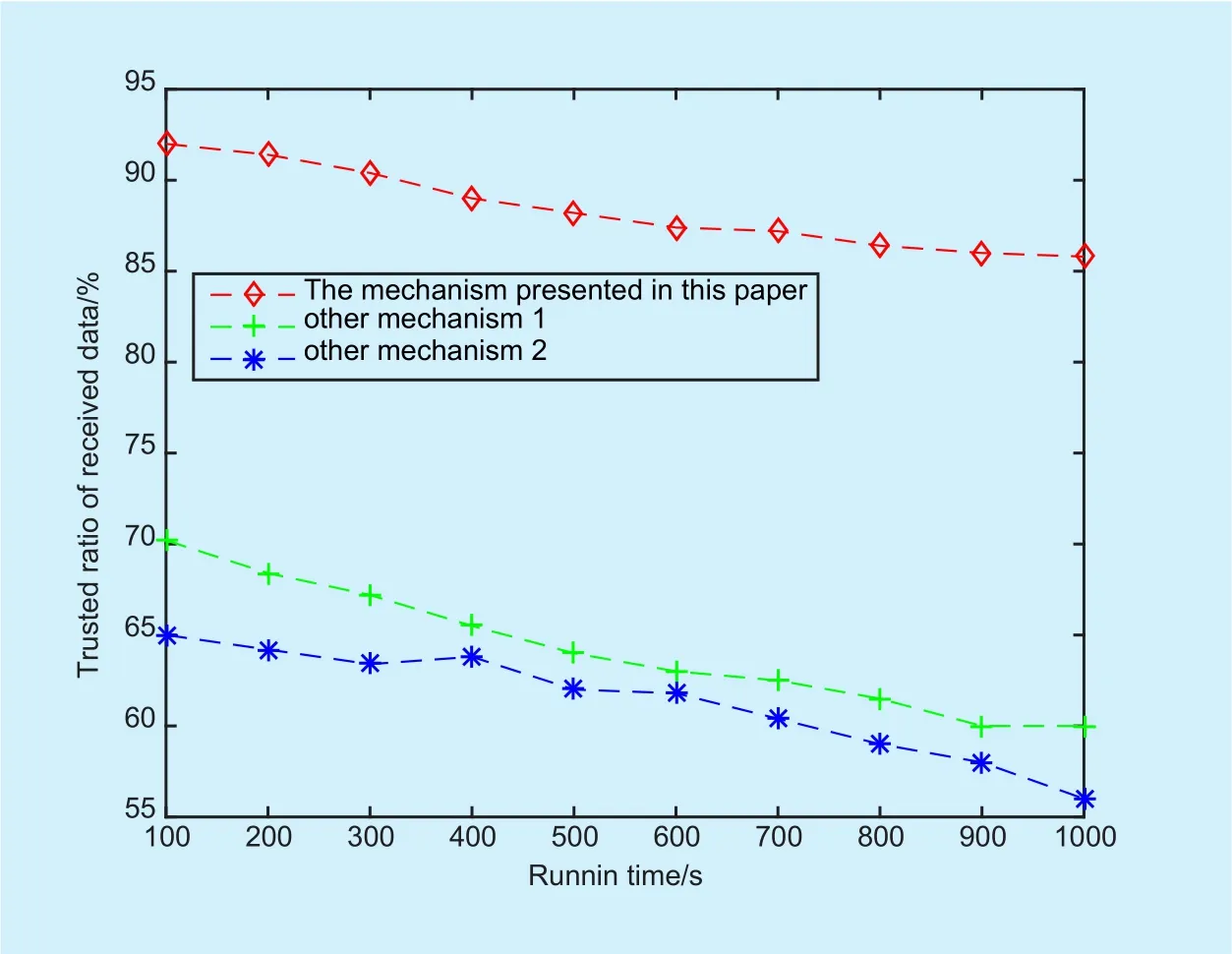
Fig. 7. The rate of trusted data in the first and the second malicious nodes mixed rate is 30%.
