Dynamic Integrity Measurement Model Based on vTPM
Ruizhong Du, Wangyang Pan,*, Junfeng Tian Cyberspace Security and Computer College, Baoding 0700,China Key Laboratory on High Trusted Information System in Hebei Province, Baoding 0700, China
I. INTRODUCTION
Trusted computing technology goes through the measurement and verification of system integrity to ensure the system credibility[1]. It must rely on TCG (Trusted Computing Group)and TPM (Trusted Platform Module) to work.Firstly, TCG establishes the trusted computing specification. TPM, a hardware component,ensures integrity measuring. Then, when the application is in running, dynamic library linking and kernel module loading, IMA[2](Integrity Measurement Architecture) which patches in kernel will measure the code and key data and offer the results to TPM, then create a Metric List (ML). When challenging,PCR metric which signed by ML and TPM will be sent to the challenger to evaluate the platform trustworthy. And a lot of redundancy will be created by inserting metric points in the system call. PRIMA[3], which is on the improvement of IMA, goes through the use of the strategy of reducing the redundancy to improve the efficiency of the system. Meanwhile,IMA and PRIMA are both static measurement for the system process. The system will not in control when after the static measurement and the software load the system. BIND[4] system metrics and hook interface are determined by the programmer. It is clear that the measurement accuracy is relatively high, but increases the programmer’s workload. It is also hard to meet the compatibility requirements. LKIM[5]system puts kernel variable as a parameter and the changed parameter as the kernel trigger point. The drawback to the LKIM system is that the variable can only find modifications to the kernel, and the integrity of the application at the user level is powerless. Literature[6]proposed to use a metric agent to implement a dynamic metric architecture for a process.This metric architecture strategy is relatively passive. Only when the metric agent receives a metric request is measured, there may be a case where the metric was tampered with a long time after the measurement agent received a measurement request, but this time is too late, so the literature proposed by the lack of initiative to measure the structure. Literature[1] proposed a dynamic measurement model which based on virtualization technology. But the model is limited to the summary value of the program code , cannot achieve dynamic integrity. Literature[7] is concerned with the remote proof of the results after the implementation of the program. It proved the process of the implementation process by measuring the whole process of implementation of the target process and the other process,file data interaction. Literature[8] proposed a cloud-based virtual machine inside and outside the hybrid monitoring dynamic measurement framework. It compared the code segment and the parameter segment of the running program in a simple way and cannot obviously show its dynamic. Literature [9] proposed a dynamic measurement model based on virtualization technology, the model strategy is limited to the summary value of the program code, the way is relatively simple. Document [10] remotely verifies the results of the program through remote challenges, and proves that the program verifies the authenticity of the interaction with other processes during runtime. Literature [11]proposed a cloud-based virtual machine inside and outside the hybrid monitoring dynamic measurement framework, run the program code and parameters of the paragraph to measure and reference list for comparison, set the strategy is relatively simple, the type of single attack.
Specific to Xen virtual machine system cannot ensure the dynamic integrity of client virtual machine when it is started. This paper put forward Dynamic Integrity Measurement Model (DIMM) of Xen Virtual Machine Based on vTPM. The main characteristic of the model is to dynamically measure the running process. The vTPM is used to encrypt the metric frame and the standard value in the process of measurement. Through the Self-modify measurement method, the historical measurement information is used as the index of the future measurement frequency, to reduce the measurement frequency enhance system security.The second part of this paper introduces the vTPM based Xen virtual machine dynamic integrity measurement model framework,the third part introduces the static measurement and dynamic measurement method, the fourth part tells the functional test and the performance test, the fifth part summarizes the whole paper and the last part is our acknowledgments fund items supported for this project.
II. SYSTEM MODEL AND EXPRESSION
The dynamic integrity measurement model of Xen virtual machine based on vTPM is composed of front-end static measurement part of client virtual machine and back-end dynamic measurement part of privileged virtual machine. The front-end is responsible for measuring some code segments and parameter segments necessary to run the program. The back-end dynamic measurement is realized by using virtual machine self-introspect, event capture technology and self-modify of the virtual as the measurement method.
Figure 1 is the framework for dynamic integrity measurement of Xen virtual machines based on vTPM, showing static and dynamic interactions between user domains and administrative domains. The model consists mainly of six components. Measurement Agent (MA)is responsible for the interaction between the front end and the back end and maintains the process metric list. Integrity Verification Module (IMV) is responsible for verifying whether the metric meets the standard. Process Integrity Measurement Module (PIMM) is responsible for the integrity of the process code segment and data segment measurement. Measurement Control List (MCL) used to describe the process of measurement information.Event Capture Module (ECM) is responsible for intercepting the process system call. The LibVMI is responsible for reading the memory data in the user domain. When the VM_EXIT event occurs, Virtual Machine Control Structure (VMCS) will store the vCPU information of the guest virtual machine.
