Multimedia Encryption with Multiple Modes Product Cipher for Mobile Devices
Yi-Nan Lin, Gwo-Jen Chiou, and Victor R. L. Shen
Abstract—The most straight forward method in multimedia encryption is to encrypt the entire stream using standard encryption methods, such as the data encryption standard (DES) or advanced encryption standard (AES). However, in the block ciphering, there exists an attack risk with the weakness of plaintextciphertext pairs (i.e. the plaintext-ciphertext pair problem). Therefore, several modes of operation are proposed to solve the above problem. As we all know,channel hopping can defend illegal listening. Thus, this paper has proposed a multimedia encryption scheme with the multiple modes product cipher (MMPC) for mobile devices. In practice, MMPC can increase the security level in wireless multimedia networks. The results of Android applications (Apps) system have shown that the overhead of MMPC is decreased by 2%in throughputs, if it is compared with that of the other straightforward mode ciphers.
1. Introduction
In the wireless networks, the confidentiality of private information is protected[1]-[3]. A block cipher itself only allows the encryption to be performed with a single data set in the cipher’s block length. Block encryption may be vulnerable to ciphertext searching, replaying, insertion, and deletion because it encrypts each block independently. Its disadvantage is that identical plaintext blocks are encrypted into the identical ciphertext blocks.
Unfortunately, non-feedback conventional block ciphers do not hide data patterns well. Non-feedback conventional block ciphers have plaintext-ciphertext pair problems with the disadvantages of limiting block region scrambles. A crack can use it to perform a known-plaintext attack. In some senses, it cannot provide serious message confidentiality. A nonfeedback conventional block cipher is not recommended at all for use in cryptographic protocols.
As the images are shown in Fig. 1, the original image in a pixel-map version in Fig. 1 (a) is encrypted with a electronic codebook (ECB) mode to create the encrypted image in Fig. 1 (b). Following the original image or the encrypted image is the number of colors used in the image and the image’s histogram. Fig. 1 (b) represents the ECB DES encryption of the original image using the key 1234567890ABCDEF.
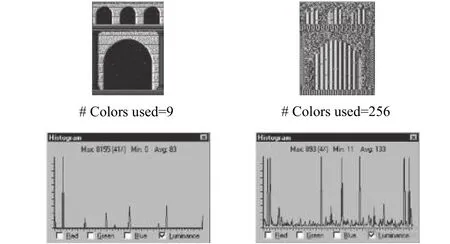
Fig. 1. One sample image with an image resulted from its encryption: (a) original image and (b) ECB data encryption standard (DES) encryption of the original image.
The non-feedback ECB mode can leave plaintext data patterns in the ciphertext. In Fig. 1, a striking example of the degree can be seen when the electronic codebook mode is used to encrypt a bitmap image which contains large areas of uniform color. The overall image may still be discerned as the pattern of identically-colored pixels in the original image remained in the encrypted version while the color of each individual pixel is encrypted. Block cipher modes of encryption different from the non-feedback ECB mode have been suggested to remedy these drawbacks. The straightforward block ciphering mode of operation (also called ECB mode) is not considered to be secure, because it is vulnerable to statistical attacks[4].
The standard modes of operation are described in the literatures[5]such as non-feedback electronic codebook (ECB)mode, cipher block chaining (CBC) mode, output feedback(OFB) mode, and cipher feedback (CFB) mode. They can all provide confidentiality. But how to choose an appropriate operation mode becomes an important issue. Different modes have different characters. For example, both CFB and OFB can be designed to operate without padding with bit-based size keystream output. BothCBCand CFB can self-synchronize to avoid the channel noise error propagation.For CFB and OFB,their encryption and decryption need only one encryption module to reach both usages. In addition, only the forward cipher function of the block cipher algorithm is used in both encryption and decryption, without the need for the inverse cipher function[1].
The rest of this paper is organized as follows. Section 2 contains the review of ciphers and video encryption algorithm(VEA). Section 3 describes how to make multiple modes ciphering with a secured mode sequence and the multiple modes product cipher (MMPC). Section 4 is the security analysis. Section 5 contains the practical implementation of mobile devices and performance evaluation. Finally, the conclusion is remarked in Section 6.
