WiGig and IEEE 802.11ad for Multi-Gigabyte-Per-Second WPAN and WLAN
Sai Shankar N,Debashis Dash,Hassan El Madi,and Guru Gopalakrishnan
(Tensorcom Inc.,5900 Pasteur Court,Carlsbad,CA 92008,USA)
Abstract The Wireless Gigabit Alliance(WiGig)and IEEE 802.11ad are developing a multigigabit wireless personal and local area network(WPAN/WLAN)speci f i cation in the 60 GHz millimeter wave band.Chipset manufacturers,original equipment manufacturers(OEMs),and telecom companies are also assisting in this development.60 GHz millimeter wave transmission will scale the speed of WLANs and WPANs to 6.75 Gbit/s over distances less than 10 meters.This technology is the first of its kind and will eliminate the need for cable around personal computers,docking stations,and other consumer electronic devices.High-definition multimedia interface(HDMI),display port,USB 3.0,and peripheral component interconnect express(PCIe)3.0 cables will all be eliminated.Fast downloads and uploads,wireless sync,and multi-gigabit-per-second WLANs will be possible over shorter distances.60 GHz millimeter wave supports fast session transfer(FST)protocol,which makes it backward compatible with 5 GHz or 2.4 GHz WLAN so that end users experience the same range as in today’s WLANs.IEEE 802.11ad speci f i es the physical(PHY)sublayer and medium access control(MAC)sublayer of the protocol stack.The MAC protocol is based on time-division multiple access(TDMA),and the PHYlayer uses single carrier(SC)and orthogonal frequency division multiplexing(OFDM)to simultaneously enable low-power,high-performance applications.
Keyw ords:60 GHz communications;IEEEstandards;WiGig;802.11ad;contention based access protocol;scheduled protocol;Beamforming;power save
1 Introduction
There is a huge amount of unlicensed spectrum available worldwide in the 60 GHz band.Academia and industry have turned to the 60 GHz spectrum because of the universal availability of unlicensed spectrum,the ever-growing number of user applications creating heavy data traffic,and the need to reduce data transfer times.Considerable efforts have been made to use this spectrum and spur the development of silicon,similar to what happened with the 2.4 GHz ISM band 15 years ago.60 GHz millimeter wave technologies offers a way to provide end users with guaranteed quality of service(QoS)for different applications.Fig.1 shows the allocation for 60 GHz in different countries[1]-[3].
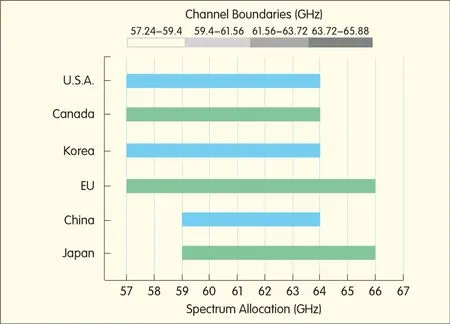
▲Figure 1.Spectrum allocation for WiGig.
60 GHz millimeter wave technologies create significant problems in designing the radio frequency(RF)front-end,processing gigabit-per-second data,and migrating to 40 nm and 28 nm low-power technologies in designing the silicon,considerable progress have been made in making it practical and feasible[4]-[6].60 GHz millimeter wave systems are needed to cater for newer applications,such as streaming video in the home or office,that have flourished as a result of last-mile access provided by internet service providers(ISPs).Such systems will also eliminate the need for cables around docking stations,and this will reduce clutter and allow easier connection between devices.There are multiple industry organizations involved in 60 GHz standardization,the notable ones being Wireless HD[7],IEEE 802.15.3c[8],WiGig[9],and IEEE 802.11ad[10].The last two of these organizations involve a large number of silicon,OEM,and telecom companies that are motivated to have a single worldwide 60 GHz standard.WiGig began standardization in 2008 and has recently released the WiGig 1.0 standard.IEEE 802.11ad also began standardization in 2008 and has recently released IEEE 802.11ad Draft 9.0 standard.These standards are similar,and in this paper,we willrefer to 802.11ad as the representative of both standards,pointing out when there is a feature that is unique to the WiGig standard.Similar standardization efforts have been made by ECMA-387 and CMMWStudy Group[2],[3].60 GHz millimeter wave is the next wireless networking technology and willappear in the market around 2014[11].It is poised to repeat the successes of Bluetooth and Wi-Fi[12].This explosive growth of the wireless industry in such a short time can also be attributed to the opening of unlicensed bands in 60 GHz by the Federal Communications Commission(FCC).
802.11ad aims to develop the protocol adaptation layers(PALs)to support a plethora of applications that will arise from the elimination of cables and from fast wireless sync and transfer.The PALs being considered by WiGig include wireless serial extension(WSE),which eliminates USB 3.0 cables;wireless bus extension(WBE),which eliminates PCIe 3.0 cables;wireless display extension(WDE),which eliminates high-definition multimedia interface(HDMI)and display port cables;and wireless secure digital(WSD),which makes secure digital input/output card(SDIO)disks wireless.The first important 60 GHz millimeter wave application to enter the market as wireless docking based on PCIe 3.0—with one second-generation lane(also called x2)—or USB 3.0.All devices with 802.11ad MAC/PHY/Radio use the corresponding PALs between the application and MAC layers to seamlessly transfer information between devices as if the devices were connected by wires.Another 60 GHz application is wireless HDMIbased on WDE,which allows transfer of uncompressed bits from devices such as set top boxes and blue ray disc players to television screens and from laptops,desktops,or ultrabooks to monitors via a display port cable replacement.The WDEalso supports H264 compressed rates for handling variations in the wireless channel and to ensure seamless content delivery to the end users.Performance of the PHYand MAC protocols is analyzed in[13]and[14].
In this paper,we describe the novel features of the MAC and PHYsublayers of the protocol stack defined in 802.11ad.In section 2,we describe the TDMAprotocol and the need for directionality in 60 GHz.In section 3,we outline the 802.11ad PHYlayer,and in section 4,we outline the MAC layer.In section 5,we outline the beamforming protocol,and in section 6 we outline the power-saving protocol.In section 7,we describe the fast session transfer,and in section 8,we show achievable rates using different MAC-and PHY-layer packet transmission options.Section 9 concludes the paper.
2 TDMA Protocol and the Need for Directionality
Interest in the 30-300 MHz millimeter wave spectrum has increased significantly because of low-cost,high-performance CMOStechnology and because of low-loss,low-cost organic packaging.A millimeterwave radio can be empowered for the same cost as a radio operating in the 5 GHz band or lower.This advantage,combined with wide available bandwidth,makes the millimeterwave spectrum more attractive than ever before for supporting new systems and applications.A millimeter wave signal can propagate over a few kilometers at lower frequencies,penetrating through different construction materials and deriving advantages from reflection and refraction;however,they are highly directional and can be sustained only over short distances.The reason for this directionality is explained by the Friis free space equation:

where PR,PT,GT,GR,λand R is the receive power,transmit power,transmit antenna gain,receive antenna gain,wavelength,and distance between the transmitter and receiver,respectively.There is a 22 d B loss when we move from 5 GHz to 60 GHz.This loss is due to lower wavelength and can be offset by using directionalantennas with higher gains.If 2 GHz bandwidth was used in 60 GHz and PT=10 d Bm,the noise figure Nf=10 d B,and the shadow fading marginσ=6 d B,1 Gbit/s throughput could not be achieved(Fig.2)[1].Therefore,the gains of directional antennas must be exploited to achieve higher rates.
