A Zonotopic-Based Watermarking Design to Detect Replay Attacks
Carlos Trapiello and Vicenç Puig
Abstract—This paper suggests the use of zonotopes for the design of watermark signals. The proposed approach exploits the recent analogy found between stochastic and zonotopic-based estimators to propose a deterministic counterpart to current approaches that study the replay attack in the context of stationary Gaussian processes. In this regard, the zonotopic analogous case where the control loop is closed based on the estimates of a zonotopic Kalman filter (ZKF) is analyzed. This formulation allows to propose a new performance metric that is related to the Frobenius norm of the prediction zonotope. Hence, the steadystate operation of the system can be related with the size of the minimal Robust Positive Invariant set of the estimation error.Furthermore, analogous expressions concerning the impact that a zonotopic/Gaussian watermark signal has on the system operation are derived. Finally, a novel zonotopically bounded watermark signal that ensures the attack detection by causing the residual vector to exit the healthy residual set during the replay phase of the attack is introduced. The proposed approach is illustrated in simulation using a quadruple-tank process.
I. INTRODUCTION
DURING the last decade, the interest aroused by cybersecurity aspects of networked control systems (NCSs) has experienced an exponential growth, currently representing one of the main trends in NCSs [1]. Some of the factors that support this increasing interest are: the potential risks to human lives as well as significant economic losses as a consequence of successful attacks; an ever-growing list of registered attacks, including famous cases like the Stuxnet malware [2];the identification of possible threats and vulnerabilities on NCSs [3]–[5]; the characterization stealthy attack policies which exploit the limitations of traditional monitoring algorithms [6], etc. Consequently, all of the above has motivated an exhaustive analysis on secure control and state estimation techniques for the case where a malicious adversary is capable of attacking either the physical components of the system or the communication network that is used to close the control loop [7], [8].
In particular, in the present paper the focus is on the detection of replay attacks from a model-based perspective (i.e.,testing the compatibility of measurements with the model of the underlying physical process), thus working under the premise that classical information security detection techniques, like timestamp, can be bypassed by an attacker. On this subject, note that an effective detection is required for deploying replay attack resilient control schemes [9], [10].Otherwise, regarding model-based detection techniques: in the pioneering work [11], the authors not only model and analyze the effect of replay attacks in the framework of stationary Gaussian processes, but also propose the injection of an exogenous signal into the control loop in order to improve the detectability of the attack. From this moment on, the design of these exogenous signals, which are denoted with the termphysical watermarking[12], has been intensively studied until becoming a well-adopted technique for the detection of replay attacks [13].
Related Work:The watermarking approaches that have been proposed in the automatic control literature can be broadly classified depending on whether they are injected in the control loop in an additive or multiplicative way. On the one hand, multiplicative watermarking schemes employ a bank of filters, placed on the plant side of the communications network, in order to watermark the sensor outputs, while the original data are reconstructed by a watermarking remover placed on the controller side [14], [15]. These schemes allow to address the closed-loop performance degradation induced by the watermark signal. However, multiplicative schemes may lose their effectiveness if the attacker is able to replace the real data before the addition of the watermark signal.
On the other hand, in additive watermarking schemes an exogenous signal is injected from the controller side at the cost of inducing some closed-loop performance degradation.In this regard, in [11], [12], an additive Gaussian signal is injected in the control loop for increasing the attack detection rate of a statistical detector. A similar watermarking scheme has been also analyzed in [16]. In [17], a Gaussian signal is injected in a combined algorithm that deals with online watermarking design and unknown system parameters identification. Furthermore, in [18], a periodical injection of a Gaussian signal is proposed for detecting discontinuous replay attacks. A stochastic game approach is proposed in [19] in order to derive an optimal control policy that switches between a control-cost optimal (but nonsecure) and watermarked (but cost-suboptimal) controllers. Moreover, in [20], a dynamic watermarking method is proposed for detecting replay attacks in linear-quadratic Gaussian (LQG) systems.
At this point, it must be highlighted that the additive schemes presented above have addressed the physical watermarking design problem from a stochastic point of view and,in particular, within the context of stationary Gaussian processes. Nevertheless, as remarked in [21], despite the characterization of uncertainties through Gaussian probability distributions is often well suited to deal with measurement noises,this description may fail to model disturbances that arise from some of lack of knowledge about deterministic behaviors and which may do not have any other stationary behavior than that of remaining within some specified bounds. Hence, in the remaining of the paper the physical watermarking design problem will be addressed from a set-based (or normbounded) paradigm [22]. These set-based techniques have proven their effectiveness in fault diagnosis and tolerant control schemes [23]. Besides, they have been recently used in order to achieve a secure state estimation in systems under bounded attacks [24], [25] and to characterize the replay attack detectability using set invariance notions [26].
Approaching the system monitoring under a set-based paradigm allows to infer in a deterministic way if the system is being attacked by testing online whether or not a residual signal belongs to a set coherent with the healthy operation of the system. Nonetheless, this unambiguous assessment poses two central challenges in the design of active attack detection schemes: i) The proposed watermarking scheme should be able to force the residual signal out of its healthy residual set whenever the system is under attack while minimizing the performance loss induced in the system operation; ii) A coherent metric to assess the performance degradation induced by a bounded watermark signal should be developed.
In order to address the latter point, zonotopic sets will be used mainly motivated by the results presented in [27], where the notion of covariation matrix of a zonotope is introduced for proposing an optimal robust state observer. Furthermore,by minimizing the weighted Frobenius norm (F-norm) of the prediction zonotope, analogous expressions are obtained regarding the optimal design of a zonotope-based observer and the standard stochastic Kalman filter (uncertainties modeled as Gaussian random variables). Consequently, in this paper, the above analogy is further exploited by analyzing the optimal control law that minimizes a cost function that takes into account the weightedF-norm of the bounding zonotope computed by a zonotopic Kalman filter (ZKF).
It must be pointed out that optimal control has been thoroughly studied under different uncertainty paradigms, namely:deterministicoptimal control [28], where uncertainty can only take one value;stochasticoptimal control [28]–[31], where uncertainty is defined as a function of a probability space;minimaxcontrol [32]–[34], where uncertainty is confined within a given set. In this regard, notice that, whereas minimax control is defined in a worst case basis, the proposed approach is based on the bounding zonotopeF-norm which,for linear-quadratic control problems, returns expressions similar to those obtained if the problem is formulated under Gaussian uncertainties. Consequently, when it comes to the active attack detection in linear systems, through this novel framework the same optimality patterns are obtained regardless of whether the detection is approached under a set-based or stochastic paradigm, what may lead to future detection schemes that merge the mutually exclusive benefits of both approaches [21].
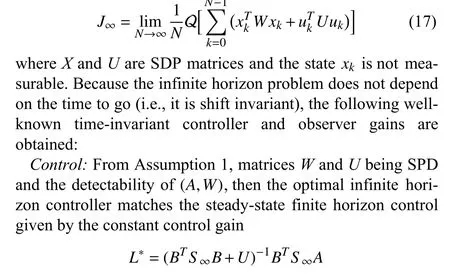
Contributions:The contributions of this paper are as follows. First, a linear-quadratic regulator (LQR) controller that operates based on the estimates of a ZKF is proposed. It is proven that this control scheme minimizes a new cost function that considers the weightedF-norm of the system states,in what can be seen as the zonotopic counterpart of the expected value of a quadratic cost function in an LQG scheme. Furthermore, for the infinite horizon control problem,the Frobenius radius of the minimum robust positive invariant set (mRPI) of the estimation error is given by the solution of the Riccati algebraic equation.
Second, the new zonotope-based cost function is used to evaluate the impact that a zonotopically bounded watermark signal has on the steady-state operation of the system. Analogous expressions to the performance loss induced by an exogenous Gaussian signal in an LQG system are obtained.
Third and finally, a zonotopically bounded watermark signal that minimizes the new cost function is proposed. This detection scheme injects a known signal in the system inputs,while filtering its effect through the estimations generated using the output data. Since the replay phase of the attack entails that the known signal is no longer observable, then the estimation error generates a new residual signal that is destabilized whenever the output data are being replayed back.Some preliminary results have been presented in the conference paper [35].
The remainder of the paper is organized as follows: Section II introduces some preliminary concepts whereas Section III presents the problem statement. Then, in Section IV the optimal finite/infinite horizon control problem based on the estimates of a ZKF is analyzed. Section V analyzes the impact of a bounded watermark signal on the previous optimal control loop. Besides, in Section VI a new guaranteed replay attack detection scheme is introduced while in Section VII the proposed results are validated in simulation using a well-known control benchmark based on a four-tank system. Finally, in Section VIII the main conclusions are drawn.
II. NOTATION, BASIC DEFINITIONS AND PROPERTIES
A. Notation
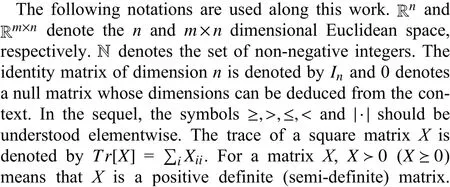
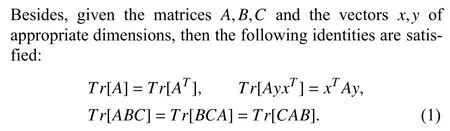
B. Basic Definitions and Properties

