Catalyzing Random Access at Physical Layer for Internet of Things:An Intelligence Enabled User Signature Code Acquisition Approach
Xiaojie Fang,Xinyu Yin,Xuejun Sha,Jinghui Qiu,Hongli Zhang
1 School of Electronic and Information Engineering,Harbin Institute of Technology,Harbin 1500001,China
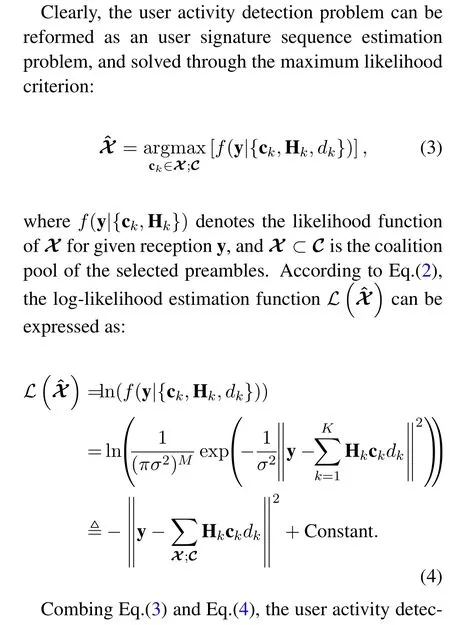
2 Science and Technology on Communication Networks Laboratory,Shijiazhuang 050050,China
3 School of Computer Science and Technology,Harbin Institute of Technology,Harbin 150001,China
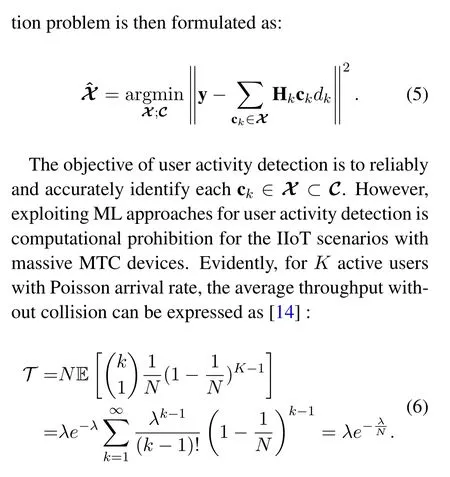
Abstract:Exploiting random access for the underlying connectivity provisioning has great potential to incorporate massive machine-type communication(MTC)devices in an Internet of Things(IoT)network.However,massive access attempts from versatile MTC devices may bring congestion to the IIoT network,thereby hindering service increasing of IIoT applications.In this paper,an intelligence enabled physical(PHY-)layer user signature code acquisition(USCA)algorithm is proposed to overcome the random access congestion problem with reduced signaling and control overhead.In the proposed scheme,the detector aims at approximating the optimal observation on both active user detection and user data reception by iteratively learning and predicting the convergence of the user signature codes that are in active.The crossentropy based low-complexity iterative updating rule is present to guarantee that the proposed USCA algorithm is computational feasible.A closed-form bit error rate(BER)performance analysis is carried out to show the efficiency of the proposed intelligence USCA algorithm.Simulation results confirm that the proposed USCA algorithm provides an inherent tradeoff between performance and complexity and allows the detector achieves an approximate optimal performance with a reasonable computational complexity.
Keywords:Internet of Things(IoT);artificial intelligence;physical layer;cross-entropy;random access
I.INTRODUCTION
With the proliferation of Industrial Internet of Things(IIoT),there has been a growing interest in leveraging IoT technologies for industrial innovation,providing a crucial foundation for a multitude of emerging industrial applications,such as smart power and heat grids,intelligence oil and natural gas distribution,smart automotive manufacturing,and intelligence transportation.In particular,incorporated through a vast variety ofthings(including sensors,controllers,actuators,mobile devices,etc.),modern industrial platforms are undergoing a tremendous upgrade from the pure surveillance-centric monitors into the comprehensive digital twin executors[1].Typically,the ubiquitous machine-type communication(MTC)devices are the key enablers forcyber-physical interactions.According to a recent report released by Gartner,Inc.,there are approximately 4.8 billion IIoT assets in the world at the end of 2019,and their number will grow by 21 percent in 2020[2].
Considering the fact that most IIoT devices are with sparse activity,limited computational overhead and low battery consumption,random access becomes essential for MTC to mitigate the coordination and interaction overheads in an IIoT network[3,4].However,as the number of interconnected devices increases,there is a prolonged surge in demand for machineoriented connections to accommodate the information exchange requirement between massive IIoT entities,which creates an avalanche of digital traffic volumes to today’s wireless communication networks[5].Collisions occurs frequency when IIoT endpoints transmit signal packets opportunistically without coordination.
Traditionally,signal collisions are prevented through media access control(MAC)protocols,e.g.the Carrier Sense Multiple Access with Collision Avoidance(CSMA/CA)in IEEE 802.11 standards where the collided signals are re-transmitted with a random back-off strategy[6].However,it is noticed that massive access attempts from versatile and massive MTC devices brings congestion to the whole network,thereby hindering service increasing of IIoT applications[7].The deficiency of conventional wireless networks in supporting massive random access becomes the main hurdle that may hamper the proliferation of IIoT.
