Anti-Jamming and Anti-Eavesdropping in A2G Communication System with Jittering UAV
Huici Wu ,Yang Wen ,Xiaofeng Tao ,Jin Xu
1 National Engineering Research Center of Mobile Network Technologies,Beijing University of Posts and Telecommunications,Beijing 100876,China
2 State Grid Hunan Electric Power Information and Communication Corporation,Changsha 410118,China
*The corresponding author,email: dailywu@bupt.edu.cn
Abstract: This paper focuses on anti-jamming and anti-eavesdropping problem in air-to-ground (A2G)communication networks considering the impact of body jitter of unmanned aerial vehicle (UAV).A full-duplex(FD)active ground eavesdropper launches jamming attack while eavesdropping to stimulate the legitimate transmitter(i.e.,UAV)to increase its transmission power.The legitimate transmitter’s objective is to against the simultaneous wiretapping and jamming with a robust and power-efficient transmission scheme.The active eavesdropper aims to minimize the system secrecy rate.To study the interaction between the legitimate transmitter and the active eavesdropper,a non-cooperative game framework is formulated.Detailed,considering the impact of UAV jitter on antenna array response and secrecy performance,we first investigate the UAV’s transmission power minimization problem for the worst scenario with minimum legitimate data rate and maximum eavesdropping data rate under UAV jitter.Then,the active eavesdropper’s secrecy rate minimization problem with the worst scenario is investigated by optimizing its jamming strategy.Nash equilibrium is proved to be existed and obtained with the proposed iterative algorithm.Finally,extensive numerical results are provided to evaluate the system secrecy performance and to show the secrecy performance gains of the proposed method.
Keywords: UAV jitter;A2G communication;active eavesdropper;non-cooperative game
I.INTRODUCTION
Due to the Line-of-Sight (LoS) links of aerial communications,unmanned aerial vehicle(UAV)communications are much more vulnerable to attacks than terrestrial communication systems.Among all kinds of wireless attacks(such as tampering,counterfeiting,Deny of Service,and eavesdropping,etc.),eavesdropping attack,especially active eavesdropping attack,is one of the most critical attacks that can hardly be countered.Full-duplex (FD) technology,widely recognized as one of the promising technique in improving spectral efficiency for future wireless networks[1],facilitates adversaries to launch active eavesdropping attacks by simultaneously transmitting jamming signals while eavesdropping[2–5].It can not only hinder legitimate communication but also wiretap confidential information,which further challenges secure UAV communications[6].Thus,anti-active eavesdropping mechanisms are imminently required for the secure UAV communication.
Recently,game theoretic approaches are widely adopted [7–9] to study complex interactions between the legitimate side and the active attacker in secure UAV communication system.In addition,UAV trajectory design has also become a promising approach to mitigate active eavesdropping [6].However,trajectory design has been widely studied to exploit the advantages of flexible mobility while the jitter of UAV platform has rarely been studied.Existing literatures on secure UAV communications either assume perfect channel station information (CSI) [10],[11],or unknown eavesdropper’s location [12],[13],which ignores the unique jitter feature of the UAV platform.Different from terrestrial communication infrastructures,UAV communication platform is susceptible to unavoidable body jitter,leading to non-negligible vibrations to the angular movements[14–16].Since the jitter of UAV platform has non-negligible negative impacts on estimation of channel information,angle of departure (AOD),and angle of arrival (AOA),which further causes instability of antenna beams,it is critically important to study robust and efficient air-toground (A2G) secure transmissions considering the impact of UAV jitter.In this paper,we focus on the impact of jitter on the A2G communications and consider the A2G communication scenario with a rotor UAV hovering at a fixed position.In this regard,we have done a preliminary investigation on the robust secure transmission considering the impact of UAV jitter in A2G passive eavesdropping scenarios[17].Therefore,it motivates us to further investigate the robust anti-active eavesdropping mechanism in the jittering UAV communication system.
In this paper,we investigate the anti-jamming and anti-eavesdropping problem in the A2G active eavesdropping system considering the impact of UAV jitter.By modeling UAV jitter on the antenna array response and secrecy performance,the achievable data rate of the legitimate channel and eavesdropping channel are obtained.The active FD-eavesdropper intends to decrease the system secrecy rate by launching jamming attacks simultaneously with eavesdropping attacks.Facing the active FD-eavesdropper,the UAVenabled base station(BS)has to optimize its confidential signal beam and artificial noise(AN)signal beam under UAV jitter to achieve a robust beamformer design against the active eavesdropper.The main contribution of this paper can be summarized as follows.
• A non-cooperative game model is established to study the strategy design and interactions between the active FD-eavesdropper and the legitimate UAV-enabled BS.Under the constraint of the worst scenario with minimum legitimate data rate and maximum eavesdropping data rate,the objective of UAV-enabled BS is to minimize its transmission power by optimizing the confidential information signal beam and AN signal beam.The eavesdropper’s target is to minimize the secrecy rate of the worst scenario with minimum jamming power by optimizing its jamming beam.
• The existence of Nash equilibrium is proved for the formulated non-cooperative game.For the UAV-enabled BS’s problem,the optimal beamforming design is derived with given jamming power.To solve the non-convex optimization problem,S-procedure and semi-definite programming (SDP) relaxation are applied to derive the optimal confidential signal beam vector and AN beam vector of the UAV-enabled BS.To solve eavesdropper’s non-convex optimization problem,S-procedure and successive convex approximation (SCA) technique are applied to approximately obtain the optimal jamming strategy for the active eavesdropper.Since the optimal solutions of UAV-enabled BS and eavesdropper are closely dependent with each other,a corresponding iterative algorithm is proposed to obtain the optimal solutions.
• Finally,numerical results are provided to study the influence of the system parameters.Simulations with maximum ratio transmission (MRT)scheme and zero-forcing (ZF) AN scheme are also provided as baseline schemes.Results show that compared to the baseline schemes,less transmission power is needed for the UAV-enabled BS while more jamming power is needed for the active eavesdropper with the proposed model.
