Decentralized Attribute-Based Encryption and Data Sharing Scheme in Cloud Storage
Xiehua Li*, Yanlong Wang, Ming Xu, Yaping Cui
College of Computer Science and Electronic Engineering, Hunan University, Hunan 410082, China
I. INTRODUCTION
In this paper, we consider data sharing scenarios in which otherwise distrusted authorities collaborate on specific projects. Such scenarios can arise as competitors work on a joint project, e.g., automotive safety equipment jointly developed by car manufacturers. In many cases, the data being shared is developed not only by the authorities, but can originate from a third party. In our example, some data may originate from a government agency that maintains sensitive data about failures and crashes. These types of scenarios are increasingly common, and require the ability to provide secure data access with fine-grained control. It is possible to provision such access using a trusted third party (TTP), such as a Certificate Authority that generates secret keys for specific data; however, TTP-based solutions are particularly problematic in multi-authority scenarios since they require distrusted principals to trust a single party.
We introduce a system for data sharing between users of distrusted authorities, without resorting to TTPs. Beyond authorities and the data owner, includes users who may not belong to any authority but need access to the data, and an distrusted third-party storage provider that hosts the data to be shared. Importantly, it does not require authorities to agree on a global identity for users: they may provide access attributes to users independently;the cryptographic mechanisms allow attributes from different authorities to combine to enable access to encrypted data and prevent collusion between authorities and users.
In this paper, we propose a novel scheme which provides fine-grained data sharing and access control among different authorities and revocation mechanism. Our scheme is based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption) that is an attribute-based fine-grained access control and encryption method for secret data sharing. We extend the original CP-ABE into a multi-authority scenario and maintain its security and efficiency properties. The main contributions of this paper are as follows:
1) We propose a scheme which can achieve secure data sharing between authorities without revealing user’s information and is tolerant to authorities and users collusion attack.
2) We propose a revocation method which loads most of the heavy computation to the cloud without leaking either the secret information or the data attributes to any distrusted third party.
3) We firstly implement this on mobile phone and measure its efficiency.
The remaining of this paper is organized as follows: We introduces a discussion of related work in Section II. Then, we propose DMA scheme and security model in Section III. Next, we provide an efficient revocation scheme in Section IV. In Section V, we analyze the performance of our scheme. We finally conclude this paper in SectionⅥ.
II. RELATED WORK
ABE is a promising technique that enables fine-grained access control to encrypted data[2-6][10][12-13]. In various ABE-based schemes, a trusted central authority (CA) is used to manage all the attributes and distribute keys. Once the CA gets compromised, there would be no privacy of the stored data. In addition, these schemes have not put much thought on user revocation and key update,which makes them less attractive for real applications. Moreover, these schemes cannot be directly applied to data access control for multi-authority based cloud storage and data sharing system.
There are many access control schemes has been proposed for the multi-authority ABE scenarios[32, 33]. Most of these schemes use CA as the TTP to generate public key and user secret keys. Chase firstly proposed a multi-authority ABE method[11] that introduced a global identifier (GID) for user secret key generation. Lewko and Waterset al. propose a new scheme based on multi- authority CPABE [15], this scheme uses CA only in the initialization phase. CA distributes the public parameters and verifies AAs according to the user’s request. Yanget alpropose a DACMACS algorithm [16], CA is responsible for the generation of the global public key and private key and distribute a unique identity for the user and all the AAs. AAs issue attributes and generate attribute keys for each user.Yang Kanet al.proposed multi-authority ABE access control scheme [17, 18], CA is responsible for authenticating all the AAs and users.In addition, CA also assigns GID for users and AID to each AA. When an attribute revocation occurs, the corresponding authority only need to change its version key and generate an update key. The server re-encrypt the ciphertext using proxy encryption method. In order to solve the problem of user’s identity protection, Taeho Jet al.proposed an anonymous privilege control scheme [19]. It can address not only the data privacy problem in cloud storage, but also the user identity privacy. This scheme generalizes an access tree to a privilege tree. Several trees are required in every encrypted file to verify user’s identity and to grant him a privilege accordingly. Hierarchy attribute-based encryption is an extension of original ABE system. Gentry and Silverberg first proposed the notion of hierarchical encryption scheme[31]. Few researches have been done on this area.
There has been some prior researches into dealing with user revocation in ABE systems[20][21]. However, although these schemes support user revocation, servers will incur heavy communication cost for ciphertext re-encryption and key updates. In addition,scheme[21] can only revoke up to a predefined number of users. Ostrovskyet al.[22] realized the immediate user revocation by using ABE that supports negative clauses. But it extends the length of the ciphertext and users’ keys. Xu and Martin [23]propose a model for dynamic user revocation and key refreshing. It uses proxy re-encryption and introduces a delegation attribute. The AA generates a delegation key share for the delegation attribute, which is used by the cloud storage for ciphertext re-encryption. However, the model was only applied to BSW’s scheme [3], it cannot be directly applied to any CP-ABE scheme without modification. J.Hur and D.K.Noh[24] solve key-escrow by using the key issuing protocol.They use 2PC protocol to prevent the key authorities from obtaining any master secret information of each other which can prevent the other to generate the whole set of user keys alone. Moreover, these revocation schemes are only appropriate for single authority. Rujet al[25]construct a DACC scheme and propose an user revocation method for scheme[14].But their revocation method incurs a heavy communication cost since DO re-encrypts and distributes new ciphertext component for each non-revoked user. Liet al.[26]proposed an attribute revocation method for multi-authority ABE, the method is only appropriate for KPABE systems, which may lack efficiency of access control in cloud storage systems. In order to achieve multi-authority ABE with efficient revocation, J.Hur and D.K.Noh[27]propose a multi-authority ABE scheme for decentralized disruption-tolerant military network (DTN). They use the method in[24].However, in the phase of key update, the data service manager will perform heavy computation at every time of key update for non-revoked users. There are also other applications using CP-ABE for securing data exchange [7].
III. PRELIMINARIES AND DEFINITIONS
We will first give the cryptographic background information of bilinear map in [3] and security model. Then, we will describe the access structure of our DMA scheme and give the security model.
3.1 Preliminaries
Let G0and G1be two multiplicative cyclic groups for prime orderpandgbe a generator of G0. The bilinear mapeis defined as,e: G0×G0→ G1. The bilinear mapehas the following properties: 1)bilinearity: ∀u,v∈ G0, anda,b∈ ZP, thene(ua,vb) =e(u,v)ab. 2) Non-degeneracy:e(g,g) ≠1. 3) Symmetry:e(ga,gb) =e(g,g)ab=e(gb,ga).
Definition: The Decisional Bilinear Diffie-Hellman(DBDH) assumption in a multiplicative cyclic group G0of prime orderpwith generatorgis stated as: givenga,gbandgcfor uniformly and independently chosena,b, c∈ZP, the following two distributions are computationally indistinguishable:
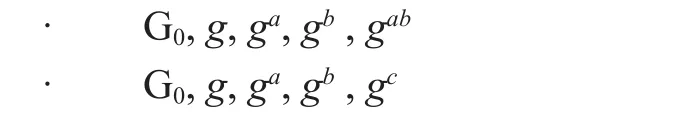
The security of our scheme is based on the DBDH assumption which is widely used in security proof of various ABE schemes. The assumption is reasonable because discrete logarithm problems in large number field are widely considered to be intractable.