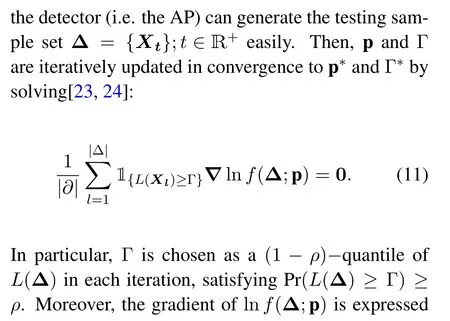
Alleviating the Random Access Channel(RACH)congestion problem has gained great attentions from both academia and industry[8,9].There are two major RACH congestion approaches in the literature.One approach is the coordinated MAC-layer protocols,as exemplified by the backoff mechanism design,access class barring,RACH resource dynamic allocation,etc[6,10].In this approach,delicately designed handshaking and channel allocation are preformed for efficient random access[11].The other collision resolution is the grant-free transmission approaches that employ preambles as user signatures and spreading codes for user data transmission without handshaking[12,13].These two approaches works well in legacy cellular systems with limited accessing devices.However,applying these approaches into IIoT applications with small data and massive transmissions would be challenging,because of the following reasons:
1)Coordinated random access protocols suffer from high control overheads.Moreover,frequent retransmissions are required ,which is unsuitable to less equipped IIoT devices with limited complexity and energy resources.
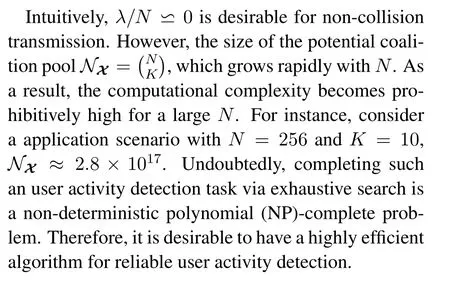
2)Despite of the satisfactorily reduced collision probability in grant-free random access approaches,complexity for user detecting and decoding grows exponentially with the number of preambles[14],which makes it unreliable in massive connection scenarios.
To overcome the RACH congestion problem with reduced signaling and control overhead,an intelligence enabled user signature code acquisition(USCA)approach is proposed by this paper.Thegrant-free random access(for uncoordinated multiple access)is considered,where a preset preamble is employed as the user signature code for data transmission.Undoubtedly,multiuser detection(MUD)plays a crucial role for user identification and user data recovery in RACH,where multiple active users transmit signals simultaneously.However,it is noticed that as the network size enlarges,complexity for optimal MUD grows exponentially.Therefore,it is of importance to design a low complexity and robust MUD algorithm to reliably accomplish the user identify and user data recovery tasks.
In this paper,we resort to a cross-entropy based intelligence search strategy to address the USCA issue[15].Instead of relying on deliberately designed user scheduling protocols,a low-complexity physical(PHY-)layer iterative USCA algorithm is proposed.Since each MTC device has equipped with an unique preamble for data transmission,the signal collision problem in RACH is solved.We also derive an approximate bit error rate(BER)upper bound to show the user data decoding performance of the proposed PHY-layer intelligence USCA algorithm.In a nutshell,the contributions of this paper are summarized as follows:
1)An intelligence enabled PHY-layer USCA algorithm is present.The cross-entropy based lowcomplexity iterative updating rule is proposed to guarantee that the computational complexity of USCA grows linearly with the network size.
2)The proposed PHY-layer intelligence USCA algorithm provides a trade-off between performance and complexity.An approximate bit error rate(BER)analysis is provided to show the user data decoding performance of the proposed algorithm.
The remainder of this paper is organized as follows.The literature on random access for MTC is reviewed in Section II.The system model and the PHYlayer random access problem formation are presented in Section III.The cross-entropy based intelligence USCA algorithm for PHY-layer random access is then proposed and analyzed in Section IV.Next,Section V provides the simulation results.Finally,Section VI draws the conclusion.
II.RELATED WORKS
In resent years,there is an increasing research interests on random access for the ubiquitous machine-type communications.Evidently,exploiting RACH for underlying connectivity provisioning is promising for the less equipped IIoT devices with sparse activity,limited computation,memory,and battery resources[16].
Inevitably,under a contention-based(or opportunistic)access mechanism,massive access attempts from versatile MTC devices brings congestion to the IIoI networks,signal collision becomes the most crucial burden that hinders the widespread deployment of IIoT applications[17].Various RACH procedures have been present to alleviate the RACH congestion problem,as exemplified the backoff mechanism design,access class barring,RACH resource dynamic allocation,etc[6,9].Deliberately designed user scheduling and resource allocation algorithm are performed by these approaches to combat RACH congestions[18].Considering the fact that MTC in IIoT applications are commonly with small data and massive transmissions,RACH procedures suffers from a high excessive signaling overheads,including scheduling and identifying an active device among the massive IIoT entities.
To mitigate the signaling and scheduling overheads,CDMA-based grant-free random access schemes are then considered for MTC[12].Differs from the conventional CDMA systems,the interconnected MTC devices are massive but only a little fraction of them are active.With unpredictable active devices in advance,identifying an active device in a massive IIoT network is computationally prohibitive[13].Therefore,investigating low-complexity user activity detection mechanisms becomes one of the research hotspots in grant-free random access schemes.Typically,compressed sensing(CS)techniques are employed to provide low-complexity active user detection[19].However,CS-based MUD strategies are sensitive to channel distortions,their performance deteriorate rapidly with error propagation.In[14],Markov chain Monte Carlo approaches are considered to provide a flexible trade-off between user detection performance and complexity.In[20],signal arriving times are identified as the user signature coexisted in the same resource block,and successive interference cancellation is employed for user date decoding.Besides,deploying the unmanned aerial vehicle(UAV)as an on demand aerial station is also a promising method to mitigate signal collisions within wide-area IoT applications[21,22].In a nutshell,existing schemes exploit the sparsity to relax or judiciously search over subsets of user signature codes for user activity detection with reduced complexity.
