Securing Parked Vehicle Assisted Fog Computing With Blockchain and Optimal Smart Contract Design
Xumin Huang,, Dongdong Ye, Rong Yu,, and Lei Shu, Senior
Abstract—Vehicular fog computing (VFC) has been envisioned as an important application of fog computing in vehicular networks. Parked vehicles with embedded computation resources could be exploited as a supplement for VFC. They cooperate with fog servers to process offloading requests at the vehicular network edge, leading to a new paradigm called parked vehicle assisted fog computing (PVFC). However, each coin has two sides.There is a follow-up challenging issue in the distributed and trustless computing environment. The centralized computation offloading without tamper-proof audit causes security threats. It could not guard against false-reporting, free-riding behaviors,spoofing attacks and repudiation attacks. Thus, we leverage the blockchain technology to achieve decentralized PVFC. Request posting, workload undertaking, task evaluation and reward assignment are organized and validated automatically through smart contract executions. Network activities in computation offloading become transparent, verifiable and traceable to eliminate security risks. To this end, we introduce network entities and design interactive smart contract operations across them. The optimal smart contract design problem is formulated and solved within the Stackelberg game framework to minimize the total payments for users. Security analysis and extensive numerical results are provided to demonstrate that our scheme has high security and efficiency guarantee.
Nomenclature
I. Introduction
VEHICULAR fog computing (VFC) has been emerged as one of the most promising directions of fog computing in transportation domains that provides lightweight and ubiquitous computing at the vehicular network edge [1]. Compute-intensive applications such as autonomous driving and augmented reality are supported well by utilizing proximal computation resources to improve service provision [2]. In vehicular networks, parked vehicles (PVs) comprise a high proportion of daily vehicles and meanwhile, have underutilized resources for task execution. In contrast to regular fog servers,PVs are also competent to process user requests and become special fog nodes [3]. A new paradigm called by parked vehicle assisted fog computing (PVFC) is defined to depict convergence of PVs and original VFC [4]. However, critical security issues should be addressed for the large-scale system implementation considering the distributed and trustless computing environment.
Centralized computation offloading causes security challenges to PVFC. For enhancing the computing capacity,more PVs are expected to undertake workloads but this results in increasing risks due to the untrustworthiness of distributed performers. In the centralized scheme, requesters and performers are strictly managed by a third party as a central authority. The scheme neglects the possible trustless environment and accessible records of network behaviors. As a consequence, the scheme based on the “trusted” central authority without tamper-proof audit gives rise to the following security threats:
1) Vulnerability:The central authority easily suffers from single point of failure, remote hijacking and DDoS attacks.Moreover, if the authority is compromised, private information of requesters and performers may be revealed,leading to privacy disclosure.
2) Maliciousness:Misbehaving requesters cause flooding attacks by submitting forged requests. Malicious performers may perform spoofing attacks, for example, pretending to accept workloads, and refusing to feedback results or upload incorrect results. Then the aggregation of all the results is procrastinated.
3) Untraceability:Without recording necessary proofs,requester and performers probably launch reward repudiation of giving and reception, respectively. Free-riding behaviors of selfish requesters and cheating behaviors of greedy performers cannot be examined.
To cope with the issues, we leverage blockchain to provide security protection for PVFC. Thus, a dedicated blockchain system, called by PVFChain, is introduced to record and validate relevant information about requesters and performers in computation offloading. As a public and immutable ledger,blockchain is composed of a chain of blocks and each block consists of a set of auditing transaction records. Consensus nodes are particularly employed as regular auditors (i.e.,miners) to verify a new block for token rewards. Valid blocks will be directly or indirectly stored in local blockchain replicas of nodes. Nowadays, blockchain has been widely applied to vehicular networks for diverse purposes, for example, simplifying distributed key management in heterogeneous vehicular communications [5], encouraging users with incentives for anonymous announcements [6] and achieving secure data storage and sharing among vehicles [7].
Owing to the great advantages of blockchain, the decentralized PVFC is fulfilled by depending on a majority of consensus nodes without any third parties, eliminating potential security risks. Request posting, workload undertaking, task evaluation and reward assignment are organized by using smart contracts, which are computer programs automatically running and published to miners for auditing. Each network entity registers to PVFChain and network activity is instructed through the smart contract execution to follow the contact based agreement. Through data auditing, accessible records about behaviors of requesters and performers are tamper-resistant. Misbehaviors of malicious requesters and performers are completely exposed due to the embedded transparency, irreversibility and accountability of smart contracts. Finally, PVFChain supports 1) identity authentication, 2) request validation, 3)computation verification, and 4) reward integrity to guard against a variety of network attacks.
In this paper, we investigate the PVFChain and optimal smart contract design for guaranteeing network security and efficiency of PVFC. Smart contract operations are designed to confirm behaviors of requesters and performers with security and privacy awareness. Based on recording proofs, network activities become uncompromising and traceable to overcome security threats in the trustless environment. Moreover, we study an optimal smart contract design problem when employing a fog server and several PVs to conduct workloads for a requester. The problem is formulated from an economic viewpoint and solved by the Stackelberg game approach. The requester acts a leader to optimize reward policy for performers (followers) responding with the number of undertaking workloads. The total workloads are allocated well to minimize the overall payment and meet task requirements simultaneously. The main contributions of the paper are summarized as follows.
1) We introduce PVFChain where blockchain with smart contract is exploited for PVFC to implement offloading services in a decentralized manner.
2) We design a feasible system model for large-scale application of PVFChain. Interactive smart contract operations across the network entities are described to address security issues.
3) We apply the Stackelberg game solution to achieve the optimal smart contract design with fairness. The reward policy is optimized to reduce the service fee of the requester while considering utility maximization for the performers.
The rest of this paper is organized as follows. Section II presents the related work. Section III describes crucial network entities and smart contract operations across them in PVFChain. In Section IV, the optimal smart contract design problem is formulated as a payment minimization problem.After that, the problem is solved within the Stackelberg game framework in Section V. Security analysis and performance evaluation of our scheme are provided in Sections VI and VII,respectively. Finally, Section VIII concludes this paper.
II. Related Work
A. Vehicular Fog Computing
Recently, researchers have presented the concept, network architectures and use cases of VFC. The concept of VFC is first introduced by Houet al.[1]. Slowly moving and parked vehicles can become crucial computational infrastructures to enlarge the computing capacity of VFC. In addition, the capability of VFC was analyzed and evaluated based on a real vehicular mobility trace in large-scale urban environment [8].Huanget al.[9] further proposed a hierarchical architecture to clarify three-level decision-making capability in the entire network of VFC. Case studies were also provided to explain how the proposed network architecture enhances current vehicular applications, e.g., traffic control, driving safety and entertainment.
Moreover, a variety of offloading schemes are studied for VFC in different application scenarios. The deep reinforcement learning was leveraged to construct an intelligent offloading system for VFC [10], where task scheduling and resource allocation were jointly optimized to improve overall user experience. The authors in [3] and [11]considered forwarding traffic among statistic cloudlet, and dynamic parked and moving-vehicle-based fog nodes, and studied how to minimize the system transmission delay.Similarly, Zhuet al.[12 ] focused on the optimal task allocation between fixed fog servers and nearby moving vehicles as mobile fog nodes to minimize a weight sum of the maximal service latency and total quality loss. In [4], PVs were exploited as lightweight fog nodes to coordinate with regular fog nodes to realize smart parking and jointly provision delay-sensitive computing services. Particularly,auction theory was used to provide PVs with available parking places and monetary rewards in a considerate way. Reference[13] also paid attention to cooperative task execution between PVs and a fog server, and tried to determine workload allocation between them to minimize the service fee in computation offloading. But general task requirements were not considered well.
Security issues are seldom discussed in the previous works.Most of them focused on optimizing task scheduling in a centralized way for improving the overall performance. The efficiency of the schemes will be degraded with the increasing number of malicious requesters and performers. Thus, our work explores security threats in offloading services of PVFC and resorts to blockchain with smart contracts for enhancing the security protection.
B. Blockchain for Vehicular Networks
Based on the high transparency, fault tolerance and tamperproof features, blockchain has been proposed to vehicular networks in different domains. For example, blockchain is convinced to have real benefits in promoting key transfer between two heterogeneous vehicular communication domains and realizing the verifiable and authentic key transfer processes [5]. When vehicles access different VFC data centers, a cross-datacenter authentication and key exchange mechanism was designed by using blockchain and elliptic curve cryptography, to support information confidentiality and mutual authenticity [14]. Performance evaluation demonstrated that the mechanism had lower computational cost and communication overheads.
The anonymity of blockchain also caused widespread concerns. Reference [6] introduced a blockchain-based incentive mechanism for encouraging vehicles to send announcements in traffic environment with privacy preservation. Similarly, the authors in [15] presented an anonymous reputation evaluation system for eliminating forged messages from malicious vehicles in the blockchain environment. The work in [7] proposed a dedicated consortium blockchain where roadside units are responsible for collecting and auditing data generated by vehicles, to guarantee high-quality data sharing among vehicles. Besides,Yanget al.[16] put forward a decentralized trust management scheme for secure message delivery among vehicles. Vehicles were employed to evaluate the credibilities of traffic-related messages, and roadside units become miners to collect ratings from vehicles and validate them.
Motivated by the existing works, we believe that the inherent distributed nature with consensus mechanisms makes blockchain suitable for orchestrating offloading services without any third party and fulfilling the decentralized PVFC.Interaction among untrusted requesters and performers can be transcoded into smart contracts and accessible on the PVFChain for validation. With the adoption of on-chain smart contracts, the credibility, programmability and traceability of network behavior records are exactly guaranteed over time. At the same time, we formulate the optimal smart contract design problem and aim to design a user-centric incentive mechanism in computation offloading.
III. PVFChain Design
A. Network Entities
As illustrated in Fig. 1, crucial network entities are proposed for feasible implementation of PVFChain. Overall, the related network entities include requester, performer and miner.When running a compute-intensive application, a mobile vehicle on the road posts a computation task to PVFChain,triggering a smart contract. The background system of PVFChain assigns an agent to be in charge of the task. The agent orchestrates offloading services at the vehicular network edge. In the PVFC environment, the agent seeks a fog server near a parking lot and employs idle PVs in the parking lot for cooperative task execution. For the necessary performer selection and decision making, the performers may be required to record some status information to the smart contract. The agent is authorized to access to the smart contract and hold prior knowledge about the task requirements and performers.