3.2 Threats model
We assume that the data owners (DOs) are honest and have no interest in collusion attack with other service providers or authorities.This assumption is reasonable because DOs have the original plaintext information. There is no need for them to collude with anyone else to get the original plaintext.
Cloud Storage Providers (CSPs) are the storage media and semi-honest, which means they can implement the program properly but are willing to get illegal profits if given the opportunity. The Attributes Authorities (AAs)are assumed to be distrusted. In our scheme,the AAs calculate and distribute attributes and partial secret keys to users. In general, AAs will follow the protocol, but they will try to collect all the secret key components andnd more useful information to decrypt any ciphertext. They have the intention to collude with other entities like user, CSP, or other AAs to gain the information they want. Our assumption is based on the real application in cloud storage, and is weaker than previous researches on security issue (see [9], [29]).
Data users are distrusted entities. They are willing to collude with any entities in this system to collect useful information that they have no rights to access to.
3.3 Access tree denition in DMA
Let Γ be a tree representing an access structure. Every non-leaf node of the tree represents a threshold gate that is described by its children and a threshold value. Ifnumxis the number of children of a nodexandkxis its threshold value, thenkx=1, the threshold gate is an ‘OR’ gate. Ifit is an ‘AND’ gate. Every leaf nodexof the tree is described by an attribute and a threshold valuekx=1. An example of access tree policy is shown in Figure 1.
The access tree in our scheme is dened as follows:
2) Each leaf node of the access tree is described as an attribute which is issued by its authority.
3) If a user’s attribute setSsatises the access tree Γ, he/she can decrypt the data that are encrypted with Γ.
3.4 Security model
Our DMA scheme consists of 4 fundamental algorithms which are formally dened as follows:
A)Setup(PK, MK): this algorithm takes nothing but implicit security parameters as input.PKis computed by the data owner and then sent to all the AAs. AAs take thePKas input and calculate their own keys individually. In addition, the data owner calculates theMKand keeps it for future use.
B)KeyGen I(MK):KeyGen Iis the algorithm that will be run by the DO. It takes the MK and a random number as input and calculates the part of the secret key componentSKufor each registered user individually.
KeyGen II(PK,attr(i)i∈{1...n}): this algorithm is run by multiple AAs for secret key components calculation. Each AA runs this algorithm to calculate the set of secret keys{SK1....SKi} for each registered user based on their attributes.
C)Encryption(PK, M,Γ): this algorithm takes as input thePK, a messageM, and an access tree Γ over the universe of attributes,where the access tree is dened by the DO. By running this algorithm, DO encrypts the messageM, sends the setCTof ciphertext and the verication parameters to the CSP.
D)Decryption(PK, CT, SK): The decryption algorithm takes as input the public parametersPK, a ciphertext setCT, and the private key setfor a set of attributes, whereSKuis calculated by DO,{SKi}iϵ{1...n}are calculated by the AAs respectively, “||” is the concatenation of secret key components. If the set of attributes satises the access treeATthen the algorithm can decrypt the ciphertext and return a messageM.
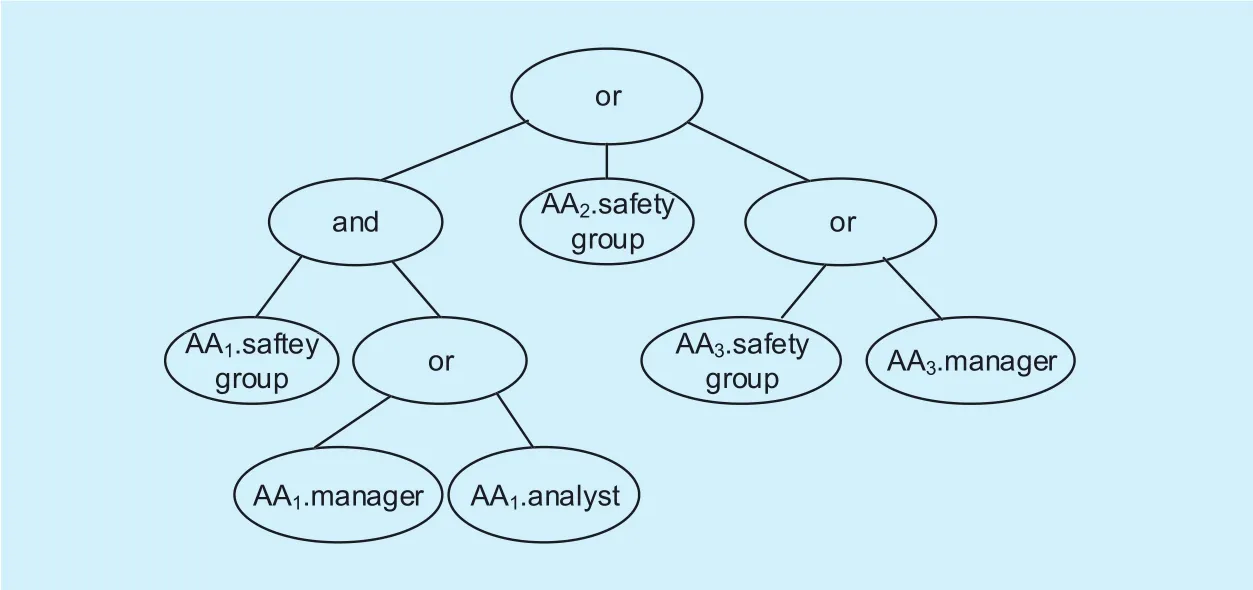
Fig. 1. Example of access tree policy in DMA.
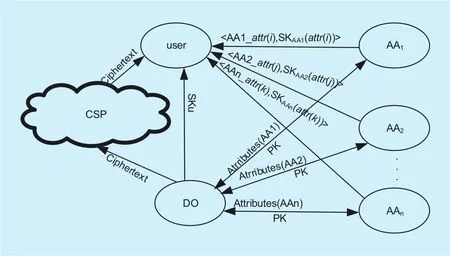
Fig. 2. DMA access control system architecture.
Init:The adversary controls a set of compromised attributes authorities {AAk} ⊂A, but DO is not under the adversary’s control. The challenge access structure Γ is chosen and given to the challenger.
Setup:The challenger runs the Setup algorithm and gives the adversaryPK.
Phase 1:The adversary submits a set of attributesSfor secret key query. ProvidedS|≠Γ, the challenger answers with a secret keySKforS. This can be repeated adaptively.
Challenge: The adversary submits two equal length messageM0andM1.The challenger choosesb∈{0,1} at random and encryptMbto Γ. The ciphertext is given to the adversary.
Phase 2: Same as Phase 1.
Guess: The adversary outputs a guessb’ofb. Ifb’=b, the adversary wins the above game. The advantage of adversary in the above game is dened as
Definition: Our scheme is secure against chosen plaintext attack if all the adversaries have at most negligible advantage in above security game.
