Quantum Key Distribution Network: Optimal Secret-Key- Aware Routing Method for Trust Relaying
Chao Yang*, Hongqi Zhang, Jinhai Su
Science and Technology Information Research Institute, Zhengzhou, Henan, China
I. INTRODUCTION
Quantum key distribution [1] (QKD) technology can provide unconditional security keys for two remote communicating partners on classical network. Through encoding and transmitting information (the secret keys needed to be distributed) by quantum state, the QKD system can establish secret keys between two partners. Because of the inherent characteristics of quantum physics, any eavesdropping on the key can be found by legitimate communication parties [2]. In addition, combined with one-time-pad (OTP) cryptographic algorithm,communicating partners can achieve unconditional security communication by QKD technology. Therefore, QKD technology is considered to be a future secure communication solution for the defense, finance, medical and other fields.
However, there still are some limits in point-to-point QKD system. Firstly, the quantum key distribution distance is still limited to a certain distance [3], which is far from global scale. Secondly, the quantum key distribution speed is also limited and relatively low[4]. Thirdly, the point-to-point QKD system just can distribute key between two partners,which can’t meet the actual communication requirements of multi-user and networking.
To overcome these limits, QKD network consisted of multiple point-to-point QKD system become the first choice [5]. So far, many researchers have concentrated on the research of the QKD network, and some small-scale QKD networks have been built to explore this new type network. According to the working principle within the QKD networks, these QKD networks could be divided into two categories: optical-path-switching network [6] and trust-relaying network [7]. The former used optical instruments, such as optical switching and wavelength division multiplexing, to temporary establish a quantum channel for any two users to generate keys. Two testing networks [8, 9] in Anhui, China, built by two groups from China are all examples of optical-path-switching QKD network. The latter used the secret keys generated by multiple intermediate independent point-to-point QKD system to encrypt and transmit the secret keys needed to be distributed, which can achieve secret key sharing between two long distance communicating partners. Since the shared secret keys between the communicating partners were protected and exchanged by multiple intermediate QKD system, this type network was also called “hop-by-hop” network [10].There also are many trust-relaying QKD networks have been built, such as the DARPA network [11, 12], the SECOQC network [13],and the 6-nodes high speed QKD network in Tokyo [14] and so on.
These previous researches provide many valuable experiences for further studying and building large-scale QKD network, however,all of these previous researches seldom focused on the routing mechanism on the QKD network [15]. As a naturally arising issue when building a practical QKD network, routing problems are worth drawing much more attentions [16].
As the secret key distribution rate of each point-to-point QKD system in QKD network is limited and relatively low, choosing an optimal path to share secret key for long distance parties is not only important to improve their communication quality but also important to improve the performance of the whole network. However, the structure of QKD network is different from the classical network, so the existing mature routing technologies used in classical network can’t be used in QKD network directly. Therefore, research on the routing mechanism of QKD network is very important to the application and development for QKD network. Q. Han, L. Yu, et.al [17] proposed a Multi-Path Search Algorithm (MPSA)for the routing search of optical-path-switching network through defining the link cost as the propagation loss of photons in the optical fiber. The OSPF protocol [18] was used to calculate the next routing hop in SECOQC network [19]. Yoshimichi Tanizawa, et.al [15]analyzed the routing problems in trust-relaying QKD network in detail and proposed a routing scheme based on OSPF protocol. The method in [15] considered the quantities of secret key associated with each link when calculating the link cost, which improved the quality assurance for the two parties’ communication.However, only considering the quantities of secret key is not enough, which will be analyzed in the following sections in detail. Li M,et.al [20] proposed a stochastic routing algorithm by considering the quantities of secret key and randomly choosing one next hop to relay secret key. This algorithm can increase the security level of key relaying in some extent, but it still cannot cover the shortages of only considering the quantities of secret key like reference [15].
In this paper, our contributions are focused on these routing issues in trust-relaying QKD network. We analyze the affecting factors for designing a quality assurance routing method on the trust-relaying QKD network and propose a secret-key-aware routing algorithm to search the optimal routing path. The proposed routing method can forecast the residual local key quantity of each QKD link more accurately when search the routing path, and can make all the links work reasonably to achieve loading balance. Since our works are focused on the trust-relaying QKD network, theQKD networkin the rest of this paper specially refers to thetrust relaying QKD network.
The rest of this paper is organized as follow.Section 2 establishes the QKD network model and gives out some reasonable assumptions for routing design. In section 3, the affecting factors are analyzed and the secret-key-aware routing method is also proposed. The experiments and the evaluation are shown in section 4, and the advantages and effectiveness of the method is also proved. The conclusions are given in section 5.
II. OUTLINE OF THE QKD NETWORK
In this section, the working principle is introduced and the structure of QKD network is analyzed at first. Then a QKD network model based on graph theory is proposed and the models of QKD nodes and QKD links are also given out latter. Simultaneously, some reasonable assumptions are made for our routing method.
2.1 The QKD network model
The QKD network consists of many independent point-to-point QKD systems based on the classical network, and each point-to-point QKD system continuously generate secret key for two adjacent end nodes. In QKD network,although all nodes are connected with each other in the classical network view, quantum channels just exist between some nodes and each node can only establishes neighbor relationship with the nodes directly connected by quantum channels. Figure 1 shows a topology example of 7-nodes QKD network.
Each node has two communication channels: classical channel and quantum channel.The classical channel is a virtual link in classical network, as the dotted line shows in figure 1, and its main work is to transmit the network control information, the encrypted information and so on. The quantum channel is established by the fibers between two adjacent nodes, as the solid line shows in figure 1, and its main work is to generate secret key for each QKD system.