2. Literature Review
Currently, data confidentiality is one of the security services in cryptography. The major concept in information security is to continue to improve encryption algorithms. There are two major types of encryption algorithms in cryptography,namely, symmetric-key algorithms[6],[7]and public-key algorithms[8],[9]. Symmetric-key algorithms also referred to as conventional encryption algorithms or single-key encryption algorithms are a class of algorithms that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. So far, it has remained the above two types of encryption algorithms most widely used.
Symmetric-key ciphers are a class of ciphers in cryptography. They use trivially related cryptographic secret keys for both encryption of plaintext and decryption of ciphertext. Symmetric-key cryptography is here to be contrasted with asymmetric-key cryptography. Symmetric-key cryptography is the only one type of encryption in use prior to the development of asymmetric-key cryptography[10],[11]. The advanced encryption standard (AES)[12]-[14]algorithm approved by National Institute of Standards and Technology (NIST) in December 2001 uses 128-bit blocks.
Multimedia data sets have special characteristics, such as coding structure, large amount of data, and real-time constraints. A multimedia stream is quite different from the traditional textual data because it has a special data structure and is also compressed[15],[16]. To provide the security requirements of confidentiality, multimedia security often uses encryption software to ensure the safety of computational complexity in the multimedia. Notice that the common thing between compression and encryption is that both try to remove redundant information[17].
There are several encryption algorithms, such as the naive algorithm and selective algorithm to secure multimedia contents. The naive method is to encrypt the entire multimedia contents using standard encryption methods such as DES and AES. Each of them has its strength and weakness in terms of the security level, speed, and resulting stream size metrics. For example, in the Moving Picture Experts Group (MPEG)contents, the basic selective algorithm is based on the MPEG IPB frames structure. Encrypting only I-frames does not provide a satisfactory secure level, because great portions of the video are visible, partly dependent on the inter-frame correlation and mainly dependent on the unencrypted I-blocks in P-frames and B-frames[18].
Zigzag-permutation algorithm[19], where the encryption is an integral part of the MPEG compression process, uses a random permutation list to map the individual 8×8 block to a 1×64 vector in “zigzag”. It consists of three steps: Step 1,generate a permutation list with cardinality of 64. Step 2, do the splitting procedure. Step 3, apply the random permutation list to the split block.
In 1998, [17] described, evaluated, and compared five representative MPEG encryption algorithms with respect to the encryption speed, security level, and stream size. It indicates that there are trade-offs among performance evaluation metrics.The choice of encryption algorithm will depend on the security requirements of the multimedia applications. Study on MPEG properties and its statistical behavior lead to the video encryption algorithm (VEA). In Fig. 2, VEA is mainly interested in dealing with the MPEG stream in a byte-by-byte fashion due to the following reasons: 1) It is easier to handle data byte-wise; 2) a single byte is meaningless in multimedia stream because, normally, the multimedia content is encoded in several bytes. This is different from text information where one byte or character has its own meaning. Therefore, VEA is used to convert an MPEG bit stream into a byte stream. And each unit has an integer between 0 and 255.
3. MMPC
The idea of using multiple confidentiality modes with a secured mode sequence to increase the security level of multimedia is described in this Section, . The traditional block ciphers have a plaintext-ciphertext pair problem with the disadvantages of limiting block region scrambles. In the literature[5],[20], standard operational modes for data confidentiality are specified using any approved block cipher,such as the AES algorithm[12]-[14]. The operational modes are ECB, cipher block chaining (CBC), cipher feedback (CFB),output feedback (OFB), and counter (CTR). These standard operational modes are used to provide the data confidentiality function. An initialization vector (IV) or initial counter value must be required for CBC, CFB, OFB, and CTR modes,performing the encryption operation at the beginning of any communication session and the decryption operation at the end.