Table 2 qualitatively compares the measurement model of sensing nodes proposed by this paper in Internet of Things with other trusted models in Internet of Things. Although this model presented by this paper has low misjudgment rates, it has variety of obvious merits. For example, compared with other models in internet of things, this model could resist a wide range of risks, such as such as Sybil attacks, Physical capture attacks, Clone node attacks, Forged identity attacks, Route attack, Dos attacks. Besides, it has some specific characteristics of active measurement,dynamic measurement and real-time feedback.Therefore, this model enjoys enormous potential and vast development prospects, and some specific measures need to be taken to make a dramatic difference. The metric function needs to be further optimized to reduce misjudgment rates and this model applied in engineering area should also be promoted in some aspects.
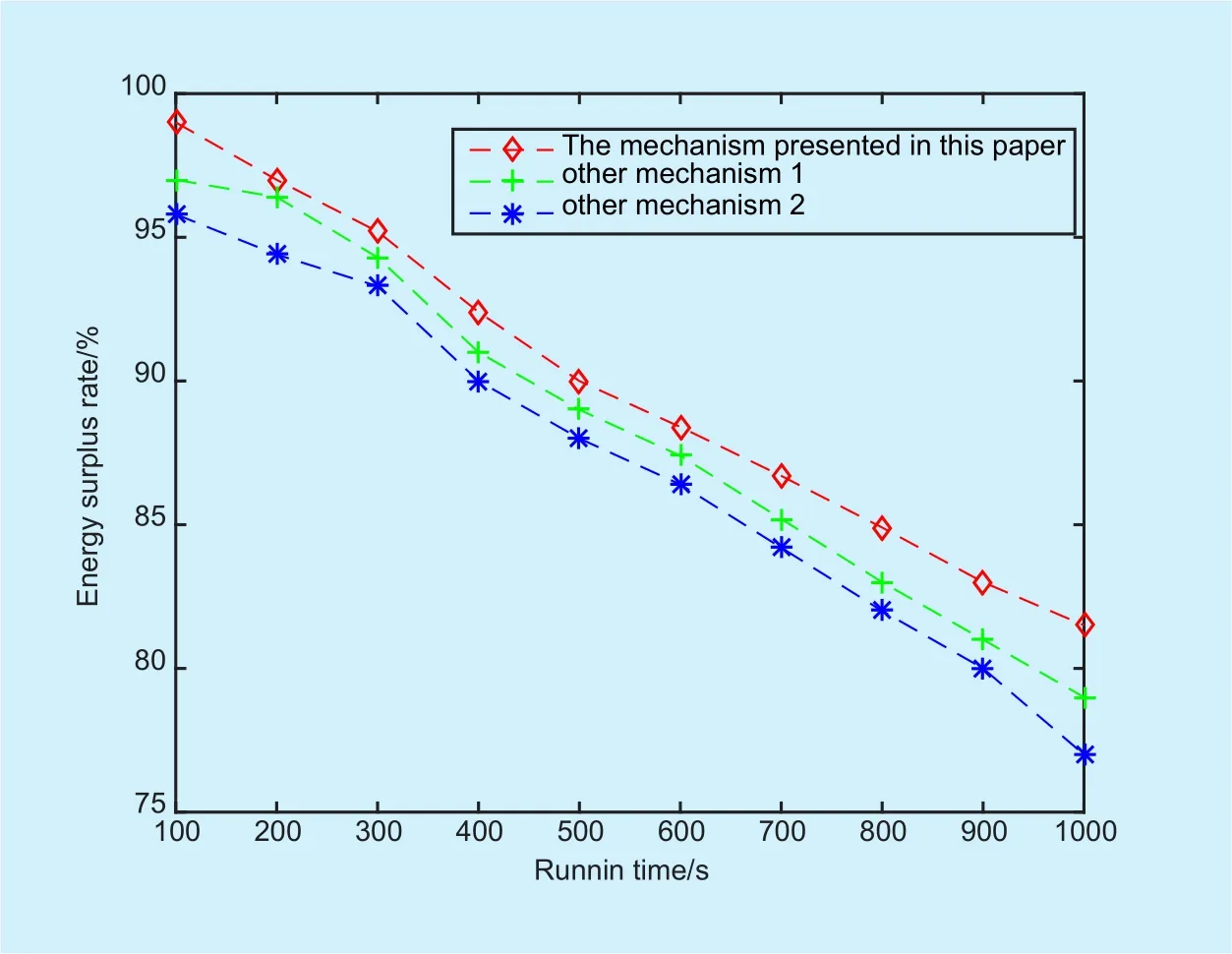
Fig. 8. The residual rate of nodes energy.