II.RELATED WORKS
Recently,implementing full-duplex techniques at the adversary has raised significant research concerns.Unlike a passive eavesdropper or jammer,an active FD eavesdropper that acts as both an eavesdropper and a jammer aims to improve the eavesdropping attack performance through launching jamming attacks,which can further challenge the secure communication.For the threat of the active FD eavesdropper,multiple antennas [18] and cooperative communication mechanism[19]have been exploited against both jamming and eavesdropping attacks.In [2],the authors investigate the optimal beamforming strategies of an active FD eavesdropper to minimize the system secrecy rate.In [3–5],the authors investigate the secure transmission problem in the presence of an active eavesdropper in the context of game theory.In [3],the authors formulate the power decision processes of the transmitter-receiver pair against the full-duplex eavesdropping attack as a two-player noncooperative game.Meanwhile,a switch strategy for the active eavesdropper is provided to determine its optimal mode to maximize the utility.The Stackelberg game,a classical and essential game in game theory,is applied to study the interaction behaviors between defenders and attackers in[4],[5].In[20],a three-stage Stackelberg game approach is proposed to model the competitions among the transmitter,relays,and the FD eavesdropper.
Despite the majority of efforts devoted to secure communication in UAV systems,including antieavesdropping transmission problem[21–24]and antijamming transmission problem [25–27],the security issue of coexistence of eavesdropping and jamming attack in UAV communication systems has relatively few works.In[28],UAV-aided secure communication in the presence of an active eavesdropper performing malicious jamming and eavesdropping attack simultaneously has been considered.In this paper,the optimal power allocation factor and the operating height of UAV is obtained.In[29],the authors consider a novel UAV communication system with both the uplink and downlink transmissions,where UAV trajectory and transmit power allocation are jointly optimized to fight against FD active eavesdropper and maximize the average secrecy rates.The work in [30] proposes an AN-aided secure transmission scheme in a FD UAV relaying network.To reduce the online computational complexity,some model-free reinforcement learningbased algorithms are proposed to maximize the average system secrecy rate by finding the optimal UAV trajectory and power allocation intelligently.Moreover,game theory combined with machine learning has been applied in the literature to counter the active attacker [7–9].Specifically,in [7],prospect theory is applied to formulate a subjective smart attack game for the UAV transmission.In [8],a Q-learning based power allocation is proposed for UAV secure communication against multiple UAV active eavesdroppers.With imperfect CSI in UAV communication networks,a non-cooperative game is formulated in[9].
Note that the above works do not take the unique jitter feature of UAV into consideration in the UAVenabled secure transmission except for our previous work[17].In[17],the authors investigate the energysaving and robust secure communication in the A2G wiretap system.Considering the impact of the UAV jitter,joint optimization of beamforming scheme over confidential information signal and AN signal is studied with the objective of transmission power minimization in[17].
Different from our previous work in[17],in this paper,we investigate the problems of secure transmission with an active FD-eavesdropper in the jittering UAV communication system.We formulate the antijamming and anti-eavesdropping transmission problem as a non-cooperative game.Besides,the unique feature of UAV jitter is considered simultaneously.
III.SYSTEM MODEL
We consider a downlink A2G wiretap and jamming system which consists of a UAV-enabled BS,a legitimate ground receiver (B),and an active FDeavesdropper (E),as shown in Figure 1.The active FD-eavesdropper transmits jamming signals to intercept the legitimate transmission while wiretaps the confidential messages of the legitimate receiver with full-duplex technique.Both the UAV-enabled BS and the FD-eavesdropper are equipped with uniform linear arrays (ULAs).The number of antennas at the UAVenabled BS and FD-eavesdropper areNUandNE,respectively.However,the legitimate ground receiver is equipped with a single antenna due to hardware limitations [17].The transmit and receive antennas at FD-eavesdropper are separately located and each antenna is equipped with a single radio frequency chain[31].antennas are used for eavesdropping andantennas are used for sending jamming signals,We consider that the UAV-enabled BS is a rotor UAV hovering at a fixed position.Therefore,a three-dimensional(3D)Cartesian coordinate system is adopted,where the coordinations of the UAV,legitimate ground receiver and the eavesdropper are denoted by(xU,yU,H0),(xB,yB,0)and(xE,yE,0),respectively.
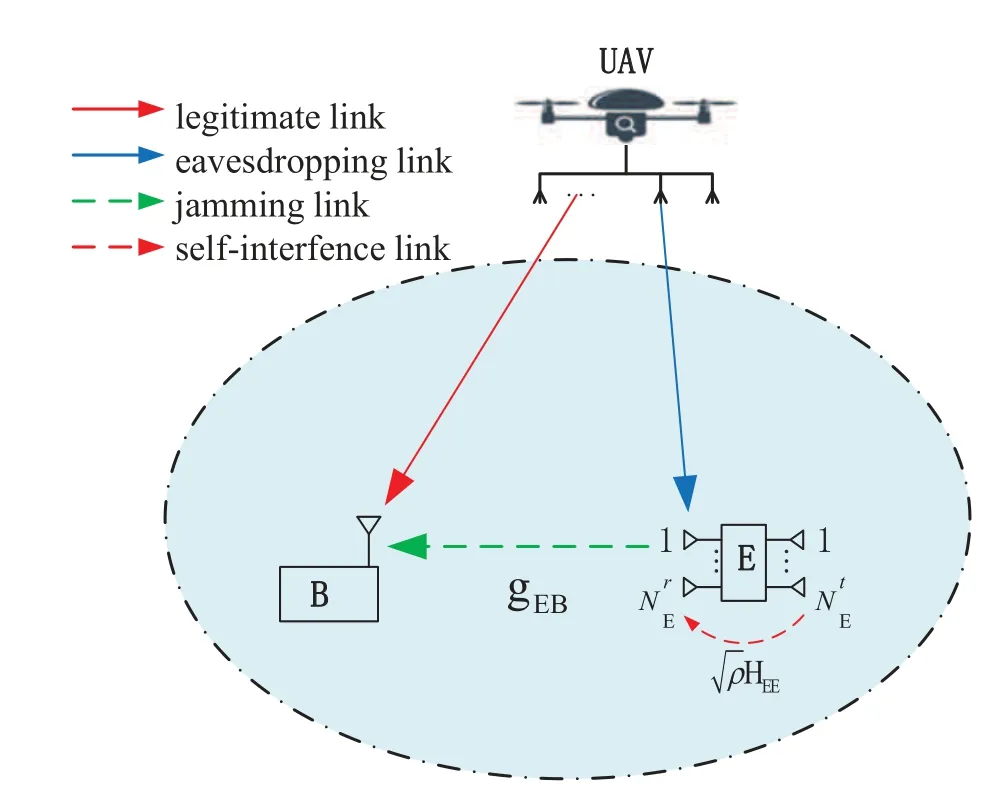
Figure 1.A2G secure communication model.
