Research on Mobile Internet Mobile Agent System Dynamic Trust Model for Cloud Computing
Weijin Jiang,Yang Wang*,Yirong Jiang,Jiahui ChenYuhui XuLina Tan
1 Institute of Big Data and Internet Innovation,Mobile E-business Collaborative Innovation Center of Hunan Province,Hunan University of Commerce,Changsha 410205,China
2 Key Laboratory of Hunan Province for New Retail Virtual Reality Technology,Hunan University of Commerce,Changsha 410205,China
3 School of Computer Science and Technology,Wuhan University of Technology,Wuhan 430073,China
4 Tonghua Normal University,Tonghua 134002,China
Abstract: This paper analyzes the reasons for the formation of security problems in mobile agent systems,and analyzes and compares the security mechanisms and security technologies of existing mobile agent systems from the perspective of blocking attacks.On this basis,the host protection mobile agent protection technology is selected,and a method to enhance the security protection of mobile agents (referred to as IEOP method) is proposed.The method first encrypts the mobile agent code using the encryption function,and then encapsulates the encrypted mobile agent with the improved EOP protocol IEOP,and then traces the suspicious execution result.Experiments show that using this method can block most malicious attacks on mobile agents,and can protect the integrity and confidentiality of mobile agents,but the increment of mobile agent tour time is not large.
Keywords: mobile internet; cloud computing; mobile agent system; subjective trust; dynamic trust management
I.INTRODUCTION
As a new Internet application business model,“Cloud computing” shields users from issues,such as data center management,big data processing,and application deployment.Through the network,users can quickly apply for or release resources according to their business needs,and pay for the resources used in an on-demand payment manner.Just as it is now convenient and quick to use hydropower,users do not have to purchase a hard-software infrastructure to liberate themselves from the heavy pressure of IT infrastructure management and maintenance,and focus more on their core business development.With its economic advantages of convenient services to attract the attention of many enterprises in the IT industry,“cloud computing” is generally considered to have a huge market growth prospects.From a technical perspective,“cloud computing” has two key points.One is the research on the distribution method of large-scale dynamic resources in resource pools; the other is the computational methods and programming methods on distributed collaborative application development platforms.For the latter,the mobile agent computing scope provides a universal reference model for the design and development of application systems in the “cloud computing” environment.The mobile agent model can realize the core idea and computing principle of mobile internet cloud computing in terms of technology,and realize the business service form of cloud computing in terms of service.However,due to the virtuality,dynamics,openness and commonality of the cloud environment,it brings great security challenges to the application of the mobile agent paradigm [1].
Mobile Agent technology is an emerging technology that is multi-disciplinary and at the forefront of international research.It is also a product of the combination of Agent and Internet in the field of artificial intelligence [2].In the cloud computing environment,the problem of resource allocation of trust security domain in mobile agent system is studied [3,4].It can track international cutting-edge technology,enrich the theoretical system of cloud computing and mobile agent model,and enhance the security performance of agent application system.It can also promote the further development of China’s distributed application technology and information security technology,and promote the application of mobile agent technology in various fields in the cloud computing environment.Therefore,it is of great theoretical and practical significance to study the security trust problem in the design of mobile agent system in cloud computing environment.
II.RELATED WORK
The trust problem of the mobile agent system has both the generality of the network trust problem and its own particularity.As early as 1990,D.Gambetta proposed “Trust is subject to the object of specific behaviors expected subjective possibility,depending on the experience and results with the change of object behavior and constantly revised” [5].In 1996,M.Blaze et al.first proposed the concept of “Trust Management”,which was used to solve the security problem of system network services.The basic idea is:trust management is to provide a secure decision framework that is suitable for network applications,open,distributed and dynamic [6].In 1999,D.Povey [7] based on the definition of M.Blaze,combined with the research results of D.Gambetta and A.Abdul-Rahman et al [8,9],gave a more universal concept:tust management is considered a process of acquiring,evaluating,and implementing Trust Intention.The 2000 version of X.509 describes the trust relationship between entities in an open network system:“In general,if an entity is assumed that another entity will behave exactly as it expects,then it is said to trust that entity.” This description of trust expresses the existence of an agreed relationship between interacting entities and some expectations for adherence to the agreed relationship.
Currently,the trust management model is generally divided into two categories.The first category is the objective rational model.It uses a rational and accurate method to express and deal with complicated trust relationships,and has objective and static management characteristics.Trusts employ a unified approach to describe and explain the “Security Policy (Security Policy)”,“security credentials (Security Gredential)”,and “Authorization critical for safe operation” between the (Trust Relationship:typical trust management model is M.Blaze ).Trust management question to be answered is:“security credentials Set C is able to prove that the request r satisfies the local security policy set P”.The second category is the subjective empirical model,which considers trust to be a subjective judgment of a particular level of specific characteristics or behavior of the object.This type of trust model believes that trust is subjective,irrational,and has an empirical experience,including the specific content of trust and the division of trust levels,which is constantly modified based on changes in the outcome of object behavior.A typical representative of D.Povey binding trust management model A.Abdul-rahman and D.Gambetta et al point of view put forward by the main function is a “trust of intent (Trust Intention) the acquisition,evaluation and implementation”,mainly related to two aspects Study:the first is how to describe and measure trust; the second is how to recommend and calculate trust based on experience.There are several other trust management models for open network systems.Although there are some differences between them,the above two types of model ideas are generally used.The PKI-based trust management model belongs to the first category.In such systems,there are few leaders to oversee the entire network node,advertised legality offending node regularly,leader node certificate issued by the CA to be guaranteed.Such systems are dependent on the center,with scalability,but there is no single point of failure.The trust management model based on local recommendation belongs to the second category.In such systems,in order to obtain the trustworthiness of a certain node,the local broadcast method is usually used to query other limited number of nodes,and the node credibility obtained by such a method is one-sided.Global trust management model,also belong to the second category.It calculates the global credibility of the node by iterating the satisfaction between adjacent nodes.The disadvantage is that the global node cannot be used effectively when it changes continuously.
In the Internet field,the commonly used network trust management models are PKI and PGP software packages.The European-developed ICE-TELL project combines PGP and PEM to define a new trust management model.The development of this project has further promoted the extensive research of the network trust model,and the following typical models have emerged.
Based on Reputation trust management model.For example,R.Guha,Derbas.G et al.proposed a reputation-based trust management model with five parameters [10,11] and gave an “A Coherent Trust Metric” algorithm.This algorithm uses five parameters to quantify and compare the trust level of a trusted entity.The reputation-based trust model is further divided into Central Trust management and Personalized Trust management.Concentrated trust is based on the complete behavioral sample of the object.For example,the literature [12] proposes a trust model that can manage all the behavior of the object.Personalized trust uses some behavioral samples to extract according to certain algorithms [13,14].
Based on Trust Management Model Behavior.Literature[15,16,17] proposed a behavior-based trust management model to allocate resources according to whether the user’s historical behavior is trustworthy.
The method of fuzzy sets is used to study direct trust management [16].Because trust is somewhat uncertain,fuzzy logic is used to deal with the subjectivity and uncertainty of subject characteristics and behavior cognition,and make decisions based on the determined trust strategy to provide effective support for judging trust status.
Trust and the issue of non-trust communication.Guba-oriented e-commerce system presents a complete set of belief propagation algorithm,part of the expression of trust between individuals for predicting the level of trust between any two objects.
The Simple Public Key Infrastructure (SPKI) method was proposed by Carl Ellison and Bill Frantz in 1996 [18],which was standardized by the IETF in 1999.The SPKI standard now in use is a mixed version of SPKII/SDSI.
The role of the SPKI trust management model is to provide the basic rules for establishing a trust chain and selecting a trust path for authentication.Mainly divided into the following four [23-25]:Strict hierarchical trust model,peer-to-peer model,mesh model and scalable multi-level trust model (ie optimized mesh model).However,none of the four models can manage all the trust problems in open network systems,and each trust model has advantages and disadvantages.At present,the most used in the network is the centralized control trust model,which is the “hierarchical model”.When a large number of system entities establish a trust relationship according to the hierarchical model,the trust chain will become longer and longer,and the complexity of trust transfer will increase rapidly,and the attenuation in the process of trust transfer cannot be well controlled.With the increasing subjective and personalized requirements for trust judgment in the process of entity interaction in open and distributed network systems,the research on “peer trust management model” and “network trust management model” has become more and more important.
In practical applications,when constructing trust relationships in distributed network application systems in different domains based on SPKI,“the fewer middlemen,the shorter the trust chain,the higher the efficiency of verifying trust anchors; the higher the locality of trust,the less the trust decays,and the higher the level of trust in the entity in the final relationship.” Therefore,in the construction of the mobile agent system trust management model,the complexity of trust verification is reduced in principle,which not only meets the requirements of trust delivery,but also controls the attenuation of trust.
The complexity of using the traditional method to solve the security problem of the mobile agent system is that it only analyzes multiple risks and multiple attacks,and the common reason that does not deeply consider the different risks is often the break of a certain trust relationship.Literature [15] analyzes the security problem of mobile agent system from the trust relationship,and uses the improved Entity Relation Graph (ERG) to describe the trust relationship between entities and obtain the Trust Requirements Graph (TRG),which expresses the trust demand status of the mobile agent system intuitively.TRG is a polygon.Vertexes are used to represent entities.Edges are used to represent trust relationships between entities and to represent the state of trust relationships [20,21].