Fig. 1. Network entities in PVFChain: requester, performer, and miner.
More specifically, cooperative and traceable offloading services are performed as follows. When receiving the submitted task with customized requirements, the agent notifies the fog server and several PVs to jointly handle the task for getting rewards. Based on the promising rewards, the fog server and each PV response with the corresponding numbers of undertaking workloads. After gathering the responses, the agent partitions the whole input data into various subsets with different data sizes, and transmits them to the fog server and every PV, respectively. Performers conduct the given workloads and upload output results to miners in PVFChain, which check them whether to meet the task requirements, e.g., accuracy performance. By executing the consensus protocol and third-party methods, valid output results are identified. The output results are aggregated by the agent to obtain a final result for the requester. Rewards are assigned from the digital wallet of the requester to those qualified performers. For traceability, relevant information including request posting, workload undertaking, task evaluation and reward assignment is recorded to form a list of transactions bundled into a block. Finally, confirmed blocks are added to PVFChain at specific intervals by miners. Next,we provide more details about the network entities as follows.
1) Requester in Computation Offloading:The offloading request is published to PVFChain through a client, which offers users with entrance to submit a computation task with task requirements. The requester utilizes key pairs issued by PVFChain for ensuring secure communications and avoiding revealing true identity. The request is sent to the nearest access point, e.g., roadside unit and base station, and further delivered to generate the new smart contract in the background system. Moreover, the requester is required to pay a deposit in advance.
The requester grants the trusted agent to specially process the task. Thus, those fog servers and PVs managed by the agent are able to realize the request. As a service proxy, the agent represents the requester to design an incentive mechanism for different performers, in order to minimize the overall payment and meet the task requirements simultaneously.
2) Performer in PVFC:In PVFC, there exist two kinds of performers for supporting proximal computing at the vehicular network edge. Here, fog servers refer to specialized edge servers applied to the transportation domains and are particularly deployed to serve vehicular users. In addition,modern vehicles are equipped with powerful processing units and large storage devices, and can be scheduled for task execution [17], particularly when they enter to the parked state with idle time. Compared with a fog server, a PV is of lightweight computing capability. But in a region, hundreds of PVs are distributed while only several fog servers are deployed. Service fee in employing a fog server is generally higher than that of scheduling a PV, due to different energy consumption cost of processing workloads.
PVFChain also provides client accounts for performers to register identities, view offloading requests and write information into smart contracts. Facing with a request,performers make decisions whether to accept it and the number of workloads independently, with the given monetary rewards. Before processing workloads, the performers are also required to afford a deposit in advance. Then the agent transmits input data with various data sizes to the fog server and different PVs, respectively. In particular, the agent communicates with local PVs with the help of a roadside unit locating in the center of the parking lot. All the performers upload output results via clients to verify their computation work, thereafter, are rewarded or punished according to auditing results.
3) Miner of PVFChain:In this paper, we consider that PVFChain could be a consortium blockchain so that write and read permissions of transaction records are granted to specific legal entities. According to [7], some roadside units are preselected and authorized to perform the consensus process in vehicular networks. For improving mining, miners also exploit available computing ability of fog servers connecting to the roadside units, to promote the mining procedure and reduce propagation and consensus time of new blocks [18].For security guarantee, the typical proof of work (PoW) is utilized as the consensus protocol, where miners compete against each other for winning the privileges of block generation.
In PVFChain, the procedure that a requester posts an offloading request, and a performer participates in serving it,is treated as a transaction in Fig. 1. We take requesterand performerwhose public and private keys areandrespectively, as an example. The transaction mainly consists of the following parts: transaction IDrelated information about task posting and signed by the requesterauxiliary information to describe task execution and signed by the performerand digital currency circulation caused by reward assignment.Here,includes task requirements, task priority and promising rewards provided by the requester.includes the received input data, the number of processing workloads, output result, actual finish time, evaluation result for the computation work and so on. The addresses about digital wallets of the requester and performer are hash addresses corresponding to their public keys, respectively.
To confirm transactions, miners audit new transactions according to the contract-based agreement. The auditing operations are described as follows. 1) For new transactions,an auditor authenticates the identities of the requester and performers, and checks the validity of the transactions. 2) It validates whether the requester and the recruited performers with the deposits are recorded, and evaluates whether the performers upload the correct output results within task deadline. 3) The auditor finally verifies how many rewards are transferred from the requester to performers to follow the reward policy.
Confirmed transactions regarding a common requester are listed into a new block, which is accessed by other auditors for consensus. Finally, the validated block is attached with a time stamp and linked to the previous block on the PVFChain.
B. Smart Contract Operations
We design interactive smart contract operations across the network entities to construct a reliable and traceable computation offloading environment. Then network behaviors are recorded and transcoded into smart contracts. As selfexecuting scripts, smart contracts are stored on the PVFChain and triggered to cope with transactions. They are automatically executed by related network entities in a predefined way. Each smart contract has a unique address on the PVFChain and allows us to express business logic for restricting network behaviors in offloading services.Nowadays, there exist several commercial platforms to support smart contracts residing on the blockchain. One of the typical platforms is Ethereum [19] and we encode smart contracts on the platform.
Smart contract operations between a requester, a service provider with employed performers and miners are shown in Fig. 2. A smart contract ensures that both the requester and performers reach an agreement and follow their prescribed behaviors. To this end, PVFChain include two parts: client as user interface and blockchain for verification. Clients allow all the network entities to interact with others while the blockchain part is to validate generated transactions.