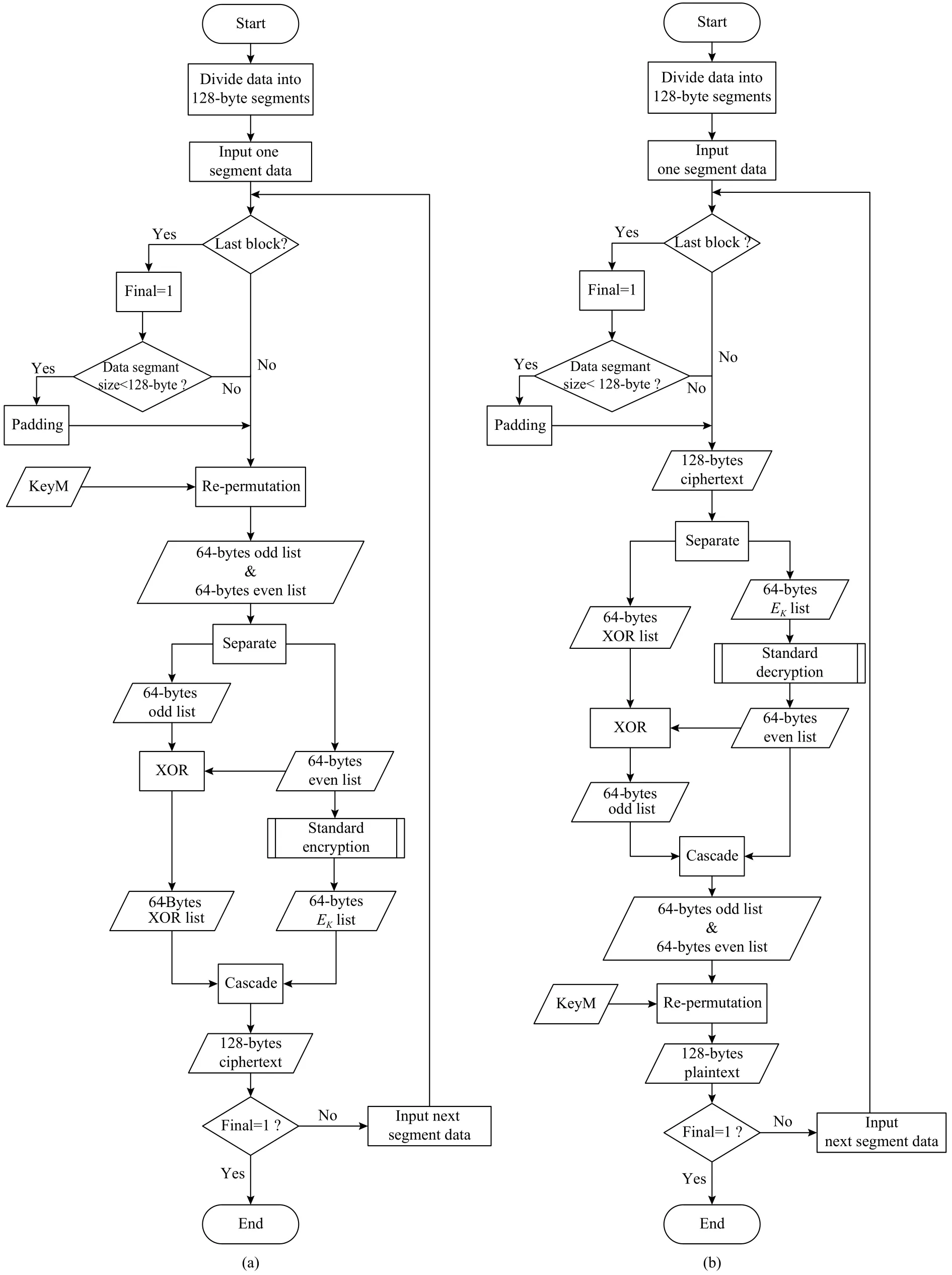
Fig. 2. Flowchart of encryption and decryption for VEA[17]: (a) encryption and (b) decryption.
The detailed descriptions are shown in the following formulas.
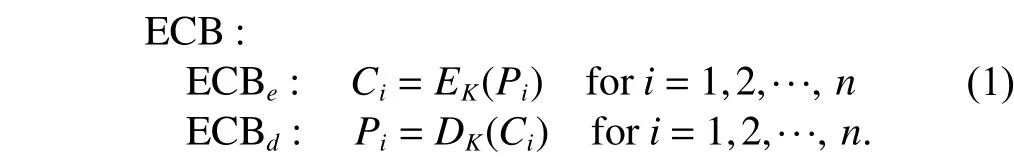

3.1 Multiple Modes Ciphering
The above cipher modes of operation can dynamically switch among them. We use a finite state machine (FSM) to explain the state between block operations in Fig. 3. The FSM means that a block cycle is changed. In general, the ECB operation mode continues to be used in a session. CBC, CFB OFB, and CTR are the same as shown in Fig. 3 (a). Fig. 3 (b)shows the multiple modes ciphering, which is proposed to achieve dynamic changes. The outside looking is as simple as the upper part although the inside operations are all busy and dynamic.