In this paper,by harnessing cross-entropy based intelligence,the proposed PHY-layer iterative USCA algorithm aims to iteratively learn and predict user signature code that are in active and finally get the approximate optimal estimation on active user detection and user data reception.Moreover,the lowcomplexity iterative updating rule guarantees that the implementation complexity of the proposed algorithm grows linearly with the network size.
III.SYSTEM MODEL AND PROBLEM FORMATION
As depicted in Figure 1,we consider a random access system consisting of one access point(AP)and multiple MTC devices.In particular,the system has a low activity factor.Therefore,the amount of the connected MTC devices are large,however,only a small proportion of them have a packet to transmit at a given slot in time.For convenience,we assume that there are totallyKactive users,andKfollows a Poisson random distribution:
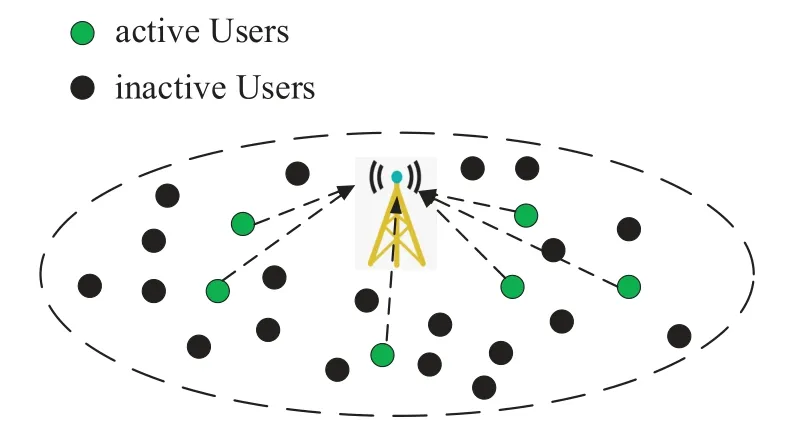
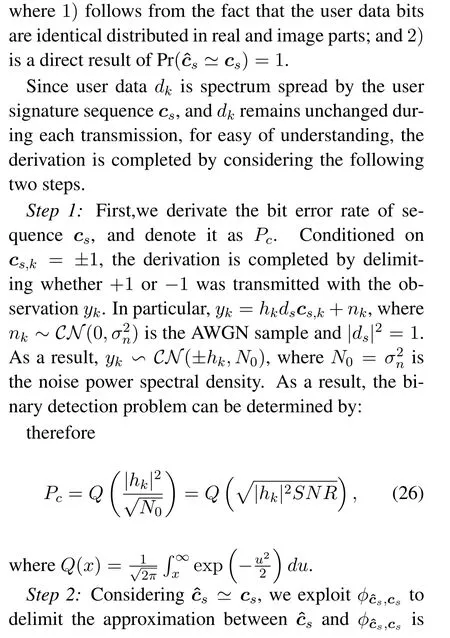
Figure 1.Illustration of the random access system with an AP and massive MTC devices where only a small proportion of MTC devices are active.
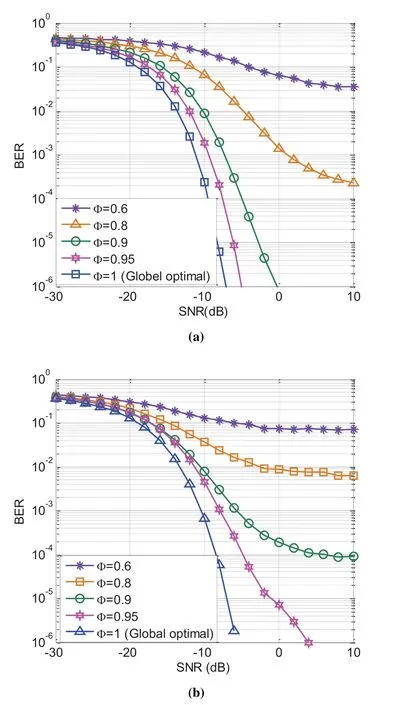
Figure 2.Performance of the USCA algorithm with different Φ:a)single active user scenario;b)multiple active user scenario.
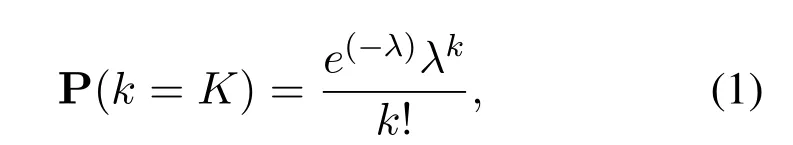
IV.CROSS-ENTROPY BASED INTELLIGENCE USER SIGNATURE CODE ACQUISITION
In this section,we model the user activity detection problem as an user signature code acquisition process.A cross-entropy based intelligence PHY-layer USCA algorithm is proposed to iteratively learn and predict user signature code that are in active and finally get the approximate optimal estimation on active user detection and user data reception.