Fig. 2. Smart contract operations.
Particularly, miners are employed in PVFChain to verify computation work for token rewards by using the third-party methods, e.g., [20] and [21]. The methods could be directly utilized to promptly check whether the output results are matched with the allocated input data and satisfy the accuracy requirement, without reexecuting the tasks. We take superresolution of license plates as an example to demonstrate how the third-party methods are used for computation verification. A requester in computation offloading may have several low-resolution images of license plates, and also own a trained DeblurGan [22], which was developed as a generative adversarial network model to achieve blind motion deblurring for given images. In PVFChain, the requester transfers images with the DeblurGan model to an agent. The agent recruits the fog server and multiple PVs to receive input data and perform the image superresolution tasks. By executing the DeblurGan model, a performer calculates new image datay(as output result) with respect to original image dataAfter that, a miner is easy to measure the meansquared error betweenandas proposed in the above reference, and further judge whetheris qualified to meet the performance of image superresolution. Finally, computation work is evaluated accordingly.
In summary, smart contract operations are conducted as follows.
Step 1: The requester submits a computation task with task requirements and a deposit to PVFChain by using the client.An agent is then specifically assigned to process the task.
Step 2: Performers can view the offloading request with the task requirements through the clients.
Step 3: Some performers feed back positive responses to the request, and are required to upload basic information about task execution along with the responses.
Step 4: The agent is authorized to realize and select appropriate performers according to the prior knowledge, and determine reward assignment for different performers.
Step 5: Suggested by the agent, the client of the requester offers promising rewards to the performers.
Step 6: According to the given rewards, the performers choose a part of workloads to process, and receive the corresponding input data from the agent for task execution.
Step 7: The performers allocate computing resources to accomplish workloads and acquire output results. They write their identities, node types, the number of processing workloads and output results into the smart contract.
Step 8: In the smart contract, a specialized transaction is triggered to authorize miners to evaluate the output results.The miners select appropriate third-party methods, based on application scenarios, to put forward evaluation results, which tell whether the according computation work is qualified.Once there exist unqualified results, backup fog servers are activated automatically to supplement the corresponding output results.
Step 9: By collecting all the output results, the agent aggregates them to form a final result and transmits it to the client of the requester.
Step 10: Ultimately, the requester offers extra payments in addition to the deposit. The promising rewards with the submitted deposits are assigned to qualified performers.
IV. Optimal Smart Contract Design Problem
There exists an essential problem for designing an optimal smart contract to encourage different performer for accomplishing workloads in PVFChain. This refers to a payment minimization problem for a requester in computation offloading, where the whole workloads are optimally allocated to a fog server near a parking lot and several PVs in the parking lot for a cooperative task execution.
Particularly, when there exist a set of requestersto be served simultaneously, we consider that the allocated computing resources from the fog serverand each PVto the requesterare equal toandrespectively, whereandare the total computing resources owned by the fog server and the PV, respectively,andrepresents the task priority. We also haveGivenandwe can pay attention to separately coping with the payment minimization problem for each requesterHence, for simplicity, we investigate how to incentivize fog serverand each PVfor serving a single requesterin the next part.
A. Utility Function of Fog Server
When running a compute-intensive application, a vehiclesends an offloading request with task requirement. The task is described in four termsTheindicates the input data size. Compared with the size of input data, the size of output data is neglected [23]. The required workloads of accomplishing the task arein terms of the number of CPU cycles. We havewhereis an application-centric parameter related to the type of running application [24]. As forit represents the latency requirement. After realizing the request, an agent seeks the fog server and appropriate PVs for undertaking workloads.
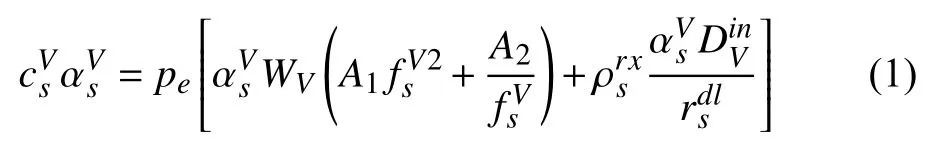
Besides, additional task execution gives rise to temporary inconvenience for the fog server, which may have individual workloads at that time. The incurred inconvenience resulted by serving the external request is modeled as[26],whereis a status-related parameter to indicate the ratio between current workloads and the maximal workloads that can be undertaken. To summarize, the utility function of the fog server is expressed as acquired rewards minus energy consumption cost and incurred inconvenience,