3.1 Channel Model
Denote hB,HE,and gEBas 1×NUchannel vector of the UAV-B channel,×NUchannel matrix of UAVE channel,and 1×channel vector of E-B channel,respectively.Block Rayleigh fading channel is considered for the ground-to-ground channel vector gEB.The entries of gEBare independent and identically distributed (i.i.d.) zero-mean circularly symmetric complex Gaussian random variables.Effective residual self-interference channel is modeled with(as in [28],[32]),where HEE∈denotes the channel matrix of the residual self-interference link,whose entries are i.i.d.zero-mean complex Gaussian random variables with unit variance.The effect of self-interference cancellation is parameterized by the factorρwith 0≤ρ≤1.The A2G channel model follows free-space path loss and small-scale fading effects as in[33].hBand HEcan be expressed as
and
wheregi=,i∈{B,E}is the path loss.α>2 is the path loss exponent,andβ0is the channel power gain at the reference distance 1 meter.diis the distance of the transceiver link.Rician fading model is adopted for small scale fading of the A2G channel.DenoteKi,i∈{B,E}as the Rician factor for the UAV-B and UAV-E channel,respectively.The channel responseandcan be written as
and
where hB,L(HE,L) is the LoS deterministic component ofhB,N(HE,N) is the non-LoS(NLoS) component of hB(HE).The entities of hB,N(HE,N) follow complex Gaussian distributionCN(0,1).Since the legitimate ground receiver is equipped with a single antenna,hB,Lis given by
wherebUis the antenna separation of ULA at UAV.λcrepresents the wavelength of the carrier center frequency.LetφBandθBdenote the horizontal and vertical angle of departure (AOD) from the antenna array at UAV to the legitimate receiver,respectively.We haveuB=cosφBsinθB.Similarly,HE,Lis given by HE,L=,whereis the array response at FD-eavesdropper,which is given by
vE=cosϕEsinϑE,whileϕEandϑEdenote the horizontal and vertical angle-of-arrival elevation (AOA)from the antenna array at UAV to FD-eavesdropper.bEis the antenna element spacing at the FD-eavesdropper.is the array response at UAV,which is given by
uE=cosφEsinθE,whereϕEandϑEdenote the horizontal and vertical AOD from the antenna array at UAV to the attacker,respectively.
3.2 Jitter Model of UAV Platform
In this paper,we focus on the impact of jitter on the A2G communications.Similar to [17],the impact of UAV jitter has little effect on the antenna array response at the ground receiver.Thus,we only consider the impact of UAV jitter on the antenna array response at UAV.The AOD estimation errors caused by UAV jitter can be modeled as bounded error forms,which are deterministic models [15].Specifically,the bounded AOD error model for actual vertical AODsθiand horizontal AODsφiis given as
Note that hB,Lis a nonlinear function with respect to ∆θiand ∆φi.To do further analysis,we approximate hB,Lby employing the following first order Taylor expansion as in[15].
For notation convenience,we define
As a result,(1)(2)can be equivalently rewritten as
3.3 Transmit Signals and Received SINR
The UAV-enabled BS transmits AN signals in conjunction with information signals.The transmit signal x∈CNU×1can be expressed as
wheres∈C1×1and w∈CNU×1are the information signal symbol and the corresponding precoding vector,respectively.We assume without loss of generally that E(ss†)=1.v∈CNU×1is the AN signal vector with v∼CN(0,V).The FD-eavesdropper transmits malicious jamming signal xE∈to deteriorate the quality of the received signals at the legitimate receiver.
The received signal at the legitimate receiver and the FD-eavesdropper can be expressed as
and
The eavesdropping rate of the UAV-E channel is calculated asRE=log2(1+γE),where the SINRγEis given by
IV.GAME-BASED PROBLEM FORMULATION
Considering the fact that the stainability and performance of UAV-enabled communication systems are fundamentally limited by the onboard energy of UAVs,it is evident that the UAV communication platform has to balance the tradeoff between the secrecy quality and the energy consumption.Therefore,in this paper,we consider that the objective of UAVenabled BS is to perform power-efficient transmissions with security concerns while the objective of the FD-eavesdropper is to deteriorate the system secrecy performance with minimum jamming power after observing strategy selections of UAV-enabled BS.
With the above considerations,we first formulate this problem using a non-cooperative game.Subsequently,the Nash equilibrium for the proposed game is defined and proved to exist.We derive the optimized information and AN signal vectors for the UAV-enabled BS and jamming vector for the FDeavesdropper successively.
4.1 Anti-Jamming and Anti-Eavesdropping Problem
For the UAV-enabled BS,it aims to minimize its transmission power while ensuring the secure transmission of the confidential messages.A transmission power minimization problem is formulated by optimizing the information signal vector and AN signal vector.The UAV’s utility function is defined as the total power consumption,i.e.,
Based on the bounded AOD error model,security performance of the worst scenario under UAV jitter is considered,i.e.,the minimum legitimate data rate of the UAV-B channel and the maximum eavesdropping data rate of the UAV-E channel are constraint.Thus,the objective of UAV-enabled BS is to solve the following problem(P1)with an optimal power allocation.
wherePthis the maximum transmission power of the UAV-enabled BS.(23b)limits the maximum transmission power.(23c) is imposed such that for a given AOD uncertainty set ΩB,the minimum data rate required by legitimate receiver is aboveηB.Constraint(23d) ensures the maximum tolerable eavesdropping data rate is less thanηE(0<ηE<ηB).Constraints(23c)and(23d)together guarantee the lower bound of secrecy rate between the UAV and legitimate receiver is aboveηB-ηE.Obviously,problem inP1 is nonconvex due to the constraints(23c)and(23d)are nonconvex.
4.2 Jamming and Eavesdropping Problem
From the FD-eavesdropper’s perspective,it attempts to minimize the system secrecy rate of the worst scenario.The worst-scenario secrecy rate under UAV jitter is expressed as
The active FD-eavesdropper aims to minimizeRSwith the least power consumption.Thus,the utility function of active FD-eavesdropper is given by
whereµis the coefficient for power price.The first item of(25)is the profit of the FD-eavesdropper.The second item is defined as the cost for jamming.When the price coefficientµis small,the FD-eavesdropper focuses more on the decrease of the system security performance,i.e.,the FD-eavesdropper can tolerate more power consumption in order to achieve greater information wiretapping.When the value ofµis set to a large value,the FD-eavesdropper focuses more on the power consumption,i.e.,the FDeavesdropper cares more about power consumption compared with information wiretapping.As a result,the FD-eavesdropper’s problem is defined as
where(26b)and(26c)are the eavesdropper’s jamming power constraints.
