A Learning Evasive Email-Based P2P-Like Botnet
Zhi Wang, Meilin Qin, Mengqi Chen, Chunfu Jia,,*, Yong Ma College of Computer and Control Engineering, Nankai University, Tianjin 0050, China Information Security Evaluation Center of Civil Aviation, Civil Aviation University of China, Tianjin 0000, China Key Lab. on High Trusted Information System in Hebei Province, Baoding 0700, China
I. INTRODUCTION
Botnet is a network of compromised computers, known as bots or zombies, that could be instructed by a controller in the Internet, socalled botmaster. Currently, botnet is one of the most significant threats to the Internet.Nowadays, the botnet keeps evolving which is composed by not only compromised computers, but also a large variety of IoT devices,including smart phones, IP cameras, routers,printers, DVRs and so on. With enormous cumulative bandwidth and computing capability,botnet is the most important and powerful tool available for cheaper and faster deployment of malware across the Internet, and easier and broader scale attacks for non-professional attackers with relatively little to no experience.
Compare to other Internet malware, the unique feature of botnet lies in its command and control (C&C) channel that connects botmaster to each bot. Most botnet C&C channels are built on the IRC or HTTP or P2P network communication protocol. The botnet C&C network traffic is different from benign traffic,such as the bad reputation of C&C server, the suspicious communication volume, regular beaconing, and so on.
Nowadays, machine learning is widely used in botnet detection system as a core component [3][4][5], that makes considerable effort in identifying the established C&C channels.After supervised or non-supervised training,botnet detection models could be automatically generated. Most known machine learning algorithms have been used in botnet detection,such as SVM, hierarchical clustering, random forest, k-means, decision tree, graph-based learning, and so on. And the published experiment results have excellent detection precision and recall on their testing datasets.
However, there is no 100% security on the Internet. With financial motivation, botnet is always evolving to avoid detection. As reported by Lastline [27], over 70% of the advanced malware created today uses one or more evasion techniques to avoid detection. Email protocol is a potential stealthy and robust botnet C&C channel. Email communication uses a P2P-like manner that sends message from sender to receiver by the relay of email servers who has excellent reputation, such as Gmail servers, Hotmail servers and so on. In this paper, we demonstrate the nature of an emailbased P2P-like botnet with the following features:
• Besides the traditional IRC, HTTP and P2P communication channels, email is a new stealthy and robust C&C channel for botnet.
• Email protocols, such as POP3, SMTP,IMAP, are not blocked by firewall, and in the Internet the email volume is very huge.
• Email servers have excellent reputation and use dynamic IP address for different connections.
• Without considering the limitation of private IP address, bots can send and receive emails to each other through email servers.
Our contributions are the following:
• We present the construction of an emailbased P2P-like botnet by means of a prototype, and release the implementation of prototype as open source to help researchers and security community be well prepared and develop effective defenses.
• A secure C&C communication is proposed that only botmaster can generate botnet commands preventing botnet takeover, and each command is unique that can be used only once.
• We evaluate the resilience of email-based P2P-like botnet against machine learning based botnet detection approaches that select reputation, traffic volume and time-related beaconing activities as features. The conformal evaluation results show that such feature selection is hard to give a high credibility and confidence prediction.
• We discuss possible defenses against emailbased P2P-like botnet.
The remainder of the paper is organized as follows. Section 2 gives the related works.Construction of email-based P2P-like botnet is discussed in details in section 3. Section 4 introduces the botnet C&C mechanism. In section 5, we evaluate the resilience to machine learning using conformal evaluation. Section 6 discusses possible countermeasures against email-based P2P-like botnet. We conclude this paper in section 7.
II. RELATED WORKS
Nowadays, machine learning is widely accepted in C&C detection system as a core component. With financial motivation, attackers keep evolving their evasion techniques. Attackers need to understand the detection mechanism by collecting the knowledge of detection approaches as much as possible, such as the target C&C protocol, training dataset, selected feature set, underlying machine learning algorithm, retraining mechanism and so on. Figure 1 shows the levels of attacker’s knowledge and the corresponding concept drift attacks,which is motivated by the work [6].