The communication between Dom0 and DomU is realized by the ring message queue,event channel, authorization table and Xenstore mechanism. The ring message queue consists of a request queue and a response queue. Event channel is an asynchronous communication mechanism between Xen and Dom. Authorization tables are used in conjunction with shared memory. Xenstore, which managed and maintained by a privileged virtual machine, is used to transfer control information and configuration information among domains. In this paper, the privileged virtual machine, the management domain refers to the Dom0, and the client virtual machine, the user domain refers to DomU.
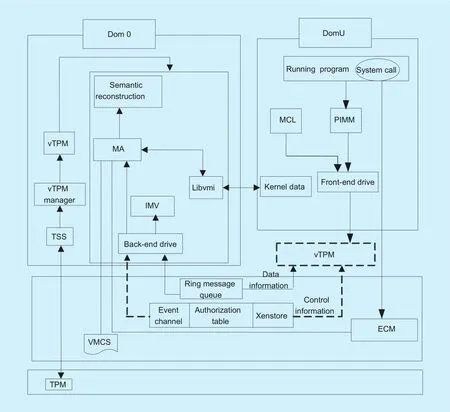
Fig. 1. Framework for Dynamic Integrity Measurement of Xen Virtual Machines Based on vTPM.
III. PROBLEM FOR MULATION
3.1 Trusted chain transfer
Trusted computing in physical machine is based on the support of TPM , while in virtual machine is based on virtual TPM (vTPM).Trusted chain is transferred to the virtual machine by vTPM in virtual environment. The vTPM is generated by the vTPM manager in the management domain, each client virtual machine corresponds to a vTPM. The privileged virtual machine corresponds to vTPM-0, the client virtual machine 1 corresponds to vTPM-1, the client virtual machine 2 corresponds to vTPM-2 ... Independent trusted computing based on TPM can be implemented to each client virtual machine by vTPM.
Figure 2 shows the establishment fl ow chart of virtual machine trust chain. First, CRTM component measures the integrity of the BIOS,then BIOS detects the hardware reliability on the motherboard, and measures the GRUB and Xen.
Hypervisor component. Make sure those critical hardware is trusted then give control to the management domain. The manager generates vTPM for each virtual machine user, and the vTPM will give a integrity measurement for all the application in user domain. That is a trusted chain from the physical hardware to the virtual machine.
3.2 vTPM-based protection methods
Relying on the support of vTPM, the dynamic integrity measurement model of Xen virtual machine based on vTPM can realize the key measurement, storage and reporting function of the system.
1) Trust start to Client virtual machines
vTPM-x (x=1,2, ...) physically plays a role in a privileged virtual machine and logically in the guest virtual machine. When the client virtual machine starts, vTPM measures the integrity of BIOS, bootloader and operating system kernel. Then stores the result in the vPCR of vTPM to ensures the trustworthiness of the initial state of the client’s virtual machine.
2) Secure Start of Dynamic Metrics Framework
After dynamic metrics framework started,vTPM measures the key components of the metrics architecture such as Integrity Verification Module, Metric Agent, and so on to ensure the security of the measurement architecture. To ensure security of the measurement architecture itself is the same important to the low coupling of the privileged virtual operating system and combine the trusted root provided by the trusted computing with the technologies such as trusted start and trust chain transfer. And put a series of security mechanisms based on trusted computing[12].
3) The encryption and decryption to the metric list
The vTPM provides platform encryption and decryption services to ensure the integrity of the benchmark. The data structure of the progress benchmark list follows:
Struct measurement_list
{
Unsigned long Process_ID;// Process_ID used to uniquely identify a process
SHA1-CTX h [Code_Hash];
SHA1-CTX h [Data_Hash]; / * The hash value of the process data page whose value is stored in the array h [Data_Hash] * /
SHA1-CTX context_hash; / * hash value of the process context * /
}
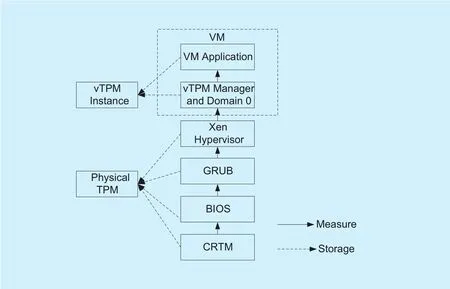
Fig. 2. The establishment fl ow chart of virtual machine trust chain.
For the safety, the metrics list maintained by the Measurement Agent in the management domain is isolated from the user virtual machine on which the application is running. Use the vTPM encryption feature to encrypt each item in the metric list. vTPM generates a pair of secret keys (public key and private key) for each process. The specific process based on vTPM protection:
(1) Let M be a process, K is a symmetric secret key generated by vTPM.
(2) K encrypted M to obtain K {M};
KPUBencrypted Process_ID and K to obtain KPUB{Process_ID, K}; If you want to get M,you must first get K, this time vTPM need KPRIdecrypt KPUB{Process_ID, K}. It is necessary to check Process_ID if the value is consistent,if not match the decryption operation fails, if the match can be obtained K, and then get the M, the encryption and decryption operations are completed by the vTPM.