IV. SYSTEM ARCHITECTURE AND KEY DISTRIBUTION
4.1 System architecture
There are 4 entities involved in the DMA system: DO (Data Owner), AA (Attributes Authority), Cloud storage provider (CSP),and user. The system architecture of DMA is shown in Figure 2. The entities are described as follows:
1. DO (Data Owner). Data owner is responsible for calculating public key, dening access policy and encrypting data under the access policy. Furthermore, the data owner needs to upload the encrypted data to the remote cloud storage server. DO keeps the attribute update list (AUL) and user list (UL) to identify the authorized user. Once revocation occurs, DO will update the two lists on both DO and CSP sides. For security purpose, DO computes part of users’ private keys called user specic keySKuand sends it directly to the particular users via secure channels. The reason why DO generates and distributesSKuis for preventing authorities collusion attack.
2. AA (Attribute Authority). AA plays the role of attributes distribution and user authorization. It computes users’ attributes based on the public parameters and distributes them to DO and users for access policy definition.Every AA can manage multiple attributes and has full control over those attributes. Moreover, AA computes attribute secret keysSKAA-i(attr(i)) and issues them to users via secure channel. AAidenotes theithAA in our scheme,attr(i) denotes an attribute issued by a an AA.
3. Cloud Server Provider (CSP). CSP is considered as a semi-trusted storage media that stores data. It is also responsible for updating the ciphertext when attribute revocation occurs. The CSP does not have the secret keys,so it can’t decrypt the ciphertext. Based on the semi-trusted assumption, CSP can implement the algorithm honestly, but it will decrypt the ciphertext once it gets the key.
4. User. Ciphertext on the cloud server can be accessed freely by users. But only when the user’s attributes satisfy the access policy that defined in the ciphertext, can he/she decrypt the ciphertext. User’s attributes are distributed by a number of authorities according to the user privileges so that it can achieve cross-domain access control. In addition, DO prevents the collusion attacks between users by embedding a random number in the private property.
4.2 Key distribution protocol
In our scheme, we refactor the original CPABE and extend the key generation algorithm to a multiple authority scenario. In this system,user needs torst register in a set of AAs and get his secret key components from these AAs and DO. The registration and key distribution procedure is shown in Figure 3. There are few steps for key distribution, the more detailed key generation will be presented in section V.
1. Users first register in an AA, and get a message with freshly generated nonceNiand AA’s signature overNi. [sigAAi;m] denotes the signature of AAiover messagem. This message is used for verification and preventing replay attack.
2. User forwards this message to DO. After verifying the user and AA, DO will generate user’s specic keySKuand send it to the user.Along withSKuDO generates another parameterPufor AA to calculate attribute secret key.Puis a blinded partial attribute key.

WhereAis the blinder, such asgx,x,r∈Zpare random numbers chosen by DO when generating user specific secret key. Here we can see that each user has a set of attribute keys that are in accordance with his/her user specic secret key. The reason to blind the partial attribute keygris because whoever getsgrcan generates whatever attribute keys he/she wants. We will describe this in details in the next section.Puis encrypted with AA’s public key, [encK_AAi; m] denotes encryption of messagemover AAi’s public key K_AAi.
3. User keeps his user specific secret key and forwards the encryptedPuto AA. AA decryptsPu. According to user’s attributesattr(i), AA calculates blinded attribute keysBSKiand sends them along with user’s attributesattr(i) and AA’s signature back to the user.
4. User forwards this message to DO. DO verifies AA, user’s attributes and give back unblinded attribute keys back to the user.
V. DMA ACCESS CONTROL SCHEME CONSTRUCTION
A. Setup(PK, MK).Letgbe the generator of a bilinear group ofG, and the prime order ofGas the bilinear map.. Letbe the hash function which maps attributes toG. DO selects two random exponentsα,η∈Zp, and computes public key and master key as follows :
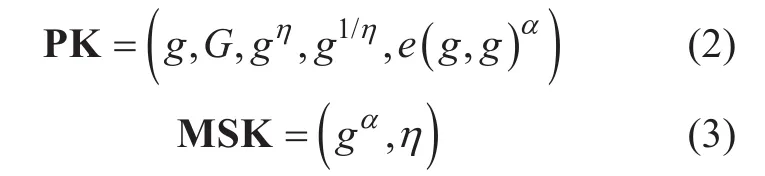
PKwill be published to all AAs.
B.KeyGen I.In the DMA scheme, the KeyGen is divided into two phrases, KeyGen I and KeyGen II.
KeyGen I(MK) is run by DO for generating user specic secret keySKu.

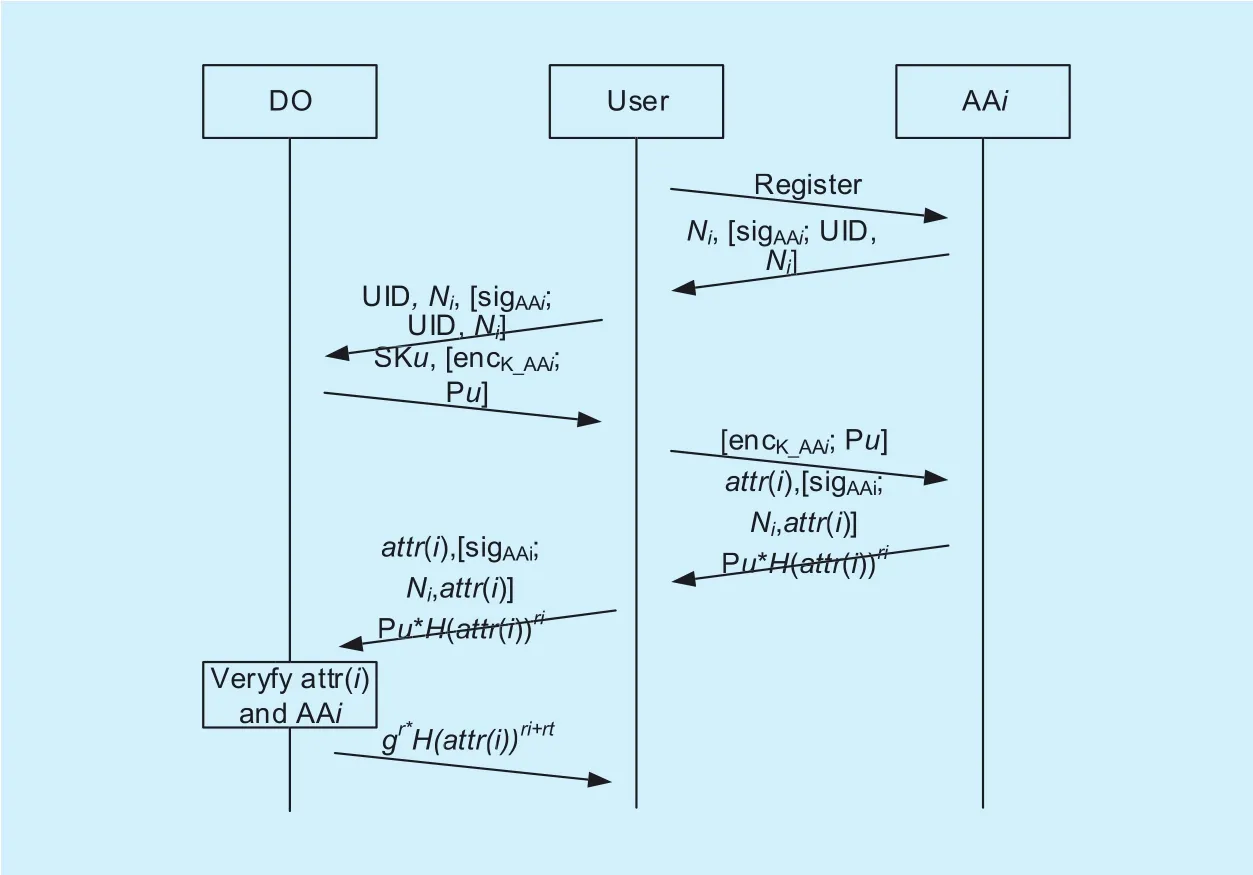
Fig. 3. Registration and key distribution protocol.