Since the quantum channel is the main concerned target, the QKD network can be represented by an undirected graphG=(V,E),whereVis the vertex set which denotes all the QKD nodes, especially,viis any one of the QKD nodes inV, andEis the edge set which denotes all the QKD links in QKD network, especially,ei,jis any one of the QKD links and represents the quantum channel between nodeviand nodevj.After describing the QKD network structure, it is necessary to clear some concepts related to the QKD network preparing for our following works.
a. Local Key
We call the key generated by point-to-point QKD system thelocal key. In QKD network,each point-to-point QKD system always independently and continuously generates local key for the two end nodes, and the two end nodes respectively set a secret key pool, calledlocal key pool, to store the local key. The local key is the materials to establish secret key for users, so the usable local key stored in each local key pool, which is called residual local key, is very important for QKD network. We useKto denote the local key for conveniently describing in the rest paper and, especially,ki,jdenotes the local key generated by the QKD system consisted of QKD linkei,jand nodesviandvj.
b. Global Key

Fig. 1. Example of a QKD network.
As we know, there may be no quantum channel and can’t generate local key for two long distance end nodes. At this time, these two end nodes can only through relaying to establish sharing key under the help of multiple intermediate nodes. The sharing key established through relaying is calledglobal key, and a certain amount of local key need to be consumed to establish it. The global key is the actually secret key used for users’ secure communications, such as voice, video and file transfer. Therefore, the global key can both exist between long distance nodes or adjacent nodes. If two adjacent nodes need global key for secure communication, the local key shared by them are token as the global key directly, otherwise, they must obtain them by the way of multiple intermediate nodes’ relaying.We useGKto denote the global key, and, especially,gks,ddenote the global key between nodevsandvd,
c. Key Exchange
The process for nodes obtaining global key is calledkey exchange. Assuming thatv1andv7need to obtain global keygk1,7and the selected relaying path is as the arc arrows shown in figure 1, then, the key exchange can be described as follow. The point-to-point QKD system between nodev1andv2generates local keyk1,2, and then nodev2encryptsk1,2byk24,shared withv4. Nodev2transmits the cipher-text tov4. When receiving the cipher-text,v4firstly decrypt it byk24,to obtaink1,2and encryptk1,2byk4,7. Nodev4also transmits the cipher-text tov7. When receiving the cipher-text fromv4,v7decrypts it and obtainsk1,2which is token as the global keygk1,7. All the cryptographic algorithms used during key exchange are OTP cryptographic algorithms, and all the intermedium nodes are trust in physical.
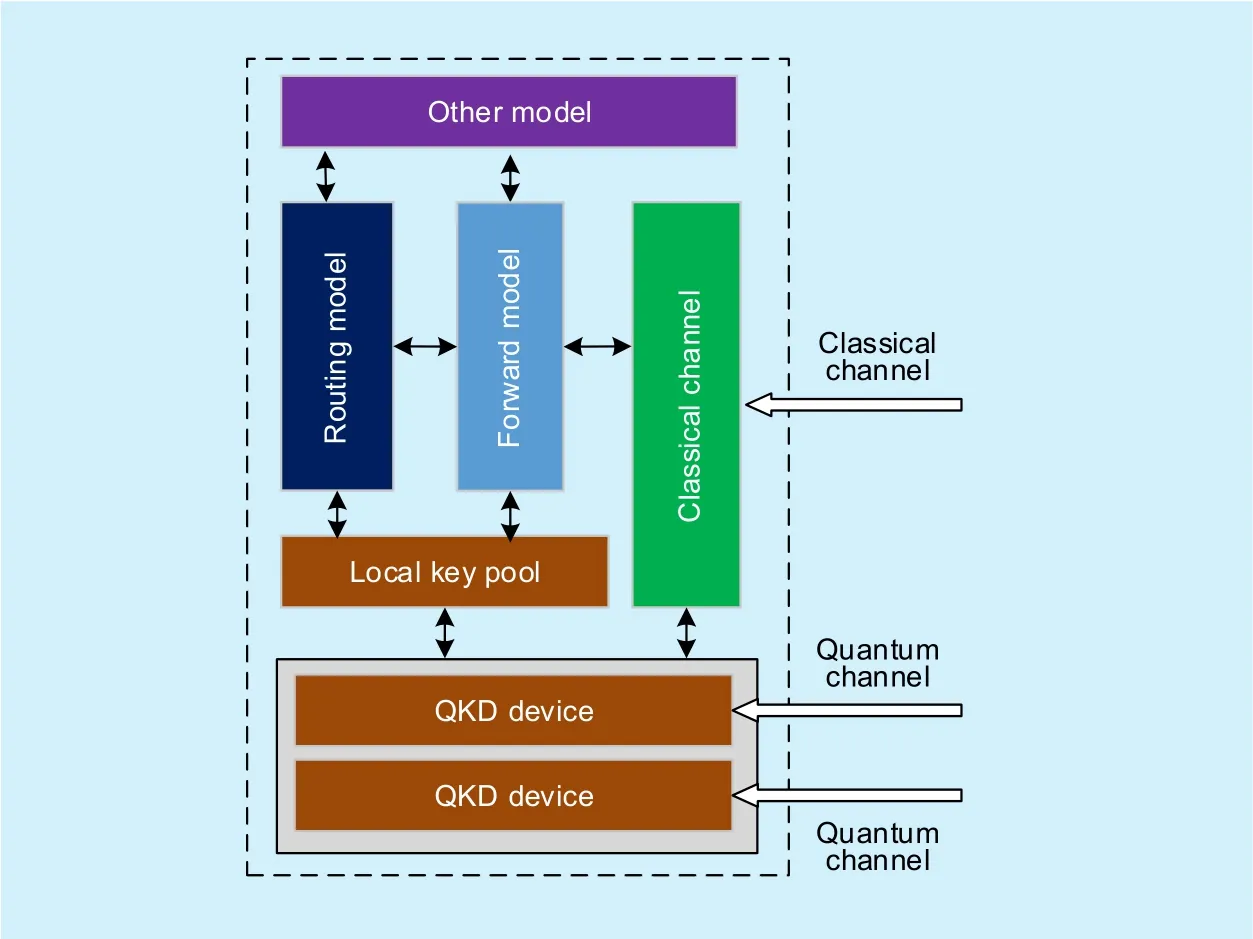
Fig. 2. The structure of QKD node.
d. Relaying Path
When the global keygks,dis exchanged fromvstovd, there are many intermediate QKD linkspassed through, where the set of intermediate QKD linksps,dis calledrelaying path.