4.1 Single Active User Scenario
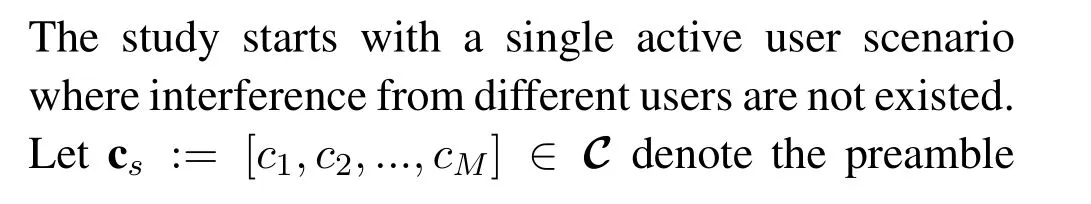


Algorithm 1.Cross-entropy based intelligence USCA algorithm for single active user.Input:The received signal y;Output:Estimated user signature sequence ˆcs;estimateduserdata ˆds.1:Stage I:Initialization State Set initial state p :=[pi =1/2]M i=1,ˆcs = Ø,ˆds =0;Set temp variable ρ;Λ = Ø; {Xt = Ø}Tt=1;iterative indicator t=0 and threshold ΓL.2:Stage II:User signature code Acquisition State 3:while ∃pi /∈{0,1}and Γ ≤ΓL do 4: t ←t+1;5:Generate T binary sequences {Xt}Tt=1 according to p;6:Calculate L(Xt);7:Resort Δ:=images/BZ_191_1649_1367_1675_1413.png{Xt}Tt=1 ∪Λimages/BZ_191_1914_1367_1940_1413.pngin descending order;8:Set Γ = L(X■ρ·T■);where■·■is the floor function.9:Update p:={p1,p2,...pM}via pj =images/BZ_191_1674_1732_1723_1777.png|Δ|t=1 IL(Xt)≥Γ·Xi,j+1 images/BZ_191_1750_1809_1798_1854.png|Δ|t=1 IL(Xt)≥Γ 2 10:Update Λ:={Xi}■ρ·T ■2 i=1 11:end while 12:end while 13:Generate ˆcs =2·p-1;14:Calculate ˆds =sgn(R{ˆcTs ·y})+sgn(I{ˆcTs ·y})j.


4.2 Multiple Active User Scenario
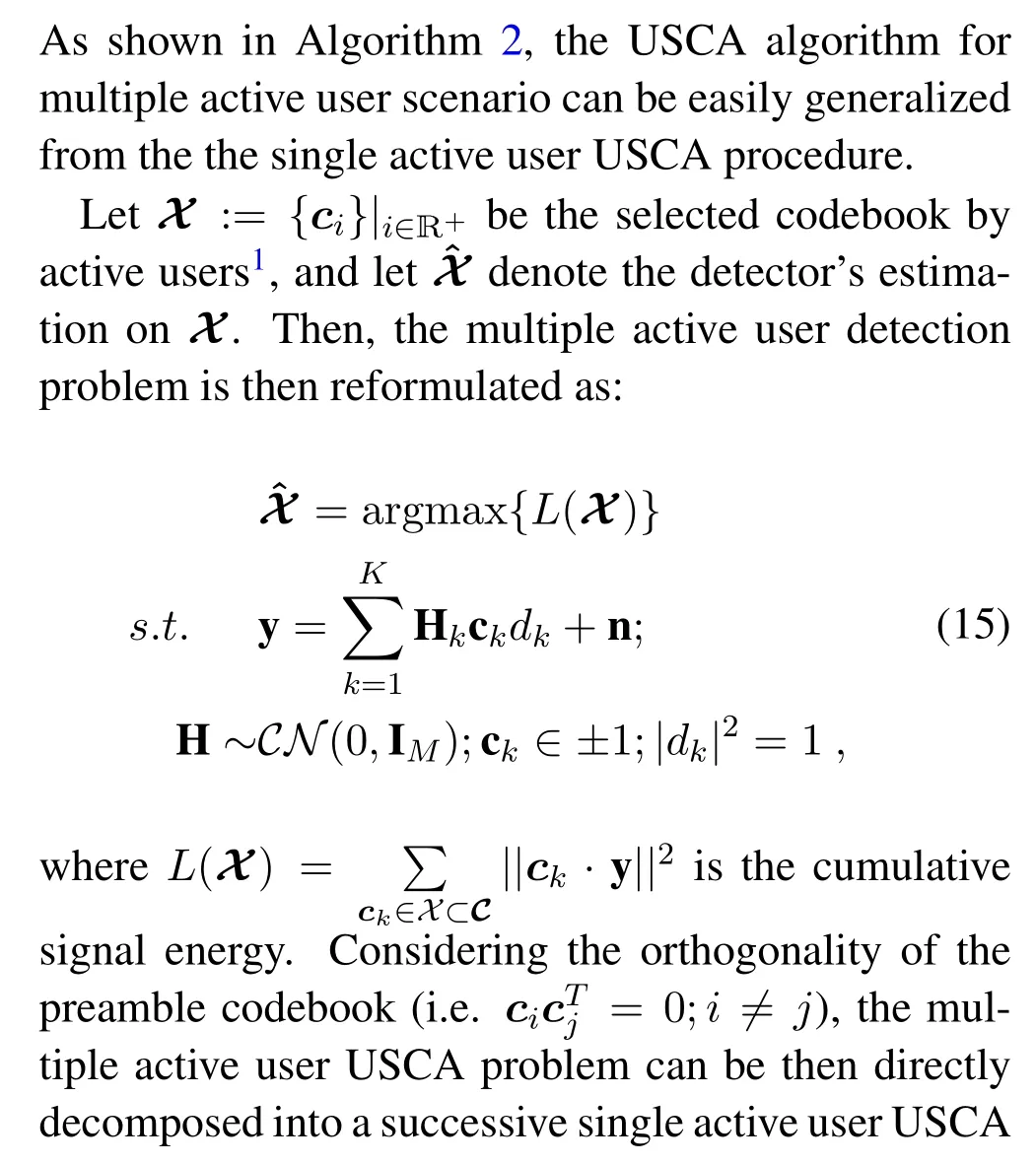