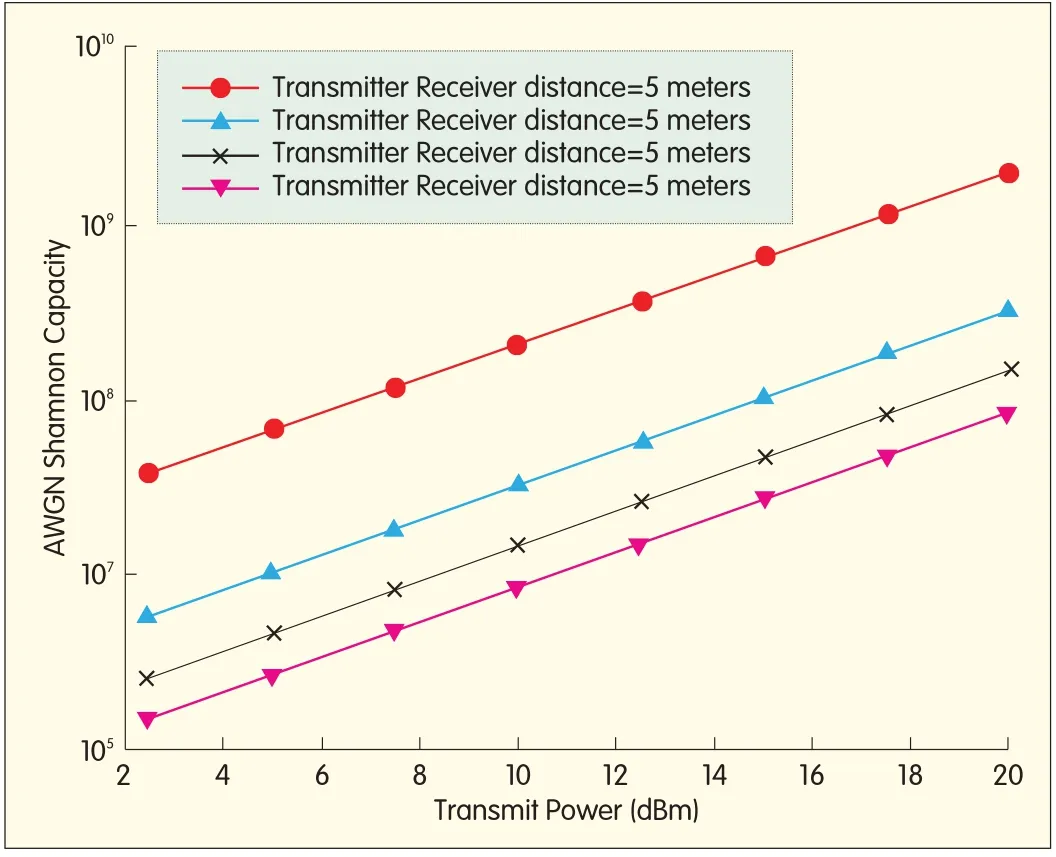
▲Figure 2.Shannon capacity versus transmit power at 60 Hz.
Directional communication requires complex discovery and beamforming protocols to establish links between different devices.Scheduled protocols such as TDMA are needed at the MAC layer to guarantee QoSat multi-gigabit-per-second rates.Randomized access protocols such as CSMA come with a random overhead that can depend on the number of users contending for the channel.Although CSMA/CAis still used to handle bursty traffic,allocation of contention-based access periods(CBAPs)is based on TDMA.
3 Physical Layer
802.11ad defines four different PHYlayers:Control PHY,SC PHY,OFDM PHYand low-power SC PHY(LPSC PHY).Control PHYis MCS 0.SC starts at MCS 1 and ends at MCS 12;OFDM PHYstarts at MCS 13 and ends at MCS 24;and LPSC starts at MCS 25 and ends at MCS 31.MCS 0 to MCS 4 are mandatory PHYMCSs.Here,we brie f l y describe the different PHYs and their packet structures.The system clock rate is 2640 MHz,and this rate is used for OFDM also.Control,SC and LPSC PHYs have a clock rate of 2/3×2640=1760 MHz.
3.1 General Packet Structure
As is common with all 802.11 packet formats,the packet consists of a short training sequence,a channel estimation sequence,the physical layer convergence procedure(PLCP)header,MAC packet,and cyclic redundancy check(CRC).Although there are different PHYs,they all have this unique structure,which ensures implementers do not need to change packet formats when using different PHYs.The only difference is that each PHYis a different size and uses a different Golay code.
The short training field(STF)and channel estimation field(CEF)help signalacquisition,automatic gain controltraining,predicting the characteristics of the channel for the decoder,frequency offset estimation and synchronization.Both STF and CEFsequences use Golay codes.The PLCPheader indicates the size of the packet as well as the modulation structure(MCS)of the packet.The MACpacket comprises MAC header and data and contains information about the destination.CRC ensures that the packet is not corrupted while being transmitted through the air.802.11ad has a TRN field comprising Golay codes.This field is used in beam tracking and refinement and is described in section 5.Fig.3 shows a typical packet in 802.11ad.
3.2 Control PHY
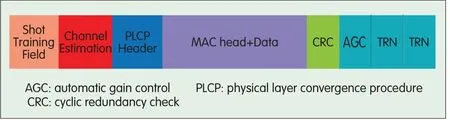
▲Figure 3.IEEE 802.11ad packet structure.
high-rate beamformed link.To help discovery and detection,the control PHYhas an STFcomprising 50 Golay sequences,each of which is 128 samples long.The CEFthat follows the STFhas nine Golay sequences.The STFcomprises 48×Gb128(n)(each 128 samples long)followed by a single repetition of-Gb128(n).The CEFcomprises Gu512(n)and Gv512(n)followed by Gv128(n).These sequences are represented as function of Ga128(n)and Gb128(n)in section 21.11 of the IEEE 802.11ad draft specification[10].Gu512(n)and Gv512(n)are given by:
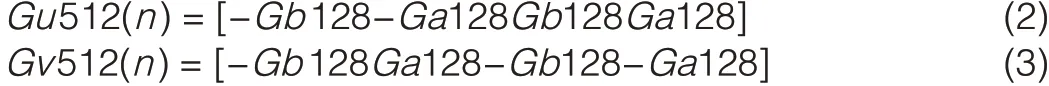
The control PHYuses BPSK with a code rate of 1/2 and is spread using a 32 code to create a PHYrate of 27.5 Mbit/s.The Control PHYis used for transmitting and receiving frames such as beacons,information request and response,probe request and response,sector sweep,sector sweep feedback,and other management and control frames.It provides reliability and exploits gain of the transmit antenna.Additionally,the first frame transmitted during the beam refinement protocol(BRP)phase is also a control PHYframe.
3.3 Single-Carrier PHY,OFDM PHY and LPSC PHY
MCSs 1 to 4 are mandatory and ensure that all devices,irrespective of their PHY,are interoperable.All the MCSs,with the exception of LPSC PHY,use LDPC code,and the LPSC uses Reed Solomon(RS)codes.The following two subsections describe the MAC header and data packet encoding process for SC PHY.Other PHYs use a similar encoding process.All packets are modulated using BPSK,QPSK,16-QAM and 64-QAM(Table 1).
3.4 Header Encoding
The header is encoded using a single SC block of NCBPBsymbols with NGIguard symbols.The bits are scrambled and encoded in the following steps:
1)The input header bits(b1,b2,...,bLH)LH=64 arescrambled,starting from the eighth bit,in order to create d1s=(q1,q2,...,qLH).
2)The LDPC code word c=(q1,q2,...,qLH,01,02,...,0504-LH,p1,p2,...,p168)is created by concatenating 504-LH zeros to the LH bits of d1s and then generating the parity bits p1,p2,...,p168so that HcT=0,where H is the parity-check matrix for the 3/4 LDPC code specification in 802.11ad.