Wherer∈Zpis a random number chosen by DO,ris unique for every user to prevent user collusion attack.
KeyGen II ((PK, attr(i)i∈{1...n})) is run by multiple AAs to calculate attribute keys for users. AAs use the blinded parameter to calculate blinded attribute keys for user.
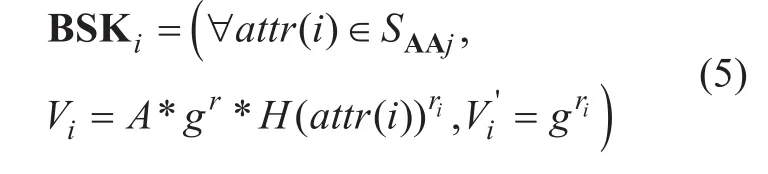
WhereSAAjdenotes the set of attributes that AAjholds.ri∈Zpis a random number for eachattr(i)∈SAAjchosen by AAj. From equation (5) we can see that ifgris given to AA or user directly, any AA or user can forge arbitrary attribute keys sinceattr(i) is a binary string andriis a random number. As shown in Figure 3, for preventing user from gettinggr, DO will send user the final attribute keys by unblinding BSKiand raisingH(attr(i))riis a random number selected by DO. Sinceriis a random number, this operation will not affect the decryption result.
The final attribute keys is described as follows.
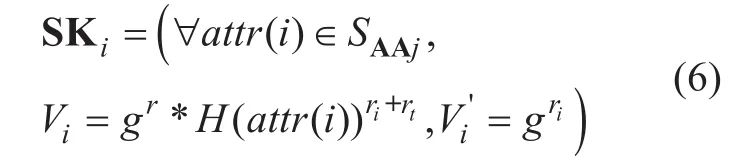
C.Encryption(PK, M, Γ). DO encrypts the messageMunder public key and the access policy Γ. The encryption algorithm chooses a polynomialqxfor each nodexin the access tree. For each nodexin the tree, set the degreedxof the polynomialqx,dx=kx-1,wherekxis the threshold value of the chosen node. The algorithm starts at the root nodeR,it chooses a random exponents∈Zpand setsThen, for any other nodex, the algorithm randomly chooses other coefficients and setqparent(x)(index(x)) such thatqx(0)=qparent(x)(index(x)), is the index of nodex’s child nodes, andparent(x) is nodex’s parent node.SupposeYis the set of leaf nodes in Γ, the ciphertext is constructed as follows:
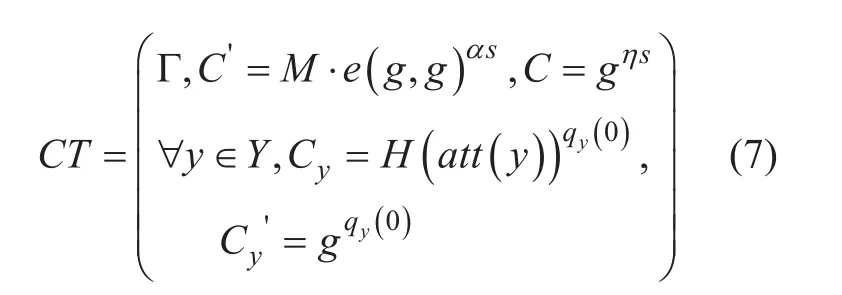
D.Decrypt (CT,SK). Only when the user’s attributes satisfy access policy defined in ciphertext, the user can decrypt the ciphertext.The decryption algorithm takes as inputs secret keys and ciphertext, whereconcatenation operation. We specify our decryption procedure as recursive algorithm. Leti=attr(y), whichattr(y) represents the value of leaf nodey, if the nodexis a leaf node andx∈S, then computes
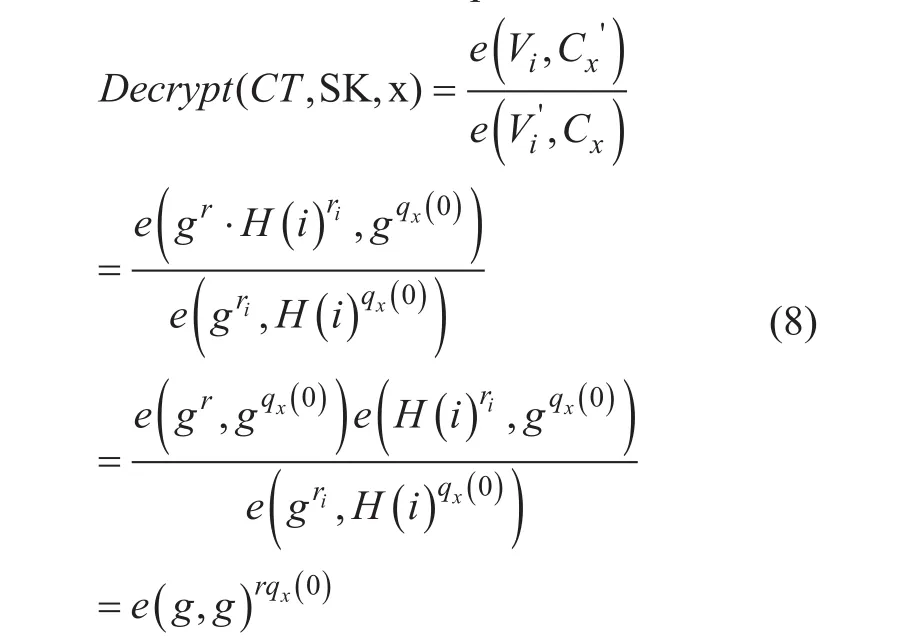
Ifi∉S, then we defineDecrypt(CT,SK,x)=⊥.