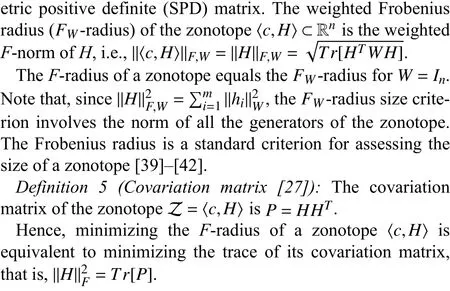
A. System Description

B. Zonotopic KF


IV. LINEAR-QUADRATIC ZONOTOPIC CONTROL
In this section, the optimal control problem for the case in which the feedback loop is closed using the estimates generated by a ZKF is analyzed. Note that, under this paradigm, at each time instantkthe real state of the system is known to be confined within a zonotope. In this regard, the following performance criterion is introduced in order to assess the system operation.
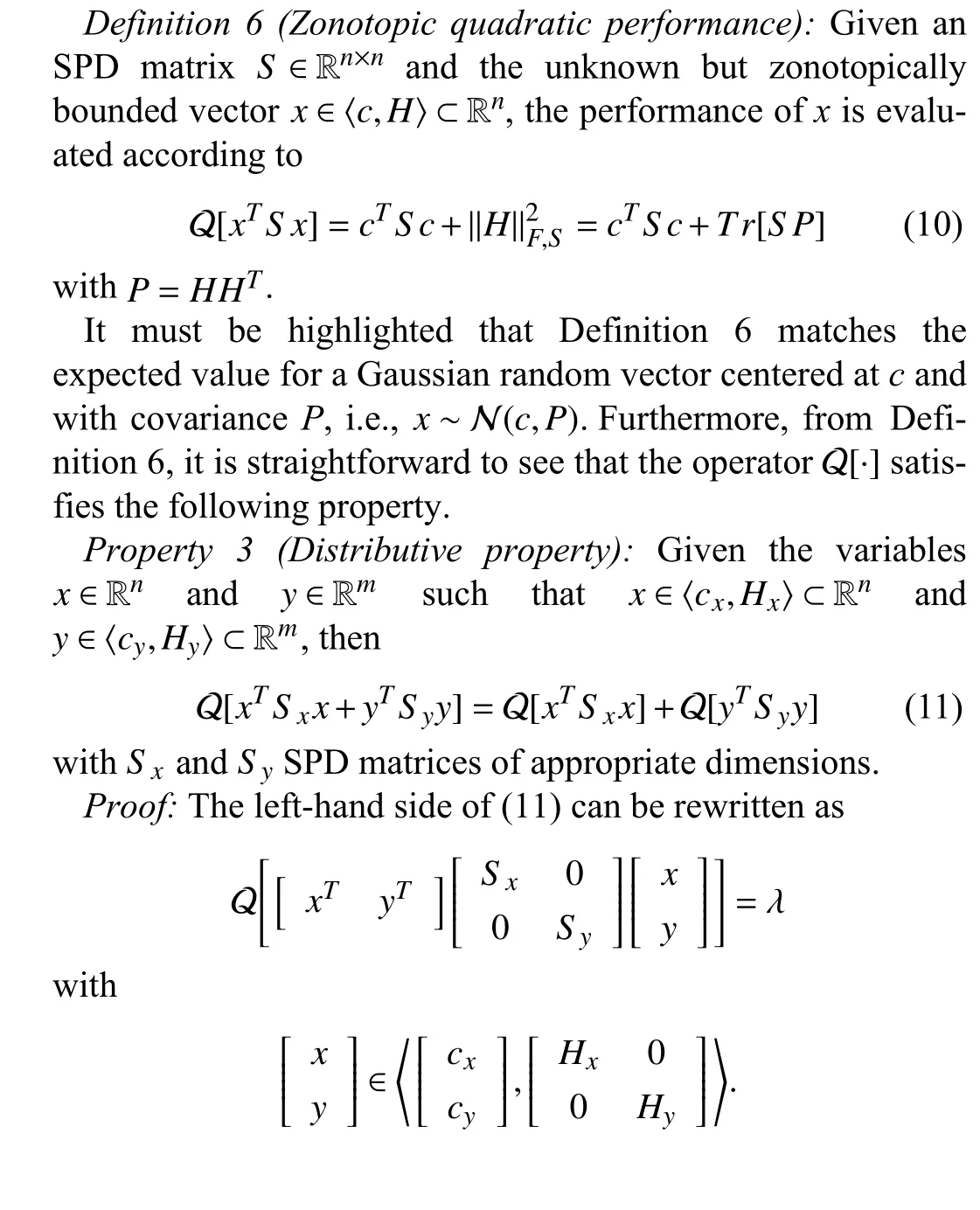
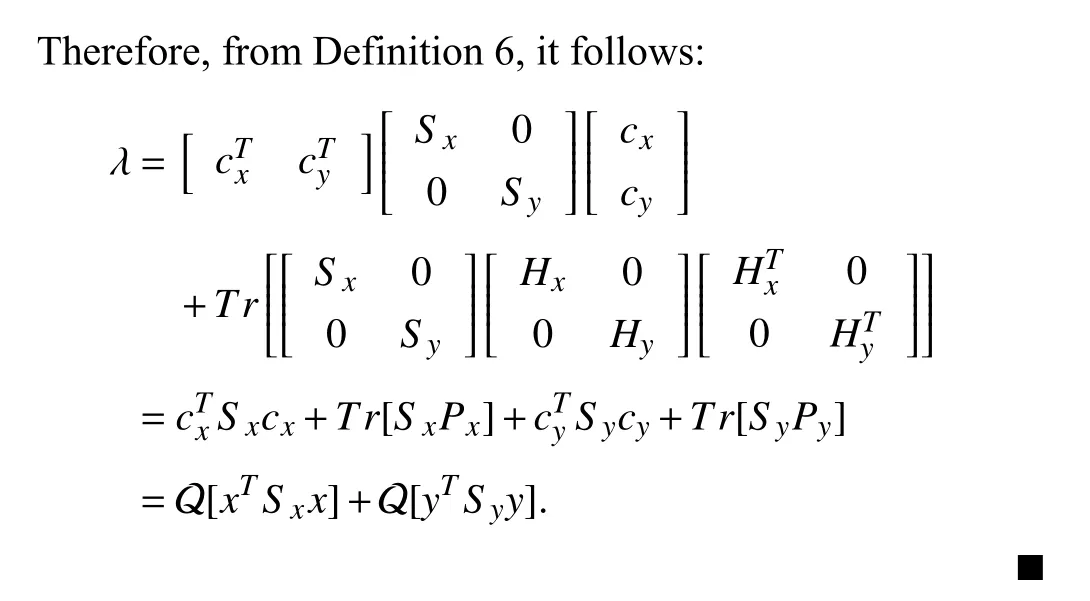
Below, the finite and infinite horizon control problems under the performance metric in Definition 6 are analyzed.
A. Finite Horizon Control

which operates based on the center of the ZKF estimator.
In order differentiate (15) from the stochastic LQG control,in the sequel the zonotopic version will be denoted as linearquadratic zonotopic (LQZ) control. For this case, from (13)and (14) it follows that the optimal value of the cost function is:

B. Infinite Horizon Control
Since many control systems operate for long periods of time, the remainder of the paper will focus on a system whose control law is obtained by solving the infinite horizon problem formulated as
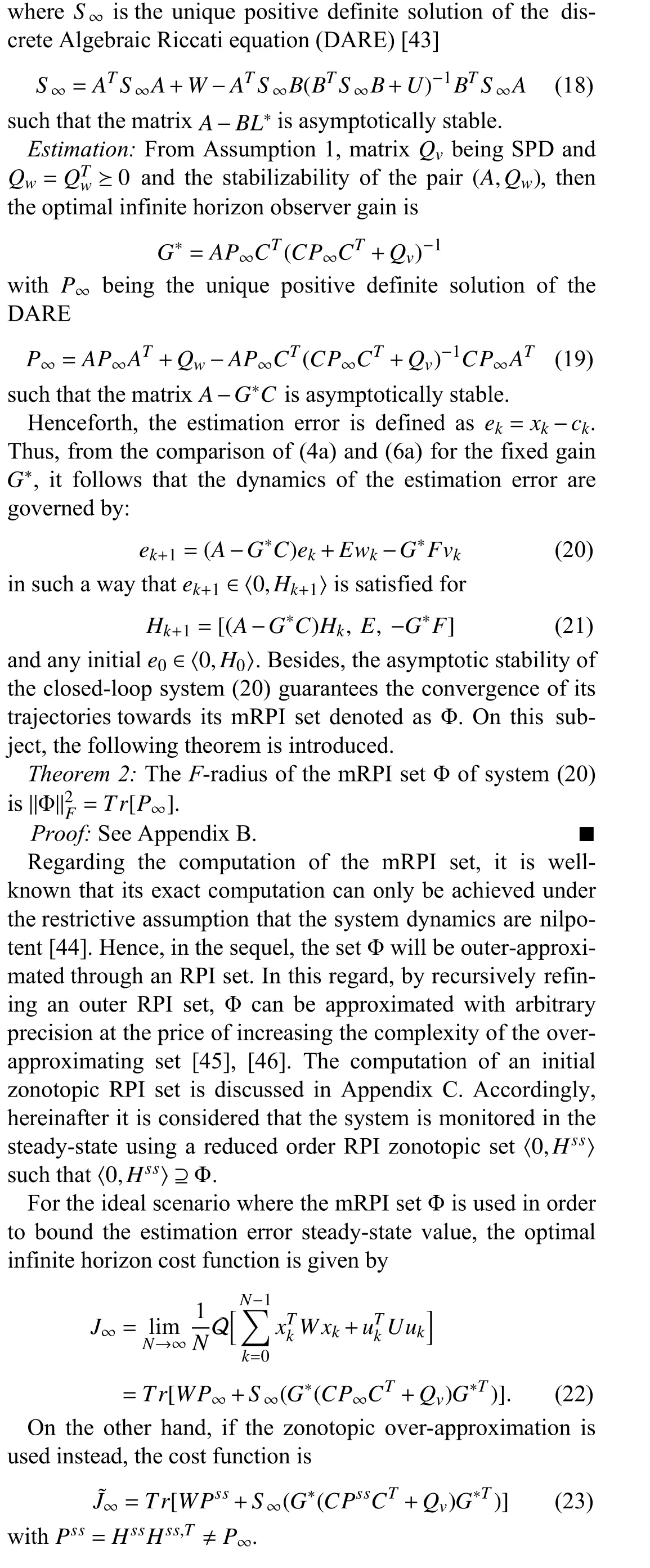
V. REPLAY ATTACK DETECTABILITY
In this section, the case where a malicious attacker can access the communications layer and record/replay the data sent through the sensors-to-controller link is analyzed. In order to characterize the effect of the attack, the following time windows are defined:
1) Record Window:Output data are assumed to be recorded forKREC={k∈N :k∈[k0,k0+l-1]}, wherel∈N denotes the size of the record window.

A. Anomaly Detector

B. Attack Detectability
Fig. 1 shows the overall control/attack/watermarking scheme under consideration. Regarding the control scheme:the control loop is closed remotely by means of an optimal controller (Section IV) that operates based on the estimates of a ZKF (Section III-B). The estimates of the ZKF are used by a set-based anomaly detector (Section V-A). Additionally, Fig. 1 depicts an attacker that may be able to spoof the data sent through the sensors-to-controller link as well as to inject an exogenous signalu¯kinto the system inputs. On the other hand,the blue dashed box shows the interaction of an additive watermark signal (Section VI) with the control loop.
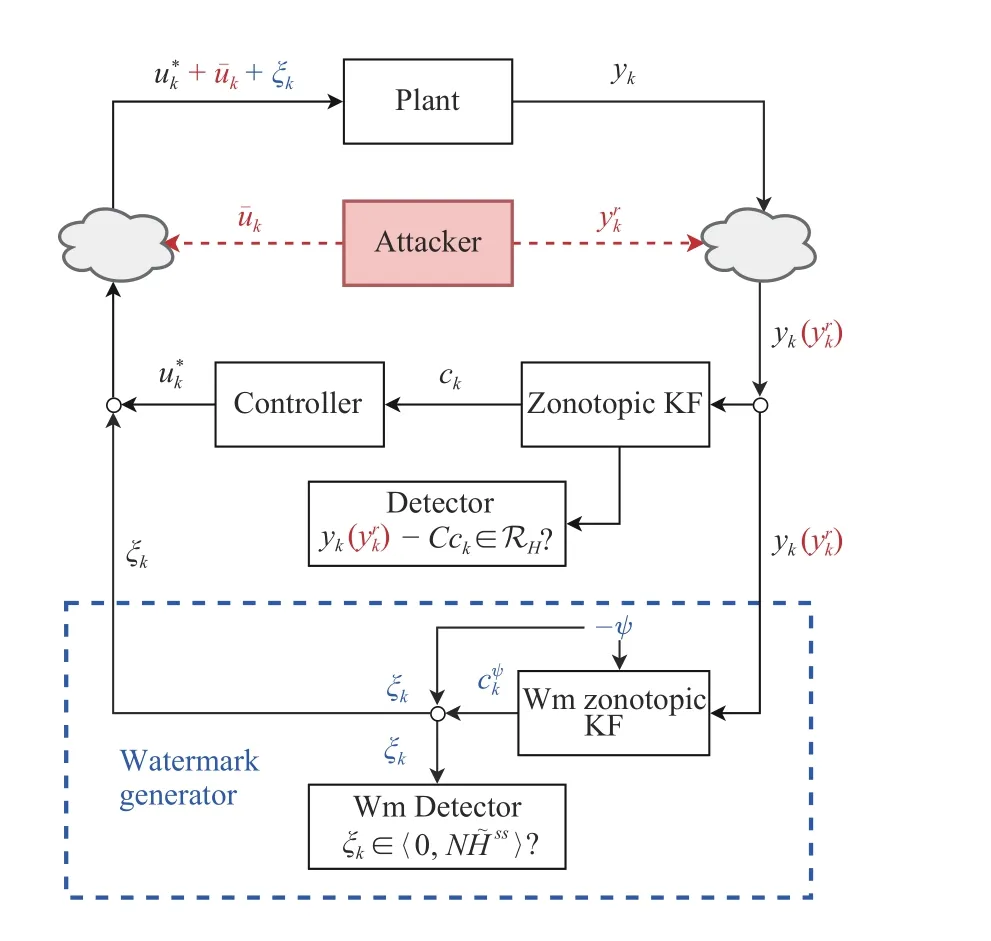
Fig. 1. Overall scheme – Replay attack (red); Watermark generator (blue).