We take a mode sequence as an example in Table 1 and Fig. 4. The control sequence is synchronous between encryption and decryption. It is pre-shared as secret and secure information.However, the additional cost of a target control sequence can be flexibly reduced according to the practical requirements of security. Our idea can extend to contain and spread to other confidentiality modes which are not yet included in the standards[5],[20].
The improvement of multimedia security is based on a secure secret. This secret of mode sequence can be created by a synchronous pseudo-random number generator.
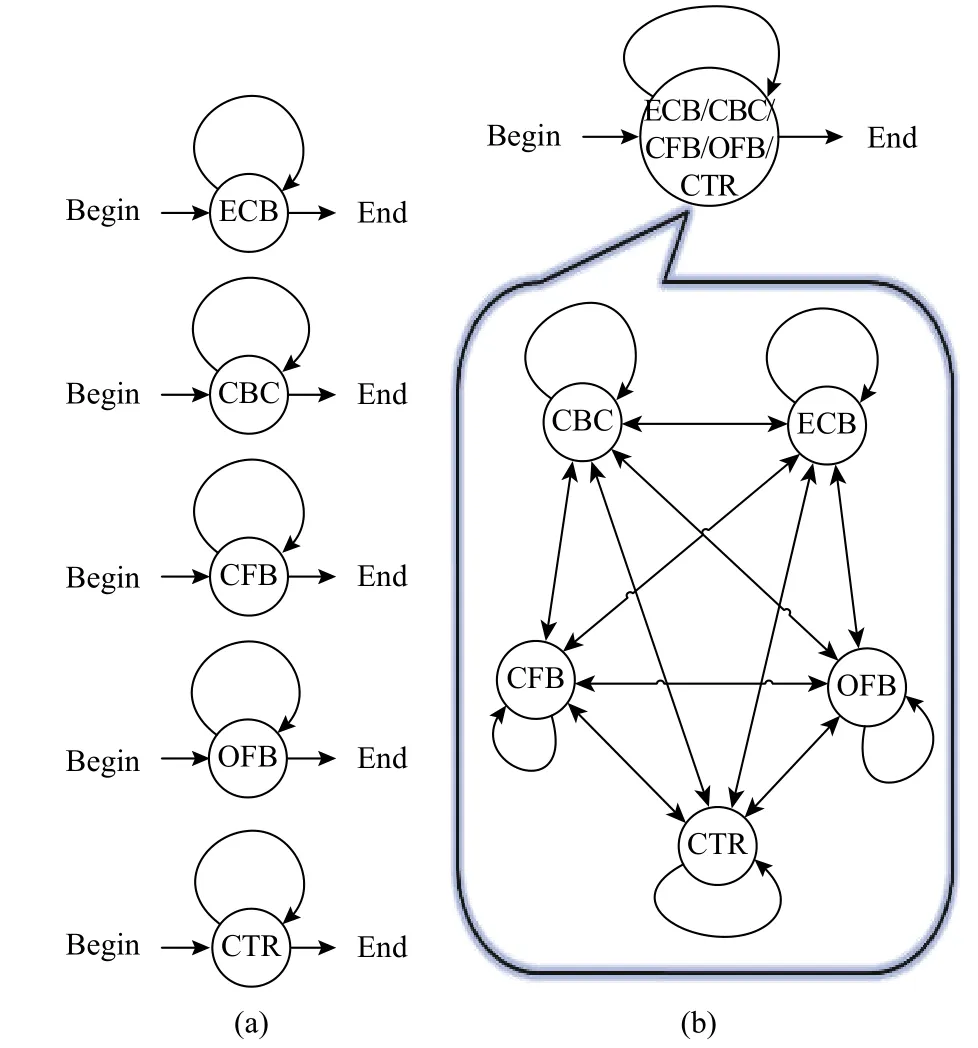
Fig. 3. Crypto task in one single session from the beginning to the end: (a) in general usage and (b) multiple modes ciphering.