Based on the network peer-to-peer trust model,the paper [17] proposes an objective trust peer management model for the mobile agent system.By implementing trust binding on the mobile agent and the source host,objective trust management and cross-certification are performed on the source host and the execution host.The SPKI+RBAC identity attribute certificate is used to solve the problem of identity authentication,operation authorization and access control between the mobile agent and the execution host.Based on SPKI technology to construct the objective trust management model of mobile agent system,it mainly solves three problems:(1) Establishing a trust relationship between entities in the mobile agent system; (2) Determine the content of the host and mobile agent trust certificate; (3) Determining and controlling the trust status between entities in the mobile agent system.
Lin Hui et al.[18] used data security and privacy protection in mobile cloud computing as the research background.For internal attack and mobile attacks,a dynamic incentive-based recommendation incentive strategy was proposed,and a reliable recommendation reputation evaluation model was established.And a new transmission reputation mechanism based on dynamic game and reliable recommendation is proposed.
In literature [19],aiming at the security requirements of current cloud computing,an identity authentication scheme suitable for cloud computing environment is proposed.The mobile agent structure model for cloud computing identity authentication scenarios is designed,and the cloud agent security authentication strategy based on mobile agent is given.The scheme introduces a trusted third-party organization to establish a quantitative trust evaluation for the authentication agent,and controls the authentication process by the judgment of trust degree before each authentication; after the authentication is completed,the trust feedback evaluation is performed.
In literature[20],in view of the dynamic,uncertain,distributed and open characteristics of cloud computing,a hierarchical trust management framework based on Agent and trust domain is used as a platform to utilize fuzzy clustering method based on personality preference.A service selection model based on trust and personality preference in cloud computing environment is proposed.In order to determine the classification that is closest to the service requester’s personality preference,a service selection algorithm is proposed.The trust evaluation mechanism is introduced,combined with direct trust and domain recommendation trust,so that the requester selects a service resource that is both secure and credible and can satisfy its personality preference in the determined classification.After the transaction is over,the service is judged according to the service satisfaction,and the trust update is performed.The model can improve the service satisfaction of the requester to a certain extent,and has certain resistance to the fraudulent behavior of the malicious entity.
Literature [21] studies the trust problem of mobile e-commerce in cloud computing environment,and divides the trust problem of mobile e-commerce in cloud computing environment into two categories:identity trust and behavior trust.Focusing on the issue of behavioral trust in the case of identity credibility,this paper proposes a mobile e-commerce trust management framework in cloud computing environment.And introducing the majority of consensus and feedback density two reputation factors to build a reputation-based trust model,which can prevent self-improvement attacks and smash attacks,and improve the robustness of the trust model.Aiming at the high dynamic of the cloud environment and the uncertainty of the number of cloud users,a replica decision mechanism is introduced to dynamically determine the optimal number of trust management service copies and improve the availability level of trust management services.The NetLogo platform is used to simulate the cloud environment,and the Epinions rating data set is used to replace the trust feedback of cloud consumers.It is verified that the majority consensus factor can improve the accuracy of the trust model prediction.The feedback density factor can improve the robustness and sensitivity of the trust model.
Literature [22] uses a social network to mine the entire multi-agent system to obtain a group of agents with potential social relationships with the agent.The recommendation information provided by the group of agents is fully trusted,and the information provided by the agents is preferentially used to calculate the recommended reputation value,and then the weights of the direct credit value and the recommended reputation value in the integrated trust value are judged according to the number of direct transactions between the two parties.
ZHANG Wen-Li et al.[23] studied the computational migration of intelligent mobile terminals,discussing the common problems of internal components and key quality attributes of computing migration systems from the perspective of software architecture,and proposed a reference trust architecture for computing migration systems.
LI Ji-Rui et al.[24] studied the mobile cloud computing energy-saving measures and cloud trust strategies under 5G networks,and proposed a research strategy for energy-saving models and methods of mobile cloud computing under 5G,providing a solid theory for practical applications.
LIU Xing et al.[25] proposed a task-based joint execution strategy (Task Collaborative Execution Policy,TCEP) based on trust management for mobile users to migrate applications to the cloud to cause a large amount of data transmission leading to high energy consumption.
Hu Haiyang et al.[26] studied the multi-objective optimization and trust method for task scheduling in mobile cloud computing environment.
The above trust management model provides an idea and framework for solving the trust problem in the interaction between the network entity (the servant and the requester).But there are still many deficiencies,including:
(1) The trust management model absoluteizes the security effect metrics.Either trust or distrust.This method is too rigid and does not adapt well to the ambiguities that appear in open network systems,including:variability,subjectivity and uncertainty.
(2) Trust strategy verification ability and efficiency are low.Some need to collect enough evidence before the trust policy consistency verification.
(3)Trust management model is not a good start.Some trust strategies are too complicated to develop.The trust management model is costly and inefficient,which seriously hinders the practical application of the model.The entity providing the service only considers the trust and security needs of the service provider without considering the trust and security requirements of the requesting party.This model is not suitable for the mobile agent system to protect the mobile agent security from the need to perform trust judgment on the execution host.
(4) The trust problem of the mobile agent system.In the cloud computing environment,there is no clear unified definition of “trust”.The researchers lack consistency in the understanding and agreement of trust.In many studies,trust and security-related concepts have many mixed uses,which is extremely the issue of trust conducive to further refine the study.
The security problems exhibited by the mobile agent in the process of “interaction between different places” are closely related to the question of “trust” between the two parties.At present,the trust management mechanism has not been established in the existing mobile agent system,and the relationship between the host and the visiting mobile agent is “weak trust or zero trust”.The mobile agent and the execution host belonging to different trust domains do not trust each other,guard each other,and even attack each other.The common cause behind multiple attacks is often the break of a chain of trust.In the mobile agent system,enhancing the security of the mobile agent system by strengthening trust management is a new way to solve the security problem of mobile agents.In recent years,the basic trust problem of open network systems has become a research hotspot.These studies have brought enlightenment and reference for the solution of the trust problem of mobile agent system.
Based on the above-mentioned related trust management analysis and research,this paper studies the trust problem of mobile agent system by combining objective rational model with subjective empirical model.On the basis of the objective trust peer management of the mobile agent system,a dynamic management method of subjective trust is proposed,which can avoid and solve the above problems.The complexity of trust verification is reduced from the design principle.Compared with the existing PKI-based trust management model,the trust certificate is designed based on SPKI+RBAC,which reduces the complexity of trust verification.It can not only meet the requirements of trust transfer and verification of mobile agent system,but also control the attenuation of trust caused by excessive trust chain [27-29].
III.DYNAMIC MANAGEMENT METHOD OF SUBJECTIVE TRUST IN MOBILE AGENT SYSTEM
By analyzing the formation,dissemination and evolution of subjective trust,the dynamic management algorithm MASTMA is proposed.Using the concept of trust degree,the security effect of the interaction behavior of the mobile agent system is measured,calculated and evaluated,and the trustworthiness of the next interaction is predicted.The interactive host can set trust thresholds for its own trust requirements,select trusted clusters,and isolate malicious hosts.
3.1 Analysis of subjective trust characteristics of mobile agent system
In practical applications,the mobile agent and the execution host have their own trust requirements,and the interaction process between the mobile agent and the execution host has the following subjective characteristics [29-31]:①Personalization of mobile agent requirements:Mobile Agents perform different tasks,and their code and data have different “sensitivity”,and their trust requirements are different.A public information query mobile agent and the execution host do not need to establish a high degree of trust cooperation mechanism,and the task can be successfully completed.A “settlement agent” in the process of completing the task in the e-commerce system,the interaction with the execution host requires a strong trust mechanism to ensure.②Execute the host’s self-interest:In an e-commerce system,the execution host is profitable in the process of providing services by the mobile agent,for example,attracting more customers (mobile agents),selling more products,and the like.If an executive host cannot obtain benefits from the services provided for the mobile agent,it will lose the motivation to establish a good trust relationship and provide quality services,that is,the motivation for establishing trust between entities is beneficial.③Locality of information collection:In the open mobile agent system,in addition to the basic trust information established by the system to obtain basic trust information,there are two channels.One is to collect the trust information of the other party through the interaction history between itself and the interacting party; the second is to obtain the trust information about the interacting party by asking the third-party host,but the trust information finally obtained is not all,but partial.④Asymmetry:Entity A believes that entity B,in turn,entity B does not necessarily believe in entity A,that is,the degree of trust of entity A to entity B is generally not equal to the degree of trust of entity B to entity A.⑤Time correlation:The credibility of each entity in the system changes with time.Entities with high trust level will be downgraded due to malicious behavior,and entities with low trust will also have the opportunity to upgrade due to good behavior.⑥Environmental relevance:The degree of subjective trust is affected by the physical interaction environment and the context.When the network environment becomes bad or the number of malicious entities in the network increases,the same task is completed,and the threshold of the degree of trust demand increases.
3.2 Mobile agent system subjective trust dynamic management model
The traditional mobile agent system objectively trusts the peer-to-peer management model.Using the SPKI certificate can determine the trust status of the other party before the interaction occurs (trust=1,no trust=0),and improve the possibility of secure interaction of the mobile agent system.But judging trust is essentially a possibility and a prediction.Whether the trust judgment before the entity interaction is truly “real” depends on whether the interaction entity has malicious behavior to determine after the interaction process is completed.Only using the objective trust peer management model can not find the malicious behavior of the intermediaries in time,can not correct the trust status in time,and can not promptly punish the offenders.
Based on the objective trust peer management model,we focus on the dynamic management method for the subjective trust demand research of the mobile agent system.Based on the interaction behavior,measure the trust status of the interactive host,and realize the dynamic management functions such as the formation,dissemination and evolution of subjective trust.
