Multi-source heterogeneous data access management framework and key technologies for electric power Internet of Things
Pengtian Guo,Kai Xiao,Xiaohui Wang,Daoxing Li
1.China Electric Power Research Institute Co.Ltd.,Beijing 100192,P.R.China
Abstract: The power Internet of Things (IoT) is a significant trend in technology and a requirement for national strategic development.With the deepening digital transformation of the power grid,China’s power system has initially built a power IoT architecture comprising a perception,network,and platform application layer.However,owing to the structural complexity of the power system,the construction of the power IoT continues to face problems such as complex access management of massive heterogeneous equipment,diverse IoT protocol access methods,high concurrency of network communications,and weak data security protection.To address these issues,this study optimizes the existing architecture of the power IoT and designs an integrated management framework for the access of multi-source heterogeneous data in the power IoT,comprising cloud,pipe,edge,and terminal parts.It further reviews and analyzes the key technologies involved in the power IoT,such as the unified management of the physical model,high concurrent access,multi-protocol access,multi-source heterogeneous data storage management,and data security control,to provide a more flexible,efficient,secure,and easy-to-use solution for multi-source heterogeneous data access in the power IoT.
Keywords: Power Internet of Things;Object model;High concurrency access;Zero trust mechanism;Multi-source heterogeneous data
0 Introduction
The term “Internet of Things” (IoT) was coined by Auto-ID Labs,which was established by the Massachusetts Institute of Technology (MIT) in 1999.Kevin Ashton,the center’s founder,proposed that the network radio frequency identification (RFID) system connects all items with the Internet through information sensing devices,such as RFID,to realize intelligent identification and management [1].At the World Summit on the Information Society (WSIS) held in Tunis in 2005,ITU formally confirmed the concept of IoT and issued the “International Telecommunication Union(ITU) Internet Reports 2005∶ The Internet of Things,”which noted that the era of IoT is coming and described the characteristics of the IoT,RFID,sensor technology,intelligent technology,nanotechnology,miniaturization technology,and other key application technologies of the IoT,as well as the challenges faced by the IoT industry [2].In July 2012,the 13th Research Group of the ITU Telecommunications Standardization Organization defined the IoT through recommendation ITU-T Y.2060 as “a global infrastructure of the information society,which provides better services through the connection of physical and virtual things based on existing and future interoperable information and communication technologies” [5].The core and foundation of the IoT is still the Internet,but its user end extends between items,greatly expanding the Internet [6].The IoT has networked and informationized the physical world of human existence,realizing the interconnection and integration of the separated physical world and information space.It has been widely utilized in industrial control,environmental monitoring,warehousing,logistics,defense,military,and other fields and has gradually become one of the focuses of the development of global science and technology strategy [3].According to the prediction of Statista,a world-famous survey and statistics portal,the number of global IoT connection equipment will reach 75.44 billion in 2025 and bring about nearly one billion dollars in market output value [4].
The world’s major economies are developing the technology layout of the IoT.In 2009,the President of the United States and business leaders held a round table meeting and proposed the concept of “smart earth” for the first time [27].Since then,the cyber-physical system(CPS),based on IoT technology,has attracted experts from enterprises and universities to participate in the development of reference frameworks and technical agreements and has continued to promote the deployment of IoT in various industries.Under the Seventh Framework Program 7(FP7),the European Union has conducted research and development on IoT through a series of projects such as IoT-A,IoT6,and open IoT,which are actively deployed in smart grids,smart cities,and smart transportation [28].The “Horizon 2020” plan proposed that IoT research should focus on sensors,architecture,identification,security,privacy,and semantic interoperability [29].In 2004,Japan proposed the u-Japan Plan to achieve connectivity between people,objects,and people.This strategy attempts to build a ubiquitous online society in which anyone can be connected at anytime,anywhere [30].During this period,the conventional designs of the IoT architecture included the networked Auto ID proposed by the MIT Auto-ID Laboratory,the IoT architecture developed by the UID Center,a nonprofit standardization organization sponsored by the University of Tokyo in Japan,the layered IoT architecture physical-net proposed by Vicaire at the University of Virginia in the United States for the management and planning of heterogeneous sensing and execution resources in a multiuser and multienvironment M2M,and other architectures developed by the European Telecommunications Standards Organization (ETSI) [31].In the Development Plan of the IoT (2016–2020) and the Three-Year Action Plan for the Construction of New Infrastructure of the IoT (2021–2023),China proposed plans to accelerate the construction of ubiquitous infrastructure,application service platforms,and data sharing service platforms for the IoT [32,33].