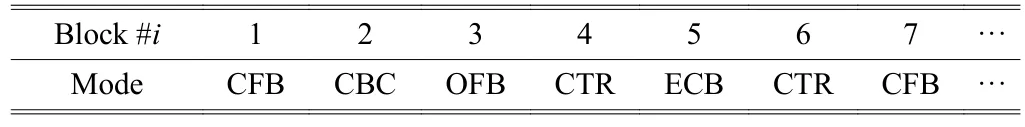
Table 1: One example of a pre-shared mode sequence.

Fig. 4. Crypto task flow diagram of a mode sequence in Table 1.
3.2 Synchronizer and Mode Selection Schemes
Two schemes are designed for mode selection. The current mode change depends on three choice bits of the last plaintext.For example, if the choice bits are 0012, then we make the current mode changed to the CBC mode. Therefore, 0002denotes ECB, 0012denotes CBC, 0102denotes CFB, 0112denotes OFB, and 1002denotes CTR. The proposed exchange mechanism is to choose 3 bits obtained from the last block plaintext before operating the current block. The mode change depends on the 3 choice bitsS, i.e.S0S1S2.
First, an easy change is done by using three bits of plaintext from the previous block plaintext before operating the current block. We define the current mode change, which depends on the msb./lsb./middle three bits of the last plaintext. The mode change depends on the partial 3-bit message:
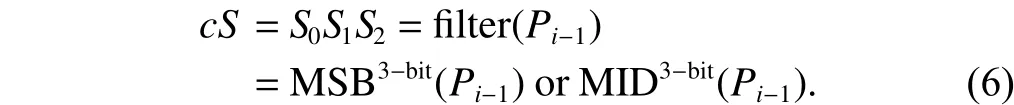
We can improve the easy change by using the Hash functions. This case results in hard scrambled performance and an extra cost of the resource.
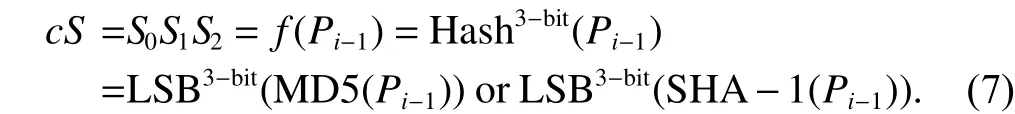
Also, we use a synchronous pseudo random number generator (PRNG) as a synchronizer of multiple modes ciphering. Here, we can use another PRNG as the keystream generator of a stream cipher. A stream cipher can be a second cipher of a product cipher, and the first cipher of this product cipher is the multiple modes cipher. A synchronous PRNG is used as a synchronizer of multiple modes ciphering and the keystream generator of a stream cipher for product ciphering.
4. Security Analysis
The idea of block ciphering modes is depicted in Fig. 5.Crossing the horizontal axis “time”, MMPC makes ciphering modes between the previous and the next block ciphering procedures different.
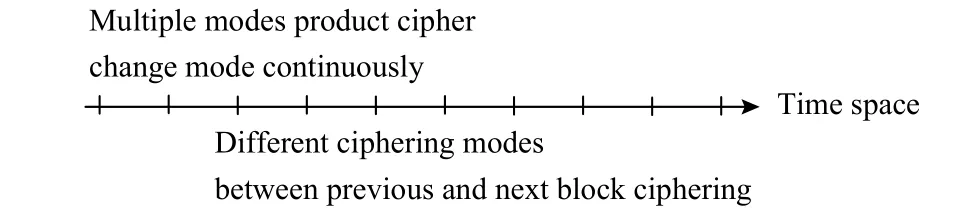
Fig. 5. Multiple modes ciphering.
The improvement of security is based on a secure secret.The extra secure mode sequence can be created by a synchronous PRNG, which is used as a synchronizer of multiple modes ciphering and the keystream generator for product ciphering together with MMPC.
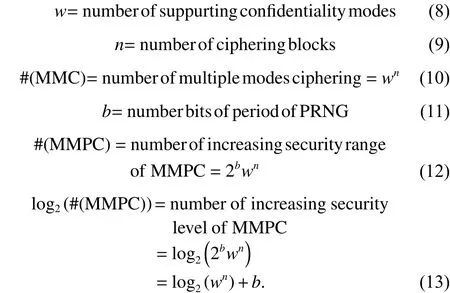
As we all know, combining #wconfidentiality modes with an MMPC which has #nciphering blocks, there arewnkinds of multimode combinations. Therefore, combining all five standard confidentiality modes withnciphering blocks, there are 5nkinds of multimode combinations.