3.2.1 Subjective trust dynamic management model
The composition of the mobile agent system supervisor trust model is shown in Figure 1 [29,30].Bottom-up:The host is in an open and dynamic network environment.The mobile agent platform (MAP) is located on the host,providing an Execution Environment (EE) for the mobile agent.The MAP is not necessarily unique on a host,but more than one.The subjective trust management model is located in the MAP and consists of three trust components:They are the trust formation component,the trust propagation component,and the trust evolution component.These management mechanisms provide a trust interaction context for the interaction entity,and monitor the interaction process and behavior of the entity.The trust formation component mainly implements the collection and calculation of trust data,the trust propagation component mainly implements the protocol exchange of trust data,and the trust evolution component mainly realizes the update of the trust data.
3.2.2 Working principle of the model
(1) Trust data collection
The trust formation component completes the basic trust data collection function.HostHatrust data collection for hostHxis divided into two parts:One is direct trust of information,from the experience of direct interaction between the hostHaand the hostHx; the second is the recommended trust information from other hostsHk(k = 1,2,...) and the hostHxinteractive direct experience obtained,and the hostHais indirect experience.Both are derived from “the determination of the host’s behavior on the interaction side” [31].This component problem to be solved is:how to translate the quality of physical interaction into the level of entity trust? That is to solve the problem of quantitative representation of trust.
(2) Trust data dissemination
The trust propagation component completes the exchange task between host trust data.Any host that joins the mobile agent system has the right to ask other hosts in the system for the trust data of the hostHxto be exchanged,and also has the obligation to provide the inquirer with the trust data collected by other hosts.If the relevant trust data of the host that was asked is not accumulated,answer it in the specified way.
(3) Trust data evolution
The trust evolution component completes the update of the trust data,and the problem to be solved is that the historical trust data and the newly collected trust data are comprehensively weighed and calculated according to a given algorithm during the update period specified by the system,and the latest trust state of the host is obtained.
On each host,the subjective trust management model acts as a self-binding unit for trust information collection,trust information exchange,and trust information update,and supports the host to complete trust state determination for other hosts.
3.2.3 Quantitative representation of trust
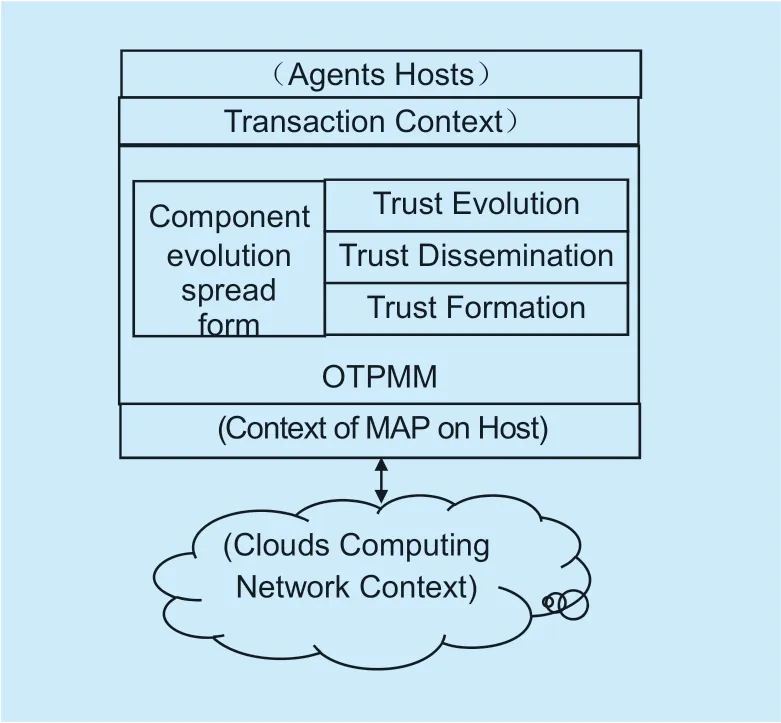
Fig.1.Subjective trust dynamic management model.
In fact,the trust relationship between network entities to be quantified is a very difficult thing.Based on the description of the Josang network trust management model and the basic concept of measuring the trust relationship of network entities,this paper studies the quantitative representation of trust relationships between entities in the mobile agent system [33-35].The Josang implementation space consists of a series of observable events generated by entities,and entity interaction events are divided into Positive Eventsn1and Negative Eventsn2.In the concept space,Josang describes the posterior probability of Binary Event based on the Beta distribution function,constructs a probability deterministic density function determined by the number of positive events and negative events observed.And the probability deterministic density function isθr0≤θ≤1,r≥0,s≥0,where θ is the probability variable,and the probability of an event of this function to calculate interaction entity generates credibility.In this paper,two basic concepts of Evidence Space and Opinion Space are introduced in the mobile agent system.The entities in the mobile agent system refer to the source host,mobile agent or execution host.The pcdf function is replaced with a Gaussian distribution probability density function GDPF (Gauss Distribution in Probability Function),because GDPF has more stable than pcdf distribution function.Based on the GDPF function,the factual space of the mobile agent system is transformed into the “level of credibility of the entity” in the conceptual space of the mobile agent system [36].
This paper uses the 5-tuple(A,X,Tx,t,c)to quantify the degree of trust in the mobile agent system [37,38],which is interpreted as:At time t,in context c,entity A believes that entity X can satisfy the trust requirement to the extent that it reachesTx.Trust is related to changes in the environment and time.At the same time,the mutual trust between the two parties is asymmetrical.At the same time in the same environment,generally(A,B,Ta,t,c)≠(B,A,Tb,t,c).The degree of trustTxis a function.In this paper,its range of values is specified as [0,1],and its value change is affected by multiple independent variables (factors).“0” indicates that the entity A complete distrust X; “1” indicates that the entity A absolute trust entity X.Except for these two extreme cases,the degree of trust in the general case is between (0,1),indicating that entity A trusts entity X to a certain extent.In this quantitative reference system,the degree of trust is no longer a simple logical value of “trust” and “no trust”,but a continuous interval.In the case where the interaction entity,the interaction time,and the interaction environment are known,the focus is on determining whether the degree of trust satisfies the trust requirements of both parties.When theTbvalue reaches the entity A enough to trust the entity B,A believes that B,A and B interact,otherwise,do not interact with it,or strengthen the security measures to pay a higher security cost to interact.
3.2.4 Basic trust data collection
(1) Recommended trust basic data collection
If the hostHadoes not have sufficient understanding of the hostHx,envisaging the hostHawant to interact with the hostHxin order to evaluate the degree of trusted hostHx,and the hostHaqueries a group of hosts {H1,H2,...HK} for trust information about hostHx.The recommendation information between the entities defined here is a set of “basic data” about the interaction behavior rather than the comprehensive calculation result of the degree of trust.The purpose of this is to eliminate the accumulation of errors generated during the comprehensive calculation of the degree of trust,and the impact of the trust preferences of the host {H1,H2,...HK}.Under normal circumstances,the number of interactions between the hostHiand entityHxis n,the number of successesn1,the number of failuresn2,Dki=n1/(n1+n2),(n=n1+n2).In order to avoid the abnormal situation that cannot be answered,it is specified in the mobile agent system as follows [39,40]:
1) All have the right to request the host system and recommend an obligation to provide information,so that “Insider.”
2) Normally,the hostHaasked more likely to trust their own host; also can ask strange host.If you do not understand being asked to hostHithe hostHx,then answerDx=0.5.
3) Evaluation recommendation information in confidence proportion accounted for by the host to choose.
(2) Direct trust data collection
Assume that the hostHahas to interact n times with the hostHxdirectly,successesn1,failuresn2,(n=n1+n2).Dax=n1/(n1+n2) to reflect the hostHaand hostHxinteractive behavior is good or bad,which is defined as a direct trust underlying data.
3.3 “public trust” Host selection
In the current research on the trust problem of network interaction entities,in the quantification and calculation of the trust degree based on the interaction behavior of the interaction entity,the average value algorithm is usually used,that is,the average value of the collected basic data is averaged,and the algorithm is simple and easy to use.But the limitation is that you can’t limit the impact of malicious recommendations.In the mobile agent system,the harm caused by the malicious host to the mobile agent is catastrophic.The algorithm used must focus on isolate the malicious host and eliminate the influence of the malicious host.
This article defines:If a third-party hostHabased only {H1,H2,...,Hk} recommendation data to calculate the extent of trusted hostsHx,and select trusted interactive objects,the selected host will be called a “public trust” host.The “public letter” host selection algorithm provides a method for selecting a trusted interactive object for the host in the mobile agent system,especially the host newly added to the mobile agent system.If the hostHawants to check the trustworthiness of hostHx,the hostHasends a series of queries about the host to the third-party host {H1,H2,...,Hk}.After the hostHaobtains a series of basic recommendation data,the recommended data is analyzed according to a certain algorithm,the degree of trust is calculated,and the calculation result is compared,and the hostHaselects the trusted host according to its own trust threshold.
3.3.1 Recommended trust computation algorithm
We divide the continuous system runtime into equally spaced inspection periods,each of which is called a “time frame” and is represented by τ(τ = 1,2,...,n).Then the interactive behavior of the interactive host is transformed into the quantitative calculation of trust degree [41].The Gaussian probability distribution theory is used to improve the average algorithm,and a more optimized algorithm is given.The algorithm is as follows.
Computing a set threshold v,the hostHahas the intention of candidate host interaction {Hx1,Hx2,...,Hxk},followed by calculation of {Tx1(v),Tx2(v),...Txk(v)},which can choose a higher level of trust list host.These hosts are selected based on recommendation after data calculation,and there is a certain degree of public trust,known as the “public trust host”.If the hostHais a newly added mobile Agent system,it is more reasonable to use this algorithm to select the interactive host.IfHaandHxhave direct interaction experience,based on direct empirical data,this algorithm needs further improvement.In the following,the trustworthiness of the recommended host itself will be considered as a “weighted value”,giving a more reasonable algorithm.