3)Bits LH+1 through 504 and bits 665 through 672 of the code word c are removed to create the sequence cs1=(q1,q2,...,qLH,p1,p2,...,p160).
4)Bits LH+1 through 504 and bits 657 through 664 of the code word c are removed to create the sequence cs2=(q1,q2,...,qLH,p1,p2,...,p152,p161,p162,...,p168)and then to create XOR with a PN sequence.The PN sequence is generated from the LFSRused for data scrambling,and the LFSRis initialized to the all-ones vector.
5)cs1and cs2are concatenated to form the sequence(cs1,cs2).The resulting 448 bits are then mapped as π/2-BPSK,and the NGIguard symbols are prepended to
The control PHY,MCS 0,is the minimum rate that all devices use to communicate with before establishing a the resulting NCBPB symbols.
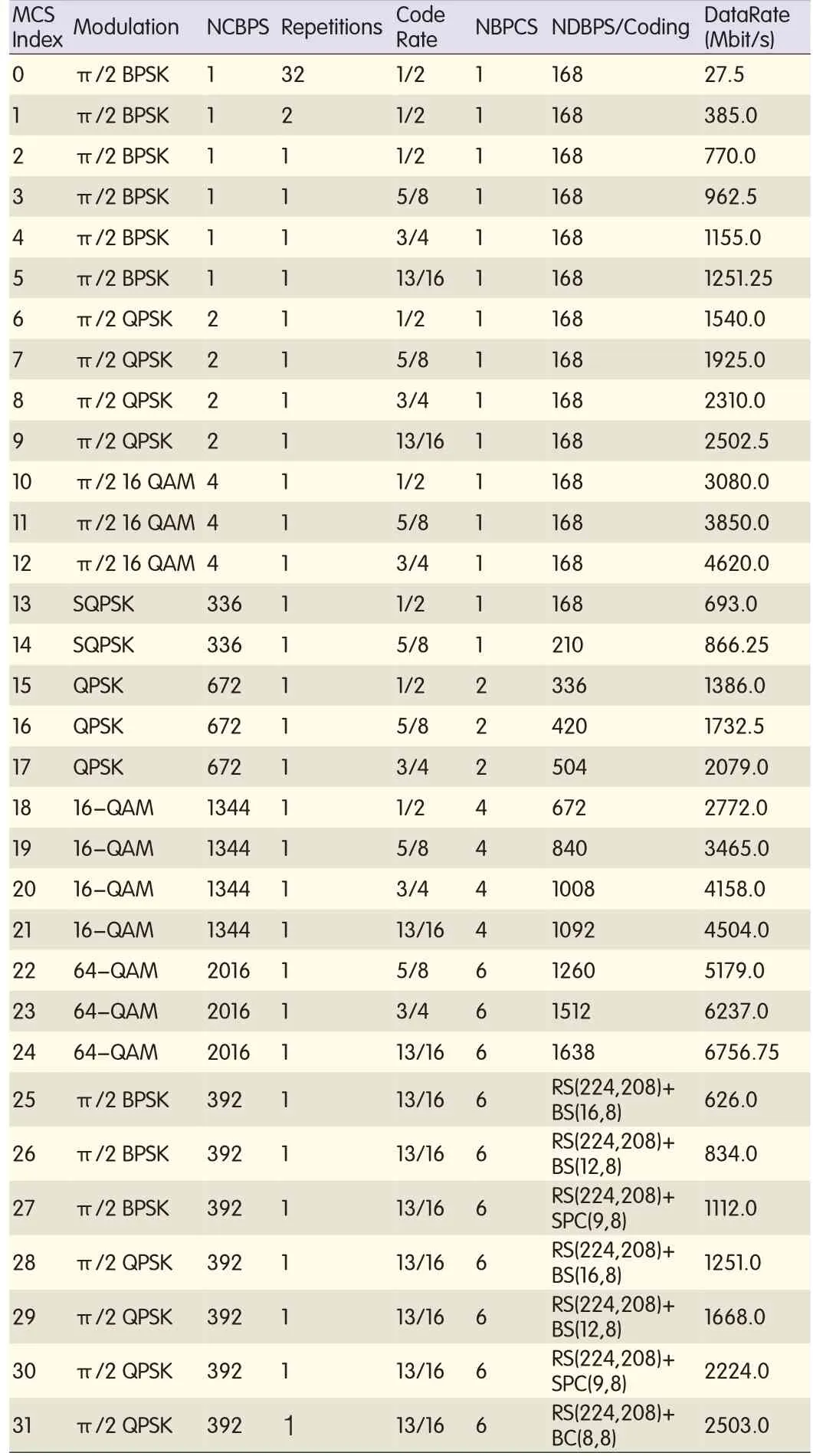
▼Table 1.PHYmodulation and coding scheme table
3.5 Data Encoding
The data packet is encoded using LDPC,which includes deciding the number of shortening/repetition bits in every code word,shortening,coding each word,and repetition of bits.Data packet encoding occurs in the following steps:
1)The number of LDPC code words is given by NCW=(length×8ρ)/(LCW×R).This is used to calculate the number of datapad bits given by NDATA_pad=(NCW×LCW×R)/ρ-(length×8),where LCW=672 is the LDPC code word length;length is the length of the PSDU defined in the header field(in octets);ρis the repetition factor(1 or
2);and Ris the code rate.The scrambled PSDU is concatenated with NDATAPAD zeros,which are scrambled using the continuation of the sequence that scrambled the PSDU input bits.
2)The output stream of the scrambler is broken into blocks of LCWD=LCW×R bits so that the mth data word is b1m,b2m,...,bmLCWDm<NCW.
3)To each data word,n-k=LCW-(R×LCW)parity bits p1m,

4)The code words are concatenated one after the other to create the coded bitstream c1,c2,...,cLCWD×NCWThe number of symbol blocks is given by NBLK=(NCW×LCW)/NCBPB,and the number of symbol block padding bits is is the number of coded bits per symbol block.

5)The coded bitstream is concatenated with NBLKPADzeros,which are scrambled using the continuation of the scrambler sequence that scrambled the PSDU input bits.Table 1 shows the MCSvalues allowed in 802.11ad.
4 Overview of 802.11AD MAC Protocol
4.1 802.11ad Superframe
The 802.11ad superframe is called the beacon intervaland comprises a beacon transmission interval(BTI),a data transfer interval(DTI),and optional association beamforming training(A-BFT)or announcement transmission intervals(ATI)(Figs.4 and 10).The DTIcan include one or more service periods(SPs)and CBAPs.