2.1 New C&C mechanism
Botnet attackers have begun to exploit many stealthy C&C channels, such as social network [7][8], email protocol [9], SMS [10] and bluetooth [11]. Erhanet al.[7] proposed social network based botnet to abuse trusted popular websites, such as twitter.com, as C&C server.Kapilet al.[9] evaluate the viability of using harmless-looking emails to delivery botnet C&C message. Social network traffic and email traffic are beyond the data collection scope of current machine learning based methods, which causes the lack of effective miti-gation strategies. What makes new protocols interesting is the introduced trusted and popular websites or email servers. First, trusted websites or email servers have very good reputation and usually are listed on the white list that all traffic to such website or server will not be monitored by botnet detection methods.Second, the trusted websites or email services are very popular and have very heavy usage volume that the light-weight occasional C&C traffic is unlikely to be noticed. However, the new botnets use the centralized architecture that all bots communicate with C&C server directly. The central C&C server is a potential single point of failure that if the C&C server is exposed to the defender, the botnet is easy to be dismantled.
2.2 Mimicry attack
Mimicry attack refers to the techniques that mimic benign behaviors reduce the differentiation between the malicious events and benign events. Wagner and Soto [12] demonstrated the mimicry attack against a host-based IDS that mimicked the legitimate sequence of system calls. Srndic and Laskov [6] presented a mimicry attack against PDFRate [13], a system to detect malicious pdf files based on the random forest classifier.
2.3 Gradient descent attack
The gradient descent is an optimization process to iteratively minimize the distance between malicious points and benign points.Srndic and Laskov [6] applied a gradient descent-kernel density estimation attack against the PDFRate system that uses SVM and random forest classifier. Biggioet al.[14] demonstrated a gradient descent component against the SVM classifier and a neural network.
2.4 Poisoning attack
Poisoning attacks work by introducing random noise or carefully crafted noise into the training data. Biggioet al.[15] proposed poisoning attacks to merge the benign and malicious clusters that make detection system unusable.
2.5 Email-based attacks
By exploiting the weakness found in humans and technique approaches, email-based attacks is becoming one of the most effective tools for attackers, such as email SPAM [16], email phishing [17][18], email masquerade attacks[19], and email botnet [9]. Using natural language processing and machine learning techniques, [18] proposed a scheme to detect malicious domains from mailing list that is earlier than traditional detection. [19] introduced a scalable email masquerade attacks using natural language generation to automatically compose spoof emails. The fake emails have the same writing style and context with previous conversations found in the compromised email account. The harmless-looking emails can also be used to carry botnet C&C message, [9]evaluated the feasibility of email-based botnet that hides C&C message in spam sent to the compromised email account.
III. EMAIL-BASED P2P-LIKE BOTNET CONSTRUCTION
How to compromise new bot candidates through all possible methods is not the focus of this paper. In this section, we present the detailed design of the botnet architecture and the recruitment process.
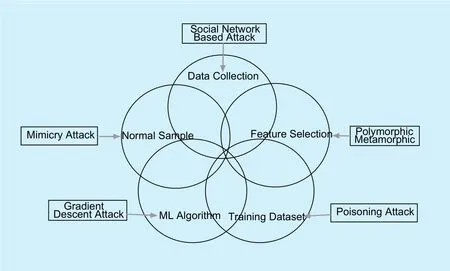
Fig. 1. Attack methods against machine learning based on different knowledge level.
3.1 Email communication
In this subsection, we will present the detailed email communication process about the most commonly used Email protocols on the Internet - POP3, IMAP and SMTP, whose default ports are listed on the Table 1. Each one of them has specic function and way of work.
POP3 and IMAP are the two most commonly used Internet mail protocols for retrieving emails. POP3 creates local copies of email and delete the originals from the email server,while IMAP keeps emails on remote email server until the user deletes them. Both protocols are supported by all modern email clients and web servers. IMAP is more suitable for reading email from different locations. We select IMAP to receive C&C emails in the email botnet. SMTP is the standard protocol for sending emails across the Internet.
Figure 2 shows the email communication process. Before sending or receiving emails,local host has to query DNS server to resolve a domain name to an IPv4 address or an IPv6 address. For loading balance of large amount of sending and receiving email requests, most email service providers would register multiple IP addresses for one domain name on DNS server. Even if using the same email account at different times, the IP address of email server is likely to be different. The IP-based time series patterns, such as the connection frequency to a destination IP address, are useless for detecting email-based botnets.