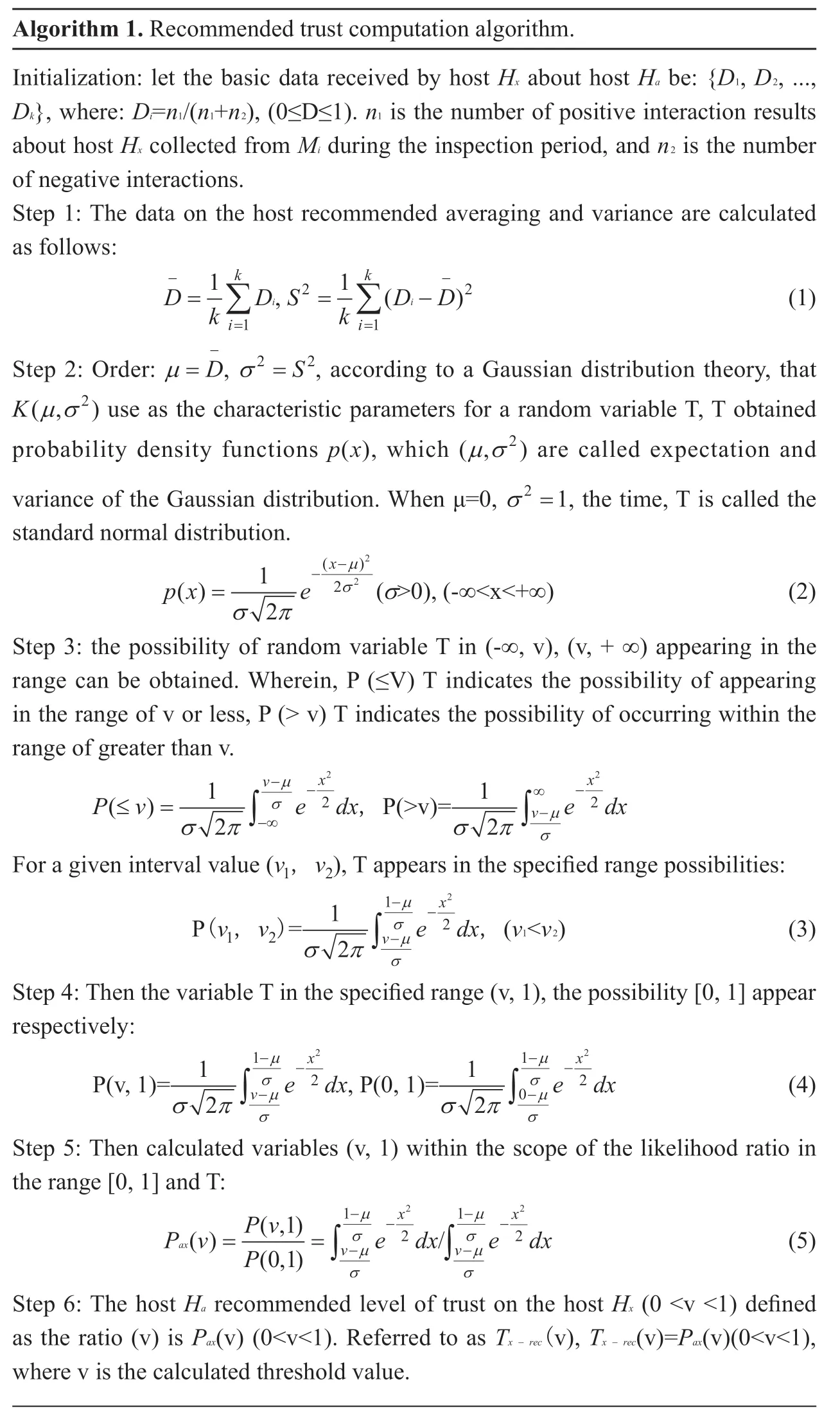
Algorithm 1.Recommended trust computation algorithm.Initialization:let the basic data received by host Hx about host Ha be:{D1,D2,...,Dk},where:Di=n1/(n1+n2),(0≤D≤1).n1 is the number of positive interaction results about host Hx collected from Mi during the inspection period,and n2 is the number of negative interactions.Step 1:The data on the host recommended averaging and variance are calculated as follows:k -=1k∑i=1k D D 2 2i,S D D= -1k∑i=1( )i- (1)Step 2:Order:µ=D-,σ2 2=S,according to a Gaussian distribution theory,that K(,)µσ2 use as the characteristic parameters for a random variable T,T obtained probability density functions px(),which (,)µσ2 are called expectation and variance of the Gaussian distribution.When μ=0,σ2=1,the time,T is called the standard normal distribution.2 1 2-( )x 2σ>0),(-∞<x<+∞) (2)Step 3:the possibility of random variable T in (-∞,v),(v,+ ∞) appearing in the range can be obtained.Wherein,P (≤V) T indicates the possibility of appearing in the range of v or less,P (> v) T indicates the possibility of occurring within the range of greater than v.px e-σµ2() (=σ π 2 2 1v-µ-x 2P v e dx ( )≤ =σ π 1 2 ∫-∞σ,P(>v)=2σ π 2 ∫v µe dx-x∞ σ-For a given interval value (v1,v2),T appears in the specified range possibilities:P(v1,v2)=2 1 1 σ--σµµ,(v1<v2) (3)Step 4:Then the variable T in the specified range (v,1),the possibility [0,1] appear respectively:P(v,1)=e dx-x 2 ∫v 2σ π 2 2 1e dx-x 2 1(4)Step 5:Then calculated variables (v,1) within the scope of the likelihood ratio in the range [0,1] and T:2σ π 2 ∫v ,P(0,1)=e dx-x 1 σ--σµµσ π 2 ∫0 1 σ--σµµ-x 22 2(,1) ∫vPv(0,1)e dx-x(5)Step 6:The host Ha recommended level of trust on the host Hx (0 <v <1) defined as the ratio (v) is Pax(v) (0<v<1).Referred to as Txrec-(v),Txrec-(v)=Pax(v)(0<v<1),where v is the calculated threshold value.2P v e dx/ax()= =P ∫v 1 σ--σµµ1 σ--σµµ
3.3.2 Recommend the impact of the host’s own trust
In the preferred third-party trusted data based on the calculation above,further consideration should be given that each host itself recommended credible extent [42].In fact,in order to evaluate the credibility of the hostHx,the credibility of the third-party host {H1,H2,...,Hk} itself queried by the hostHaalso needs to be evaluated.Their degree of trust has a negligible impact on the degree of trust recommended by the hostHx,especially to exclude recommended data from malicious hosts.The following two cases are considered.If the hostHahas experience in interacting with the hostHibeing queried,the direct trust level of the host pair is used as the weight to adjust the recommended data from the host.If hostHadoes not interact with hostHibeing queried,the direct trust level for the pair is 0.5.
Suppose directly trust third-party {H1,H2,...,Hk} for {t1,t2,...,tk},the recommended data from {H1,H2,...,Hk} of {D1,D2,...,Dk} are weighted ,and then calculate the degree of recommendation trust of the weighted algorithms such as formula (6) below.
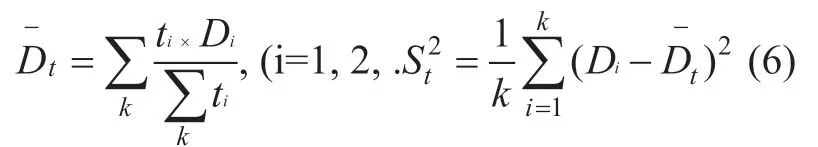
3.3.3 Update recommend trust
With the passage of time (τ = 1,2,...,n),the recommended trust level with respect to the hostHxis updated,and the recommended trust level of the n+1th time frame comes from the recommended trust level of the nth time frame and the recommended trust level of the n-1th time frame.Take part historical inheritance confidence data,add some trust in the current update policy data,control and adjust the update rate by a factor β (τ).
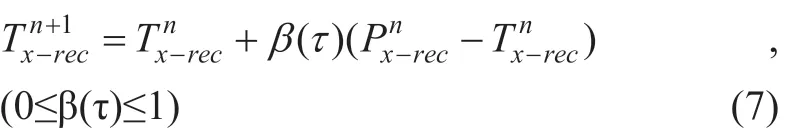
When β(τ)=1,all current trust data is used,and the update speed is the fastest.
When β(τ)=0,all historical trust data is used,and the update speed is the slowest.
When 0<β(τ)<1,as β(τ)=0.5,the historical trust data and the current trust data are each taken in half.
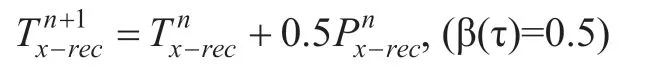
The choice of the β(τ) factor can vary for different mobile agent systems.An update is a process that requires given appropriate update cycle.For some real-time applications,the speed is too slow,stale data,resulting in the loss of trust degree evaluation results timeliness,prediction error increases; but the update speed is too fast,it will cause system instability or shock.Some will be given later simulation and discussion of β (τ) update rate.
3.3.4 Direct calculation trust
In fact,hostHa’s trust evaluation of hostHxis primarily influenced by direct interaction experience.If the hostHaand the hostHxhave already had experience in interacting with each other,use the algorithm given in the previous section to calculate the direct trust base data.The hostHacan obtain the trust level of the hostHxby direct experience,which is called the degree of direct trust,and is recorded asTxdir-(v).