4.2 Service Period Channel Access
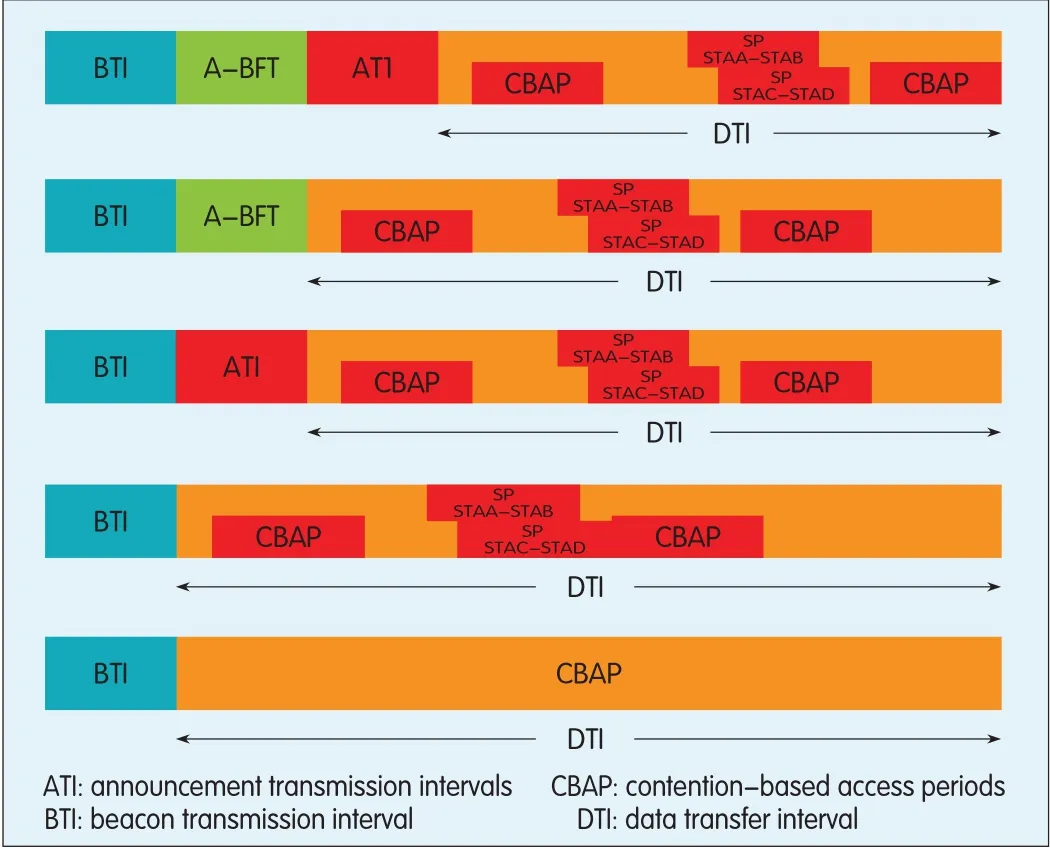
▲Figure 4.Examples of 802.11ad beacon intervals.
An SPis a scheduled access period between two stations:a transmitter and receiver.SPs are suitable for directional(high-gain)antenna use.New features introduced by 802.11ad include spatial sharing,where SPs need not be out of synch,that is,an SPbetween stations A and Bmay occur at the same time as another SPbetween stations C and D.IEEE 802.11ad also introduces dynamic SPallocation,truncation,and extension.An SPallocation is dynamic if it is not initially scheduled by the personal basic service set(PBSS)control point/access point(PCP/AP)but is scheduled during an existing SPor CBAP.SPtruncation occurs when the transmitter station relinquishes the remaining time in its SP.SP extension occurs when the transmitter station extends the SP duration it had been allocated.
4.3 CBAPChannel Access
During a CBAP,all stations contend for channelaccess using a hybrid TDMA-CSMA/CA scheme based on 802.11 enhanced EDCA.802.11ad provides physical carrier sensing mechanism,provided by the physical layer,and a virtual carrier-sensing mechanism,provided by the MAC layer.Physical carrier sensing uses clear channel assessment(CCA).
Virtual carrier sensing uses a timer called network allocation vector(NAV).NAVindicates,in microseconds,how long the channel is reserved by another station and counts down to 0.The virtual carrier-sensing mechanism uses request-to-send/directional multigigabit clear-to-send(RTS/DMG CTS)frames.When a station receives an RTS/DMG CTSframe,it sets its NAVto the value in the Duration field in the MAC header of the RTS/DMG CTS.Stations also use the Duration field of other frames to update their NAVs;however,the frame’s destination address must be different from the receiving station’s MACaddress,and the value of the Duration field must be greater than the current NAVvalue.Stations may have a unique NAVor may have one NAVper sector.If a station has multiple NAVs and at least one has a non-zero value,the virtual carrier-sensing mechanism considers the medium busy.The medium is considered busy if either the physical or virtual carrier-sensing mechanism indicates it is busy;otherwise,it is considered idle.802.11ad defines four different access categories(ACs)that have different priorities based on the user priority(UP)of the data being transferred.In order of increasing priority,these ACs are background(BK),best effort(BE),video(VI),and voice(VO).Only BEis mandatory in the standard,that is,only BEis implemented or allfour are.When allfour ACs are implemented,all ACs within a given station have to contend with each other and with other stations for channel access.Each ACcontends for a channel in the following way:After the medium has been idle for a period of time,called the arbitration interframe space(AIFS[AC]),the station contending for access randomly sets its backoff timer to a between 0 and the contention window(CW[AC]).CW[AC]is initialized to CWmin[AC]and is updated after every transmission.In case of transmission failure,CW[AC]is updated using

When CW[AC]reaches CWmax[AC],it remains unchanged for any remaining retries.In the case of transmission success,CW[AC]is reset to CWmin[AC].At every slot time boundary,the medium is sensed.If the medium is found to be idle,the backoff timer is decremented;otherwise,it is suspended.When the backoff timer for a particular AC reaches 0,that AC obtains exclusive channel access for a period of time called the transmit opportunity(TXOP[AC]).During the TXOP[AC],only frames with UPmapping to that AC may be transmitted.If the backoff timers of two or more ACs reach zero at the same time,channel access is granted to the AC with the highest priority,and the other ACs treat this occurrence as if it were an external collision that happened in the wireless medium.The other ACs then enter backoff phase.For each AC,EDCA parameters such as CWmin[AC],CWmax[AC],AIFS[AC]and TXOP[AC]are calculated by the PCP/APand included in the DMG beacon,probe response,or(re)association response frames transmitted by the PCP/AP.Higher-priority ACs are granted lower values for CWmin[AC],CWmax[AC],AIFS[AC]so that they can gain channel access while lower-priority ACs are still in backoff phase.
4.4 Packet Aggregation
802.11ad is capable of a multi-gigabyte-per-second data rate because of features such as packet aggregation and block acknowledgement in addition to directionalantennas.The basic MAC data unit is called MAC protocol data unit(MPDU)and comprises a MAC header and a MAC service data unit(MSDU)or MAC payload.APHYheader and an MPDU comprise a PHYPDU(PPDU).802.11ad uses the Galois/counter mode(GCM)protocol for data encryption.This protocolwas designed for encryption at multi-gigabytes-per-second data rates.
An encrypted MPDU includes a GCM protocol header and a MIC field.Fig.5 shows the MPDU structure.Fig.6 shows the MPDU structure with encryption turned on.Packet aggregation involves combining several packets into a single packet.When several MSDUs or MPDUs are combined,the resulting packet is called aggregated MSDU(A-MSDU)(Fig.7)or aggregated MPDU(A-MPDU)(Fig.8).802.11ad uses a new type of packet aggregation called aggregated PPDU(A-PPDU).In an A-PPDU packet,several PPDUs are transmitted back-to-back without interframe spacing(IFS)and preamble in between.A-PPDUreduces overhead associated with IFSand MAC/PHYheader processing.
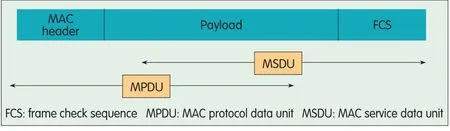
▲Figure 5.802.11ad MPDUstructure.