B. Utility Function of Parked Vehicle
A part of PVs are selected to support the offloading service.Due to parking behaviors and resource availability, various PVs show different serviceabilities in being employed to execute tasks with reliability and efficiency guarantee.
According to the existing work in [13], the predicted probability of a PV that will continue to stay parked in a whole task scheduling time period, can be utilized as a crucial metric to evaluate the serviceability of the PV. As an employer, the agent is responsible for seeking PVs with higher serviceabilities periodically. The time span of this time period is denoted as. With the everlasting records and complex analysis, the probability density function about parking durations of PVs is acquired. The function is expressed bywhereis the parking duration and has a considerable range,The accumulative parking durations up to the beginning of the time period is detected asWe estimate the probability of staying continuously in the following time period by

On the other hand, computing capability of PV(namely,is regarded as the other metric to evaluate the serviceability. For computing efficiency, a qualified performer is required to have great computing capability with regard to a threshold valueHence, the serviceability of the PV for serving requester(represented by) is equal to a weight sum ofand

In the incentive mechanism, all the PVs are encouraged to compete against each other for earning income from the offloading service. By jointly considering the number of workloads and serviceability for task execution, the agent allocates rewards to PVbased on the following the rule:whereis the percentage of the workloads undertaken by the PV andis the total reward offered by requesterto award all the participating PVs. In this way, the agent considers fair reward allocation, and also encourages those PVs with higher serviceabilities to undertake more workloads.
Similarly, task execution causes energy consumption cost to PVDuring the task execution, the power consumption of CPU execution is[27], whereandare the hardware parameter and computational speed respectively, of the CPU to serve the requester. Then the consumed energy for CPU execution is. The agent transmits the input data to each PV with the help of a roadside unit in the center of the parking lot. Considering the data transmission cost, we calculate the total energy consumption costby

We formulate the downlink channel model between PVand the roadside unit with the utilization of orthogonal frequency division multiplexing technology. Sois acquired by

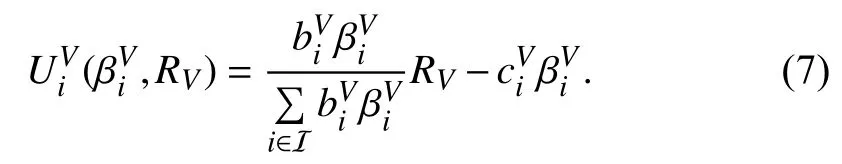
For utility maximization, the PV makes a decision onwith respect toand strategies of other PVs.
C. Payment Minimization Problem
As for the requesting vehicle, the utility function is directly bound up with service fee in computation offloading. Note that the requesting vehicle only consumes energy to submit the task with task requirements to the agent through the client.After that, the agent acts as a trusted service proxy to partition the task and transmit according input data to the fog server and parked vehicles for a cooperative task execution.Compared with the total payment given to the performers,communication cost of the requesting vehicle is fixed, and can be neglected in this paper.
To employ the fog server and several PVs, cost function of the requester in terms of the total payment is shown by