The continuous system uptime is divided into equal statistical period,each study period called a “time frame”,with τ (τ = 1,2,...,k) represents.Within each time frame τ,assumptions and direct interactionn1+n2times,positive eventn1times,negative eventn2times.Definition of direct experience data calculated by the formula (8).
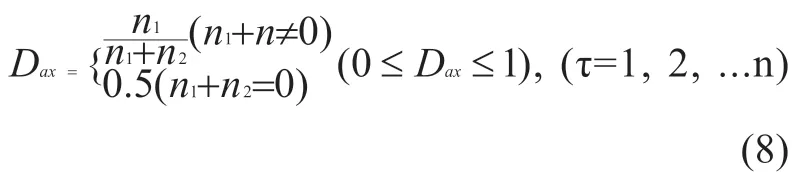
In k successive time frame for
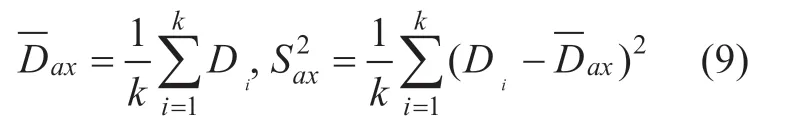
With the passage of time (τ = 1,2,...,n),the recommended trust level with respect to the hostHxis updated,and the recommended trust level of the n+1th time frame comes from the recommended trust level of the nth time frame and the recommended trust level of the n-1th time frame.Take part historical inheritance confidence data,add some trust in the current update policy data,control and adjust the update rate by a factor λ(τ).
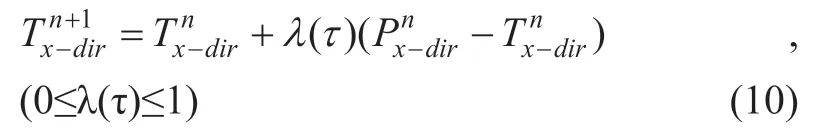
When λ (τ) = 1,all current trust data is used,and the update speed is the fastest.
When λ (τ) = 0,all historical trust data is used,and the update speed is the slowest.
When 0 <λ (τ) <1,such as λ (τ) = 0.5,the historical trust data and the current trust data are each taken in half.
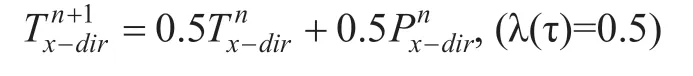
Similarly,the choice of the λ(τ) factor can be different for different mobile agent systems.An appropriate update period τ needs to be given.If the update speed is too slow and the data is outdated,the trust evaluation result will be lost in time,and the prediction bias will increase; if the update too fast,it will cause system instability or shock.Some will be given later simulation and discussion on λ (τ) update rate.
Based on the working mechanism of the subjective trust model and based on the above-mentioned host direct trust measurement method,the hostHacan evaluate the trust degree (Txdir-) of the hostHxaccording to its own direct interaction experience,and determine the trust threshold valueToautonomously.IfTx>To,the hostHainteracts with the hostHx; Otherwise,do not interact with,or strengthen safety measures after interaction.When a host joins the mobile agent system,over time,a list of trusted clusters is gradually formed on the host.The size of this trust group is large or small,and it is dynamically changing.There will always be new members joining,and some old members will withdraw for some reason.There are two important factors affecting the formation of trust fleet:one is the time period of trust data update; the other is the trust threshold specified by the host.The effects of these two parameters are discussed below.
(1) Time frame determination
In this paper,the Mobile Agent System trusted data update time period is defined as the time frame (represented by τ),which is a mobile Agent system global variables.In a time frame,the number of host data,and trust and confidence of the masses are relatively constant.The selection of the time frame τ length is specific to the application of the mobile agent system,and is determined by experimental debugging.It is necessary to avoid the system trust data from being stale,to predict the increase of uncertainty,and to avoid too short a system to oscillate and to form a stable state within the period.In the mobile agent system,the value of the time frame τ is relatively stable.
(2) Trust threshold selection
In this paper,the minimum trust requirement value that the host (Ha,Hx) can interact with is called the trust threshold,which is denoted byTo.ThresholdTois a trust called cluster parameters or local variables on the host.The host selects a sufficient threshold based on the nature of the task it is to perform.WhenTx>To,it is considered credible and can interact with it; WhenTx<To,it is considered credible and do not interact with it.In the mobile agent system,the selected trust threshold of each host can be different.
(3) Changes in trust fleet
The formation of the trust cluster in this paper is not statically divided by organization or geography,but by the subjective trust requirement of the host [43].The trust cluster is in dynamic change.When the system time frame and the trust threshold of the known host are determined,the reasons that affect the change of the trusted cluster are as follows:①some hosts,due to long-term offline or online dormancy,do not interact with other members for a long time,resulting in stale data,the degree of trust is reduced,and may be marginalized by trusted groups.②some hosts have a lot of interactions.If the credibility is not high,they will be marginalized by the host’s trusted cluster.In particular,a small number of malicious hosts implement malicious behavior,the credibility is rapidly declining,will be isolated,and finally eliminated by the trusted cluster.The more malicious a malicious host commits a malicious act,the faster it is isolated.③New trust partners who meet the trust criteria will continue to join.
According to the above discussion,in each inspection period,the direct experience data of the hostHato the hostHxcan be collected,and the recommended data {D1,D2,...,Dk} ofHxcan be obtained by querying the third party{H1,H2,...,Hk}.Comparing the difference between the direct empirical dataDaand the recommended data {D1,D2,...,Dk},the direct trust degree {T1,T2,...Tk} of the recommender {H1,H2,...,Hk} is adjusted.The adjustment method is:if (Da,Dk) has a good consistency,then increase the direct trust ofMk; otherwise,the direct trust ofMkwill be reduced.This adjustment has an isolated effect on maliciously recommended hosts that intentionally provide high recommendation and low recommendation values [44,45].The specific algorithm is as follows:
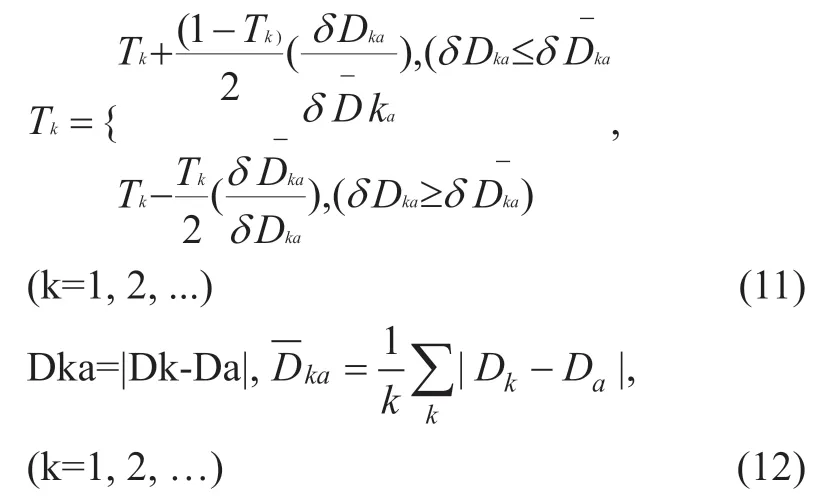
Based on the direct trust threshold (Tx-dir>T0) and the recommended trust threshold (Tx-rec>T0),the trusted host list is selected,and the host with the bad recommendation behavior can be further analyzed by using the above algorithm.
3.4 Comprehensive calculation of trust
The accuracy of the measurement,evaluation and prediction of the trust level of the interactive host in the mobile agent system is the basis for optimizing the new management.More generally,consider both direct trust data and recommended trust data.A more reasonable algorithm is to comprehensively calculate the direct trust degree and the recommended trust degree of the obtained hostHk,and finally obtain the comprehensive evaluation result of the trust degree of the hostHato the hostHk.Sections 3.3 and 3.4 discuss the calculation and update of recommended trust levels and direct trust levels,respectively.On this basis,this section studies the comprehensive calculation method of trust degree and the control problem of trust evolution speed [46].
Considering the direct trust levelTxdir-ofHatoHx,and the recommended trust levelTxrec-ofHxcollected byHa,define a variable that comprehensively measures trust,called “Trust Degree”.“Trust Degree” is used to quantitatively represent the trustworthiness of interactive hosts in a mobile agent system,which means the possibility that hostHainteracts with another hostHxin a given environment to obtain a positive result (trust:Tx=1).Txis a comprehensive measure of trust that is used to quantitatively evaluate the current level of trustworthiness of an entity in a mobile agent system and to predict the degree of trust in the next interaction with that entity.The following is a “trust” comprehensive calculation process.
During the same study period,the direct trust levelTxdir-and the recommended trust strengthTxrec-are weighted and summed,where ρ is the confidence coefficient.
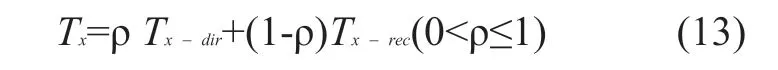
The choice of the confidence factor ρ is determined autonomously by the hostHa.The general situation is:when the hostHais a new member,and has not collected enough confidence data,the weight of the confidence factor is smaller,and as the interaction time increases,the confidence factor gradually increases.The trust calculation for hostHxis closely related to the behavior of hostHxin a different environment (or context context).The degree of trustTxis changed with time frames.The trust degree calculated by the latest trust data in the current time frame is used to predict the interaction of the interaction result in the next time frame,expressing a possibility rather than an inevitable result.