3.3 Static measurements
A process is a form of dynamic execution of a program. The running process has an image file in memory[16], which reflects the function and information of the process, and the image is constantly changing[17]. The static metric measures the unaltered parameter value, initialized data (including initialized data segment, initialized stack segment). The frontend hashes the code to be measured, passes the measured hash value through the ring message queue in the virtual machine monitor to the back end of the integrity verification module[18]. If the measurement results and integrity of the benchmark value of the module (hash reference value provided by the manufacturer) is the same as the process, it can be trusted and move on. at this time , putting the integrity verification module design to the back end is a consideration for multiple client virtual machine. Adding an integrity verification module to each virtual user would increase its burden and adding full integrity to the management domain would cause frequent switching between the user domain and the admin domain. Comparison showed that the latter overhead is less than the former.

Algorithm 1. Front-end static measurement FSM (Front-end Static Measurement)algorithm.Input: File absolute path, file attributes.Output: File hash value.FSM_Hash(File,Att1, Att 2, Att 3……) // The file’s absolute path (File) and file attribute information (Att1, Att2, Att3, ...){1. fp=FOPEN(File,”rb”)// Open the file you want to measure 2. FREAD(FiIeStream, 1,len, fp);// Read the contents of the file into memory 3. FiIe_hash=vTPM_SHA-1 (FileStream+ Att 1+ Att 2+ Att 3+ ……); //Invokes vTPM for hash operation and returns its value 4. FCL0SE(fp);5. ReturnFile_hash;}Step 1,write the needed measured file’s absolute path of the attribute information(including file type, open mode, file size, modification time, etc.) into the Process Integrity Measurement Module (PIMM).Step 2, PIMM opens the file in binary and reads it into memory , Calling the hash function vTPM_SHA-1 in vTPM to hash the file.Step3, return File_hash, the hash value will be passed to the integrity authentication module of Xen through the virtual machine monitor loop message queue.
3.4 Dynamic measurements model DIMM
TCG trusts the state of the platform for the behavior is executed according to the pre-strategy. The back-end dynamic measurement module mainly analyzes the behavior of the process, compare the actual behavior of the process and the pre-set trusted strategy.Trusted policies are developed by the system administrator. Back-end measurement mainly for key system calls, the system key file hash value, the expected strategy.
3.4.1 Event Interception
System call is a multi-core with a certain function that kernel provides. Event interception in Xen virtual machines refers to interception system calls in user domains[14]. Intercepts of system calls are behavioral monitoring. Event interception and control method in client system is one of the most key techniques to monitor client system[21]. Event intercept module,located in the Xen Virtual Machine Monitor(VMM) , is responsible for event interception.When the VM_EXIT event occurs, the CPU information of the guest virtual machine is stored in the virtual machine control structure (VMCS, VMCS in VMM). The privileged virtual machine can effectively reconstruct the semantic information of the system call by VMCS to identify use’ behaviors. Through the semantic gap that between the interception of information and virtual machine, VMCS need to transfer intercept the binary data into virtual machine internal high-level semantics.
Interception includes the read and write files and the creation process of key events.The interception of the system call works with SYSENTER_CS_MSR, SYSENTER_ESP_MSR and SYSENTER_EIP_MSR[19]. The main steps as follows:
1) The event capture module saves the register SYSENTER_EIP_MSR and sets it to a memory address that does not exist.
2) When system call works in the guest virtual machine, the SYSENTER_EIP_MSR value that does not exist in memory will lead to page fault exception handling, resulting virtual machine VM_EXIT instruction. Then exception handling module can not be processed normally.
3) Event acquisition module get the system call number from the customer virtual machine vCPU in the EAX register. The reason that exception handling module arise page fault, if the address does not exist (step 1), the client virtual machine can determine whether a system call has been made ,then continue to judge whether the process is creating or deleting. If the process is created, it can obtains the ESP pointer from VMCS then obtain the Thread_info structure. Thread_info contains a pointer to the task_struct structure, then obtain the related information about process , process number, process name and so on.
4) Finally, in event module ,the saved original system call entry address that captured will be written back to the register SYSENTER_EIP_MSR, to execute the real system calls which in the kernel.
3.4.2 Virtual machine introspection LibVMI[19] is a program developed by Brian D. Payne et al. Of Sandia[20] National Laboratory to provide virtual machine introspection. Using LibVMI on a guest virtual machine makes it easy to transparently read and write to the virtual machine’s memory.LibVMI in library and fuction is much better than XenAccess. LibVMI does not modify the virtual machine manager and the target operating system, thus avoiding the introduction of vulnerabilities and enhancing security. Figure 3 shows the deployment scenario of LibVMI.It shows the process that LibVMI get Linux kernel symbol table.