Usually, email service providers offer safe channel for users, such as Gmail, that it is impossible to intercept the contents of a secure email. And most commercial email servers have excellent reputation, that email-base botnet can avoid traditional reputation-based detection algorithm. Even the botnet is found,it is not a good choice to destroy the botnet by shutting down the email server because there are a large number of benign email accounts.Overall, email channel is an excellent candidate to build stealthy and robust botnet.

Table I. Email protocols.
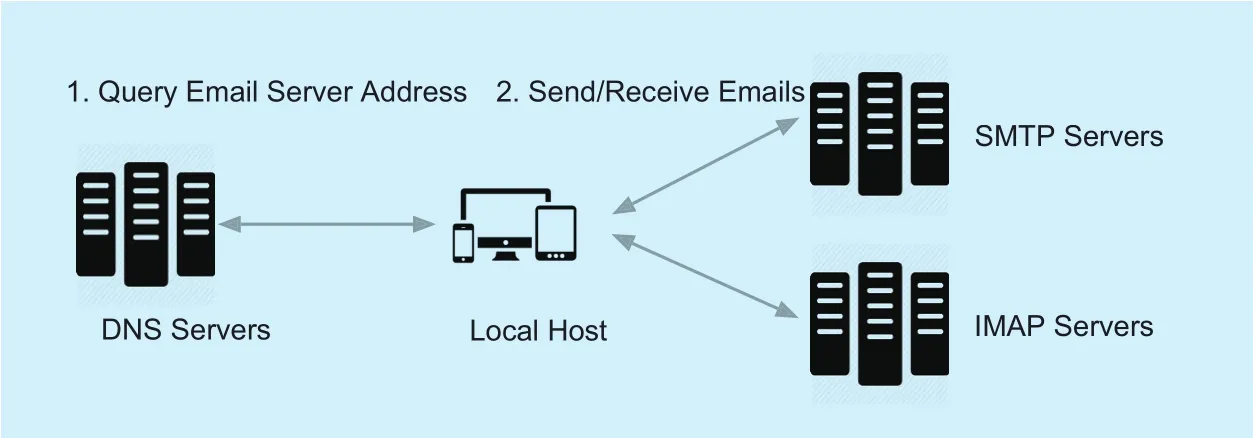
Fig. 2. The email communication process.
3.2 Botnet architecture
Taking into account the selection of bot candidates, P2P botnet can be classied into three categories: parasite P2P botnet, leeching P2P botnet and bot-only P2P botnet.
In the parasite P2P architecture, all bot candidates are chosen from the same existing P2P network. For leeching P2P botnet, botmaster could recruit vulnerable hosts throughout the entire Internet, butnally they will participate in and depend on an existing P2P network. In bot-only P2P botnet, all peers are bots without benign hosts, and the whole botnet resides in an independent network. In this paper, we select bot-only P2P architecture to build email P2P-like botnet without benign peers that is fl exible to scale.
3.3 Botnet construction
Unlike traditional botnets, the email-based P2P-like botnet does not require a bootstrap program. The network connectivity of botnet is only determined by the peer list in each bot.In this way, the email-based botnet gets over the bootstrap vulnerability.
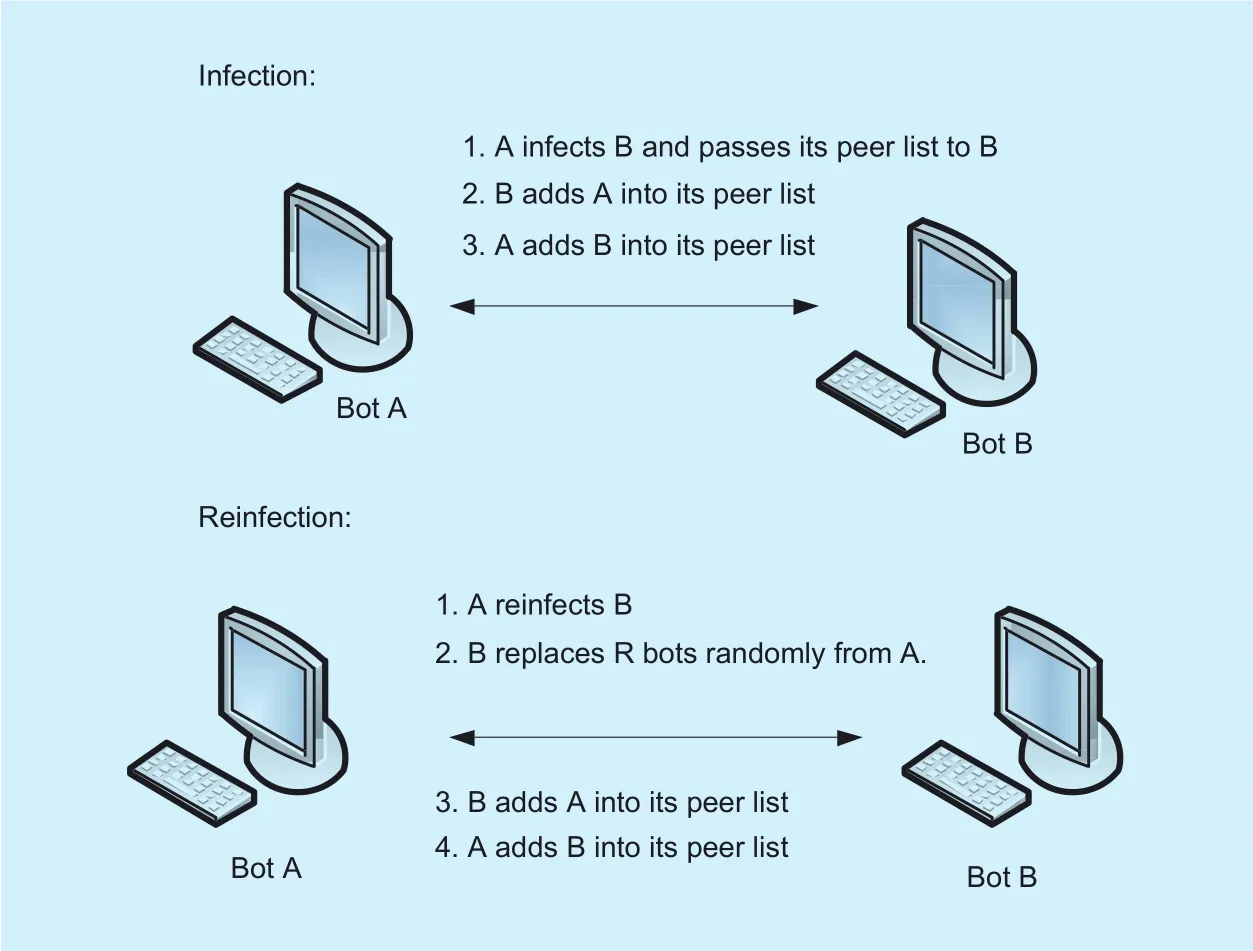
Ping Wanget al.[20] utilize the new infection and reinfection mechanism to propagate botnet. In this paper, we employ the similar way to build peer lists. Here, we assume that the size of peer list in each bot is congured to beM. When bot A compromises a vulnerable host B, A passes its own peer list to this newly infected