So far,problemsP1 andP2 form a non-cooperative game for the A2G secure communication with an active eavesdropper.
4.3 Definition and Existence of Nash Equilibrium
The Nash equilibrium is defined as an optimal response set where none of the game players,i.e.,the UAV-enabled BS or active FD-eavesdropper,can further acquire utility improvement by changing its strategy unilaterally.Therefore,the Nash equilibrium in our proposed game model formed byP1 andP2 can be defined as follows.
Definition 1.DenotebytheNashequilibriumoftheformulatedgame,thenforanyQw,Qv,QE,thereexists
According to the definition of Nash equilibrium,it is proved that there exists a unique Nash equilibrium following [34],[35].Also,according to [36],Nash equilibrium can be decomposed into finding the best response strategy for the UAV-enabled BS and eavesdropper.In the following subsection,we will study the Nash equilibrium and solve the problemP1 of Eq.(23)and problemP2 of Eq.(26).
V.SOLUTION OF THE FORMULATED NON-COOPERATIVE GAME
5.1 Solutions of Nash Equilibrium
Due to the sequential game structure,we will analyze Nash equilibrium from two sides,respectively.Firstly,for fixed FD-eavesdropper’s jamming power,the best response of the UAV-enabled BS can be obtained by solving P1,which is in term of confidential information signal beam and AN signal beam.Then,the optimal responding strategy of the FD-eavesdropper,QE,can be obtained by applying Qwand Qvinto P2.
Step 1:Solving Optimal Beamforming Vectors Qwand Qv: Firstly,we fix the jamming transmit covariance matrix QEand deal with the corresponding strategy in term of transmission beamforming design of UAV.Since the logarithmic function is a monotonically increasing function,the constraints (23c) and(23d)can be rewritten as
With the continuity of the AOD uncertainties causing by UAV jitter,constraints (29) and (30) involve inf inite inequality constraints,which are intractable semi-inf inite constraints.In order to make the problem tractable,we use S-procedure to remove AOD uncertainties and transform(29)and(30)into linear matrix inequalities (LMIs) to resolve this non-convex problem.
By applying S-procedure,we obtain the LMIs in the follow:
where the matrices
Substituting(31)and(32)into the original problem(23),we can expressP1 as the following equivalent problem.
Step 2:Solving Optimal Covariance Matrix of FDeavesdropper QE: In the previous part,we have tackled the UAV-enabled BS’s problem and obtained the optimal conf idential information signal beamforming and AN signal design with given jamming power.Now we solve the follower’s problem to determine the optimal jamming strategy.Expressions for the optimal jamming power of active FD-eavesdropper are derived as (26).We substitute the best UAV’s strategy with optimal values and given by (40) into the FD-eavesdropper’s objective function.Due to the secrecy rate function,the formulated problem (26) is highly non-convex.By introducing auxiliary variables{rb,sb,re,se,t1,t2}as follows,
The original problem(26)can be reformulated as
However,the constraints(45c)-(45f)make the problem still non-convex.Similarly,to deal with the continuity of AOD uncertainties,we can introduce Sprocedure to rewrite the constraints(45c)-(45f)as following LMIs.
On the basis of analysis above,the problem in(45)can be equivalently reformulated as
where C={QE,sb,re,t1,t2,ς1,ς2,ς3,ς4}are the optimization variables.Then,the convex optimization problem(50)can be solved by the toolbox CVX.
With the existence of a best response,we proposed a strategy iterative algorithm to obtain the Nash equilibrium of the formulated non-cooperative game.Details of the iterative algorithm are shown in Algorithm 1.First,initializing the jamming power of the active FD-eavesdropper as zero and solving the UAV-enabled BS’s problem with S-procedure and SDP.Then,solving the FD-eavesdropper’s problem by the first-order Taylor expansions.When all the updated transmission power of UAV-enabled BS and jamming covariance matrix of FD-eavesdropper nearly keep unchanged,the iteration stops.Otherwise,another round of iteration starts.
5.2 Complexity Analysis
In this section,we analyze the complexity of our proposed iterative algorithm obtaining the Stackelberg equilibrium.Similar to [37],the complexity of iterative algorithm can be approximately estimated through the complexity analysis of solving problemP1 andP2.The problemP1 is equivalently transformed a SDP problem.According to [38],we conclude that the complexity for obtaining solution to(40)is abouto1=O((2NU+1)3+(2NU+1)2).As for the problemP2,it contains the exponential functions and LMI constraints.By adopting the complexity analysis steps following [39],we conclude that the complexity for obtaining solution to(50)is abouto2=O((+5)3.5ln(1/ε))whereεis a given solution accuracy.Therefore,the approximate computational complexity of Algorithm 1 per iteration is abouto1+o2.
VI.SIMULATION RESULTS
In this section,numerical results and simulations are provided to validate our theoretical analysis and to demonstrate the performance of the proposed model.The number of antennas equipped at UAV-enabled BS and FD-eavesdropper areNU=8,=4 and=4,respectively.Without specification,the coordinations of the UAV-enabled BS,legitimate ground receiver and eavesdropper are(0,0,80m),(20m,0,0)and([17],respectively.The environment dependent parameters are set toα1=-1,α2=3,α3=5,β1=44,β2=9 andβ3=2 ln 3/πas in[40].The legitimate channel’s minimum data rate is set asηB=1.5 bit/s/Hz and the maximum eaves-dropping data rate is set asηE=1 bit/s/Hz.Moreover,we set the coefficient of jamming power priceµ=1.The other system parameters are listed in Table 1 unless otherwise specified.
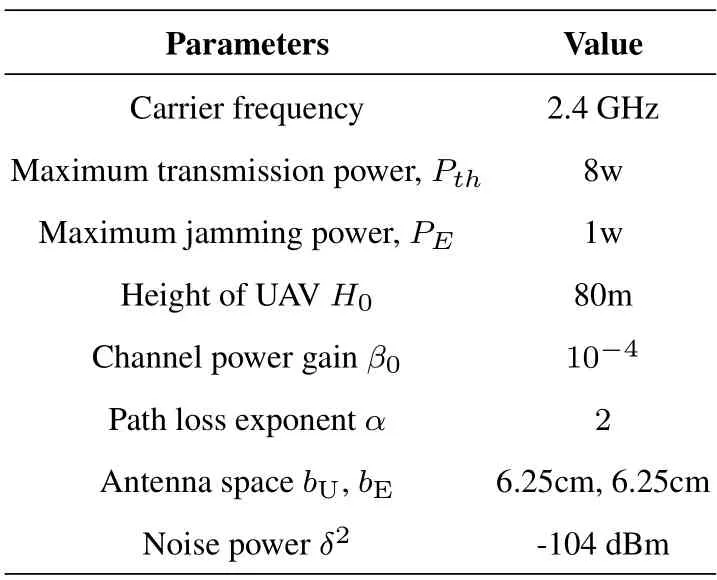
Table 1.System parameters.