When the PRNG with a maximumbbits of period is used as a synchronizer of multiple modes ciphering and the keystream generator for product ciphering, the increasing security range of MMPC with multiple modes ciphering and product ciphering has 5n×2bkinds of resulting combinations.The increasing security level of MMPC has log2(5n×2b)=log2(5n)+bbits.
5. Implementation
In wireless networks, the confidentiality of private information is protected by the algorithms[1]-[3]. A block cipher itself only allows the encryption to be performed with a single data set in the cipher’s block length. Block encryption may be vulnerable to ciphertext searching,replaying, insertion, and deletion because it encrypts each block independently.
We have programed a multiple modes AES-128 ciphering App on the IDE platform in eclipse JUNO 64-bit version[21].There are comparison results from three different mobile devices, which are running this Android App. The testing performance and specifications of each mobile device are described in Table 2. We use two multimedia files as the test samples. The characteristics of our multimedia test files are shown in Table 3.
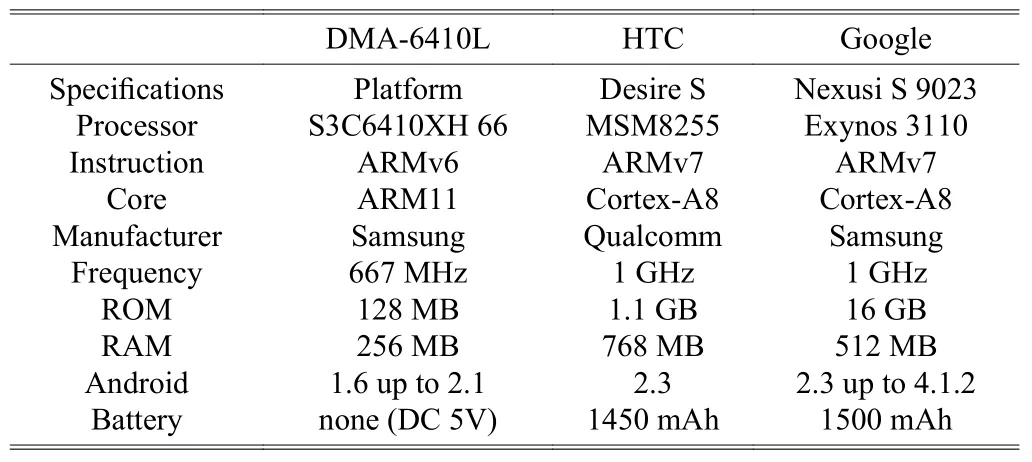
Table 2: Specifications of our mobile devices