host B, and B will add A into this peer list. Any two bots that have found each other will exchange their peer lists to construct new lists. If bot A reinfects bot B, bot B will then replaceR(R<M) randomly selected entries in its peer list withRentries in bot A peer list.And bot A and B will add each other into their peer lists.
Figure 3 shows the process of the botnet construction. The reinfection procedure can effectively interconnect different infection paths together, making a botnet connected evenly and randomly. With random and dynamic architecture, the email-based botnet would be more robust to botnet takedown.
IV. COMMAND AND CONTROL MECHANISM
The botnet is the main platform for carrying out large scale cybercrimes. The core of a botnet is its C&C mechanism which includes 3 components: master, channel and bots as shown in Figure 4. More and more defenders focus on detecting the C&C communication,trying to cut off the C&C channel and shut down the botnet. To design a complete botnet C&C mechanism, a stealthy and robust channel must be built between the botmaster and all compromised bots, through which the botmaster can send commands to effectively control all bots. In this paper, we hide C&C communication in plain email sigh to decrease the risk of detecting master, channel and bots.
4.1 Hide C&C channel
To make the C&C channels become robust,there are many evading techniques such as fastflux and domainflux[21] . With fastflux,the bots would query a certain domain that is mapped onto a set of IP addresses that change frequently. However, fast flux uses only one single domain name, which will lead to a single point of failure. In domain flux,the botmaster associates one or more IP with several domains to avoid being easily blocked by blacklisting. Although the fast flux and domain fl ux techniques can hide botnet C&C server behind a set of IP addresses or randomly generated domain names, the defenders can also identify the botnets through DNS traffic analysis.