When the nodexis not a leaf node, for all the nodeszthat are the children ofx, the outputs is stored asFz. LetSxbe an arbitrarykx-sized set of child nodes. If no such set exists, the function will return ⊥. The recursive computation is shown as follows:
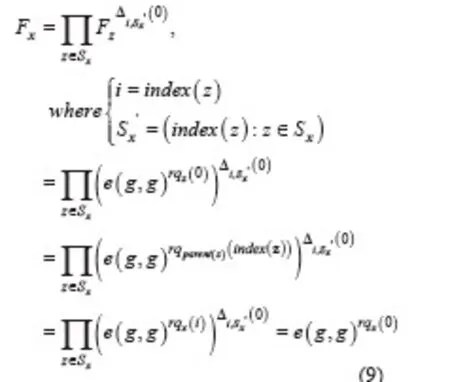
The algorithm recalls the Lagrange polynomial interpolation to decrypt the ciphertext.If the set of attributes satisfy the access tree,we defineThen computes:
VI. REVOCATION IN DMA
Revocation is an expensive computation in ABE system since revoking a specific attribute key of a user will rekey the whole set of key components. Therefore, a single attribute revocation in ABE requires all users who share the same attribute to update their secret keys even if other attributes are still valid. For example,in the joint project of car manufactures scenario, suppose there is a userUxhas attributes{AA1.safety group,AA1.analyst}, and a set of files that are encrypted under the access policy shown in Figure 1. In the ABE system, in order to revokeUxeither {AA1.safety group} or{AA1.analyst} should be revoked, which will rekey all other users who has these two attributes. Moreover, both the access policy and ciphertexts need to be updated. This seems very inefficient and may cause DO overload in terms of computation and communication costs.
In order to minimize the computation and communication costs of our system, we define two types of revocation:user revocationandattribute revocation.User revocationis implemented when DO wants to revoke specific user/users. Attribute revocation is implemented when DO or AA wants to revoke attribute.
6.1 User revocation
Based on our observation, revoking a specific user actually is revoking his privilege of decrypting ciphertexts. In our scheme ciphertextrevocation can be done by either updateαors.αis the secret parameter generated by DO,sis the root value of access policy. In our scheme we choose to updateαwhen revoking a specific user, so that the access policy is maintained when user revocation occurs. User revocation is carried out by DO directly.
When user revocation happens, DO needs to update both public parametere(g,g)αand all effected ciphertexts to provide forward security. The ciphertext update will be implemented by the CSP to reduce computation load on DO. The user revocation procedure is shown in Figure 4.
In the user revocation, DO picks a random valueα1, update the public key and master secret key and the UL. DO sendsto the CSP to update the ciphertext. Based on the security assumption, CSP will honestly calculateC', but CSP cannot get anything about the original plaintextm. User who is still legitimate in the system can contact DO to update his user specific secret key. DO will check the user list and regenerate user’s specific secret key. CSP will re-encrypt all ciphertexts to guarantee forward security.
6.2 Attribute revocation
In our scheme, the attribute revocation will revoke a set of attributes and users who possess the revoked attributes.

Fig. 4. User revocation procedure.
Attribute revocation is a challenging task in cloud storage because it requires rekeying over large number of users and updating the ciphertexts encrypted with the revoked attributes. The traditional solution usually consists of few steps: ① DO re-defines the access policy by eliminating revoked attributes; ②DO re-encrypts the affected files and uploads them to the CSP; ③DO re-generates new secrete keys for the legitimate users who possess the revoked attributes. The traditional revocation requires DO to carry out all computation and communication, which is very inefficient and makes DO the bottleneck.
In our scheme, we shift the heavy computation from DO to CSP to release DO from overwhelmed computation. Our attribute revocation scheme contains three operations:add attributes, delete attributes and attributes update.
A. Add/delete attributes. Adding or deleting attributes from access policy will cause the update of access tree and associated ciphertexts. User’s secret key will not change in the adding/deleting attribute procedure. Thus,communication is taking place only between CSP and DO. Based on the analysis in section texts based on the new access tree. The add/delete attributes procedure is shown in Figure 5. In Figure 5, Γ' is the updated access tree,Y' is the updated attribute set that includes all leaf nodes in Γ'.CT' is the re-encrypted ciphertext over Γ'.6.1, we can see that updating access tree requires changing of root values. In this case,the DO will select a random numbers'∈Zpand assigns' as the new root value to the access tree Γ. CSP will re-encrypt the cipher-B. Update attributes. Attributes update will not only cause the update of access tree and associated ciphertexts but also introduce rekeying of attribute secret keys for each affected user. For example, the attribute “AA1.safety group” in Figure 1 changes to “AA1.safety department” and the old attribute “AA1.safety group” no longer exists. This update will cause few operations: ①AA1needs to generate attribute secret key of “AA1.safety department” and distributes it to people in the safety department. Meanwhile, the old attribute and secret key of “AA1. safety group”need to be eliminated; ② DO needs to update access tree and associated ciphertexts from“AA1. safety group” to “AA1.safety department” . ③ people from the old safety group now need to get attribute secret key of “AA1.safety department” from AA1. The new attribute key generation and distribution is activated by AA1, the procedure follows the protocol shown in Figure 3 without user registration and SKu. Attribute update procedure is shown in Figure 6.
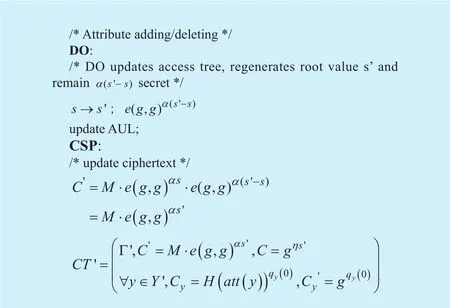
Fig. 5. Procedure of adding/deleting attributes.
In Figure 6,i′ is the updated attribute,Γ',Y',CT' have the same meaning with those described in Figure 5.
Revocation will not affect decryption process that is defined in Equation (7) to Equation(9). Our revocation scheme can achieve the fine-grained user-level and attribute-level access control such as an immediate user revocation in attribute group and immediate attribute revocation. The whole revocation is completed by DO, CSP and AA. Compared with existing schemes, DO’s computation cost is lower when revocation happens.
VII. SECURITY AND PERFORMANCE ANALYSIS
7.1 Security analysis
The Decisional Bilinear Diffie-Hellman(DBDH) problem in groupGof prime orderpwith generatorgis defined as follows:andwherez=abc,decide whetherz=abcorzis a random element.
Theorem 1:If Decisional Bilinear Diffie-Hellman assumption holds in group(G,GT), then our scheme is chosen-plaintext secure in standard model.
Proof:Suppose there exists a probabilistic polynomial time adversaryAdvcan attack our scheme in the security model above with advantageε. We prove that the following DBDH game can be solved with advantagebe a bilinear map, whereGis a multiplicative cyclic group of prime orderpand generatorg. First the DBDH challenger flips a binary coinotherwise he setswherea,b,c∈Zpare randomly selected.The challenger then gives the simulatorThe simulatorSimthen plays the role of a challenger in the following DBDH game.
InitThe adversaryAdvcreates an access tree Γ∗which he wants to be challenged(Nodes inside the tree should be defined byAdv).
SetupSimsets the parame-For alli∈S, it will choose a randomand setOtherwise it chooses a random numberβi∈Zpand setsThen it will give this public parameters toAdv.
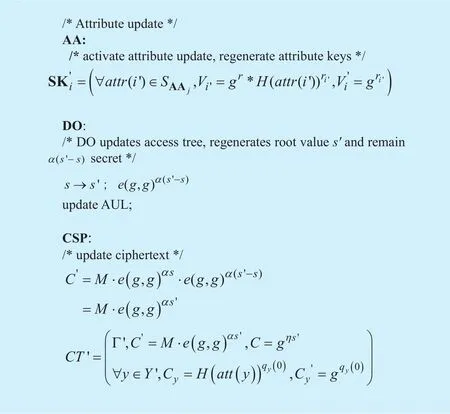
Fig. 6. Procedure of attributes update.