VI. CONCLUSION
According to the sensing nodes of Internet of Things need real-time trace its trusted value in some application scenes, this paper proposes a trusted attestation mechanism which is based on the dynamic measurement for sensing nodes of Internet of Things and proposes a dynamic trusted measurement model of sensing nodes that quantify the interaction between different nodes, the behavior of nodes and the state of nodes. This paper realizes the dynamic trusted measurement and feedback control of sensing nodes with the characteristic of different nodes. This paper uses many attribute computing functions, such as the direct trusted measurement function, the trusted risk assessment function, the feedback control function,the data behavior sending function and the sensing nodes activity function, to realize the dynamic trusted measurement of sensing nodes from several dimensions and show the real-time change of the trusted measurement value of sensing nodes. Through the calculation of trusted measurement value in the vertical time dimension, this paper can find the malicious nodes effectively and realize the feedback control of sensing nodes. Meanwhile, on the basis of this, the local verifier revocation group signature which is provable security realizes the trusted attestation of nodes in the standard model and this mechanism can real-time trace the trusted measurement value of nodes in data transmission. This mechanism realizes the dynamic tracing of trusted measurement value of nodes and proof the security of this mechanism in standard model. Through the simulation experimental, this mechanism can defense kinds of attacks to sensing nodes and effectively guarantee the trust of data transmission between nodes and realize the real-time tracing of sensing nodes.
This work was supported by the National Natural Science Foundation of China (The key trusted running technologies for the sensing nodes in Internet of things: 61501007,The research of the trusted and security environment for high energy physics scientific computing system: 11675199). General Project of science and technology project of Beijing Municipal Education Commission:KM201610005023, the outstanding personnel training program of Beijing municipal Party Committee Organization Department(The Research of Trusted Computing environment for Internet of things in Smart City:2014000020124G041). The key technology research and validation issue for the emergency treatment telemedicine public service platform which integrates the military and civilian and bases on the broadband wireless networks(No.2013ZX03006001-005), the issue belongs to Major national science and technology projects

Table II. Comparison of trust measurement model in this paper and other models.
[1] ROMANA R, ZHOUA J, LOPEZB J, “On the features and challenges of security & privacy in distributed Internet of Things”[J].Computer Networks, vol. 57, no. 10, 2013, pp. 2266-2279.
[2] Gongyi Wu, Ying Wu, Introduction to Internet of things Engineering[M], Machinery Industry Press, 2012.
[3] Z.H Qian, Y.J Wang, “Research on Internet of Things Technology and Application”[J],Journal of Electronics, vol. 40, no. 5, 2012, pp. 1023-1029.
[4] Chun-Wei Tsai, Chin-Feng Lai, Athanasios V.Vasilakos, “Future Internet of Things: open issues and challenges”[J],Wireless Networks, vol.20, no. 8, 2014, pp. 2201-2217.
[5] Dhananjay S, Gaurav T, Jara AJ, “A survey of Internet-of-things: Future vision, architecture,challenges and services”[C],In: Proc. of the 2014 IEEE World Forum on Internet of Things (WFIOT). IEEE, 2014, pp. 287-292.
[6] Perera C, Zaslavsky A, Liu CH, Compton M,Christen P, Georgakopoulos D, “Sensor search techniques for sensing as a service architecture for the Internet of things”,IEEE Sensors Journal,vol. 14, no. 2, 2014, pp. 406-420.
[7] Theodorakopoulos G, Baras J S, “On trust models and trust evaluation metrics for ad hoc networks”[J],IEEE Journal on Selected Areas in Communications, vol. 24, no. 2, 2006, pp. 318-328.
[8] Mengmeng Sun, Yuanan Liu, Kaiming Liu, “Security analysis and security mechanism research in Internet of things”[J],Confidential Science and Technology, vol. 21, no. 3, 2011, pp. 61-66.
[9] Jing Sun, Xiujuan Sun, HuiqunZhao, Ka Wang,“Research on trusted mechanism in Internet of things”[C],Proc. The 14th Chinese Fault Tolerant Computing Conference, 2011, pp. 1-10.
[10] Zhang C, Lin X, Lu R, Ho P, RAISE, “An Efficient RSU-aided MessageAuthentication Mechanism in Vehicular Communication Network”s[C],Proc.Communications Society, 2008, pp. 1451-1457.