The process of obtaining kernel symbol mainly by the follows: 1) Metric Proxy Requests view kernel symbols. 2) LibVMI obtains kernel symbol’s virtual address through System map. 3) Find the virtual address that corresponding to the kernel page directory,and obtain the corresponding page table. 4)Find the correct data page with the page table. 5) Return the data page to LibVMI. 6) Lib-VMI returns the data to the metric agent.

Fig. 3. How to get Linux kernel symbol table with LibVMI.
On Linux systems, when the executable imagefiles on the disk are loaded, the disk address space is mapped to the virtual address space.Each process in Linux has a process descriptor task_struct, which is in the header file linux/sched. In the process descriptor there is a member variable description process corresponding to the memory descriptor, called mm_struct.Each process has and only one mm_struct structure, it abstracts and describes the linux view of the process address space of all infor-mation, mm_struct defined in include/linux/mm_types.h. There is a point to a number of virtual storage space structure vm_area_struct link header mmap, through the header can be found in the process corresponding to all the virtual storage area, including some important member variables start_code, end_code, start_data, end_code and so on. The memory structure of the process is shown in Figure 4.
Based on Libvmi, metric agent can obtain the data structure task_struct of the system kernel symbol in the client virtual machine.The data structure can be used to obtain the list of processes, and then the target process is mapped to the hash operation of the file memory, and the result is compared with the metric list maintained by the metric agent module Compare to determine whether the system behavior is malicious.
The memory structure of the process is shown in Figure 4.
On Linux systems, when the executable image files on the disk are loaded, the disk address space is mapped to the virtual address space.Each process in Linux has a process descriptor task_struct, which is in the header file linux/sched. In the process descriptor there is a member variable description process corresponding to the memory descriptor, called mm_struct.Each process has and only one mm_struct structure, it abstracts and describes the linux view of the process address space of all information, mm_struct defined in include/linux/mm_types.h. There is a point to a number of virtual storage space structure vm_area_struct link header mmap, through the header can be found in the process corresponding to all the virtual storage area, including some important member variables start_code, end_code, start_data, end_code and so on. The memory structure of the process is shown in Figure 4.

Table I. Metric control lists.

Fig. 4. Process memory organization.
Based on Libvmi, metric agent can obtain the data structure task_struct of the system kernel symbol in the client virtual machine.The data structure can be used to obtain the list of processes, and then the target process is mapped to the hash operation of the file memory, and the result is compared with the metric list maintained by the metric agent module Compare to determine whether the system behavior is malicious.
3.4.3 Self-modify dynamic measurement strategy
Each user domain maintains a Measurement Control List (MCL), which is used to describe the information that the process is measuring.The design is shown in Table 1.
Note: Tn (True numbers), said the current user domain of the process from the last measurement failure to the current cumulative measure of the number of correct. Fn (True numbers), said the current user domain the process from the last measurement is correct to the present cumulative measurement failures.Rt (Remaining time, the remaining time of the cycle), said the the remaining time from current user domain to the next , Sc (Scan cycle),which indicates the scan cycle of the metric agent to the measurement record list. Tcurrent is the interval between the two processes that are taken by the self-modifying metric.
For the convenience of the study, the metric control list is initialized as follows: Tn= 0, Fn=0, Rt is initially the initial measurement cycle IMC (Initial Measurement Cycle) that does not take the self-modifying metric, Rt=IMC=30s,Sc = 5s. Tcurrent changes with Fn and Tn; the most recent measurement period Tcurrent is the value calculated by MA according to the Fn and Tn values in the current MCL.
Tcurrent Calculation Method: The value of the measurement period Tcurrent is calculated from the original measurement period IMC and the measurement frequency F. The calculation method is Tcurrent = IMC/F, where F is calculated as follows:
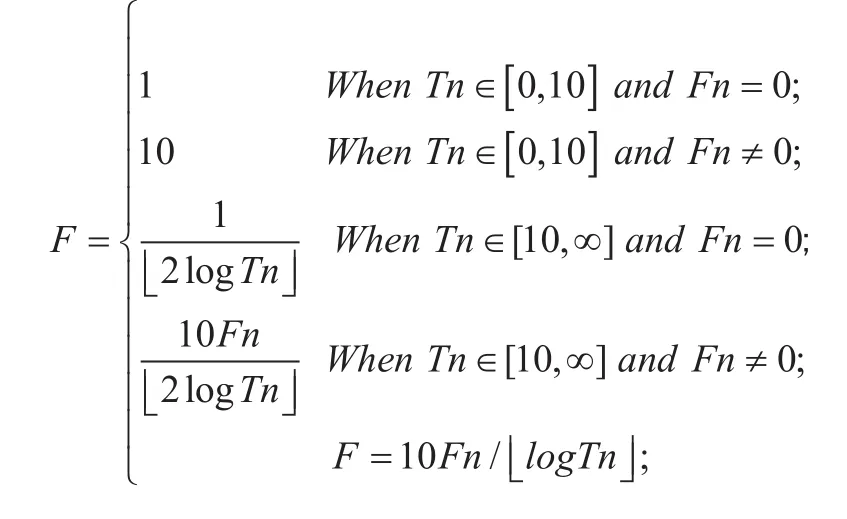
Example: Let a process for the P1, Fn= 0,Tn=100, you can calculate F=1/4, the measurement cycle Tcurrent = 4IMC=120s, that is, every 120s to do a measurement of the process; Fn=1, Tn=100, can be calculated F=5/2,the measurement cycle Tcurrent=0.4IMC=12s, that is, every 12s to do a measurement of the process. As can be seen from the example, the shorter the time from the next metric as the number of errors is increased...