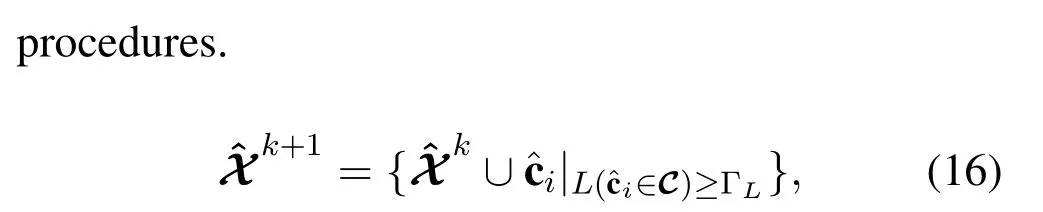

Algorithm 2.Cross-entropy based intelligence USCA algorithm for Multiple active user.Input:The received signal y;Output:Estimated user signature sequence set ˆX;estimated user data ˆdk;(k = 1,2,...,K).1:Stage I:Initialization State Set initial state p :=[pi = 1/2]Mi=1,ˆX = Ø,ˆdk|Kk=1 =0;Set temp variable ρ;Λ=Ø;{Xt =Ø}Tt=1;Set thresholds ΓL Set iterative indicator t=0,k =0.2:Stage II:User signature code Acquisition State 3:while 1 do 4:while ∃p(j)i /∈{0,1}do 5:t ←t+1;6:Generate T binary sequences{Xt}Tt=1 with p;7:Calculate L(Xt);8:Resort X :=images/BZ_192_1704_1460_1731_1505.png{Xt}Tt=1 ∪Λimages/BZ_192_1969_1460_1996_1505.pngin descending order;9:Set Γ = L(X■ρ·T■);where■·■is the floor function.10:if(t ≤tmax or Γ ≥ΓL)then 11:Update p:={p1,p2,...pM}via pj =images/BZ_192_1695_1883_1744_1928.pngT+|Λ|t=1 IL(Xt)≥Γ·Xi,j+1 images/BZ_192_1770_1959_1819_2005.pngT+|Λ|t=1 IL(Xt)≥Γ 2 12:else 13:Break;14:end if 15:end If 16:Update Λ:={Xi}■ρ·T ■2 i=1 17:end while 18:end while 19: k ←k+1;20:Generate ˆck =2·p-1;21:Calculate ˆdk=sgn(R{ˆcTk ·y})+sgn(I{ˆcTk ·y})j.22:y ←y-ˆck ˆdk;23:Reset p(0) :=[p(0)i =1/2]Mi=1;Λ=Ø;{Xt =Ø}Tt=1.24:end while 25:end while