[11] Aijaz A, Bochow B, Dotzer F, Festag A, Gerlach M, Kroh R, LeinmullerT, “Attacks on Inter Vehicle Communication Systems - an Analysis”[C],Proc.in 3rd International Workshop on Intelligent Transportation, 2006, pp. 2-16.
[12] Guette G, Ducourthial B, “On the Sybil attack detection in VANET”[C],Proc. 2007 IEEE Internatonal Conference on Mobile Adhoc and Sensor Systems IEEE, 2007, pp. 1-6.
[13] Gerlach M, Trust for vehicular applications,“Autonomous Decentralized Systems”[C],Proc.2007. ISADS’07. Eighth International Symposium,2007, pp. 295-304.
[14] Cencioni P and Pietro R D, VIPER, “A vehicle-to-infrastructure communication privacy enforcement protocol”[C],Proc. Mobile Adhocand Sensor Systems, 2008, pp. 1-6.
[15] Choi J Y, Jakobsson M, Wetzel S, “Balancing auditability and privacy in vehicular networks”[C],Proc. Proceedings of the 1st ACM international workshop on Quality of service & security in wireless and mobile networks - Q2SWinet’05,2005, pp. 79.
[16] C. Lesjak, D. Hein and J. Winter, “Hardware-security technologies for industrial IoT: TrustZone and security controller”,Proc. IECON 2015- 41st Annual Conference of the IEEE Industrial Electronics Society, Yokohama, 2015, pp.002589-002595.
[17] H. Dagale et al., “CyPhyS+: A Reliable and Managed Cyber-Physical System for Old-Age Home Healthcare over a 6LoWPAN Using Wearable Motes”,Proc. 2015 IEEE International Conference on Services Computing, 2015, pp. 309-316.
[18] A. Rghioui, A. L’aarje, F. Elouaai and M. Bouhorma, “The Internet of Things for healthcare monitoring: Security review and proposed solution,”Proc. 2014 Third IEEE International Colloquium in Information Science and Technology (CIST),2014, pp. 384-389.
[19] M. Sarvabhatla, M. Giri and C. S. Vorugunti,“Cryptanalysis of “a biometric-based user authentication mechanism for heterogeneous wireless sensor networks”,Proc. 2014 Seventh International Conference on ContemporaryComputing (IC3), 2014, pp. 312-317.
[20] K. Ntalianis and N. Tsapatsoulis, “Remote Authentication via Biometrics: A Robust Video-Object Steganographic Mechanism Over Wireless Networks, ”Proc. in IEEE Transactions on Emerging Topics in Computing, 2016, pp. 156-174.
[21] Y. Ren and A. Bonkerche. “Performance analysis of trust-based node evaluation mechanisms in wireless and mobile ad hoc networks”.In Proc,of the 2009 IEEE International Conference on Communications (ICC 2009), 2009, pp. 535-5539.
[22] S.B Cai, Q.L Han, Z.G Gao, D.S Yang, J. Zhao.“Research on Cloud Trust Model for Malicious Node Detection in Wireless Sensor NetWork”,Journal of Electronics, vol. 40, no. 11, 2012, pp.2232-2238.
[23] S. Ganeriwal, L. K. Balzano and M. B. Srivastava,“Reputation-based framework for high integrity sensor networks”,Proc. ACM Transactions on Sensor Networks (TOSN), 2016 , pp. 15-19.
[24] C. Kamhoua, N. Pissinou and K. Maldd, “Game theoretic modeling and evolution of trust in autonomous multi-hop networks: Application to network security and privacy”.In Proc. of the 2011 IEEE International Conference on Communications (ICC 2011), 2011, pp. 1-6.
[25] Trusted Computing Group [EB/OL]. https://www.trustedcoinputinggroup.org. Nov, 2011.
[26] Haldar, V., D. Chandra and M. Franz, “Semantic Remote Attestation – Virtual Machine Directed Approach to Trusted Computing”, in: Proceedings of the 3rd VirtualMachine Research and Technology Symposium, San Jose, 2004, pp. 6-7.