The specific process is as follows:
Step 1: Initialize the MCL items, the initialization process as described in Section 3.3.3;
Step 2: the remaining time of the cycle minus the metric agent scan cycle to determine whether the process should be measured, if you need to measure, turn Step 3, if you do not need to measure, turn Step 4;
Step 3: determine the process is the correct measure or the wrong measure, if the correct measure to step 3.1, if the wrong measure,turn Step 3.2;
Step 3.1: correct the number of measures plus 1, and update Rt;
Step 3.2: Correct the number of measurements cleared, the number of error measures plus 1 and update Rt, notify the other user domain the process of measurement errors;

Algorithm 2. Adaptive Dynamic Measurement Strategy ADMS (Adaptive Dynamic Measurement Strategy) pseudo-code algorithm.Enter: MCL table entries.Output: The updated MCL table entries.ADMS(MCL){1. Init(MCL);// Initialize the MCL table entries 2. Rt←Rt-Sc;3. if (Rt<=0);4. { Measure progress P;5. If (P)6. { Tn←Tn+1;7. Rt←Tcurrent; // If the process of measuring the right P Tn plus 1.8. }9. else 10. { Tn←0;11. Fn←Fn+1;12. Rt←Tcurrent;13. Notify other Dom; // If the process metric is wrong, Tn is 0, the error count is incremented by 1, and other user domains will be notified.14. }15. }16. else 17. end;18. Return(MCL);}
Step 4: The metric ends and returns the MCL .
3.4.4 The specific steps of back-end metrics
1. Run the process of static measurement obtain the trust, the MCL table for all processes corresponding to the Rt minus SC, remove the list of Rt<=0 in the process, set these processes set to P1, the system is currently running the process of P2, then P1 ∩ P2 is the need to measure the process. The MCL sends the Process_ID that needs the metric to the MA.
2. The ECM in the virtual machine monitor intercepts the system call of the running process. The measurement agent module obtains the relevant information of the process through the VMCS to check whether the system call sequence is consistent with the preset policy and whether sensitive operation is involved.Where Σ is a set of all system calls that may be performed by a program, Σ* is a set of all sequences on Σ that are determined by a preset strategy, and whether the system call sequence is in the Σ* set, that is, whether Set strategy consistent.
3. The need to measure the process through the LibVMI mapping process will be the target of the implementation of its hash file operation, and the measurement agent module to compare the default value (event capture module can be opened through the task_struct process involved in the current file) , To determine whether the damage to the key system files (where the system kernel file is defined as a key file, such as certain documents can only be read and write by a specific process),update the MCL table, if the measurement error also notify other user domain, The user domain receives the notification and scans the MCL table and updates it.
4. With the system call interception and Lib-VMI as the measurement means, the adaptive dynamic measure is used to identify and kill the threatening process running in the system.
IV. TEST
The function test and performance test of the proposed dynamic performance measurement model of Xen virtual machine based on vTPM. The function test is to test whether the proposed method can ensure the credibility of the process running. The performance test is to evaluate whether the overhead generated by the dynamic metric model is within the acceptable range. The performance test is compared with the classical static measurement model IMA, and the cost of the method proposed in this paper. Experimental environment configuration:chine manager installed on WindowsXP and Ubuntu12.04.1 system.
4.1 Functional testing
(1) Attacks on the SSH Program
In the integrity measurement model, we select the more common attacks on the SSH program to illustrate its effectiveness. SSH is a protocol that provides secure remote login and other secure network services over an insecure network. An attacker acquires a user’s login by using a forged public key between a user and a remote host. Results are shown in Table 2. Table 2 (a) shows the attack before the system of all the processes to measure and calculate the hash value, Table 2 (b) shows after the attacker successfully attack on the SSH program, the program has been replaced by a modified procedure, and the hash value has changed. The system successfully detects the difference and rejects its running.
(2) Tamper Attacks on Sub-modules
Table 3 is the attack on sub-module, Table 3 (a) is the hash value before tampering, Table 3 (b) is the tampered hash value, we can see the hash value changed significantly from the figure, DIMM has identified out effectively.
Hardware configuration: Intel Core i5 3.20GHZ * 4 processors, memory, 8GB, 1TB hard drive.