Power IoT is the application of IoT in the smart grid and results from the development of information and communication technology to a certain degree [8].The IoT of power systems forms a huge intelligent network between various electrical equipment of the power system and between equipment and personnel through various information-sensing devices or distributed readers,such as RFID devices,infrared sensors,global positioning systems,and laser scanners,combined with existing network,database,and middleware technologies.The IoT can effectively integrate communication and power system infrastructure resources,improve the power system informatization level and the utilization efficiency of the existing power system infrastructure,and provide important technical support for power grid generation,transmission,transformation,distribution,and consumption [7].According to the 14th Five-Year Plan and 2035 vision,State Grid Co.Ltd.will build a novel type of power system with novel energy as the primary objective of following the national strategy and making every effort to achieve carbon peaking and carbon neutrality goals.Via the construction of power IoT,the effective utilization of stock-associated terminal equipment resources,realization of the source network load of all interactions,facilitation of business synergies and data,improvement of the source network load interactive level of the power system and core links such as storage and adjustment ability,and abundant power regulation can raise the level of power grid safety while increasing power grid operation efficiency [16,23].Power IoT has developed rapidly.After more than ten years of development,the application of power IoT has established a certain foundation.For example,State Grid Co.Ltd.has connected more than 540 million terminals (sets),such as smart electric meters,in 2020,with a daily data collection increment of more than 60 TB.With the deepening of the digital transformation of the power grid,China’s electric power system has preliminarily constructed the power IoT system,comprising end,side,pipe,and cloud parts[1][15].However,compared with the requirements of digital infrastructure construction and perception capacity expansion,the construction of the power IoT is still facing the challenges of high concurrency,access,and interaction[17,18].
Given the above problems,this study designs the overall framework for multi-source heterogeneous data access in the power IoT based on the existing power IoT architecture.It analyzes its key technologies to aid the novel digital power infrastructure,improve the digital and intelligent level of the power grid,promote the transformation and enhancement of the power grid to the energy internet,and help build a clean,low-carbon,safe,and efficient energy system.
1 Framework
Presently,the industry generally divides power IoT into three layers∶ the perception,network,and platform layers[33] (Fig.1).The sensing layer comprises several sensing nodes deployed in each sensing object.A sensing network is formed through self-organization to achieve intelligent collaborative sensing,intelligent recognition,information collection and processing,and automatic control of power grid objects and the operating environment.The network layer integrates and expands different types of communication networks,such as power wireless broadband,wireless public communication networks,wireless sensor networks,and power optical transmission networks,to achieve information transmission,routing,and control between the sensing and platform layers and to provide highly reliable,safe,and large-scale data transmission services for sensing information.The platform layer utilizes a unified data center to provide information management,equipment management,and other services.It can analyze and process the perception layer’s information and data according to different business needs,supporting business applications.

Fig.1 Conventional Power IoT architecture
With the development of the power IoT,the demand for data processing and analysis on the edge is increasing.A study [10] adds an edge computing layer based on the original three-tier architecture,highlighting the computing and analysis capabilities of the edge side.Xiong K,et al.[11] provides the overall structure of the power IoT from the network design level,in combination with the characteristics of 5G communication technology.The above documents provide a reference basis for the construction and development of power IoT;however,there are still some deficiencies in the current architectural design.First,it focuses on the hierarchical mode and interaction mode of the power IoT and lacks solutions for high concurrent access to the power IoT.Second,it focuses on accessing data at the perception level and lacks the design of data fusion management.Finally,there is a lack of security management and control strategies for the overall power IoT.
This study optimizes the existing architecture of the power IoT and designs the overall framework of multisource heterogeneous data access management of the power IoT,which comprises cloud,pipe,edge,and terminal parts,based on key technologies such as unified management of the object model,high concurrency access,multi-protocol access,data fusion management,and full-link security control,as presented in Fig.2.