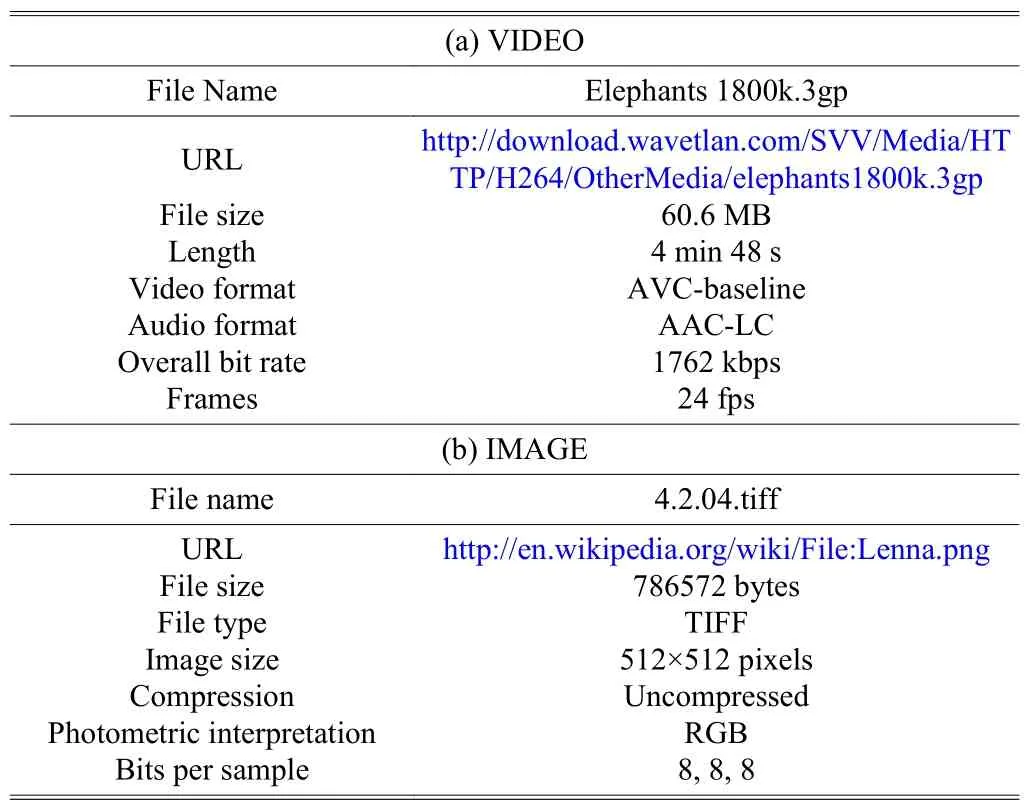
Table 3: Characteristics of our samples
We test one hundred times on each file and calculate the average processing time. The processing results from straightforward ciphering are shown in Table 4. The processing results from multiple modes ciphering are shown in Table 5.Fig. 6 shows that the multiple modes ciphering throughputs are set between 2.5 Mbps and 53.7 Mbps on the current general class of mobile devices. Fig. 7 shows the MMPC encryption results.
Symmetric-key encryption algorithms can use either stream ciphers or block ciphers. Block ciphers take a number of bits to be encrypted as a single unit, padding the plaintext so that it can be a multiple of block size. A block with 64 bits has been commonly used. The AES[12]-[14]algorithm approved by NIST in December 2001 uses a block with 128 bits. Many modern block ciphers have invertible functions different from other non-invertible functions.
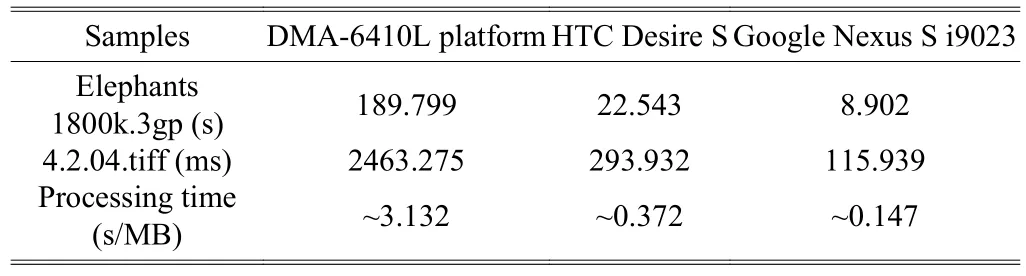
Table 4: Simulation results from straightforward ECB mode

Fig. 6. Throughput performance from the results in Table 4 and Table 5.
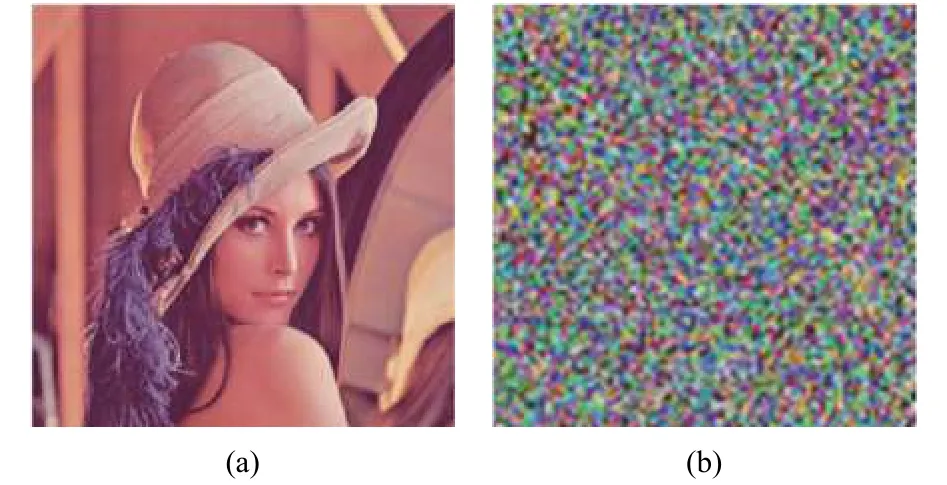
Fig. 7. MMPC encryption results: (a) original image and (b)encrypted image.