Software configuration: virtual machine monitor (VMM) using Xen4.1.4 system, management domain virtual machine operating system using Ubuntu12.04.1, Xen virtual ma-
4.2 Performance testing
Performance test is a test for the system performance influenced by theb self-modifying dynamic metric DIMM model. Compare with the general Xen virtual platform and analyze the delay caused by the model.Experiments test the system call by using the Lmbench that is a simple and portable micro-evaluation tool.Select I/O from the Lmbench I/O to operate Null I/O, system call Null call, document state operate Stat, after document is opened,immediately shut down the operation of Open+close, read and write operations Write,Fork+exec Read and Fork execve operation is performed after. By comparing the DIMM model of Xen found in the test set of Null I/O,Null call, Stat, Open+close, Read and Write under Xen platform and time cost are close to the cost of Fork+exec is very large, Fork+exec operation to get the executable file of the hash value through the FSM algorithm in section 3.3, this part is the main reason for the DIMM model with a larger the Xen platform overhead, but the calculation of hash value calculated only once before running, with a smaller proportion of Fork+exec accounted for in system calls, so in DIMM this cost is within acceptable limits.
Figure 5 is an example of a Self-modifying Dynamic Metric Measures. Assuming that k is the number of scans, k = 0 initializes 3 processes IMC is 30s, Sc is 5s, k∈ [0,8] ,belongs to first stage; When k = 9, process 1measurement error, Tcurrent = IMC / 10Fn = 30/10= 3s,At this point, the processes 2, 3 of the Tcurrent did not change, k ∈ [9,99] belongs to the second stage; When k = 100, 1 process Tcurrent = (IMC / 10Fn) / 4 = 12s, process 2,3 Tcurrent = IMC * 2 * 2 = 120s, k ∈ [100,999]belongs to the third stage; When k = 1045,process 2 measurement error, process 2Tcurrent = (IMC / 10) / 6 = 18s, while process1,3 calculation of Tcurrent are 180s, k ∈ [1000,∞] belongs to the fourth stage.
It can be seen from Figure 5 that process3 does not occur measurement error. Along with the longer measurement interval, process1 is consistent with process 3 ,because process 1 occured error measurement in the second stage and did not have measurement error in the fourth stage. the process 2 occurs the measurement error the fourth stage that led to the measurement interval is less than the initialization time. Therefore, the self-modifying metric can reduce the metric frequency by using the historical metric as an indicator of the frequency of the future measurement.
Table 5 is a performance comparison of DIMM dynamic metrics and IMA using static metrics. The table gives the number of processes, the process name, the metric, and the measurement time consuming. DIMM only includes CPU time consuming, IMA includes: I/O time consuming and metric time consuming.

Table II(a). The results of the pre-attack experiments.

Table II(b). The results of the pre-attack experiments.

Table III(a). The hash value before tampering.

Table III(b). Tampered hash value.
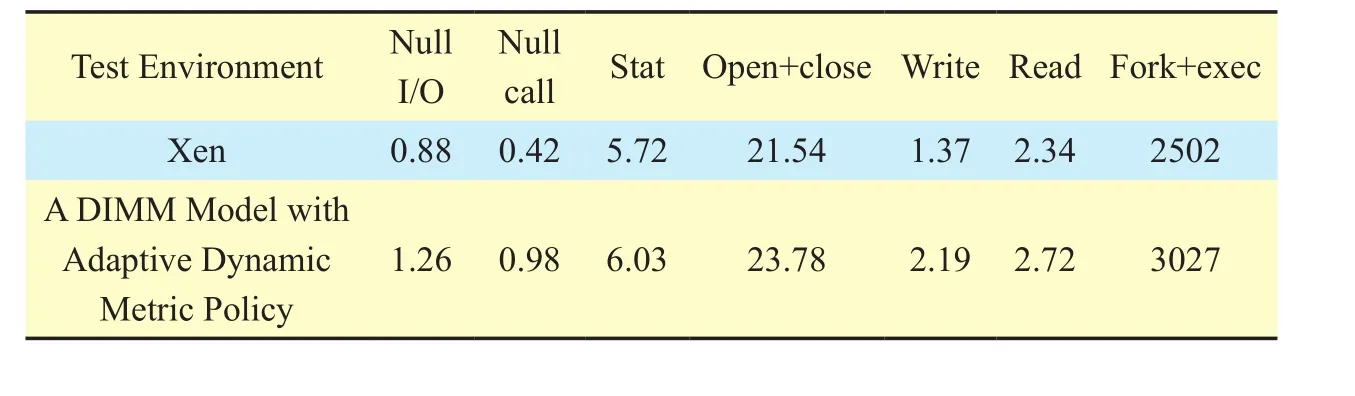
Table IV. Comparison of DIMM model and xen system call test results (μs).
As can be seen from Table 5, Time-consuming of 25 processes in DIMM and IMA CPU are 93.224ms, 812.726ms. ssh-agent, nautilus,netns ... gnome-terminal respectively are respectively key management processes, System file management process, network simulation process ... terminal simulation process. The time-consuming unit in these processes’ is in milliseconds. It is clear that the IMA total time is far greater than the DIMM model, which is due to the fact that the I/O operation time in the IMA static metric is almost occupied by the entire measurement time. The static metric needs to be measured by the disk by the disk.To the memory, and the DIMM dynamic measurement only need to be measured code from the user state copy to memory, fully aware of the performance of the DIMM model was signicantly better than the IMA model.