Fig.2 Overall framework of multi-source heterogeneous data access in power IoT
The terminal comprises various kinds of electric power terminals.The object model,based on a unified configuration,is a set of awareness and implementation control terminal units.These units primarily include the power supply,grid,user sides,and the supply chain,which involves a terminal device,the device or the state of an object measured,electric parameters,and the environment that permits the collection and measurement of data,with simple data processing,control,and communications functions.Edge refers to intelligent devices,which are capable of edge computing,deployed in the area.These devices can locally aggregate all kinds of perceptual data in a certain area and standardize the processing and uploading of collected data based on the object model.The edge computing framework is the basic platform software running on the edge IoT agent that realizes the unified and life-cycle management of all types of terminals and application services by the IoT management platform.A software-defined terminal agent is constructed based on an edge-computing framework that realizes software and hardware function decoupling,software function portability,and reconfiguration and supports the application service of object association once developed and utilized.Tube is the data transmission channel between edge and cloud,which comprises a remote communication network.Cloud is a cloud-based IoT management platform that provides unified support for power IoT applications.Pipes refer to various remote communication networks,including power optical fibers,wireless private networks,and wireless public networks.Load balancing and traffic optimization strategies were configured on the pipe side to achieve efficient and low-delay data transmission.Cloud refers to the IoT management platform,data center,and technology center deployed in the cloud,as well as the upper-layer power service applications they support.The IoT management platform provides multi-protocol parsing and adaptation,unified object model management,device management,temporary data storage,and other functions.The summarized relational,time-series,and graph data are uploaded to the data center for persistent storage after processing.The technology center provides artificial intelligence,big data analysis,and other services.It also performs fusion modeling and analysis on multi-source heterogeneous data in the data center,supporting upperlevel power business applications.
2 Key technology
2.1 Unified object model management technology
The underlying foundation of the IoT is physical devices,including physical and information communication terminals,which have a certain degree of perception,communication,computing,and control execution capabilities [26].One of the core goals of the IoT is to digitally describe these physical entities.The conventional method involves configuring access management strategies for different types of physical devices on the IoT management platform and controlling them by category.However,there are many kinds of physical terminals for power IoT,and even the same type of equipment may be difficult to utilize directly in conventional methods for management because of differences between different manufacturers.The object model is a data model defined for devices and other entities.It primarily realizes the digitalization of devices in the physical world and describes the functions of entities that facilitate digital representation in the cloud.The object model description is based on the semantic IoT standard,establishes the ontology model of the object,and provides a standardized object analytical system and integrated management methods.It mainly includes three dimensions∶attributes (what is real),services (what entities can do),and events (what entities can provide information) [19-21].However,the field of power IoT involves a significant number of terminal devices and data model descriptions with different structures that lack unified standard constraints.To ensure compatibility with different devices,the object model should follow industry standards and specifications,extract commonalities from various devices and sensors,define unified attributes,services,and events for them,and serve as a unified basic template for describing and managing various devices and sensors.In addition,configuration management can be performed with gateways or edge IoT agents for some old devices in power scenarios that cannot be configured directly with physical models.Taking an energy meter as an example,the configuration results of the physical model are presented in Tables 1–3.

Table 2 Electric meter message domain

Table 3 Electric meter service domain
After the configuration is completed,the object model is delivered to the edge-computing node in a JSON file through the IoT management platform,and the edge-and side-object models are updated and synchronized.The side devices are connected to other side devices,corresponding to a unique object model based on the defined object model.
The object model is related to the standardization of IoT facilities.However,the field of power IoT involves a significant number of terminal devices and data model descriptions with different structures,as well as a lack of unified standard constraints.In addition,many old and existing devices are involved in power scenarios;therefore,it is difficult to configure an object model directly.Configuration management must be performed through a gateway or edge object connection agent.Device-side research and development (R&D) and cloud development were decoupled using the object model.Based on the object model,the terminal device entity can be digitally described,and device virtualization can be performed in the cloud,as demonstrated in Fig.3.