2.2 The QKD node model
In this paper, a node structure similar to the QBB node [21] in SECOQC network was adopted in our QKD network. Every QKD node is a computer with multi-QKD device, and it works both as an access point of application and as an intermediate relaying node. Each QKD device in a node is connected to a neighbor node by a QKD link and continuously generates local key. On the other hand, all the nodes are connected to a classical network by classical channels. The QKD node structure is shown as figure 2.
From the view of QKD network structure,each QKD node can be seen as an aggregation of multiple QKD devices. Since the works of QKD devices are generating local key, and each QKD device corresponds to an independent local key pool, therefore, a QKD nodevican be formulated as follow.
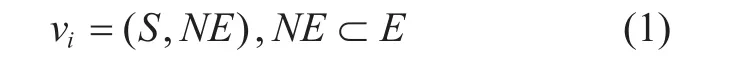
whereNEis the set of edges that connectviand its neighbor nodes, andSis the set of local key pools, especially,sei,jis the local key pool corresponding to the edgeei,jthat connectedviand its neighborvj, and the value ofsei,jindicates the maximum capacity of that local key pool. The maximum capacity of each pool can be different, but the couple of pools corresponding to the same QKD link must be the same.
To get a more complete routing mechanism,we make the following simplifying assumptions for QKD nodes’ some works which is not the research focus in this paper.
Assumption 1:Every QKD node periodically broadcasts the maximum capacity S of all the local key pools within it and the edges NE corresponding to each pool to all the other QKD nodes, and we assume that the period is τ1.
Assumption 2:When the global key gks,d is relaying from node vi to vj,vi will directly get the local key required from the key pool sei,j.If the quantity of residual local key in sei,j is not enough, vi will regard this relaying as a failure relaying and note the source node about this failure.
Under assumption 1, every node can get the topology of the QKD network soon, which is important to the routing mechanism. Actually,there is a queue for each local key pool in a node, but the function of the queue is mainly to solve the problem of processing speed lack in each node. Since the generation rate is related low, and we don’t want the relaying process wait too long in a node, we make the assumption 2 to guarantee the delay of key exchange within an acceptable range.
2.3 The QKD link model
A QKD link is an independent quantum channel and continually generates local key for the two end nodes all the time, but the local key is randomly consumed by key exchange. The generation rate is a very important parameter for a QKD link as well as the consumption rate and the quantity of residual local key corresponding to this link. So a QKD link can be formulated as follow.

whereMis the quantity of residual local key corresponding to linkrespectively are average local key generation rate and average consumption rate ofei,j. These three parameters can be obtained by the two end nodes ofviandvj.
Under assumption 2, only if the residual local keys of all the QKD links within the relaying pathps,dare enough to meet the relaying requirement, the key exchange can be success,which can be formulated as follow.
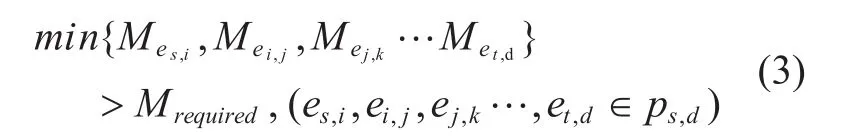
where theMrequiredis the quantity of local key required for each QKD link.
In order to improve the success rate of key exchange, we only search the relaying path within the set of QKD links that satisfies:
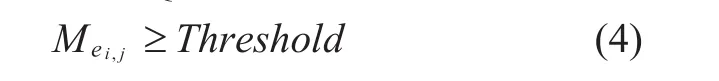
whereThresholdis a threshold of residual local key for each QKD links.
Therefore, it is very important for each QKD node to be aware of the all the residual local key in QKD network to calculate the routing path, so we make the follow assumption according to requirements proposed in[15].
Assumption 3:The quantity of residuallocal key Mei,j,average generation rateand average consumption rateof allQKD links ei,j are broadcasts periodically to all the QKD nodes by the two end nodes of ei,j,and we assume that the period is τ2 and τ2<<τ1.
III. THE PROPOSED ROUTING ALGORITHM
3.1 Problem analysis
The purpose of routing mechanism in QKD network is to find out an optimal relaying path for successful key exchange. In [15], the requirements for the routing protocol on the QKD network were proposed, and a protocol based on OSPF was proposed. Compared with OSPF routing algorithm, the only difference is that the routing algorithm used in [15] took the number of the residual local keys as an additional cost information for each link. Although the chosen relaying path is the optimum path for this key exchange round, it may not be the optimum one for the whole QKD network.The analysis is shown as follow.
As shown in figure 3, there are two possible relaying path fromvstovd, which areThe states of all QKD links are recorded as shown in the figure.We use a certain set of keys, e.g. 1024bit, as the unit of the local key, denoted byunit, then the unit of generation rate and consumption rate can be defined asunit/s.We also assume that there are 9unitglobal keys required to be exchanged. Next, let us look into the follow two scenarios.