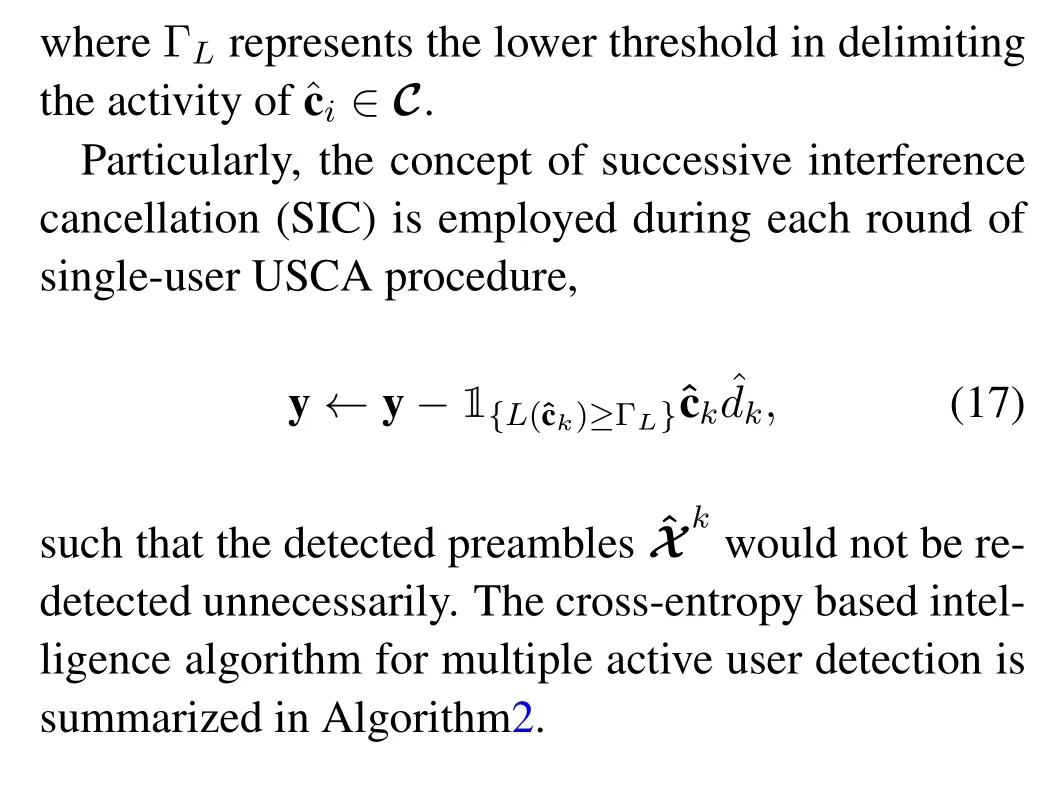
4.3 Convergence and Decoding Performance Analysis


V.SIMULATION RESULTS AND DISCUSSION
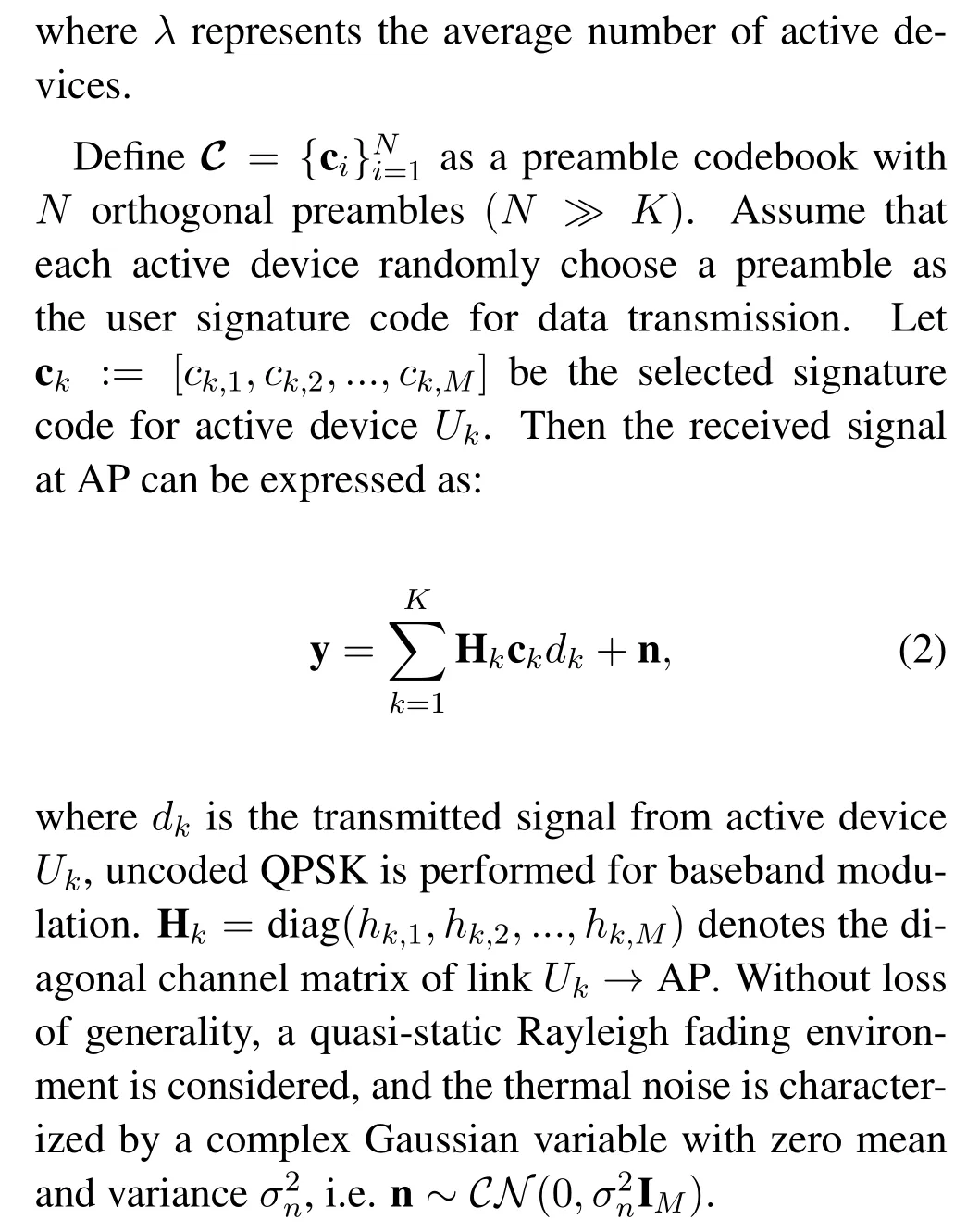
In this section,simulation results are presented to show the performance of the cross-entropy based intelligence USCA algorithm.During the simulation,a random access network with totally 2000 MTC devices has been considered.In particular,the MTC devices are assumed with sparse activity,and the number of active devices follows the Poisson distribution shown in Eq.(1).Without loss of generality,Walsh sequences with lengthM= 256 are used to establish the preamble codebook,uncoded QPSK are performed for user data modulation,and the wireless channel betweenUk → APis modeled by a quasi-static Rayleigh fading environment withBER is performed as the main measurement for USCA performance evaluation,since user data can be correctly decoded if and only if its signature sequence has been reliably captured in advance.