The degree of trust is updated according to the algorithm given by equation (14).The algorithm implements two functions:first,if entityHarepeatedly interacts with entityHxand finds thatHxcontinues to maintain good behavior (affirmative event),Hx’s trust degreeTxwill continue to grow,tending to a maximum of 1,and if entityHxhas malicious behavior,its trust will drop rapidly; second,if there is a large change in the degree of trust between time frames n-1 and n,this large amount of changeHxnwill have a large effect,and vice versa.στ() known as the coefficient update control the update speed of trust.
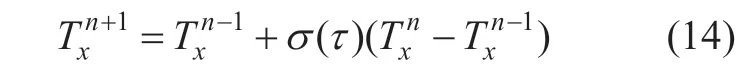
Further discussion of ρ in equation (13) is as follows [40-43]:
Case 1:If the hostHais a very confident,it can only be based on its experience of direct trust evaluation and forecast data,namelyTx=Txdir-,ρ=1.
Case 2:On the contrary,if it is not a very confident host,it can only recommend the use of the data evaluation and prediction of confidenceTx=Txrec-,ρ=0.If you are a member of a new system,it had to useTx=Txrec-,ρ=0 host of interactive forecasting trust,then the definition of initial direct trust to recommend a new hosttk0=0.5(k=1,2,...),and initial confidence coefficient ρ = 0,ρ andtk0with the increase in the number of interactions is updated.
Case 3:In general,the rational use and that the use of formula (13) to predict the level of trust entities.Now confidence factor ρ is defined in accordance with Equation (15) is calculated,whereIτis the number of interactions,and (a,b) is the designated constant,according to the trust needs to choose.With the growth of the number of interactions,ρ tends to a,(a,b) control of the ρ and maximum growth rate.
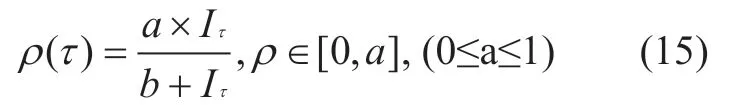
Case 4:In equation (14),Txis an important factor in the choice of weights to consider is the trend should rise slowly,declining rapidly features.This feature of human society and the trust relationship is very similar characteristics,rising slowly to encourage the host through a long,sustained malicious entity.For example,certain entities in several successive time frame to keep a good record of trust,and then suddenly malicious acts get some benefit,both to the interactive fatal losses.σ parameter selection in accordance with formula (16).
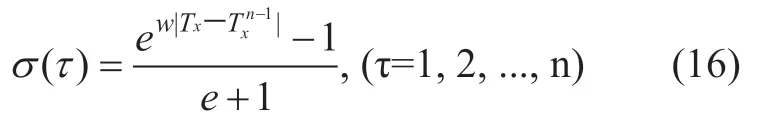
wupdate speed control parameter.Two adjacent time frame,calculate the incremental △Txtrust influence of a time frame.In the simulation experiment,we will examine trends σ (τ) of.
IV.SIMULATION EXPERIMENT ANALYSI
The key properties and parameter selections of equations (1) to (16) given in the above dynamic trust metrics and evaluation methods are verified by a series of simulation experiments [47-50].
4.1 Experimental conditions
Experiment 1 examines the algorithm of equation (1),and the result is shown in figure 2.Take hostHato investigate multiple interactions withHxas an example to illustrate [44]:The more bad interactions of hostHx,the higher the value converted to the underlying trust dataDax.IfHxalways maintains good behavior,when the interaction time reaches τ=50 frames,the value ofDaxis almost equal to 1; conversely,the more bad interactions of hostHx,the lower the value converted to the base trust dataDax.If the bad behavior persists,the value ofDaxis almost equal to 0 when the interaction time reaches τ=50 frames.If the host’sHxinteraction behavior is mixed,the value ofDaxfluctuates around 0.5.Therefore,Daxin equation (1) can correctly reflect the degree of behavior ofHain the series of interactions with hostHx.When K does not understandHx,HaconsidersDax= 0.5.
Experiment 2 examines the algorithm of equation (5),and the result is shown in Figure 3.Let the trust demand threshold beTo,and let v=To,you can see the change of the direct (or recommended) trust degreeTxof the hostHxwhen calculating the base value v (depending on the collected data is direct or recommend trust data).It can be seen that the higher theTovalue,the higher the expectation requirement for the host satisfyingTx>To,and the fewer the number of hosts satisfying the condition.For example,when the calculation base value v=trust thresholdTo=0.8,it can be seen from figure 3 that only the candidate host whose mathematical expectation value of the host interaction behavior μ>0.6 can be included in the trusted interaction object.
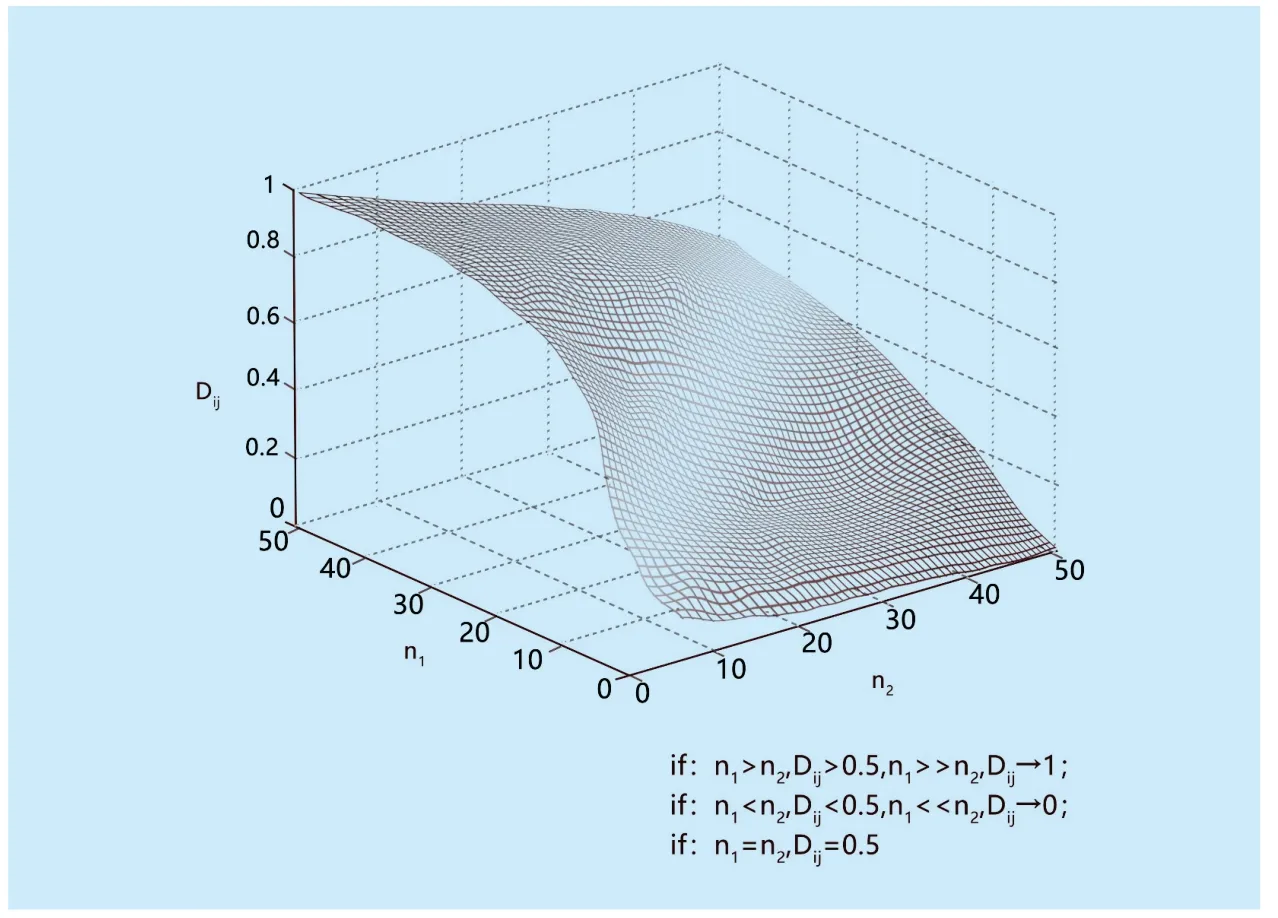
Fig.2.Verify Dij(n1,n2),(t=1,2,…,50)
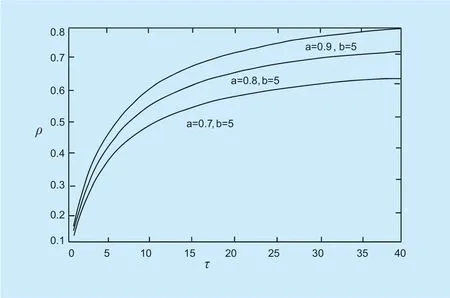
Fig.3.The relationship between the degree of Hx trust and the mathematical expectation of its behavior at different v values.
Experiment 3 verifies the formula (15),and the result is shown in figure 4.The main consideration here is that if the hostHais a new member,it wants to interact withHx.Since there is no direct empirical data,the initial value of the confidence factor is 0,and the trust information must first be collected from the third-party entity.As the interaction experience increases,the confidence factor gradually increases.(a,b) is a pair of constants,a is the maximum confidence factor,and b is used to control the growth rate of the confidence factor according to different situations.The experimental results show that when (a,b) takes different values,when the number of interactions betweenHaandHxincreases gradually,the confidence coefficient ρ gradually increases smoothly,and the confidence coefficient approaches the maximum value.In the experiment,three sets of data were selected for comparison [45].When the time frame τ=40,the confidence coefficient almost reached their respective maximum values.