Figure 2 and Figure 3 show the convergence behavior of the proposed algorithms.The convergence to the Nash equilibrium can be shown in this part for both UAV-enabled BS and the active FD-eavesdropper.Two cases with=0.05 and=0.1 are considered.The curves in Figure 2 and Figure 3 show that the iterative algorithm converges to the optimal solutions within about 3-4 loops,which validates the efficiency of the proposed non-cooperative game-based algorithm.
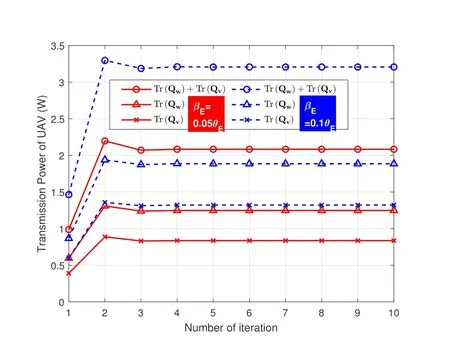
Figure 2.Convergence behavior of the proposed algorithms in the case of =0.05 and =0.1.
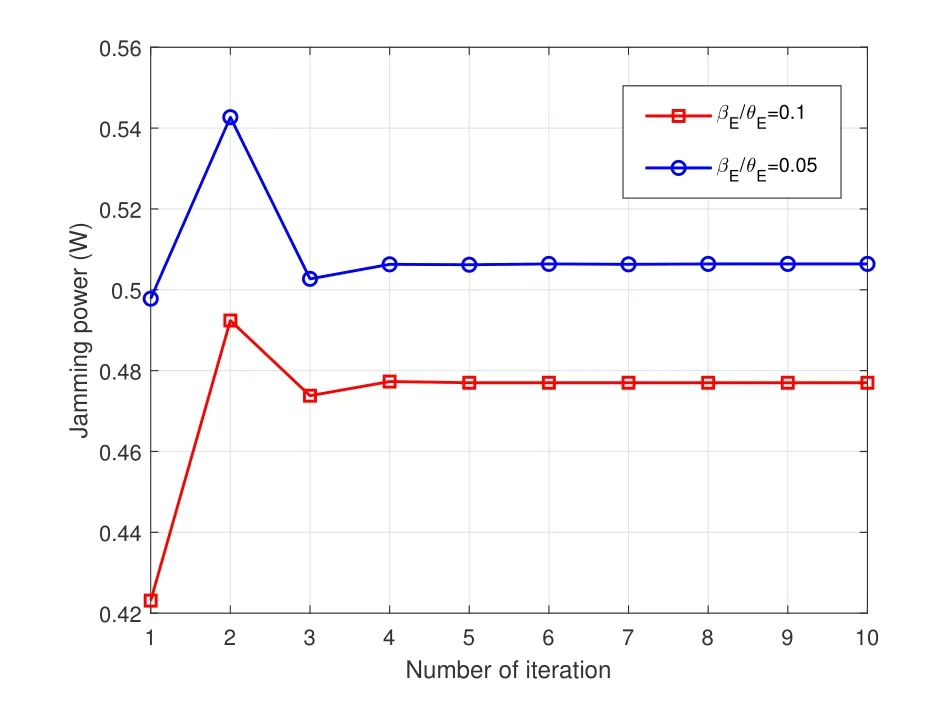
Figure 3.Convergence behavior of the proposed algorithms in the case of =0.05 and =0.1.
To demonstrate the outperformance of the proposed game model and optimized solutions,simulations with two baseline schemes are provided.For baseline scheme 1,MRT is adopted at UAV-enabled BS to transmit the information signal.The beamforming vector of UAV-enabled BS is set as w=wherepis the power allocated to the information signal,which is optimized together with the power allocated to the AN.For baseline scheme 2,we employ a zero-forcing design for AN referred as ZF AN scheme[41].Specifically,ZF AN scheme denotes that AN is injected into the zero space of legitimate receiver’s channel.Then,we minimize the total transmitted power of UAV.
To study the impact of the self-interference factor,Figure 4 and Figure 5 show the transmission power of UAV-enabled BS and the jamming power of active eavesdropper w.r.t self-interference factorρ,respectively.The achieved UAV transmission power with different self-interference factors is shown in Figure 4.The total UAV transmission power decreases as the self-interference factors increase.That is because the effectiveness of jamming attack becomes weaker with the increase of self-interference factor.Then,the corresponding transmission power of UAV meeting the secure transmission requirement can be lower.We can see from Figure 5,as expected,that the jamming power of FD-eavesdropper decreases drastically with higher self-interference.When the self-interference factor becomes sufficiently high,the active eavesdropper gradually ceases the jamming attack and reduces to a passive eavesdropper.On the other hand,we can see from Figure 4 and Figure 5 that the total transmission power of UAV-enabled BS with the proposed scheme is less than that with the baseline scheme.However,the jamming power with the proposed scheme is much higher than that with the baseline scheme.
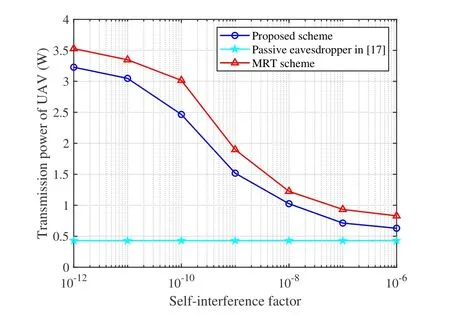
Figure 4.Transmission power of UAV w.r.t. the selfinterference factor with =0.1.