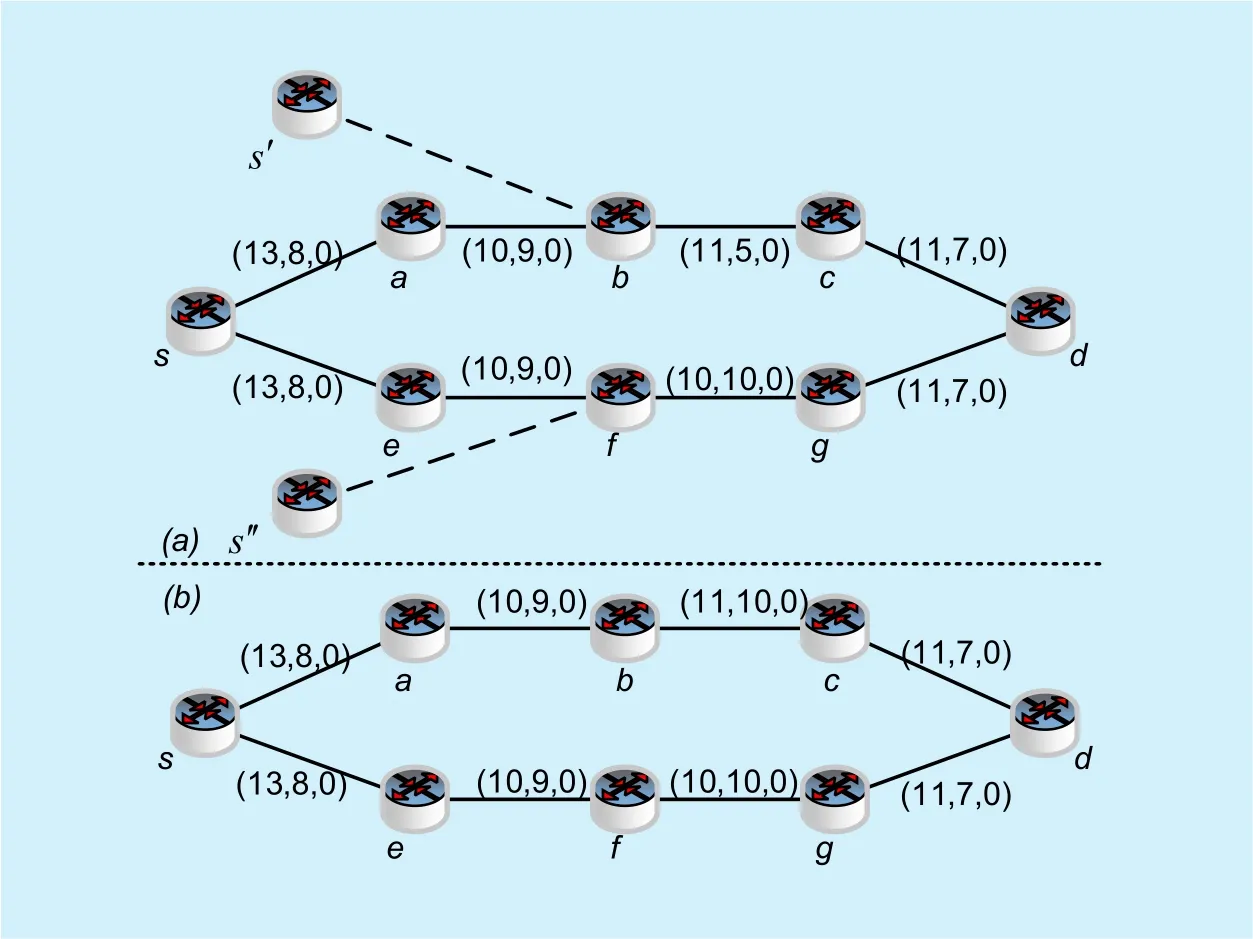
Fig. 3. Example of key exchange scenarios.
Scenario A:As shown in figure 3(a), inthe states of es,a,ea,b andec,d are the same as es,e,ee,f and eg,d respectively, and there are more residual local key of eb,c than ef,g,but the generation rate of eb,c is lower than ef,g.If the key exchangeoccurs at time t1,we can easily find that
is the optimal path according to [15], and the state of eb,c changes to eb,c=(2,5,0)after key exchange. At time t1+1the state of eb,c is eb,c=(7,5,9),and assuming that there are another9unit global keys needed to be exchanged from node vs′to vd just right at this time. Because the residual local key of eb,c is not enough, vs′is forced to wait. However, ifvs chooseas the optimal relaying pathat t1,the local keys consumed in ef,g will resumed very soon. At t1+1,even if there are another9unit global keys needed to be exchanged from node vs′to vd,the residual local keys of ef,g will be still enough. There-fore, the relaying pathis not always theoptimal one from vs to vd in view of the whole network performance.
Scenario B:As shown in figure 3(b), inpath pthe states of es,a,ea,b andec,d are the same as es,e,ee,f and eg,d respectively, and there are more residual local key of eb,c than ef,g,but the generation rate of eb,c is the same as ef,g.For some reasons, the maximum capacities of local key pools in vf and vg are just10unit,which means that the local key pool of ef,g is full, but the capacities of the other QKD links are large enough.Similarly, the pathis select to be theoptimal path according to [15] at t1,and the state of eb,c changes to eb,c=(2,10,0)after key exchange. At t1+1the state of eb,c will be eb,c=(12,10,9),but the state of ef,g will still be ef,g=(10,10,0).If there are another9unit global keys needed to be exchangedfrom node vs to vd at t1+1,the pathtill the optimal one according to [15]. However, since the local key pool of ef,g is full at t1,the local keys generated by ef,g from time t1to t1+1will be abandoned, which is also a waste for the whole QKD network.
Overall, only considering the residual local key when calculates link cost is not enough to improve the performance of the whole QKD network. So a secret-key-aware routing method is proposed in this paper, which considers more factors, e.g. the generation and consumption rate of QKD link and the local key depletion index of each local key pool. Our method can improve the performance of the whole QKD network.
3.2 Estimation of residual local key quantity for QKD link
Because of the generating and consuming,the residual local key quantities of QKD links change all the time, which results that each QKD node is almost impossible to know the residual local key information of all the QKD links immediately. In order to estimate the change tendency of the residual local key more accurately, a dynamic model of the residual local key is proposed in this section.Since QKD nodes update the state of QKD links periodically and the period.isτ2(see assumption 3), we only need to estimate the change tendency within one period cycle.