Fi g. 3. Botnet construction process.
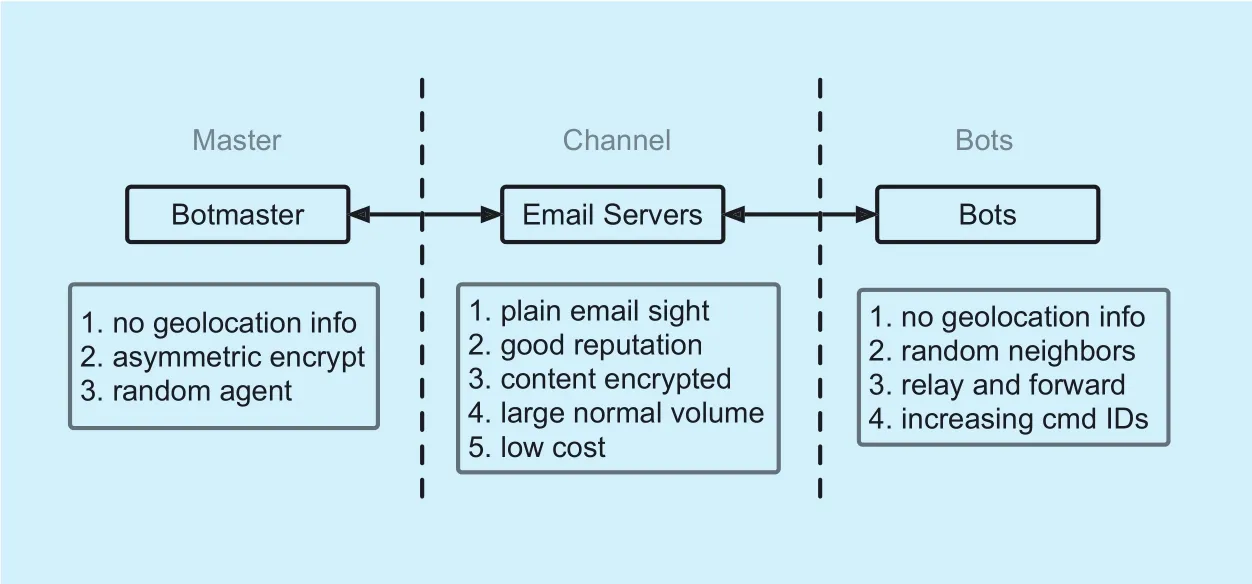
Fig. 4. Botnet command and control mechanism including 3 components: master,channel and bots.
In this paper, we hide botnet C&C channel in the plain email sight. Besides the traditional IRC, HTTP and P2P communication channels,email is a new stealthy and robust C&C channel for botnet. Email protocols, such as POP3,SMTP, IMAP, are not blocked by firewall.Commonly, botnet use the newly registered IP addresses or domains which have poor reputation, and the communication to new IP or domain is suspicious which will draw more attentions. Email servers have excellent reputation, and in the Internet the email volume is very huge, so that the botnet C&C behavior is more likely to get lost in the normal email crowd. Without considering the limitation of private IP address, email botnet can send and receive emails to each other through email servers. Comparing to the cost of registering a public IP address or a domain, the cost of registering an email account is much less.And email accounts reveal less geolocation information of master and bots than public IP addresses and domain. Currently, most email service providers offer safe channel for their users, so it is very hard for defenders to master the contents of a captured email by only analyzing its traffic. In addition to computers, as long as the compromised host can run python scripts, we can add it to our botnet, including IoT devices, smart phones and tablets.
The traditional C&C channels can be categorized as pull and push manners. In the pull manner, bots retrieve commands actively from a place where botmaster publish commands,while the push manner means bots passively wait for commands to come. Both pull and push manners are one-way command transmission that are different from commonly used normal network communication channels and are very prone to be found. The email channel is bidirectional. Bots can periodically connect to email servers to check and receive new commands in the pull manner, then reply to the command with response or forward the command to its neighbors in the push manner.All commands are relayed by email servers in the email channel. And all botnet C&C behaviors follow the commonly used email manner,including send, receive, reply and forward functions, which mimic email usage behavior of a normal human user.