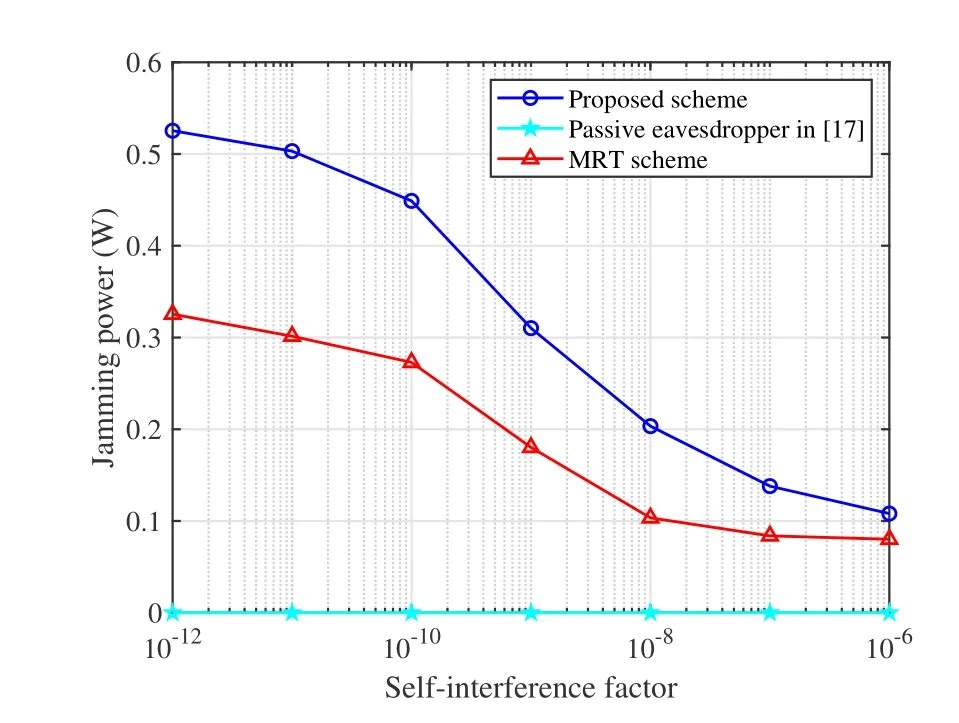
Figure 5.Jamming power w.r.t. the self-interference factor with=0.1.
The result reveals the outperformance of the proposed model in terms of saving UAV-enabled BS’s power and consuming active FD-eavesdropper’s jamming power.
To study the impact of constraint of secrecy rate requirement,Figure 6 and Figure 7 show the transmission power of UAV-enabled BS and the jamming power of active eavesdropper w.r.t minimum required data rate of legitimate receiver,ηB,respectively.We setηE=1 bit/s/Hz,=0.01 and=0.05 in Figure 6 and Figure 7.It can be seen that the total UAV transmission power increases with the increase ofηB.The is due to the fact that secrecy rate requirement becomes more stringent when the minimum required data rate of legitimate receiver increases.Thus,more transmission power is required to meet the secure transmission requirment.It is also seen that jamming power of FD-eavesdropper increases with higherηB.
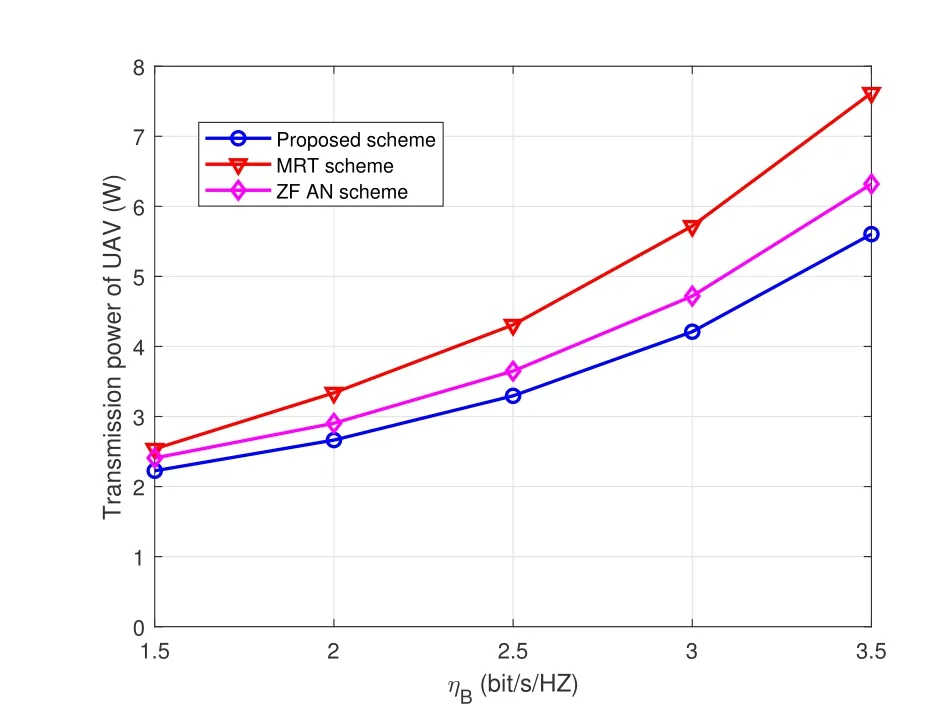
Figure 6.Transmission power of UAV w.r.t. minimum required data rate of legitimate receiver.
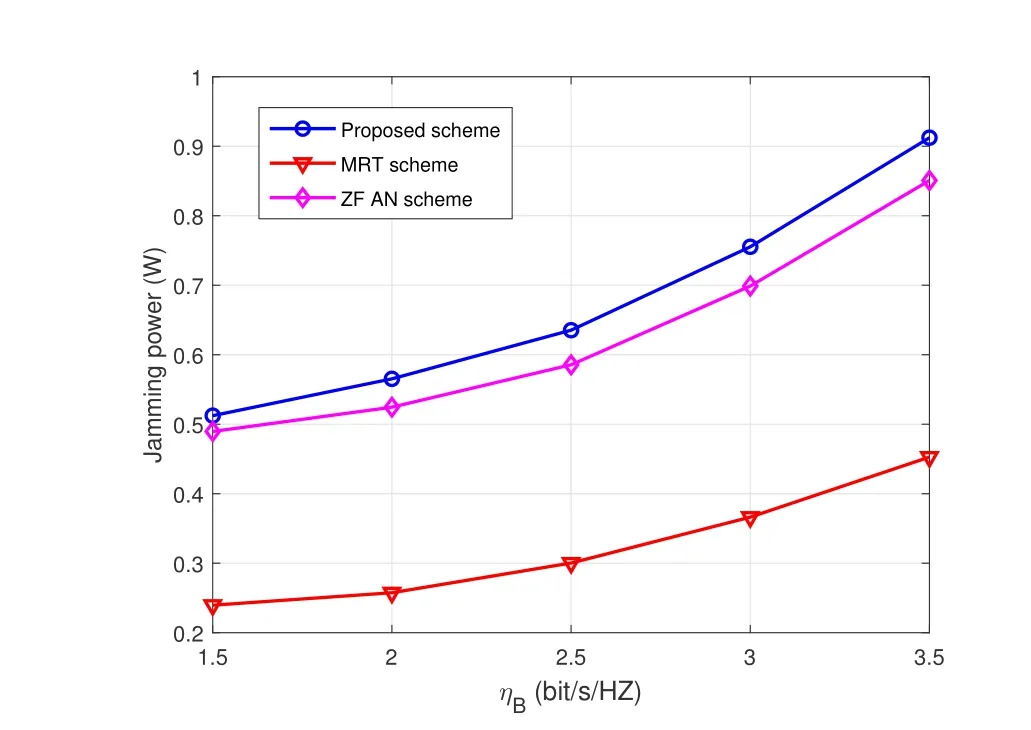
Figure 7.Jamming power w.r.t. minimum required data rate of legitimate receiver.