3.2.1 Local key generation model
As we know, there are many factors, e.g. temperature and physical jitter of the fiber, that affect the generation rate of QKD link, so the generation rate changes all the time. If the generation rate ofei,jisµei,j(t) at timet,then the total generating quantity of local key,denoted byin an update cycle can be formulated as:

Then the average generation rate, denoted byin an update cycle can be formulated as:
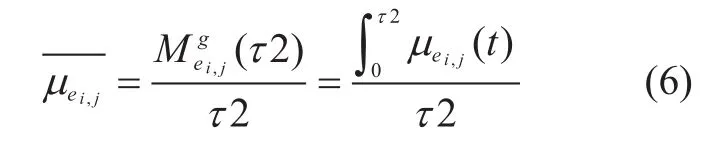
The average generation rate reflects the generation speed ofei,jin a period time, and that is the actually usable parameter to forecast the change tendency of the residual local key.
3.2.2 Local key consumption model
Since the local keys required for key exchange are consumed at once when the process of global key relaying passes through a QKD linkei,j(see assumption 2), the total consuming quantity of local key ofei,j, denoted byin an update cycle can be formulated as:

whereI(t) is an indicator function and is assignedI(t)=1 only when the process of global key relaying passes throughei,j, otherwiseI(t)=0, andR(t) is the local key quantity required for key exchange when the process of global key relaying passes throughei,j.
Then the average consumption rate, denoted byin an update cycle can be formulated as:
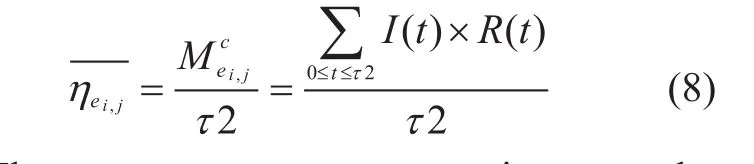
The same as average generation rate, the average consumption rate is also an important usable parameter that reflects the consumption speed ofei,jin a period time. In order to get a more accurate consumption rate, the statistical time interval can be much longer.
3.2.3 Local key quantity dynamic model
When the QKD network working, QKD node can obtains the recent states of all the QKD links by the update message (see assumption 3) before an update cycle starting. Since the quantity of local key is limited by the maximum capacitySei,j, the residual local key ofei,jin an update cycle can be formulated as:
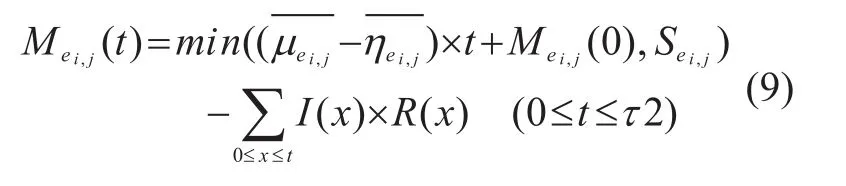
3.3 The cost of QKD link and relaying path
The basic idea of our algorithm is to assign a cost to each link, which is an exponential function in its residual local key and then calculate the shortest path with respect to this metric.To account for the timing relationship between the local key generation and consumption, we also need to measure the effect of previously key exchange. To this end, we define the local key depletion indexλei,j(t) for each local key pool.

The significance ofλei,j(t) lies in providing a normalized priority level for each QKD link according to the empty degree of local key pool, which can prevent wasting local key when the pool is full. As we know the more empty the local key pool is, the lower the priority level is. So from formula (10), we can find thatλei,j(t) is inversely proportional to the priority level ofei,j.
In this paper, the cost metricassociated with each QKD link is give by:

whereSei,jis the maximum capacity of the local key pool corresponding tois the last received average generation rate associated withei,j,λei,j(t) is the local key depletion index ofei,j, andεis an appropriately chosen constants. Althoughλei,j(t) has provided a normalized priority level for each QKD link, it is not so clearly to distinguish the priority levels of some similar QKD links since the range ofλei,j(t) is onlySo we use an exponential function to expand the distinction of priority level for each QKD link. As the larger the value ofεis, the faster the value ofελei,j(t)increases, so we can also adjust the weight of the priority level in the cost function by adjusting the value ofε. In our algorithm,the default value ofεisε=10.
The cost associated with a relaying path can therefore be calculated as:
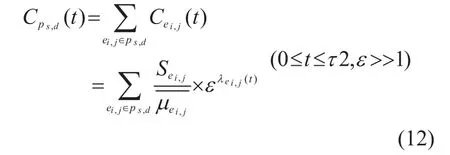
Next, let us look at the link cost metric defined in formula (11), and understand intuitively why our routing algorithm has good performance:
1) Note that the metric in formula (11) for each link is an inversely linear function of the generation rate and an exponential function of the depletion index. So it provides us with a clear guideline of how to balance the importance of residual local key and the generation rate.
2) Consider the condition that the generation rate of each link is variable while the residual local keys for QKD links are constant and similar with each other as well as the maximum capacity of local pool. By using the cost function in formula (11), the network automatically directs the relaying path to the links with a faster generation rate, since these links with high generation rate will advertise a cheaper cost.
3) Note that even thoughSei,jis in the numerator in formula (11), it does not imply that links with larger local key pool capacity are assigned a higher cost. The reason is thatSei,jis also embedded in the exponentialλei,j(t).
3.4 Secret-key-aware routing algorithm
Searching for an optimal relaying pathps,dfromvstovdin the QKD networkG=(V,E)is to find a relaying path with the cheapest cost. The purpose of our proposed algorithm can be described as follow:

where all the links in the path must satisfies formula (4), otherwise,vdwill be marked unreachable.
In order to improve the success rate of key exchange, our algorithm provides not only the optimal relaying path but also some sub-optimal path. The proposed routing algorithm is also based on Dijkstra algorithm [22], and it is described as follow.
The above algorithm can be explained as follow in detail:
Step 1:Pre-process the QKD networkGby the formula (4), cut out all the QKD links that do not satisfies formula (4), then a new networkGcuris obtained.
Step 2: Search for the relaying path with the cheapest cost fromvitovdby Dijkstra algorithm. If successfully finding out this path,record the next hopvnextas well as the cost of the path and then go to step 3, otherwise, go to step 4.