Fig. 5. Comparison of examples of Self-modify dynamic measurement.
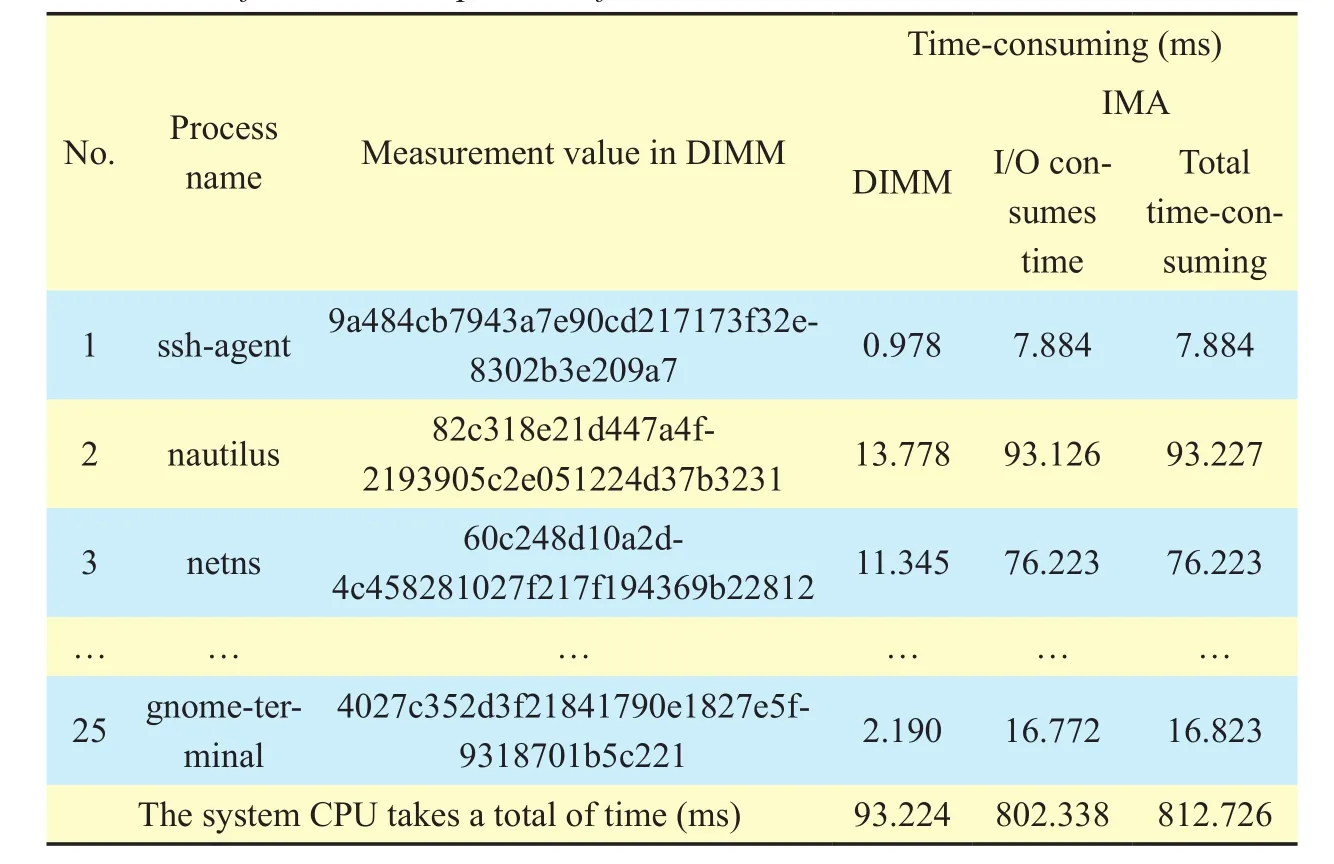
Table V. Performance comparison of DIMM model and IMA.
V. CONCLUSIONS
This paper proposes a dynamic integrity measurement model of Xen virtual machine based on vTPM. The user domain and management domain in Xen respectively measure static and dynamic processes. This model enhances the dynamic integrity and security of virtual machines .Finally, the measurement framework is built by using integrity measure, system call intercept, virtual machine introspection technique and adaptive metric strategy. To a certain extent, to ensure the dynamic credibility of the platform, and has some anti-attack capability.The experiment proves the feasibility of the model. The limitations of the proposed model are that process of attacking can not be effectively identified, which is the author needs to improve and perfect the next step.
ACKNOWLEDGEMENTS
This project is supported by National Natural Science Foundation of China(61170254,61379116), Hebei Natural Science Foundation Project (F2016201244), Hebei Province Science and Technology Research Project of Higher Education (ZD2016043), Hebei Engineering Technology Research Center for IOT Data Acquisition & Processing, North China Insitute of Science and Technology, Hebei 065201,China,we hereby express our thanks.