4.2 Fortify master and bots
In order to mitigate takeover challenge, we introduce asymmetric cryptography to prevent disguised commands. Botmaster could use a secret private key to encrypt commands and send it to bots by email channel, while bots keep a public key they can use to decrypt commands from emails. The private key which is used to encrypt commands is stored in the botmaster computer, and only botmaster have access to it. Even if the defenders get the detailed information about a bot using honeypot,they still cannot fabricate commands to take over the entire botnet.
Another challenge for botnet is the replay attack. Replay attack is often used to find compromised hosts by defenders that resend the command emails to all hosts and recognize compromised hosts who response the command. In this paper, each command issued by botmaster has a unique command id. When a bot received a command, it will check if it is a new command or not by command id to prevent command loop and replay attack. To simplify the process of checking new command id, we introduce an automatically increasing command id issued by botmaster that each bot just needs to remember the maximum id ever seen. When a bot receives a command, whose id is larger than the maximum one ever seen,it will perform activities according to the new command and update the stored maximum id. Otherwise, bot will discard the command email.
Before the issue of new command, the botmaster randomly chooses one of the compromised hosts as an agent. The botmaster only send commands to the randomly selected agent, and the agent adds its email address into the command email and forwards the command email to its peer list. Each bot received the new command email will further distribute the command to its neighbors. All the command response emails from normal peers will be sent back to the agent, and the agent will relay the response to the botmaster.Therefore, only randomly selected agent can communicate with botmaster that is resilient to disruption.
V. EVALUATION
In this section, we are going to evaluate the evasion ability of email-based P2P-like botnet against machine learning based botnet detectors.
We mimic normal email communication and develop prototype email-based P2P-like botnet. In the experiment, we introduce the dynamic sleep time to control the time interval and duration that make C&C trafc more similar to the normal email traffic generated by email clients, such as Microsoft Outlook,Mozilla Thunderbird and Apple Mail.
The benign email netfl ow data are collected from a local ISP for 15 days, and the C&C email trafc are generated from our prototype botnet. For privacy concerns, our evaluation dataset only contains netflows information without detailed packet content. The malicious dataset consists of 400,000 netflows, and the benign email dataset contains 1000,000 netfl ows.
From netflows, we first extracted the following features, as shown in Table 2.
Second, we need to carry out data processing. All the features must be normalized before analyzing. There are a lot of different methods for data normalization. Here, we use Min-Max scaling method.
5.1 Assessment
To assess the stealthy of email-based P2P-like botnet, we select unsupervised clustering algorithm DBSCAN [22] and dimension reduction algorithm tSNE [23] and conformal clustering[24] to see the similarity between malicious dataset and benign dataset at volume features and time-related features.
The DBSCAN is a density-based clustering algorithm: given a set of points in some space, it groups together points that are closely packed together, marking as outliers that lie alone in low-density regions. Figure 5 is the DBSCAN clustering result. All the points included bot and normal are mixed together and then use DBSCAN to do clustering. The result is that only one cluster is found, which indicates malicious email data are indistinguishable from the begin data.
The tSNE is a kind of reduced dimension visualization algorithm, which maps the multi-dimensional features to two or three dimensions. The goal of tSNE is to make the distance similar to the elements on the low dimension remain close to each other. Figure 6 shows the relationship of malicious and benign data in 2 dimensions. The malicious bot points are superimposed over the benign ones that malicious and benign data interfere with each other a lot.

Tab le II. Feature selection.

F ig. 5. DBSCAN clustering result on the mixed malicious and benign data.
Conformal clustering is a clustering technique based on conformal prediction [25].Unlike traditional clustering methods, this technique allows to control the number of objects that are left outside of any cluster by setting up a required condence level. Figure 7 visualizes the clustering results of various signicant levels for the KNN non-conformal measure in the tSNE space, that indicates the malicious trafc are mixed with normal trafc together at different signicant levels.

Fi g. 6. tSNE result on the mixed malicious and benign data.

Fig. 7. P-values distribution and signicant levels of malicious and benign data.
VI. DISCUSSION
Nowadays, machine learning is widely used in malware detection system as a core component. The machine learning algorithm is designed under the assumption that all datasets follow the same underlying data distribution.But the real-world malware data distribution is not stable and changes with time. Arce [26]pointed out that machine learning itself could be the weakest link in the security chain. By exploiting the knowledge of the machine learning algorithm, many well-crafted evasion approaches have been proposed.