Step 3:Cut out the QKD link fromvitovnext, then a new networkGcur′ is obtained. Letand go back to step 2.
Step 4:Put all the next hop tovdin costincreasing order and then the routing table is obtained.
IV. PERFORMANCE EVALUATION
4.1 Simulation environment
The testing of proposed routing scheme is based on the simulation of QKD network. Figure 4 is the topology of the test QKD network.In this network, there are 55 QKD links and 25 QKD nodes including 7 source/destination nodes which can work both as source and destination node of key exchange, and all the QKD nodes are connected to the same classical network.

Secret-key-aware routing algorithm:At each QKD nodes vi:Pre-process G, obtain Gcur;While(true)Search a cheapest cost relaying path pi,d by Dijkstra algorithm;If (pi,d exist and min ,M Thresholde pei,j> ∈ij id, ,)then record vnext and C t= ′End while Order the next hop in cost- increasing End of algorithmei,j();Else break;Cut out ei,next from Gcur, then obtain Gcur′Let G G cur cur
In order to contrast our method with the method proposed in [15], both of these two methods are test on the same network shown in figure 4 and all the parameters as set as follow. For both of these two methods, the local key generation rate of each QKD link is randomly generated between 10kps to 20kbps and changes once per second, the maximum capacities of the local key pools associated with each QKD link are 1Mb, and the all initial quantities of local key pools are 300Kb. Perhaps the maximum capacity is a little small,but from the following simulation result, it is already suitable. We adoptτ1=30sas the information updating period of QKD nodes in our method, which is the same as the OSPF protocol. And both of these two methods adoptτ2=5s, a much higher frequency than OSPF protocol according to [15], as the state updating period of QKD links. In addition, we assume that the key exchange requests of each source/destination node are produced by a Poisson distribution and the global key quantity of each key exchange is randomly generated between 10kbit to 20kbit. And we also assume that the destination node of each key exchange is randomly set to be one of the source/destination node except the source node.

Fig. 5. The success rate of key exchange.
4.2 Evaluation metrics
Before implementing the simulation, we define the two metrics to evaluate the performance of these two routing methods.
• The success rate of key exchange. This metric is calculated along with the network working. It is a fundamental indicator of a routing method in the sense that it represents the validity and feasibility of a routing method. The higher the value is, the more efficiently the routing method is.
• The residual local key and its distribution of residual local key. This metric measures the distribution of the residual local key of all QKD links. The higher the values of all the QKD links are, the more robust the routing method is. In addition, for a better routing method, the residual local key distributes more uniform and the standard deviation is much smaller.
• The residual local key change tendency of QKD links. This metric is an indicator of the link ability to relaying global key, and it also represents the robustness of a routing method. For a better routing method, the residual local key of most QKD links should keep increasing all the time or stead un-reducing at least.
4.3 Results
Based on the metrics defined above, we mainly measure the values of three aspects: (i) the success rate of key exchange, (ii) the residual local key of all the links and (iii) the change tendency of some randomly choosing links.
4.3.1 The success rate of key exchange
We let every source node record every key exchange and the exchange result all the time. All the records are collected together every 10s to calculate the total success rate of the network during the simulating. Then the change of the key exchange success rate for both routing methods under our simulation environment are obtained. The result is shown as the follow figure.
Figure 5 shows that the key exchange success rates of both methods reduce gradually along with the network working. This result can be explained by the fact that the initial local key of each QKD link is consumed and the key exchange depends on the real time generating local keys gradually. We also find that the success rate of our method is always higher than [15], so we can say that our method performance better than [15] in key exchange success rate.
4.3.2 The distribution of residual secret key After the network working smoothly, we let every QKD node record the residual local key of all the QKD links connected to this node every 10s. At the end of the simulation, the average of residual secret key can be calculated for every QKD link. The average residual secret key for all the QKD links in our simulation are shown as figure 6.
From figure 6 we can see that the residual local key of all the QKD links distribute in various quantities for both methods. For the method in [15], the residual key quantities of many QKD links are very high and nearly full,while the rest QKD links are related very low and even less than 100Kb. On the other hand,for our method, there also are some QKD links with very high quantities of the residual key in the network edge position, but the QKD links with residual local key quantities distributing between 150Kb to 400Kb occupy the majority. This phenomenon can be observed much clearer on the statistical distribution charts of residual key, and they are shown as figure 7.
This result can be explained as follow the fact that the participation frequency (related to the loading balance) of each QKD link is various during key exchange. Obviously, the lower the residual key quantity is, the higher the participation frequency is. So the QKD links participating in key exchange are mainly focus on some of them for the method in[15], while, for our method, all the QKD links participate in key exchange with almost equal opportunity. Therefore, we can say our method performance much better in loading balance.
4.3.3 The residual local key change tendency of QKD links
The best way is to record the residual local key of all the QKD links to observe the residual local key change tendency, however, that would make the result figure very complex and difficult to observe. So we just randomly choose some QKD links and record the residual local key of them to achieve that purpose. In this experiment, the QKD nodes of 8, 14 and 19 are chosen to record the residual local key for the QKD links of 17, 36 and 51 respectively every 10s. The results are shown as follow.