Phase 1Advqueries for as many private keys, which correspond to attribute setsS1,S2, …Sq, where none of them satisfy the Γ∗.After receiving the key queries,Simcomputes the private key components to respondAdv’s requests.Simfirst defines a polynomialqxfor each nodexof Γ∗. For each nodexof Γ∗, we knowqxcompletely ifxcan be satisfied; ifxis not satisfied, then at leastgqx(0)is known.Simsetsfor each nodexof access tree,Simdefines the final polynomialFor alli∈Sk, he randomly picksi∈Sk, and computeotherwiseThen,simreturns the created private key toAdv.
ChallengeThe adversaryAdvsubmits two equal length challenge messagesM0andM1to the challenger. The challenger flips a binary coinγ, and returns the following ciphertext toAdv.
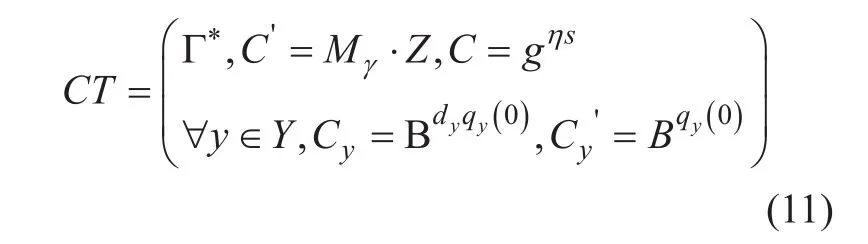
Ifμ=1,Z=e(g,g)abc. Letα=ab,s=c, ThenTherefore,CTis a valid ciphertext of the messagemγ. Otherwise, ifSincez∈Zpis a random element,C'∈GTis a random element, thereforeCTcontains no information aboutmγ.
Phase 2Repeat Phase 1 adaptively.
GuessAdvsubmits a guessγ' ofγ. Ifγ'=γ,Simoutputsµ=1, indicating that it was given a valid DBDH-tuple, otherwise it outputsµ=0, indicating that he was given a random 5-element tuple .
Whenµ=0, the adversaryAdvlearns no information aboutγ, so we haveSince the challenger guessesµ'=0 whenγ'=γ, we haveIfµ=1, the adversaryAdvgets a valid ciphertext ofmγ.Adv'sadvantage in this situation isεby definition,so we havethe challenger guessesµ'=1 whenγ'=γ,we haveSo the overall advantage ofSimin this DBDH game is:
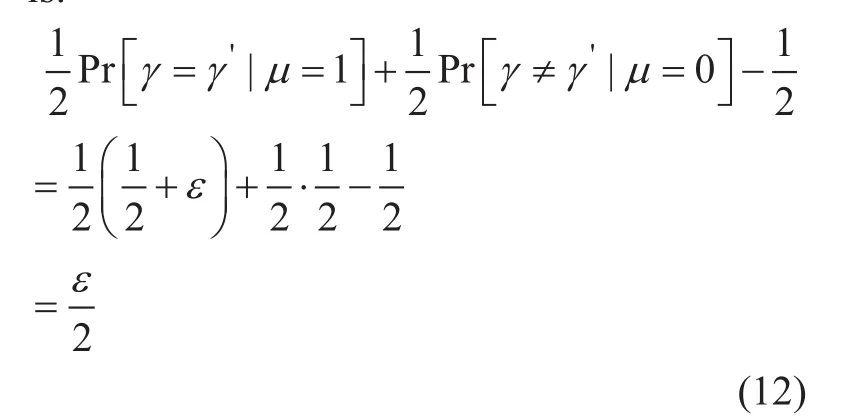
Theorem2Our scheme is secure against collusion attack between users and authorities.
In our scheme, in order to decrypt the ciphertext, the attacker must obtain bilinear pairinge(g,g)αs. In order to perform attack successfully, attacker must collect all valid attribute secret keys,but from the form of attribute secret keywe can see thatwhereris a random value chosen uniquely for each legitimate user. Based on Equation (8)to Equation (10), decryption process can be implemented successfully iff=e(g,g)αs, which requires user specific secret key of the authorized users. Based on the security assumption in section 3.2 authorized user will not participate in collusion attack.
In revocation, once the user is revoked, DO will re-encrypt the plaintext, generate new ciphertextMe(g,g)α'sorMe(g,g)αs'and new private key componentsorBut the revoked users only has previous secret keys, so the revoked users can not decrypt.Our scheme can also resist collusion attacks between attribute authorities. Attribute authority is only responsible for generating the attribute keys, even if multiple authorities collude,they will not obtain calculating factorgr.Therefore, they can not get whole secret keys and decrypt the ciphertext.
7.2 Performance evaluation
We present the performance evaluation based on our DMA implementation prototype. Our experiment is implemented on a Linux Ubuntu with Inter(R)Core(TM) i5-6500 @ 3.2GHz and 2GB RAM. The code is modified on original CP-ABE library[28].The code uses the Pairing-Based Cryptography(PBC) library version 0.5.12 to implement the access control scheme. We will compare the computation efficiency of both encryption and decryption in two criteria: the number of authorities and the number of attributes per authority. In order to show the efficiency of our scheme, we implement other similar schemes that are propose in[9][29][32][33] for comparison purpose.
Figure 7 shows the comparison of key generation time with different number of authori-ties. The number of authorities changes from 2 to 10, each authority issues 20 attribute keys.Figure 8 shows the comparison of key generation time with different number of attributes.The number of authorities in this experiment is set to be 4, the number of attributes generated by each authority varies from 2 to 25.
Figure 9 and Figure 10 show the comparison of encryption and decryption time with different number of attributes. The encryption and decryption time are measured under file size 100KB, attributes number varies from 2 to 20.
Figure 11 and Figure 12 show the comparison of encryption and decryption time with different file size. The number of attributes is set to be 20, the file size varies from 2 MB to 256 MB.
From the experiment results we find out that our scheme makes much improvement in key generation, encryption and decryption under different system set. The reason why our scheme is very efficient is that we refactor the original CP-ABE and extend it into multi-authority scenario.
7.3 APP performance evaluation
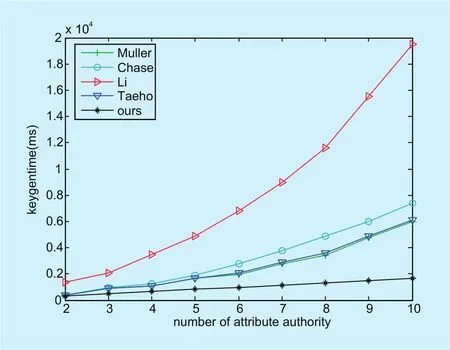
Fig. 7. KeyGen time with different number of authorities.

Fig. 8. KeyGen time with different number of attributes.