The agent tries to minimize the total payment for maximizing user satisfaction and meeting task requirements simultaneously. First, the whole workloads should be entirely offloaded,The task also has the strict latency requirement for processing on the fog server and each PV.The total delay on the fog server side includes data transmission time and task execution time, namely,

Similarly, the total delay resulted by on the PV side is

For minimizing the service fee of the requester, the agent optimizes various rewards for different performers by solving the following problem:

In PVFChain, the optimal smart contract design problem is transformed to solve the payment minimization problem above for enriching user satisfaction.
V. Stackelberg Game Solution
We utilize the Stackelberg game approach to solve the payment minimization problem in PVFChain. The proposed Stackelberg game model can be solved by the subgame perfect Nash equilibrium. According to previous works, a subgame perfect Nash equilibrium indicates a Nash equilibrium of every subgame in the original game. We exploit backward induction as the typical method to discuss subgame perfect equilibrium.
A. Stackelberg Game Model
In this paper, we design the incentive mechanism for two kinds of performers by modeling the strategic interaction between them and the requesting vehicle as a two-stage singleleader multi-follower Stackelberg game. The agent of requesting vehicledetermines the reward policygiven to the fog server and PV group, respectively. In turn, the performers reply to the agent with the numbers of undertaking workloads for maximizing the utilities with respect to the promising rewards, as explained in (2) and (7), respectively.Particularly, each PV belonging to the group competes in a noncooperative workload determination subgame. In summary, we define the two-stage reward-participation game as follows.
Stage 1: Reward policy. The agent of requesting vehicleoptimizes the reward policy for various performers with different responses in order to minimize the payments and satisfy necessary constraints shown by problem in (11)


The objective of the Stackelberg game between the requester and all the performers is to find the unique Stackelberg equilibrium at which the leader obtains the minimal payments given the best responses of the followers. At that time, both of them have no motivations to unilaterally change their decisions.Given the single-leader multi-follower Stackelberg game, we further define the Stackelberg equilibrium as follows.
Definition 1 (Stackelberg equilibrium):There exists a set of strategieswhich is the Stackelberg equilibrium if and only if the requesterfog serverand any PVisatisfy the following inequalities, respectively.

We try to find the subgame perfect Nash equilibrium to achieve the Stackelberg equilibrium. In the proposed game,there exists a subgame among PVs and they strictly compete in a non-cooperative fashion. The Nash equilibrium of the subgame is denoted aswhere the utility of each PVcannot be maximized further by adopting a different strategy other than the given strategiesFor the fog server, the best response is acquired asby maximizing the utility with respect toAs for the leader, it determines the optimal reward policy for the fog server and PV group to obtain the minimal payments by predicting their best responses. To reach the Stackelberg equilibrium, we adopt the backward induction in this paper.
B. Best Response Analysis
We first analyze the best response of the fog serverGiven the reward parameterthe fog server always has the optimal strategy becausecan be converted into an optimal utility function in terms ofWe take the first and second derivatives ofwith respect toand easily have

The utility function is concave and this indicates that the maximal value of the function exists. By usingwe have
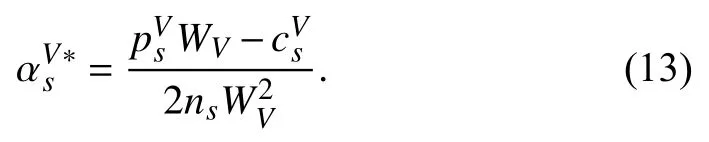
The best response is acquired by the fog server when determining the number of undertaking workloads for serving requesting vehiclein order to maximize the utility under the condition of given

Due to the negative value of the second-order derivative,is a strictly concave function. So PVhas a unique and optimal strategy with respect toand. We use the first-order optimality conditionand have

Furthermore, we calculate
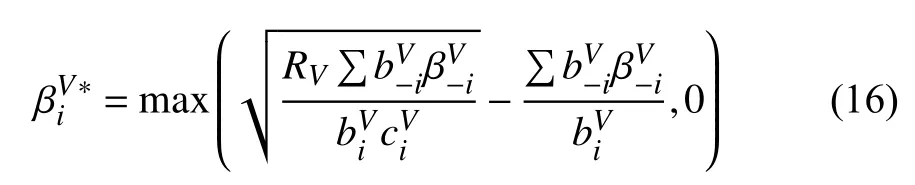
We temporarily assume that each PV would like to participate in the offloading service. Summing up (15) over all the PVs, we get
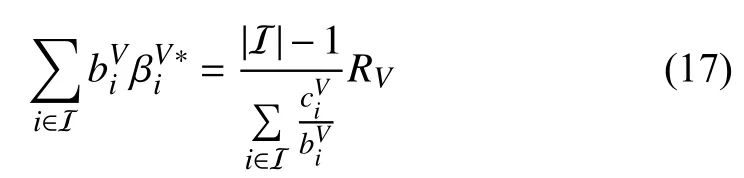

Next, we try to seek a subsetand each PV in the subset accepts workloads, namely,To this end, the subsetmeets the following constraint:

Finally, the best response of each PV in the setis summarized as follows:

As proved by [29], the above best response of each PV achieves the unique Nash equilibrium in the subgame. We also know thatwhere
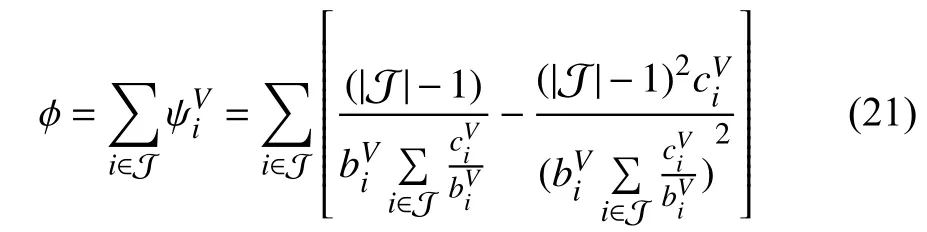
When realizing all the parametersandthe agent estimatesby using an iterative algorithm presented in [29].In this paper, the agent proactively evaluatesand requires each PV to uploadfor calculatingand.
C. Stackelberg Equilibrium
The agent realizes the task requirements. For performer selection, the performers are also required to write basic information about task execution into the smart contract before receiving workloads. The basic information refers toin a transaction. For the fog server,includesandFor a PV,includesandBy accessing to the smart contract, the agent knows the prior knowledge, and can estimate the optimal strategies of each PV and the fog server. After that, the original problem in (11) is transformed as


Based on the equality constraint, we easily transform the goal function of the above problemin terms ofand have


Considering all the constraints in the problem,is updated by

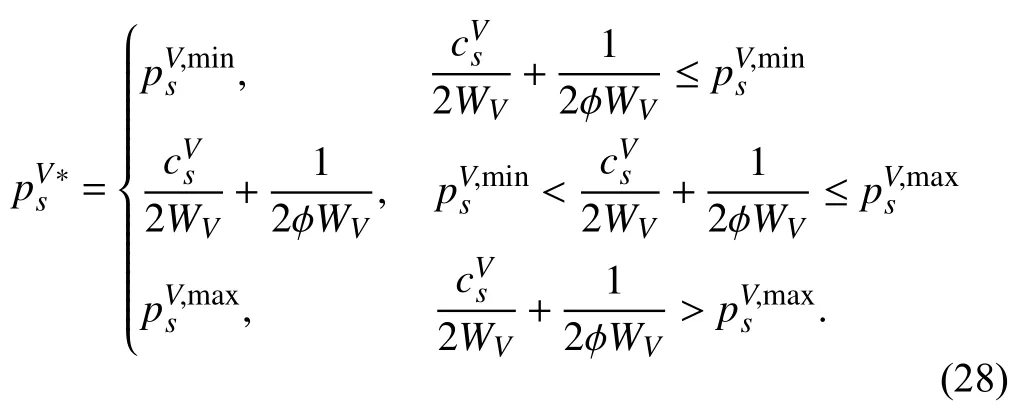
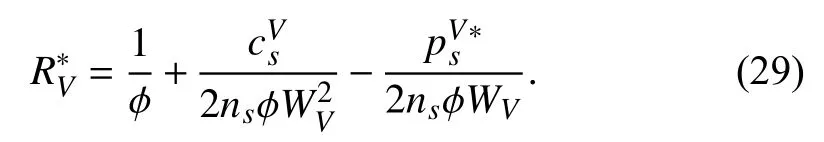
When the agent has global knowledge of the performers recorded in the smart contract, the simplified optimization problem is formulated. Ultimately, there exists a unique solutionto be solved as the best response of the requesting vehicle based on the prediction ofandAt this time, the unique Stackelberg equilibrium is reached when all the players, including the fog server, each PV and requesting vehicle, have their optimized payoff and cost, respectively, considering the strategies chosen by other players in the game. They have no incentives to change the decisions and take other actions. The solutionis transmitted to the client of the requester as suggestion. Then the requester releases the predetermined reward policy to the fog server and PVs accordingly. As predicated, they response withandand write the decisions into the smart contract.
To efficiently release the rewardsto the PVs, the agent could utilize the following distributed algorithm to achieve the Nash equilibrium of the non-cooperative subgame in an iterative way, owing to mutual interaction with each PV. First,the agent publishes the task requirements, serviceabilities of current PVs and total reward to the PVs. Algorithm 1 is executed iteratively and converges within a limited number of iteractions. In one iteration, each PV makes the decision according to (16) after knowing current strategies of the other PVs from the agent. All the decisions are collected to the agent. In the next iteration, each PV is notified with the new strategies of the others, and updates the decision and uploads it when necessary. The same interactive procedure between the agent and all the PVs (as illustrated by line 3 to 7)continues until the decision of each PV is changeless within a specific rangeFinally, the Nash equilibrium is approximately achieved and the approximate accuracy is determined by a precision thresholdwhich also influences the number of iterations.