In this paper, we proposed the novel stealthy and robust botnet C&C channel to evade machine learning detection approaches. The experiment results show horizontal correlation learning algorithm is difficult to separate malicious email traffic from normal email trafc based on the volume features and time-related features.
Although botnet C&C channel and architecture is changed, all peers share the same life cycle and present similar malicious behaviors.Vertical correlation algorithm is good at cluster similar peer behaviors under the same life cycle. To increase evasion resilience, multiple vertical and horizontal correlation algorithms can be composed together that increase the detection method diversity and cover more different underlying malware data distribution.
In the future, we will focus on integrating more diverse machine learning algorithms such as vertical and horizontal correlation algorithms, and the online model quality assessment approach to recognize model aging and data concept drift and update model to consist with latest data.
VII. CONCLUSION
Building machine learning models of malware behaviors is widely used as a panacea towards effective, scalable, and automatic malware detection. Attackers keep learning the latest machine learning based detection systems and evolving evasion techniques to generate new sustainable variants. Concept drift is the well-known vulnerability of machine learning which is exploited by attackers to launch well-crafted concept drift attacks artificially,such as mimicry attacks, gradient descent attacks and poisoning attacks.
Researchers have started to pay attention to new botnets using different evasion techniques. In this paper, we demonstrate a novel stealthy and robust botnet. We explore the nature of email-based P2P-like botnet, analyzing the construction and C&C mechanism, evaluating the evasion ability against horizontal correlation algorithm, and discussing malware data concept drift and possible defense strategies.
We hope to shed light on email-based P2P-like botnets, and help researchers and security community be well prepared and develop effective defenses against this novel botnet attacks.
ACKNOWLEDGEMENTS
The authors acknowledge the National Key Basic Research Program of China (Grant:2013CB834204), the National Natural Science Foundation of China (Grant: 61300242,61772291), the Tianjin Research Program of Application Foundation and Advanced Technology (Grant: 15JCQNJC41500, 17JCZDJC30500), the Open Project Foundation of Information Security Evaluation Center of Civil Aviation, Civil Aviation University of China(Grant: CAAC-ISECCA- 201701, CAAC-ISECCA-201702)
Reference
[1] M. Antonakakis, T. April, M. Bailey, et al., “Understanding the mirai botnet,”Proc. the 26th USENIX Security Symposium (USENIX Security 17), 2017, pp. 1093-1110.
[2] Y. Ye, T. Li, D. Adjeroh, et al. ,”A survey on malware detection using data mining techniques,”Proc. ACM Comput. Surv., vol. 50, no. 41, 2017,pp. 1–40.
[3] M. Demontis, B. Melis, D. Biggio, et al., “Yes,Machine Learning Can Be More Secure! A Case Study on Android Malware Detection,”IEEE Trans. Dependable and Secure Computing, vol.PP, no. 99, 2017, pp. 1-1.
[4] S. Garca, M. Grill, J. Stiborek, et al., “An Empirical Comparison of Botnet Detection Methods.”Computers and Security, vol. 45, no. 45, 2014,pp. 45:100-123.
[5] S. Garca, A. Zunino, M. Campo, “Survey on Network-based Botnet Detection Methods,”Security and Communication Networks, vol. 7, no. 5,2014, pp. 7:878-903.
[6] N. Sendic, P. Laskov, “Practical Evasion of a Learning-based Classier: A Case Study,”Proc.the 35th IEEE Symposium on Security and Privacy (S&P), 2014, pp. 197-211.
[7] E. Kartaltepe, J. Morales, S. Xu, et al., “Social Network- based Botnet Command-and-Control:Emerging Threats and Counter-measures,”Proc.the Applied Cryptography and Network Security International Conference, 2010, pp. 511–528.
[8] T. Yin, Y. Zhang, S. Li, “Drsnbot: A Social Network-based Botnet with Strong Destroy-resistance,”Proc. the IEEE International Conference on Networking, Architecture, and Storage, 2014,pp. 191–199.
[9] K. Singh, A. Srivastava, J. Giffin, et al., “Evaluating Emails Feasibility for Botnet Command and Control,”Proc. the IEEE International Conference on Dependable Systems and Networks with Ftcs and DCC, 2008, pp. 376–385.
[10] Y. Zeng,G. Shink, X. Hu, “Design of SMS Commanded-and-controlled and P2P-structured Mobile Botnets,”Proc. the Fifth ACM Conference on Security and Privacy in Wireless and Mobile Networks, WISEC ’12, 2012, pp. 137–148.