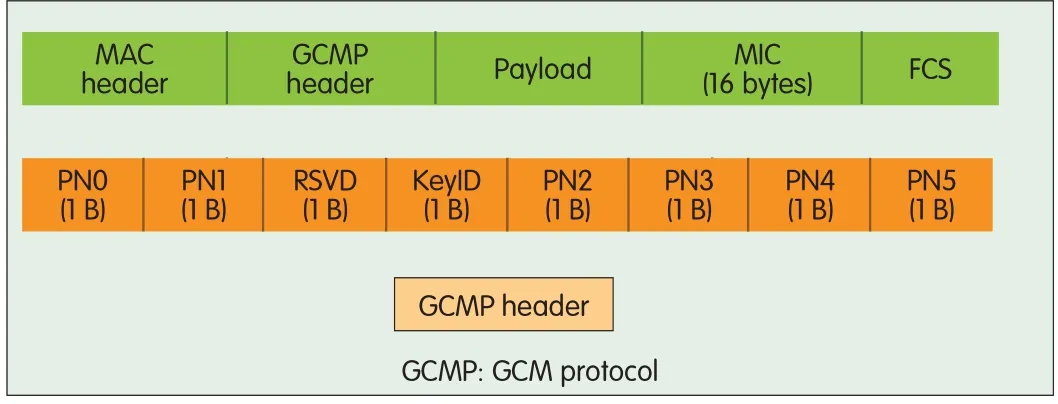
▲Figure 6.802.11ad MPDUstructure with encryption turned on.

▲Figure 7.802.11ad A-MSDUstructure.

▲Figure 8.802.11ad A-MPDUstructure.
4.5 Acknowledgement Policies
802.11ad defines a frame acknowledgement(ACK)policy called block acknowledgement.When block ACK is enabled,the transmitting station transmits a block of frames one frame at a time immediately after each other without waiting for the receiver to acknowledge the previous frame.After the entire block of frames has been transmitted,the receiving station sends a control frame called block ACKthat includes a bitmap.The bitmap,in which each bit corresponds to a frame,indicates which frames were received successfully and which ones were not.The receiver knows to send a block ACK frame when it receives a block ACK request frame from the transmitter.This ACK policy allows the transmitter to use shorter IFSbetween frames,and it eliminates the IFSbetween each frame and its individual ACK frame,as in a typical stop-and-wait protocol.Fig.9 shows normal ACK and block ACK policies.
5 Beamforming Protocol
Because of the highly directional nature of 60 GHz communications,the transmitter and receiver antennas need to be aligned in the right direction to obtain maximum gain.802.11ad supports up to four transmitter antennas,four receiver antennas,and 128 sectors.Beamforming is mandatory in 802.11ad,and both transmitter-side and receiver-side beamforming are supported.
Beamforming can be done at the transmitter side,receiver side,or at both sides[15].Transmitter-side beamforming usually requires feedback from the receiver,especially when the transmitter-to-receiver and receiver-to-transmitter channels are not reciprocal.The need for feedback can be reduced or eliminated by using space time codes;however,this can cause considerable overhead in the setting-up beamforming[16].802.11ad uses a selection-based protocol in which the transmitter sends training from certain sectors that are pre-defined according to distinct antenna patterns created by changing the antenna weights[17].The receiver antenna maintains an omnidirectionalpattern and measures the strength of the received signal from the different sectors.It responds with information about the best sector and measured quality.With this feedback,the transmitter chooses the best sector to use while transmitting to the receiver.Similarly,in receiver-side training,the receiver repeats the training from the transmitter,which is sent using an omnidirectional antenna pattern,and measuring the strength of the received signal through pre-defined receive sectors.
The station that starts the beamforming training is called the initiator,and the recipient is called the responder.Beamforming in 802.11ad involves sector-level sweep(SLS),BRP,and beam tracking(BT).Fig.10 shows the sequence of this beamforming.Each of the steps in the sequence is allowed in a particular part of the beacon interval(Fig.11).SLSenables reliable communication at the lowest supported rate(called MCS0 in 802.11ad).Usually,transmitter-side training is done during the SLS.The BRPenables receiver training and iteratively trains the transmitter and receiver sides to improve on the values found during the SLS.Both SLSand BRPphases use their own specialpackets for beamforming training.By contrast,BTcan be done during data transmission.It is used to track the beamforming state and improve it during data transmission.BTis implemented by adding training(TRN)fields to the back of a data packet.
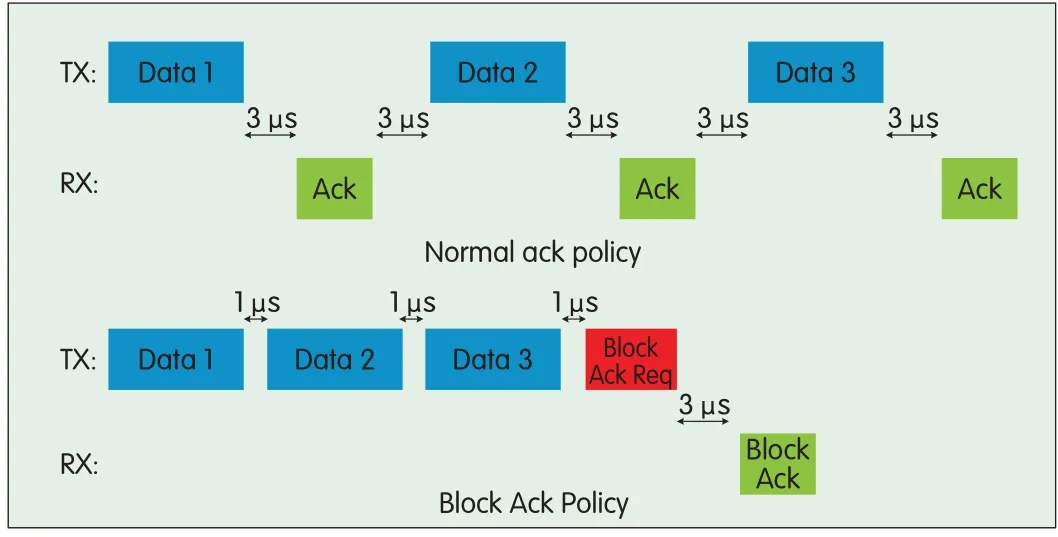
▲Figure 9.Normal ACKpolicy and block ACKpolicy.
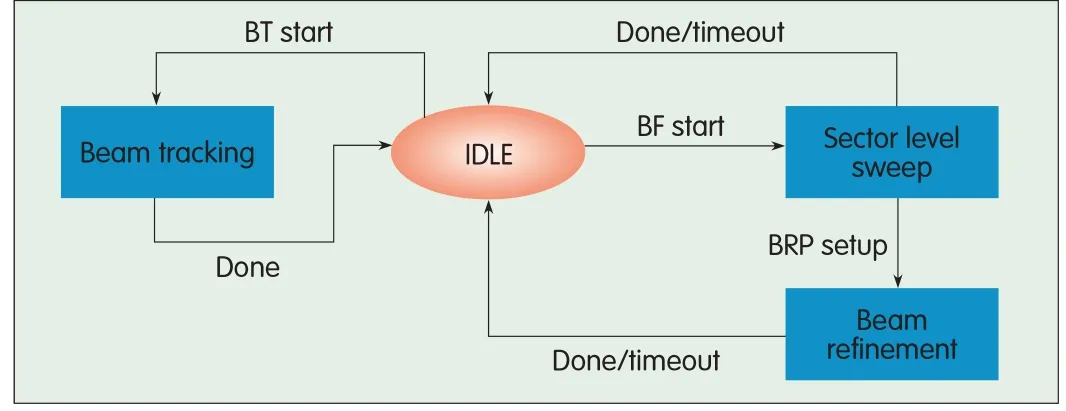
▲Figure 10.The sequence in which the differentphases of beamforming occur in 802.11ad/WiGig standard.