To study the impact of AOD uncertainties,Figure 8 and Figure 10 show the transmission power of UAVenabled BS w.r.t the maximum normalized vertical AOD estimation error at the legitimate receiver and the FD-eavesdropper,respectively,i.e.,and.We fix the self-interference factorρ=10-10for this part of simulations.It can be seen from Figure 8 and Figure 10 that the transmission power of UAV-enabled BS increases with the increase ofand,which means that the more violent of UAV jitter,it is more difficult for the UAV to transmit accurate beamforming.Therefore,the UAV can only improve the total transmission power to satisfy security requirement of the legitimate link.Besides,it is revealed that the proposed robust scheme outperforms the both baseline schemes over the entire considered range ofand.When=0.04,the proposed scheme can save approximate 15.3% and 8.1% power compared with MRT scheme and ZF AN scheme.When=0.1,the proposed scheme can save about 8.1%and 14.5%power compared with the two baselines.
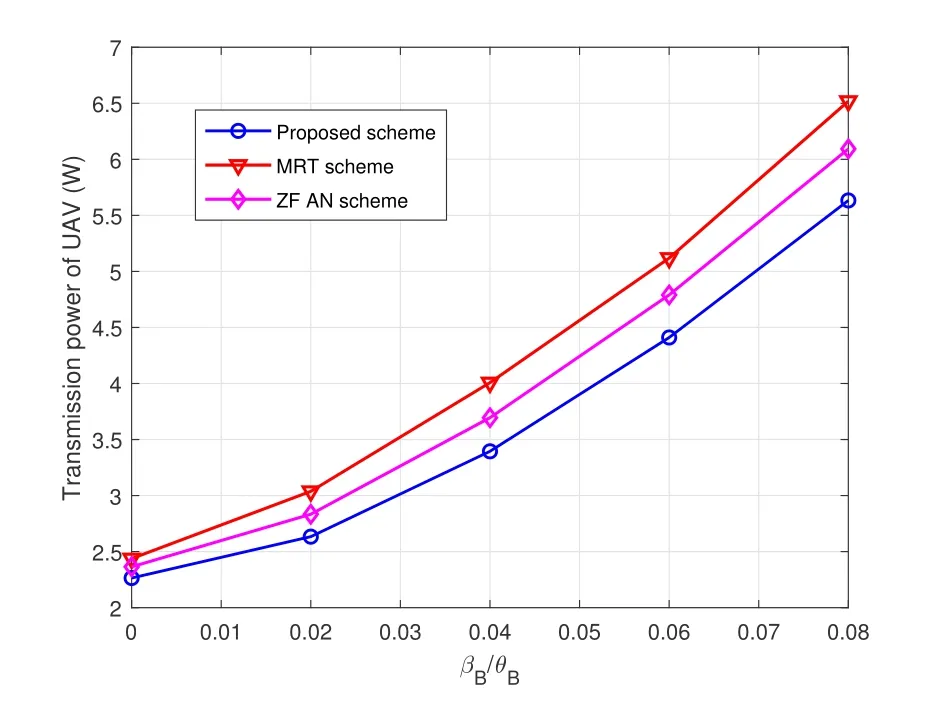
Figure 8.Transmission power of UAV w.r.t. the variations of legitimate receiver’s AOD.
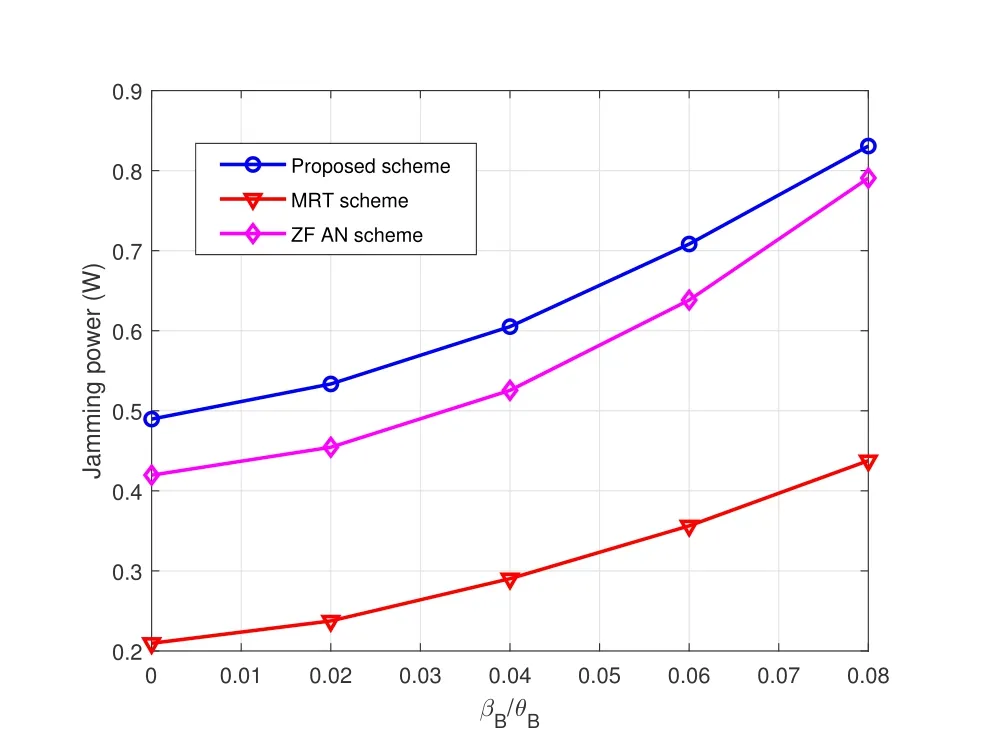
Figure 9.Jamming power w.r.t. the variations of legitimate receiver’s AOD.