Fig.3 Application development framework of IoT platform based on the object model
2.2 Multi-protocol access technology
During the construction of power IoT,protocol adaptation serves as the key point.However,solving the problem of connecting stock equipment to the platform is difficult [4].Presently,the IoT management platform generally only supports the mainstream protocols of the IoT,such as MQTT and CoAP.However,several types of power-system equipment have different transmission protocols.For example,the MQTT protocol is directly used by the fusion terminal to access the IoT management platform;however,DL/T698.45,IEC104,and other proprietary power protocols are used for the purchase and distribution of inventory equipment that cannot be directly connected to the IoT platform.The conventional method typically stipulates a transmission protocol and formulates a protocol resolution strategy before the IOT management platform accesses the equipment.However,this method has two disadvantages.First,it is necessary to formulate the corresponding protocol resolution strategy for different equipment,which requires operation and maintenance engineers to configure the strategy,consuming a lot of human resources.Second,protocol analysis on the IoT management platform also increases the computing burden of the platform server,which may lead to high latency under high concurrent access conditions.
As an emerging technology,edge computing migrates computing and data storage tasks from the cloud to a location closer to the device to reduce latency and improve response speed and data security.Improving the edgecomputing capability provides a novel solution for multiprotocol resolution.Protocol conversion modules are deployed in edge agents or device gateways to implement protocol adaptation,data resolution,and forwarding services for different terminals,including data decryption,protocol conversion,and data processing.Conventional power protocols,such as 698.45,1376.1,376.1,101,and 104,are included in the protocol library and analyzed according to the protocol rules,message content,and business data using MQTT,CoAP,and other mainstream IoT protocols.Other protocols are automatically parsed through visual parameter configuration and parameter encapsulation.Based on the microservice architecture,the horizontal service expansion of mass terminal access unifies the multi-protocol access channels of different business departments.Deploying protocol conversion modules at the edge can allow adaptation to various protocols,enable better compatibility with device and sensor diversity,and make it easier for the system to adapt to constantly changing technological environments and device requirements.This can also reduce the computational burden on IoT management platforms and improve their processing performance.The multiprotocol adaptation strategy is illustrated in Fig.4.
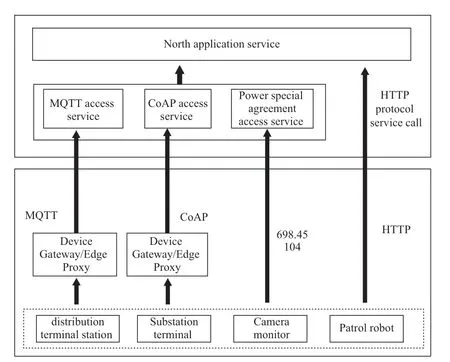
Fig.4 Multi-protocol adaptation strategy
2.3 High concurrency access technology
There are hundreds of millions of terminal devices in power IoT.Even if the data are uploaded in batches,they will reach more than ten million levels of concurrency in peak hours.High-concurrency access technology is based on load balancing,traffic optimization,and other strategies to achieve the optimal selection of network links and efficient,balanced utilization of cloud resources [25].Load balancing is essential in highly concurrent and readily available systems [22].The goal is to distribute the network traffic evenly to multiple servers to improve the system’s overall response speed and availability.To cope with the exponential growth in data and high concurrent access,large data centers must deploy load-balancing modules to handle large external or internal workloads and improve resource utilization [24].
Presently,the load-balancing strategy of the IoT management platform is typically to deploy load-balancing software such as NGINX in the access server to achieve load balancing in seven layers,namely,the application layer.This method can solve the concurrent access requirements of 100,000 to one million levels;however,it is difficult to support high concurrent access requirements of more than 10 million levels.
Therefore,this study proposed a load-balancing strategy based on four and seven layers of IoT access to achieve a high concurrency of over ten million levels.Four-layer load balancing is based on transport layer protocols,such as TCP and UDP.It distributes traffic to different servers based on the client’s IP address and port number.Its main advantage is its fast processing speed,as it focuses only on lower-level network information.Four-layer load-balancing is suitable for scenarios with strict latency requirements.