Algorithm 1. Distributed algorithm to solve βV∗i Input: Given and .R∗V{cVi ,bV }i Output: .{βV∗,k i }i∈I 1 Initialization: Precision threshold , and each is randomly assigned with a small value.2 repeat ∑ bV−iβV−i 3 Broadcast to each PV.PVi ∈I ζ k=0 βV∗,0 i 4 for do 5 Update according to (16) and upload it to the agent.6 end k=k+1 βV∗,k+1 i 7 Goto the next round, . βV ∗,k i −βV∗,k−1i ≤ς 8 until ;9 final;10 return {βV∗,ki }
VI. Security Analysis and Discussion
A. Security Analysis for PVFChain
In this paper, we introduce PVFChain to guarantee network security and efficiency for PVFC by using blockchain with an optimal smart contract design. Smart contract operations are proposed to record relevant information and evaluate behaviors of requesters and performers in computation offloading. Security and privacy requirements can be satisfied.First, all the network entities should be registered with valid identities, and use them to maintain authenticated and secure communications. This preserves a certain level of individual privacy by permitting users to register with issued key pairs instead of revealing true identity. Besides, tasks are automatically released, executed, evaluated and awarded via the smart contract execution, and to generate committed transactions recorded on the blockchain, achieving immutability, auditability and transparency of implementing decentralized offloading services. Owing to contract enforcement, network behaviors become consistent and nonrepudiable in the nonfully trusted environment. The great advantages of PVFChain are summarized as follows.
1) Identity Authentication: Each identity is strictly authenticated to avoid illegal entities. In the meantime, the true identities of all the requesters and performers still remain unknown. This ensures authenticity and anonymity to remove impersonation attacks and avoid privacy leakage during the service provision.
2) Request Validation: Every request is submitted with a deposit, eliminating false-reporting and free-riding behaviors of malicious requesters. By checking the attached signature,the malicious requesters are easier to be identified and punished. The utilization of deposit prevents the malicious requesters from flooding the entire network with forged requests.
3) Computation Verification: Honest performers are recognized when their computation work is successfully accepted. Output results uploaded by them should be proved to satisfy accuracy performance. By using the deposit mechanism, the proposed scheme also guards against spoofing attacks from malicious performers that may offer misleading results to procrastinate the procedure of output result aggregation.
4) Reward Integrity: Tamper-resistant transaction records guarantee the process integrity of reward assignment. So reward assignment from the requesters to performers becomes untampered, accountable and traceable. Both of them should realize and follow the promising reward policy according to the contract-based agreement. In other words, they have no chances to launch reward repudiation of giving and reception.Free-riding behaviors and greedy charge are overcome.
B. Discussion About the Deposit Mechanism
As Ethereum is an open and programmable Blockchain platform, we develop the programmable smart contracts by using the specially designed blockchain virtual machine,Ethereum virtual machine (EVM), which provides an isolated runtime environment for handling the computation and state of smart contracts in Ethereum. After calling an
API, we know the sum of all the gas for the executed operations required by a designed smart contract is about 374 200. As measured by the work in [30], when miners employ fog servers for mining and we set that there are only 10 miners whose fog servers are widely connected, the average delay of verifying a block can be small to multiple milliseconds. To estimate the average block propagation delaythe average data size of blockskb, the transmission rate between any two minersMbps and two coefficientsmilliseconds.
To eliminate malicious performers, deposit mechanism is used in PVFChain. If the malicious performers are not able to submit correct output results in time, the preserved deposits are deducted by the background system for specific purposes,e.g, compensating for requesters with poor user experience.Clearly, a larger deposit causes more financial losses to the malicious performers. The strict deposit mechanism is effective to remove security risks resulted by the malicious performers. However, participation willingness of normal performers, in terms of probability to accept the recruitment in computation offloading, may also be influenced by the strict deposit mechanism. For a performer, the participation willingness of undertaking workloads is roughly decreased with an increasing deposit. Here, we use the sigmoid function to model various participation willingness losses for a normal performer with respect to different deposits, as shown in Fig. 3(a). Letrepresent the deposit, the participation willingness loss in probabilityis evaluated by


Fig. 3. Discussion about the tradeoff in the deposit setting.
For a network operator, there exists a tradeoff problem when determining the deposit θ to achieve an acceptable tradeoff between penalty acquisition from malicious performers and overall participation willingness losses caused to normal performers. Considering there existperformers and the ratio of malicious performers isdue to the participation willingness loss, the utility of the network operator in the deposit mechanism is expressed by

VII. Numerical Results
A. Performance Comparison of Different Schemes
We evaluate the performance of the proposed scheme for PVFChain by extensive simulations. We consider a scenario where a requesting vehiclesends a computation task to an agent which employs a fog serverand several PVsin a parking lot for jointly processing the workloads. The power consumption models of the fog server and each PV in CPU execution refer to [25] and [14], respectively. Within the coverage of a local roadside unit, nearby PVs use the downlink channel model in [31] to receive the input data.Particularly, parking behaviors are formulated according to a real dataset from ACT Government Open Data Portal dataACT. The real dataset uses the SmartParking app to collect 180295 parking records in the Manuka shopping precinct within a month [32]. More simulation parameters are found in Table I.
In the simulations, we select about 60 000 PVs in the dataset for an observation, and make data statistic and analysis on their parking behaviors. To summarize, the parking duration of a PV ranges from 8 to 240 min. Based on the statistic data, we draw the frequency distribution histogram about the parking durations of all the PVs in the dataset, as shown in Fig. 4(a) . Here, the class interval for grouping statistics is 10 min. Furthermore, we use the professional curve fitting tool provided by the MATLAB software, cftool,to fit and get the probability density function (PDF) of the parking durations of these PVs. The fitting PDF is illustrated by the black curve in the figure.
According to the fitting PDF, we measure the serviceability of PVfor task execution in a given task scheduling time period.indicates the time span of the time period. Based on(4), the serviceability of a PV is equal to the weight sum of the predicted probability of staying continuously within the time spanand relative value of the computing capability.
As shown in Fig. 4(b) , the serviceability of PVis decreased with the extending time span, accumulative parking durationsand reduced computing capabilityFirst, the serviceability of a PV is decreased with the expanding time window. The increasing value ofmeans that the PV is required to stay continuously within longer time durations, decreasing the estimated value ofBesides, those PVs that have been parked with longer time durations are exactly inadequate for being selected as performers. This is because that for them, the probability of a sudden departure is increased and thus, this leads to a lower serviceability. For example, within the 45 min time window, the evaluated serviceability of PVthat has been parked with 50 min will be reduced about 7% whenis increased to 100 min. At last,the serviceability can be clearly improved with the increasing computing capabilityIn the following simulations, the task scheduling time period is set 30 min. The PVs with the serviceability higher than 0.75 are deserved to be employed as reliable and efficient performers.
To show great advantages of our scheme, we compare the performances between PVFChain and three baseline schemes.Current VFC schemes only schedule the fog server task execution (e.g., [33]), or PVs (e.g., [1]) for task execution.Moreover, we introduce a baseline PVFC scheme where the uniform reward policy is published to both the fog server andall the participating PVs for fairness. More specifically, the whole workloads are allocated to all the PVs belonging to the setand the fog server in parallel and distributed computing environment within the latency requirement. According to(13),is calculated to stimulate the fog server for undertaking the given rewards. After that, the total payment of the requester isas the same reward policy is released to each participating PV. Here, to describe the offloading request, the computation task of requesteris represented bymegacycle per KB and