C. Performance Loss Induced By A Zonotopically-Bounded Watermark Signal

VI. ZONOTOPICALLY BOUNDED WATERMARK SIGNAL DESIGN
A. Design of an Extended State Estimator
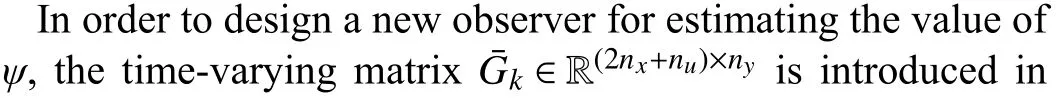
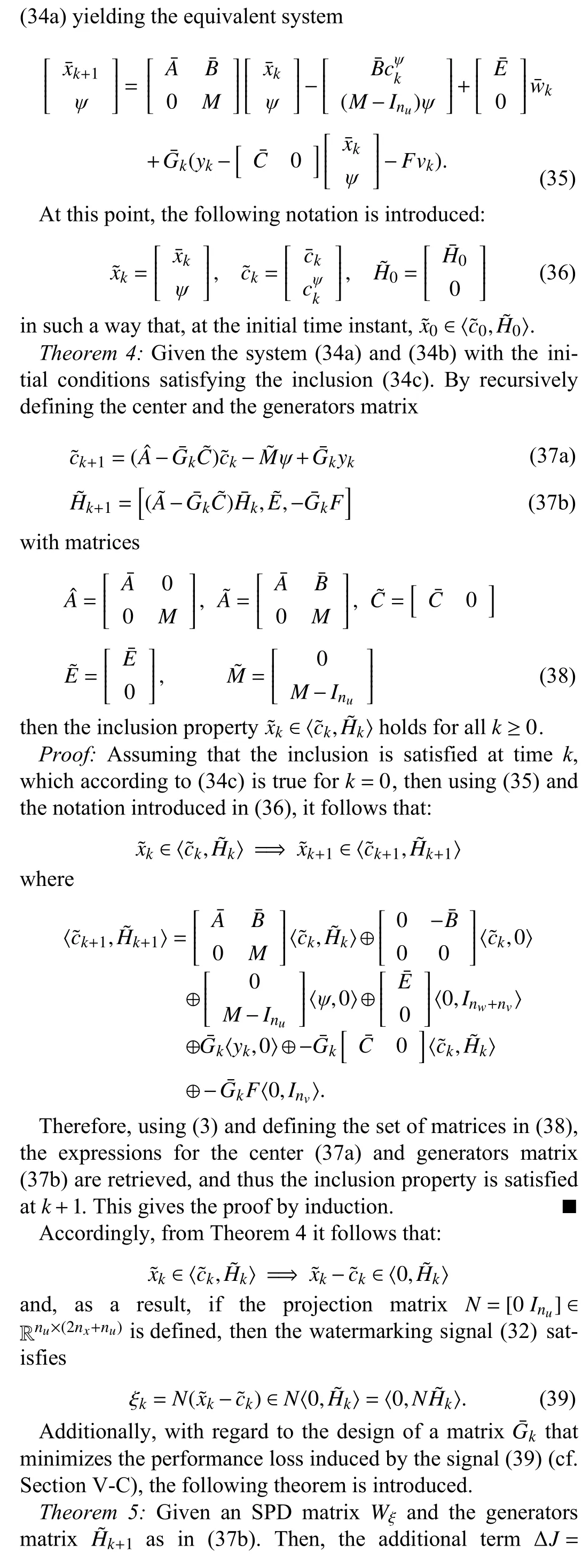

B. Watermarked System Stability
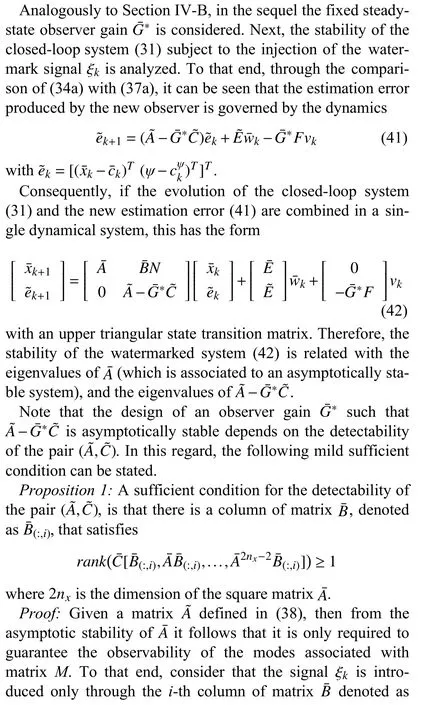
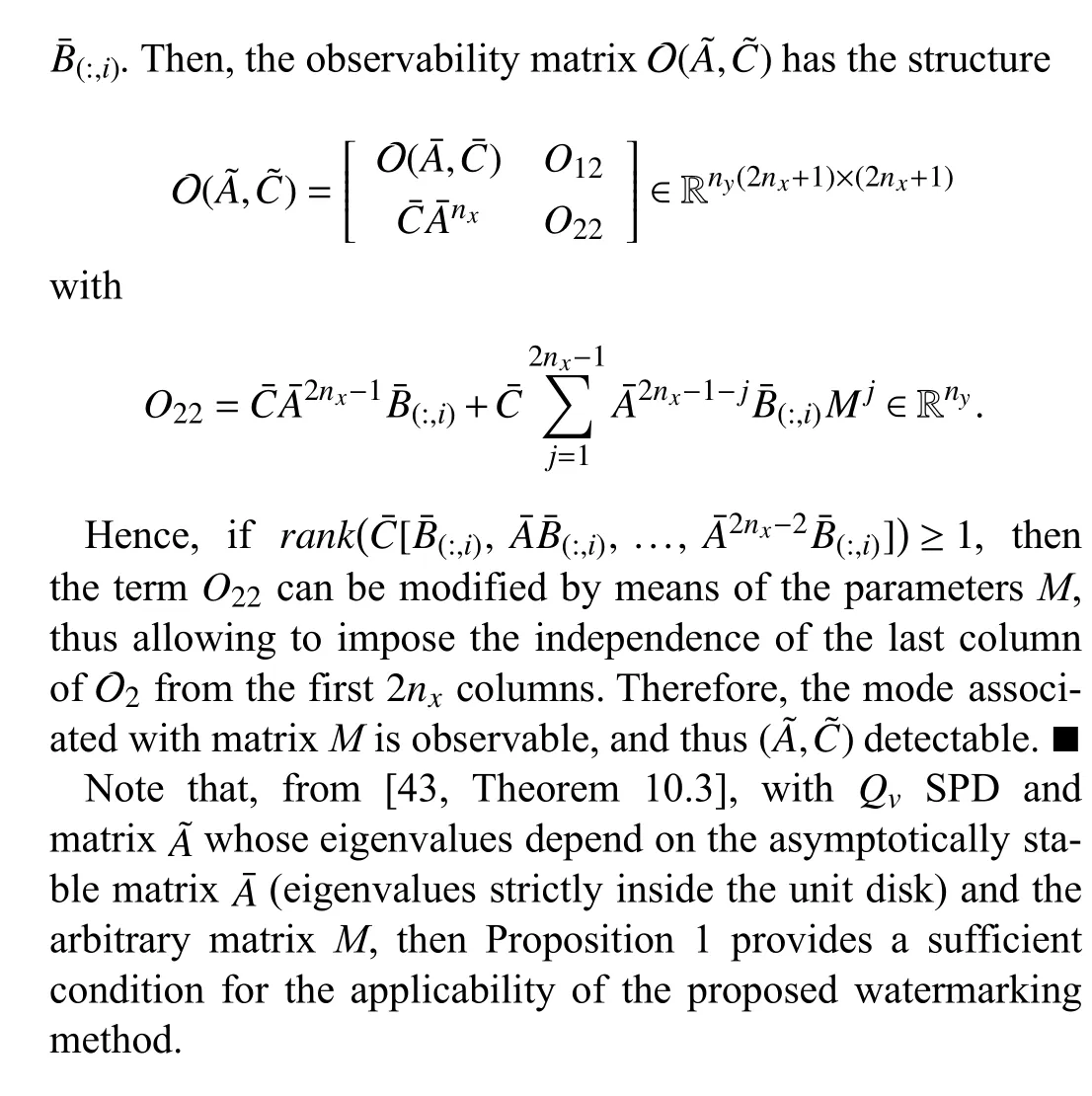
C. Attack Detection