We have implemented the encryption and decryption schemes on the IDE platform in the eclipse JUNO 64-bit version[21]: i) the straightforward ECB mode AES, ii) the CBC mode AES, and iii) our MMPC AES. Then, the encryption and decryption schemes with two samples are tested. And three same kinds of mobile devices are used for running the implemented Android App. Our encryption results are better than those from the existing triple-DES and AES.
As shown in Table 6, the straightforward ECB mode AES has the maximum execution time. The CBC mode has a 101.1% speed overhead if it is compared with the straightforward ECB mode AES. Our MMPC AES increases speed overhead only by 0.2% on average if it is compared with the CBC mode AES. The secret key expansion overhead of our scheme is a mode operation key, which can be a secret mode sequence, a constant secret with 128 bits of pseudo random number seed, or just a secret initial vector (IV) with any digital content size.
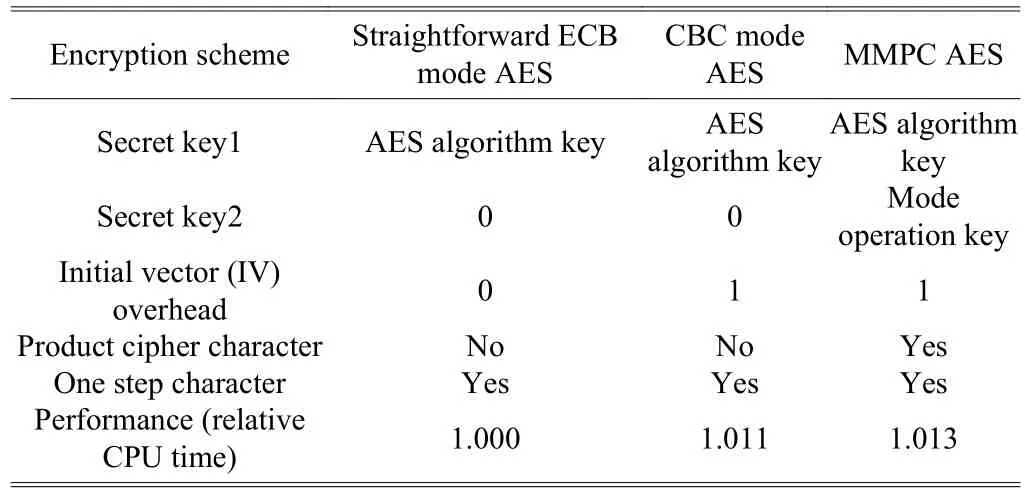
Table 6: Comparisons of our MMPC with others in AES
6. Conclusions
Most of the contents in wireless networks are the products obtained from social applications or multimedia applications.Therefore, people can frequently share their information with one another, especially including large scale data sets, such as video streaming. In this paper, we have proposed an approach to improve multimedia security with multiple modes ciphering for mobile devices. The contributions of this paper are stated as follows:
1) The seamless changing confidentiality modes of ciphering operation are easily used to selectthe standard modes.
2) In the multimedia encryption software, our Android App system has shown that an overhead of multiple modes ciphering is estimated from 1.3% to 2%. It is just a certain decreasing throughputs if it is compared with the straight for ward ciphering.
3) MMPC can increase an acceptable security level in wireless multimedia networks.
In order to increase the feasibility of our approach, e.g.more tested mobile devices, the proposed App system needs to be further improved in the future.
 Journal of Electronic Science and Technology2018年2期
Journal of Electronic Science and Technology2018年2期
- Journal of Electronic Science and Technology的其它文章
- Improved Method of Contention-Based Random Access in LTE System
- Model-Based Adaptive Predictive Control with Visual Servo of a Rotary Crane System
- Systematic Synthesis on Pathological Models of CCCII and Modified CCCII
- Secure Model to Generate Path Map for Vehicles in Unusual Road Incidents Using Association Rule Based Mining in VANET
- Mining Frequent Sets Using Fuzzy Multiple-Level Association Rules
- Improvement of an ID-Based Deniable Authentication Protocol