[11] K. Singh, S. Sangl, N. Jain, et al., “Evaluating Bluetooth as a Medium for Botnet Command and Control,”Proc. the 7th International Conference on Detection of Intrusions and Malware,and Vulnerability Assessment, 2010, pp. 61–80.
[12] D. Wagner, P. Soto, “Mimicry Attacks on Hostbased Intrusion Detection Systems,”Proc. the 9th ACM Conference on Computer and Communications Security, CCS ’02,2002, pp. 255–264.
[13] C. Smutz, A. Stavrou, “Malicious PDF Detection Using Metadata and Structural Features,”Proc.the 28th Annual Computer Security Applications Conference,2012, pp. 239–248.
[14] B. Biggio, I. Pillai, S. Rotabulo, et al., “Is Data Clustering in Adversarial Settings Secure?,”Proc.the 2013 ACM Workshop on Artificial Intelligence and Security, AISec ’13, (New York, NY,USA), pp. 87–98, ACM, 2013.
[15] B. Biggio, K. Rieck, D. Ariu, et al., “ Poisoning Behavioral Malware Clustering,”Proc. the 2014 Workshop on Artificial Intelligent and Security Workshop, AISec ’14, 2014, pp. 27–36.
[16] PA. Chirita, J. Diederich, W. Nejdl, “Using Ranking for SPAM Detection”Proc. the 14th ACM International Conference on Information and Knowledge Management,CIKM ’05, 2005, pp.373–380.
[17] M. Khonji, Y. IRAQI, A. Jones, “Phishing Detection: A Literature Survey”IEEE Communications Surveys Tutorials, vol. 15, no. 4, 2013, pp.15:2091– 2121.
[18] C. Huang, S. Hao, L. Invernizzi, et al., “Gossip:Automatically Identifying Malicious Domains from Mailing List Discussions,”Proc. the ACM Asia Conference on Computer and Communications Security (ASIACCS) 2017, 2017, pp. 494-505.
[19] S. Baki, R. Verma, A. Mukherjee, et al., “Scaling and Effectiveness of Email Masquerade Attacks:Exploiting Natural Language Generation,”Proc.Asia Conference on Computer and Communications Security (ASIACCS) 2017, 2017, pp.469-482.
[20] P. Wang, S. Sparks, C. Zou, “An Advanced Hybrid Peer-to-peer Botnet,”IEEE Transaction on Dependable and Secure Computing, vol. 7, no. 2,2010, pp. 7(2):113-127.
[21] W. Salusky, R. Danford, “Know your enemy: Fastflux service networks,”The Honeynet Project,2007, pp. 1–24.
[22] M. Ester, P. Kriegelh, J. Sander, et al., “A Density-based Algorithm for Discovering Clusters in Large Spatial Databases with Noise,”Proc. the Second International Conference on Knowledge Discovery and Data Mining, 1996, pp. 226–231.
[23] L. Maaten, G. Hinton, L. V. D, “Visualizing Data Using t-SNE,”Journal of Machine Learning Research, 2008, pp. 9:2579–2605.
[24] G. Cherubin, I. Nouretdinov, A. Gammerman, et al., “Conformal Clustering and Its Application to Botnet Traffic,”Proc. the Third International Symposium of Statistical Learning and Data Sci-ences, 2015, pp. 313–322.
[25] V. Vovk, A. Gammerman, G. Shafer, “Algorithmic Learning in a Random World,”Springer, 2014,pp.1-16.
[26] I. Arce, “The Weakest Link Revisited,”IEEE Security and Privacy, vol. 99, no. 2, 2003, pp. 72–76.
[27] Lastline Webinar. https://go.lastline.com/webinar-protect-your-network-from-evasive-malware.html
- China Communications的其它文章
- CYBERSPACE SECURITY: FOR A BETTER LIFE AND WORK
- A Cloud-Assisted Malware Detection and Suppression Framework for Wireless Multimedia System in IoT Based on Dynamic Differential Game
- An Integration Testing Framework and Evaluation Metric for Vulnerability Mining Methods
- Powermitter: Data Exfiltration from Air-Gapped Computer through Switching Power Supply
- CAPT: Context-Aware Provenance Tracing for Attack Investigation
- Decentralized Attribute-Based Encryption and Data Sharing Scheme in Cloud Storage