VII. NUMERICAL EXAMPLE
The quadruple-tank system [47] is a well-known benchmark used to evaluate control and supervision strategies, and it is also employed to evaluate cyber-attack detection techniques in [5], [7]. The nonlinear dynamics of the system are described as follows:

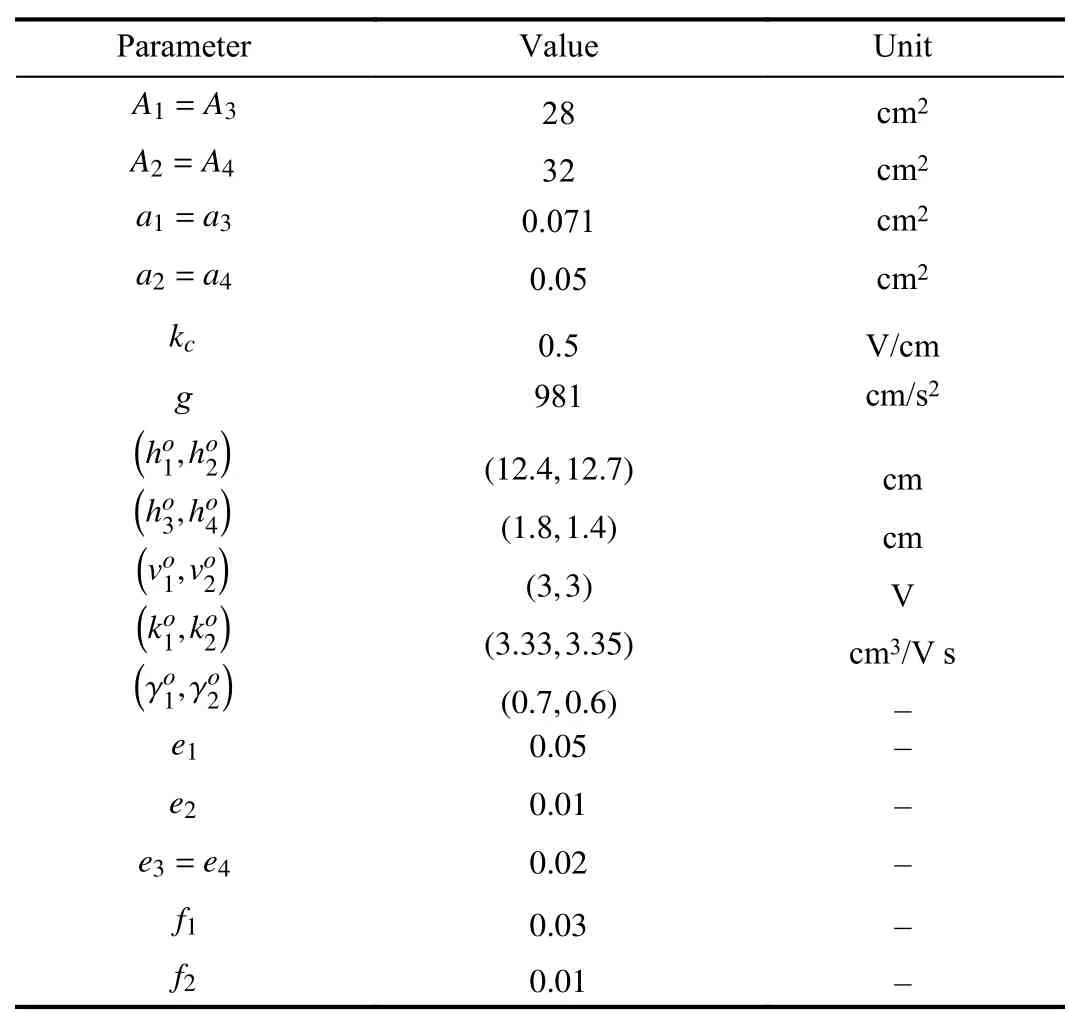
TABLE I QUADRUPLE TANK PROCESS PARAMETERS
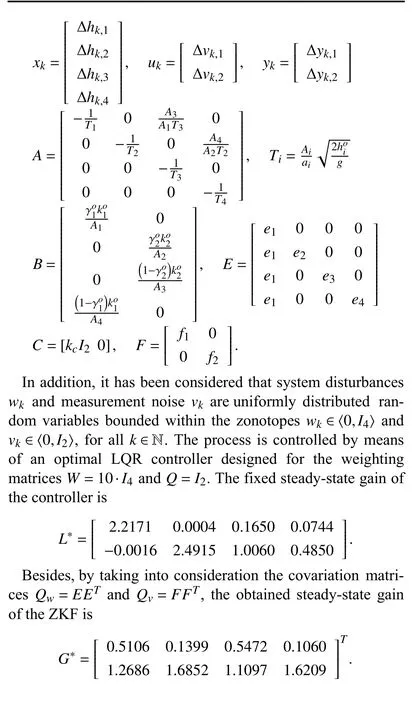
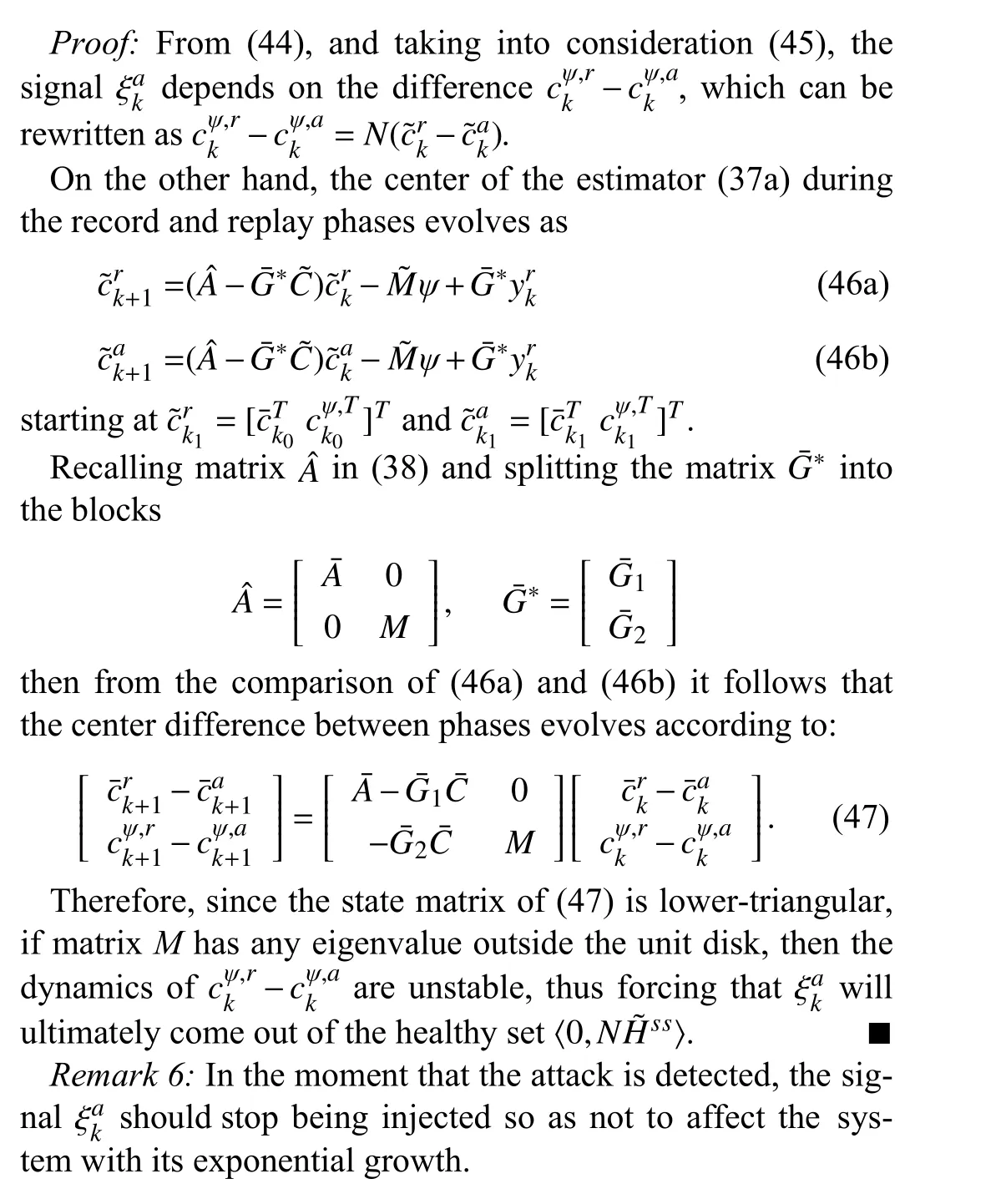
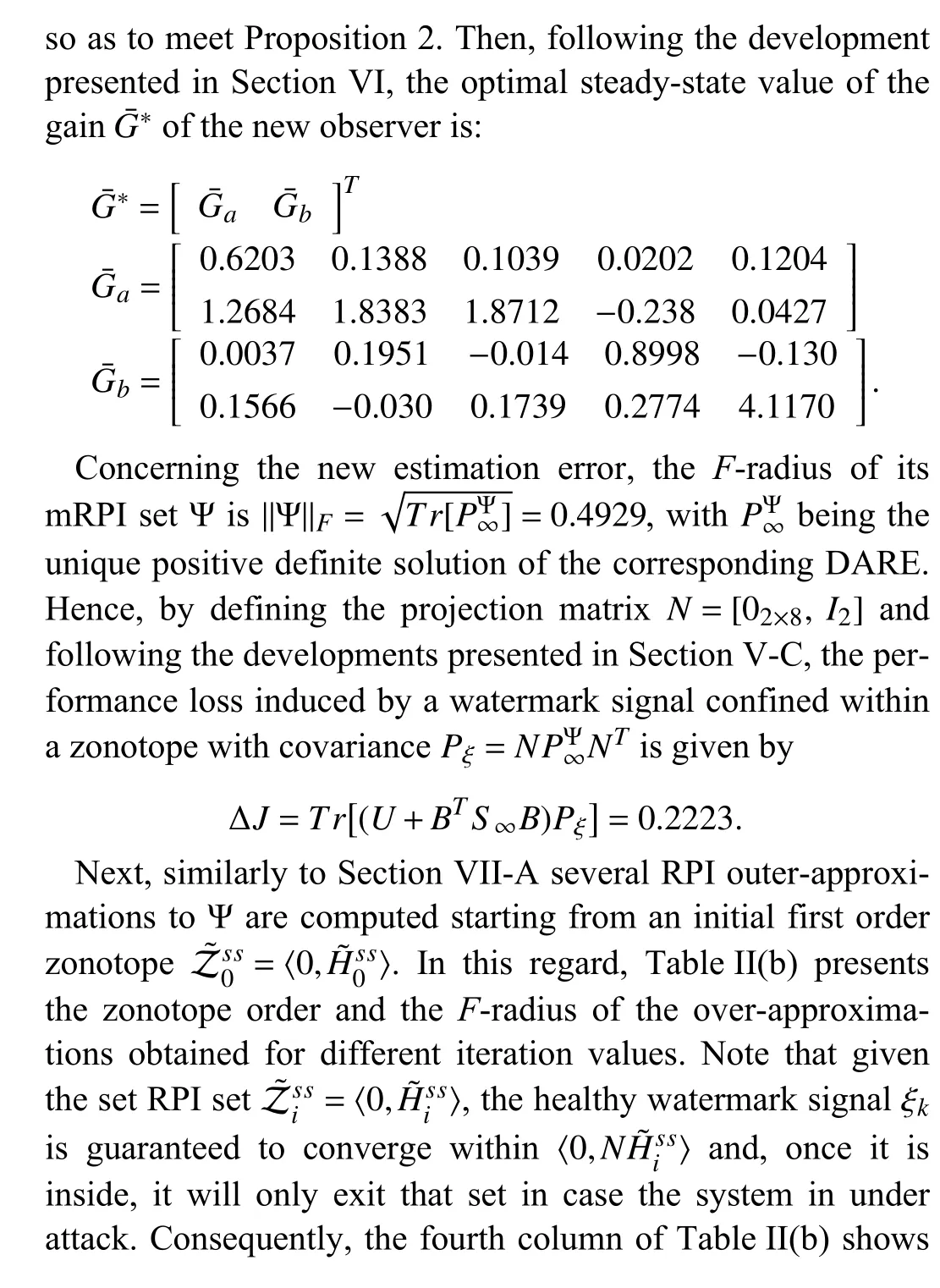
At this point, it must be highlighted that the eigenvalues of matrixA-G*C-BL*are {-0.1739,0.4005,0.9513±0.0278i},that is, it is asymptotically stable, and thus there is no guarantee that the replay attack can be detected (cf. (28)). In other words, in the remainder of this section, Assumption 3 concerning the attack undetectability prevails thus motivating the injection of a watermark signal in the control loop.
A. Performance Assessment
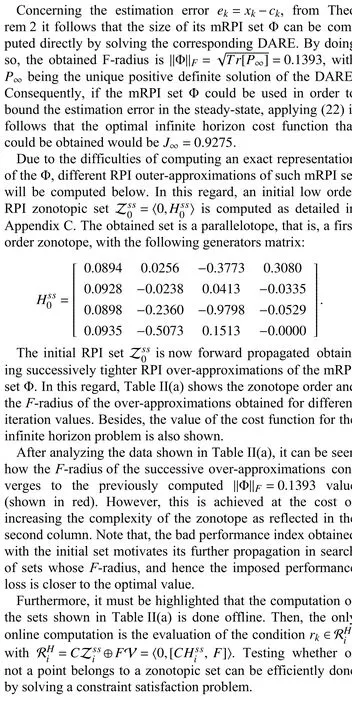
B. Watermark Signal Design
In order to design a watermark signal like the one presented in Section VI, the tuning matrixMmust be defined. In this regard, the following matrixMis introduced:

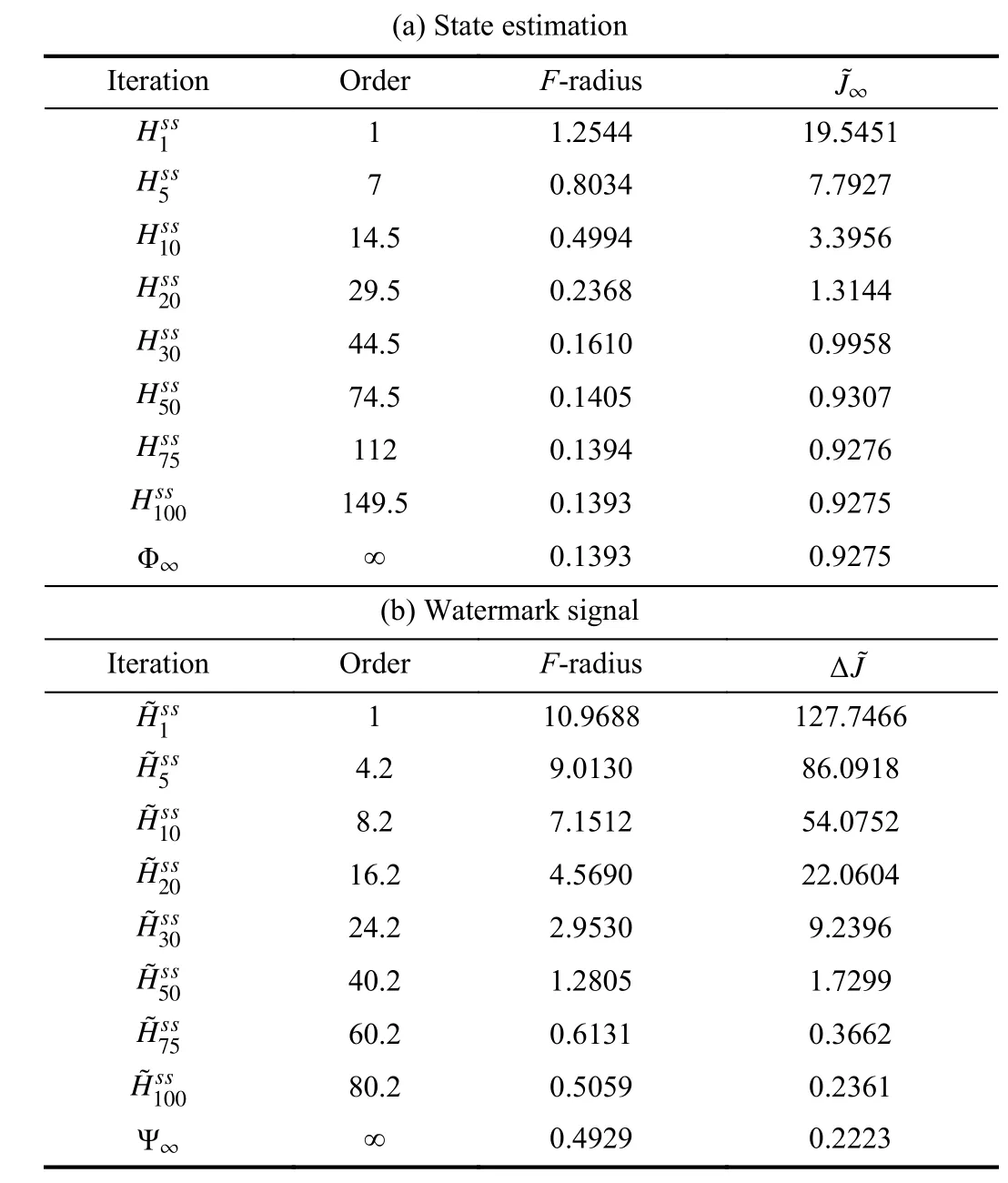
TABLE II ZONOTOPIC RPI APPROXIMATIONS OF THE MRPI SET
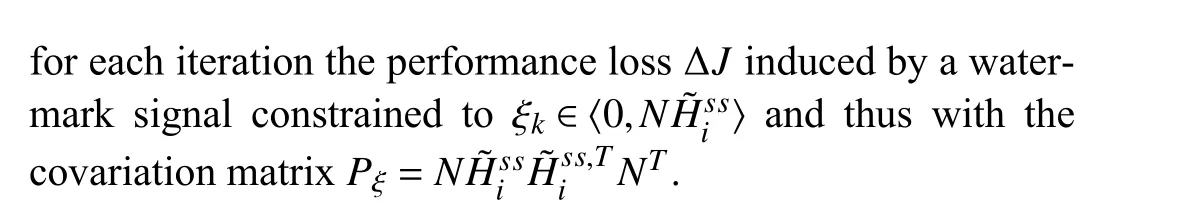
C. Attack Simulation
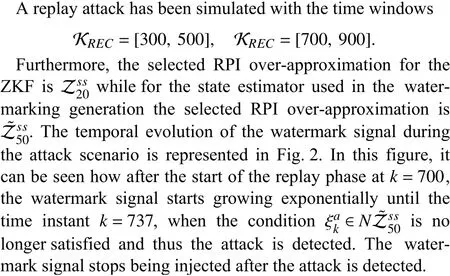
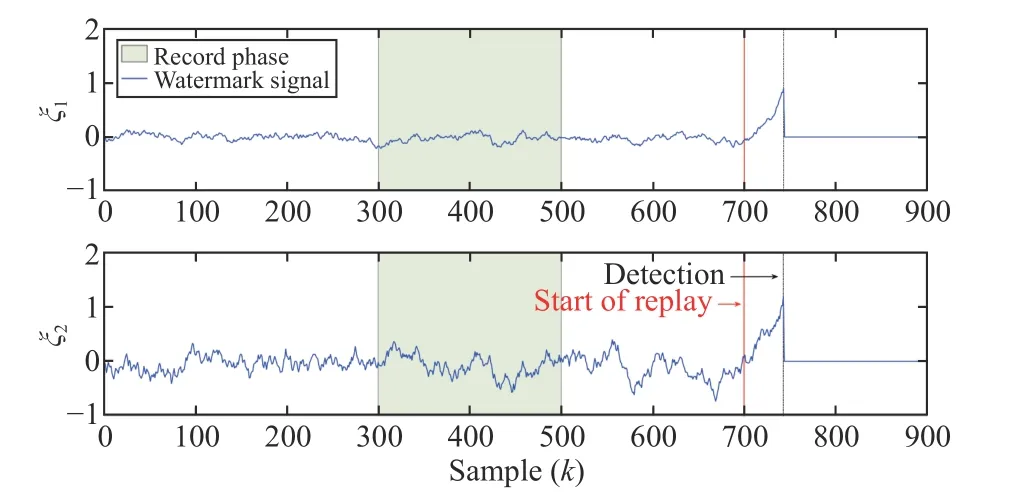
Fig. 2. Temporal evolution of the watermark signal.
On the other hand, Fig. 3 shows the effect caused on the system outputs by the injection of the watermark signal. It can be seen how the performance of the system is hardly degraded before the replay phase and how after the start of this phase the effect of the increasing watermark signal becomes more evident. It should be highlighted that since the control loop is affected by the data replay, the stability of the plant after the attack detection, atk=737, is due solely to the fact that the open-loop system is stable.