Fig. 9. Encryption time with different number of authorities
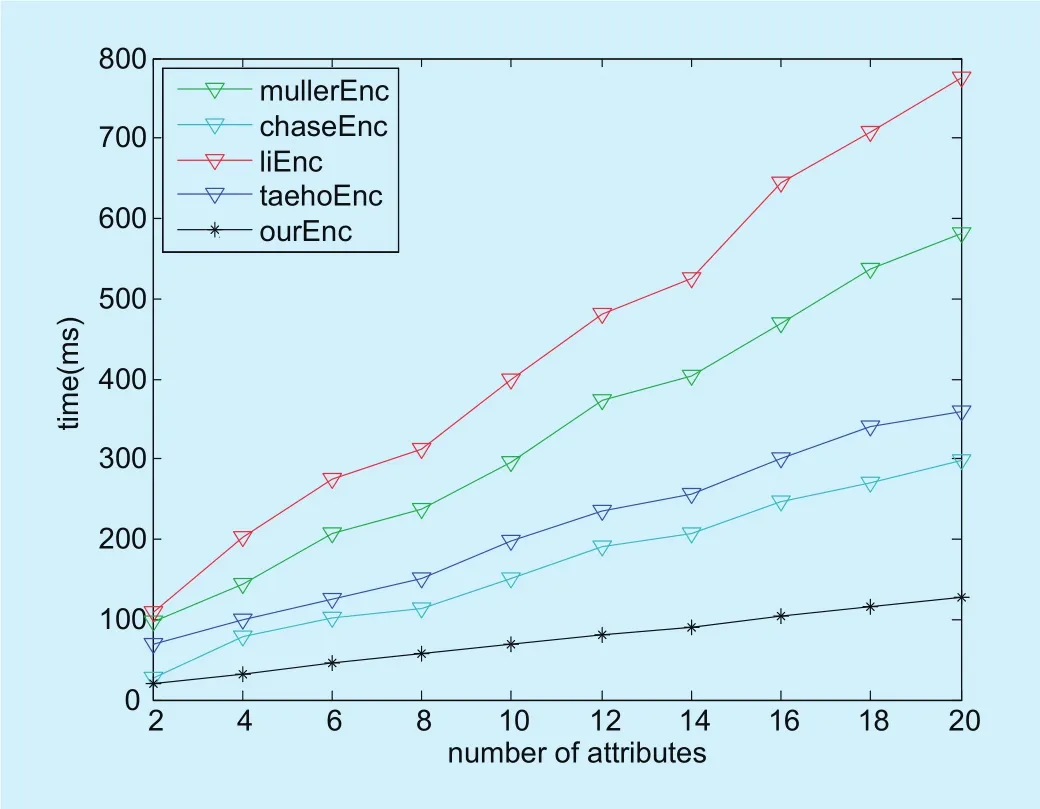
Fig. 10. Decryption time with different number of attributes.
We firstly implement the DMA in mobile phone and measure its efficiency. The measurement is done by a public mobile applica-tion performance test platform www.testin.cn.The test is carried out on 50 mobile devices run Android system from different manufactures. The performance results of DMA is shown in Table I.
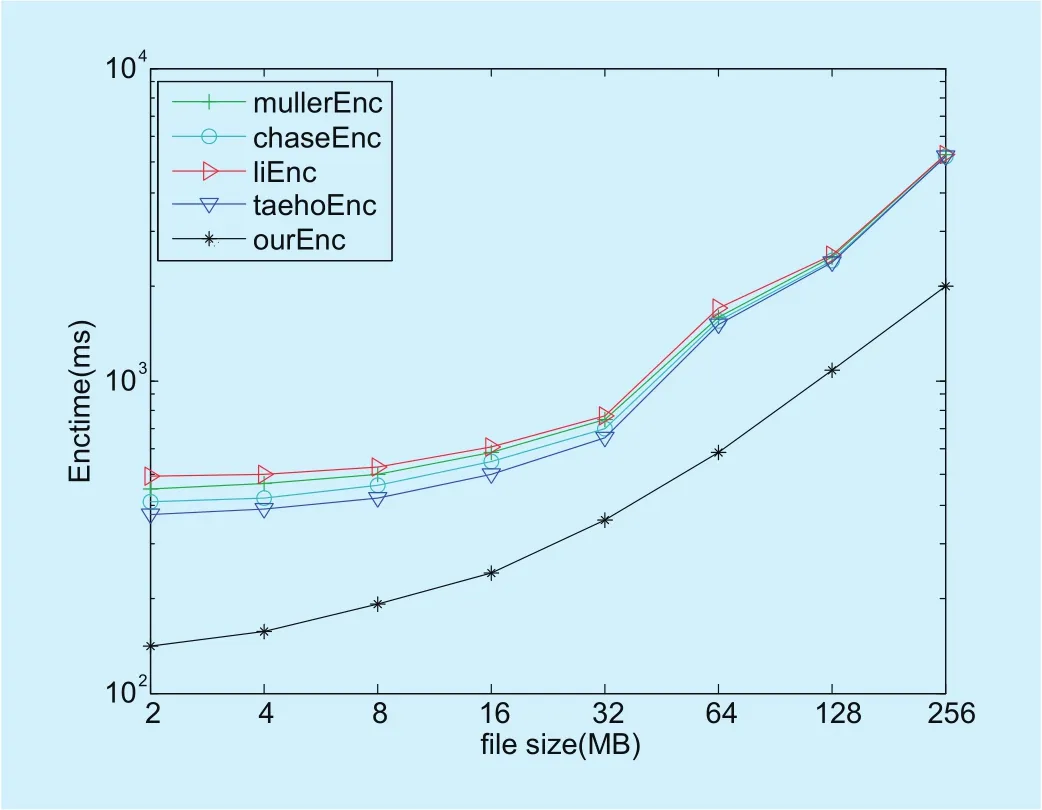
Fig. 11. Encryption time with different size of files.

Fig. 12. Decryption time with different size of files.

Table I. Performance of DMA on mobile phones.
VIII. CONCLUSION
Our scheme presents the access control method based on Multi-Authority ABE. We use access tree that manage attributes which belongs to different authorities to achieve cross-domain data storage and access control. Theoretical analysis and experiment demonstrate that our scheme can not only achieve ciphertext access control, preventing collusion attacks between users and authorities; but also improve the efficiency of ciphertext encryption and decryption. Therefore, the proposed method can be applied to multi-authority scenario in cloud storage for efficient data encryption and decryption and provides an effective way to access data for cross-domain. In addition,we propose fine-grained user-level and attribute-level revocation schemes with low computation and communication costs.
ACKNOWLEDGEMENTS
This work is supported by the National Natural Science Foundation of China under grant 61402160. Hunan Provincial Natural Science Foundation of China under grant 2016JJ3043. Open Funding for Universities in Hunan Province under grant 14K023.
[1] R. Chow, P. Golle, M. Jakobssonet al., “Controlling Data in the Cloud: Outsourcing Computation without Outsourcing Control”.Proceedings of IEEE 3rd International Conference on Cloud Computing, pp.85-90, July 2010.
[2] A. Shamir. “Identity-based crypto systems and signature schemes.”Proceedings of Advances in Cryptology (CRYPTO’84). Berlin, Springer Berlin Heidelberg, pp. 47–53, 1984.
[3] J. Bethencourt, A. Sahai, B. Waters. “Ciphertext-policy Attribute-based Encryption.”Proceedings of IEEE Symposium Security and Privacy. Berkeley, CA, pp. 321-334, 2007.
[4] B. Waters. “Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization.”Proceedings of Public Key Cryptography (PKC’11), pp.53-70, 2011.