Experiment 4 verifies the formula (16),and the results are shown in figure 5.The amount of change between the two time frames is 0 <△Tax<1,and the parameter w controls the evolution speed ofTax.The experimental results show that when the coefficient w=1,σ(τ)min=0,the evolution rate is the slowest,and σ(τ)max=0.46 has the fastest evolution speed.At this time,the maximum influence of △Tijon theTaxvalue in the next time frame is 0.46.As can be seen from Figure 9,when the parameter is selected w = 2,the trust will get faster the speed of evolution,but the stable region of the algorithm △Tmaxis around 0.77.When choosing w = 1.5,△Tmaxis around 1.If compared with w=2,Taxhas a slower rate of evolution; if compared with w = 1,Taxhas a faster rate of evolution.
The experimental results obtained according to the trust degree synthesis algorithm (14) are shown in figure 6.It can be seen that the algorithm has a slow rising fast falling feature.If hostHxcontinues to maintain good interaction behavior for multiple time frames,hostHxcan gradually gain high trust; after obtaining high trust,Hxsuddenly implements malicious behavior in the interaction to obtain illegal benefits,his trust will decline rapidly,be seen byHaand spread through trust,so that the trusted group is isolated [46].IfHxwants to restore the higher trust he once had,it needs to make long-term efforts to maintain good interactions in order to restore his “trust”.This main feature of the trust degree comprehensive calculation algorithm effectively suppresses the malicious behavior of the host.
Equations (11) and (12) give an algorithm for hostHato isolate the hostMk(k = 1,2,...) with bad or malicious recommendation behavior based on direct empirical data on hostHx.The simulation experiment results are illustrated as follows in Figure 7,Figure 8,and Figure 9:it can be seen from Figure 7 that the recommendation data of the recommenderM3to the hostHxis the best with the direct empirical data of the hostHatoHx.The recommendation data of recommendersM1andM2is inconsistent with the direct empirical data ofHa,which is much higher than and directly below the direct empirical data ofHa.Depending on the algorithm used,Hacan conclude that:M3is more believable,andM1andM2may be suspected of malicious recommendations.
Based on the direct recommendation data ofHa,the degree of deviation of the recommended data ofM1,M2andM3is further examined.and the degree of deviation from the recommended data,the results shown in figure 8.As can be seen from figure 8 in a plurality of successive cyclesand study within the first few cyclesafter several cycleswhereis the mean difference.Depending on the algorithm used,Ha’s trust in recommending hostM3will increase,while trust inM1andM2will decrease.
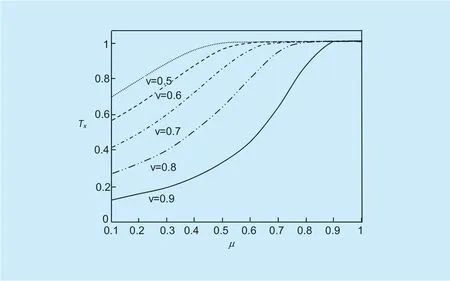
Fig.4.ρ (τ) changes in the trend.
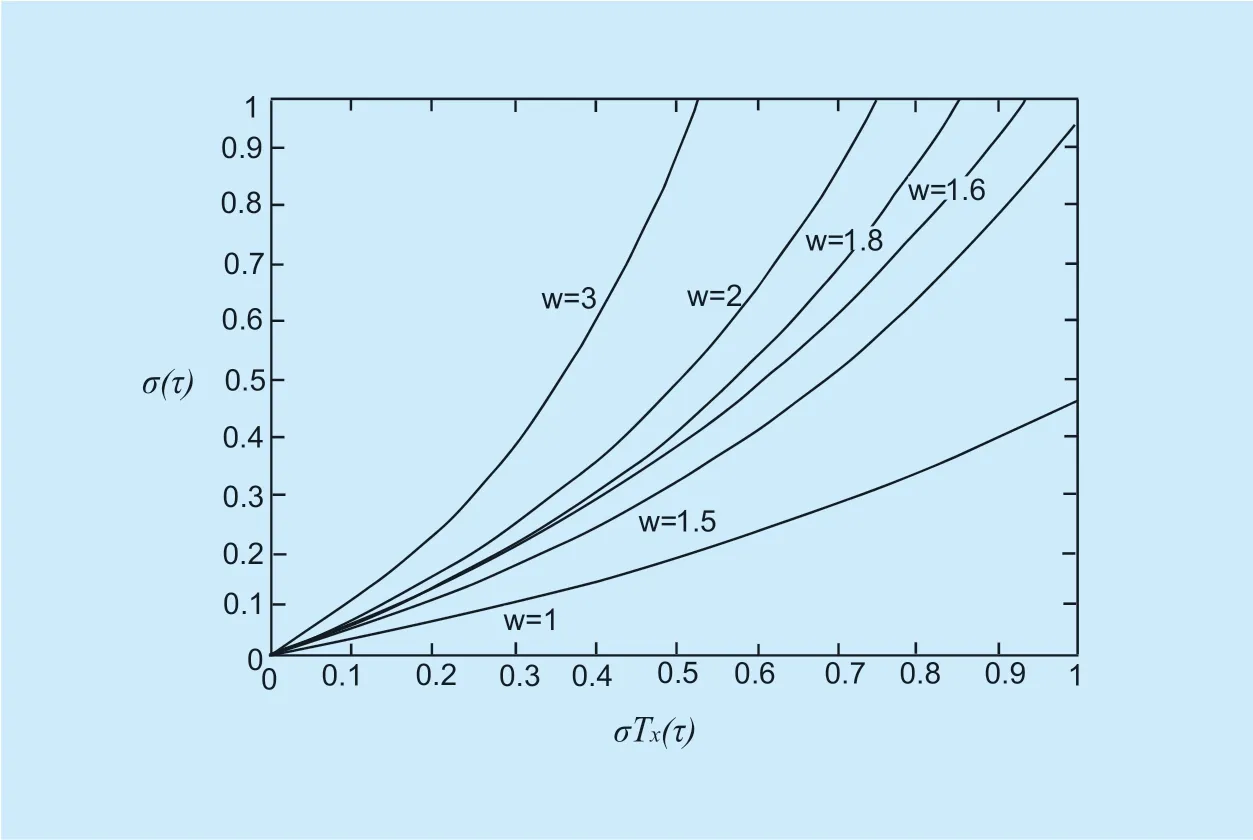
Fig.5.Change trend of σ (τ) at different w.
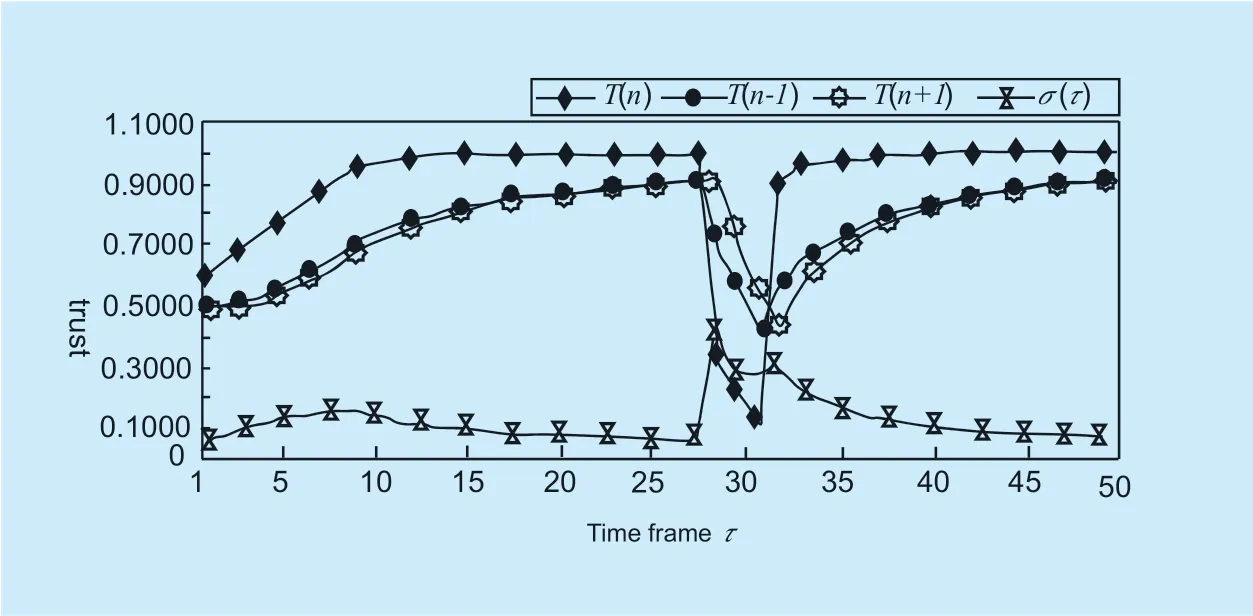
Fig.6.Changes in trust trends (w=1.5).