Fig. 3. Temporal evolution of the system outputs.
The mean times (tm) required in the simulations to monitor the operation of the system online are1Laptop (Intel i7 1.8 GHz, 16 GB RAM) running Windows 10; optimization using Cplex 12.8 [48].
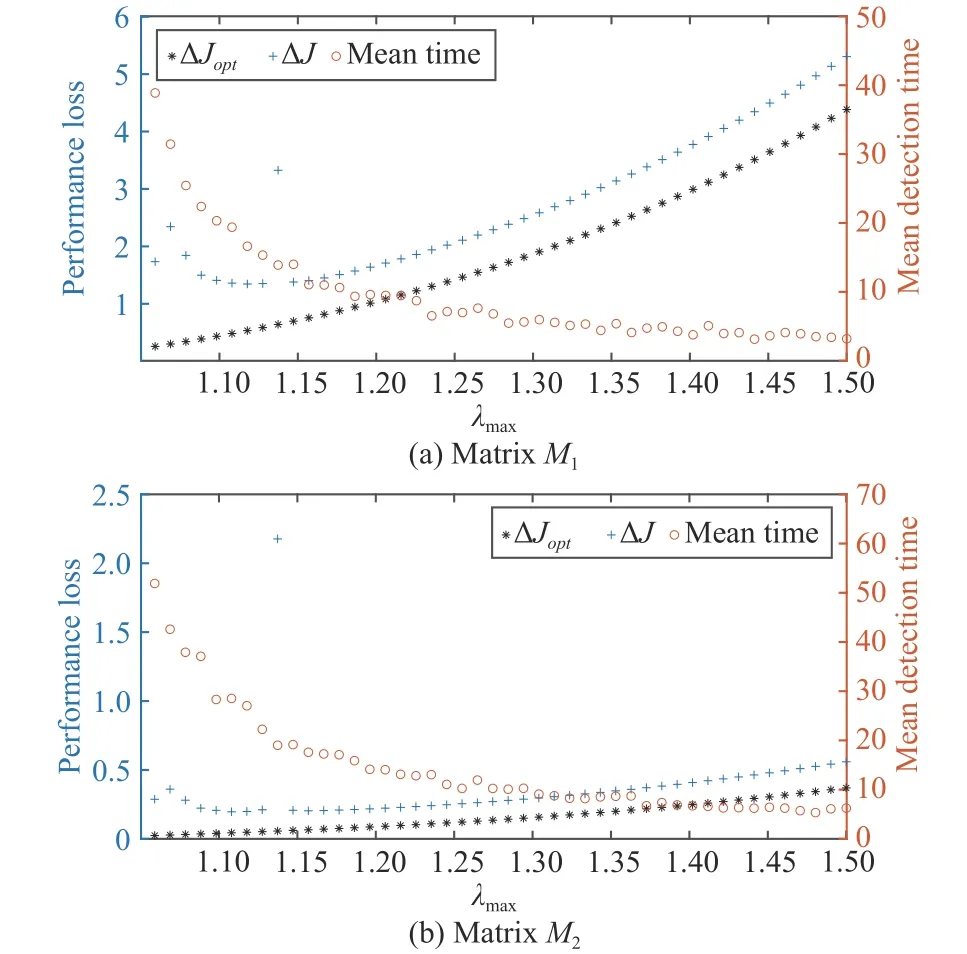
Fig. 4. Performance loss vs mean detection time.
VIII. CONCLUSIONS
This paper has investigated the use of zonotopes for the design of watermark signals. The proposed approach has exploited the recent analogy found between stochastic and deterministic fields in the context of optimal state estimation,and extended it to optimal control. By means of this analogy,the system performance can be assessed and its steady-state operation may be related with the size of the mPRI set of the estimation error. Furthermore, similar expressions regarding the impact of a Gaussian watermark signal on the performance of an LQG system and the impact of a zonotopically bounded signal on the weightedF-norm of the states have been obtained. These analogous optimal patterns, motivate further studies in the attack detection for systems which are simultaneously subject to bounded disturbances and Gaussian noise, thus merging the usually mutually exclusive benefits granted by set-based techniques and stochastic techniques.Moreover, some unresolved issues, like the effect of the reduction operator in the convergence of the Riccati difference equations, appear as appealing problems that clearly deserve an in-depth study. Other future research directions include: the extension of the zonotopic framework to more complex attack policies like, for example, stealthy attacks; the consideration of input and state constraints; the adaptation of the watermarking method to distributed monitoring architectures, thus addressing the scalability to large-scale systems;and the consideration of continuous time systems.

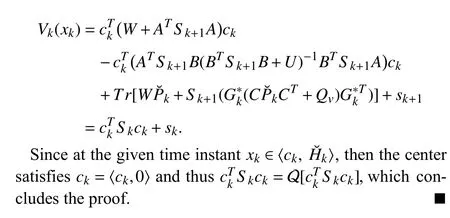
APPENDIX B PROOF OF THEOREM 2

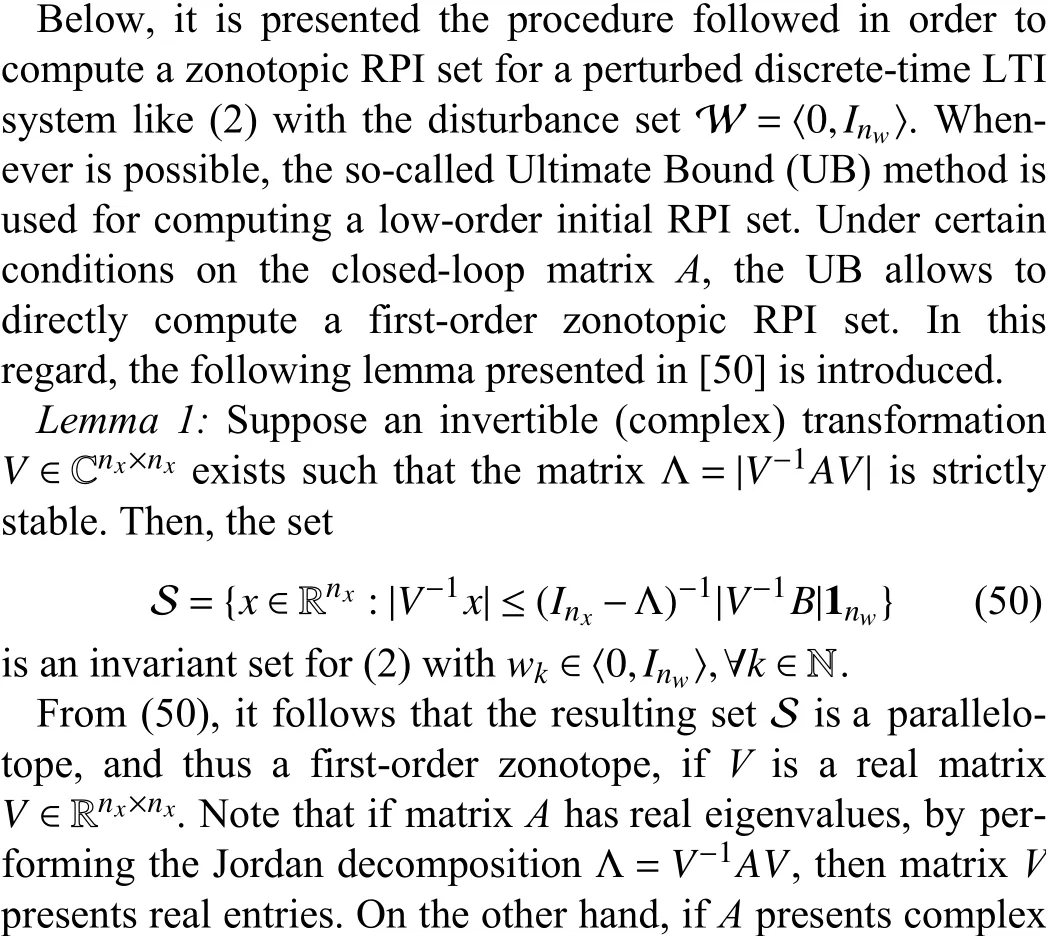
APPENDIX C COMPUTING AN INITIAL ZONOTOPIC RPI SET
 IEEE/CAA Journal of Automatica Sinica2022年11期
IEEE/CAA Journal of Automatica Sinica2022年11期
- IEEE/CAA Journal of Automatica Sinica的其它文章
- Adaptive Generalized Eigenvector Estimating Algorithm for Hermitian Matrix Pencil
- Recursive Filtering for Nonlinear Systems With Self-Interferences Over Full-Duplex Relay Networks
- Receding-Horizon Trajectory Planning for Under-Actuated Autonomous Vehicles Based on Collaborative Neurodynamic Optimization
- A Bi-population Cooperative Optimization Algorithm Assisted by an Autoencoder for Medium-scale Expensive Problems
- On RNN-Based k-WTA Models With Time-Dependent Inputs
- Frequency Regulation of Power Systems With a Wind Farm by Sliding-Mode-Based Design