TABLE I Simulation parameters

Fig. 4. Observations about PVs in the dataset.
As shown in Table II, the task is executed at a considerate cost, to meet the latency requirement in our scheme. In the fog server based VFC, the total payment is rapidly increased since the whole workloads are executed by the fog server with the higher expense. Finally, the total payment of the scheme is 64% more than that of our scheme. In this paper, we combine idle resources from PVs with current resources in the fog server to achieve parallel computing. The execution time is decreased to satisfy the latency requirement. Moreover, after optimizing workload allocation among different performers,the total payment of the requester is further minimized. The smallest execution time is clearly acquired in the introduced scheme with the uniform reward policy. This is because without any competition, all the PVs are arbitrarily permitted to participate in the offloading service given the uniform reward policy while a subset of the PVs would like to undertake workloads in the competitive environment of our scheme. Nevertheless, compared with the introduced baseline scheme, our scheme still causes less monetary cost, decreasing about 35%, owing to diverse reward setting for different performers.

TABLE II Performance Comparison of Different Schemes
We also realize that the latency requirement cannot be satisfied as the whole task is entirely assigned to all the participating PVs, by lettingThe execution time resulted in PV based VFC is much longer, and approximates to 2 s, which cannot be exactly tolerated in compute-intensive applications. This means that compared with existing schemes, our scheme fully meets the payment minimization goal and latency constraint.
B. Impacts to the Stackelberg Game
Next, the impacts of different system parameters for the best responses of a requesterfog serverand each PVin the Stackelberg game are discussed.
But once a part of workloads need to be allocated to the fog server, the obvious increment ofis caused. For example,given the same values ofandUSD, the total payment is increased about 57% when more workloads appear since the size of input data is changed from 4000 to 5000 KB. To satisfy the same latency requirement, the workloads allocated to the fog server are increased. This directly leads to higher payments. In turn, the relaxed latency requirement results in less workloads assigned to the fog server. This gives rise to the reduction of the total payment, as shown in Fig. 6(b) . WhenandUSD, the total payment is declined about 66% onceis extended from 160 to 240 ms. Furthermore, for task execution, the higher expenditure of energy consumptiondirectly makes the increment ofWhen the fixed cost about task execution is increased, more monetary cost is exactly necessary to incentivize the performers for undertaking the same workloads, as illustrated in Fig. 5(c).
Various best responses of the fog server with respect to different parameters are shown in Fig. 6 . We take a computation task with specific parametersandKB as an example and letUSD. As shown in Fig. 6(a), the optimal rewards for employing the fog server to process per workloadis related to computing capability ofAccording to (1), with the improvement ofpower consumption of CPU execution in the fog server is increased. As a consequence, more energy is consumed for conducting workloads. A higher value ofis then required to offer sufficient monetary rewards for the fog server.Besides, Fig. 6(b) illustrates that when the latency requirementis decreased, the percentage of the workloads assigned to the fog serveris reduced accordingly. Due to the prolonged latency requirement, more workloads can be allocated to the PVs with lower computing capability and energy consumption, aiming to minimize the total payment.Thenis decreased to about 5% when the tolerated latency becomes 420 ms.

Fig. 5. Comparison of total payment of the requester CV with respect to different hV, LV and pe.

Fig. 6. Comparison of the best response of the fog server with respect to different LV and ∆f.
At last, we pay attention to the best strategies of the PVs under different conditions. First, as mentioned above, the total percentage of the workloads undertaken by all the PVsis increased with the prolonged latency requirementFor payment minimization, the agent assigns most of the workloads to the PVs, meanwhile, the total rewardis improved for encouraging them to undertake more workloads,as indicated by Fig. 7(a).

Fig. 7. Comparison of the best responses of the PVs with respect to different LV, RV and
VIII. Conclusions
Towards secure PVFC, we propose PVFChain with an optimal smart contract design to conduct computation offloading in a totally decentralized way, finally improving network security and efficiency. Request posting, workload undertaking, task evaluation and reward assignment are organized and validated automatically through the smart contract execution. To implement PVFChain, we propose the crucial network entities and consider smart contract operations across them. Moreover, we study the optimal smart contract design problem, which is formulated as a payment minimization problem and solved within the Stackelberg game framework, to employ a fog server and several PVs as performers for jointly processing workloads. The requester(leader) optimizes the reward policy for performers(followers) to improve user satisfaction while also considering utility maximization for them. Security analysis is provided to demonstrate that PVFChain maintains anonymous interaction,guards against flooding and spoofing attacks and ensures accountable reward assignment. Numerical results also indicate that the Stackelberg game approach is efficient and effective to maximize user satisfaction from an economic viewpoint.
In the future, we pay attention to the combination of PVFChain and social transportation system by adding and coping with the human and social dimension into offloading service scenario, as proposed by [34]. Privacy sensitivity of requesters and social ties among various PVs as local performers could be studied. Based on necessary social information, the decision-making process is further performed in a comprehensive way.
 IEEE/CAA Journal of Automatica Sinica2020年2期
IEEE/CAA Journal of Automatica Sinica2020年2期
- IEEE/CAA Journal of Automatica Sinica的其它文章
- Artificial Intelligence Applications in the Development of Autonomous Vehicles: A Survey
- Data-Driven Based Fault Prognosis for Industrial Systems: A Concise Overview
- Review of Antiswing Control of Shipboard Cranes
- Research Progress of Parallel Control and Management
- Influence of Data Clouds Fusion From 3D Real-Time Vision System on Robotic Group Dead Reckoning in Unknown Terrain
- Effect of a Traffic Speed Based Cruise Control on an Electric Vehicle’s Performance and an Energy Consumption Model of an Electric Vehicle