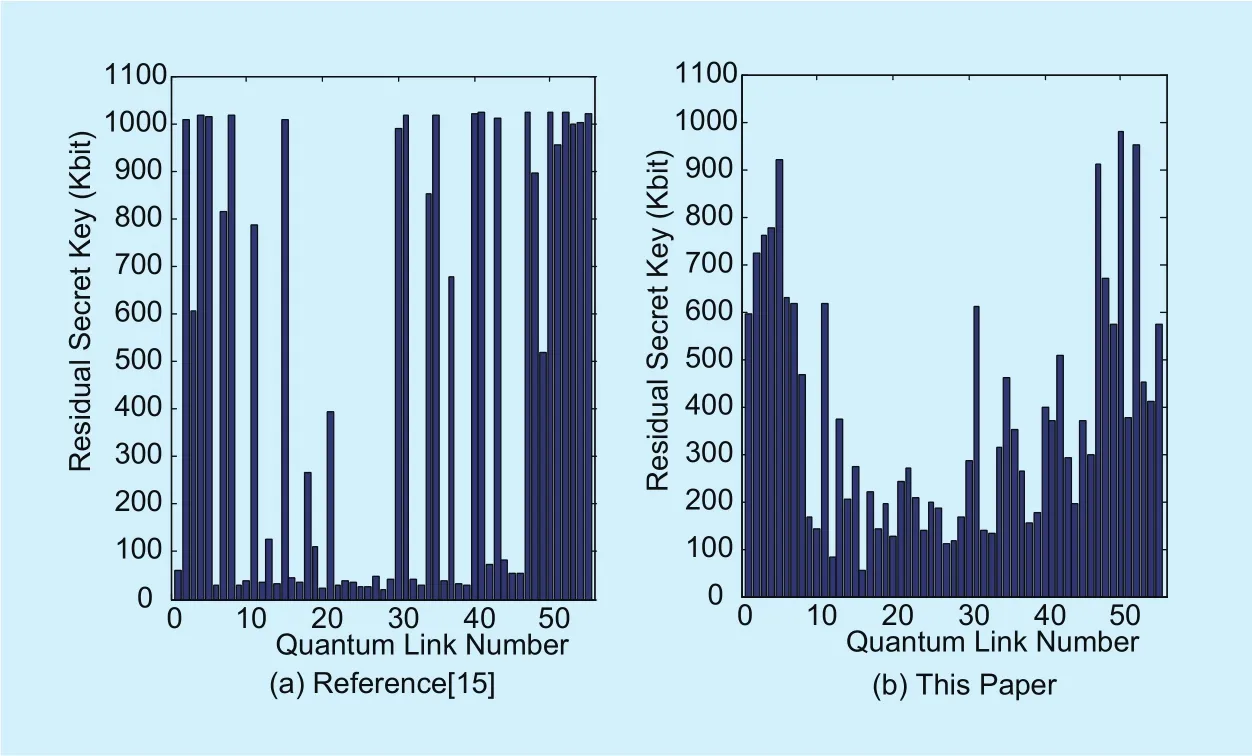
Fig. 6. The average residual local key for all QKD links.
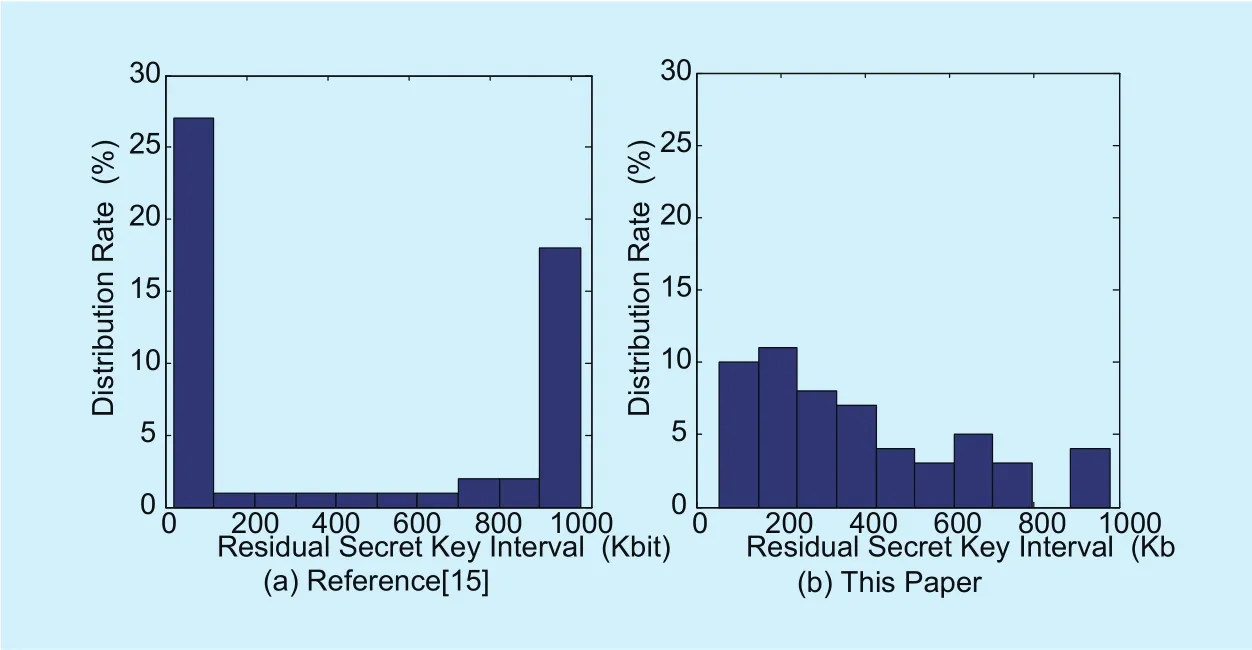
Fig. 7. The statistical distribution of average residual local key.
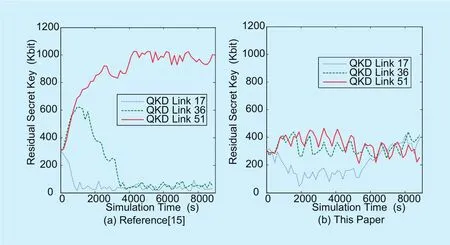
Fig. 8. The change tendency of some QKD links.
Figure 8 shows that the residual local key quantities of all these QKD links change all the time. For the method in [15], different QKD links have different residual local key change tendency, while, for our method, the residual local key quantities of all these QKD links fluctuate upward and downward around a certain quantity respectively. This result indicates that our method can trade off the local key generation and consumption of QKD links.