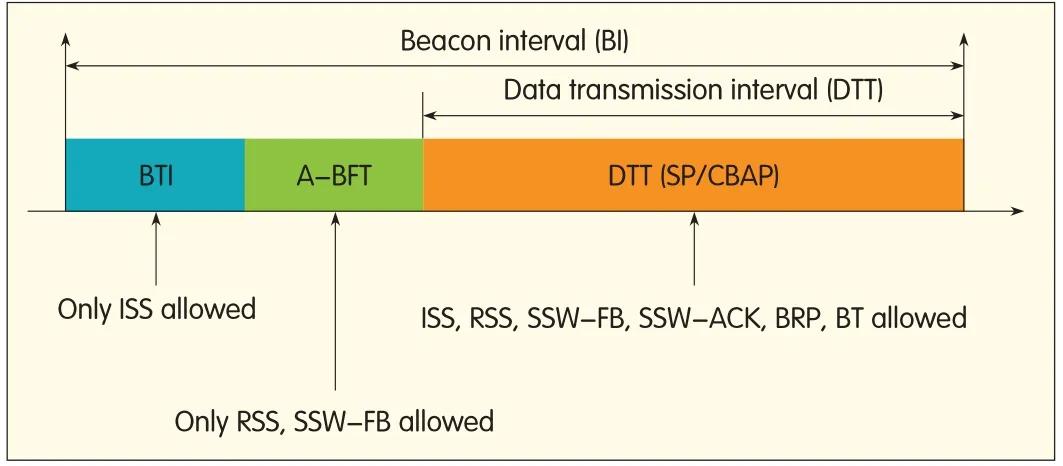
▲Figure 11.Different transmission periods and BFphases allowed in each partof the beacon interval.
The SLSinvolves initiator sector sweep(ISS),responder sector sweep(RSS),sector sweep feedback(SSW-FB),and sector sweep acknowledgement(SSW-ACK).The BRP comprises setup,multiple sector ID detection(MID),beam combining(BC),and BRPtransactions.Of these,MID and BC are optional features for 802.11ad supporting stations.BT comprises BTrequest and BTresponse.The parameters for exchanging beamforming packets are obtained using the capability element in the beacon packets,probe request/response packets,or information request/response packets.
5.1 Beaconing and Sector-Level Sweep
At the start of every BTI,the PCP/APMACschedules an initiator transmit sector sweep(TXSS)to transmit beacons through all sectors.The PCP/APcan also fragment the TXSS across multiple beacon intervals if the BTIis insufficient and cannot complete the TXSS.A station without a PCP/APuses an omnidirectional receiving antenna configuration to scan non-associated beacons or receive associated beacons from the PCP/APand determine the best sector/antenna ID using the sector sweep field at the end of TXSS.In a beacon,CDOWN is the number of pending beacon transmissions for completion of TXSS,with 0 being completion.
If multiple transmit antennas are supported,a PCP/AP station cannot switch its transmit antennas for beacon transmission within a BTInor can it transmit a beacon more than once using the same antenna con f i guration.To minimize potential interference,the PCP/AP changes the order of sectors across beacon intervals if multiple directional beacon transmissions are required or waits for a random delay at the start of beacon interval if only a single beacon is to be transmitted(Fig.12).
5.2 A-BFTProtocol
The PCP/APannounces the existence of an A-BFTperiod in the beacons,and this information is used for association and beamforming training for new stations,such as PBSS stations,that join the network.A-BFTmay not be present in each beacon interval and may be periodically inserted by the AP/PCP.The A-BFTperiod allows stations to perform RSS and SSW-FB phases of beamforming with the PCP/AP.It is assumed that the new station has already used the beacons sent from all the transmit sectors of the PCP/APto perform an ISSwith the PCP/APduring the BTI.The A-BFTperiod is a slotted phase where each slot is a multiple of the time required for RSSand SSW-FB.The new stations use random backoff to select the A-BFTslot for an RSS.When beamforming is done during A-BFT,the SSW-ACKphase is skipped,and BRPis done during the data transmission interval if necessary.There may be no chance to do RSS during A-BFTbecause stations use random access;therefore,the AP/PCPmay schedule an SPto continue beamforming with the particular station.
5.3 Sector-Level Sweep
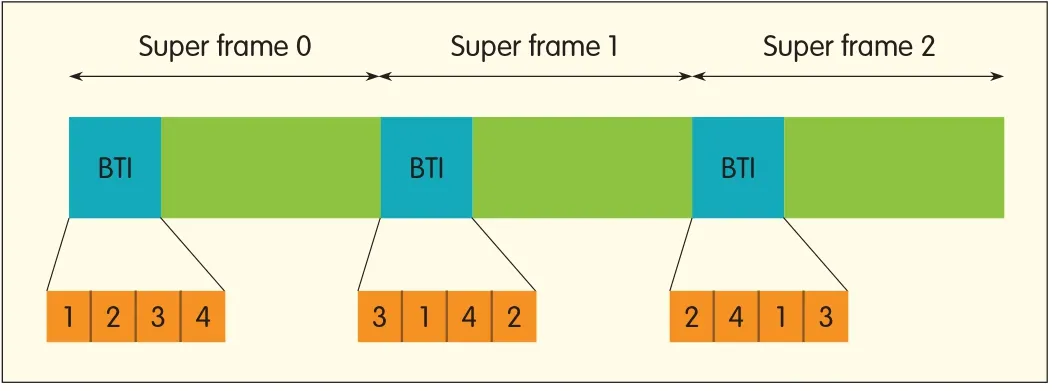
▲Figure 12.Asample DMG beacon transmission by a PCPhaving one transmitantenna with four sectors.
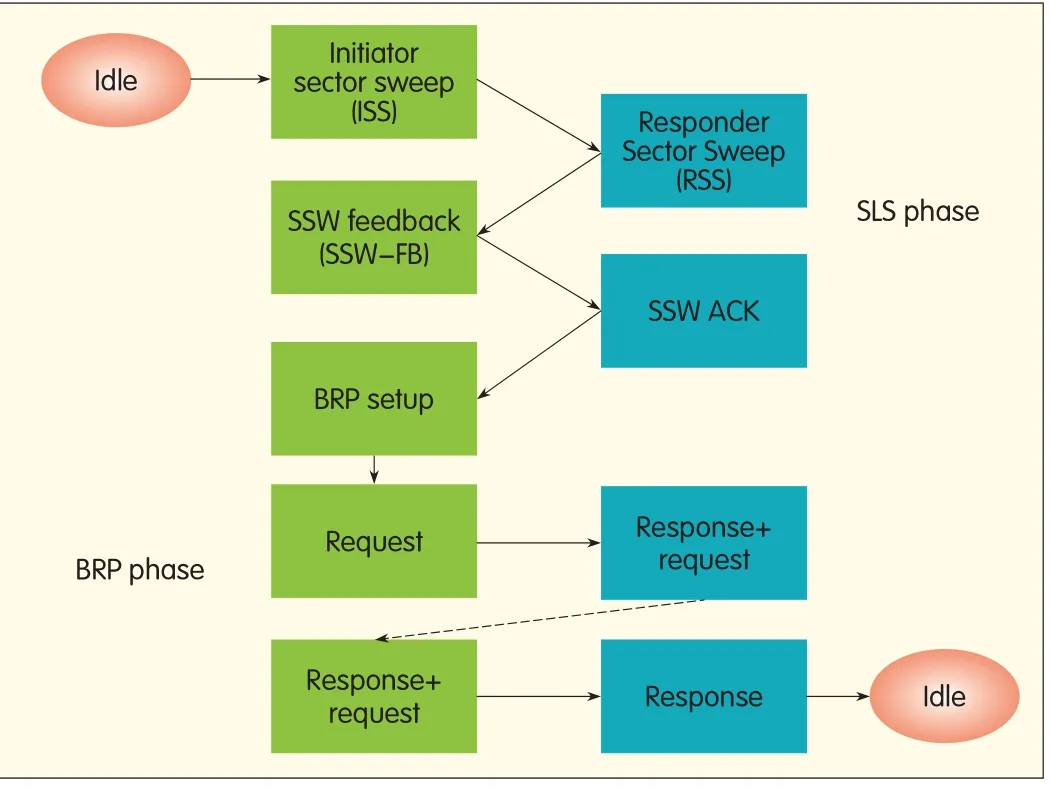
▲Figure 13.Parts of the sector levelsweep and beam refinement phases of the beamforming in 802.11ad.