Seven-layer load balancing is based on application-layer protocols such as HTTP and HTTPS.It can distribute traffic to different servers based on the request content,such as URLs,header information,and message bodies.Because it focuses on higher-level network information,sevenlayer load balancing can achieve more complex distribution strategies.A combination of four-and seven-layer loadbalancing strategies can achieve more efficient and flexible traffic distribution in IoT access.For example,a four-layer load balancer can handle several low-latency requests,whereas complex application-level requests can be routed to a seven-layer load balancer for processing.This improves the system’s performance and meets the processing requirements of complex requests.Specifically,the Layer 4 switch provides a unified IP access address for the outside world.The terminal device and edge IoT agent do not need to understand the real IP address corresponding to each server on the cloud platform.The external data traffic received by the cloud platform must pass through the Layer 4 switch,which is responsible for forwarding the request of the terminal device and edge IoT agent to the server and then establishing a TCP connection between the terminal device,edge IoT agent,and server.In NAT mode,when Layer 4 exchanges and the device schedules access requests,the destination IP address is first converted,and then the access request is forwarded to each front-end access server in the back end.Therefore,the four-layer load balancing can unify the access terminal and edge IoT agent equipment and forward the upstream information of the equipment to the software-defined access agent according to the established load-balancing strategy.
2.4 Multi-source heterogeneous data storage management technology
Power IoT data have reached the petabyte scale,which implies that the power industry must cope with the challenges of a large amount of data and various data formats.The rate span of power data generation is large[13],including millisecond wide-area vector measurement,real-time data,second-level steady state monitoring data,minute-level micro-meteorological data,hour-level operation ticket circulation data,and longer-time cycle equipment experimental data.Many data sources and complex interaction methods exist,such as Web services,special power protocols,and special file formats.There are many types of data,such as real-time,historical,text,multimedia,time-series,structured,semi-structured,and unstructured data.The lack of effective management of various types of data in the power grid and the difficulty in forming effective information from isolated data have significantly hindered the operation management and scientific decision-making of the power grid;thus,the development requirements of the future power grid can no longer be met [12].
In the field of big data storage,the Hadoop development team developed Google’s non-open-source Google File System (GFS) and implemented the open-source Hadoop Distributed File System (HDFS) of the GFS.HDFS distributes data access and storage among many servers through an efficient distributed algorithm.It can reliably store multiple backups while distributing access to all servers in the cluster.The GFS is a scalable distributed file system that manages large-scale,distributed dataintensive computing.It utilizes inexpensive commercial hardware to build a system and provides fault-tolerant and high-performance services to many users.Regarding data management,the most famous is the Bigtable data management technology proposed by Google.Bigtable is a distributed storage system that is designed to manage structured data.This data can be expanded to a very large scale,such as petabytes of data on thousands of commercial servers.The MapReduce programming mode is primarily utilized in big-data computing.MapReduce is a programming model and an efficient task-scheduling model.MapReduce is suitable for cloud computing and has good performance in multi-core and multi-processor,cellprocessor,and heterogeneous clusters.This programming mode applies only to writing programs loosely coupled within a task,which can be highly parallelized.
The main data sources of the power grid include business management data from the power grid application system,Power grid operation monitoring data,enterprise external economic policy,social networks,and meteorological data,which are characterized by different sources,complex types,different capacities,and high levels of security management and control.With master data and metadata management at the core,building a substantial,panoramic data governance technical architecture to control master data and metadata,data quality,structure,security,architecture,and management is important.
(1) Master data and metadata management
Master data are the core business data of the power information system and typical long-term data utilized across multiple applications.Master data are mainly developed internally and extracted from unstructured data that have been analyzed or unexplored.Seamlessly integrating unstructured content metadata with conventional metadata management must thus be adopted.The main management content of the master data and metadata are illustrated in Fig.5.

Fig.5 Master data and metadata management content allocation
The metadata management and master data management architectures need to be adjusted owing to the introduction of big data technology.For the proposed summary architecture of master data and metadata management in the power IoT big data environment,metadata and master data acquisition,storage,and management applications are based on the data architecture,technical architecture,and application architecture of big data.The ESB data flow is presented in Fig.6.