Figure 2 compares the user data decoding performance of the USCA algorithm with different Φ.The single active user scenario and multiple active user scenario are studied in Figure 2a and Figure 2b,respectively.Particularly,the symbol Φ is an abbreviation ofφˆci,ciwhich denotes the Pearson’s linear correlation coefficient between ˆciandci.In USCA algorithms,the detector(or AP)is designed to progressively learns to obtain an global optimal estimation on user signature sequences by iteratively recording and analyzing the convergence of each element inci.As can been seen in Figure 2,the global optimal solution is obtained with Φ = 1 for both single and multiple active user scenarios.From Figure 2 we can also see that the decrement in Φ results in an obvious degradation in the user data decoding performance.More specifically,an error floor can be clearly observed for Φ = 0.8 and Φ = 0.6 whenSNR ≥5dBunder the single active user scenario.That is because when Φ is small,a large proportion of the element inciwould be wrongly estimated.As a result,USCA failures becomes the main barrier for user data decoding instead of the noise and channel distortions.Thus,user data are erroneously decoded with high probability.
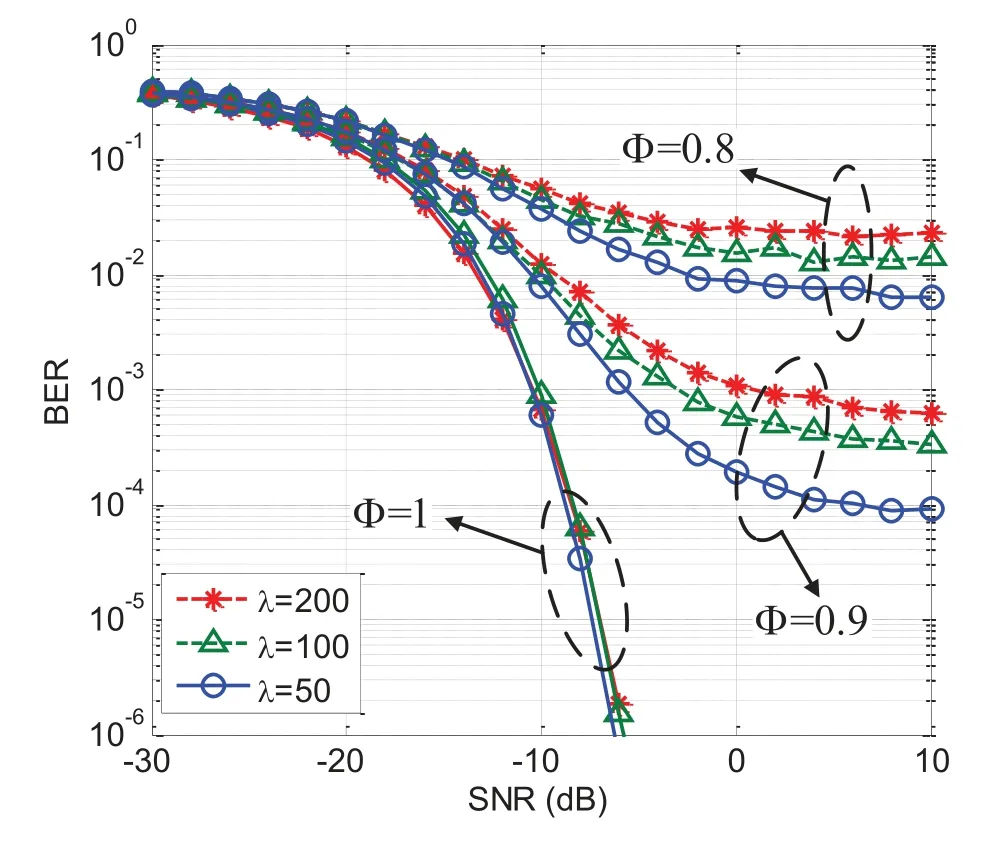
Figure 3.Performance of the USCA algorithm for multiple active user scenario with different Φ and λ.
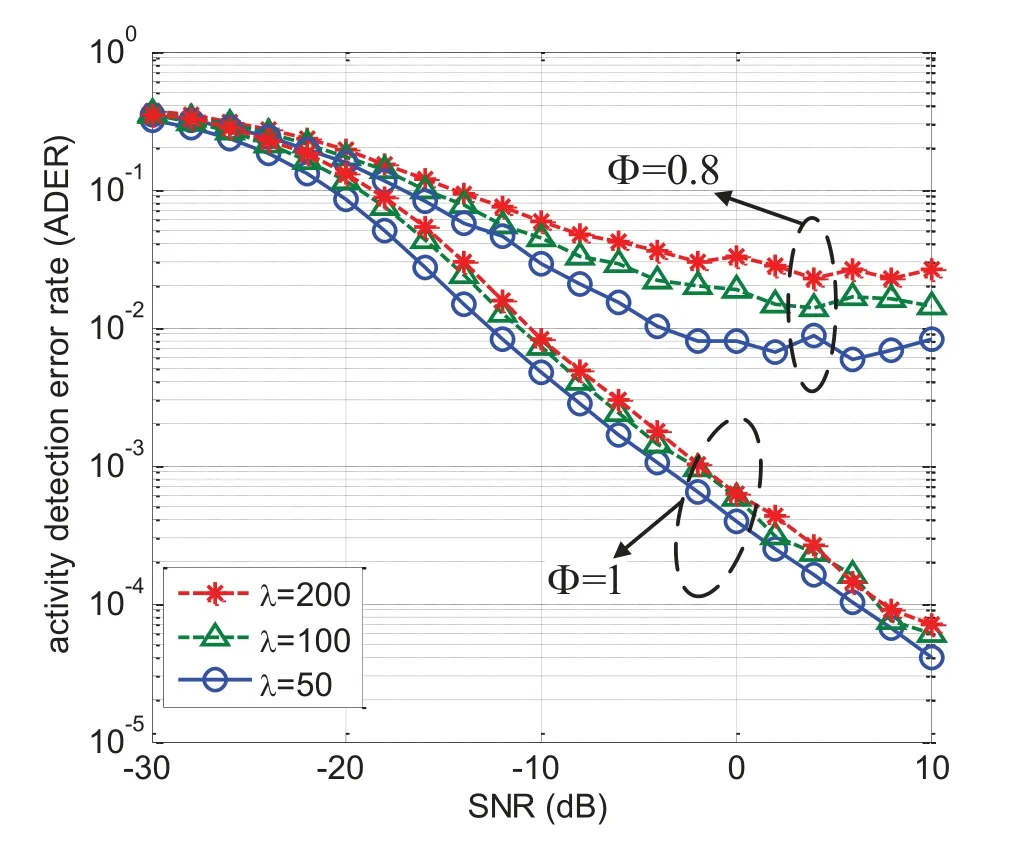
Figure 4.ADER performance of the cross-entropy based intelligence USCA algorithm for different Φ and λ.