V. CONCLUSIONS
In this paper we address the routing problem for the trust relaying QKD network. We build the QKD network model as well as the QKD node and link for easily analyzing and understanding this network. Then a secret-keyaware routing algorithm is proposed to search the optimal relaying path. In our algorithm,a dynamic model for the residual local key is proposed to forecast the residual local key quantity of each QKD link more accurately,and the cost of QKD link and relaying path are calculated according to multiple affecting factors, which ensures that our routing method has a good performance. The comparison simulation shows that our routing method can increase the success rate of key exchange, make all the QKD links participate key exchange with almost equal opportunity to achieve load balance and trade off the local key generation and consumption of each QKD link. Therefore, the proposed method can contribute to effectively improve the network overall performance. However, the secret key consumption in the proposed scheme is not analyzed quantitatively and the traffic flow requested in classical network is also not taken into consideration. We intend to research them with a quantitative measure in future work.
[1] C.H. Bennett, G. Brassard. “Quantum Cryptography: Public Key Distribution and Coin Tossing”,Proceedings of the IEEE International Conference on Computers, Systems, and Signal Processing,pp. 175-179, Bangalore, India, 1984.
[2] W. Ping, G. Chen, K. Pham, et al.. “Quantum key distribution for security guarantees over QoS-driven 3D satellite networks”,SPIE Defense& Security, Vol. 9085, no. 18, pp. 5450-5453,2014.
[3] S. Wang, et al. “2 GHz Clock Quantum Key Distribution over 260 km of Standard Telecom Fiber”,Optics Letters, Vol. 37, no. 6, pp. 1008-1010, 2012.
[4] A. J. Shields, A. R. Dixon, et al. “Gigahertz Decoy Quantum Key Distribution with 1 Mbit/s Secure Key Rate”,Optics Express, Vol. 16, no. 23, pp.18790-18797, 2008.
[5] H. Jiajia, S. H. Sun, and L. M. Liang. “A Three-Node QKD Network Based on a Two-Way QKD System”.Chinese Physics Letters, Vol. 28, no. 4,pp. 40303-40305, 2011.
[6] P. Toliver, R. J. Runser, T. E. Chapuran, et.al.“Experimental investigation of quantum key distribution through transparent optical switch elements”.IEEE Photonics Technology Letters,Vol. 15, no. 11, pp. 1669-1671, 2003.
[7] N. Lütkenhausc, R. Romain, et al. “Quantum key distribution and cryptography: a survey”.Dagstuhl Seminar Proceedings, 2010.
[8] S.Wang, W. Chen, et al. “Field test of wavelength-saving quantum key distribution network”,Optics Letters, Vol. 35, no. 14, pp. 2454-2456, 2010.
[9] C. Z. Peng, H. Liang, J. Wang, et al. “Metropolitan all-pass and inter-city quantum communication network”.Optics Express, Vol. 18, no. 26, pp.27217-27225, 2010.
[10] R. Alléaume, et al. “Topological optimization of quantum key distribution networks”.New Journal of Physics, Vol. 11, no. 7, pp. 075002-075027, 2009.
[11] C. Elliott. “The DARPA Quantum Network”,arX-iv:quant-ph/0412029, 2005.
[12] C. Elliott, A. Colvin, D. Pearson, O. Pikalo, J.Schlafer, and H. Yeh, “Current status of the DARPA Quantum Network”,SPIE - The International Society for Optical Engineering, Vol. 5815, no. 1,pp. 138-149, March, 2005.
[13] M. Peev, T. Lorünser, et al. “The SECOQC Quantum Key Distribution Network in Vienna”,New Journal of Physics, Vol. 11, no. 11, pp. 075001-075037 2009.
[14] M. Fujiwara, H. Ishizuka, S. Miki, T. Yamashita, Z.Wang, et al. “Field test of quantum key distribution in the Tokyo QKD Network”,Optics Express,Vol. 19, no. 11, pp. 10387-10409, 2011.
[15] Y. Tanizawa, R. Takahashi and A. R. Dixon. “A routing method designed for a Quantum Key Distribution network”,Eighth International Conference on Ubiquitous and Future Networks IEEE,pp.208-214 2016.
[16] S. Rass, M. A. Sfaxi, S. Ghernaoutihlie, K. Kyamakya. “Secure Message Relay over Networks with QKD-Links”,International Conference on Quantum IEEE Computer Society, pp. 10-15,2008.
[17] Q. Han, et al. “A novel QKD network routing algorithm based on optical-path-switching”,Journal of Information Hiding & Multimedia Signal Processing, Vol. 5, no. 1, pp. 13-19, 2014.
[18] J. Moy, “OSPF Version 2”,RFC2328 IETF,Apr.1998.
[19] M. Dianati, R. Alléaume, M. Gagnaire, X. Shen.“Architecture and protocols of the future European quantum key distribution network”,Security & Communication Networks, Vol. 1, no. 1,pp. 57-74, 2008.
[20] M. Li, D. Quan, C. Zhu. “Stochastic routing in quantum cryptography communication network based on cognitive resources”,International Conference on Wireless Communications& Signal Processing IEEE, pp. 1-4, 2016.
[21] O. Maurhart. “QKD networks based on Q3P. Applied Quantum Cryptography”,Springer Berlin Heidelberg, pp. 151-171, 2010.
[22] E. W. Dijkstra. “A note on two problems in connexion with graphs”,Numerische Mathematik,Vol. 1, no. 1, pp. 269-271, 1959.
- China Communications的其它文章
- CYBERSPACE SECURITY: FOR A BETTER LIFE AND WORK
- A Cloud-Assisted Malware Detection and Suppression Framework for Wireless Multimedia System in IoT Based on Dynamic Differential Game
- An Integration Testing Framework and Evaluation Metric for Vulnerability Mining Methods
- Powermitter: Data Exfiltration from Air-Gapped Computer through Switching Power Supply
- CAPT: Context-Aware Provenance Tracing for Attack Investigation
- Decentralized Attribute-Based Encryption and Data Sharing Scheme in Cloud Storage