[5] Shulan Wang, Junwei Zhou, Josph K. Liu, et al. “An Efficient File Hierarchy Attribute-Based Encryption Scheme in Cloud Computing”.IEEE Transactions on Information Forensics and Secu-rity, vol.11, no.6, pp. 1265-1277, 2016.
[6] A. Balu, K. Kuppusamy. “An expressive and provably secure ciphertext-policy attribute-based encryption.”Information Sciences, vol. 276, pp.354–362, Aug. 2014.
[7] H. Kwon, D. Kim, C. Hahn, et al. “Security authentication using ciphertext policy attribute-based encryption in mobile multi-hop networks.”Multimedia Tools and Applications,vol.75, pp.1-15, 2016.
[8] V. Goyal, A. Jain, O. Pandey, A. Sahai, “Bounded ciphertext policy attribute based encryption.”Proceedings of the 35th International Colloquium(ICALP’08). Lecture Notes in Computer Science,vol. 5126. Springer, pp. 579–591, 2008.
[9] M. Chase. “Multi-authority attribute based encryption.”Proceedings of Cryptography Conference on Theory of Cryptography (TCC’07),Amsterdam, Springer Berlin Heidelberg, pp. 515–534, 2007.
[10] J. Liu, X. Huang, and J. K. Liu, “Secure sharing of personal health records in cloud computing:ciphertext-policy attribute-based signcryption,”Future Generation Computer Systems, vol. 52,pp. 67–76, Nov. 2015.
[11] M. Chase and S. S. M. Chow, “Improving privacy and security in multi-authority attribute-based encryption.”Proceedings of the 16th ACM Con-ference on Computer and Communications Security (CCS’09), pp. 121–130, 2009.
[12] A. Ahire, P. Jawalkar. “Secure system for data sharing using cipher-text policy attribute encryption with message authentication codes for data integrity.”International Research Journal of Engineering and Technology, vol. 22, no.5,pp:1021-1027, Aug. 2015.
[13] A. B. Lewko, T. Okamoto, A. Sahai, K. Takashima,and B. Waters. “Fully secure functional encryption: Attribute-based encryption and (hierarchical) inner product encryption.”Proceedings of the 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques: Advances in Cryptology ( EUROCRYPT’10). Springer, pp. 62–91, 2010.
[14] H. Lin, Z. F. Cao, X. Liang. “Secure threshold multi-authority attribute-based encryption without a central authority.”Proceedings of International Conference on Cryptology,pp.426−436, 2008.
[15] A Lewko and B. Waters. “Decentralizing attribute-based encryption.“Proceedings of International Conference on the Theory and Applications of Cryptographic Techniques, pp. 568–588,2011.
[16] K. Yang , X. Jia, K. Ren. “DAC-MACS: Effective Date Access Control for Multi-Authority Cloud Storage Systems.”IEEE Transactions on Information Forensics and Security, vol.8, no 11, pp.1790-1801, 2013.
[17] K. Yang , X. Jia. “Attribute-based Access Control for Multi-Authority System in Cloud Storage.”Proceedings of International Conference on Distributed Computing Systems (ICDCS),pp. 536-545, 2012.
[18] K. Yang , X. Jia. “Expressive, Efficient and Revocable Data Access Control for Multi-Authority Cloud Storage.”IEEE Transactions on Parallel and Distributed Systems, vol.25, no.7, pp. 1735-1744, 2013.
[19] J. Taeho, X. Li, Z. Wan, et al. “Privacy Preserving Cloud Data Access With Multi-Authorities.”Proceedings of IEEE INFOCOM, pp. 2625-2633,2013.
[20] S. Yu, C. Wang, K. Ren, and W. Lou. “Attribute based data sharing with attribute revocation.”Proceedings of the 5th ACM Symposium on Information, Computer and Communications Security, pp. 261–270, 2010.
[21] S. Jahid, P. Mittal, and N. Borisov, “Easier: Encryption-based access control in social networks with efficient revocation, ”Proceedings of the 6th ACM Symposium on Information,Computer and Communications Security, pp.411–415, 2011.
[22] R. Ostrovsky, A.Sahai, B. Waters. “Attribute-Based encryption with non-monotonic access structures.”Proceedings of the ACM Conference On Computer and Communications Security.pp. 195−203, 2007.
[23] Z. Xu and K. M. Martin. “Dynamic user revocation and key refreshing for attribute-based encryption in cloud storage.”Proceedings of 2012 IEEE 11th International Conference on Trust,Security and Privacy in Computing and Communications, pp. 844–849, 2012.
[24] J. Hur. “Improving Security and Efficiency in Attribute-Based Data Sharing.”IEEE Transactions on Knowledge and Data Engineering, vol. 25, no.10, pp. 2271 - 2282, 2013.
[25] S. Ruj, A. Nayak, I. Stojmenovic. “DACC: Distributed Access Control in Clouds.”Proceedings of IEEE TrustCom, pp. 91-98, 2011.
[26] M. Li, S. Yu , Y. Zheng, et al. “Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption.”IEEE Transactions on Parallel and Distributed Systems, vol. 24, no. 1, pp. 131-143, 2012.
[27] J. Hur, K. Kang. “Secure Data Retrieval for Decentralized Disruption-Tolerant Military Networks.”IEEE/ACM Transactions on Networking,vol. 22, no.1, pp. 16-26, 2014.
[28] J. Bethencourt, A. Sahai, B. Waters. The cpabe toolkit [OL]. http://acsc.csl.sri.com/cpabe/.2007.3.
[29] T. Jung, X. Li, Z. Wan, et al. “Control cloud data access privilege and anonymity with fully anonymous attribute-based encryption.”IEEE Transaction on Information Forensics and Security,vol. 10, no. 1, pp. 190-199, Jan. 2015.
[30] R. Canetti. “Decisional Deffie-Hellman assump-tion.”Encyclopedia of Cryptography and Security, pp.140-142, 2005.
[31] C. Gentry, A. Silverberg. “Hierarchy ID-based cryptography.”Advances in Cryptology, pp.548-566, Dec. 2002.
[32] S. Muller, S. Katzenbeisser, and C. Eckert,“On multi-authority ciphertext-policy attribute-based encryption, ”Bulletin of the Korean Mathematical Society,vol. 46, no. 4, pp. 803–819, 2009.
[33] J. Li, Q. Huang, X. Chen, S. S. Chow, D. S. Wong,and D. Xie, “Multiauthority ciphertext-policy attribute-based encryption with accountability.”Proceedings of ACM Symposium on Information(ASIACCS), pp. 386-390, 2011.
- China Communications的其它文章
- CYBERSPACE SECURITY: FOR A BETTER LIFE AND WORK
- A Cloud-Assisted Malware Detection and Suppression Framework for Wireless Multimedia System in IoT Based on Dynamic Differential Game
- An Integration Testing Framework and Evaluation Metric for Vulnerability Mining Methods
- Powermitter: Data Exfiltration from Air-Gapped Computer through Switching Power Supply
- CAPT: Context-Aware Provenance Tracing for Attack Investigation
- TPTVer: A Trusted Third Party Based Trusted Verifier for Multi-Layered Outsourced Big Data System in Cloud Environment