The SLSis the basic type of beamforming supported by 802.11ad.It comprises ISS,RSS,SSW-FB and SSW-ACK.The link from the initiator to the responder is called the initiator link,and the link from the responder to the initiator is called the responder link.During SLS,the ISSphase is used to train the initiator link,and the RSSis used to train the responder link.The RSScontains feedback about the best sector found during ISS,and the SSW-FBcontains the best sector found in the RSS.In SLSis concluded with an SSW-ACK(Fig.13).A station can have separate transmitter and receiver chains with their own antenna configurations.Hence,for each of the initiator and responder links,the transmitter and receiver can be trained independently to perform beamforming.The protocol used to train the transmitter during SLSis called TXSS,and the protocol used to train the receiver is called RXSS.This gives rise to four possibilities;if an ISSis used to the train the transmitter side of the initiator link,the phase is called ISSTXSS.Similarly,the other three possibilities are ISS RXSS,RSSTXSS,and RSSRXSS.
During TXSS,the transmitter sends a separate SSWframe from different available transmit sectors,the number of which can be pre-negotiated between stations.The receiver maintains a quasi-omnireceive configuration.If the receiver has multiple antennas,the transmitter repeats this process for each receive antenna.The receiver measures the quality of the packet received from each of the transmit sectors by cycling through all of its receive antennas in quasi-omni mode.In the end,the receiver replies with the best sector.The standard allows a vendor-specific algorithm to decide the best sector.Similarly,during RXSS,the transmitter uses an omniantenna configuration,and the receiver changes receive sectors to determine which the best receive sector.
The SLSphase can be initiated by the PCP/APduring the BTIby performing an ISS.Then,the RSSand FB phases are completed during the A-BFTannounced by the PCP/AP.In this case,the BRPphase completed in an ATIor DTI.Alternatively,a station can either use a CBAPperiod(also announced in the beacon)or schedule an SPto perform beamforming with another station.The DTIcan be used for all the phases of beamforming(Fig.11).
The BRPphase comprises a setup phase followed by a beam-re f i nement phase based on request-response(Fig.13).The request-response packets of the setup phase are exchanged until the responder(receiver)sets the capability-request field in the BRPpacket at 0.This is followed by a response from the initiator(transmitter)with the capability-request field set at 0.
The beam-refinement request can be a transmitter-or receiver-refinement request.A transmitter-refinement request indicates the need for transmitter antenna training by the transmission station and vice versa.The transmitter station adds TRN-Tsubfields to the BRPframe.The receiver station holds data that it obtained by measuring the TRN-Tfields.The receiver station responds to a receiver-refinement request(sent by the transmitter station)by appending TRN-R subfields to its response frames,that is,an ACKor block ACK frame.
The SLSand BRPphases of beamforming usually precede data transmission.They are completed right at the beginning of beamforming and are repeated periodically as needed.Beamtracking is used for beamforming training during data transmission to accommodate channelchanges between two SLS/BRPbeamforming training phases.In beamtracking,training f i elds comprising CEand STFfields are attached to the back of data packets or,for example,ACK/BA,to train the transmitter or receiver(Fig.3).802.11ad allows for three types of beamtracking,and the type of beamtracking is signaled using three parameters in the PLCPheader.The three parameters of interest are packet type,training length,and beamtracking request.Of these,the training length is always greater than zero.If the training length is zero,the other two fields are reserved,and the packet does not contain any beamtracking training or request.Table 2 shows the types of training indicated by the PLCPparameters.

▼Table 2.Types of beamtracking indicated by the PLCPparameters
6 Power-Save Protocol
Dedicated SPs in 802.11ad allow battery-powered stations to hibernate during data transmission periods that are not assigned to them.An 802.11ad station can be in one of the two power-save states:doze or awake.When awake,a station is fully powered;when in doze,the station is powered off.A station’s power-save state in various sections in a beacon interval depends on whether the station is in active mode or power-save mode.In power-save mode,stations with or without PCP/APcan doze for one or more consecutive BIs,or sections of a BI,more if they were permanently in active mode.A station must check its peer’s wakeup schedule before sending any individually addressed MPDUs to the peer station because it may be in doze mode.Astation without PCP/APcan always use information request/response frames to request the wakeup schedule from any of its peers if required.Fig.14 shows power management modes and state transitions.
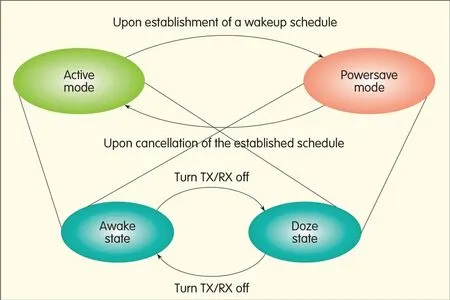
▲Figure 14.Power management-mode/state transitions.
A station without PCP/APthat has not established a wakeup schedule with its peer is in active mode.To switch from active to power-save mode,the station establishes a wakeup schedule with PCP/AP.It does this by including a wakeup schedule(WS)element in its power-save con f i guration request.To switch from power-save mode to active mode,the station without PCP/APsends a power-save configuration request in which the power management bit is set at 0.The station immediately switches to active mode upon receipt of the ACK frame from PCP/AP.
APCP/APstation includes its WSin its beacon or announcement frames before switching to power-save mode.When switching back to active mode,it ceases including the WSin these frames.The PCP/APstation keeps track of the wakeup schedules of all associated stations without PCP/AP.In addition,APs also have to buffer MPDUs addressed to associated stations in doze state and forward these MPDUs at designated times.
7 Fast Session Transfer Protocol
Fast session transfer(FST)protocol allows different streams or sessions to transfer smoothly from one channel to another in the same band or different bands.This protocol makes 802.11ad compatible with the forthcoming 802.11ac standard and other existing standards,such as 802.11a/b/g/n.The protocolallows different radios in the same device to operate simultaneously or not simultaneously.Devices with 802.11ac and 802.11ad can have same MACaddress or different MAC addresses.If the same MAC address is used for all the radios in different bands then FSTis in transparent mode.If the MAC addresses differ according to channel/band,then FSTis not transparent.
A simple example of FSTis a video stream to be established between STAAand STAB in the 2.4 GHz band using direct-link setup(DLS).The STAs are 40 m apart.The video uses 802.11n radio at 144.4 Mbit/s and H.264 compression.After some time,the user of STA Amoves very close to STAB so that the separation is less than 3 m.Both STA A and STA B understand that they have 60 GHz radio,which was discovered during in 60 GHz discovery mode.They then transition to 60 GHz channel 2 and use an uncompressed stream by closing their link at MCS 12,which is 4.62 Gbit/s(Fig.15).