[27] Sadeghi, A.-R. and C.StUble, “Property-based attestation for computing platforms:caring about properties, not mechanisms in:C.Hempelmann and V. Raskin”,Proc.Proceedings of the New Security Paradigms Workshop 2004,Nova Scotia, 2004, pp. 67-77.
[28] Liqun Chen, “A Protocol for Property Based Attestation”,Proc. STC, 06, Alexandria, Virginia,2006, pp. 7-16.
[29] Seshadri A, Luk M, Perrig A, L van Doom, P.Khosla, “Externally Verifiable Code Execution”[J].Communications of the ACM, vol. 49, no. 9,2006, pp. 45-49.
[30] Poritz J, Schunter M, Van Herreweghen E etc. Property attestation scalable and privacy-friendly security assessment of peer computers [R]. New York: IBM, 2004.
[31] TAN Liang CHEN Ju. “Remote Attestation Project of the Running Environment of the Trusted Terminal” [J].Journal of Software, vol. 25, no. 6,2014, pp. 1273-1290.
[32] Korthaus R, Sadeghi A R, Stüble C etc. “A practical property-based bootstrap architecture”[C].Proc. ACM. In Proceedings of the 2009 ACM workshop on Scalable trusted computing, 2009,pp. 29-38.
[33] P. Gasti, J. Šeděnka, Q. Yang, G. Zhou and K. S.Balagani, “Secure, Fast, and Energy-Efficient Outsourced Authentication for Smartphones, ”Proc. in IEEE Transactions on Information Forensics and Security, 2016, pp. 2556-2571.
[34] I.-R. Chen and J. Guo, “Dynamic Hierarchical Trust Management of Mobile Groups and Its Application to Misbehaving Node Detection, ”Proc. in 2014 IEEE 28th International Conference on Advanced Information Networking and Applications, 2014, pp. 49-56.
[35] D. Chen, G. Chang, D. Sun, J. Li, J. Jia, and X.Wang, “TRM-IoT: A trust management model based on fuzzy reputation for internet of things,”Comput. Sci. Inf. Syst., vol. 8, no. 4, 2011, pp.1207-1228.
[36] A. F. Skarmeta, J. L. Hernandez-Ramos, and M. V.Moreno, “A decentralized approach for security and privacy challenges in the Internet of Things,”Proc. in 2014 IEEE World Forum on Internet of Things, 2014, pp. 67-72.
[37] G. Schryen, M. Volkamer, S. Ries, and S. M. Habib,“A Formal Approach Towards Measuring Trust in Distributed Systems, ”Proc. Acm Symposium on Applied Computing, 2011, pp. 1739-1745.
[38] M. Anuar, M. Isa, N. N. Mohamed, H. Hashim,S. Farid, S. Adnan, J. A. Manan, and R. Mahmod,“A Lightweight and Secure TFTP Protocol for Smart Environment, ”Proc. IEEE Symposium on Computer Applications & Industrial Electronics,2012, pp. 302–306.
[39] A. Mana, H. Koshutanski, and E. J. Perez, “A trust negotiation based security framework for service provisioning in load-balancing clusters, ”Comput. Secur., vol. 1, no. Elsevier, 2011, pp. 4–25.
[40] W. U. Qiu-xin, “Secure solution of trusted Internet of things base on TCM, ”J. China Univ., vol.20, no. 12, 2013, pp. 47–53.
[41] X. Xu, N. Bessis, and J. Cao, “An Autonomic Agent Trust Model for IoT systems, ”Procedia Computer Science,vol. 21, no.11, 2013, pp. 107–113
[42] Y. Ben, A. Olivereau, D. Zeghlache, and M. Laurent, “Trust management system design for the Internet of Things: A contextaware and multiservice approach, ”Comput. Secur., vol. 39, no.11, 2013, pp. 351–365.
- China Communications的其它文章
- CYBERSPACE SECURITY: FOR A BETTER LIFE AND WORK
- A Cloud-Assisted Malware Detection and Suppression Framework for Wireless Multimedia System in IoT Based on Dynamic Differential Game
- An Integration Testing Framework and Evaluation Metric for Vulnerability Mining Methods
- Powermitter: Data Exfiltration from Air-Gapped Computer through Switching Power Supply
- CAPT: Context-Aware Provenance Tracing for Attack Investigation
- Decentralized Attribute-Based Encryption and Data Sharing Scheme in Cloud Storage