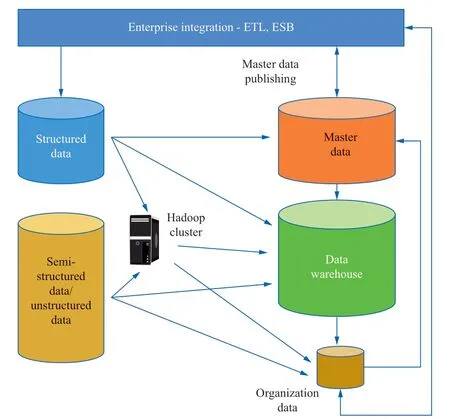
Fig.6 ESB data flow
(2) Data life cycle management
Data life cycle management refers to the management of data assets.Management covers rules,policies,processes,roles,and responsibilities that are used to guide overall management.Management guarantees that data are accurate,consistent,complete,available,and safe.Data strategy and standards must be updated owing to the introduction of unstructured and diverse data sources.Business data ownership has also been redefined owing to the introduction of novel or external data sources.Thus,the corresponding data workflow is affected.The master data management program will eventually be required to manage the relationship between internal and external data.Data go through a cycle of creation and modification,replication and distribution,protection and recovery,archiving and recall,and final deletion.At all stages of the data lifecycle,data must be stored,protected,and accessed in full accordance with business requirements.Data are enterprise assets,and their life cycles are often longer than those of hardware equipment and applications.Data lifecycle management must be performed from cost control,information management and tracking,and data security perspectives.
(3) Data quality management
Data quality refers to the data’s ability to meet an organization’s business,system,and technical requirements.Data quality is typically described according to integrity,timeliness,accuracy,consistency,and relevance.Data quality in big data environments is driven by the instances of utilization.Applications have different expectations for data quality.For example,clickstream analysis and intrusion detection require different levels of accuracy.The rules,policies,and cleaning standards of data quality must be reevaluated in this environment.
(4) Data structure
The data structure describes the internal organization of the data.It includes multiple levels of data,ranging from interdisciplinary data models to independent systems.The impact of the data structure in a big data environment is primarily caused by data diversity.Data classification standards and logical data models must adapt to unstructured data content and the process of extracting structured information from unstructured data.
(5) Data security management
Data security is a process and technology that ensures that data are not accessed,browsed,edited,or deleted without authorization.With the integration of diverse data sources,appropriate compliance and security policies must be analyzed and standardized to comply with local,national,and international regulations.This includes ①data access security∶ host system access authorization,database storage at different security levels,and user division for different applications;② data storage security∶ regular full backup and real-time incremental backup that can support rapid data recovery;and ③data security audit∶ file,network,and other access log records,independently stored logs,and regularly audited sensitive data operations.
(6) Data service management
Data service management provides unified access to various data services through service interfaces.By adopting a standardized interface access protocol and unified control of user and data access to ensure data securitym,the service can be expanded and customized to meet future data access requirements.
2.5 Security management and control technology of power IoT
The information stored in the power IoT is massive,distributed,diverse,real-time,dynamic,and interactive [17].The network boundary on the terminal side will become fuzzy and complex.The one-to-one access between data and users in the conventional public key encryption scheme cannot meet the requirements of the complex power IoT system.The zero-trust mechanism was first proposed by Kindervag.Its core idea is that,by default,person,device,or system inside or outside the network should not be trusted.It must be based on the trust foundation of authentication and the authorization of heavy access control.After years of practice,Google released BeyondCorp,a zero-trust architecture,in 2014,which was gradually recognized by the industry.Zero trust subverts the access control paradigm and guides the security architecture from network to identity centricity.Its essential demand is identity-centered access control [18].
The construction of power IoT is based on the construction of a unified identity,with the zero-trust network security architecture as a reference,to conduct unified identity management and achieve identity authentication between power IoT devices and services.Dynamic permission control is performed based on the environmental and access attributes of the equipment to achieve continuous trust evaluation of each access subject of the power IoT,dynamic access control,and trusted security access.Reliable interconnection,security interaction,intelligent defense,and dynamic prevention and control are achieved through the security protection of the “cloud management edge end”power IoT architecture.The security protection architecture of power IoT based on a zero-trust mechanism is illustrated in Fig.7.