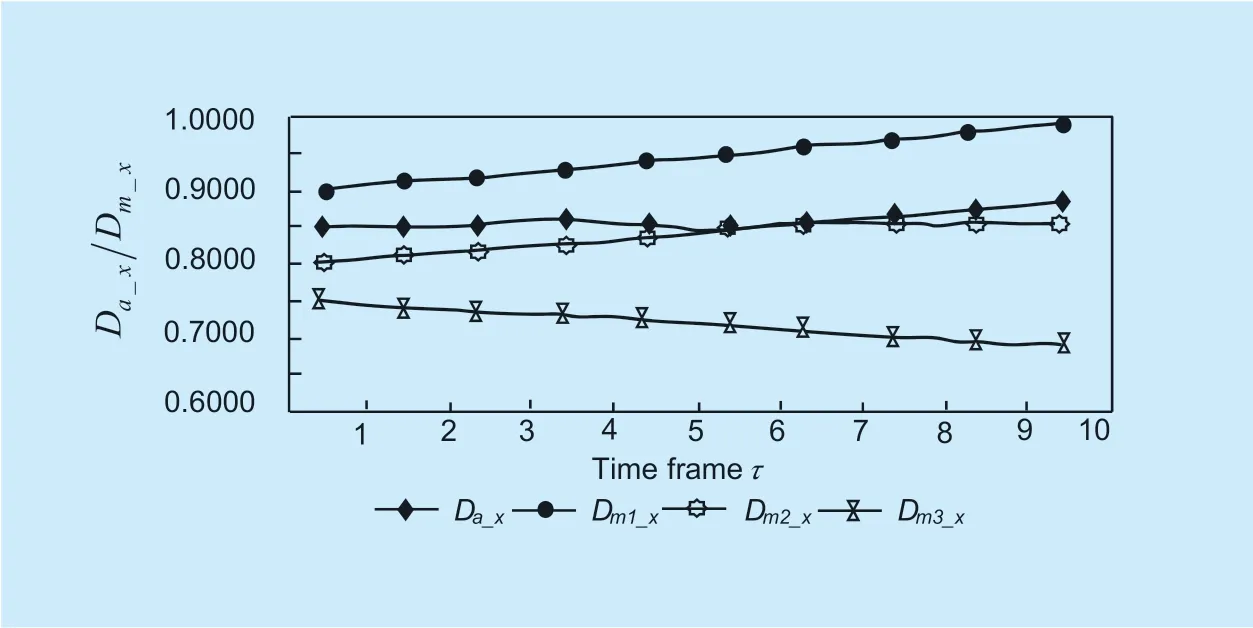
Fig.7.Comparison of direct empirical data with recommended dat.
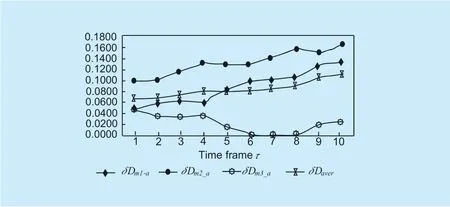
Fig.8.Differences between direct empirical data and recommended data.
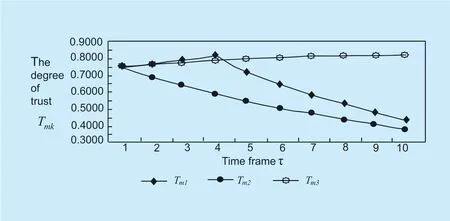
Fig.9.The effect of the difference between the direct empirical data and the recommended data on Tmk.
The effect of the difference between the direct empirical data and the recommended data onTmkis shown in Figure 9.It can be seen from figure 9 that according to equations (11) and (12),in the course of the investigation,the recommendation data of the recommender 3 to the hostHxand the direct empirical data of the hostHatoHxare the best.HostHa’s direct trust to him gradually increases,and the degree of improvement depends on the degree of consistency.The higher the consistency,the faster the increase; the recommendation data of recommendersM1andM2is inconsistent with the direct empirical data ofHa.Regardless of the direct empirical data far higher or lower thanHa,the direct trust of hostHais gradually reduced.The magnitude of the decrease depends on the degree of deviation.The greater the degree of deviation,the faster the reduction.Therefore,the functions of the equations (11) and (12) can effectively isolate the malicious recommendation host.
Therefore,the following conclusions can be drawn:the simulation results verify the correctness of the “public letter host selection algorithm”,“isolated malicious recommender algorithm” and “trust level comprehensive calculation algorithm” given in this paper [51-53].It can be used to evaluate the subjective trust status of the host to be interacted in the mobile agent system,and predict the trustworthiness of the host to be interacted in the next time frame.The series of algorithms given can stimulate the trusted host and isolate the malicious host,which has the function of “punishing evil and promoting good”.It can effectively manage the subjective trust dynamic management of the mobile agent system.
4.2 Comparison with Josang Algorithm
Josang constructed a probability deterministic density functionpcdf(r,s) determined by the observed number of positive events r and the number of negative events s in the research literature on network trust [27],which use this function to calculate the probability0≤θ≤1,r≥0,s≥0; where θ is the probability variable) that a network entity will generate positive and negative events.In the mobile agent system,the mobile agent and the source host are trusted and bound,andpcdf(r,s) is replaced by the Gauss distribution probability density function.According to this function,the interaction result of the mobile agent and the execution host is converted into the trust degree.Compared with the pcdf algorithm constructed by Josang,the mobile agent system trust management mechanism proposed in this paper has the following advantages:
4.2.1 Good flexibility
In this paper,based on the algorithm P(v,μ,σ) given by Gaussian probability distribution theory,and then the execution host and mobile agent interaction behavior is quantified as the trust degree calculation,you can choose to calculate the threshold value v.The characteristic parameters (μ,σ) in the algorithm P(v,μ,σ) are mathematical expectation and variance,respectively,which can not only measure the degree of trust of the host,but also indicate the stability of the trust level of the host.According to the algorithm P(v,μ,σ),the recommended trust data and the direct data can be used to calculate the recommendation trust degree and the direct trust degree respectively.On this basis,the comprehensive trust degree calculation is more flexible and expressive.
4.2.2 Targeted
This paper gives an isolated malicious (interactive or recommended) main calculation method based on direct trust,and more prominently determines the subjective trust judgment requirements of the mobile agent system.For the following two points:①HostHxhas no malicious behavior on hostHaand cannot represent malicious behavior on HostHb.The reverse is also true.HostHahas reason to believe that the direct trust toHxis more reliable than the recommended trust.②HostHadetermines whether it is a malicious recommender based on the consistency of the recommended trust and direct trust.The recommender and the low recommender who are too high compared with the direct trust value have malicious recommendation.The host trusts the recommenders who have a good consistency with their direct trust.The isolated malicious host algorithm presented in this paper fully demonstrates the direct interaction experience of hostHaas the reference value,and the effect ofHamalicious host is better.
4.2.3 Self-starting
For the new hostHathat has just joined the mobile agent system,although there is no direct experience data,it can immediately obtain the recommended trust data ofHx,and use the “public mail host selection algorithm” to select the trusted interactive object,which has better self-starting property.
4.2.4 Subjective autonomy
After HostHaaccumulates sufficient direct trust data in the mobile agent system,it can set the trust threshold according to its own trust demand preference,select a set of trusted interactive objects (including the public trust the host,the host and comprehensive self-confidence trusted host),and have better autonomy.
4.2.5 Better dynamic adaptability
Each interactive host can determine whether it is trusted by other hosts(or the host’s mobile Agent),while judging whether it trusts other hosts(see themselves as can beHx).Therefore,it can self-adjust and win more interactors to better adapt to the living environment.
The shortcoming of the model algorithm is that the host’s choice of trust threshold is based on the host’s own trust requirements and preferences.This paper does not further consider the impact of this preference on the stability of the dynamic trust cluster around the host.
V.CONCLUSION
Divide the trust problem in the mobile agent system into objective trust and subjective trust to divide and conquer.Based on the analysis of the use of SPKI related certificates,this paper studies the problem of dynamic management of subjective trust in mobile agent system under the objective trust management framework of SPKI-based mobile agent system.The trust requirement of the entity (host or mobile agent) in the mobile agent system is analyzed,and a subjective trust dynamic management model consisting mainly of three trust components is proposed.Among them,the trust forms a component and completes the collection of trust data; the trust propagation component completes the communication of trust and the exchange of trust data; trusts the evolution component and completes the update of the trust data.The quantitative representation method of trust in the mobile agent system is given.Based on the basic ideas of description and metric trust proposed in the Josang network trust management model,two basic concepts of Evidence Space and Opinion Space are introduced in the mobile agent system.In the fact space of the mobile agent system,the “good or bad result of entity interaction behavior” is transformed into the “level of credibility of the entity” in the concept space.Using Gaussian Probability Distribution Theory,the method of changing the degree of trust of the host in the mobile agent system is given.“Trust” is used to indicate the degree of trust that HostHaconsiders HostHxwithin a specified time frame in the Mobile Agent system to evaluate and predict the next secure interaction with HostHx.A subjective trust dynamic management algorithm is proposed.Finally,through a set of simulation experiments,the feasibility of the proposed algorithm to measure the degree of host trust in the mobile agent system is verified,and the effectiveness of the trust group to improve the security of the interaction in the mobile agent system is verified.
ACKNOWLEDGMENT
This work was supported by the National Natural Science Foundation of China (61772196; 61472136),the Hunan Provincial Focus Social Science Fund (2016ZDB006),Hunan Provincial Social Science Achievement Review Committee results appraisal identification project (Xiang social assessment 2016JD05),Key Project of Hunan Provincial Social Science Achievement Review Committee (XSP 19ZD1005).The authors gratefully acknowledge the financial support provided by the Key Laboratory of Hunan Province for New Retail Virtual Reality Technology (2017TP1026).)
- China Communications的其它文章
- Constructing Certificateless Encryption with Keyword Search against Outside and Inside Keyword Guessing Attacks
- Enhancing Interest Forwarding for Fast Recovery from Unanticipated Data Access Failure in NDN
- EEG Source Localization Using Spatio-Temporal Neural Network
- DDoS Attack Detection Scheme Based on Entropy and PSO-BP Neural Network in SDN
- Customizing Service Path Based on Polymorphic Routing Model in Future Networks
- Energy-Efficient Joint Caching and Transcoding for HTTP Adaptive Streaming in 5G Networks with Mobile Edge Computing