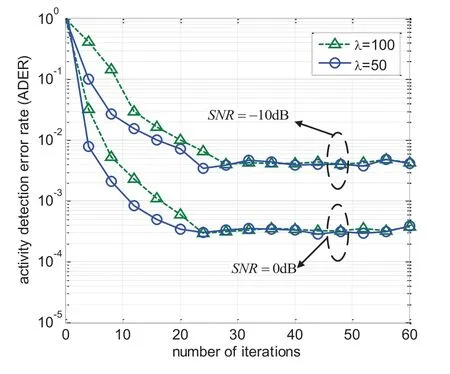
Figure 5.ADER performance of the cross-entropy based intelligence USCA algorithm for different numbers of iterations when λ ∈{50,100}and SNR ∈{-10,0}dB.

VI.CONCLUSION
In this paper,an intelligence enabled PHY-layer USCA scheme is proposed to overcome RACH congestion problem with reduced signaling and control overhead.In the proposed USCA scheme,the detector is designed to progressively learn to get the approximate optimal estimation on active user detection and user data reception by iteratively analyzing the convergence of the received signal.The cross-entropy based low-complexity iterative updating rule guarantees that the proposed USCA algorithm is computational feasible.An approximate BER performance analysis has been carried out to show the performance of the proposed intelligence USCA algorithm.Besides,simulation results also demonstrates that the proposed USCA algorithm achieves a approximate optimal performance with a reasonable computational complexity.
ACKNOWLEDGEMENT
This work was supported in part by Natural Science Foundation of Heilongjiang Province of China under Grant YQ2021F003,in part by the National Natural Science Foundation of China under Grant 61901140,in part by China Postdoctoral Science Foundation Funded Project under Grant 2019M650067 and in part by Science and Technology on Communication Networks Laboratory under Grant SCX21641X003.
APPENDIX
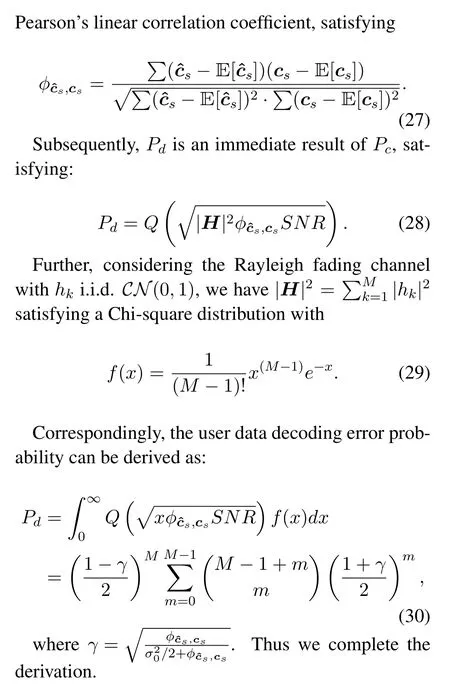
Here we show the detailed derivation of the Eq.(22).Typically,the BER for user data decoding can be formulated as follows:
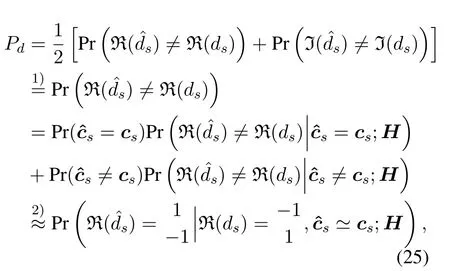
- China Communications的其它文章
- Wireless Network Requirements and Solutions for the Future Circular Collider:A Hostile Indoor Environment
- Time-Domain Dual Component Computation Diversity Based on Generalized Hybrid Carrier
- On the Performance of Active Analog Self-Interference Cancellation Techniques for Beyond 5G Systems
- Multi Object Tracking Using Gradient-Based Learning Model in Video-Surveillance
- A Task-Resource Joint Management Model with Intelligent Control for Mission-Aware Dispersed Computing
- Research on Online Education Consumer Choice Behavior Path Based on Informatization