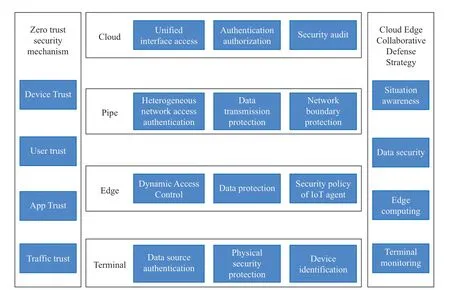
Fig.7 Data access flow of power IoT based on multi-layer load balancing
Establishing a unified identification library of the power IoT at the end and side provides basic key identification for business and ensures the standardization of business system subjects.Based on the unified object model,a unified identification system for all entity objects is established to provide a unified identification technology and an interoperability basis for identity and access control management.After the realization of comprehensive identification,the user,device,and application are fully identified to complete centralized identity governance.Authentication is continuous through the device list service,and trust is evaluated through continuous authentication.Through a dynamic calculation of risk and trust,application access is blocked and audited,the status of the power IoT terminal is continuously monitored,and the corresponding access control strategy is adjusted.The application’s access to the policy center is continuously monitored,and the access log output is sent to the analysis platform for risk assessment.Big data analysis and artificial intelligence technology are utilized to analyze risks,support risk quantification,realize monitoring and auditing of the application’s access to the strategy center,realize dynamic perception and intelligent analysis of power IoT security scenarios,respond timely to attacks,and ensure safe and stable operation of the power IoT system.
3 Application prospect
The proposed framework was applied and demonstrated in the Tianjin Binhai New Area.Based on the power IoT architecture,we built the connection management of the distributed and asynchronous architecture,the unified multiterritory model of things management,the edge cloud collaborative collection and control service components,and integrated the deployment with the existing Tianjin IoT management platform,as illustrated in Fig.8.The platform provides multi-protocol high concurrent access to IoT terminals,unified modeling services for power system models,and other capabilities,supporting the IoT management platform to achieve 100 million-level equipment access and 10 millionlevel parallel connections and achieving unified and efficient access control of massive heterogeneous power IoT terminals.
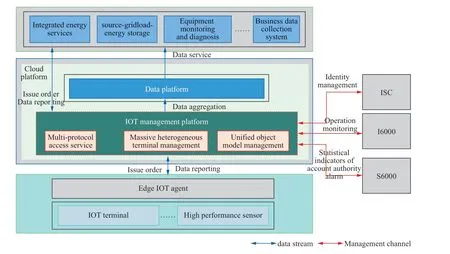
Fig.8 Tianjin Binhai power IoT architecture
Based on the IoT management platform,the intelligent perception and diagnosis module of transmission,transformation,and distribution equipment faults was built,enabling status assessment,fault diagnosis,and visual display of transmission,transformation,and distribution equipment.The intelligent diagnosis of 25 typical faults of seven types of transmission,transformation,and distribution equipment was also achieved.The accuracy of the comprehensive diagnosis of typical faults reached over 88%,achieving accurate identification and tight control of the status of transmission and distribution equipment in coastal demonstration areas.This is illustrated in Fig.9.

Fig.9 Fault effect of transmission,transformation,and distribution equipment
4 Conclusion
The power IoT represents a current development trend that aligns with the demands of strategic national development.IoT technology enhances intelligent management and deepens the information perception of power grid systems.However,the construction of power IoT still faces challenges such as managing massive heterogeneous IoT equipment,accommodating diverse protocol access methods,handling high concurrency in network communication,and improving conventional security protection.In response to these issues,this study designed a comprehensive framework for managing access to multi-source heterogeneous data in power IoT based on the existing power IoT architecture.It also examined the key technologies integral to this framework.Implementing the power IoT in the Tianjin Binhai Area demonstrates these concepts in practice,providing a reference for future work on the power IoT.
Acknowledgments
This work was supported by the National Key Research and Development Program of China (grant number 2019YFE0123600).
Declaration of Competing Interest
The authors have no conflicts of interest to declare.
 Global Energy Interconnection2024年1期
Global Energy Interconnection2024年1期
- Global Energy Interconnection的其它文章
- A Special Issue “Planning and Optimal Operation of New-Type Power System” of Global Energy Interconnection
- Localization method of subsynchronous oscillation source based on high-resolution time-frequency distribution image and CNN
- Robust optimal dispatch strategy of integrated energy system considering CHP-P2G-CCS
- Stochastic programming based coordinated expansion planning of generation,transmission,demand side resources,and energy storage considering the DC transmission system
- Optimal dispatching strategy for residential demand response considering load participation
- Optimal scheduling of a township integrated-energy system using the adjustable heat-electricity ratio model