[1] Yang Bei. “Dynamic integrity measurement model based on trusted computing” [D].Shaanxi: Shaanxi Normal University, Master’s degree thesis,2011.
[2] SAILER R, ZHANG Xiao-lan, JAEGER T, et al. “Design and implementation of a TCG-based integrity measurement architecture” [C].Proccedings of the 13th Conference on USENIX Security Symposium.Berkeley: USENIX Association, 2004: 223 -238.
[3] JAEGER T, SAILER R, SHANKAR U. PRIMA: “Policy-reduced integrity measurement architecture”[C].Proceedings of the 11th ACM Symposium on Access Control Models and Technologies. New York: ACM Press,2006: 19-28.
[4] SHI E, PERRIG A, Van DOORN L. “BIND: anegrained attestation service for secure distributed systems”[C].Proceedings of IEEE Symposium on Security and Privacy. Washington DC: IEEEComputer Society,2005: 154-168 .
[5] LOSCOCCO P A, WILSON P W, PENDERGRASS J A, et al. “Linux kernel integrity measurement using contextual inspection” [C].Proceedings of ACM Workshop on Scalable Trusted Computing.New York: ACM Press,2007: 21-29.
[6] LIU Zi-Wen, FENG Deng-Guo. “Dynamic Integrity Measurement Architecture Based on Trusted Computing”[J].Journal of Electronics & Information Technology,2010, 32 (4): 875-879.
[7] Gu Liang, Ding Xu-hua, Deng RH, Xie Bing, and Mei Hong. “Remote attestation on program execution”[C].Conference on Computer and Communications Security Proceedings of the 3rd ACM workshop on Scalable trusted computing.Alexandria, Virginia, USA,2008: 11-20.
[8] Y. Wang and Y. Luo. “An In-Out-VM measurement architecture against dynamic attacks in clouds”[C].In Proceedings of the 14th International Conference on Communication Technolog,Nov 2012.
[9] Yang Bei. “Based on trusted computing dynamic integrity metrics model” [D].Shaanxi: Shaanxi Normal University,2011.6.
[10] Gu Liang, Ding Xu-hua, eng R H, ie Bing, nd Mei Hong. “Remote Attestation on Program Execution”[C].Conference on Computer and Communications Security Proceedings of the3rd ACM Workshop on Scalable Trusted Computing.Alexandria, irginia, SA, 008: 11-20.
[11] Y. Wang and Y. Luo. “An In-Out-VM Measurement Architecture Against Dynamic Dttacks in Clouds”[C].In Proceedings of the 14th International Conference on Communication Technolog,Nov 2012.
[12] ZHANG Wen-rong. “Study on trust monitoring framework of cloud platform”[D].Wuhan:Huazhong University of Science and Technology,Master’s degree thesis, 2013.
[13] Wang Jing. “Virtualization of Equipment with Strongly Isolated Operating System” [D].Beijing:University of Science and Technology of China,Ph.D.
[14] Xin Siyuan. “Study on Trusted Architecture and Model of Trusted Operating System” [D].Zhengzhou:PLA University of Information Engineering,Ph.D.
[15] Trusted Computing Group. TCG specification architecture overview,version1.4[EB/OL].[2013-04-22]. http://www.trustecomputinggroup.org/tcg_architecture_overview_version_14.
[16] XIANG Guofu, GAI Hai. “Virtualization-based security monitoring”[J] .Journal of Software,2012,23 (8): 2173-2187.
[17] Journal of Nanjing University of Science and Technology, 2010, 39 (2): 236-240. [14] SHI Yi,LI Shu-ying. Semantic Reconstruction Method Based on System Call Analysis in Xen Virtualization Platform [J].
[18] http://code.google.com/p/vmitools/.
[19] http://www.sandia.gov/.
[20] Hou Wenting. “Design and Implementation of Personalized Security Monitoring System for Virtual Machine Based on Xen Platform”[D].Xi’an: Xi’an University of Electronic Science and Technology, Master’s Dissertation,2014.
[21] Lin Jie, Liu Chuanyi. “IVirt: Virtual Machine Self-examination based on the operating environment integrity measurement mechanism”[J].Journal of Computers, 2015, 38 (1).
- China Communications的其它文章
- CYBERSPACE SECURITY: FOR A BETTER LIFE AND WORK
- A Cloud-Assisted Malware Detection and Suppression Framework for Wireless Multimedia System in IoT Based on Dynamic Differential Game
- An Integration Testing Framework and Evaluation Metric for Vulnerability Mining Methods
- Powermitter: Data Exfiltration from Air-Gapped Computer through Switching Power Supply
- CAPT: Context-Aware Provenance Tracing for Attack Investigation
- Decentralized Attribute-Based Encryption and Data Sharing Scheme in Cloud Storage