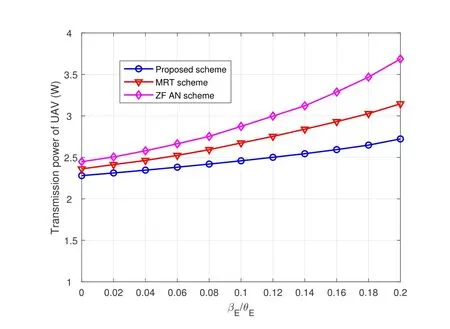
Figure 10.Transmission power of UAV w.r.t. the variations of eavesdropper’s AOD.
Further,we can see the proposed robust scheme can save more power with higher uncertainty of active eavesdropper’s AOD compared with the both baseline schemes.This is because our proposed scheme has a more efficient utilization of AN power as the uncertainty of AOD increases.The results indicate that a significant amount of transmit power can be saved by our proposed robust scheme compared to the two baseline schemes,which is meaningful for energysaving and secure communication in A2G communication networks.
Figure 9 and Figure 11 show the jamming power w.r.tand,respectively.The jamming power at eavesdropper increases with the increase ofthree schemes.Also evidently,we can see that the jamming power at the active eavesdropper under the proposed scheme is much higher than the one under the MRT scheme and ZF AN scheme over the entire considered range ofand,which means the proposed scheme makes the active eavesdropper costs greater jamming power price to degrade the system secrecy rate.MRT scheme achieves the least power consuming at active FD-eavesdropper.Further,the jamming power of the active eavesdropper decreases slightly with the increase of.This is due to the fact that more power should be allocated to the AN beams with the increase of uncertainty of active eavesdropper’s AOD to meet the secure requirments such that the UAV becomes insensitive to jamming attacks.As such,the jamming power is lowered with the increase ofsince the effectiveness of jamming attacks becomes weak under these cases.
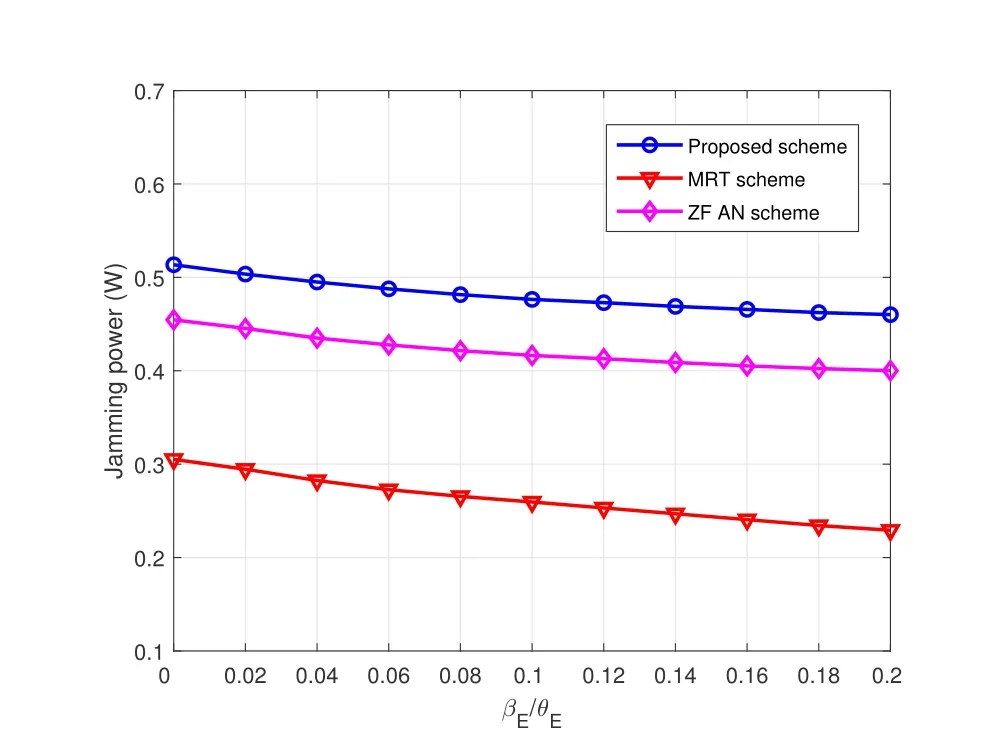
Figure 11.Jamming power w.r.t. the variations of eavesdropper’s AOD.
VII.CONCLUSION
In this paper,we have investigated secure UAV communication against active eavesdropping in an A2G communication system considering the impact of UAV jitter.To study the strategic interactions between the UAV-enabled BS and the active FD-eavesdropper,a non-cooperative game model has been formulated with the worst-scenario secrecy performance under UAV jitter.The existence of Nash equilibrium has been proved and an iterative algorithm has been proposed to obtain solutions to the Nash equilibrium.Comparing with the performance with MRT scheme and ZF AN scheme applied at UAV-enabled BS,the proposed model can achieve more power saving at UAV-enabled BS and more power consuming at active FD-eavesdropper.Besides,the robustness of the proposed scheme with respect to UAV jitter has also been proved.
ACKNOWLEDGEMENT
This work was supported in part by the Beijing Municipal Natural Science Foundation under Grant 4212005,in part by the National Natural Science Foundation of China under 62271076,in part by Young Elite Scientists Sponsorship Program by CAST(YESS20200283),and in part by the Fundamental Research Funds for the Central Universities under Grant 2242022k60006.
- China Communications的其它文章
- Learning-Based Dynamic Connectivity Maintenance for UAV-Assisted D2D Multicast Communication
- AIGC Scenario Analysis and Research on Technology Roadmap of Internet Industry Application
- Dynamic Visible Light Positioning Based on Enhanced Visual Target Tracking
- Ultra Dense Satellite-Enabled 6G Networks: Resource Optimization and Interference Management
- Analysis and Optimization of Validation Procedure in Blockchain-Enhanced Wireless Resource Sharing and Transactions
- A Study of Ensemble Feature Selection and Adversarial Training for Malicious User Detection