This video stream established in 60 GHz channel 2 can be moved to 60 GHz channel 1 if there is congestion in channel 2.It can also be moved to channel4 in 5 GHz or channel 6 in 2.4 GHz when STA A starts to move away from STA B.In this example,video compression,such as H.264 and that used in the WiGig WDEspeci f i cation,ensures that the session does not drop because of large range or insufficient bandwidth.The application and MAC layers interact with PHYto optimize the smooth delivery of content to the end application.They compress the video whenever the band is not 60 GHz by using IEEE 802.11ac or IEEE 802.11n and then transition to uncompressed video using 60 GHz SC or OFDM modes when the range is less than three meters.This ensures the highest QoS.The FSTalso ensures that a subset of streams can be transferred from one channel/band to another while the remaining streams are in the original channel/band.
8 Packet Throughput
The modulation and coding schemes in section 3 along with the normal ACK,A-MSDU,and A-MPDU packet structures in section 4 allow the 60 GHz radios to change between very different achievable throughputs depending on the packet size.Fig.16 shows the MAC layer throughput versus packet size sent at different MCSvalues.Similarly,Fig.17 shows the throughput versus packet size when A-MPDU is used.In Figs.16 and 17,BTI,ABFTand AToverheads are not taken into account.The parameters described in section 3 can also be found in section 21.3 of[9].
9 Conclusion
802.11ad are standardizing 60 GHz technology to facilitate multi-gigabit-per-second communications over shorter distances.This standard has many new features to improve and sustain high-speed communications with TDMA single-carrier and OFDM schemes.They allow for scheduled and contention-based access,beamforming,and power-save mechanisms that decrease power consumption and increase throughput.Future evolution of 802.11ad towards full MIMO support and channel bonding can further increase its data rate.With the advent of new technologies to make these protocols practical,and with standardization by bodies such as WiGig and IEEE,truly wireless broadband will be achieved with 60 GHz,and allwires in PANs will be eliminated.
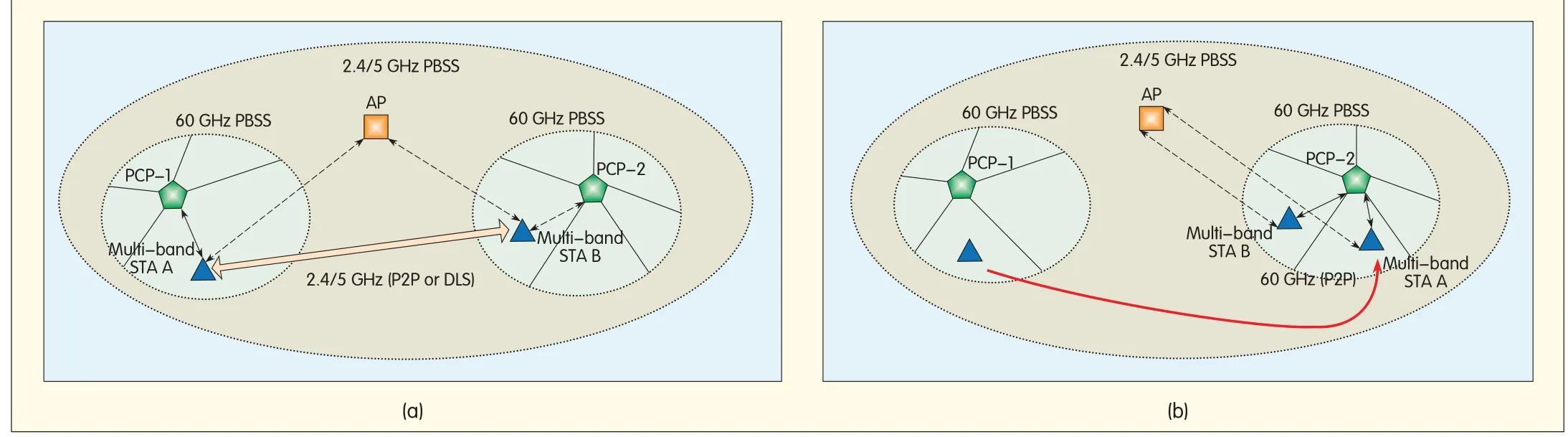
▲Figure 15.Fastsession transfer done by peer stations(STAs)Aand Bin an a)2.4 GHz channeland b)a 60 GHz channel.

▲Figure 16.Single carrier throughput as a function of the packet size for different MCSvalues for non-aggregated packets.
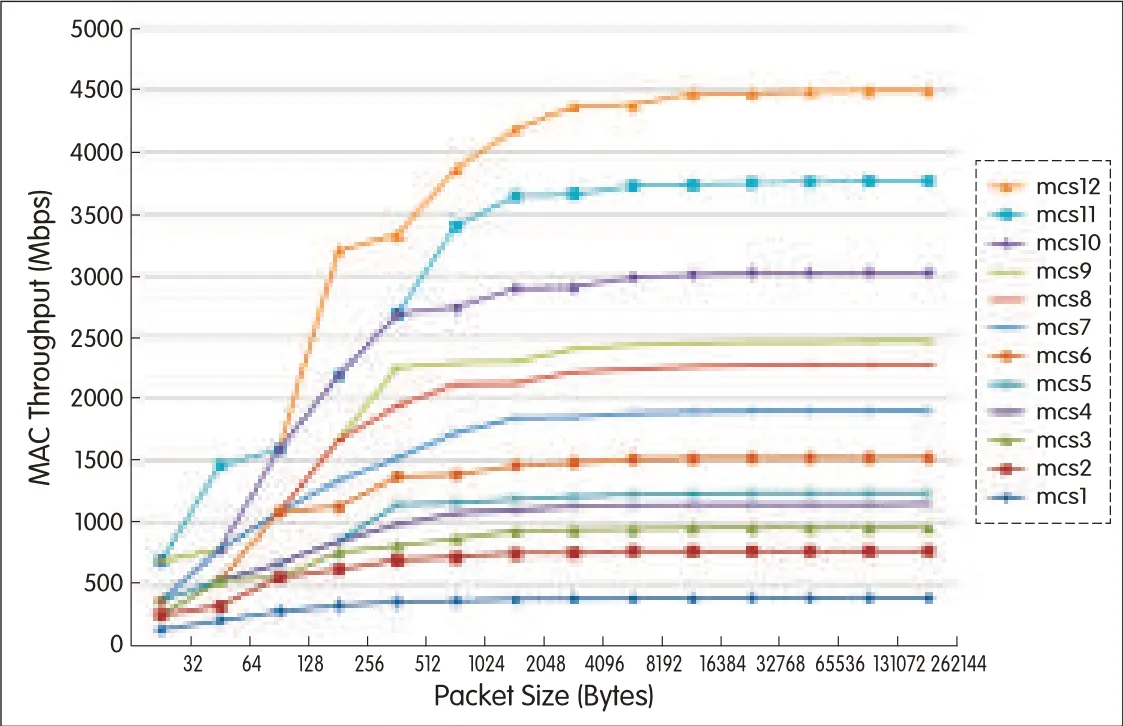
▲Figure 17.Single carrier throughput as a function of the packet size fordifferent MCSvalues for A-MPDUpackets.
- ZTE Communications的其它文章
- Millimeter Wave Communication for Cellular and Cellular-802.11 Hybrid Networks
- Millimeter Wave and Terahertz Communications:Feasibility and Challenges
- Modeling Human Blockers in Millimeter Wave Radio Links
- 60 GHz SIWSteerable Antenna Array in LTCC
- Line-of-Sight MIMOfor Next-Generation Microwave Transmission Systems
- Terabit Superchannel Transmission:ANyquist-WDM Approach

